Access control in organizations
You can set up Single Sign-On (SSO) to be able to map access control rules from your organization’s Identity Provider.
Advanced and more fine-grained access control can be achieved with Resource Groups.
The Resource Group feature is part of the Enterprise Hub.
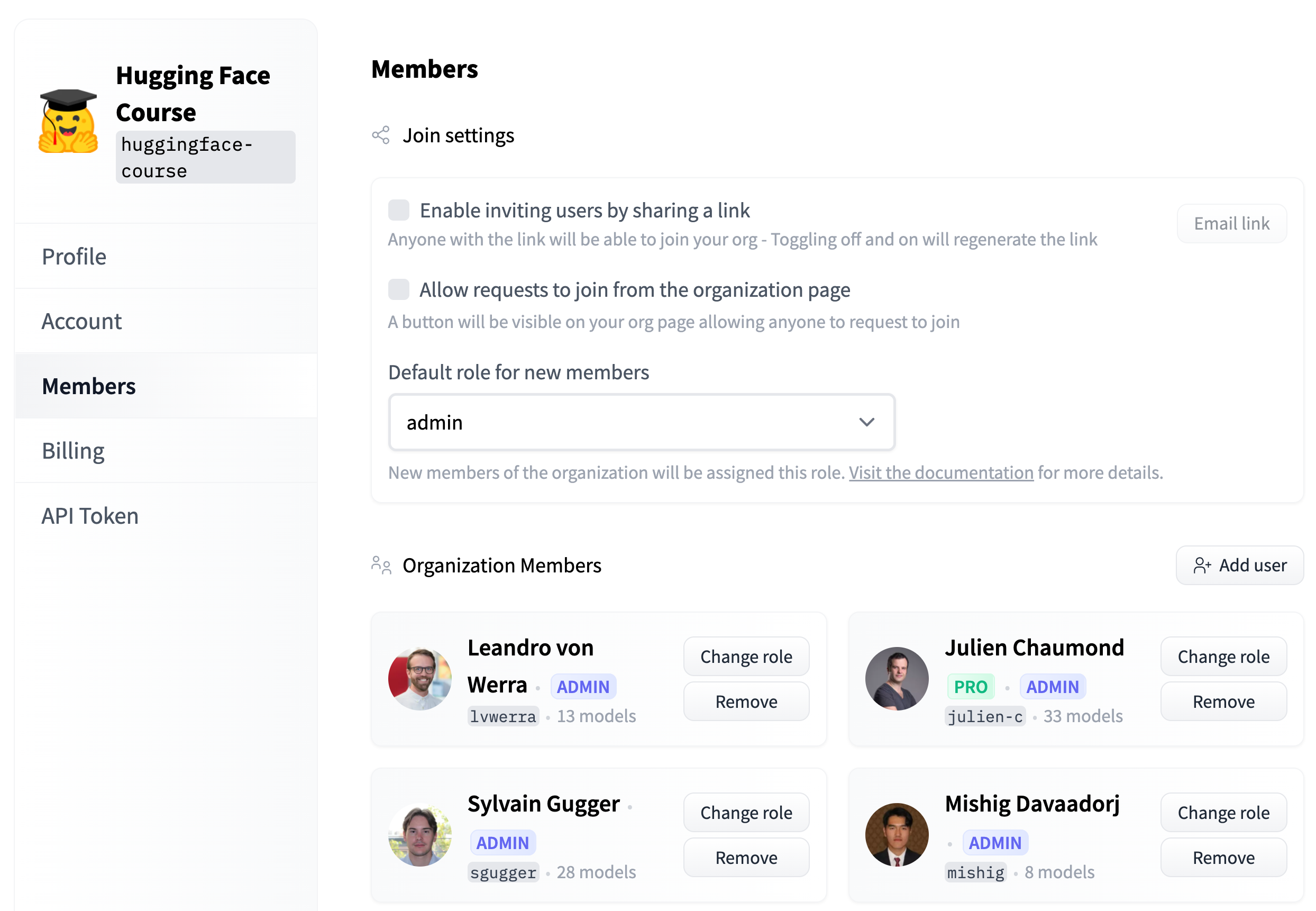
Members of organizations can have four different roles: read, contributor, write, or admin:
read: read-only access to the Organization’s repos and metadata/settings (eg, the Organization’s profile, members list, API token, etc).contributor: additional write rights to the subset of the Organization’s repos that were created by the user. I.e., users can create repos and then modify only those repos. This is similar to thewriterole, but scoped to repos created by the user.write: write rights to all the Organization’s repos. Users can create, delete, or rename any repo in the Organization namespace. A user can also edit and delete files from the browser editor and push content withgit.admin: in addition to write rights on repos, admin members can update the Organization’s profile, refresh the Organization’s API token, and manage Organization members.
As an organization admin, go to the Members section of the org settings to manage roles for users.
Viewing members’ email address
You may be able to view the email addresses of members of your organization. The visibility of the email addresses depends on the organization’s SSO configuration, or verified organization status.
- If you verify a domain for your organization, you can view members’ email addresses for the verified domain.
- If SSO is configured for your organization, you can view the email address for each of your organization members by setting
Matching email domainsin the SSO configuration

